Page 1

User Manual
Chung Nam Electronics (CNE)
IEEE 802.11b/g/n USB Dongle
(Model #: WLC322NAM)
User Manual
Version 0.1
July 2008
- 1 -
Page 2

User Manual
Contents
Chapter 1: Product Information .....................................................................................3
1.1 Introduction....................................................................................................... 3
1.2 Features.............................................................................................................3
1.3 LED Status........................................................................................................3
Chapter 2: Installation Guide.........................................................................................4
2.1 Overview...........................................................................................................4
2.2 Installation procedure........................................................................................4
2.2.1 Software installation ...............................................................................4
2.2.2 Hardware Installation............................................................................10
Chapter 3: Configuration .............................................................................................11
3.1 Using Atheros configuration utility ................................................................ 11
3.2 Using Windows Zero Configuration...............................................................15
3.3 Link status.......................................................................................................18
Chapter 4: Regulatory information.............................................................................. 19
4.1 FCC Information to User ................................................................................19
4.2 FCC Guidelines for Human Exposure ............................................................19
4.3 FCC Electronic Emission Notices ..................................................................19
Chapter 5: Technical Specifications ............................................................................ 21
Appendix A: Specifications ..................................................................................21
Appendix B: Glossary........................................................................................... 22
- 2 -
Page 3

User Manual
Chapter 1: Product Information
1.1 Introduction
The CNE Wireless USB Adapter is a USB 2.0 pen-size wireless dongle supporting
IEEE 802.11b/g /n 2.4GHz radio operation, The WLAN Adapter provide high-speed
wireless connection with data rate from 1 Mbps up to 300Mbps theoretically.
Additionally, wireless roaming allows the user to move among different AP without
losing the current connection. The adapter provides excellent security features
including:TKIP, AES, WPA, and up to 128 bit WEP encryption security make the
network almost impenetrable.
Featuring high performance transmission rates, simple installation and adaptability, as
well as strong security the USB WLAN adapter is the perfect solution for small office
and home needs.
1.2 Features
z Complies with IEEE 802.11b/g, IEEE 802.11n Draft 2.0 standards.
z 2T2R Modes for Antenna configurations.
z Dynamic data rate: Maximum data rate up to 300Mbps. Auto fallback switchi
-ng with 54, 48, 36, 24, 18, 12, 11, 9, 6, 5.5, 2 and 1Mbps.
z Reverse Direction Data Flow and Frame Aggregation.
z Multiple BSSID Support.
z Wireless data encryption with 64, 128 encryption for security
z Lower Power with Advanced Power Management.
z Drivers supports Windows2000, XP and Vista, Linux
1.3 LED Status
The LED on the top of this card indicates Link/Act status. It blinks at green light
when sending and receiving data.
- 3 -
Page 4
User Manual
Chapter 2: Installation Guide
2.1 Overview
The USB WLAN Adapter Setup Wizard will guide you through the installation
procedure for Windows 2000, XP, Vista and Linux. This Wizard will also guide you
installing the Utility and drivers.
In case you plug in the hardware before installing the software, you will be prompted
by “Found New Hardware Wizard”, please click the Cancel button, and run the Setup
Wizard program from the installation CD-ROM shipped together with the WLAN
Adapter.
All of following sections are written based on Windows XP.
* Note: The comments and conditions for other OS platforms may be different from
this chapter.
2.2 Installation procedure
2.2.1 Software installation
1. Insert the Resource CD into the CD/DVD-ROM drive of your computer, and
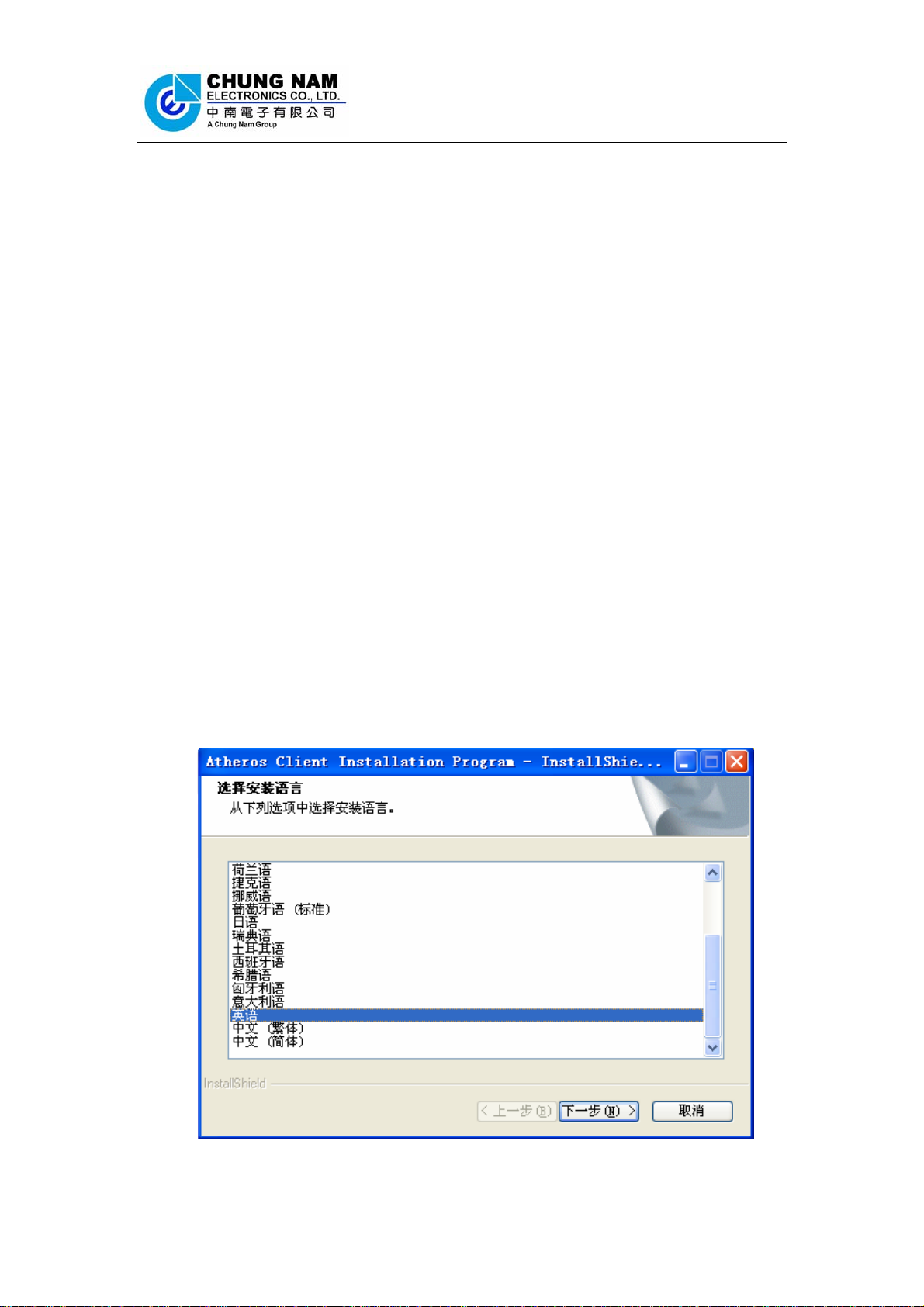
execute ‘Setup.exe’ to install the driver. Figure 2-1 should then appear, please select
the language that you want (e.g. English) and click ‘Next’:
Figure 2-1 Language selection
- 4 -
Page 5
User Manual
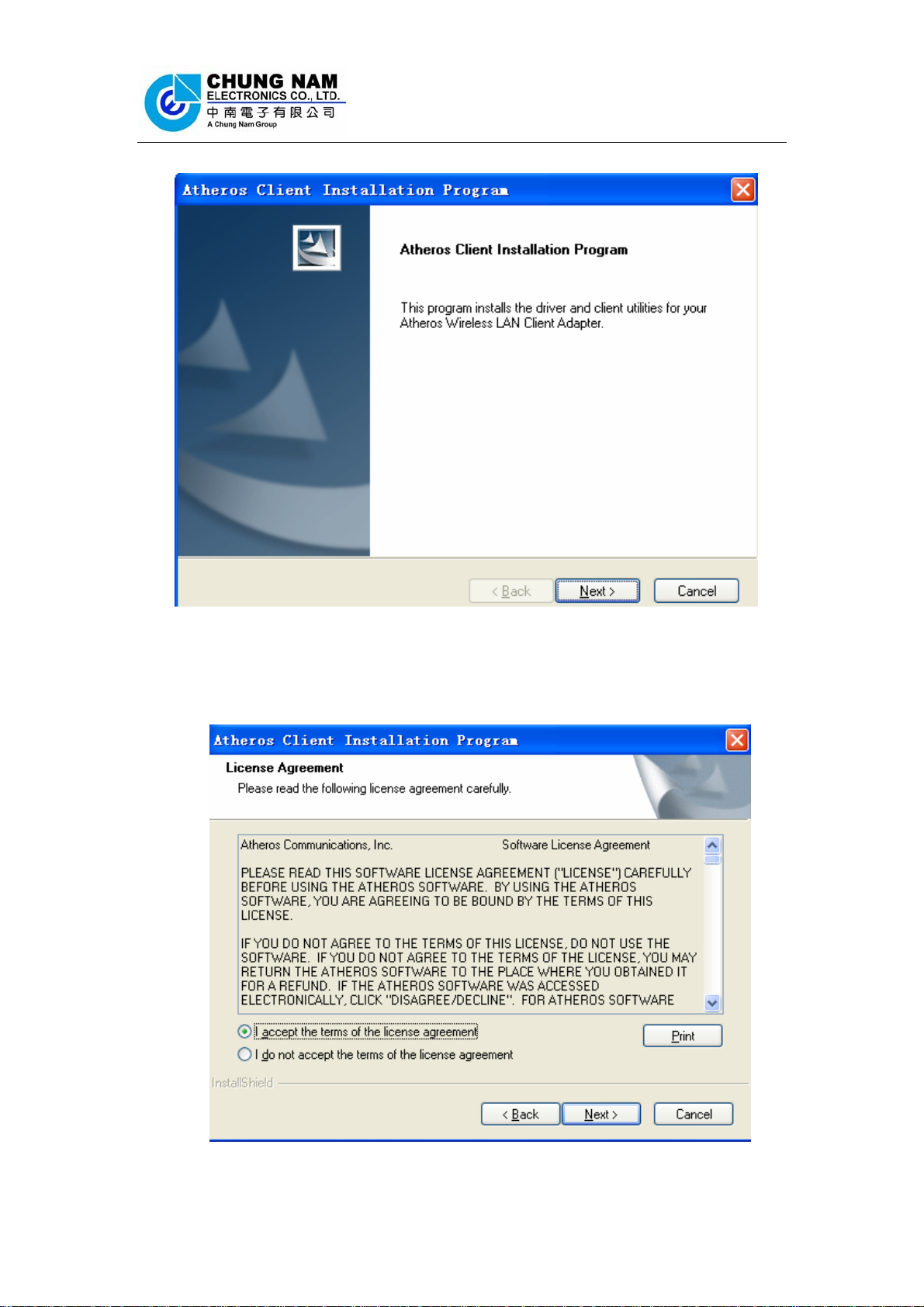
2. Figure 2-2 will appear on the screen, please click ‘Next’
Figure 2-2 Atheros client installation program
3. You will see a license agreement dialog box shown in Figure 2-3, select ‘I accept
the terms of the license agreement’ and click ‘Next’
Figure 2-3 license agreement
- 5 -
Page 6
User Manual
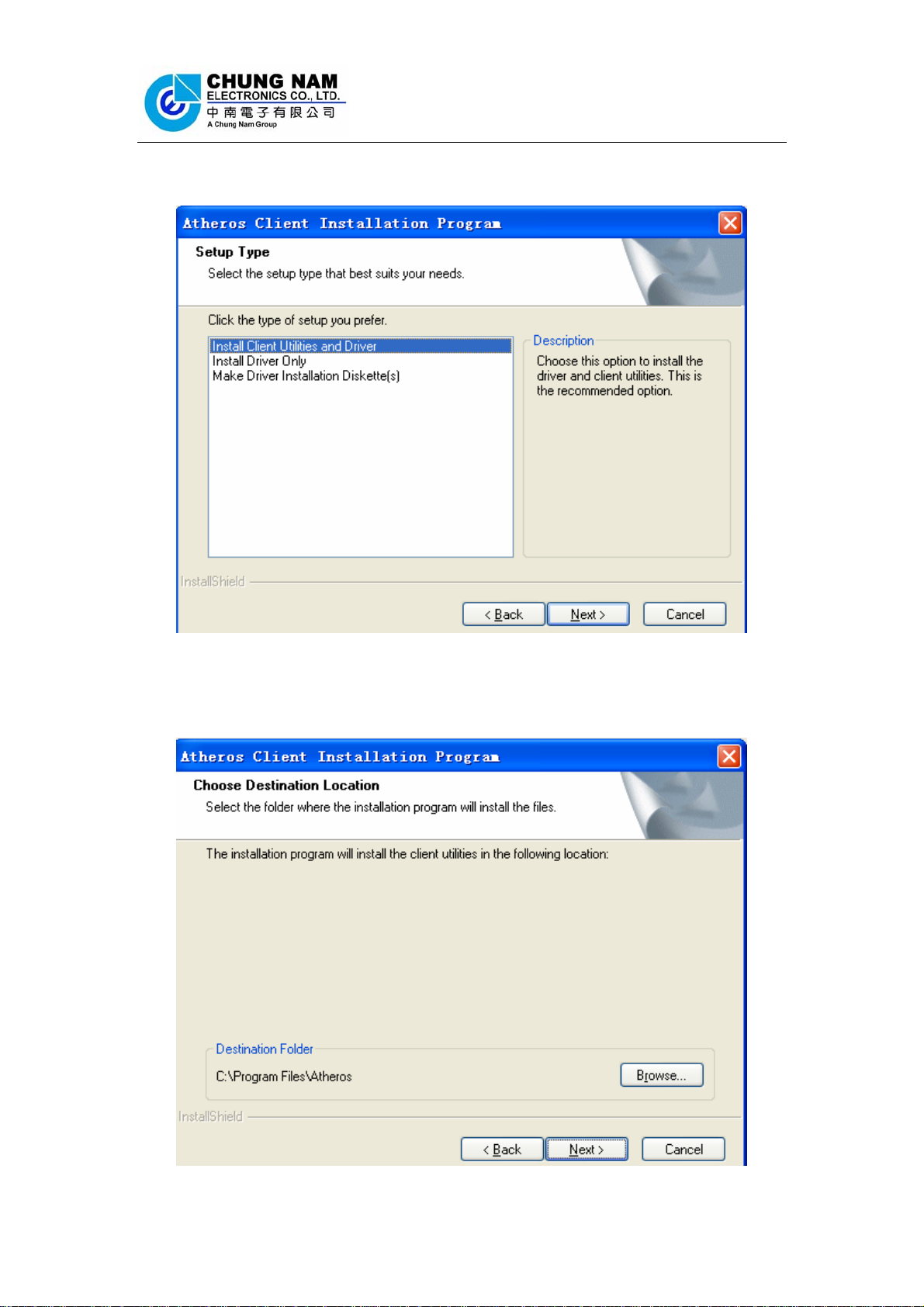
4. Figure 2-4 appears on the screen, please select ‘Install Client Utilities and
Driver’ and click ‘Next’
Figure 2-4 Setup Type
5. Choose the path of installation and select program folder in your PC and click
‘Next’ to continue.
Figure 2-5 choose the path of installation
- 6 -
Page 7
User Manual
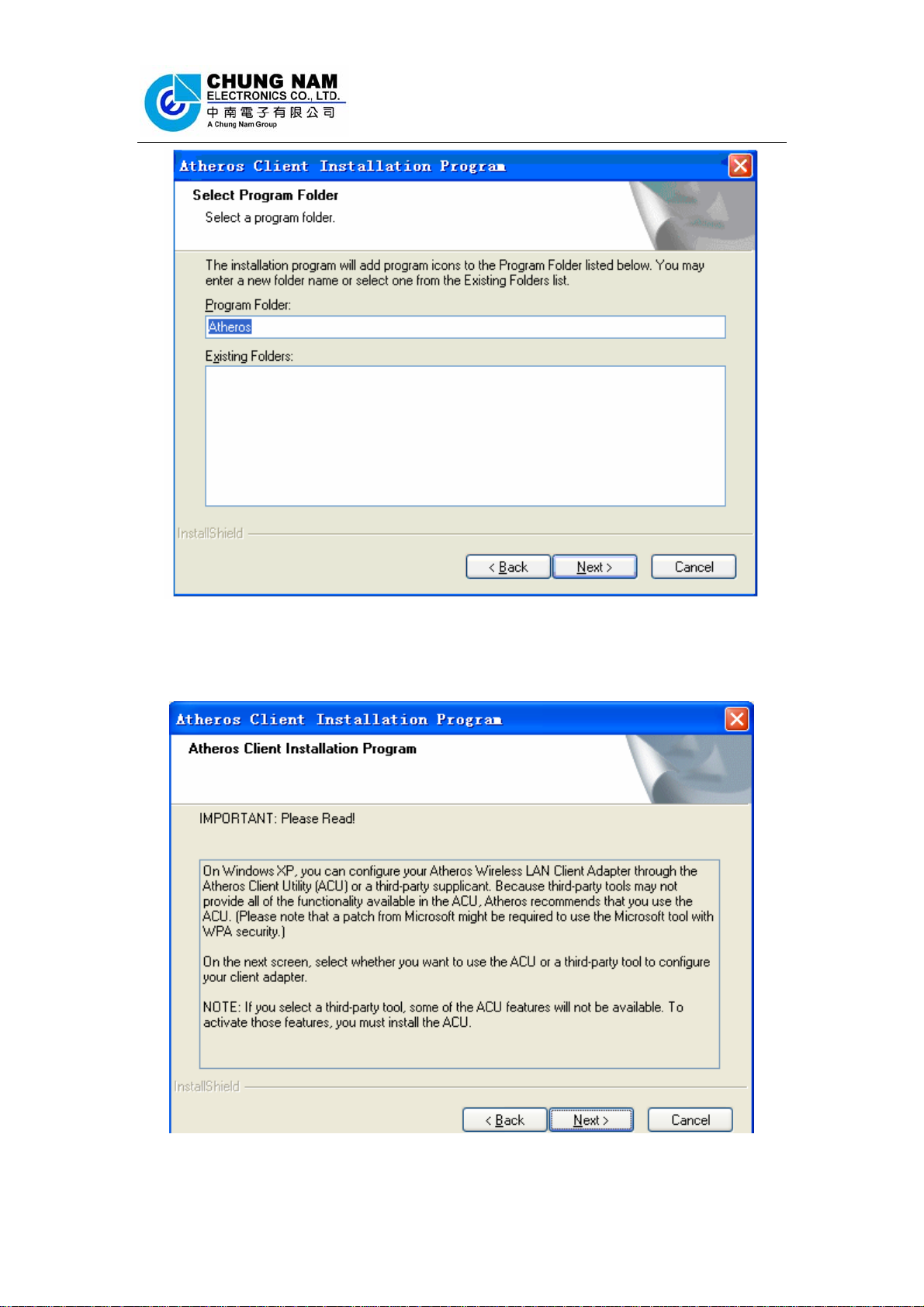
Figure 2-6 select program folder
6. The dialog box as Figure 2-7 will appear, please read it carefully and then click
‘Next’
Figure 2-7 Notice of installation
- 7 -
Page 8

User Manual
7. Please select ‘Atheros Client Utility (ACU) and Supplicant’ in this dialog box as
Figure 2-8 choose configuration and click ‘Next’
Figure 2-8 choose configuration
8. Please select ‘Do Not Install Single Sign On feature set’ as Figure 2-9 single sign
on feature set install option and click ‘Next’
Figure 2-9 single sign on feature set install option
9. A warning box will show in your computer as Figure 2-10, please click OK
- 8 -
Page 9

User Manual
Figure 2-10 install warning
10. Please waiting for running automatically for a moment, after the files have been
successfully installed, the screen in Figure 2-11 will appear. Click the button ‘Finish’
to finish the wizard
Figure 2-11 finish installing
11. After installing the software, please plug the WLAN Adapter into your PC for
hardware installation. In case you want to understand the detail hardware installation
instructions, please refer to next section - Hardware Installation.
- 9 -
Page 10

User Manual
2.2.2 Hardware Installation
If you have been successfully installed the driver, please plugged the USB WLAN
Adapter into your PC. The OS will automatically detect the USB WLAN Adapter and
automatically select the appropriate driver for Adapter. If it does not, please follow
the setup steps to finish the driver installation.
After installing the driver and plugging the WLAN Adapter to the PC successfully,
you should see an icon appearing in your system icon box as shown in Figure
2-12. Now, you can start to enjoy the high speed wireless connectivity with the USB
WLAN Adapter.
Click Here
Figure 2-12 the icon of the adapter
When you want to start to use this WLAN Adapter, please click on the icon in
right-click, and a menu as Figure 2-13 will popup. Please select ‘Open Atheros
Client Utility’ to start configuration program. If you want to close configuration
utility, please click ‘Exit’.
Figure 2-13 the menu of adapter configuration
* Note: If you stopped configuration utility by ‘Exit’ function, you’ll not be able to
maintain the wireless link to the access point you wish to use. In this case, you can
start configuration utility again by clicking: Start -> All Programs ->Atheros ->
Atheros Client Utility
- 10 -
Page 11

User Manual
Chapter 3: Configuration
This section shows you how to configure you the adapter in order to getting
connection to a wireless access point. There are two kinds of ways that you can carry
out configuration:
1) Using the Atheros configuration utility which comes with wireless adapter driver;
2) Using built-in windows zero configuration utility.
3.1 Using Atheros configuration utility
Please follow the following instructions in order to use Atheros configuration utility
to connect to wireless access point.
1. Right-click the icon located at system icon box of desktop and click ‘Open
Atheros Client Utility’, the figure of Atheros configuration utility will show up
as the Figure 3-1.
Figure 3-1 the profile management of Atheros configuration utility
● New : Create a new profile, or Add a profile from an existing wireless access point
or wireless device
● Modify: Modify current setting parameter for SSID
- 11 -
Page 12

User Manual
● Import: Save current Profile
● Export: Export old Profile by set previously
● Scan: Scan different access point
● Order: Profiles-Order for different profiles
2 Please click on the button ‘Scan’, and appear a dialog box as Figure 3-2 of below
Figure 3-2 Available infrastructure and Ad Hoc Networks
● Network Name (SSID): The Service Set IDentifier of wireless access point or
other network device. You can think it as the name of access point of wireless device.
● Signal strength: shows the strength of signal
● Channel: shows transmit signal channel in use
- 12 -
Page 13

User Manual
2. Please select a router and click ‘Activate’ in dialog box of Available infrastructu-
re and Ad Hoc Networks, appear the information as below, and input your definitional
into Figure 3-3 setting of General of Profile Management
Figure 3-3 setting of General of Profile Management
● Profile: Identifies the configuration profile. This name must be unique. Profile
names are not case-sensitive.
● Client Name: default
● SSID1: default
- 13 -
Page 14

User Manual
3. Please click the button ‘Security’ and select ‘Pre-share key (static WEP)’ in
Profile Management as Figure 3-4, and input “xxxxxxxxxxxx” into ‘WEP key’,
and click ‘OK’
Figure 3-4 Configure Pre-shared Keys ( Static WEP)
● Set security option: Please select a wireless authentication type you wish to use.
Available options are ‘WPA/WPA2’, ‘WPA/WPA2 pass phrase’, ‘802.11x’,
‘Pre-shared key (static WEP)’, and ‘None’
● Key Entry : Key #1, Key #2, Key #3, Key #4, the Key groups. You can enter 10
hexadecimal digits (any combination of 0-9, a-f, A-F) or 5 ASCII characters for 64-bit
(also called 40bits)
- 14 -
Page 15

User Manual
3.2 Using Windows Zero Configuration
Windows XP and Vista has a built-in wireless network configuration utility, called as
‘Windows Zero Configuration’ (WZC). You can also use WZC to configure the
wireless network parameter for the adapter
* Note: Before setting your wireless network parameter, please start-up ‘Windows
Zero Configuration’ (WZC)
1. Right-click the icon
of desktop, click ‘Select Client software’ and select ‘Winows’
Figure 3-5 Select way of Windows Zero Configuration
2. Click the button ‘Start’ (should be located at the bottom-left corner of windows
desktop), select ‘Control Panel’ -> ‘Network and Internet Connections’ ->
‘network Connection’
of Atheros configuration utility located at system icon box
3. Right-click ‘Wireless Network Connection’ (it may have a number as suffix if
you have more than one wireless adapter, please make sure you right-click the
‘Ralink 802.11n Wireless LAN Card’, then select ‘View Available Wireless
Networks’.
- 15 -
Page 16

User Manual
Figure 3-6 set wireless Network Connection
5. All wireless access points in proximity will be displayed here. If the access point
you want to use is not displayed here, please try to move your computer closer to the
access point, or you can click ‘Refresh network list’ to rescan access points. Click
the access point you want to use if it’s shown, then click ‘Connect’.
Figure 3-7 Choose a wireless network to connect
6. If the access point is protected by encryption, you have to input its security key or
passphrase here. It must match the encryption setting on the access point. If the access
- 16 -
Page 17

User Manual
point you selected does not use encryption, you’ll not be prompted for security key or
passphrase.
Figure 3-8 setting of security key or passphrase
7. If you can see ‘Connected’ message, the connection between your computer and
wireless access point is successfully established.
Figure 3-9 wireless network been connect
- 17 -
Page 18

User Manual
3.3 Link status
This portion describes the link status of the USB WLAN Adapter. To check the link
status of the adapter, please right-click the icon of Atheros configuration utility
located at your system icon box.
Figure 3-10 Status of the Atheros configuration utility
The Figure 3-10 will show up on the screen and you can find all the link information
(IP Address, Signal Strtength .etc) for the WLAN adapter.
In case you click the button ‘Advance’, the screen will all related information for the
wireless access point that your WLAN adapter connected to.
- 18 -
Page 19

User Manual
Chapter 4: Regulatory information
4.1 FCC Information to User
This product does not contain any user serviceable components. Any product changes
or modifications will invalidate all applicable regulatory certifications and approvals.
4.2 FCC Guidelines for Human Exposure
FCC RF exposure statement: This equipment complies with FCC radiation exposure
limits set forth for an uncontrolled environment. End users must follow the specific
operating instructions for satisfying RF exposure compliance. To maintain compliance
with FCC RF exposure compliance requirements please follow operation instructions
as document in this manual.
This device has been tested for compliance with FCC RF Exposure (SAR) limits in the
typical laptop computer configuration and this device can be used in desktop or laptop
computers with USB slots. Other applications like handheld PDAs (personal digital
assistants) or similar device has not been verified and may not compliance with related
RF exposure rule and such use should be prohibited. This device with its antenna must
not be co-located or operated in conjunction with any other antenna or transmitter.
4.3 FCC Electronic Emission Notices
This device complies with part 15 of the FCC Rules. Operation is subject to the
following two conditions:
1. This device may not cause harmful interference
2. This device must accept any interference received, including interference that may
cause undesired operation.
This equipment has been tested and found to comply with the limits for a class B digital
device, pursuant to part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference in a residential installation.
This equipment generates, uses and can radiate radio frequency energy and, if not
installed and used in accordance with the instructions, may cause harmful interference
to radio communications. However, there is no guarantee that interference will not
occur in a particular installation. If this equipment does cause harmful interference to
radio or television reception, which can be determined by turning the equipment off and
on, the user is encouraged to try to correct the interference by one or more of the
following measures:
---Reorient or relocate the receiving antenna.
- 19 -
Page 20

User Manual
---Increase the separation between the equipment and receiver.
---Connect the equipment into an outlet on a circuit different from that to which the
receiver is connected.
---Consult the dealer or an experienced radio/TV technician for help.
- 20 -
Page 21

User Manual
Chapter 5: Technical Specifications
Appendix A: Specifications
General
Interface A-type USB 2.0 Connector
Standards IEEE802.11b, IEEE802.11g, 802.11n Draft 2.0
Operating System Windows 98SE, ME, 2000, XP, Vista
Transmission Distance
Frequency 2.412GHz ~ 2.462GHz
Sensitivity
Spread Spectrum Direct Sequence Spread Spectrum (DSSS)
Radio Data Rate
Modulation
Media Access Protocol CSMA/CA with ACK
Data Security
In door up to 100m, out door up to 300m
(Actual performance depends on environment).
54Mbps -65dBm (Typical)
MSC7 HT20 -64dBm(Typical)
MSC7 HT40 -61dBm(Typical)
Wireless
54/48/36/24/18/12/9/6 Mbps 11g OFDM,
11/5.5/2/1 Mbps 11b DSSS
802.11b: CCK, QPSK, BPSK
802.11g: OFDM
Draft-11n: DBPSK, DQPSK, 16-QAM, 64-QAM
64/128 bit WEP, TKIP/AES,
IEEE 802.1X authentication
Physical Environmental
Working Temperatur e 0ºC~40ºC (32ºF~104ºF)
Storage Temperatur e -40ºC~70ºC (-40ºF~158ºF)
Humidity 10%~90% RH, Non-condensing
- 21 -
Page 22

User Manual
Appendix B: Glossary
* 802.11b - The 802.11b standard specifies a wireless product networking at 11 Mbps
using direct-sequence spread-spectrum (DSSS) technology and operating in the
unlicensed radio spectrum at 2.4GHz, and WEP encryption for security. 802.11b
networks are also referred to as Wi-Fi networks.
* 802.11g - specification for wireless networking at 54 Mbps using direct-sequence
spread-spectrum (DSSS) technology, using OFDM modulation and operating in the
unlicensed radio spectrum at 2.4GHz, and backward compatibility with IEEE 802.11b
devices, and WEP encryption for security.
* Ad-hoc Network - An ad-hoc network is a group of computers, each with a wireless
adapter, connected as an independent 802.11 wireless LAN. Ad-hoc wireless
computers operate on a peer-to-peer basis, communicating directly with each other
without the use of an access point. Ad-hoc mode is also referred to as an
Independent Basic Service Set (IBSS) or as peer-to-peer mode, and is useful at a
departmental scale or SOHO operation.
* DSSS (Direct-Sequence Spread Spectrum) - DSSS generates a redundant bit
pattern for all data transmitted. This bit pattern is called a chip (or chipping code).
Even if one or more bits in the chip are damaged during transmission, statistical
techniques embedded in the receiver can recover the original data without the need
for retransmission. To an unintended receiver, DSSS appears as low power
wideband noise and is rejected (ignored) by most narrowband receivers. However, to
an intended receiver (i.e. another wireless LAN endpoint), the DSSS signal is
recognized as the only valid signal, and interference is inherently rejected (ignored).
* FHSS (Frequency Hopping Spread Spectrum) - FHSS continuously changes (hops)
the
carrier frequency of a conventional carrier several times per second according to a
pseudo-random set of channels. Because a fixed frequency is not used, and only the
transmitter and receiver know the hop patterns, interception of FHSS is extremely
difficult.
* Infrastructure Network - An infrastructure network is a group of computers or other
devices, each with a wireless adapter, connected as an 802.11 wireless LAN. In
infrastructure mode, the wireless devices communicate with each other and to a
wired network by first going through an access point. An infrastructure wireless
network connected to a wired network is referred to as a Basic Service Set (BSS). A
set of two or more BSS in a single network is referred to as an Extended Service Set
(ESS). Infrastructure mode is useful at a corporation scale, or when it is necessary to
connect the wired and wireless networks.
* Spread Spectrum - Spread Spectrum technology is a wideband radio frequency
technique developed by the military for use in reliable, secure, mission-critical
communications systems. It is designed to trade off bandwidth efficiency for reliability,
integrity, and security. In other words, more bandwidth is consumed than in the case
- 22 -
Page 23

User Manual
of narrowband transmission, but the trade off produces a signal that is, in effect,
louder and thus easier to detect, provided that the receiver knows the parameters of
the spread-spectrum signal being broadcast. If a receiver is not tuned to the right
frequency, a spread-spectrum signal looks like background noise. There are two
main alternatives, Direct Sequence Spread Spectrum (DSSS) and Frequency
Hopping Spread Spectrum (FHSS).
* SSID - A Service Set Identification is a thirty-two character (maximum) alphanumeric
key identifying a wireless local area network. For the wireless devices in a network to
communicate with each other, all devices must be configured with the same SSID.
This is typically the configuration parameter for a wireless PC card. It corresponds to
the ESSID in the wireless Access Point and to the wireless network name.
* WEP (Wired Equivalent Privacy) - A data privacy mechanism based on a 64-bit or
128-bit or 152-bit shared key algorithm, as described in the IEEE 802.11 standard.
* Wi-Fi - A trade name for the 802.11b wireless networking standard, given by the
Wireless Ethernet Compatibility Alliance (WECA, see http://www.wi-fi.net), an
industry standards group promoting interoperability among 802.11b devices.
* WLAN (Wireless Local Area Network) - A group of computers and
associated devices communicate with each other wirelessly, which
network serving users are limited in a local area.
* WPA (Wi-Fi Protected Access) - A wireless security protocol use TKIP (Temporal Key
Integrity Protocol) encryption, which can be used in conjunction with a RADIUS server.
THE END
- 23 -
 Loading...
Loading...