Check Point InterSpect 210, InterSpect 410, InterSpect 210N, InterSpect 610, InterSpect 610F Datasheet

InterSpect
Internal intrusion prevention and
network access control
YOUR CHALLENGE
To date, IT security organizations have focused on the network perimeter.
However, many of today’s attacks are introduced from inside the network.
Laptops, PDAs, and other devices travel into and out of the network daily,
making it possible for legitimate users to infect the network or unwittingly grant
attackers access to the network via a Trojan horse or other spyware.
Many worms have propagated inside the network after being introduced by
an internal source. Once a single network device has been infected, the entire
network can be compromised very quickly, resulting in costs related to system
downtime, lost productivity, and clean up and recovery of IT systems. With such
costly threats becoming increasingly common, organizations have come to
realize that they must improve their internal security controls to provide better
defenses against worms, unauthorized access threats, and other attacks within
their internal networks.
OUR SOLUTION
Check Point InterSpect™ is an internal security gateway that blocks attacks
such as worms, denial of service (DOS), and email-borne malware that are introduced inside the network. InterSpect combines intelligent intrusion prevention,
network zone segmentation, and host quarantine capabilities built specifically
for unique internal network requirements to deliver the most comprehensive
internal security solution available. Specifically, InterSpect provides:
• Intelligent intrusion prevention—proactive protection against today’s evolving
threats, including worms and Day Zero attacks
Data Sheet
The NGX platform delivers a unified
security architecture for Check Point
perimeter, internal, and Web security.
PRODUCT DESCRIPTION
InterSpect™ combines intrusion
prevention, network zone
segmentation, and network access
control built specifically for the unique
requirements of internal networks.
PRODUCT FEATURES
■
Intrusion prevention
■
Network zone segmentation
■
Quarantine of suspicious computers
■
LAN protocol protection
■
Integrated Web application security
■
Endpoint security integration
PRODUCT BENEFITS
■
Proactively protects against internal
worms and Day Zero attacks
■
Creates internal network segments,
each with its own security policy
■
Provides the most comprehensive
protection for LAN protocols
■
Enforces PC network access policy
and quarantines rogue endpoints
■
Protects against new threats through
SmartDefense™ Services
• Network zone segmentation—segmentation of the internal network into
organizational security zones, each with its own security policy
• Quarantining of suspicious computers—prevention of unsecured computers
from accessing the network
• LAN protocol protection—the deepest and most comprehensive support for
Microsoft, Citrix ICA, and other LAN protocols
InterSpect is designed for flexible and nondisruptive deployment into existing
network environments.
NGX HIGHLIGHTS
■
SmartCenter™ and Provider-1®
centralized management integration
Check Point protects every part of your
network—perimeter, internal, Web—
to keep your information resources safe,
accessible, and easy to manage.
1

InterSpect
• Integrated Web application security—protection of Web
servers from common exploits such as SQL injection,
command injection, and buffer overflows
• Endpoint security integration—security policy enforcement
for endpoints accessing the network
• Integrated SMART management—scalable and easy to
use, this ensures security policy is always up-to-date
InterSpect is supported by SmartDefense™ Services, which
maintain the most current preemptive security for the Check
Point security infrastructure. To help you stay ahead of
new threats and attacks, SmartDefense Services provide
real-time updates and configuration advisories for defenses
and security policies.
FEATURES
Intelligent intrusion prevention
InterSpect provides proactive protection against today’s
evolving threats, such as worms, DOS attacks, and emailborne malware, including proactive protection against
Day Zero attacks. InterSpect is equipped with a version of
SmartDefense customized for internal network security that
allows administrators to configure, enforce, and update
all network and application attack defenses. All defenses
can be configured to run in “monitor-only” mode to enable
administrators to fine-tune policies without interrupting
network services. InterSpect intrusion prevention capabilities
are based on INSPECT, the industry’s most intelligent and
adaptive security inspection technology, and is backed by
SmartDefense Services, a security research and response
service that provides ongoing and real-time updates and
advisories for defenses and security policies.
Network zone segmentation
The application segments the network into multiple administrator-defined security zones to prevent unauthorized
access between zones. This prevents users or compromised
computers on the network from accessing information and
systems that they are not authorized to view. Network
zone segmentation also contains attacks within a subsegment of the network. Administrators can also create different
security policy profiles for each zone—including virtual
zones—enabling fine-grained and tailored security policies
to be deployed to different segments of the network with
minimal administrative effort.
Quarantine
InterSpect can identify suspicious or infected computers on
the network and quarantine them, preventing the rest of the
network from being compromised. It has multiple options
for quarantining, enabling administrators to isolate infected
hosts to a security zone or switch port and also allows administrators to quarantine specific hosts by MAC address. It is
useful to quarantine clients or servers during security patch
deployment and helps ease the risk of infection while network
administrators identify, install, and test patches. InterSpect
provides user notification to hosts that have been quarantined via a customized dynamic Web page. This notification
helps to minimize the time spent troubleshooting the issue at
the helpdesk and also allows the network administrator to be
made aware of the issue, reducing user downtime.
LAN protocol protection
For LAN security, InterSpect provides the deepest and
most comprehensive protection for Microsoft protocols
like CIFS, DCOM, MS RPC, and MS SQL, as well as other
LAN protocols such as Citrix ICA, DCE RPC, HTTP, and
Sun RPC. In the case of Citrix ICA, InterSpect can secure
individual Citrix servers, protect specific Citrix services, block
unauthorized applications running over Citrix, and prevent
protocol violations. By taking advantage of updates available via SmartDefense Services, InterSpect users can keep
their internal LAN security infrastructure up-to-date as new
attacks and threats emerge.
Integrated Web application security
InterSpect also features integrated Web application security
through Web Intelligence™, a set of advanced capabilities
2
InterSpect includes SmartDefense for internal networks,
providing preemptive protection for known and unknown
attacks inside the network.
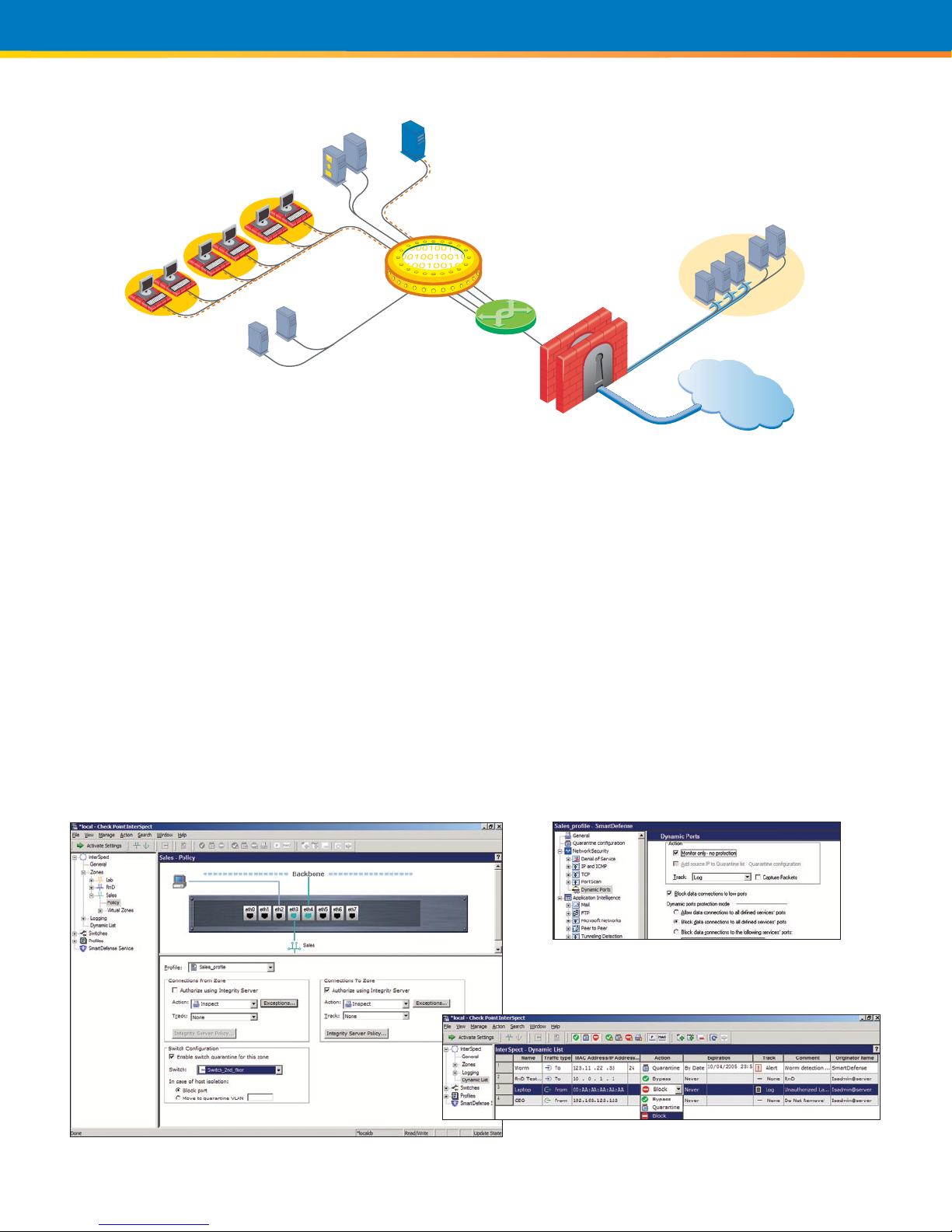
Internet
DMZ
VPN-
1
Integrity
Check Point
InterSpect
Authentication
Server
Integrity Server
Internal Application
Server
s
Switc
h
HR
Manufacturing
Finance
Web Server Poo
l
Extranet Application
Server
s
Integrity
Corporate Network
InterSpect is the only solution specifically designed for internal security. It
can provide security on the network backbone and per network segment.
Internal intrusion prevention and network access control
that detects and prevents attacks against the Web infrastructure. It provides comprehensive protection for Web servers
against common Web application exploits like buffer overflows, command injection, and SQL injection. This includes
Check Point’s patent-pending Malicious Code Protector™,
which offers a revolutionary way of identifying buffer overflow,
heap overflows, and other malicious executable code attacks
that target Web servers and other applications without relying
on signature-based detection.
Endpoint security integration
InterSpect integrates with Check Point Integrity™ to provide
Cooperative Enforcement® of network and endpoint security
policies. This ensures that only compliant users can access
network resources while noncompliant users and nodes
will be quarantined and notified appropriately. Integrity
combined with InterSpect provides a critical component of
Check Point’s Total Access Protection framework, securing
both desktop and laptop PCs that connect to the corporate
network, as well as the network itself.
Unified security management
Under the NGX platform, InterSpect can now be managed
from the same console and server and by the same
administrators that manage other Check Point products
using the SmartCenter™ and Provider-1®/SiteManager-1™
unified management platforms. This includes the Security
Management Architecture (SMART) solutions and the VPN-1®
line of gateways.
From the same console, administrators can manage all
their Check Point gateways and also deploy SmartDefense
updates to multiple devices simultaneously with a single
operation, thereby reducing administrative burden and errors.
PERFORMANCE
InterSpect is an appliance that has been designed to meet
the performance demands of internal security. It is based
on SecurePlatform™, Check Point’s hardened-security
operating system. To ensure the highest level of performance,
InterSpect also includes Check Point’s patented SecureXL™
security acceleration technology.
Monitor-only mode logs attacks without interrupting
connectivity and Web Intelligence and SmartDefense
operate as an intrusion detection device.
InterSpect is managed by SmartCenter, allowing integrated
management, logging, and monitoring. InterSpect quarantines
down to the switch-port level.
3

DEPLOYMENT MODES
To support various deployments, InterSpect can work in three inline operating modes (bridge, switch, and router mode). Monitor-only
capability can be used with all modes.
Description Primary deployment scenarios
Bridge mode
InterSpect bridges one or more segments to the backbone
and is invisible to the IP network
Switch mode
InterSpect acts as a multiport bridge in which all ports are
bridged together to make one zone
Router mode
InterSpect acts as a router, and every active port is configured
with a different IP address
Monitor-only capability
InterSpect inspects traffic without enforcing safeguards and
defenses (can be used with bridge, switch, or router modes)
Transparent deployment of segmentation, worm defense,
and quarantine
Transparent deployment of worm defense and quarantine
when full segmentation is not required
Sophisticated network-zone segmentation for multiple
security zones
Pilot deployments to understand InterSpect’s effect on legacy
applications prior to active, inline deployment
SPECIFICATIONS
Target One workgroup protection Multiple workgroup protection Gigabit network protection
Operating environment Check Point SecurePlatform Check Point SecurePlatform Check Point SecurePlatform
Throughput 200 Mbps 500 Mbps 1,000 Mbps
Fiber interfaces N/A Add-on available
Expansion slots N/A 1 1
Inspection ports 2 3-10 3-14
Management port 1 1 1
Maximum ports 3 Copper: 10 or Fiber: 8 Copper: 14 or Fiber: 8
Failover NIC (FON) N/A
Interface speed 10/100/1,000 Mbps 10/100/1,000 Mbps 10/100/1,000 Mbps
VLAN support 8 VLANs 128 VLANs Unlimited VLANs
SmartDefense Services Included for one year Included for one year Included for one year
Width 16.7 in./42.5 cm 17.61 in./44.7 cm 17.61 in./44.7 cm
Height 1.68 in./4.2 cm (1U) 1.68 in./4.2 cm (1U) 1.68 in./4.2 cm (1U)
Depth 21.9 in./55.5 cm 27 in./68.3 cm 27 in./68.3 cm
Weight 27 lbs./12.25 kg 35 lbs./15.9 kg 35 lbs./15.9 kg
Power 100-220 volts 50/60 Hz 100-220 volts 50/60 Hz 100-220 volts 50/60 Hz
InterSpect 210/210N InterSpect 410 InterSpect 610/610F
Add-on available
(included on 610F)
Integrated
(copper)
Add-on available
(copper or fiber)
Add-on available
(copper or fiber)
©2003-2006 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application Intelligence, Check Point Express, Check Point Express CI, the Check Point logo, AlertAdvisor,
ClusterXL, ConnectControl, Connectra, Connectra Accelerator Card, Cooperative Enforcement, Cooperative Security Alliance, CoSa, DefenseNet, Eventia, Eventia Analyzer, Eventia Reporter,
FireWall-1, FireWall-1 GX, FireWall-1 SecureServer, FloodGate-1, Hacker ID, IMsecure, INSPECT, INSPECT XL, Integrity, Integrity SecureClient, Integrity Clientless Security, InterSpect, IQ Engine,
NG, NGX, Open Security Extension, OPSEC, OSFirewall, Policy Lifecycle Management, Provider-1, Safe@Office, SecureClient, SecureKnowledge, SecuRemote, SecurePlatform, SecurePlatform
Pro, SecureServer, SecureUpdate, SecureXL, SecureXL Turbocard, SiteManager-1, SmartCenter, SmartCenter Express, SmartCenter Power, SmartCenter Pro, SmartCenter UTM, SmartConsole,
SmartDashboard, SmartDefense, SmartDefense Advisor, Smarter Security, SmartLSM, SmartMap, SmartPortal, SmartUpdate, SmartView, SmartView Monitor, SmartView Reporter, SmartView
Status, SmartViewTracker, SofaWare, SSL Network Extender, Stateful Clustering, TrueVector, Turbocard, UAM, UserAuthority, User-to-Address Mapping, VPN-1, VPN-1 Accelerator Card,
VPN-1 Edge, VPN-1 Express, VPN-1 Express CI, VPN-1 Power, VPN-1 Power VSX, VPN-1 Pro, VPN-1 SecureClient, VPN-1 SecuRemote, VPN-1 SecureServer, VPN-1 UTM, VPN-1
UTM Edge, VPN-1 VSX, Web Intelligence, ZoneAlarm, ZoneAlarm Anti-Spyware, ZoneAlarm Antivirus, ZoneAlarm Internet Security Suite, ZoneAlarm Pro, Zone Labs, and the Zone
Labs logo are trademarks or registered trademarks of Check Point Software Technologies Ltd. or its affiliates. All other product names mentioned herein are trademarks or
registered trademarks of their respective owners. The products described in this document are protected by U.S. Patent No. 5,606,668, 5,835,726, 6,496,935, 6,873,988,
and 6,850,943 and may be protected by other U.S. Patents, foreign patents, or pending applications.
September 26, 2006 P/N 502272
Worldwide Headquarters
3A Jabotinsky Street, 24th Floor
Ramat Gan 52520, Israel
Tel: 972-3-753-4555
Fax: 972-3-575-9256
Email: info@checkpoint.com
4
U.S. Headquarters
800 Bridge Parkway
Redwood City, CA 94065
Tel: 800-429-4391; 650-628-2000
Fax: 650-654-4233
www.checkpoint.com
 Loading...
Loading...