Cabletron Systems CyberSWITCH CSX150, CyberSWITCH CSX154, CyberSWITCH CSX155, CyberSWITCH 150 User Manual

SMALL OFFICE
REMOTE ACCESS SWITCH
USER’S GUIDE
Release 7.2
Cabletron Systems
(603) 332-9400 phone
(603) 337-3075 fax
support@ctron.com

USER’S GUIDE
2 CyberSWITCH
NOTICE
You may post this document on a network server for public use as long as no
modificati ons are ma de to th e docume n t .
Cabletron Systems reserves the right to make changes in specifications and other
information contained in this document without prior notice. The reader should in
all cases consult Cabletron Systems to determine whether any such changes have
been made.
The hardware, firmware, or software described in this manual is subject to change
without notice.
IN NO EVENT SHALL CABLETRON SYSTEMS BE LIABLE FOR ANY
INCIDENTAL, INDIRECT, SPECIAL, OR CONSEQUENTIAL DAMAGES
WHATSOEVER (INCLUDING BUT NOT LIMITED TO LOST PROFITS) ARISING
OUT OF OR RELATED TO THIS MANUAL OR THE INFORMATION
CONTAINED IN IT, EVEN IF CABLETRON SYSTEMS HAS BEEN ADVISED OF,
KNOWN, OR SHOULD HAVE KNOWN, THE POSSIBILITY OF SUCH
DAMAGES.
©Copyrigh t 1998 by Cabletron Sy stems, Inc. All rights reserved.
Cabletron Systems, Inc.
P.O. Box 5005
Rochester, NH 03866-500 5
Order Number: 9032450
VIRU S D ISCLAIMER
Cabletron Systems has tested its software with current virus checking
technologies. H owev er, because no anti-vir us sy stem is 100% reliable, we strongly
cauti on you to wr ite pro tect and th en verif y that th e Licen sed Sof tware, pr ior to
installing it, is virus-free with an anti-viru s system in which yo u have confi denc e.
Cabletron Systems makes no representations or warranties to the effect that the
Licensed Software is virus-free.
Copyright © July 1997, by Cabletron Systems, Inc. All rights reserved.
Only qualified personnel should perform installation
procedures.
!
CAUTION

Small Office Remote Access Switch 3
TRADEMARKS
Cabletron Systems, CyberSWITCH, MMAC-Plus, SmartSWITCH, SPECTRUM,
and SecureFast Virtual Remote Access Manager are trademarks of Cabletron
Systems, Inc.
All other product names m entioned in this manual are tradema rks or registered
trademarks of their re sp e ctive companies.
COPYRIGHTS
All of the code for this product is copyright ed by Cable tron System s , Inc.
© Copyright 1991-1997 Cabletron Systems, Inc. All rights reserved. Printed in the
United States of America .
Portio ns of the code for this p roduct are co pyrighted by the follow ing corpor ations:
Epilogue Technolo gy Co rporat io n
Copyright 1991-1993 by Epilogue Technology Corporation. All rights reserved .
Livingston Enterprises, Inc.
Copyright 1992 Livingston Enterprises, Inc.
Security Dynamics Technologies Inc.
Copyright 1995 by Security Dynamics Technologies Inc. All rights reserved.
Stac El e c troni cs
Stac Electronics 1993, including one or more U.S. Patents No. 4701745, 5016009,
5126739 and 5146221 and other pending patents.
Telenetw orks
Copyright 1991, 92, 93 by Telene tworks. All rights reser ved .
FCC NOTICE
This device complies with Part 15 of th e FC C rules. Operation is subject to the
following two conditions: (1) this d e vice m ay no t cause har mful interference, and
(2) this device must accept any int erference received, includ ing interference that
may caus e undesire d o pe ra ti on.
NOTE: This equipment has been tested and found to comply with the limits for a
Class A digital device, pursuant to Part 15 of the FCC rules. These limits are
designed to provide reasonable protection against harmful interference when the
equipment is operated in a commercial environment. This equipment uses,
generates, and can radiate radio frequency energy and if not installed in
accordance with the operator’s manual, may cause harmful interference to radio
communications. Operation of this equipment in a residential area is likely to cause
interference in which case the user will be required to correct the interference at his
own expense.

USER’S GUIDE
4 CyberSWITCH
WARNING : Changes or modific ations made to this d evice wh ich ar e not expr essly
approved by the party responsible for compliance could void the user’s authority
to operate the equipment.
DOC NOTICE
This digital apparatus do es not exceed the Class A limits for radio noise emissions
from digital apparatus set out in the Radio Interference Regulations of the
Canadian Departme nt of Commun ications.
Le présent appareil numérique n’émet pas de bruits radioélectriques dépassant les
limites applicables aux appareils numériques de la class A prescrites dans le
Règlement sur le brouillage radioélectrique édicté par le ministère des
Communicatio ns du Cana d a.
VCCI NOTICE
This is a Class 1 product based on the standard of the Voluntary Control Council
for Interference by Information Technology Equipment (VCCI). If th is equipment
is used in a domestic environment, radio disturbance may arise. When such
trouble occurs, th e user may be requir e d to take correc tive actions.
CABLETRON SYSTEMS, INC. PROGRAM LICENSE AGREEMENT
IMPORTANT: Before utilizing this product, carefully read this License Agreement.
This document is an agreement between you, the end user, and Cabletron Systems,
Inc. ("Cabletron") that sets forth your rights and obligations with respect to the
Cabletron software program (the "Program") contained in this package. The
Progra m may be contai ned in fi rmware, ch ips or ot her media. BY UTILIZ ING THE
ENCLOSED PRODUCT, YOU ARE AGREEING TO BECOME BOUND BY THE
TERMS OF THIS AGREEMENT, WHICH INCLUDES THE LICENSE AND THE
LIMITATION OF WA RRANTY A ND DISCLAIMER O F LIABILITY. IF YOU DO
NOT AGREE TO THE TERMS OF THIS AGREEMENT, PROMPTLY RETURN
THE UNUSED PRODUCT TO THE PLACE OF PURCHASE FOR A FULL
REFUND.

Small Office Remote Access Switch 5
CONTENTS
Using this Guide 22
Documentation Set 23
Guide Conventions 24
SYSTEM OVERVIEW 25
The CyberSWITCH 26
The Cybe rS W I TC H Ne t w or k 26
Unique System Featur es 27
Interoperability Overv iew 29
Interoperability Protocols 29
Interoperability Devices 30
Security Overview 31
Network Interface Overview 31
System Compon e nts 32
Remote ISDN Devices 32
Switches Supported 33
Hardware Overvi ew 34
Safety Considerations 34
System Platforms 35
CyberSWIT CH Cha r acteristics 35
CyberS WITCH Series 36
CyberSWITCH Front Panel 36
CyberSWITCH Back Panel 37
Software Overview 39
Overview 39
System software 39
System Files 39
Configuration Files 39
Operational Files 40
User Level Security Files 41
SYSTEM INSTALLATION 42
Orderi n g IS DN Service (US Only ) 43
Overview 43
Orde ring NI-1 Lines Using EZ-ISDN Code s 43
Orde ring NI-1 Lines Using NI-1 ISDN Ordering Codes 43
For Non-POTS Devices 43
For Single POTS Devices 43
For Dual POTS Devices 44

USER’S GUIDE
6 CyberSWITCH
Ordering BRI ISDN Lines using Provisioning Settings 44
Provisioning Settings for AT&T 5ESS Switches 45
AT&T 5ESS NI-1 Service 45
AT&T 5ESS Custom Point-to-Poin t Service 46
Provision Sett ings for Northern Telecom DMS-100 Switches 46
Northern Telecom DMS100 NI-1 Service 47
Northern Telecom DMS100 Custom Service 48
Hardware Installat ion 49
Pre-Installation Requirements 49
Accessing the CyberSWITCH 50
Overview 50
Making Connections 50
Direct Co nne ction 50
Null-Modem Connection to a PC 50
Chan g i n g th e B a u d Rate 52
Remote Connec tion using Telne t 52
Establishing an Administration Session 53
Powering On 53
Accessing th e Re lease Notes 54
Upgrading System Software 56
Overview 56
Upgrading Software 56
Local Software Upgrade 57
Local Upgrade of the Second Stage Boot (SSB) 57
Local Upgrade of the Operational Software (OSW) 58
Remote Software Upgrade 58
Remote Upgrade of the Second Stage Boot (SSB) 59
Remote Upgrade of the Operational Software (OSW) 60
Chan g e De fault s to Se c u re Syste m 61
Return Conf iguration to Factory Defaults 62
Accessing th e Re lease Notes 62
BASIC CONFIGURATION 63
Configuration Tools 64
Overview 64
CFGEDI T 64
Executing CFG EDIT 64
Saving CFGEDIT Changes 65
Dynamic Management 65
Executing Dynamic Management 65
Utility Dynamic Management Commands 66
Saving Dynamic Managem e n t Changes 66
Default Configuration 67
Using the Network Worksheets 67
Using the Configuration Chap ters 68

Small Office Remote Access Switch 7
Configuring Resources and Lines 69
Overview 69
Resources 69
Configuring Resour ces 69
Resource Configuration Elements 71
Resource B ackground Information 71
Lines 72
Configuring Line s 72
Configuring Changes fo r a COM M P O RT Res ou rc e 73
Line Configuration Elements 74
Line Background Information 77
Subaddresses 78
Configuring a Subaddress 78
Subaddress Configuration Elements 78
Subaddresses Background Information 78
POTS Option 78
Configuring the POTS Option 78
POTS Configuration Ele m ent s 80
POTS Background Information 80
Configuring Basic Bridging 81
Overview 81
MAC Layer Bridging Option 81
Enabling/Disabling Bridging 81
MAC Layer Bridging Configuration Elements 81
MAC Layer Bridging Background Info rma tion 82
Configuring Basic IP Rou ting 83
Overview 83
Interne t P rotocol (IP) Option 83
Enabling IP 83
IP Option Configuration El e ments 84
IP Background Information 84
IP Operating Mode 84
Configuring the IP Operating Mode 84
IP Operating Mode Configuration Elements 85
IP Operating Mode Background Information 85
IP Network Interfaces 86
Configuring Interfaces 86
Network Interface Configuration Elements 88
IP Network Inte rface Background Inform ation 93
IP RIP and the IP Network Interf aces 97
IP RIP over Dedicated Connections 101
IP Host Operating Mode and the IP Network Interfaces 103
Using Multiple IP Addres ses 103
Static Routes 105
Configuring Static Routes 105
Static Route Configurati on Elements 107
Static Route Background Information 109
Default Routes 110
Configuring Default Routes 110
Default Route Configuration Elements 110

USER’S GUIDE
8 CyberSWITCH
Routing Information Protocol (RIP) Option 111
Enabling/Disabling IP RIP 111
IP RIP Configuration Elements 112
IP RIP Background Information 112
SECURITY 113
Security Overview 114
Overview 114
Security Level 114
Syste m Opti ons an d I n f or mation 115
Device Level Databases 115
User Level Databases 116
Off-node Server Information 116
Network Login Information 116
Configuring Security Level 117
Overview 117
No Security 119
Configuring No Secur ity 119
Device Level Security 120
Configuring Device Level Security 120
Device Level Security Backgr ound Info rma ti on 120
Overvie w of Device Auth e ntication Pr ocess 121
User Level Security 121
Configuring User Lev e l Securit y 121
User Level Security Backgr ou nd Info rma tion 121
Authentication Using a Security Token Card 122
System Requirements 123
Authenti cation Process with User Level Securi ty 124
Device and User Level Security 125
Configuring Device an d Us er Level S ecur ity 12 5
Device and User Level Backgroun d In formation 126
Configuring System Options and Information 127
Overview 127
System Options 127
Configuring System Options 127
Syste m Opti ons Conf i g u r a ti o n E le ment s 1 2 8
System Options Background Information 130
System Information 131
Configuring Syst em Information 131
System Information Configuration Elements 131
System Information Background Information 132
Administ rative Session 132
Configuring Administrative Sessions 132
Administrativ e Sessio n Conf igur ation Ele m ent s 133
Administrative Session Backgroun d In formation 134
Alterna tive Database Location Background Information 134
Session Inactiv i ty Background Information 134
Number of Administrat ive Telnet Sessions Background Information 134

Small Office Remote Access Switch 9
Telnet Server TCP Port Number Background Information 134
Emergency Telnet Server Port Number Background Information 135
Configuring Device Level Databas e s 13 6
Overview 136
On-node Devi ce Database 136
Configuring an On-node Device Database 136
On-node Device Entries 137
Configuring On-node Device Entries 137
On-node Dev ice Database Con f iguration Elements 14 4
General Configuration Ele m ent s 144
ISDN Configuration Elements 144
Frame Relay Access Configur ation Ele m ent s 146
X.25 Access Configur ation Elements 146
Authentication Configuration Elements 146
IP Information Configuration Elements 148
IPX Information Configur ation Elements 148
AppleTalk Information Configuration Elements 149
Bridge Information Co nfiguration Element s 150
POTS Information 151
Compression Configuration Elements 151
On-node Device Database Background Information 151
On-node Dev ice Database Se cu rity Requirements 152
Off-node Device Database Location 156
Configuring Off-node Device Database Location 156
Off-node Device Database Location Configuration Elements 156
Off-node Device Database Location Background Information 156
Configuring User Level Databases 157
Overview 157
User Le vel Au th e ntica ti o n D a ta b a se Loc at i o n 15 7
Configuring Authentication Database Location 157
User Level Authen tica tion Datab as e Loc ation Co nfigur a tion Ele me nt s 158
User Level Authentication Database Location Background Information 158
Configuring Off-node Server Information 159
Overview 159
Multiple Administration Login Names 159
VRA Manager Authentication Serv e r 160
Configuring VRA Manager Authentication Server 160
VRA Manager Authentication Serv e r Configuration Elements 161
VRA Manager Authentication Se rver Background Informati on 161
RADIUS Authe ntication Server 161
Configuring a RADIUS Authentication Server 161
RADIUS Authentication S e rver Configuration Elements 163
RADIUS Authentication Server Background Information 163
TACACS Authenti cation Server 164
Configuring a TACACS Authenti cation Server 164
TACACS Authentication Server Configuration Elements 165
TACACS Authentication Server Background Information 165

USER’S GUIDE
10 CyberSWITCH
ACE Authentication Server 166
Configuring an ACE Authenti cation Server 166
ACE Authentication Server Configuration Elements 167
ACE Authentication Server Background Information 168
Configuring Network Login Infor mation 169
Overview 169
Network Login General Configuration 169
Configuring General Network Login Information 169
Network Login General Configuration Background Information 170
Network Login Banners 171
Configuring Netw ork Lo gin Banner s 171
Network Login Banners Background Information 171
Login Configuration Specific to RADIUS Server 172
Configuring RADIU S Serve r Login Info rma tion 172
Login Configuration Specific to RADIUS Server Background Information 173
Login Configuration Specif i c to TACAC S Serv er 173
Configuring TACACS Server Login Information 173
Login Configuration Specif i c to TACAC S Serve r Backg round Information 175
ADVANCED CONFIGURATION 176
Configuring Alternate Accesses 177
Dedi ca te d Acce ss e s 1 7 7
Configuring a Dedicat ed Acc es s 177
Dedicated Access Configurat ion Element s 177
Dedicated Access Background Information 178
X.25 Accesses 179
Configuring an X.25 Ac cess 179
Basic Configuration Inf orm a tion 179
LAPB Configura tion Info rma tion 1 80
X.25 Configuration Information 180
Permanent Virtual Circuit Information 182
X.25 Configuratio n Elements 182
X.25 Line Configuration Elements 182
LAPB Configuration Elements 183
X.25 Access Configur ation Elements 184
PVC Configuration Elements 187
X.25 Access Background Inf orm ation 188
Current X.25 Restrictions 190
Frame Relay Accesses 190
Configurin g a Frame Relay Access 190
Configuring General Ac ces s Informa tion 190
Configuring a PVC 191
Frame Relay General Configuration Elements 192
Frame Relay PVC Configuration Elements 193
Frame Relay Access Background Information 195
The Local Management Interface Overview 196
Data Rate Control Overview 196
Congestion Control Overview 197
Curren t Re strictions 197

Small Office Remote Access Switch 11
Configuring Advanced Bridgin g 19 9
Overview 199
Bridge Dial Out 199
Configuring the Device List for Bridge Dial Out 200
MAC Hardware Filtering 201
Enabling/Disab lin g MAC Ha r dwa re Filt ering 201
MAC Hardware Filtering Background Information 201
Spanning Tr ee Protocol 202
Configuring Spanning Tree Protocol 202
Spanning Tree Protocol Co nfigura tion Elem e nts 202
Bridge Mode of Operation 202
Configuring the Bridge Mode of Operation 202
Bridge Mode of Opera tion Co nfigu ra tion Elem ent s 202
Bridge Mode of Operation Background Infor matio n 202
Unrestricted Bridge Mode 202
Restricted Bridge Mode 203
Mode of Hardwa re Filtering 2 03
Configuring Mode of Har dwa re Filte ring 203
Hardware Filtering Mode Backgrou nd Informatio n 203
Manual Mode Hardware Filtering 204
Auto Mode Hardware Filtering 204
Bridge Filters 204
Configuring Bridge Filters 204
Bridge Filter Configur atio n Elem ent s 207
Protocol Definition Configuration Elements 207
Bridge Filter Configur atio n Elem ent s 207
Hardware Filter Conf iguratio n Elem ents 208
Bridge Filters Backgrou nd Info rma tion 209
Protocol Definitions 209
Bridge Filter Definitions 210
Dial Out Using Bridge Filters 216
Example: Bridge Dial Out Using a Destina tion MAC Add ress Filter 216
Known Connect List 218
Configuring the Known Co nnec t List 218
Known Connect List Configur ation Ele m ent s 219
Known Connect List Back ground Infor matio n 219
Configur in g A dva n c ed IP Ro uting 220
Overview 220
Static ARP Table Entries 220
The Isolate d M ode 220
Configuring the Isolate d Mode 220
Isolated Mode Configuration Elements 221
Isolated Mode Backgroun d In formation 221
Static Route Lookup via RADIUS 221
Configuring Stati c Route Lookup via RADIUS 221
Static Route via RADIUS Configuration Elements 221
Static Route Lookup via RADIUS Background Information 221
IP Address Pool 222
Configuring an IP Address Pool 222
IP Address Pool Configuration Elements 222
IP Address Pool Background Information 222

USER’S GUIDE
12 CyberSWITCH
IP Filters 223
Initiating the IP Filter Configuration 223
Configuring Packet Types 224
Configuring the Comm on IP Portio n 225
Configuring TCP 226
Configuring UDP 226
Configuring ICMP 227
Configuring Forward ing Filt ers 228
Configuring Connection Filters 229
Using CFGEDIT 22 9
Configuring Exception Filter 230
Modifying the Final Condition for a Filter 231
Applying Filters 231
Applying Filters to Network Interfaces 231
Applying the Global Forwarding Filter 231
Applying per-device Forwarding Filters 231
IP Filters Configuration Elements 232
IP Filters Background Information 233
Filter Compositio n 234
Types of Filters 234
Role of Filters in the IP Processing Flow 235
Packet Types 236
Limitations 237
Example of an IP Filter Configuration 238
DHCP Relay Agent 240
Configuring a DHCP Relay Agent 240
DHCP Configuration Elements 241
DHCP Background Information 241
DHCP/BOOTP Relay Agen t Env ironm ent s 241
Example DHCP Configurations 243
DHCP Proxy Client 247
Configuring the DHCP Proxy Client 247
DHCP Configuration Elements 248
DHCP Background Information 248
Sample Configuration: IP Router with DHCP Proxy Client 249
Configuring IPX 251
Overview 251
Configuring IPX Information 252
IPX Routing Op tion 253
Enabling/Disabling IPX 253
IPX Option Configuration Element 253
IPX Option Background Information 254
IPX Internal Network Number 254
Configuring the IPX Internal Network Number 254
IPX Internal Network Number Configuration Element 254
IPX Network Number Background Information 255

Small Office Remote Access Switch 13
IPX Network Interf aces 255
Configurin g IPX Net work Interfaces 255
IPX Network Interface Configuration Elements 257
General IPX Network Interface Configuration Elements 257
RIP IPX Network Interface Configuration Elements 257
SAP IPX Network Interface Configuration Elements 258
IPX Network Interface Background Informatio n 259
IPX Routing P rotocols 260
Configuring IPX Routing Pr otocols 260
IPX Routing P rotocol Configuration Ele ments 260
IPX Routing P rotocol Background Information 261
Routing/Service Tables 261
Special Conside r ations - Remo te LA N Inter f ace 262
IPX Static Routes 263
Configurin g IPX Static Routes 263
IPX Static Routes Confi g uration Elements 264
IPX Static Routes Background Information 264
IPX NetWare Static Servi ces 265
Configuring IPX NetWare Static Services 265
IPX NetWare Static Servi ces Configuration Elements 266
IPX NetWare Static Servi ces Background Information 267
IPX Spoofing 267
Configuring IPX Spoofing 267
IPX Spoofing Configuration Elements 268
IPX Spoofing Background Information 268
Watchdog Protocol 269
SPX Protocol 269
IPX Type 20 Packet Handling 270
Configuring IPX Type 20 Packet Handling 270
IPX Type 20 Packet Handling Configuration Elements 271
IPX Type 20 Packet Handling Device Configuration Elements 271
IPX Type 20 Packet Handling Background Informati on 271
IPX Isolated Mode 271
Configurin g IPX Isolated Mode 271
IPX Isolated Mode Configuration Elements 271
IPX Isolated Mode Background Information 272
IPX Triggered RIP/SAP 272
Displaying WAN Peer List 272
Configuring Triggered RIP/SAP Global Timers 273
Configuration Elements 273
Triggered RIP/SAP Back groun d In formation 274
IPX-Specific Infor mation for Devices 274
Configuring IPX Device s 274
WAN Devices 274
Remote LAN Devices 277
IPX Configuration Elements for Devices 278
IPX Background Information for Devices 279
IPX Triggered RIP/SAP Device Background 279

USER’S GUIDE
14 CyberSWITCH
Configuring SNMP 280
Configuring SNMP 280
SNMP Configuration Elements 282
SNMP Background Information 283
Configuring AppleTalk Routing 2 8 7
AppleTalk Rou ting Option 287
Enabling AppleTalk Routing 287
AppleTalk Rou ting Option Configuration El e ment 288
AppleTalk Routi ng Background Inf ormation 288
AppleTalk Ports 288
Configuring AppleTalk Ports 288
AppleTalk Ports Configuration Elements 289
AppleTalk Ports B ackground Information 290
The AppleTalk Network Type 290
Dynami c Node Address Assignment 290
The Zone Concept 291
AppleTalk Remote LAN 291
AppleTalk Static Rout e s 292
Configuring AppleTalk Static Routes 292
AppleTalk Routi ng Static Routes Configurati on El e men ts 293
AppleTalk Routi ng Static Routes Background Information 293
AppleTalk Capacities 293
Configuring AppleTalk Capacities 293
AppleTalk Capacities Configuration Elements 293
AppleTalk Capacities Background Information 294
AppleTalk Isolated Mode 294
Configuring the AppleTalk Isolated Mode 294
AppleTalk Isolated Mode Configuration Elements 294
Configuring Call Control 29 5
Overview 295
Throughput Monitor 295
Configuring the Throughp ut Monitor 295
Throughput Monitor Configuration Elements 296
Throughput Monitor Background Information 297
Overload Condition Monitori ng 298
Underload Condition Monitoring 298
Idle Condition Monit oring 299
Throughput Monitor Configuration Example 299
Call Int erval Parameter s 30 0
Configuring the Call Inter val P arameters 300
Call Interval Config urat ion Element s 300
Call Interval Background Information 300
Monthly Call Charge 301
Configuring Monthly Call Charge 301
Monthly Call Charge Configuration Elements 301
Monthly Call Charge Background Info rmation 301
Call Restrictions 302
Configuring Call Re strict ion s 302
Call Restriction Configuration Element s 302
Call Rest ri c tions Back ground Inf o rm a t i on 30 4

Small Office Remote Access Switch 15
Bandwidth Reservation 305
Configuring Bandw idt h Res erv ation 305
Bandwidth Rese rvatio n Configur a tion Elem ent s 307
Bandwidth Reservation Background Information 308
Semipermanent Connections 308
Configuring Semipermanent Connections 308
Semipermanent Connections Configuration Elements 310
Semipermanent Connection s Background Information 310
Interactions with Other Features 310
VRA Manager as a Call Contro l Mana ger 31 2
Configuring VRA Mana ger for Ca ll Contro l 312
Configuration Elements 312
Background Informati on 313
Call Control Manage m ent 313
Limitations/Considerations 314
Configu ring Other Advance d O p tions 315
Overview 315
PPP Configuration 315
Configuring PPP 315
PPP Configuration Elements 316
PPP Background Information 317
PPP Link Failure Detection 317
PPP Reference Documents 318
Default Line Protocol 319
Configuring Default Line P rotocol 319
Default Li ne Protocol Configuration Ele ments 319
Default Line Protocol Background Informatio n 319
Log Options 320
Configuring Log Options 320
Log Options Configuration Elements 320
Log Options B ackground Info rmation 321
Local Log File Overvie w 321
Syslog Server Overview 321
CDR Log Report Overview 322
Compression Options 327
Configur ing Compressi on Options 32 7
Compression Options Configuration Elements 327
Compression Options Background Infor mati on 328
Compr essio n and CCP 329
TFTP 330
Configuring TF TP 330
TFTP Configura tion Elem en ts 331
TFTP Background Information 331
File Attributes 332
Configuring File Attributes 332
File Attributes Configuration Elem ent s 332
File Attributes Background Inf orm ation 3 32

USER’S GUIDE
16 CyberSWITCH
TROUBLESHOOTING 334
System Verification 335
Verifying Hardware Resources are Operational 335
Verifying WAN Lines are Available for Use 336
Verifying LAN Connection is Operational 336
Verifying Bridge is Initialized 337
Verifying IP Router is Initialized 337
Verifying a Dedicated Con nection 338
Verifying a Frame Relay Connection 338
Verifying an X.25 Connecti on 339
Verifying Remote Device Connectivity 339
Verifying Multi-Level Security 339
Verifying IP Host Mode is Operational 341
Verifying IP Host is Initialized 341
Verifying IP Host Mode is Operational 341
Verifying I P Host Mode Operation over a LAN connection 341
Verifyi ng I P Host Mode Operatio n ov e r a WAN con nection 342
Verifying IP Routing Over Interfaces 342
Verifying IP Routing Over a LAN Interface 342
Verifying IP Routing Over a WAN Interface 343
Verifying IP Routing Over a WAN (Direct Host) Interface 345
Verifying IP Routing Over a WAN Remote LAN Interface 346
Verifying IP Routing Over a WAN UnNumbered Interface 347
Verifying IP Filters 348
Verifying IP RIP 348
Verifying IP RIP is Initialized 348
Verifying IP RIP Output Processing on a LAN Interface 349
Verifying I P RIP I nput Processing on a LAN Inte rface 350
Verifying IP RIP Output Processing on a WAN Interface 350
Verify IP RIP Inpu t Processing Operational on a WAN Interf ace 351
Verifying IPX Router is Initialized 352
Verifying IPX Routing is Operational 352
Verifying IPX Ro uting over a LA N Connection 353
Verifying an IPX Remote LAN Connection 353
Verifying IPX Rou ti ng over a WAN Connection 354
Verifying Triggered RIP/SA P 354
Verifying the AppleTalk Routing Feature 354
Verifying AppleTalk Routing is Initialized 354
Verifying AppleTalk Routing is Operational 355
Verifying AppleTalk Routing Operational over the LAN connection 356
Verifying AppleTalk Routing Operation over a WAN connection 356
Verifying SNMP is Operational 357
Verifying the Dial Out Feature 358
Verifying Call Detail Recording 358
Verifying Compressio n is Op erational 3 59
Verifying Reserved Bandwidth is Operational 359
Verifying PPP Link Failure Detection is Operational 359
Verifying DHCP Relay Agent 360
Verifying DHCP Relay Agent Initialization 360
Verifying the Relay Agent is Enabled 361
Verifying the Relay Agent is Operational 361

Small Office Remote Access Switch 17
Verifying DHCP: Proxy Client 362
Verifying DHCP Proxy Client Initialization 362
Verifying the Proxy Client is Enabled 363
Verifying the Proxy Client is Operational 363
UDP Ports 363
IP Address Pool 364
Verifying a Semipermanen t Conne cti on 364
Verifying Proxy ARP is Operational 364
Problem Diagnosis 366
Overview 366
LAN Adapter 366
Bridge Initializa tion 367
IP Routing Initialization 367
WAN Line Availability 367
Dedicated Co nnections 369
Frame Relay Connections 369
X.25 Connections 370
Remote Device Connect iv ity 371
Multi-Level Security 372
LAN Attach ment 372
IP Host Mode 373
IP Host Initialization 373
IP Host Mode Operation over the LAN connection 373
IP Host Mode Operation over the WAN connection 374
IP Routing Over Interface Connections 374
IP Routing Over the LAN Interf ace Co nnec tion 3 74
IP Routing Over a WAN Interface Connection 375
IP Routing Over a WAN (Direct Host) Interface Connecti on 376
IP Routing Over a WAN RLAN Interface Connection 377
IP Routing Over a WAN UnNumbered Interface Connection 378
IP Filters 378
IP RIP 379
IP RIP Initialization 379
IP RIP Output P rocessing on a LAN Interface 380
IP RIP Input Processing on a LAN Interface 380
IP RIP Output P rocessing on a WAN Interface 381
IP RIP Input Processing on a WAN Interface 381
IPX Routing 382
IPX Routing Initialization 382
IPX Routing ove r the LAN Connection 382
IPX Routing ove r the Remote LAN Connection 383
IPX Routing ove r the WAN Connection 384
IPX Routing and Service Tables 385
Triggered RIP/SAP Start Up 386
Triggered RIP/SAP Operation 386
AppleTalk Routing 386
AppleTalk Routi ng Initialization 387
AppleTalk Routing Operational ov er the LAN connection 387
AppleTalk Routing Operational ov er the WAN connection 389
SNMP 390
Dial Out 392

USER’S GUIDE
18 CyberSWITCH
Call Detail Recording 393
Compression 393
DHCP: Relay Agent 395
Relay Agent Initializa tion 395
Enabling the Relay Agent 395
Relay Agent Operatio n 396
DHCP: Proxy Client 396
Proxy Client Initialization 396
Enabling the Proxy Client 396
Proxy Client Operation 397
Proxy ARP Operation 398
LED Indicators 399
Overview 399
Local Area Network LED Indicators 399
WAN LED Indicators 399
Service I ndicator 4 00
Service I ndicator R e ma ins Lit 401
Service Indicator Blinks 401
System Messages 403
Overview 403
Informational Messages 403
Boot Messages 404
Initialization Messages 404
Normal Operation Messages 404
Status Messages 404
Spanning Tree Messages 405
Warning Messages 405
Error Messages 405
System Message Summary 405
Trace Messages 464
Overview 464
Call Trace Messages 465
Call Trace Message Summary 466
IP Filters Trace Messages 471
PPP Packet Trace Messages 472
WAN FR_IETF Trace Messages 474
X.25 Trace Messages 474
X.25 Trace Message Summary 474
X.25 (LAPB) Trace Messages 477
X.25 (LAPB) Trace Message Summary 477
SYSTEM MAINTENANCE 479
Remote Management 480
Overview 480
AMP Ou t-of-Band Management 480
Installation and Configuration 480
Usage Instru ctions 481

Small Office Remote Access Switch 19
SNMP 482
Installation and Configuration 483
Usage Instru ctions 483
Telnet 484
Installation and Configuration 485
Usage Instru ctions 485
TFTP 487
Installation and Configuration 487
Usage Instru ctions 488
Remote Installation wi th USER2 489
System Commands 491
Overview 491
Accessing Admin istration Services 491
Setti n g th e I P Ad d r e s s 4 92
Boot Device Comm a nds 492
Accessing Dynamic Managem ent 493
Viewing Operational Inf orm ation 493
Viewing Throughput Information 497
Throughput Monitor Contents 498
Saving Operational Information 499
Clearing Opera tional Inf orm atio n 499
Configuration-R ela te d Comm an d s 500
Restarting the CyberSWITCH 500
Setti n g the D ate an d T ime 501
File Utility Commands 501
Terminating Admin istration Sessions 502
AppleTalk Routing Commands 503
Bridge Commands 507
Call Control Co m ma nd s 508
Call Detail Recording Commands 511
Call Restriction Commands 512
Compression Information Commands 512
DHCP Com m an ds 51 2
Frame Relay Commands 513
IP Routing Commands 515
IPX Rou ting Commands 519
ISDN Usage Commands 521
LAN Commands 522
Log Commands 522
Packet Capture Commands 522
RADIUS Command s 526
SNMP Co mma nds 528
TCP Commands 528
Telnet Commands 528
Termina l Commands 531
TFTP Commands 532
Trace Commands 533
UDP Command s 5 3 4
User Level Security Commands 534
WAN Comm an ds 535
X.25 Commands 535

USER’S GUIDE
20 CyberSWITCH
System Statistics 537
Overview 537
Connectivity Statistics 537
Call Restriction Statistics 538
Call Statistics 538
Throughput Monitoring Statistics 538
AppleTalk Statisti cs 539
AppleTalk Protocol Statistics 539
AppleTalk Data Delivery Protocol (DDP) Statistics 539
AppleTalk Echo Protocol (AEP) Sta ti stics 540
AppleTalk Rou ting Table Maintenance Proto col (RTMP) Statistics 541
AppleTalk Zone Informati on Protocol (ZIP) Statistics 541
AppleTalk Name Binding Protocol (NBP) Statistics 542
AppleTalk Transaction Protocol (ATP) Statistics 542
AppleTalk Port Statistics 543
Bridge Statistics 544
Call Detail Recording Stat istic s 544
Compression St atistics 545
Compression Related Statistics 545
Decompressi on Related Statistics 545
DHCP Statistics 546
Common DHCP Statisti cs 546
DHCP Relay Agent Statistic s 547
DHCP Proxy Client Statistics 548
Frame Relay Statisti cs 549
Access Related Statis tics 549
PVC Related Statist i cs 551
LAN Stati st ics 552
IP Statistics 553
IP Group Statistics 553
ICMP Group Statistics 554
IPX Statistics 556
IPX General Statistics 556
IPX Basic System Table Statistics 556
IPX Advanced System Table Stati stics 557
IPX RIP Statis tics 558
IPX Triggered RIP Statisti cs 559
IPX Route Statistics 559
IPX SAP Statistics 560
IPX Triggered SAP Statistics 560
IPX Service Statistics 560
RIP Statist ics 561
RIP Global Stati stics 561
RIP Interface Statistics 561
SNMP Statistics 562
TCP Statistics 564
TFTP Statistics 565
Statistics for Serve r or Rem o te initia ted TF TP Ac tiv ity 565
Statistics for Loca l or Clien t Initia ted TFTP Ac tiv ity 566
Statistics for all TFTP Activity 566
UDP Statistics 567
WAN FR_IETF Statistics 568

Small Office Remote Access Switch 21
WAN Statistics 568
X.25 Statistics 569
X.25 Access Related Statistics 569
X.25 Virtual Circuit (VC) Rel ated Statistics 571
Routine Maintena nce 57 2
Overview 572
Installing/Upgrading System Software 572
Executing Configu ration Changes 572
Configuration Files 572
Making Changes Using CFGEDIT 572
Making Changes Using Manage Mode 573
Configuration Backup and Rest ore 573
Obtaining System Custom Information 573
APPENDICES 574
System Worksheets 575
Network Topology 576
System Details 577
Resources 577
Lines 577
Accesses 578
Device Information 579
Bridging and Routing Info rm ation 580
Bridging 580
IP Routing 58 0
IPX Routing 581
AppleTalk Routing 582
CFGEDIT Map 583
Overview 583
Main Menu 583
Physical Resources Menu 584
Options Menu 585
Security Menu 588
Getting Assistance 591
Reporting Problems 591
Contacting Cablet ron Sy stems 591
Administrative Console Commands Table 593
Manage Mode Commands Table 601
Cause Code s Ta ble 605
INDEX 612

U
SING THIS GUIDE
The User’s Guide is divided into the following parts:
S
YSTEM OVERVIEW
We begin with an overview of bridging, routing, and specific CyberSWITCH features. Next, we
provide an overview for both the system software and hardware.
S
YSTEM INSTALLATION
In this sec tio n of the User’s Guide we provide guidelines for ordering ISDN service in the US, and a
step-by-step descr iption of installi ng hardw a re and upgrading software.
B
ASIC CONFIGURATION
We define basic configuration as the configura tion n eeded by most devices . These are the areas of
configuration that will get your system up and running. Note that not all configuration steps in this
part are required. For example, if you are only using bridging, you will have no need to complete
the configuration steps included in the chapter titled Configuring Basic IP Routing.
S
ECURITY CONFIGURATION
The CyberSWITCH provides a great variety of security options. For example, you may use device
level se cu rity, use r l eve l secur ity , or i f pr efe rred , no secu ri ty. You m ay al so perfo rm auth enti ca tion
of a device/ user in different ways. The security information may be stored on several differ e nt
types of databases, either local ly or on a variety of remote databases.
System secu rity also allow s the configuration of administrative session (Teln e t se ssion)
enhancements. This provides secure access to the system along with flexible control.
A
DVANCED CONFIGURATION
We defi n e advan c e d co n f igura ti on as a wa y to fine tun e y o u r system, or to co nf i gu re options that
are not necessarily needed by the majority of devices. For example, use this sectio n to configure an
alternate access, or to set up SNMP to manage your syste m.
T
ROUBLESHOOTING
Troubleshooting begins with information for verifying your system installation, and continues
with steps to take if there are problems with the installation. Next, it includes a description of
system LED indicato rs, followed by system messages and trace messag e s. Each message listing in
these chapters provides the message itself, a message definition, and where appropriate, possible
corrective actions.
S
YSTEM MAINTENANCE
In this section, we provide information to help you maintain your CyberSWITCH once it is
operating. System maintenance information includes information regarding remote management,
a chapter on both the system comm ands and the system statistics, and routine maintenance
procedures.

Small Office Remote Access Switch 23
U
SING THIS GUIDE
Documentation Set
APPENDICES
The User’s Guide provides the following appendices:
N
ETWORK WORKSHEETS
These worksheets are provided to help you gather pertinent infor mat i on for co n fi guring your
system. We recommend that you print copies of these blank forms and fill in the appropriate
information before you begin configuring your system.
CFGEDI T M
AP
This map provides a guide thro ugh the Conf igur ation Ed itor str ucture, and may be a helpful
reference when configuring the CyberSWITCH using the CFGEDIT utility.
G
ETTING ASSISTANCE
This appendix provides information for getting assistance if you run into problems when
installing your system. A FAX form is included. You can print this form, fill out the information
requested, and FAX it to Cabletron Systems, using the provided FAX number.
A
DMINISTRATION CONSOLE COMMANDS
Provide s a tab ular list ing of the system administration console commands and th e ir uses.
M
ANAGE MODE COMMANDS
Provide s a tab ular list ing of the Manage Mode commands and their uses.
C
AUSE CODES
Provides a tabular listing of Q.931 Cause Codes and their meanings. These cause codes may
appear in call trace messages.
DOCUMENTATION SET
This guide, the User’ s Gu ide, provides information to install and configure your system. It also
provides information you may need to refer to keep your system running efficiently after it is up
and running. For example, it provides a listi ng of system messages. Each message listing provides
a definition of w hat the message means, and where appropriate, corrective action you can take.
Many other subjects are covered, including routine maintenance, hardware information, system
verifi cation, and problem diagnosis.
This gu ide is one in te gral part of the e ntire do cument a tio n se t . P le a se re f e r to th e d o cument s
described below for additional information.
The Example Networks Guide includes several example networks, beginning with a simple network,
and progressing to m ore complex networks. These example network chapters provide
configuration instructions that you may find helpful in configuring your own similar network.
The Quick Star t p rov ides abbr eviat ed inst alla tion and co nfiguration instructio ns for exper ie nced
users. Specific instructions for setti ng u p various types of remote dev ices are also i nc luded.
The R ADIUS Authentication User’s Guide describ e s the setup of the RADIUS server software on a
UNIX-based system. RADIUS (Remote Authentication Dial In User Service) provides multiple

USER’S GUIDE
24 CyberSWITCH
systems c entr al databa se ac cess for sec urity authenti catio n purpos es. I nstru ctions for ob tainin g th is
electronic document ca n be found in Co nfiguring Off-node Server Informat ion.
If you have Internet access, you may obtain this guide by following the steps outlined below:
• Use your Web browser to get to the foll owing address:
http:// ser vice.nei.com
• From the re su lting screen, click on Public.
•Click on the Radius director y.
•Click on the Docs directory. The guide will be under this directory.
The Release Notes provide release highlights and important information related to this release. The
Release Notes may be displa yed during sof tware installation (o r upgrade). They may also be
displayed after the system is operatin g by issuing the
list rel_note.txt
console command.
GUIDE CONVENTIONS
The following conven tions are used throughout the documentation:
Syste m Commands
All system comma nds (A dm inist rati on and Mana ge Mo de com mand s) are italic iz ed, and in a
different font than the general text. For example, if you are instruct ed to enter the command to test
for proper LAN connections, the command would appear as follows:
lan stats
CFGEDI T S CREENS
Screens that appear on the monitor as you are configuring your system using the CFGEDIT utility
will be displayed using the style shown b elow:
M
ONITOR DISPLAYS
Any messages or text that is displayed on your monitor w ill be shown in the style be low:
LAN Port <port #> is now in the LISTENING state
WAN Port <port #> is now in the FORWARDING state
LAN Port <port #> is now in the LEARNING state
LAN Port <port #> is now in the FORWARDING state
D
OCUMENTATION TITLES
All references to CyberSWITCH documentation titles will use the same font as normal text, but will
be italicized. For example, all references to the User’s Guide will appear as:
User’s Guide
Main Menu:
1) Physical Resources
2) Options
3) Security
4) Save Changes
Select function from above or <RET> to exit:
S
YSTEM OVERVIEW
We inc l u de th e f ollowi ng cha p te r s i n th e Sy stem Ov ervi ew segment of the User’s Guide.
• The CyberSWITCH
Provides the “big picture” view of a CyberSWITCH network. We include an overview of
unique system features, interoperability, security, interfaces, system components, remote
devices, and switches supported.
• Hardware Overview
A description of system platforms.
• Software Overview
A description of the CyberSWITCH’s system and administrative sof t ware. We also include a
description of system files.

T
HE CYBER
SWITCH
Because of the strong personal computer presence in the business environment, a move to
graphical user interfaces, and the need to make the best use of available resources, there is a
growing demand for high speed LAN access for remote devices. PC users need to be part of a workgroup or ente rprise LAN, and remote access from home, field office s, and other remote locations
has become a necessity.
With the de mand for remote LAN access, the remote devi ce’s requirement for b a ndwidth has
exceeded the capabilities of traditional analog modems. High-speed digital dedicated lines can
certainly provide su fficie nt band wi dt h for LAN inter con n ect ion . How ever , beca use of the high
monthly charges associated with dedicated services, the costs are prohibitive for individual users.
New forms of networking are now possible and affordable using the Integrated Services Digital
Network (ISDN) . ISDN is being deploy ed by majo r teleco mmunications comp anie s world- w ide.
With ISDN ser vices, t he costs o f LAN inte rconnect ion are b ased on ac tual usa ge — the user gets the
bandwidth of dedicated digital service at dial-up prices.
Our products offer internetworking solutions for small businesses as well as large corporations.
THE CYBER SWI TCH NETWORK
System software has been developed specifically for an embedded communications platform. It
uses a flas h file system (i nstea d of a hard disk) an d a two-st age boot device t o ini tialize t he plat form
and download the system software. The system software is preconfi gured to allow immediate
connect ion to a local area netwo rk (LAN) or a wide area net work (WAN) with Teln et and/or TFTP
access.
This system is geared toward the small office, offering a variety of internetworking capabilities.
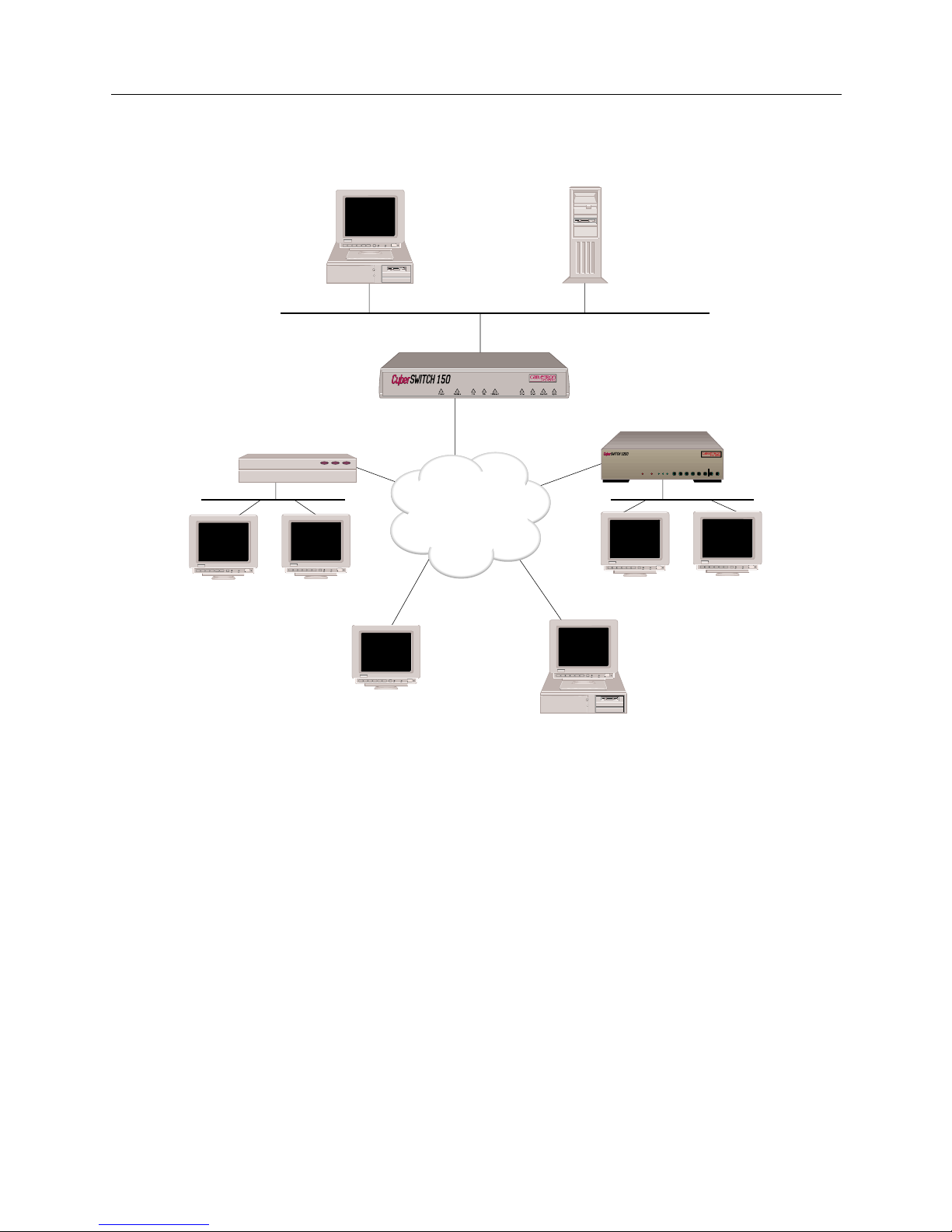
Small Office Remote Access Switch 27
THE C
YBER
SWITCH
Unique System Features
UNIQUE SYSTEM FEATURES
The CyberSWITCH combines unique features that improve cost-effectiveness, reliability, and
performance for wide area network connections to remote devices. These features include:
• Authentication Servers
Provide a central database for networks with more than one CyberSWITCH. The central
database consists of manageable, informatio nal data (refe rred to as the Device List or Device
Table). This data is acces sed and used for aut hentication when a n ew connection is esta blished
to the system.
• Bandwidth Agility
The system dynamically controls the bandwidth in use between itself and other PPP devices.
This is accomplished by estab lishing a nd dis c onn ecting calls . The num be r of calls is limited
only by the types and number of lines available. The system monitors the connections for
utilization and will add an d remove the connec tions based on use r- configurable throughput
parameters. As network ba ndw id th requirem ent s increa se or decrea se, the system will
ISDN
Host
File Server
Remote ISDN Bridge
Workstation
Workstation
PC
(with BRI ISDN TA)
BRI
BRI
Workstation
BRI
BRI
Workstation
Workstation
CSX150
B25B27
B26B28
WORKGROUP REMOTE ACCESS SWITCH
B29
E1 ONLYB-CHANNELS
LAN
10BASE-TRXTXSERVICE
B31
B30L1
B21B23
B22B24
B17B19
B18B20
B13B15
B14B16
E1DT1
D
B9B11
B10B12
B5 B7
B6 B8
B1 B3
B2 B4
POWER

USER’S GUIDE
28 CyberSWITCH
automati cally adju st th e nu mber of ne twork con nect ion s. Thus, your n et work costs w il l ref lec t
the actual bandwidth being used.
• Filtering
Allows you to control the flow of frames through the network. Filtering becom es nec essary if
you need to re strict remote access or con trol widespread transmission of sp oradic messages.
Customer-defined filters can forw ard messages based on addresses, protocol, or packet data.
• Data Compressi on
Allows the system to negotiate compression algorithms with another device on the network.
After successfully negotiating compression, data is compressed by the remote device and
transmi tte d to the system. The system deco mp resses the data, processes the information
contained in the user data, and forwards the data as required. The system can receive data
coming over a WAN or a LAN, and compress the data before transmitting it to another device
on the network. The net ef fect is to i ncrease int erconnect bandwidth by de creasing
transmi ssion time. If negotiati on for compre ssion fails, data is transmitted uncomp ressed.
• Dial Out Capability
The system will dial out to remo te dev ices . Th is featur e allows the sy st em to accep t user data
receiv e d on the Ethernet LA N or I S DN network and initiate a data connectio n to the remote
device specified in the user data. This allows devices on the local LAN to initiate connections
to networks connected to the system ove r the switched digital network. The system monitors
the connection for utilization and will rem ove the connection when it becomes idle.
• Dynamic Management
Provides a “real- time” manageme nt mechan ism that allows many system p arameters to be
changed with out interrupti ng the current execution state of the system software. Th is feature
consists of a series of console comman ds that enable a user to displa y current system
paramet ers , c ha ng e man y par ame ter s d yna mica lly , and wri t e cha ng es t o d isk f il es s o th at the y
remain permanent.
• High Speed Digital Connections
The system supp orts 56Kbps and 64Kbps co nnections to remote locatio ns. These dial- up digital
connections provide re liable high throughpu t connections for effici ent data tran sf e r for the
same cost as analog connections. If any r e mote devices conn e cted to the system support multi-
link PPP, up to 32 parallel connections can be made at either 56Kbps or 64Kbps.
• IP Filters
The IP filters allow you to control the transmission of individual IP packets based on the packet
type. You can specify packet type by IP address (source or destination) or by IP protocol (TCP,
UDP, ICMP).
Once you specify a packet type, two forms of IP filtering are available:
• Forwarding Filters, applied at discrete points of the IP processing path to determine if a
packet continues its normal processing, and a
• Connection Filter, which determines if an IP packet requiring a WAN connection may continue.
•Packet Capture
In order to monitor incoming LAN data, the CyberSWITCH packet capture feature will allow
you to capture, display, save, and load bridged or routed data packets.

Small Office Remote Access Switch 29
THE C
YBER
SWITCH
Interoperability Overview
• Protocol Discrimination
It is possible for multiple types of remote devices to use the same line. The system can
determine the device type and the protocol encapsulation used by remote devices.
• RS232 Port: Dual Usage
If your installation requires you to process PPP-Async data, this feature allows you to use the
RS232 port for either console acc ess or a serial data connection. This dual usage is possible
throu gh the Cyb erSWITCH’s s u pp ort of Aut o se nse mode and Te r m i n a l mo d e :
• Autosense mode determines whether you are trying to connect using a VT emulation or PPP-
Async, and connects you appropriately. (VT emulation requires you to perform four carriage returns to receive a login prompt.)
• Terminal mode assumes that you o nly wa nt to connec t usi ng VT emu latio n. A log in p rompt
is displayed as soon as the connec tion is made.
•Security
Security is a key issue for all central site network mana gers and is a priority with the
CyberSWITCHs. The modules provide high level features that help prevent unauthorized or
inadver tent acc ess to c riti cal data and reso urces. The mo dules su pport ex tensiv e secu rity lev els
including:
• PPP PAP and CHAP
• User n a me a n d pa ssword
• Calling Line ID (CLID)
• Ethernet Address
• User Authentication
• Device Authentication
• SecureFas t Virtual Remote Ac cess (SFVRA)
• TACACS Client with Radius Server
•RADIUS
• Security Dynamic’s A CE/SecurID
• Simultaneous Connections
The system su p ports si mu l ta n e o u s con nections to multiple l o ca t i on s. Thes e lo ca t i ons can
connect by using different channels on the same line, or they can connect on different lines. This
pooling of lines among many poten tial locations is more cost e f f e ctive than alternative poin tto-point lines.
INTEROPERABILITY OVERVIEW
“Interoperability” is the ability to operate and exchange information in a heterogeneous network.
The CyberSWITCH supports interoperability with many different remote devices over ISDN.
INTEROPERABILITY PROTOCOLS
In order to commun icate wi th vari ous remot e devic es over I SDN, the CyberSWI TCH must i dentif y
the device type and the protocol it is using.
The CyberSWITCH supports the following line protocols:
• HDLC Ethernet Frames
• Ordered Protocol for Ethernet Frames
• Point-to-Point Protocol (PPP) Encapsulation for IP Datagrams

USER’S GUIDE
30 CyberSWITCH
The CyberSWITCH supports the following PPP protocols:
• Link Control Protocol ( LCP)
• Multilink Protocol (MLP)
• Authentication Protocols
Challenge Handshake Authen tication Protocol (CHAP)
Password Authentication Protocol (PAP)
• Network Con trol Protocols (NCP)
Interne t P rotocol Control Protocol for TCP/IP (IPCP)
Intern e t work Packet Exchange Co ntrol Protocol for IPX (I PXCP)
Bridge Control Pro toc ol for bridg es (BCP)
• Compressi on Control Pr otocol (CCP)
• AppleTalk Control Protocol (ATCP)
The CyberSWITCH supports the fo llowing AppleTalk protocols:
• EtherTalk Link Access Protocol (ELAP)
• AppleTalk Address Resoluti on Protocol (AARP)
• PPP AppleTalk/AppleTalk Control Protocol (ATCP)
• Datagram Delivery Protoco l (DDP )
• Routing Tab le Maintenance P rotocol (RTMP)
• AppleTalk Echo Protocol (AEP)
• Name Binding Protocol (NBP)
• Zone Inform ation Protocol (ZIP)
INTEROPERABILITY DEVICES
Remote devi ces that may conn e ct to the CyberSWITCH include the follow ing:
• MAC Lay er Bridges
•IP Host Devices
• IP Router Dev ices
• IPX Route rs
• AppleTalk Routers
MAC layer bridge s connec t to the syste m using the HD LC bridge encap sula tion line p rotoc ol .
These devi ces send transpar ently bridged E therne t frames to the sy stem. MAC layer br idges do not
process ne twork layer protocols. The y forward all packets based on source and destinati on MAC
addresses.
IP Host devices are single workstations or PCs that co nne ct to the system at the IP network layer.
These devices use either the RFC1294 based protocol or PPP to communicate with the system.
IP router devices are single devices that represent many ot her IP hosts and ro uters to the syste m.
They must use the CHAP or PAP protocol to identif y themselves to the system. IP routers usually
provide IP network address information at connection time (and use PPP to send user data to the
system).
IPX routers are single devices that perform network layer tasks (addressing, routing, and
switchin g) to move packet s from one loca tion on the network to another. IPX routers use the
Internetwork Packet Exchange (IPX) protocol, typical of the NetWare environment.
AppleTalk routers route AppleTalk datagrams based on address information. They support the
following protocols: RTMP, NBP, and ZIP.
 Loading...
Loading...