Comodo Security Comodo Firewall Pro 3.0 User Manual

Comodo Firewall Pro 3.0 – User Guide 1
Creating Trust Online
TM
Comodo Firewall Pro 3.0
User Guide

Table of Contents
Comodo Firewall Pro – Introduction ................................................................................................................................ 4
What's New in Comodo Firewall Pro ........................................................................................................................... 7
Installation ..................................................................................................................................................................... 9
System Requirements ................................................................................................................................................ 25
Starting Comodo Firewall Pro .................................................................................................................................... 25
General Navigation and Firewall Summary .............................................................................................................. 27
Understanding Alerts .................................................................................................................................................. 30
Firewall Task Center ........................................................................................................................................................ 36
Network Security Policy .............................................................................................................................................38
Pre-defined Firewall Policies ..................................................................................................................................... 52
Attack Detection Settings .......................................................................................................................................... 54
Firewall Behavior Settings ......................................................................................................................................... 58
View Firewall Events ................................................................................................................................................... 61
Define a New Trusted Application ............................................................................................................................. 66
Define a New Blocked Application ............................................................................................................................ 68
Stealth Ports Wizard ................................................................................................................................................... 70
View Active Connections ........................................................................................................................................... 73
My Port Sets ................................................................................................................................................................ 75
My Network Zones ...................................................................................................................................................... 78
My Blocked Network Zones ....................................................................................................................................... 81
Defense+ Tasks Overview ............................................................................................................................................... 84
View Defense+ Events ................................................................................................................................................ 87
My Protected Files ...................................................................................................................................................... 91
My Quarantined Files .................................................................................................................................................. 94
My Pending Files ......................................................................................................................................................... 96
Comodo Firewall Pro 3.0 – User Guide 2

My Own Safe Files ....................................................................................................................................................... 98
View Active Process List .......................................................................................................................................... 100
My Trusted Software Vendors ................................................................................................................................. 101
Scan My System ........................................................................................................................................................ 106
My Protected Registry Keys .................................................................................................................................... 108
My Protected COM Interfaces .................................................................................................................................. 111
Computer Security Policy ........................................................................................................................................ 114
Image Execution Control Settings .......................................................................................................................... 120
Predefined Security Policies .................................................................................................................................... 122
Defense+ Settings ..................................................................................................................................................... 123
Miscellaneous Overview ................................................................................................................................................ 129
Manage My Configurations ...................................................................................................................................... 135
Diagnostics ................................................................................................................................................................ 140
Check for Updates .................................................................................................................................................... 141
Submit Suspicious Files ........................................................................................................................................... 143
Browse Support Forums .......................................................................................................................................... 146
Help ............................................................................................................................................................................ 147
About .......................................................................................................................................................................... 148
About Comodo ............................................................................................................................................................... 149
Comodo Firewall Pro 3.0 – User Guide 3

Comodo Firewall Pro - Introduction
Overview
Comodo Firewall Pro offers 360° protection against internal and external threats by combining enterprise class packet
filtering firewall with an advanced host intrusion prevention system. The new-look interface facilitates quick and easy
access to all major settings, including the powerful and highly configurable security rules interface.
Built from the ground upwards with our security in mind, this award winning firewall constantly monitors and defends your
system from inbound and outbound attacks. Version 3.0 now features a fully fledged Host Intrusion Prevention System
called Defense+ to protect your critical operating system files and block viruses and malware before they ever get the
chance to install. In fact, Defense+ is so good at blocking malware, you may never need a dedicated anti-virus program
ever again.
The new-look firewall features a friendly graphical user interface; highly granular configuration options; easily understood
and informative alerts; wizard-based detection of trusted zones and much more. Comodo Firewall Pro delivers enterprise
class protection and can be used ‘out of the box’ - so even the most inexperienced users will not have to deal with
complex configuration issues after installation.
Comodo Firewall Pro includes an integrated executable file database, which is a comprehensive classification of all
known executable files. It is the only firewall which provides such significant information with users.
This introductory section is intended to provide an overview of the basics of Comodo Firewall Pro and should be of
interest to all users.
Introduction
• What's New In Comodo Firewall Pro
• Installing Comodo Firewall Pro
• System Requirements
• Starting Comodo Firewall
• General Navigation and Firewall Summary
• Understanding Alerts
The remaining three sections of the guide cover every aspect of the configuration Comodo Firewall Pro. Advanced users
interested in configuring their own security policies and rules may want to make 'Network Security Policy' and 'Computer
Security Policy ' their starting points.
Firewall Task Center
• Overview of Task Interface
Comodo Firewall Pro 3.0 – User Guide 4

Common Tasks
• View Firewall Events
• Define a New Trusted Application
• Define a New Blocked Application
• Stealth Ports Wizard
• View Active Connections
• My Port Sets
• My Network Zones
• My Blocked Network Zones
Advanced
• Network Security Policy
• Predefined Firewall Policies
• Attack Detection Settings
• Firewall Behavior Settings
Defense+ Task Center
• Overview of Task Interface
Common Tasks
• View Defense+ Events
• My Protected Files
• My Quarantined Files
• My Pending Files
• My Own Safe Files
• View Active Process List
• My Trusted Software Vendors
Comodo Firewall Pro 3.0 – User Guide 5

• Scan my System
• My Protected Registry Keys
• My Protected COM Interfaces
Advanced
• Computer Security Policy
• Predefined Security Policies
• Image Execution Control Settings
• Defense+ Settings
Miscellaneous
• Overview of Miscellaneous Tasks Interface
• Settings
• Manage My Configurations
• Diagnostics
• Check For Updates
• Submit Suspicious Files
• Browse Support Forums
• Help
• About
Comodo Firewall Pro 3.0 – User Guide 6

What's New in Comodo Firewall Pro
New in Version 3.0
NEW! Defense+ Host Intrusion Prevention System Control
• Virtually Bulletproof protection against root-kits, inter-process memory injections, key-loggers and more;
• Authenticates the integrity of every program before allowing it to load into your computer’s memory;
• Alerts you every time unknown or untrusted applications attempts to run or install;
• Blocks Viruses, Trojans and Spy-ware before they can ever get onto your system;
• Prevents unauthorized modification of critical operating system files and registry entries.
IMPOROVED! Advanced Network Firewall Engine
Comodo Firewall Pro has always offered the highest levels of perimeter security against inbound and outbound threats –
meaning you get the strongest possible protection against hackers, malware and identity thieves. Now we’ve improved it
again by adding new features such as Stealth Mode to make your PC completely invisible to opportunistic port scans;
Wizard based auto-detection of trusted zones; Password protection of firewall settings; Diagnostics to analyze your
system for potential conflicts with the firewall and much more.
NEW! Intuitive Graphical User Interface
• Summary screen gives an at-a-glance snapshot of your security settings;
• Easy and quick navigation between each module of the firewall;
• Simple point and click configuration – no steep learning curves;
• New completely redesigned security rules interface - you can quickly set granular access rights and privileges on
a global or per application. The firewall also contains pre-set policies and wizards that help simplify the rule
setting process.
IMPROVED! Security rules interface
Version 3.0 gives offers more control over security settings than ever before. Users can quickly set granular internet
access rights and privileges on a global or per application basis using the flexible and easy to understand GUI. This
version also sees the introduction of pre-set security policies which allow you to deploy a sophisticated hierarchy of
firewall rules with a couple of mouse clicks.
IMPROVED! Application Behavior Analysis
CFP 3.0 features advanced protocol driver level protection - essential for the defense of your PC against Trojans that run
their own protocol drivers.
Improved! Event logging
Comodo Firewall Pro 3.0 – User Guide 7

Version 3.0 features a vastly improved log management module – allowing users to export records of firewall activity
according to several user-defined filters. Beginners and advanced users alike will greatly benefit from this essential
troubleshooting feature.
NEW! Added new ‘Training Mode’ and 'Clean PC' Mode
This mode enables the firewall and host intrusion prevention systems to automatically create ‘allow’ rules for new
components of applications you have decided to trust, so you won’t receive pointless alerts for those programs you trust –
the firewall will learn how they work and only warn you when it detects truly suspicious behavior.
NEW! Windows Security Center Integration
Comodo Firewall Pro 3.0 is fully recognized by Windows Vista/XP Security Center as a trusted firewall.
IMPROVED! Application Recognition Database (Extensive and proprietary application safe list)
Comodo Firewall Pro includes an extensive white-list of safe executables called the ‘Comodo Safe-List Database’. This
database checks the integrity of every executable and Firewall Pro will alert you of potentially damaging applications
before they are installed. This level of protection is new because traditionally firewalls only detect harmful applications
from a blacklist of known malware – often-missing new forms of malware as might be launched in day zero attacks.
Firewall Pro is continually updated and currently over 1,000,000 applications are in Comodo Safe list,
representing virtually one of the largest safe lists within the security industry.
NEW! Self Protection against Critical Process Termination
Viruses and Trojans often try to disable your computer’s security applications so that they can operate without detection.
Comodo Firewall Pro protects its own registry entries, system files and processes so malware can never shut it down or
sabotage the installation.
IMPROVED! Submit Suspicious Files to Comodo
Are you the first victim of a brand new type of spyware? Users can help combat zero-hour threats by using the built in
submit feature to send files to Comodo for analysis. Comodo will then analyze the files for any potential threats and
update our database for all users.
Comodo Firewall Pro 3.0 – User Guide 8

Installation
Before you install Comodo Firewall Pro, read the installation instructions carefully and also review the system
requirements listed in this chapter.
Installation Process
To install, download the Comodo Firewall Pro setup files to your local hard drive. (setup.exe can be downloaded from
http://www.personalfirewall.comodo.com )
Next, double click on the setup file to start the installation wizard and follow the process as below.
STEP 1: Uninstall Other Firewall Programs
Before you install Comodo Firewall Pro, you must uninstall any third party Firewall programs installed in your PC. This is
necessary as other firewall programs may interfere with the installation of Comodo Firewall Pro and reduce the protection
offered by it. Click Yes.
Comodo Firewall Pro 3.0 – User Guide 9
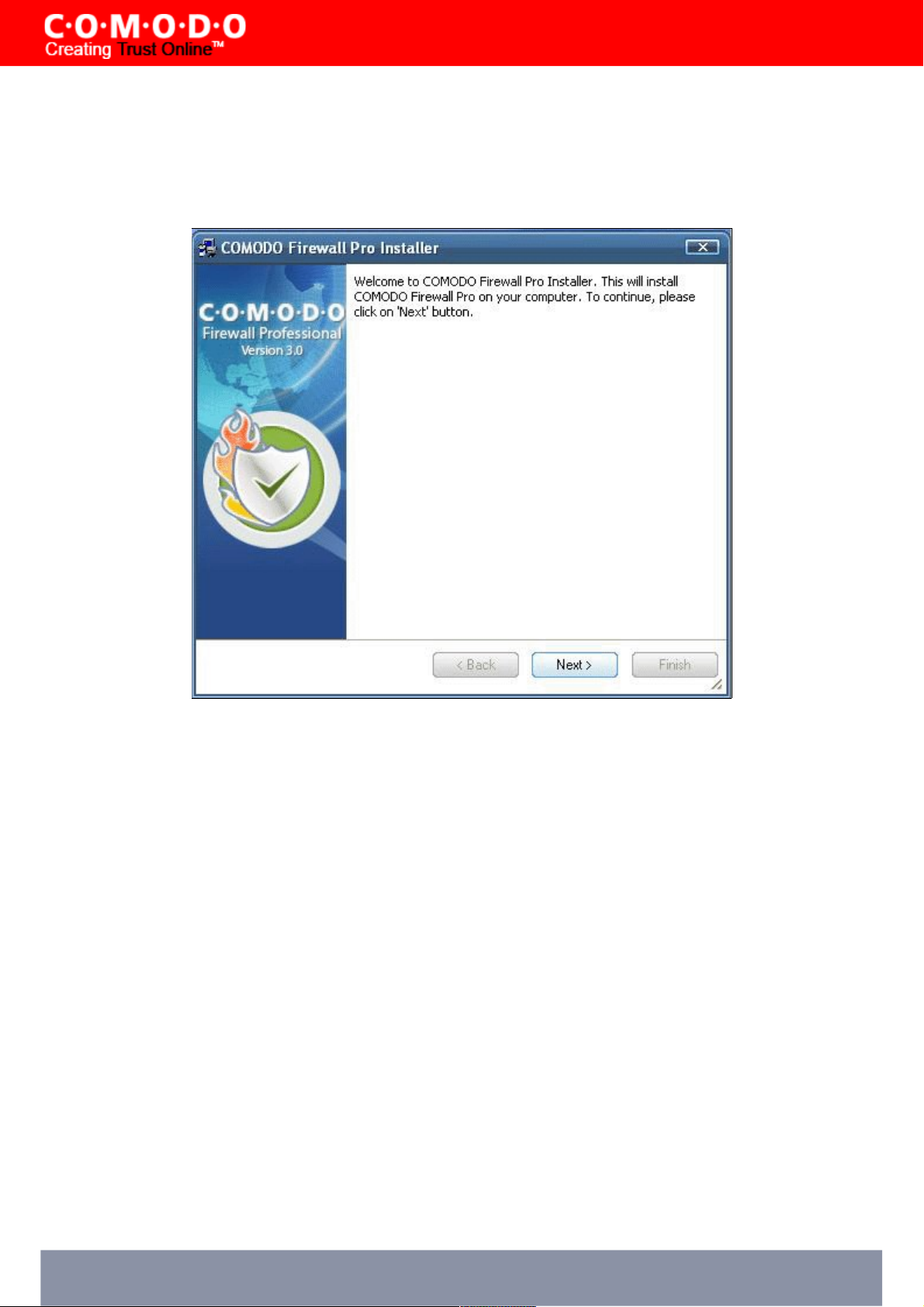
STEP 2: Welcome dialog box
The set up program starts automatically and the Welcome wizard is displayed. At this time, you may cancel the install
process or continue with the Comodo Firewall Pro Setup program. Click Next to continue.
Comodo Firewall Pro 3.0 – User Guide 10
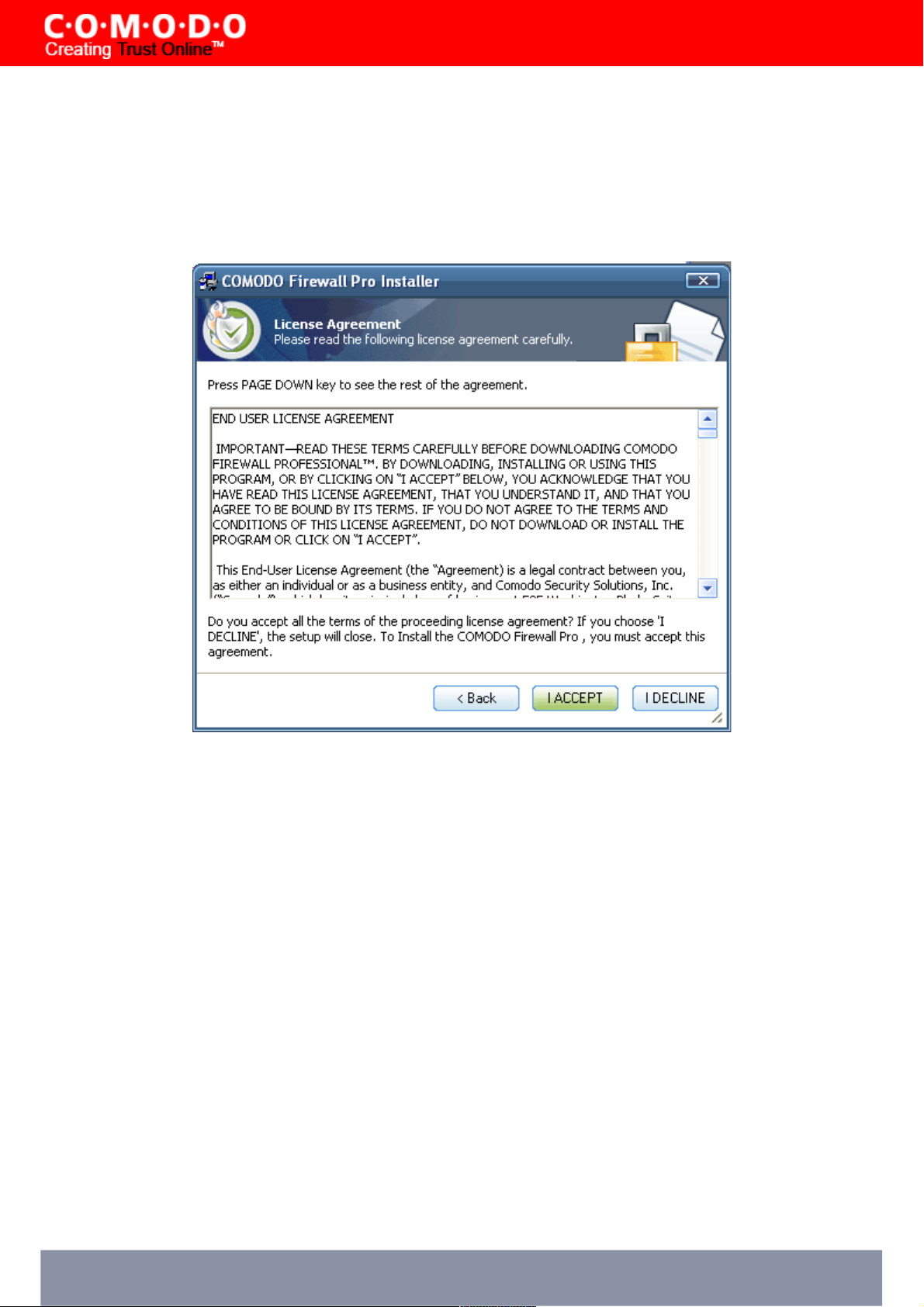
STEP 3: License Agreement
When Comodo Firewall Pro is installed for the first time, you must complete the initialization phase by reading and
accepting the license agreement. After you read the End-User License Agreement, click Yes to continue installation. If
you decline, you cannot continue with the installation.
Comodo Firewall Pro 3.0 – User Guide 11
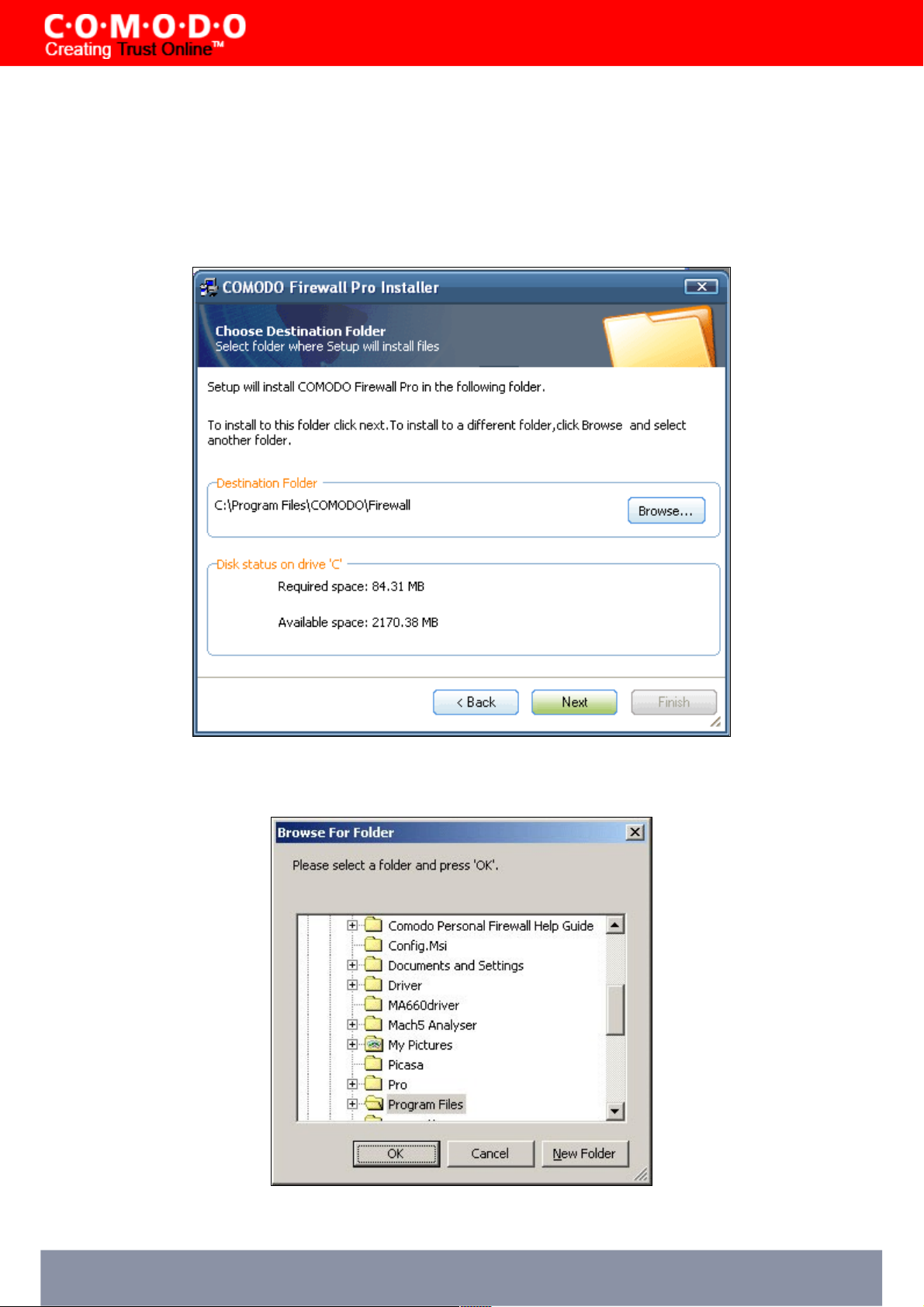
STEP 4: Location Destination Folder
On the Destination Wizard page, confirm the location of the Firewall installation files.
To install the program in the default destination location, click Next. The default destination directory is the C:\Program
Files\Comodo\Firewall.
If you do not wish to install the Firewall files in the default location, to install to a different folder, click BROWSE and
select another folder. Click OK to continue with the installation process.
Comodo Firewall Pro 3.0 – User Guide 12
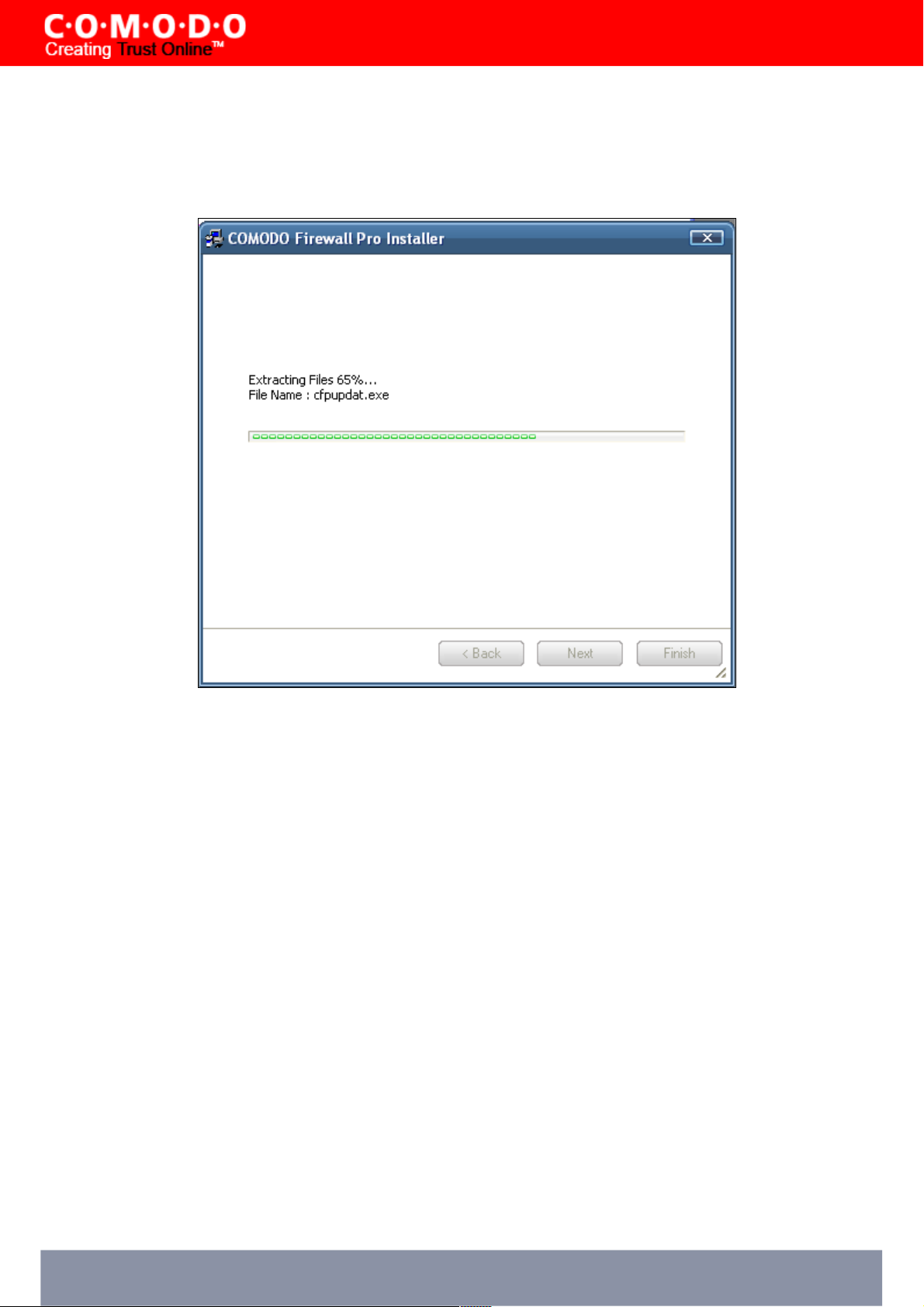
STEP 5: Set Up Status Box
A setup status dialog box is displayed. You will see a progress bar indicating that files are being installed.
STEP 6: Welcome Screen
A configuration wizard dialog box will open. Click "Next" to continue with installation.
Comodo Firewall Pro 3.0 – User Guide 13
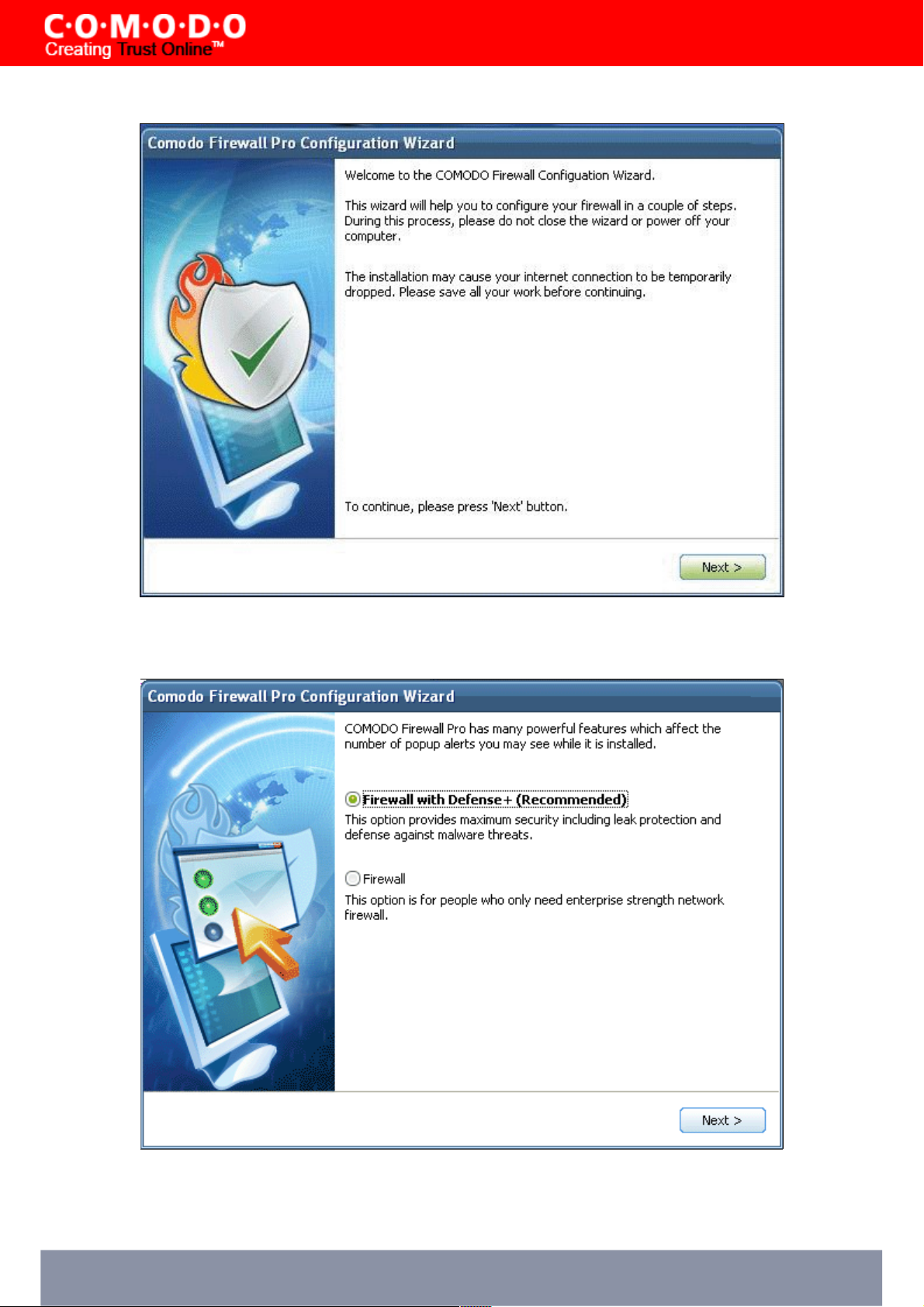
STEP 7: Install Defense+
Next you choose which type of installation (and protection level) you would prefer :
Comodo Firewall Pro 3.0 – User Guide 14
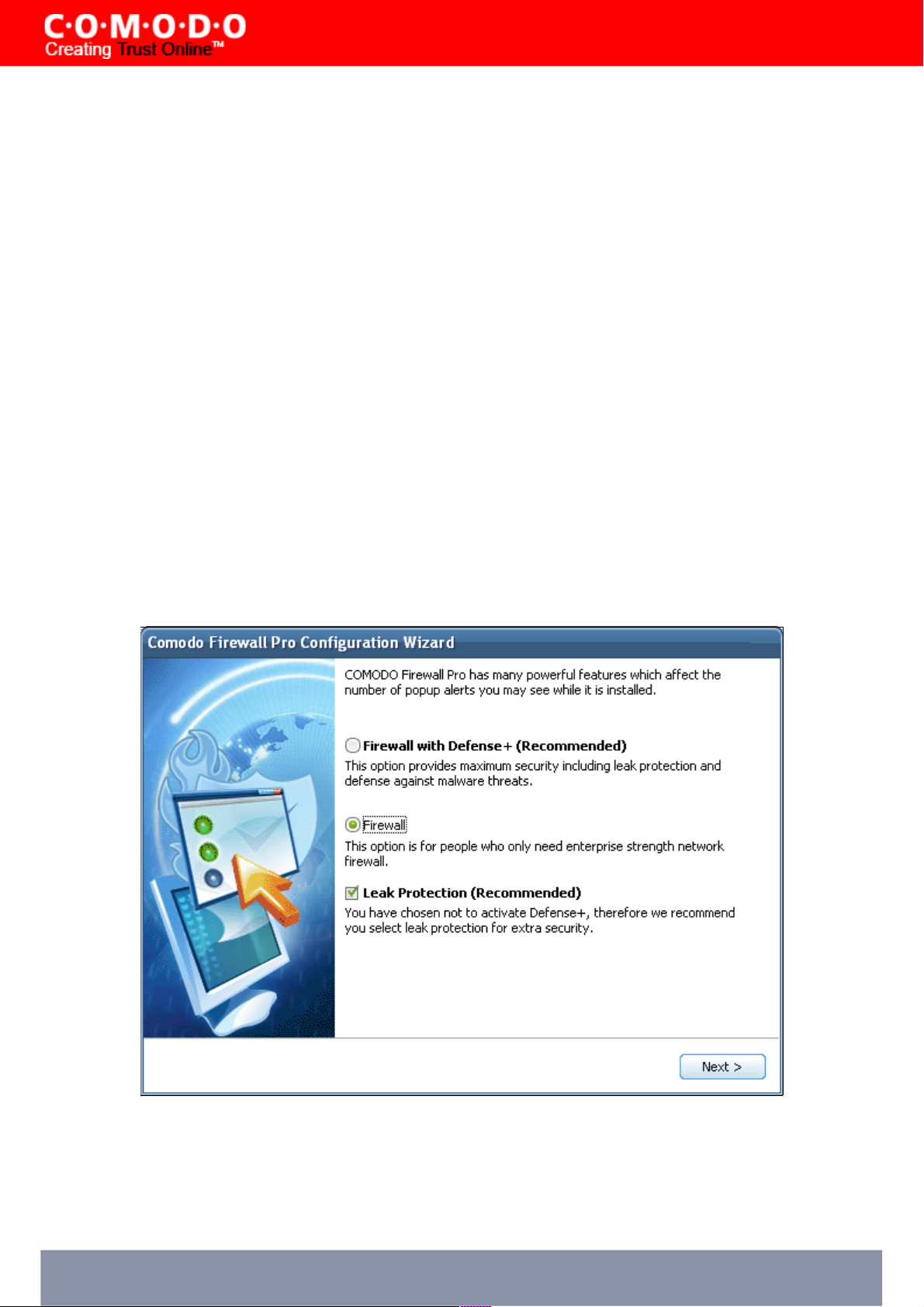
The choices explained:
Firewall with Defense+ (Recommended) - This is the most complete option and offers the greatest level of security.
Choosing this will install Comodo Firewall Pro's Host Intrusion Prevention System - "Defense+" - in addition to the packet
filtering firewall. Defense+ can stop malware, viruses, trojans and worms before they ever get a chance to install
themselves by blocking their ability to make changes to your operating system, applications, registry, running processes
and important system files. This extra layer of protection represents an significant increase in security and is
recommended for the vast majority of users.
Firewall ('Leak Protection' option NOT checked)- This option is only recommended for experienced firewall users
that have alternative Host Intrusion Prevention software installed on their systems. Choosing this option will install ONLY
the packeting filtering network and will not offer leak protection - essential for blocking malicious software (like worms and
trojans) from making outgoing connection attempts. This isn't to say this option is an unwise choice (the network firewall
is one of the strongest available - offering highly effective and configurable inbound and outbound protection) but it is
important to realise that, on it's own, it does not offer the leak protection afforded by Defense+.
If you do not wish to install the full Defense+ option but still want leak protection then we advise you choose:
Firewall (with 'Leak Protection' option checked) - This option installs the packet filtering firewall as above and some,
but not all, Defense+ functionality to provide effective leak protection against malware. Simplistically speaking, this option
will monitor the activities of suspicious executables and will alert the user when an internet connection leak could occur.
Certain monitoring and file/folder protection is, however, disabled under this configuration. This option will create a
protection level that is similar to, but slightly more secure than, the protection offered by Comodo Firewall Pro 2.4.
Click 'Next' to continue installation.
Comodo Firewall Pro 3.0 – User Guide 15
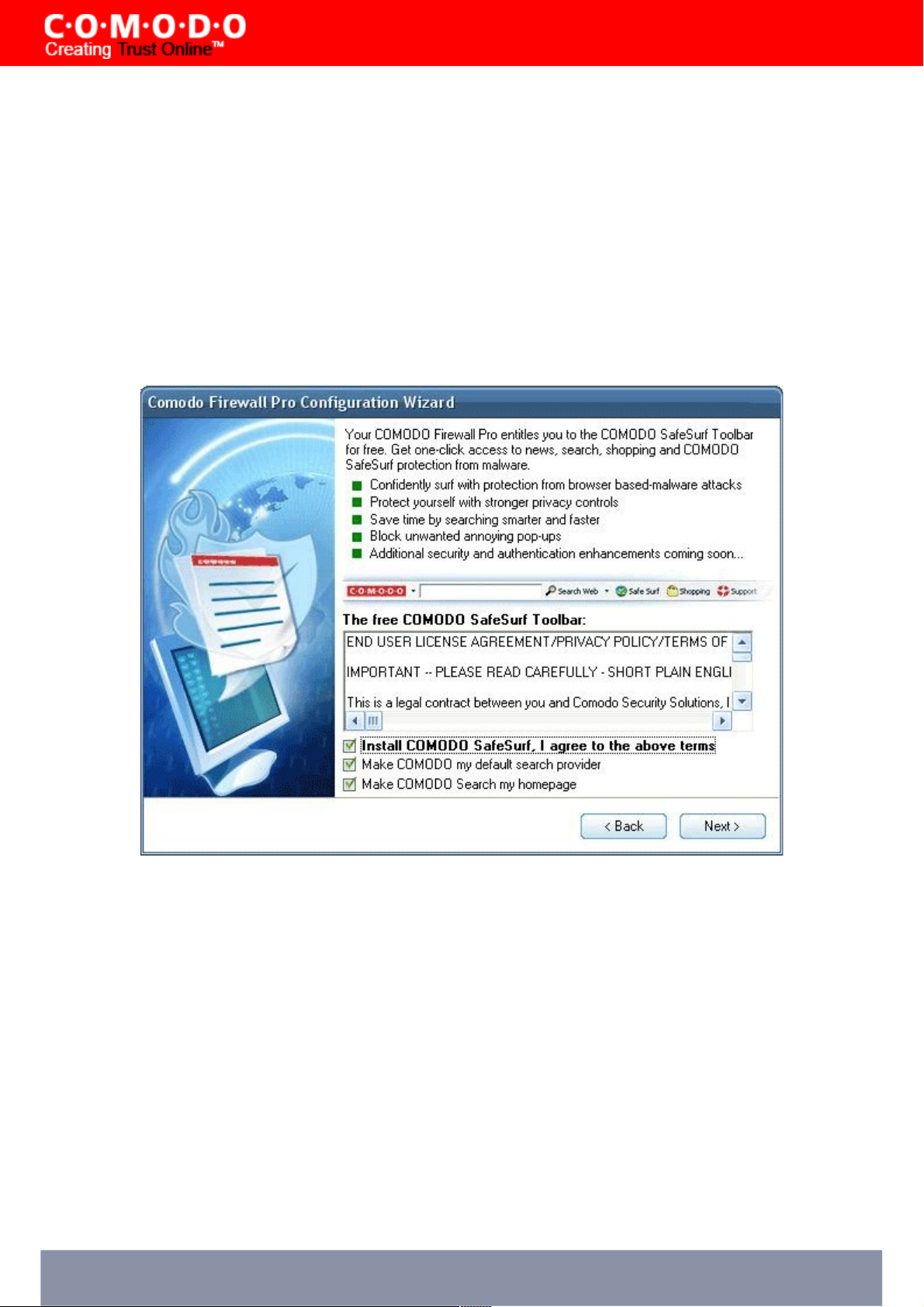
STEP 8: Install Comodo SafeSurf Browser Toolbar
The Comodo SafeSurf Toolbar protects against data theft, computer crashes and system damage by preventing most
types of Buffer Overflow attacks. This type of attack occurs when a malicious program or script deliberately sends more
data to a target applications memory buffer than the buffer can handle - which can be exploited to create a back door to
the system though which a hacker can gain access. Comodo developed the SafeSurf Toolbar explicitly to protect endusers from these kinds of attacks whilst they browse the Internet. After installation, the program will monitor and protect
the memory space of all applications that are running on your system and immediately block any buffer overflow attacks.
Apart from providing another essential layer of protection, the toolbar also provides one-click access to news, search,
shopping; a built in pop-up blocker; is compatible with all major browsers and can be separately uninstalled or disabled at
any time after installation.
After reviewing the EULA and installation options, click 'Next' to continue.
STEP 9: Starting configuration
Next, the installer will begin configuring your system and copying the application signature database to your computer.
Comodo Firewall Pro 3.0 – User Guide 16
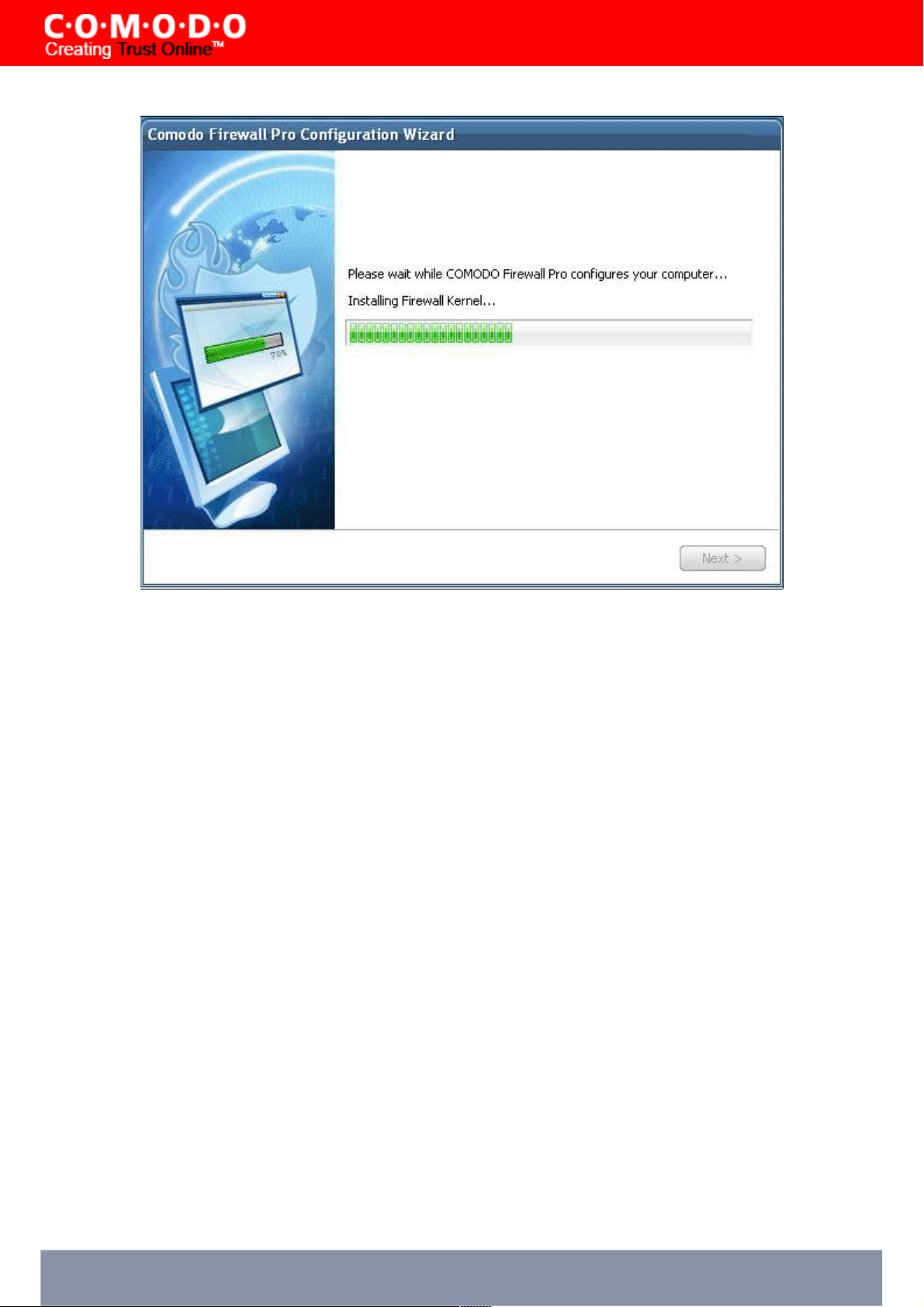
STEP 10: Malware Scanning Setup
Next, Comodo Firewall Pro will scan your computer's fixed drives for the presence of known malware and viruses. It is
strongly recommended that you run the scan as it will help ensure that you computer enjoys the maximum protection
levels right from the first installation of the firewall.
Click Next to begin the scan. If you don't wish to scan at this time then un-check the 'Scan My System for Malware' box
and click 'Finish'.
Comodo Firewall Pro 3.0 – User Guide 17
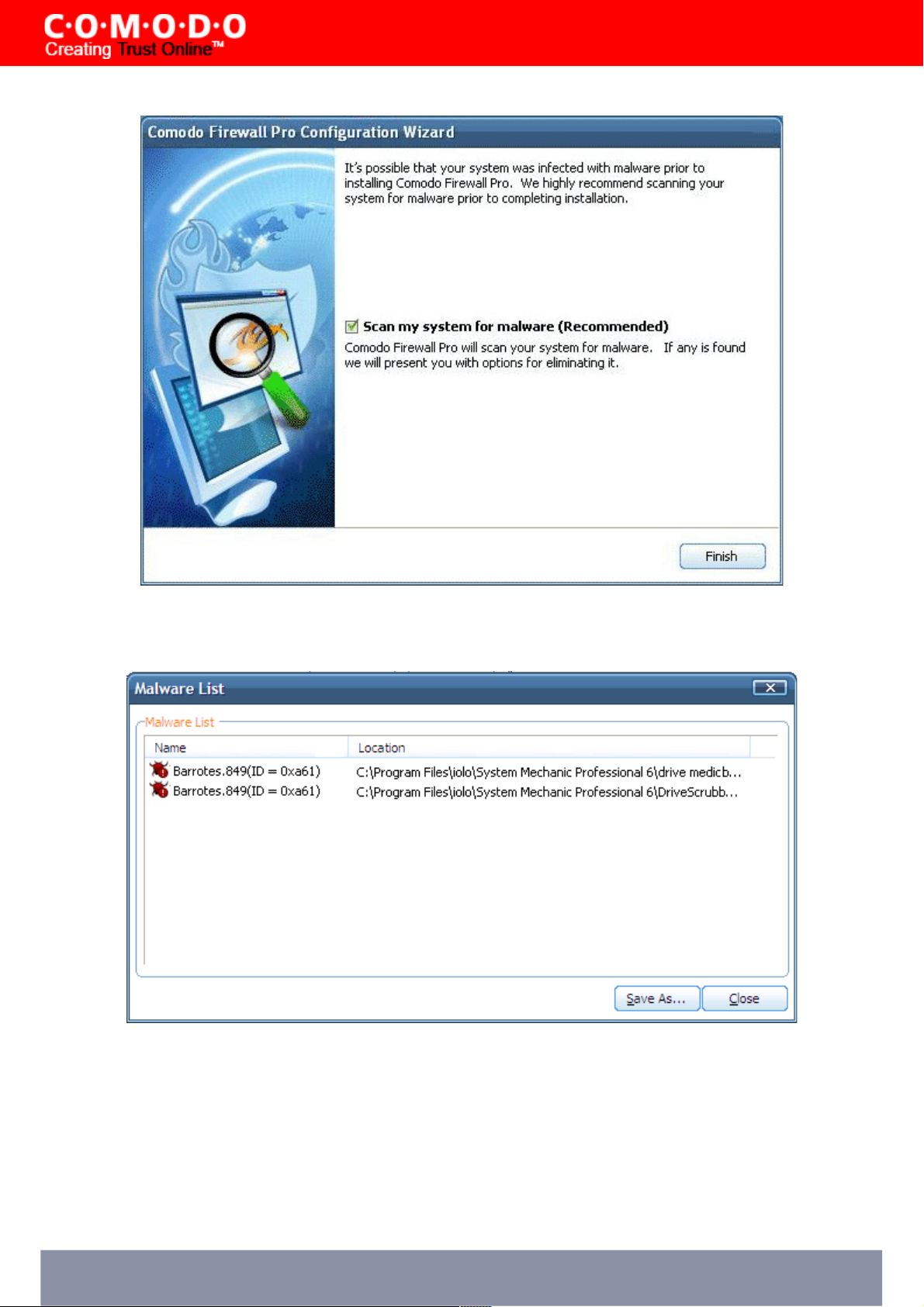
STEP 11: Scanning Progress and Results
Comodo Firewall Pro will now scan your fixed drives for the presence of known viruses and trojans.
At scan completion, you will see a list of any discovered malware.
Comodo Firewall Pro 3.0 – User Guide 18
The example above shows a typical list of discovered malware. By default, all discovered malware is selected
(checkmarked). If you Click "Save As", the detected malware can be saved in your system. Clicking 'Delete All' will
instruct Comodo Firewall Pro to attempt to delete the selected malware. (This is the recommended option). If you click
'Exit' WITHOUT deleting the listed malware, you will be given the following reminder:
Click 'No' to skip malware deletion and proceed to the last stage - Restarting Your System. Click 'Yes' to return to the
scan results screen to delete the discovered malware.
Comodo Firewall Pro 3.0 – User Guide 19
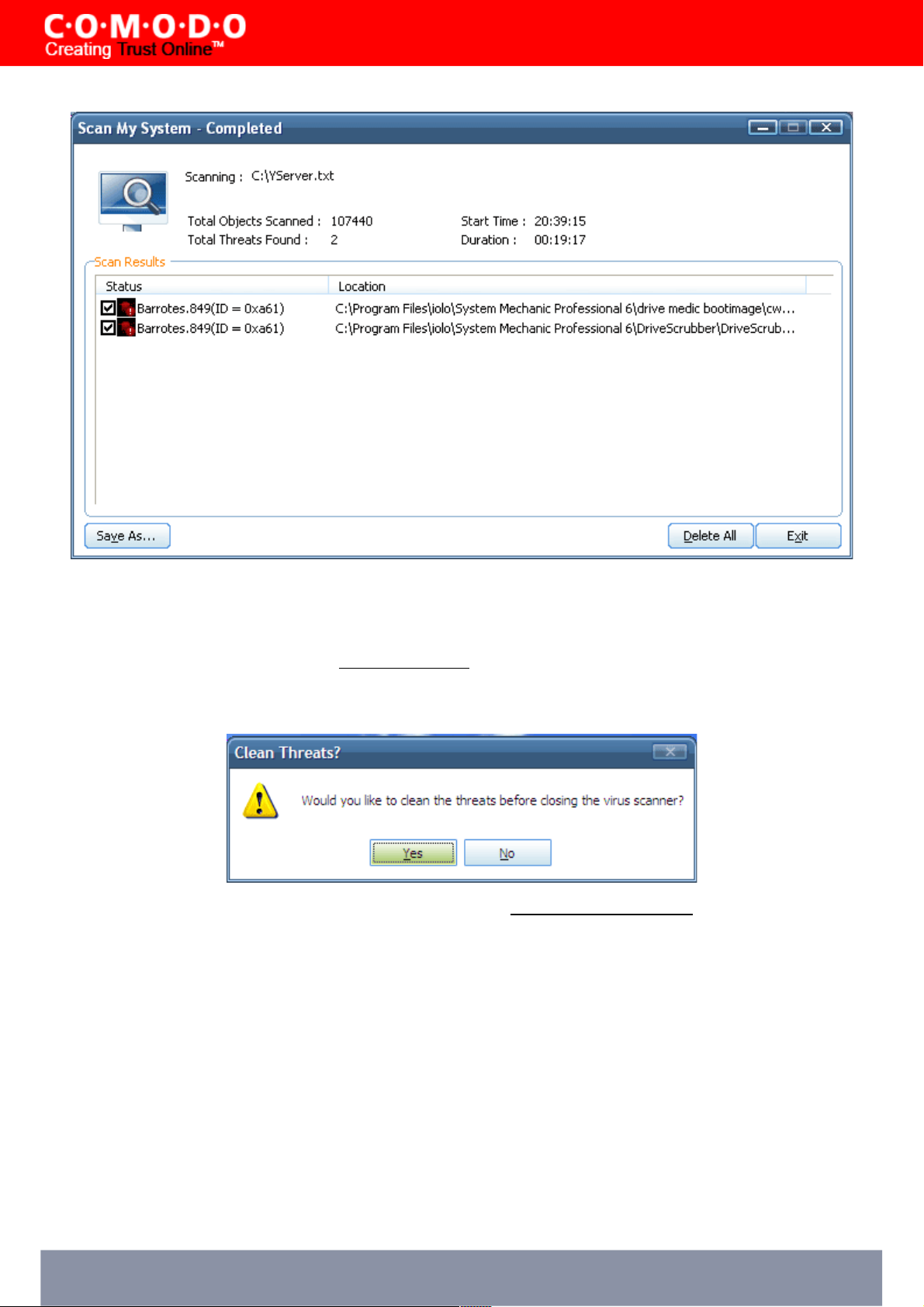
STEP 12: Restart your system
Your system must be restarted in order to finalise the installation. Please save any unsaved data and Click Finish to
reboot. Uncheck the 'Restart Now' option If you would rather reboot at a later time.
STEP 13: After you restart your machine:
After restarting, if your computer is connected to a home or work network, then you will be prompted to configure it at the
'New Private Network Detected!' dialog:
Comodo Firewall Pro 3.0 – User Guide 20

Step 1: Even home users with a single computer will have to configure a home network in order to connect to the internet
(this is usually displayed in the Step 1 text field as you network card). Most users should accept this name.
Step 2: If you wish your computer to accept connections from other PC's in this network or for printer sharing, then also
select this option (e.g. a work or home network). This will then become a trusted network. Users that only have a single
home computer connecting to the internet should avoid this setting.
Select 'Do not automatically detect new networks' If you are an experienced user that wishes to manually set-up their own
trusted networks (this can be done in 'My Network Zones' and through the 'Stealth Ports Wizard')
You must select OK to confirm your choice. If you click on 'Close' button, all the network connections will be blocked.
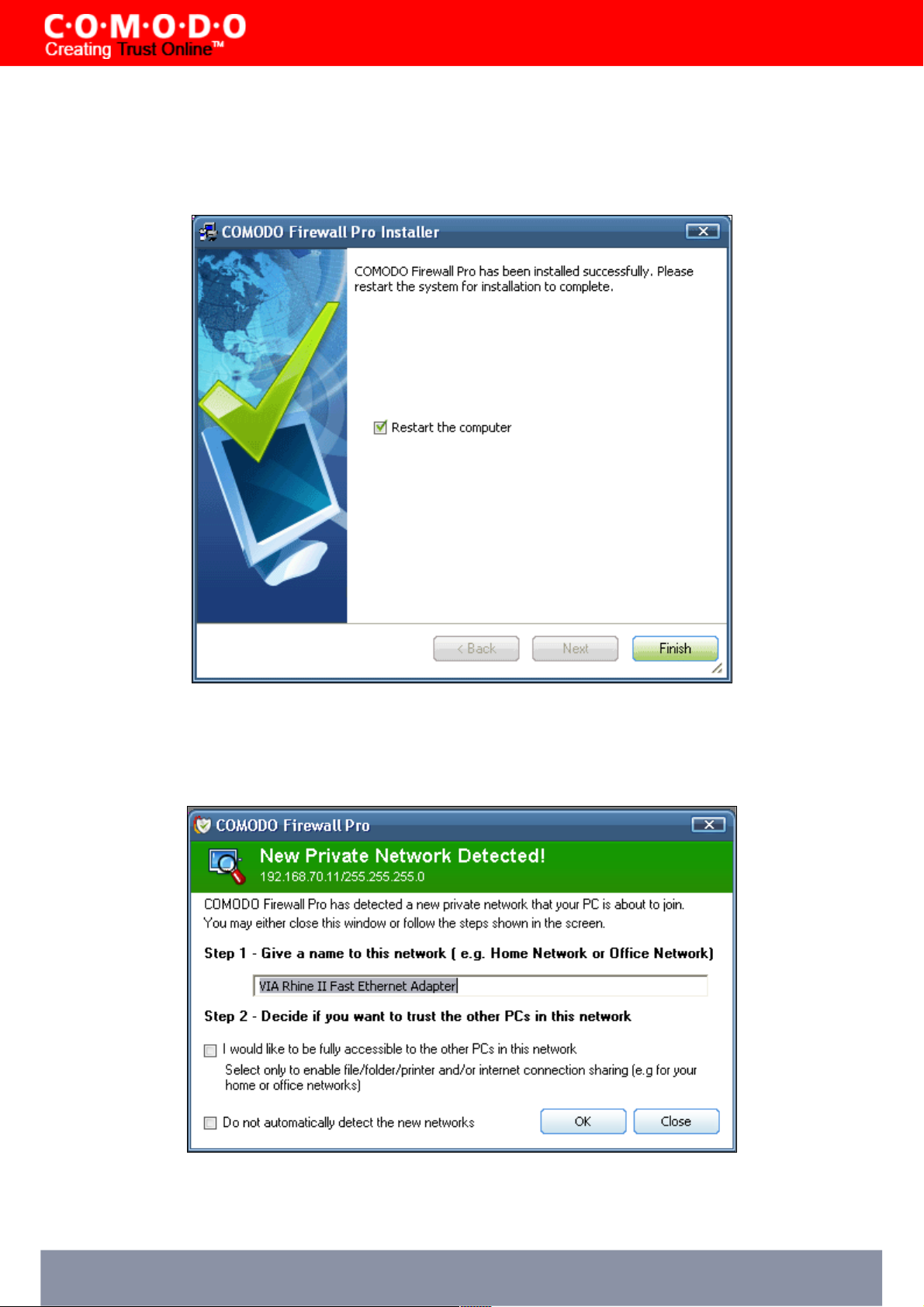
STEP 14: Comodo Firewall Pro Plus
After first rebooting, all users are offered the opportunity to upgrade to Comodo Firewall Pro Plus.
Comodo Firewall Pro Plus is a virus protection and removal service that delivers security and peace of mind above and
beyond traditional anti-virus solutions. From just $39 per year, Comodo experts will remotely diagnose then cleanse your
system of malware and viruses if your machine should become infected. After totally eradicating the malicious software
using a range of specialist security tools , our experts will then reconfigure your firewall to set your computer up for
maximum security. Comodo Firewall Pro Plus is available in two service offerings :
• Comodo Pro Plus - Warranty Only - $39 per year. Virus removal and system remediation in the event your PC
becomes infected by malware. 2 incidents per year. *
• Comodo Pro Plus - Warranty + Installation - $79 per year. Same incident based remediation service as above
PLUS expert installation and configuration of your firewall.
Users that take advantage of the Pro Plus warranty will enjoy the peace of mind afforded by having security experts on
call 24 hours a day to help out in case of emergency.
Scenario one: If no malware remains on your system after the earlier scan then will see the following information dialog
after Windows startup:
Comodo Firewall Pro 3.0 – User Guide 21
Select 'Yes, I'm Interested...' then 'Next >' to be directed to the Comodo website where you can find more details about
the warranty and to complete the registration process.
Select 'No, thanks' then 'Next >' if you are not interested in upgrading to Comodo Firewall Pro Plus. The Comodo Firewall
Pro interface will then open.
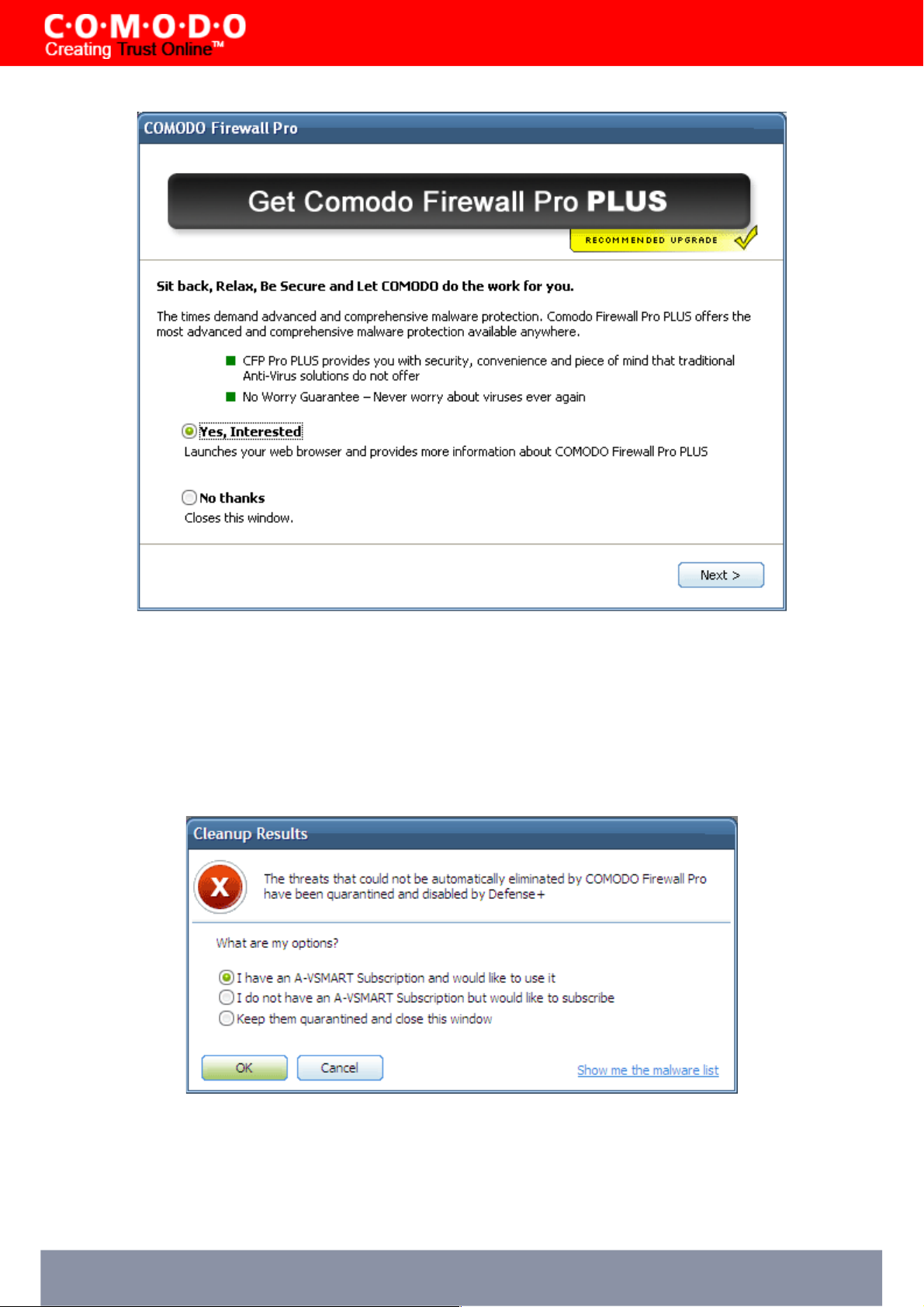
Scenario Two: If any malware could not be automatically deleted (because doing so would be harmful to important files
or to your computer) then you will see the following dialog box:
What are my options?:
• I have an A-VSMART subscription and would like to use it - For existing warranty holders only. Selecting this
option (and clicking OK) will connect to the Comodo servers so you can begin placing a request to remove the
Comodo Firewall Pro 3.0 – User Guide 22

malware on your machine. Comodo Firewall Pro will automatically link the malware scan results to your account.
After professionally removing the malware, our experts will also configure your firewall for optimal security.
• I do not have an A-VSMART subscription but would like to subscribe - Register for an A-VSMART
warranty and get Comodo experts to remove the malware for you before professionally installing and configuring
your firewall for optimal security. If you select this option Comodo Firewall Pro will open your internet browser
and connect to the Comodo website to complete the ordering process.
• Keep them quarantined and close this window: . Clicking 'No' at this dialog will skip the application/service
engagement process and restart your computer. The identified malware will automatically be rendered harmless
and can be manually reviewed and/or removed at a later time by visiting the quarantine section of Comodo
Firewall Pro.
Click OK to continue onto the Comodo Firewall Pro Management interface.
Comodo Firewall Pro management interface
After installation, the Comodo Firewall Pro shortcut will be displayed on the Windows desktop:
To start Comodo Firewall Pro, double-click on the shortcut (or the tray icon) and the management interface will open.
Your computer is automatically protected by the firewall every time you start it. You do not have to explicitly start the
firewall to protect your computer.
Comodo Firewall Pro 3.0 – User Guide 23
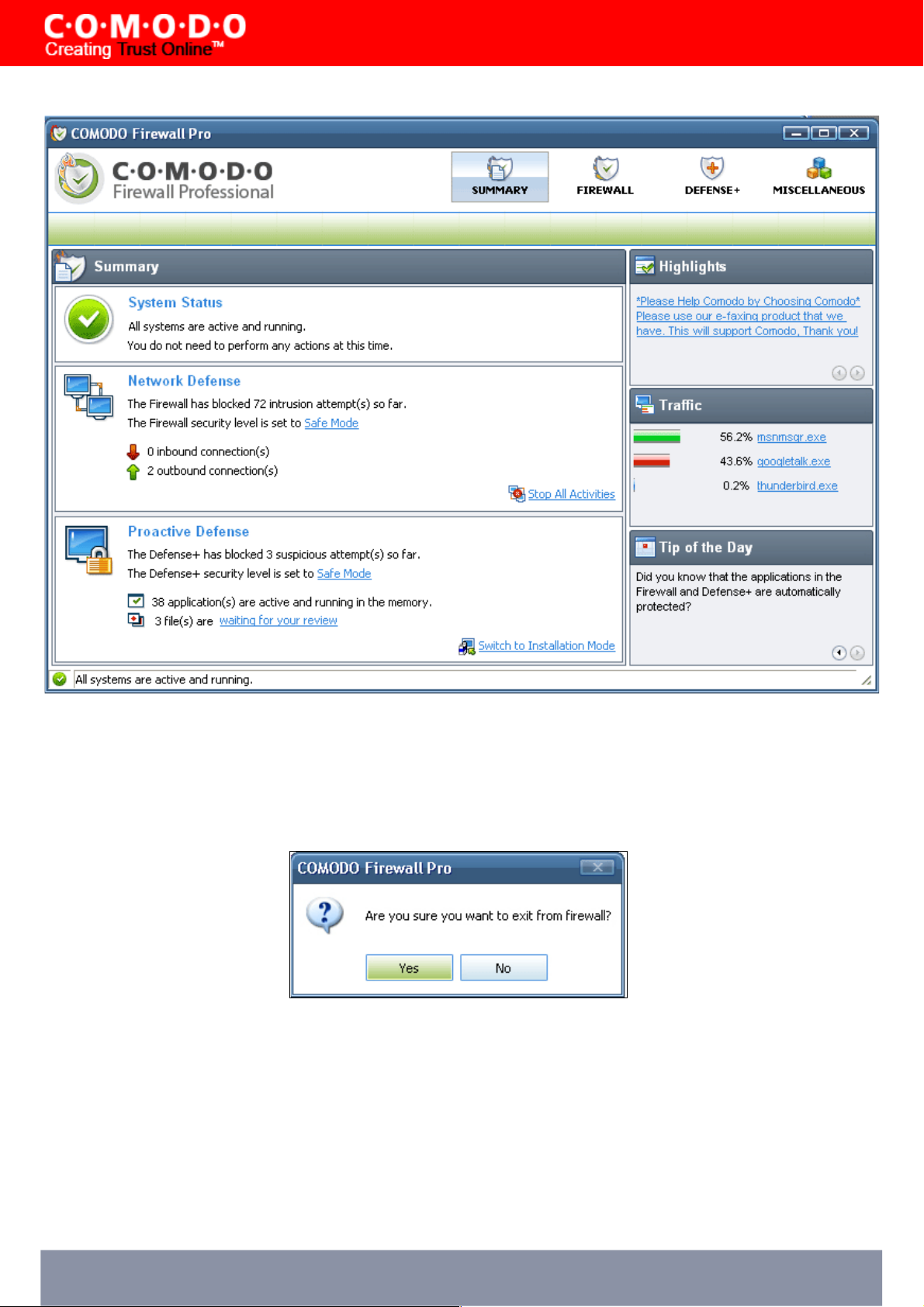
Closing this window will exit the Comodo Firewall Pro management interface. The firewall will remain active, protecting
your computer, in the background.
To completely shut the program down, right-click on the Comodo Firewall Pro and select 'Exit'. If you choose to exit, you
will see a dialog box confirming whether you want to exit or not.
If you choose to exit, the Firewall will be disabled and will not protect your PC.
Comodo Firewall Pro 3.0 – User Guide 24

System Requirements
To ensure optimal performance of Comodo Firewall Pro, please ensure that your PC complies with the minimum system
requirements as stated below:
• Windows Vista (Both 32-bit and 64-bit versions)
• Windows XP (Both 32-bit and 64-bit versions)
• Internet Explorer Version 5.1 or above
• 64 MB available RAM
• 60 MB hard disk space for 32-bit versions and 80MB for 64-bit versions
Starting Comodo Firewall Pro
After installation, Comodo Firewall Pro will automatically start whenever you start Windows. In order to configure and
view settings within Comodo Firewall Pro you need to access the management interface.
There are 3 different ways to access the management interface of Comodo Firewall Pro - System Tray Icon, via Windows
Desktop, via the Windows Start menu.
1. Comodo Firewall Pro Tray Icon
Just double click the shield icon to start the main firewall interface. (By right-clicking on the tray icon, you can access
short cuts to other firewall settings).
2. Windows Desktop
Just double click the shield icon in the desktop to start Comodo Firewall Pro.
3. Start Menu
Comodo Firewall Pro 3.0 – User Guide 25
You can also access Comodo Firewall Pro via the Windows Start Menu.
Click 'Start' and select All Programs->Comodo-> Firewall->Comodo Firewall Pro.
Using any of the methods outlined above will lead you to the main interface as shown below:
Comodo Firewall Pro 3.0 – User Guide 26
General Navigation and Firewall Summary
After installation, Comodo Firewall Pro automatically protects any computer on which it is installed. You do not have to
start the program to be protected.
See Starting Comodo Firewall Pro if you are unsure of how to access the main interface.
Persistent Navigation
Comodo Firewall Pro is divided into four main areas indicated by the icons at the top right hand corner of the interface.
Each of these areas contains several sub-sections that allow you total control over configuration of the firewall and
defense+ settings.
Summary - contains at-a-glance details of firewall settings, activity and new. See the 'Summary' section for more details.
Firewall - clicking this icon will take you to the ' Firewall Tasks ' configuration area. Advanced users are advised to first
visit the Network Security Policy area for an introduction to firewall policies and rule creation
Defense+ - clicking this icon will take you to the 'Defense+' configuration area. Advanced users are advised to first visit
the Computer Security Policy area for an introduction to Defense+ policies and rule creation
Miscellaneous - clicking this icon will take you to the 'Miscellaneous' options section which contains several areas
relating to overall configuration.
Firewall Summary
By default, the management interface displays the 'Summary' area information. You can access this area at any time by
selecting the 'Summary' tab as shown above.
Comodo Firewall Pro 3.0 – User Guide 27
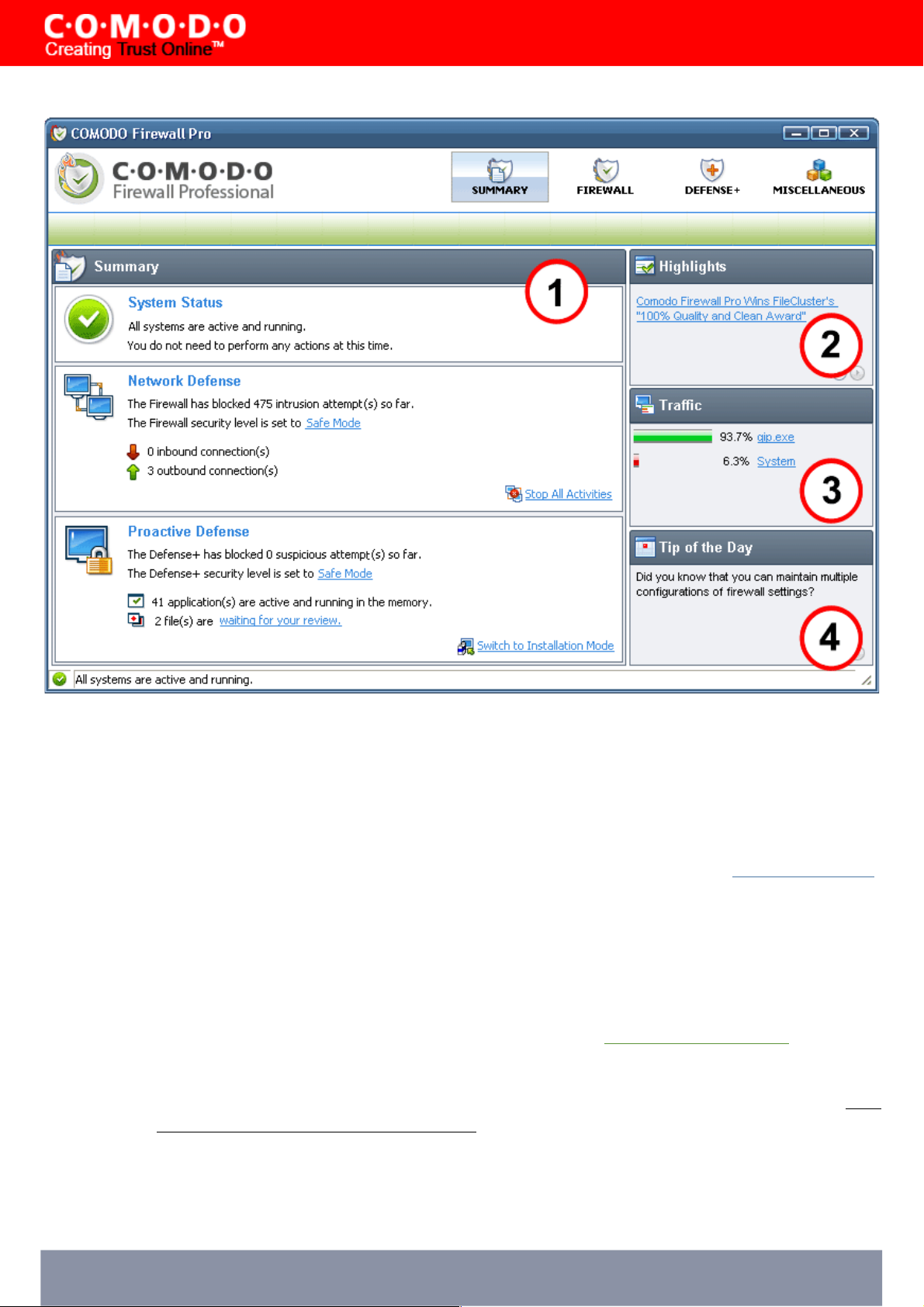
1. Summary:
• System Status - shows systems activity and recommendations on actions you need to perform.
• Network Defense - The 'Network Defense' area contains:
• The total number of intrusion attempts that the firewall has blocked since installation
• Your current Firewall Security Level (or 'Firewall Behaviour Setting) is shown in blue, underlined font.
'Safe Mode' is the Firewall security setting in the example shown above.
• Comodo Firewall Pro allows you to quickly customize firewall security by using the Firewall Security
Level slider to move between preset security levels. Clicking on this blue text opens the firewall behavior
settings panel and allows you to adjust the security level to your own preferences. This section also
allows you to configure the frequency of alerts.
For a complete explanation of this part of the firewall, please see 'Firewall Behavior Settings'.
• Inbound/Outbound Connections. A numerical summary of currently active inbound and outbound
connections to and from your computer. More details on active connections can be found in the 'View
Active Connections' section of 'Firewall Tasks' and the 'Traffic' section on the summary screen.
Comodo Firewall Pro 3.0 – User Guide 28
• 'Stop All Activities' / 'Restore All Activities' - Allows you to toggle network activity on or off.
Specifically, clicking 'Stop All Activities' will instantly block all incoming and outgoing network connections
- placing the firewall in the 'Block All Mode' of 'Firewall Security Settings'. Similarly, clicking 'Restore All
Activities' will re-implement your previous Firewall Security Level
• Proactive Defense - The 'Proactive Defense' area contains:
• The total number of suspicious activities that Defense+ has blocked since installation.
• Your current Defense+ Security Level - shown in blue, underlined font. 'Safe Mode' is the Defense+
security setting in the example shown above.
• Comodo Firewall Pro allows you to quickly customize the Defense+ security level using a convenient
slider to move between preset security levels. Clicking on this blue text opens the Defense+ Settings
panel allows you to quickly access this slider to adjust this security level to your own preferences. This
section also allows you to configure the frequency of alerts. For a complete explanation of this section,
please see 'Defense+ Settings'.
• Number of Currently Active Processes - A quick summary of all processes/applications that are
running on your computer. You can see in-depth details of all running processes by in the 'View Active
Processes' module of Defense+ Tasks.
• Number of files waiting for your review - The number of files currently in the 'My Pending Files'
section. See the 'My Pending Files' section of this help guide for more details.
• 'Switch to Installation Mode' / ' Switch to Previous Mode' - Allows you to quickly toggle between
'Defense+ Installation mode' and your most recent Defense+ Security Level.
'Installation Mode' allows you to quickly install or run an application that you trust which is, as yet,
unknown to Comodo Firewall Pro. For more details, see Defense+ Settings.
2. Highlights - The Highlights section displays information about Security Alerts and News related to Comodo Firewall
Pro & latest Critical security updates. Clicking on the text in the Highlights box takes you to the Comodo website to read
more details.
3. Traffic - The summary screen of Comodo Firewall Pro displays a bar graph showing the applications that are currently
connected to the internet and are sending or receiving data. The summary also displays the % of total traffic each
application is responsible for and the filename of the executable. Clicking on any application leads to the more detailed
'View Active Connections' interface.
4. Tip of the Day - This section contains helps you to use Comodo Firewall Pro to its maximum potential by displaying
information about features you may have missed.
Comodo Firewall Pro 3.0 – User Guide 29
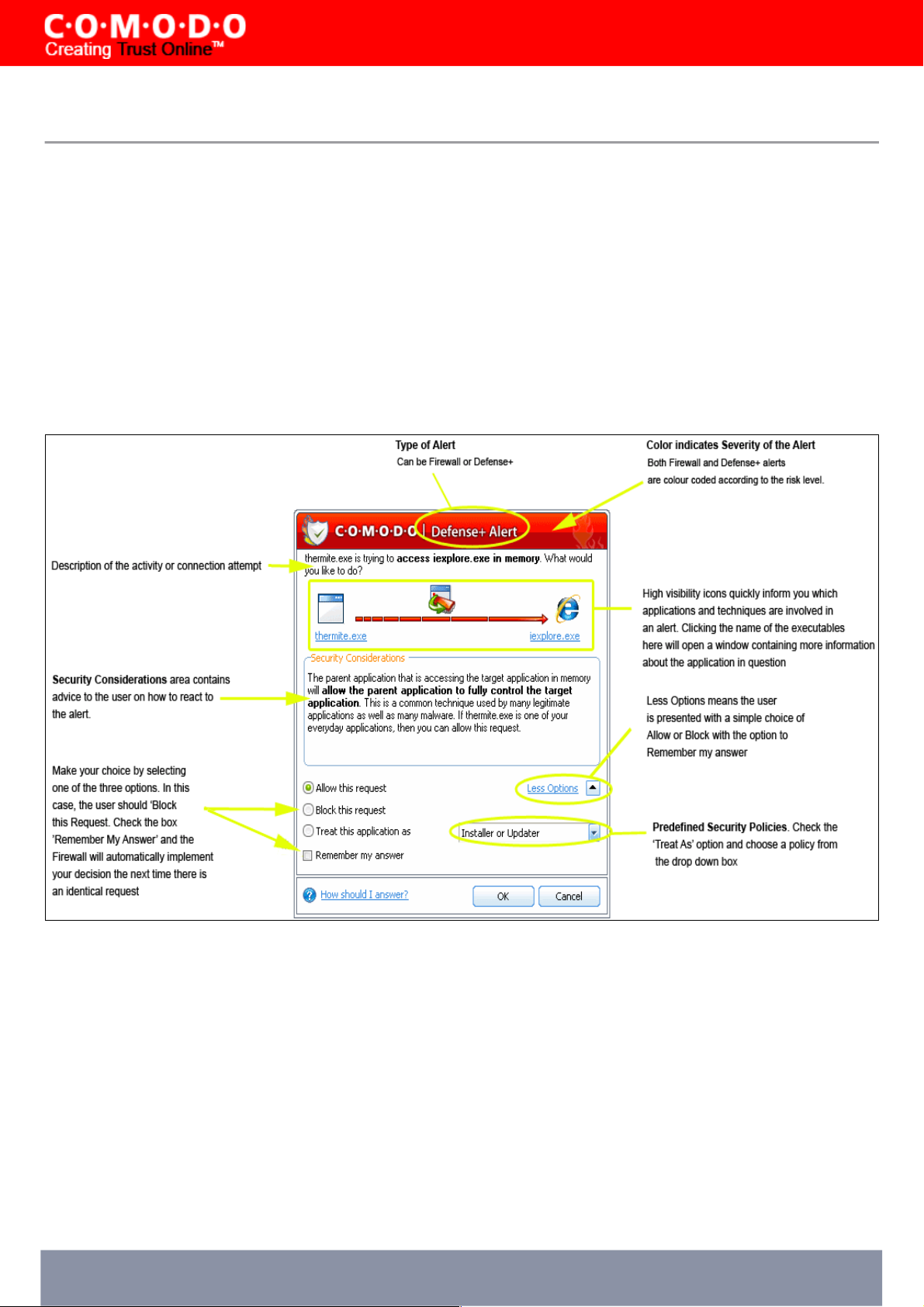
Understanding Alerts
After first installing Comodo Firewall Pro, it is likely that you will see a number of pop-up alerts. This is perfectly normal
and indicates that the firewall is learning your the behavior of your applications and establishing which programs need
Internet access. Each alert provides information and options to allow or block any request and to instruct the firewall how
to behave in future.
Alerts Overview
Comodo Firewall Pro alerts come in two varieties, Firewall Alerts and Defense+ Alerts. Broadly speaking, Firewall alerts
inform you about network connection attempts, whereas Defense+ alerts tell you about the behavior of application on
your system. In both cases, the alert can contain very important security warnings or may simply occur because you are
running an application for the first time. Your reaction should depend on the information that is presented at the alert.
Severity Level
The upper strip of both Defense+ and Firewall alerts are color coded according to risk level. This provides a fast, at-aglance, indicator of the severity of the alert. However, it cannot be stressed enough that you should still read the 'Security
Considerations' section in order to reach an informed decision on allowing or blocking the activity.
Yellow Alerts - Low Severity - In most cases, you can safely approve these connection request or activity. The
'Remember my answer for this application' option is automatically pre-selected for safe requests
Orange Alerts - Medium Severity - Carefully read the ‘Security Considerations section before making a decision. These
Comodo Firewall Pro 3.0 – User Guide 30
 Loading...
Loading...