Page 1

Introduction
Note This document may be copied in its entirety and without modification. All copies must include the
FIPS 140-2 Nonproprietary Security Policy for
Cisco 7206VXR NPE-400 Router with VAM
This is a non-proprietary Cryptographic Module Security Policy for Cisco Systems. This security policy
describes how the 7206 VXR NPE-400 with VPN Acceleration Module (VAM) (Hardware Version:
7206-VXR; VAM: Hardware Version 1.0, Board Version A0; Firmware Version: Cisco IOS software
Version12.3(3d)) meets the security requirements of FIPS 140-2 and how to run the module in a secure
FIPS 140-2 mode. This policy was prepared as part of the Level 2 FIPS 140-2 validation of the module.
copyright notice and statements on the last page.
FIPS 140-2 (Federal Information Processing Standards Publication 140-2 — Security Requirements for
Cryptographic Modules) details the U.S. Government requirements for cryptographic modules. More
information about the FIPS 140-2 standard and validation program is available on the NIST website at
http://csrc.nist.gov/cryptval/.
This document includes the following sections:
• Introduction, page 1
• FIPS 140-2 Submission Package, page 2
• Overview, page 2
• Cryptographic Module, page 3
• Module Interfaces, page 3
• Roles and Services, page 6
• Physical Security, page 8
• Cryptographic Key Management, page 9
• Self-Tests, page 15
• Secure Operation, page 16
• Obtaining Documentation, page 17
Corporate Headquarters:
Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706 USA
Copyright © 2004 Cisco Systems, Inc. All rights reserved.
Page 2

FIPS 140-2 Submission Package
• Documentation Feedback, page 18
• Obtaining Technical Assistance, page 18
• Obtaining Additional Publications and Information, page 20
FIPS 140-2 Submission Package
The Security Policy document is one item in the FIPS 140-2 Submission Package. In addition to this
document, the Submission Package includes:
• Vendor evidence document
• Finite state machine
• Module software listing
• Other supporting documentation as additional references
With the exception of this Non-Proprietary Security Policy, the FIPS 140-2 Validation Submission
Documentation is proprietary to Cisco Systems, Inc. and is releasable only under appropriate
non-disclosure agreements. For access to these documents, contact Cisco Systems, Inc. See “Obtaining
Technical Assistance” section on page 18.
Overview
Cisco 7206VXR routers support gigabit capabilities to improve data, voice, and video integration in both
the service provider and enterprise environments. Cisco 7206VXR routers support a high-speed network
services engine (NSE), the high-speed network processing engine (NPE-400), and other network
processing engines.
Cisco 7206VXR routers accommodate a variety of network interface port adapters and an Input/Output
(I/O) controller. A Cisco 7206VXR router equipped with an NPE-400 supports up to six high-speed port
adapters and higher-speed port adapter interfaces including Gigabit Ethernet and OC-12 ATM (Optical
Carrier-12 Asynchronous Transfer Mode). Cisco 7206VXR routers accommodate up to two AC-input or
DC-input power supplies.
Cisco 7206VXR routers support the following features:
• Online insertion and removal (OIR)—Adds, replaces, or removes port adapters without interrupting
the system.
• Dual hot-swappable, load-sharing power supplies—Provides system power redundancy; if one
power supply or power source fails, the other power supply maintains system power without
interruption. Also, when one power supply is powered off and removed from the router, the second
power supply immediately takes over the router power requirements without interrupting normal
operation of the router.
• Environmental monitoring and reporting functions—Maintains normal system operation by
resolving adverse environmental conditions prior to loss of operation.
• Downloadable software—Loads new images into Flash memory remotely, without having to
physically access the router.
The Cisco 7206 VXR router incorporates a single VPN Acceleration Module (VAM) cryptographic
accelerator card. The VAM is installed in one of the port adapter slots.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
2
OL-3959-01
Page 3
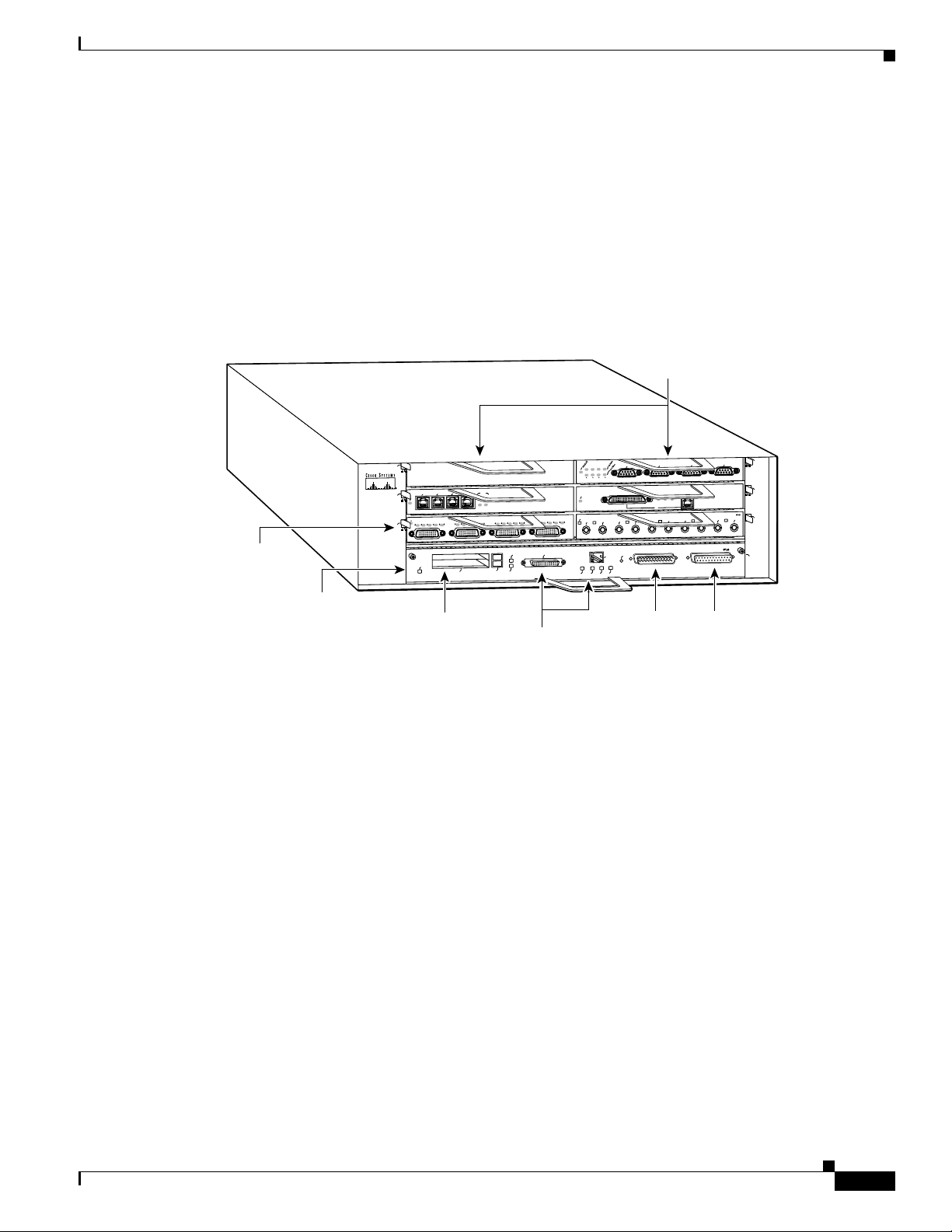
Cryptographic Module
The Cisco 7206VXR NPE-400 router with VAM is a multiple-chip standalone cryptographic module.
The Cisco 7206VXR supports multi-protocol routing and bridging with a wide variety of protocols and
port adapter combinations available for Cisco 7200 series routers. The metal casing that fully encloses
the module establishes the cryptographic boundary for the router, all the functionality discussed in this
document is provided by components within the casing. The Cisco 7206VXR has six slots for port
adapters, one slot for an input/output (I/O) controller, and one slot for a network processing engine or
network services engine.
Figure 1 Cisco 7206VXR NPE-400 Router (Front View)
Port adapter
lever
I/O controller
Cisco 7200
Series
5
1
0
ENABLED
3
EN
CD
LB
RC
RD
TC
TD
1
ENABLED
PC card slots
0
3
2
LINK
3
1
2
0
TC
TD
CD
LB
RC
RD
TC
TD
EJECT
PCMCIA
SLOT 0
ETHERNET 10BT
ENABLED
L
IA
FAST SER
N
E
CD
LB
RC
RD
TC
TD
CD
LB
RC
RD
FE MII
SLOT 1
X
X
X
R
T
R
1
0
S
E
R
PU
C
J-45
R
MII
RJ45
RJ45
EN
OK
EN
1O PWR
LINK
Optional Fast Ethernet port
(MII receptacle and RJ-45 receptacle)
Port adapters
1
5
K
4
J
II
IN
R
L
M
0
X
X
X
X
T
T
E
R
T
R
2
FAST ETHERNET INPUT/OUTPUT CONTROLLER
Auxiliary
port
TOKEN RING
3
2
E
T
S
A
F
ETHERNET-10BFL
X
X
R
T
3
Console
port
Cryptographic Module
6
T
E
N
R
E
H
T
4
TX
2
4
0
H5997
The Cisco 7206VXR NPE-400 uses an RM7000 microprocessor that operates at an internal clock speed
of 350 MHz. The NPE-400 uses SDRAM for storing all packets received or sent from network interfaces.
The SDRAM memory array in the system allows concurrent access by port adapters and the processor.
The NPE-400 has three levels of cache: a primary and a secondary cache that are internal to the
microprocessor, and a tertiary 4-MB external cache that provides additional high-speed storage for data
and instructions.
The Cisco 7206VXR router comes equipped with one 280W AC-input power supply. (A 280W DC-input
power supply option is available.) A power supply filler plate is installed over the second power supply
bay. A fully configured Cisco 7206VXR router operates with only one installed power supply; however,
a second, optional power supply of the same type provides hot-swappable, load-sharing, redundant
power.
Module Interfaces
The interfaces for the router are located on the front panel Input/Output (I/O) Controller, with the
exception of the power switch and power plug. The module has two Fast Ethernet (10/100 RJ-45)
connectors for data transfers in and out. The module also has two other RJ-45 connectors for a console
terminal for local system access and an auxiliary port for remote system access or dial backup using a
modem.
OL-3959-01
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
3
Page 4
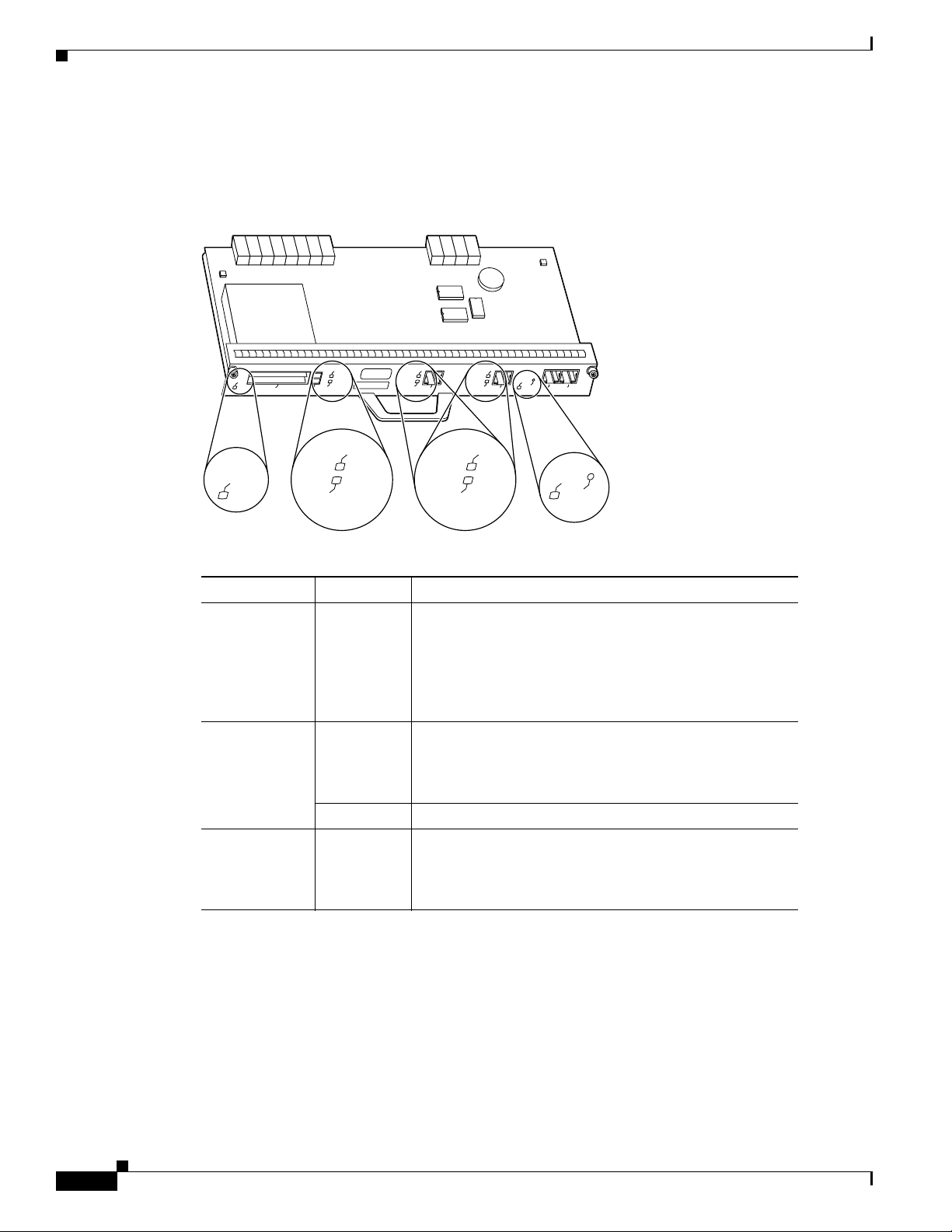
Module Interfaces
Table 1 shows the front panel LEDs, which provide overall status of the router operation. The front panel
displays whether or not the router is booted, if the redundant power is attached and operational, and
overall activity/link status.
Figure 2 Cisco 7206VXR Router Front Panel LEDs
C7200-I/O-2FE/E
ENABLED
ENABLED
SLOT 1
SLOT 0
EJECT
PCMCIA
SLOT 1
SLOT 0
LINK
FE/E 0
100 Mbps
100 Mbps
DUAL FAST ETHERNET INPUT/OUTPUT CONTROLLER
LINK
IO
O
FE/E 1
100 Mbps
LINK
R
PW
K
CPU
AUX
RESET
CONSOLE
IO PWR
OK
CPU
RESET
33444
LED Indication Description
Enabled Green Indicates that the network processing engine or network
services engine and the I/O controller are enabled for
operation by the system; however, it does not mean that
the Fast Ethernet port on the I/O controller is functional or
enabled. This LED goes on during a successful router boot
and remains on during normal operation of the router.
IO POWER OK Amber Indicates that the I/O controller is on and receiving DC
power from the router midplane. This LED comes on
during a successful router boot and remains on during
normal operation of the router.
Off Power off or failed
Slot 0
Slot 1
Green These LEDs indicate which PC Card slot is in use by
coming on when either slot is being accessed by the
system. These LEDs remain off during normal operation
of the router.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
4
OL-3959-01
Page 5
Module Interfaces
LED Indication Description
Link Green Indicates that the Ethernet RJ-45 receptacle has
established a valid link with the network.
Off This LED remains off during normal operation of the
router unless there is an incoming carrier signal.
100 Mbps Green Indicates that the port is configured for 100-Mbps
operation (speed 100), or if configured for auto
negotiation (speed auto), the port has detected a valid link
at 100 Mbps.
Off If the port is configured for 10-Mbps operation, or if it is
configured for auto negotiation and the port has detected a
valid link at 10 Mbps, the LED remains off.
The VPN Acceleration Module (VAM) is a single-width acceleration module that provides
high-performance, hardware-assisted tunneling and encryption services suitable for virtual private
network (VPN) remote access, site-to-site intranet, and extranet applications. It also provides platform
scalability and security while working with all services necessary for successful VPN
deployments—security, quality of service (QoS), firewall and intrusion detection, and service-level
validation and management. The VAM off-loads IPSec processing from the main processor, thus freeing
resources on the processor engines for other tasks.
The VAM has three LEDs, as shown in Figure 3.
Figure 3 VAM LEDs
ENCRYPT/COMP
ENABLE
BOOT
ERROR
SA-VAM
61177
LED Label Color State Function
ENABLE Green On Indicates the VAM is powered up and enabled for
operation.
BOOT Amber Pulses Indicates the VAM is operating.
On Indicates the VAM is booting or a packet is being
encrypted or decrypted.
ERROR Amber On Indicates an encryption error has occurred. This
LED is normally off.
All physical interfaces are separated into the logical interfaces from FIPS as shown in Table 1.
OL-3959-01
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
5
Page 6
Roles and Services
Table 1 FIPS 140-2 Logical Interface
Router Physical Interface FIPS 140-2 Logical Interface
10/100BASE-TX LAN Port
Port Adapter Interface
Console Port
Auxiliary Port
PCMCIA Slot
10/100BASE-TX LAN Port
Port Adapter Interface
Console Port
Auxiliary Port
PCMCIA Slot
Power Switch
Console Port
Auxiliary Port
10/100BASE-TX LAN Port LEDs
Enabled LED
PCMCIA LEDs
IO Pwr Ok LED
VA M L E Ds
Console Port
Auxiliary Port
Power Plug Power Interface
Data Input Interface
Data Output Interface
Control Input Interface
Status Output Interface
In addition to the built-in interfaces, the router also has additional port adapters that can optionally be
placed in an available slot. These port adapters have many embodiments, including multiple Ethernet,
token ring, and modem cards to handle frame relay, ATM, and ISDN connections.
Note These additional port adapters were excluded from this FIPS 140-2 Validation.
Roles and Services
Authentication is role-based. There are two main roles in the router that operators may assume: the
Crypto Officer role and the User role. The administrator of the router assumes the Crypto Officer role to
configure and maintain the router using Crypto Officer services, while Users exercise only the basic User
services. Both roles are authenticated by providing a valid username and password. The configuration
of the encryption and decryption functionality is performed only by the Crypto Officer after
authentication to the Crypto Officer role by providing a valid Crypto Officer username and password.
Once the Crypto Officer configured the encryption and decryption functionality, the User can use this
functionality after authentication to the User role by providing a valid User username and password. The
Crypto Officer can also use the encryption and decryption functionality after authentication to the
Crypto Officer role. The module supports RADIUS and TACACS+ for authentication and they are used
in the FIPS mode. See the Cisco 7206VXR Installation and Configuration Guide for more configuration
information.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
6
OL-3959-01
Page 7

The User and Crypto Officer passwords and the RADIUS/TACACS+ shared secrets must each be at least
8 alphanumeric characters in length. See the “Secure Operation” section on page 16 for more
information. If only integers 0-9 are used without repetition for an 8 digit PIN, the probability of
randomly guessing the correct sequence is 1 in 1,814,400. Including the rest of the alphanumeric
characters drastically decreases the odds of guessing the correct sequence.
Crypto Officer Role
During initial configuration of the router, the Crypto Officer password (the “enable” password) is
defined. A Crypto Officer assigns permission to access the Crypto Officer role to additional accounts,
thereby creating additional Crypto Officers.
The Crypto Officer role is responsible for the configuration and maintenance of the router. The Crypto
Officer services consist of the following:
• Configures the Router: Defines network interfaces and settings, creates command aliases, sets the
protocols the router will support, enables interfaces and network services, sets system date and time,
and loads authentication information.
• Defines Rules and Filters: Creates packet filters that are applied to User data streams on each
interface. Each Filter consists of a set of rules, which define a set of packets to permit or deny based
characteristics such as protocol ID, addresses, ports, TCP connection establishment, or packet
direction.
• Status Functions: Views the router configuration, routing tables, active sessions; views SNMP MIB
II statistics, health, temperature, memory status, voltage, packet statistics; reviews accounting logs,
and views physical interface status.
Roles and Services
User Role
• Manages the Router: Logs off users, shuts down or reloads the router, manually backs up router
configurations, views complete configurations, manager user rights, and restores router
configurations.
• Sets Encryption/Bypass: Sets up the configuration tables for IP tunneling; sets keys and algorithms
to be used for each IP range or allow plaintext packets to be set from specified IP address.
• Changes Port Adapters: Inserts and removes adapters in a port adapter slot.
A User enters the system by accessing the console port with a terminal program. The IOS prompts the
User for their password. If the password is correct, the User is allowed entry to the IOS executive
program. The services available to the User role consist of the following:
• Status Functions: Views state of interfaces, state of layer 2 protocols, and version of IOS currently
running
• Network Functions: Connects to other network devices (via outgoing telnet or PPP) and initiates
diagnostic network services (i.e., ping, mtrace)
• Terminal Functions: Adjusts the terminal session (e.g., lock the terminal, adjust flow control)
• Directory Services: Displays directory of files kept in flash memory
OL-3959-01
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
7
Page 8

Physical Security
Physical Security
The router is encased in a steel chassis. The front of the router includes six port adapter slots. The rear
of the router includes on-board LAN connectors, PC Card slots, and Console/Auxiliary connectors,
power cable connection, a power switch, and access to the Network Processing Engine.
Any port adapter slot not populated with a port adapter must be populated with a slot cover (blank port
adapter) to operate in FIPS compliant mode. Slot covers are included with each router; additional covers
may be ordered from Cisco. You apply the same procedure for labeling port adapters covers as for the
port adapters.
Once the router has been configured to meet FIPS 140-2 Level 2 requirements, the router cannot be
accessed without signs of tampering. The word ‘Open’ may appear on the label if it was peeled away
from the surface of the module. The Crypto Officer should be instructed to record serial numbers, and
to inspect for signs of tampering or changed numbers periodically.
To seal the system, apply serialized tamper-evidence labels as described below, and as shown in Figure 4
and Figure 5:
Step 1 Clean the cover of any grease, dirt, or oil before applying the tamper evidence labels. Alcohol-based
cleaning pads are recommended for this purpose. The ambient air must be above 10C, otherwise the
labels may not properly cure.
Step 2 The tamper evidence label should be placed so that the one half of the label covers the enclosure and the
other half covers the 7206 VXR NPE-400 Input/Output Controller.
Step 3 The tamper evidence label should be placed over the Flash PC Card slots on the Input/Output Controller.
Step 4 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the port adapter slot 1.
Step 5 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the port adapter slot 2.
Step 6 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the port adapter slot 3.
Step 7 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the port adapter slot 4.
Step 8 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the port adapter slot 5.
Step 9 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the port adapter slot 6.
Step 10 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the network processing engine.
Step 11 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the power supply plate.
Step 12 The tamper evidence label should be placed so that one half of the label covers the enclosure and the
other half covers the redundant power supply plate.
Step 13 Allow the labels to cure for five minutes.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
8
OL-3959-01
Page 9

Figure 4 Tamper Evidence Label Placement (Front View)
5
ETHERNET 10BT
ENABLED
IAL
SER
FAST
N
E
CD
LB
RC
RD
TC
TD
CD
LB
RC
RD
FE MII
SLOT 1
X
X
T
R
0
R
MII
RJ45
RJ45
EN
OK
EN
1O PWR
LINK
Port adapter
lever
Cisco 7200
Series
3
2
1
0
ENABLED
3
EN
RC
RD
TC
TD
1
ENABLED
LINK
3
1
2
0
TC
TD
CD
LB
RC
RD
TC
TD
CD
LB
EJECT
PCMCIA
SLOT 0
I/O controller
PC card slots
Optional Fast Ethernet port
(MII receptacle and RJ-45 receptacle)
Figure 5 Tamper Evidence Label Placement (Rear View)
Port adapters
0
X
TX
R
1
T
SE
5
PU RE
C
J-4
Auxiliary
port
2
1
5
K
4
J
II
IN
R
L
M
0
X
X
X
R
T
R
3
2
FAST ETHERNET INPUT/OUTPUT CONTROLLER
Console
Cryptographic Key Management
TOKEN RING
6
3
T
E
N
R
E
H
T
E
T
S
FA
4
ETHERNET-10BFL
X
X
X
T
R
T
2
4
0
119934
port
Chassis
grounding
receptacles
Power supply
filler plate
Network processing engine
or network services engine
Power switch
Cryptographic Key Management
The router securely administers both cryptographic keys and other critical security parameters such as
passwords. The tamper evidence seals provide physical protection for all keys. All keys are also
protected by the password-protection on the Crypto Officer role login, and can be zeroized by the Crypto
Officer. Keys are exchanged manually and entered electronically via manual key exchange or Internet
Key Exchange (IKE).
The modules contain a cryptographic accelerator card (VAM), which provides DES (56-bit) (only for
legacy systems), and 3DES (168-bit) IPSec encryption, MD5 and SHA-1 hashing, and has hardware
support for DH and RSA key generation.
The module supports the following critical security parameters (CSPs):
AC-input
power supply
Internal fans
AC-input
receptacle
NETW
ORK PROCESSING ENGINE-150
119933
OL-3959-01
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
9
Page 10
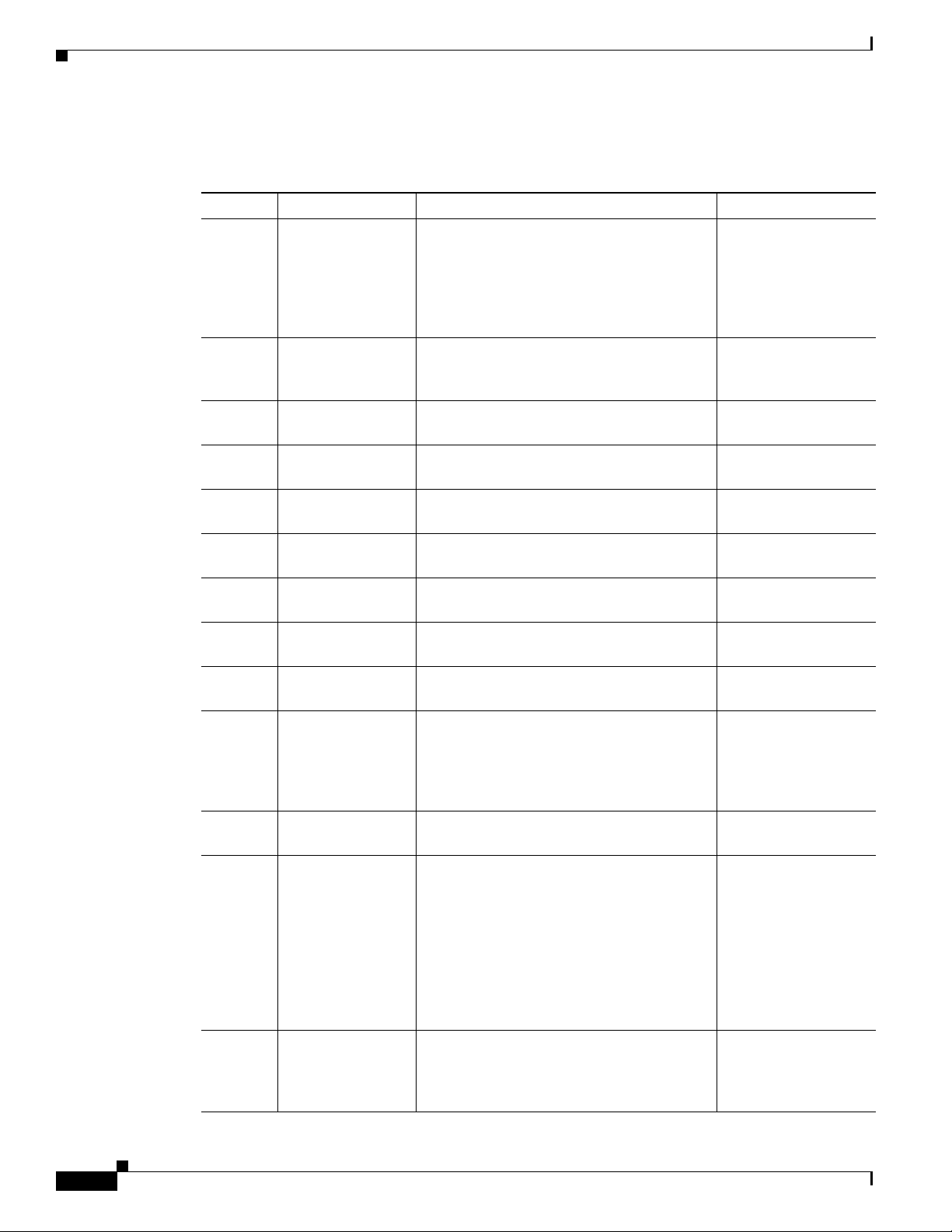
Cryptographic Key Management
The module supports the following critical security parameters (CSPs):
Table 2 Critical Security Parameters
# CSP Name Description Storage
1 CSP 1 This is the seed key for X9.31 PRNG. This
2 CSP2 The private exponent used in Diffie-Hellman
3 CSP3 The shared secret within IKE exchange.
4 CSP4 Same as above DRAM
5 CSP5 Same as above DRAM
6 CSP6 Same as above DRAM
7 CSP7 The IKE session encrypt key. The
8 CSP8 The IKE session authentication key. The
9 CSP9 The RSA private key. “crypto key zeroize”
10 CSP10 The key used to generate IKE skeyid during
11 CSP11 This key generates keys 3, 4, 5 and 6. This
12 CSP12 The RSA public key used to validate
13 CSP13 The fixed key used in Cisco vendor ID
key is stored in DRAM and updated
periodically after the generation of 400
bytes; hence, it is zeroized periodically.
Also, the operator can turn off the router to
zeroize this key.
(DH) exchange. Zeroized after DH shared
secret has been generated.
Zeroized when IKE session is terminated.
zeroization is the same as above.
zeroization is the same as above.
command zeroizes this key.
preshared-key authentication. The no crypto
isakmp key command zeroizes it. This key
can have two forms based on whether the key
is related to the hostname or the IP address.
key is zeroized after generating those keys.
signatures within IKE. These keys are
expired either when CRL (certificate
revocation list) expires or 5 secs after if no
CRL exists. After above expiration happens
and before a new public key structure is
created this key is deleted. This key does not
need to be zeroized because it is a public key;
however, it is zeroized as mentioned here.
generation. This key is embedded in the
module binary image and can be deleted by
erasing the Flash.
DRAM
(plaintext)
DRAM
(plaintext)
DRAM
(plaintext)
(plaintext)
(plaintext)
(plaintext)
DRAM
(plaintext)
DRAM
(plaintext)
NVRAM
(plaintext)
NVRAM
(plaintext)
DRAM
(plaintext)
DRAM
(plaintext)
NVRAM
(plaintext)
10
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
Page 11

Cryptographic Key Management
Table 2 Critical Security Parameters (Continued)
# CSP Name Description Storage
14 CSP14 The IPSec encryption key. Zeroized when
IPSec session is terminated.
15 CSP15 The IPSec authentication key. The
zeroization is the same as above.
16 CSP16 The RSA public key of the CA. The no
crypto ca trust <label> command
DRAM
(plaintext)
DRAM
(plaintext)
NVRAM
(plaintext)
invalidates the key and it frees the public key
label which in essence prevent use of the key.
This key does not need to be zeroized
because it is a public key.
17 CSP17 This key is a public key of the DNS server.
Zeroized using the same mechanism as
NVRAM
(plaintext)
above. The no crypto ca trust <label>
command invalidates the DNS server public
key and it frees the public key label which in
essence prevent use of that key. This label is
different from the label in the above key.
This key does not need to be zeroized
because it is a public key.
18 CSP18 The SSL session key. Zeroized when the SSL
connection is terminated.
19 CSP19 The ARAP key that is hardcoded in the
module binary image. This key can be
DRAM
(plaintext)
Flash
(plaintext)
deleted by erasing the Flash.
20 CSP20 This is an ARAP user password used as an
authentication key. A function uses this key
DRAM
(plaintext)
in a DES algorithm for authentication.
21 CSP21 The key used to encrypt values of the
configuration file. This key is zeroized when
NVRAM
(plaintext)
the no key config-key command is issued.
22 CSP22 This key is used by the router to authenticate
itself to the peer. The router itself gets the
DRAM
(plaintext)
password (that is used as this key) from the
AAA server and sends it onto the peer. The
password retrieved from the AAA server is
zeroized upon completion of the
authentication attempt.
23 CSP23 The RSA public key used in SSH. Zeroized
after the termination of the SSH session.
DRAM
(plaintext)
This key does not need to be zeroized
because it is a public key; However, it is
zeroized as mentioned here.
24 CSP24 The authentication key used in PPP. This key
is in the DRAM and not zeroized at runtime.
DRAM
(plaintext)
One can turn off the router to zeroize this key
because it is stored in DRAM.
OL-3959-01
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
11
Page 12
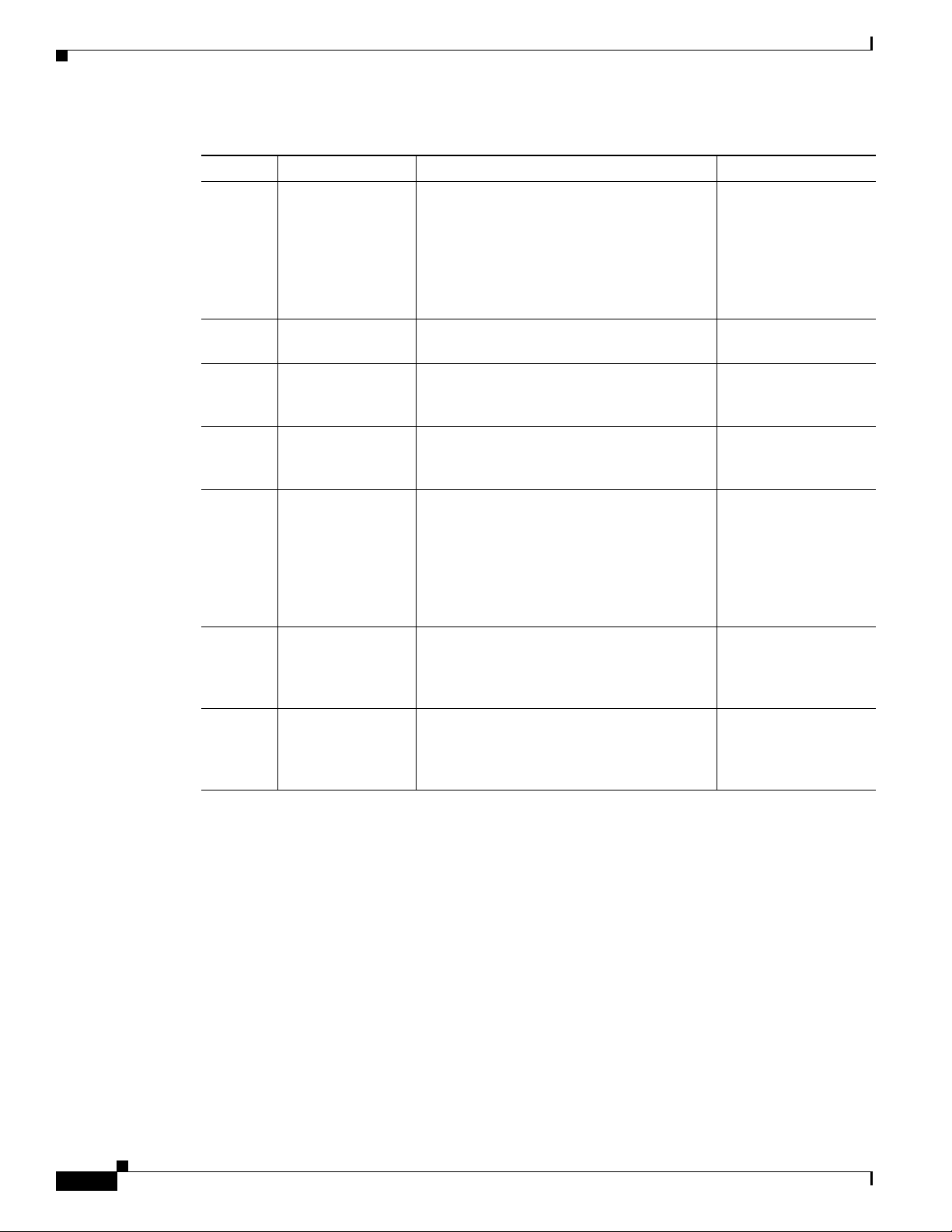
Cryptographic Key Management
Table 2 Critical Security Parameters (Continued)
# CSP Name Description Storage
25 CSP25 This key is used by the router to authenticate
26 CSP26 This is the SSH session key. It is zeroized
27 CSP27 The password of the User role. This
28 CSP28 The plaintext password of the Crypto Officer
29 CSP29 The ciphertext password of the Crypto
30 CSP30 The RADIUS shared secret. This shared
31 CSP31 The TACACS+ shared secret. This shared
itself to the peer. The key is identical to #22
except that it is retrieved from the local
database (on the router itself). Issuing the no
username password command zeroizes the
password (that is used as this key) from the
local database.
when the SSH session is terminated.
password is zeroized by overwriting it with a
new password.
role. This password is zeroized by
overwriting it with a new password.
Officer role. However, the algorithm used to
encrypt this password is not FIPS approved.
Therefore, this password is considered
plaintext for FIPS purposes. This password
is zeroized by overwriting it with a new
password.
secret is zeroized by executing the “no” form
of the RADIUS shared secret set command.
secret is zeroized by executing the “no” form
of the TACACS+ shared secret set command.
NVRAM
(plaintext)
DRAM
(plaintext)
NVRAM
(plaintext)
NVRAM
(plaintext)
NVRAM
(plaintext)
DRAM
(plaintext),
NVRAM
(plaintext)
DRAM
(plaintext),
NVRAM
(plaintext)
12
The services accessing the CSPs, the type of access and which role accesses the CSPs are listed in the
Figure 6.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
Page 13

Figure 6 Role and Service Access to CSPs
Cryptographic Key Management
OL-3959-01
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
13
Page 14

Cryptographic Key Management
14
The module supports DES (only for legacy systems), 3DES, DES-MAC, TDES-MAC, AES, SHA-1,
HMAC SHA-1, MD5, MD4, HMAC MD5, Diffie-Hellman, RSA (for digital signatures and
encryption/decryption (for IKE authentication)) cryptographic algorithms. The MD5, HMAC MD5, and
MD4 algorithms are disabled when operating in FIPS mode.
The module supports three types of key management schemes:
• Manual key exchange method that is symmetric. DES/3DES/AES key and HMAC-SHA-1 key are
exchanged manually and entered electronically.
• Internet Key Exchange method with support for exchanging pre-shared keys manually and entering
electronically.
–
The pre-shared keys are used with Diffie-Hellman key agreement technique to derive DES,
3DES or AES keys.
–
The pre-shared key is also used to derive HMAC-SHA-1 key.
• Internet Key Exchange with RSA-signature authentication.
All pre-shared keys are associated with the Crypto Officer role that created the keys, and the Crypto
Officer role is protected by a password. Therefore, the Crypto Officer password is associated with all the
pre-shared keys. The Crypto Officer needs to be authenticated to store keys. All Diffie-Hellman (DH)
keys agreed upon for individual tunnels are directly associated with that specific tunnel only via the IKE
protocol.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
Page 15

Key Zeroization
All of the keys and CSPs of the module can be zeroized. Please refer to the Description column of
Table 2 for information on methods to zeroize each key and CSP.
Self-Tests
To prevent secure data from being released, it is important to test the cryptographic components of a
security module to insure all components are functioning correctly. The router includes an array of
self-tests that are run during startup and periodically during operations. If any of the self-tests fail, the
router transitions into an error state. Within the error state, all secure data transmission is halted and the
router outputs status information indicating the failure.
Self-tests performed by the IOS image:
• Power-up tests
–
Firmware integrity test
–
RSA signature KAT (both signature and verification)
–
DES KAT
Self-Tests
–
TDES KAT
–
AES KAT
–
SHA-1 KAT
–
PRNG KAT
–
Power-up bypass test
–
Diffie-Hellman self-test
–
HMAC-SHA-1 KAT
• Conditional tests
–
Conditional bypass test
–
Pairwise consistency test on RSA signature
–
Continuous random number generator tests
Self-tests performed by the VAM (cryptographic accelerator):
• Power-up tests
–
Firmware integrity test
–
RSA signature KAT (both signature and verification)
–
DES KAT
–
TDES KAT
–
SHA-1 KAT
–
HMAC-SHA-1 KAT
–
PRNG KAT
OL-3959-01
• Conditional tests
–
Pairwise consistency test on RSA signature
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
15
Page 16

Secure Operation
–
Continuous random number generator test
Secure Operation
The Cisco 7206VXR NPE-400 router with a single VPN Acceleration Module (VAM) meets all the Level
2 requirements for FIPS 140-2. Follow the setting instructions provided below to place the module in
FIPS mode of operation. Operating this router without maintaining the appropriate settings will remove
the module from the FIPS approved mode of operation.
Initial Setup
• The Crypto Officer ensures that the VAM cryptographic accelerator card is installed in the module
by visually confirming the presence of the VAM in a port adapter slot.
• The Crypto Officer must apply tamper evidence labels as described in the “Physical Security”
section on page 8 of this document.
• Only a Crypto Officer may add and remove port adapters. When removing the tamper evidence label,
the Crypto Officer should remove the entire label from the router and clean the cover of any grease,
dirt, or oil with an alcohol-based cleaning pad. The Crypto Officer must re-apply tamper evidence
labels on the router as described in the “Physical Security” section on page 8 of this document.
System Initialization and Configuration
• The Crypto Officer must perform the initial configuration. The Cisco IOS software version 12.3(3d)
is the only allowable image. No other image may be loaded.
• The value of the boot field must be 0x0102. This setting disables break from the console to the ROM
monitor and automatically boots the IOS image. From the configure terminal command line, the
Crypto Officer enters the following syntax:
config-register 0x0102
• The Crypto Officer must create the “enable” password for the Crypto Officer role. The password
must be at least 8 characters and is entered when the Crypto Officer first engages the enable
command. The Crypto Officer enters the following syntax at the “#” prompt:
enable secret [PASSWORD]
• The Crypto Officer must always assign passwords (of at least 8 characters) to users. Identification
and authentication on the console port is required for Users. From the configure terminal command
line, the Crypto Officer enters the following syntax:
line con 0
password [PASSWORD]
login local
• The Crypto Officer shall only assign users to a privilege level 1 (the default).
• The Crypto Officer shall not assign a command to any privilege level other than its default.
16
• The Crypto Officer may configure the module to use RADIUS or TACACS+ for authentication.
Configuring the module to use RADIUS or TACACS+ for authentication is optional. If the module
is configured to use RADIUS or TACACS+, the Crypto-Officer must define RADIUS or TACACS+
shared secret keys that are at least 8 characters long.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
Page 17

• If the Crypto Officer loads any IOS image onto the router, this will put the router into a non-FIPS
mode of operation.
IPSec Requirements and Cryptographic Algorithms
There are two types of key management method that are allowed in FIPS mode: Internet Key Exchange
(IKE) and IPSec manually entered keys.
Although the IOS implementation of IKE allows a number of algorithms, only the following algorithms
are allowed in a FIPS 140-2 configuration:
• ah-sha-hmac
• esp-des
• esp-sha-hmac
• esp-3des
• esp-aes
The following algorithms are not FIPS approved and should be disabled:
• MD-4 and MD-5 for signing
• MD-5 HMAC
Obtaining Documentation
Protocols
All SNMP operations must be performed within a secure IPSec tunnel.
Remote Access
• Telnet access to the module is only allowed via a secure IPSec tunnel between the remote system
and the module. The Crypto Officer must configure the module so that any remote connections via
telnet are secured through IPSec.
• SSH access to the module is only allowed if SSH is configured to use a FIPS-approved algorithm.
The Crypto Officer must configure the module so that SSH uses only FIPS-approved algorithms.
Obtaining Documentation
Cisco documentation and additional literature are available on Cisco.com. Cisco also provides several
ways to obtain technical assistance and other technical resources. These sections explain how to obtain
technical information from Cisco Systems.
Cisco.com
OL-3959-01
You can access the most current Cisco documentation at this URL:
http://www.cisco.com/univercd/home/home.htm
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
17
Page 18

Documentation Feedback
You can access the Cisco website at this URL:
http://www.cisco.com
You can access international Cisco websites at this URL:
http://www.cisco.com/public/countries_languages.shtml
Ordering Documentation
You can find instructions for ordering documentation at this URL:
http://www.cisco.com/univercd/cc/td/doc/es_inpck/pdi.htm
You can order Cisco documentation in these ways:
• Registered Cisco.com users (Cisco direct customers) can order Cisco product documentation from
the Ordering tool:
http://www.cisco.com/en/US/partner/ordering/index.shtml
• Nonregistered Cisco.com users can order documentation through a local account representative by
calling Cisco Systems Corporate Headquarters (California, USA) at 408 526-7208 or, elsewhere in
North America, by calling 800 553-NETS (6387).
Documentation Feedback
You can send comments about technical documentation to bug-doc@cisco.com.
You can submit comments by using the response card (if present) behind the front cover of your
document or by writing to the following address:
Cisco Systems
Attn: Customer Document Ordering
170 West Tasman Drive
San Jose, CA 95134-9883
We appreciate your comments.
Obtaining Technical Assistance
For all customers, partners, resellers, and distributors who hold valid Cisco service contracts, Cisco
Technical Support provides 24-hour-a-day, award-winning technical assistance. The Cisco Technical
Support Website on Cisco.com features extensive online support resources. In addition, Cisco Technical
Assistance Center (TAC) engineers provide telephone support. If you do not hold a valid Cisco service
contract, contact your reseller.
18
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
Page 19

Cisco Technical Support Website
The Cisco Technical Support Website provides online documents and tools for troubleshooting and
resolving technical issues with Cisco products and technologies. The website is available 24 hours a day,
365 days a year at this URL:
http://www.cisco.com/techsupport
Access to all tools on the Cisco Technical Support Website requires a Cisco.com user ID and password.
If you have a valid service contract but do not have a user ID or password, you can register at this URL:
http://tools.cisco.com/RPF/register/register.do
Submitting a Service Request
Using the online TAC Service Request Tool is the fastest way to open S3 and S4 service requests. (S3
and S4 service requests are those in which your network is minimally impaired or for which you require
product information.) After you describe your situation, the TAC Service Request Tool automatically
provides recommended solutions. If your issue is not resolved using the recommended resources, your
service request will be assigned to a Cisco TAC engineer. The TAC Service Request Tool is located at
this URL:
Obtaining Technical Assistance
http://www.cisco.com/techsupport/servicerequest
For S1 or S2 service requests or if you do not have Internet access, contact the Cisco TAC by telephone.
(S1 or S2 service requests are those in which your production network is down or severely degraded.)
Cisco TAC engineers are assigned immediately to S1 and S2 service requests to help keep your business
operations running smoothly.
To open a service request by telephone, use one of the following numbers:
Asia-Pacific: +61 2 8446 7411 (Australia: 1 800 805 227)
EMEA: +32 2 704 55 55
USA: 1 800 553 2447
For a complete list of Cisco TAC contacts, go to this URL:
http://www.cisco.com/techsupport/contacts
Definitions of Service Request Severity
To ensure that all service requests are reported in a standard format, Cisco has established severity
definitions.
Severity 1 (S1)—Your network is “down,” or there is a critical impact to your business operations. You
and Cisco will commit all necessary resources around the clock to resolve the situation.
Severity 2 (S2)—Operation of an existing network is severely degraded, or significant aspects of your
business operation are negatively affected by inadequate performance of Cisco products. You and Cisco
will commit full-time resources during normal business hours to resolve the situation.
OL-3959-01
Severity 3 (S3)—Operational performance of your network is impaired, but most business operations
remain functional. You and Cisco will commit resources during normal business hours to restore service
to satisfactory levels.
Severity 4 (S4)—You require information or assistance with Cisco product capabilities, installation, or
configuration. There is little or no effect on your business operations.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
19
Page 20

Obtaining Additional Publications and Information
Obtaining Additional Publications and Information
Information about Cisco products, technologies, and network solutions is available from various online
and printed sources.
• Cisco Marketplace provides a variety of Cisco books, reference guides, and logo merchandise. Visit
Cisco Marketplace, the company store, at this URL:
http://www.cisco.com/go/marketplace/
• The Cisco Product Catalog describes the networking products offered by Cisco Systems, as well as
ordering and customer support services. Access the Cisco Product Catalog at this URL:
http://cisco.com/univercd/cc/td/doc/pcat/
• Cisco Press publishes a wide range of general networking, training and certification titles. Both new
and experienced users will benefit from these publications. For current Cisco Press titles and other
information, go to Cisco Press at this URL:
http://www.ciscopress.com
• Pack et magazine is the Cisco Systems technical user magazine for maximizing Internet and
networking investments. Each quarter, Packet delivers coverage of the latest industry trends,
technology breakthroughs, and Cisco products and solutions, as well as network deployment and
troubleshooting tips, configuration examples, customer case studies, certification and training
information, and links to scores of in-depth online resources. You can access Packet magazine at this
URL:
http://www.cisco.com/packet
• iQ Magazine is the quarterly publication from Cisco Systems designed to help growing companies
learn how they can use technology to increase revenue, streamline their business, and expand
services. The publication identifies the challenges facing these companies and the technologies to
help solve them, using real-world case studies and business strategies to help readers make sound
technology investment decisions. You can access iQ Magazine at this URL:
http://www.cisco.com/go/iqmagazine
• Internet Protocol Journal is a quarterly journal published by Cisco Systems for engineering
professionals involved in designing, developing, and operating public and private internets and
intranets. You can access the Internet Protocol Journal at this URL:
http://www.cisco.com/ipj
• World-class networking training is available from Cisco. You can view current offerings at
this URL:
http://www.cisco.com/en/US/learning/index.html
20
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
Page 21

Obtaining Additional Publications and Information
This document is to be used in conjunction with the documents that shipped with your hardware.
CCSP, the Cisco Square Bridge logo, Cisco Unity, Follow Me Browsing, FormShare, and StackWise are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live,
Play, and Learn, and iQuick Study are service marks of Cisco Systems, Inc.; and Aironet, ASIST, BPX, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, Cisco, the Cisco
Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Empowering the Internet Generation,
Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, GigaDrive, GigaStack, HomeLink, Internet Quotient, IOS, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness
Scorecard, LightStream, Linksys, MeetingPlace, MGX, the Networkers logo, Networking Academy, Network Registrar, Packet, PIX, Post-Routing, Pre-Routing, ProConnect,
RateMUX, Registrar, ScriptShare, SlideCast, SMARTnet, StrataView Plus, SwitchProbe, TeleRouter, The Fastest Way to Increase Your Internet Quotient, TransPath, and VCO
are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship
between Cisco and any other company. (0406R)
Copyright © 2004 Cisco Systems, Inc. All rights reserved.
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
21
Page 22

Obtaining Additional Publications and Information
22
FIPS 140-2 Nonproprietary Security Policy for Cisco 7206VXR NPE-400 Router with VAM
OL-3959-01
 Loading...
Loading...