Page 1

Page 2

User’s Guide
Network Blaster Wireless USB Adapter CW2230
Information in this document is subject to change without notice and does not represent a commitment on the part of Creative
Technology Ltd. No part of this manual may be reproduced or transmitted in any form or by any means, electronic or mechanical,
including photocopying and recording, for any purpose without the written permission of Creative Technology Ltd. The software
described in this document is furnished under a license agreement and may be used or copied only in accordance with the terms of
the license agreement. It is against the law to copy the software on any other medium except as specifically allowed in the license
agreement. The licensee may make one copy of the software for backup purposes only.
The Software License Agreement is found in a separate folder on the Installation CD.
Copyright © 2004 Creative Technology Ltd. All rights reserved.
Version 1.0
August 2004
The Creative logo and Blaster are registered trademarks, and Network Blaster is a trademark of Creative Technology Ltd. in the
United States and/or other countries. Microsoft, MS-DOS, Windows and the Windows logo are registered trademarks of Microsoft
Corporation. Intel and Pentium are registered trademarks of Intel Corporation. All other products are trademarks or registered
trademarks of their respective owners and are hereby recognized as such. All specifications are subject to change without prior
notice. Actual contents may differ slightly from those pictured.
Page 3

Contents
Page 4

iiii
Contents
Introduction
Package Contents ............................................................................................................................... iv
System Requirements ........................................................................................................................ iv
Model Number, Serial Number and MAC Address ................................................................. v
More Help .............................................................................................................................................. v
Product Registration ........................................................................................................................... v
Customer Support Services and Warranty ................................................................................ v
Document Conventions ................................................................................................................... vi
1 About Your USB Adapter
2 Installing Your USB Adapter
Installing the Driver and Network Blaster Wireless USB Adapter Utility ........................... 2-1
Connecting Your USB Adapter ........................................................................................................... 2-6
Uninstalling the Driver and Network Blaster Wireless USB Adapter Utility ...................... 2-7
3 Connecting To A Wireless LAN
About the Network Blaster Wireless USB Adapter Utility Icon .............................................. 3-1
In Windows XP/2000/Me/98 SE .......................................................................................................... 3-2
Using Windows Wireless Network Connection (Windows XP only) .................................. 3-4
4 Configuring Settings
Connecting to a network in Infrastructure mode ......................................................................... 4-1
Scanning available access points ................................................................................................. 4-1
Specifying the SSID (Service Set Identity) ............................................................................... 4-3
Page 5

iiiiii
Connecting to a network in Ad-Hoc mode .................................................................................... 4-5
Link status information ........................................................................................................................... 4-7
Driver and utility version ....................................................................................................................... 4-7
Appendixes
A About Wireless LANs
Features and Benefits of Wireless LANs ......................................................................................... A-1
About Ad-Hoc Mode ............................................................................................................................. A-2
About Infrastructure Mode .................................................................................................................. A-3
Setting Up Wireless LANs ................................................................................................................... A-4
B About Network Security
About Wired Equivalent Privacy ......................................................................................................... B-1
C Technical Specifications
D Safety Precautions
General Safety .......................................................................................................................................... D-1
Exposure to Radio Frequency Caution ............................................................................................ D-1
Federal Communication Commission Interference Statement ................................................ D-1
E Glossary
Page 6

Introduction
Page 7

Introduction iv
Introduction
Thank you for choosing the Creative Network Blaster™ Wireless USB Adapter
CW2230.
Your USB Adapter is easy to set up and supports wireless connection speeds of up
to 54 Mbps*. Features include an auto-fallback function that lets you achieve the
fastest possible connection speeds, as well as 64 or 128-bit WEP, or WPA-PSK
encryption.
Pac k a g e
Contents
The following items are included in your package:
❑
Creative Network Blaster Wireless USB Adapter CW2230
❑ USB Extension cable
❑ Quick Start leaflet
❑ Installation CD
System
Requirements
❑ Microsoft
®
Windows® XP, Windows 2000, Windows Millennium Edition (Me) or Windows
98 Second Edition (SE)
❑ Intel Pentium II 233 MHz processor, or equivalent
❑ 20 MB free hard disk space
❑ 64 MB RAM
❑ CD-ROM/DVD-ROM drive
❑ Available USB port
*Available only with USB 2.0.
For USB 2.0 support,
you may need to install
the USB 2.0 driver
provided by your
hardware vendor.
Page 8

Introduction v
Model Number,
Serial Number
and MAC Address
You will find a model number, a serial number and a MAC address on your USB
Adapter.
You will need to provide model and serial numbers when contacting Customer
Support Services. And you may need to provide the MAC address to a network
administrator if you are going to use your device on a large network, such as in a
school or office.
More Help Depending on the type of broadband internet service that you subscribe to, you
may need additional information from your internet service provider to complete
the setup of your USB Adapter. Contact your internet service provider's customer
or technical support staff for details.
Product
Registration
Enjoy a host of benefits by registering your product during installation, or at
www.creative.com/register. Benefits include:
❑
Service and product support from Creative
❑ Exclusive updates on promotions and events
Customer
Support Services
and Warranty
Customer Support Services information can be found on the Installation CD.
d:\support\<language>\support.pdf
Warranty information can also be found on the Installation CD.
d:\warranty\<region>\<language>\warranty.pdf
(replace d:\ with the drive letter of your CD-ROM/DVD-ROM drive, <region> with
the region that you are in and <language> with the language that the document
is in)
Please keep your Proof of Purchase for the duration of the Warranty
period.
Page 9

Introduction vi
Document
Conventions
This User’s Guide uses the following icons to highlight useful or urgent information.
Tip. This tells you about short cuts or hints relating to a feature.
Note. This highlights additional or important information about a
feature.
Caution! This highlights proper usage of your product. Use this
information to avoid risky situations.
Warning! This warns you of possible hazards to yourself or your
product, that may result in injury or damage.
Page 10

About Your USB Adapter
Page 11
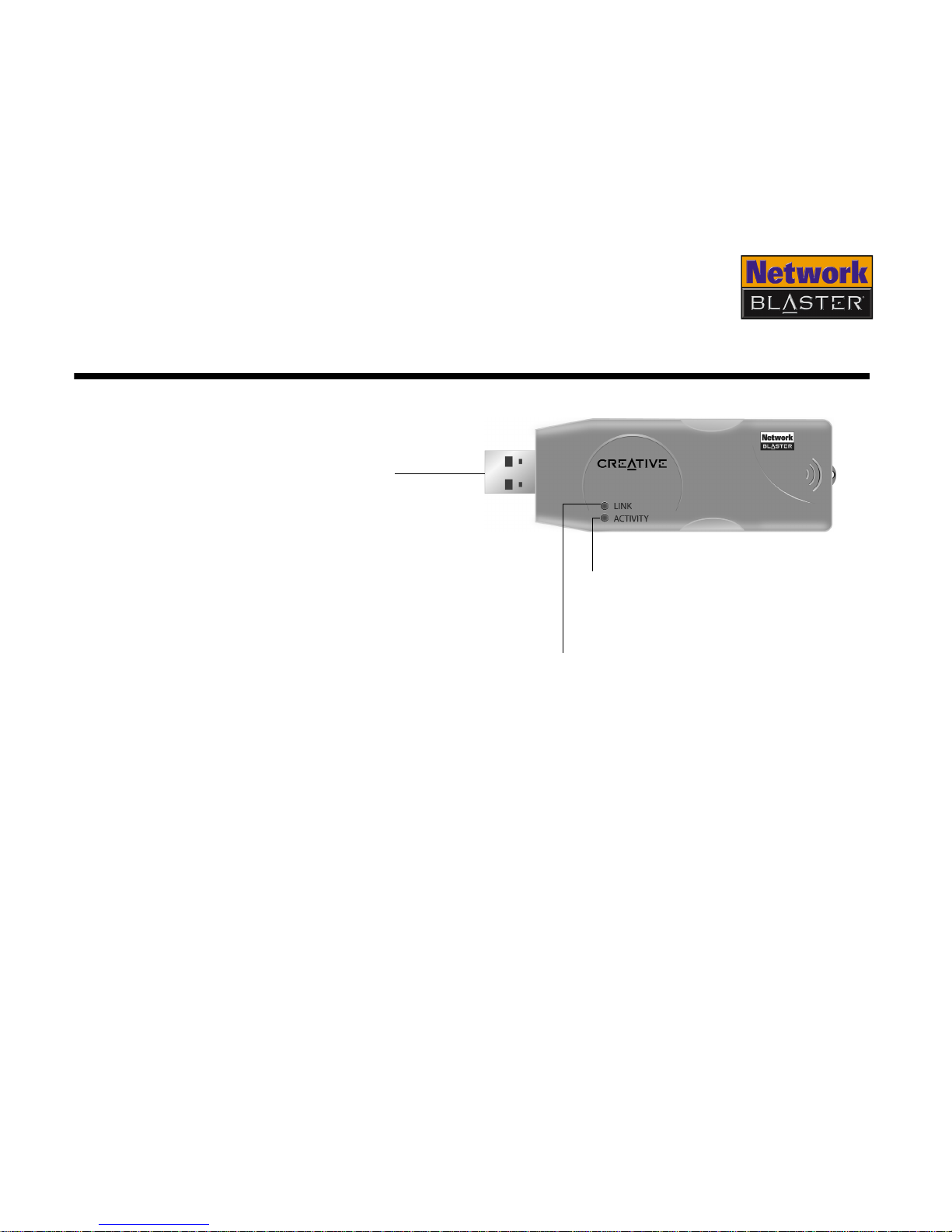
About Your USB Adapter 1-1
About Your USB Adapter
LINK LED
Blinks when your USB adapter is scanning for
available networks and lights up when
connected to a network.
Activity LED
Indicates the activity status. When
blinking green, the USB adapter is
transferring or receiving data.
USB connector
Insert this into your
computer's USB port.
Page 12

Installing Your USB Adapter
Page 13
Installing Your USB Adapter 2-1
Installing Your USB Adapter
Installing the
Driver and
Network
Blaster
Wireless USB
Adapter Utility
DO NOT connect the USB adapter to your computer before installing the software.
You will be required to do so halfway through the installation.
1. Turn on your computer and insert the Installation CD into your CD-ROM/
DVD-ROM drive. Your CD should start automatically. If it does not, follow the
steps below:
i. Start Windows Explorer.
ii. On the left pane, click the My Computer icon.
iii. Right-click the CD-ROM/DVD-ROM drive icon, and then click Autoplay.
2. Click the Install Software option.
3. Select the drivers and applications to install, and then click the OK button.
4. When the Creative Network Blaster Wireless USB Adapter Utility dialog
box appears, click the Next button.
5. In the next dialog box that appears, click the Next button.
6. In Windows XP, when the Creative Network Blaster Wireless USB Adapter
Utility dialog box similar to Figure 2-1 appears, click the OK button.
Windows 98 SE users
may be prompted to
insert their Win 98 SE
installation CD during
installation. If so,
insert the Win 98 SE
installation CD into
your CD-ROM/DVDROM drive, and then
click the OK button.
Figure 2-1
Page 14
Installing Your USB Adapter 2-2
For Windows XP only
7. At the time of this product’s release, Microsoft strongly encouraged companies
to submit their hardware solutions for certification. If a hardware device driver
is not submitted, or does not qualify for Microsoft certification, a warning
message similar to Figure 2-2 appears.
You may see this message when installing this driver. If you do, you may
choose to click the Continue Anyway button. Creative has tested this driver
on Windows XP, and it does not impair or destabilize your computer. If you
need more XP-related information, go to the product web site's Help.
8. Click the Finish button.
9. Connect your USB adapter to your computer’s USB port. See "Connecting Your
USB Adapter" on page 2-6.
Figure 2-2
Page 15
Installing Your USB Adapter 2-3
10. When the Found New Hardware Wizard dialog box similar to Figure 2-3
appears, click the Install the software automatically (Recommended)
option, and then click the Next button.
11. If the Hardware Installation dialog box similar to Figure 2-4 appears, click
the Continue Anyway button.
12. Click the Finish button.
Figure 2-3
Figure 2-4
Page 16

Installing Your USB Adapter 2-4
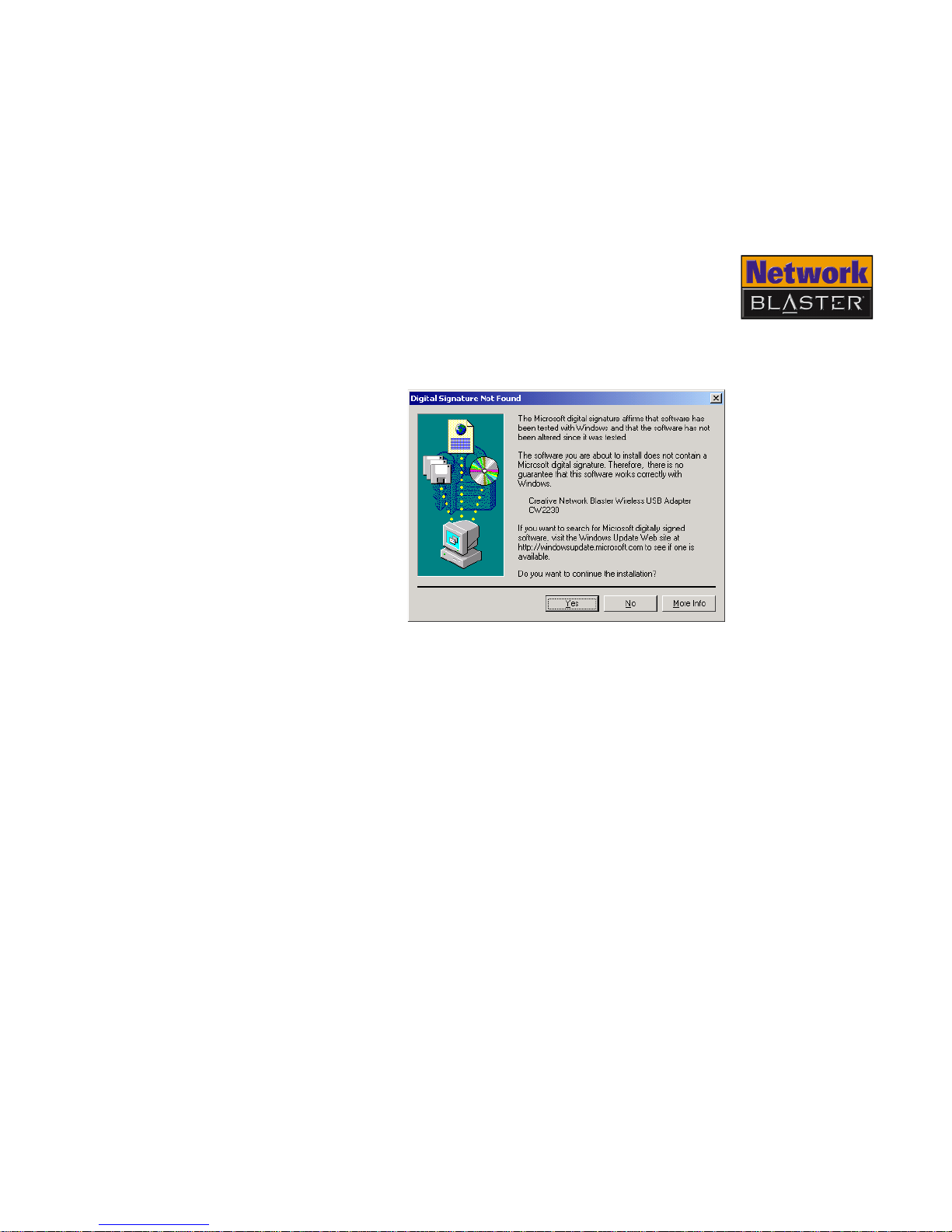
For Windows 2000 only
7. If the Digital Signature Not Found dialog box similar to Figure 2-5 appears,
click the Yes button.
8. Click the Finish button.
Figure 2-5
Page 17
Installing Your USB Adapter 2-5
9. If the Digital Signature Not Found dialog box similar to Figure 2-6 appears,
click the Yes button.
10. Connect your USB adapter to your computer’s USB port. See "Connecting Your
USB Adapter" on page 2-6.
For Windows Me and Windows 98 SE only
5. When prompted, restart your computer.
6. Connect your USB adapter to your computer’s USB port. See "Connecting Your
USB Adapter" on page 2-6.
For instructions on how to connect to a wireless LAN, see "Connecting To A
Wireless LAN" on page 3-1.
Figure 2-6
Page 18

Installing Your USB Adapter 2-6
Connecting
Your USB
Adapter
To connect your USB adapter to your computer’s USB port, do the following:
If necessary, connect your USB adapter to your computer’s USB port using the
provided USB Extension cable.
Your computer’s USB
port may be located on
the front panel. If your
USB adapter does not
fit into the USB port
located on the back
panel, connect it to the
USB port located on
the front panel.
USB port
USB port
USB Extension cable
Page 19

Installing Your USB Adapter 2-7
Uninstalling
the Driver and
Network
Blaster
Wireless USB
Adapter Utility
You may at times need to uninstall and then reinstall the drivers to correct
problems or make version upgrades. The following instructions tell you how to
uninstall the driver and Network Blaster Wireless USB Adapter Utility in all
Windows operating systems.
1. Close all applications.
2. Click Start -> Programs or All Programs -> Creative -> Network Blaster
Wireless USB Adapter CW2230 -> Uninstall Driver and Utility.
3. When the Confirm Uninstall dialog box appears, click the OK button.
4. In Windows XP/2000, click the Finish button.
In Windows Me/98 SE, when prompted, restart your computer.
5. Disconnect the USB adapter.
Page 20

Connecting To A Wireless LAN
Page 21

Connecting To A Wireless LAN 3-1
Connecting To A Wireless LAN
After installing your USB Adapter, you can connect to a wireless LAN.
Before you can connect to a network, you need to decide if you are connecting to
another wireless client or to an access point (you may easily switch between
modes if your requirements change). Use Ad-hoc mode if you are connecting
directly to another wireless client. Use Infrastructure mode if you are connecting to
an access point.
In either mode, the Service Set Identifier (SSID) and Wired Equivalent Privacy
(WEP) must have the same settings. For more information, see "About Wireless
LANs" on page A-1.
About the
Network
Blaster
Wireless USB
Adapter Utility
Icon
Name Description
❍ Startup icon
❍ After installing the driver and Network Blaster Wireless USB
Adapter Utility, this icon appears on your computer’s
taskbar.
❍ Network Blaster
USB Adapter Utility
icon
❍ When your USB adapter is connected to a network, this icon
appears on your computer’s taskbar.
❍ The Network Blaster USB Adapter Utility icon
disappears when you disconnect the USB adapter from your
computer, or when you are not running Network Blaster
Wireless USB Adapter Utility.
❍ Low signal
strength icon
❍ The bars on the Network Blaster Wireless USB Adapter
Utility icon indicate the signal strength. If the signal
strength is low, this icon appears.
❍ Disconnected icon
❍ When your USB adapter is not connected to a network, the
Network Blaster Wireless USB Adapter Utility icon
looks like this.
Page 22

Connecting To A Wireless LAN 3-2
In Windows
XP/2000/Me/98
SE
1. Click the Network Blaster
Wireless USB Adapter Utility
icon on your taskbar.
2. In Windows XP, when the
Wireless Zero Configuration
dialog box appears (Figure 3-1),
click the Yes button.
3. When the Network Blaster
Wireless USB Adapter Utility
dialog box (Figure 3-2) appears,
on the left pane, click Site
Survey.
4. Click the Refresh button. A list
of available access points and
Ad-hoc stations appears.
5. Under Available Networks,
select the network to connect to,
and then click the Connect
button.
To co n n e c t t o a
network by specifying
the SSID, refer to
"Specifying the SSID
(Service Set Identity)"
on page 4-3.
You can also click
Start -> Programs/
All Programs ->
Creative -> Network
Blaster Wireless
USB Adapter
CW2230 -> Network
Blaster Wireless
USB Adapter Utility
to launch the Network
Blaster Wireless USB
Adapter Utility.
Figure 3-1
Figure 3-2
Page 23

Connecting To A Wireless LAN 3-3
6. When the Profile Edit dialog box
(Figure 3-3) appears, click the
OK button.
Your computer automatically
connects to the selected
network.
Figure 3-3
Page 24

Connecting To A Wireless LAN 3-4
Using
Windows
Wireless
Network
Connection
(Windows XP
only)
In Windows XP, you can also connect to a wireless LAN using the Windows Wireless
Network Connection.
1. After installing the driver software, right-click the Network Blaster Wireless
USB Adapter icon or , and then click Enable Zero Configuration.
2. Right-click the Windows Wireless Network Connection icon
(Figure 3-4), and then click View Available Wireless
Networks.
3. When the Connect to Wireless
Network dialog box
(Figure 3-5) appears, select a
network to connect to, and then
click the Connect button.
For more instructions on using
the Windows Wireless Network
Connection, refer to the Windows
XP online help.
Figure 3-4
Figure 3-5
Page 25

Configuring Settings
Page 26

Configuring Settings 4-1
Configuring Settings
Connecting to
a network in
Infrastructure
mode
You can connect to a network in Infrastructure or Ad-Hoc mode. For Ad-Hoc mode
connection steps, see "Connecting to a network in Ad-Hoc mode" on page 4-5.
Infrastructure mode connection steps are found below.
Scanning available
access points
1. Click the Network Blaster
Wireless USB Adapter Utility
icon on the taskbar.
2. On the left pane, click Site
Survey (Figure 4-1).
3. Click the Refresh button.
A list of available access points
and Ad-hoc stations appears.
4. Under Available Networks,
select the network to connect to,
and then click the Connect
button.
Figure 4-1
Page 27

Configuring Settings 4-2
5. When the Profile Edit dialog box
appears, click the Encryption tab
(Figure 4-2).
To configure WEP
6. Click the Authentication box and
select Auto.
7. Click the Data Encryption box
and select WEP.
8. Click the Key Length box and
select 64 or 128 bits.
9. Select the Hex or ASCII option.
10. Type either Hex (10 or 26
characters) or ASCII (5 or 13
characters) values. These keys
serve as passwords that encrypt
your data before transmission.
11. Click the OK button.
To configure WPA-PSK
6. Click the Authentication box and
select WPA-PSK.
7. Click the Data Encryption box
and select TKIP or AES.
8. In the Pre-shared Key box, type
a password, which encrypts your
data before transmission.
9. Click the OK button.
Figure 4-2
It is recommended
that you set up WEP or
WPA-PSK encryption.
This can help prevent
unauthorized users
from accessing your
network. For more
information on
encryption settings,
refer to "Configuring
Settings" on page 4-1.
Page 28

Configuring Settings 4-3
Specifying the
SSID (Service Set
Identity)
1. Click the Network Blaster
Wireless USB Adapter Utility
icon on the taskbar.
2. On the left pane, click Site
Survey (Figure 4-3).
3. Under Profile Name, click the
New button.
4. When the Profile Edit dialog box
(Figure 4-4) appears, click the
General tab.
5. In the SSID box, type a name for
your SSID.
6. Click the Encryption tab.
Figure 4-3
Figure 4-4
Page 29

Configuring Settings 4-4
To configure WEP
7. Click the Authentication box and select Auto.
8. Click the Data Encryption box and select WEP.
9. Click the Key Length box and select 64 or 128 bits.
10. Select the Hex or ASCII option.
11. Type either Hex (10 or 26 characters) or ASCII (5 or 13 characters) values.
These keys serve as passwords that encrypt your data before transmission.
12. Click the OK button.
To configure WPA-PSK
7. Click the Authentication box and select WPA-PSK.
8. Click the Data Encryption box and select TKIP or AES.
9. In the Pre-shared Key box, type a password, which encrypts your data
before transmission.
10. Click the OK button.
It is recommended
that you set up WEP or
WPA-PSK encryption.
This can help prevent
unauthorized users
from accessing your
network. For more
information on
encryption settings,
refer to "Configuring
Settings" on page 4-1.
Page 30

Configuring Settings 4-5
Connecting to
a network in
Ad-Hoc mode
1. Click the Network Blaster
Wireless USB Adapter Utility
icon on the taskbar.
2. On the left pane, click Site
Survey (Figure 4-5).
3. Click the Refresh button.
A list of available access points
and Ad-hoc stations appears.
4. Under Available Networks,
select the network to connect to,
and then click the Connect
button.
5. When the Profile Edit dialog box
appears, click the General tab
(Figure 4-6).
6. In the SSID box, type a name for
your SSID.
7. Click the Network Type box and
select Ad hoc Station.
8. Click the Encryption tab.
Figure 4-5
Figure 4-6
Page 31

Configuring Settings 4-6
To configure WEP
9. Click the Authentication box and select Auto.
10. Click the Data Encryption box and select WEP.
11. Click the Key Length box and select 64 or 128 bits.
12. Select the Hex or ASCII option.
13. In the Network key box, type either Hex (10 or 26 characters) or ASCII (5
or 13 characters) values. These keys serve as passwords that encrypt your
data before transmission.
14. Click the OK button.
To configure WPA-PSK
7. Click the Authentication box and select WPA-PSK.
8. Click the Data Encryption box and select TKIP or AES.
9. In the Pre-shared Key box, type a password, which encrypts your data
before transmission.
10. Click the OK button.
It is recommended
that you set up WEP or
WPA-PSK encryption.
This can help prevent
unauthorized users
from accessing your
network. For more
information on
encryption settings,
refer to "Configuring
Settings" on page 4-1.
Page 32

Configuring Settings 4-7
Link status
information
1. Click the Network Blaster
Wireless USB Adapter Utility
icon on the taskbar.
2. To view network information such
as signal strength and link quality,
on the left pane, click Status
(Figure 4-7).
Driver and
utility version
1. Click the Network Blaster
Wireless USB Adapter Utility
icon on the taskbar.
2. To view the current driver and
utility version of Network Blaster
Wireless USB Adapter Utility, on
the left pane, click Version
Information (Figure 4-8).
Figure 4-7
Figure 4-8
Page 33

About Wireless LANs
Page 34

About Wireless LANs A-1
About Wireless LANs
Setting up wireless LANs is a revolutionary way of connecting devices to each
other. In a wireless LAN, information is transmitted using radio waves. This means
that you can establish a network of wireless devices in a room or across different
rooms without linking them with wires and cables.
Depending on your needs, a wireless LAN can be the sole network solution, or an
extension of a wired LAN.
Features and
Benefits of
Wireless LANs
Using wireless LANs has many advantages. Here are some of them:
❑
Convenience, cost effectiveness and flexibility
Setting up a wireless LAN is easy, fast and cost effective as you do not need to install new
wiring.
❑ Mobility
Unlike wired LANs, a wireless LAN allows you to move around and still remain connected
to the network.
❑ Scalability
You can choose to configure your wireless LAN in Ad-hoc mode or Infrastructure mode. In
Ad-hoc mode, a wireless client can communicate with other wireless clients directly. In
Infrastructure mode, one or more wireless clients are connected to an access point (AP),
and this AP connects these wireless clients to other wireless and wired clients. See "About
Ad-Hoc Mode" on page A-2 and "About Infrastructure Mode" on page A-3 for more
information.
Page 35

About Wireless LANs A-2
About Ad-Hoc
Mode
Ad-hoc mode allows for wireless-to-wireless communication. Wireless clients
connected in this way can share files, printers, drives and other resources, as well
as access the Internet using a shared modem. However, a wireless client can only
communicate with other wireless clients that:
❑
are part of the same wireless LAN workgroup
❑ share the same IEEE 802.11 standard
❑ are within a fixed range
Ad-hoc mode is also known as Peer-to-Peer mode.
Figure A-1: Ad-hoc Network
Printer
Broadband
modem
DVD-ROM drive
Internet
Wireless LAN
External hard
disk drive
Page 36

About Wireless LANs A-3
About
Infrastructure
Mode
In Infrastructure mode, a wireless client communicates with other wired and
wireless clients through an AP. A wireless client connected in this way can access
the resources of the Ethernet LANs and wireless LANs of the AP, including access to
the Internet using a shared modem.
Figure A-2: Infrastructure Network
Wireless AP
Wired LAN
Wireless clients
Internet
Broadband
modem
Switch
Page 37

About Wireless LANs A-4
Setting Up
Wireless LANs
When setting up a wireless LAN, take note of the following points:
❑
Start by determining the areas to be networked, the number of users and the type of
devices to be used. Then determine if you require APs and where they should be placed.
❑ If two APs are placed close to each other, you can optimize your bandwidth by setting
them to different channels.
❑ Radio waves can pass through walls and glass but not metal. If the signal on the other
side of a wall is weak, it may be that the wall has reinforcing metal in its structure. Install
another AP to circumvent this problem or move your AP to another location.
❑ Floors usually have metal girders and metal reinforcing struts that weaken radio waves.
Page 38

About Network Security
Page 39

About Network Security B-1
About Network Security
About Wired
Equivalent
Privacy
WEP is a data stream encryption technology that allows for the definition of up to
four keys shared between wireless devices. Unauthorized devices that do not have
the same keys are locked out. Only devices with the same keys can communicate
with each other. Refer to the diagrams below for details on how the keys work.
When typing the keys,
use either
hexadecimal
characters, which are
the letters A to F and
the numbers 0 to 9, or
ASCII characters.
default key
When Keys 1-4 and the selected default key for both wireless devices are the same, they
can communicate with each other.
default key
Page 40

About Network Security B-2
When Keys 1-4 for both wireless devices are the same but the selected default key is
different, they can communicate with each other.
default key default key
When Keys 1-4 for both wireless devices are different but the selected default key is the
same, they can communicate with each other.
default key default key
Page 41

About Network Security B-3
When Keys 1-4 and the selected default key in both wireless devices are different, they
cannot communicate with each other.
default key
default key
Page 42

Technical Specifications
Page 43

Technical Specifications C-1
Technical Specifications
Standards ❑ IEEE 802.11g
Interface ❑ USB 2.0 compliant
Antenna ❑ PCB antenna
Frequency Band ❑ 2.4–2.4835 GHz
Data Rate ❑ OFDM: 54, 48, 36, 24, 18, 12, 9 Mbps
❑ DSSS/CCK: 11, 5.5, 2, 1 Mbps
Channels ❑ 11 Channels (US, Canada)
Security ❑ 64 or 128-bit WEP encryption
❑ WPA-PSK
Page 44

Safety Precautions
Page 45

Safety Precautions D-1
Safety Precautions
General Safety
To avoid the risk of fire, electric shock or personal injury, note the following
precautions when using the product:
❑
Do not expose the product to direct sunlight or excessive heat.
❑ Do not place the product in surroundings that exceed 40°C (104°F).
❑ Avoid humid conditions. Do not place the product near a water source or outlet.
❑ Do not clean the product with a damp cloth or liquid cleaner.
❑ Do not put any weight on the product.
❑ Allow only qualified personnel to service or repair the product, if such is necessary.
Exposure to
Radio
Frequency
Caution
❑ The radiated output power of this device is far below the FCC radio frequency exposure
limits. Nevertheless, the device shall be used in such a manner that the potential for
human contact during normal operation is minimized.
❑ The product and any attached external antenna, if supported, shall be placed in such a
manner to minimize the potential for human contact during normal operation.
❑ In order to avoid the possibility of exceeding the FCC radio frequency exposure limits,
human proximity to the antenna shall not be less than 2.5 cm (1 inch) during normal
operation.
❑ The indoor antenna must be totally isolated and does not have a line of sight to an
external GPS antenna, to avoid feedback reflected RF signal.
Federal
Communicatio
n Commission
Interference
Statement
This equipment has been tested and found to comply with the limits for a Class B
digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to
provide reasonable protection against harmful interference in a residential
installation. This equipment generates, uses and can radiate radio frequency
energy and, if not installed and used in accordance with the instructions, may
cause harmful interference to radio communications. However, there is no
guarantee that interference will not occur in a particular installation. If this
equipment does cause harmful interference to radio or television reception, which
can be determined by turning the equipment off and on, the user is encouraged to
try to correct the interference by one of the following measures:
Page 46

Safety Precautions D-2
• Reorient or relocate the receiving antenna.
• Increase the separation between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which
the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) This device may not cause harmful interference, and
(2) this device must accept any interference received, including interference that
may cause undesired operation.
FCC Caution: Any changes or modifications not expressly approved by the party
responsible for compliance could void the user's authority to operate this
equipment.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an
uncontrolled environment. This equipment should be installed and operated with
minimum distance 20cm between the radiator & your body.
This transmitter must not be co-located or operating in conjunction with any other
antenna or transmitter.
INFORMATION TO USER:
The users manual or instruction manual for an intentional or unintentional radiator
shall caution the user that changes or modifications not expressly approved by the
party responsible for compliance could void the user's authority to operate the
equipment.
Page 47

Glossary
Page 48

Glossary E-1
Glossary
10 Base-T A wiring standard used for Ethernet networks that can transmit data at up to 10
Mbps transmission using baseband unshielded twisted pair cables. The maximum
cable length is 100 meters (330 feet).
Ad-hoc mode A small peer-to-peer network mode, in which wireless clients are connected to
each other directly without using an AP. Some of the wireless clients are part of the
network for a limited duration. They are also in close proximity with the rest of the
network. According to the IEEE 802.11g specification, Ad-hoc mode is referred to
as an independent basic service set.
Antenna A device that intercepts radio frequency (RF) waves from the atmosphere and
converts them to corresponding signal voltages.
AP (Access Point) A networking device that transparently bridges wireless computers to a wired local
network.
ASCII (American
Standard Code for
Information
Interchange)
ASCII is the most common format for text files in computers and on the Internet.
In an ASCII file, each alphabetic, numeric, or special character is represented with
a 7-bit binary number (a string of seven 0s or 1s). 128 possible characters are
defined.
Bandwidth A measure of the maximum rate of data transfer. A higher bandwidth allows more
data transmission in a given period of time. For digital services, the bandwidth is
usually expressed in bits or bytes per second.
Binary A number system that has only two digits, 0 and 1.
Page 49

Glossary E-2
Bridge A hardware device that links two or more physical networks and manages the
transfer of data between these networks. The two networks connected can be alike
or dissimilar.
Broadband A transmission media that can handle the transmission of multiple messages at
different frequencies, at one time. Broadband signals use analog carriers.
BSS (Basic Service
Set)
A group of wireless clients and an AP using the same ID (SSID).
Channel A channel is a separate path through which signals can flow.
dBm (Decibels Per
Milliwatt)
A unit of measurement used to express relative difference in power or intensity,
relative to 1 mW.
DHCP (Dynamic
Host Configuration
Protocol)
A method of assigning a temporary IP address to a host, such as a computer,
connected on a specific network. With dynamic addressing, a particular host may
have a different IP address each time it connects to the network.
Digital Data expressed as a string of 0s and 1s. Each of these digits is referred to as a bit
(and a string of 8 bits that a computer can address individually as a group is a
byte).
DNS (Domain
Name System)
This allows you to specify a symbolic name, a meaningful and easy-to-remember
“handle”, instead of an IP address. The DNS is the way that Internet domain
names are located and translated into IP addresses.
Page 50

Glossary E-3
DNS Server A server that contains both the English and numerical addresses of all computers
connected to the Internet. When you specify an e-mail or IP address using the
“English” domain name, the DNS server will return the corresponding numeric
address.
Domain Name A domain name locates an organization or other entity on the Internet.
Driver A program that a computer uses to control the operation of a peripheral device,
such as a keyboard, modem, monitor, card, or cable.
DSSS (Direct
Sequence Spread
Spectrum)
A digital modulation technique that spreads data transmissions across the entire
available frequency band in a pre-arranged scheme. Under DSSS, each bit of data
to be transmitted is encoded with a redundant pattern called a chip. The chipping
code is known only to the sending and receiving clients, making it difficult for an
intruder to intercept and decipher the encoded wireless data. DSSS is used in IEEE
802.11b networks.
Dynamic IP address See DHCP (Dynamic Host Configuration Protocol).
Encryption A procedure to convert a file from its original form to one that can be read only by
the intended recipient.
ESS (Extended
Service Set)
A group of wireless clients and multiple APs using the same ID (ESSID) form an
ESS.
ESSID (Extended
Service Set Identity)
An ASCII string that is used by a wireless network. Wireless clients with a different
ESSID from your network’s ESSID cannot connect to your network. An ESSID can
be as long as 32 characters.
Page 51

Glossary E-4
Ethernet A LAN protocol that supports data transfer rates of 10 Mbps. It is a widely
implemented LAN standard that operates over the twisted pair or coaxial cable. A
version of Ethernet, called 100 Base-T (or FastEthernet), supports data transfer
rates of 100 Mbps.
FastEthernet An Ethernet specification with a speed of 100 Mbps (10 times faster than
10BaseT).
Fragmentation
Threshold
The size at which the transmitted data packets are fragmented. The range extends
from 256 to 2346 bytes.
Full duplex Simultaneous and independent data transmission, between two communicating
computers, in both directions.
Half duplex A data transmission system where two computers can send and receive data but in
which data transmission can occur in only one direction at a time.
Hexadecimal A number system with a base of 16. The 16 digits in the hexadecimal system are
0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, f.
Hub A device used for connecting nodes in a star topology, that is, all the nodes are
connected to a central hub. A passive hub simply organizes the wiring, while an
active hub, besides organizing the wiring, regenerates and retransmits the signals.
IEEE 802.11 A family of wireless network standards, which includes 802.11a, 802.11b,
802.11e, and 802.11g (draft). The original 802.11 standard was first approved in
1997 but was not very successful because it was relatively slow at 2 Mbps.
IEEE 802.11b A high-bit wireless network standard that works on the 2.4 GHz band and utilizes
DSSS (direct sequence spread spectrum) technology. It offers data bit rates of up
to 11 Mbps and the range is from 200 to 300 feet for maximum speed.
Page 52

Glossary E-5
IEEE 802.11g The 802.11g specifications specify a maximum data transfer rate of 54 Mbps, an
operating frequency of 2.4 GHz, backward compatibility with 802.11g devices and
WEP encryption for security.
Infrastructure mode A LAN or other small network mode in which wireless clients are part of the
network and use one or more APs to connect to a wired network. Each AP is
connected to the Ethernet network using a standard Ethernet cable. In IEEE
802.11g specification, the infrastructure mode is referred to as the Basic Service
Set.
Interface The physical arrangement that supports the attachment of a device to a connector
or to another device.
IP (Internet
Protocol)
The standard protocol within TCP/IP that defines the basic unit of information by
breaking down data messages into packets, routing and transporting the packets
over networks, then reassembling the packets at their destination. IP corresponds
to the Network layer (layer 3) in the ISP/OSI model.
IP address The address for a computer on a TCP/IP network. The IP address identifies a
particular machine on a network. The format of an IP address is a 32-bit numeric
address written as four numbers separated by periods. Each number can be 0 to
255, for example, 11.160.10.240 is an IP address. Any machine connected to the
Internet is assigned an IP address.
ISM (Industrial,
Scientific and
Medical) band
There are four unlicensed bands for wireless networks and these bands are
commonly known as ISM bands. These bands are found on the 900 MHz, 2.4 GHz
and 5 GHz (two) frequency bands.
KB (Kilobytes) 1 KB equals 1,024 bytes.
Page 53

Glossary E-6
Kbps (Kilobits Per
Second)
A measure of data transfer speed.
LAN (Local Area
Network)
A computer network that spans a relatively small area. Most LANs are confined to
an office, single building, or group of buildings.
LED (Light Emitting
Diode)
An electric component that emits light (turns ON) when current flows through it.
MAC (Media Access
Control) address
A unique number that is assigned by manufacturers to each Ethernet network
device. A MAC address lets a network identify Ethernet network devices at the
hardware level.
Mbps (Megabits Per
Second)
A measure of data transfer speed.
Megabits/Megabytes One million bits/bytes.
Modem A device that allows a computer to transmit data to other computers.
NAT (Network
Address Translation)
An Internet standard that enables a LAN to use one set of IP addresses for internal
traffic and a second set of IP addresses for external traffic. NAT provides a type of
firewall security by hiding internal IP addresses. Since they are used internally,
such IP addresses will not be in conflict with those used by other companies and
organizations.
Network Mask See Subnet Mask.
Page 54

Glossary E-7
NIC (Network
Interface Card)
A card that is installed in a computer so that it can be connected to a network. The
NIC manages the flow of network information to and from the computer.
PCMCIA (Personal
Computer Memory
Card International
Association)
An industry group organized in 1989 to promote standards for a card-size memory
or I/O device that would fit into a personal computer.
PCMCIA Card A card-size memory or I/O device that connects to a personal computer. The
PCMCIA card has a 68-pin connector that connects into a slot in the computer.
PING (Packet
Internet Groper)
An Internet program used to determine whether a specific IP address is accessible.
It works by sending a packet to the specified address and waiting for a reply. PING
is used primarily to troubleshoot network connections.
Preamble A preamble is a signal, in the form of series of pulses, used in network
communication to synchronize the transmission timing between two or more
systems. There are two options, Short and Long. The Short option improves
throughput performance.
Protocol A set of agreed-upon rules for transmitting data between two devices. A user’s
computer must support the right protocols for the computer to communicate with
other computers.
Reboot When a computer is shut down and restarted, it is rebooting.
RJ-11 A connector/socket for two pairs (four wires) of twisted pair cables that are used
primarily to connect telephone equipment in the United States.
Page 55

Glossary E-8
RJ-45 A connector/socket for four pairs of twisted pair cables that are used commonly to
connect computers onto a local-area network, especially to the Ethernet. The only
difference between an RJ-45 and RJ-11 connector is that an RJ-45 connector is
slightly wider.
Router A hardware device that connects two separately functional networks using the
same or different protocols. Routers look at the destination addresses on the
packets passing through them and then decide which route to send them on.
RTS (Request to
Send) Threshold
This threshold refers to when your device sends out RTS frames to reserve
bandwidth for maximum data transmission. If a transmitted data frame is larger
than the threshold value, the RTS frame sent out will request for more bandwidth.
SSID (Service Set
Identity)
A group name shared by all members of an IEEE 802.11 standard wireless
network. Only wireless devices with the same SSID are allowed to establish
connections.
Static IP address A permanent IP address assigned to a computer (host) connected on a specific
network.
Subnet or
Subnetwork
Any network that is a part of a larger IP network and is identified by a subnet
address.
Subnet Mask A 32-bit string of a TCP/IP address — a part of which is the network address and
another part the host address. A Subnet Mask is usually represented in dotteddecimal notation, for example, 255.255.255.0.
Switch A device used for connecting nodes in a star topology. In a star topology, all nodes
are connected to a central switch. By monitoring packets, a switch learns which
devices are connected to its ports and then sends a packet to the appropriate port
only.
Page 56

Glossary E-9
TCP/IP
(Transmission
Control Protocol/
Internet Protocol)
A suite of communication protocols that are used by computers or networking
devices on the Internet so that they can communicate with each other. TCP/IP
uses several protocols, the two main being TCP and IP.
Twisted pair cable A cable that consists of two wires twisted together. This cable is less expensive but
more brittle than a coaxial cable.
USB (Universal
Serial Bus)
A plug-and-play interface that allows the user to attach a device without having to
add an adapter card and turning off the computer.
WAN (Wide Area
Network)
A computer network that spans a relatively large geographical area. Typically, a
WAN consists of two or more LANs.
WEP (Wired
Equivalent Privacy)
A wired security policy defined by the IEEE 802.11 working group. WEP uses the
RC-4 40-bit encryption algorithm to scramble all data before it is transmitted.
Vendors add proprietary encryption features to their software, taking the
encryption level up to 128 bits.
Wi-Fi Wi-Fi is promoted by the Wireless Ethernet Compatibility Alliance (WECA). It
places a stamp of certification on wireless products that are interoperable with
other 802.11b compliant products.
WPA-PSK (Wi-Fi
Protected AccessPre Shared Key)
With WPA-PSK encryption, your encryption keys are automatically changed and
authenticated between devices after a specific time period, or after a specific
number of packets are transmitted.
Page 57

 Loading...
Loading...