Page 1

Operating Manual
Phantom II
Wireless Ethernet Bridge/Serial Gateway
PN 001-0000-600 Rev A
January 2016
299 Johnson Ave, Suite 110
Waseca, MN 56093
Phone: (800) 992-7774
Fax: (507) 833-6748
www.calamp.com
Page 2
Phantom II
© CalAmp
2
Important User Information
Warranty
CalAmp. warrants that each product will be free of defects in material and workmanship for a period of one (1) year for its products. The warranty commences on the date the product is shipped by CalAmp. CalAmp’s sole liability and responsibility under
this warranty is to repair or replace any product which is returned to it by the Buyer and which CalAmp. determines does not
conform to the warranty. Product returned to CalAmp. for warranty service will be shipped to CalAmp. at Buyer’s expense and
will be returned to Buyer at CalAmp.’s expense. In no event shall CalAmp. be responsible under this warranty for any defect
which is caused by negligence, misuse or mistreatment of a product or for any unit which has been altered or modified in any
way. The warranty of replacement shall terminate with the warranty of the product.
Warranty Disclaims
CalAmp. makes no warranties of any nature of kind, expressed or implied, with respect to the hardware, software, and/or products
and hereby disclaims any and all such warranties, including but not limited to warranty of non-infringement, implied warranties of
merchantability for a particular purpose, any interruption or loss of the hardware, software, and/or product, any delay in pro- viding
the hardware, software, and/or product or correcting any defect in the hardware, software, and/or product, or any other
warranty. The Purchaser represents and warrants that CalAmp. has not made any such warranties to the Purchaser or its agents
CALAMP. EXPRESS WARRANTY TO BUYER CONSTITUTES CALAMP. SOLE LIABILITY AND THE BUYER’S SOLE
REMEDIES. EXCEPT AS THUS PROVIDED, CALAMP. DISCLAIMS ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING ANY WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PROMISE.
CALAMP. PRODUCTS ARE NOT DESIGNED OR INTENDED TO BE USED IN ANY LIFE SUPPORT
RELATED DEVICE OR SYSTEM RELATED FUNCTIONS NOR AS PART OF ANY OTHER CRITICAL SYSTEM AND ARE GRANTED NO FUNCTIONAL WARRANTY.
Indemnification
The Purchaser shall indemnify CalAmp. and its respective directors, officers, employees, successors and assigns including any
subsidiaries, related corporations, or affiliates, shall be released and discharged from any and all manner of action, causes of
action, liability, losses, damages, suits, dues, sums of money, expenses (including legal fees), general damages, special damages,
including without limitation, claims for personal injuries, death or property damage related to the products sold hereunder, costs
and demands of every and any kind and nature whatsoever at law.
IN NO EVENT WILL CALAMP. BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, INCIDENTAL, BUSINESS INT ERRUPTION, CATAST ROPHIC, PUNITIVE OR OTHER DAMAGES WHICH MAY BE CLAIMED TO ARISE IN
CONNECTION WITH THE HARDWARE, REGARDLESS OF THE LEGAL THEORY BEHIND SUCH CLAIMS, WHETHER
IN TORT, CONTRACT OR UNDER ANY APPLICABLE STATUTORY OR REGULATORY LAWS, RULES,
REGULATIONS, EXECUTIVE OR ADMINISTRATIVE ORDERS OR DECLARATIONS OR OTHERWISE, EVEN IF
CALAMP. HAS BEEN ADVISED OR OTHERWISE HAS KNOWLEDGE OF THE POSSIBILITY OF SUCH DAMAGES
AND TAKES NO ACTION TO PREVENT OR MINIMIZE SUCH DAMAGES. IN THE EVENT THAT REGARDLESS OF
THE WARRANTY DISCLAIMERS AND HOLD HARMLESS PROVISIONS INCLUDED ABOVE CALAMP. IS SOMEHOW HELD LIABLE OR RESPONSIBLE FOR ANY DAMAGE OR INJURY, CALAMP.'S LIABILITY FOR ANYDAMAGES SHALL NOT EXCEED THE PROFIT REALIZED BY CALAMP. ON THE SALE OR PROVISION OF THE HARDWARE TO THE CUSTOMER.
Proprietary Rights
The Buyer hereby acknowledges that CalAmp. has a proprietary interest and intellectual property rights in the Hardware, Software and/or Products. The Purchaser shall not (i) remove any copyright, trade secret, trademark or other evidence of CalAmp.’s
ownership or proprietary interest or confidentiality other proprietary notices contained on, or in, the Hardware, Software or Products, (ii) reproduce or modify any Hardware, Software or Products or make any copies thereof, (iii) reverse assemble, reverse
engineer or decompile any Software or copy thereof in whole or in part, (iv) sell, transfer or otherwise make available to others
the Hardware, Software, or Products or documentation thereof or any copy thereof, except in accordance with this Agreement.
Page 3

Phantom II
© CalAmp
3
When operating at elevated temperature extremes, the surface may exceed +70 Celsius. For user
safety, the Viper should be installed in a restricted access location.
WARNING — EXPLOSION HAZARD, do not connect while circuit is live unless area is known to be
non-hazardous.
Important User Information (continued)
About This Manual
It is assumed that users of the products described herein have either system integration or
design experience, as well as an understanding of the fundamentals of radio communications.
Throughout this manual you will encounter not only illustrations (that further elaborate on the
accompanying text), but also several symbols which you should be attentive to:
Caution or Warning
Usually advises against some action which could result in undesired or
detrimental consequences.
Point to Remember
Highlights a key feature, point, or step which is noteworthy. Keeping
these in mind will simplify or enhance device usage.
Tip
An idea or suggestion to improve efficiency or enhance usefulness.
Information
Information regarding a particular technology or concept.
UL Listed Models Only
For more information see APPENDIX F — UL Installation Instructions
Page 4

Phantom II
© CalAmp
4
FCCID: NS908P24
IC: 3143A-08P24
FCCID: NS908P25
IC: 3143A-08P25
This device complies with Part 15 of the FCC Rules.
Operation is subject to the following two conditions:
(1) this device may not cause harmful interference,
and (2) this device must accept any interference
received including interference that may cause
undesired operation.
This device complies with Part 15 of the FCC Rules.
Operation is subject to the following two conditions:
(1) this device may not cause harmful interference,
and (2) this device must accept any interference
received including interference that may cause
undesired operation.
Important User Information (continued)
Regulatory Requirements
To satisfy FCC RF exposure requirements for mobile transmitting devices, a separation
distance of 23cm or more should be maintained between the antenna of this device and
persons during device operation. To ensure compliance, operations at closer than this
WARNING
WARNING
WARNING
WARNING
SAMPLE LABEL REQUIREMENT:
distance is not recommended. The antenna being used for this transmitter must not be
co-located in conjunction with any other antenna or transmitter.
This device can only be used with approved Antennas. Please contact CalAmp if you
need more information or would like to order an antenna.
MAXIMUM EIRP
FCC Regulations allow up to 36dBm Effective Isotropic Radiated Power (EIRP).
Therefore, the sum of the transmitted power (in dBm), the cabling loss and the antenna
gain cannot exceed 36dBm.
EQUIPMENT LABELING
This device has been modularly approved. The manufacturer, product name, and FCC
and Industry Canada identifiers of this product must appear on the outside label of the
end-user equipment.
For Phantom II
Please Note: These are only sample labels; different products contain different identifiers. The
actual identifiers should be seen on your devices if applicable.
Page 5
Phantom II
© CalAmp
5
CSA Class 1 Division 2 Option
CSA Class 1 Division 2 is Available Only on
Specifically Marked Units
If marked this for Class 1 Division 2 – then this product is available
for use in Class 1, Division 2, in the indicated Groups on the product.
In such a case the following must be met:
The transceiver is not acceptable as a stand-alone unit for use in
hazardous locations. The transceiver must be mounted within a
separate enclosure, which is suitable for the intended application.
Mounting the units within an approved enclosure that is certified for
hazardous locations, or is installed within guidelines in accordance
with CSA rules and local electrical and fire code, will ensure a safe
and compliant installation.
The antenna feed line; DC power cable and interface cable must be
routed through conduit in accordance with the National Electrical
Code.
Do not connect or disconnect equipment unless power has been
switched off or the area is known to be non-hazardous.
Installation, operation and maintenance of the transceiver should be
in accordance with the transceiver’s installation manual, and the
National Electrical Code.
Tampering or replacement with non-factory components may
adversely affect the safe use of the transceiver in hazardous
locations, and may void the approval.
The wall adapters supplied with your transceivers are NOT Class 1
Division 2 approved, and therefore, power must be supplied to the
units using the screw-type or locking type connectors supplied from
CalAmp. and a Class 1 Division 2 power source within your panel.
If you are unsure as to the specific wiring and installation guidelines
for Class 1 Division 2 codes, contact CSA International.
Page 6

Phantom II
© CalAmp
6
Rev 0
Initial release
March 2010
Rev 1
Changes made to properly reflect CalAmp branding.
April 2010
Rev 2
Rev 3
Changes to section 2.0 and 6.0, Appendix B
Added IP Discovery Appendix A, Sec 3.1.2 Firmware Upgrade
February 2011
May 2011
Rev A
Added UL Certifications
January 2016
Revision History
Page 7
Phantom II
© CalAmp
7
Table of Contents
1.0 Overview 10
1.1 Performance Features ............................................................................................................................................. 12
1.2 Specifications ............................................................................................................................................................ 12
2.0 Quick Start 14
2.1 Web Interface............................................................................................................................................................ 14
2.1.1 Requirements.............................................................................................................................................. 14
2.1.2 Device Connections ................................................................................................................................... 14
2.1.3 Connecting to the Web Interface ............................................................................................................. 14
2.1.4 Master Configuration ................................................................................................................................. 15
2.1.5 Remote Configuration................................................................................................................................ 15
2.1.6 Check Connectivity .................................................................................................................................... 15
2.2 Text User Interface .................................................................................................................................................. 16
2.2.1 Requirements.............................................................................................................................................. 16
2.2.2 Device Connections ................................................................................................................................... 16
2.2.3 Serial Configuration ................................................................................................................................... 16
2.2.4 Master Configuration ................................................................................................................................. 17
2.2.5 Remote Configuration................................................................................................................................ 18
2.2.6 Check Connectivity .................................................................................................................................... 19
3.0 Hardware Features 20
3.1 Overview.................................................................................................................................................................... 20
3.1.1 Phantom II Mechanical Drawings ............................................................................................................ 21
3.1.2 Connectors & Indicators ............................................................................................................................ 22
3.1.2.1
3.1.2.2
Front ........................................................................................................................................... 22
Rear............................................................................................................................................ 23
4.0 Operating Modes 24
4.1 Master ........................................................................................................................................................................ 24
4.2 Repeater .................................................................................................................................................................... 24
4.3 Remote ...................................................................................................................................................................... 24
5.0 Network Topologies 25
Note: This section includes examples of configurations for each of the following:
5.1 Point-to-Point (PTP) ................................................................................................................................................. 25
5.2 Point-to-Multipoint (PMP) ........................................................................................................................................ 27
5.3 Peer-to-Peer (P2P) .................................................................................................................................................. 30
5.4 Everyone-to-Everyone (E2E).................................................................................................................................. 32
Page 8
Phantom II
© CalAmp
8
Table of Contents (continued)
6.0 Configuration 34
6.1 Overview ....................................................................................................................................................................34
6.1.1 Logon Window.............................................................................................................................................35
6.1.2 Welcome Window .......................................................................................................................................37
6.1.3 System Configuration .................................................................................................................................38
6.1.4 Network Configuration. ..............................................................................................................................42
6.1.4.1 Local IP Configuration ..............................................................................................................43
6.1.4.2 NTP Server Configuration........................................................................................................52
6.1.4.3 DHCP Server Configuration ....................................................................................................54
6.1.4.4 SNMP Agent Configuration .....................................................................................................60
6.1.4.5 Bridge Configuration.................................................................................................................66
6.1.4.6 Quality of Service ......................................................................................................................67
6.1.4.7 L2 Mesh......................................................................................................................................69
6.1.5 Radio Configuration ....................................................................................................................................70
6.1.6 COM1 and COM2 Configuration...............................................................................................................90
6.1.7 USB Configuration ................................................................................................................................... 102
6.1.8 Security Configuration............................................................................................................................. 103
6.1.8.1 Admin Password Configuration............................................................................................ 104
6.1.8.2 Upgrade Password Configuration ....................................................................................... 105
6.1.8.3 Wireless Encryption Configuration ...................................................................................... 106
6.1.8.4 UI (User Interface) Access Configuration........................................................................... 110
6.1.8.5 Authentication Configuration ................................................................................................ 112
6.1.8.6 Firewall Configuration ........................................................................................................... 115
6.1.9 System Information.................................................................................................................................. 129
6.1.10 System Tools ............................................................................................................................................ 136
6.1.10.1 System Maintenance............................................................................................................. 137
6.1.10.2 Reboot System ....................................................................................................................... 138
6.1.10.3 Reset System to Default ....................................................................................................... 139
6.1.10.4 Radio Channels Noise Level ................................................................................................ 140
6.1.10.5 Network Discovery................................................................................................................. 142
6.1.10.6 Remote Sleep Control ........................................................................................................... 142
6.1.10.7 Local Power Saving ............................................................................................................... 142
6.1.10.8 Logout ...................................................................................................................................... 145
6.1.4.1.1 Bridge ...................................................................................................................43
6.1.4.1.2 Router ...................................................................................................................47
6.1.4.1.2.1 Wireless Port IP Configuration ................................................48
6.1.4.1.2.2 VPN Configuration ....................................................................50
6.1.4.3.1 Bridge ...................................................................................................................54
6.1.4.3.2 Router ...................................................................................................................54
6.1.8.6.1 Policies .............................................................................................................. 116
6.1.8.6.2 Rules.................................................................................................................. 119
6.1.8.6.3 Port Forwarding................................................................................................ 123
6.1.8.6.4 MAC List ............................................................................................................ 125
6.1.8.6.5 Blacklist.............................................................................................................. 127
6.1.8.6.6 Reset Firewall to Factory Default .................................................................. 128
7.0 Installation 146
7.1 Path Calculation ..................................................................................................................................................... 149
7.2 Installation of Antenna System Components..................................................................................................... 150
7.2.1 Antennas ................................................................................................................................................... 151
7.2.2 Coaxial Cable ........................................................................................................................................... 152
7.2.3 Surge Arrestors ........................................................................................................................................ 152
7.2.4 External Filter............................................................................................................................................ 153
Page 9
Phantom II
© CalAmp
9
Table of Contents (continued)
Appendices
Appendix A: IP Discovery Utility ............................................................................................ 154
Appendix B: Upgrade Procedure (DOS Prompt) ..................................................................... 155
Appendix C: RS485 Wiring ................................ ................................................................... 158
Appendix D: Serial Interface ................................................................................................ .. 159
Appendix E: Customer Interface Schematic ........................................................................... 160
Appendix F: UL Certifications ............................................................................................... 163
Page 10

Phantom II
© CalAmp
10
1.0 Overview
A BRIDGE separates two network
segments within the same logical
network (subnet).
A ROUTER forwards data across
internetworks (different subnets).
A SERIAL GATEWAY allows
asynchronous serial data to enter
(as through a gate) the realm of IP
communications.
The serial data is encapsulated
within UDP or TCP packets.
The Phantom II is a high-performance wireless Ethernet bridge and
serial gateway. Alternately, a Master Phantom II unit may be configured to operate as a wireless Ethernet router (and serial gateway).
When properly configured and installed, long range communications
at very high speeds can be achieved.
The Phantom II operates within the 902-928MHz ISM frequency
band, employing frequency hopping spread spectrum (FHSS) and
also, for 1.2 Mbps operation, digital transmission service (DTS) technology.
They provide reliable wireless Ethernet bridge functionality as well
gateway service for asynchronous data transfer between most equipment types which employ an RS232, RS422, or RS485 interface.
The small size and superior performance of the Phantom II makes it
ideal for many applications. Some typical uses for this modem:
SCADA
Remote telemetry
Traffic control
Industrial controls
Remote monitoring
LAN extension
1.1 Performance Features
Transmission within a public, license-exempt band of the
radio spectrum1 - this means that the modems may be used
without access fees or recurring charges (such as those
incurred by cellular airtime)
Maximum allowable transmit power (1 Watt) - 4 Watts Max
EIRP
Longest range
Transparent, low latency link providing reliable wireless IP/
Ethernet communications with constant baud rate over
distance
1
920-928MHz, which is license-exempt within North America, may need to be
factory-configured differently for other areas: contact CalAmp.
GPS
Wireless video
Robotics
Display signs
Fleet management
Page 11
Phantom II
© CalAmp
11
1.1 Overview
Each unit supports all modes of operation (Master, Repeater,
Remote)
Repeater may also be used concurrently as a Remote unit
Flexible wireless networking: point-to-point, point-to-multipoint,
peer-to-peer, store and forward repeater, layer 2 mesh
Communicates with virtually all PLCs, RTUs, and serial devices
through either one of two available RS232 interface, RS422, or
RS485
Fastest serial rates: 300 baud to 921 kbps
Advanced serial port supports legacy serial devices, including
RTS, CTS, DSR, DTR, and DCD.
Easy to manage through web- or text-based user interface, or
SNMP
Wireless firmware upgrades
System wide remote diagnostics
32-bit CRC, selectable retransmission
Advanced security features
Industrial temperature specifications
DIN rail mountable
Optional Class 1 Div 2
Supporting co-located independent networks and with the ability to
carry both serial and IP traffic, the Phantom II supports not only
network growth, but also provides the opportunity to migrate from
asynchronous serial devices connected today to IP-based devices in
the future.
Page 12
Phantom II
© CalAmp
12
1.0 Overview
1.2 Phantom II Specifications
Electrical/General
Frequency: 902-928MHz*
(* Contact CalAmp for additional frequencies)
Spreading Method: Frequency Hopping /DTS
Band Segments: Selectable via Freq. Restriction
Error Detection: 32 bits of CRC, ARQ
Caution: Using a power
supply that does not provide
proper voltage or current may
damage the modem.
Tip: Future enhancements of
the Phantom II products may
require higher current
requirements than listed. It is
good design practice to over
spec pow er supplies to allow
for future design options.
Data Encryption: 128-bit WEP/WPA (Canada & USA only)
-AES - Optional 128/256-bit AES Encryption,
Secure Shell, HTTPS (Canada & USA only)
Range:
Up to 20+ miles @ 1.2 Mbps
Up to 40+ miles @ 345 kbps
Output Power: 100mW to 1W (20-30dBm)
Sensitivity: -101 dBm @ 345 kbps link rate
-97 dBm @ 1.2 Mbps link rate
Serial Baud Rate: 300 bps to 921 kbps
USB: USB 2.0
Ethernet: 10/100 BaseT, Auto - MDI/X, IEEE 802.3
Link Rate: 345 kbps or 1.2 Mbps
Network Protocols: TCP, UDP, TCP/IP, TFTP, ARP, ICMP, DHCP,
HTTP, HTTPS*, SSH*, SNMP, FTP, DNS, Serial
over IP, QoS
Operating Modes: Master, Remote, Repeater
Management:
(* Only available in –AES)
Local Serial Console, Telnet, WebUI, SNMP, FTP &
Wireless Upgrade, RADIUS authentication, VLAN
Diagnostics:
Battery Voltage, Temperature, RSSI, remote
diagnostics
Core Voltage: Enclosed: 7-30 VDC
Page 13
Phantom II
© CalAmp
13
1.0 Overview
1.2 Phantom II Specifications (Continued)
Environmental
Operation Temp: -40oF(-40oC) to 170oF(75oC)
Mechanical
Humidity: 5% to 95% non-condensing
Dimensions:
Weight:
Antenna: Reverse Polarity TNC (RP-TNC) connector
Data, etc: AVX-Kyocera 5046 Series 60 pin board to board
2.25” (57mm) X 3.75” (95mm) X 1.75” (45mm)
Approx. 237 grams (8 oz)
connectors
Page 14
Phantom II
© CalAmp
14
2.1 Quick Start
To ensure that the Phantom II unit
is at its DEFAULT factory settings,
once it has powered-up and the
Status LED is ON (after 1 minute),
press and hold the front CFG
button for 8 seconds - the Status
LED will initially blink, then be on
solid, and then the unit will reset.
This Quick Start Guide will enable you to promptly establish basic IP
connectivity between a pair of Phantom II modems in a point-to-point
(ref. 5.1) configuration.
Note that the units arrive from the factory with a Radio Configuration
of ‘Remote’ and the Local Network setting configured as ‘Static’ (IP
Address 192.168.1.254, Subnet Mask 255.255.255.0, and Gateway
192.168.1.1).
2.1 Programming Option 1 - Web Interface
2.1.1 Requirements
To Program your Phantom II using the web interface, you will need:
At least (2) two Phantom II (factory configured) with Power
Adapter and Rubber Ducky Antenna. Each factory configured
Phantom II has the following default settings: ‘Remote’ with Local
Network Settings ‘Static’ (IP Address 192.168.1.254, Subnet
Mask 255.255.255.0, Gateway 192.168.1.1)
PC with NIC (Ethernet) card
Ethernet cable. If your PC does not support Auto MDIX, you will
need to use a crossover cable
2.1.2 Device Connections
Connect Rubber Ducky to the antenna port of each Phantom II
Connect power adapters to 120 VAC outlets and to each Phan-
tom II Using an Ethernet cable,
Connect the Phantom II that will be the MASTER device to the
PC NIC
2.1.3 Connecting to the Web Interface
Open a Web Browser and enter the IP Address of the Phantom II
into the URL address line
Press [Enter]
A login window will appear. Enter default user name (admin) and
default password (admin)
Press [Enter]
Page 15
Phantom II
© CalAmp
15
2.1 Quick Start
2.1.4 Master Configuration
Select Network Configuration > Local IP Config. Assign unit IP
Address, Subnet Mask and Gateway. [Submit]
NOTE: If the Local IP Address of the Phantom II is changed to a new
network, the PC NIC IP Address must also be reassigned to the new
network.
Open a Web Browser and enter the newly assigned IP Address
of the Phantom II into the URL address line
A login window will appear. Enter admin for the default user-
name. Enter admin for the default password.
Press [Enter]
Select Radio Configuration
Select Master as the Operation Mode
Select Point-to-Point as the Network Type. [Submit]
2.1.5 Remote Configuration .
Repeat the above for the other Phantom II, giving it a new unique
IP Address. By default the Operation Mode is already configured
as a Remote
Change the Destination Unit on the Master radio to match the
Unit Address of the Remote radio. [Submit]
2.1.6 Check Connectivity
With both units powered-on, in proximity to each other, their
RSSI LEDs should be illuminated
With the PC connected to one of the Phantom II units with an
Ethernet cable, open a web browser and enter the IP Address of
‘the other’ unit to verify a wireless connection
To simulate data traffic over the radio network, connect a PC to
the Ethernet port of the Phantom II and PING each unit in the
network multiple times
Page 16
Phantom II
© CalAmp
16
2.1 Quick Start
2.2 Programming Option 2 - Text User Interface
2.2.1 Requirements
To program your Phantom II using the text interface, you will need:
At least (2) two Phantom II (factory configured) with Power
Adapter and Rubber Ducky Antenna. Each factory configured
Phantom II has the following default settings: ‘Remote’ with Local
Network Settings ‘Static’ (IP Address 192.168.1.254, Subnet
Mask 255.255.255.0, Gateway 192.168.1.1)
PC with NIC (Ethernet) card and COM (serial) port with
HyperTerminal (or equivalent). If your PC does not have a Serial
port, you will need a serial to USB adapter
Diagnostic serial cable (DB9-DB9)
Ethernet cable. If your PC does not support Auto MDIX, you will
need to use a crossover cable
2.2.2. Device Connections
Connect Rubber Ducky to the antenna port of each Phantom II
Connect power adapters to 120 VAC outlets and to each
Phantom II
Using a diagnostic serial cable, connect the DIAGNOSTICS port
of the Phantom II that will be the MASTER device to an available
COM port on the PC
2.2.3 Serial Configuration
Run HyperTerminal (or equivalent terminal program) on the PC
and configure the selected Serial/COM port for 115200 bps, 8
data bits, no parity, 1 stop bit, and no flow control
Activate the HyperTerminal connection. Press [Enter]. A login
prompt will appear
Enter default user name (admin). Press [Enter]
Enter default password (admin). Press [Enter]
Page 17
Phantom II
© CalAmp
17
2.0 Quick Start
View the PC’s NETWORK
SETTINGS (TCP/IP Properties) to
determine an appropriate IP
Address, Subnet Mask, and
Gateway for the Phantom II.
(For basic testing, the Gateway
value is not critical.)
If a connection is being made to a
network (LAN), check with the
Network Administrator for an
available static IP address(es) so
as not to potentially create an IP
address conflict.
2.2.4 Master Configuration
Select [B] Network Configuration
Select [A] Local IP Config
Select [B] Enter IP Address
Select [C] Enter Subnet Mask
Select [D] Enter IP Gateway; Press [Enter]
Press [U] to SAVE the configuration changes
Press [Esc] twice to return to the MAIN MENU
Select [C] Radio Configuration
Select [B] Operation Mode
Select [A] Master
Select [I] Network Type
Select [B] Point-to-Point
Select [J] Destination Unit. Enter the number 20.
Press [Enter]
Press [U] to SAVE the configuration changes
Press [Esc] to return to the MAIN MENU
Press [Q] to Quit
Page 18
Phantom II
© CalAmp
18
2.0 Quick Start
2.2.5 Remote Configuration
Remove the Serial connection from the MASTER device
and connect it to the next Phantom II.
Press [Enter] to open the log in prompt
Enter default user name (admin). Press [Enter]
Enter default password (admin). Press [Enter]
Select [B] Network Configuration
Select [A] Local IP Config
Select [B] Enter IP Address
Select [C] Enter Subnet Mask
Select [D] Enter IP Gateway. Press [Enter]
Press [U] SAVE the configuration changes
Press [Esc] twice to return to the MAIN MENU
Select [C] Radio Configuration
Select [F] Unit Address. Enter number 20. Press [Enter]
Select [I] Network Type
Select [B] Point-to-Point
Press [U] to SAVE the configuration changes
Press [Esc] to return to the MAIN MENU
Press [Q] to Quit .
Page 19
Phantom II
© CalAmp
19
2.1 Quick Start
2.2.6 Check Connectivity
With both units powered-on, in proximity to each other, their
RSSI LEDs should be illuminated
With the PC connected to one of the Phantom II units with an
Ethernet cable, open a web browser and enter the IP Address of
‘the other’ unit to verify a wireless connection
To simulate data traffic over the radio network, connect a PC to
the Ethernet port of the Phantom II and PING each unit in the
network multiple times
Page 20

Phantom II
© CalAmp
20
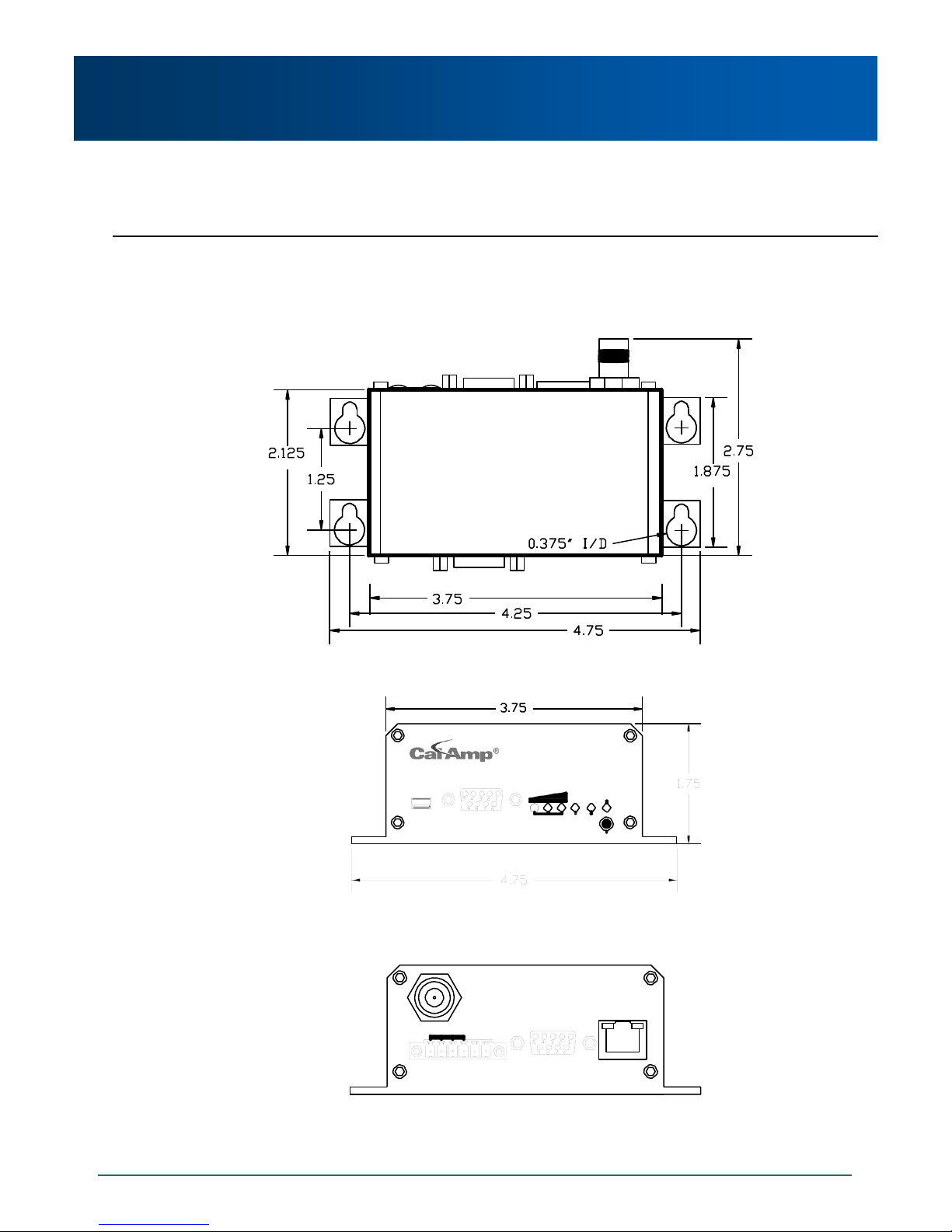
3.0 Hardware Description
3.1 Overview
The Phantom II provides a fully enclosed, stand alone modem, requiring only cabled connections. The
Phantom II can be used on a table top like surface, or using the mounting holes provided can be mounted
anywhere for a permanent solution.
Power
Data (Serial) Interface
Ethernet Interface
USB Interface
Indicators
Antenna
Any Phantom II may be configured as a Master, Repeater (or Repeater/Remote), or Remote.
This versatility is very convenient from a ’sparing’ perspective, as well for convenience in becoming very
familiar and proficient with using the module: if you are familiar with one unit, you will be familiar with all units.
Image 3-1: Phantom II
Page 21
Phantom II
© CalAmp
21
Nano IP Enclosed
Top View
microhard SYSTEMS INC.
Phantom II
STA TUS
US B DI AG NOS TI C
RSSI
TX RX
CONF IG
Front View
Phantom II
Top View
Front
ANTENNA
RS4 85/422
DAT A
ETH ERNET
TxB -
TxA -
RxB -
RxA -
GN D
-
Vin + -
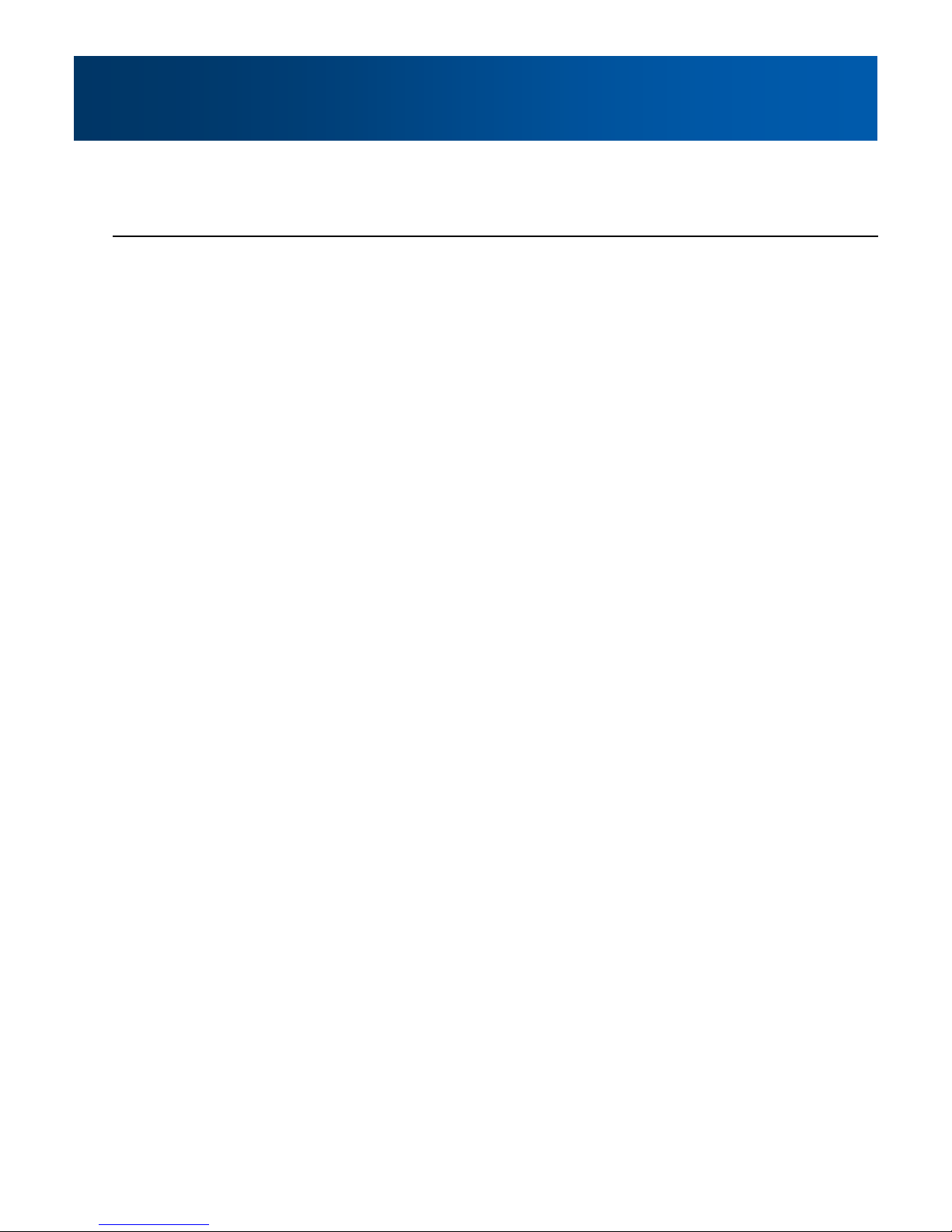
3.0 Hardware Description
3.1.1 Phantom II Mechanical Drawings
Image 3-2: Phantom II Top View
Image 3-3: Phantom II Front View
Back View
Image 3-4: Phantom II Back View
Notes: The dimension unit is inches.
Page 22
Phantom II
© CalAmp
22
microhard SYSTEMS INC.
Phantom II
STA TUS USB
DIAGNOSTIC
RSSI
TX RX
CONFIG
Signal
Name
PIN
#
Input or
Output
RXD
2
O
TXD 3 I
SG
5
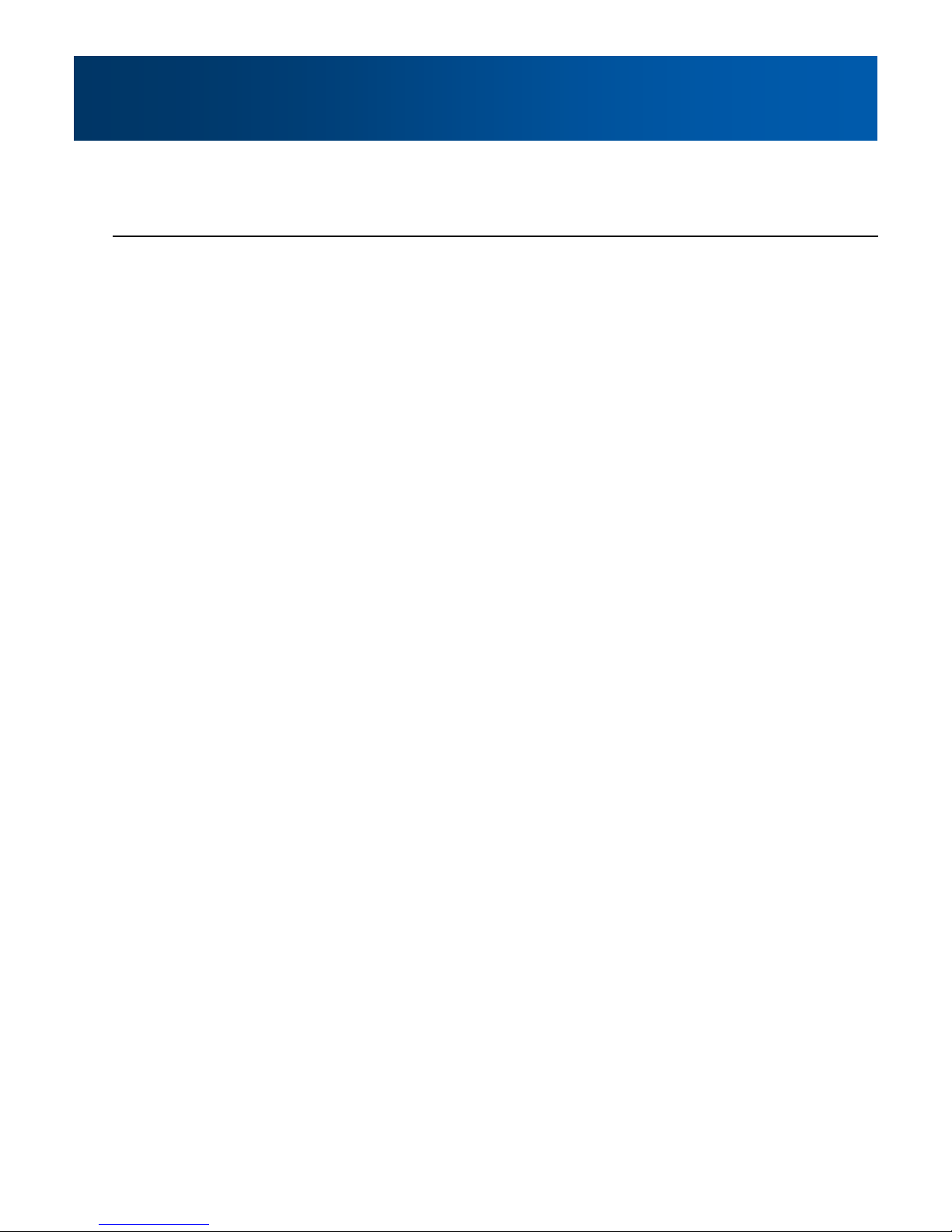
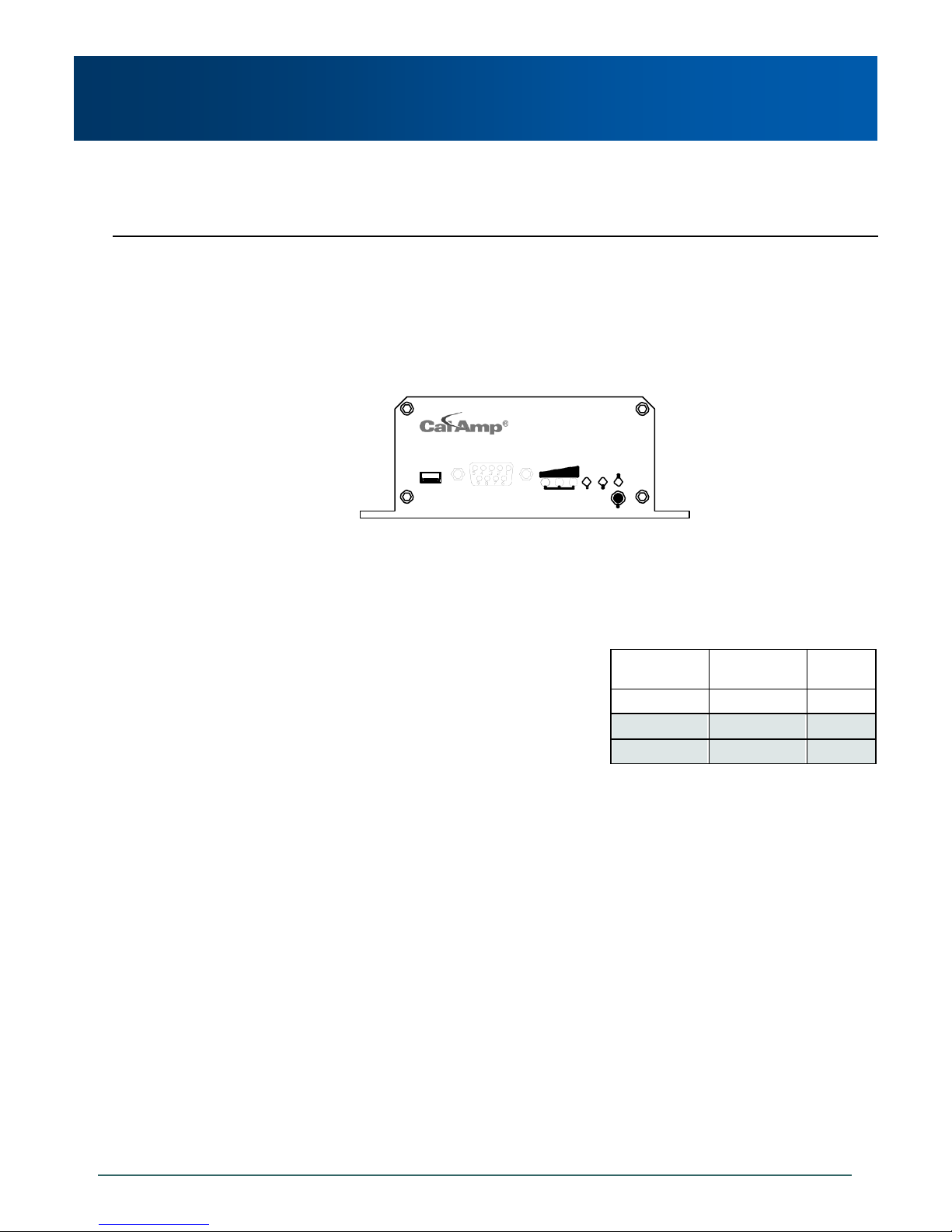
3.0 Hardware Description
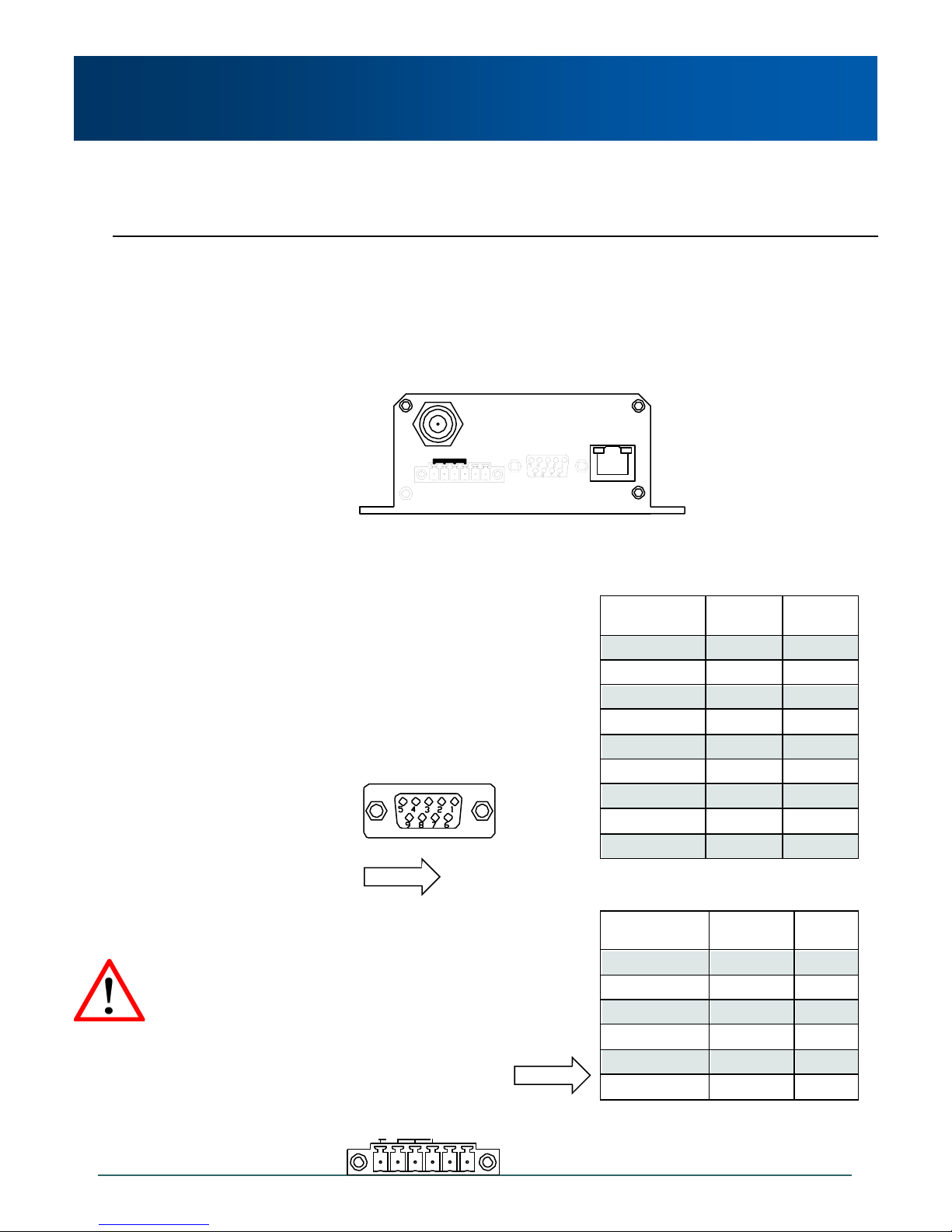
3.1.2 Connectors and Indicators
3.1.2.1 Front
On the front of the Phantom II is the USB port, DIAGNOSTIC port, CONFIG Button, and the RSSI,
STATUS, TX and RX LED’s.
Image 3-5: Phantom II Front View
The USB port can be used for:
USB Console Port
USB to Serial Data Routing
USB to Ethernet Data Routing
The Diagnostic port (RS232) is used for:
Text User Interface (local console port) at 115.2
kbps and HyperTerminal (or equivalent).
User data (serial, RS-232, wired for RxD, TxD, and
SG)
CONFIG Button
Holding this button depressed while powering-up the Phantom II will boot the unit into FLASH FILE
SYSTEM RECOVERY mode. The default IP address for system recovery (not for normal access to the
unit) is static: 192.168.1.39. To use this feature, please contact CalAmp for the Phantom II Firmware
Upgrade & Recovery Application Note.”
Table 3-1: Diagnostic Port RS232 Pin Assignment
If the unit has been powered-up for some time (>1 minute), depressing the CFG Button for 8 seconds
will result in FACTORY DEFAULTS being restored, including a static IP address of 192.168.1.254. This
IP address is useable in a Web Browser for accessing the Web User Interface.
TX LED (Red) / RX LED (Green)
When illuminated, the TX LED indicates that the modem is transmitting data over the air and the RX
LED indicates that the modem is synchronized and has received valid packets
Receive Signal Strength Indicator (RSSI) (3x Green)
As the received signal strength increases, starting with the furthest left, the number of active RSSI LEDs
increases. Signal strength is calculated based on the last four valid received packets with correct CRC.
STATUS LED
Upon initial application of power the STATUS LED will be illuminated for approximately 20 seconds,
after which time it will being to blink slowly (loading) for an additional 25 seconds, then stay ON
‗solid‘ (indicating it has achieved its specific operational status).
Page 23
Phantom II
© CalAmp
23
Green Conn.
Pin No.
Name
Input or
Output
1
TxB (D+) O 2
TxA (D-)
O
3
RxB (R+)
I
4
RxA (R-)
I
5
Vin -
6
Vin +
I
RS485/422
A N TENNA
RS485/422
DA TA
ETHER N E T
Tx B
-
Tx A
-
RxB
-
RxA
-
GND
-
Vi n+
-
TxB -
TxA -
RxB -
RxA -
GND -
Vin + -
Name
Data Port
Input or
Output
DCD
1
O
RXD
2
O
TXD 3 I
DTR 4 I
SG
5
DSR
6
O
RTS 7 I
CTS
8
O
RING
9
O
3.0 Hardware Description
3.1.2 Connectors and Indicators
Caution: Using a power
supply that does not
provide proper voltage
may damage the modem.
3.1.2.2 Rear
On the back of the Phantom II is the Data port, RS485/422 interface, Ethernet port, as well as the power
connections.
Image 3-6: Phantom II Rear View
The DATA (RS232 Port (DCE)) on the rear
of the circuit board is used for:
RS232 serial data (300-921 kbps) when
in DATA MODE, or
for configuring the modem when in
COMMAND MODE.
The RS422/485 Port is used to interface the Phantom II
to a DTE with the same interface type. Either the RS232
or RS422/485 interface is used for data traffic.
Vin+/Vin– is used to power the unit. The input Voltage
range is 7-30 VDC.
Table 3-2: Data RS232 Pin Assignment
Table 3-3: Data RS422/485 / Vin Pin Assignment
Page 24
Phantom II
© CalAmp
24
4.0 Operating Modes
A Phantom II may be configured for any operating mode. This is very
convenient for purposes of sparing and becoming familiar with their
configuration menus.
4.1 Master
One per network, the source of synchronization for the system. The
Master controls the flow of data through the system.
4.2 Repeater
Required only if necessary to establish a radio path between a
Master and Remote(s); stores and forwards the data sent to it.
Synchronizes to Master and provides synchronization to
‘downstream’ units.
If a local device is attached to a Repeater’s serial data port, the
Repeater will also behave as a Remote (aka Repeater/Remote).
As they are added to a radio network it is good practice to use the
values 2-17, sequentially, for Repeater Unit Addresses.
Adding one or more Repeaters within a network will HALVE the
throughput; the throughput is halved only once, i.e. it does not
decrease with the addition of more Repeaters.
If there is a ‘radio (signal) path’ requirement to provide Repeater
functionality, but throughput is critical, the repeating function may be
accomplished by placing two Phantom II modems at the Repeater
site in a ‘back-to-back’ configuration. One Phantom II would be
configured as a Remote in the ‘upstream’ network; the other a
Master in the ‘downstream’ network. Local connection between the
modems would be accomplished with a crossover cable (for the
Ethernet connection). Each modem would require its own antenna;
careful consideration should be given with respect to antenna
placement and Phantom II configuration.
4.3 Remote
Endpoint/node within a network to which a local device is attached.
Communicates with Master either directly or through one or more
Repeaters. See Sections 5.3 and 5.4 for information regarding
‘Remote-to-Remote’ communications.
Page 25
Phantom II
© CalAmp
25
5.0 Network Topologies
The Phantom II may be configured to operate in a number of
different operating modes and participate in various network
The RADIO network topology
determines the paths available
for the movement of data.
Take this important fact into
consideration when selecting a
network topology.
topologies.
Note: This section describes radio network topologies in general
and includes examples of corresponding Radio Configuration
settings. Refer to section 6 for further detailed information
regarding configuration options.
5.1 Point-to-Point (PTP)
In a Point-to-Point network, a path is created to transfer data
between
considered the Master modem and Point B a Remote. Such a
PTP network may also involve one or more Repeaters (in a storeand-forward capacity) should the radio signal path dictate such a
requirement.
Point A and Point B, where Point A may be
A PTP configuration may also be used in a more dynamic sense:
there may be many Remotes (and Repeaters) within such a
network, however the Master may have its ‘Destination Address’
changed as and when required to communicate with a specific
remote unit.
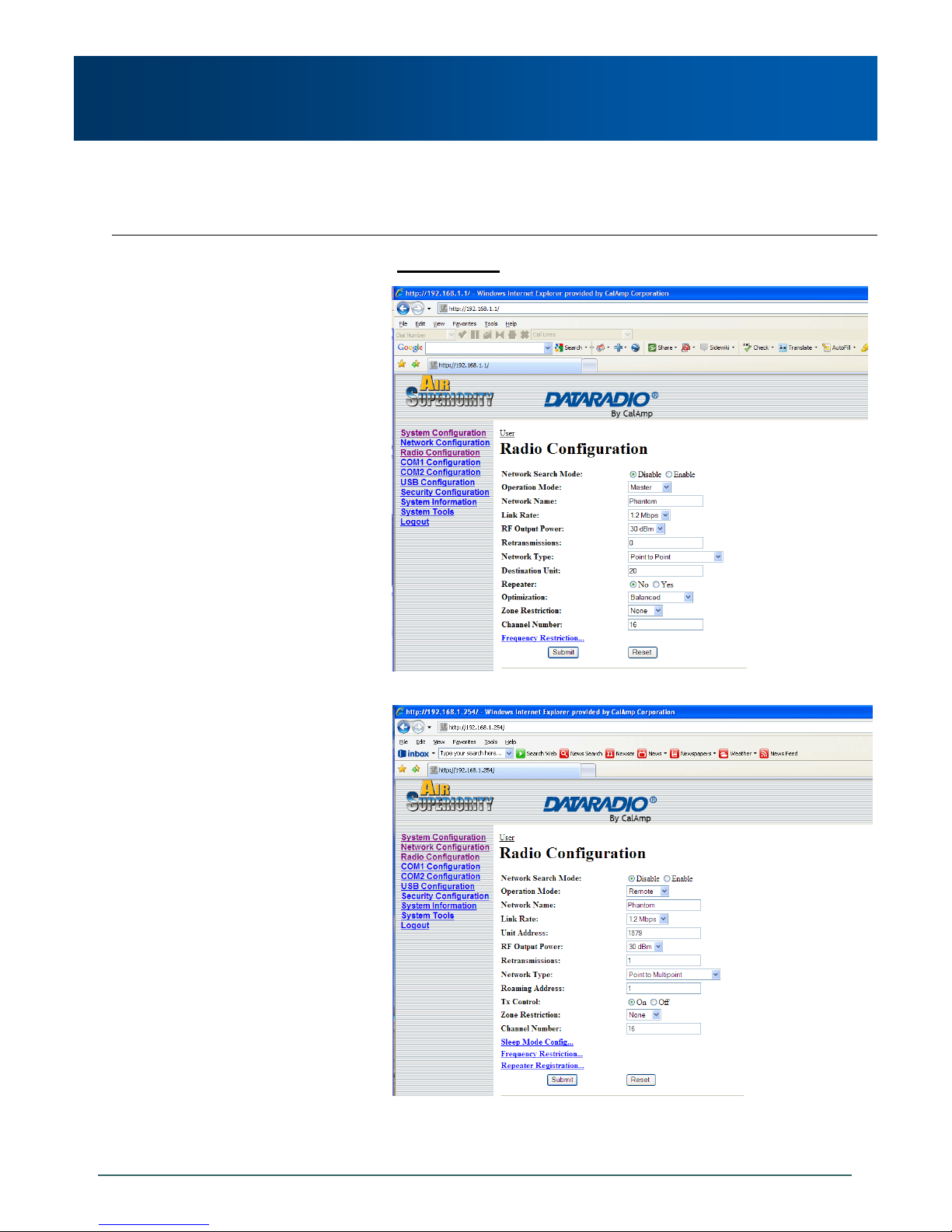
An example of a basic PTP network consisting of two Phantom II
modems is on the next page.
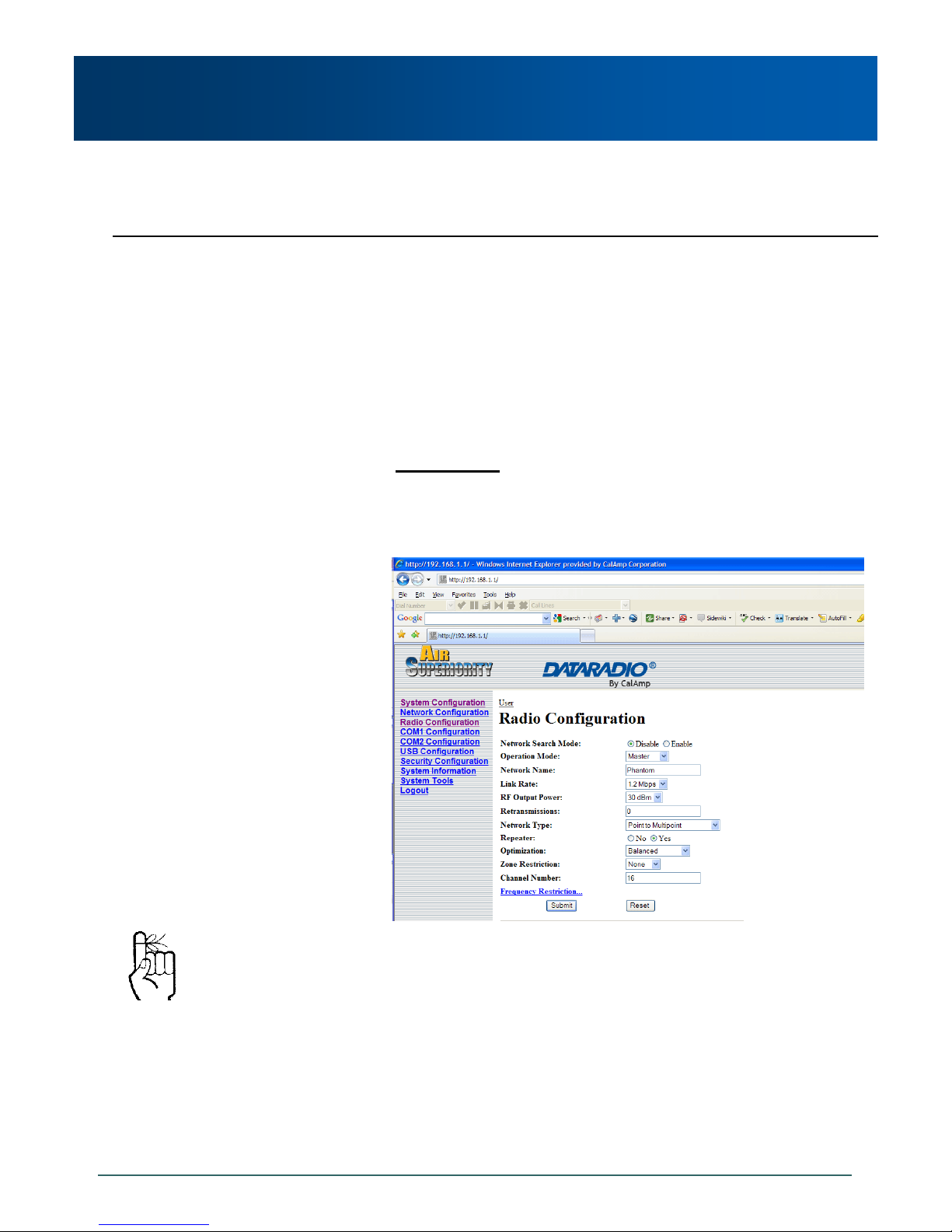
As shown in Example 5.1.1:
Configuration options are based upon the chosen
Operating Mode of the unit: select the Operating Mode
first.
The DESTINATION UNIT for the MASTER is the UNIT
ADDRESS of the REMOTE, and vice versa (noting that
the MASTER’s Unit Address (not visible) is preset, and
must remain as, ‘1’).
For a PTP system, RETRANSMISSIONS on a
MASTER is not as critical a setting as it is in a Point-toMultipoint (PMP) system.
Page 26
Phantom II
© CalAmp
26
5.0 Network Topologies
Example 5.1.1
Image 5-1: PTP Example 5.1.1 Master
Image 5-2: PTP Example 5.1.1 Remote
Page 27
Phantom II
© CalAmp
27
5.0 Network Topologies
5.2 Point-to-Multipoint (PMP)
In a Point-to-Multipoint network, a path is created to transfer data
between the Master modem and numerous remote modems. The
remote modems may simply be Remotes with which the Master
communicates directly, and/or Remotes which communicate via
Repeaters. Some or all of the Repeaters may also act as Remotes
in this type of Network, i.e. the Repeaters are not only storing and
forwarding data, but are also acting as Remotes. Such Repeaters
may be referred to as ‘Repeater/Remotes’.
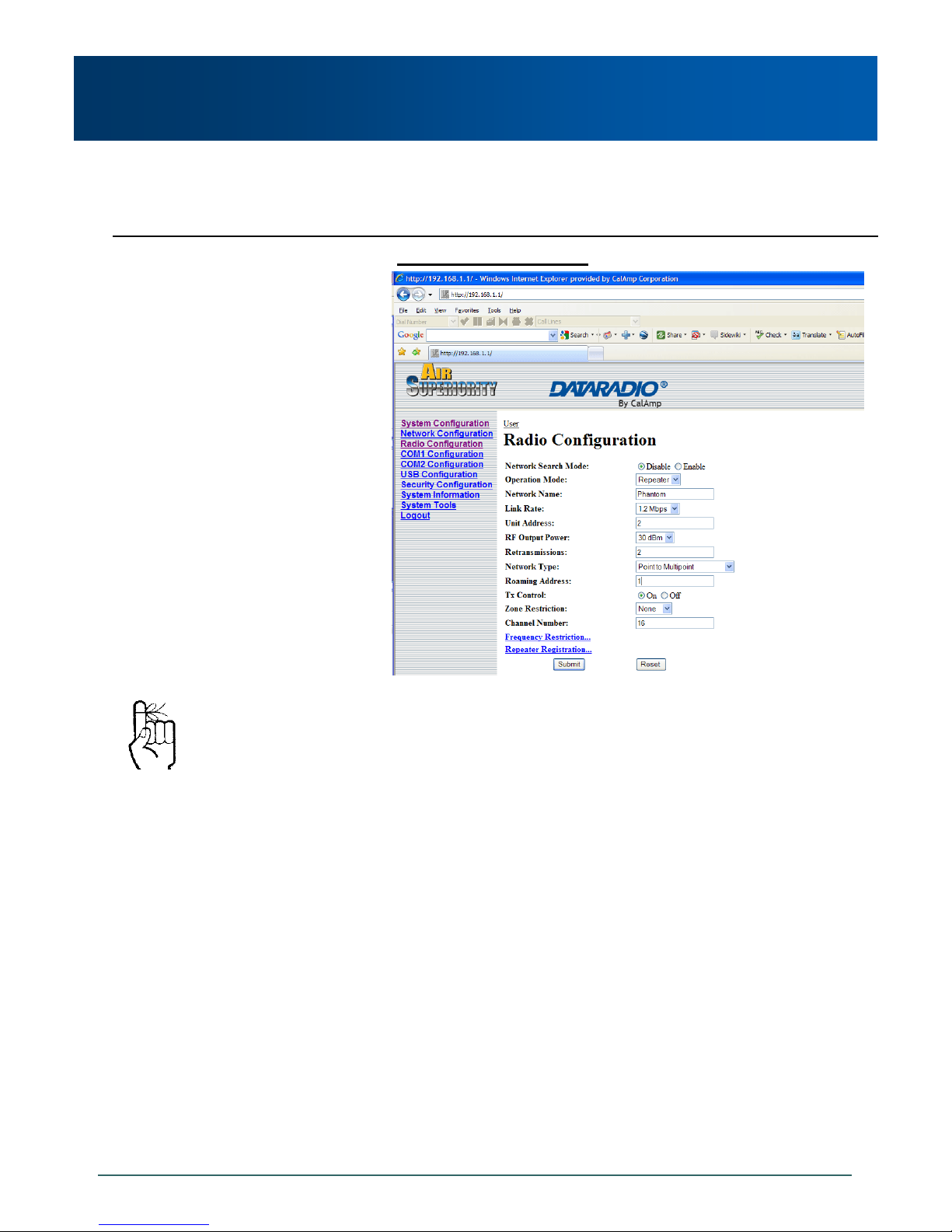
Example 5.2.1
A 4-node network consisting of a Master, 1 Repeater, and 2
Remotes. 1 Remote is to communicate with the Master through a
Repeater; the other is to communicate directly with the Master.
Refer to Section 6.1.5 for
important information regarding
the configuration of a PMP
Master’s Retransmissions.
Image 5-3: PMP Example 5.2.1: Master
There is no DESTINATION UNIT displayed as, in PMP,
the DESTINATION is preset to 65535: the
BROADCAST address (‘multipoint’).
RETRANSMISSIONS are set to 0. Refer to Section
6.1.5 for more information.
There is a REPEATER in this example network,
therefore the MASTER’s ‘Repeater’ configuration
option is set to Yes.
Page 28
Phantom II
© CalAmp
28
5.1 Network Topologies
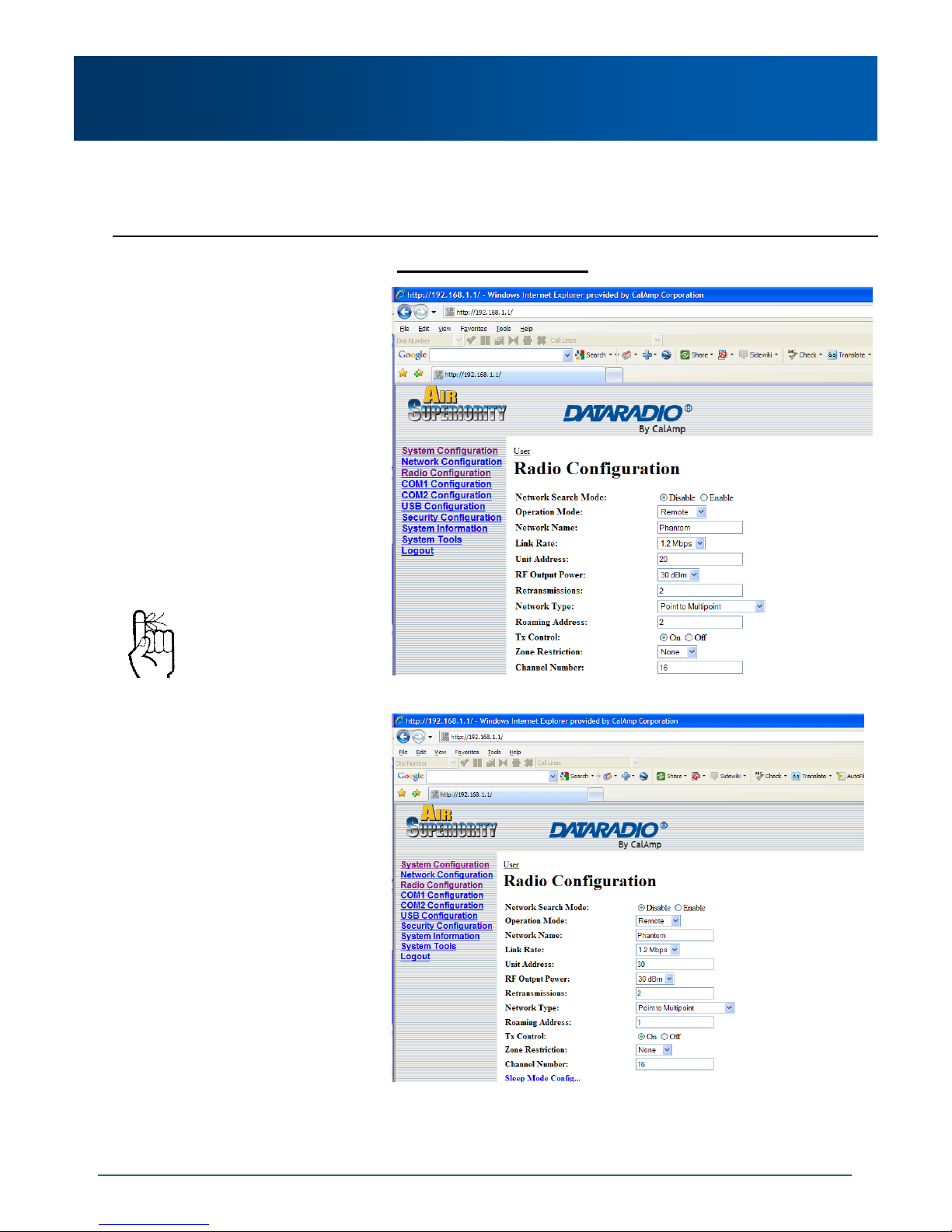
Example 5.2.1 (continued)
Image 5-4: PMP Example 5.2.1: Repeater
When bench testing PMP with a
REPEATER in the network,
configure the REMOTE to
synchronize to the REPEATER
via the REMOTE’s ROAMING
ADDRESS field. If this is not
done, with the REMOTE in close
proximity to the MASTER and its
ROAMING set as 1 (default), the
REMOTE will simply synchronize
with (and pass data directly to)
the MASTER, bypassing the
REPEATER altogether.
On the following page are the configurations for the REMOTES.
The ROAMING address for the REPEATER is set to 1:
the UNIT ADDRESS of the MASTER. This means that
this REPEATER will synchronize to, and communicate
directly with, the MASTER.
There is no DESTINATION UNIT field for remote units
in a PMP network: the destination is predefined as
‘1’ (the MASTER ‘point’).
Remote 20’s ROAMING ADDRESS is set to 2, the
UNIT ADDRESS of the REPEATER. This Remote will
synchronize to the Repeater and communicate via the
Repeater to the Master.
Remote 30’s ROAMING ADDRESS is set to 1 (the
UNIT ADDRESS of the MASTER): it will synchronize
to, and communicate directly with, the MASTER.
Page 29
Phantom II
© CalAmp
29
5.0 Network Topologies
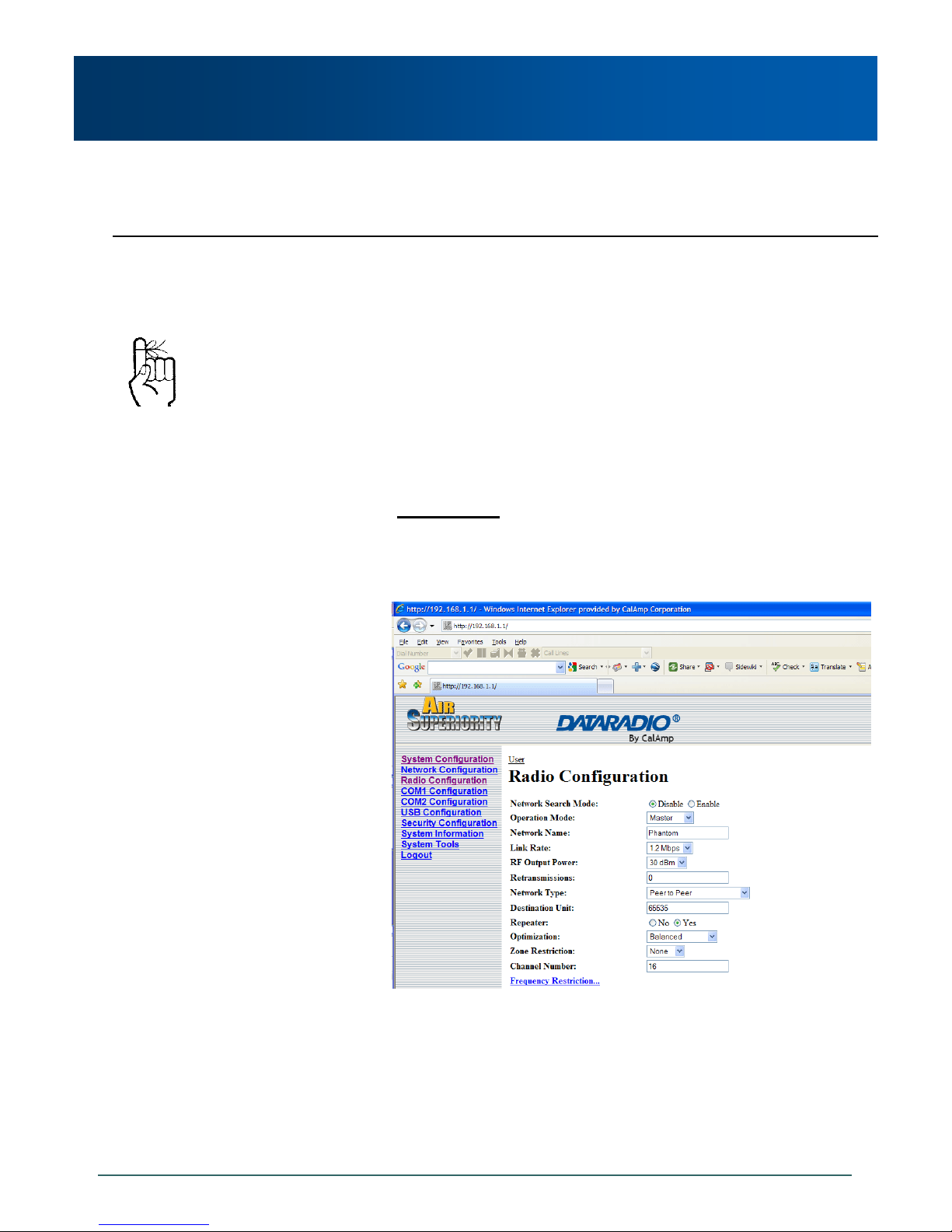
Example 5.2.1 (continued)
Each modem in any network
must have a unique Unit
Address.
Image 5-5: PMP Example 5.2.1: Remote 20
Image 5-6: PMP Example 5.2.1: Remote 30
Page 30
Phantom II
© CalAmp
30
5.0 Network Topologies
5.3 Peer-to-Peer (P2P)
P2P mode is used for communications between pairings of remote
modems.
e.g. Remote 20 can exchange data with (only) Remote 30,
Remote 21 can exchange data with (only) Remote 35, etc.
A P2P network requires a Master
modem.
The data being transmitted from
one Remote to another in P2P
mode is transferred via the
Master.
The Master will resend the data incoming to it from both Remotes to
both/all Remotes; one Remote’s data has a Destination Unit being
the other Remote and vice versa.
Example 5.3.1
A device located at a pump station must communicate bidirectionally with another device at a water tank. The MASTER
Phantom II must reside in an office at a separate location.
Image 5-7: P2P Example 5.3.1: Master
All Phantom II modems within a particular network must be configured to have the same Network Type.
continued...
Page 31

Phantom II
© CalAmp
31
5.0 Network Topologies
Example 5.3.1 (continued)
Image 5-8: P2P Example 5.3.1: Remote 25
Image 5-9: P2P Example 5.3.1: Remote 35
Page 32

Phantom II
© CalAmp
32
5.1 Network Topologies
5.4 Everyone-to-Everyone (E2E)
E2E mode is used for communications between all remote modems.
i.e. data from every modem is broadcast to every other
modem in the network.
An E2E network requires a
Master modem.
The data being transmitted from
remote units in an E2E network
travels to the Master and is then
re-broadcast to all other remotes.
Considering the amount of data re-broadcasting (via the Master), it
is a very bandwidth-intensive network topology.
Example 5.4.1
1 Master and 3 remote units must all communicate with each other.
Image 5-10: E2E Example 5.4.1: Master
There is no DESTINATION UNIT configuration option
as the DESTINATION is predefined to be the broadcast
address (65535) when in E2E mode.
Page 33

Phantom II
© CalAmp
33
5.0 Network Topologies
Example 5.4.1 (continued)
Each unit must have its own
unique Unit Address.
Image 5K: E2E Example 5.4.1: Remote
The Remotes will all be configured as per the above screen capture, with the exception of the UNIT ADDRESS. Each Remote (of
the 3 in this example) must have its own unique UNIT ADDRESS,
e.g. 50, 51, and 52.
Page 34

Phantom II
© CalAmp
34
6.0 Configuration
6.1
Overview
The following factors must be considered when preparing to
configure the modems:
the application
network topology
physical distribution of the network
data interface requirements
Components involved in the configuration process of the Phantom II:
interfacing with the modem, and
selecting and inputting the desired operational
parameters
All configuration of the Phantom II is accomplished with a PC as
shown in Section 2.0 There are no DIP switches to set; switches
which may subsequently become inadvertently misadjusted or
intermittent.
Page 35

Phantom II
© CalAmp
35
6.0 Configuration
6.1.1 Logon Window
Upon successfully accessing the Phantom II using a Web Browser,
the Logon window will appear.
For security, do not allow the
web browser to remember the
User Name or Password.
Image 6-1: Logon Window
The factory default User Name is: admin
The default password is: admin
It is advisable to change the login
Password (see Section 6.1.6.1).
Do not FORGET the new
password as it cannot be
recovered.
Note that the password is case sensitive. It may be changed
(discussed further along in this section), but once changed, if
forgotten, may not be recovered.
Page 36

Phantom II
© CalAmp
36
6.1 Configuration
When entered, the password appears as ’dots’ as shown in the
image below. This display format prohibits others from viewing the
password.
The ‘Remember my password’ checkbox may be selected for
purposes of convenience, however it is recommended to ensure it
is deselected - particularly once the unit is deployed in the field for one primary reason: security.
Image 6-2: Logon Window With Password Input
Soft Buttons
processing.
Cancel
OK
Inputs the selected values into the Phantom II for
Cancels the logon process.
Page 37

Phantom II
© CalAmp
37
6.0 Configuration
6.1.2
Welcome Window
The Welcome window displays the specific Phantom II’ name
(entered as the Radio Description in the System Configuration
menu). This name quickly confirms the ’identity’ of the unit being
perused and appears in all menu windows.
Image 6-3: Welcome Window
Also displayed is various ‘version’ information:
Hardware Version - applicable to the motherboard of
the Phantom II
Software Version - this software resides on the
motherboard and is also referred to as the unit’s
’firmware’
Page 38

Phantom II
© CalAmp
38
6.0 Configuration
6.1.3 System Configuration
As per the previous section, the Radio Description is defined within
this menu, as are an assortment of other configuration options.
Image 6-4: System Configuration Window
System Operation Mode
The radio button options presented here determine whether the
Phantom II unit will operate at a BRIDGE or a ROUTER. Only a
MASTER unit should ever be configured as a router.
Select the System Operation Mode ‘first’, i.e. prior to configuring
other options within the unit.
Values
Bridge
Bridge
Router
Page 39

Phantom II
© CalAmp
39
Values
6.0 Configuration
The Radio Description must not
be confused with the Network
Name (Radio Configuration
menu). The Network Name
MUST be exactly the same on
each unit within a Phantom II
network.
Radio Description
The Radio Description is simply a convenient identifier for a specific
Phantom II, e.g. Pump Station 5, 123 Main Street, etc. This feature
is most welcome when accessing units from afar with large
networks: a convenient cross-reference for the unit’s IP address.
This ‘name’ appears in all menu windows. It has no bearing on the
unit’s operation.
User
up to 30 characters
Date (yyyy-mm-dd)
The calendar date may be entered in this field. Note that the
entered value is lost should the Phantom II lose power for some
reason.
Values
valid date values, where
yyyy = 4-digit year
mm = 2-digit month
dd
= 2-digit day
Time (hh:mm:ss)
The calendar date may be entered in this field. Note that the
entered value is lost should the Phantom II lose power for some
reason.
Values
valid time values, where
hh
mm = 2-digit minutes
ss = 2-digit seconds
= 2-digit hours
Page 40

Phantom II
© CalAmp
40
Values
6.0 Configuration
UTC Time Offset (+/-hh:mm)
Input the Universal Coordinated Time offset in this field, if so
desired. + indicates that local time is ahead of UTC time; - behind.
00:00
valid time values, where
hh
mm = 2-digit minutes
Console Timeout (s)
This value determines when the console connection (made via
COM2) will timeout after becoming inactive.
= 2-digit hours
Values
60
0-65535 (seconds)
Traffic Watchdog Timer (s)
The Traffic Watchdog Timer will reset the unit if there has been no
RF activity in the configured time. 0 = Disabled (default)
Values
0
0-65535 (seconds)
Page 41

Phantom II
© CalAmp
41
Values
6.1 Configuration
System Default Button
Enabled by default, when the CONFIG button on the front of the
Phantom II is held down for 10s while the unit is powered up, the
unit will reset and all settings will be reset to factory defaults. When
disabled the unit will reset, but the setting will not be overwritten.
Enable
Disable
Soft Buttons
Synchronize with NTP Server
Useable to have related parameters on this page updated
with current time values when valid NTP Server information
has been configured and the service is enabled within the
modem (see Section 6.1.4.2 for additional information).
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 42

Phantom II
© CalAmp
42
6.0 Configuration
6.1.4 Network Configuration
The Network Configuration menu consists of a number of
submenus, all of which provide various options pertaining to
configuring the units to be part of an IP network. These settings do
not effect the ‘radio’ communications network aspect of the system,
however, be mindful of the Network Type (Radio Configuration
menu) as that dictates the possibilities for the flow of network data.
For a basic implementation, only the Local IP Configuration
(submenu) options need to be defined.
Image 6-5: Network Configuration, Top Level Menu
The Ethernet MAC address (as displayed above) is that of the
ETHERNET interface located at the rear of the Phantom II.
The Wireless MAC address is for internal purposes.
Page 43

Phantom II
© CalAmp
43
6.1 Configuration
6.1.4.1 Local IP Configuration
6.1.4.1.1 Bridge
This submenu, along with Radio Configuration settings, are the
minimum which must be considered when implementing any
Phantom II network.
It must be determined if the unit is to be either:
assigned an IP address (by a DHCP server), or
DHCP: Dynamic Host
Configuration Protocol may be
used by networked devices
(Clients) to obtain unique
network addresses from a DHCP
server.
Advantage:
Ensures unique IP addresses are
assigned, from a central point
(DHCP server) within a network.
Disadvantage:
The address of a particular
device is not ‘known’ and is also
subject to change.
STATIC addresses must be
tracked (to avoid duplicate use),
yet they may be permanently
assigned to a device.
Once the above is ascertained, the items within this submenu may
be configured.
given a static (unchanging) IP address.
Image 6-6: Network Configuration (Bridge), Local IP Configuration
Submenu
IP Address Mode
If ‘static’ is selected, the three following fields (see Image 6F) are to
be manually populated with values which will suit the network/
devices to which the Phantom II is connected.
continued...
Page 44

Phantom II
© CalAmp
44
6.0 Configuration
If DHCP mode is selected, but
there is no DHCP server
available, after the DHCP timeout
period the units will default to
function simply as a ’wireless
bridge’.
IP Address Mode (continued)
If ‘DHCP’ is selected, the three following fields (see Image 6F) will
be automatically populated by the DHCP server. The DHCP
Timeout value may be manually modified from the factory default
value.
Note that the factory default setting is static.
Values
static
static
dhcp
IP Address
If DHCP is selected (see above), a unique IP address will be
assigned to the Phantom II; if STATIC IP address mode has been
selected, enter a suitable value for the specific network.
Within any IP network, each
device must have its own unique
IP address.
A SUBNET MASK is a bit mask
that separates the network and
host (device) portions of an IP
address.
The ‘unmasked’ portion leaves
available the information required
to identify the various devices on
the subnet.
Subnet Mask
For a small private network with IP addresses appearing similar to
192.168.1.xx (Class C address), the standard 255.255.255.0
subnet mask may be applicable.
If DHCP mode is selected (see above/top), the DHCP server will
populate this field.
Values
192.168.1.254
valid value is specific to the
network
Values
255.255.255.0
valid value is specific to the
network
Page 45

Phantom II
© CalAmp
45
6.0 Configuration
IP Gateway
If the Phantom II devices are integrated into a network which has a
defined gateway, then, as with other hosts on the network, this
gateway’s IP address will be entered into this field. If there is a
DHCP server on the network, and the IP Address Mode (see
previous page) is selected to be DHCP, the DHCP server will
populate this field with the appropriate gateway address.
A GATEWAY is a point within a
network that acts as an entrance
to another network.
In typical networks, a router acts
as a gateway.
In a very small network (e.g. point-to-point, and STATIC IP Address
Mode), the gateway value is not critical. The IP address of the most
significant device on the overall network may be entered, or, if only
two Phantom II modems are being used, make the gateway of
Phantom II No. 1 = IP address of Phantom II No. 2; gateway of
Phantom II No. 2 = IP address of Phantom II No. 1. The idea
behind this approach is: If a Phantom II at ‘one end’ of a wireless
link receives a packet it is unsure where to send, send it to the
other end of the wireless link (i.e. the other Phantom II) where it
was quite likely destined.
A simple way of looking at what the gateway value should be is: If
a device has a packet of data is does not know where to send, send
it to the gateway. If necessary - and applicable - the gateway can
forward the packet onwards to another network.
192.168.1.1
valid value is specific to the
network
DHCP Timeout
This value determines for how long the Phantom II will await to
receive information from a DHCP server. If this timeout expires, the
unit will assign itself a random Class D IP address (and subnet
mask) and function simply as a wireless bridge.
Values
60
1-65535 (seconds)
Values
Page 46

Phantom II
© CalAmp
46
6.1 Configuration
DNS Mode
The setting determines whether the Phantom II unit will have its
DNS Server information entered manually (static) or if it will obtain
the information (provided it is available) via the connected network.
Values
static
automatic
static
Preferred DNS Server
If DNS Mode is static, enter valid IP Address of accessible
Preferred DNS Server in this field.
Values
0.0.0.0
valid DNS Server IP address
Alternate DNS Server
If DNS Mode is static, enter valid IP Address of accessible Alternate
DNS Server in this field.
Values
0.0.0.0
valid DNS Server IP address
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 47

Phantom II
© CalAmp
47
6.0 Configuration
Only the MASTER Phantom II
unit may be configured as a
Router.
6.1.4.1 Local IP Configuration
6.1.4.1.2 Router
If the Phantom II unit has been configured as a Router (under the
System Configuration menu), the Network Configuration will
present some additional options to those presented if the unit was
configured as a Bridge.
The Ethernet Port IP Configuration applies to the ‘wired’ port (at
rear of Phantom II unit), which may also be considered as the WAN
(Wide Area Network) port.
The Wireless Port IP Configuration applies to the LAN (Local Area
Network): the LAN consists of the devices, and Phantom II units,
connected to each other via the wireless (radio) network.
Image 6-7: Network Configuration (Router), Local IP Configuration
Submenu
Refer to the preceding section for configuring the Ethernet Port,
keeping in mind that the settings apply only to the ‘wired’
connection of the MASTER unit.
There are two other options to be discussed further on the following
pages:
Wireless Port IP Configuration
VPN Configuration
Page 48

Phantom II
© CalAmp
48
Values
6.0 Configuration
6.1.4.1.2.1 Wireless Port IP Configuration
Image 6-8: Network Configuration (Router), Wireless Port IP
Configuration Submenu
IP Address
This address MUST be STATIC (i.e. DHCP is not applicable).
Within any IP network, each
device must have its own unique
IP address.
192.168.2.1
valid value is specific to the
network, typically a Class C
private IP
Subnet Mask
For a small private network with IP addresses appearing similar to
192.168.1.x (Class C address), the standard 255.255.255.0 subnet
mask may be applicable.
Values
255.255.255.0
valid value is specific to the
network
Page 49

Phantom II
© CalAmp
49
6.1 Configuration
Preferred DNS Server
If applicable, enter valid IP address of Preferred DNS Server which
exists within the LAN (the wireless subnet) in this field.
Values
0.0.0.0
valid DNS Server IP address
Alternate DNS Server
If applicable, enter valid IP address of Alternate DNS Server which
exists within the LAN (the wireless subnet) in this field.
Values
0.0.0.0
valid DNS Server IP address
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 50

Phantom II
© CalAmp
50
6.0 Configuration
6.1.4.1.2.2 VPN Configuration
VPN: Virtual Private Network. A
communications path connecting
a device on a WAN with a device
on a LAN.
Image 6-9: Network Configuration (Router), VPN Configuration
Submenu
A Virtual Private Network (VPN) may be configured to enable a direct
communications link between one device on the WAN and another
on the LAN.
VPN Status
Enable (default) enables the service; Disable disables it.
Enable
Disable
VPN Admin Password
Select a unique password of 32 characters maximum, casesensitive.
Values
Values
admin
32 characters maximum
Enable
Page 51

Phantom II
© CalAmp
51
6.1 Configuration
VPN Admin Repeat Password
Enter the same unique password of 32 characters maximum, casesensitive, which was entered in the preceding/above field.
Values
admin
32 characters maximum
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 52

Phantom II
© CalAmp
52
6.0 Configuration
6.1.4.2 NTP Server Configuration
The Network Time Protocol (NTP) feature may be ENABLED,
provided there is an NTP server available and its IP address or
’name’ is entered in the appropriate field.
NTP may be used to synchronize
the time in the Phantom II within
a network to a reference time
source.
Image 6-10: Network Configuration, NTP Server Config. Submenu
NTP Server Status
Note that if NTP Server Status is ENABLED, the ‘Synchronize with
NTP Server’ soft button on the System Configuration menu will be
available for use.
Leave as DISABLED (default) if a server is not available.
Values
Disable
Disable
Enable
Page 53

Phantom II
© CalAmp
53
6.1 Configuration
NTP Server (IP/Name)
IP address or domain name for NTP server (on local LAN or
website (provided that Internet access is available)) is to be entered
in this field if the NTP Server Status is configured as ENABLED.
Values
0.0.0.0
valid NTP server IP address
or ‘name’
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 54

Phantom II
© CalAmp
54
6.0 Configuration
6.1.4.3 DHCP Server Configuration
There is a difference in how the DHCP Server operates based on
whether the Phantom II unit (Master) is configured to function as a
bridge or a router.
6.1.4.3.1 Bridge
The Phantom II Master may be configured to provide dynamic host
control protocol (DHCP) service to all attached (either wired or wireless-connected) devices.
Configuration field descriptions are discussed in the following section.
6.1.4.3.2 Router
A Phantom II Master may be configured to provide dynamic host
control protocol (DHCP) service for an entire LAN (or section
thereof). Recall that the LAN consists of wirelessly connected Phantom II units and those IP addressable devices which are connected
to them. If this feature is to be utilized, it would be enabled on the
Master Phantom II unit, noting that such a DHCP Server service
must not be enabled on any other Phantom II units or devices which
reside on the same network segment.
With this service enabled on the Master, it can assign IP addresses
(as well as subnet mask and gateway) to the LAN radios and IP devices attached to them provided they are set for DHCP as opposed
to static.
The DHCP Server may also be used to manage up to five MAC address bindings. MAC address binding is employed when certain devices are to be assigned specific IP addresses (effectively issuing
them a ‘static’ IP address). Such devices are identified by their
unique MAC address: the DHCP Server ensures that a specified IP
address is assigned to a specific MAC address (hence, device - either a Phantom II or other IP-based device attached to the LAN).
Page 55

Phantom II
© CalAmp
55
Values
6.0 Configuration
Image 6-11: Network Configuration, DHCP Server Config.
Prior to enabling this service,
verify that there are no other
devices - either wired (e.g. LAN)
or wireless (e.g. another
Phantom II) with an active DHCP
SERVER service.
(The Server issues IP address
information at the request of a
DHCP Client, which receives the
information.)
Server Status
Choose to enable or disabled the DHCP Server service. Note that
there can only be one such service residing on a network segment otherwise, duplicate IP addresses could be assigned and exist on a
network, which would result in problems. Devices on the network,
which are intended to receive IP address information from this
DHCP Server, must have their local IP settings set for ‘DHCP’ (as
opposed to ‘static’)
Disable
Disable
Enable
Page 56

Phantom II
© CalAmp
56
6.0 Configuration
Server Subnet
Not to be confused with the Server Netmask (see below). Enter the
network’s ‘root’ address, e.g. if devices are to be assigned
addresses such as 192.168.1.5 and 192.168.1.6, enter 192.168.1.0
in this field.
Values
192.168.2.0
valid server subnet value for
specific network
Server Netmask
In this field, input the subnet mask which is to be applied to the
network. For basic, small, private networks, a Class C subnet mask
such as 255.255.255.0 could be used.
Values
255.255.255.0
valid subnet mask value for
specific network
Starting Address
This is the starting (‘lower boundary’) IP address of the range of IP
addresses (also known as ’IP address pool’) to be issued by the
DHCP Server to the applicable devices on the network.
Values
192.168.2.5
IP address as per above
Page 57

Phantom II
© CalAmp
57
WINS Address
DNS Address
Values
6.0 Configuration
Ending Address
This is the ending (‘upper boundary’) IP address of the range of IP
addresses to be issued by the DHCP Server to the applicable
devices on the network.
Values
192.168.2.239
IP address as per above
Gateway Address
DNS: Domain Name Service is
an Internet service that translates
easily- remembered domain
names into their not-so-easilyremembered IP addresses.
Being that the Internet is based
on IP addresses, without DNS, if
one entered the domain name
www.calamp.com, for example,
into the URL line of a web
browser, the webs ite ‘could not
be found’.
Input the address of the desired gateway.
192.168.2.1
IP address as per above
Input the IP address of the Domain Name Service (DNS) to be
provided by this DHCP Server.
WINS: Windows Internet
Naming Service keeps track of
which IP address is assigned to
which computer on a Windows
network: a process known as
name resolution. It automatically
updates, which is particularly
important on a network where
DHCP is in use.
0.0.0.0
Valid DNS IP address
Windows Internet Naming Service (WINS) address to be provided
by this server.
Values
0.0.0.0
Valid WINS IP address
Values
Page 58

Phantom II
© CalAmp
58
Values
6.0 Configuration
New Binding MAC
In this field, input the MAC address (in specified format) of the
device to which a specific IP address is to be bound.
For the Phantom II, the MAC address of the unit may be found on
the label on the bottom of the unit, or it may be viewed on the
Network Configuration menu of that unit.
An address binding is a mapping
between a specific IP address
and the MAC address of a
specific client.
00:00:00:00:00:00
MAC address of target
device
New Binding IP
Enter the IP address - from within the range identified with the
Starting Address and Ending Address parameters input previously which is to be ‘bound’ to the MAC address identified in the New
Binding MAC field (described above).
Values
0.0.0.0
IP address from within range
identified in Starting Address
and Ending Address fields
Page 59

Phantom II
© CalAmp
59
6.1 Configuration
Soft Buttons
Add
After entering a New Binding MAC address and a New
Binding IP address, click this soft button to ADD this new
binding relationship.
Once ‘added’, the new relationship will be given a number
(e.g. Bound 1) and appear at the lower portion of the DHCP
Server Config. menu display, showing both the MAC and
corresponding IP address.
Note that the ADD action must be followed by SUBMIT for
the changes to be written to the Phantom II’ memory.
Delete
If binding relationships are present, the drop down box (to
left of Delete soft button) may be used to select a particular
binding, and the DELETE soft button used to delete it.
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 60

Phantom II
© CalAmp
60
6.1 Configuration
6.1.4.4 SNMP Agent Configuration
The Phantom II may be configured to operate as a Simple Network
SNMP: Simple Network
Management Protocol provides
a method of managing network
devices from a single PC running
network management software.
Managed networked devices are
referred to as SNMP agents.
Management Protocol (SNMP) agent.
Network management is most important in larger networks, so as to
be able to manage resources and measure performance.
SNMP may be used in several ways:
configure remote devices
monitor network performance
detect faults
audit network usage
detect authentication failures
A SNMP management system (a PC running SNMP management
software) is required for this service to operate. This system must
have full access to the Phantom II network. Communications is in
the form of queries (information requested by the management system) or traps (information initiated at, and provided by, the SNMP
agent in response to predefined events).
Objects specific to the Phantom II are hosted under private enterprise number 21703.
An object is a variable in the device and is defined by a Management
Information Database (MIB). Both the management system and the
device have a copy of the MIB. The MIB in the management system
provides for identification and processing of the information sent by a
device (either responses to queries or device-sourced traps). The
MIB in the device relates subroutine addresses to objects in order to
read data from, or write data to, variables in the device.
An SNMPv1 agent accepts commands to retrieve an object, retrieve
the next object, set an object to a specified value, send a value in
response to a received command, and send a value in response to
an event (trap).
SNMPv2c adds to the above the ability to retrieve a large number of
objects in response to a single request.
SNMPv3 adds strong security features including encryption; a shared
password key is utilized. Secure device monitoring over the Internet
is possible. In addition to the commands noted as supported above,
there is a command to synchronize with a remote management station.
Page 61

Phantom II
© CalAmp
61
6.0 Configuration
Image 6-12: Network Configuration, SNMP Agent Config.
SNMP Operation Mode
If disabled, no SNMP service is provided from the device. Enabled,
the device - now an SNMP agent - can support SNMPv1, v2, & v3.
Values
Disable
Disable
V1&V2&V3
Read Only Community Name
Effectively a plain-text password mechanism used to weakly
authenticate SNMP queries. Being part of the community allows the
SNMP agent to process SNMPv1 and SNMPv2c requests. This
community name has only READ priority.
continued...
Page 62

Phantom II
© CalAmp
62
6.0 Configuration
Read Only Community Name (continued)
Values
public
character string
Read Write Community Name
Effectively a plain-text password mechanism used to weakly
authenticate SNMP queries. Being part of the community allows the
SNMP agent to process SNMPv1 and SNMPv2c requests. This
community name has only READ/WRITE priority.
Values
private
character string
SNMP V3 User Name
Defines the user name for SNMPv3.
Values
V3user
character string
V3 User Read Write Limit
Defines accessibility of SNMPv3; select either Read Only or Read/
Write priority. If Read Only is selected, the SNMPv3 user may only
read information; if Read Write is selected, the SNMPv3 user may
read and write (set) variables.
Values
Read Only
Read Only
Read Write
Page 63

Phantom II
© CalAmp
63
6.0 Configuration
V3 User Authentication Level
Defines SNMPv3 user’s authentication level.
NoAuthNoPriv: No authentication, no encryption.
AuthNoPriv:
AuthPriv:
Authentication, no encryption.
Authentication, encryption.
Values
NoAuthNoPriv
NoAuthNoPriv
AuthNoPriv
AuthPriv
V3 Authentication Password
SNMPv3 user’s authentication password. Only valid when V3 User
Authentication Level set to AuthNoPriv or AuthPriv (see above).
Values
00000000
character string
V3 Authentication Password
SNMPv3 user’s encryption password. Only valid when V3 User
Authentication Level set to AuthPriv (see above).
Values
00000000
character string
Page 64

Phantom II
© CalAmp
64
6.0 Configuration
SNMP Trap Version
Select which version of trap will be sent should a failure or alarm
condition occur.
Values
V1 Traps
V1 Traps
V2 Traps
V3 Traps
V1&V2 Traps
V1&V2&V3 Traps
Auth Failure Traps
If enabled, an authentication failure trap will be generated upon
authentication failure.
Disable
Disable
Trap Community Name
The community name which may receive traps.
Values
TrapU ser
character string
Values
Enable
Page 65

Phantom II
© CalAmp
65
6.1 Configuration
Trap Manage Host IP
Defines a host IP address where traps will be sent to (e.g. SNMP
management system PC IP address).
Values
0.0.0.0
applicable host’s IP address
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 66

Phantom II
© CalAmp
66
6.1 Configuration
6.1.4.5 Bridge Configuration
In most deployments, Spanning Tree Protocol (STP) will not be
required. It does consume a small amount of bandwidth. The
default is ‘Off’.
STP: Spanning Tree Protocol is
a link management protocol
which will accommodate the
availability of redundant data
paths but inhibit the possibility of
a loop being created: a loop
could create endless traffic
‘around’ a LAN, consuming much
of the bandwidth.
Note that this menu item will not appear if the Phantom II unit is
configured to be a router.
Image 6-13: Network Configuration, Bridge Config. Submenu
Spanning Tree Protocol Status
Selection of STP operational status within the Phantom II: On or
Off.
Values
Off
On
Off
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 67

Phantom II
© CalAmp
67
6.0 Configuration
6.1.4.6 Quality of Service
Quality of Service (QoS) may be applied to various data which enter
the Phantom II. This section describes configuring QoS for data
which enters via the Ethernet port.
QoS: Quality of Service is
applied to networks where it is
desired to give particular data
traffic/protocol(s) priority over
other data traffic.
Image 6-14: Network Configuration, Quality of Service Submenu
Quality of Service Status
If Enabled, the defined protocols and ports will have the QoS
service applied to them.
Values
Disable
Disable
To define particular ports, protocol, and priority to be assigned, see
the example of such a configuration exercise on the following page.
Enable
Page 68

Phantom II
© CalAmp
68
6.1 Configuration
Example 6.1.4.6.1
Assume that we want to add high priority to TCP traffic on Port
8080:
In the IP Port field, enter 8080.
Select the radio button for TCP.
Select the radio button for High Priority.
Click the ADD NEW soft button.
Click the SUBMIT soft button.
The following screen capture shows the result of the above actions:
Image 6-15: Network Configuration, QoS Example
The mini window shows port 8080, TCP traffic, as having High
Priority. To apply the configuration: select Enable and SUBMIT.
As ports are defined, the mini window and list boxes (specific to
Priority) become populated. To DELETE any defined port, simply
select it via the appropriate list box and click the DELETE soft
button.
Page 69

Phantom II
© CalAmp
69
6.1 Configuration
6.1.4.7 L2 Mesh
L2 stands for layer 2. When enabled, forwarding is performed at the
MAC layer (layer 2) on the master unit. This allows Remote-toRemote communications possible. The master unit forwards packets
that are not destined for its own LAN back to the wireless interface.
Packets that contain the master unit destination MAC address are
forwarded to the master unit’s Ethernet port, not the wireless
interface. In comparison to Everyone-to-Everyone mode, this mode
consumes less bandwidth and therefore is more efficient.
Values
Disable
Disable
Enable
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 70

Phantom II
© CalAmp
70
6.0 Configuration
6.1.5 Radio Configuration
The parameters within the Radio Configuration menu must be input
properly; they are the most basic requirement for radio network
connectivity.
Prior to configuration, the network topology must be known (see
Section 5.0); the role (operating mode) of the specific Phantom II
must also be known.
Image 6-16: Radio Configuration Menu (upper portion)
Network Search Mode
The above screen capture depicts Radio Configuration menu option
with Network Search Mode disabled. The screen capture shows
what configuration options are available when Network Search
Mode is enabled.
continued...
Page 71

Phantom II
© CalAmp
71
6.0 Configuration
Network Search Mode (continued)
Image 6-17: Radio Configuration Menu (upper portion), with
Network Search Mode Enabled
With Network Search Mode enabled, Master units with the same
authentication key may be found by Remote units even if they have
different network names.
This feature, which must be enabled on all participating units,
allows for ‘roaming’ between networks.
Values
Disable
Disable
Enable
Page 72

Phantom II
© CalAmp
72
6.0 Configuration
Operation Mode
Select the mode of operation for the Phantom II: Master, Repeater,
or Remote. A Phantom II may be configured for any role required
within a radio network. This is convenient for reasons of familiarity
with any/all units, as well as for hardware sparing purposes.
Master: Only one per network. For all Network Types data either
The selected Operation Mode will
effect which configuration options
are presented.
i.e. There are settings which
apply to a Master which do not
apply, and are therefore not
presented, for a Remote.
originates at, is destined to, or ‘passes through’ the Master.
Repeater: May act simply as a ‘Repeater’ to store and forward
data to/from an upstream unit to/from a downstream unit (e.g. when
there is a long distance between the latter units), or, may act as a
Repeater/Remote in which case the above function is performed
AND the unit may also exchange data as a Remote within the
network.
If 1 or more repeaters are to be in a network, on the Master (only)
the Repeater(s) YES configuration must be selected.
If 2 or more repeaters are to be in a network: the above ‘YES’
setting applies as does the requirement for Repeater Registration
(discussed further on in this section).
Remote: Interfaces with remote devices and communicates with
Master either directly or via Repeater(s). Communications between
2 or more Remotes is possible - through the Master - see
Network Types (further on in this section, and also refer to Section
5.3, 5.4).
Remote
Master
Repeater
Remote
Authentication Key
The Authentication Key is used to define the network search group:
Masters with the same key can be found by Remotes with different
Network Names.
Values
continued...
Page 73

Phantom II
© CalAmp
73
6.0 Configuration
Authentication Key (continued)
Values
Public
Character string
Network Name
All Phantom II modems in a given network must have the same
Network Name. This unique network address is not only a security
feature for a particular network, but also allows other networks -
Change the default value for the
Network Name to something
unique for your network. Do this
for an added measure of security
and to differentiate your network
from others which may be
operating nearby.
with their own unique network address - to operate in the same
area without the possibility of undesired data exchange between
networks.
The Network Name can also be used as the single parameter to
change when a Remote is to ’switch’ from operating between
distinct networks.
The Network Name is also taken into consideration in the frequency
hopping algorithm: change the Network Name and the hopping
pattern will change.
Values
Phantom
character string
Link Rate
This is the RF communications Link Rate. A lower link rate offers
better receive sensitivity performance; a higher link rate, better
throughput. All Phantom II modems in a network must use the
same Link Rate.
Values
1.2 Mbps
1.2 Mbps
345 kbps
Adaptive
Page 74

Phantom II
© CalAmp
74
30
(1000)
20
(100)
21
(125)
22
(160)
23
(200)
24
(250)
25
(320)
26
(400)
27
(500)
28
(630)
29
(800)
Values
6.0 Configuration
If the Operation Mode is set to
MASTER, the Unit Address field
will NOT be displayed in the
Radio Configuration menu.
By setting the unit to Master, its
Unit Address will be 1.
Unit Address
The unit address is, and must be, a unique identifier of each
modem in a network.
The Master has by default, and must retain, a unit address of 1;
65535 is the broadcast address.
Values
number varies
2-65534
RF Output Power
This setting establishes the transmit power level which will be
FCC regulations allow for up to
36dBi effective isotropic
radiated power (EIRP). The
sum (in dBm) of the
transmitted power, the cabling
loss, and the antenna gain
cannot exceed 36dBm.
presented to the antenna connector at the rear of the Phantom II.
Unless required, the RF Output Power should be set not for
maximum, but rather for the minimum value required to maintain an
adequate system fade margin.
dBm (mW equivalent)
Page 75

Phantom II
© CalAmp
75
6.0 Configuration
Retransmissions
This register determines the maximum amount of times that a
packet will be retransmitted (in addition to the initial transmission),
noting the following specific behaviors in various network
In a PMP system, set
Retransmissions to the minimum
value required as, effectively, the
data throughput from Master to
Remotes is divided by 1 plus the
Retransmissions value.
topologies:
PMP: Master will retransmit each data packet the exact number of
times specified in the Retransmissions field; Remote will retransmit
only if necessary, and then only until a given packet is
acknowledged or the value of the Remote’s Retransmissions field is
reached (after which it will discard the packet if retransmission not
successful). *See also ‘PMP with ACK” described in the Network
Type (below).
PTP: Phantom II will retransmit to its counterpart only if necessary,
and to a maximum number of the value specified in its
Retransmissions field. Packet is discarded if retransmissions are
not successful.
Values
1
0-255
Network Type
ALL modems in a network must
have the SAME value for
Network Type.
Defines the type of RADIO network (see Section 5.0 for a detailed
description of network topologies).
In a point-to-multipoint (PMP) network, the Master broadcasts data
to all units, and all remote units send their data (ultimately) to the
Master.
A point-to-point (PTP) network involves a Master and a Remote
(with 0 or more Repeaters between them).
Peer-to-Peer (P2P) supports communication (through the Master)
between 2 (typically remote) units.
In an Everyone-to-Everyone (E2E) network, all units communicate
with all other units, through the Master. Note that this mode is very
bandwidth-intensive.
continued...
Page 76

Phantom II
© CalAmp
76
6.0 Configuration
Keep in mind that the Network
Type determines the path that
data will take.
i.e. In a PMP system, the data
flows from the Master to
Remotes, and from Remotes to
the Master. If a ping to Remote
B was sent to Remote A, it will
not arrive as the data cannot
travel from Remote to Remote.
Similarly, a ping to a Repeater
from a Remote will not arrive
either: the destination for a
Remote in a PMP system is the
Master - not a Repeater, even
though it appears in the data
‘path’ to the Master.
Network Type (continued)
Point-to-Multipoint with ACK is a configuration whereby the Network
functions as a Point-to-Multipoint, but the Retransmissions behave
as a combination of PTP and PMP in that: If retransmissions are
set to 5 (for example) on the Master, and the packets it sends to the
Remotes result in an ACK being received by each of the Remotes
in the network, the Master will not send the data again (refer to the
PMP behavior described in the preceding Retransmissions section).
If, however, the Master does NOT receive an ACK from all Remotes
in the network, it will then revert to sending the data again,
to the maximum number of Retransmissions specified, for a
period of one minute, after which time it will revert to behaving as it
did originally.
This mode of operation is particularly well-suited to fixed PMP
networks when multipoint operation is required as is maximum
throughput.
The selected Network Type will effect the Radio Configuration
menu somewhat, i.e. If Point-to-Multipoint is selected for a Remote,
there is no menu item for a Destination Address as the destination
is - must be - the Master (Unit Address 1).
Values
Point-to-Multipoint
Point-to-Multipoint
Point-to-Point
Peer-to-Peer
Everyone-to-Everyone
PMP with ACK
Page 77

Phantom II
© CalAmp
77
6.0 Configuration
Destination Unit
As the name implies, this register specifies the ultimate destination
for Phantom II data. Different network topologies dictate the
configuration of the Destination Unit (address):
For a Remote in a Point-to-Multipoint network, this menu option will
not appear: by definition, the destination is the Master (UA = 1).
For the Master in PMP, its Destination Unit (Address) is 65535—the
broadcast address as it sends its data to all points.
In a Point-to-Point configuration, the destination is to be specified
(for a Remote: the Master); in the Master’s Radio Configuration,
specify the Unit Address of the Remote Unit to which it is to send its
data.
In Peer-to-Peer, the Remotes are configured with the target peer’s
UA as the Destination Address, the Master with 65535.
In Everyone-to-Everyone, the Destination Address for ALL units is
65535 - the broadcast address - as every unit sends its data to
every other unit (through the Master). E2E is a very bandwidth
intensive network topology.
Values
2
1-65535
Tx Control
This configuration option does not apply to a Master Phantom II.
On (the default) permits the Phantom II to transmit, i.e. RF
emissions are enabled.
Off configures the Phantom II for RECEIVE ONLY. If ‘Off’ is
selected, ‘On’ may only be selected LOCALLY.
Values
On
On
Off
Page 78

Phantom II
© CalAmp
78
6.0 Configuration
Roaming Address
This feature allows a Remote unit to synchronize with a specified
‘upstream’ unit (either Master or Repeater). The options are as
follows:
When bench testing 3 Phantom II
for a Master-Repeater-Remote
link, be sure to set the Rem ote’s
Roaming Address to the Unit
Address (UA) of the Repeater,
and the Repeater’s Roaming
Address to the UA (1) of the
Master.
This will ensure that data is
routed from the Remote through
the Repeater to the Master;
otherwise, if the Remote’s
Roaming Address is left at the
default value of 1, the Remote
will communicate directly with the
Master, bypassing the Repeater
altogether.
65535: With this value as its Roaming Address, a Remote will
synchronize with an upstream unit which has the same Network
Name as the Remote. Should that upstream unit fail, this Remote
will attempt to synchronize with another ’upstream’ unit within the
same network (i.e. same Network Name). This ability is particularly
well-suited to mobile applications.
1-254: In most static (fixed) networks, where there are no
Repeaters, the default value of 1 is maintained: All Remotes
synchronize to the Master (whose unit address is 1).
In networks where Repeaters are present, the value of a Remote’s
Roaming Address typically corresponds to the particular upstream
modem with which a particular Remote is intended to communicate,
e.g. Remote with Unit Address 3 may have a Roaming Address of
2, where the modem with Unit Address 2 is a Repeater between the
Remote and the Master; the Repeater will have a Roaming Address
of 1 as it is to synchronize to the Master.
The Roaming Address dictates to which Phantom II (by Unit
Address (UA)) a Remote (or Repeater) will ’look’ or ’attach to’ for its
upstream signal path.
See the description of Network Profile earlier in this section for
more information about roaming-type options. The Network Profile
allows for roaming between networks whereas the Roaming
Address provides for roaming within a network.
Values
1
65535 full roaming
1-254 specific (fixed) unit
addresses (Master or
Repeater) with which to
associate
Page 79

Phantom II
© CalAmp
79
Values
6.0 Configuration
Repeater
This setting applies to the Master only.
The default value is No, stating there are no Repeaters in the
With one or more Repeaters in
the system, a network’s
throughput is divided in half.
Exercising the option of back-toback ‘Repeaters’ - which
requires 2 Phantom II modems at
a ‘Repeater’ site - eliminates the
division of bandwidth.
If there is more than one
Repeater in a network, the
Repeaters should be ‘registered’.
See ‘Repeater Registration’
further along in this section re
how to accomplish this.
network.
If there are 1 or more Repeaters in the network, configure this
setting as Yes.
No
No
Yes
Page 80

Phantom II
© CalAmp
80
6.0 Configuration
Optimization
This setting applies to the Master only.
‘Balanced’ is the default setting and is typically the best choice for
‘Optimization’. The other options are High Throughput (when
throughput is a priority) and Low Latency (best suited to small
packets).
Optimization is a trade-off between throughput and latency.
Values
20 ms
High Throughput (40 ms)
Balanced (20 ms)
Low Latency (5 ms)
Zone Restriction
Zone restriction dictates within which band (zone) of frequencies
that a particular unit will operate.
Using zones simplifies network deployment by providing a
convenient reference (e.g. Zone 1) within which a given network
can operate, thereby minimizing the potential for internetwork
interference. This is particularly useful when used in conjunction
with Network Search Mode to facilitate minimal interference among
adjacently deployed networks.
The tables on the following page illustrate the various zones and
their associated frequency restrictions. Note that there is a
difference between zone ‘values’ depending on the Wireless Link
Rate selected.
continued…
Page 81

Phantom II
© CalAmp
81
Zone
No.
Restrict From
Start (MHz)
Restrict To
End (MHz)
Restrict From
Start (MHz)
Restrict to
End (MHz)
1
923.200
927.600
2
902.400
902.800
924.000
927.600
3
902.400
903.600
924.800
927.600
4
902.400
904.400
925.600
927.600
5
902.400
905.200
926.400
927.600
6
902.400
906.000
927.200
927.600
7
902.400
906.800
8
912.800
917.200
Zone
No.
Restrict From
Start (MHz)
Restrict To
End (MHz)
Restrict From
Start (MHz)
Restrict to
End (MHz)
1
909.750
926.250
2
902.400
905.250
912.750
926.250
3
902.400
908.250
915.750
926.250
4
902.400
911.250
918.750
926.250
5
902.400
914.250
921.750
926.250
6
902.400
917.250
924.750
926.250
7
902.400
920.250
8
906.750
923.250
6.0 Configuration
Zone Restriction (continued)
Table 6-1: Restricted Bands for UA1 at 345 kbps Link Rate
Table 6-2: Restricted Bands for UA1 at 1.2Mbps Link Rate
Values
None
Zone 1, 2, 3, 4, 5, 6, 7, and 8
Page 82

Phantom II
© CalAmp
82
6.0 Configuration
Channel Number
This setting applies only if the Link Rate is set to 1.2 Mbps.
Channel Number defines the number of channels the unit will hop
on. The minimum number is 4. (Digital Transmission System
(DTS) technology is applied at the 1.2 Mbps link rate.)
(This setting does not apply if the Link Rate is 345 kbps because of
the 64 channels that are available, the unit must hop on exactly 50 there is not option to either increase or decrease this amount.)
Values
16
4-16
Scrolling down the Radio Configuration menu on a remote reveals
further configuration options: Frequency Restriction and Repeater
Registration. Typically the former is not required; the latter only
applies if there are 2 or more Repeaters in your network.
Image 6-18: Radio Configuration Menu (lower portion)
Page 83

Phantom II
© CalAmp
83
Values
Values
6.0 Configuration
Sleep Mode (Remote)
No Sleep: Sleep mode is disabled by default.
Auto Wakeup: Unit will wakeup from activity on serial port,
Ethernet port or radio data, if the Radio Awake Time is a nonzero
value. Power consumption is about 35-45 mA @ 12VDC.
Serial Port Wakeup: Unit will wakeup from serial port or radio data
if Radio Awake Time is nonzero value. Power consumption is about
15-25mA @ 12VDC.
Ethernet Port Wakeup: Unit will wakeup from Ethernet port or
radio data if Radio Awake Time is a nonzero value. Power
consumption is about 30-40mA @ 12VDC.
Power Shutdown: Timer control shutdown mode. Controlled by
Radio Awake Time and Radio Sleep Time parameters. System will
reboot when the radio wakes up. Power consumption is about 1mA
@ 12 VDC.
Values
No Sleep
No Sleep
Auto Wakeup
Serial Port Wakeup
Ethernet Port Wakeup
Power Shutdown
Awake Time
Defines how long the unit will keep awake. If set to 0, the radio will
The Phantom II will enter sleep
mode after 60 seconds when the
system is rebooted.
not wakeup until data is received from the serial or Ethernet port.
0-65535 (seconds)
Page 84

Phantom II
© CalAmp
84
6.0 Configuration
Sleep Time
Defines how long the unit will sleep. If set to 0, the radio will not
enter sleep mode.
0-65535 (seconds)
Idle Time
System idle time before going into sleep mode cycle.
Values
1-65535 (seconds)
Frequency Restriction
By default, the Phantom II will hop on frequencies across the entire
902-928 MHz ISM band. For some applications or within certain
operating environments it may be desired to prohibit the modem
Values
All modems in the network must
have the same frequency
restriction configured within them.
from operating on specific frequencies or range(s) of frequencies.
The modem will not allow ‘too many’ frequencies to be restricted; it
requires a certain amount of bandwidth within which to operate to
comply with regulations.
continued...
Page 85

Phantom II
© CalAmp
85
6.0 Configuration
Frequency Restriction (continued)
The input format is:
UA: channel number, or
UA: channel number-channel number z, or
UA: channel number,<no space>chnl number-chnl number
where UA is the Unit Address, and
channel number is the channel number (not frequency) of
the channel to be restricted.
The input formats above describe single channel, range of
channels, or a combination thereof. A number of input fields may
Use the Radio Channels Noise
Level tool (see Section 6.1.10.4)
to help identify the frequency/
range of possible interfering
signals within the 902-928MHz
ISM band, and then use the
Frequency Restriction feature to
configure the Phantom II to avoid
them.
be used, or a combination of restrictions input in one field.
The image below shows an example of configuring a Phantom II
(with 345 kbps as an available Link Rate) to not operate on
channels 1 through 10.
Image 6-19: Frequency Restriction, 345 kbps
Page 86

Phantom II
© CalAmp
86
Link Rate
Star Freq.
(MHz)
Channel
Space
(MHz)
# of
Channels
345 kbps
902.400
.400
63
1.2 Mbps
903.750
1.500
15
6.0 Configuration
Frequency Restriction (continued)
Channel Numbers can be calculated based on the frequency and
link rate (determines channel spacing).
For 900 MHz Models:
Channel 1 is at 902.4MHz. Therefore, to calculate the frequency of
channel n:
Freq channel n = 902.4 + ((n-1) x CW) MHz.
Use the provided table below to calculate the channel number:
Example:
The frequency of channel 78 of a unit using a link rate of
230kbps is:
Freq channel 78 = 902.4 + ((78-1) x 0.280)
= 902.4 + (77 x 0.280)
= 902.4 + 21.56
= 923.96 MHz
Page 87

Phantom II
© CalAmp
87
6.0 Configuration
Frequency Restriction (continued)
With the Phantom II having the option of, and configured for, a Link
Rate of 1.2 Mbps, the Frequency Restriction input format remains
the same (as for 345 kbps described previously), however, the
Channel Number must be reduced by the number of channels
restricted, i.e. If Channels 1-3 are restricted, the Channel Number is
to be decreased from 16 to 13, as per the following example (image
below):
Image 6-20: Frequency Restriction, 1.2 Mbps
The Frequency Restriction ‘value’ must be input into EVERY
MODEM in a network. Oftentimes the applicable Unit Address (as
input in the format detailed previously) will be ‘1’ - indicating that
that the Master modem - to which other units synchronize - will not
be transmitting on the specified channel(s). All units in the system
will use this information - as input into each one of them - to
generate the appropriate hopping pattern for the network.
Page 88

Phantom II
© CalAmp
88
6.0 Configuration
Repeater Registration (Remote)
In order to ensure that generated hopping patterns are orthogonal
to each other (thereby minimizing possible interference between
network segments), if there is more than 1 Repeater in a network,
ALL Repeaters must be registered in EVERY Phantom II.
The following image depicts an example:
Image 6-21: Repeater Registration
In the above example, there is a total of 3 Repeaters in the system,
with Unit Addresses of 7, 18, and 25. Again, these Repeater UAs
must be added into each/every Phantom II’ Repeater Registration
field.
Format:
x,y,z
where
x, y, and z are Repeater UAs,
Page 89

Phantom II
© CalAmp
89
6.1 Configuration
Soft Buttons
Submit
Write parameter values into Phantom II memory.
Reset
Restore ‘currently’ modified parameter values to those
which were previously written into Phantom II memory.
Page 90

Phantom II
© CalAmp
90
6.0 Configuration
6.1.6
COM1 and COM2 Configuration
The menus ’COM1 Configuration’ and ’COM2 Configuration’ are
used to configure the serial device server for the serial
communications ports:
COM1, the rear DE9 connector on the Phantom II, and
COM2, the front DE9 connector, respectively.
Serial device data may be brought into a LAN network through
TCP, UDP, or multicast; it may also exit the Phantom II network on
another Phantom II’ serial port.
COM1 is a full-featured RS232 interface dedicated to serial data
traffic. It supports hardware handshaking. By default, this port is
enabled.
COM2 is, by default, disabled. In this state, it may be used as the
console port for the text user interface. Enabled, it becomes
another serial port for data traffic. It is a 3-wire (TxD, RxD, and SG)
interface and does not support hardware handshaking.
For brevity, only COM1 is fully detailed in this section; the relative
limitations of COM2 are noted where applicable.
Image 6-22: COM1 Configuration Menu (upper portion)
Page 91

Phantom II
© CalAmp
91
6.0 Configuration
Image 6-23: COM1 Configuration Menu (including lower portion)
Port Status
Select operational status of port. Enabled by default.
*COM2 is Disabled by default. If COM2 is Enabled and there is a
desire to switch it back to Disabled (console mode) via the serial
connection to it, the escape sequence of ‘+++’ may be entered at
the Data Baud Rate for which the port is configured.
Values
Enable
Enable
Disable
Channel Mode
Determines which (rear of unit) serial interface shall be used to
connect to external devices: RS232, RS485, or RS422. This
option applies only to COM1. When an interface other than RS232
is selected, the DE9 port will be inactive.
*COM2 is RS232 only, 3-wire (TxD, RxD, and SG).
...continued
Page 92

Phantom II
© CalAmp
92
Values
6.0 Configuration
Channel Mode (continued)
Values
RS232
RS232
RS485
RS422
Data Baud Rate
The serial baud rate is the rate at which the modem is to
communicate with the attached local asynchronous device.
Note: Most PCs do not readily
support serial communications
greater than 115200 bps.
*COM2 data baud rate maximum is 115200 bps.
9600 (bps)
230400
115200
57600
38400
28800
19200
7200
4800
3600
2400
1200
600
300
14400
9600
460800 and 921600 may be
selected for RS422 or
RS485 Channel Modes.
Data Format
This setting determines the format of the data on the serial port.
The default is 8 data bits, No parity, and 1 Stop bit.
Values
8N1
.
8N1
8N2
8E1
8O1
7N1
7N2
7E1
7O1
7E2
7O2
Page 93

Phantom II
© CalAmp
93
6.0 Configuration
Flow Control
Flow control may be used to enhance the reliability of serial data
communications, particularly at higher baud rates. If the attached
device does not support hardware handshaking, leave this setting
Software flow control (XON/
XOFF) is not supported.
at the default value of ‘None’.
When CTS Framing is selected, the Phantom II uses the CTS
signal to gate the output data on the serial port. Figure 6A below
illustrates the timing of framed output data.
*COM2 does not support Flow Control.
Drawing 6-1: CTS Output Data Framing
Values
None
None
Hardware
CTS Framing
Pre-Data Delay (ms)
Refer to Figure b on the preceding page.
*COM2 does not support this function.
Values
100
0-65535 (ms)
Page 94

Phantom II
© CalAmp
94
6.0 Configuration
Post-Data Delay (ms)
Refer to Figure b on the preceding page.
*COM2 does not support this function.
Values
100
0-65535 (ms)
Data Mode
This setting defines the serial output data framing.
In Transparent mode (default), the received data will be output
promptly from the Phantom II.
When set to Seamless, the serial port server will add a gap
between data frames to comply with the MODBUS protocol for
example. See ‘Character Timeout’ on the next page for related
information.
Values
Transparent
Transparent
Seamless
Character Timeout
In Seamless mode, this setting determines when the serial server
will consider the recently-received incoming data as being ready to
transmit. As per the MODBUS standard. Frames will be marked as
‘bad’ if the time gap between frames is greater than 1.5 characters,
but less than the Character Timeout value.
The serial server also uses this parameter to determine the time
gap inserted between frames. It is measured in ‘characters’ and
related to baud rate.
continued...
Page 95

Phantom II
© CalAmp
95
6.0 Configuration
Character Timeout (continued)
Example: If the baud rate is 9600 bps, it takes approximately 1ms
to move one character. With the Character Timeout set to 4, the
timeout period is 4ms. When the calculated time is less than
3.5ms, the serial server will set the character timeout to a minimum
value of 3.5ms.
If the baud rate is greater than 19200 bps, the minimum character
timeout is internally set to 750us (microseconds).
Values
20
0-65535
Maximum Packet Size
Defines the buffer size that the serial server will use to receive data
from the serial port. When the server detects that the Character
Timeout criteria has been met, or the buffer is full, it packetizes the
received frame and transmits it.
Values
1024
Priority
This setting effects the Quality of Service (QoS) associated with the
data traffic on the specific COM port.
1-2048 (bytes)
Values
Normal
Normal
Medium
High
Page 96

Phantom II
© CalAmp
96
6.1 Configuration
The protocol selected in the IP
Protocol Config field will
determine which configuration
options appear in the remainder
of the COMn Configuration
Menu.
UDP: User Datagram Protocol
does not provide sequencing
information for the packets sent
nor does it establish a
’connection’ (‘handshaking’) and
is therefore most suited to
communicating small packets of
data.
TCP: Transmission Control
Protocol in contrast to UDP does
provide sequencing information
and is connection-oriented; a
more reliable protocol,
particularly when large amounts
of data are being communicated.
Requires more bandwidth than
UDP.
IP Protocol Config
This setting determines which protocol the serial server will use to
transmit serial port data over the Phantom II network.
TCP Client: When TCP Client is selected and data is received on
its serial port, the Phantom II takes the initiative to find and connect
to a remote TCP server. The TCP session is terminated by this
same unit when the data exchange session is completed and the
connection timeout has expired. If a TCP connection cannot be
established, the serial port data is discarded.
Remote Server Address
IP address of a TCP server which is ready to
accept serial port data through a TCP connection.
For example, this server may reside on a LAN
network server.
Default: 0.0.0.0
Remote Server Port
A TCP port which the remote server listens to,
awaiting a session connection request from the
TCP Client. Once the session is established, the
serial port data is communicated from the Client to
the Server.
Default: 20001
Outgoing Connection Timeout
This parameter determines when the Phantom II
will terminate the TCP connection if the connection
is in an idle state (i.e. no data traffic on the serial
port).
Default: 60 (seconds)
TCP Server: In this mode, the Phantom II will not INITIATE a
session, rather, it will wait for a Client to request a session of it (it’s
being the Server—it ‘serves’ a Client). The unit will ‘listen’ on a
specific TCP port. If a session is established, data will flow from the
Client to the Server, and, if present, from the Server to the Client. If
a session is not established, both Client-side serial data, and
Server-side serial data , if present, will be discarded.
Local Listening Port
The TCP port which the Server listens to. It allows
a TCP connection to be created by a TCP Client to
carry serial port data.
Default: 20001
continued...
Page 97

Phantom II
© CalAmp
97
6.1 Configuration
A UDP or TCP port is an
application end-point. The IP
address identifies the device and,
as an extension of the IP
address, the port essentially ‘fine
tunes ’ where the data is to go
‘within the device’.
Be careful to select a port
number that is not predetermined
to be associated with another
application type, e.g. HTTP uses
port 80.
IP Protocol Config (continued)
Incoming Connection Timeout
Established when the TCP Server will terminate the
TCP connection is the connection is in an idle
TCP Client/Server: In this mode, the Phantom II will be a
combined TCP Client and Server, meaning that it can both initiate
and serve TCP connection (session) requests. Refer to the TCP
Client and TCP Server descriptions and settings described
previously as all information, combined, is applicable to this mode.
state.
Default: 300 (seconds)
continued...
Page 98

Phantom II
© CalAmp
98
6.1 Configuration
IP Protocol Config (continued)
UDP Point-to-Point: In this configuration the Phantom II will send
serial data to a specifically-defined point, using UDP packets. This
same Phantom II will accept UDP packets from that same point.
Remote IP Address
IP address of distant device to which UDP packets
are sent when data received at serial port.
Default: 0.0.0.0
Remote Port
UDP port of distant device mentioned above.
Default: 20001
Listening Port
UDP port which the Phantom II listens to
(monitors). UDP packets received on this port are
forwarded to the unit’s serial port.
Default: 20001
UDP Point-to-Multipoint (P): This mode is configured on a
Phantom II which is to send multicast UDP packets; typically, the
Multicast is a one-to-many
transmission of data over an IP
network. It is an efficient method
of transmitting the same data to
many recipients. The recipients
must be members of the specific
multicast group.
MASTER in the Phantom II network.
Multicast IP Address
A valid multicast address this unit uses to send
multicast UDP packets upon receiving data from
the serial port. The default value is a good
example of a valid multicast address.
Default: 224.1.1.1
Multicast Port
A UDP port that this Phantom II will send UDP
packets to. The Multipoint (MP - see the UDP
Point-to-Multipoint (MP) description) stations
should be configured to listen to this point in order
to receive multicast packets from this Phantom II.
Default: 20001
TTL: Time to Live is the number
of hops a packet can travel
before being discarded.
In the context of multicast, a TTL
value of 1 restricts the range of
the packet to the same subnet.
Listening Port
The UDP port that this unit receives incoming data
on from multiple remote units.
Default: 20011
Time to Live
Time to live for the multicast packets.
Default: 1 (hop)
continued...
Page 99

Phantom II
© CalAmp
99
6.1 Configuration
In a Point-to-Multipoint (PMP)
network topology which is to
utilize UDP multicast, typically
the MASTER would be
configured as ’(P)’ (the POINT)
and the REMOTES would be
configured as ’(MP)’ (the
MULTIPOINTS).
IP Protocol Config (continued)
UDP Point-to-Multipoint (MP): This protocol is selected on the
units which are to receive multicast UDP packets, typically the
Remote units. See the previous description of UDP Point-toMultipoint (P). Note: Firmware version 1.1.14 or later.
Remote IP Address
The IP address of a distant device (Phantom II or,
for example, a PC) to which the unit sends UDP
packets of data received on the serial port. Most
often this is the IP address of the Master Phantom
II.
Default: 0.0.0.0
Remote Port
The UDP port associated with the Remote IP
Address (above). In the case of this ‘Remote’
being the Master Phantom II, the value in this field
should match the Listening Port of the Master (see
UDP Point-to-Multipoint (P)).
Default: 20011
Multicast IP Address
A valid MULTICAST address that this unit will use
to receive multicast UDP packets sent by a UDP
Point-to-Multipoint (P) unit. Note that the default
value for this field matches the default Multicast IP
Address of the UDP Point-to-Multipoint (P)
configuration described on the previous page.
Default: 224.1.1.1
Multicast Port
The UDP port that this unit will use, along with the
Multicast IP Address detailed above, to receive the
multicast UDP packets sent by the UDP Point-toMultipoint (P) unit.
Default: 20001
continued...
Page 100

Phantom II
© CalAmp
100
6.1 Configuration
IP Protocol Config (continued)
UDP Multipoint-to-Multipoint
Multicast IP Address
A valid multicast address the unit will use to send
multicast UDP packets upon receiving them at its
serial port.
Default: 224.1.1.1
Multicast Port
UDP port that the packets are sent to. Multipoint
stations should be configured to listen to this port in
order to receive multicast packets.
Default: 20011
Time to Live
Time to live for the multicast packets.
Default: 1 (hop)
Listening Multicast IP Address
A valid multicast address the unit is to listen to
receive multicast UDP packets sent by another
UDP Multipoint-to-Multipoint unit.
Default: 224.1.1.1
Listening Multicast Port
UDP port that the unit will listen to for multicast
UDP packets sent by another UDP Multipoint-toMultipoint unit.
Default: 20011
SMTP Client: If the Phantom II network has Internet access, this
protocol may be used to send the data received on the serial port
(COM1), in a selectable format (see Transfer Mode (below)), to an
e-mail addressee. Both the SMTP Server and the e-mail
addressee must be ‘reachable’ for his feature to function.
SMTP: Simple Mail Transport
Protocol is a protocol used to
transfer mail across an IP
network.
Mail Subject
Enter a suitable ‘e-mail subject’ (e-mail heading).
Default: COM1 Message
Mail Server (IP/Name)
IP address or ‘Name’ of SMTP (Mail) Server.
Default: 0.0.0.0
continued...
 Loading...
Loading...