Page 1

Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
First Published: February 29, 2012
Last Modified: March 22, 2012
Americas Headquarters
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-1706
USA
http://www.cisco.com
Tel: 408 526-4000
800 553-NETS (6387)
Fax: 408 527-0883
Text Part Number: OL-26590-01
Page 2

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS,
INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH
THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY,
CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY.
The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version
of the UNIX operating system. All rights reserved. Copyright©1981, Regents of the University of California.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS.
CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT
LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS
HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: http://
www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership
relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown
for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
©
Cisco Systems, Inc. All rights reserved.
Page 3

CONTENTS
Preface
CHAPTER 1
CHAPTER 2
Preface xi
Audience xi
Document Conventions xi
Related Documentation for Nexus 3000 Series NX-OS Software xii
Obtaining Documentation and Submitting a Service Request xiv
New and Changed Information for this Release 1
New and Changed Information for this Release 1
Overview 3
Layer 2 Ethernet Switching Overview 3
VLANs 3
Private VLANs 4
Spanning Tree 4
STP Overview 4
Rapid PVST+ 5
MST 5
STP Extensions 5
CHAPTER 3
Configuring Ethernet Interfaces 7
Information About Ethernet Interfaces 7
About the Interface Command 7
About the Unidirectional Link Detection Parameter 8
Default UDLD Configuration 9
UDLD Aggressive and Nonaggressive Modes 9
About Interface Speed 10
About the Cisco Discovery Protocol 10
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 iii
Page 4

Contents
Default CDP Configuration 10
About the Error-Disabled State 10
About Port Profiles 11
Guidelines and Limitations for Port Profiles 11
About the Debounce Timer Parameters 11
About MTU Configuration 11
Configuring Ethernet Interfaces 11
Configuring the UDLD Mode 12
Changing an Interface Port Mode 13
Configuring Interface Speed 14
Disabling Link Negotiation 15
Configuring the CDP Characteristics 16
Enabling or Disabling CDP 17
CHAPTER 4
Enabling the Error-Disabled Detection 18
Enabling the Error-Disabled Recovery 19
Configuring the Error-Disabled Recovery Interval 19
Configuring the Debounce Timer 20
Configuring the Description Parameter 20
Disabling and Restarting Ethernet Interfaces 21
Displaying Interface Information 21
Displaying Input Packet Discard Information 23
Default Physical Ethernet Settings 24
Configuring VLANs 27
Information About VLANs 27
Understanding VLANs 27
VLAN Ranges 28
Creating, Deleting, and Modifying VLANs 29
About the VLAN Trunking Protocol 30
Guidelines and Limitations for VTP 30
Configuring a VLAN 30
Creating and Deleting a VLAN 30
Configuring a VLAN 31
Adding Ports to a VLAN 32
Configuring a VLAN as a Routed SVI 33
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
iv OL-26590-01
Page 5

Contents
Configuring a VLAN as a Management SVI 34
Configuring VTP 34
Verifying VLAN Configuration 36
CHAPTER 5
Configuring Private VLANs 37
Information About Private VLANs 37
Primary and Secondary VLANs in Private VLANs 38
Private VLAN Ports 38
Primary, Isolated, and Community Private VLANs 39
Associating Primary and Secondary VLANs 40
Private VLAN Promiscuous Trunks 41
Private VLAN Isolated Trunks 41
Broadcast Traffic in Private VLANs 41
Private VLAN Port Isolation 41
Guidelines and Limitations for Private VLANs 42
Configuring a Private VLAN 42
Enabling Private VLANs 42
Configuring a VLAN as a Private VLAN 43
Associating Secondary VLANs with a Primary Private VLAN 43
Configuring an Interface as a Private VLAN Host Port 45
CHAPTER 6
Configuring an Interface as a Private VLAN Promiscuous Port 45
Configuring a Promiscuous Trunk Port 46
Configuring an Isolated Trunk Port 46
Configuring the Allowed VLANs for PVLAN Trunking Ports 46
Configuring Native 802.1Q VLANs on Private VLANs 47
Verifying the Private VLAN Configuration 47
Configuring Access and Trunk Interfaces 49
Information About Access and Trunk Interfaces 49
Understanding Access and Trunk Interfaces 49
Understanding IEEE 802.1Q Encapsulation 50
Understanding Access VLANs 51
Understanding the Native VLAN ID for Trunk Ports 52
Understanding Allowed VLANs 52
Understanding Native 802.1Q VLANs 52
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 v
Page 6

Contents
Configuring Access and Trunk Interfaces 53
Configuring a LAN Interface as an Ethernet Access Port 53
Configuring Access Host Ports 54
Configuring Trunk Ports 54
Configuring the Native VLAN for 802.1Q Trunking Ports 55
Configuring the Allowed VLANs for Trunking Ports 55
Configuring Native 802.1Q VLANs 56
Verifying Interface Configuration 57
CHAPTER 7
CHAPTER 8
Configuring Switching Modes 59
Information About Switching Modes 59
Guidelines and Limitations for Switching Modes 60
Licensing Requirements for Switching Modes 60
Default Settings for Switching Modes 61
Configuring Switching Modes 61
Enabling Store-and-Forward Switching 61
Reenabling Cut-Through Switching 61
Feature History for Switching Modes 62
Configuring Rapid PVST+ 63
Information About Rapid PVST+ 63
Understanding STP 63
STP Overview 63
Understanding How a Topology is Created 64
Understanding the Bridge ID 64
Bridge Priority Value 64
Extended System ID 65
STP MAC Address Allocation 65
Understanding BPDUs 66
Election of the Root Bridge 67
Creating the Spanning Tree Topology 67
Understanding Rapid PVST+ 68
Rapid PVST+ Overview 68
Rapid PVST+ BPDUs 69
Proposal and Agreement Handshake 70
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
vi OL-26590-01
Page 7

Contents
Protocol Timers 71
Port Roles 71
Port States 72
Rapid PVST+ Port State Overview 72
Blocking State 73
Learning State 73
Forwarding State 73
Disabled State 74
Summary of Port States 74
Synchronization of Port Roles 74
Processing Superior BPDU Information 75
Processing Inferior BPDU Information 76
Spanning-Tree Dispute Mechanism 76
Port Cost 76
Port Priority 77
Rapid PVST+ and IEEE 802.1Q Trunks 77
Rapid PVST+ Interoperation with Legacy 802.1D STP 77
Rapid PVST+ Interoperation with 802.1s MST 78
Configuring Rapid PVST+ 78
Enabling Rapid PVST+ 78
Enabling Rapid PVST+ per VLAN 79
Configuring the Root Bridge ID 80
Configuring a Secondary Root Bridge 81
Configuring the Rapid PVST+ Port Priority 82
Configuring the Rapid PVST+ Pathcost Method and Port Cost 83
Configuring the Rapid PVST+ Bridge Priority of a VLAN 83
Configuring the Rapid PVST+ Hello Time for a VLAN 84
Configuring the Rapid PVST+ Forward Delay Time for a VLAN 85
Configuring the Rapid PVST+ Maximum Age Time for a VLAN 85
Specifying the Link Type 85
Restarting the Protocol 86
Verifying Rapid PVST+ Configurations 86
CHAPTER 9
Configuring Multiple Spanning Tree 89
Information About MST 89
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 vii
Page 8

Contents
MST Overview 89
MST Regions 90
MST BPDUs 90
MST Configuration Information 91
IST, CIST, and CST 91
IST, CIST, and CST Overview 91
Spanning Tree Operation Within an MST Region 92
Spanning Tree Operations Between MST Regions 92
MST Terminology 93
Hop Count 94
Boundary Ports 94
Spanning-Tree Dispute Mechanism 95
Port Cost and Port Priority 96
Interoperability with IEEE 802.1D 96
Interoperability with Rapid PVST+: Understanding PVST Simulation 97
Configuring MST 97
MST Configuration Guidelines 97
Enabling MST 97
Entering MST Configuration Mode 98
Specifying the MST Name 99
Specifying the MST Configuration Revision Number 100
Specifying the Configuration on an MST Region 100
Mapping and Unmapping VLANs to MST Instances 102
Mapping Secondary VLANs to Same MSTI as Primary VLANs for Private VLANs 102
Configuring the Root Bridge 103
Configuring a Secondary Root Bridge 104
Configuring the Port Priority 105
Configuring the Port Cost 106
Configuring the Switch Priority 106
Configuring the Hello Time 107
Configuring the Forwarding-Delay Time 108
Configuring the Maximum-Aging Time 108
Configuring the Maximum-Hop Count 109
Configuring PVST Simulation Globally 109
Configuring PVST Simulation Per Port 110
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
viii OL-26590-01
Page 9

Contents
Specifying the Link Type 111
Restarting the Protocol 111
Verifying MST Configurations 112
CHAPTER 10
Configuring STP Extensions 113
About STP Extensions 113
Information About STP Extensions 113
Understanding STP Port Types 113
Spanning Tree Edge Ports 113
Spanning Tree Network Ports 114
Spanning Tree Normal Ports 114
Understanding Bridge Assurance 114
Understanding BPDU Guard 114
Understanding BPDU Filtering 115
Understanding Loop Guard 116
Understanding Root Guard 116
Configuring STP Extensions 117
STP Extensions Configuration Guidelines 117
Configuring Spanning Tree Port Types Globally 117
Configuring Spanning Tree Edge Ports on Specified Interfaces 118
CHAPTER 11
CHAPTER 12
Configuring Spanning Tree Network Ports on Specified Interfaces 119
Enabling BPDU Guard Globally 120
Enabling BPDU Guard on Specified Interfaces 121
Enabling BPDU Filtering Globally 122
Enabling BPDU Filtering on Specified Interfaces 123
Enabling Loop Guard Globally 124
Enabling Loop Guard or Root Guard on Specified Interfaces 124
Verifying STP Extension Configuration 125
Configuring LLDP 127
Configuring Global LLDP Commands 127
Configuring Interface LLDP Commands 129
Configuring the MAC Address Table 131
Information About MAC Addresses 131
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 ix
Page 10

Contents
Configuring MAC Addresses 131
Configuring a Static MAC Address 131
Configuring the Aging Time for the MAC Table 132
Clearing Dynamic Addresses from the MAC Table 133
Verifying the MAC Address Configuration 133
CHAPTER 13
CHAPTER 14
Configuring IGMP Snooping 135
Information About IGMP Snooping 135
IGMPv1 and IGMPv2 136
IGMPv3 137
IGMP Snooping Querier 137
IGMP Forwarding 137
Configuring IGMP Snooping Parameters 138
Verifying IGMP Snooping Configuration 141
Configuring Traffic Storm Control 143
Information About Traffic Storm Control 143
Traffic Storm Guidelines and Limitations 144
Configuring Traffic Storm Control 145
Verifying Traffic Storm Control Configuration 146
Traffic Storm Control Example Configuration 146
Default Traffic Storm Settings 146
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
x OL-26590-01
Page 11

Preface
This preface contains the following sections:
Audience, page xi
•
Document Conventions, page xi
•
Related Documentation for Nexus 3000 Series NX-OS Software, page xii
•
Obtaining Documentation and Submitting a Service Request, page xiv
•
Audience
This publication is for experienced network administrators who configure and maintain Cisco Nexus Series
devices.
Document Conventions
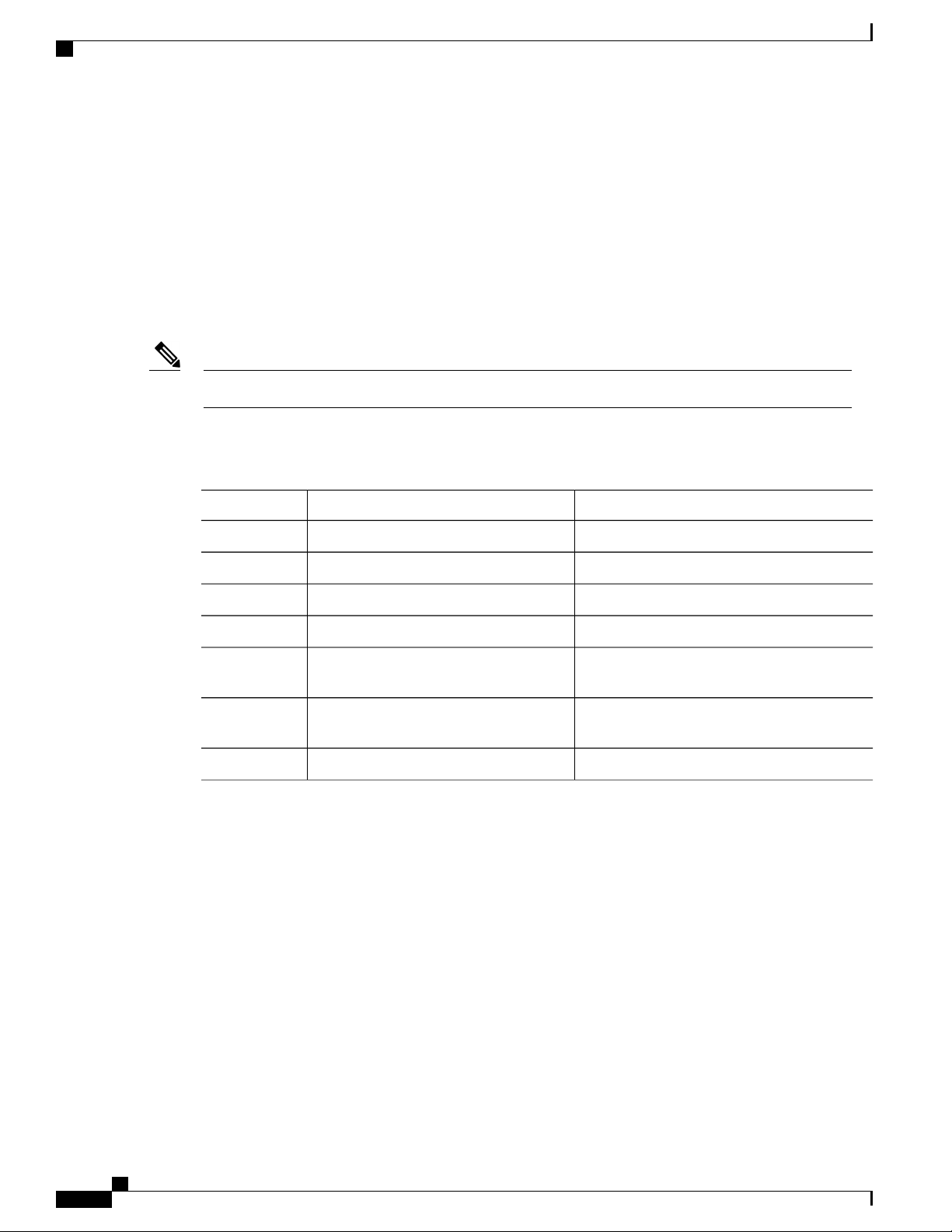
Command descriptions use the following conventions:
DescriptionConvention
bold
Italic
[x | y]
{x | y}
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 xi
Bold text indicates the commands and keywords that you enter literally
as shown.
Italic text indicates arguments for which the user supplies the values.
Square brackets enclose an optional element(keyword or argument).[x]
Square brackets enclosing keywords or arguments separated by a vertical
bar indicate an optional choice.
Braces enclosing keywords or arguments separated by a vertical bar
indicate a required choice.
Page 12
Related Documentation for Nexus 3000 Series NX-OS Software
Preface
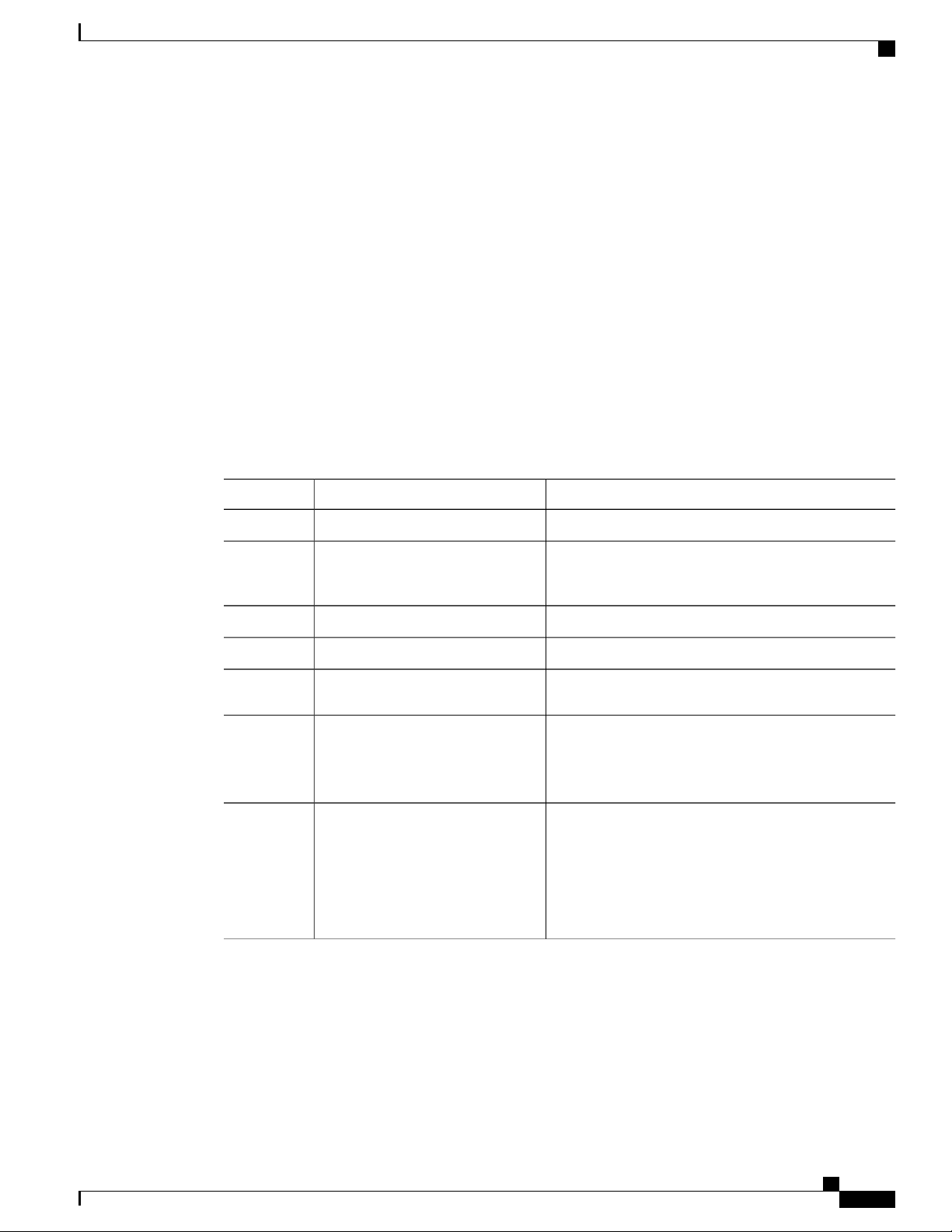
DescriptionConvention
[x {y | z}]
Nested set of square brackets or braces indicate optional or required
choices within optional or required elements. Braces and a vertical bar
within square brackets indicate a required choice within an optional
element.
variable
Indicates a variable for which you supply values, in context where italics
cannot be used.
string
A nonquoted set of characters. Do not use quotation marks around the
string or the string will include the quotation marks.
Examples use the following conventions:
DescriptionConvention
Terminal sessions and information the switch displays are in screen font.screen font
Information you must enter is in boldface screen font.boldface screen font
italic screen font
Arguments for which you supply values are in italic screen font.
Nonprinting characters, such as passwords, are in angle brackets.< >
Default responses to system prompts are in square brackets.[ ]
!, #
An exclamation point (!) or a pound sign (#) at the beginning of a line
of code indicates a comment line.
This document uses the following conventions:
Note
Means reader take note. Notes contain helpful suggestions or references to material not covered in the
manual.
Caution
Means reader be careful. In this situation, you might do something that could result in equipment damage
or loss of data.
Related Documentation for Nexus 3000 Series NX-OS Software
The entire Cisco NX-OS 3000 Series documentation set is available at the following URL:
http://www.cisco.com/en/US/products/ps11541/tsd_products_support_series_home.html
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
xii OL-26590-01
Page 13

Preface
Related Documentation for Nexus 3000 Series NX-OS Software
Release Notes
The release notes are available at the following URL:
http://www.cisco.com/en/US/products/ps11541/prod_release_notes_list.html
Installation and Upgrade Guides
The installation and upgrade guides are available at the following URL:
http://www.cisco.com/en/US/products/ps11541/prod_installation_guides_list.html
The documents in this category include:
Cisco Nexus 5000 Series, Cisco Nexus 3000 Series, and Cisco Nexus 2000 Series Safety Information
•
and Documentation
Regulatory, Compliance, and Safety Information for the Cisco Nexus 5000 Series, Cisco Nexus 3000
•
Series, and Cisco Nexus 2000 Series
Cisco Nexus 3000 Series Hardware Installation Guide
•
Configuration Guides
The configuration guides are available at the following URL:
http://www.cisco.com/en/US/products/ps11541/products_installation_and_configuration_guides_list.html
The documents in this category include:
Configuration Limits for Cisco NX-OS
•
Fundamentals Configuration Guide
•
Layer 2 Switching Configuration Guide
•
Multicast Configuration Guide
•
Quality of Service Configuration Guide
•
Security Configuration Guide
•
System Management Configuration Guide
•
Unicast Routing Configuration Guide
•
Verified Scalability Guide for Cisco NX-OS
•
Technical References
The technical references are available at the following URL:
http://www.cisco.com/en/US/products/ps11541/prod_technical_reference_list.html
Error and System Messages
The error and system message reference guides are available at the following URL:
http://www.cisco.com/en/US/products/ps11541/products_system_message_guides_list.html
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 xiii
Page 14

Preface
Obtaining Documentation and Submitting a Service Request
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information,
see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco
technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What's New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed
and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free
service and Cisco currently supports RSS version 2.0.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
xiv OL-26590-01
Page 15

CHAPTER 1
New and Changed Information for this Release
The following table provides an overview of the significant changes to this guide for this current release.
The table does not provide an exhaustive list of all changes made to the configuration guides or of the new
features in this release.
New and Changed Information for this Release, page 1
•
New and Changed Information for this Release
The following table provides an overview of the significant changes to this guide for this current release. The
table does not provide an exhaustive list of all changes made to the configuration guides or of the new features
in this release.
Table 1: New and Changed Features
Switching Modes
DescriptionFeature
switching mode. There are two switching
modes: cut-through and store-and-forward.
Changed
in
Release
5.0(3)U3(1)Added a new chapter about configuring your
Where DocumentedAdded or
Configuring Switching
Modes, on page 59
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 1
Page 16

New and Changed Information for this Release
New and Changed Information for this Release
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
2 OL-26590-01
Page 17

Overview
This chapter contains the following sections:
Layer 2 Ethernet Switching Overview, page 3
•
VLANs, page 3
•
Private VLANs, page 4
•
Spanning Tree , page 4
•
Layer 2 Ethernet Switching Overview
The device supports simultaneous, parallel connections between Layer 2 Ethernet segments. Switched
connections between Ethernet segments last only for the duration of the packet. New connections can be made
between different segments for the next packet.
The device solves congestion problems caused by high-bandwidth devices and a large number of users by
assigning each device (for example, a server) to its own 10-, 100-, 1000-Mbps, or 10-Gigabit collision domain.
Because each LAN port connects to a separate Ethernet collision domain, servers in a switched environment
achieve full access to the bandwidth.
Because collisions cause significant congestion in Ethernet networks, an effective solution is full-duplex
communication. Typically, 10/100-Mbps Ethernet operates in half-duplex mode, which means that stations
can either receive or transmit. In full-duplex mode, which is configurable on these interfaces, two stations
can transmit and receive at the same time. When packets can flow in both directions simultaneously, the
effective Ethernet bandwidth doubles. 1/10-Gigabit Ethernet operates in full-duplex only.
CHAPTER 2
VLANs
A VLAN is a switched network that is logically segmented by function, project team, or application, without
regard to the physical locations of the users. VLANs have the same attributes as physical LANs, but you can
group end stations even if they are not physically located on the same LAN segment.
Any switch port can belong to a VLAN, and unicast, broadcast, and multicast packets are forwarded and
flooded only to end stations in that VLAN. Each VLAN is considered as a logical network, and packets
destined for stations that do not belong to the VLAN must be forwarded through a bridge or a router.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 3
Page 18

Private VLANs
All ports, including the management port, are assigned to the default VLAN (VLAN1) when the device first
comes up. A VLAN interface, or switched virtual interface (SVI), is a Layer 3 interface that is created to
provide communication between VLANs.
The devices support 4094 VLANs in accordance with the IEEE 802.1Q standard. These VLANs are organized
into several ranges, and you use each range slightly differently. Some of these VLANs are reserved for internal
use by the device and are not available for configuration.
Inter-Switch Link (ISL) trunking is not supported on the NX-OS software for the Cisco Nexus 3000 Series.Note
Private VLANs
Private VLANs provide traffic separation and security at the Layer 2 level.
A private VLAN is one or more pairs of a primary VLAN and a secondary VLAN, all with the same primary
VLAN. The two types of secondary VLANs are isolated and community VLANs. Hosts on isolated VLANs
communicate only with hosts in the primary VLAN. Hosts in a community VLAN can communicate only
among themselves and with hosts in the primary VLAN but not with hosts in isolated VLANs or in other
community VLANs.
Regardless of the combination of isolated and community secondary VLANs, all interfaces within the primary
VLAN comprise one Layer 2 domain, and therefore, require only one IP subnet.
Overview
Spanning Tree
This section discusses the implementation of the Spanning Tree Protocol (STP). Spanning tree is used to refer
to IEEE 802.1w and IEEE 802.1s. When the IEEE 802.1D Spanning Tree Protocol is referred to in the
publication, 802.1D is stated specifically.
STP Overview
STP provides a loop-free network at the Layer 2 level. Layer 2 LAN ports send and receive STP frames,
which are called Bridge Protocol Data Units (BPDUs), at regular intervals. Network devices do not forward
these frames but use the frames to construct a loop-free path.
802.1D is the original standard for STP, and many improvements have enhanced the basic loop-free STP.
You can create a separate loop-free path for each VLAN, which is named Per VLAN Spanning Tree (PVST+).
Additionally, the entire standard was reworked to make the loop-free convergence process faster to keep up
with the faster equipment. This STP standard with faster convergence is the 802.1w standard, which is known
as Rapid Spanning Tree (RSTP).
Finally, the 802.1s standard, Multiple Spanning Trees (MST), allows you to map multiple VLANs into a
single spanning tree instance. Each instance runs an independent spanning tree topology.
Although the software can interoperate with legacy 802.1D systems, the system runs Rapid PVST+ and MST.
You can use either Rapid PVST+ or MST in a given VDC; you cannot mix both in one VDC. Rapid PVST+
is the default STP protocol for Cisco NX-OS for the Cisco Nexus 3000 Series.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
4 OL-26590-01
Page 19
Overview
Rapid PVST+
Note
Rapid PVST+
MST
Cisco NX-OS for the Cisco Nexus 3000 Series uses the extended system ID and MAC address reduction;
you cannot disable these features.
In addition, Cisco has created some proprietary features to enhance the spanning tree activities.
Rapid PVST+ is the default spanning tree mode for the software and is enabled by default on the default
VLAN and all newly created VLANs.
A single instance, or topology, of RSTP runs on each configured VLAN, and each Rapid PVST+ instance on
a VLAN has a single root device. You can enable and disable STP on a per-VLAN basis when you are running
Rapid PVST+.
The software also supports MST. The multiple independent spanning tree topologies enabled by MST provide
multiple forwarding paths for data traffic, enable load balancing, and reduce the number of STP instances
required to support a large number of VLANs.
MST incorporates RSTP, so it also allows rapid convergence. MST improves the fault tolerance of the network
because a failure in one instance (forwarding path) does not affect other instances (forwarding paths).
Note
Changing the spanning tree mode disrupts the traffic because all spanning tree instances are stopped for
the previous mode and started for the new mode.
You can force specified interfaces to send prestandard, rather than standard, MST messages using the
command-line interface.
STP Extensions
The software supports the following Cisco proprietary features:
• Spanning tree port types—The default spanning tree port type is normal. You can configure interfaces
connected to Layer 2 hosts as edge ports and interfaces connected to Layer 2 switches or bridges as
network ports.
• Bridge Assurance—Once you configure a port as a network port, Bridge Assurance sends BPDUs on
all ports and moves a port into the blocking state if it no longer receives BPDUs. This enhancement is
available only when you are running Rapid PVST+ or MST.
• BPDU Guard—BPDU Guard shuts down the port if that port receives a BPDU.
• BPDU Filter—BPDU Filter suppresses sending and receiving BPDUs on the port.
• Loop Guard—Loop Guard prevents the nondesignated ports from transitioning to the STP forwarding
state, which prevents loops in the network.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 5
Page 20

STP Extensions
Overview
• Root Guard—Root Guard prevents the port from becoming the root in an STP topology.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
6 OL-26590-01
Page 21

CHAPTER 3
Configuring Ethernet Interfaces
This chapter contains the following sections:
Information About Ethernet Interfaces, page 7
•
Configuring Ethernet Interfaces, page 11
•
Displaying Interface Information, page 21
•
Displaying Input Packet Discard Information, page 23
•
Default Physical Ethernet Settings , page 24
•
Information About Ethernet Interfaces
The Ethernet ports can operate as standard Ethernet interfaces connected to servers or to a LAN.
On a Cisco Nexus 3000 Series switch, the Ethernet interfaces are enabled by default.
About the Interface Command
You can enable the various capabilities of the Ethernet interfaces on a per-interface basis using the interface
command. When you enter the interface command, you specify the following information:
• Interface type—All physical Ethernet interfaces use the ethernet keyword.
Slot number
•
Slot 1 includes all the fixed ports.
◦
Slot 2 includes the ports on the upper expansion module (if populated).
◦
Slot 3 includes the ports on the lower expansion module (if populated).
◦
Port number
•
Port number within the group.
◦
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 7
Page 22

About the Unidirectional Link Detection Parameter
The interface numbering convention is extended to support use with a Cisco Nexus 2000 Series Fabric Extender
as follows:
switch(config)# interface ethernet [chassis/]slot/port
Chassis ID is an optional entry to address the ports of a connected Fabric Extender. The chassis ID is
•
configured on a physical Ethernet or EtherChannel interface on the switch to identify the Fabric Extender
discovered via the interface. The chassis ID ranges from 100 to 199.
About the Unidirectional Link Detection Parameter
The Cisco-proprietary Unidirectional Link Detection (UDLD) protocol allows ports that are connected through
fiber optics or copper (for example, Category 5 cabling) Ethernet cables to monitor the physical configuration
of the cables and detect when a unidirectional link exists. When the switch detects a unidirectional link, UDLD
shuts down the affected LAN port and alerts the user. Unidirectional links can cause a variety of problems,
including spanning tree topology loops.
UDLD is a Layer 2 protocol that works with the Layer 1 protocols to determine the physical status of a link.
At Layer 1, autonegotiation takes care of physical signaling and fault detection. UDLD performs tasks that
autonegotiation cannot perform, such as detecting the identities of neighbors and shutting down misconnected
LAN ports. When you enable both autonegotiation and UDLD, Layer 1 and Layer 2 detections work together
to prevent physical and logical unidirectional connections and the malfunctioning of other protocols.
A unidirectional link occurs whenever traffic transmitted by the local device over a link is received by the
neighbor but traffic transmitted from the neighbor is not received by the local device. If one of the fiber strands
in a pair is disconnected, as long as autonegotiation is active, the link does not stay up. In this case, the logical
link is undetermined, and UDLD does not take any action. If both fibers are working normally at Layer 1,
then UDLD at Layer 2 determines whether those fibers are connected correctly and whether traffic is flowing
bidirectionally between the correct neighbors. This check cannot be performed by autonegotiation, because
autonegotiation operates at Layer 1.
A Cisco Nexus 3000 Series switch periodically transmits UDLD frames to neighbor devices on LAN ports
with UDLD enabled. If the frames are echoed back within a specific time frame and they lack a specific
acknowledgment (echo), the link is flagged as unidirectional and the LAN port is shut down. Devices on both
ends of the link must support UDLD in order for the protocol to successfully identify and disable unidirectional
links.
Configuring Ethernet Interfaces
Note
By default, UDLD is locally disabled on copper LAN ports to avoid sending unnecessary control traffic
on this type of media.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
8 OL-26590-01
Page 23
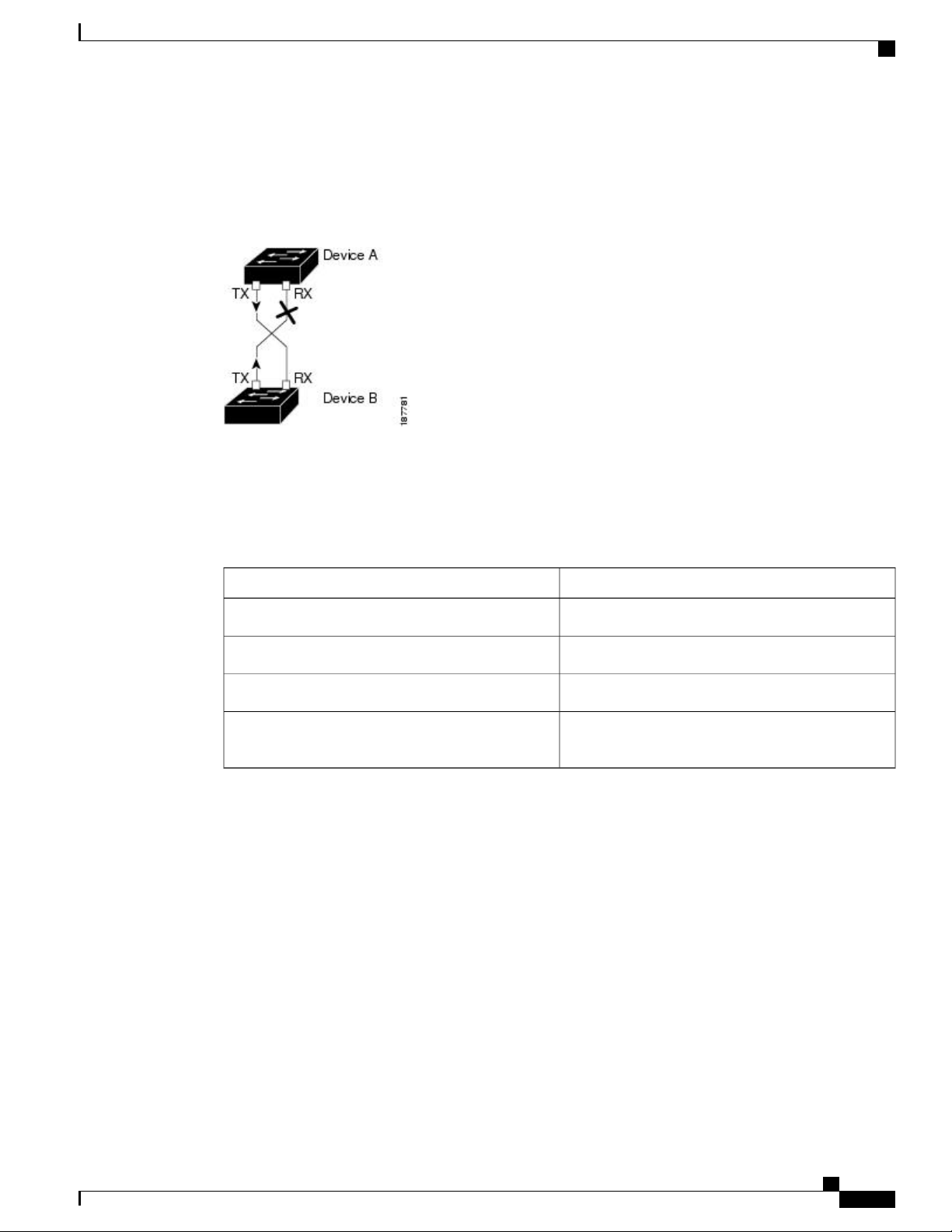
Configuring Ethernet Interfaces
The following figure shows an example of a unidirectional link condition. Device B successfully receives
traffic from Device A on the port. However, Device A does not receive traffic from Device B on the same
port. UDLD detects the problem and disables the port.
Figure 1: Unidirectional Link
Default UDLD Configuration
About the Unidirectional Link Detection Parameter
The following table shows the default UDLD configuration.
Table 2: UDLD Default Configuration
UDLD per-port enable state for twisted-pair (copper)
media
UDLD Aggressive and Nonaggressive Modes
UDLD aggressive mode is disabled by default. You can configure UDLD aggressive mode only on
point-to-point links between network devices that support UDLD aggressive mode. If UDLD aggressive mode
is enabled, when a port on a bidirectional link that has a UDLD neighbor relationship established stops
receiving UDLD frames, UDLD tries to reestablish the connection with the neighbor. After eight failed retries,
the port is disabled.
To prevent spanning tree loops, nonaggressive UDLD with the default interval of 15 seconds is fast enough
to shut down a unidirectional link before a blocking port transitions to the forwarding state (with default
spanning tree parameters).
When you enable the UDLD aggressive mode, the following occurs:
Default ValueFeature
Globally disabledUDLD global enable state
DisabledUDLD aggressive mode
Enabled on all Ethernet fiber-optic LAN portsUDLD per-port enable state for fiber-optic media
Disabled on all Ethernet 10/100 and 1000BASE-TX
LAN ports
One side of a link has a port stuck (both transmission and receive)
•
One side of a link remains up while the other side of the link is down
•
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 9
Page 24

About Interface Speed
In these cases, the UDLD aggressive mode disables one of the ports on the link, which prevents traffic from
being discarded.
About Interface Speed
A Cisco Nexus 3000 Series switch has a number of fixed 10-Gigabit ports, each equipped with SFP+ interface
adapters.
About the Cisco Discovery Protocol
The Cisco Discovery Protocol (CDP) is a device discovery protocol that runs over Layer 2 (the data link layer)
on all Cisco-manufactured devices (routers, bridges, access servers, and switches) and allows network
management applications to discover Cisco devices that are neighbors of already known devices. With CDP,
network management applications can learn the device type and the Simple Network Management Protocol
(SNMP) agent address of neighboring devices running lower-layer, transparent protocols. This feature enables
applications to send SNMP queries to neighboring devices.
CDP runs on all media that support Subnetwork Access Protocol (SNAP). Because CDP runs over the data-link
layer only, two systems that support different network-layer protocols can learn about each other.
Each CDP-configured device sends periodic messages to a multicast address, advertising at least one address
at which it can receive SNMP messages. The advertisements also contain time-to-live, or holdtime information,
which is the length of time a receiving device holds CDP information before discarding it. Each device also
listens to the messages sent by other devices to learn about neighboring devices.
The switch supports both CDP Version 1 and Version 2.
Configuring Ethernet Interfaces
Default CDP Configuration
The following table shows the default CDP configuration.
Table 3: Default CDP Configuration
About the Error-Disabled State
An interface is in the error-disabled (err-disabled) state when the inteface is enabled administratively (using
the no shutdown command) but disabled at runtime by any process. For example, if UDLD detects a
unidirectional link, the interface is shut down at runtime. However, because the interface is administratively
Default SettingFeature
EnabledCDP interface state
60 secondsCDP timer (packet update frequency)
180 secondsCDP holdtime (before discarding)
EnabledCDP Version-2 advertisements
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
10 OL-26590-01
Page 25
Configuring Ethernet Interfaces
enabled, the interface status displays as err-disabled. Once an interface goes into the err-disabled state, you
must manually reenable it or you can configure an automatic timeout recovery value. The err-disabled detection
is enabled by default for all causes. The automatic recovery is not configured by default.
When an interface is in the err-disabled state, use the errdisable detect cause command to find information
about the error.
You can configure the automatic err-disabled recovery timeout for a particular err-disabled cause by changing
the time variable.
The errdisable recovery cause command provides automatic recovery after 300 seconds. To change the
recovery period, use the errdisable recovery interval command to specify the timeout period. You can specify
30 to 65535 seconds.
If you do not enable the err-disabled recovery for the cause, the interface stays in the err-disabled state until
you enter the shutdown and no shutdown commands. If the recovery is enabled for a cause, the interface is
brought out of the err-disabled state and allowed to retry operation once all the causes have timed out. Use
the show interface status err-disabled command to display the reason behind the error.
About Port Profiles
About Port Profiles
The Cisco Nexus 3000 Series device does not support Port Profiles.
Guidelines and Limitations for Port Profiles
The Cisco Nexus 3000 Series device does not support Port Profiles.
About the Debounce Timer Parameters
The debounce timer feature is not supported on Nexus 3000.
About MTU Configuration
The Cisco Nexus 3000 Series switch does not fragment frames. As a result, the switch cannot have two ports
in the same Layer 2 domain with different maximum transmission units (MTUs). A per-physical Ethernet
interface MTU is not supported. Instead, the MTU is set according to the QoS classes. You modify the MTU
by setting Class and Policy maps.
When you show the interface settings, a default MTU of 1500 is displayed for physical Ethernet interfaces.Note
Configuring Ethernet Interfaces
The section includes the following topics:
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 11
Page 26
Configuring the UDLD Mode
Configuring the UDLD Mode
You can configure normal or aggressive unidirectional link detection (UDLD) modes for Ethernet interfaces
on devices configured to run UDLD. Before you can enable a UDLD mode for an interface, you must make
sure that UDLD is already enabled on the device that includes the interface. UDLD must also be enabled on
the other linked interface and its device.
To use the normal UDLD mode, you must configure one of the ports for normal mode and configure the other
port for the normal or aggressive mode. To use the aggressive UDLD mode, you must configure both ports
for the aggressive mode.
Before you begin, UDLD must be enabled for the other linked port and its device.Note
To configure the UDLD mode, perform this task:
Procedure
Configuring Ethernet Interfaces
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
switch(config)# interface type slot/port
Enters configuration mode.switch# configure terminal
Enables UDLD for the device.switch(config)# feature udld
Disables UDLD for the device.switch(config)# no feature udld
Displays the UDLD status for the device.switch(config)# show udld global
Specifies an interface to configure, and enters
interface configuration mode.
Step 6
Step 7
switch(config-if)# udld {enable | disable
| aggressive}
switch(config-if)# show udld interface
Enables the normal UDLD mode, disables
UDLD, or enables the aggressive UDLD mode.
Displays the UDLD status for the interface.
This example shows how to enable the UDLD for the switch:
switch# configure terminal
switch(config)# feature udld
This example shows how to enable the normal UDLD mode for an Ethernet port:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# udld enable
This example shows how to enable the aggressive UDLD mode for an Ethernet port:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# udld aggressive
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
12 OL-26590-01
Page 27
Configuring Ethernet Interfaces
This example shows how to disable UDLD for an Ethernet port:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# udld disable
This example shows how to disable UDLD for the switch:
switch# configure terminal
switch(config)# no feature udld
Changing an Interface Port Mode
You can configure a Quad small form-factor pluggable (QSFP+) port by using the hardware profile portmode
command. To restore the defaults, use the no form of this command.
To change an interface port mode, preform this task:
Procedure
Changing an Interface Port Mode
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
Step 7
switch(config)# copy
running-config bootflash:
my-config.cfg
profile portmode portmode
switch(config)# copy
running-config startup-config
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Copies the running configuration to the bootflash. You
can use this file to configure your device later.
Removes all the interface configurations.switch(config)# write erase
Reloads the Cisco Nexus 3000 Series switch software.switch(config)# reload
Changes the interface port mode.switch(config)# [no] hardware
(Optional)
Saves the change persistently through reboots and restarts
by copying the running configuration to the startup
configuration.
Reloads the Cisco Nexus 3000 Series switch software.switch(config)# reload
Manually apply all the interface configuration. You can
refer to the configuration file that you saved earlier.
Note
The interface numbering changes if the ports
are changed from 40G mode to 4x10G mode or
vice-versa.
This example shows how to change the port mode to 48x10g+4x40g for QSFP+ ports:
switch# configure terminal
switch(config) copy running-config bootflash:my-config.cfg
switch(config)# write erase
switch(config)# reload
WARNING: This command will reboot the system
Do you want to continue? (y/n) [n] y
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 13
Page 28

Configuring Interface Speed
switch(config)# hardware profile portmode 48x10g+4x40g
Warning: This command will take effect only after saving the configuration and reload!
Port configurations could get lost when port mode is changed!
switch(config)# copy running-config startup-config
switch(config)# reload
WARNING: This command will reboot the system
Do you want to continue? (y/n) [n] y
This example shows how to change the port mode to 48x10g+4x40g for QSFP+ ports and verify the changes:
switch# configure terminal
switch(config)# hardware profile portmode 48x10g+4x40g
Warning: This command will take effect only after saving the configuration and r
eload! Port configurations could get lost when port mode is changed!
switch(config)# show running-config
!Command: show running-config
!Time: Thu Aug 25 07:39:37 2011
version 5.0(3)U2(1)
feature telnet
no feature ssh
feature lldp
username admin password 5 $1$OOV4MdOM$BAB5RkD22YanT4empqqSM0 role network-admin
ip domain-lookup
switchname BLR-QG-5
ip access-list my-acl
10 deny ip any 10.0.0.1/32
20 deny ip 10.1.1.1/32 any
class-map type control-plane match-any copp-arp
class-map type control-plane match-any copp-bpdu
:
:
control-plane
service-policy input copp-system-policy
hardware profile tcam region arpacl 128
hardware profile tcam region ifacl 256
hardware profile tcam region racl 256
hardware profile tcam region vacl 512
hardware profile portmode 48x10G+4x40G
snmp-server user admin network-admin auth md5 0xdd1d21ee42e93106836cdefd1a60e062
<--Output truncated-->
switch#
This example shows how to restore the default port mode for QSFP+ ports:
switch# configure terminal
switch(config)# no hardware profile portmode
Warning: This command will take effect only after saving the configuration and r
eload! Port configurations could get lost when port mode is changed!
switch(config)#
Configuring Ethernet Interfaces
Configuring Interface Speed
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface type
slot/port
Step 3
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
14 OL-26590-01
switch(config-if)# speed speed
Enters configuration mode.switch# configure terminal
Enters interface configuration mode for the specified
interface. This interface must have a 1-Gigabit Ethernet SFP
transceiver inserted into it.
Sets the speed on the interface.
Page 29
Configuring Ethernet Interfaces
The following example shows how to set the speed for a 1-Gigabit Ethernet port:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# speed 1000
Disabling Link Negotiation
PurposeCommand or Action
This command can only be applied to a physical Ethernet
interface. The speed argument can be set to one of the
following:
10 Mbps
•
100 Mbps
•
1 Gbps
•
10Gbps
•
automatic
•
Note
If the interface and transceiver speed is mismatched, the SFP validation failed message is displayed when
you enter the show interface ethernet slot/port command. For example, if you insert a 1-Gigabit SFP
transceiver into a port without configuring the speed 1000 command, you will get this error. By default,
all ports are 10 Gigabits.
Disabling Link Negotiation
You can disable link negotiation using the no negotiate auto command. By default, auto-negotiation is enabled
on 1-Gigabit ports and disabled on 10-Gigabit ports. By default, auto-negotiation is enabled on the Cisco
Nexus 3064 and 3064-X switches and disabled on the Cisco Nexus 3048 switch.
This command is equivalent to the IOS speed non-negotiate command.
Note
Cisco does not recommend that you to enable auto negotiation on 10-Gigabit ports. Enabling
auto-negotiation on 10-Gigabit ports brings the link down. By default, link negotiation is disabled on
10-Gigabit ports.
Procedure
PurposeCommand or Action
Step 1
Step 2
Enters configuration mode.switch# configure terminal
Selects the interface and enters interface mode.switch(config)# interface ethernet
slot/port
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 15
Page 30

Configuring the CDP Characteristics
Configuring Ethernet Interfaces
PurposeCommand or Action
Step 3
Step 4
switch(config-if)# no negotiate auto
switch(config-if)# negotiate auto
This example shows how to disable auto negotiation on a specified Ethernet interface (1-Gigabit port):
switch# configure terminal
switch(config)# interface ethernet 1/1
switch(config-if)# no negotiate auto
switch(config-if)#
This example shows how to enable auto negotiation on a specified Ethernet interface (1-Gigabit port):
switch# configure terminal
switch(config)# interface ethernet 1/5
switch(config-if)# negotiate auto
switch(config-if)#
Configuring the CDP Characteristics
You can configure the frequency of Cisco Discovery Protocol (CDP) updates, the amount of time to hold the
information before discarding it, and whether or not to send Version-2 advertisements.
To configure CDP characteristics for an interface, perform this task:
Disables link negotiation on the selected Ethernet
interface (1-Gigabit port).
(Optional)
Enables link negotiation on the selected Ethernet
interface. The default for 1-Gigabit ports is enabled.
Procedure
Step 1
Step 2
Step 3
Step 4
switch(config)# [no] cdp
advertise {v1 | v2 }
switch(config)# [no] cdp format
device-id {mac-address |
serial-number | system-name}
switch(config)# [no] cdp
holdtime seconds
PurposeCommand or Action
Enters configuration mode.switch# configure terminal
(Optional)
Configures the version to use to send CDP advertisements.
Version-2 is the default state.
Use the no form of the command to return to its default
setting.
(Optional)
Configures the format of the CDP device ID. The default is
the system name, which can be expressed as a fully qualified
domain name.
Use the no form of the command to return to its default
setting.
(Optional)
Specifies the amount of time a receiving device should hold
the information sent by your device before discarding it. The
range is 10 to 255 seconds; the default is 180 seconds.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
16 OL-26590-01
Page 31

Configuring Ethernet Interfaces
Enabling or Disabling CDP
PurposeCommand or Action
Use the no form of the command to return to its default
setting.
Step 5
switch(config)# [no] cdp timer
seconds
This example shows how to configure CDP characteristics:
switch# configure terminal
switch(config)# cdp timer 50
switch(config)# cdp holdtime 120
switch(config)# cdp advertise v2
Enabling or Disabling CDP
You can enable or disable CDP for Ethernet interfaces. This protocol works only when you have it enabled
on both interfaces on the same link.
To enable or disable CDP for an interface, perform this task:
Procedure
(Optional)
Sets the transmission frequency of CDP updates in seconds.
The range is 5 to 254; the default is 60 seconds.
Use the no form of the command to return to its default
setting.
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface type slot/port
Enters configuration mode.switch# configure terminal
Enters interface configuration mode for the specified
interface.
Step 3
Enables CDP for the interface.switch(config-if)# cdp enable
To work correctly, this parameter must be enabled
for both interfaces on the same link.
Step 4
Disables CDP for the interface.switch(config-if)# no cdp enable
The following example shows how to enable CDP for an Ethernet port:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# cdp enable
This command can only be applied to a physical Ethernet interface.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 17
Page 32

Enabling the Error-Disabled Detection
Enabling the Error-Disabled Detection
You can enable error-disable (err-disabled) detection in an application. As a result, when a cause is detected
on an interface, the interface is placed in an err-disabled state, which is an operational state that is similar to
the link-down state.
Procedure
Configuring Ethernet Interfaces
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
Step 6
Example:
switch# config t
switch(config)#
errdisable detect cause {all | link-flap |
loopback}
Example:
switch(config)# errdisable detect cause
all
switch(config)#
shutdown
Example:
switch(config)# shutdown
switch(config)#
no shutdown
Example:
switch(config)# no shutdown
switch(config)#
show interface status err-disabled
Example:
switch(config)# show interface status
err-disabled
copy running-config startup-config
Example:
switch(config)# copy running-config
startup-config
Enters configuration mode.config t
Specifies a condition under which to place the
interface in an err-disabled state. The default is
enabled.
Brings the interface down administratively. To
manually recover the interface from the
err-disabled state, enter this command first.
Brings the interface up administratively and
enables the interface to recover manually from
the err-disabled state.
Displays information about err-disabled
interfaces.
(Optional) Copies the running configuration to
the startup configuration.
This example shows how to enable the err-disabled detection in all cases:
switch(config)#errdisable detect cause all
switch(config)#
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
18 OL-26590-01
Page 33

Configuring Ethernet Interfaces
Enabling the Error-Disabled Recovery
You can specify the application to bring the interface out of the error-disabled (err-disabled) state and retry
coming up. It retries after 300 seconds, unless you configure the recovery timer (see the errdisable recovery
interval command).
Procedure
Enabling the Error-Disabled Recovery
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Example:
switch#config t
switch(config)#
errdisable recovery cause {all | udld |
bpduguard | link-flap | failed-port-state |
pause-rate-limit}
Example:
switch(config)#errdisable recovery cause
all
switch(config-if)#
show interface status err-disabled
Example:
switch(config)#show interface status
err-disabled
copy running-config startup-config
Example:
switch(config)#copy running-config
startup-config
Enters configuration mode.config t
Specifies a condition under which the interface
automatically recovers from the err-disabled
state, and the device retries bringing the
interface up. The device waits 300 seconds to
retry. The default is disabled.
Displays information about err-disabled
interfaces.
(Optional) Copies the running configuration to
the startup configuration.
This example shows how to enable err-disabled recovery under all conditions:
switch(config)#errdisable recovery cause all
switch(config)#
Configuring the Error-Disabled Recovery Interval
You can use this procedure to configure the err-disabled recovery timer value. The range is from 30 to 65535
seconds. The default is 300 seconds.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 19
Page 34

Configuring the Debounce Timer
Procedure
Configuring Ethernet Interfaces
PurposeCommand or Action
Step 1
Step 2
Example:
switch#config t
switch(config)#
errdisable recovery interval interval
Enters configuration mode.config t
Specifies the interval for the interface to
recover from the err-disabled state. The range
is from 30 to 65535 seconds. The default is
300 seconds.
Displays information about err-disabled
Step 3
Example:
switch(config)#errdisable recovery
interval 32
switch(config-if)#
show interface status err-disabled
interfaces.
Example:
switch(config)#show interface status
err-disabled
Step 4
copy running-config startup-config
(Optional) Copies the running configuration
to the startup configuration.
Example:
switch(config)#copy running-config
startup-config
This example shows how to enable err-disabled recovery under all conditions:
switch(config)#errdisable recovery cause all
switch(config)#
Configuring the Debounce Timer
This feature is not supported on the Nexus 3000 product.
Configuring the Description Parameter
To provide textual interface descriptions for the Ethernet ports, perform this task:
Procedure
PurposeCommand or Action
Step 1
Step 2
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
20 OL-26590-01
switch(config)# interface type slot/port
Enters configuration mode.switch# configure terminal
Enters interface configuration mode for the
specified interface.
Page 35

Configuring Ethernet Interfaces
Disabling and Restarting Ethernet Interfaces
PurposeCommand or Action
Step 3
switch(config-if)# description test
This example shows how to set the interface description to "Server 3 Interface."
switch# configure terminal
switch(config)# interface ethernet 1/3
switch(config-if)# description Server 3 Interface
Disabling and Restarting Ethernet Interfaces
You can shut down and restart an Ethernet interface. This action disables all of the interface functions and
marks the interface as being down on all monitoring displays. This information is communicated to other
network servers through all dynamic routing protocols. When shut down, the interface is not included in any
routing updates.
To disable an interface, perform this task:
Procedure
Step 1
Specifies the description for the interface.
PurposeCommand or Action
Enters configuration mode.switch# configure terminal
Step 2
switch(config)# interface type slot/port
Step 3
Step 4
The following example shows how to disable an Ethernet port:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# shutdown
The following example shows how to restart an Ethernet interface:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# no shutdown
Displaying Interface Information
To view configuration information about the defined interfaces, perform one of these tasks:
Enters interface configuration mode for the
specified interface.
Disables the interface.switch(config-if)# shutdown
Restarts the interface.switch(config-if)# no shutdown
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 21
Page 36

Displaying Interface Information
Configuring Ethernet Interfaces
PurposeCommand
switch# show interface type slot/port
Displays the detailed configuration of the specified
interface.
switch# show interface type slot/port capabilities
Displays detailed information about the capabilities
of the specified interface. This option is only available
for physical interfaces
switch# show interface type slot/port transceiver
Displays detailed information about the transceiver
connected to the specified interface. This option is
only available for physical interfaces.
Displays the status of all interfaces.switch# show interface brief
switch# show interface flowcontrol
Displays the detailed listing of the flow control
settings on all interfaces.
The show interface command is invoked from EXEC mode and displays the interface configurations. Without
any arguments, this command displays the information for all the configured interfaces in the switch.
The following example shows how to display the physical Ethernet interface:
switch# show interface ethernet 1/1
Ethernet1/1 is up
Hardware is 1000/10000 Ethernet, address is 000d.eca3.5f08 (bia 000d.eca3.5f08)
MTU 1500 bytes, BW 10000000 Kbit, DLY 10 usec,
reliability 255/255, txload 190/255, rxload 192/255
Encapsulation ARPA
Port mode is trunk
full-duplex, 10 Gb/s, media type is 1/10g
Input flow-control is off, output flow-control is off
Auto-mdix is turned on
Rate mode is dedicated
Switchport monitor is off
Last clearing of "show interface" counters never
5 minute input rate 942201806 bytes/sec, 14721892 packets/sec
5 minute output rate 935840313 bytes/sec, 14622492 packets/sec
Rx
129141483840 input packets 0 unicast packets 129141483847 multicast packets
0 broadcast packets 0 jumbo packets 0 storm suppression packets
8265054965824 bytes
0 No buffer 0 runt 0 Overrun
0 crc 0 Ignored 0 Bad etype drop
0 Bad proto drop
Tx
119038487241 output packets 119038487245 multicast packets
0 broadcast packets 0 jumbo packets
7618463256471 bytes
0 output CRC 0 ecc
0 underrun 0 if down drop 0 output error 0 collision 0 deferred
0 late collision 0 lost carrier 0 no carrier
0 babble
0 Rx pause 8031547972 Tx pause 0 reset
The following example shows how to display the physical Ethernet capabilities:
switch# show interface ethernet 1/1 capabilities
Ethernet1/1
Model: 734510033
Type: 10Gbase-(unknown)
Speed: 1000,10000
Duplex: full
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
22 OL-26590-01
Page 37

Configuring Ethernet Interfaces
Trunk encap. type: 802.1Q
Channel: yes
Broadcast suppression: percentage(0-100)
Flowcontrol: rx-(off/on),tx-(off/on)
Rate mode: none
QOS scheduling: rx-(6q1t),tx-(1p6q0t)
CoS rewrite: no
ToS rewrite: no
SPAN: yes
UDLD: yes
MDIX: no
FEX Fabric: yes
The following example shows how to display the physical Ethernet transceiver:
switch# show interface ethernet 1/1 transceiver
Ethernet1/1
The following example shows how to display a brief interface status (some of the output has been removed
for brevity):
switch# show interface brief
Displaying Input Packet Discard Information
sfp is present
name is CISCO-EXCELIGHT
part number is SPP5101SR-C1
revision is A
serial number is ECL120901AV
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125mm fiber is 82 m(s)
Link length supported for 62.5/125mm fiber is 26 m(s)
cisco id is -cisco extended id number is 4
-------------------------------------------------------------------------------Ethernet VLAN Type Mode Status Reason Speed Port
Interface Ch #
-------------------------------------------------------------------------------Eth1/1 200 eth trunk up none 10G(D) -Eth1/2 1 eth trunk up none 10G(D) -Eth1/3 300 eth access down SFP not inserted 10G(D) -Eth1/4 300 eth access down SFP not inserted 10G(D) -Eth1/5 300 eth access down Link not connected 1000(D) -Eth1/6 20 eth access down Link not connected 10G(D) -Eth1/7 300 eth access down SFP not inserted 10G(D) -...
The following example shows how to display the CDP neighbors:
switch# show cdp neighbors
Capability Codes: R - Router, T - Trans-Bridge, B - Source-Route-Bridge
Device ID Local Intrfce Hldtme Capability Platform Port ID
d13-dist-1 mgmt0 148 S I WS-C2960-24TC Fas0/9
n5k(FLC12080012) Eth1/5 8 S I s N5K-C5020P-BA Eth1/5
S - Switch, H - Host, I - IGMP, r - Repeater,
V - VoIP-Phone, D - Remotely-Managed-Device,
s - Supports-STP-Dispute
Displaying Input Packet Discard Information
Beginning with Cisco NX-OS Release 5.0(3)U2(1), you can get detailed information on what specific condition
led to an input discard on a given interface. Use the show hardware internal interface indiscard-stats
front-port x command to determine the condition that could be potentially responsible for the input discards
that are seen on port eth1/x. The switch output shows the discards for IPv4, STP, input policy, ACL specific
discard, generic receive drop, and VLAN related discards.
This example shows how to determine the condition that could be potentially responsible for the input discards:
switch# show hardware internal interface indiscard-stats front-port 1
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 23
Page 38

Default Physical Ethernet Settings
+-----------------------------------------+-----------------+----------------+
| Counter Description | Count | |
+-----------------------------------------+-----------------+----------------+
+-----------------------------------------+-----------------+----------------+
Counter Information:
IPv4 Discards--- IPv4 Discards represent errors at the IP layer, for example the IP checksum error.
•
STP Discards--- STP Discards are incremented when the receive interface STP state is not forwarding
•
the packets received.
Policy Discards--- Policy Discards are incremented when there are discards because of input policy on
•
the interface.
ACL Drops---ACL drops indicate that incoming packets match an ACL entry with a drop action.
•
Receive Drops--- This drop increment represents a condition when no output port is determined for an
•
ingress packet. Receive drops happen because of variety of reasons including IPv4, STP and policy
discards. The drop counter increments in conjunction with one of the above counters or separately.
Configuring Ethernet Interfaces
IPv4 Discards 0
STP Discards 0
Policy Discards 100
ACL Drops 0
Receive Drops 0
Vlan Discards 33
Vlan Discard--- Vlan Discard indicates vlan-based discards. For example, a vlan tagged packet ingressing
•
on a port which is not a member of the vlan.
This example shows how to clear all the input discard counters which is useful for debugging purposes.:
Switch# show hardware internal interface indiscard-stats front-port 1 clear
+-----------------------------------------+-----------------+----------------+-------------------------------------+
| Counter Description | Count | Last Increment | Last
Increment Time |
+-----------------------------------------+-----------------+----------------+-------------------------------------+
Discard Stats have been reset
+-----------------------------------------+-----------------+----------------+-------------------------------------+
Default Physical Ethernet Settings
The following table lists the default settings for all physical Ethernet interfaces:
1
Default SettingParameter
Auto (full-duplex)Duplex
ARPAEncapsulation
1500 bytesMTU
AccessPort Mode
Auto (10000)Speed
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
24 OL-26590-01
Page 39

Configuring Ethernet Interfaces
1
MTU cannot be changed per-physical Ethernet interface. You modify MTU by selecting maps of QoS classes.
Default Physical Ethernet Settings
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 25
Page 40

Default Physical Ethernet Settings
Configuring Ethernet Interfaces
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
26 OL-26590-01
Page 41

Configuring VLANs
This chapter contains the following sections:
Information About VLANs, page 27
•
Configuring a VLAN, page 30
•
Information About VLANs
Understanding VLANs
A VLAN is a group of end stations in a switched network that is logically segmented by function or application,
without regard to the physical locations of the users. VLANs have the same attributes as physical LANs, but
you can group end stations even if they are not physically located on the same LAN segment.
Any switch port can belong to a VLAN, and unicast, broadcast, and multicast packets are forwarded and
flooded only to end stations in that VLAN. Each VLAN is considered as a logical network, and packets
destined for stations that do not belong to the VLAN must be forwarded through a router. The following figure
shows VLANs as logical networks. The stations in the engineering department are assigned to one VLAN,
CHAPTER 4
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 27
Page 42

VLAN Ranges
Configuring VLANs
the stations in the marketing department are assigned to another VLAN, and the stations in the accounting
department are assigned to another VLAN.
Figure 2: VLANs as Logically Defined Networks
VLAN Ranges
VLANs are usually associated with IP subnetworks. For example, all the end stations in a particular IP subnet
belong to the same VLAN. To communicate between VLANs, you must route the traffic.
By default, a newly created VLAN is operational; that is, the newly created VLAN is in the no shutdown
condition. Additionally, you can configure VLANs to be in the active state, which is passing traffic, or the
suspended state, in which the VLANs are not passing packets. By default, the VLANs are in the active state
and pass traffic.
The extended system ID is always automatically enabled in Cisco NX-OS devices.Note
The device supports up to 4094 VLANs in accordance with the IEEE 802.1Q standard. The software organizes
these VLANs into ranges, and you use each range slightly differently.
For information about configuration limits, see the configuration limits documentation for your switch.
This table describes the VLAN ranges.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
28 OL-26590-01
Page 43

Configuring VLANs
Creating, Deleting, and Modifying VLANs
Table 4: VLAN Ranges
UsageRangeVLANs Numbers
2—1005
1006—3967 and 4048—4093
Normal1
Normal
Extended
Internally allocated3968-4047 and 4094
Cisco default. You can use this
VLAN, but you cannot modify or
delete it.
You can create, use, modify, and
delete these VLANs.
You can create, name, and use
these VLANs. You cannot change
the following parameters:
The state is always active.
•
The VLAN is always
•
enabled. You cannot shut
down these VLANs.
These 80 VLANs and VLAN 4094
are allocated for internal device
use. You cannot create, delete, or
modify any VLANs within the
block reserved for internal use.
The software allocates a group of VLAN numbers for features like multicast and diagnostics, that need to use
internal VLANs for their operation. You cannot use, modify, or delete any of the VLANs in the reserved
group. You can display the VLANs that are allocated internally and their associated use.
Creating, Deleting, and Modifying VLANs
VLANs are numbered from 1 to 4094. All configured ports belong to the default VLAN when you first bring
up the switch. The default VLAN (VLAN1) uses only default values. You cannot create, delete, or suspend
activity in the default VLAN.
You create a VLAN by assigning a number to it. You can delete VLANs as well as move them from the active
operational state to the suspended operational state. If you attempt to create a VLAN with an existing VLAN
ID, the switch goes into the VLAN submode but does not create the same VLAN again.
Newly created VLANs remain unused until ports are assigned to the specific VLAN. All the ports are assigned
to VLAN1 by default.
Depending on the range of the VLAN, you can configure the following parameters for VLANs (except the
default VLAN):
VLAN name
•
Shutdown or not shutdown
•
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 29
Page 44

About the VLAN Trunking Protocol
When you delete a specified VLAN, the ports associated to that VLAN are shut down and no traffic flows.
However, the system retains all the VLAN-to-port mapping for that VLAN, and when you reenable, or recreate,
the specified VLAN, the system automatically reinstates all the original ports to that VLAN.
Configuring VLANs
Note
Commands entered in the VLAN configuration submode are immediately executed.
VLANs 3968 to 4047 and 4094 are reserved for internal use; these VLANs cannot be changed or used.
About the VLAN Trunking Protocol
VTP is a distributed VLAN database management protocol that synchronizes the VTP VLAN database across
domains. A VTP domain includes one or more network switches that share the same VTP domain name and
that are connected with trunk interfaces. Each device can be in one VTP domain, Layer 2 trunk interfaces,
and Layer 2 port channels.
Guidelines and Limitations for VTP
VTP has the following configuration guidelines and limitations:
VLAN 1 is required on all trunk ports used for switch interconnects if VTP is supported in the network.
•
Disabling VLAN 1 from any of these ports prevents VTP from functioning properly.
If you enable VTP, you must configure either version 1 or version 2.
•
The show running-configuration command does not show VLAN or VTP configuration information
•
for VLANs 1 to 1000.
VTP pruning is not supported.
•
If you are using VTP in a Token Ring environment, you must use version 2.
•
You must enter the copy running-config startup-config command followed by a reload after changing
•
a reserved VLAN range. For example:
switch(config)# system vlan 2000 reserve
This will delete all configs on vlans 2000-2127. Continue anyway? (y/n) [no] y
After the switch reload, VLANs 2000 to 2127 are reserved for internal use, which requires that you enter
the copy running-config startup-config command before the switch reload. Creating VLANs within
this range is not allowed.
SNMP can perform GET and SET operations on the CISCO-VTP-MIB objects.
•
Configuring a VLAN
Creating and Deleting a VLAN
You can create or delete all VLANs except the default VLAN and those VLANs that are internally allocated
for use by the switch. Once a VLAN is created, it is automatically in the active state.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
30 OL-26590-01
Page 45

Configuring VLANs
Configuring a VLAN
Note
When you delete a VLAN, ports associated to that VLAN shut down. The traffic does not flow and the
packets are dropped.
Procedure
PurposeCommand or Action
Step 1
Step 2
{vlan-id | vlan-range}
Enters configuration mode.switch# configure terminal
Creates a VLAN or a range of VLANs.switch(config)# vlan
If you enter a number that is already assigned to a VLAN, the switch
puts you into the VLAN configuration submode for that VLAN. If
you enter a number that is assigned to an internally allocated VLAN,
the system returns an error message. However, if you enter a range
of VLANs and one or more of the specified VLANs is outside the
range of internally allocated VLANs, the command takes effect on
only those VLANs outside the range. The range is from 2 to 4094;
VLAN1 is the default VLAN and cannot be created or deleted. You
cannot create or delete those VLANs that are reserved for internal
use.
Step 3
switch(config-vlan)# no
vlan {vlan-id | vlan-range}
Deletes the specified VLAN or range of VLANs and removes you
from the VLAN configuration submode. You cannot delete VLAN1
or the internally allocated VLANs.
This example shows how to create a range of VLANs from 15 to 20:
switch# configure terminal
switch(config)# vlan 15-20
You can also create and delete VLANs in the VLAN configuration submode.Note
Configuring a VLAN
To configure or modify the VLAN for the following parameters, you must be in the VLAN configuration
submode:
Name
•
Shut down
•
Note
You cannot create, delete, or modify the default VLAN or the internally allocated VLANs. Additionally,
some of these parameters cannot be modified on some VLANs.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 31
Page 46

Adding Ports to a VLAN
Procedure
Configuring VLANs
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config)# vlan {vlan-id
| vlan-range}
switch(config-vlan)# name
vlan-name
Enters configuration mode.switch# configure terminal
Enters VLAN configuration submode. If the VLAN does not
exist, the system first creates the specified VLAN.
Names the VLAN. You can enter up to 32 alphanumeric
characters to name the VLAN. You cannot change the name of
VLAN1 or the internally allocated VLANs. The default value is
VLANxxxx where xxxx represent four numeric digits (including
leading zeroes) equal to the VLAN ID number.
Step 4
switch(config-vlan)# state
{active | suspend}
Sets the state of the VLAN to active or suspend. While the VLAN
state is suspended, the ports associated with this VLAN are shut
down, and that VLAN does not pass any traffic. The default state
is active. You cannot suspend the state for the default VLAN or
VLANs 1006 to 4094.
Step 5
switch(config-vlan)# no
shutdown
(Optional)
Enables the VLAN. The default value is no shutdown (or
enabled). You cannot shut down the default VLAN, VLAN1, or
VLANs 1006 to 4094.
This example shows how to configure optional parameters for VLAN 5:
switch# configure terminal
switch(config)# vlan 5
switch(config-vlan)# name accounting
switch(config-vlan)# state active
switch(config-vlan)# no shutdown
Adding Ports to a VLAN
After you have completed the configuration of a VLAN, assign ports to it. To add ports, perform this task:
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface {ethernet
slot/port | port-channel number}
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
32 OL-26590-01
Enters configuration mode.switch# configure terminal
Specifies the interface to configure, and enters the
interface configuration mode. The interface can be
a physical Ethernet port or an EtherChannel.
Page 47

Configuring VLANs
Configuring a VLAN as a Routed SVI
PurposeCommand or Action
Step 3
switch(config-if)# switchport access vlan
vlan-id
This example shows how to configure an Ethernet interface to join VLAN 5:
switch# configure terminal
switch(config)# interface ethernet 1/13
switch(config-if)# switchport access vlan 5
Configuring a VLAN as a Routed SVI
You can configure a VLAN to be a routed switch virtual interface (SVI).
Before You Begin
Install the Layer 3 license. For more information, see License and Copyright Information for Cisco
•
NX-OS Software available at the following URL: http://www.cisco.com/en/US/docs/switches/datacenter/
sw/4_0/nx-os/license_agreement/nx-ossw_lisns.html.
Make sure you understand the guidelines and limitations of this feature. For information, see Guidelines
•
and Limitations for SVIs.
Procedure
Sets the access mode of the interface to the
specified VLAN.
PurposeCommand or Action
Step 1
Step 2
Step 3
interface-vlan vlan-id
Enters global configuration mode.configure terminal
Enables the creation of SVIs.feature interface-vlan
Creates a VLAN interface (SVI) and enters
interface configuration mode.
Step 4
copy running-config startup-config
Copies the running configuration to the startup
configuration.
The following example shows how to configure a VLAN as a routed SVI:
switch# configure terminal
switch(config)# feature interface-vlan
switch(config)# interface vlan 5
switch(config-if)# copy running-config startup-config
switch(config-if)#
The following example shows how to remove the routed SVI function from a VLAN:
switch# configure terminal
switch(config)# no interface vlan 5
switch(config-if)# copy running-config startup-config
switch(config-if)#
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 33
Page 48

Configuring a VLAN as a Management SVI
What to Do Next
You can configure routing protocols on this interface.
Configuring a VLAN as a Management SVI
You can configure a VLAN to be a management switch virtual interface (SVI).
Procedure
Configuring VLANs
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
The following example shows how to configure a VLAN as a management SVI:
switch# configure terminal
switch(config)# feature interface-vlan
switch(config)# interface vlan 5
switch(config-if)# management
switch(config-if)# copy running-config startup-config
switch(config-if)#
The following example shows how to remove the management function from an SVI:
switch# configure terminal
switch(config)# interface vlan 5
switch(config-if)# no management
switch(config-if)# copy running-config startup-config
switch(config-if)#
Configuring VTP
interface-vlan vlan-id management
copy running-config startup-config
Enters global configuration mode.configure terminal
Enables the creation of SVIs.feature interface-vlan
Creates a VLAN interface (SVI) and configures the
SVI to be used for in-band management.
Copies the running configuration to the startup
configuration.
You can enable and configure VTP. If you enable VTP, you must configure either version 1 or version 2. If
you are using VTP in a Token Ring environment, you must use version 2.
Procedure
PurposeCommand or Action
Step 1
Step 2
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
34 OL-26590-01
Enters global configuration mode.switch# configure terminal
Enables VTP on the device. The default is disabled.switch(config)# feature vtp
Page 49

Configuring VLANs
Configuring VTP
PurposeCommand or Action
Step 3
Step 4
Step 5
Step 6
Step 7
Step 8
Step 9
Step 10
Step 11
switch(config)# vtp domain
domain-name
switch(config)# vtp version {1 | 2}
switch(config)# vtp file file-name
switch(config)# vtp password
password-value
switch# show vtp status
switch# show vtp counters
switch# show vtp interface
switch# show vtp password
Specifies the name of the VTP domain that you want
this device to join. The default is blank.
Sets the VTP version that you want to use. The default
is version 1.
Specifies the ASCII filename of the IFS file system
file where the VTP configuration is stored.
Specifies the password for the VTP administrative
domain.
Exits the configuration submode.switch(config)# exit
(Optional)
Displays information about the VTP configuration on
the device, such as the version, mode, and revision
number.
(Optional)
Displays information about VTP advertisement
statistics on the device.
(Optional)
Displays the list of VTP-enabled interfaces.
(Optional)
Displays the password for the management VTP
domain.
Step 12
switch# copy running-config
startup-config
(Optional)
Copies the running configuration to the startup
configuration.
This example shows how to configure VTP for the device:
switch# configure terminal
switch(config)# feature vtp
switch(config)# vtp domain accounting
switch(config)# vtp version 2
switch(config)# exit
switch#
This example shows the VTP status and that the switch is capable of supporting Version 2 and that the switch
is running Version 1:
switch(config)# show vtp status
VTP Status Information
----------------------
VTP Version : 2 (capable)
Configuration Revision : 0
Maximum VLANs supported locally : 1005
Number of existing VLANs : 502
VTP Operating Mode : Transparent
VTP Domain Name :
VTP Pruning Mode : Disabled (Operationally Disabled)
VTP V2 Mode : Disabled
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 35
Page 50

Verifying VLAN Configuration
VTP Traps Generation : Disabled
MD5 Digest : 0xF5 0xF1 0xEC 0xE7 0x29 0x0C 0x2D 0x01
Configuration last modified by 60.10.10.1 at 0-0-00 00:00:00
VTP version running : 1
Verifying VLAN Configuration
Use one of the following commands to verify the configuration:
Configuring VLANs
PurposeCommand
switch# show running-config vlan [vlan_id | vlan_range]
switch# show vlan [brief | id [vlan_id | vlan_range] | name name |
summary ]
Displays VLAN information.
Displays selected configuration
information for the defined
VLAN(s).
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
36 OL-26590-01
Page 51

Configuring Private VLANs
This chapter contains the following sections:
Information About Private VLANs, page 37
•
Guidelines and Limitations for Private VLANs, page 42
•
Configuring a Private VLAN, page 42
•
Verifying the Private VLAN Configuration, page 47
•
Information About Private VLANs
A private VLAN (PVLAN) partitions the Ethernet broadcast domain of a VLAN into subdomains, allowing
you to isolate the ports on the switch from each other. A subdomain consists of a primary VLAN and one or
more secondary VLANs (see the following figure). All VLANs in a PVLAN domain share the same primary
VLAN. The secondary VLAN ID differentiates one subdomain from another. The secondary VLANs may
either be isolated VLANs or community VLANs. A host on an isolated VLAN can only communicate with
CHAPTER 5
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 37
Page 52

Primary and Secondary VLANs in Private VLANs
the associated promiscuous port in its primary VLAN. Hosts on community VLANs can communicate among
themselves and with their associated promiscuous port but not with ports in other community VLANs.
Figure 3: Private VLAN Domain
Configuring Private VLANs
You must first create the VLAN before you can convert it to a PVLAN, either primary or secondary.Note
Primary and Secondary VLANs in Private VLANs
A private VLAN domain has only one primary VLAN. Each port in a private VLAN domain is a member of
the primary VLAN; the primary VLAN is the entire private VLAN domain.
Secondary VLANs provide isolation between ports within the same private VLAN domain. The following
two types are secondary VLANs within a primary VLAN:
• Isolated VLANs—Ports within an isolated VLAN cannot communicate directly with each other at the
Layer 2 level.
• Community VLANs—Ports within a community VLAN can communicate with each other but cannot
communicate with ports in other community VLANs or in any isolated VLANs at the Layer 2 level.
Private VLAN Ports
The three types of PVLAN ports are as follows:
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
38 OL-26590-01
Page 53

Configuring Private VLANs
Primary, Isolated, and Community Private VLANs
• Promiscuous port—A promiscuous port belongs to the primary VLAN. The promiscuous port can
communicate with all interfaces, including the community and isolated host ports, that belong to those
secondary VLANs associated to the promiscuous port and associated with the primary VLAN. You can
have several promiscuous ports in a primary VLAN. Each promiscuous port can have several secondary
VLANs or no secondary VLANs that are associated to that port. You can associate a secondary VLAN
to more than one promiscuous port, as long as the promiscuous port and secondary VLANs are within
the same primary VLAN. You may want to do this for load-balancing or redundancy purposes. You can
also have secondary VLANs that are not associated to any promiscuous port.
A promiscuous port can be configured as an access port.
• Isolated port—An isolated port is a host port that belongs to an isolated secondary VLAN. This port has
complete isolation from other ports within the same PVLAN domain, except that it can communicate
with associated promiscuous ports. PVLANs block all traffic to isolated ports except traffic from
promiscuous ports. Traffic received from an isolated port is forwarded only to promiscuous ports. You
can have more than one isolated port in a specified isolated VLAN. Each port is completely isolated
from all other ports in the isolated VLAN.
An isolated port can be configured an access port.
• Community port—A community port is a host port that belongs to a community secondary VLAN.
Community ports communicate with other ports in the same community VLAN and with associated
promiscuous ports. These interfaces are isolated from all other interfaces in other communities and from
all isolated ports within the PVLAN domain.
A community port must be configured as an access port.
Primary, Isolated, and Community Private VLANs
Primary VLANs and the two types of secondary VLANs (isolated and community) have these characteristics:
• Primary VLAN— The primary VLAN carries traffic from the promiscuous ports to the host ports, both
isolated and community, and to other promiscuous ports.
• Isolated VLAN —An isolated VLAN is a secondary VLAN that carries unidirectional traffic upstream
from the hosts toward the promiscuous ports. You can configure only one isolated VLAN in a PVLAN
domain. An isolated VLAN can have several isolated ports. The traffic from each isolated port also
remains completely separate.
• Community VLAN—A community VLAN is a secondary VLAN that carries upstream traffic from the
community ports to the promiscuous port and to other host ports in the same community. You can
configure multiple community VLANs in a PVLAN domain. The ports within one community can
communicate, but these ports cannot communicate with ports in any other community or isolated VLAN
in the private VLAN.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 39
Page 54

Primary, Isolated, and Community Private VLANs
The following figure shows the traffic flows within a PVLAN, along with the types of VLANs and types of
ports.
Figure 4: Private VLAN Traffic Flows
Configuring Private VLANs
Note
The PVLAN traffic flows are unidirectional from the host ports to the promiscuous ports. Traffic received
on primary VLAN enforces no separation and forwarding is done as in a normal VLAN.
A promiscuous access port can serve only one primary VLAN and multiple secondary VLANs (community
and isolated VLANs). With a promiscuous port, you can connect a wide range of devices as access points to
a PVLAN. For example, you can use a promiscuous port to monitor or back up all the PVLAN servers from
an administration workstation.
In a switched environment, you can assign an individual PVLAN and associated IP subnet to each individual
or common group of end stations. The end stations need to communicate only with a default gateway to
communicate outside the private VLAN.
Associating Primary and Secondary VLANs
To allow host ports in secondary VLANs to communicate outside the PVLAN, you associate secondary
VLANs to the primary VLAN. If the association is not operational, the host ports (community and isolated
ports) in the secondary VLAN are brought down.
You can associate a secondary VLAN with only one primary VLAN.Note
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
40 OL-26590-01
Page 55

Configuring Private VLANs
Private VLAN Promiscuous Trunks
For an association to be operational, the following conditions must be met:
The primary VLAN must exist and be configured as a primary VLAN.
•
The secondary VLAN must exist and be configured as either an isolated or community VLAN.
•
Note
Use the show vlan private-vlan command to verify that the association is operational. The switch does
not display an error message when the association is nonoperational.
If you delete either the primary or secondary VLAN, the ports that are associated with the VLAN become
inactive. Use the no private-vlan command to return the VLAN to the normal mode. All primary and secondary
associations on that VLAN are suspended, but the interfaces remain in PVLAN mode. When you convert the
VLAN back to PVLAN mode, the original associations are reinstated.
If you enter the no vlan command for the primary VLAN, all PVLAN associations with that VLAN are
deleted. However, if you enter the no vlan command for a secondary VLAN, the PVLAN associations with
that VLAN are suspended and are restored when you recreate the specified VLAN and configure it as the
previous secondary VLAN.
In order to change the association between a secondary and primary VLAN, you must first remove the current
association and then add the desired association.
Private VLAN Promiscuous Trunks
The Cisco Nexus 3000 Series device does not support Private VLAN trunk ports.
Private VLAN Isolated Trunks
The Cisco Nexus 3000 Series device does not support Private VLAN trunk ports.
Broadcast Traffic in Private VLANs
Broadcast traffic from ports in a private VLAN flows in the following ways:
The broadcast traffic flows from a promiscuous port to all ports in the primary VLAN (which includes
•
all the ports in the community and isolated VLANs). This broadcast traffic is distributed to all ports
within the primary VLAN, including those ports that are not configured with private VLAN parameters.
The broadcast traffic from an isolated port is distributed only to those promiscuous ports in the primary
•
VLAN that are associated to that isolated port.
• The broadcast traffic from community ports is distributed to all ports within the port’s community and
to all promiscuous ports that are associated to the community port. The broadcast packets are not
distributed to any other communities within the primary VLAN or to any isolated ports.
Private VLAN Port Isolation
You can use PVLANs to control access to end stations as follows:
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 41
Page 56

Guidelines and Limitations for Private VLANs
Configure selected interfaces connected to end stations as isolated ports to prevent any communication.
•
For example, if the end stations are servers, this configuration prevents communication between the
servers.
Configure interfaces connected to default gateways and selected end stations (for example, backup
•
servers) as promiscuous ports to allow all end stations access to a default gateway.
Guidelines and Limitations for Private VLANs
When configuring PVLANs, follow these guidelines:
You must have already created the VLAN before you can assign the specified VLAN as a private VLAN.
•
You must enable PVLANs before the switch can apply the PVLAN functionality.
•
You cannot disable PVLANs if the switch has any operational ports in a PVLAN mode.
•
Enter the private-vlan synchronize command from within the Multiple Spanning Tree (MST) region
•
definition to map the secondary VLANs to the same MST instance as the primary VLAN.
Configuring Private VLANs
Configuring a Private VLAN
Enabling Private VLANs
You must enable PVLANs on the switch to use the PVLAN functionality.
The PVLAN commands do not appear until you enable the PVLAN feature.Note
Procedure
Step 1
Step 2
Step 3
switch(config)# no feature
private-vlan
PurposeCommand or Action
Enters configuration mode.switch# configure terminal
Enables the PVLAN feature on the switch.switch(config)# feature private-vlan
(Optional)
Disables the PVLAN feature on the switch.
Note
You cannot disable PVLANs if there are
operational ports on the switch that are in
PVLAN mode.
This example shows how to enable the PVLAN feature on the switch:
switch# configure terminal
switch(config)# feature private-vlan
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
42 OL-26590-01
Page 57

Configuring Private VLANs
Configuring a VLAN as a Private VLAN
To create a PVLAN, you first create a VLAN, and then configure that VLAN to be a PVLAN.
Before You Begin
Ensure that the PVLAN feature is enabled.
Procedure
Configuring a VLAN as a Private VLAN
PurposeCommand or Action
Step 1
Step 2
switch(config)# vlan {vlan-id |
Enters configuration mode.switch# configure terminal
Places you into the VLAN configuration submode.
vlan-range}
Step 3
switch(config-vlan)# private-vlan
{community | isolated | primary}
Configures the VLAN as either a community, isolated,
or primary PVLAN. In a PVLAN, you must have one
primary VLAN. You can have multiple community and
isolated VLANs.
Step 4
switch(config-vlan)# no private-vlan
{community | isolated | primary}
(Optional)
Removes the PVLAN configuration from the specified
VLAN(s) and returns it to normal VLAN mode. If you
delete either the primary or secondary VLAN, the ports
that are associated with the VLAN become inactive.
This example shows how to assign VLAN 5 to a PVLAN as the primary VLAN:
switch# configure terminal
switch(config)# vlan 5
switch(config-vlan)# private-vlan primary
This example shows how to assign VLAN 100 to a PVLAN as a community VLAN:
switch# configure terminal
switch(config)# vlan 100
switch(config-vlan)# private-vlan community
This example shows how to assign VLAN 200 to a PVLAN as an insolated VLAN:
switch# configure terminal
switch(config)# vlan 200
switch(config-vlan)# private-vlan isolated
Associating Secondary VLANs with a Primary Private VLAN
When you associate secondary VLANs with a primary VLAN, follow these guidelines:
The secondary-vlan-list parameter cannot contain spaces. It can contain multiple comma-separated items.
•
Each item can be a single secondary VLAN ID or a hyphenated range of secondary VLAN IDs.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 43
Page 58

Associating Secondary VLANs with a Primary Private VLAN
The secondary-vlan-list parameter can contain multiple community VLAN IDs and one isolated VLAN
•
ID.
Enter a secondary-vlan-list or use the add keyword with a secondary-vlan-list to associate secondary
•
VLANs with a primary VLAN.
Use the remove keyword with a secondary-vlan-list to clear the association between secondary VLANs
•
and a primary VLAN.
You change the association between a secondary and primary VLAN by removing the existing association
•
and then adding the desired association.
If you delete either the primary or secondary VLAN, the VLAN becomes inactive on the port where the
association is configured. When you enter the no private-vlan command, the VLAN returns to the normal
VLAN mode. All primary and secondary associations on that VLAN are suspended, but the interfaces remain
in PVLAN mode. If you again convert the specified VLAN to PVLAN mode, the original associations are
reinstated.
If you enter the no vlan command for the primary VLAN, all PVLAN associations with that VLAN are lost.
However, if you enter the no vlan command for a secondary VLAN, the PVLAN associations with that VLAN
are suspended and are reinstated when you recreate the specified VLAN and configure it as the previous
secondary VLAN.
Configuring Private VLANs
Before You Begin
Ensure that the PVLAN feature is enabled.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# vlan primary-vlan-id
Enters configuration mode.switch# configure terminal
Enters the number of the primary VLAN that you are
working in for the PVLAN configuration.
Step 3
switch(config-vlan)# private-vlan
association {[add] secondary-vlan-list
| remove secondary-vlan-list}
Associates the secondary VLANs with the primary
VLAN. Use the remove keyword with a
secondary-vlan-list to clear the association between
secondary VLANs and a primary VLAN.
Step 4
switch(config-vlan)# no private-vlan
association
(Optional)
Removes all associations from the primary VLAN and
returns it to normal VLAN mode.
This example shows how to associate community VLANs 100 through 110 and isolated VLAN 200 with
primary VLAN 5:
switch# configure terminal
switch(config)# vlan 5
switch(config-vlan)# private-vlan association 100-110, 200
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
44 OL-26590-01
Page 59

Configuring Private VLANs
Configuring an Interface as a Private VLAN Host Port
Configuring an Interface as a Private VLAN Host Port
In PVLANs, host ports are part of the secondary VLANs, which are either community VLANs or isolated
VLANs. Configuring a PVLAN host port involves two steps. First, you define the port as a PVLAN host port
and then you configure a host association between the primary and secondary VLANs.
We recommend that you enable BPDU Guard on all interfaces configured as a host ports.Note
Before You Begin
Ensure that the PVLAN feature is enabled.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface type
[chassis/]slot/port
Enters configuration mode.switch# configure terminal
Selects the port to configure as a PVLAN host
port. This port can be on a FEX (identified by the
chassis option).
Step 3
Configures the port as a host port for a PVLAN.switch(config-if)# switchport mode
private-vlan host
Step 4
Step 5
switch(config-if)# switchport private-vlan
host-association {primary-vlan-id}
{secondary-vlan-id}
switch(config-if)# no switchport
private-vlan host-association
Associates the port with the primary and secondary
VLANs of a PVLAN. The secondary VLAN can
be either an isolated or community VLAN.
(Optional)
Removes the PVLAN association from the port.
This example shows how to configure Ethernet port 1/12 as a host port for a PVLAN and associate it to
primary VLAN 5 and secondary VLAN 101:
switch# configure terminal
switch(config)# interface ethernet 1/12
switch(config-if)# switchport mode private-vlan host
switch(config-if)# switchport private-vlan host-association 5 101
Configuring an Interface as a Private VLAN Promiscuous Port
In a PVLAN domain, promiscuous ports are part of the primary VLAN. Configuring a promiscuous port
involves two steps. First, you define the port as a promiscuous port and then you configure the mapping
between a secondary VLAN and the primary VLAN.
Before You Begin
Ensure that the PVLAN feature is enabled.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 45
Page 60

Configuring a Promiscuous Trunk Port
Procedure
Configuring Private VLANs
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
Step 5
This example shows how to configure Ethernet interface 1/4 as a promiscuous port associated with primary
VLAN 5 and secondary isolated VLAN 200:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# switchport mode private-vlan promiscuous
switch(config-if)# switchport private-vlan mapping 5 200
switch(config)# interface type slot/port
switch(config-if)# switchport mode
private-vlan promiscuous
switch(config-if)# switchport
private-vlan mapping {primary-vlan-id}
{secondary-vlan-list | add
secondary-vlan-list | remove
secondary-vlan-list}
switch(config-if)# no switchport
private-vlan mapping
Enters configuration mode.switch# configure terminal
Selects the port to configure as a PVLAN
promiscuous port. A physical interface is required.
This port cannot be on a FEX.
Configures the port as a promiscuous port for a
PVLAN. You can only enable a physical Ethernet
port as the promiscuous port.
Configures the port as a promiscuous port and
associates the specified port with a primary VLAN
and a selected list of secondary VLANs. The
secondary VLAN can be either an isolated or
community VLAN.
(Optional)
Clears the mapping from the PVLAN.
Configuring a Promiscuous Trunk Port
You cannot perform this task because the Cisco Nexus 3000 Series device does not support Private VLAN
trunk ports.
Configuring an Isolated Trunk Port
You cannot perform this task because the Cisco Nexus 3000 Series device does not support Private VLAN
trunk ports.
Configuring the Allowed VLANs for PVLAN Trunking Ports
You cannot perform this task because the Cisco Nexus 3000 Series device does not support Private VLAN
trunk ports.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
46 OL-26590-01
Page 61

Configuring Private VLANs
Configuring Native 802.1Q VLANs on Private VLANs
Configuring Native 802.1Q VLANs on Private VLANs
You cannot perform this task because the Cisco Nexus 3000 Series device does not support Private VLAN
trunk ports.
Verifying the Private VLAN Configuration
To display PVLAN configuration information, use the following commands:
PurposeCommand
Displays the features enabled on the switch.switch# show feature
switch# show interface switchport
Displays information on all interfaces configured as
switch ports.
Displays the status of the PVLAN.switch# show vlan private-vlan [type]
This example shows how to display the PVLAN configuration:
switch# show vlan private-vlan
Primary Secondary Type Ports
------- --------- --------------- ------------------------------------------5 100 community
5 101 community Eth1/12, Eth100/1/1
5 102 community
5 110 community
5 200 isolated Eth1/2
switch# show vlan private-vlan type
Vlan Type
---- ----------------5 primary
100 community
101 community
102 community
110 community
200 isolated
The following example shows how to display enabled features (some of the output has been removed for
brevity):
switch# show feature
Feature Name Instance State
-------------------- -------- -------fcsp 1 enabled
...
interface-vlan 1 enabled
private-vlan 1 enabled
udld 1 disabled
...
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 47
Page 62

Verifying the Private VLAN Configuration
Configuring Private VLANs
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
48 OL-26590-01
Page 63

CHAPTER 6
Configuring Access and Trunk Interfaces
This chapter contains the following sections:
Information About Access and Trunk Interfaces, page 49
•
Configuring Access and Trunk Interfaces, page 53
•
Verifying Interface Configuration, page 57
•
Information About Access and Trunk Interfaces
Understanding Access and Trunk Interfaces
Ethernet interfaces can be configured either as access ports or a trunk ports, as follows:
An access port can have only one VLAN configured on the interface; it can carry traffic for only one
•
VLAN.
A trunk port can have two or more VLANs configured on the interface; it can carry traffic for several
•
VLANs simultaneously.
Cisco NX-OS supports only IEEE 802.1Q-type VLAN trunk encapsulation.Note
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 49
Page 64

Understanding IEEE 802.1Q Encapsulation
The following figure shows how you can use trunk ports in the network. The trunk port carries traffic for two
or more VLANs.
Figure 5: Devices in a Trunking Environment
Configuring Access and Trunk Interfaces
In order to correctly deliver the traffic on a trunk port with several VLANs, the device uses the IEEE 802.1Q
encapsulation or tagging method.
To optimize the performance on access ports, you can configure the port as a host port. Once the port is
configured as a host port, it is automatically set as an access port, and channel grouping is disabled. Use the
host designation to decrease the time it takes the designated port to begin to forward packets.
Note
Only an end station can be set as a host port; you will receive an error message if you attempt to configure
other ports as hosts.
If an access port receives a packet with an 802.1Q tag in the header other than the access VLAN value, that
port drops the packet without learning its MAC source address.
Note
An Ethernet interface can function as either an access port or a trunk port; it cannot function as both port
types simultaneously.
Understanding IEEE 802.1Q Encapsulation
A trunk is a point-to-point link between the device and another networking device. Trunks carry the traffic
of multiple VLANs over a single link and allow you to extend VLANs across an entire network.
To correctly deliver the traffic on a trunk port with several VLANs, the device uses the IEEE 802.1Q
encapsulation (tagging) method. This tag carries information about the specific VLAN to which the frame
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
50 OL-26590-01
Page 65

Configuring Access and Trunk Interfaces
and packet belong. This method allows packets that are encapsulated for several different VLANs to traverse
the same port and maintain traffic separation between the VLANs. The encapsulated VLAN tag also allows
the trunk to move traffic end-to-end through the network on the same VLAN.
Figure 6: Header without and with 802.1Q Tag Included
Understanding Access VLANs
Understanding Access VLANs
When you configure a port in access mode, you can specify which VLAN will carry the traffic for that interface.
If you do not configure the VLAN for a port in access mode, or an access port, the interface carries traffic for
the default VLAN (VLAN1).
You can change the access port membership in a VLAN by specifying the new VLAN. You must create the
VLAN before you can assign it as an access VLAN for an access port. If you change the access VLAN on an
access port to a VLAN that is not yet created, the system will shut that access port down.
If an access port receives a packet with an 802.1Q tag in the header other than the access VLAN value, that
port drops the packet without learning its MAC source address.
Note
If you assign an access VLAN that is also a primary VLAN for a private VLAN, all access ports with that
access VLAN will also receive all the broadcast traffic for the primary VLAN in the private VLAN mode.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 51
Page 66

Understanding the Native VLAN ID for Trunk Ports
Understanding the Native VLAN ID for Trunk Ports
A trunk port can carry untagged packets simultaneously with the 802.1Q tagged packets. When you assign a
default port VLAN ID to the trunk port, all untagged traffic travels on the default port VLAN ID for the trunk
port, and all untagged traffic is assumed to belong to this VLAN. This VLAN is referred to as the native
VLAN ID for a trunk port. The native VLAN ID is the VLAN that carries untagged traffic on trunk ports.
The trunk port sends an egressing packet with a VLAN that is equal to the default port VLAN ID as untagged;
all the other egressing packets are tagged by the trunk port. If you do not configure a native VLAN ID, the
trunk port uses the default VLAN.
Configuring Access and Trunk Interfaces
Note
Native VLAN ID numbers must match on both ends of the trunk.
Understanding Allowed VLANs
By default, a trunk port sends traffic to and receives traffic from all VLANs. All VLAN IDs are allowed on
each trunk. However, you can remove VLANs from this inclusive list to prevent traffic from the specified
VLANs from passing over the trunk. You can add any specific VLANs later that you may want the trunk to
carry traffic for back to the list.
To partition spanning tree protocol (STP) topology for the default VLAN, you can remove VLAN1 from the
list of allowed VLANs. Otherwise, VLAN1, which is enabled on all ports by default, will have a very big
STP topology, which can result in problems during STP convergence. When you remove VLAN1, all data
traffic for VLAN1 on this port is blocked, but the control traffic continues to move on the port.
Understanding Native 802.1Q VLANs
To provide additional security for traffic passing through an 802.1Q trunk port, the vlan dot1q tag native
command was introduced. This feature provides a means to ensure that all packets going out of a 802.1Q
trunk port are tagged and to prevent reception of untagged packets on the 802.1Q trunk port.
Without this feature, all tagged ingress frames received on a 802.1Q trunk port are accepted as long as they
fall inside the allowed VLAN list and their tags are preserved. Untagged frames are tagged with the native
VLAN ID of the trunk port before further processing. Only those egress frames whose VLAN tags are inside
the allowed range for that 802.1Q trunk port are received. If the VLAN tag on a frame happens to match that
of the native VLAN on the trunk port, the tag is stripped off and the frame is sent untagged.
This behavior could potentially be exploited to introduce "VLAN hopping" in which a hacker could try and
have a frame jump to a different VLAN. It is also possible for traffic to become part of the native VLAN by
sending untagged packets into an 802.1Q trunk port.
To address the above issues, the vlan dot1q tag native command performs the following functions:
On the ingress side, all untagged data traffic is dropped.
•
On the egress side, all traffic is tagged. If traffic belongs to native VLAN then it is tagged with the native
•
VLAN ID.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
52 OL-26590-01
Page 67

Configuring Access and Trunk Interfaces
This feature is supported on all the directly connected Ethernet and EtherChannel interfaces of the Cisco
Nexus 3000 Series switch.
Configuring Access and Trunk Interfaces
Note
You can enable the vlan dot1q tag native command by issuing the command in the global configuration
mode.
Configuring Access and Trunk Interfaces
Configuring a LAN Interface as an Ethernet Access Port
You can configure an Ethernet interface as an access port. An access port transmits packets on only one,
untagged VLAN. You specify which VLAN traffic that the interface carries. If you do not specify a VLAN
for an access port, the interface carries traffic only on the default VLAN. The default VLAN is VLAN1.
The VLAN must exist before you can specify that VLAN as an access VLAN. The system shuts down an
access port that is assigned to an access VLAN that does not exist.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface {{type
slot/port} | {port-channel
number}}
Enters configuration mode.switch# configure terminal
Specifies an interface to configure, and enters interface
configuration mode.
Step 3
Step 4
This example shows how to set an interface as an Ethernet access port that carries traffic for a specific VLAN
only:
switch# configure terminal
switch(config)# interface ethernet 1/10
switch(config-if)# switchport mode access
switch(config-if)# switchport access vlan 5
switch(config-if)# switchport
mode {access | trunk}
switch(config-if)# switchport
access vlan vlan-id
Sets the interface as a nontrunking nontagged single-VLAN
Ethernet interface. An access port can carry traffic in one
VLAN only. By default, an access port carries traffic for
VLAN1; to set the access port to carry traffic for a different
VLAN, use the switchport access vlan command.
Specifies the VLAN for which this access port will carry
traffic. If you do not enter this command, the access port
carries traffic on VLAN1 only; use this command to change
the VLAN for which the access port carries traffic.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 53
Page 68

Configuring Access Host Ports
Configuring Access Host Ports
By using switchport host, you can make an access port a spanning-tree edge port, and enable bpdu filtering
and bpdu guard at the same time.
Before You Begin
Ensure that you are configuring the correct interface; it must be an interface that is connnected to an end
station.
Procedure
Configuring Access and Trunk Interfaces
PurposeCommand or Action
Step 1
Step 2
Step 3
This example shows how to set an interface as an Ethernet access host port with EtherChannel disabled:
switch# configure terminal
switch(config)# interface ethernet 1/10
switch(config-if)# switchport host
Configuring Trunk Ports
You can configure an Ethernet port as a trunk port; a trunk port transmits untagged packets for the native
VLAN plus encapsulated, tagged, packets for multiple VLANs.
Cisco NX-OS supports only 802.1Q encapsulation.Note
switch(config)# interface type
slot/port
switch(config-if)# switchport host
Enters configuration mode.switch# configure terminal
Specifies an interface to configure, and enters interface
configuration mode.
Sets the interface to spanning-tree port type edge, turns
on bpdu filtering and bpdu guard.
Note
Apply this command only to switchports which
connect to hosts.
To configure a trunk port, perform this task:
Procedure
PurposeCommand or Action
Step 1
Step 2
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
54 OL-26590-01
switch(config)# interface {type
slot/port | port-channel number}
Enters configuration mode.switch# configure terminal
Specifies an interface to configure, and enters interface
configuration mode.
Page 69

Configuring Access and Trunk Interfaces
Configuring the Native VLAN for 802.1Q Trunking Ports
PurposeCommand or Action
Step 3
switch(config-if)# switchport
mode {access | trunk}
Sets the interface as an Ethernet trunk port. A trunk port can
carry traffic in one or more VLANs on the same physical
link (VLANs are based on the trunk-allowed VLANs list).
By default, a trunk interface can carry traffic for all VLANs.
To specify that only certain VLANs are allowed on the
specified trunk, use the switchport trunk allowed vlan
command.
This example shows how to set an interface as an Ethernet trunk port:
switch# configure terminal
switch(config)# interface ethernet 1/3
switch(config-if)# switchport mode trunk
Configuring the Native VLAN for 802.1Q Trunking Ports
If you do not configure this parameter, the trunk port uses the default VLAN as the native VLAN ID.
Procedure
PurposeCommand or Action
Step 1
Enters configuration mode.switch# configure terminal
Step 2
Step 3
switch(config)# interface {type slot/port
| port-channel number}
switch(config-if)# switchport trunk
native vlan vlan-id
Specifies an interface to configure, and enters
interface configuration mode.
Sets the native VLAN for the 802.1Q trunk. Valid
values are from 1 to 4094, except those VLANs
reserved for internal use. The default value is
VLAN1.
This example shows how to set the native VLAN for an Ethernet trunk port:
switch# configure terminal
switch(config)# interface ethernet 1/3
switch(config-if)# switchport trunk native vlan 5
Configuring the Allowed VLANs for Trunking Ports
You can specify the IDs for the VLANs that are allowed on the specific trunk port.
Before you configure the allowed VLANs for the specified trunk ports, ensure that you are configuring the
correct interfaces and that the interfaces are trunks.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 55
Page 70

Configuring Native 802.1Q VLANs
Procedure
Configuring Access and Trunk Interfaces
PurposeCommand or Action
Step 1
Step 2
switch(config)# interface {type
slot/port | port-channel number}
Step 3
switch(config-if)# switchport trunk
allowed vlan {vlan-list all | none
[add |except | none | remove
{vlan-list}]}
This example shows how to add VLANs to the list of allowed VLANs on an Ethernet trunk port:
switch# configure terminal
switch(config)# interface ethernet 1/3
switch(config-if)# switchport trunk allow vlan 15-20
Configuring Native 802.1Q VLANs
Enters configuration mode.switch# configure terminal
Specifies an interface to configure, and enters interface
configuration mode.
Sets allowed VLANs for the trunk interface. The default is
to allow all VLANs on the trunk interface: 1 to 3967 and
4048 to 4094. VLANs 3968 to 4047 are the default VLANs
reserved for internal use by default; this group of VLANs is
configurable. By default, all VLANs are allowed on all trunk
interfaces.
Note
You cannot add internally allocated VLANs as
allowed VLANs on trunk ports. The system returns
a message if you attempt to list an internally
allocated VLAN as an allowed VLAN.
Typically, you configure 802.1Q trunks with a native VLAN ID, which strips tagging from all packets on that
VLAN. This configuration allows all untagged traffic and control traffic to transit the Cisco Nexus 3000 Series
switch. Packets that enter the switch with 802.1Q tags that match the native VLAN ID value are similarly
stripped of tagging.
To maintain the tagging on the native VLAN and drop untagged traffic, enter the vlan dot1q tag native
command. The switch will tag the traffic received on the native VLAN and admit only 802.1Q-tagged frames,
dropping any untagged traffic, including untagged traffic in the native VLAN.
Control traffic continues to be accepted untagged on the native VLAN on a trunked port, even when the vlan
dot1q tag native command is enabled.
The vlan dot1q tag native command is enabled on global basis.Note
Procedure
PurposeCommand or Action
Step 1
Enters configuration mode.switch# configure terminal
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
56 OL-26590-01
Page 71

Configuring Access and Trunk Interfaces
Verifying Interface Configuration
PurposeCommand or Action
Step 2
switch(config)# vlan dot1q tag
native
Step 3
switch(config)# no vlan dot1q tag
native
Step 4
switch# show vlan dot1q tag native
The following example shows how to enable 802.1Q tagging on the switch:
switch# configure terminal
switch(config)# vlan dot1q tag native
switch(config)# exit
switch# show vlan dot1q tag native
vlan dot1q native tag is enabled
Verifying Interface Configuration
To display access and trunk interface configuration information, perform one of these tasks:
Enables dot1q (IEEE 802.1Q) tagging for all native
VLANs on all trunked ports on the Cisco Nexus 3000
Series switch. By default, this feature is disabled.
(Optional)
Disables dot1q (IEEE 802.1Q) tagging for all native
VLANs on all trunked ports on the switch.
(Optional)
Displays the status of tagging on the native VLANs.
PurposeCommand
switch# show interface switchport
Displays the interface configurationswitch# show interface
Displays information for all Ethernet interfaces,
including access and trunk interfaces.
Displays interface configuration information.switch# show interface brief
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 57
Page 72

Verifying Interface Configuration
Configuring Access and Trunk Interfaces
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
58 OL-26590-01
Page 73

Configuring Switching Modes
This chapter contains the following sections:
Information About Switching Modes, page 59
•
Guidelines and Limitations for Switching Modes, page 60
•
Licensing Requirements for Switching Modes, page 60
•
Default Settings for Switching Modes, page 61
•
Configuring Switching Modes, page 61
•
Feature History for Switching Modes, page 62
•
Information About Switching Modes
The switching mode determines whether the switch begins forwarding the frame as soon as the switch has
read the destination details in the packet header or waits until the entire frame has been received and checked
for cyclic redundancy check (CRC) errors before forwarding them to the network.
The switching mode is applicable to all packets being switched or routed through the hardware and can be
saved persistently through reboots and restarts.
The switch operates in either of the following switching modes:
CHAPTER 7
Cut-Through Switching Mode
Cut-through switching mode is enabled by default. Switches operating in cut-through switching mode start
forwarding the frame as soon as the switch has read the destination details in the packet header. A switch in
cut-through mode forwards the data before it has completed receiving the entire frame.
The switching speed in cut-through mode is faster than the switching speed in store-and-forward switching
mode.
Store-and-Forward Switching Mode
When store-and-forward switching is enabled, the switch checks each frame for cyclic redundancy check
(CRC) errors before forwarding them to the network. Each frame is stored until the entire frame has been
received and checked.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 59
Page 74

Guidelines and Limitations for Switching Modes
Because it waits to forward the frame until the entire frame has been received and checked, the switching
speed in store-and-forward switching mode is slower than the switching speed in cut-through switching mode.
Guidelines and Limitations for Switching Modes
Consider the following guidelines and limitations for each of the switching modes:
Cut-Through Switching Mode Guidelines and Limitations
Packets with frame check sequence (FCS) errors are dropped. For example:
•
For the Cisco Nexus 3064PQ platform, packets smaller than or equal to 768 bytes are dropped.
•
For Cisco Nexus 3016, 3064E, 3064X, and 3048 platforms, packets smaller than or equal to 560
•
bytes are dropped.
For the Cisco Nexus 3064PQ platform, packets larger than 769 or equal to bytes are forwarded.
•
For 3016, 3064E, 3064X, and 3048 platforms, packets larger than or equal to 561 bytes are
•
forwarded.
Configuring Switching Modes
Packets with FCS errors are not mirrored if SPAN is configured.
•
Store-and-Forward Switching Mode Guidelines and Limitations
Packets that are smaller than the maximum transmission unit (MTU) size configured on the switch with
•
FCS errors are dropped.
Packets with FCS errors are not mirrored if SPAN is configured.
•
The CPU port always operates in store-and-forward mode. Any packets forwarded to the CPU with FCS
•
errors are dropped.
Store-and-forward mode activates automatically for a port when the switch identifies that the port is
•
oversubscribed and the ingress rate is greater than the switching capacity of the egress port. For example,
when the port ingress rate is 10 gigabit and the switching capacity of the egress port is 1 gigabit.
Note
The global configuration does not change, even if store-and-forward mode is activated
for an oversubscribed port.
Licensing Requirements for Switching Modes
Cut-through switching mode and store-and-forward switching modes do not require licenses. Any feature not
included in a license package is bundled with the Cisco NX-OS system images and is provided at no extra
charge to you. For a complete explanation of the Cisco NX-OS licensing scheme, see the Cisco NX-OS
Licensing Guide.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
60 OL-26590-01
Page 75

Configuring Switching Modes
Default Settings for Switching Modes
Cut-through switching is enabled by default.
Configuring Switching Modes
Enabling Store-and-Forward Switching
Enabling store-and-forward switching mode might impact your port-to-port switching latency.Note
Procedure
Default Settings for Switching Modes
Step 1
Step 2
store-forward
Step 3
This example shows how to enable store-and-forward switching:
switch# configure terminal
switch(config) # switching-mode store-forward
switch(config) #
switch(config)# copy running-config
startup-config
Reenabling Cut-Through Switching
Cut-through switching is enabled by default. To reenable cut-through switching, use the no form of the
switching-mode store-forward command.
Procedure
PurposeCommand or Action
Enters global configuration mode.switch# configure terminal
Enables store-and-forward switching mode.switch(config) # switching-mode
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
PurposeCommand or Action
Step 1
Step 2
OL-26590-01 61
switch(config) # no switching-mode
store-forward
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
Enters global configuration mode.switch# configure terminal
Disables store-and-forward switching mode. Enables
cut-through switching mode.
Page 76

Feature History for Switching Modes
Configuring Switching Modes
PurposeCommand or Action
Step 3
switch(config)# copy running-config
startup-config
This example shows how to reenable cut-through switching:
switch# configure terminal
switch(config) # no switching-mode store-forward
switch(config) #
Feature History for Switching Modes
Table 5: Feature History for Switching Modes
(Optional)
Saves the change persistently through reboots and
restarts by copying the running configuration to the
startup configuration.
InformationReleasesFeature Name
This feature was introduced.5.0(3)U3(1)Store-and-Forward Switching
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
62 OL-26590-01
Page 77

Configuring Rapid PVST+
This chapter contains the following sections:
Information About Rapid PVST+, page 63
•
Configuring Rapid PVST+, page 78
•
Verifying Rapid PVST+ Configurations, page 86
•
Information About Rapid PVST+
The Rapid PVST+ protocol is the IEEE 802.1w standard, Rapid Spanning Tree Protocol (RSTP), implemented
on a per VLAN basis. Rapid PVST+ interoperates with the IEEE 802.1D standard, which mandates a single
STP instance for all VLANs, rather than per VLAN.
Rapid PVST+ is enabled by default on the default VLAN (VLAN1) and on all newly created VLANs in
software. Rapid PVST+ interoperates with switches that run legacy IEEE 802.1D STP.
RSTP is an improvement on the original STP standard, 802.1D, which allows faster convergence.
CHAPTER 8
Note
Spanning tree is used to refer to IEEE 802.1w and IEEE 802.1s. If the text is discussing the IEEE 802.1D
Spanning Tree Protocol, 802.1D is stated specifically.
Understanding STP
STP Overview
For an Ethernet network to function properly, only one active path can exist between any two stations.
When you create fault-tolerant internetworks, you must have a loop-free path between all nodes in a network.
The STP algorithm calculates the best loop-free path throughout a switched network. LAN ports send and
receive STP frames, which are called Bridge Protocol Data Units (BPDUs), at regular intervals. Switches do
not forward these frames, but use the frames to construct a loop-free path.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 63
Page 78

Understanding STP
Multiple active paths between end stations cause loops in the network. If a loop exists in the network, end
stations might receive duplicate messages and switches might learn end station MAC addresses on multiple
LAN ports. These conditions result in a broadcast storm, which creates an unstable network.
STP defines a tree with a root bridge and a loop-free path from the root to all switches in the network. STP
forces redundant data paths into a blocked state. If a network segment in the spanning tree fails and a redundant
path exists, the STP algorithm recalculates the spanning tree topology and activates the blocked path.
When two LAN ports on a switch are part of a loop, the STP port priority and port path cost setting determine
which port on the switch is put in the forwarding state and which port is put in the blocking state.
Understanding How a Topology is Created
All switches in an extended LAN that participate in a spanning tree gather information about other switches
in the network by exchanging of BPDUs. This exchange of BPDUs results in the following actions:
The system elects a unique root switch for the spanning tree network topology.
•
The system elects a designated switch for each LAN segment.
•
The system eliminates any loops in the switched network by placing redundant interfaces in a backup
•
state; all paths that are not needed to reach the root switch from anywhere in the switched network are
placed in an STP-blocked state.
Configuring Rapid PVST+
The topology on an active switched network is determined by the following:
The unique switch identifier Media Access Control (MAC) address of the switch that is associated with
•
each switch
The path cost to the root that is associated with each interface
•
The port identifier that is associated with each interface
•
In a switched network, the root switch is the logical center of the spanning tree topology. STP uses BPDUs
to elect the root switch and root port for the switched network, as well as the root port and designated port
for each switched segment.
Understanding the Bridge ID
Each VLAN on each switch has a unique 64-bit bridge ID consisting of a bridge priority value, an extended
system ID (IEEE 802.1t), and an STP MAC address allocation.
Bridge Priority Value
The bridge priority is a 4-bit value when the extended system ID is enabled.
Note
In Cisco NX-OS, the extended system ID is always enabled; you cannot be disable the extended system
ID.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
64 OL-26590-01
Page 79

Configuring Rapid PVST+
Extended System ID
Understanding STP
A 12-bit extended system ID field is part of the bridge ID.
Figure 7: Bridge ID with Extended System ID
The switches always use the 12-bit extended system ID.
Combined with the bridge ID, the system ID extension functions as the unique identifier for a VLAN.
Table 6: Bridge Priority Value and Extended System ID with the Extended System ID Enabled
Extended System ID (Set Equal to the VLAN ID)Bridge Priority Value
Bit
Bit
15
16
STP MAC Address Allocation
Extended system ID and MAC address reduction is always enabled on the software.Note
With MAC address reduction enabled on any switch, you should also enable MAC address reduction on all
other connected switches to avoid undesirable root bridge election and spanning tree topology issues.
When MAC address reduction is enabled, the root bridge priority becomes a multiple of 4096 plus the VLAN
ID. You can only specify a switch bridge ID (used by the spanning tree algorithm to determine the identity
of the root bridge, the lowest being preferred) as a multiple of 4096. Only the following values are possible:
0
•
4096
•
8192
•
12288
•
Bit
14
Bit
13
Bit
12
Bit
11
Bit 1Bit 2Bit 3Bit 4Bit 5Bit 6Bit 7Bit 8Bit 9Bit
10
124816326412825651210242048409681921638432768
16384
•
20480
•
24576
•
28672
•
32768
•
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 65
Page 80

Understanding STP
Configuring Rapid PVST+
36864
•
40960
•
45056
•
49152
•
53248
•
57344
•
61440
•
STP uses the extended system ID plus a MAC address to make the bridge ID unique for each VLAN.
Note
If another bridge in the same spanning tree domain does not run the MAC address reduction feature, it
could achieve root bridge ownership because its bridge ID may fall between the values specified by the
MAC address reduction feature.
Understanding BPDUs
Switches transmit bridge protocol data units (BPDUs) throughout the STP instance. Each switch sends
configuration BPDUs to communicate and compute the spanning tree topology. Each configuration BPDU
contains the following minimal information:
The unique bridge ID of the switch that the transmitting switch determines is the root bridge
•
The STP path cost to the root
•
The bridge ID of the transmitting bridge
•
Message age
•
The identifier of the transmitting port
•
Values for the hello, forward delay, and max-age protocol timer
•
Additional information for STP extension protocols
•
When a switch transmits a Rapid PVST+ BPDU frame, all switches connected to the VLAN on which the
frame is transmitted receive the BPDU. When a switch receives a BPDU, it does not forward the frame but
instead uses the information in the frame to calculate a BPDU, and, if the topology changes, initiate a BPDU
transmission.
A BPDU exchange results in the following:
One switch is elected as the root bridge.
•
The shortest distance to the root bridge is calculated for each switch based on the path cost.
•
A designated bridge for each LAN segment is selected. This is the switch closest to the root bridge
•
through which frames are forwarded to the root.
A root port is selected. This is the port providing the best path from the bridge to the root bridge.
•
Ports included in the spanning tree are selected.
•
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
66 OL-26590-01
Page 81

Configuring Rapid PVST+
Election of the Root Bridge
For each VLAN, the switch with the lowest numerical value of the bridge ID is elected as the root bridge. If
all switches are configured with the default priority (32768), the switch with the lowest MAC address in the
VLAN becomes the root bridge. The bridge priority value occupies the most significant bits of the bridge ID.
When you change the bridge priority value, you change the probability that the switch will be elected as the
root bridge. Configuring a lower value increases the probability; a higher value decreases the probability.
The STP root bridge is the logical center of each spanning tree topology in a network. All paths that are not
needed to reach the root bridge from anywhere in the network are placed in STP blocking mode.
BPDUs contain information about the transmitting bridge and its ports, including bridge and MAC addresses,
bridge priority, port priority, and path cost. STP uses this information to elect the root bridge for the STP
instance, to elect the root port leading to the root bridge, and to determine the designated port for each segment.
Creating the Spanning Tree Topology
In the following figure, Switch A is elected as the root bridge because the bridge priority of all the switches
is set to the default (32768) and Switch A has the lowest MAC address. However, due to traffic patterns,
number of forwarding ports, or link types, Switch A might not be the ideal root bridge. By increasing the
priority (lowering the numerical value) of the ideal switch so that it becomes the root bridge, you force an
STP recalculation to form a new spanning tree topology with the ideal switch as the root.
Understanding STP
Figure 8: Spanning Tree Topology
When the spanning tree topology is calculated based on default parameters, the path between source and
destination end stations in a switched network might not be ideal. For instance, connecting higher-speed links
to a port that has a higher number than the current root port can cause a root-port change. The goal is to make
the fastest link the root port.
For example, assume that one port on Switch B is a fiber-optic link, and another port on Switch B (an unshielded
twisted-pair [UTP] link) is the root port. Network traffic might be more efficient over the high-speed fiber-optic
link. By changing the STP port priority on the fiber-optic port to a higher priority (lower numerical value)
than the root port, the fiber-optic port becomes the new root port.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 67
Page 82

Understanding Rapid PVST+
Understanding Rapid PVST+
Rapid PVST+ Overview
Rapid PVST+ is the IEEE 802.1w (RSTP) standard implemented per VLAN. A single instance of STP runs
on each configured VLAN (if you do not manually disable STP). Each Rapid PVST+ instance on a VLAN
has a single root switch. You can enable and disable STP on a per-VLAN basis when you are running Rapid
PVST+.
Rapid PVST+ is the default STP mode for the switch.Note
Rapid PVST+ uses point-to-point wiring to provide rapid convergence of the spanning tree. The spanning tree
reconfiguration can occur in less than 1 second with Rapid PVST+ (in contrast to 50 seconds with the default
settings in the 802.1D STP).
Configuring Rapid PVST+
Rapid PVST+ supports one STP instance for each VLAN.Note
Using Rapid PVST+, STP convergence occurs rapidly. Each designated or root port in the STP sends out a
BPDU every 2 seconds by default. On a designated or root port in the topology, if hello messages are missed
three consecutive times, or if the maximum age expires, the port immediately flushes all protocol information
in the table. A port considers that it loses connectivity to its direct neighbor root or designated port if it misses
three BPDUs or if the maximum age expires. This rapid aging of the protocol information allows quick failure
detection. The switch automatically checks the PVID.
Rapid PVST+ provides for rapid recovery of connectivity following the failure of a network device, a switch
port, or a LAN. It provides rapid convergence for edge ports, new root ports, and ports connected through
point-to-point links as follows:
• Edge ports—When you configure a port as an edge port on an RSTP switch, the edge port immediately
transitions to the forwarding state. (This immediate transition was previously a Cisco-proprietary feature
named PortFast.) You should only configure on ports that connect to a single end station as edge ports.
Edge ports do not generate topology changes when the link changes.
Enter the spanning-tree port type interface configuration command to configure a port as an STP edge
port.
We recommend that you configure all ports connected to a host as edge ports.Note
• Root ports—If Rapid PVST+ selects a new root port, it blocks the old root port and immediately transitions
the new root port to the forwarding state.
• Point-to-point links—If you connect a port to another port through a point-to-point link and the local
port becomes a designated port, it negotiates a rapid transition with the other port by using the
proposal-agreement handshake to ensure a loop-free topology.
Rapid PVST+ achieves rapid transition to the forwarding state only on edge ports and point-to-point links.
Although the link type is configurable, the system automatically derives the link type information from the
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
68 OL-26590-01
Page 83

Configuring Rapid PVST+
Understanding Rapid PVST+
duplex setting of the port. Full-duplex ports are assumed to be point-to-point ports, while half-duplex ports
are assumed to be shared ports.
Edge ports do not generate topology changes, but all other designated and root ports generate a topology
change (TC) BPDU when they either fail to receive three consecutive BPDUs from the directly connected
neighbor or the maximum age times out. At this point, the designated or root port sends out a BPDU with the
TC flag set. The BPDUs continue to set the TC flag as long as the TC While timer runs on that port. The value
of the TC While timer is the value set for the hello time plus 1 second. The initial detector of the topology
change immediately floods this information throughout the entire topology.
When Rapid PVST+ detects a topology change, the protocol does the following:
Starts the TC While timer with a value equal to twice the hello time for all the non-edge root and
•
designated ports, if necessary.
Flushes the MAC addresses associated with all these ports.
•
The topology change notification floods quickly across the entire topology. The system flushes dynamic
entries immediately on a per-port basis when it receives a topology change.
Note
The TCA flag is used only when the switch is interacting with switches that are running legacy 802.1D
STP.
The proposal and agreement sequence then quickly propagates toward the edge of the network and quickly
restores connectivity after a topology change.
Rapid PVST+ BPDUs
Rapid PVST+ and 802.1w use all six bits of the flag byte to add the role and state of the port that originates
the BPDU, and the proposal and agreement handshake. The following figure shows the use of the BPDU flags
in Rapid PVST+.
Figure 9: Rapid PVST+ Flag Byte in BPDU
Another important change is that the Rapid PVST+ BPDU is type 2, version 2, which makes it possible for
the switch to detect connected legacy (802.1D) bridges. The BPDU for 802.1D is version 0.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 69
Page 84

Understanding Rapid PVST+
Proposal and Agreement Handshake
As shown in the following figure, switch A is connected to switch B through a point-to-point link, and all of
the ports are in the blocking state. Assume that the priority of switch A is a smaller numerical value than the
priority of switch B.
Figure 10: Proposal and Agreement Handshaking for Rapid Convergence
Configuring Rapid PVST+
Switch A sends a proposal message (a configuration BPDU with the proposal flag set) to switch B, proposing
itself as the designated switch.
After receiving the proposal message, switch B selects as its new root port the port from which the proposal
message was received, forces all non-edge ports to the blocking state, and sends an agreement message (a
BPDU with the agreement flag set) through its new root port.
After receiving the agreement message from switch B, switch A also immediately transitions its designated
port to the forwarding state. No loops in the network can form because switch B blocked all of its non-edge
ports and because there is a point-to-point link between switches A and B.
When switch C connects to switch B, a similar set of handshaking messages are exchanged. Switch C selects
the port connected to switch B as its root port, and both ends of the link immediately transition to the forwarding
state. With each iteration of this handshaking process, one more network device joins the active topology. As
the network converges, this proposal-agreement handshaking progresses from the root toward the leaves of
the spanning tree.
The switch learns the link type from the port duplex mode: a full-duplex port is considered to have a
point-to-point connection and a half-duplex port is considered to have a shared connection. You can override
the default setting that is controlled by the duplex setting by entering the spanning-tree link-type interface
configuration command.
This proposal/agreement handshake is initiated only when a non-edge port moves from the blocking to the
forwarding state. The handshaking process then proliferates step-by-step throughout the topology.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
70 OL-26590-01
Page 85

Configuring Rapid PVST+
Protocol Timers
Understanding Rapid PVST+
The following table describes the protocol timers that affect the Rapid PVST+ performance.
Table 7: Rapid PVST+ Protocol Timers
DescriptionVariable
Port Roles
Hello timer
Determines how often each switch broadcasts BPDUs
to other switches. The default is 2 seconds, and the
range is from 1 to 10.
Forward delay timer
Determines how long each of the listening and
learning states last before the port begins forwarding.
This timer is generally not used by the protocol but
is used as a backup. The default is 15 seconds, and
the range is from 4 to 30 seconds.
Maximum age timer
Determines the amount of time protocol information
received on an port is stored by the switch. This timer
is generally not used by the protocol, but it is used
when interoperating with 802.1D spanning tree. The
default is 20 seconds; the range is from 6 to 40
seconds.
Rapid PVST+ provides rapid convergence of the spanning tree by assigning port roles and learning the active
topology. Rapid PVST+ builds upon the 802.1D STP to select the switch with the highest priority (lowest
numerical priority value) as the root bridge. Rapid PVST+ then assigns one of these port roles to individual
ports:
• Root port—Provides the best path (lowest cost) when the switch forwards packets to the root bridge.
• Designated port—Connects to the designated switch, which incurs the lowest path cost when forwarding
packets from that LAN to the root bridge. The port through which the designated switch is attached to
the LAN is called the designated port.
• Alternate port—Offers an alternate path toward the root bridge to the path provided by the current root
port. An alternate port provides a path to another switch in the topology.
• Backup port—Acts as a backup for the path provided by a designated port toward the leaves of the
spanning tree. A backup port can exist only when two ports are connected in a loopback by a point-to-point
link or when a switch has two or more connections to a shared LAN segment. A backup port provides
another path in the topology to the switch.
• Disabled port—Has no role within the operation of the spanning tree.
In a stable topology with consistent port roles throughout the network, Rapid PVST+ ensures that every root
port and designated port immediately transition to the forwarding state while all alternate and backup ports
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 71
Page 86

Understanding Rapid PVST+
are always in the blocking state. Designated ports start in the blocking state. The port state controls the operation
of the forwarding and learning processes.
A port with the root or a designated port role is included in the active topology. A port with the alternate or
backup port role is excluded from the active topology (see the following figure).
Figure 11: Sample Topology Demonstrating Port Roles
Configuring Rapid PVST+
Port States
Rapid PVST+ Port State Overview
Propagation delays can occur when protocol information passes through a switched LAN. As a result, topology
changes can take place at different times and at different places in a switched network. When a LAN port
transitions directly from nonparticipation in the spanning tree topology to the forwarding state, it can create
temporary data loops. Ports must wait for new topology information to propagate through the switched LAN
before starting to forward frames.
Each LAN port on a software using Rapid PVST+ or MST exists in one of the following four states:
• Blocking—The LAN port does not participate in frame forwarding.
• Learning—The LAN port prepares to participate in frame forwarding.
• Forwarding—The LAN port forwards frames.
• Disabled—The LAN port does not participate in STP and is not forwarding frames.
When you enable Rapid PVST+, every port in the software, VLAN, and network goes through the blocking
state and the transitory states of learning at power up. If properly configured, each LAN port stabilizes to the
forwarding or blocking state.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
72 OL-26590-01
Page 87

Configuring Rapid PVST+
Blocking State
Understanding Rapid PVST+
When the STP algorithm places a LAN port in the forwarding state, the following process occurs:
The LAN port is put into the blocking state while it waits for protocol information that suggests it should
•
go to the learning state.
The LAN port waits for the forward delay timer to expire, moves the LAN port to the learning state, and
•
restarts the forward delay timer.
In the learning state, the LAN port continues to block frame forwarding as it learns the end station
•
location information for the forwarding database.
The LAN port waits for the forward delay timer to expire and then moves the LAN port to the forwarding
•
state, where both learning and frame forwarding are enabled.
A LAN port in the blocking state does not participate in frame forwarding.
A LAN port in the blocking state performs as follows:
Discards frames received from the attached segment.
•
Learning State
Discards frames switched from another port for forwarding.
•
Does not incorporate the end station location into its address database. (There is no learning on a blocking
•
LAN port, so there is no address database update.)
Receives BPDUs and directs them to the system module.
•
Receives, processes, and transmits BPDUs received from the system module.
•
Receives and responds to network management messages.
•
A LAN port in the learning state prepares to participate in frame forwarding by learning the MAC addresses
for the frames. The LAN port enters the learning state from the blocking state.
A LAN port in the learning state performs as follows:
Discards frames received from the attached segment.
•
Discards frames switched from another port for forwarding.
•
Incorporates the end station location into its address database.
•
Receives BPDUs and directs them to the system module.
•
Receives, processes, and transmits BPDUs received from the system module.
•
Receives and responds to network management messages.
•
Forwarding State
A LAN port in the forwarding state forwards frames. The LAN port enters the forwarding state from the
learning state.
A LAN port in the forwarding state performs as follows:
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 73
Page 88

Understanding Rapid PVST+
Disabled State
A LAN port in the disabled state does not participate in frame forwarding or STP. A LAN port in the disabled
state is virtually nonoperational.
A disabled LAN port performs as follows:
Forwards frames received from the attached segment.
•
Forwards frames switched from another port for forwarding.
•
Incorporates the end station location information into its address database.
•
Receives BPDUs and directs them to the system module.
•
Processes BPDUs received from the system module.
•
Receives and responds to network management messages.
•
Discards frames received from the attached segment.
•
Discards frames switched from another port for forwarding.
•
Configuring Rapid PVST+
Does not incorporate the end station location into its address database. (There is no learning, so there is
•
no address database update.)
Does not receive BPDUs from neighbors.
•
Does not receive BPDUs for transmission from the system module.
•
Summary of Port States
The following table lists the possible operational and Rapid PVST+ states for ports and the corresponding
inclusion in the active topology.
Table 8: Port State Active Topology
Port StateOperational Status
Is Port Included in the Active
Topology?
NoBlockingEnabled
YesLearningEnabled
YesForwardingEnabled
NoDisabledDisabled
Synchronization of Port Roles
When the switch receives a proposal message on one of its ports and that port is selected as the new root port,
Rapid PVST+ forces all other ports to synchronize with the new root information.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
74 OL-26590-01
Page 89

Configuring Rapid PVST+
Understanding Rapid PVST+
The switch is synchronized with superior root information received on the root port if all other ports are
synchronized. An individual port on the switch is synchronized if either of the following applies:
That port is in the blocking state.
•
It is an edge port (a port configured to be at the edge of the network).
•
If a designated port is in the forwarding state and is not configured as an edge port, it transitions to the blocking
state when the Rapid PVST+ forces it to synchronize with new root information. In general, when the Rapid
PVST+ forces a port to synchronize with root information and the port does not satisfy any of the above
conditions, its port state is set to blocking.
After ensuring that all of the ports are synchronized, the switch sends an agreement message to the designated
switch that corresponds to its root port. When the switches connected by a point-to-point link are in agreement
about their port roles, Rapid PVST+ immediately transitions the port states to the forwarding state. The
sequence of events is shown in the following figure.
Figure 12: Sequence of Events During Rapid Convergence
Processing Superior BPDU Information
A superior BPDU is a BPDU with root information (such as a lower switch ID or lower path cost) that is
superior to what is currently stored for the port.
If a port receives a superior BPDU, Rapid PVST+ triggers a reconfiguration. If the port is proposed and is
selected as the new root port, Rapid PVST+ forces all the other ports to synchronize.
If the received BPDU is a Rapid PVST+ BPDU with the proposal flag set, the switch sends an agreement
message after all of the other ports are synchronized. The new root port transitions to the forwarding state as
soon as the previous port reaches the blocking state.
If the superior information received on the port causes the port to become a backup port or an alternate port,
Rapid PVST+ sets the port to the blocking state and sends an agreement message. The designated port continues
sending BPDUs with the proposal flag set until the forward-delay timer expires. At that time, the port transitions
to the forwarding state.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 75
Page 90

Understanding Rapid PVST+
Processing Inferior BPDU Information
An inferior BPDU is a BPDU with root information (such as a higher switch ID or higher path cost) that is
inferior to what is currently stored for the port.
If a designated port receives an inferior BPDU, it immediately replies with its own information.
Spanning-Tree Dispute Mechanism
The software checks the consistency of the port role and state in the received BPDUs to detect unidirectional
link failures that could cause bridging loops.
When a designated port detects a conflict, it keeps its role, but reverts to a discarding state because disrupting
connectivity in case of inconsistency is preferable to opening a bridging loop.
The following figure illustrates a unidirectional link failure that typically creates a bridging loop. Switch A
is the root bridge, and its BPDUs are lost on the link leading to switch B. The 802.1w-standard BPDUs include
the role and state of the sending port. With this information, switch A can detect that switch B does not react
to the superior BPDUs it sends and that switch B is the designated, not root port. As a result, switch A blocks
(or keeps blocking) its port, thus preventing the bridging loop. The block is shown as an STP dispute.
Configuring Rapid PVST+
Port Cost
Note
Figure 13: Detecting Unidirectional Link Failure
Rapid PVST+ uses the short (16-bit) pathcost method to calculate the cost by default. With the short
pathcost method, you can assign any value in the range of 1 to 65535. However, you can configure the
switch to use the long (32-bit) pathcost method, which allows you to assign any value in the range of 1
to 200,000,000. You configure the pathcost calculation method globally.
The STP port path-cost default value is determined from the media speed and path-cost calculation method
of a LAN interface. If a loop occurs, STP considers the port cost when selecting a LAN interface to put into
the forwarding state.
Table 9: Default Port Cost
Bandwidth
Long Path-cost Method of Port CostShort Path-cost Method of Port
Cost
2,000,00010010 Mbps
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
76 OL-26590-01
Page 91

Configuring Rapid PVST+
Rapid PVST+ and IEEE 802.1Q Trunks
Port Priority
Bandwidth
Cost
You can assign lower cost values to LAN interfaces that you want STP to select first and higher cost values
to LAN interfaces that you want STP to select last. If all LAN interfaces have the same cost value, STP puts
the LAN interface with the lowest LAN interface number in the forwarding state and blocks other LAN
interfaces.
On access ports, you assign port cost by the port. On trunk ports, you assign the port cost by the VLAN; you
can configure the same port cost to all the VLANs on a trunk port.
If a loop occurs and multiple ports have the same path cost, Rapid PVST+ considers the port priority when
selecting which LAN port to put into the forwarding state. You can assign lower priority values to LAN ports
that you want Rapid PVST+ to select first and higher priority values to LAN ports that you want Rapid PVST+
to select last.
If all LAN ports have the same priority value, Rapid PVST+ puts the LAN port with the lowest LAN port
number in the forwarding state and blocks other LAN ports. The possible priority range is from 0 through
224 (the default is128), configurable in increments of 32. software uses the port priority value when the LAN
port is configured as an access port and uses VLAN port priority values when the LAN port is configured as
a trunk port.
Long Path-cost Method of Port CostShort Path-cost Method of Port
200,00019100 Mbps
20,00041 Gigabit Ethernet
2,000210 Gigabit Ethernet
Rapid PVST+ and IEEE 802.1Q Trunks
In a network of Cisco switches connected through 802.1Q trunks, the switches maintain one instance of STP
for each VLAN allowed on the trunks. However, non-Cisco 802.1Q switches maintain only one instance of
STP for all VLANs allowed on the trunks.
When you connect a Cisco switch to a non-Cisco switch through an 802.1Q trunk, the Cisco switch combines
the STP instance of the 802.1Q VLAN of the trunk with the STP instance of the non-Cisco 802.1Q switch.
However, all per-VLAN STP information that is maintained by Cisco switches is separated by a cloud of
non-Cisco 802.1Q switches. The non-Cisco 802.1Q cloud that separates the Cisco switches is treated as a
single trunk link between the switches.
Rapid PVST+ Interoperation with Legacy 802.1D STP
Rapid PVST+ can interoperate with switches that are running the legacy 802.1D protocol. The switch knows
that it is interoperating with equipment running 802.1D when it receives a BPDU version 0. The BPDUs for
Rapid PVST+ are version 2. If the BPDU received is an 802.1w BPDU version 2 with the proposal flag set,
the switch sends an agreement message after all of the other ports are synchronized. If the BPDU is an 802.1D
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 77
Page 92

Rapid PVST+ Interoperation with 802.1s MST
BPDU version 0, the switch does not set the proposal flag and starts the forward-delay timer for the port. The
new root port requires twice the forward-delay time to transition to the forwarding state.
The switch interoperates with legacy 802.1D switches as follows:
• Notification—Unlike 802.1D BPDUs, 802.1w does not use TCN BPDUs. However, for interoperability
with 802.1D switches, Cisco NX-OS processes and generates TCN BPDUs.
• Acknowledgement—When an 802.1w switch receives a TCN message on a designated port from an
802.1D switch, it replies with an 802.1D configuration BPDU with the TCA bit set. However, if the
TC-while timer (the same as the TC timer in 802.1D) is active on a root port connected to an 802.1D
switch and a configuration BPDU with the TCA set is received, the TC-while timer is reset.
This method of operation is required only for 802.1D switches. The 802.1w BPDUs do not have the TCA bit
set.
• Protocol migration—For backward compatibility with 802.1D switches, 802.1w selectively sends 802.1D
configuration BPDUs and TCN BPDUs on a per-port basis.
When a port is initialized, the migrate-delay timer is started (specifies the minimum time during which 802.1w
BPDUs are sent), and 802.1w BPDUs are sent. While this timer is active, the switch processes all BPDUs
received on that port and ignores the protocol type.
If the switch receives an 802.1D BPDU after the port migration-delay timer has expired, it assumes that it is
connected to an 802.1D switch and starts using only 802.1D BPDUs. However, if the 802.1w switch is using
802.1D BPDUs on a port and receives an 802.1w BPDU after the timer has expired, it restarts the timer and
starts using 802.1w BPDUs on that port.
Configuring Rapid PVST+
If you want all switches to renegotiate the protocol, you must restart Rapid PVST+.Note
Rapid PVST+ Interoperation with 802.1s MST
Rapid PVST+ interoperates seamlessly with the IEEE 802.1s Multiple Spanning Tree (MST) standard. No
user configuration is needed.
Configuring Rapid PVST+
Rapid PVST+, which has the 802.1w standard applied to the Rapid PVST+ protocol, is the default STP setting
in the software.
You enable Rapid PVST+ on a per-VLAN basis. The software maintains a separate instance of STP for each
VLAN (except on those VLANS on which you disable STP). By default, Rapid PVST+ is enabled on the
default VLAN and on each VLAN that you create.
Enabling Rapid PVST+
Once you enable Rapid PVST+ on the switch, you must enable Rapid PVST+ on the specified VLANs.
Rapid PVST+ is the default STP mode. You cannot simultaneously run MST and Rapid PVST+.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
78 OL-26590-01
Page 93

Configuring Rapid PVST+
Enabling Rapid PVST+ per VLAN
Note
Note
Changing the spanning tree mode disrupts traffic because all spanning tree instances are stopped for the
previous mode and started for the new mode.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# spanning-tree
mode rapid-pvst
Enters configuration mode.switch# configure terminal
Enables Rapid PVST+ on the switch. Rapid PVST+ is the
default spanning tree mode.
Note
Changing the spanning tree mode disrupts traffic
because all spanning tree instances are stopped for
the previous mode and started for the new mode.
This example shows how to enable Rapid PVST+ on the switch:
switch# configure terminal
switch(config)# spanning-tree mode rapid-pvst
Because STP is enabled by default, entering the show running-config command to view the resulting
configuration does not display the command that you entered to enable Rapid PVST+.
Enabling Rapid PVST+ per VLAN
You can enable or disable Rapid PVST+ on each VLAN.
Rapid PVST+ is enabled by default on the default VLAN and on all VLANs that you create.Note
Procedure
Step 1
terminal
Step 2
Step 3
switch(config)#
spanning-tree vlan-range
switch(config)# no
spanning-tree vlan-range
PurposeCommand or Action
Enters configuration mode.switch# configure
Enables Rapid PVST+ (default STP) on a per VLAN basis. The
vlan-range value can be 2 through 4094 (except reserved VLAN
values).
(Optional)
Disables Rapid PVST+ on the specified VLAN.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 79
Page 94

Configuring the Root Bridge ID
This example shows how to enable STP on a VLAN:
switch# configure terminal
switch(config)# spanning-tree vlan 5
PurposeCommand or Action
Caution
Configuring Rapid PVST+
Do not disable spanning tree on a VLAN unless all switches
and bridges in the VLAN have spanning tree disabled. You
cannot disable spanning tree on some of the switches and
bridges in a VLAN and leave it enabled on other switches
and bridges. This action can have unexpected results
because switches and bridges with spanning tree enabled
will have incomplete information regarding the physical
topology of the network.
Do not disable spanning tree in a VLAN without ensuring
that there are no physical loops present in the VLAN.
Spanning tree serves as a safeguard against
misconfigurations and cabling errors.
Configuring the Root Bridge ID
The software maintains a separate instance of STP for each active VLAN in Rapid PVST+. For each VLAN,
the switch with the lowest bridge ID becomes the root bridge for that VLAN.
To configure a VLAN instance to become the root bridge, modify the bridge priority from the default value
(32768) to a significantly lower value.
When you enter the spanning-tree vlan vlan_ID root command, the switch checks the bridge priority of
the current root bridges for each VLAN. The switch sets the bridge priority for the specified VLANs to 24576
if this value will cause the switch to become the root for the specified VLANs. If any root bridge for the
specified VLANs has a bridge priority lower than 24576, the switch sets the bridge priority for the specified
VLANs to 4096 less than the lowest bridge priority.
Note
Caution
The spanning-tree vlan vlan_ID root command fails if the value required to be the root bridge is less
than 1.
The root bridge for each instance of STP should be a backbone or distribution switch. Do not configure
an access switch as the STP primary root.
Enter the diameter keyword to specify the network diameter (that is, the maximum number of bridge hops
between any two end stations in the network). When you specify the network diameter, the software
automatically selects an optimal hello time, forward delay time, and maximum age time for a network of that
diameter, which can significantly reduce the STP convergence time. You can enter the hello-time keyword
to override the automatically calculated hello time.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
80 OL-26590-01
Page 95

Configuring Rapid PVST+
Configuring a Secondary Root Bridge
Note
With the switch configured as the root bridge, do not manually configure the hello time, forward-delay
time, and maximum-age time using the spanning-tree mst hello-time, spanning-tree mst forward-time,
and spanning-tree mst max-age configuration commands.
Procedure
Step 1
Step 2
switch(config)# spanning-tree vlan
vlan-range root primary [diameter
dia [hello-time hello-time]]
This example shows how to configure the switch as the root bridge for a VLAN:
switch# configure terminal
switch(config)# spanning-tree vlan 5 root primary diameter 4
Configuring a Secondary Root Bridge
PurposeCommand or Action
Enters configuration mode.switch# configure terminal
Configures a software switch as the primary root bridge.
The vlan-range value can be 2 through 4094 (except
reserved VLAN values.) The dia default is 7. The
hello-time can be from 1 to 10 seconds, and the default
value is 2 seconds.
Note
When you configure a software switch as the secondary root, the STP bridge priority is modified from the
default value (32768) so that the switch is likely to become the root bridge for the specified VLANs if the
primary root bridge fails (assuming the other switches in the network use the default bridge priority of 32768).
STP sets the bridge priority to 28672.
Enter the diameter keyword to specify the network diameter (that is, the maximum number of bridge hops
between any two end stations in the network). When you specify the network diameter, the software
automatically selects an optimal hello time, forward delay time, and maximum age time for a network of that
diameter, which can significantly reduce the STP convergence time. You can enter the hello-time keyword
to override the automatically calculated hello time.
You configure more than one switch in this manner to have multiple backup root bridges. Enter the same
network diameter and hello time values that you used when configuring the primary root bridge.
With the switch configured as the root bridge, do not manually configure the hello time, forward-delay
time, and maximum-age time using the spanning-tree mst hello-time, spanning-tree mst forward-time,
and spanning-tree mst max-age global configuration commands.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 81
Page 96

Configuring the Rapid PVST+ Port Priority
Procedure
Configuring Rapid PVST+
PurposeCommand or Action
Step 1
Step 2
switch(config)# spanning-tree vlan
vlan-range root secondary [diameter
dia [hello-time hello-time]]
This example shows how to configure the switch as the secondary root bridge for a VLAN:
switch# configure terminal
switch(config)# spanning-tree vlan 5 root secondary diameter 4
Configuring the Rapid PVST+ Port Priority
You can assign lower priority values to LAN ports that you want Rapid PVST+ to select first and higher
priority values to LAN ports that you want Rapid PVST+ to select last. If all LAN ports have the same priority
value, Rapid PVST+ puts the LAN port with the lowest LAN port number in the forwarding state and blocks
other LAN ports.
The software uses the port priority value when the LAN port is configured as an access port and uses VLAN
port priority values when the LAN port is configured as a trunk port.
Enters configuration mode.switch# configure terminal
Configures a software switch as the secondary root
bridge. The vlan-range value can be 2 through 4094
(except reserved VLAN values.) The dia default is 7.
The hello-time can be from 1 to 10 seconds, and the
default value is 2 seconds.
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
switch(config)# interface type
slot/port
switch(config-if)# spanning-tree
[vlan vlan-list] port-priority priority
Enters configuration mode.switch# configure terminal
Specifies the interface to configure, and enters interface
configuration mode.
Configures the port priority for the LAN interface. The
priority value can be from 0 to 224. The lower the value,
the higher the priority. The priority values are 0, 32, 64,
96, 128, 160, 192, and 224. All other values are rejected.
The default value is 128.
This example shows how to configure the access port priority of an Ethernet interface:
switch# configure terminal
switch(config)# interface ethernet 1/4
switch(config-if)# spanning-tree port-priority 160
You can only apply this command to a physical Ethernet interface.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
82 OL-26590-01
Page 97

Configuring Rapid PVST+
Configuring the Rapid PVST+ Pathcost Method and Port Cost
Configuring the Rapid PVST+ Pathcost Method and Port Cost
On access ports, you assign port cost by the port. On trunk ports, you assign the port cost by VLAN; you can
configure the same port cost on all the VLANs on a trunk.
Note
In Rapid PVST+ mode, you can use either the short or long pathcost method, and you can configure the
method in either the interface or configuration submode.The default pathcost method is short.
Procedure
PurposeCommand or Action
Step 1
Step 2
Step 3
Step 4
switch(config)# spanning-tree
pathcost method {long | short}
switch(config)# interface type
slot/port
switch(config-if)# spanning-tree
[vlan vlan-id] cost [value | auto]
Enters configuration mode.switch# configure terminal
Selects the method used for Rapid PVST+ pathcost
calculations. The default method is the short method.
Specifies the interface to configure, and enters interface
configuration mode.
Configures the port cost for the LAN interface. The cost
value, depending on the pathcost calculation method, can
be as follows:
• short—1 to 65535
• long—1 to 200000000
Note
You configure this parameter per interface on
access ports and per VLAN on trunk ports.
The default is auto , which sets the port cost on both the
pathcost calculation method and the media speed.
This example shows how to configure the access port cost of an Ethernet interface:
switch# configure terminal
switch (config)# spanning-tree pathcost method long
switch (config)# interface ethernet 1/4
switch(config-if)# spanning-tree cost 1000
You can only apply this command to a physical Ethernet interface.
Configuring the Rapid PVST+ Bridge Priority of a VLAN
You can configure the Rapid PVST+ bridge priority of a VLAN.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 83
Page 98

Configuring the Rapid PVST+ Hello Time for a VLAN
Configuring Rapid PVST+
Note
Be careful when using this configuration. For most situations, we recommend that you configure the
primary root and secondary root to modify the bridge priority.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# spanning-tree vlan
vlan-range priority value
Enters configuration mode.switch# configure terminal
Configures the bridge priority of a VLAN. Valid values
are 0, 4096, 8192, 12288, 16384, 20480, 24576, 28672,
32768, 36864, 40960, 45056, 49152, 53248, 57344, and
61440. All other values are rejected. The default value is
32768.
This example shows how to configure the bridge priority of a VLAN:
switch# configure terminal
switch(config)# spanning-tree vlan 5 priority 8192
Configuring the Rapid PVST+ Hello Time for a VLAN
Note
You can configure the Rapid PVST+ hello time for a VLAN.
Be careful when using this configuration. For most situations, we recommend that you configure the
primary root and secondary root to modify the hello time.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# spanning-tree vlan
vlan-range hello-time hello-time
Enters configuration mode.switch# configure terminal
Configures the hello time of a VLAN. The hello
time value can be from 1 to 10 seconds. The
default is 2 seconds.
This example shows how to configure the hello time for a VLAN:
switch# configure terminal
switch(config)# spanning-tree vlan 5 hello-time 7
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
84 OL-26590-01
Page 99

Configuring Rapid PVST+
Configuring the Rapid PVST+ Forward Delay Time for a VLAN
Configuring the Rapid PVST+ Forward Delay Time for a VLAN
You can configure the forward delay time per VLAN when using Rapid PVST+.
Procedure
PurposeCommand or Action
Step 1
Step 2
This example shows how to configure the forward delay time for a VLAN:
switch# configure terminal
switch(config)# spanning-tree vlan 5 forward-time 21
switch(config)# spanning-tree vlan
vlan-range forward-time forward-time
Enters configuration mode.switch# configure terminal
Configures the forward delay time of a VLAN. The
forward delay time value can be from 4 to 30
seconds, and the default is 15 seconds.
Configuring the Rapid PVST+ Maximum Age Time for a VLAN
You can configure the maximum age time per VLAN when using Rapid PVST+.
Procedure
PurposeCommand or Action
Step 1
Step 2
switch(config)# spanning-tree vlan
vlan-range max-age max-age
Enters configuration mode.switch# configure terminal
Configures the maximum aging time of a VLAN.
The maximum aging time value can be from 6 to 40
seconds, and the default is 20 seconds.
This example shows how to configure the maximum aging time for a VLAN:
switch# configure terminal
switch(config)# spanning-tree vlan 5 max-age 36
Specifying the Link Type
Rapid connectivity (802.1w standard) is established only on point-to-point links. By default, the link type is
controlled from the duplex mode of the interface. A full-duplex port is considered to have a point-to-point
connection; a half-duplex port is considered to have a shared connection.
If you have a half-duplex link physically connected point-to-point to a single port on a remote switch, you
can override the default setting on the link type and enable rapid transitions.
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
OL-26590-01 85
Page 100

Restarting the Protocol
If you set the link to shared, STP moves back to 802.1D.
Procedure
Configuring Rapid PVST+
PurposeCommand or Action
Step 1
Step 2
Step 3
This example shows how to configure the link type as a point-to-point link:
switch# configure terminal
switch (config)# interface ethernet 1/4
switch(config-if)# spanning-tree link-type point-to-point
You can only apply this command to a physical Ethernet interface.
switch(config)# interface type
slot/port
switch(config-if)# spanning-tree
link-type {auto | point-to-point |
shared}
Restarting the Protocol
A bridge running Rapid PVST+ can send 802.1D BPDUs on one of its ports when it is connected to a legacy
bridge. However, the STP protocol migration cannot determine whether the legacy switch has been removed
from the link unless the legacy switch is the designated switch. You can restart the protocol negotiation (force
the renegotiation with neighboring switches) on the entire switch or on specified interfaces.
Enters configuration mode.switch# configure terminal
Specifies the interface to configure, and enters the interface
configuration mode.
Configures the link type to be either a point-to-point link or
shared link. The system reads the default value from the
switch connection, as follows: half duplex links are shared
and full-duplex links are point-to-point. If the link type is
shared, the STP reverts to 802.1D. The default is auto, which
sets the link type based on the duplex setting of the interface.
PurposeCommand
switch# clear spanning-tree detected-protocol
[interface interface [interface-num | port-channel]]
The following example shows how to restart Rapid PVST+ on an Ethernet interface:
switch# clear spanning-tree detected-protocol interface ethernet 1/8
Restarts Rapid PVST+ on all interfaces on the switch
or specified interfaces.
Verifying Rapid PVST+ Configurations
To display Rapid PVST+ configuration information, perform one of these tasks:
PurposeCommand
Displays the current spanning tree configuration.switch# show running-config spanning-tree [all]
Cisco Nexus 3000 NX-OS Layer 2 Switching Configuration Guide, Release 5.0(3)U3(1)
86 OL-26590-01
 Loading...
Loading...