Bosch NDV-3502-F02, NDV-3502-F03, NDV-3503-F02, NDV-3503-F03 Specsheet

H.265
Video | FLEXIDOME IP micro 3000i
FLEXIDOME IP micro 3000i
www.boschsecurity.com
u 1080p and 5MP resolutions
u Built-in Essential Video Analytics to trigger relevant
alerts and quickly retrieve data
The FLEXIDOME IP micro 3000i is built for highquality, 24/7 performance, with a range of reliable
surveillance features, including
Essential Video Analytics, and is designed for easy
installation.
The compact and minimalist design provides high
installation flexibility and offers various mounting
options.
Functions
Essential Video Analytics
The built-in video analysis reinforces the Intelligenceat-the-Edge concept and now delivers even more
powerful features. Essential Video Analytics is ideal for
use in controlled environments with limited detection
ranges.
The system reliably detects, tracks, and analyzes
objects, and alerts you when predefined alarms are
triggered. A smart set of alarm rules makes complex
tasks easy and reduces false alarms to a minimum.
Metadata is attached to your video to add sense and
structure. This enables you to quickly retrieve the
relevant images from hours of stored video. Metadata
can also be used to deliver irrefutable forensic
evidence or to optimize business processes based on
people counting or crowd density information.
u Fully configurable H.265 multi-streaming
u High Dynamic Range (120 dB) for challenging bright
and dark scenes
u Built-in microphone for audio recording
High Dynamic Range
The high dynamic range mode is based on a multipleexposure process that captures more details in the
highlights and in the shadows even in the same scene.
The result is that you can easily distinguish objects
and features, for example, faces with bright backlight.
The actual dynamic range of the camera is measured
using Opto-Electronic Conversion Function (OECF)
analysis according to IEC 62676 Part 5.
Intelligent streaming
Smart encoding capabilities, together with Intelligent
Dynamic Noise Reduction technology and analytics,
reduce the bandwidth consumption to extremely low
levels. Only relevant information in the scene, like
motion, or objects found with the analytics, need to be
encoded.
The camera is capable of triple streaming which allows
the camera to deliver independent, configurable
streams for live viewing, recording, or remote
monitoring via constrained bandwidths.
Each of these streams can be adapted independently
to deliver high quality video, perfectly tailored to
purpose, while reducing bit rate by up to 90%
compared to a standard camera.
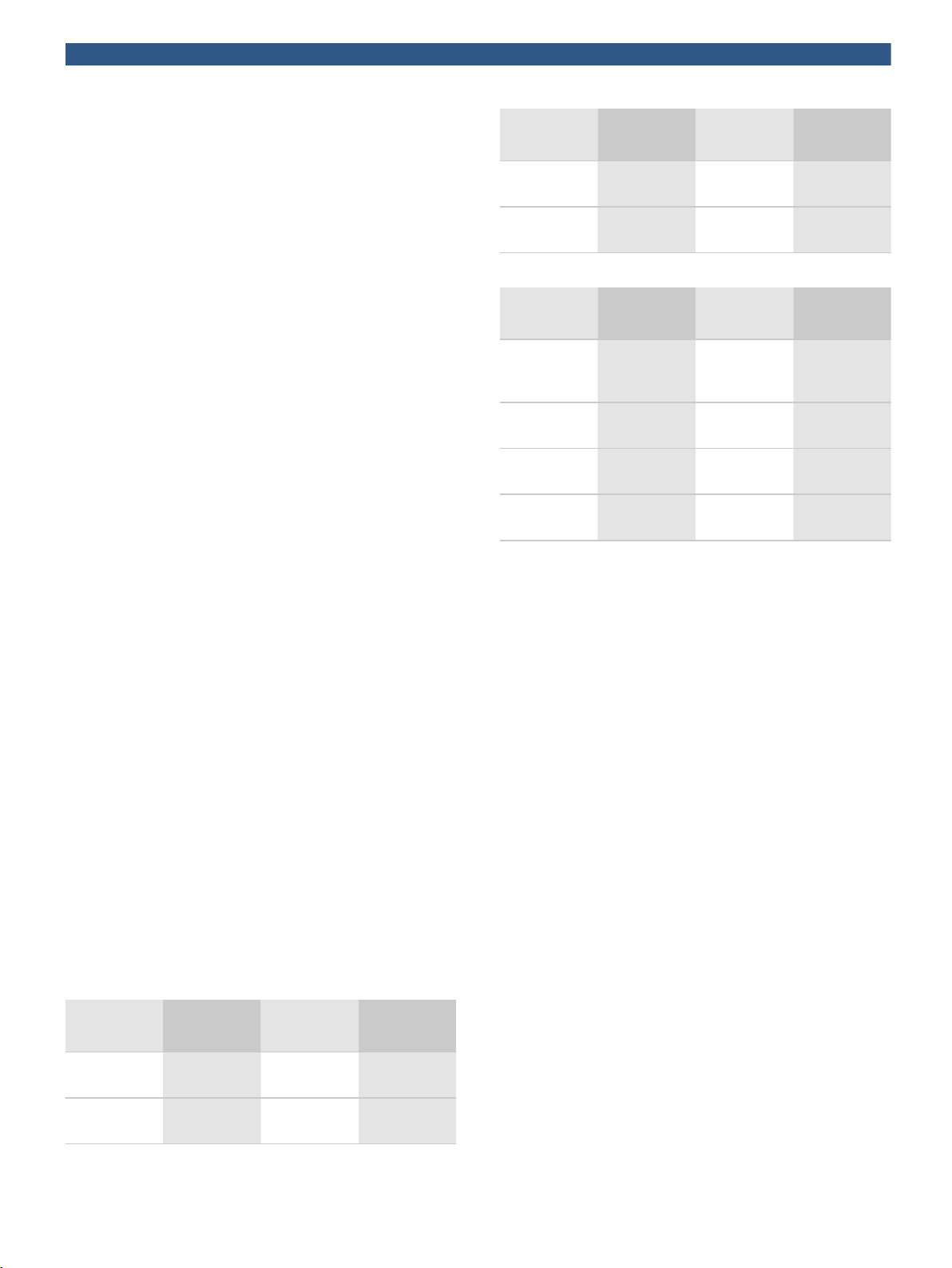
| FLEXIDOME IP micro 3000i
2
H.265 high-efficiency video encoding
The camera is designed on the most efficient and
powerful H.264 and H.265/HEVC encoding platform.
The camera is capable of delivering high-quality and
high-resolution video with very low network load. With
a doubling of encoding efficiency, H.265 is the new
compression standard of choice for IP video
surveillance systems.
Tamper and motion detection
A wide range of configuration options is available for
alarms signaling camera tampering. A built-in algorithm
for detecting movement in the video can also be used
for alarm signaling.
Built-in microphone and audio alarm
The camera has a built-in microphone to allow
operators to listen in on the monitored area. Audio
detection can be used to generate an alarm if needed.
Recording and storage management
Recording management can be controlled by the
Bosch Video Recording Manager application, or the
camera can use local storage and iSCSI targets
directly without any recording software.
Local storage can be used for recording "at the edge"
or for Automatic Network Replenishment (ANR)
technology to improve the overall recording reliability.
Pre-alarm recording in RAM reduces bandwidth
consumption on the network and extends the effective
life of the memory card.
Edge recording
Insert a memory card into the card slot to store up to
2 TB of local alarm recording. Pre-alarm recording in
RAM reduces recording bandwidth on the network,
and extends the effective life of the memory card.
It has advanced edge recording providing a reliable
storage solution possible due to the combination of
these functions:
• Industrial SD card support allows for extreme lifetime
• Health monitoring of industrial SD cards provide early
service indications.
DORI coverage
DORI (Detect, Observe, Recognize, Identify) is a
standard system (EN-62676-4) for defining the ability
of a camera to distinguish persons or objects within a
covered area. The maximum distance at which a
camera/lens combination can meet these criteria is
shown below:
1080p camera with 2.3 mm or 2.8 mm lens
DORI DORI
definition
Detect 25 px/m
(8 px/ft)
Observe 63 px/m
(19 px/ft)
Distance
2.3 mm/
2.8 mm
17 m/28 m
(56 ft/93 ft)
7 m/11 m
(22 ft/37 ft)
Horizontal
width
77 m
(252 ft)
30 m
(100 ft)
DORI DORI
definition
Recognize 125 px/m
(38 px/ft)
Identify 250 px/m
(76 px/ft)
Distance
2.3 mm/
2.8 mm
3 m/6 m
(11 ft/19 ft)
2 m/3 m
(6 ft/9 ft)
Horizontal
width
15 m
(50 ft)
8 m
(25 ft)
5.3MP camera with 2.3 mm or 2.8 mm lens
DORI DORI
definition
Detect 25 px/m
(8 px/ft)
Observe 63 px/m
(19 px/ft)
Recognize 125 px/m
(38 px/ft)
Identify 250 px/m
(76 px/ft)
Distance
2.3 mm/
2.8 mm
37 m/57 m
(121 ft/
188 ft)
15 m/23 m
(48 ft/75 ft)
7 m/11 m
(24 ft/38 ft)
4 m/6 m
(12 ft/19 ft)
Horizontal
width
123 m
(403 ft)
49 m
(160 ft)
25 m
(81 ft)
12 m
(40 ft)
Easy installation
Power for the camera can be supplied via a Powerover-Ethernet compliant network cable connection.
With this configuration, only a single cable connection
is required to view, power, and control the camera.
Using PoE makes installation easier and more costeffective, as cameras do not require a local power
source.
The camera can also be supplied with power from
+12 VDC power supplies.
For trouble-free network cabling, the camera supports
Auto-MDIX which allows the use of straight or crossover cables.
Data security
Special measures have been put in place to ensure the
highest level of security for device access and data
transport. The three-level password protection with
security recommendations allows users to customize
device access. Web browser access can be protected
using HTTPS and firmware updates can also be
protected with authenticated secure uploads.
The on-board Trusted Platform Module (TPM) and
Public Key Infrastructure (PKI) support, guarantee
superior protection from malicious attacks. The 802.1x
network authentication with EAP/TLS, supports
TLS 1.2 with updated cipher suites including AES 256
encryption.
The advanced certificate handling offers:
• Self-signed unique certificates automatically created
when required
• Client and server certificates for authentication
• Client certificates for proof of authenticity
• Certificates with encrypted private keys
 Loading...
Loading...