
LE2700A LE2710C LE2721C
LE2700AE LE2711C LE2722C
LE2700UK LE2720C LE2731C
LE2700 Series Hardened Managed Modular Switches
User Manual
This Layer 2 modular rackmount managed Gigabit Ethernet switch
has four module slots that accommodate 8-port 10/100/1000BASE-T RJ-45
and SFP modules, and 4-port 10GE SFP+ and 100-Mbps fiber ST and fiber
SC modules.
Customer
Support
Information
Order toll-free in the U.S.: Call 877-877-BBOX (outside U.S. call 724-746-5500)
FREE technical support 24 hours a day, 7 days a week: Call 724-746-5500 or fax 724-746-0746
Mailing address: Black Box Corporation, 1000 Park Drive, Lawrence, PA 15055-1018
Web site: www.blackbox.com • E-mail: info @blackbox.com

Trademarks Used in this Manual
Trademarks Used in this Manual
Black Box and the Double Diamond logo are registered trademarks of BB Technologies, Inc.
Any other trademarks mentioned in this manual are acknowledged to be the property of the trademark owners.
Disclaimer:
Black Box Network Services shall not be liable for damages of any kind, including, but not limited to, punitive, consequential or
cost of cover damages, resulting from any errors in the product information or specifications set forth in this document and Black
Box Network Services may revise this document at any time without notice.
We‘re here to help! If you have any questions about your application
or our products, contact Black Box Tech Support at 724-746-5500
or go to blackbox.com and click on “Talk to Black Box.”
You’ll be live with one of our technical experts in less than 60 seconds.
Page 2
724-746-5500 | blackbox.com

FCC and IC RFI Statements
Federal Communications Commission and Industry Canada Radio Frequency Interference
Statements
This equipment generates, uses, and can radiate radio-frequency energy, and if not installed and used properly, that is, in strict
accordance with the manufacturer’s instructions, may cause inter ference to radio communication. It has been tested and found to
comply with the limits for a Class A computing device in accordance with the specifications in Subpart B of Part 15 of FCC rules,
which are designed to provide reasonable protection against such interference when the equipment is operated in a commercial
environment. Operation of this equipment in a residential area is likely to cause interference, in which case the user at his own
expense will be required to take whatever measures may be necessary to correct the interference.
Changes or modifications not expressly approved by the party responsible for compliance could void the user’s authority to
operate the equipment.
This digital apparatus does not exceed the Class A limits for radio noise emis sion from digital apparatus set out in the Radio
Interference Regulation of Industry Canada.
Le présent appareil numérique n’émet pas de bruits radioélectriques dépassant les limites applicables aux appareils numériques
de la classe A prescrites dans le Règlement sur le brouillage radioélectrique publié par Industrie Canada.
724-746-5500 | blackbox.com
Page 3

NOM Statement
Instrucciones de Seguridad
(Normas Oficiales Mexicanas Electrical Safety Statement)
1. Todas las instrucciones de seguridad y operación deberán ser leídas antes de que el aparato eléctrico sea operado.
2. Las instrucciones de seguridad y operación deberán ser guardadas para referencia futura.
3. Todas las advertencias en el aparato eléctrico y en sus instrucciones de operación deben ser respetadas.
4. Todas las instrucciones de operación y uso deben ser seguidas.
5. El aparato eléctrico no deberá ser usado cerca del agua—por ejemplo, cerca de la tina de baño, lavabo, sótano mojado o cerca
de una alberca, etc.
6. El aparato eléctrico debe ser usado únicamente con carritos o pedestales que sean recomendados por el fabricante.
7. El aparato eléctrico debe ser montado a la pared o al techo sólo como sea recomendado por el fabricante.
8. Servicio—El usuario no debe intentar dar servicio al equipo eléctrico más allá a lo descrito en las instrucciones de operación.
Todo otro servicio deberá ser referido a personal de servicio calificado.
9. El aparato eléctrico debe ser situado de tal manera que su posición no interfiera su uso. La colocación del aparato eléctrico
sobre una cama, sofá, alfombra o superficie similar puede bloquea la ventilación, no se debe colocar en libreros o gabinetes
que impidan el flujo de aire por los orificios de ventilación.
10. El equipo eléctrico deber ser situado fuera del alcance de fuentes de calor como radiadores, registros de calor, estufas u otros
aparatos (incluyendo amplificadores) que producen calor.
11. El aparato eléctrico deberá ser connectado a una fuente de poder sólo del tipo descrito en el instructivo de operación, o como
se indique en el aparato.
12. Precaución debe ser tomada de tal manera que la tierra fisica y la polarización del equipo no sea eliminada.
13. Los cables de la fuente de poder deben ser guiados de tal manera que no sean pisados ni pellizcados por objetos colocados
sobre o contra ellos, poniendo particular atención a los contactos y receptáculos donde salen del aparato.
14. El equipo eléctrico debe ser limpiado únicamente de acuerdo a las recomendaciones del fabricante.
15. En caso de existir, una antena externa deberá ser localizada lejos de las lineas de energia.
16. El cable de corriente deberá ser desconectado del cuando el equipo no sea usado por un largo periodo de tiempo.
17. Cuidado debe ser tomado de tal manera que objectos liquidos no sean derramados sobre la cubierta u orificios de ventilación.
18. Servicio por personal calificado deberá ser provisto cuando:
A: El cable de poder o el contacto ha sido dañado; u
B: Objectos han caído o líquido ha sido derramado dentro del aparato; o
C: El aparato ha sido expuesto a la lluvia; o
D: El aparato parece no operar normalmente o muestra un cambio en su desempeño; o
E: El aparato ha sido tirado o su cubierta ha sido dañada.
Page 4
724-746-5500 | blackbox.com

Table of Contents
Table of Contents
1. Specifications ......................................................................................................................................................................... 8
2. Overview .............................................................................................................................................................................10
2.1 Introduction ................................................................................................................................................................. 10
2.2 Features ....................................................................................................................................................................... 10
2.3 What’s Included .......................................................................................................................................................... 11
2.4 Hardware Description .................................................................................................................................................. 12
3. Hardware Installation ...........................................................................................................................................................16
3.1 Rackmount Installation ................................................................................................................................................ 16
3.2 Module Installation ...................................................................................................................................................... 16
3.2.1 RJ-45 Module (LE2720C) ....................................................................................................................................16
3.2.2 SFP Module (LE2721C) ....................................................................................................................................... 17
3.2.3 100/1000 Mbps SFP Module (LE2722C) or 10G SFP+ Module (LE2731C) ..............................................................17
3.2.4 Power Module .................................................................................................................................................. 18
3.3 Wiring .........................................................................................................................................................................19
3.3.1 Grounding .......................................................................................................................................................... 19
3.3.2 Fault Relay .......................................................................................................................................................... 19
3.3.3 Redundant Power Inputs .................................................................................................................................... 19
3.4 Connection .................................................................................................................................................................. 20
3.4.1 Cables ................................................................................................................................................................. 20
3.4.2 SFP .....................................................................................................................................................................22
3.4.3 B-Ring/B-Chain ..................................................................................................................................................22
4. Redundancy.........................................................................................................................................................................25
4.1 B-Ring ......................................................................................................................................................................... 25
4.1.1 Introduction ........................................................................................................................................................ 25
4.1.2 Configurations .................................................................................................................................................... 25
4.2 B-Chain ....................................................................................................................................................................... 26
4.2.1 Introduction ........................................................................................................................................................ 26
4.2.2 Configurations ....................................................................................................................................................26
4.3 MRP ............................................................................................................................................................................. 26
4.3.1 Introduction ........................................................................................................................................................ 26
4.3.2 Configurations ....................................................................................................................................................26
4.4 STP/RSTP/MSTP ...........................................................................................................................................................27
4.4.1 STP/RSTP ............................................................................................................................................................27
4.4.2 MSTP ..................................................................................................................................................................30
4.4.3 CIST .................................................................................................................................................................... 33
4.5 Fast Recovery ............................................................................................................................................................... 34
5. Management .......................................................................................................................................................................35
5.1 Basic Settings ...............................................................................................................................................................36
5.1.1 System Information .............................................................................................................................................36
5.1.2 Admin and Password .......................................................................................................................................... 37
5.1.3 Authentication .................................................................................................................................................... 37
5.1.4 IP Settings ........................................................................................................................................................... 38
5.1.5 IPv6 Settings ....................................................................................................................................................... 39
5.1.6 HTTPS ................................................................................................................................................................. 39
5.1.7 S SH .....................................................................................................................................................................40
5.1.8 LLDP ...................................................................................................................................................................40
724-746-5500 | blackbox.com
Page 5

Table of Contents
5.1.9 Modbus TCP .......................................................................................................................................................43
5.1.10 Backup/Restore Configurations ......................................................................................................................... 43
5.1.11 Firmware Update ...............................................................................................................................................44
5.2 DHCP Server ................................................................................................................................................................ 44
5.2.1 Basic Settings ......................................................................................................................................................44
5.2.2 Dynamic Client List .............................................................................................................................................44
5.2.3 Client List ...........................................................................................................................................................44
5.2.4 Relay Agent ........................................................................................................................................................ 45
5.3 Port Setting ................................................................................................................................................................. 47
5.3.1 Port Control ........................................................................................................................................................47
5.3.2 Port Trunk ..........................................................................................................................................................48
5.3.3 LACP ..................................................................................................................................................................49
5.3.4 Loop Ground ......................................................................................................................................................52
5.4 VLAN ........................................................................................................................................................................... 53
5.4.1 VLAN Membership ............................................................................................................................................. 53
5.4.2 Port Configurations ............................................................................................................................................ 54
5.4.3 Private VLAN ...................................................................................................................................................... 62
5.5 SNMP ..........................................................................................................................................................................64
5.5.1 SNMP System Configurations .............................................................................................................................64
5.5.2 SNMP Community Configurations .....................................................................................................................66
5.5.3 SNMP User Configurations .................................................................................................................................66
5.5.4 SNMP Group Configurations ..............................................................................................................................68
5.5.5 SNMP View Configurations ................................................................................................................................68
5.5.6 SNMP Access Configurations ..............................................................................................................................69
5.6 Traffic Prioritization ...................................................................................................................................................... 70
5.6.1 Storm Control ..................................................................................................................................................... 70
5.6.2 Port Classification ............................................................................................................................................... 71
5.6.3 Port Tag Remaking ............................................................................................................................................. 72
5.6.4 Port DSCP ...........................................................................................................................................................73
5.6.5 Port Policing ....................................................................................................................................................... 74
5.6.6 Queue Policing ................................................................................................................................................... 75
5.6.7 QoS Egress Port Scheduler and Shapers ............................................................................................................. 76
5.6.8 Port Scheduled ................................................................................................................................................... 78
5.6.9 Port Shaping ....................................................................................................................................................... 78
5.6.10 DSCP Based QoS ...............................................................................................................................................79
5.6.11 DSCP Translation ............................................................................................................................................... 80
5.6.12 DSCP Classification ...........................................................................................................................................80
5.6.13 QoS Control List ................................................................................................................................................ 81
5.6.14 QoS Counters ...................................................................................................................................................83
5.6.15 QCL Status ........................................................................................................................................................83
5.7 Multicast ......................................................................................................................................................................84
5.7.1 IGMP Snooping ...................................................................................................................................................84
5.7.2 VLAN Configurations of IGMP Snooping ............................................................................................................85
5.7.3 IGMP Snooping Status ........................................................................................................................................ 86
5.7.4 Groups IGMP Snooping Information ..................................................................................................................87
5.8 Security ........................................................................................................................................................................87
5.8.1 Remote Control Security Configurations .............................................................................................................87
5.8.2 Device Binding ...................................................................................................................................................88
5.8.3 ACL Ports ........................................................................................................................................................... 92
5.8.4 AAA ................................................................................................................................................................. 101
5.8.5 RADIUS ............................................................................................................................................................ 102
Page 6
724-746-5500 | blackbox.com

Table of Contents
5.8.6 NAS (802.1x) .................................................................................................................................................... 107
5.9 Alerts ......................................................................................................................................................................... 115
5.9.1 Fault Alarm ....................................................................................................................................................... 115
5.9.2 System Warning ............................................................................................................................................... 115
5.10 Monitor and Diag ...................................................................................................................................................... 118
5.10.1 MAC Table ...................................................................................................................................................... 118
5.10.2 Port Statistics .................................................................................................................................................. 120
5.10.3 Port Mirroring ................................................................................................................................................. 122
5.10.4 System Log Information .................................................................................................................................. 123
5.10.5 Cable Diagnostics ........................................................................................................................................... 124
5.10.6 SFP Monitor .................................................................................................................................................... 125
5.10.7 Ping................................................................................................................................................................. 125
5.11 Synchroniz ation ......................................................................................................................................................... 127
5.12 Troubleshooting ......................................................................................................................................................... 13 0
5.12.1 Factory Defa u lt s .............................................................................................................................................. 130
5.12.2 System Reboot ................................................................................................................................................ 130
5.13 Command Line Interface Management ..................................................................................................................... 130
724-746-5500 | blackbox.com
Page 7
Chapter 1: Specifications
1. Specifications
Ethernet Standards IEEE 802.3 10BASE-T,
IEEE 802.3u 100BASE-TX and 100BASE-FX,
IEEE 802.3ab 1000BASE-T,
IEEE 802.3z 100BASE-X,
IEEE 802.3ae 10 Gigabit Ethernet,
IEEE 802.3ad LACP (Link Aggregation Control Protocol),
IEEE 802.1p COS (Class of Service),
IEEE 802.1q VLAN tagging,
IEEE 802.1w RSTP (Rapid Spanning Tree Protocol),
IEEE 802.1s MSTP (Multiple Spanning Tree Protocol),
IEEE 802.1x authentication,
IEEE 801.1AB LLDP (Link Layer Discovery Protocol)
Jumbo Frames Up to 9.6 KB
MAC Tab le 8 K
Network Redundancy MR P,
MSTP (RSTP/STP compatible)
Priority Queues 8
Processing Store-and-forward
Security Features Device binding,
Enable/disable ports, MAC based port security,
Port-based network access control (802.1x),
Single 802.1x and Multiple 802.1x,
MAC-based authentication,
QoS assignment,
Guest VLAN,
MAC address limit,
TACACS+,
VLAN (802.1Q) to segregate and secure network traffic,
Radius centralized password management,
SNMPv3 encrypted authentication and access security,
Https/SSH enhance network security,
Web and CLI authentication and authorization,
Authorization (15 levels),
IP source guard
Software Features IEEE 1588v2 clock synhronization,
IEEE 801.1D Bridge, auto MAC address learning/aging and MAC address (static),
Multiple Registration Protocol (MRP),
MSTP (RSTP/STP compatible),
Redundant Ring with recovery time less tham 30 ms over 250 units,
Quality of Service (802.1p) for real-time traffic,
VLAN (802.1Q) with VLAN tagging,
IGMP v2/v3 Snooping,
Port configuration, status, statistics, monitoring, security,
DHCP Server/Client,
DHCP Relay,
Modbus TCP,
DNS client proxy,
SMTP Client
Page 8
724-746-5500 | blackbox.com

Chapter 1: Specifications
Connectors LE2700A, LE2700AE, LE2700UK:
RS-232 Serial Console Port: (1) RJ-45 via console cable, 115200 bps, 8, N, 1;|
Fault contact: 24-VDC, 1-A relay;
LE2710C: (4) 100FX SC;
LE2711C: (4) 100FX ST;
LE2720C: (8) 10 /100 /100 0BASE-T RJ-45;
LE2721C: (8) slots for 100/1000-Mbps SFP modules;
LE2722C: (4) slots for 100/1000 Mbps SFP modules;
LE2731C: (4) slots for 10GE SFP+ modules
Indicators LE2700A, LE2700AE, LE2700UK:
(39) LEDs:
(1) PWR, (1) PWR1, (1) PWR2, (1) RM, (1) Ring, (1) Fault, (1) Def, (1) Link, (1) SPD,
(1) FDX, (1) RMT,
(28) Port LEDs;
LE2720C:
(2) LEDs per port;
LE2731C:
(1) LED per port
Environmental Temperature Tolerance:
Operating: -40 to +185° F (-40 to +85° C);
Storage: -40 to +185° F (-40 to +85° C);
Humidity:
Operating: 5 to 95%, noncondensing
Power Input: Dual 88–264 VAC/100–370 VDC power inputs at terminal block;
Consumption (Typ.): 43.5 watts max.;
Overload Current Protection: Present
Dimensions 1.73"H x 17.32"W x 12.8"D (4.4 x 44 x 32.5 cm), 19" rackmountable
Weight 14.5 lb. (6.6 kg)
Approvals EMI:
FCC Part 15,
CISPR (EN55022) Class A,
EN50155 (EN50121-3-2, EN55011, EN50121-4 );
EMS:
EN61000-4-2 (ESD),
EN61000-4-3 (RS),
EN61000-4-4 (EFT),
EN61000-4-5 (Surge),
EN61000-4-6 (CS),
EN61000-4-8,
EN61000-4-11
724-746-5500 | blackbox.com
Page 9

Chapter 2: Overview
2. Overview
2.1 Introduction
The LE2700 Series Hardened Managed Modular Switches are ideal for industrial Ethernet applications. Use them to control and
monitor equipment at oil/gas wells transmission facilities, water/wastewater, IP security/surveillance cameras and alarms, utilities,
or building HVAC systems.
The LE2700 Series Hardened Managed Modular Switches are scalable, flexible, cost-effective, and reliable. The 4-Slot Chassis is a
Layer 2 modular rackmount managed Gigabit Ethernet switch with four module slots. 8-port 10/100/1000BASE-T RJ-45 and SFP
modules, and 4-port 10GE SFP+ and 100-Mbps fiber ST and fiber SC modules are also available.
Figure 2-1. Available models.
Part Number Description
LE2700A Hardened Managed Modular Switch, 4-Slot Chassis, US
LE2700AE Hardened Managed Modular Switch, 4-Slot Chassis, EU
LE2700UK Hardened Managed Modular Switch, 4-Slot Chassis, UK
LE2710C 4-port 100FX multimode 2 km SC module
LE2711C 4-port 100FX multimode 2 km ST module
LE2720C 8-port 10 /100/1000BA SE-T R J-45 module
LE2721C 8-port 100/1000 Mbps SFP module
LE2722C 4-port 100/1000 Mbps SFP module
LE2731C 4-port 10 GE SFP+ module
2.2 Features
• Modular design with dual power supplies enables flexible network planning by allowing users to add capacity as demand
increases. Choose the right quantity, speed, and range of interfaces for the application. Purchase the capacity you need when
you need it.
• Environmentally hardened case withstands operating temperatures of -40 to +185° F (-40 to +85° C).
• Managed switch enables you to configure and monitor installations remotely.
• Supports Web, SNMP, and console user interfaces.
• Choose from copper, fiber, 10/100/1000-Mbps, and 10GE interfaces.
• Complies with IEEE 802.3az energy efficient standards.
• Manages traffic with 802.1p/q tagged frames.
• Handles jumbo frames.
• Supports IEEE 1588v2 synchronization.
• Accommodates high availability protocols, including xSTP, link aggregation, and redundant ring protocols.
• Supports IP multicast snooping with IGMPv2/3.
• Authenticates ACLs, TACACS+, and 802.1x users.
Page 10
724-746-5500 | blackbox.com

Chapter 2: Overview
2.3 What’s Included
Your package should include the following items. If anything is missing or damaged, contact Black Box Technical Support
at 724-746-5500 or info@blackbox.com.
LE2700A:
• LE2700 Series Hardened Managed Modular Switch with power supply
• U.S. power cord
LE2700AE:
• LE2700 Series Hardened Managed Modular Switch with power supply
• EU. power cord
LE2700UK:
• LE2700 Series Hardened Managed Modular Switch with power supply
• UK power cord
LE2710C:
4-port 100FX multimode 2 km SC module
LE2711C :
4-port 100FX multimode 2 km ST module
LE2720C:
8-port 10 /100/1000BA SE-T R J-45 module
LE2721C :
8-port 100/1000 Mbps SFP module
LE2722C:
4-port 100/1000 Mbps SFP module
LE2731C :
4-port 10 GE SFP+ module
You can download this user manual from the Black Box Web site.
To download from the Web site:
1. Go to www.blackbox.com
2. Enter the part number (LE2700A) in the search box:
3. Click on the “Resources” tab on the product page, and select the document you wish to download.
724-746-5500 | blackbox.com
Pa ge 11
Chapter 2: Overview
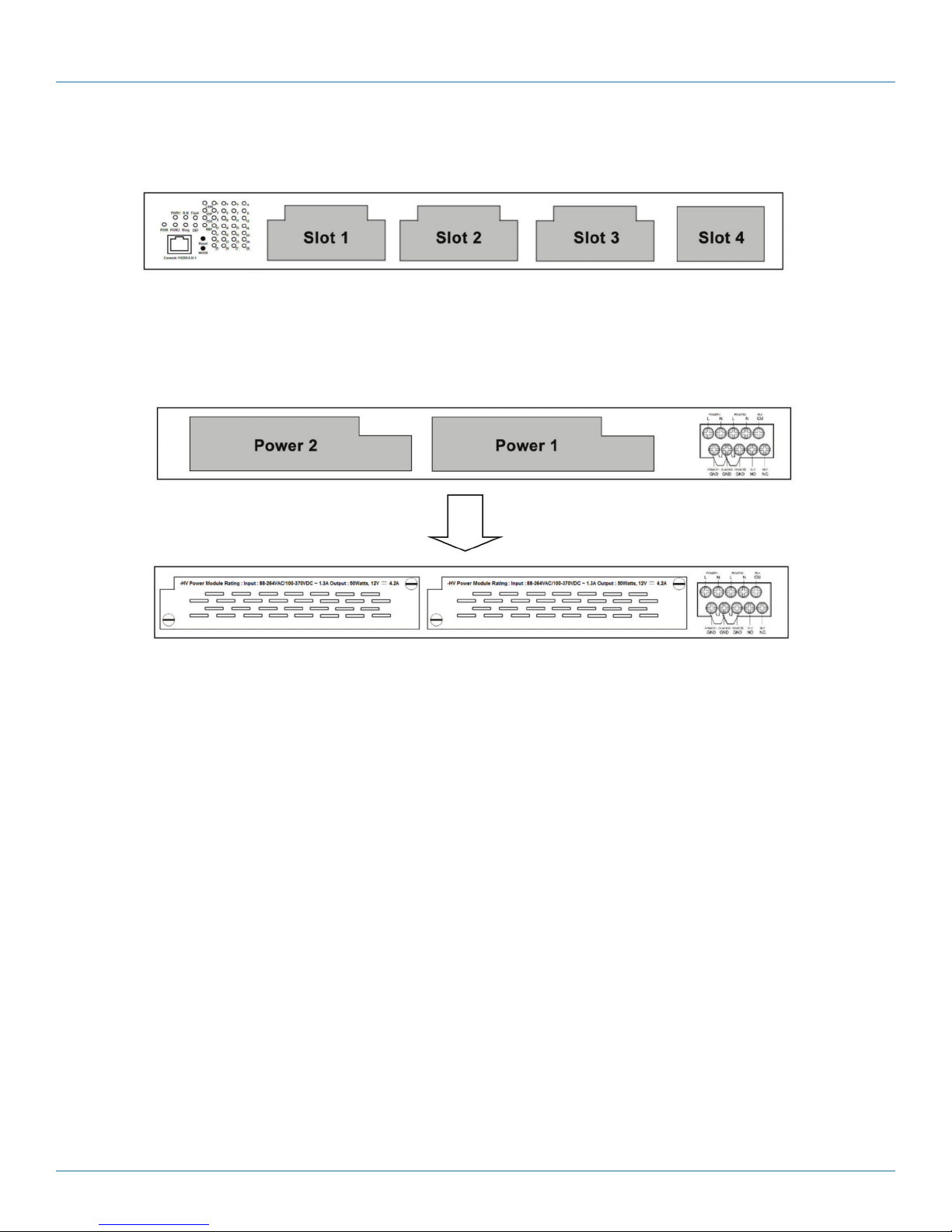
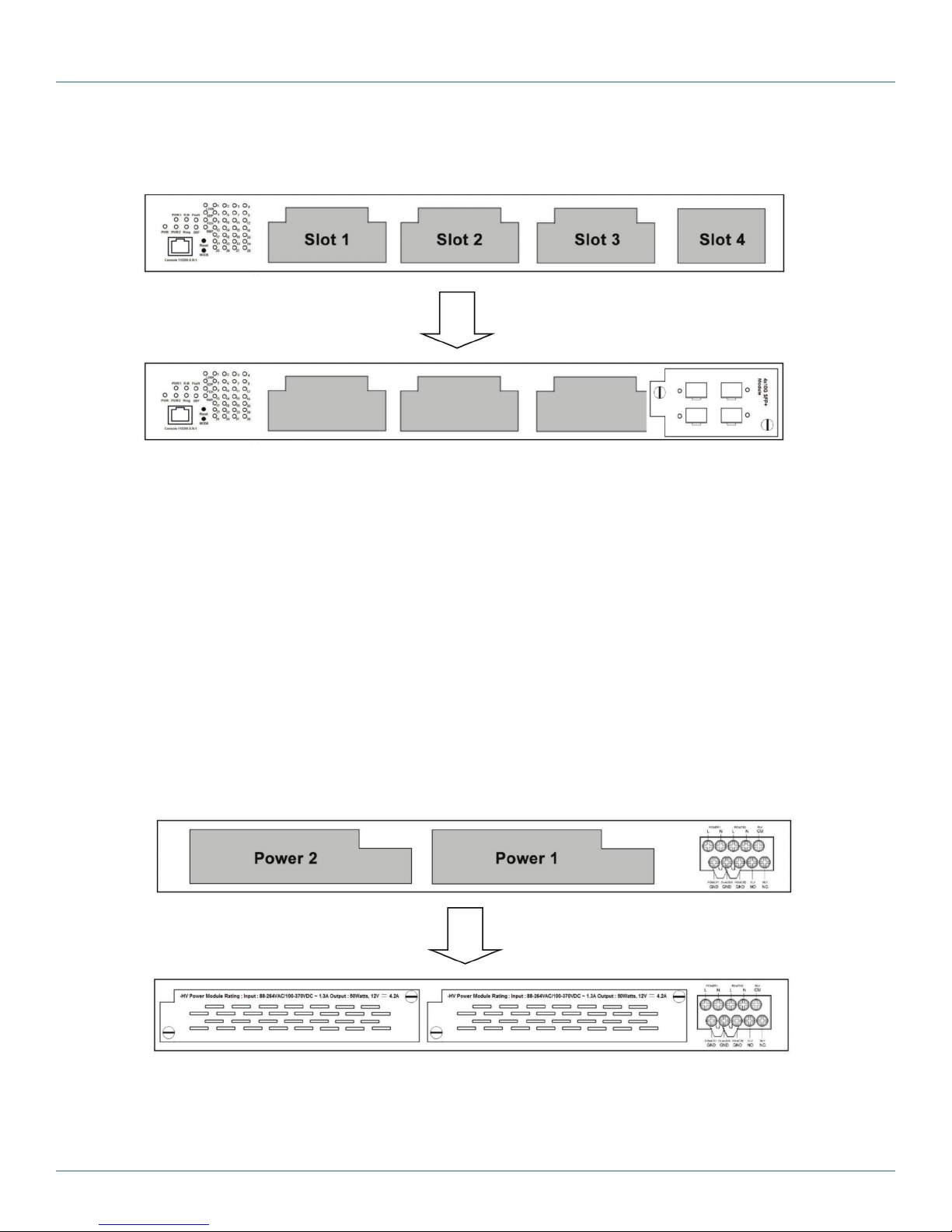
2.4 Hardware Description
10-Gigabit or Gigabit Ethernet module
installs in slot 4
Figure 2-1. Front panel.
Power module slot 2
Power module
installed in slot 2
Power module slot 1
Power module
installed in slot 1
Figure 2-2. Back panel.
Page 12
724-746-5500 | blackbox.com

Chapter 2: Overview
On the rear panel of the switch are two panel module slots and one terminal block. The terminal blocks include two power pairs
for redundant power supply.
2
3 45 1 6
8
Table 2-2. LE2700 Series Hardened Managed Modular Switches Components2
Number Component Description
1
2
3
Model name
System and Port status LEDs System LEDs include PWR/PWR1/PWR2/R.M/Ring/Fault/DEF.
Serial console port
Front view
Rear view
Name of product
Port LEDs include LINK/SPD/FDX/port number.
Links to console for management.
7
4
5 LED mode button To change port LED mode, press the Mode button.
6 Ethernet module slots Enable different RJ-45/SFP modular combinations based on your needs.
7 Power input module slots Houses power input modules.
8 Terminal block Links to DC connector.
Reset button
Press Reset for 3 seconds to reset and 5 seconds to return to factory default.
724-746-5500 | blackbox.com
Page 13

Chapter 2: Overview
B-Ring provides two 10 Gigabit modules and four Gigabit Ethernet modules to meet your demand for high speed. For applications requiring long-distance data transmission, B-Ring also provides several fiber modules to meet your needs. Please refer to the
following table for available modules.
The modules are not hot-swappable. Be sure to turn off power before changing modules; otherwise, the system will not detect
newly inserted modules.
Table 2-3. Switch Modules.
Part Number Description
LE2710C 4-port 100FX multimode 2 km SC module
LE2711C 4-port 100FX multimode 2 km ST module
LE2720C 8-port 10 /100/1000BA SE-T R J-45 module
LE2721C 8-port 100/1000 Mbps SFP module
LE2722C 4-port 100/1000 Mbps SFP module
LE2731C 4-port 10 GE SFP+ module
Figure 2-4. SFP Modules.
Part Number Description Compatible Switch Modules
LFP401 SFP, 155-Mbps Fiber with Extended Diagnostics, 850-nm
Multimode, LC, 2 km
LFP402 SFP, 155-Mbps Fiber with Extended Diagnostics, 1310-nm Multimode, LC,
2 km
LFP403 SFP, 155-Mbps Fiber with Extended Diagnostics, 1310-nm,
Single-Mode, LC, 30 km
LFP404 SFP, 155-Mbps Fiber with Extended Diagnostics, 1310-nm
Single-Mode, Plus, LC, 60 km
LFP411 SFP, 1.25-Gbps Fiber with Extended Diagnostics, 850-nm
Multimode, LC, 300 m
LFP412 SFP, 1.25-Gbps Fiber with Extended Diagnostics, 1310-nm Multimode, LC,
2 km
LFP413 SFP, 1.25-Gbps Fiber with Extended Diagnostics, 1310-nm
Single-Mode, LC, 10 km
LFP414 SFP, 1.25-Gbps Fiber with Extended Diagnostics, 1310-nm
Single-Mode, LC, 30 km
LSP421 10GBASE-SR SFP+, 850-nm Multimode, 300 m, LC LE2731C
LSP422 10GBASE-SR SFP+, 1310-nm Single-Mode, 10 km, LC LE2731C
LE2721C
LE2721C
LE2721C
LE2721C
LE2721C
LE2721C
LE2721C
LE2721C
Page 14
724-746-5500 | blackbox.com

Table 2-5. LE2700 Series Hardened Managed Modular Switches LEDs.
Number LED Color Status Description
1
PWR Green On DC power on
Green Blinking Upgrading firmware
Chapter 2: Overview
2
3
4
5
6
7
8
9
10
11
PW1 Green On DC power module 1 activated
PW2 Green On DC power module 2 activated
R.M. Green
Ring Green On Ring enabled
Green Slowly blinking Ring structure is broken (i.e. part of the ring is disconnected)
Green Fast blinking Ring disabled
Fault Amber On Errors (power failure or port malfunctioning)
DEF Green On System reset to default
RMT Green On Accessed remotely
LNK Green On Port link up
SPD Green Blinking Data transmitted
FDX Amber On Port works under full duplex
On
Ring Master
724-746-5500 | blackbox.com
Page 15
Chapter 3: Hardware Installation
3. Hardware Installation
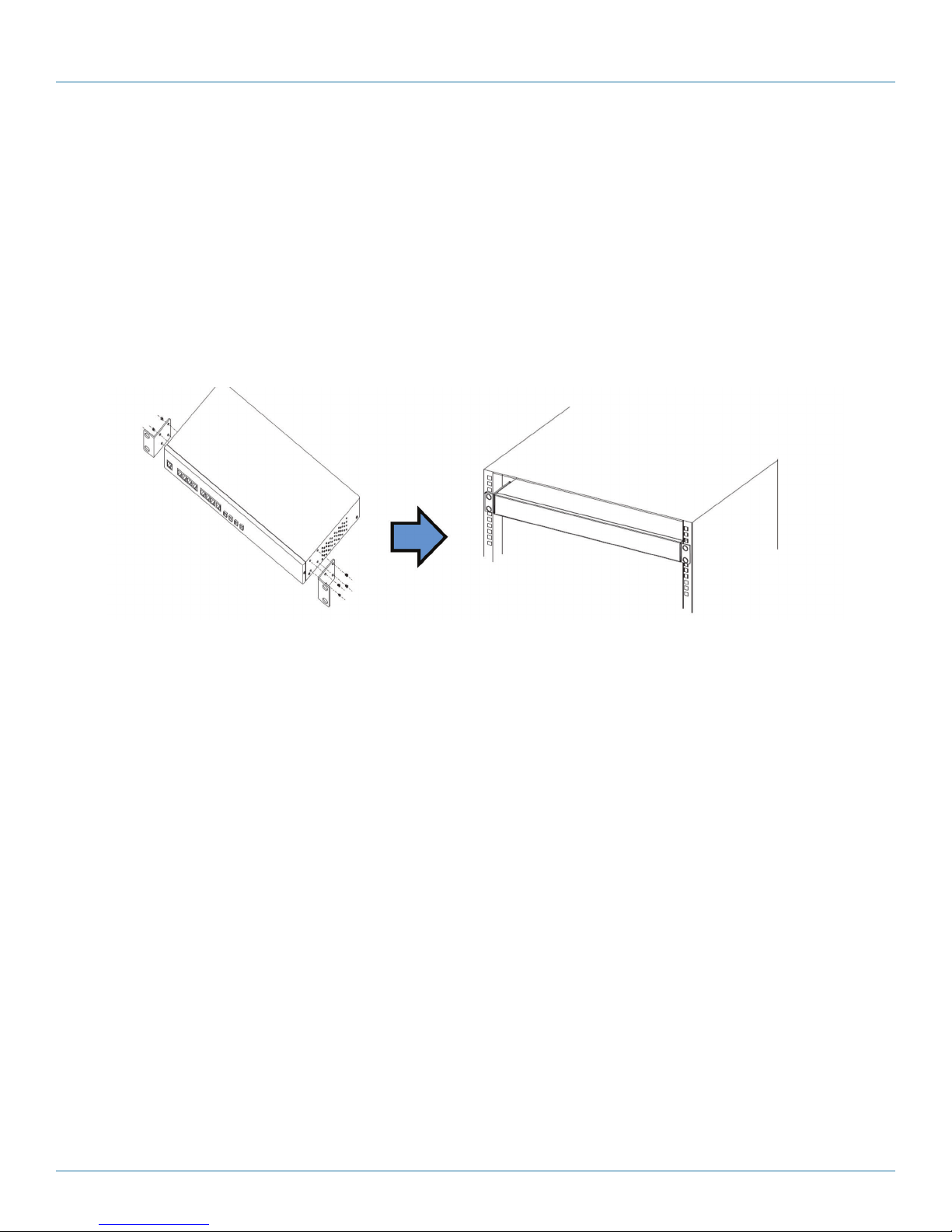
3.1 Rackmount Installation
The switch comes with two rackmount kits to allow you to fasten the switch to a rack in any environment.
Follow the steps below to install the switch to a rack.
Step 1: Install left and right front mounting brackets to the switch using 4 M3 screws on each side provided with switch.
Step 2: With front brackets orientated in front of the rack, nest front and rear brackets together. Fasten together using remaining
M4 screws into counter sunk holes.
Step 3: Fasten the front mounting bracket to the front of the rack.
Figure 3-1. Installing the module.
3.2 Module Installation
3.2.1 RJ-45 Module (LE2720C)
Each LE2700 Series Hardened Managed Modular Switches switch supports a maximum of three RJ-45 modules, giving you a total
of 24 RJ-45 ports. Follow the steps bellow for installation.
Step 1: Switch off the power of the switch.
Step 2: Insert the modules in Slot 1, 2, and 3 respectively.
Step 3: Switch on the power of the switch.
Page 16
724-746-5500 | blackbox.com
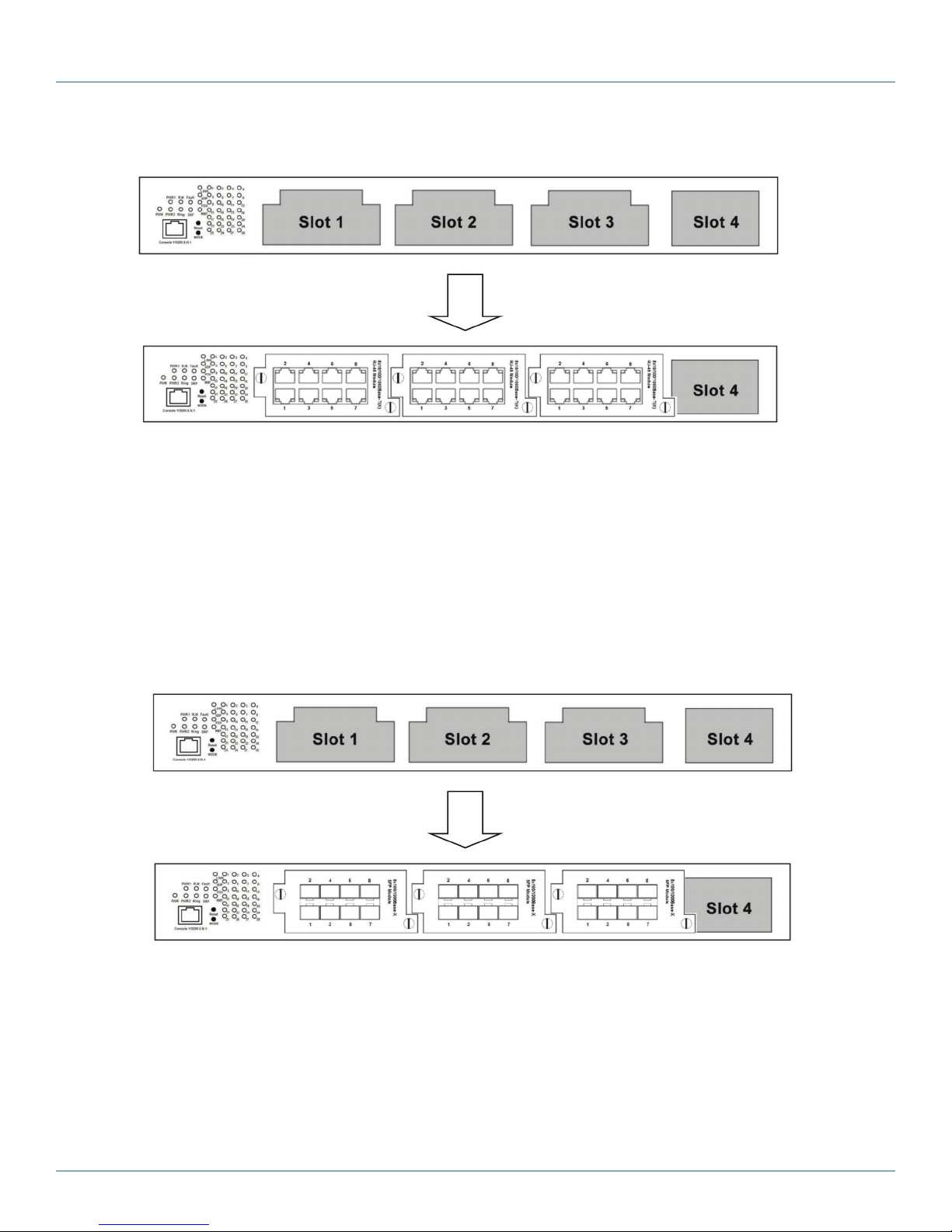
Figure 3-3. RJ-45 module.
Chapter 3: Hardware Installation
3.2.2 SFP Module (LE2721C)
Each LE2700 Series Hardened Managed Modular Switches switch supports a maximum of three SFP modules, giving you a total
of 24 SFP ports. Follow the steps bellow for installation.
Step 1: Switch off the power of the switch.
Step 2: Insert the modules in Slot 1, 2, and 3 respectively.
Step 3: Switch on the power of the switch.
3.2.3 100/1000 Mbps SFP Module (LE2722C) or 10G SFP+ Module (LE2731C)
Each LE2700 Series Hardened Managed Modular Switches switch supports one 4-port GE SFP or 10G SFP+ module, giving you a
total of four GE or 10G ports. Follow the steps bellow for installation. The module can be plugged into the 10-Gigabit Ethernet
port of the switch and links the switch with a fiberoptic network.
Follow the steps bellow for installation.
Step 1: Switch off the power of the switch.
Step 2: Insert the module in Slot 4.
Figure 3-4. SFP module.
724-746-5500 | blackbox.com
Page 17
Chapter 3: Hardware Installation
Step 3: Switch on the power of the switch.
CAUTION:
Figure 3-5. 10G SFP+ module.
1. The 10G slot can accommodate a Gigabit or 10G module (LE2722C or LE2731C); therefore, do not insert the LE2722C or
LE2731C module in other slots.
2. Removing and installing an Ethernet module can shorten its useful life. Do not remove and insert the modules more often than
is absolutely necessary.
3.2.4 Power Module
Each LE2700 Series Hardened Managed Modular Switches switch supports a maximum of two power modules. Follow the steps
bellow for installation.
Step 1: Switch off the power of the switch.
Step 2: Insert the modules in Power 1 and 2 slots respectively.
Step 3: Switch on the power of the switch.
Page 18
Figure 3-6. Power module.
724-746-5500 | blackbox.com
Chapter 3: Hardware Installation
3.3 Wiring
WARNING:
Do not disconnect modules or wires unless power has been switched off or the area is known to be non-hazardous. The devices
may only be connected to the supply voltage shown on the type plate.
ATTENTION:
1. Be sure to disconnect the power cord before installing and/or wiring your switches.
2. Calculate the maximum possible current in each power wire and common wire. Observe all electrical codes dictating the
maximum current allowable for each wire size.
3. If the current goes above the maximum ratings, the wiring could overheat, causing serious damage to your equipment.
4. Use separate paths to route wiring for power and devices. If power wiring and device wiring paths must cross, make sure the
wires are perpendicular at the intersection point.
5. Do not run signal or communications wiring and power wiring through the same wire conduit. To avoid interference, wires
with different signal characteristics should be routed separately.
6. You can use the type of signal transmitted through a wire to determine which wires should be kept separate. The rule of
thumb is that wiring sharing similar electrical characteristics can be bundled together.
7. Separate input wiring from output wiring.
8. Label the wiring to all devices in the system.
3.3.1 Grounding
Grounding and wire routing help limit the effects of noise due to electromagnetic interference (EMI). Run the ground connection
from the ground screws to the grounding surface prior to connecting devices.
3.3.2 Fault Relay
The relay contact of the 2-pin terminal block connector is used to detect user-configured events. The two wires attached to the
fault contacts form an open circuit when a user-configured event is triggered. If a user-configured event does not occur, the fault
circuit remains closed.
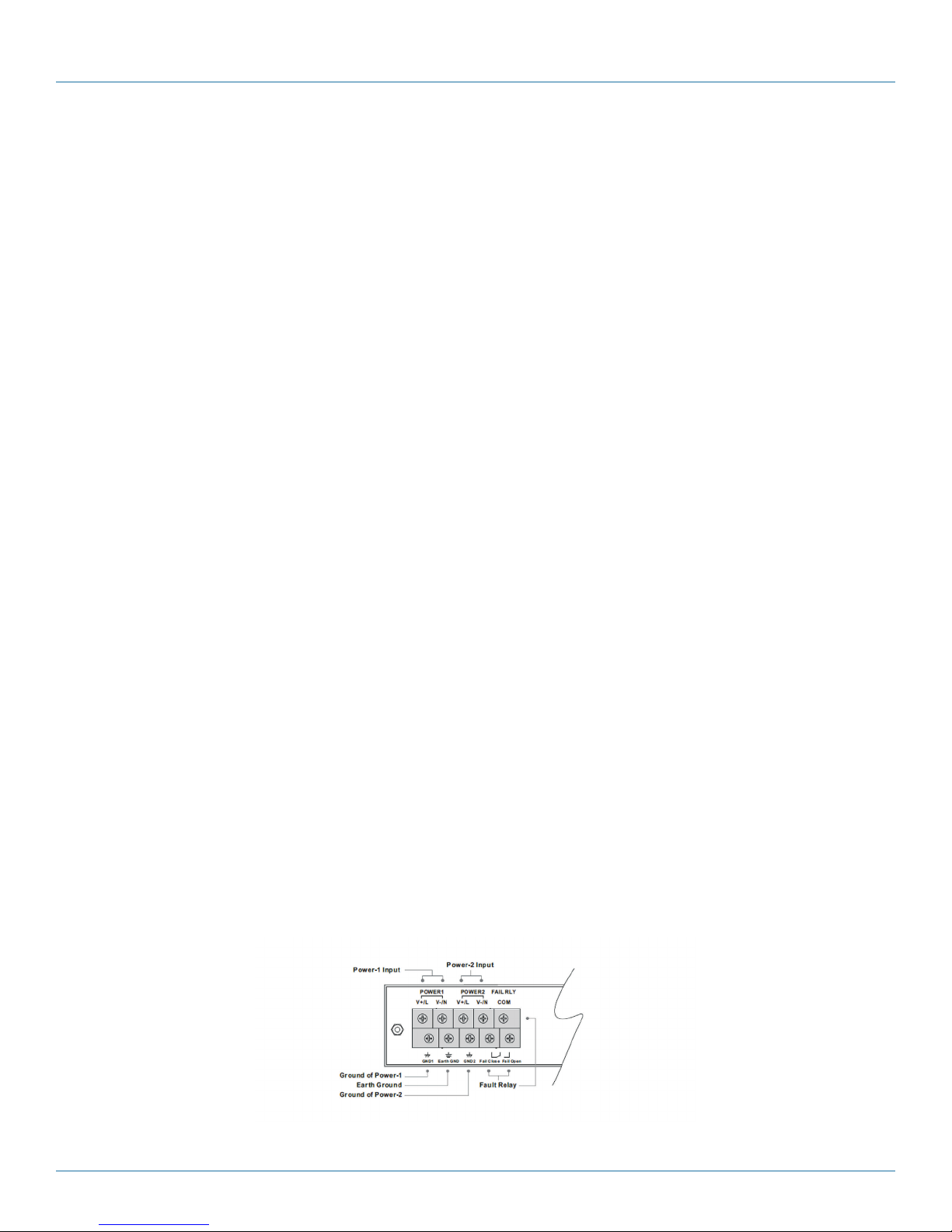
3.3.3 Redundant Power Inputs
The LE2700 Series Hardened Managed Modular Switches switches support dual redundant power supplies, Power Supply 1
(PWR1) and Power Supply 2 (PWR2). The connections for PWR1, PWR2 and the RELAY are located on the terminal block.
Step 1: Insert the negative/positive DC wires into the V-/ V+ terminals, respectively.
Step 2: To keep the DC wires from pulling loose, use a small flat-blade screwdriver to tighten the wire-clamp screws on the front
of the terminal block connector.
Step 3: Insert the plastic terminal block connector prongs into the terminal block receptor.
Figure 3-7. Redundant power inputs.
724-746-5500 | blackbox.com
Page 19

Chapter 3: Hardware Installation
3.4 Connection
3.4.1 C ab l e s
1000/100BASE-TX/10BASE-T Pin Assignments
The LE2700 Series Hardened Managed Modular Switches switches come with standard Ethernet ports. According to the link type,
the switch uses CAT 3, 4, 5,5e UTP cables to connect to any other network devices (PCs, servers, switches, routers, or hubs).
Refer to the following table for cable specifications.
Table 3-1. Cable types and specifications.
Cable Type Max. Length Connector
10BASE-T CAT3, 4, 5 100-ohm UTP 328 ft. (100 m) RJ-45
100BASE-TX CAT5 100-ohm UTP UTP 328 ft. (100 m) RJ-45
1000BASE-TX CAT5/CAT5e 100-ohm UTP UTP 328 ft. (100 m) RJ-45
With 1000/100BASE-TX/10BASE-T cables, pins 1 and 2 are used for transmitting data, and pins 3 and 6 are used for receiving
data.
Table 3-2. 10/100BASE-T RJ-45 pin assignments.
Pin Number Assignment
1 TD+
2 TD-
3 RD+
4 Not used
5 Not used
6 RD-
7 Not used
8 Not used
Table 3-3. 1000BASE-T RJ-45 pin assignments.
Pin Number Assignment
1 BI_DA+
2 BI_DA-
3 BI_DB+
4 BI_DC+
5 B I _D C-
6 BI_DB-
7 BI_DD+
8 BI_DD-
The LE2700 series switches support auto MDI/MDI-X operation. You can use a cable to connect the switch to a PC. Table 3-4
shows the 10BASE-T/ 100BASE-TX MDI and MDI-X port pinouts.
Page 20
724-746-5500 | blackbox.com
Chapter 3: Hardware Installation
Table 3-4. 10/100BASE-T MDI/MDI-X Pin Assignments.
Pin Number MDI port MDI-X port
1 TD+(transmit) RD+(receive)
2 TD- (transmit) RD- (receive)
3 RD+(receive) TD+(transmit)
4 Not used Not used
5 Not used Not used
6 RD- (receive) TD- (transmit)
7 Not used Not used
8 Not used Not used
Table 3-5. 1000BASE-T MDI/MDI-X Pin Assignments.
Pin Number MDI port MDI-X port
1 BI_DA+ BI_DB+
2 BI_DA- BI_DB-
3 BI_DB+ BI_DA+
4 BI_DC+ BI_DD+
5 B I _D C- BI_DD-
6 BI_DB- BI_DA-
7 BI_DD+ BI _DC+
8 BI_DD- BI _ DC-
NOTE: “+” and “-” signs represent the polarity of the wires that make up each wire pair.
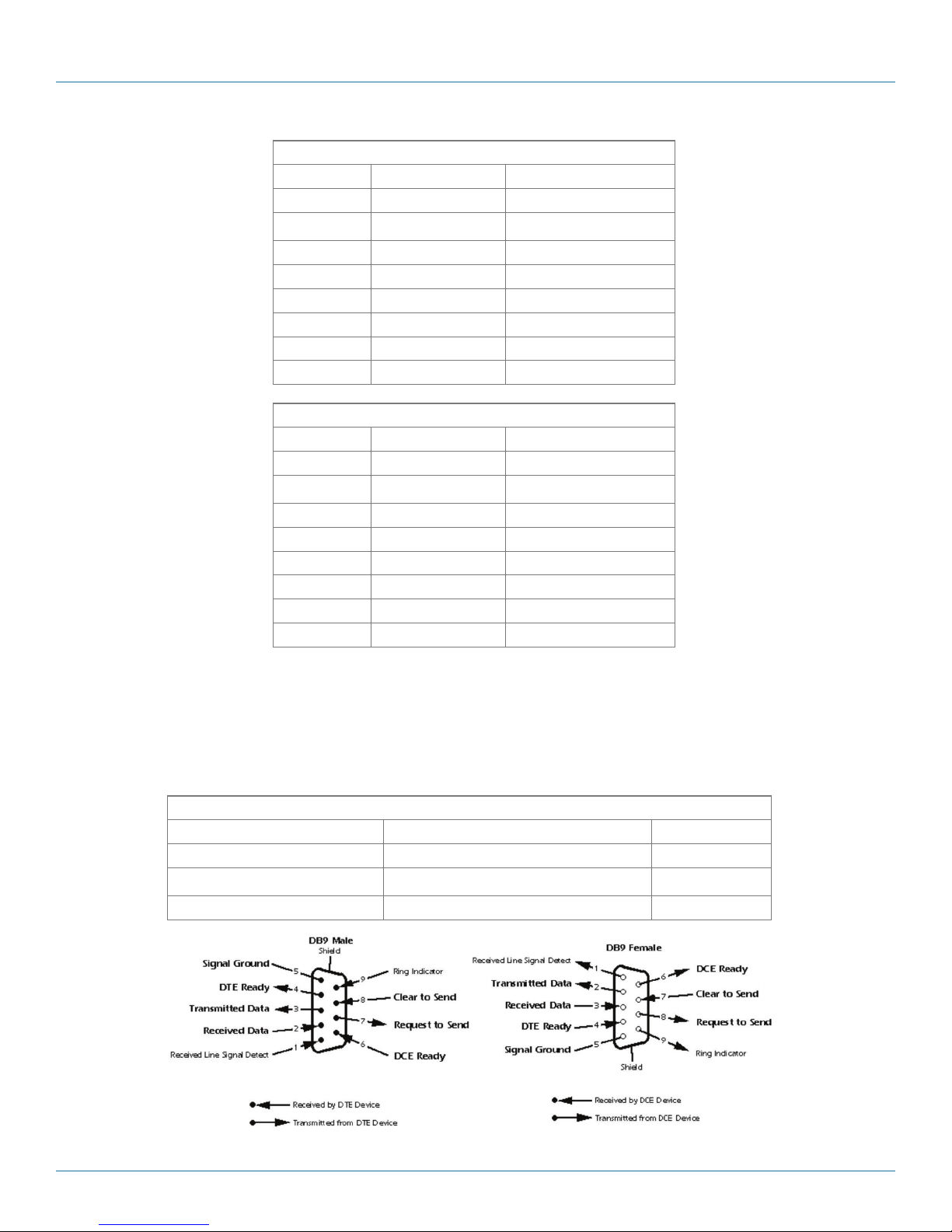
RS-232 port wiring
You can manage the LE2700 Series Switch via console ports using a RS-232 cable (included). Connect the port to a PC via the
RS-232 cable with a DB9 female connector. The DB9 female connector of the RS-232 cable should be connected to the PC while
the other end of the cable (RJ-45 connector) should be connected to the console port of the switch.
Table 3-6. RS-232 port wiring.
PC Pinout (Male) Assignment RS-232 with DB9 Female Connector DB9 to RJ-45
Pin #2 RD Pin #2 TD Pin #2
Pin #3 TD Pin #3 RD Pin #3
Pin #5 GD Pin #5 GD Pin #5
Figure 3-8. RS-232 port wiring diagram.
724-746-5500 | blackbox.com
Page 21
Chapter 3: Hardware Installation
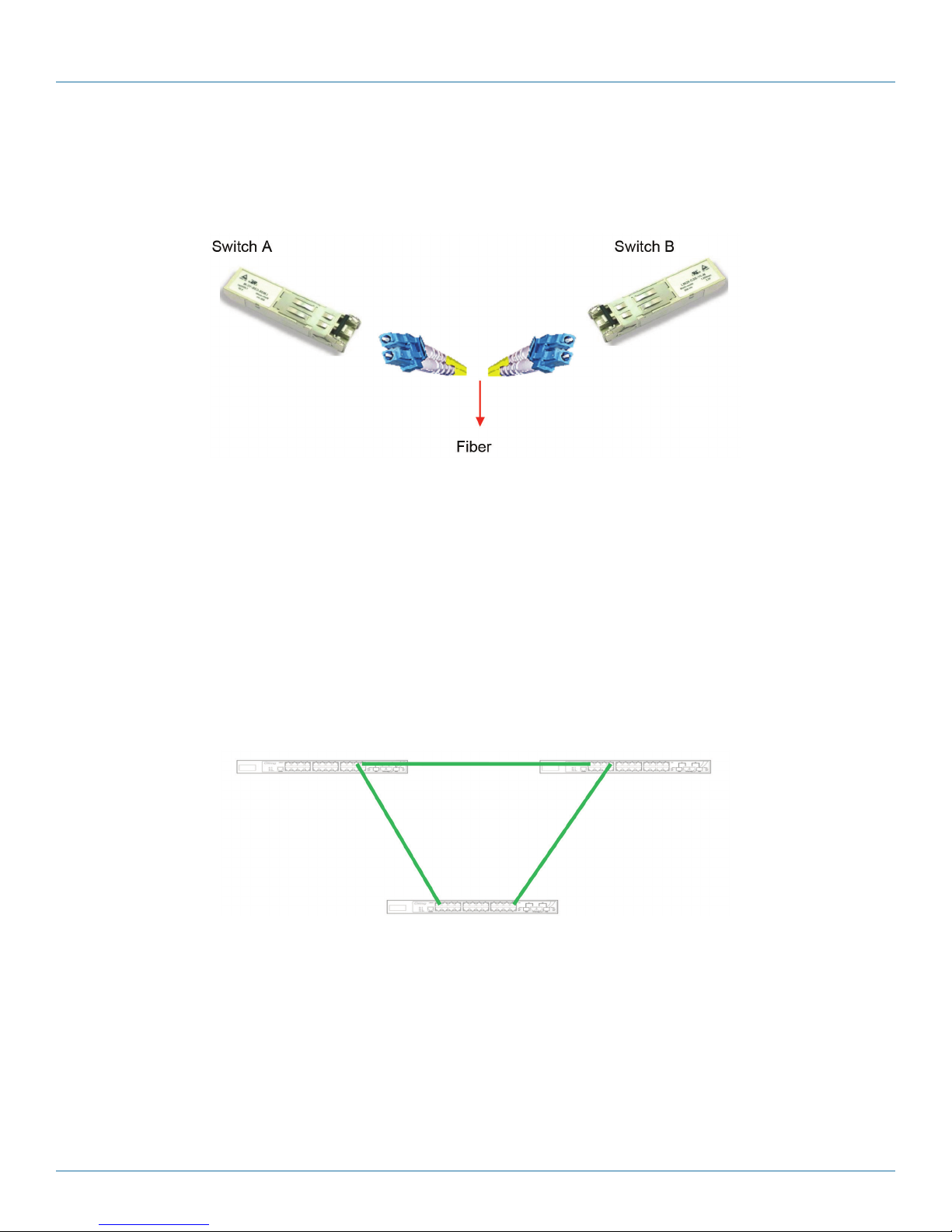
3.4.2 SFP
The switch comes with fiber optical ports that can connect to other devices using SFP modules. The fiber optical ports are in
multimode (0 to 550 m, 850 nm with 50/125-µm, 62.5/125-µm fiber) and single-mode with LC connectors. Remember to
connect the TX port of Switch A should be connected to the RX port of Switch B.
Figure 3-9. Fiber optic ports.
3.4.3 B-Ring/B-Chain
B-Ring
You can connect three or more switches to form a ring topology to gain network redundancy capabilities through the following
steps.
1. Connect each switch to form a daisychain using an Ethernet cable.
2. Set one of the connected switches to be the master and make sure the port setting of each connected switch on the
management page corresponds to the physical ports connected. For information about the port setting, please refer to
Section 4.1.2, Configuration.
3. Connect the last switch to the first switch to form a ring topology.
B-Ring
Figure 3-10. B-Ring.
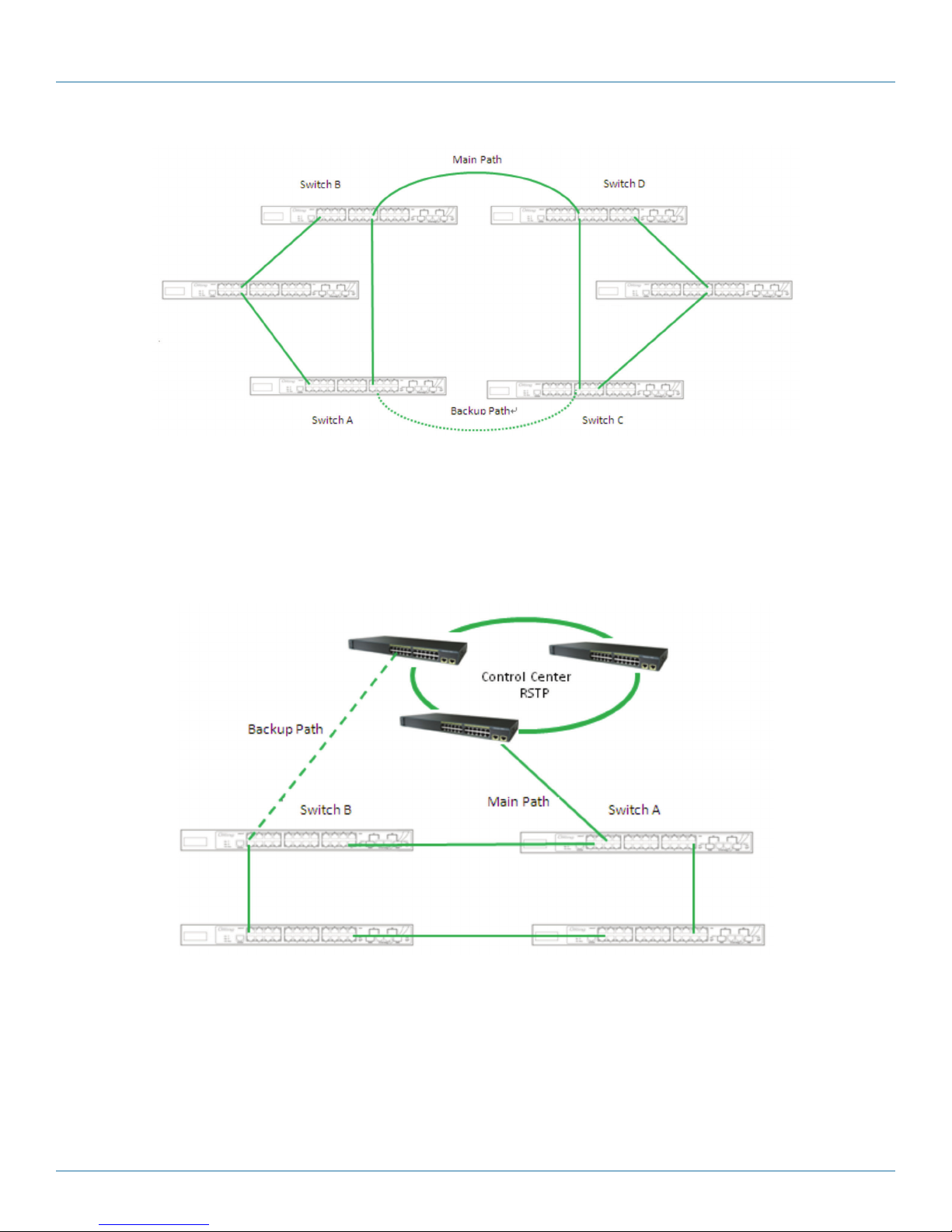
Coupling Ring
If you already have two B-Ring topologies and would like to connect the rings, you can form them into a coupling ring. All you
need to do is select two switches from each ring to be connected, for example, switch A and B from Ring 1 and switch C and D
from ring 2. Decide which port on each switch to be used as the coupling port and then link them together, for example, port 1
of switch A to port 2 of switch C and port 1 of switch B to port 2 of switch D. Then, enable Coupling Ring option by checking
the checkbox on the management page and select the coupling ring in correspondence to the connected port. For more
information on port setting, refer to Section 4.1.2, Configuration. Once the setting is completed, one of the connections will act
as the main path while the other will act as the backup path.
Page 22
724-746-5500 | blackbox.com
Chapter 3: Hardware Installation
B-Ring
Figure 3-11. Coupling ring.
Dual Homing
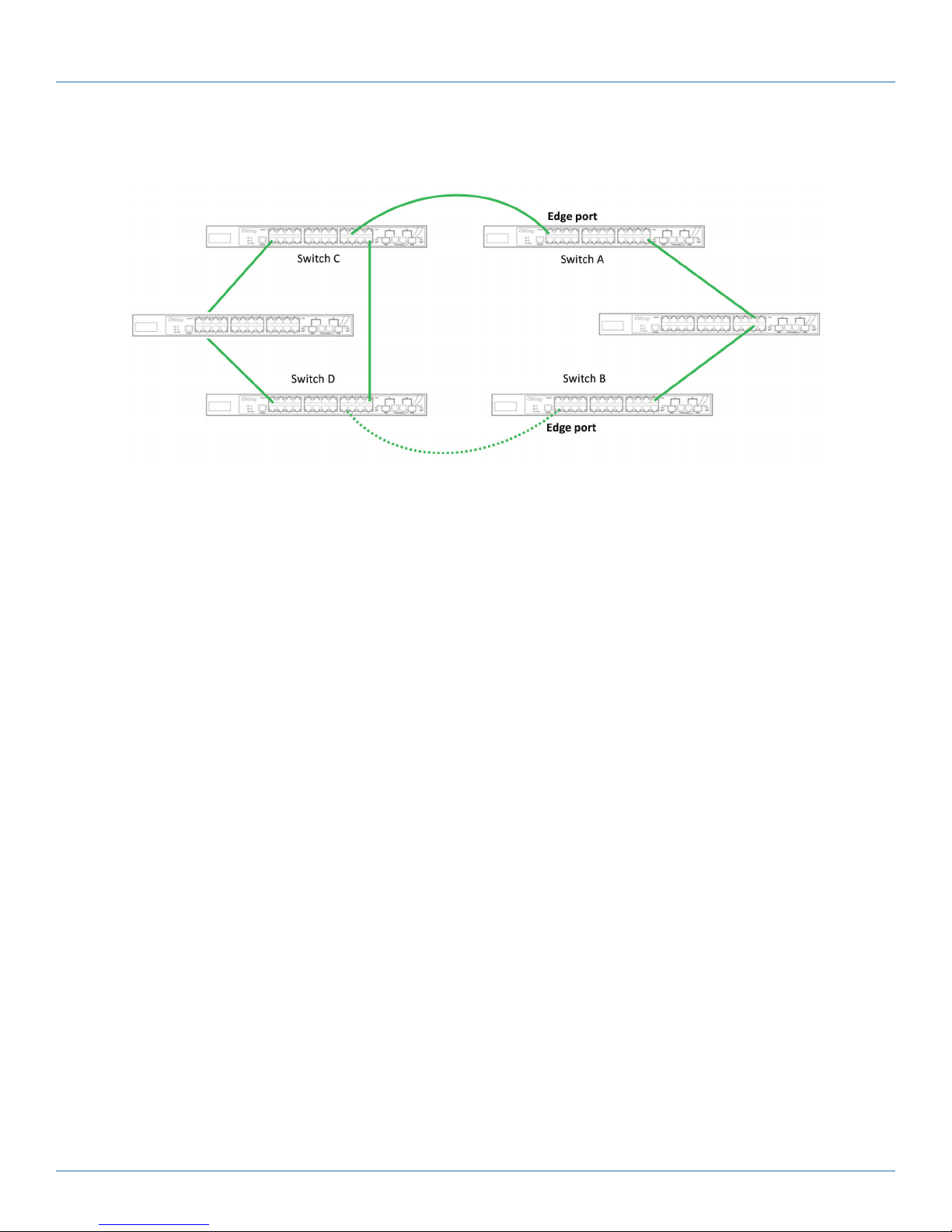
If you want to connect your ring topology to a RSTP network environment, you can use dual homing. Choose two switches
(Switch A & B) from the ring for connecting to the switches in the RSTP network (Ciscos switches). The connection of one of the
switches (Switch A or B) will act as the primary path, while the other will act as the backup path that is activated when the
primary path connection fails.
B-Ring
B-Chain
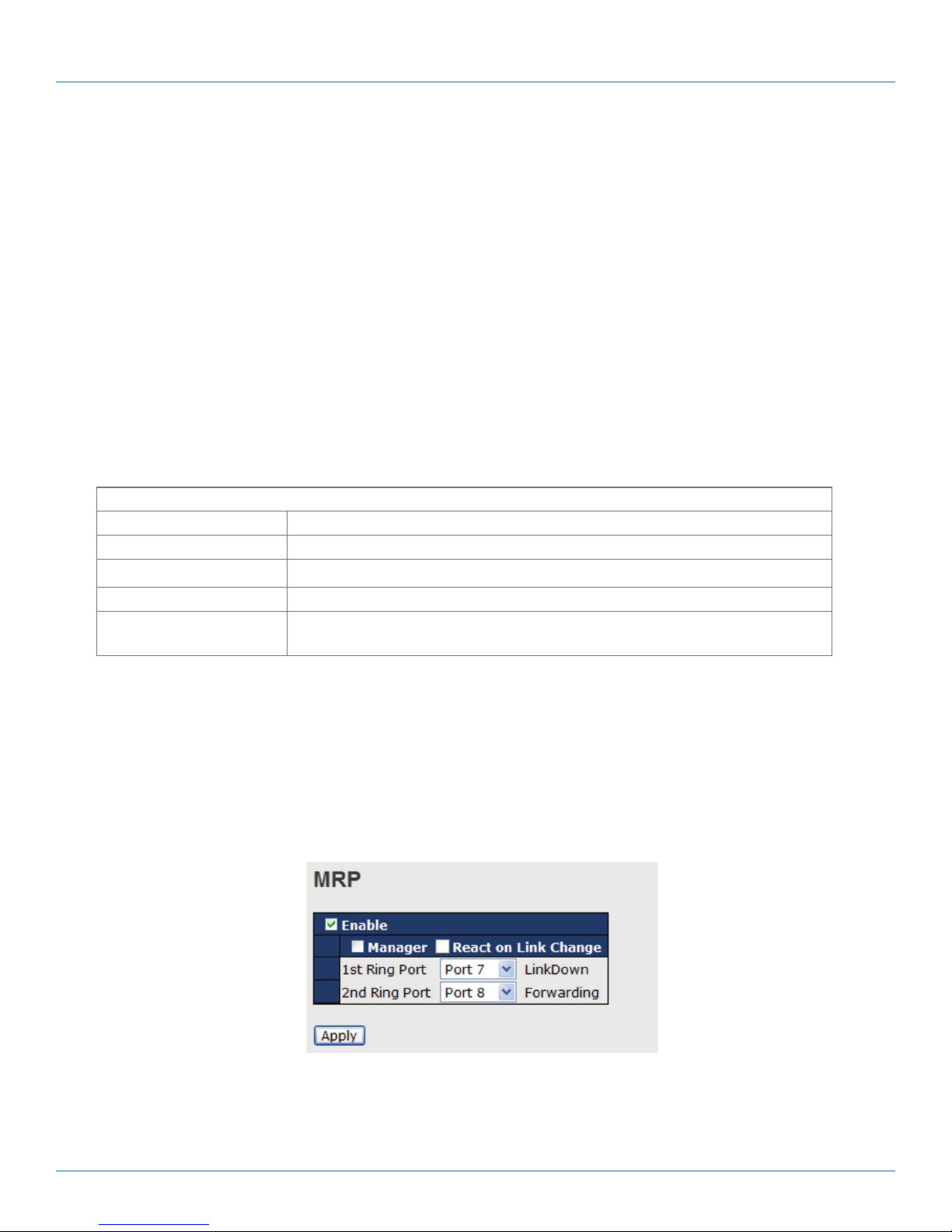
When connecting multiple B-Rings to meet your expansion demand, you can create an B-Chain topology through the following
steps.
1. Select two switches from the chain (Switch A & B) that you want to connect to the B-Ring and connect them to the switches in
the ring (Switch C & D).
2. In correspondence to the port connected to the ring, configure an edge port for both of the connected switches in the chain
by checking the box in the management page (see Section 4.1.2, Configuration).
B-Ring
Figure 3-12. Dual homing.
724-746-5500 | blackbox.com
Page 23
Chapter 3: Hardware Installation
3. Once the setting is completed, one of the connections will act as the main path, and the other as the backup path.
B-Ring
Figure 3-13. B-Chain.
Page 24
724-746-5500 | blackbox.com

Chapter 4: Redundancy
4. Redundancy
Redundancy for minimized system downtime is one of the most important concerns for industrial networking devices. Hence,
B-Ring has developed proprietary redundancy technologies including B-Ring, O-RSTP, and Open-Ring featuring faster recovery
time than existing redundancy technologies widely used in commercial applications, such as STP, RSTP, and MSTP. B-Ring’s
proprietary redundancy technologies not only support different networking topologies, but also assure the reliability of the
network.
4.1 B-Ring
4.1.1 Introduction
B-Ring is a proprietary redundant ring technology, with recovery time of less than 10 milliseconds and up to 250 nodes. The ring
protocols identify one switch as the master of the network, and then automatically block packets from traveling through any of
the network’s redundant loops. If one branch of the ring gets disconnected from the rest of the network, the protocol automatically readjusts the ring so that the part of the network that was disconnected can reestablish contact with the rest of the network. The B-Ring redundant ring technology can protect mission-critical applications from network interruptions or temporary
malfunction with its fast recover technology.
4.1.2 Configurations
B-Ring supports three ring topologies: Ring Master, Coupling Ring, and Dual Homing. You can configure the settings in the
interface below.
Table 4-1. Configuration screen components.
Label Description
Redundant Ring Check to enable B-Ring topology.
Ring Master Only one ring master is allowed in a ring. However, if more than one switch are
set to enable Ring Master, the switch with the lowest MAC address will be the
active ring master and the others will be backup masters.
1st Ring Port The primary port when the switch is ring master.
2nd Ring Port The backup port when the switch is ring master.
Coupling Ring Check to enable Coupling Ring. Coupling Ring can divide a big ring into two
smaller rings to avoid network topology changes affecting all switches. It is a good
method for connecting two rings.
Coupling Port Ports for connecting multiple rings. A coupling ring needs four switches to build
an active and a backup link.
Links formed by the coupling ports will run in active/backup mode.
Dual Homing Check to enable Dual Homing. When Dual Homing is enabled, the ring will be
connected to normal switches through two RSTP links (ex: backbone Switch). The
two links work in active/backup mode, and connect each ring to the normal
switches in RSTP mode.
Apply Click to apply the configurations.
NOTE: Do not set one switch as ring master and coupling ring at the same time, because this could cause heavy
loading.
724-746-5500 | blackbox.com
Page 25
Chapter 4: Redundancy
4.2 B-Chain
4.2.1 Introduction
B-Chain is Black Box’s revolutionary network redundancy technology which enhances network redundancy for any backbone
networks, providing ease-of-use and maximum fault-recovery swiftness, flexibility, compatibility, and cost-effectiveness in a set
of network redundancy topologies. The self-healing Ethernet technology designed for distributed and complex industrial networks
enables the network to recover in less than 10 ms for up to 250 switches if at any time a segment of the chain fails.
B-Chain allows multiple redundant rings of different redundancy protocols to join and function together as a large and the most
robust network topologies. It can create multiple redundant networks beyond the limitations of current redundant ring
technologies.
4.2.2 Configurations
B-Chain is very easy to configure and manage. Only one edge port of the edge switch needs to be defined. Other switches beside
them just need to have B-Chain enabled.
Table 4-2. B-Chain screen options.
Label Description
Enable Check to enable B-Chain function
1st Ring Port The first port connecting to the ring.
2nd Ring Port The second port connecting to the ring.
Edge Port A B-Chain topology must begin with edge ports. The ports with a smaller switch
MAC address will serve as the backup link and RM LED will light up.
4.3 MRP
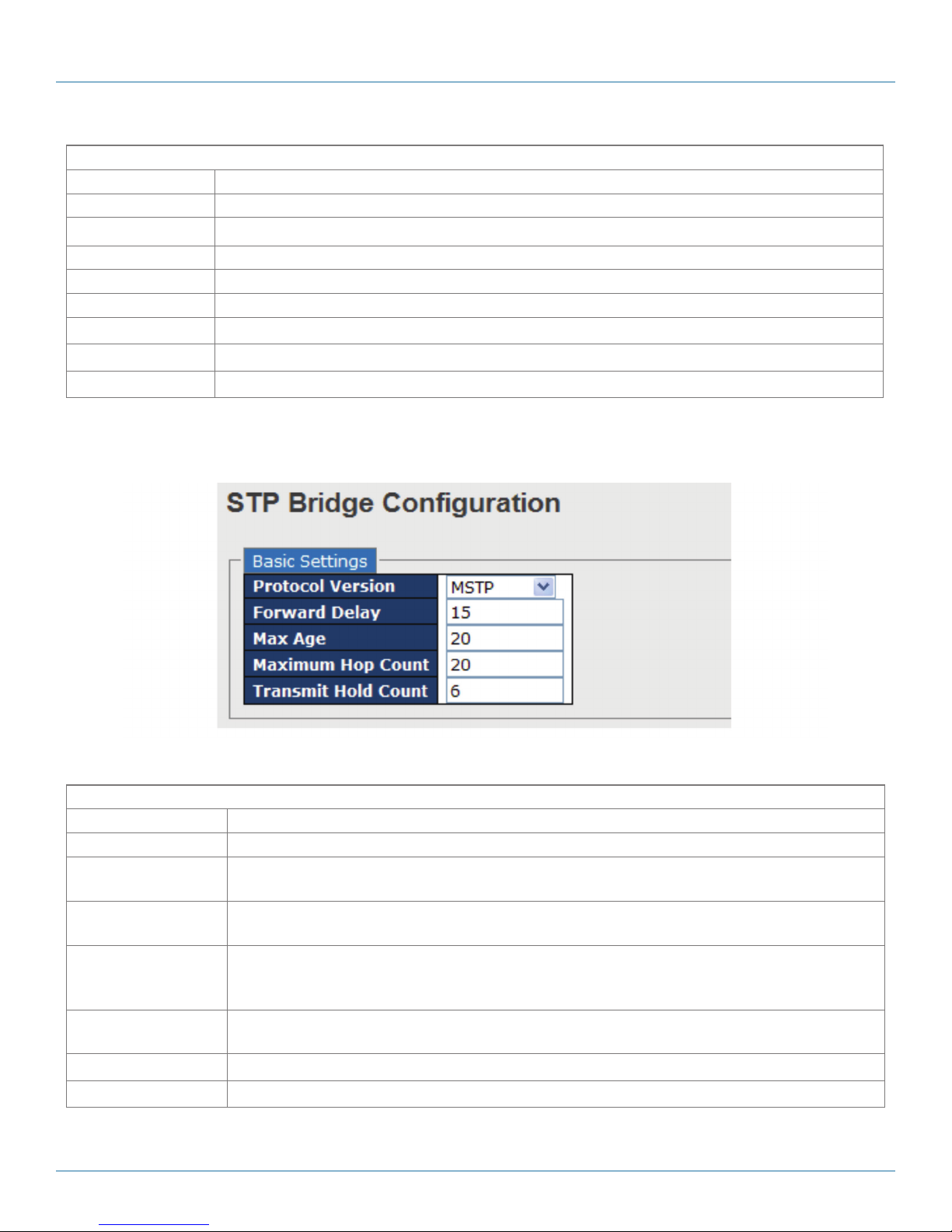
4.3.1 Introduction
MRP (Media Redundancy Protocol) is an industry standard for high-availability Ethernet networks. MRP allowing Ethernet switches
in ring configuration to recover from failure rapidly to ensure seamless data transmission. A MRP ring (IEC 62439) can support up
to 50 devices and will enable a back-up link in 80ms (adjustable to max. 200ms/500ms).
4.3.2 Configurations
Page 26
Figure 4-1. MRP screen.
724-746-5500 | blackbox.com

Chapter 4: Redundancy
Table 4-3. MRP configuration screen options.
Label Description
Enable Enables the MRP function
Manager Every MRP topology needs a MRP manager. One MRP topology can only have a
Manager. If two or more switches are set to be Manager, the MRP topology will
fail.
React on Link Change
(Advanced mode)
1st Ring Port Chooses the port which connects to the MRP ring
2nd Ring Port Chooses the port which connects to the MRP ring
4.4 STP/RSTP/MSTP
4.4.1 STP/RSTP
STP (Spanning Tree Protocol), and its advanced versions RSTP (Rapid Spanning Tree Protocol) and MSTP (Multiple Spanning Tree
Protocol), are designed to prevent network loops and provide network redundancy. Network loops occur frequently in large networks as when two or more paths run to the same destination, broadcast packets may get in to an infinite loop and hence causing congestion in the network. STP can identify the best path to the destination, and block all other paths. The blocked links will
stay connected but inactive. When the best path fails, the blocked links will be activated. Compared to STP which recovers a link
in 30 to 50 seconds, RSTP can shorten the time to 5 to 6 seconds.
Faster mode. Enabling this function will cause MRP topology to converge more
rapidly. This function only can be set in MRP manager switch.
STP Bridge Status
This page shows the status for all STP bridge instances.
Figure 4-2. STP bridge screen.
Table 4-4. STP bridge screen options.
Label Description
MSTI The bridge instance. You can also link to the STP detailed bridge status.
Bridge ID The bridge ID of this bridge instance.
Root ID The bridge ID of the currently selected root bridge.
Root Port The switch port currently assigned the root port role.
Root Cost Root path cost. For a root bridge, this is zero. For other bridges, it is the sum of
port path costs on the least cost path to the Root Bridge.
Topology Flag The current state of the Topology Change Flag for the bridge instance.
Topology Change Last The time since last Topology Change occurred.
Refresh Click to refresh the page immediately.
Auto-refresh Check this box to enable an automatic refresh of the page at regular intervals.
724-746-5500 | blackbox.com
Page 27

Chapter 4: Redundancy
STP Port Status
This page displays the STP port status for the currently selected switch.
Figure 4-3. STP Port Status screen.
Table 4-5. STP Port Status screen options.
Label Description
Port The switch port number to which the following settings will be applied.
CIST Role The current STP port role of the CIST port. The values include: AlternatePort, BackupPort, RootPort,
and DesignatedPort.
State The current STP port state of the CIST port. The values include: Blocking, Learning, and Forwarding.
Uptime The time since the bridge port is last initialized.
Refresh Click to refresh the page immediately.
Auto-refresh Check this box to enable an automatic refresh of the page at regular intervals.
STP Statistics
This page displays the STP port statistics for the currently selected switch.
Page 28
Figure 4-4. STP statistics screen.
724-746-5500 | blackbox.com
Chapter 4: Redundancy
Table 4-6. STP statistics screen options.
Label Description
Port The switch port number to which the following settings will be applied.
RSTP The number of RSTP configuration BPDUs received/transmitted on the port.
STP The number of legacy STP configuration BPDUs received/transmitted on the port.
TCN The number of (legacy) topology change notification BPDUs received/transmitted on the port.
Discarded Unknown The number of unknown spanning tree BPDUs received (and discarded) on the port.
Discarded Illegal The number of illegal spanning tree BPDUs received (and discarded) on the port.
Refresh Click to refresh the page immediately.
Auto-refresh Check to enable an automatic refresh of the page at regular intervals.
STP Bridge Configurations
Table 4-7. STP Bridge Configuration screen options.
Label Description
Protocol Version The version of the STP protocol. Valid values include STP, RSTP, and MSTP.
Forward Delay The delay used by STP bridges to transit root and designated ports to forwarding (used in STP
compatible mode). The range of valid values is 4 to 30 seconds.
Max Age The maximum time the information transmitted by the root bridge is considered valid. The range of
valid values is 6 to 40 seconds, and Max Age must be <= (FwdDelay-1)*2.
Maximum Hop Count This defines the initial value of remaining hops for MSTI information generated at the boundary of
an MSTI region. It defines how many bridges a root bridge can distribute its BPDU information to.
The range of valid values is 4 to 30 seconds, and MaxAge must be <= (FwdDelay-1)*2.
Transmit Hold Count The number of BPDUs a bridge port can send per second. When exceeded, transmission of the next
BPDU will be delayed. The range of valid values is 1 to 10 BPDUs per second.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
Figure 4-5. STP Bridge Configuration screen.
724-746-5500 | blackbox.com
Page 29
Chapter 4: Redundancy
4.4.2 MSTP
Since the recovery time of STP and RSTP takes seconds, which are unacceptable in some industrial applications, MSTP was developed. The technology supports multiple spanning trees within a network by grouping and mapping multiple VLANs into different
spanning-tree instances, known as MSTIs, to form individual MST regions. Each switch is assigned to an MST region. Hence, each
MST region consists of one or more MSTP switches with the same VLANs, at least one MST instance, and the same MST region
name. Therefore, switches can use different paths in the network to effectively balance loads.
Port Settings
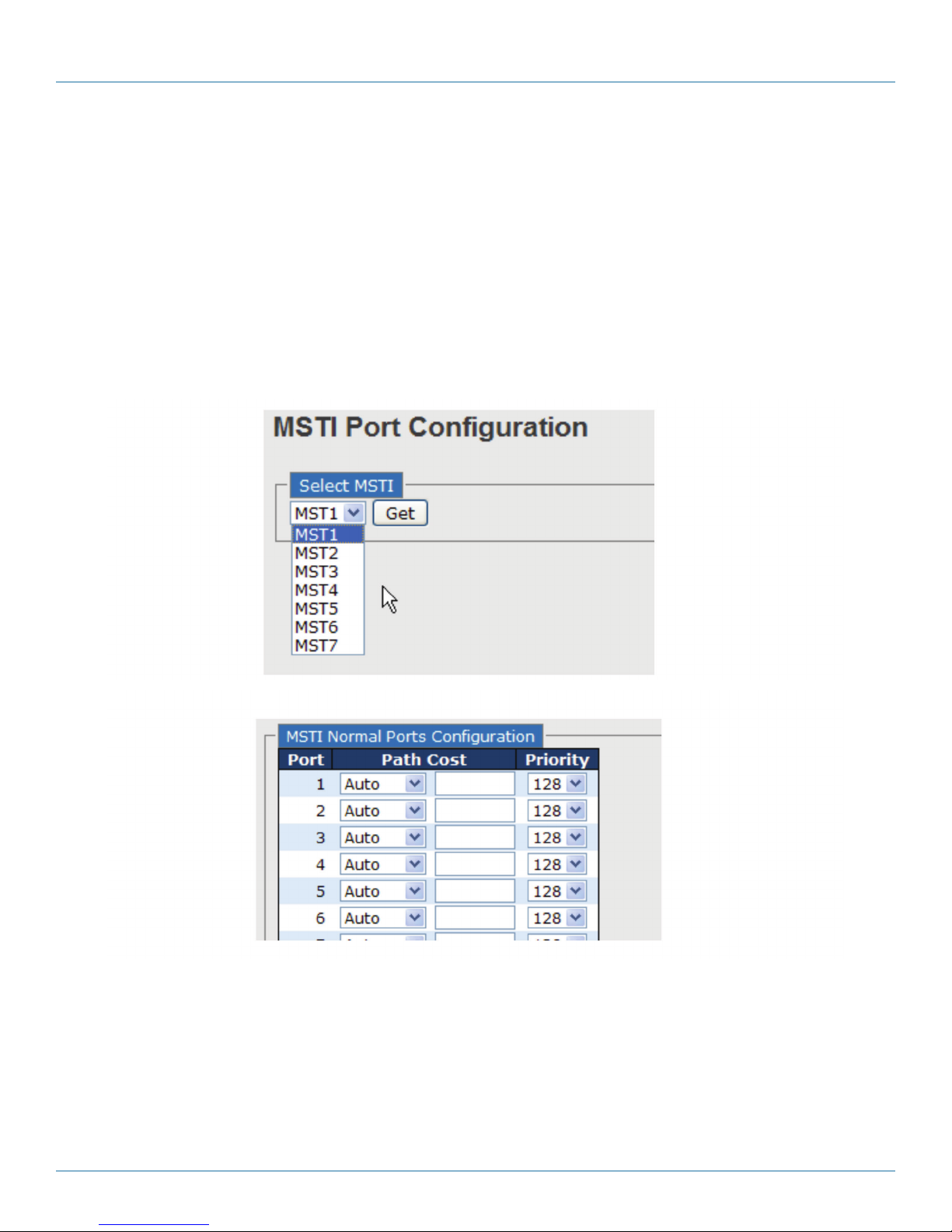
This page allows you to examine and change the configurations of current MSTI ports. A MSTI port is a virtual port, which is
instantiated separately for each active CIST (physical) port for each MSTI instance configured and applicable for the port. The MSTI
instance must be selected before MSTI port configuration options are displayed.
This page contains MSTI port settings for physical and aggregated ports. The aggregation settings are stack global.
Page 30
Figure 4-6. MSTI Port Configuration screens.
724-746-5500 | blackbox.com

Chapter 4: Redundancy
Table 4-8. MSTI Port Configuration screen options.
Label Description
Port The switch port number of the corresponding STP CIST (and MSTI) port.
Path Cost Configures the path cost incurred by the port. Auto will set the path cost according to the physical
link speed by using the 802.1D-recommended values. Specific allows you to enter a user-defined
value. The path cost is used when establishing an active topology for the network. Lower path cost
ports are chosen as forwarding ports in favor of higher path cost ports. The range of valid values is 1
to 200000000.
Priority Configures the priority for ports having identical port costs. (See above).
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
Mapping
This page allows you to examine and change the configurations of current STP MSTI bridge instance.
Figure 4-7. MSTI Configuration screen.
724-746-5500 | blackbox.com
Page 31

Chapter 4: Redundancy
Table 4-9. MSTI Configuration screen options.
Label Description
Configuration Name The name which identifies the VLAN to MSTI mapping. Bridges must share the name and revision
(see below), as well as the VLAN-to-MSTI mapping configurations in order to share spanning trees for
MSTIs (intra-region). The name should not exceed 32 characters.
Configuration
Revision
MSTI The bridge instance. The CIST is not available for explicit mapping, as it will receive the VLANs not
VLANS Mapped The list of VLANs mapped to the MSTI. The VLANs must be separated with commas and/or space. A
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
Priority
Revision of the MSTI configuration named above. This must be an integer between 0 and 65535.
explicitly mapped.
VLAN can only be mapped to one MSTI. An unused MSTI will be left empty (ex. without any mapped
VLANs).
This page allows you to examine and change the configurations of current STP MSTI bridge instance priority.
Figure 4-8. MSTI configuration screen.
Label Description
MSTI The bridge instance. CIST is the default instance, which is always active.
Priority Indicates bridge priority. The lower the value, the higher the priority. The bridge priority, MSTI
instance number, and the 6-byte MAC address of the switch forms a bridge identifier.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
Page 32
Table 4-10. MSTI configuration screen options.
724-746-5500 | blackbox.com

Chapter 4: Redundancy
4.4.3 CIST
With the ability to cross regional boundaries, CIST is used by MSTP to communicate with other MSTP regions and with any RSTP
and STP single-instance spanning trees in the network. Any boundary port, that is, if it is connected to another region, will automatically belongs solely to CIST, even if it is assigned to an MSTI. All VLANs that are not members of particular MSTIs are members of the CIST.
Port Settings
Figure 4-9. Port settings screen.
Table 4-11. Port Settings screen options.
Label Description
Port The switch port number to which the following settings will be applied.
STP Enabled Check to enable STP for the port.
Path Cost Configures the path cost incurred by the port. Auto will set the path cost according to the physical
link speed by using the 802.1D-recommended values. Specific allows you to enter a user-defined
value. The path cost is used when establishing an active topology for the network. Lower path cost
ports are chosen as forwarding ports in favor of higher path cost ports. The range of valid values is 1
to 200000000.
Priority Configures the priority for ports having identical port costs. (See above).
OpenEdge (setate
flag)
AdminEdge Configures the operEdge flag to start as set or cleared.(the initial operEdge state when a port is
AutoEdge Check to enable the bridge to detect edges at the bridge port automatically. This allows operEdge to
Restricted Role When enabled, the port will not be selected as root port for CIST or any MSTI, even if it has the best
A flag indicating whether the port is connected directly to edge devices or not (no bridges attached).
Transiting to the forwarding state is faster for edge ports (operEdge set to true) than other ports.
initialized).
be derived from whether BPDUs are received on the port or not.
spanning tree priority vector. Such a port will be selected as an alternate port after the root port has
been selected. If set, spanning trees will lose connectivity. It can be set by a network administrator to
prevent bridges outside a core region of the network from influencing the active spanning tree topology because those bridges are not under the full control of the administrator. This feature is also
known as Root Guard.
724-746-5500 | blackbox.com
Page 33

Chapter 4: Redundancy
Table 4-11 (continued). Port Settings screen options.
Label Description
Restricted TCN When enabled, the port will not propagate received topology change notifications and topology changes to
other ports. If set, it will cause temporary disconnection after changes in an active spanning trees topology as
a result of persistent incorrectly learned station location information. It is set by a network administrator to
prevent bridges outside a core region of the network from causing address flushing in that region because
those bridges are not under the full control of the administrator or is the physical link state for the attached
LANs transitions frequently.
Point2Point Configures whether the port connects to a point-to-point LAN rather than a shared medium. This can be
configured automatically or set to true or false manually. Transiting to forwarding state is faster for point-topoint LANs than for shared media.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
4.5 Fast Recovery
Fast recovery mode can be set to connect multiple ports to one or more switches. IGPS-9084GP with fast recovery mode will provide redundant links. Fast recovery mode supports 12 priorities. Only the first priority will be the active port, and the other ports
with different priorities will be backup ports.
Label Description
Active Activates fast recovery mode.
port Ports can be set to 12 priorities. Only the port with the highest priority will be the active port. 1st Priority is
the highest.
Apply Click to activate the configurations.
Page 34
Figure 4-10. Fast Recovery screen.
Table 4-12. Fast Recovery screen options.
724-746-5500 | blackbox.com

Chapter 5: Management
5. Management
The switch can be controlled via a built-in Web server that supports Internet Explorer (Internet Explorer 5.0 or above versions) and
other Web browsers such as Chrome. Therefore, you can manage and configure the switch easily and remotely. You can also
upgrade firmware via a Web browser. The Web management function not only reduces network bandwidth consumption, but
also enhances access speed and provides a user-friendly viewing screen.
NOTE: By default, IE5.0 or later version do not allow Java applets to open sockets. You need to modify the browser setting sepa-
rately in order to enable Java applets for network ports.
Preparing for Web Management
You can access the management page of the switch via the following default values:
IP Addr e s s : 192.16 8 .10.1
Subnet Mask: 255.255.255.0
Default Gateway: 192.168.10.254
User Name: admin
Password: admin
System Login
1. Launch Internet Explorer.
2. Type http:// and the IP address of the switch. Press Enter.
Figure 5-1. System login.
3. A login screen appears.
4. Type in the username and password. The default username and password is admin.
5. Click Enter or OK button, the management Web page appears.
After logging in, you can see the information of the switch as shown in the next screen.
Figure 5-2. Login screen.
724-746-5500 | blackbox.com
Page 35

Chapter 5: Management
Figure 5-3. System information.
On the right-hand side of the management interface shows links to various settings. You can click on the links to access the configuration pages of different functions.
5.1 Basic Settings
Basic Settings allow you to configure the basic functions of the switch.
5.1.1 Sy s tem Information
This page shows the general information of the switch.
Figure 5-4. System information configuration.
Table 5-1. System information configuration screen options.
Label Description
System Name An administratively assigned name for the managed node. By convention, this is the node's fully-qualified
domain name. A domain name is a text string consisting of alphabets (A-Z, a-z), digits (0-9), and minus
sign (-). Space is not allowed to be part of the name. The first character must be an alpha character. And
the first or last character must not be a minus sign. The allowed string length is 0 to 255.
System Description Description of the device.
System Location The physical location of the node (e.g., telephone closet, 3rd floor). The allowed string length is 0 to 255,
and only ASCII characters from 32 to 126 are allowed.
Page 36
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-1 (continued). System information configuration screen options.
Label Description
System Contact The textual identification of the contact person for this managed node, together with information on how
to contact this person. The allowed string length is 0 to 255, and only ASCII characters from 32 to 126 are
allowed.
System Timezone
offset (minutes)
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
5.1.2 Admin & Password
This page allows you to configure the system password required to access the web pages or log in from CLI.
Provides the time-zone offset from UTC/GMT.
The offset is given in minutes east of GMT. The valid range is from -720 to 720 minutes.
Figure 5-5. System Password screen.
Table 5-2. System Password screen options.
Label Description
Old Password The existing password. If this is incorrect, you cannot set the new password.
New Password The new system password. The allowed string length is 0 to 31, and only ASCII characters from 32 to 126
are allowed.
Confirm New
Password
Save Click to save changes.
Re-type the new password.
5.1.3 Authentication
This page allows you to configure how a user is authenticated when he/she logs into the switch via one of the management
interfaces.
Figure 5-6. Authentication Method Configuration screen.
724-746-5500 | blackbox.com
Page 37

Chapter 5: Management
Table 5-3. Authentication Method Configuration screen options.
Label Description
Client The management client for which the configuration below applies.
Authentication
Method
Fallback Check to enable fallback to local authentication.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
5.1.4 IP Settings
You can configure IP information of the switch in this page.
Authentication Method can be set to one of the following values:
None: authentication is disabled and login is not possible.
Local: local user database on the switch is used for authentication.
Radius: a remote RADIUS server is used for authentication.
If none of the configured authentication servers are active, the local user database is used for
authentication. This is only possible if Authentication Method is set to a value other than none or local.
Figure 5-7. IP Configuration screen.
Table 5-4. IP Configuration screen options.
Label Description
DHCP Client Enable the DHCP client by checking this box. If DHCP fails or the configured IP address is zero, DHCP will
retry. If DHCP retry fails, DHCP will stop trying and the configured IP settings will be used.
IP Address Assigns the IP address of the network in use. If DHCP client function is enabled, you do not need to assign
the IP address. The network DHCP server will assign the IP address to the switch and it will be displayed in
this column. The default IP is 192.168.10.1.
IP Mask Assigns the subnet mask of the IP address. If DHCP client function is enabled, you do not need to assign
the subnet mask.
IP Router Assigns the network gateway for the switch. The default gateway is 192.168.10.254.
VLAN ID Provides the managed VLAN ID. The allowed range is 1 through 4095.
DNS Server Provides the IP address of the DNS server in dotted decimal notation.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
Page 38
724-746-5500 | blackbox.com

Chapter 5: Management
5.1.5 IPv6 Settings
You can configure IPv6 information of the switch on the following page.
Figure 5-8. IPv6 Configuration screen.
Table 5-5. IPv6 Configuration screen options.
Label Description
Auto Configuration Check to enable IPv6 auto-configuration. If the system cannot obtain the stateless address in time, the
configured IPv6 settings will be used. The router may delay responding to a router solicitation for a few
seconds; therefore, the total time needed to complete auto-configuration may be much longer.
Address Provides the IPv6 address of the switch. IPv6 address consists of 128 bits represented as eight groups of
four hexadecimal digits with a colon separating each field (:). For example, in 'fe80::215:c5ff:fe03:4dc7',
the symbol '::' is a special syntax that can be used as a shorthand way of representing multiple 16-bit
groups of contiguous zeros; but it can appear only once. It can also represent a legally valid IPv4 address.
For example, “::192.1.2.34”.
Prefix Provides the IPv6 prefix of the switch. The allowed range is 1 to 128.
Router Provides the IPv6 address of the switch. IPv6 address consists of 128 bits represented as eight groups of
four hexadecimal digits with a colon separating each field (:). For example, in 'fe80::215:c5ff:fe03:4dc7',
the symbol '::' is a special syntax that can be used as a shorthand way of representing multiple 16-bit
groups of contiguous zeros; but it can appear only once. It can also represent a legally valid IPv4 address.
For example, “::192.1.2.34”.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
5.1.6 HTTPS
You can configure the HTTPS mode in the following page.
Figure 5-9. HTTPS Configuration screen.
724-746-5500 | blackbox.com
Page 39

Chapter 5: Management
Table 5-6. HTTPS Configuration options.
Label Description
Mode Indicates the selected HTTPS mode. When the current connection is HTTPS, disabling HTTPS will automati-
cally redirect web browser to an HTTP connection. The modes include:
Enabled: enable HTTPS.
Disabled: disable HTTPS.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
5.1.7 SSH
You can configure the SSH mode in the following page.
Figure 5-10. SSH Configuration screen.
Table 5-7. SSH Configuration screen options.
Label Description
Mode Indicates the selected SSH mode. The modes include:
Enabled: enable SSH.
Disabled: disable SSH.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
5.1.8 LLDP
LLDP Configurations
This page allows you to examine and configure current LLDP port settings.
Page 40
Figure 5-11. LLDP Configurations.
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-8. LLDP Configuration screen options.
Label Description
Port The switch port number to which the following settings will be applied.
Mode Indicates the selected LLDP mode.
Rx only: the switch will not send out LLDP information, but LLDP information from its neighbors will be analyzed.
Tx only: the switch will drop LLDP information received from its neighbors, but will send out LLDP information.
Disabled: the switch will not send out LLDP information, and will drop LLDP information received from its neighbors.
Enabled: the switch will send out LLDP information, and will analyze LLDP information received from its neighbors.
LLDP Neighbor Information
This page provides a status overview for all LLDP neighbors. The following table contains information for each port on which an
LLDP neighbor is detected. The columns include the following information:
Figure 5-12. LLDP Neighbor Information screen.
Table 5-9. LLDP Neighbor Information screen options.
Label Description
Local Port The port that you use to transmits and receives LLDP frames.
Chassis ID The identification number of the neighbor sending out the LLDP frames.
Remote Port ID The identification of the neighbor port.
System Name The name advertised by the neighbor.
Port Description The description of the port advertised by the neighbor.
System
Capabilities
Management
Address
Refresh Click to refresh the page immediately.
Description of the neighbor's capabilities. The capabilities include:
1. Other
2. Repeater
3. Bridge
4. WLAN Access Point
5. Router
6. Telephone
7. DOCSIS Cable Device
8. Station Only
9. Reserved
When a capability is enabled, a (+) will be displayed. If the capability is disabled, a (-) will be displayed.
The neighbor's address that can be used to help network management. This may contain the neighbor's IP
address.
Auto-Refresh Check to enable an automatic refresh of the page at regular intervals.
724-746-5500 | blackbox.com
Page 41

Chapter 5: Management
Port Statistics
This page provides an overview of all LLDP traffic. Two types of counters are shown. Global counters will apply settings to the
whole switch stack, while local counters will apply settings to specified switches.
Figure 5-13. Port Statistics screen.
Global Counters
Table 5-10. Global Counters options.
Label Description
Neighbor entries were last changed at Shows the time when the last entry was deleted or added.
Total Neighbors Entries Added Shows the number of new entries added since switch reboot.
Total Neighbors Entries Deleted Shows the number of new entries deleted since switch reboot.
Total Neighbors Entries Dropped Shows the number of LLDP frames dropped due to full entry table.
Total Neighbors Entries Aged Out Shows the number of entries deleted due to expired time-to-live.
Table 5-11. Local Counters options.
Label Description
Local Port The port that receives or transmits LLDP frames.
Tx Frames The number of LLDP frames transmitted on the port.
Rx Frames The number of LLDP frames received on the port.
Rx Errors The number of received LLDP frames containing errors.
Frames Discarded If a port receives an LLDP frame, and the switch's internal table is full, the LLDP frame
will be counted and discarded. This situation is known as "too many neighbors" in the
LLDP standard. LLDP frames require a new entry in the table if Chassis ID or Remote
Port ID is not included in the table. Entries are removed from the table when a given
port links down, an LLDP shutdown frame is received, or when the entry ages out.
TLVs Discarded Each LLDP frame can contain multiple pieces of information, known as TLVs (Type
Length Value). If a TLV is malformed, it will be counted and discarded.
TLVs Unrecognized The number of well-formed TLVs, but with an unknown type value.
Org. Discarded The number of organizationally TLVs received.
Page 42
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-11 (continued). Local Counters options.
Label Description
Age-Outs Each LLDP frame contains information about how long the LLDP information is valid
(age-out time). If no new LLDP frame is received during the age-out time, the LLDP
information will be removed, and the value of the age-out counter will be incremented.
Refresh Click to refresh the page immediately.
Clear Click to clear the local counters. All counters (including global counters) are cleared
upon reboot.
Auto-refresh Check to enable an automatic refresh of the page at regular intervals.
5.1.9 Modbus TCP
This page shows Modbus TCP support of the switch. (For more information regarding Modbus, please visit http://www.modbus.
org/)
Figure 5-14. Modbus configuration screen.
Table 5-12. Modbus TCP support.
Label Description
Mode Shows the existing status of the Modbus TCP function.
5.1.10 Backup/Restore Configurations
You can save/view or load switch configurations. The configuration file is in XML format.
Figure 5 -15.
724-746-5500 | blackbox.com
Page 43

Chapter 5: Management
5.1.11 Firmware Update
This page allows you to update the firmware of the switch.
Figure 5-16. Firmware Update screen.
5.2 DHCP Server
The switch provides DHCP server functions. By enabling DHCP, the switch will become a DHCP server and dynamically assigns IP
addresses and related IP information to network clients.
5.2.1 Basic Settings
This page allows you to set up DHCP settings for the switch. You can check the Enabled checkbox to activate the function. Once
the box is checked, you will be able to input information in each column.
5.2.2 Dynamic Client List
When DHCP server functions are activated, the switch will collect DHCP client information and display in the following table.
5.2.3 Client List
You can assign a specific IP address within the dynamic IP range to a specific port. When a device is connected to the port and
requests for dynamic IP assigning, the switch will assign the IP address that has previously been assigned to the connected device.
Page 44
Figure 5-17. DHCP Server Configuration screen.
Figure 5-18. DHCP Dynamic Client List.
724-746-5500 | blackbox.com

Chapter 5: Management
Figure 5-19. DHCP Client Lists screen.
5.2.4 Relay Agent
DHCP relay is used to forward and transfer DHCP messages between the clients and the server when they are not in the same
subnet domain. You can configure the function in this page.
Figure 5-20. DHCP Relay Configuration screen.
Table 5-13. DHCP Relay Configuration screen options.
Label Description
Relay Mode Indicates the existing DHCP relay mode. The modes include:
Enabled: activate DHCP relay. When DHCP relay is enabled, the agent forwards and transfers DHCP
messages between the clients and the server when they are not in the same subnet domain to prevent the
DHCP broadcast message from flooding for security considerations.
Disabled: disable DHCP relay
Relay Server Indicates the DHCP relay server IP address. A DHCP relay agent is used to forward and transfer DHCP mes-
sages between the clients and the server when they are not in the same subnet domain.
Relay
Information
Mode
Indicates the existing DHCP relay information mode. The format of DHCP option 82 circuit ID format is
"[vlan_id][module_id][port_no]". The first four characters represent the VLAN ID, and the fifth and sixth
characters are the module ID. In stand-alone devices, the module ID always equals to 0; in stacked devices, it
means switch ID. The last two characters are the port number. For example, "00030108" means the DHCP
message received form VLAN ID 3, switch ID 1, and port No. 8. The option 82 remote ID value equals to the
switch MAC address.
The modes include: Enabled: activate DHCP relay information. When DHCP relay information is enabled, the
agent inserts specific information (option 82) into a DHCP message when forwarding to a DHCP server and
removes it from a DHCP message when transferring to a DHCP client. It only works when DHCP relay mode
is enabled.
Disabled: disable DHCP relay information
724-746-5500 | blackbox.com
Page 45

Chapter 5: Management
Table 5-13 (continued). DHCP Relay Configuration screen options.
Label Description
Relay Information
Policy
The relay statistics show the information of relayed packets of the switch.
Indicates the policies to be enforced when receiving DHCP relay information. When DHCP relay information
mode is enabled, if the agent receives a DHCP message that already contains relay agent information, it will
enforce the policy. The Replace option is invalid when relay information mode is disabled. The policies
includes:
Replace: replace the original relay information when a DHCP message containing the information is received.
Keep: keep the original relay information when a DHCP message containing the information is received.
Drop: drop the package when a DHCP message containing the information is received.
Figure 5-21. DHCP Relay Statistics.
Table 5-14. DHCP Relay Statistics screen options.
Label Description
Transmit to Server The number of packets relayed from the client to the server.
Transmit Error The number of packets with errors when being sent to clients.
Receive from Server The number of packets received from the server.
Receive Missing Agent Option The number of packets received without agent information.
Receive Missing Circuit ID The number of packets received with Circuit ID.
Receive Missing Remote ID The number of packets received with the Remote ID option missing.
Receive Bad Circuit ID The number of packets whose Circuit ID do not match the known circuit ID.
Receive Bad Remote ID The number of packets whose Remote ID do not match the known Remote ID.
Figure 5-22. Client Statistics screen.
Page 46
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-15. Client Statistics screen options.
Label Description
Transmit to Client The number of packets relayed from the server to the client.
Transmit Error The number of packets with errors when being sent to servers.
Receive from Client The number of packets received from the server.
Receive Agent Option The number of received packets containing relay agent information.
Replace Agent Option The number of packets replaced when received messages contain relay agent information.
Keep Agent Option The number of packets whose relay agent information is retained.
Drop Agent Option The number of packets dropped when received messages contain relay agent information.
5.3 Port Setting
Port Setting allows you to manage individual ports of the switch, including traffic, power, and trunks.
5.3.1 Port Control
This page shows current port configurations. Ports can also be configured here.
Label Description
Port The switch port number to which the following settings will be applied.
Link The current link state is shown by different colors. Green indicates the link is up and red
means the link is down.
Current Link Speed Indicates the current link speed of the port.
Configured Link Speed The drop-down list provides available link speed options for a given switch port.
Auto selects the highest speed supported by the link partner.
Disabled disables switch port configuration.
<> configures all ports.
Figure 5-23. Port Configuration screen.
Table 5-16. Port Configuration screen options.
724-746-5500 | blackbox.com
Page 47

Chapter 5: Management
Table 5-16 (continued). Port Configuration screen options.
Label Description
Flow Control When Auto is selected for the speed, the flow control will be negotiated to the capacity advertised by
the link partner.
When a fixed-speed setting is selected, that is what is used. Current Rx indicates whether pause frames
on the port are obeyed, and Current Tx indicates whether pause frames on the port are transmitted. The
Rx and Tx settings are determined by the result of the last auto-negotiation.
You can check the Configured column to use flow control. This setting is related to the setting of
Configured Link Speed.
Maximum Frame You can enter the maximum frame size allowed for the switch port in this column, including FCS. The
allowed range is 1518 bytes to 9600 bytes.
Power Control Shows the current power consumption of each port in percentage. The Configured column allows you to
change power saving parameters for each port.
Disabled: all power savings functions are disabled.
ActiPHY: link down and power savings enabled.
PerfectReach: link up and power savings enabled.
Enabled: both link up and link down power savings enabled.
Total Power Usage Total power consumption of the board, measured in percentage.
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
Refresh Click to refresh the page. Any changes made locally will be undone.
5.3.2 Port Trunk
This page allows you to configure the aggregation hash mode and the aggregation group.
Figure 5-24. Aggregation Mode Configuration screen.
Table 5-17. Aggregation Mode Configuration screen options.
Label Description
Source MAC Address Calculates the destination port of the frame. You can check this box to enable the source
MAC address, or uncheck to disable. By default, Source MAC Address is enabled.
Destination MAC Address Calculates the destination port of the frame. You can check this box to enable the destination
MAC address, or uncheck to disable. By default, Destination MAC Address is disabled.
IP Address Calculates the destination port of the frame. You can check this box to enable the IP address,
or uncheck to disable. By default, IP Address is enabled.
TCP/UDP Port Number Calculates the destination port of the frame. You can check this box to enable the TCP/UDP
port number, or uncheck to disable. By default, TCP/UDP Port Number is enabled.
Page 48
724-746-5500 | blackbox.com

Chapter 5: Management
Figure 5-25. Aggregation Group Configuration screen.
Table 5-18. Aggregation Group Configuration screen options.
Label Description
Group ID Indicates the ID of each aggregation group. Normal means no aggregation. Only one group ID
is valid per port.
Port Members Lists each switch port for each group ID. Select a radio button to include a port in an aggrega-
tion, or clear the radio button to remove the port from the aggregation. By default, no ports
belong to any aggregation group. Only full duplex ports can join an aggregation and the ports
must be in the same speed in each group.
5.3.3 LACP
This page allows you to enable LACP functions to group ports together to form single virtual links, thereby increasing the bandwidth between the switch and other LACP-compatible devices. LACP trunks are similar to static port trunks, but they are more
flexible because LACP is compliant with the IEEE 802.3ad standard. Hence, it is interoperable with equipment from other vendors
that also comply with the standard. You can change LACP port settings in this page.
Figure 5-26. LACP Port Configuration screen.
724-746-5500 | blackbox.com
Page 49

Chapter 5: Management
Table 5-19. LACP Port Configuration screen options.
Label Description
Port Indicates the ID of each aggregation group. Normal indicates there is no aggregation. Only one group ID is
valid per port.
LACP Enabled Lists each switch port for each group ID. Check to include a port in an aggregation, or clear the box to
remove the port from the aggregation. By default, no ports belong to any aggregation group. Only full
duplex ports can join an aggregation and the ports must be in the same speed in each group.
Key The Key value varies with the port, ranging from 1 to 65535. Auto will set the key according to the physi-
cal link speed (10Mb = 1, 100Mb = 2, 1Gb = 3). Specific allows you to enter a user-defined value. Ports
with the same key value can join in the same aggregation group, while ports with different keys cannot.
Role Indicates LACP activity status. Active will transmit LACP packets every second, while Passive will wait for a
LACP packet from a partner (speak if spoken to).
Save Click to save changes.
Reset Click to undo any changes made locally and revert to previously saved values.
LACP System Status
This page provides a status overview for all LACP instances.
Figure 5-27. LACP System Status screen.
Table 5-20. LACP System Status screen options.
Label Description
Aggr ID The aggregation ID is associated with the aggregation instance. For LLAG, the ID is shown as 'isid:aggr-id'
and for GLAGs as “aggr-id.”
Partner System ID System ID (MAC address) of the aggregation partner
Partner Key The key assigned by the partner to the aggregation ID
Last Changed The time since this aggregation changed.
Local Ports Indicates which ports belong to the aggregation of the switch/stack. The format is: “Switch ID:Port.”
Refresh Click to refresh the page immediately
Auto-refresh Check to enable an automatic refresh of the page at regular intervals
LACP Status
This page provides an overview of the LACP status for all ports.
Page 50
724-746-5500 | blackbox.com

Chapter 5: Management
Figure 5-28. LACP Status screen.
Table 5-21. LACP Status screen options.
Label Description
Port Switch port number
LACP Yes means LACP is enabled and the port link is up. No means LACP is not enabled or the port link is down.
Backup means the port cannot join in the aggregation group unless other ports are removed. The LACP
status is disabled.
Key The key assigned to the port. Only ports with the same key can be aggregated.
Aggr ID The aggregation ID assigned to the aggregation group.
Partner System ID The partner’s system ID (MAC address).
Partner Port The partner’s port number associated with the port.
Refresh Click to refresh the page immediately.
Auto-refresh Check to enable an automatic refresh of the page at regular intervals.
LACP Statistics
This page provides an overview of the LACP statistics for all ports.
Figure 5-29. LACP Statistics screen.
Table 5-22. LACP Statistics screen options.
Label Description
Port Switch port number
LACP Transmitted The number of LACP frames sent from each port.
LACP Received The number of LACP frames received at each port.
Discarded The number of unknown or illegal LACP frames discarded at each port.
Refresh Click to refresh the page immediately.
Auto-refresh Check to enable an automatic refresh of the page at regular intervals.
Clear Click to clear the counters for all ports.
724-746-5500 | blackbox.com
Page 51

Chapter 5: Management
5.3.4 Loop Gourd
This feature prevents loop attack. When receiving loop packets, the port will be disabled automatically, preventing the loop attack
from affecting other network devices.
Figure 5-30. Loop Gourd screen.
Table 5-23. Loop Gourd screen options.
Label Description
Enable Loop Protection Activate loop protection functions (as a whole)
Transmission Time The interval between each loop protection PDU sent on each port. The valid value is 1 to 10 seconds.
Shutdown Time The period (in seconds) for which a port will be kept disabled when a loop is detected (shutting down
the port). The valid value is 0 to 604800 seconds (7 days). A value of zero will keep a port disabled
permanently (until the device is restarted).
Figure 5-31. Port Configuration screen.
Table 5-24. Port Configuration screen options.
Label Description
Port Switch port number
Enable Activate loop protection functions (as a whole)
Action Configures the action to take when a loop is detected. Valid values include Shutdown Port, Shutdown Port, and
Log or Log Only.
Tx Mode Controls whether the port is actively generating loop protection PDUs or only passively look for looped PDUs.
Page 52
724-746-5500 | blackbox.com

Chapter 5: Management
5.4 VLAN
5.4.1 VLAN Membership
You can view and change VLAN membership configurations for a selected switch stack in this page. Up to 64 VLANs are
supported. This page allows for adding and deleting VLANs as well as adding and deleting port members of each VLAN.
Figure 5-32. VLAN Membership Configuration screen.
Table 5-25. VLAN Membership Configuration screen options.
Label Description
Delete Check to delete the entry. It will be deleted during the next save.
VLAN ID The VLAN ID for the entry.
MAC Address The MAC address for the entry.
Port Members Checkmarks indicate which ports are members of the entry. Check or uncheck as needed to modify the entry.
Add New
VLAN
Click to add a new VLAN ID. An empty row is added to the table, and the VLAN can be configured as needed.
Valid values for a VLAN ID are 1 through 4095.
After clicking Save, the new VLAN will be enabled on the selected switch stack but contains no port members.
A VLAN without any port members on any stack will be deleted when you click Save.
Click Delete to undo the addition of new VLANs.
724-746-5500 | blackbox.com
Page 53

Chapter 5: Management
5.4.2 Port Configurations
This page allows you to set up VLAN ports individually.
Figure 5-33. VLAN Port Configuration screen.
Table 5-26. VLAN Port Configuration screen options.
Label Description
Ethertype for customer
S-Ports
Port The switch port number to which the following settings will be applied.
Port type Port can be one of the following types: Unaware, Customer (C-port), Service (S-port), Custom Service
Ingress Filtering Enable ingress filtering on a port by checking the box. This parameter affects VLAN ingress processing.
Frame Type Determines whether the port accepts all frames or only tagged/untagged frames. This parameter
Port VLAN Mode The allowed values are None or Specific. This parameter affects VLAN ingress and egress processing.
Port VLAN ID Configures the VLAN identifier for the port. The allowed range of the values is 1 through 4095. The
Tx Tag Determines egress tagging of a port. Untag_pvid: all VLANs except the configured PVID will be
This field specifies the Ether type used for custom S-ports. This is a global setting for all custom
S-ports.
(S-custom-port). If port type is Unaware, all frames are classified to the port VLAN ID and tags are not
removed.
If ingress filtering is enabled and the ingress port is not a member of the classified VLAN of the frame,
the frame will be discarded. By default, ingress filtering is disabled (no check mark).
affects VLAN ingress processing. If the port only accepts tagged frames, untagged frames received on
the port will be discarded. By default, the field is set to All.
If None is selected, a VLAN tag with the classified VLAN ID is inserted in frames transmitted on the
port. This mode is normally used for ports connected to VLAN-aware switches. Tx tag should be set to
Untag_pvid when this mode is used.
If Specific (the default value) is selected, a port VLAN ID can be configured (see below). Untagged
frames received on the port are classified to the port VLAN ID. If VLAN awareness is disabled, all
frames received on the port are classified to the port VLAN ID. If the classified VLAN ID of a frame
transmitted on the port is different from the port VLAN ID, a VLAN tag with the classified VLAN ID
will be inserted in the frame.
default value is 1. The port must be a member of the same VLAN as the port VLAN ID.
tagged. Tag_all: all VLANs are tagged. Untag_all: all VLANs are untagged.
Page 54
724-746-5500 | blackbox.com

Chapter 5: Management
Introduction of Port Types
Below is a detailed description of each port type, including Unaware, C-port, S-port, and S-custom-port.
Table 5-27. Port types.
Ingress Action Egress Action
Unaware
The function of
Unaware can be used
for 802.1QinQ (double
tag).
C- p or t When the port receives untagged frames, an untagged
When the port receives untagged frames, an untagged
frame obtains a tag (based on PVID) and is forwarded.
When the port receives tagged frames:
1. If the tagged frame contains a TPID of 0x8100, it will
become a double-tag frame and will be forwarded.
2. If the TPID of tagged frame is not 0x8100
(ex. 0x88A8), it will be discarded.
frame obtains a tag (based on PVID) and is forwarded.
When the port receives tagged frames:
The TPID of a frame transmitted by
Unaware port will be set to 0x8100.
The final status of the frame after egressing
will also be affected by the Egress Rule.
The TPID of a frame transmitted by C-port
will be set to 0x8100.
1. If the tagged frame contains a TPID of 0x8100, it will
be forwarded.
2. If the TPID of tagged frame is not 0x8100
(ex. 0x88A8), it will be discarded.
S-port When the port receives untagged frames, an untagged
frame obtains a tag (based on PVID) and is forwarded.
When the port receives tagged frames:
1. If the tagged frame contains a TPID of 0x8100, it will
be forwarded.
2. If the TPID of tagged frame is not 0x88A8
(ex. 0x8100), it will be discarded.
S-custom-port When the port receives untagged frames, an untagged
frame obtains a tag (based on PVID) and is forwarded.
When the port receives tagged frames:
1. If the tagged frame contains a TPID of 0x8100, it will
be forwarded.
2. If the TPID of tagged frame is not 0x88A8
(ex. 0x8100), it will be discarded.
The TPID of a frame transmitted by S-port
will be set to 0x88A8.
The TPID of a frame transmitted by
S-custom-port will be set to a self-customized value, which can be set by the user via
Ethertype for Custom S-ports.
724-746-5500 | blackbox.com
Page 55

Chapter 5: Management
Page 56
Figure 5-34.
724-746-5500 | blackbox.com

Chapter 5: Management
Figure 5-35.
724-746-5500 | blackbox.com
Page 57

Chapter 5: Management
Examples of VLAN Settings
VLAN Access Mode:
Figure 5-36.
Switch A,
Port 7 is VLAN Access mode = Untagged 20
Port 8 is VLAN Access mode = Untagged 10
Below are the switch settings.
Figure 5-37.
Page 58
724-746-5500 | blackbox.com

VLAN 1Q Trunk Mode:
Chapter 5: Management
Figure 5-38.
Switch B,
Port 1 = VLAN 1Qtrunk mode = tagged 10, 20
Port 2 = VLAN 1Qtrunk mode = tagged 10, 20
Below are the switch settings.
Figure 5-39.
Figure 5-40.
724-746-5500 | blackbox.com
Page 59

Chapter 5: Management
VLAN Hybrid Mode:
Port 1 VLAN Hybrid mode = untagged 10
Tagged 10, 20
Below are the switch settings.
Figure 5-41.
Page 60
Figure 5-42.
Figure 5-43.
724-746-5500 | blackbox.com

Chapter 5: Management
VLAN QinQ Mode:
VLAN QinQ mode is usually adopted when there are unknown VLANs, as shown in the figure below.
VLAN “X” = Unknown VLAN
Figure 5-44. VLAN QinQ mode.
Port 1 VLAN Settings:
Figure 5-45. VLAN Settings scren.
Figure 5-46. VLAN settings screen.
724-746-5500 | blackbox.com
Page 61

Chapter 5: Management
VLAN ID Settings
When setting the management VLAN, only the same VLAN ID port can be used to control the switch.
VLAN Settings:
Figure 5-47.
5.4.3 Private VLAN
The private VLAN membership configuration for the switch can be monitored and modified here. Private VLANs can be added or
deleted here. Port members of each private VLAN can be added or removed here. Private VLANs are based on the source port
mask, and there are no connections to VLANs. This means that VLAN IDs and private VLAN IDs can be identical.
A port must be a member of both a VLAN and a private VLAN to be able to forward packets. By default, all ports are VLAN
unaware and members of VLAN 1 and private VLAN 1.
A VLAN-unaware port can only be a member of one VLAN, but it can be a member of multiple private VLANs.
FIgure 5-48. Private VLAN Membership Configuration screen.
Page 62
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-28. Private VLAN Membership Configuration screen options.
Label Description
Delete Check to delete the entry. It will be deleted during the next save.
Private VLAN ID Indicates the ID of this particular private VLAN.
MAC Address The MAC address for the entry.
Port Members A row of check boxes for each port is displayed for each private
VLAN ID. You can check the box to include a port in a private VLAN.
To remove or exclude the port from the private VLAN, make sure the
box is unchecked. By default, no ports are members, and all boxes
are unchecked.
Adding a New Static Entry Click Add new Private LAN to add a new private VLAN ID. An empty
row is added to the table, and the private VLAN can be configured as
needed. The allowed range for a private VLAN ID is the same as the
switch port number range. Any values outside this range are not
accepted, and a warning message appears. Click OK to discard the
incorrect entry, or click Cancel to return to the editing and make a
correction.
The private VLAN is enabled when you click Save.
The Delete button can be used to undo the addition of new private
VLANs.
Table 5-29. Port Isolation Configuration screen options.
Label Description
Port Members A check box is provided for each port of a private VLAN.
Figure 5-49. Port Isolation Configuration screen.
When checked, port isolation is enabled for that port.
When unchecked, port isolation is disabled for that port.
By default, port isolation is disabled for all ports.
724-746-5500 | blackbox.com
Page 63

Chapter 5: Management
5.5 SNMP
5.5.1 SNMP System Configurations
Figure 5-50. SNMP system configuration screen.
Table 5-30. SNMP System Configuration screen options.
Label Description
Mode Indicates existing SNMP mode. Possible modes include:
Enabled: enable SNMP mode
Disabled: disable SNMP mode
Version Indicates the supported SNMP version. Possible versions include:
SNMP v1: supports SNMP version 1.
SNMP v2c: supports SNMP version 2c.
SNMP v3: supports SNMP version 3.
Read Community Indicates the read community string to permit access to SNMP agent. The allowed string length is 0
to 255, and only ASCII characters from 33 to 126 are allowed.
The field only suits to SNMPv1 and SNMPv2c. SNMPv3 uses USM for authentication and privacy and
the community string will be associated with SNMPv3 community table.
Write Community Indicates the write community string to permit access to SNMP agent. The allowed string length is 0
to 255, and only ASCII characters from 33 to 126 are allowed.
The field only suits to SNMPv1 and SNMPv2c. SNMPv3 uses USM for authentication and privacy and
the community string will be associated with SNMPv3 community table.
Engine ID Indicates the SNMPv3 engine ID. The string must contain an even number between 10 and 64 hexa-
decimal digits, but all-zeros and all-'F's are not allowed. Change of the Engine ID will clear all original
local users.
Page 64
724-746-5500 | blackbox.com

Figure 5-51. SNMP Trap Configuration screen.
Chapter 5: Management
Table 5-31. SNMP Trap Configuration screen options.
Label Description
Trap Mode Indicates existing SNMP trap mode. Possible modes include:
Enabled: enable SNMP trap mode
Disabled: disable SNMP trap mode
Trap Version Indicates the supported SNMP trap version. Possible versions include:
SNMP v1: supports SNMP trap version 1
SNMP v2c: supports SNMP trap version 2c
SNMP v3: supports SNMP trap version 3
Trap Community Indicates the community access string when sending SNMP trap packets. The allowed string length is
0 to 255, and only ASCII characters from 33 to 126 are allowed.
Trap Destination
Address
Trap Destination IPv6
Address
Trap Authentication
Failure
Trap Link-up and Linkdown
Indicates the SNMP trap destination address.
Provides the trap destination IPv6 address of this switch. IPv6 address consists of 128 bits represented
as eight groups of four hexadecimal digits with a colon separating each field (:). For example, in
'fe80::215:c5ff:fe03:4dc7', the symbol '::' is a special syntax that can be used as a shorthand way of
representing multiple 16-bit groups of contiguous zeros; but it can only appear once. It also uses a
following legally IPv4 address. For example, “::192.1.2.34”
Indicates the SNMP entity is permitted to generate authentication failure traps. Possible modes
include:
Enabled: enable SNMP trap authentication failure
Disabled: disable SNMP trap authentication failure
Indicates the SNMP trap link-up and link-down mode. Possible modes include:
Enabled: enable SNMP trap link-up and link-down mode
Disabled: disable SNMP trap link-up and link-down mode
Trap Inform Mode Indicates the SNMP trap inform mode. Possible modes include:
Enabled: enable SNMP trap inform mode
Disabled: disable SNMP trap inform mode
724-746-5500 | blackbox.com
Page 65

Chapter 5: Management
Table 5-31 (continued). SNMP Trap Configuration screen options.
Label Description
Trap Inform Timeout
(seconds)
Trap Inform Retry Times Configures the retry times for SNMP trap inform. The allowed range is 0 to 255.
Configures the SNMP trap inform timeout. The allowed range is 0 to 2147.
5.5.2 SNMP Community Configurations
This page allows you to configure SNMPv3 community table. The entry index key is Community.
Figure 5-52. SNMPv3 Communities Configuration screen.
Table 5-32. SNMPv3 Communities Configuration screen options.
Label Description
Delete Check to delete the entry. It will be deleted during the next save.
Community Indicates the community access string to permit access to SNMPv3 agent. The allowed string length
is 1 to 32, and only ASCII characters from 33 to 126 are allowed.
Source IP Indicates the SNMP source address.
Source Mask Indicates the SNMP source address mask.
5.5.3 SNMP User Configurations
This page allows you to configure SNMPv3 user table. The entry index keys are Engine ID and User Name.
Page 66
Figure 5-53. SNMP Users Configuration screen.
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-33. SNMPv3 Users Configuration screen options.
Label Description
Delete Check to delete the entry. It will be deleted during the next save.
Engine ID An octet string identifying the engine ID that this entry should belong to. The string must contain an
even number between 10 and 64 hexadecimal digits, but all-zeros and all-'F's are not allowed. The
SNMPv3 architecture uses User-based Security Model (USM) for message security and View-based
Access Control Model (VACM) for access control. For the USM entry, the usmUserEngineID and
usmUserName are the entry keys. In a simple agent, usmUserEngineID is always that agent's own
snmpEngineID value. The value can also take the value of the snmpEngineID of a remote SNMP
engine with which this user can communicate. In other words, if user engine ID is the same as
system engine ID, then it is local user; otherwise it's remote user.
User Name A string identifying the user name that this entry should belong to. The allowed string length is 1 to
32, and only ASCII characters from 33 to 126 are allowed.
Security Level Indicates the security model that this entry should belong to. Possible security models include:
NoAuth, NoPriv: no authentication and none privacy
Auth, NoPriv: Authentication and no privacy
Auth, Priv: Authentication and privacy
The value of security level cannot be modified if the entry already exists, which means the value must
be set correctly at the time of entry creation.
Authentication Protocol Indicates the authentication protocol that this entry should belong to. Possible authentication proto-
cols include:
None: no authentication protocol
MD5: an optional flag to indicate that this user is using MD5 authentication protocol
SHA: an optional flag to indicate that this user is using SHA authentication protocol
The value of security level cannot be modified if the entry already exists, which means the value must
be set correctly at the time of entry creation.
Authentication Password A string identifying the authentication pass phrase. For MD5 authentication protocol, the allowed
string length is 8 to 32. For SHA authentication protocol, the allowed string length is 8 to 40. Only
ASCII characters from 33 to 126 are allowed.
Privacy Protocol Indicates the privacy protocol that this entry should belong to. Possible privacy protocols include:
None: no privacy protocol
DES: an optional flag to indicate that this user is using DES authentication protocol
Privacy Password A string identifying the privacy pass phrase. The allowed string length is 8 to 32, and only ASCII
characters from 33 to 126 are allowed.
724-746-5500 | blackbox.com
Page 67

Chapter 5: Management
5.5.4 SNMP Groups Configuration
This page allows you to configure SNMPv3 group table. The entry index keys are Security Model and Security Name.
Figure 5-54. SNMPv3 Groups Configuration screen.
Table 5-34. SNMPv3 Groups Configuration screen options.
Label Description
Delete Check to delete the entry. It will be deleted during the next save.
Security Model Indicates the security model that this entry should belong to. Possible security models included:
v1: Reserved for SNMPv1.
v2c: Reserved for SNMPv2c.
usm: User-based Security Model (USM).
Security Name A string identifying the security name that this entry should belong to. The allowed string length is 1
to 32, and only ASCII characters from 33 to 126 are allowed.
Group Name A string identifying the group name that this entry should belong to. The allowed string length is 1
to 32, and only ASCII characters from 33 to 126 are allowed.
5.5.5 SNMP View Configurations
This page allows you to configure SNMPv3 view table. The entry index keys are View Name and OID Subtree.
Figure 5-55. SNMPv3 Views Configuration screen.
Page 68
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-35. SNMPv3 Views Configuration screen options.
Label Description
Delete Check to delete the entry. It will be deleted during the next save.
View Name A string identifying the view name that this entry should belong to. The allowed string length is 1 to
32, and only ASCII characters from 33 to 126 are allowed.
View Type Indicates the view type that this entry should belong to. Possible view types include:
Included: an optional flag to indicate that this view subtree should be included.
Excluded: An optional flag to indicate that this view subtree should be excluded.
Generally, if an entry's view type is Excluded, it should exist another entry whose view type is
Included, and its OID subtree oversteps the Excluded entry.
OID Subtree The OID defining the root of the subtree to add to the named view. The allowed OID length is 1 to
128. The allowed string content is digital number or asterisk (*).
5.5.6 SNMP Access Configurations
This page allows you to configure SNMPv3 access table. The entry index keys are Group Name, Security Model, and Security
Level.
Figure 5-56. SNMPv3 Access Configuration screen.
Table 5-36. SNMPv3 Access Configuration screen options.
Label Description
Delete Check to delete the entry. It will be deleted during the next save.
Group Name A string identifying the group name that this entry should belong to. The allowed string length is 1
to 32, and only ASCII characters from 33 to 126 are allowed.
Security Model Indicates the security model that this entry should belong to. Possible security models include:
any: Accepted any security model (v1|v2c|usm).
v1: Reserved for SNMPv1.
v2c: Reserved for SNMPv2c.
usm: User-based Security Model (USM).
Security Level Indicates the security model that this entry should belong to. Possible security models include:
NoAuth, NoPriv: no authentication and no privacy
Auth, NoPriv: Authentication and no privacy
Auth, Priv: Authentication and privacy
Read View Name The name of the MIB view defining the MIB objects for which this request may request the current
values. The allowed string length is 1 to 32, and only ASCII characters from 33 to 126 are allowed.
Write View Name The name of the MIB view defining the MIB objects for which this request may potentially SET new
values. The allowed string length is 1 to 32, and only ASCII characters from 33 to 126 are allowed.
724-746-5500 | blackbox.com
Page 69

Chapter 5: Management
5.6 Traffic Prioritization
5.6.1 Storm Control
There is a unicast storm rate control, multicast storm rate control, and a broadcast storm rate control. These only affect flooded
frames, i.e. frames with a (VLAN ID, DMAC) pair not present on the MAC Address table.
The rate is 2^n, where n is equal to or less than 15, or "No Limit". The unit of the rate can be either pps (packets per second) or
kpps (kilopackets per second). The configuration indicates the permitted packet rate for unicast, multicast, or broadcast traffic
across the switch.
NOTE: Frames sent to the CPU of the switch are always limited to approximately 4 kpps. For example, broadcasts in the
management VLAN are limited to this rate. The management VLAN is configured on the IP setup page.
Figure 5-57. Storm Control Configuration screen.
Table 5-37. Storm Control Configuration screen options.
Label Description
Frame Type The settings in a particular row apply to the frame type listed here: unicast, multicast, or broadcast.
Status Enable or disable the storm control status for the given frame type.
Rate The rate unit is packet per second (pps), configure the rate as 1K, 2K, 4K, 8K, 16K, 32K, 64K, 128K,
256K, 512K, or 1024K. The 1 kpps is actually 1002.1 pps.
Page 70
724-746-5500 | blackbox.com

Chapter 5: Management
5.6.2 Port Classification
QoS is an acronym for Quality of Service. It is a method to achieve efficient bandwidth utilization between individual applications
or protocols.
Figure 5-58. QoS Ingres Port Classification screen.
Table 5-38. QoS Ingres Port Classification screen options.
Label Description
Port The port number for which the configuration below applies.
QoS Class Controls the default QoS class.
All frames are classified to a QoS class. There is a one to one mapping between QoS class, queue,
and priority. A QoS class of 0 (zero) has the lowest priority.
If the port is VLAN aware and the frame is tagged, then the frame is classified to a QoS class that is
based on the PCP value in the tag as shown below. Otherwise the frame is classified to the default
QoS class.
PCP value: 0 1 2 3 4 5 6 7
QoS class: 1 0 2 3 4 5 6 7
If the port is VLAN aware, the frame is tagged, and Tag Class is enabled, then the frame is classified
to a QoS class that is mapped from the PCP and DEI value in the tag. Otherwise the frame is classified to the default QoS class.
The classified QoS class can be overruled by a QCL entry.
NOTE: If the default QoS class has been dynamically changed, then the actual default QoS class is
shown in parentheses after the configured default QoS class.
DP level Controls the default Drop Precedence Level.
All frames are classified to a DP level.
If the port is VLAN aware and the frame is tagged, then the frame is classified to a DP level that is
equal to the DEI value in the tag. Otherwise the frame is classified to the default DP level.
If the port is VLAN aware, the frame is tagged, and Tag Class is enabled, then the frame is classified
to a DP level that is mapped from the PCP and DEI value in the tag. Otherwise the frame is classified
to the default DP level.
The classified DP level can be overruled by a QCL entry.
724-746-5500 | blackbox.com
Page 71

Chapter 5: Management
Table 5-38 (continued). QoS Ingres Port Classification screen options.
Label Description
PCP Controls the default PCP value.
All frames are classified to a PCP value.
If the port is VLAN aware and the frame is tagged, then the frame is classified to the PCP value in
the tag. Otherwise the frame is classified to the default PCP value.
DEI Controls the default DEI value.
All frames are classified to a DEI value.
If the port is VLAN aware and the frame is tagged, then the frame is classified to the DEI value in the
tag. Otherwise the frame is classified to the default DEI value.
Tag Class Shows the classification mode for tagged frames on this port.
Disabled: Use default QoS class and DP level for tagged frames.
Enabled: Use mapped versions of PCP and DEI for tagged frames.
Click on the mode to configure the mode and/or mapping.
NOTE: This setting has no effect if the port is VLAN unaware. Tagged frames received on VLAN-
unaware ports are always classified to the default QoS class and DP level.
DSCP Based Click to enable DSCP Based QoS Ingress Port Classification.
5.6.3 Port Tag Remaking
This page provides an overview of QoS Egress Port Tag Remarking for all switch ports.
Figure 5-59. QoS Egress Port Tag Remarking.
Page 72
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-39. QoS Egress Port Tag Remarking screen options.
Label Description
Port The switch port number to which the following settings will be applied. Click on the port number to
configure tag remarking.
Mode Enable or disable the storm control status for the given frame type.
Shows the tag remarking mode for this port.
Classified: use classified PCP/DEI values
Default: use default PCP/DEI values
Mapped: use mapped versions of QoS class and DP level
Rate The rate unit is packet per second (pps), configure the rate as 1K, 2K, 4K, 8K, 16K, 32K, 64K, 128K,
256K, 512K, or 1024K. The 1 kpps is actually 1002.1 pps.
5.6.4 Port DSCP
This page allows you to configure basic QoS Port DSCP settings for all switch ports.
Figure 5-60. QoS Egress Port DSCP Configuration screen.
Table 5-40. QoS Egress Port DSCP Configuration screen options.
Label Description
Port Shows the list of ports for which you can configure DSCP Ingress and Egress settings.
Ingress In Ingress settings, you can change ingress translation and classification settings for individual ports.
There are two configuration parameters available in Ingress:
1. Translate
2. Classify
1. Translate Check to enable ingress translation.
2. Classify Classification has 4 different values.
Disable: no Ingress DSCP classification
DSCP=0: classify if incoming (or translated if enabled) DSCP is 0.
Selected: classify only selected DSCP whose classification is enabled as specified in DSCP Translation
window for the specific DSCP.
All: classify all DSCP
724-746-5500 | blackbox.com
Page 73

Chapter 5: Management
Table 5-40 (continued). QoS Egress Port DSCP Configuration screen options.
Label Description
Egress Port egress rewriting can be one of the following options:
Disable: no Egress rewrite
Enable: rewrite enabled without remapping
Remap DP Unaware: DSCP from the analyzer is remapped and the frame is remarked with a remapped DSCP
value. The remapped DSCP value is always taken from the ”DSCP Translation->Egress Remap DP0” table.
Remap DP Aware: DSCP from the analyzer is remapped and the frame is remarked with a remapped DSCP value.
Depending on the DP level of the frame, the remapped DSCP value is either taken from the 'DSCP Translation>Egress Remap DP0' table or from the “DSCP Translation->Egress Remap DP1” table.
5.6.5 Port Policing
This page allows you to configure Policer settings for all switch ports.
Figure 5-61. QoS Ingress Port Policers screen.
Table 5-41. QoS Ingress Port Policers screen options.
Label Description
Port The port number for which the configuration below applies.
Enable Check to enable the policer for individual switch ports.
Rate Configures the rate of each policer. The default value is 500. This value is restricted to 100 to 1000000 when the
Unit is kbps or fps, and is restricted to 1 to 3300 when the Unit is Mbps or kfps.
Unit Configures the unit of measurement for each policer rate as kbps, Mbps, fps, or kfps. The default value is kbps.
Flow
Control
If Flow Control is enabled and the port is in Flow Control mode, then pause frames are sent instead of being
discarded.
Page 74
724-746-5500 | blackbox.com

5.6.6 Queue Policing
This page allows you to configure Queue Policer settings for all switch ports.
Figure 5-62. QoS Ingress Queue Policers screen.
Table 5-42. QoS Ingress Queue Policers screen options.
Label Description
Chapter 5: Management
Port The port number for which the configuration below applies.
Enable(E) Check to enable queue policer for individual switch ports.
Rate Configures the rate of each queue policer. The default value is 500. This value is restricted to 100 to 1000000
when the Unit is kbps, and is restricted to 1 to 3300 when the Unit is Mbps.
This field is only shown if at least one of the queue policers is enabled.
Unit Configures the unit of measurement for each queue policer rate as kbps or Mbps. The default value is kbps.
This field is only shown if at least one of the queue policers is enabled.
724-746-5500 | blackbox.com
Page 75

Chapter 5: Management
5.6.7 QoS Egress Port Scheduler and Shapers
This page allows you to configure Scheduler and Shapers for a specific port.
Strict Priority
Label Description
Scheduler Mode Controls whether the scheduler mode is Strict Priority or Weighted on this switch port.
Queue Shaper Enable Check to enable queue shaper for individual switch ports.
Queue Shaper Rate Configures the rate of each queue shaper. The default value is 500. This value is restricted to 100 to
1000000 when the Unit is kbps, and it is restricted to 1 to 3300 when the Unit is Mbps.
Queues Shaper Unit Configures the rate for each queue shaper. The default value is 500. This value is restricted to 100 to
1000000 when the Unit is kbps, and it is restricted to 1 to 3300 when the Unit is Mbps.
Queue Shaper Excess Allows the queue to use excess bandwidth.
Port Shaper Enable Check to enable port shaper for individual switch ports.
Port Shaper Rate Configures the rate of each port shaper. The default value is 500 This value is restricted to 100 to
1000000 when the Unit is kbps, and it is restricted to 1 to 3300 when the Unit is Mbps.
Port Shaper Unit Configures the unit of measurement for each port shaper rate as kbps or Mbps. The default value is
kbps.
Page 76
Figure 5-63. Strict Priority screen.
Table 5-43. Strict Priority screen options.
724-746-5500 | blackbox.com

Weighted
Chapter 5: Management
Figure 5-64. QoS Egress Port Scheduler and Shapers Port 1.
Table 5-44. QoS Egress Port Scheduler and Shapers Port 1 screen options.
Label Description
Scheduler Mode Controls whether the scheduler mode is Strict Priority or Weighted on this switch port.
Queue Shaper Enable Check to enable queue shaper for individual switch ports.
Queue Shaper Rate Configures the rate of each queue shaper. The default value is 500. This value is restricted to 100 to
1000000 when the Unit is kbps, and it is restricted to 1 to 3300 when the Unit is Mbps.
Queues Shaper Unit Configures the rate of each queue shaper. The default value is 500. This value is restricted to 100 to
1000000 when the Unit is kbps, and it is restricted to 1 to 3300 when the Unit is Mbps.
Queue Shaper Excess Allows the queue to use excess bandwidth.
Queue Scheduler
Weight
Queue Scheduler
Percent
Port Shaper Enable Check to enable port shaper for individual switch ports.
Configures the weight of each queue. The default value is 17. This value is restricted to 1 to 100. This
parameter is only shown if Scheduler Mode is set to Weighted.
Shows the weight of the queue in percentage. This parameter is only shown if Scheduler Mode is set to
Weighted.
724-746-5500 | blackbox.com
Page 77

Chapter 5: Management
Table 5-44 (continued). QoS Egress Port Scheduler and Shapers Port 1 screen options.
Label Description
Port Shaper Rate Configures the rate of each port shaper. The default value is 500. This value is restricted to 100 to
1000000 when the Unit is kbps, and it is restricted to 1 to 3300 when the Unit is Mbps.
Port Shaper Unit Configures the unit of measurement for each port shaper rate as kbps or Mbps. The default value is kbps.
5.6.8 Port Scheduled
This page provides an overview of QoS Egress Port Schedulers for all switch ports.
Figure 5-65. QoS Egress Port Schedulers screen.
Table 5-45. QoS Egress Port Schedulers screen options.
Label Description
Port The switch port number to which the following settings will be applied.
Click on the port number to configure the schedulers.
Mode Shows the scheduling mode for this port.
Qn Shows the weight for this queue and port.
5.6.9 Port Shaping
This page provides an overview of QoS Egress Port Shapers for all switch ports.
Page 78
Figure 5-66. QoS Egress Port Shapers screen.
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-46. QoS Egress Port Shapers screen options.
Label Description
Port The switch port number to which the following settings will be applied. Click on the port number to configure the
shapers.
Mode Shows disabled or actual queue shaper rate - e.g. “800 Mbps.”
Qn Shows disabled or actual port shaper rate - e.g. “800 Mbps.”
5.6.10 DSCP Based QoS
This page allows you to configure basic QoS DSCP-based QoS Ingress Classification settings for all switches.
Figure 5-67. DSCP-Based QoS Ingress Classification screen.
Table 5-47. DSCP-Based QoS Ingress Classification screen options.
Label Description
DSCP Maximum number of supported DSCP values is 64.
Trust Check to trust a specific DSCP value. Only frames with trusted DSCP values are mapped to a specific QoS class
and drop precedence level. Frames with untrusted DSCP values are treated as a non-IP frame.
QoS Class QoS class value can be any number from 0–7.
DPL Drop Precedence Level (0–1)
724-746-5500 | blackbox.com
Page 79

Chapter 5: Management
5.6.11 DSCP Translation
This page allows you to configure basic QoS DSCP translation settings for all switches. DSCP translation can be done in Ingress or
Egress.
Figure 5-68. DSCP Translation screen.
Table 5-48. DSCP Translation screen options.
Label Description
DSCP Maximum number of supported DSCP values is 64 and valid DSCP value ranges from 0 to 63.
Ingress Ingress DSCP can be first translated to new DSCP before using the DSCP for QoS class and DPL map.
There are two configuration parameters for DSCP Translation -
1. Translate: DSCP can be translated to any of (0-63) DSCP values.
2. Classify: check to enable ingress classification.
Egress Configurable egress parameters include;
Remap DP0: controls the remapping for frames with DP level 0. You can select the DSCP value from a selected
menu to which you want to remap. DSCP value ranges form 0 to 63.
Remap DP1: controls the remapping for frames with DP level 1. You can select the DSCP value from a selected
menu to which you want to remap. DSCP value ranges form 0 to 63.
5.6.12 DSCP Classification
This page allows you to configure the mapping of QoS class and Drop Precedence Level to DSCP value.
Page 80
Figure 5-69. DSCP Classification screen.
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-49. DSCP Classification screen options.
Label Description
QoS Class Actual QoS class
DPL Actual Drop Precedence Level
DSCP Select the classified DSCP value (0–63)
5.6.13 QoS Control List
This page allows you to edit or insert a single QoS control entry at a time. A QCE consists of several parameters. These parameters
vary with the frame type you select.
Figure 5-70. QCE Configuration screen.
724-746-5500 | blackbox.com
Page 81

Chapter 5: Management
Label Description
Table 5-50. QCE Configuration screen options.
Port
Members
Key
Parameters
Any Allow all types of frames.
Ethernet Valid Ethernet values can range from 0x600 to 0xFFFF or Any' but excluding 0x800(IPv4) and 0x86DD(IPv6).
LLC SSAP Address: valid SSAP (Source Service Access Point) values can range from 0x00 to 0xFF or Any. The default
SNAP PID: valid PID (a.k.a ethernet type) values can range from 0x00 to 0xFFFF or Any. The default value is Any.
IPv4 Protocol IP Protocol Number: (0-255, TCP or UDP) or Any.
IPv6 Protocol IP protocol number: (0-255, TCP or UDP) or Any.
Check to include the port in the QCL entry. By default, all ports are included.
Key configurations include:
Tag: value of tag, can be Any, Untag or Tag.
VID: valid value of VLAN ID, can be any value from 1 to 4095 Any: user can enter either a specific value or a
range of VIDs.
PCP: Priority Code Point, can be specific numbers (0, 1, 2, 3, 4, 5, 6, 7), a range (0-1, 2-3, 4-5, 6-7, 0-3, 4-7) or
Any
DEI: Drop Eligible Indicator, can be any of values between 0 and 1 or Any
SMAC: Source MAC Address, can be 24 MS bits (OUI) or Any
DMAC Type: Destination MAC type, can be unicast (UC), multicast (MC), broadcast (BC) or Any
Frame Type can be the following values:
Any
Ethernet
LLC
SNAP
IPv4
IPv6
NOTE: All frame types are explained below.
The default value is Any.
value is Any.
DSAP Address: valid DSAP (Destination Service Access Point) values can range from 0x00 to 0xFF or Any. The
default value is Any.
Control Valid Control: valid values can range from 0x00 to 0xFF or Any. The default value is Any.
Source IP: specific Source IP address in value/mask format or Any. IP and mask are in the format of x.y.z.w
where x, y, z, and w are decimal numbers between 0 and 255. When the mask is converted to a 32-bit binary
string and read from left to right, all bits following the first zero must also be zero.
DSCP (Differentiated Code Point): can be a specific value, a range, or Any. DSCP values are in the range 0-63
including BE, CS1-CS7, EF or AF11-AF43.
IP Fragment: Ipv4 frame fragmented options include 'yes', 'no', and 'any'.
Sport Source TCP/UDP Port: (0-65535) or Any, specific value or port range applicable for IP protocol UDP/TCP
Dport Destination TCP/UDP Port: (0-65535) or Any, specific value or port range applicable for IP protocol UDP/
TCP
Source IP IPv6 source address: (a.b.c.d) or Any, 32 LS bits.
DSCP (Differentiated Code Point): can be a specific value, a range, or Any. DSCP values are in the range 0-63
including BE, CS1-CS7, EF or AF11-AF43.
Sport Source TCP/UDP port: (0-65535) or Any, specific value or port range applicable for IP protocol UDP/TCP
Dport Destination TCP/UDP port: (0-65535) or Any, specific value or port range applicable for IP protocol UDP/
TCP
Page 82
724-746-5500 | blackbox.com

Table 5-50 (continued). QCE Configuration screen options.
Label Description
Action Parameters Class QoS class: (0–7) or Default
Valid Drop Precedence Level value can be (0–1) or Default.
Valid DSCP value can be (0–63, BE, CS1–CS7, EF or AF11–AF43) or Default.
Default means that the default classified value is not modified by this QCE.
5.6.14 QoS Counters
This page provides the statistics of individual queues for all switch ports.
Chapter 5: Management
Figure 5-71. Queuing Counters screen.
Table 5-51. Queuing Counters screen options.
Label Description
Port The switch port number to which the following settings will be applied.
Qn There are 8 QoS queues per port. Q0 is the lowest priority.
Rx/ Tx The number of received and transmitted packets per queue.
5.6.15 QCL Status
This page shows the QCL status by different QCL users. Each row describes the QCE that is defined. It is a conflict if a specific
QCE is not applied to the hardware due to hardware limitations. The maximum number of QCEs is 256 on each switch.
Figure 5-72. QoS Control List Status screen.
724-746-5500 | blackbox.com
Page 83

Chapter 5: Management
Table 5-52. QoS Control List Status screen options.
Label Description
User Indicates the QCL user
QCE# Indicates the index of QCE
Frame Type Indicates the type of frame to look for incoming frames. Possible frame types are:
Any: the QCE will match all frame type.
Ethernet: Only Ethernet frames (with Ether Type 0x600-0xFFFF) are allowed.
LLC: Only (LLC) frames are allowed.
SNAP: Only (SNAP) frames are allowed.
IPv4: the QCE will match only IPV4 frames.
IPv6: the QCE will match only IPV6 frames.
Port Indicates the list of ports configured with the QCE.
Action Indicates the classification action taken on ingress frame if parameters configured are matched with the
frame's content.
There are three action fields: Class, DPL, and DSCP.
Class: Classified QoS; if a frame matches the QCE, it will be put in the queue.
DPL: Drop Precedence Level; if a frame matches the QCE, then DP level will set to a value displayed under DPL
column.
DSCP: if a frame matches the QCE, then DSCP will be classified with the value displayed under DSCP column.
Conflict Displays the conflict status of QCL entries. As hardware resources are shared by multiple applications,
resources required to add a QCE may not be available. In that case, it shows conflict status as Yes, otherwise it
is always No.
NOTE: Conflict can be resolved by releasing the hardware resources required to add the QCL entry by pressing
Resolve Conflict button.
5.7 Multicast
5.7.1 IGMP Snooping
This page provides IGMP Snooping related configurations.
Figure 5-73. IGMP Snooping Configuration screen.
Page 84
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-53. IGMP Snooping Configuration screen options.
Label Description
Snooping Enabled Check to enable global IGMP snooping.
Unregistered
IPMCv4Flooding
enabled
Router Port Specifies which ports act as router ports. A router port is a port on the Ethernet switch that leads
Fast Leave Check to enable fast leave on the port.
5.7.2 VLAN Configurations of IGMP Snooping
Each page shows up to 99 entries from the VLAN table, with a default value of 20, selected by the Entries Per Page input field.
When first visited, the web page will show the first 20 entries from the beginning of the VLAN Table. The first displayed will be
the one with the lowest VLAN ID found in the VLAN Table.
Check to enable unregistered IPMC traffic flooding.
towards the Layer 3 multicast device or IGMP querier.
If an aggregation member port is selected as a router port, the whole aggregation will act as a router
port.
The VLAN input field allows the user to select the starting point in the VLAN Table. Clicking the Refresh button will update the
displayed table starting from that or the next closest VLAN Table match.
The >> will use the last entry of the currently displayed entry as a basis for the next lookup. When the end is reached, the text No
more entries is shown in the displayed table. Use the |<< button to start over.
Figure 5-74. IGMP Snooping VLAN Configuration screen.
724-746-5500 | blackbox.com
Page 85

Chapter 5: Management
Table 5-54. IGMP Snooping VLAN Configuration screen options.
Label Description
Delete Check to delete the entry. The designated entry will be deleted during the next save.
VLAN ID The VLAN ID of the entry.
IGMP Snooping Enable Check to enable IGMP snooping for individual VLAN. Up to 32 VLANs can be selected.
IGMP Querier Check to enable the IGMP Querier in the VLAN.
5.7.3 IGMP Snooping Status
This page provides IGMP snooping status.
Figure 5-75. IGMP Snooping Status screen.
Table 5-55. IGMP Snooping Status screen options.
Label Description
VLAN ID The VLAN ID of the entry.
Querier Version Active Querier version
Host Version Active Host version
Querier Status Shows the Querier status as ACTIVE or IDLE
Querier Receive The number of transmitted Querier
V1 Reports Receive The number of received V1 reports
V2 Reports Receive The number of received V2 reports
V3 Reports Receive The number of received V3 reports
V2 Leave Receive The number of received V2 leave packets
Refresh Click to refresh the page immediately
Clear Clear all statistics counters
Auto-refresh Check to enable an automatic refresh of the page at regular intervals
Port Switch port number
Status Indicates whether a specific port is a router port or not
Page 86
724-746-5500 | blackbox.com

Chapter 5: Management
5.7.4 Groups Information of IGMP Snooping
Entries in the IGMP Group Table are shown on this page. The IGMP Group Table is sorted first by VLAN ID, and then by group.
Figure 5-76. IGMP Snooping Group Information screen.
Table 5-56. IGMP Snooping Group Information screen options.
Label Description
VLAN ID The VLAN ID of the group
Groups The group address of the group displayed
Port Members Ports under this group
5.8 Security
5.8.1 Remote Control Security Configurations
Remote Control Security allows you to limit the remote access to the management interface. When enabled, requests of the client
which is not in the allow list will be rejected.
Figure 5-77. Remote Control Security Configuration screen.
724-746-5500 | blackbox.com
Page 87

Chapter 5: Management
Table 5-57. Remote Control Security Configuration screen options.
Label Description
Port Port number of the remote client
IP Address IP address of the remote client. 0.0.0.0 means “any IP.”
Web Check to enable management via a Web interface
Telnet Check to enable management via a Telnet interface
SNMP Check to enable management via a SNMP interface
Delete Check to delete entries
5.8.2 Device Binding
This page provides device binding configurations. Device binding is a powerful way to monitor devices and network security.
Figure 5-78. Device Binding screen.
Table 5-58. Device Binding screen options.
Label Description
Mode Indicates the device binding operation for each port. Possible modes are:
---: disable
Scan: scans IP/MAC automatically, but no binding function
Binding: enables binding. Under this mode, any IP/MAC that does not match the
entry will not be allowed to access the network.
Shutdown: shuts down the port (No Link)
Alive Check Active Check to enable alive check. When enabled, switch will ping the device continually.
Alive Check Status Indicates alive check status. Possible statuses are:
---: disable
Got Reply: receive ping reply from device, meaning the device is still alive
Lost Reply: not receiving ping reply from device, meaning the device might have
been dead.
Stream Check Active Check to enable stream check. When enabled, the switch will detect the stream
change (getting low) from the device.
Stream Check Status Indicates stream check status. Possible statuses are:
---: disable
Normal: the stream is normal.
Low: the stream is getting low.
DDoS Prevention Action Check to enable DDOS prevention. When enabled, the switch will monitor the
device against DDOS attacks.
Page 88
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-58 (continued). Device Binding screen options.
Label Description
DDoS Prevention Status Indicates DDOS prevention status. Possible statuses are:
---: disable
Analyzing: analyzes packet throughput for initialization
Running: analysis completes and ready for next move
Attacked: DDOS attacks occur
Device IP Address Specifies IP address of the device
Device MAC Address Specifies MAC address of the device
Advanced Configurations
Alias IP Address
This page provides Alias IP Address configuration. Some devices might have more than one IP addresses. You could specify the
other IP address here.
Figure 5-79. Aiias IP Address screen.
Table 5-59. Aiias IP Address screen options.
Label Description
Alias IP Address Specifies alias IP address. Keep 0.0.0.0 if the device does not have an alias IP address.
Alive Check
You can use ping commands to check port link status. If port link fails, you can set actions from the drop-down list.
Figure 5-80. Alive Check screen.
724-746-5500 | blackbox.com
Page 89

Chapter 5: Management
Table 5-60. Alive Check screen options.
Label Description
Link Change Disables or enables the port
Only log it Simply sends logs to the log server
Shut Down the Port Disables the port
Reboot Device Disables or enables PoE power
DDoS Prevention
This page provides DDOS Prevention configurations. The switch can monitor ingress packets, and perform actions when DDOS
attack occurred on this port. You can configure the setting to achieve maximum protection.
Figure 5-81. DDOS Prevention screen.
Label Description
Mode Enables or disables DDOS prevention of the port
Sensibility Indicates the level of DDOS detection. Possible levels are:
Packet Typ e Indicates the types of DDoS attack packets to be monitored. Possible
Socket Number If packet type is UDP (or TCP), please specify the socket number here.
Table 5-61. DDOS Prevention screen options.
Low: low sensibility
Normal: normal sensibility
Medium: medium sensibility
High: high sensibility
types are:
RX Total: all ingress packets
RX Unicast: unicast ingress packets
RX Multicast: multicast ingress packets
RX Broadcast: broadcast ingress packets
TCP: TCP ingress packets
UDP: UDP ingress packets
The socket number can be a range, from low to high. If the socket
number is only one, please fill the same number in the low and high
fields.
Page 90
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-61 (continued). DDOS Prevention screen options.
Label Description
Filter If packet type is UDP (or TCP), please choose the socket direction (Destination/Source).
Action Indicates the action to take when DDOS attacks occur. Possible actions are:
---: no action
Blocking 1 minute: blocks the forwarding for 1 minute and log the event
Blocking 10 minute: blocks the forwarding for 10 minutes and log the event
Blocking: blocks and logs the event
Shunt Down the Port: shuts down the port (No Link) and logs the event
Only Log it: simply logs the event
Reboot Device: if PoE is supported, the device can be rebooted. The event will be logged.
Status Indicates the DDOS prevention status. Possible statuses are:
---: disables DDOS prevention
Analyzing: analyzes packet throughput for initialization
Running: analysis completes and ready for next move
Attacked: DDOS attacks occur
Device Description
This page allows you to configure device description settings.
Figure 5-82. Device Description screen.
Table 5-62. Device Description screen options.
Label Description
Device Type Indicates device types. Possible types are: --- (no specification), IP Camera, IP Phone, Access Point,
PC, PLC, and Network Video Recorder
Location Address Indicates location information of the device. The information can be used for Google Mapping.
Description Device descriptions
724-746-5500 | blackbox.com
Page 91

Chapter 5: Management
Stream Check
This page allows you to configure stream check settings.
Figure 5-83. Stream Check screen.
Table 5-63. Stream Check screen options.
Label Description
Mode Enables or disables stream monitoring of the port.
Action Indicates the action to take when the stream gets low. Possible actions are:
---: no action
Log it: simply logs the event
5.8.3 ACL Ports
This page allows you to configure the ACL parameters (ACE) of each switch port. These parameters will affect frames received on
a port unless the frame matches a specific ACE.
Page 92
Figure 5-84. ACL Ports Configuration screen.
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-64. ACL Ports Configuration screen options.
Label Description
Port The switch port number to which the following settings will be applied.
Policy ID Select to apply a policy to the port. The allowed values are 1 to 8. The default value is 1.
Action Select to Permit to permit or Deny to deny forwarding. The default value is Permit.
Rate Limiter ID Select a rate limiter for the port. The allowed values are Disabled or numbers from 1 to 15. The
default value is Disabled.
Port Copy Select which port frames are copied to. The allowed values are Disabled or a specific port number.
The default value is Disabled.
Logging Specifies the logging operation of the port. The allowed values are:
Enabled: frames received on the port are stored in the system log
Disabled: frames received on the port are not logged
The default value is Disabled.
NOTE: System log memory capacity and logging rate is limited.
Shutdown Specifies the shutdown operation of this port. The allowed values are:
Enabled: if a frame is received on the port, the port will be disabled.
Disabled: port shut down is disabled.
The default value is Disabled.
Counter Counts the number of frames that match this ACE.
Rate Limiters
This page allows you to configure the rate limiter for the ACL of the switch.
Figure 5-85. ACL Rate Limiter Configuration screen.
724-746-5500 | blackbox.com
Page 93

Chapter 5: Management
Table 5-65. ACL Rate Limiter Configuration screen options.
Label Description
Rate Limiter ID The rate limiter ID for the settings contained in the same row.
Rate The rate unit is packet per second (pps), which can be configured as 1, 2, 4, 8, 16, 32, 64, 128,
256, 512, 1K, 2K, 4K, 8K, 16K, 32K, 64K, 128K, 256K, 512K, or 1024K.
The 1 kpps is actually 1002.1 pps.
ACL Control List
This page allows you to configure ACE (Access Control Entry).
An ACE consists of several parameters. These parameters vary with the frame type you have selected. First select the ingress port
for the ACE, and then the frame type. Different parameter options are displayed according to the frame type you have selected.
A frame matching the ACE can be configured here.
Figure 5-86. ACE Configuration screen.
Table 5-66. ACE Configuration screen.
Label Description
Ingress Port Indicates the ingress port to which the ACE will apply.
Any: the ACE applies to any port
Port n: the ACE applies to this port number, where n is the number of the switch port.
Policy n: the ACE applies to this policy number, where n can range from 1 to 8.
Frame Type Indicates the frame type of the ACE. These frame types are mutually exclusive.
Any: any frame can match the ACE.
Ethernet Type: only Ethernet type frames can match the ACE. The IEEE 802.3 descripts the value
of length/types should be greater than or equal to 1536 decimal (equal to 0600 hexadecimal).
ARP: only ARP frames can match the ACE. Notice the ARP frames will not match the ACE with
Ethernet type.
IPv4: only IPv4 frames can match the ACE. Notice the IPv4 frames will not match the ACE with
Ethernet type.
Action Specifies the action to take when a frame matches the ACE.
Permit: takes action when the frame matches the ACE.
Deny: drops the frame matching the ACE.
Page 94
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-66 (continued). ACE Configuration screen.
Label Description
Rate Limiter Specifies the rate limiter in number of base units. The allowed range is 1 to 15. Disabled means
the rate limiter operation is disabled.
Port Copy Frames matching the ACE are copied to the port number specified here. The allowed range is the
same as the switch port number range. Disabled means the port copy operation is disabled.
Logging Specifies the logging operation of the ACE. The allowed values are:
Enabled: frames matching the ACE are stored in the system log.
Disabled: frames matching the ACE are not logged.
NOTE: System log memory capacity and logging rate is limited.
Shutdown Specifies the shutdown operation of the ACE. The allowed values are:
Enabled: if a frame matches the ACE, the ingress port will be disabled.
Disabled: port shutdown is disabled for the ACE.
Counter Indicates the number of times the ACE matched by a frame.
Figure 5-87. MAC Parameters screen.
Table 5-67. MAC Parameters screen options.
Label Description
SMAC Filter (Only displayed when the frame type is Ethernet Type or ARP.)
Specifies the source MAC filter for the ACE.
Any: no SMAC filter is specified (SMAC filter status is “don't-care”).
Specific: if you want to filter a specific source MAC address with the ACE, choose this value. A
field for entering an SMAC value appears.
SMAC Value When Specific is selected for the SMAC filter, you can enter a specific source MAC address. The
legal format is "xx-xx-xx-xx-xx-xx". Frames matching the ACE will use this SMAC value.
DMAC Filter Specifies the destination MAC filter for this ACE.
Any: no DMAC filter is specified (DMAC filter status is “don't-care”).
MC: frame must be multicast.
BC: frame must be broadcast.
UC: frame must be unicast.
Specific: If you want to filter a specific destination MAC address with the ACE, choose this value.
A field for entering a DMAC value appears.
724-746-5500 | blackbox.com
Page 95

Chapter 5: Management
Table 5-67 (continued). MAC Parameters screen options.
Label Description
DMAC Value When Specific is selected for the DMAC filter, you can enter a specific destination MAC address.
The legal format is “xx-xx-xx-xx-xx-xx.” Frames matching the ACE will use this DMAC value.
Figure 5-88. VLAN Parameters screen.
Table 5-68. VLAN Parameters screen menu.
Label Description
VLAN ID Filter Specifies the VLAN ID filter for the ACE
Any: no VLAN ID filter is specified (VLAN ID filter status is "don't-care").
Specific: if you want to filter a specific VLAN ID with the ACE, choose this value. A field for entering a
VLAN ID number appears.
VLAN ID When Specific is selected for the VLAN ID filter, you can enter a specific VLAN ID number. The allowed
range is 1 to 4095. Frames matching the ACE will use this VLAN ID value.
Tag Priority Specifies the tag priority for the ACE. A frame matching the ACE will use this tag priority. The allowed
number range is 0 to 7. Any means that no tag priority is specified (tag priority is “don't-care”).
Page 96
Figure 5-89. IP Parameters screen.
724-746-5500 | blackbox.com

Chapter 5: Management
Table 5-69. IP Parameters screen options.
Label Description
IP Protocol Filter Specifies the IP protocol filter for the ACE
Any: no IP protocol filter is specified (“don't-care”).
Specific: if you want to filter a specific IP protocol filter with the ACE, choose this value. A field for
entering an IP protocol filter appears.
ICMP: selects ICMP to filter IPv4 ICMP protocol frames. Extra fields for defining ICMP parameters will
appear. For more details of these fields, please refer to the help file.
UDP: selects UDP to filter IPv4 UDP protocol frames. Extra fields for defining UDP parameters will appear.
For more details of these fields, please refer to the help file.
TCP: selects TCP to filter IPv4 TCP protocol frames. Extra fields for defining TCP parameters will appear.
For more details of these fields, please refer to the help file.
IP Protocol Value Specific allows you to enter a specific value. The allowed range is 0 to 255. Frames matching the ACE
will use this IP protocol value.
IP TTL Specifies the time-to-live settings for the ACE
Zero: IPv4 frames with a time-to-live value greater than zero must not be able to match this entry.
Non-zero: IPv4 frames with a time-to-live field greater than zero must be able to match this entry.
Any: any value is allowed (“don't-care”).
IP Fragment Specifies the fragment offset settings for the ACE. This includes settings of More Fragments (MF) bit and
Fragment Offset (FRAG OFFSET) for an IPv4 frame.
No: IPv4 frames whose MF bit is set or the FRAG OFFSET field is greater than zero must not be able to
match this entry.
Yes: IPv4 frames whose MF bit is set or the FRAG OFFSET field is greater than zero must be able to
match this entry.
Any: any value is allowed (“don't-care”).
IP Option Specifies the options flag settings for the ACE
No: IPv4 frames whose options flag is set must not be able to match this entry.
Yes: IPv4 frames whose options flag is set must be able to match this entry.
Any: any value is allowed (“don't-care”).
SIP Filter Specifies the source IP filter for this ACE
Any: no source IP filter is specified (Source IP filter is “don't-care”).
Host: source IP filter is set to Host. Specify the source IP address in the SIP Address field that appears.
Network: source IP filter is set to Network. Specify the source IP address and source IP mask in the SIP
Address and SIP Mask fields that appear.
SIP Address When Host or Network is selected for the source IP filter, you can enter a specific SIP address in dotted
decimal notation.
SIP Mask When Network is selected for the source IP filter, you can enter a specific SIP mask in dotted decimal
notation.
DIP Filter Specifies the destination IP filter for the ACE
Any: no destination IP filter is specified (destination IP filter is “don't-care”).
Host: destination IP filter is set to Host. Specify the destination IP address in the DIP Address field that
appears.
Network: destination IP filter is set to Network. Specify the destination IP address and destination IP
mask in the DIP Address and DIP Mask fields that appear.
DIP Address When Host or Network is selected for the destination IP filter, you can enter a specific DIP address in
dotted decimal notation.
DIP Mask When Network is selected for the destination IP filter, you can enter a specific DIP mask in dotted
decimal notation.
724-746-5500 | blackbox.com
Page 97

Chapter 5: Management
Figure 5-90. ARP Parameters screen.
Table 5-70. ARP Parameters screen options.
Label Description
ARP/RARP Specifies the available ARP/RARP opcode (OP) flag for the ACE
Any: no ARP/RARP OP flag is specified (OP is “don't-care”).
ARP: frame must have ARP/RARP opcode set to ARP
RARP: frame must have ARP/RARP opcode set to RARP.
Other: frame has unknown ARP/RARP Opcode flag.
Request/Reply Specifies the available ARP/RARP opcode (OP) flag for the ACE
Any: no ARP/RARP OP flag is specified (OP is “don't-care”).
Request: frame must have ARP Request or RARP Request OP flag set.
Reply: frame must have ARP Reply or RARP Reply OP flag.
Sender IP Filter Specifies the sender IP filter for the ACE
Any: no sender IP filter is specified (sender IP filter is "don't-care").
Host: sender IP filter is set to Host. Specify the sender IP address in the SIP Address field that appears.
Network: sender IP filter is set to Network. Specify the sender IP address and sender IP mask in the SIP
Address and SIP Mask fields that appear.
Sender IP
Address
Sender IP Mask When Network is selected for the sender IP filter, you can enter a specific sender IP mask in dotted
Target IP Filter Specifies the target IP filter for the specific ACE
Target IP Address When Host or Network is selected for the target IP filter, you can enter a specific target IP address in
Target IP Mask When Network is selected for the target IP filter, you can enter a specific target IP mask in dotted
When Host or Network is selected for the sender IP filter, you can enter a specific sender IP address in
dotted decimal notation.
decimal notation.
Any: no target IP filter is specified (target IP filter is “don't-care”).
Host: target IP filter is set to Host. Specify the target IP address in the Target IP Address field that
appears.
Network: target IP filter is set to Network. Specify the target IP address and target IP mask in the Target
IP Address and Target IP Mask fields that appear.
dotted decimal notation.
decimal notation.
Page 98
724-746-5500 | blackbox.com

Label Description
Chapter 5: Management
Table 5-70 (continued). ARP Parameters screen options.
ARP SMAC
Match
RARP SMAC
Match
IP/Ethernet
Length
IP Specifies whether frames will meet the action according to their ARP/RARP hardware address space (HRD)
Ethernet Specifies whether frames will meet the action according to their ARP/RARP protocol address space (PRO)
Specifies whether frames will meet the action according to their sender hardware address field (SHA) settings.
0: ARP frames where SHA is not equal to the SMAC address
1: ARP frames where SHA is equal to the SMAC address
Any: any value is allowed (“don't-care”).
Specifies whether frames will meet the action according to their target hardware address field (THA)
settings.
0: RARP frames where THA is not equal to the SMAC address
1: RARP frames where THA is equal to the SMAC address
Any: any value is allowed (“don't-care”)
Specifies whether frames will meet the action according to their ARP/RARP hardware address length (HLN)
and protocol address length (PLN) settings.
0: ARP/RARP frames where the HLN is equal to Ethernet (0x06) and the (PLN) is equal to IPv4 (0x04) must
not match this entry.
1: ARP/RARP frames where the HLN is equal to Ethernet (0x06) and the (PLN) is equal to IPv4 (0x04) must
match this entry.
Any: any value is allowed (“don't-care”).
settings.
0: ARP/RARP frames where the HLD is equal to Ethernet (1) must not match this entry.
1: ARP/RARP frames where the HLD is equal to Ethernet (1) must match this entry.
Any: any value is allowed (“don't-care”).
settings.
0: ARP/RARP frames where the PRO is equal to IP (0x800) must not match this entry.
1: ARP/RARP frames where the PRO is equal to IP (0x800) must match this entry.
Any: any value is allowed (“don't-care”).
Figure 5-91. ICMP Parameters screen.
724-746-5500 | blackbox.com
Page 99

Chapter 5: Management
Table 5-71. ICMP Parameters screen options.
Label Description
ICMP Type Filter Specifies the ICMP filter for the ACE
Any: no ICMP filter is specified (ICMP filter status is "don't-care").
Specific: if you want to filter a specific ICMP filter with the ACE, you can enter a specific ICMP value. A field
for entering an ICMP value appears.
ICMP Type Value When Specific is selected for the ICMP filter, you can enter a specific ICMP value. The allowed range is 0 to
255. A frame matching the ACE will use this ICMP value.
ICMP Code Filter Specifies the ICMP code filter for the ACE
Any: no ICMP code filter is specified (ICMP code filter status is "don't-care").
Specific: if you want to filter a specific ICMP code filter with the ACE, you can enter a specific ICMP code
value. A field for entering an ICMP code value appears.
ICMP Code Value When Specific is selected for the ICMP code filter, you can enter a specific ICMP code value. The allowed
range is 0 to 255. A frame matching the ACE will use this ICMP code value.
Figure 5-92. TCP Parameters and UDP Parameters screens.
Table 5-72. TCP Parameters and UDP Parameters screens options.
Label Description
TCP/ UDP Source
Filter
TCP/ UDP Source
No.
TCP/ UDP Source
Range
Specifies the TCP/UDP source filter for the ACE
Any: no TCP/UDP source filter is specified (TCP/UDP source filter status is "don't-care").
Specific: if you want to filter a specific TCP/UDP source filter with the ACE, you can enter a specific TCP/UDP
source value. A field for entering a TCP/UDP source value appears.
Range: if you want to filter a specific TCP/UDP source range filter with the ACE, you can enter a specific
TCP/UDP source range. A field for entering a TCP/UDP source value appears.
When Specific is selected for the TCP/UDP source filter, you can enter a specific TCP/UDP source value. The
allowed range is 0 to 65535. A frame matching the ACE will use this TCP/UDP source value.
When Range is selected for the TCP/UDP source filter, you can enter a specific TCP/UDP source range value.
The allowed range is 0 to 65535. A frame matching the ACE will use this TCP/UDP source value.
Page 100
724-746-5500 | blackbox.com
 Loading...
Loading...