Page 1

ELS10-26 MIB REFERENCE
GUIDE
9032244-01
Page 2

Page 3

Notice
NOTICE
Cabletron Systems reserves the right to make changes in specifications and other information
contained in this document without prior notice. The reader should in all cases consult Cabletron
Systems to determine whether any such changes have been made.
The hardware, firmware, or software described in this manual is subject to change without notice.
IN NO EVENT SHALL CABLETRON SYSTEMS BE LIABLE FOR ANY INCIDENTAL,
INDIRECT, SPECIAL, OR CONSEQUENTIAL DAMAGES WHATSOEVER (INCLUDING BUT
NOT LIMITED TO LOST PROFITS) ARISING OUT OF OR RELATED TO THIS MANUAL OR
THE INFORMATION CONTAINED IN IT, EVEN IF CABLETRON SYSTEMS HAS BEEN
ADVISED OF, KNOWN, OR SHOULD HAVE KNOWN, THE POSSIBILITY OF SUCH
DAMAGES.
Copyright 1997 by Cabletron Systems, Inc., P.O. Box 5005, Rochester, NH 03866-5005
All Rights Reserved
Printed in the United States of America
Order Number: 9032244-01 September 1997
Cabletron Systems, SPECTRUM,
SmartSTACK, ELS10-26TX, FEPIM, FEPIM-TX and FEPIM-FX
Cabletron Systems, Inc.
All other product names mentioned in this manual may be trademarks or registered trademarks of
their respective companies.
This device complies with Part 15 of the FCC rules. Operation is subject to the following two
conditions: (1) this device may not cause harmful interference, and (2) this device must accept any
interference received, including interference that may cause undesired operation.
NOTE:
This equipment has been tested and found to comply with the limits for a Class A digital
device, pursuant to Part 15 of the FCC rules. These limits are designed to provide reasonable
protection against harmful interference when the equipment is operated in a commercial environment.
This equipment uses, generates, and can radiate radio frequency energy and if not installed in
accordance with the operator’s manual, may cause harmful interference to radio communications.
Operation of this equipment in a residential area is likely to cause interference in which case the user
will be required to correct the interference at his own expense.
WARNING:
party responsible for compliance could void the user’s authority to operate the equipment.
Changes or modifications made to this device which are not e xpressly appro v ed by the
and
LANVIEW
FCC NOTICE
are registered trademarks and
are trademarks of
Printed on Recycled Paper
i
Page 4

Notice
DOC NOTICE
This digital apparatus does not exceed the Class A limits for radio noise emissions from digital
apparatus set out in the Radio Interference Regulations of the Canadian Department of
Communications.
Le présent appareil numérique n’émet pas de bruits radioélectriques dépassant les limites applicables
aux appareils numériques de la class A prescrites dans le Règlement sur le brouillage radioélectrique
édicté par le ministère des Communications du Canada.
VCCI NOTICE
This is a Class A product based on the standard of the Voluntary Control Council for Interference by
Information Technology Equipment (VCCI). If this equipment is used in a domestic environment,
radio disturbance may arise. When such trouble occurs, the user may be required to take corrective
actions.
CABLETRON SYSTEMS, INC. PROGRAM LICENSE AGREEMENT
IMPORTANT:
This document is an agreement between you, the end user, and Cabletron Systems, Inc. (“Cabletron”)
that sets forth your rights and obligations with respect to the Cabletron software program (the
“Program”) contained in this package. The Program may be contained in firmware, chips or other
media. BY UTILIZING THE ENCLOSED PRODUCT, YOU ARE AGREEING TO BECOME
BOUND BY THE TERMS OF THIS AGREEMENT, WHICH INCLUDES THE LICENSE AND
THE LIMITATION OF WARRANTY AND DISCLAIMER OF LIABILITY. IF YOU DO NOT
AGREE TO THE TERMS OF THIS AGREEMENT, PROMPTLY RETURN THE UNUSED
PRODUCT TO THE PLACE OF PURCHASE FOR A FULL REFUND.
Before utilizing this product, carefully read this License Agreement.
ii
Page 5

Notice
CABLETRON SOFTWARE PROGRAM LICENSE
1. LICENSE
package subject to the terms and conditions of this License Agreement.
You may not copy, reproduce or transmit any part of the Program except as permitted by the
Copyright Act of the United States or as authorized in writing by Cabletron.
2. OTHER RESTRICTIONS. You may not reverse engineer, decompile, or disassemble the
Program.
3. APPLICABLE LA W. This License Agreement shall be interpreted and governed under the laws
and in the state and federal courts of New Hampshire. You accept the personal jurisdiction and
venue of the New Hampshire courts.
. You have the right to use only the one (1) copy of the Program provided in this
EXCLUSION OF WARRANTY AND DISCLAIMER OF LIABILITY
1. EXCLUSION OF
writing, Cabletron makes no warranty, expressed or implied, concerning the Program (including
its documentation and media).
CABLETRON DISCLAIMS ALL WARRANTIES, OTHER THAN THOSE SUPPLIED TO
YOU BY CABLETRON IN WRITING, EITHER EXPRESSED OR IMPLIED, INCLUDING
BUT NOT LIMITED TO IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE, WITH RESPECT TO THE PROGRAM, THE
ACCOMP ANYING WRITTEN MA TERIALS, AND ANY A CCOMP ANYING HARDWARE.
2. NO LIABILITY FOR CONSEQUENTIAL DAMAGES. IN NO EVENT SHALL
CABLETRON OR ITS SUPPLIERS BE LIABLE FOR ANY DAMAGES WHATSOEVER
(INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF BUSINESS,
PROFITS, BUSINESS INTERRUPTION, LOSS OF BUSINESS INFORMATION, SPECIAL,
INCIDENTAL, CONSEQUENTIAL, OR RELIANCE DAMAGES, OR OTHER LOSS)
ARISING OUT OF THE USE OR INABILITY TO USE THIS CABLETRON PRODUCT,
EVEN IF CABLETRON HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES. BECAUSE SOME STATES DO NOT ALLOW THE EXCLUSION OR
LIMITATION OF LIABILITY FOR CONSEQUENTIAL OR INCIDENTAL DAMAGES, OR
ON THE DURATION OR LIMITATION OF IMPLIED WARRANTIES, IN SOME
INSTANCES THE ABOVE LIMITATIONS AND EXCLUSIONS MAY NOT APPLY TO
YOU.
WARRANTY. Except as may be specifically provided by Cabletron in
UNITED STATES GOVERNMENT RESTRICTED RIGHTS
The enclosed product (a) was developed solely at private expense; (b) contains “restricted computer
software” submitted with restricted rights in accordance with Section 52227-19 (a) through (d) of the
Commercial Computer Software - Restricted Rights Clause and its successors, and (c) in all respects
is proprietary data belonging to Cabletron and/or its suppliers.
For Department of Defense units, the product is licensed with “Restricted Rights” as defined in the
DoD Supplement to the Federal Acquisition Regulations, Section 52.227-7013 (c) (1) (ii) and its
successors, and use, duplication, disclosure by the Government is subject to restrictions as set forth in
subparagraph (c) (1) (ii) of the Rights in Technical Data and Computer Software clause at
252.227-7013. Cabletron Systems, Inc., 35 Industrial Way, Rochester, New Hampshire 03867-0505.
iii
Page 6

Notice
DECLARATION OF CONFORMITY
Application of Council Directive(s):
Manufacturer’s Name:
Manufacturer’s Address:
European Representative Name:
European Representative Address:
Conformance to Directive(s)/Product Standards:
Equipment T ype/Environment:
W e the undersigned, hereby declare, under our sole responsibility, that the equipment packaged
with this notice conforms to the above directives.
Manufacturer Legal Representative in Europe
89/336/EEC
73/23/EEC
Cabletron Systems, Inc.
35 Industrial Way
PO Box 5005
Rochester, NH 03867
Mr. J. Solari
Cabletron Systems Limited
Nexus House, Newbury Business Park
London Road, Newbury
Berkshire RG13 2PZ, England
EC Directive 89/336/EEC
EC Directive 73/23/EEC
EN 55022
EN 50082-1
EN 60950
Networking Equipment, for use in a
Commercial or Light
Environment.
Industrial
Mr. Ronald Fotino Mr. J. Solari
___________________________________ ___________________________________
Full Name Full Name
Principal Compliance Engineer Managing Director - E.M.E.A.
___________________________________ ___________________________________
Title Title
Rochester, NH, USA Newbury, Berkshire, England
___________________________________ ___________________________________
Location Location
iv
Page 7

TABLE OF CONTENTS
Chapter 1 Introduction
1.1 Related Documentation...................................................1-2
1.2 Getting Help....................................................................1-3
1.3 Document Conventions...................................................1-4
1.4 SNMP Primitives............................................................1-5
1.5 MIB Primitive Types ......................................................1-6
1.6 User Functions................................................................1-7
1.7 Navigating Through the MIBTree Structure...................1-9
1.8 TFTP...............................................................................1-13
1.8.1 Retrieving All Parameters...................................1-15
1.8.2 Setting All Parameters ........................................1-15
1.9 Additional Interfaces.......................................................1-16
Chapter 2 TCP/IP MIB-II
2.1 System Group..................................................................2-1
2.2 Interfaces Group..............................................................2-2
2.3 Address Translation Group.............................................2-8
2.4 IP Group..........................................................................2-9
2.4.1 IP Address Table.................................................2-12
2.4.2 IP Routing Table.................................................2-14
2.4.3 IP Address Translation Table..............................2-17
2.4.4 IP Additional Objects..........................................2-18
2.5 ICMP Group....................................................................2-19
2.6 TCP Group......................................................................2-22
2.7 UDP Group .....................................................................2-22
2.7.1 UDP Listener Table ............................................2-23
2.8 EGP Group......................................................................2-24
2.9 OIM Subtree....................................................................2-24
2.10 Transmission Group........................................................2-24
2.11 SNMP Management Group.............................................2-25
2.12 Cabletron Interface Group ..............................................2-29
2.13 Cabletron Interface Port Group.......................................2-32
2.14 Cabletron Com Port Configuration Group......................2-35
v
Page 8

Contents
2.15 SNMP Version Group.....................................................2-37
2.16 Trap Description .............................................................2-38
2.17 Cabletron MIB 2 Extensions...........................................2-39
Chapter 3 Ethernet MIB
3.1 Generic Ethernet-Like Group .........................................3-1
3.2 Ethernet-Like Statistics Group........................................3-2
3.3 Ethernet-Like Collision Statistics Group........................3-5
3.4 Ethernet-Like Tests Group..............................................3-6
3.5 Ethernet-Like Errors Group............................................3-6
3.6 Ethernet-Like Chipsets Group ........................................3-6
Chapter 4 Bridge MIB
4.1 Base Group......................................................................4-1
4.2 Spanning Tree Group......................................................4-3
4.3 Transparent Group..........................................................4-9
Chapter 5 PPP MIB
5.1 PPP Link Control Table..................................................5-1
5.2 PPP IP Table...................................................................5-10
Chapter 6 ELS10-26 MIB
6.1 System Group..................................................................6-1
6.1.1 Hardware Configuration Group..........................6-2
6.1.2 LXSW Configuration Group...............................6-4
6.1.3 Administration Group.........................................6-6
6.1.4 Software Distribution Group...............................6-11
6.1.5 Addresses Configuration Group .........................6-13
6.1.6 Cabletron Interfaces Group.................................6-16
6.1.7 Cabletron Dot3 Group.........................................6-20
vi
Page 9

Contents
6.1.8 Cabletron UART Interface Group ......................6-23
6.1.9 Cabletron Protocol Group...................................6-24
6.1.10 Cabletron Trunking Group..................................6-26
6.1.11 Cabletron Workgroup Management Group........6-29
6.1.12 Cabletron Trap Management Group...................6-31
6.1.13 Ping Management MIB.......................................6-35
6.1.14 Traceroute...........................................................6-41
6.1.15 Traceroute Management MIB.............................6-42
6.1.16 Port Mirroring.....................................................6-47
Chapter 7 Traps
7.1 Generic Traps..................................................................7-1
7.2 Enterprise Specific Traps For The ELS10-26.................7-2
vii
Page 10

Contents
viii
Page 11

CHAPTER 1
INTRODUCTION
This manual is for system administrators responsible for
configuring, monitoring, and maintaining the ELS10-26. Much of
the configuration of the ELS10-26 needs to be done using an
SNMP-based network management station. This manual contains
the SNMP MIB variables you may need to configure, monitor, and
manage your ELS10-26. You should use this manual with the
ELS10-26 User Guide
your NMS.
The contents of each chapter are described below.
and with the documentation provided with
• Chapter 1,
primitives, describes the functions the MIB variables can be used
to perform, and describes how to use TFTP to download the
ELS10-26 system software.
• Chapter 2,
variables.
• Chapter 3,
variables.
• Chapter 4,
• Chapter 5,
MIB variables.
• Chapter 6,
MIB variables.
• Chapter 7,
traps.
Introduction
TCP/IP MIB-II
Ethernet MIB
Bridge MIB
PPP MIB
ELS10-26 MIB
Traps
, describes generic and enterprise-specific
, provides an overview of the SNMP
, describes the standard TCP/IP MIB
, describes the standard Ethernet MIB
, describes the Bridge MIB variables.
, describes the PPP link control and IP table
, describes the Cabletron enterprise
1-1
Page 12

Introduction
1.1 RELATED DOCUMENTATION
You may need to refer to the following Cabletron documentation:
•
ELS10-26 User Guide
management instructions for the ELS10-26. It also describes how
to use the Local Console Manager (LCM), which is a
non-intelligent terminal interface to the ELS10-26.
If you need internetworking reference material, you may find the
following books helpful:
•
Interconnections, Bridges and Routers,
Wesley © 1992.
•
Internetworking with TCP/IP: Principles, Protocols, and Architecture
(2nd edition), Volumes I and II, Douglas Comer,
Prentice Hall © 1991.
•
The Simple Book, An Introduction to Management of TCP/IP-based
internets
(2nd edition), Marshall T. Rose, Prentice Hall © 1994.
– contains installation, configuration, and
Radia Perlman, Addison
This manual describes the software interface between the NMS
and the ELS10-26. This is relevant for an ELS10-26 running Version
1.0 software. The NMS communicates with the ELS10-26 software.
The Network Management, or UART, port is the interface to the
Local Console Manager (LCM). LCM is a non-intelligent terminal
interface that can be used to configure and monitor status for the
ELS10-26.
1-2
Page 13

Introduction
1.2 GETTING HELP
If you need additional support related to the ELS10-26, or if you
have any questions, comments, or suggestions concerning this
manual, contact Cabletron Systems Global Call Center:
Phone: (603) 332-9400
Internet mail: support@ctron.com
FTP: ctron.com (134.141.197.25)
Login: anonymous
Password: your email address
BBS: (603) 335-3358
Modem setting: 8N1: 8 data bits, No parity, 1 stop bit
Before calling Cabletron Systems Global Call Center, have the
following information ready:
• Your Cabletron Systems contract number
• A description of the failure
• The serial and revision numbers of all Cabletron Systems
products in the network
• A description of any action(s) already taken to resolve the
problem (e.g., changing mode switches, rebooting the unit, etc.)
• A description of your network environment (layout, cable type,
etc.)
• Network load and frame size at the time of trouble (if known)
• The device history (i.e., have you returned the device before, is
this a recurring problem, etc.)
• Any previous Return Material Authorization (RMA) numbers
For additional information about Cabletron Systems products,
visit our World Wide Web site: http://www.cabletron.com
1-3
Page 14

Introduction
1.3 DOCUMENT CONVENTIONS
The following conventions are used throughout this document:
LCM commands, prompts, and information displayed by the
computer appear in Courier typeface, for example:
Current Number of Learned Addresses: 133
Information that you enter appears in Courier bold typeface, for
example:
ELS10-26 >
status
Information that you need to enter with a command is enclosed in
angle brackets < >. For example, you must enter a port number
and an IP address to execute the
ipaddr <port #> <IP address>
command:
ELS10-26 >
ipaddr 6 192.138.217.40
Field value options appear in bold typeface.
The following conventions are also used in this document:
Note:
Calls the reader’s attention to any item of information that may be
of special importance.
Tip:
Caution:
Conveys helpful hints concerning procedures or actions.
Contains information essential to avoid damage to the
equipment.
1-4
Page 15

Introduction
1.4 SNMP PRIMITIVES
The major software interface between the NMS and ELS10-26
consists of one simple mechanism – the exchange of SNMP (Simple
Network Management Protocol, RFC 1157) datagrams over any
available physical media. The following restrictions apply:
• All datagrams must obey SNMP format.
• All datagrams must be sent via UDP and IP. Thus, all datagrams
will have UDP and IP headers.
• Datagrams may be sent over any of the following physical
media:
- Ethernet/802.3 LAN - the datagram must have an Ethernet
MAC header, with an Ethernet frame type of IP; or, the
datagram must be in 802.3 format with IP-encapsulation as
defined by RFC 1042.
- UART (out-of-band management port) - the datagram must
have a PPP header, which indicates that the datagram
contains an IP packet. (The ELS10-26 automatically detects
the presence of a PPP connection versus being connected to
a non-intelligent terminal.)
The NMS must rely on IP, rather than MAC addressing for all
datagrams sent to an ELS10-26. Therefore:
• All datagrams from the ELS10-26 are addressed to either an
NMS or the broadcast IP address.
• Within the context of this document, the terms “datagram,”
“packet,” and “PDU” are synonymous.
1-5
Page 16

Introduction
1.5 MIB PRIMITIVE TYPES
The MIB definitions in this document may reference the primitive
types that are described in the Structure and Identification of
Management Information for TCP/IP-based Internets, RFC 1155.
RFC 1155 is based on the Specification of Abstract Syntax Notation
One, ASN.1. The primitive types are described in Table 1-1.
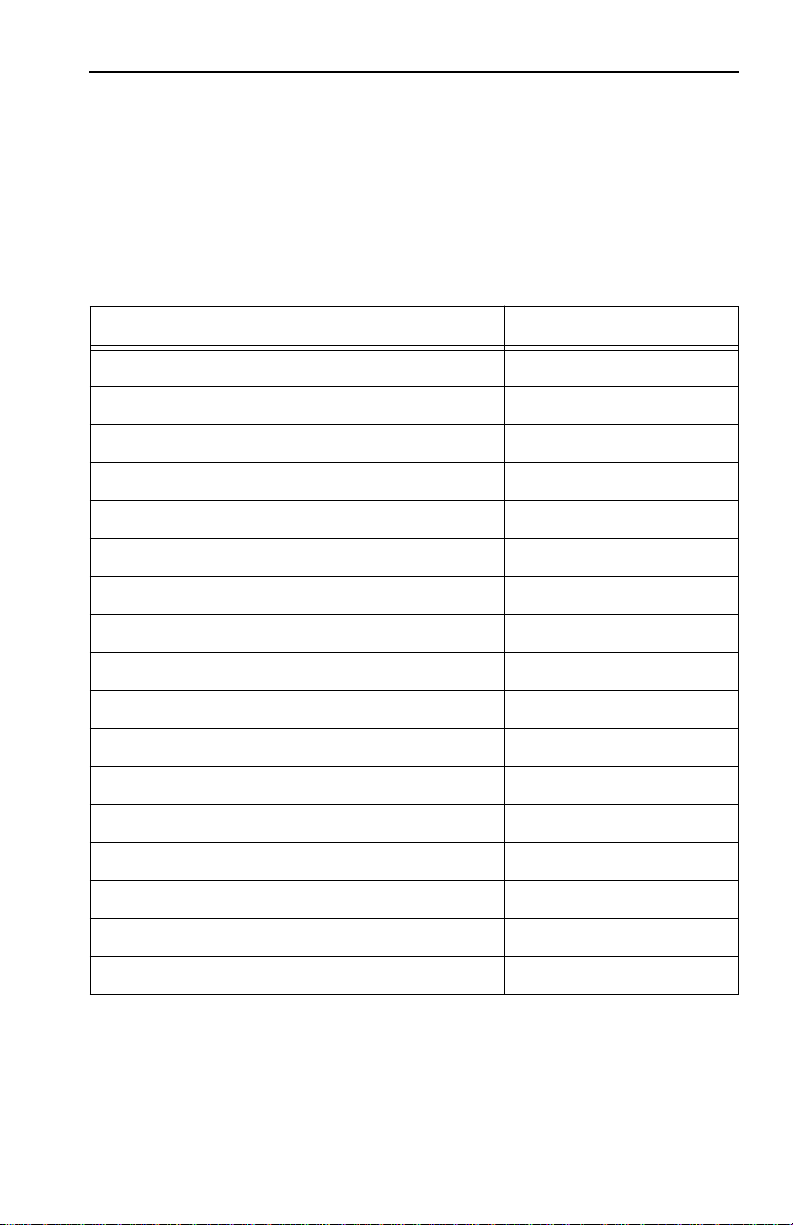
Table 1-1 Primitive Descriptions
Primitive Size Description
Enumerated Integer with possible true (1)
Boolean 1 byte
or false (2) values; note that the ASN.1
BOOLEAN primitive type is not used
BridgeID 8 bytes
Counter 4 bytes max Unsigned value
DisplayString n X 1 byte Array of printable ascii characters
Gauge 4 bytes Non-negative integer
Integer 4 bytes max Signed value
IpAddress 4 bytes Internet address
MacAddress 6 bytes Ethernet address
OctetString n X 1 byte Array of bytes
PhysAddress n X 1 byte
PortID 2 bytes
TimeTicks 4 bytes
Priority and MAC address used to identify
a spanning tree bridge
Array of bytes, using the same as a MAC
Address
Priority and port number used to identify a
spanning tree port
Max time counter with a granularity of
1/100th of a second (also known as
centiseconds)
1-6
Page 17

Introduction
1.6 USER FUNCTIONS
The SNMP primitives may be used to accomplish the following
functions:
• Obtain the ELS10-26’s current value of certain parameters - the
NMS uses the GetRequest or GetNextRequest PDU, and the
ELS10-26 responds with a GetResponse PDU. If the NMS issues
a GetRequest for an unsupported parameter, the ELS10-26 sends
ErrorStatus1. If the NMS
a GetResponse with a noSuchName
issues a GetNextRequest for an unsupported parameter, the
ELS10-26 skips to the next object.
• Change the ELS10-26’s value of certain parameters - the NMS
uses the SetRequest PDU, and the ELS10-26 responds with a
GetResponse PDU. The ELS10-26 will change both its current
value and its local default to be used when the ELS10-26 reboots,
unless noted otherwise.
• Obtain the current value of certain parameters and
simultaneously change the value of other parameters - the NMS
uses the SetRequest PDU, and the ELS10-26 responds with a
GetResponse PDU. For the parameters which are being obtained
rather than changed, the NMS must use the ASN.1 NULL value
with the SetRequest PDU.
• Provide notification of significant events - the ELS10-26 uses the
Trap PDU and/or the GetResponse PDU. The NMS uses the
SetRequest PDU to control the frequency that the ELS10-26 may
send Trap PDUs.
1.
If implementing the parameter is required, it might seem more reasonable to
return a GetResponse with no error and the ASN.1 NULL value as the
parameter’s value; howev er, leading authorities such as Marshall T. Rose (author
of
The Simple Book
existing SNMP management stations do not handle NULL values correctly.
) suggest that noSuchName be returned, because many
1-7
Page 18

Introduction
The ELS10-26 implements two non-standard features with respect
to the SNMP SetRequest:
• The variable bindings within a SetRequest are sometimes
processed sequentially rather than simultaneously. For example,
if a SetRequest contains two parameters with an incorrect value
specified for the second parameter, the ELS10-26 returns a
badValue error to the NMS; however, the ELS10-26 may have
updated its value for the first parameter.
• The values within the variable bindings of the returned
GetResponse may reflect meaningful information, rather than
being an exact copy of the values from the SetRequest. For
example, if a SetRequest contains two variable bindings, the first
specifying that memory should be examined and the second
specifying the contents of the memory, then the ELS10-26’s
GetResponse will update the value of the second variable
binding to contain the actual contents of the memory.
1-8
Page 19

Introduction
1.7 NAVIGATING THROUGH THE MIBTREE STRUCTURE
The MIB structure is a hierarchical tree structure. Each MIB
variable has a numeric value that indicates its place in the
hierarchy. The structure was originally created, and is still
maintained by the International Organization for Standardization
(ISO) and the International Telecommunications Union (ITU), two
international standards organizations. You can get and set MIB
variables by navigating down the tree to a specific MIB, a group or
table within that MIB, and then to the individual variable.
Figure 1-1 shows the path down the MIB tree structure. Under the
“mib-2” and the Cabletron enterprise branch, are all the relevant
MIBs that the ELS10-26 supports.
1-9
Page 20

Introduction
iso
1
org
3
dod
6
internet
1
mgmt
2
mib-2
1
system interfaces add trans ip
1
234 39
Figure 1-1 MIB Hierarchical Structure
experimental
3
private
4
enterprise
......
1
sigma
97
rdbmsMIB
Table 1-2 provides the branch structure that is under MIB-II. To
reach any of the MIB-II objects you would start with the prefix
1.3.6.1.2.1. For example, to reach an object in the system group, you
would start with 1.3.6.1.2.1.1. To find the amount of time the
ELS10-26 had been running, you would want to get the sysUpTime
variable, which is the third object in the system group. So the get
command would look like:
get 1.3.6.1.2.1.1.3.0
1-10
Page 21
Introduction
The zero at the end (.0), indicates that this is a single instance, and
that only one value can be returned. Whenever you are looking for
a variable with only one value, you must include the .0 at the end.
Some variables may have multiple values, such as an IP address
and an associated port number.
Table 1-2 MIB-II Group Descriptions
MIB-II Group Number (1.3.6.1.2.1.)
System 1
Interfaces 2
Address T r anslation 3
Internet Protocol (IP) 4
Internet Control Message (ICMP) 5
Transmission Control Protocol (TCP) 6
User Datagram Protocol (UDP) 7
Exterior Gateway Protocol (EGP) 8
CMIP over TCP (CMOT) 9
Transmission 10
SNMP 11
GenericIF 12
AppleTalk 13
Open Shortest Path First (OSPF) 14
Border Gateway Protocol (BGP) 15
Remote Network Monitoring (RMON) 16
Bridge 17
There are additional groups under MIB-II, but all groups are not
supported by the ELS10-26.
1-11
Page 22

Introduction
The Cabletron MIB is under the private enterprise MIB branch. To
identify a variable in the Cabletron MIB, you would start with the
private enterprise prefix of 1.3.6.1.4.1, and add the specific
Cabletron ID of 97. The result, 1.3.6.1.4.1.97, is the complete prefix
for a Cabletron MIB variable. You would then add the specific
object ID to complete the MIB variable.
For example, to find the sysID currently defined in the ELS10-26,
you would want to get the sysID variable in the Cabletron MIB
group and add it to the prefix 1.3.6.1.4.97. After the prefix, add the
Cabletron MIB, 1.1. As stated above, the zero {0} indicates that this
variable is a single instance and only one variable can be returned.
The get command would look like:
get 1.3.6.1.4.1.97.1.1
At the beginning of each chapter in this Reference Guide, the prefix
for each MIB group is provided. To calculate the specific MIB
variable, you add the specific object ID to the prefix for that MIB
group.
1-12
Page 23

Introduction
1.8 TFTP
TFTP (Trivial File Transfer Protocol, RFC 1350) is used for:
• Distribution of new software.
• Bulk retrieval of all of the parameters of a ELS10-26.
• Bulk setting of all of the parameters of a ELS10-26.
TFTP has no inherent security provision; however, all files have
special data encryption, and the ELS10-26 will reject files that have
not been encrypted. In addition, SNMP primitives may be used to
prevent the ELS10-26 from accepting unauthorized TFTP requests,
even if the files have the special data encryption. Refer to the
description of the sxswdis branch of Cabletron’s private MIB for
TFTP security details.
Software Distribution
TFTP is used for the distribution of new software. The new
software will be automatically invoked when an ELS10-26 reboots.
New software is released in two files:
• dnld_hdr
• dnld_software
To distribute the new software to an ELS10-26, the TFTP procedure
is as follows:
1. Start TFTP on the NMS, or on any other device which can
provide TFTP services. (Typically, TFTP must be started from
the same directory that contains the files to be transferred.)
TFTP must be told the IP address of the remote host (the IP
address of the ELS10-26), and the file transfer mode (which
must be “binary”).
2. Use TFTP to retrieve all of the ELS10-26’s parameters, as
described in a subsection below. This step is not required, but it
1-13
Page 24

Introduction
is recommended if you need to go back to the version of
software that is currently being executed by the ELS10-26.
3. Tell TFTP to transfer (“put”) the first file, (dnld_hdr).
4. Wait one minute, or until the ELS10-26 sends the SNMP Trap
described in the swdis branch of SMC’s private MIB. (The Trap
will be sent when the ELS10-26 is ready for the second file,
which will be somewhat shorter than three minutes.)
5. Tell TFTP to transfer the second file, (dnld_software). This
transfer should take approximately one minute.
The initial one minute waiting may be omitted and this second
transfer may be initiated immediately following the first
transfer; however, that causes the second transfer to take
approximately two minutes, and creates a slightly heavier
network load during the file transfer.
Note:
If the above TFTP sequence is abnormally terminated, there is no
cause for alarm, since the ELS10-26 maintains a back-up set of
software, and the ELS10-26 will not use the incomplete new
software.
Older versions of software may be distributed to an ELS10-26,
provided that the older software is at least Version 2.3. To
distribute the older software to an ELS10-26, the above TFTP
procedure should be altered, with the following step being
performed before the older software is distributed.
If the bulk retrieval of all of the parameters of the ELS10-26 had
been performed while the ELS10-26 was executing that older
software, that retrieved file should be used to do a bulk set of all
parameters (as described below). Otherwise, when the older
software is distributed and the ELS10-26 reboots, the older
software will not understand the format of the ELS10-26’s
2
parameters.
1-14
Page 25

Introduction
1.8.1 Retrieving All Parameters
TFTP is used for retrieval of the parameters of an ELS10-26, as
follows
:
1. Start TFTP (as described earlier). TFTP must be told the IP
address of the remote host (i.e., the ELS10-26), and the file
transfer mode (which must be “binary”).
2. Tell TFTP to retrieve (i.e., “get”) the ELS10-26’s Configuration
file (i.e., file name “config”).
3. After about ten seconds, the TFTP operation will complete.
1.8.2 Setting All Parameters
TFTP is used for bulk setting of all of the parameters of an
ELS10-26, as follows:
1. Start TFTP (as described earlier). TFTP must be told the IP
address of the remote host (i.e., the IP address of the ELS10-26),
and the file transfer mode (which must be “binary”).
2. Tell TFTP to send (i.e., “put”) the ELS10-26’s Configuration file
(i.e., file name “config”).
3. After about twenty seconds, the TFTP operation will complete.
2.
The software will re-initialize all of the ELS10-26’s parameters to the factory
specified defaults.
1-15
Page 26

Introduction
1.9 ADDITIONAL INTERFACES
In addition to SNMP and TFTP, the ELS10-26 employs the
following protocols, as part of its software interface with an NMS:
• UDP - User Datagram Protocol, RFC 768.
• IP - Internet Protocol, RFC 791.
• ARP - Ethernet Address Resolution Protocol, RFC 826.
• RARP - Reverse Address Resolution Protocol, RFC 903. RARP is
only used when no IP addresses have been assigned to the
ELS10-26.
1-16
Page 27

CHAPTER 2
TCP/IP MIB-II
The ELS10-26 supports the TCP/IP MIB-II, as defined by
Management Information Base for Network Management of TCP/
IP-based Internets MIB-II
March 1991. The MIB is divided into groups of parameters. The
individual groups are described in the subsections below. You may
want to refer to the actual TCP/IP MIB, since this document
paraphrases the standard MIB in order to provide ELS10-26-related
descriptions.
, RFC 1213 (K. McCloghrie, editor), dated
Note:
The MIB tree prefix for reaching the TCP/IP MIB-II is:
The access types of some of the TCP/IP MIB parameters have been
extended from Read-Only to Read-Write. However, unless
otherwise indicated, the access type of all parameters is as indicated
in the standard MIB.
1.3.6.1.2.1.
2.1 SYSTEM GROUP
system {mib-2 1}
The TCP/IP System Group parameters are described below.
sysDescr {system 1}
DisplayString Read-Only
A textual description of the ELS10-26 is Cabletron “moduleName”
Rev “FirmwareRevision” “LinkTimeandDate” i.e., Cabletron
ELS10-26 Rev xx:xx:xx 03/04/97--11:30:25
sysObjectID {system 2}
Object Identifier Read-Only
The identifier of the variable used to identify the type of entity.
Cabletron’s MIB sysID parameter will have a value that indicates
that it is a bridge. So sysObjectID contains the object identifier of
2-1
Page 28

TCP/IP MIB-II
the Cabletron MIB sysID object, i.e., {1 3 6 1 4 1 97 5 7}. Special
versions of the ELS10-26, made for third-party vendors may use
different values for sysID.
sysUpTime {system 3}
TimeTicks Read-Only
The time, in centiseconds, since the ELS10-26 was last booted.
sysContact {system 4}
DisplayString Read-Write
The name and address of the contact person for the ELS10-26.
sysName {system 5}
DisplayString Read-Write
The Internet name of the contact person for the ELS10-26. The
LCM prompt consists of sysName followed by “>”. (LCM is a
non-intelligent terminal interface that can be used to configure and
monitor status for the ELS10-26.)
sysLocation {system 6}
DisplayString Read-Write
The physical location of the ELS10-26.
sysServices {system 7}
Integer Read-Only
The sum of the services supported by the ELS10-26. Values
include:
(2) the ELS10-26 is a bridge only
2.2 INTERFACES GROUP
interfaces {mib-2 2}
The TCP/IP Interfaces Group parameters are described below.
2-2
Page 29

TCP/IP MIB-II
ifNumber {interfaces 1}
Integer Read-Only
The number of ports (whether alive or dead), including the UART.
ifTable {interfaces 2}
Not Accessible
A list of interface entries; one per port (ifNumber in total).
ifEntry {ifTable 1}
Not Accessible
A set of objects for an interface entry. The individual components
are described below.
ifIndex {ifEntry 1}
Integer Read-Only
The port number, beginning with 1 for the first port. This number
always matches the instance of the ifEntry. For example, {ifIndex 3}
contains the value “3”.
2-3
Page 30

TCP/IP MIB-II
ifDescr {ifEntry 2}
DisplayString Read-Only
A textual description of the port. One of the following text strings:
• Ethernet/802.3 TP
• Network Management Port (this is the UART port)
• Fast Ethernet/802.3u TP (twisted pair connection)
• Fast Ethernet/802.3u FX (fiber connection)
• Fast Ethenet/802.3u T4 (2 twisted pairs, category 5)
ifType {ifEntry 3}
Integer Read-Only
The type of the port, i.e., one of the following:
• (6) - ethernet-csmacd
• (23) - ppp (for the UART port).
ifMtu {ifEntry 4}
Integer Read-Only
The size (in bytes) of the largest network datagram which may be
sent or received on the port. This does not include the MAC
header, LLC header, and FCS. For CSMA/CD ports, the Ethernet
Frame Type is considered part of the MAC header, but there is no
LLC header. Specifying a value of zero in a SetRequest indicates
that the interface is to default to the largest MTU available for that
media. The effective value is always returned in the GetResponse.
ifSpeed {ifEntry 5}
Integer Read-Only
The port’s estimated MAC-level bandwidth, in bits per second.
The bandwidth will be in the range 1,200 - 100,000,000.
2-4
Page 31

TCP/IP MIB-II
ifPhysAddress {ifEntry 6}
1
Physical Address Read-Write
The MAC address of the port. For the UART port, this field should
be an octet string of zero length.
ifAdminStatus {ifEntry 7}
Integer Read-Write
The desired state of the port, i.e., one of the following:
• up (1) - setting the port’s state to up causes the port’s statistics to
be reset
• down (2) - the port is not to be used
• testing (3) - the port is to be put into local loopback (this value is
not saved if the unit reboots)
ifOperStatus {ifEntry 8}
Integer Read-Only
The current status of the port, i.e., one of the following:
• up (1) - the port can send/receive NMS packets; however,
whether or not the port has its bridging functions enabled is
unknown.
• down (2) - the port is broken, or is intentionally physically
disabled.
• testing (3) - the port is in local loopback.
ifLastChange {ifEntry 9}
TimeTicks Read-Only
The time, in centiseconds relative to sysUpTime, since the port
entered its last state (as defined by ifOperStatus).
1.
The standard MIB definition is Read-Only.
2-5
Page 32

TCP/IP MIB-II
ifInOctets {ifEntry 10}
Counter Read-Only
The total number of bytes received on the port, counting the MAC
header and FCS, but not counting the bytes in packets that were
rejected due to hardware errors. All counters are 32-bit wide
wrap-around counters which can only be reset by restarting the
port or by rebooting the ELS10-26.
ifInUcastPkts {ifEntry 11}
Counter Read-Only
The number of non-multicast packets received by the port,
regardless of the packet’s outcome (i.e., whether the packet was
filtered or forwarded).
ifInNUcastPkts {ifEntry 12}
Counter Read-Only
The number of multicast packets received by the port, regardless of
the packet’s outcome (i.e., whether the packet was filtered or
forwarded).
ifInDiscards {ifEntry 13}
Counter Read-Only
The number of packets received by the port, which were filtered
because of a lack of resources to receive the packet (see
lxifRxQueues).
ifInErrors {ifEntry 14}
Counter Read-Only
The number of packets received by the port, which were discarded
due to hardware reception errors.
ifInUnknownProtos {ifEntry 15}
Read-Only
This value is always zero.
2-6
Page 33

TCP/IP MIB-II
ifOutOctets {ifEntry 16}
Counter Read-Only
The total number of bytes transmitted out the port, counting the
MAC header and FCS.
ifOutUcastPkts {ifEntry 17}
Counter Read-Only
The number of non-multicast packets transmitted out the port,
regardless of whether or not hardware transmission errors were
encountered.
ifOutNUcastPkts {ifEntry 18}
Counter Read-Only
The number of multicast packets transmitted out the port,
regardless of whether or not hardware transmission errors were
encountered.
ifOutDiscards {ifEntry 19}
Counter Read-Only
The number of packets to be transmitted out the port, but were not
transmitted due to non-error reasons. The definition of non-error
reasons is implementation dependent. The ELS10-26 defines
non-error reasons as packet congestion. Packet congestion occurs
when too many packets are to be queued for transmission, or when
packets have been awaiting transmission for too long a time
period.
ifOutErrors {ifEntry 20}
Counter Read-Only
The number of packets that were to be transmitted out the port,
but incurred transmission hardware errors.
2-7
Page 34

TCP/IP MIB-II
ifOutQLen {ifEntry 21}
Gauge Read-Only
The maximum length ever obtained by the port’s outbound packet
queue (in packets) is not available, so this value is always one.
ifSpecific {ifEntry 22}
Object Identifier Read-Only
The object identifier of the MIB for the type of port, i.e., one of the
following:
{dot3} for Ethernet ports (dot3 is defined
later, as {transmission 7}).
{ppp} for the UART (ppp is defined later, as
{experimental 18}).
2.3 ADDRESS TRANSLATION GROUP
at {mib-2 3}
The TCP/IP Address Translation Group parameters are minimally
supported (i.e., for any parameter in this group, the ELS10-26
returns a GetResponse with a noSuchName ErrorStatus). It is
anticipated that the Address Translation Group will be deleted
from TCP/IP MIB III, since there will be separate address
translation tables for every type of network protocol (indeed,
TCP/IP MIB II already defines the IP Address Translation Table).
The TCP/IP Address Translation Group parameters are described
below.
2-8
Page 35

TCP/IP MIB-II
atTable {at 1}
Not Accessible
atEntry {atTable 1}
Not Accessible
atIfIndex {atEntry 1}
Integer Read-Write
All GetResponse PDUs indicate a noSuchName ErrorStatus.
atPhysAddress {atEntry 2}
Physical Address Read-Write
All GetResponse PDUs indicate a noSuchName ErrorStatus.
atNetAddress {atEntry 3}
Network Address Read-Write
All GetResponse PDUs indicate a noSuchName ErrorStatus.
2.4 IP GROUP
ip {mib-2 4)
The TCP/IP IP Group parameters are described below.
ipForwarding {ip 1}
Integer Read-Write
Whether the ELS10-26 is an IP router. This value is always host (2).
Attempts to write a different value to this field will not change its
value, and “badValue” GetResponse PDUs are returned for all
such SetRequest PDUs.
ipDefaultTTL {ip 2}
Integer Read-Write
The value, in seconds, to insert into the Time-To-Live field of the IP
header when this ELS10-26 creates IP datagrams.
2-9
Page 36

TCP/IP MIB-II
ipInReceives {ip 3}
Counter Read-Only
The total number of IP packets received from all ports (including
the UART).
ipInHdrErrors {ip 4}
Counter Read-Only
The number of packets received that were discarded due to errors
in the IP header.
ipInAddrErrors {ip 5}
Counter Read-Only
The number of packets received that were discarded due to an
invalid (or nonroutable) destination IP address in the IP header.
ipForwDatagrams {ip 6}
Counter Read-Only
The number of packets received that were routed towards a final
IP destination.
2
ipInUnknownProtos {ip 7}
Counter Read-Only
The number of packets received that were addressed to this
ELS10-26’s IP, but were discarded because of an unknown or
unsupported protocol.
ipInDiscards {ip 8}
Counter Read-Only
The number of packets that were received without error, but were
not processed (due to insufficient resources, for example).
2.
This appears to be a typographical error in the TCP/IP MIB, since the name
should be ipInForwDatagrams.
2-10
Page 37

TCP/IP MIB-II
ipInDelivers {ip 9}
Counter Read-Only
The total number of input packets successfully delivered to the IP
user-protocol layers.
ipOutRequests {ip 10}
Counter Read-Only
The total number of IP output packets generated by this ELS10-26.
This count does not include any packets represented in
ipForwDatagrams.
ipOutDiscards {ip 11}
Counter Read-Only
The total number of output packets which were discarded (due to
lack of resources, for example). This counter includes packets
which would be included in ipForwDatagrams if any such packets
were discarded.
ipOutNoRoutes {ip 12}
Counter Read-Only
The number of packets which were discarded because no route
could be found to transmit them to their destination. This counter
includes any packets counted in ipForwDatagrams which meet
this “no-route” criterion.
ipReasmTimeout {ip 13}
Integer Read-Only
The maximum time, in seconds, that received fragments are held
while they are awaiting reassembly within this ELS10-26.
ipReasmReqds {ip 14}
Counter Read-Only
The number of IP fragments received which needed to be
reassembled within this ELS10-26.
2-11
Page 38

TCP/IP MIB-II
ipReasmOKs {ip 15}
Counter Read-Only
The number of IP datagrams which were successfully reassembled.
ipReasmFails {ip 16}
Counter Read-Only
The number of failures (for whatever reason timed-out, errors, etc.)
detected by the IP reassembly algorithm. This is not necessarily a
count of discarded IP fragments since some algorithms (notably
RFC 815) can lose track of the number of fragments by combining
them as they are received.
ipFragOKs {ip 17}
Counter Read-Only
The number of IP datagrams that have been successfully
fragmented within this ELS10-26.
ipFragFails {ip 18}
Counter Read-Only
The number of IP datagrams that have been discarded because
they needed to be fragmented but could not be (e.g., because their
“Don’t Fragment” flag was set).
ipFragCreates {ip 19}
Counter Read-Only
The number of IP datagram fragments that have been generated
by this ELS10-26.
2.4.1 IP Address Table
The TCP/IP IP Address Table contains the IP addressing
information for each port. The parameters are described below.
2-12
Page 39

TCP/IP MIB-II
ipAddrTable {ip 20}
Not Accessible
A list of IP address entries; one per IP address. If a port has not yet
learned its IP address, then an ipAddrEntry might not exist for the
port (i.e., having an ipAddrEntry with an IP address of zero is not
acceptable).
ipAddrEntry {ipAddrTable 1}
Not Accessible
A set of objects for an ipAddrTable entry. The individual
components are described below.
ipAdEntAddr {ipAddrEntry 1}
IP Address Read-Only
The IP address itself. Although this field is Read-Only, the
ELS10-26’s lxifIPAddr parameter can be written to affect changes.
ipAdEntIfIndex {ipAddrEntry 2}
Integer Read-Only
The port number which has the indicated IP address.
ipAdEntNetMask {ipAddrEntry 3}
IP Address Read-Only
The network/subnet mask associated with the IP address. For
SetRequests, a mask of zero may be specified, in which case, the
ELS10-26 will create the correct network mask for a non-subnetted
network. For GetRequests, the ELS10-26 will always convert a
value of zero into the correct network mask.
ipAdEntBcastAddr {ipAddrEntry 4}
Integer Read-Only
The value for the least significant bit for broadcasts, i.e., the
constant 1.
2-13
Page 40

TCP/IP MIB-II
ipAdEntReasmMaxSize {ipAddrEntry 5}
Integer Read-Only
The largest IP datagram which can be reassembled, i.e., the
constant 4470.
2.4.2 IP Routing Table
The TCP/IP IP routing table contains the routing information for
each route currently known by the ELS10-26. When adding a row,
the entire row must be specified, except for the following defaults:
• ipRouteDest is obtained from the row’s instance identifier.
• ipRouteMetric1 defaults to 0.
• ipRouteMetric2 defaults to lxadminStaticPreference.
• ipRouteMetric3 through ipRouteMetric5 default to -1.
• ipRouteNextHop is obtained from the row’s instance identifier.
• ipRouteType defaults to “direct” if ipRouteNextHop is not
specified, or if ipRouteNextHop is specified and it, combined
with ipRouteMask, equals the same network as that defined by
ipRouteDest.
• ipRouteProto defaults to “netmgmt”.
• ipRouteMask defaults to the standard network class mask based
on the row’s instance identifier (except 255.255.255.255 is used if
the row’s instance identifier contains a non-zero host portion).
Parameters include the following variables:
ipRouteTable {ip 21}
Not Accessible
A list of routing entries; one per route. An entry is keyed by an IP
address (ipRouteDest, defined below). If there are multiple entries
2-14
Page 41

TCP/IP MIB-II
for the same IP address, then only the entry being used by the IP
forwarding process is available for SNMP access.
ipRouteEntry {ipRouteTable 1}
Not Accessible
A set of objects for an ipRouteTable entry. The individual
components are described below.
ipRouteDest {ipRouteEntry 1}
IP Address Read-Write
The destination IP address of this route.
ipRouteIfIndex {ipRouteEntry 2}
Integer Read-Write
The port number of the next hop.
ipRouteMetric1 {ipRouteEntry 3}
Integer Read-Write
The primary routing metric for this route. This is the zero-based
hop count to ipRouteDest. That is, a hop count of zero indicates
that ipRouteDest is on a directly connected network.
ipRouteMetric2 {ipRouteEntry 4}
Integer Read-Write
An alternative routing metric for this route. This must be greater
than zero.
ipRouteMetric3 {ipRouteEntry 5}
Integer Read-Write
An alternative routing metric for this route.
ipRouteMetric4 {ipRouteEntry 6}
Integer Read-Write
An alternative routing metric for this route.
2-15
Page 42

TCP/IP MIB-II
ipRouteNextHop {ipRouteEntry 7}
IP Address Read-Write
The IP address of the route’s next hop.
ipRouteType {ipRouteEntry 8}
Integer Read-Write
The type of the route, one of the following:
• other (1) - none of the below.
• invalid (2) - the entry should be considered to be non-existent.
• direct (3) - the entry is a route to a directly connected network.
• indirect (4) - the entry is a route to a remote network.
ipRouteProto {ipRouteEntry 9}
Integer Read-Only
The manner in which the route was learned.
ipRouteAge {ipRouteEntry 10}
Integer Read-Write
The number of seconds since the route was last updated or
deemed to be correct.
ipRouteMask {ipRouteEntry 11}
IP Address Read-Write
The mask to be combined with the destination IP address using the
AND operator, before being compared to the value in the
ipRouteDest field.
ipRouteMetric5 {ipRouteEntry 12}
Integer Read-Write
An alternative routing metric for this route.
2-16
Page 43

TCP/IP MIB-II
ipRouteInfo {ipRouteEntry 13}
Object Identifier Read-Write
A reference to additional MIB definitions, specific to the routing
protocol which is responsible for this route. This information is not
present in the ELS10-26, so ipRouteInfo should be set to the object
identifier {0 0}.
2.4.3 IP Address Translation T able
The TCP/IP IP address translation table contains mappings of
Internet addresses to MAC addresses, except for the Internet
addresses of the ELS10-26 itself. The parameters are Read/Write,
according to TCP/IP MIB-II; however, the ELS10-26 has the
restriction that a dynamic entry should not be modified, except to
be made “invalid” (any other modifications will cause a static
entry to be created). When adding a row, the following defaults are
used:
• ipNetToMediaIfIndex is obtained from the row’s instance
identifier.
• ipNetToMediaPhysAddress defaults to 0.
• ipNetToMediaNetAddress is obtained from the row’s instance
identifier.
• ipNetToMediaType defaults to “static”.
Parameters include the following:
ipNetToMediaTable {ip 22}
Not Accessible
A list of IP address translation entries; one per port number and IP
address.
2-17
Page 44

TCP/IP MIB-II
ipNetToMediaEntry {ipNetToMediaTable 1}
Not Accessible
A set of objects for an ipNetToMediaTable entry. The individual
components are described below.
ipNetToMediaIfIndex {ipNetToMediaEntry 1}
Integer Read-Write
The port number for which this entry is effective.
ipNetToMediaPhysAddress {ipNetToMediaEntry 2}
Physical Address Read-Write
The MAC address (for the PPP port, this should be a zero length
octet string; for Ethernet ports, this should be a little-endian six
byte address).
ipNetToMediaNetAddress {ipNetToMediaEntry 3}
IP Address Read-Write
The IP address which corresponds to the ipNetToMediaPhysAddress.
ipNetToMediaType {ipNetToMediaEntry 4}
Integer Read-Write
The type of address mapping, one of the following:
• other (1) - none of the below.
• invalid (2) - the entry should be considered to be non-existent.
• dynamic (3) - the mapping was dynamically learned.
• static (4) - the mapping was statically configured.
2.4.4 IP Additional Objects
The TCP/IP additional IP objects are described below.
2-18
Page 45

TCP/IP MIB-II
ipRoutingDiscards {ip 23}
Counter Read-Only
The number of valid routing entries that were discarded.
2.5 ICMP GROUP
icmp {mib-2 5}
The TCP/IP ICMP Group parameters are described below.
icmpInMsgs {icmp 1}
Counter Read-Only
The total number of ICMP messages which were received by this
ELS10-26. This includes all messages represented by icmpInErrors.
icmpInErrors {icmp 2}
Counter Read-Only
The number of ICMP messages which were received with errors
(bad checksums, bad length, etc.).
icmpInDestUnreachs {icmp 3}
Counter Read-Only
The number of ICMP “Destination Unreachable” messages
received.
icmpInTimeExcds {icmp 4}
Counter Read-Only
The number of ICMP “Time Exceeded” messages received.
icmpInParmProbs {icmp 5}
Counter Read-Only
The number of ICMP “Parameter Problem” messages received.
2-19
Page 46

TCP/IP MIB-II
icmpInSrcQuenchs {icmp 6}
Counter Read-Only
The number of ICMP “Source Quench” messages received.
icmpInRedirects {icmp 7}
Counter Read-Only
The number of ICMP “Redirect” messages received.
icmpInEchos {icmp 8}
Counter Read-Only
The number of ICMP “Echo (request)” messages received.
icmpInEchoReps {icmp 9}
Counter Read-Only
The number of ICMP “Echo Reply” messages received.
icmpInTimestamps {icmp 10}
Counter Read-Only
The number of ICMP “Timestamp (request)” messages received.
icmpInTimestampsReps {icmp 11}
Counter Read-Only
The number of ICMP “Timestamp Reply” messages received.
icmpInAddrMasks {icmp 12}
Counter Read-Only
The number of ICMP “Address Mask Request” messages received.
icmpInAddrMaskReps {icmp 13}
Counter Read-Only
The number of ICMP “Address Mask Reply” messages received.
2-20
Page 47

TCP/IP MIB-II
icmpOutMsgs {icmp 14}
Counter Read-Only
The total number of ICMP messages which were sent by this
ELS10-26. This includes all messages counted by icmpOutErrors.
icmpOutErrors {icmp 15}
Counter Read-Only
The number of ICMP messages which this ELS10-26 did not send
due to problems discovered entirely within the ICMP subsystem
(such as lack of buffers).
icmpOutDestUnreachs {icmp 16}
Counter Read-Only
The number of ICMP “Destination Unreachable” messages sent.
icmpOutTImeExcds {icmp 17}
Counter Read-Only
The number of ICMP “Time Exceeded” messages sent.
icmpOutParmProbs {icmp 18}
Counter Read-Only
The number of ICMP “Parameter Problem” messages sent.
icmpOutSrcQuenchs {icmp 19}
Counter Read-Only
The number of ICMP “Source Quench” messages sent.
icmpOutRedirects {icmp 20}
Counter Read-Only
The number of ICMP “Redirect” messages sent.
icmpOutEchos {icmp 21}
Counter Read-Only
The number of ICMP “Echo (request)” messages sent.
2-21
Page 48

TCP/IP MIB-II
icmpOutEchoReps {icmp 22}
Counter Read-Only
The number of ICMP “Echo Reply” messages sent.
icmpOutTimestamps {icmp 23}
Counter Read-Only
The number of ICMP “Timestamp (request)” messages sent.
icmpOutTimestampReps {icmp 24}
Counter Read-Only
The number of ICMP “Timestamp Reply” messages sent.
icmpOutAddrMasks {icmp 25}
Counter Read-Only
The number of ICMP “Address Mask Request” messages sent.
icmpOutAddrMaskReps {icmp 26}
Counter Read-Only
The number of ICMP “Address Mask Reply” messages sent.
2.6 TCP GROUP
tcp {mib-2 6}
The TCP Group is not supported since the ELS10-26 does not
support TCP.
2.7 UDP GROUP
udp {mib-2 7}
The TCP/IP UDP Group parameters are described below.
2-22
Page 49

TCP/IP MIB-II
udpInDatagrams {udp 1}
Counter Read-Only
The total number of UDP datagrams delivered to UDP users.
udpNoPorts {udp 2}
Counter Read-Only
The total number of received UDP datagrams for which there was
no application at the destination port.
udpInErrors {udp 3}
Counter Read-Only
The number of received UDP datagrams that could not be
delivered for reasons other than the lack of an application at the
destination port.
udpOutDatagrams {udp 4}
Counter Read-Only
The total number of UDP datagrams sent from this ELS10-26.
2.7.1 UDP Listener Table
The TCP/IP UDP Listener Table parameters are described below.
udpTable {udp 5}
Not Accessible
A table containing UDP listener information. The table has entries
for the following UDP port numbers port 69 (default TFTP port
number), port 161 (SNMP port number), and port 520 (RIP port
number).
udpEntry {udpTable 1}
Not Accessible
The entry information of the IP address and UDP port
combination.
2-23
Page 50

TCP/IP MIB-II
udpLocalAddress {udpEntry 1}
IP Address Read-Only
The all zeroes IP address (0.0.0.0), which indicates that the UDP
listener is willing to accept UDP datagrams for any IP address
associated with the ELS10-26.
udpLocalPort {udpEntry 2}
Integer Read-Only
The UDP port number, i.e., one of 69, 161, and 520. Note that
reception of SNMP Traps (UDP port number 162) is not supported
by the ELS10-26.
2.8 EGP GROUP
egp {mib-2 8}
The EGP Group is not supported since the ELS10-26 does not
support EGP.
2.9 OIM SUBTREE
cmot {mib-2 9}
The OSI Subtree, as defined in OSI internet management,
Management Information Base, RFC 1214 (L. LaBarre, editor), dated
April 1991, is not supported.
2.10 TRANSMISSION GROUP
transmission {mib-2 10}
The supported TCP/IP Transmission Group parameters are
described in later sections of this document. The transmission
group supported is:
dot3 {transmission 7}
2-24
Page 51

TCP/IP MIB-II
2.11 SNMP MANAGEMENT GROUP
snmp {mib-2 11}
The TCP/IP SNMP Group parameters are described below.
snmpInPkts {snmp 1}
Counter Read-Only
The number of SNMP PDUs received by the ELS10-26.
snmpOutPkts {snmp 2}
Counter Read-Only
The number of SNMP PDUs created by the ELS10-26.
snmpInBadVersions {snmp 3}
Counter Read-Only
The number of SNMP PDUs received by the ELS10-26 which had
an unsupported SNMP version.
snmpInBadCommunityNames {snmp 4}
Counter Read-Only
The number of SNMP PDUs received by the ELS10-26 which had
an unrecognized SNMP community name.
snmpInBadCommunityUses {snmp 5}
Counter Read-Only
The number of SNMP PDUs received by the ELS10-26 which had
an authentication failure.
snmpInASNParseErrs {snmp 6}
Counter Read-Only
The number of SNMP PDUs received by the ELS10-26 which had
an ASN.1 parsing error while being decoded by the ELS10-26.
2-25
Page 52

TCP/IP MIB-II
snmpInBadTypes {snmp 7}
Counter Read-Only
All GetResponse PDUs indicate a noSuchName ErrorStatus, since
this variable is no longer used.
snmpInTooBigs {snmp 8}
Counter Read-Only
Always zero, since the ELS10-26 ignores all SNMP response PDUs.
snmpInNoSuchNames {snmp 9}
Counter Read-Only
Always zero, since the ELS10-26 ignores all SNMP response PDUs.
snmpInBadValues {snmp 10}
Counter Read-Only
Always zero, since the ELS10-26 ignores all SNMP response PDUs.
snmpInReadOnlys {snmp 11}
Counter Read-Only
Always zero, since the ELS10-26 ignores all SNMP response PDUs.
snmpInGenErrs {snmp 12}
Counter Read-Only
Always zero, since the ELS10-26 ignores all SNMP response PDUs.
snmpInTotalReqVars {snmp 13}
Counter Read-Only
The total number of MIB objects which have been successfully
retrieved by the ELS10-26 as a result of SNMP GetRequest or
GetNext PDUs.
2-26
Page 53

TCP/IP MIB-II
snmpInTotalSetVars {snmp 14}
Counter Read-Only
The total number of MIB objects which have been successfully
altered by the ELS10-26 as a result of SNMP SetRequest PDUs.
snmpInGetRequests {snmp 15}
Counter Read-Only
The total number of SNMP GetRequest PDUs received by the
ELS10-26, which have been processed with no errors.
snmpInGetNexts {snmp 16}
Counter Read-Only
The total number of SNMP GetNext PDUs received by the
ELS10-26, which have been processed with no errors.
snmpInSetRequests {snmp 17}
Counter Read-Only
The total number of SNMP SetRequest PDUs received by the
ELS10-26, which have been processed with no errors.
snmpInGetResponses {snmp 18}
Counter Read-Only
Always zero, since the ELS10-26 ignores all SNMP response PDUs.
snmpInTraps {snmp 19}
Counter Read-Only
Always zero, since the ELS10-26 ignores all SNMP Trap PDUs.
snmpOutTooBigs {snmp 20}
Counter Read-Only
The total number of SNMP PDUs created by the ELS10-26, with a
value of “tooBig” in the PDU’s “ErrorStatus”.
2-27
Page 54

TCP/IP MIB-II
snmpOutNoSuchNames {snmp 21}
Counter Read-Only
The total number of SNMP PDUs created by the ELS10-26, with a
value of “noSuchName” in the PDU’s “ErrorStatus”.
snmpOutBadValues {snmp 22}
Counter Read-Only
The total number of SNMP PDUs created by the ELS10-26, with a
value of “badValue” in the PDU’s “ErrorStatus”.
snmpOutReadOnlys {snmp 23}
Counter Read-Only
All GetResponse PDUs indicate a noSuchName ErrorStatus, since
this variable is no longer used.
snmpOutGenErrs {snmp 24}
Counter Read-Only
The total number of SNMP PDUs created by the ELS10-26, with a
value of “genErr” in the PDU’s “ErrorStatus”.
snmpOutGetRequests {snmp 25}
Counter Read-Only
Always zero, since the ELS10-26 never creates any SNMP request
PDUs.
snmpOutGetNexts {snmp 26}
Counter Read-Only
Always zero, since the ELS10-26 never creates any SNMP request
PDUs.
snmpOutSetRequests {snmp 27}
Counter Read-Only
Always zero, since the ELS10-26 never creates any SNMP request
PDUs.
2-28
Page 55

TCP/IP MIB-II
snmpOutGetResponses {snmp 28}
Counter Read-Only
The total number of SNMP GetResponse PDUs created by the
ELS10-26.
snmpOutTraps {snmp 29}
Counter Read-Only
The total number of SNMP Trap PDUs created by the ELS10-26.
snmpEnableAuthenTraps {snmp 30}
Integer Read-Write
Whether authentication failures should cause the ELS10-26 to
generate authentication-failure Trap PDUs. Values include:
• enabled (1) - generate traps
• disabled (2) - do not generate traps
2.12 CABLETRON INTERFACE GROUP
ctIfTable {ctIf 1}
This table defines an extension to the interface table.
SYNTAX SEQUENCE OF ctIfEntry
ACCESS not accessible
STATUS mandatory
ctIfEntry {ctIfTable 1}
This defines each conceptual row within the ctIfTable.
SYNTAX CtIfEntry
ACCESS not accessible
STATUS mandatory
2-29
Page 56

TCP/IP MIB-II
ctIfNumber {ctIfEntry 1}
This defines the interface that is being described. This is the same
as IfIndex.
SYNTAX INTEGER
ACCESS read-only
STATUS mandatory
ctIfPortCnt {ctIfEntry 2}
This defines the number of ports on the interface that are being
described.
SYNTAX INTEGER
ACCESS read-only
STATUS mandatory
ctIfConnectionType {ctIfEntry 3}
This defines the specific type of interface connection (BRIM, etc.).
This is defined within ctron-oids. This differs from the nature of
the interface as defined by IfType as found in MIB-II.
SYNTAX OBJECT IDENTIFIER
ACCESS read-only
STATUS mandatory
ctIfLAA {ctIfEntry 4}
This object is used by a device (with Token Ring interface) to set a
Locally Administered Address (LAA) for its MAC hardware
address. When set, this LAA will override the default Universally
Administered Address, or burned in address of the interface. For
devices that do not support LAA, a read will return all zeros. Any
write attempt return BADVALUE. For devices that support LAA,
valid values are 4000 0000 0000 to 4000 7fff ffff, and 0000 0000 0000
(a value of all zeros causes interface to use the burned in address).
A set (write) with an invalid value, returns BADVALUE. After a
write, new values will only become active after the Token Ring
2-30
Page 57

TCP/IP MIB-II
interface has been closed and then opened again. A read of
ctIfLAA will always return the same values as IfPhysAddress,
except in the case where; o ctIfLAA has been set, but interface has
not yet been closed and reopened, in this case the last set value is
returned. Note that a read of IfPhysAddress will always return the
physical address currently being used by the interface.
SYNTAX OCTET STRING (SIZE (6))
ACCESS read-write
STATUS mandatory
ctIfDuplex {ctIfEntry 5}
This defines the capability of the underlying hardware in
supporting full duplex. This object will have a value of
fullDuplex(3) if all hardware is capable of supporting full duplex
operation.
SYNTAX INTEGER {other(1), standard(2), full(3)}
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.2.1.1.5
The OID will actually be 1.3.6.1.4.1.52.4.3.3.2.1.1.5.X where X is the
interface number requested. This is what the port is set to, NOT of
what it is capable. It will report full (3) or standard (2) on ethernet
ports, and other (1) for fast ethernet ports. It will report other (1) on
our UART (Local Console Management or PPP) port.
ctIfCapability {ctIfEntry 6}
DESCRIPTION
Defines the capability of the underlying hardware in supporting
full duplex. This object will have a value of fullDuplex (3) if all
hardware is capable of supporting full duplex operation.
2-31
Page 58

TCP/IP MIB-II
SYNTAX INTEGER {other (1), standard (2), fullDuplex
(3), fastEthernet (4)}
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.2.1.1.6
The OID will actually be 1.3.6.1.4.1.52.4.3.3.2.1.1.6.X where X is the
interface number (port number) requested. It will report
fullDuplex (3) on our ethernet ports, and fastEthernet (4) on our
fast ethernet ports. It will report other (1) on our UART (Local
Console Management or PPP) port.
2.13 CABLETRON INTERFACE PORT GROUP
ctIfPortTable {ctIfPort 1}
This table defines an extension to the interface table.
SYNTAX SEQUENCE OF ctIfPortEntry
ACCESS not accessible
STATUS mandatory
ctIfPortEntry {ctIfPortTable 1}
DESCRIPTION
This defines each conceptual row within the ctIfPortTable.
SYNTAX CtIfPortEntry
ACCESS not-accessible
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.3.1.1
INDEX
ctIfPortIfNumber
2-32
Page 59

TCP/IP MIB-II
ctIfPortPortNumber
ctIfPortPortNumber {ctIfPortEntry 1}
This defines the port that is being described.
SYNTAX INTEGER
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.3.1.1.1
The OID will actually be 1.3.6.1.4.1.52.4.3.3.3.1.1.1.X.Y where X is
the interface number and Y is the port requested. X will increment
from 1 to 28 (25 Ethernet, 2 Fast Ethernet, and the LCM port). Y
will always be 1 because there is only one port per interface. We
will always return a value of 1, because there is only one port on
the interface.
ctIfPortIfNumber {ctIfPortEntry 2}
This defines the interface on which the port is being defined.
SYNTAX INTEGER
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.3.1.1.2
The OID will actually be 1.3.6.1.4.1.52.4.3.3.3.1.1.1.X.Y where X is
the interface number and Y is the port requested. X will increment
from 1 to 28 (25 Ethernet, 2 Fast Ethernet, and the LCM port). Y
will always be 1 because there is only one port per interface. We
will return our port number, which will actually be the same as X.
2-33
Page 60

TCP/IP MIB-II
ctIfPortType {ctIfPortEntry 3}
DESCRIPTION
This defines the specific type of port (EPIM, TPIM). This is defined
within ctron-oids.
SYNTAX OBJECT IDENTIFIER
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.3.1.1.3
The OID will actually be 1.3.6.1.4.1.52.4.3.3.3.1.1.1.X.Y where X is
the interface number and Y is the port requested. X will increment
from 1 to 28 (25 Ethernet, 2 Fast Ethernet, and the LCM port). Y
will always be 1 because there is only one port per interface. This
variable should describe the hardware device itself by media type
and type of connection. We have an Ethernet connection to an
RJ45. This means that we will return an OID of
1.3.6.1.4.1.52.3.8.1.1.1.6 to show portRJ45 (CTRON-OIDS):
oid_value_assignment.
ctIfPortLinkStatus {ctIfPortEntry 4}
This defines the status of the port connection.
SYNTAX INTEGER {notLinked(1), linked(2), notApplica-
ble(3)}
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.52.4.3.3.3.1.1.4
The OID will actually be 1.3.6.1.4.1.52.4.3.3.3.1.1.1.X.Y where X is
the interface number and Y is the port requested. We will return
the link status for the ethernet and fast ethernet ports. We will
return notApplicable (3) for the UART port.
2-34
Page 61

TCP/IP MIB-II
2.14 CABLETRON COM PORT CONFIGURATION GROUP
ctCpTable {ctIfCp 1}
This table defines a Com Port Table.
SYNTAX SEQUENCE OF ctCPEntry
ACCESS not accessible
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.4.1
ctCpEntry {ctCpTable 1}
This defines each conceptual row within the ctCpTable.
SYNTAX ctCpEntry
ACCESS not accessible
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.4.1.1
INDEX
ctComPort
ctComPort {ctCpEntry 1}
This is the index into the Com Port Table and defines the Com Port
that is being described. com1 = 1, com2 = 2.
SYNTAX INTEGER
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.4.1.1.1
We only have one UART port. This means the OID will always be
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.4.1.1.1.1, and we will
always return a value of 1.
2-35
Page 62

TCP/IP MIB-II
ctCpFunction {ctCpEntry 2}
DESCRIPTION
This defines the Com Port Function supported by that Com Port.
SYNTAX INTEGER {lm(1), ups(2), slip(3), ppp(4)}
ACCESS read-write
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.4.1.1.2
The OID will actually be 1.3.6.1.4.1.52.4.3.3.4.1.1.2.1 because there
is only one UART port. We support LM and PPP simultaneously. If
we detect a PPP packet we do negotiations and enter into PPP
mode. As long as PPP keeps live messages we’ll stay there. If they
don’t we revert back to VT100 emulation. We will sample the port
at the time the request comes in and return a value of LM (1), or
PPP (4) depending on what state the port is in at the time of the
request.
ctIfNum {ctCpEntry 3}
DESCRIPTION
This defines the interface that is being described. This is the same
as ifIndex. This is only valid if ctCpFunction is PPP, otherwise 0.
SYNTAX INTEGER
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.4.1.1.3
The OID will actually be 1.3.6.1.4.1.52.4.3.3.4.1.1.3.1 because we
only have the one UART port. We will return our port number for
the UART port.
2-36
Page 63

TCP/IP MIB-II
ctCpAdminStatus {ctCpEntry 4}
DESCRIPTION
The administrative state of the Com Port.
SYNTAX INTEGER {disabled(1), enabled(2)}
ACCESS read-only
STATUS mandatory
OBJECT IDENTIFIER: 1.3.6.1.4.1.52.4.3.3.4.1.1.4
The OID will actually be 1.3.6.1.4.1.52.4.3.3.4.1.1.4.1 because we
only have the one UART port.
We don’t allow this port to be turned on or off. Because of this, it
will be READ-ONLY.
It will always return enabled (2).
2.15 SNMP VERSION GROUP
enableSNMPv1 Not Supported {ctSNMP 1}
This object allows control over the SNMPv1 protocol. If set to a
value of disable(1) then the SNMPv1 protocol will not be accepted
by the device.
SYNTAX INTEGER {disabled(1), enabled(2)}
ACCESS read-write
STATUS mandatory
enableSNMPv2 Not Supported {ctSNMP 2}
This allows control over the SNMPv2 protocol. If set to a value of
disable(1) then the SNMPv2 protocol will not be accepted by the
device.
SYNTAX INTEGER {disabled(1), enabled(2)}
ACCESS read-write
2-37
Page 64

TCP/IP MIB-II
STATUS mandatory
2.16 TRAP DESCRIPTION
InterfacePortInsertion Not Supported.
Specific Trap Type Code - 0x1A0
This trap will be generated when it is detected that an interface
port has been inserted. The information will include:
ctIfNumber {ctIfEntry 1}
ctIfPortNumber {ctIfPortEntry 1}
ctPortType {ctIfPortEntry 3}
Specific Trap Type Code - 0x1A1
This trap will be generated when it is detected that an interface
port has been removed. The information will include:
ctIfNumber {ctIfEntry 1}
ctIfPortPortNumber {ctIfPortEntry 1}
InterfacePortLinkUp
Specific Trap Type Code - 0x1A2
This trap will be generated when it is determined that a port on a
strictly bridging interface (not “repeater”) has been connected to a
LAN. This is only appropriate for ports that support the concept of
a link state. The information will include:
ctIfNumber {ctIfEntry 1}
ctIfPortPortNumber {ctIfPortEntry 1}
2-38
Page 65

TCP/IP MIB-II
InterfacePortLinkDown
Specific Trap Type Code - 0x1A3
This trap will be generated when a previously attached bridging
port has been disconnected from a LAN. This is only appropriate
for ports that support the concept of a link state. The information
will include:
ctIfNumber {ctIfEntry 1}
ctIfPortPortNumber {ctIfPortEntry 1}
This trap will be sent when a link goes down.
2.17 CABLETRON MIB 2 EXTENSIONS
ctmib2-ext-mib Cabletron’s extension to the MIB-II
This module provides authoritative definitions for part of the
naming tree below:
cabletron {enterprises 52}
This module will be extended, as additional sub-sections of this
naming tree are defined.
IMPORTS ctronMib2FROM CTRON-MIB-NAMES OBJECT-TYPE
FROM RFC-1212
Textual Convention
DisplayString ::= OCTET STRING
This data type is used to model textual information from the NVT
ASCII character set. By convention, objects of this syntax are
declared as having: SIZE (0.255)
2-39
Page 66

TCP/IP MIB-II
This MIB defines Cabletron extensions to MIB-II. Groups within
this MIB refer to the group in which the objects pertain within
MIB-II.
Groups within this MIB are:
commonDevOBJECT IDENTIFIER {ctronMib2 1}
ctIfPortOBJECT IDENTIFIER {ctronMib2 2}
ctIfPortOBJECT IDENTIFIER {ctronMib2 3}
ctIfCpOBJECT IDENTIFIER {ctronMib2 4}
ctSNMP OBJECT IDENTIFIER {ctronMib2 5}
ctSONET OBJECT IDENTIFIER {ctronMib2 6}
The commonDevice group of this group is an extension to the
system group MIB2. It contains similar information to that defined
within the system group of MIB-II.
Implementation of this group is optional for Cabletron devices.
comDeviceTime
OBJECT-TYPE
SYNTAX DisplayString(SIZE (8))
ACCESS read-write
STATUS mandatory
DESCRIPTION The current time of day, in 24 hour
format, as measured by the device.
The representation shall use the stan-
dard HHMMSS format.
::= {commonDev 1}
comDeviceDate
2-40
Page 67

OBJECT-TYPE
SYNTAX DisplayString(SIZE (8))
ACCESS read-write
STATUS mandatory
DESCRIPTION The current date, as measured by the
::= {commonDev 2}
comDeviceBoardMap
OBJECT-TYPE
SYNTAXINTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION Contains a bit encoded representa-
TCP/IP MIB-II
device. The representation shall use
the standard MMDDYY format.
tion of slots that contain MIM
boards. If a bit is one, then that slot is
occupied by a board.
::= {commonDev 3}
ctIF group implementation of this group is optional.
The ctIf group contains information about the type of interface, i.e.
the type of BRIM etc. This information is not available in the
interface group of MIB-II.
ctIfTable
OBJECT-TYPE
SYNTAXSEQUENCE OF CtIfEntry
ACCESS not accessible
STATUS mandatory
DESCRIPTION This table defines an extension to the
interface table.
2-41
Page 68

TCP/IP MIB-II
::= {ctIf 1}
ctIfEntry
OBJECT-TYPE
SYNTAXCtIfEntry
ACCESS not accessible
STATUS mandatory
DESCRIPTION This defines each conceptual row
INDEX {ctIfNumber}
::= {ctIfTable 1}
CtIfEntry::=
SEQUENCE
{ctIfNumber INTEGER,
ctIfPortCnt INTEGER,
ctIfConnectionType OBJECT IDENTIFIER,
ctIfLAA OCTET STRING,
ctIfDuplex INTEGER,
ctIfCapability INTEGER,
ctIfRedundancy INTEGER }
within the ctIfTable.
ctIfNumber
OBJECT-TYPE
SYNTAXINTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION This defines the interface that is
2-42
being described. This is the same as
ifIndex.
Page 69

::= {ctIfEntry 1}
ctIfPortCnt
OBJECT-TYPE
SYNTAXINTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION This defines the number of ports on
INDEX {ctIfNumber}
::= {ctIfEntry 2}
ctIfConnectionType
OBJECT-TYPE
SYNTAXOBJECTIDENTIFIER
ACCESS read-only
STATUS mandatory
DESCRIPTION Defines the specific type of interface
INDEX {ctIfNumber}
TCP/IP MIB-II
the interface that is being described.
connection (BRIM etc.). This is
defined within ctron-oids. This differs from the nature of the interface
as defined by ifType as found in
MIB-II.
::= {ctIfEntry 3}
ctIfLAA
OBJECT-TYPE
SYNTAXOCTET STRING (SIZE (6))
ACCESS read-write
2-43
Page 70

TCP/IP MIB-II
STATUS mandatory
DESCRIPTION This object is used by a device (with
a Token Ring interface) to set a
Locally Administered Address
(LAA) for its MAC hardware
address. When set, this LAA will
override the default Universally
Administered Address or burned-in
address of the interface.
For devices that do not support LAA:
a read will return all zeroes
any write attempt will return BADVALUE
For devices that suport LAA:
valid values are 4000 0000 0000 to 4000 7fff ffff, and 0000
0000 0000 (a value of all zeroes causes interface to use the
burned-in address).
a set (write) with an invalid value returns BADVALUE.
after a write, new values will only become active after
Token Ring interface has been closed and then opened
again.
a read of ctIfLAA will always return the same value as
ifPhysAddress, except in the case where; o ctIfLAA has
been set, but interface has not yet been closed and
re-opened. In this case the last set value is returned.
Note that a read of ifPhysAddress will always return the
physical address currently being used by the interface.
::= {ctIfEntry 4}
ctIfDuplex
OBJECT-TYPE
SYNTAXINTEGER {other (1), standard (2), full (3)}
ACCESS read-write
2-44
Page 71

STATUS mandatory
DESCRIPTION Defines the specific type of interface
connection (BRIM etc.). Defines the
duplex mode in which the interface
is set to operate.
For devices that do not support this capability:
a read will return standard (2).
any write attempt will return BADVALUE.
fast ethernet devices will report other (1).
::= {ctIfEntry 5}
ctIfCapability
OBJECT-TYPE
SYNTAXINTEGER {other (1), standard (2), full duplex
(3), fastEthernet (4)}
ACCESS read-only
STATUS mandatory
DESCRIPTION Defines the capability of the underly-
ing hardware in supporting full
duplex. This object will have a value
of fullDuplex (3) if all hardware is
capable of supporting full duplex
operation.
TCP/IP MIB-II
::= {ctIfEntry 6}
ctIfRedundancy
OBJECT-TYPE
SYNTAXINTEGER {redundant (1), not-redundant (2)}
ACCESS read-only
STATUS mandatory
2-45
Page 72

TCP/IP MIB-II
DESCRIPTION Defines whether or not an interface
supports redundancy.
::= {ctIfEntry 7}
ctIfPort group implementation of this group is optional
The ctIfPort group contains information about the type of port on
the interface i.e., the type of EPIM,TPIM etc. This information is
not available in the interface group of MIB-II.
ctIfPortTable
OBJECT-TYPE
SYNTAXSEQUENCEOF CtIfPortEntry
ACCESS not accessible
STATUS mandatory
DESCRIPTION This defines each conceptual row
within the ctIfPortTable.
INDEX {ctIfPortNumber}
ctIfPortPortNumber
::= {ctIfPortTable 1}
ctIfPortEntry
OBJECT-TYPE
SYNTAX {CtIfPortPortNumber}
ACCESS not accessible
STATUS mandatory
DESCRIPTION This defines each conceptual row
INDEX {ctIfPortNumber}
2-46
within the ctIfPortTable.
ctIfPortPortNumber
Page 73

::= {ctIfPortTable 1}
ctIfPortEntry::=
SEQUENCE
{ctIfPortPortNumber INTEGER,
ctIfPortIfNumber INTEGER,
ctIfPortType OBJECT IDENTIFIER,
ctIfPortLinkStatus INTEGER}
ctIfPortPortNumber
OBJECT-TYPE
SYNTAX
INTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION This defines the port being
TCP/IP MIB-II
described.
::= {ctIfPortEntry 1}
ctIfPortIfNumber
OBJECT-TYPE
SYNTAX
INTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION This defines the interface that the
port being described is on.
2-47
Page 74

TCP/IP MIB-II
::= {ctIfPortEntry 2}
ctIfPortType
OBJECT-TYPE
SYNTAX OBJECT IDENTIFIER
ACCESS read-only
STATUS mandatory
DESCRIPTION Defines the specific type of the port
::= {ctIfPortEntry 3}
ctIfPortLinkStatus
OBJECT-TYPE
SYNTAX
INTEGER {not linked (1), linked (2), notAppli-
ACCESS read-only
STATUS mandatory
DESCRIPTION Defines the status of the port connec-
(EPIM,TPIM). This is defined within
ctron oids.
cable (3).}
tion.
::= {ctIfPortEntry 4}
ctIfPort group implementation of this group is optional
The ctIfCp group contains information about the com port
configuration on the MMAC Management Modules (i.e., EMME,
TRMM) and on the MMAC-Plus Environmental Module.
ctCpTable
OBJECT-TYPE
SYNTAXSEQUENCEOF CtIfCpEntry
2-48
Page 75

ACCESS not accessible
STATUS mandatory
DESCRIPTION This table defines a Com Port Table.
::= {ctIfCp 1}
ctCpEntry
OBJECT-TYPE
SYNTAX CtCpEntry
ACCESS not accessible
STATUS mandatory
DESCRIPTION This defines each conceptual row
INDEX {ctComPort}
::= {ctCpTable 1}
TCP/IP MIB-II
within the ctCpTable.
ctCpEntry::=
SEQUENCE
{ctComPort INTEGER,
ctCpFunction INTEGER,
ctIfNum INTEGER,
ctCpAdminStatus INTEGER}
ctComPort
OBJECT-TYPE
SYNTAXINTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION This is the index into the Com Port
Table and defines the Com Port that
2-49
Page 76

TCP/IP MIB-II
{ctCpEntry 1}
ctCpFunction
OBJECT-TYPE
SYNTAXINTEGER {lm(1), Local Management (default),
ACCESS read-write
STATUS mandatory
DESCRIPTION Defines the Com Port Function sup-
{ctCpEntry 2}
is being described. com1 = 1,
com2 = 2
ups (2) UPS, slip (3) SLIP, ppp
(4) PPP}
ported by that Com Port.
ctIfNum
OBJECT-TYPE
SYNTAXINTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION This defines the interface that is
{ctCpEntry 3}
ctCpAdminStatus
OBJECT-TYPE
SYNTAXINTEGER {disabled (1), enabled (2) (default)}
ACCESS read-write
2-50
being described. This is the same as
ifIndex. This is only valid if ctCpFunction is SLIP or PPP, otherwise 0.
Page 77

TCP/IP MIB-II
STATUS mandatory
DESCRIPTION The administrative state of the Com
Port.
{ctCpEntry 4}
The SNMP group. Implementation of this group is mandatory
when the SNMPv2 protocol is present within the device.
enableSNMPv1
OBJECT-TYPE
SYNTAXINTEGER {disable (1), enable (2)}
ACCESS read-write
STATUS mandatory
DESCRIPTION This object allows control over the
SNMPv1 protocol. If set to a value of
disable (1) then the SNMPv1 proto-
col will not be accepted by the
device.
{ctSNMP 1}
enableSNMPv2
OBJECT-TYPE
SYNTAXINTEGER {disable (1), enable (2)}
ACCESS read-write
STATUS mandatory
DESCRIPTION This object allows control over the
SNMPv2 protocol. If set to a value of
disable (1) then the SNMPv2 proto-
col will not be accepted by the
device.
2-51
Page 78

TCP/IP MIB-II
{ctSNMP 2}
{ctSNMP 3} is obsolete
The ctSonet group is an optional group. It contains information
pertaining to the optical connectivity speed.
ctSonetEntry
OBJECT-TYPE
SYNTAXSEQUENCEOF CtSonetEntry
ACCESS not accessible
STATUS mandatory
DESCRIPTION This table defines the Sonet table.
INDEX {ctSonetIfIndex}
{ctSonetTable 1}
CtSonetEntry::=
SEQUENCE
{ctSonetIfIndex INTEGER,
ctSonetMediumType INTEGER}
ctSonetIfIndex
OBJECT-TYPE
SYNTAX
INTEGER
ACCESS read-only
STATUS mandatory
DESCRIPTION This defines the interface being
2-52
described. It is the same as IfIndex.
Page 79

{ctSonetEntry 1}
ctSonetMediumType
OBJECT-TYPE
SYNTAX
INTEGER {sonet (1), sdh (2)}
ACCESS read-write
STATUS mandatory
DESCRIPTION This variable identifies whether a
SONET or an SDH signal is used
across this interface.
{ctSonetEntry 2}
Trap description
InterfacePortInsertion
Specific Trap Type Code- 0x1A0
TCP/IP MIB-II
This trap will be generated when it is detected that an interface
port has been inserted. The interesting information will include:
ctIfNumber {ctIfEntry 1}, ctIfPortPortNumber
{ctIfPortEntry 1}, ctIfPortType
{ctIfPortEntry 3}
Trap description
InterfacePortInsertion
Specific Trap Type Code - 0x1A1
This trap will be generated when it is determined that a port has
been removed. The interesting information will include:
ctIfNumber {ctIfEntry 1}, ctIfPortPortNumber
{ctIfPortEntry 1},
Trap description
InterfacePortLinkUp
2-53
Page 80

TCP/IP MIB-II
Specific Trap Type Code - 0x1A2
This trap will be generated when it is determined that a port on a
strictly bridging interface (not a “repeater”) has been connected to
a LAN. This is only appropriate for ports that support the concept
of a link state. The interesting information will include:
ctIfNumber {ctIfEntry 1}, ctIfPortPortNumber
{ctIfPortEntry 1},
Trap description
InterfacePortLinkDown
Specific Trap Type Code - 0x1A3
2-54
Page 81

CHAPTER 3
ETHERNET MIB
The ELS10-26 supports the Ethernet MIB as defined in Definitions of
Managed Objects for the Ethernet-like Interface Types, RFC 1284
(J. Cook, editor), dated December 1991.
The MIB tree prefix for reaching the GenericIF group is:
1.3.6.1.2.1.12.
3.1 GENERIC ETHERNET-LIKE GROUP
dot3Table {dot3 1}
Not Accessible
A list of interface entries; one per Ethernet port. The entry
instances correspond to the ELS10-26’s port numbers.
dot3Entry {dot3Table 1}
Not Accessible
A set of operational attributes for an Ethernet entry. The individual
components are described below.
dot3Index {dot3Entry 1}
Integer Read-Only
The ELS10-26’s Ethernet port number.
dot3InitializeMAC {dot3Entry 2}
Integer Read-Write
Whether the port has been initialized. Initializing a port
automatically resets all of the port’s statistics, and enables transmit
and receive (the receiver will be in promiscuous mode). The value
of dot3InitializeMAC is not saved in the event that the ELS10-26
reboots. Values include:
• initialized (1)
• uninitialized (2)
3-1
Page 82

Ethernet MIB
dot3MACSubLayerStatus {dot3Entry 3}
Integer Read-Write
Treated identically to dot3InitializeMAC. Values include:
• enabled (1)
• disabled (2)
dot3MulticastReceiveStatus {dot3Entry 4}
Integer Read-Write
Whether the port is able to receive multicasts. This is always
enabled when the port is enabled, and always disabled when the
port is disabled. Values include:
• enabled (1)
• disabled (2)
dot3TxEnabled {dot3Entry 5}
Integer Read-Write
Whether the port is able to transmit. This is always enabled when
the port is enabled, and always disabled when the port is disabled.
Values include:
• true (1)
• false (2)
dot3TestTdrValue {dot3Entry 6}
Gauge Read-Only
Always zero, since the results of TDR tests are not available.
3.2 ETHERNET-LIKE STATISTICS GROUP
The dot3StatsTable is specified in a unique manner. That is, the
RFC specifies that value of 0 should be returned for counters that
are not implemented.
3-2
Page 83

Ethernet MIB
dot3StatsTable {dot3 2}
Not Accessible
A list of interface entries; one per Ethernet port, which correspond
to the dot3Table entries.
dot3StatsEntry {dot3StatsTable 1}
Not Accessible
A set of statistics for an Ethernet entry. The individual components
are described below.
dot3StatsIndex {dot3StatsEntry 1}
Integer Read-Only
The ELS10-26’s Ethernet port number.
dot3StatsAlignmentErrors {dot3StatsEntry 2}
Counter Read-Only
Number of received packets with frame alignment errors since the
port was last enabled.
dot3StatsFCSErrors {dot3StatsEntry 3}
Counter Read-Only
Number of received packets with FCS errors (and without frame
alignment errors) since the port was last enabled.
dot3StatsSingleCollisionFrames {dot3StatsEntry 4}
Counter Read-Only
The number of frames that experienced a single collision.
dot3StatsMultipleCollisionFrames {dot3StatsEntry 5}
Counter Read-Only
The number of successfully transmitted frames that experienced
more than one collision.
3-3
Page 84

Ethernet MIB
dot3StatsSQETestErrors {dot3StatsEntry 6}
Counter Read-Only
The number of times an SQE failure (i.e., heartbeat lost) occurred,
since the port was last enabled.
dot3StatsDeferredTransmissions {dot3StatsEntry 7}
Counter Read-Only
The number of frames for which the first transmission attempt was
successful, but delayed because the medium was busy.
dot3StatsLateCollisions {dot3StatsEntry 8}
Counter Read-Only
The number of times that a late collision was detected while the
ELS10-26 was transmitting a frame.
dot3StatsExcessiveCollisions {dot3StatsEntry 9}
Counter Read-Only
The number of times a frame transmission attempt experienced
excessive collisions, since the port was last enabled.
dot3StatsInternalMACTransmitErrors {dot3StatsEntry 10}
Counter Read-Only
The number of times a frame transmission attempt experienced an
error other than dot3StatsSQETestErrors,
dot3StatsExcessiveCollisions, or dot3StatsCarrierSenseErrors,
since the port was last enabled.
dot3StatsCarrierSenseErrors {dot3StatsEntry 11}
Counter Read-Only
The number of times that a carrier sense condition was lost during
a transmission attempt, since the port was last enabled.
3-4
Page 85

Ethernet MIB
dot3StatsExcessiveDeferrals {dot3StatsEntry 12}
Counter Read-Only
The number of times that transmission was deferred for an
excessive period of time.
dot3StatsFrameTooLongs {dot3StatsEntry 13}
Counter Read-Only
The number of times a received packet was too long, since the port
was last enabled.
dot3StatsInRangeLengthErrors {dot3StatsEntry 14}
Counter Read-Only
The number of received frames with an incorrect LLC data size.
Zero is always returned.
dot3StatsOutOfRangeLengthErrors {dot3StatsEntry 15}
Counter Read-Only
The number of received frames with an LLC data size that is too
large (not including frames that have an Ethernet frame type field).
Zero is always returned.
dot3StatsInternalMACReceiveErrors {dot3StatsEntry 16}
Counter Read-Only
The number of times a frame reception failed due to an error
condition not already accounted for, since the port was last
enabled.
3.3 ETHERNET-LIKE COLLISION STATISTICS GROUP
dot3CollTable {dot3 5}
This group is minimally supported (i.e., the ELS10-26 returns a
GetResponse with a noSuchName ErrorStatus).
3-5
Page 86

Ethernet MIB
3.4 ETHERNET-LIKE TESTS GROUP
dot3Tests {{dot3 6}
There are no MIB variables in this group.
3.5 ETHERNET-LIKE ERRORS GROUP
dot3Errors {dot3 7}
There are no MIB variables in this group.
3.6 ETHERNET-LIKE CHIPSETS GROUP
dot3ChipSets {dot3 8}
There are no MIB variables in this group.
3-6
Page 87

CHAPTER 4
BRIDGE MIB
The ELS10-26 supports the Bridge MIB {mib-2 17} as defined in
Definitions of Managed Objects for Bridges, RFC 1286 (Decker,
Langille, Rijsinghani, and McCloghrie, editors).
The MIB tree prefix for reaching the Bridge MIB-II is:
1.3.6.1.2.1.17
4.1 BASE GROUP
dot1dBase {dot1dBridge 1}
dot1dBaseBridgeAddress {dot1dBase 1}
Octet String Read-Only
The MAC address used by this bridge when it must be referred to
in a unique fashion. It is recommended that this be the numerically
smallest MAC address of all ports that belong to this bridge.
However it is only required to be unique. When concatenated with
dot1dStpPriority a unique BridgeIdentifier is formed which is used
in the Spanning Tree Protocol.
The ELS10-26 dot1dBaseBridgeAddress is the MAC address of
port 1.
dot1dBaseNumPorts {dot1dBase 2}
Integer Read-Only
The number of ports controlled by this bridging entity.
Identical to ifNumber; however, the ELS10-26 prevents bridging
from being enabled for the last (port 25), which is reserved for
out-of-band management.
4-1
Page 88

Bridge MIB
dot1dBaseType {dot1dBase 3}
Integer Read-Only
Indicates what type of bridging this bridge can perform. If a bridge
is actually performing a certain type of bridging this will be
indicated by entries in the port table for the given type.
The ELS10-26 is always transparent-only (2).
dot1dBasePortTable {dot1dBase 4}
Not Accessible
A table that contains generic information about every port that is
associated with this bridge.
All ELS10-26 Ethernet ports are included in this table, regardless of
whether any form of bridging is currently enabled for the ports.
dot1dBasePortEntry {dot1dBasePortTable 1}
Not Accessible
A list of information for each port of the bridge.
dot1dBasePort {dot1dBasePortEntry 1}
Integer Read-Only
The port number of the port for which this entry contains bridge
management information.
Identical to dot1dBasePortIfIndex.
dot1dBasePortIfIndex {dot1dBasePortEntry 2}
Integer Read-Only
The value of the instance of the ifIndex object for the interface
corresponding to this port.
dot1dBasePortCircuit {dot1dBasePortEntry 3}
Object Identifier Read-Only
For a port which (potentially) has the same value of
dot1dBasePortIfIndex as another port on the same bridge, this
object contains the name of an object instance unique to this port.
4-2
Page 89

Bridge MIB
For example, in the case where multiple ports correspond
one-to-one with multiple X.25 virtual circuits, this value might
identify an (e.g., the first) object instance associated with the X.25
virtual circuit corresponding to this port. For a port which has a
unique value of dot1dBasePortIfIndex, this object can have the
value {0 0}.
Always {0 0}.
dot1dBasePortDelayExceededDiscards {dot1dBasePortEntry 4}
Counter Read-Only
The number of frames discarded by this port due to excessive
transit delay through the bridge.
dot1dBasePortMtuExceededDiscards {dot1dBasePortEntry 5}
Counter Read-Only
The number of frames discarded by this port due to an excessive
size.
4.2 SPANNING TREE GROUP
dot1dStp {dot1dBridge 2}
dot1dStpProtocolSpecification {dot1dStp 1}
Integer Read-Only
An indication of what version of the Spanning Tree Protocol is
being run. The value decLb100(2) indicates the DEC LANbridge
100 Spanning Tree protocol. IEEE 802.1d implementations will
return ieee8021d(3). If future versions of the IEEE Spanning Tree
Protocol are released that are incompatible with the current
version a new value will be defined.
Always iee8021d (3).
4-3
Page 90

Bridge MIB
dot1dStpPriority {dot1dStp 2}
Integer Read-Write
The value of the write-able portion of the Bridge ID, i.e., the first
two octets of the (8 octet long) Bridge ID. The other (last) 6 octets of
the Bridge ID are given by the value of dot1dBaseBridgeAddress.
Any value from 0 to 65535 may be specified.
dot1dStpTimeSinceTopologyChange {dot1dStp 3}
Time Ticks Read-Only
The time (in hundredths of a second) since the last time a topology
change was detected by the bridge entity.
Zero if a topology change is in progress; otherwise, the time since
the topology last stabilized.
dot1dStpTopChanges {dot1dStp 4}
Counter Read-Only
The total number of topology changes detected by this bridge since
the management entity was last reset or initialized.
dot1dStpDesignatedRoot {dot1dStp 5}
Octet String Read-Only
The bridge identifier of the root of the spanning tree as determined
by the Spanning Tree Protocol as executed by this node. This value
is used as the Root Identifier parameter in all Configuration Bridge
PDUs originated by this node.
dot1dStpRootCost {dot1dStp 6}
Integer Read-Only
The cost of the path to the root as seen from this bridge.
dot1dStpRootPort {dot1dStp 7}
Integer Read-Only
The port number of the port which offers the lowest cost path from
this bridge to the root bridge.
4-4
Page 91

Bridge MIB
Port number of this bridge’s current spanning tree root port, or 0, if
this bridge is the current spanning tree root bridge.
dot1dStpMaxAge {dot1dStp 8}
Integer Read-Only
The maximum age of Spanning Tree Protocol information learned
from the network on any port before it is discarded, in units of
hundredths of a second. This is the actual value that this bridge is
currently using.
dot1dStpHelloTime {dot1dStp 9}
Integer Read-Only
The amount of time between the transmission of Configuration
bridge PDUs by this node on any port when it is the root of the
spanning tree or trying to become so, in units of hundredths of a
second. This is the actual value that this bridge is currently using.
dot1dStpHoldTime {dot1dStp 10}
Integer Read-Only
This time value determines the interval length during which no
more than two Configuration bridge PDUs shall be transmitted by
this node, in units of hundredths of a second.
dot1dStpForwardDelay {dot1dStp 11}
Integer Read-Only
This time value, measured in units of hundredths of a second,
controls how fast a port changes its spanning state when moving
towards the Forwarding state. The value determines how long the
port stays in a particular state before moving to the next state. For
example, how long a port stays in the Listening state when moving
from Blocking to Learning. This value is also used, when a
topology change has been detected and is underway, to age all
dynamic entries in the Forwarding Database.
Note: This value is the one that this bridge is currently using, in contrast
to dot1dStpBridgeForwardDelay which is the value that this bridge
4-5
Page 92

Bridge MIB
and all others would start using if/when this bridge were to become
the root.
dot1dStpBridgeMaxAge {dot1dStp 12}
Time Ticks Read-Write
The value that all bridges use for MaxAge when this bridge is
acting as the root. Note that 802.1d/D9 specifies that the range for
this parameter is related to the value of dot1dStpBridgeHelloTime.
The granularity of this timer is specified by 802.1d/D9 to be 1
second. An agent may return a badValue error if a set is attempted
to a value which is not a whole number of seconds.
The Max Age Time must be at least 6 seconds, and must adhere to
the following equations involving Max Age Time, Forward Delay
Time, and Hello Time:
2 x (Forward Delay Time - 1) >= Max Age Time
Max Age >= 2 x (Hello Time + 1)
dot1dStpBridgeHelloTime {dot1dStp 13}
Time Ticks Read-Write
The value that all bridges use for HelloTime when this bridge is
acting as the root. The granularity of this timer is specified by
802.1d/D9 to be 1 second. An agent may return a badValue error if
a set is attempted to a value which is not a whole number of
seconds.
The Hello Time must adhere to the equation described in the
variable dot1dStpBridgeMaxAge, involving Max Age Time and
Hello Time.
dot1dStpBridgeForwardDelay {dot1dStp 14}
Time Ticks Read-Write
The value that all bridges use for ForwardDelay when this bridge
is acting as the root. Note that 802.1d/D9 specifies that the range
for this parameter is related to the value of
dot1dStpBridgeMaxAge. The granularity of this timer is specified
4-6
Page 93

Bridge MIB
by 802.1d/D9 to be 1 second. An agent may return a badValue
error if a set is attempted to a value which is not a whole number
of seconds.
The Forward Delay Time must be at least 4 seconds, and must
adhere to the aforementioned equation involving Max Age Time
and Forward Delay Time.
dot1dStpPortTable {dot1dStp 15}
Not Accessible
A table that contains port-specific information for the Spanning
Tree Protocol.
All ELS10-26 ports, except for the last port (port 25), are included
in this table, regardless of whether the Spanning Tree Protocol is
currently enabled for the ports.
dot1dStpPortEntry {dot1dStpTable 1}
Not Accessible
A list of information maintained by every port about the Spanning
Tree Protocol state for that port.
dot1dStpPort {dot1dStpPortEntry 1}
Integer Read-Only
The port number of the port for which this entry contains
Spanning Tree Protocol management information.
dot1dStpPortPriority {dot1dStpPortEntry 2}
Integer Read-Write
The value of the priority field which is contained in the first (in
network byte order) octet of the (2 octet long) Port ID. The other
octet of the Port ID is given by the value of dot1dStpPort.
Any value from 0 to 255 may be specified.
4-7
Page 94

Bridge MIB
dot1dStpPortState {dot1dStpPortEntry 3}
Integer Read-Only
The port’s current state as defined by application of the Spanning
Tree Protocol. This state controls what action a port takes on
reception of a frame. If the bridge has detected a port that is
malfunctioning it will place that port into the broken (6) state. For
ports which are disabled (see dot1dStpPortEnable), this object will
have a value of disabled (1).
dot1dStpPortEnable {dot1dStpPortEntry 4}
Integer Read-Write
The enabled/disabled status of the port.
The ELS10-26 does not change the parameter’s value when
processing a SetRequest - refer to the lxsprotoBridge parameter in
Cabletron’s enterprise-specific MIB for the SetRequest capabilities.
dot1dStpPortPathCost {dot1dStpPortEntry 5}
Integer Read-Write
The contribution of this port to the path cost of paths towards the
spanning tree root which include this port.
Any value from 0 to 65535 may be specified; specifying a value of 0
will cause the ELS10-26 to automatically compute the proper
default value.
1
dot1dStpPortDesignatedRoot {dot1dStpPortEntry 6}
Octet String Read-Only
The unique Bridge Identifier of the Bridge recorded as the Root in
the Configuration BPDUs transmitted by the Designated Bridge
for the segment to which the port is attached.
1.
The proper default is the inverse of the media baud rate (e.g., 10 for FDDI, 100
for Ethernet). The effective value is always returned in the GetResponse.
4-8
Page 95

Bridge MIB
dot1dStpPortDesignatedCost {dot1dStpPortEntry 7}
Integer Read-Only
The path cost of the Designated Port of the segment connected to
this port. This value is compared to the Root Path Cost field in
received bridge PDUs.
dot1dStpPortDesignatedBridge {dot1dStpPortEntry 8}
Octet String Read-Only
The Bridge Identifier of the bridge which this port considers to be
the Designated Bridge for this port’s segment.
dot1dStpPortDesignatedPort {dot1dStpPortEntry 9}
Octet String Read-Only
The Port Identifier of the port on the Designated Bridge for this
port’s segment.
dot1dStpPortForwardTransitions {dot1dStpPortEntry 10}
Counter Read-Only
The number of times this port has transitioned from the Learning
state to the Forwarding state.
4.3 TRANSPARENT GROUP
do1dTp {dot1dBridge 4}
dot1dTpLearnedEntryDiscards {dot1dTp 1}
Counter Read-Only
The total number of Forwarding Database entries, which have
been or would have been learned, but have been discarded due to
a lack of space to store them in the Forwarding Database. If this
counter is increasing, it indicates that the Forwarding Database is
regularly becoming full (a condition which has unpleasant
performance effects on the subnetwork). If this counter has a
significant value but is not presently increasing, it indicates that
the problem has been occurring but is not persistent.
4-9
Page 96

Bridge MIB
dot1dTpAgingTime {dot1dTp 2}
Integer Read-Write
The timeout period in seconds for aging out dynamically learned
forwarding information.
dot1dTpFdbTable {dot1dTp 3}
Not Accessible
A table that contains information about unicast entries for which
the bridge has forwarding and/or filtering information. This
information is used by the transparent bridging function in
determining how to propagate a received frame.
A superset of this table’s information can be found by using
Cabletron’s enterprise-specific Addresses Configuration Group.
dot1dTpFdbEntry {dot1dTpFdbTable 1}
Not Accessible
Information about a specific unicast MAC address for which the
bridge has some forwarding and/or filtering information.
dot1dTpFdbAddress {dot1dTpFdbEntry 1}
Octet String Read-Only
A unicast MAC address for which the bridge has forwarding and/
or filtering information.
dot1dTpFdbPort {dot1dTpFdbEntry 2}
Integer Read-Only
Either the value 0, or the port number of the port on which a frame
having a source address equal to the value of the corresponding
instance of dot1dTpFdbAddress has been seen. A value of 0
indicates that the port number has not been learned but that the
bridge does have some forwarding/filtering information about
this address (e.g., in the dot1dStaticTable). Implementors are
encouraged to assign the port value to this object whenever it is
learned even for addresses for which the corresponding value of
dot1dTpFdbStatus is not learned(3).
4-10
Page 97

Bridge MIB
dot1dTpFdbStatus {dot1dTpFdbEntry 3}
Integer Read-Only
The status of this entry. The meanings of the values are other (1)
none of the following. This would include the case where some
other MIB object (not the corresponding instance of
dot1dTpFdbPort, nor an entry in the dot1dStaticTable) is being
used to determine if and how frames addressed to the value of the
corresponding instance of dot1dTpFdbAddress are being
forwarded. invalid (2) this entry is not longer valid (e.g., it was
learned but has since aged-out), but has not yet been flushed from
the table. learned (3) the value of the corresponding instance of
dot1dTpFdbPort was learned, and is being used. self (4) the value
of the corresponding instance of dot1dTpFdbAddress represents
one of the bridge’s addresses. The corresponding instance of
dot1dTpFdbPort indicates which of the bridge’s ports has this
address. mgmt (5) the value of the corresponding instance of
dot1dTpFdbAddress is also the value of an existing instance of
dot1dStaticAddress.
dot1dTpPortTable {dot1dTp 4}
Not Accessible
A table that contains information about every port that is
associated with this transparent bridge.
A table that contains all Ethernet ports, not just those enabled for
bridging.
dot1dTpPortEntry {dot1dTpPortTable 1}
Not Accessible
A list of information for each port of a transparent bridge.
dot1dTpPort {dot1dTpPortEntry 1}
Integer Read-Only
The port number of the port for which this entry contains
Transparent bridging management information.
4-11
Page 98

Bridge MIB
dot1dTpPortMaxInfo {dot1dTpPortEntry 2}
Integer Read-Only
The maximum size of the INFO (non-MAC) field that this port will
receive or transmit.
The type/length field (2 octets) in Ethernet/802.3 packets are
considered to be part of the MAC header.
dot1dTpPortInFrames {dot1dTpPortEntry 3}
Counter Read-Only
The number of frames that have been received by this port from its
segment. Note that a frame received on the interface
corresponding to this port is only counted by this object if and only
if it is for a protocol being processed by the local bridging function.
dot1dTpPortOutFrames {dot1dTpPortEntry 4}
Counter Read-Only
The number of frames that have been transmitted by this port to its
segment. Note that a frame transmitted on the interface
corresponding to this port is only counted by this object if and only
if it is for a protocol being processed by the local bridging function.
dot1dTpPortInDiscards {dot1dTpPortEntry 5}
Counter Read-Only
Count of valid frames received which were discarded (i.e., filtered)
by the Forwarding Process.
Count of valid frames which were discarded, including local traffic
that was discarded.
4-12
Page 99

CHAPTER 5
PPP MIB
The ELS10-26 supports RFC 1471 for PPP link control and RFC
1473 for PPP IP support.
The MIB tree for reaching the PPP group is:
1.3.6.1.2.1.10
ppp {transmission 23}
5.1 PPP LINK CONTROL TABLE
pppLCP {ppp 1}
pppLinkStatusTable {pppLink1}
Not-Accessible
A table containing PPP-Link specific variables for this PPP
implementation.
pppLinkStatusEntry {pppLinkStatusTable 1}
Not-Accessible
Management information about a particular PPP Link.
pppLinkStatusPhysicalIndex {pppLinkStatusEntry 1}
Integer Read-only
The value of ifIndex that identifies the lower-level interface over
which this PPP Link is operating. This interface would usually be
an HDLC or RS-232 type of interface. If there is no lower layer
interface element, or there is no ifEntry for the element, or the
element can not be identified, then the value of this object is 0. For
example, suppose that PPP is operating over a serial port. This
would use two entries in the ifTable. The PPP could be running
over ‘interface’ number 123 and the serial port could be running
over ‘interface’ number 987. Therefore, ifSpecific.123 would
contain the OBJECT IDENTIFIER ppp
pppLinkStatusPhysicalIndex.123 would contain 987, and
5-1
Page 100

PPP MIB
ifSpecific.987 would contain the OBJECT IDENTIFIER for the
serial-port’s media-specific MIB.
pppLinkStatusBadAddresses {pppLinkStatusEntry 2}
Counter Read-only
The number of packets received with an incorrect address field.
This counter is a component of the ifInErrors variable that is
associated with the interface that represents this PPP Link.
pppLinkStatusBadControls {pppLinkStatusEntry 3}
Counter Read-only
The number of packets received on this link with an incorrect
control field. This counter is a component of the ifInErrors variable
that is associated with the interface that represents this PPP Link.
pppLinkStatusPacketTooLongs {pppLinkStatusEntry 4}
Counter Read-only
The number of received packets that have been discarded because
their length exceeded the MRU. This counter is a component of the
ifInErrors variable that is associated with the interface that
represents this PPP Link.
Note: Packets which are longer than the MRU but which are successfully
received and processed are NOT included in this count.
pppLinkStatusBadFCSs {pppLinkStatusEntry 5}
Counter Read-only
The number of received packets that have been discarded due to
having an incorrect FCS. This counter is a component of the
ifInErrors variable that is associated with the interface that
represents this PPP Link.
pppLinkStatusLocalMRU {pppLinkStatusEntry 6}
Integer Read-only
The current value of the MRU for the local PPP Entity. This value is
the MRU that the remote entity is using when sending packets to
5-2
 Loading...
Loading...