Canon imageRUNNER ADVANCE, imageRUNNER ADVANCE DX, imagePRESS Lite systems User Manual

White Paper: Canon imageRUNNER ADVANCE / imageRUNNER ADVANCE DX / imagePRESS Lite Security
INTENT OF THIS DOCUMENT:
Canon recognizes the importance of information security and the challenges that your organization faces.
This white paper provides information security facts for Canon imageRUNNER ADVANCE /
imageRUNNER ADVANCE DX / imagePRESS Lite systems (hereafter called imageRUNNER ADVANCE).
It provides details on imageRUNNER ADVANCE security technology for networked and stand-alone
environments, as well as an overview of Canon’s device architecture, framework and product technologies
as related to document and information security.
This White Paper is primarily intended for the administrative personnel of a customer charged with
responsibility for the configuration and maintenance of imageRUNNER ADVANCE systems. The
information in this document may be used to more clearly understand the many imageRUNNER ADVANCE
security-related configuration capabilities offered by Canon. The imageRUNNER ADVANCE system offers
a number of standard and optional capabilities that, when used by a customer, can help facilitate effective
management and security of data processed and stored by the system. Ultimately, it is the customer’s
responsibility to select the method(s) most appropriate for securing their information.
Canon does not warrant that use of the information contained within this document will prevent malicious
attacks, or prevent misuse of your imageRUNNER ADVANCE systems.
Products shown with optional accessories/equipment. The features reviewed in this white paper include both standard and optional
solutions for imageRUNNER ADVANCE systems. Specifications and availability subject to change without notice.
Version 3.10.5
June 2020

2
Table of Contents
1. Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
2. Device Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
3. Information Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
4. Network Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
5. Security Monitoring & Management . . . . . . . . . . . . . . . . . . . . 34
6. Logging & Auditing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
7. Canon Solutions & Regulatory Requirements . . . . . . . . . . . . 40
8. Conclusion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
9. Addendum . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
3
Section 1 — Introduction
Security Market Overview
In today’s digital world, risks to networks and devices come in more forms and from more directions than
ever before. From identity theft and intellectual property loss to infection by viruses and Trojan horses, IT
administrators today find themselves playing an additional role of security officer to adequately protect
information and assets from threats from the outside as well as within.
Nearly every day destructive threats emerge and undiscovered vulnerabilities are exposed, proving that you
can never be too secure. IT administrators need a holistic security strategy that can be applied at every level
of the organization — from servers, desktops and devices such as MFPs, to the networks that connect them
all.
As if the risks to computers, networks and devices weren’t difficult enough to address, increased
governmental regulations add an additional layer of strict compliance standards that must be met.
Legislation such as Sarbanes-Oxley Act (SOX), Gramm-Leach-Bliley Act (GLB), Health Insurance
Portability and Accountability Act (HIPAA), Family Education Rights Privacy Act (FERPA) and
Homeland Security Presidential Directive (HSPD)-12 all require that IT administrators ensure the security,
privacy, accuracy and reliability of information receives the utmost attention.
Imaging & Printing Security Overview
Any networked Multifunction Printer is potentially at risk of being attacked through the network. For this
reason, MFPs require security measures just like PCs. Techniques of malicious adversaries evolve every
day, and it is required not only to take actions against existing attack methods but also to provide a multilayered defense with multiple proactive protection methods. Furthermore, because an MFP is also a
document handling device, in addition to IT device security measures, document-specific security measures
such as preventing printout take-away, is also required.
The Canon imageRUNNER ADVANCE Security White Paper has been designed to provide detailed
information on how imageRUNNER ADVANCE systems can address a wide variety of security concerns.
Canon imageRUNNER ADVANCE systems offer many standard security capabilities, as well as a number
of advanced security options that may be added for a higher level of confidentiality, integrity and
availability of your mission critical information.
Canon continues to take information security measures to gain customer's trust, and be proactive in
acquiring and maintaining third-party accreditation.
Key Security Concentration Areas
Canon recognizes the vital need to help prevent data loss, protect against unwanted device use, and mitigate
the risk of information being compromised. As a result, all imageRUNNER ADVANCE systems include
many standard security features to help safeguard information. Canon imageRUNNER ADVANCE
security capabilities fall into five key areas:
Device Security
Information Security
Network Security
Security Monitoring / Management Tools
Logging & Auditing
NOTE: Please refer to Table 9.2 in Addendum for the Security Features Table illustrating Device
compatibility, and where a feature is standard or optional on the device.

4
Canon dedicates a significant amount of time and resources to continually improve the
security capabilities of its imageRUNNER ADVANCE devices. Numerous robust
capabilities are available for administrators to restrict access to the device’s features and
functions at a granular level, while maintaining high availability and productivity.
Note:
Depending on the model, some features are within the standard feature set of the device, while others
require additional accessories. Document Scan Lock and Tracking***, Encrypted Secure Print, Secure
Watermark Encrypted PDF**, Fax, Control Card System, Removable HDD***, HDD Data Erase
Scheduler, and IEEE2600 Common Criteria Certification are available as options. IEEE2600 Common
Criteria Certification may not be available at time of launch. Check the price list for availability.
*Only available with 3rd edition models and imageRUNNER ADVANCE DX models. McAfee
Embedded Control requires Unified Firmware Platform v3.9 or later
**Standard with DX models, 3rd edition and 2nd edition models. Optional with 1st edition models.
***Not available on imageRUNNER ADVANCE DX models.
****Standard with DX models. Available on 3rd edition, 2nd edition and 1st edition models with Unified
Firmware Platform V3.10.
†There is no Removable HDD Kit option for DX models, but DX models (excluding C3700 Series) can
have their HDD removed. When the connector reaches its service life, it must be purchased and replaced
by a service technician.

5
Section 2 — Device Security
imageRUNNER ADVANCE Controller Security
The imageRUNNER ADVANCE series is built upon a platform that provides powerful enhancements to security
and productivity. The architecture centers on an operating system powered by an embedded version of Linux,
which is quickly becoming the most widely adopted platform for sophisticated devices. The source version used by
imageRUNNER ADVANCE devices has been hardened by removing all unnecessary drivers and services so that
only the ones essential to its operation are included.
The nature of embedded Linux and the hardening of the operating system drastically reduce the exposure to
exploits as compared to a desktop or server version of a Linux or Windows operating system. Canon strives to
develop products that meet or exceed our customer’s security requirements. Some of the security related activities
include independent testing by security consulting companies of Canon imageRUNNER ADVANCE devices
during various phases of the development process to flush out any potential vulnerability prior to production. Also,
Canon has collaborated with industry initiatives, such as the development of the IEEE 2600 CC Certification
standards for hardcopy device and system security.
Authentication
Canon imageRUNNER ADVANCE systems include a number of authentication options which administrators can
use to ensure that only approved walk-up and network-based users can access the device and its functions, such as
print, copy and Scan and Send features. Beyond limiting access to only authorized users, authentication also
provides the ability to control usage of color output, and total print counts by department or user.
Device-Based Authentication
Universal Login Manager
ULM (Universal Login Manager) is a server-less login application for imageRUNNER ADVANCE
devices (standard on third generation imageRUNNER ADVANCE, imageRUNNER ADVANCE DX and
imagePRESS Lite), which provides an easy and convenient solution for user authentication. Ideal for small
to medium size businesses, ULM’s simple user authentication includes card log-in (requires an additional
option), PIN code, or user name and password, using local or Active Directory (AD), with minimal IT
requirements. Utilizing AMS (Access Management System), found on all imageRUNNER ADVANCE
devices, ULM allows comprehensive control of access on a per-user basis. In addition, ULM delivers
simplified tracking, allowing organizations to obtain a simple overview of user or device usage activity.
User Authentication (UA)
The User Authentication (UA) is new MEAP login service which is available on the imageRUNNER
ADVANCE C3300 Series, third generation imageRUNNER ADVANCE, imageRUNNER ADVANCE DX
and imagePRESS Lite models. User Authentication combines the SSO-H and Department ID functions
available on other imageRUNNER ADVANCE Models. UA can manage up to 5,000 user accounts within
1,000 department codes
Department ID Mode
An embedded feature within imageRUNNER ADVANCE systems, the Department ID Management mode permits
administrators to control device access. If Department ID authentication is enabled, end users are required to enter
a four digit password before they are able to access the device. Up to 1,000 Department IDs can be configured and
each can be configured with device function limitations, such as limiting, printing, copying and access to Advance
Boxes, Mail Boxes and facsimile.
Access to Advanced Boxes, Mail Boxes, and Scan and Send (if applicable) can each be turned “On” or “Off” from
the Limit Functions screen located under Department ID Management.
The settings can be made under Settings / Registration >Management Settings > User Management >
Department ID Management

6
Single Sign-OnHybrid (SSO-H) Login
Single Sign-On Hybrid (SSO-H) is a Multifunctional Embedded Application Platform (MEAP) login service that
can be used stand-alone with user data registered locally on the device or in conjunction with an Active Directory
(AD) network environment. SSO-H supports the following modes:
Local Device Authentication – with credentials stored in the device
Domain Authentication – in this mode, user authentication can be linked to an Active Directory
environment on the network
Domain Authentication + Local Device Authentication
When used in Domain Authentication mode, a user must successfully authenticate using valid credentials on the
system’s control panel, Remote UI utility, or web browser when accessed via a network prior to gaining access to
any of the device functions.
SSO-H ships standard with MEAP capable imageRUNNER ADVANCE systems※ and can support up to 200
trusted domains plus the users that belong to the same domain as the device. Canon imageRUNNER ADVANCE
systems also ship with SSO-H, which supports direct authentication against an Active Directory domain using
Kerberos or NTLMv2 as the authentication protocol. SSO-H does not require any additional software to perform
the user authentication as it is able to directly communicate with the Active Directory domain controllers. In Local
Device Authentication mode, SSO-H can support up to 5,000 users. For a combined use of Domain Authentication
and Local Device Authentication, an LDAP server can be configured instead of Domain Authentication.
※This feature is not pre-packaged on third generation imageRUNNER ADVANCE models, imageRUNNER ADVANCE DX and imagePRESS Lite.
Card-Based Authentication
uniFLOW Card Authentication
When combined with the optional uniFLOW, imageRUNNER ADVANCE systems are able to securely
authenticate users through contactless cards, chip cards, magnetic cards and PIN codes. uniFLOW supports
HID Prox, MIFARE, Legic, Hitag and Magnetic cards natively using its own reader, as well as others
through custom integrations. Certain models of RF Ideas Card Readers can also be integrated to support
authentication using radio-frequency identification (RFID) cards.
Advanced Authentication—Common Access Card (CAC)/Personal Identity Verification (PIV) Card
Federal agencies—both civilian and military (DoD)—require enhanced user authentication, data security,
and information assurance to help comply with the requirements of the Homeland Security Presidential
Directive 12 (HSPD-12). Employees must verify their identity and security classifications using secure and
reliable forms of identification, such as Common Access Card (CAC) and Personal Identity Verification
(PIV). And with networked multifunction printers (MFPs) being deployed on a greater scale in these
locations, Canon developed Advanced Authentication CAC/PIV—an easy-to-use, two-factor embedded
authentication solution to lock and unlock Canon devices. This serverless solution ensures that all device
functions are locked down until users insert their government-issued Common Access Card/Personal
Identity Verification into the card reader and enter their PIN. Only those authenticated individuals are
granted access to the device. This also supports FIPS 140-2 validated cryptography and integrates with
AMS for device feature access control.
Authorized Send Common Access Card (CAC)/Personal Identity Verification (PIV) Card
To fulfill the strict security requirements of government agencies as dictated by Homeland Security
Presidential Directive-12 (HSPD-12), imageRUNNER ADVANCE systems support the use of Common
Access Card (CAC) and/or Personal Identity Verification (PIV) card authentication for the embedded
Authorized Send MEAP application. Authorized Send for CAC/PIV is a server-less application that
protects the Scan-to-Email, Scan-to-Network Folder and Scan-to-Network Fax functions, while allowing
general use of walk-up operations like print and copy. This also integrates with AMS for granular access
control of ASEND functionality.
Authorized Send for CAC/PIV supports two-factor authentication by prompting users to insert their card
into the device’s card reader and requiring them to enter their PIN. ASEND for CAC/PIV supports the
Online Certificate Status Protocol (OCSP) to check the revocation status of the user’s card, and then

7
authenticates the user against the Public Key Infrastructure (PKI) and Active Directory. Once
authenticated, users can access the document distribution features of Authorized Send.
Authorized Send for CAC/PIV supports enhanced e-mail security features such as non-repudiation, digital
signing of e-mail, and encryption of e-mail and file attachments. The cryptographic engine used by
Authorized Send for CAC/PIV has undergone the stringent testing and validation requirements of the FIPS
140-2 standard.
Control Cards/Card Reader System
Canon imageRUNNER ADVANCE systems offer support for an optional Control Card/Card Reader
system for device access and to manage usage. The Control Card/Card Reader system option requires the
use of intelligent cards that must be inserted in the system before granting access to functions, which
automates the process of Department ID authentication. The optional Control Card/Card Reader system
manages populations of up to 1,000 departments or users.
Access Control
Canon imageRUNNER ADVANCE systems support a number of access control options to help you
manage the use of device settings and functions in addition to specific capabilities of certain functions.
Canon offers solutions that can lock down the entire device, or simply lock down specific functions (e.g.
Send-to-Email), while leaving other applications available for general use. With the power and flexibility
of MEAP, some solutions can be customized to meet your specific requirements.
Access Management System
The Access Management System, which is standard on imageRUNNER ADVANCE systems, can be used
to tightly control access to device functionality. Restrictions can be assigned to users and groups, to restrict
entire functions or restrict specific features within a function. Access restrictions are managed in units
called “roles”. Roles contain information that determines which of the various functions of the device may
be used or not.
Roles can be set up based on individual user’s job title or responsibilities or by group, enabling the
administrator to create roles specific to certain departments or workgroups. Since the administrator is not
limited to restricting all or none of a particular function, the roles can be as specific as is required for a
number of business needs. Beyond the Base roles which contain default access restrictions, up to 100 new
Custom roles can be registered for up to 5,000 users (when user is used). The administrator can also define
whether to allow unregistered users to log in as guests and then specify settings for guest user’s roles.
The following describes the various Base access levels (roles) that are available:
Privileges by Access Level
Predefined Role
Access Privileges
Administrator
Given privileges to operate all device functions.
Network
Manager/Admin
Network manager mainly manages the settings related to the network under Settings/Registration.
Device Manager/Admin
Device Manager can specify settings related to management settings for paper type and function
settings for Send/Receive.
Power User
Given privileges to operate all device functions, except managing the device itself.
General User
Given privileges to operate all device functions, except managing the device itself and
specifying/registering address book.
Limited User
Restricted from device management, all send functions and only allowed 2-sided printing and
copying.
Guest
Restricted from device management, all send functions and only allowed 2-sided printing and
copying.
8
The following functions and features can be restricted:
When the Access Management System has been enabled, users must log in to the device using ULM, UA
or SSO-H user authentication. Access Management System supports authentication through local device
authentication as well as Active Directory using SSO-H, which includes support for Kerberos
Authentication. Once a user logs into the device with their user name and password, the device can
determine which roles are assigned to that particular user. Restrictions are applied based on the assigned
roles. If an entire function is restricted, it will appear grayed out to the user after authentication.
Function Level Authentication
Canon imageRUNNER ADVANCE systems offer the ability to limit the use of specific functions by
authorized users by requiring authentication to use sensitive functions with Function Level Authentication.
Function Level Authentication is a part of Access Management System and works with ULM, UA, or SSOH for authentication. It enables administrators to choose precisely which functions are permitted by walkup and network users without entering credentials versus the ones that require a user to login. For example,
administrators may choose to allow all users to make black-and-white copies while prompting users to
login if they choose to output color or use the Scan and Send function.
Password-Protected System Settings
As a standard feature, imageRUNNER ADVANCE systems setup screens support password protection to
restrict device setting changes from the control panel and Remote UI tool. System Administrators can set
network information, system configuration, enable, and disable network and printing protocols among
many other options. Canon highly recommends setting an administrator password at time of installation
since it controls critical device settings.
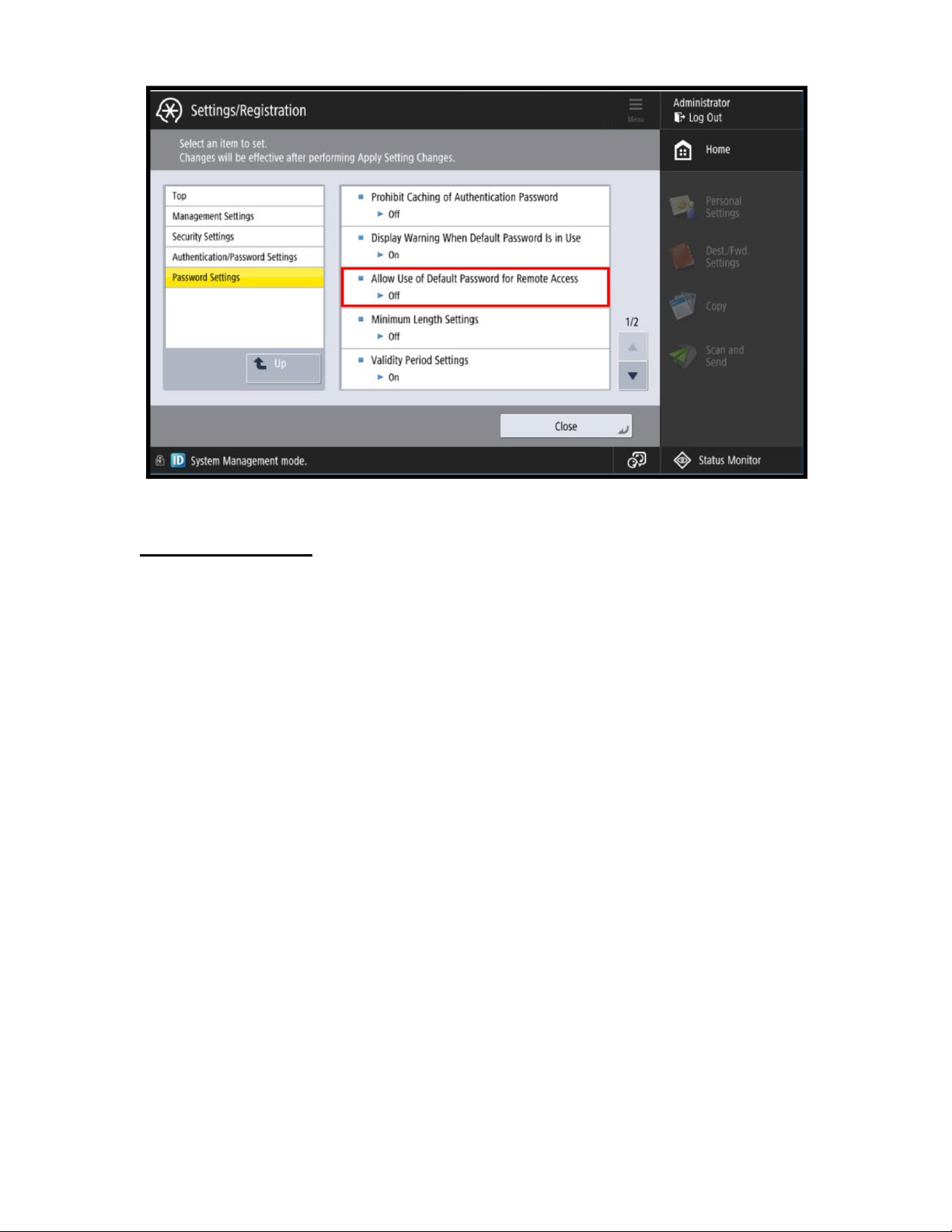
Remote UI Default Password Change
Due to the enhancement of California law SB327, also known as California Consumer Privacy Act (CCPA)
which went into effect on January 2020, any device that has remote access must provide additional security
in the form of: Unique passwords for each device or Require user to change the default password to a
unique password before use. Canon complies with the law by preventing remote access to the device until
the default password/PIN for the Administrator/System Manager account is changed. What changes is the
ability to access the Remote UI through your web browser when the default password/PIN of “7654321” is
currently set on the device. Depending on the series of device, access to the RUI will be prevented or the
RUI will be disabled until the default password is changed.
Dep ID w/o AMS
(with any Auth (DA, SSO-H or ULM)
Auth (SSO-H or ULM) w/AMS Auth (UA) w/o AMS Max 32 functions Auth (UA or ULM) w/AMS
MAX 3 functions MAX 32 functions MAX 32 functions MAX 32 functions
1 Store/Access Files, Fax/i-Fax inbox Copy Copy Copy
2 Send/Fax Scan and Send Scan and Send Scan and Send
3 Other Fax Fax Fax
4 Secured Print Secured Print Secured Print
5 Access Store Files Access Store Files Access Store Files
6 Scan and Store Scan and Store Scan and Store
7 Fax/i-Fax Inbox Fax/i-Fax Inbox Fax/i-Fax Inbox
8 Hold Hold Hold
9 Scanner Scanner Scanner
10 Printer Printer Printer
11 Tutorial Tutorial Tutorial
12 Web Access Web Access Web Access
13 MEAP Applications Dest./Fwd. Setting Dest./Fwd. Setting
14 Web Access favorite Web Access favorite
15 MEAP Applications MEAP Applications
Gen2
Gen3 / DX
9
Scan and Send Security
On devices that have Scan and Send enabled, certain information such as fax numbers and e-mail addresses
may be considered confidential and sensitive. For these devices, there are additional security features to
prevent confidential information from being accessed.
Address Book Password
Administrative and individual passwords can be set for Address Book Management functions. A system
administrator can define the specific Address Book data that can be viewed by users, effectively masking
private details. This password may be set separately so individuals other than the System Manager can
administer the Address Book.
By setting a password for an Address Book, the ability to Store, Edit, or Erase individual and group e-mail
addresses in the Address Book is restricted. Therefore, only individuals with the correct password for an
Address Book will be able to make modifications.
This is not the same functionality when password protecting an Address Book. Administrators who are
looking to Import/Export an Address Book, can elect to set a password when exporting the File. That
password is then required to Import the Address Book. The Address Book Import/Export function is
available through the Remote UI utility.
Access Code for Address Book
End-users will also have the capacity to place an access number code on addresses in the Address Book.
When registering an address, users can then enter an Access Number to restrict the display of that entry in
the Address Book. This function limits the display and use of an address in the Address Book to those users
who have the correct code. The Access Number can be turned on or off, depending on the level of security
the end-user finds necessary.
Settings/Registration > Set Destination > Register Destinations > Register New Destinations, from here the
user can register an new e-mail address, fax number, I-Fax, file or group address and set an access code for
that specific address entry in the address book.
Destination Restriction Function

10
Data transmission to a new destination through the Scan and Send and Fax function can be restricted,
prohibiting transmissions to locations other than the destinations registered or permitted by the System
Manager.
By restricting sending of faxes, e-mails, I-faxes, and files to new destinations using the procedure below, data
can only be sent to previously registered destinations. As you can no longer enter or send to new destinations,
setting this mode with an Address Book PIN increases security when sending. Sending is only allowed in the
following cases when this mode is set:
If you specify a destination stored in the Address Book
If you specify a destination obtained via an LDAP server
If you specify a destination by pressing a one-touch button
If you recall stored [Favorite Settings] including destinations
If you select [Send to Myself]
11
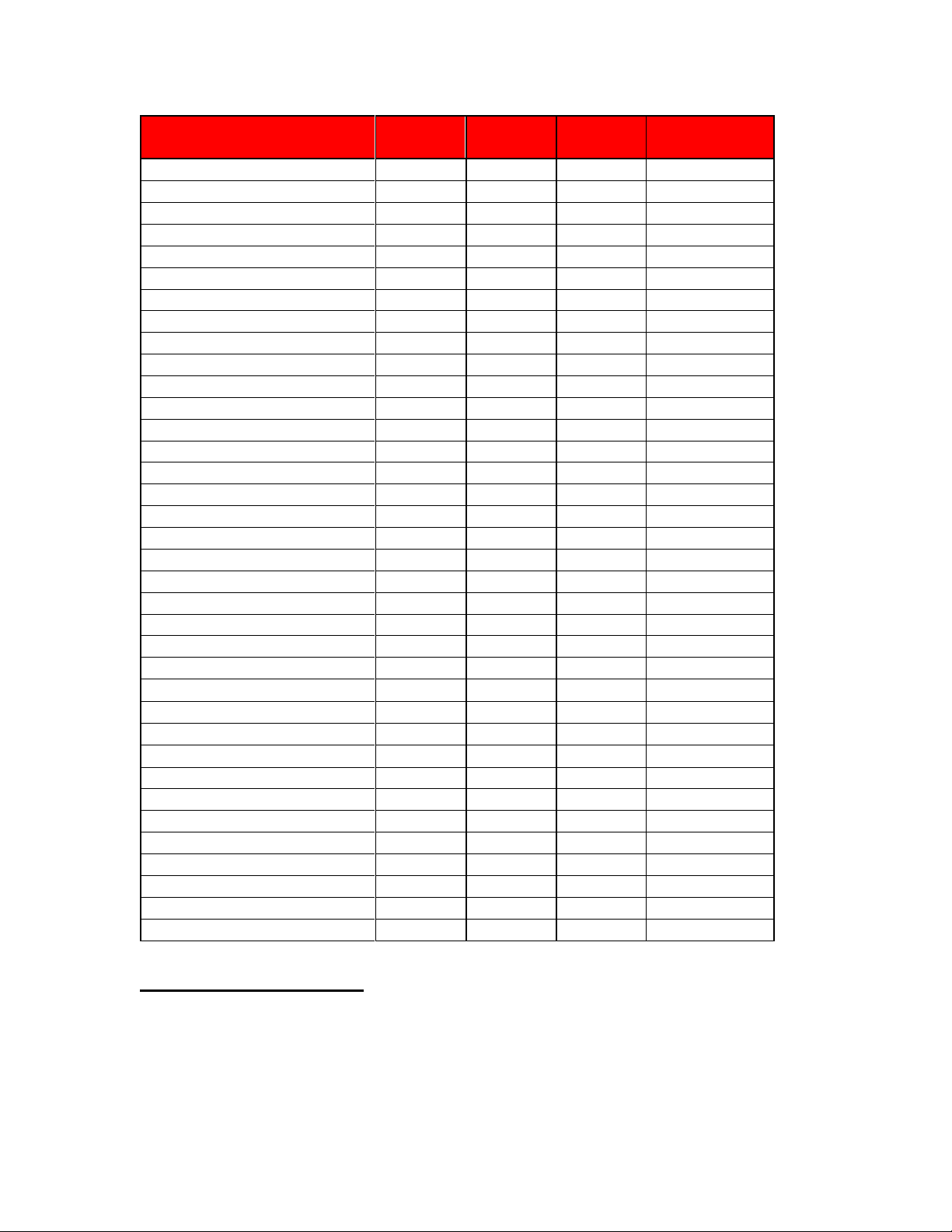
SMB Protocol Support Chart (Send to SMB)
*only supported with latest firmware release
Print Driver Security Features
Print Job Accounting
A standard feature in Canon’s printer drivers, print job accounting requires users to enter an administrator defined password prior to printing, thereby restricting device access to those who are authorized to print.
Printing restrictions can be set using Department ID credentials, User Account Credentials, or through the
Access Management System.
Series
SMB 1.0
supported
SMB 2.0
supported
SMB 3.0
supported
Special FW
For SMB2.0/3.0
iR 1435 / 1435+ series
YES
YES - -
iR 1643 series
YES
YES
YES
-
iR 2500 series
YES - -
YES
iR 1700 series
YES
YES
iR ADV 400iF/500iF
YES - -
YES
iR ADV 3200 series
YES - -
YES
iR ADV 4000 series
YES - -
YES
iR ADV 4200 series
YES - -
YES
iR ADV 715iF II/III series
YES
YES
YES
-
iR ADV 4500/II/III series
YES
YES*
YES*
-
iR ADV DX 4700 series
YES
YES
YES
-
iR ADV 6000 series
YES - -
YES
iR ADV 6200 series
YES - -
YES
iR ADV 6500/II/III series
YES
YES*
YES*
-
iR ADV DX 6700 series
YES
YES*
YES*
-
iR ADV DX 6000i
YES
YES*
YES*
-
iR ADV 8000 series
YES - -
YES
iR ADV 8200 series
YES - -
YES
iR ADV 8500/II/III series
YES
YES*
YES*
-
iR ADV DX 8700 series
YES
YES*
YES*
-
iR ADV C250iF/C350iF
YES - -
YES
iR ADV C255iF/C355iF
YES
YES*
YES*
-
iR ADV C256iF/II/III C356iF/II/III
YES
YES*
YES*
-
iR ADV C3300 series
YES
YES - YES
iR ADV C3500/II/III series
YES
YES*
YES*
-
iR ADV DX C3700 series
YES
YES
YES
-
iR ADV C5000 series
YES - -
YES
iR ADV C5200 series
YES - -
YES
iR ADV C5500/II/III series
YES
YES*
YES*
-
iR ADV DX C5700 series
YES
YES*
YES*
-
iR ADV C7000 series
YES - -
YES
iR ADV C7200 series
YES - -
YES
iR ADV C7500/II/III series
YES
YES*
YES*
-
iR ADV DX C7700 series
YES
YES*
YES*
-
iR ADV C475iF III series
YES
YES
YES
-
imagePRESS Lite C165
YES
YES
YES
-
12
Custom Driver Configuration Tool
Administrators can create custom driver profiles for users to limit access to print features and specify
default settings, thereby protecting the device against unauthorized use, enforcing internal policies and
better controlling output costs. Security conscious settings that can be defined and enforced include duplex
output, secure print, B&W only on color devices, watermarks and custom print profiles, as well as hiding
any desired functions.
USB Block
USB Block allows the System Administrator to help protect the imageRUNNER ADVANCE systems
against unauthorized access through the built-in USB interface. Access to the device’s USB interface for
desktop access and the device’s host mode for other USB devices can each be permitted or disabled.
Go to Settings / Registration > Preferences > External Interface > USB Settings.
All imageRUNNER ADVANCE models and select imageRUNNER models have the ability to restrict USB usage
for memory, but allow USB usage for peripherals such as keyboards and card readers. Canon’s USB feature
provides the capability to view and print from the devices only for non-executable files, such as .pdf, .jpg, .tiff, and
.png. Executable files cannot be performed on the device, and this prevents viruses from spreading if being
accessed.
Third Party MEAP Application and Development
Canon actively collaborates with leading third-party software companies to develop custom solutions for
imageRUNNER ADVANCE systems, known as MEAP applications. Each MEAP enabled device includes
a number of safeguards to help ensure the security and integrity of information stored on the device.
Access to the Software Development Kit for MEAP is tightly restricted and controlled through licensing.
Once an application has been developed, it is thoroughly reviewed by Canon to ensure that it meets strict
guidelines for operability and security. Following the review, the application is digitally signed with a
special encrypted signature to protect the integrity of the application. If the application is modified in any
way, the signature code will not match and the application will not be permitted to run on the device. These
safety measures make it virtually impossible for an altered or rogue MEAP application to be executed on an
imageRUNNER ADVANCE system.
Security Measures to Protect Against Malware and Tampering of Firmware/Applications
Since its inception, the imageRUNNER ADVANCE series has been designed with security in mind.
Security measures to protect against malware/firmware tampering have been implemented that do not allow
for installation or execution of programs without a digital signature applied by Canon when updating
firmware, executing processes or installing MEAP applications. In order to further assist in the prevention
of data disclosure due to unknown attacks/springboard attacks, additional security enhancements have been
made for the third generation imageRUNNER ADVANCE 3rd edition, imageRUNNER ADVANCE DX
and imagePRESS Lite models.
The following program tampering detection function is introduced to counter unknown attacks.
Verify System at Startup
McAfee Embedded Control
Note: These features are only available on third generation imageRUNNER ADVANCE 3rd edition
models, imageRUNNER ADVANCE DX and imagePRESS Lite, and must be enabled. McAfee
Embedded Control requires Unified Firmware Platform (UFP) v3.9 or later

13
Verify System at Startup
Once enabled, the Verify System at Startup function runs a process during startup to verify that
tampering of boot code, OS, firmware and MEAP applications has not occurred. If tampering of one
of these areas is detected, the system will not start. By using the hardware as the ‘Root of Trust’,
enhanced security against software tampering is provided. Furthermore, standard cryptographic
technologies (hash, digital signature) are used for verification.
In order to use this function, the administrator should set “Verify System at Startup” to ON (Default: OFF).
Settings/Registration>Management Settings>Security Settings>Verify System at Startup
When this function is turned ON, warmup time is increased because the verification process is
performed when the device is started. However, it does not affect the time to wake up from sleep
mode or the restore time for quick startup, because the verification process is only performed at device
startup.
If tampering of boot code/OS/firmware/MEAP applications is detected, the device boot process is
halted and an error code is displayed on the control panel. In order to recover from that state, it may be
necessary to reinstall the firmware/MEAP application.
McAfee Embedded Control
Once enabled, McAfee Embedded Control allows only known programs contained in the dynamic
whitelist to be executed on the MFP. Other programs not listed in the whitelist are considered
unauthorized and will not be permitted to execute. This helps prevent worms, viruses, spyware, and
other malware from compromising the device. A log of all prevented executions is available in the
Audit Log when Runtime Intrusion Detection is enabled. McAfee Embedded Control delivers the
following:
Provides file integrity of Canon authorized firmware/applications against the whitelist to help
prevent tampering.
Helps prevent the execution of unknown software code (malware) not on the whitelist.
Helps prevent unauthorized rewriting of registered software modules.
Detects tampering of the whitelist itself.
Permits only authorized system processes to implement changes on device.
To turn on McAfee Embedded Control, it is necessary to turn on Verify System at Startup (Default OFF).
Settings/Registration>Management Settings>Security Settings>Verify System at Startup
The administrator will also need to set “McAfee Embedded Control” to ON (Default OFF).
Settings/Registration>Management Settings>Security Settings>McAfee Embedded Control
Whitelists are created in each storage partition in which native device software modules are installed.
McAfee Embedded Control checks the value held in the whitelist in advance of the module executing,
and verifies the value generated by the execution of the module during operation. If the two values
match, the verification is successful. If the two values do not match, the verification is unsuccessful
and execution of the module fails. The following outlines what will occur if the verification is
unsuccessful:
(a) The firmware verification process begins when the execution module registered in whitelist is
started. If verification fails, the execution is blocked and an error code (E614-xxxx) is
displayed.
(b) When attempted execution of a non-registered software module is detected, the execution stops
and the event is reported in the audit log.

14
(c) When attempts to rewrite or delete a registered software module located on the whitelist is
detected, the attempt is blocked and a record of the error code is saved in the audit log.
(d) Validation of the whitelist itself is performed at startup of any software module. If tampering of
the whitelist is detected, the execution is blocked and an error code is displayed. The error code
is displayed according to the location of the software module where tampering was detected.
Error code example: (E614-xxxx for firmware, E602-xxxx for MEAP application)
(e) The whitelist is updated as required when the system firmware is updated or when authorized
MEAP applications are installed. In order to maintain consistency, when the software module is
updated, the whitelist itself and the transaction log recording the change history of the whitelist
are also updated.
Audit Log Related to Runtime System Protection Function
All recordable activities related to the Verify System at Startup and Runtime Intrusion Detection with
McAfee Embedded Control processes are listed in the Device Management Log and can be notified in real
time to a Security Admin through integration with a SIEM system.
Section 3 — Information Security
Protecting your organization’s confidential information is a mission that Canon takes seriously. From your
documents, faxes and e-mails to the underlying data on the internal hard disk drive and in memory, Canon
has built in many controls to help ensure that your information does not become compromised.
Document Security
Secure Printing
Secured Print / Encrypted Secured Print
Encrypted Secured Print and Secured Print are print functions that hold a job in queue until the user enters
the appropriate password at the device. This ensures that the user is in close proximity before the document
is printed and minimizes unattended documents left at the device. The imageRUNNER ADVANCE system
requires the user to set a password in the print driver window when sending a print job from a connected
PC. The same password is also required for releasing the job at the device. When using the Encrypted
Secured Print software*, security is further enhanced by using AES 256-Bit Encryption to protect the print
job data while in transit across the network. On systems equipped with the optional Encrypted Secured
Print, administrators can use the print job restriction feature to permit only encrypted print jobs at the
designated device. *the third Generation imageRUNNER ADVANCE, imageRUNNER ADVANCE DX and imagePRESS Lite has this feature as standard.
uniFLOW Secure Print
Exclusive to Canon is uniFLOW, which is optional modular software designed to reduce costs, improve
productivity and enhance security. From a security perspective, uniFLOW provides secure printing
Secured Print Screen from the Printer Driver
Print Job Status Screen
15
capabilities by holding jobs at the server until released by the user at any desired imageRUNNER
ADVANCE system. From their desktop, users print documents by choosing the uniFLOW server as the
printer. At the chosen device, users can be authenticated using a wide variety of supported methods. Users
can then access the uniFLOW MEAP client application from the device’s control panel and release their
job from their queue of pending documents.
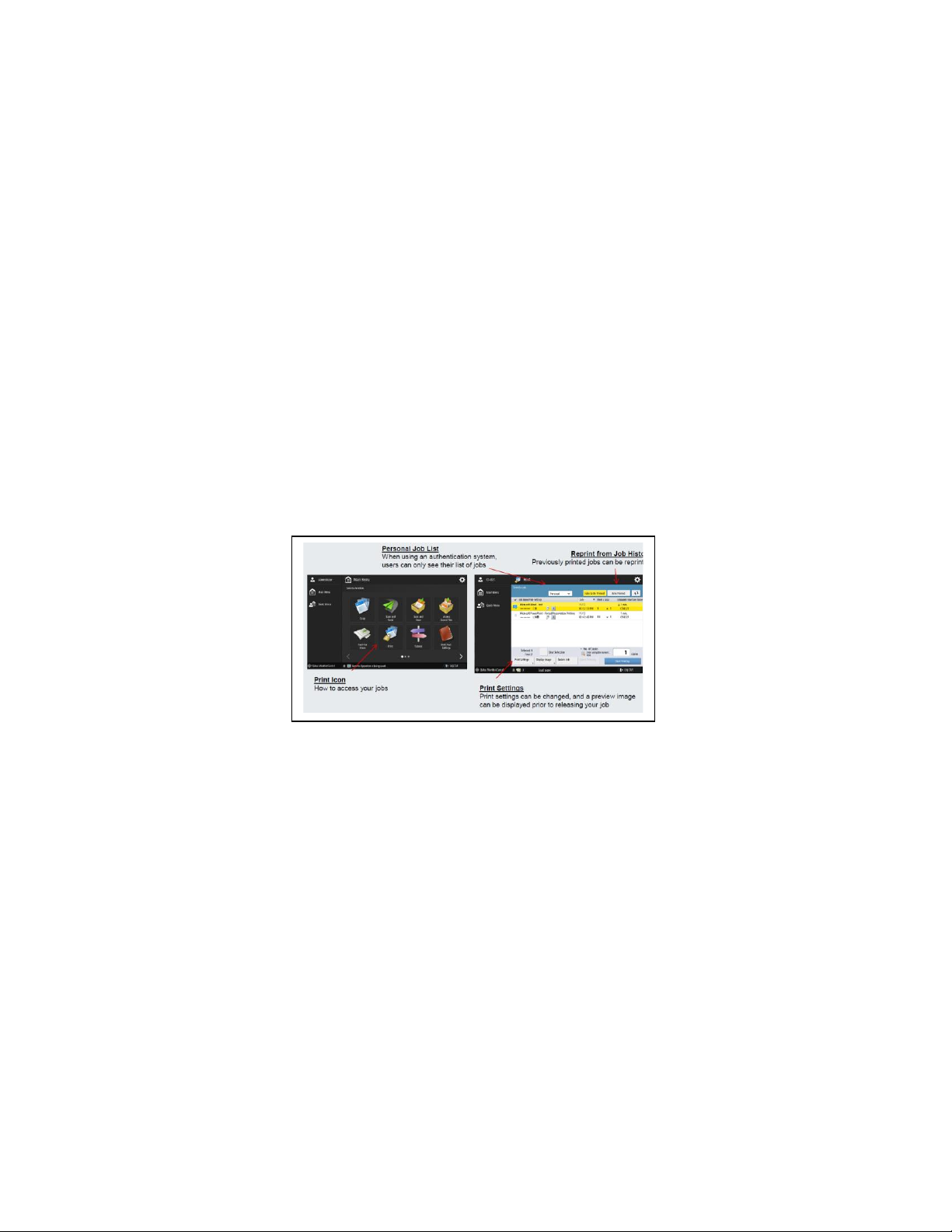
Forced Hold Printing
Canon third generation imageRUNNER ADVANCE, imageRUNNER ADVANCE DX and imagePRESS
Lite models come with an enhancement of the “Secure Printing” function, where IT administrators can
enforce secure print for all, or select users. The setting only needs to be changed in the
Settings/Registration screen on the local device UI. Print driver settings do not need to be changed.
Rules can be set up based on certain conditions (unknown owner, owner name, IP address, and/or port) to
hold as a regular document, print immediately or cancel). Administrators can set how long documents in
job hold will be held (from 10 min – 72 hours), and can choose whether to auto delete after printing or keep
until expiration or manual deletion.
With Forced Hold Printing, IT Administrators can help reduce the amount of wasted prints, by requiring
users to release their jobs after submitting them to the printer, which can reduce the amount of uncollected
printouts around the MFP.
Forced Hold Printing also helps to ensure that the user receives their desired output the first time, by
allowing the user to preview their job, change print settings from the hold queue, and even print a sample
file before printing an entire job.
 Loading...
Loading...