Page 1

May 2010
LES1101A
LES1102A
1101 and 1102 Secure Device Servers
Securely monitor, access, and control the computers,
networking devices, telecommunications equipment,
and power supplies in your data room
or communications centers.
Manage your servers:
• Locally across your management LAN
or through the local serial console port.
• Remotely across the Internet or private network.
Customer
Support
Information
Order toll-free in the U.S.: Call 877-877-BBOX (outside U.S. call 724-746-5500) •
FREE technical support 24 hours a day, 7 days a week: Call 724-746-5500 or fax 724-746-0746 •
Mailing address: Black Box Corporation, 1000 Park Drive, Lawrence, PA 15055-1018 •
Web site: www.blackbox.com
• E-mail: info@blackbox.com
Page 2

1101 and 1102 Secure Device Servers
Federal Communications Commission and Industry Canada Radio Frequency Interference Statements
This equipment generates, uses, and can radiate radio-frequency energy, and if not installed and used properly, that is, in strict accordance with the
manufacturer’s instructions, may cause interference to radio communication. It has been tested and found to comply with the limits for a Class A
computing device in accordance with the specifications in Subpart J of Part 15 of FCC rules, which are designed to provide reasonable protection
against such interference when the equipment is operated in a commercial environment. Operation of this equipment in a residential area is likely to
cause interference, in which case the user at his own expense will be required to take whatever measures may be necessary to correct the
interference. Changes or modifications not expressly approved by the party responsible for compliance could void the user’s authority to operate
the equ ipment.
This digital apparatus does not exceed the Class A limits for radio noise emission from digital apparatus set out in the Radio Interference Regulation
of Industry Canada.
Le présent appareil numérique n’émet pas de bruits radioélectriques dépassant les limites applicables aux appareils numériques de la classe A
prescrites dans le Règlement sur le brouillage radioélectrique publié par Industrie Canada.
2
724-746-5500 | blackbox.com
Page 3

FCC and IC RFI Statements
Normas Oficiales Mexicanas (NOM) Electrical Safety Statement
INSTRUCCIONES DE SEGURIDAD
1. Todas las instrucciones de seguridad y operación deberán ser leídas antes de que el aparato eléctrico sea operado.
2. Las instrucciones de seguridad y operación deberán ser guardadas para referencia futura.
3. Todas las advertencias en el aparato eléctrico y en sus instrucciones de operación deben ser respetadas.
4. Todas las instrucciones de operación y uso deben ser seguidas.
5. El aparato eléctrico no deberá ser usado cerca del agua—por ejemplo, cerca de la tina de baño, lavabo, sótano
mojado o cerca de una alberca, etc..
6. El aparato eléctrico debe ser usado únicamente con carritos o pedestales que sean recomendados por el fabricante.
7. El aparato eléctrico debe ser montado a la pared o al techo sólo como sea recomendado por el fabricante.
8. Servicio—El usuario no debe intentar dar servicio al equipo eléctrico más allá a lo descrito en las instrucciones de
operación. Todo otro servicio deberá ser referido a personal de servicio calificado.
9. El aparato eléctrico debe ser situado de tal manera que su posición no interfiera su uso. La colocación del aparato
eléctrico sobre una cama, sofá, alfombra o superficie similar puede bloquea la ventilación, no se debe colocar en
libreros o gabinetes que impidan el flujo de aire por los orificios de ventilación.
10. El equipo eléctrico deber ser situado fuera del alcance de fuentes de calor como radiadores, registros de calor,
estufas u otros aparatos (incluyendo amplificadores) que producen calor.
11. El aparato eléctrico deberá ser connectado a una fuente de poder sólo del tipo descrito en el instructivo de operación,
o como se indique en el aparato.
12. Precaución debe ser tomada de tal manera que la tierra fisica y la polarización del equipo no sea eliminada.
13. Los cables de la fuente de poder deben ser guiados de tal manera que no sean pisados ni pellizcados por objetos
colocados sobre o contra ellos, poniendo particular atención a los contactos y receptáculos donde salen del aparato.
14. El equipo eléctrico debe ser limpiado únicamente de acuerdo a las recomendaciones del fabricante.
15. En caso de existir, una antena externa deberá ser localizada lejos de las lineas de energia.
16. El cable de corriente deberá ser desconectado del cuando el equipo no sea usado por un largo periodo de tiempo.
17. Cuidado debe ser tomado de tal manera que objectos liquidos no sean derramados sobre la cubierta u orificios de
ventilación.
18. Servicio por personal calificado deberá ser provisto cuando:
A: El cable de poder o el contacto ha sido dañado; u
B: Objectos han caído o líquido ha sido derramado dentro del aparato; o
C: El aparato ha sido expuesto a la lluvia; o
D: El aparato parece no operar normalmente o muestra un cambio en su desempeño; o
E: El aparato ha sido tirado o su cubierta ha sido dañada.
European Community (CE) Electromagnetic Compatibility Directive
This equipment has been tested and found to comply with the protection requirements of European Emission Standard EN55022/EN61000-3 and
the Generic European Immunity Standard EN55024.
EMC:
EN55022 (2003)/CISPR-2 (2002): class A
IEC61000-4-2 (2001): 4KV CD, 8KV AD
IEC61000-4-3 (2002): 3V/m
IEC61000-4-4 (2001):1KV (power line), 0.5KV (signal line)
724-746-5500 | blackbox.com
3
Page 4

1101 and 1102 Secure Device Servers
Trademarks Used in this Manual
Black Box and the Double Diamond logo are registered trademarks of BB Technologies, Inc.
Mac is a registered trademark of Apple Computers, Inc.
Linux is a registered trademark of Linus Torvalds.
Internet Explorer, Windows, Windows Me, Windows NT, and Windows Vista are a registered trademarks of Microsoft Corporation.
Nagios is a registered trademark of Nagios Enterprises LLC.
Java and Solaris are trademarks of Sun Microsystems, Inc.
Unix is a registered trademark of X/Open Company Ltd.
Any other trademarks mentioned in this manual are acknowledged to be the property of the trademark owners.
4
724-746-5500 | blackbox.com
Page 5

Table of Contents
5
Table of Contents
1. Specifications.......................................................................................................................................................................................................... 9
2. Overview ................................................................................................................................................................................................................10
2.1 Introduction....................................................................................................................................................................................................10
2.2 Manual Organization ....................................................................................................................................................................................10
2.3 Types of Users ..................................................................................................................................................................................................10
2.4 Management Console ....................................................................................................................................................................................11
2.5 Hardware Description .....................................................................................................................................................................................11
2.5.1 LES1101A Front Panel .........................................................................................................................................................................11
2.5.2 LES1101A Back Panel..........................................................................................................................................................................12
2.5.3 LES1102A Front Panel .........................................................................................................................................................................13
2.5.4 LES1102A Back Panel..........................................................................................................................................................................13
2.6 What’s Included ......................................................................................................................................................................................14
2.6.1 LES1101A.....................................................................................................................................................................................14
2.6.2 LES1102A.....................................................................................................................................................................................14
3. Installation ................................................................................................................................................................................................................15
3.1 Power Connection...........................................................................................................................................................................................15
3.2 Network Connection.......................................................................................................................................................................................15
3.3 Serial Port Connection ....................................................................................................................................................................................15
3.3.1 Non RS-232 Serial Port Pinouts—LES1102A .....................................................................................................................................16
3.3.2 Non RS-232 Serial Port Pinouts—LES1101A .....................................................................................................................................17
4. System Configuration ................................................................................................................................................................................................18
4.1 Management Console Connection................................................................................................................................................................18
4.1.1 Connected PC/Workstation Setup .....................................................................................................................................................18
4.1.2 Browser Connection ............................................................................................................................................................................19
4.2 Administrator Password ..................................................................................................................................................................................20
4.3 Network IP Address .........................................................................................................................................................................................21
4.4 System Services ................................................................................................................................................................................................22
4.5 Communications Software .............................................................................................................................................................................24
4.5.1 SDT Connector.....................................................................................................................................................................................24
4.5.2 PuTTY....................................................................................................................................................................................................25
4.5.3 SSHTerm ...............................................................................................................................................................................................25
5. Serial Port, Host, Device, and User Configuration ...................................................................................................................................................26
5.1 Configure Serial Ports......................................................................................................................................................................................26
5.1.1 Common Settings................................................................................................................................................................................27
5.1.2 Console Server Mode ..........................................................................................................................................................................28
5.1.3 SDT Mode.............................................................................................................................................................................................31
5.1.4 Device (RPC, UPS, EMD) Mode...........................................................................................................................................................32
5.1.5 Terminal Server Mode .........................................................................................................................................................................32
5.1.6 Serial Bridging Mode ...........................................................................................................................................................................32
5.1.7 Syslog ....................................................................................................................................................................................................33
5.2 Add/Edit Users .................................................................................................................................................................................................34
5.3 Authentication .................................................................................................................................................................................................36
5.4 Network Hosts .................................................................................................................................................................................................36
5.5 Trusted Networks ............................................................................................................................................................................................37
5.6 Serial Port Redirection .....................................................................................................................................................................................37
5.7 Managed Devices ............................................................................................................................................................................................38
6. Secure SSH Tunneling and SDT Connector...............................................................................................................................
6.1 Configuring for SSH Tunneling to Hosts .......................................................................................................................................................41
6.2 SDT Connector Client Configuration .............................................................................................................................................................41
6.2.1 SDT Connector Installation..................................................................................................................................................................41
6.2.2 Configuring a New Console Server Gateway in the SDT Connector Client....................................................................................42
6.2.3 Auto-Configure SDT Connector Client with the User’s Access Privileges .......................................................................................43
6.2.4 Make an SDT Connection through the Gateway to the Host..........................................................................................................44
6.2.5 Manually Adding Hosts to the SDT Connector Gateway .................................................................................................................44
6.2.6 Manually Adding New Services to the New Hosts............................................................................................................................45
6.2.7 Adding a Client Program to be Started for the New Service ...........................................................................................................47
6.3 SDT Connector to Management Console .....................................................................................................................................................49
6.4 SDT Connector–Telnet or SSH Connect to Serially Attached Devices.........................................................................................................49
6.5 Using SDT Connector for Out-of-Band Connection to the Gateway..........................................................................................................50
6.6 Importing (and Exporting) Preferences ..........................................................................................................................................................52
...............................40
724-746-5500 | blackbox.com
5
Page 6

6
1101 and 1102 Secure Device Servers
6.7 SDT Connector Public Key Authentication .................................................................................................................................................... 52
6.8 Setting Up SDT for Remote Desktop Access ................................................................................................................................................. 53
6.8.1 Enable Remote Desktop on the Target Windows Computer to be Accessed ................................................................................ 53
6.8.2 Configure the Remote Desktop Connection Client .......................................................................................................................... 54
6.9 SDT SSH Tunnel for VNC ................................................................................................................................................................................ 56
6.9.1 Install and Configure the VNC Server on the Computer to be Accessed........................................................................................ 56
6.9.2 Install, Configure, and Connect the VNC Viewer ............................................................................................................................. 58
6.10 Using SDT to Connect to Hosts that are Serially Attached to the Gateway ............................................................................................. 59
6.10.1 Establish a PPP Connection between the Host COM Port and the Console Server ..................................................................... 60
6.10.2 Setup SDT Serial Ports on the Console Server ................................................................................................................................. 62
6.10.3 Setup SDT Connector to SSH Port Forward over the Console Server Serial Port.......................................................................... 63
6.10.4 SSH Tunneling Using Other SSH Clients (for example, PuTTY) ...................................................................................................... 63
7. Alerts and Logging..................................................................................................................................................................................................... 67
7.1 Configure SMTP/SMS/SNMP/Nagios Alert Service........................................................................................................................................ 67
7.1.1 Email Alerts........................................................................................................................................................................................... 67
7.1.2 SMS Alerts ............................................................................................................................................................................................ 68
7.1.3 SNMP Alerts ......................................................................................................................................................................................... 68
7.1.4 Nagios Alerts ........................................................................................................................................................................................ 69
7.2 Activate Alert Events and Notifications .......................................................................................................................................................... 69
7.2.1 Add a New Alert .................................................................................................................................................................................. 70
7.2.2 Configuring General Alert Types ........................................................................................................................................................ 70
7.2.3 Configuring Power Alert Type ............................................................................................................................................................ 72
7.3 Remote Log Storage........................................................................................................................................................................................ 73
7.4 Serial Port Logging .......................................................................................................................................................................................... 73
7.5 Network TCP or UDP Port Logging ................................................................................................................................................................ 73
8. Power Management .................................................................................................................................................................................................. 75
8.1 Remote Power Control (RPC) ......................................................................................................................................................................... 75
8.1.1 RPC Connection................................................................................................................................................................................... 75
8.1.2 RPC Access Privileges and Alerts......................................................................................................................................................... 77
8.1.3 User Power Management ................................................................................................................................................................... 77
8.1.4 RPC Status ............................................................................................................................................................................................ 78
8.2 Uninterruptible Power Supply Control (UPS)................................................................................................................................................. 78
8.2.1 Managed UPS Connections ................................................................................................................................................................ 79
8.2.2 Remote UPS Management.................................................................................................................................................................. 82
8.2.3 Controlling UPS Powered Computers ................................................................................................................................................ 83
8.2.4 UPS Alerts ............................................................................................................................................................................................. 83
8.2.5 UPS Status ............................................................................................................................................................................................ 83
8.2.6 Overview of Network UPS Tools (NUT) .............................................................................................................................................. 84
9. Authentication ........................................................................................................................................................................................................... 87
9.1 Authentication Configuration ........................................................................................................................................................................ 87
9.1.1 Local Authentication............................................................................................................................................................................ 87
9.1.2 TACACS Authentication ..................................................................................................................................................................... 87
9.1.3 RADIUS Authentication ....................................................................................................................................................................... 88
9.1.4 LDAP Authentication ........................................................................................................................................................................... 89
9.1.5 RADIUS/TACACS User Configuration ................................................................................................................................................ 89
9.2 Pluggable Authentication Modules (PAM) .................................................................................................................................................... 90
9.3 SSL Certificate .................................................................................................................................................................................................. 91
10. Nagios Integration ................................................................................................................................................................................................... 94
10.1 Nagios Overview............................................................................................................................................................................................ 94
10.2 Central Management and Setting Up SDT for Nagios ............................................................................................................................... 95
10.2.1 Setup Central Nagios Server ............................................................................................................................................................. 96
10.2.2 Setup Distributed Console Servers ................................................................................................................................................... 96
10.3 Configuring Nagios Distributed Monitoring ............................................................................................................................................... 98
10.3.1 Enable Nagios on the Console Server .............................................................................................................................................. 98
10.3.2 Enable NRPE Monitoring ................................................................................................................................................................... 99
10.3.3 Enable NSCA Monitoring.................................................................................................................................................................. 99
10.3.4 Configure Selected Serial Ports for Nagios Monitoring ..................................................................................................................100
10.3.5 Configure Selected Network Hosts for Nagios Monitoring............................................................................................................100
10.3.6 Configure the Upstream Nagios Monitoring Host..........................................................................................................................100
10.4 Advanced Distributed Monitoring Configuration .......................................................................................................................................100
10.4.1 Sample Nagios Configuration...........................................................................................................................................................100
10.4.2 Basic Nagios Plug-Ins .........................................................................................................................................................................103
10.4.3 Number of Supported Devices .........................................................................................................................................................103
10.4.4 Distributed Monitoring Usage Scenarios .........................................................................................................................................104
6
724-746-5500 | blackbox.com
Page 7

Table of Contents
11. System Management ..............................................................................................................................................................................................106
11.1 System Administration and Reset ................................................................................................................................................................106
11.2 Upgrade Firmware ........................................................................................................................................................................................107
11.3 Configure Date and Time .............................................................................................................................................................................108
11.4 Configuration Backup...................................................................................................................................................................................108
12. Status Reports ..........................................................................................................................................................................................................110
12.1 Port Access and Active Users........................................................................................................................................................................110
12.2 Statistics .........................................................................................................................................................................................................110
12.3 Support Reports ............................................................................................................................................................................................111
12.4 Syslog .............................................................................................................................................................................................................112
12.5 Dashboard .....................................................................................................................................................................................................112
12.5.1 Configuring the Dashboard ..............................................................................................................................................................113
12.5.2 Creating Custom Widgets for the Dashboard ................................................................................................................................114
13. Management ...........................................................................................................................................................................................................115
13.1 Device Management.....................................................................................................................................................................................115
13.2 Port and Host Logs ........................................................................................................................................................................................115
13.3 Serial Port Terminal Connection ...................................................................................................................................................................116
13.4 Power Management .....................................................................................................................................................................................117
14. Configuration from the Command Line................................................................................................................................................................118
14.1 Accessing Config from the Command Line................................................................................................................................................118
14.2 Serial Port Configuration ..............................................................................................................................................................................120
14.3 Adding and Removing Users........................................................................................................................................................................122
14.4 Adding and Removing User Groups ............................................................................................................................................................124
14.5 Authentication ...............................................................................................................................................................................................124
14.6 Network Hosts...............................................................................................................................................................................................125
14.7 Trusted Networks ..........................................................................................................................................................................................126
14.8 Cascaded Ports ..............................................................................................................................................................................................127
14.9 UPS Connections ...........................................................................................................................................................................................127
14.10 RPC Connections ........................................................................................................................................................................................128
14.11 Managed Devices........................................................................................................................................................................................129
14.12 Port Log .......................................................................................................................................................................................................129
14.13 Alerts............................................................................................................................................................................................................130
14.14 SMTP and SMS............................................................................................................
14.15 SNMP ...........................................................................................................................................................................................................132
14.16 Administration.............................................................................................................................................................................................132
14.17 IP Settings ....................................................................................................................................................................................................132
14.18 Date and Time Settings ..............................................................................................................................................................................133
14.19 DHCP Server ................................................................................................................................................................................................134
14.20 Services ........................................................................................................................................................................................................134
14.21 NAGIOS........................................................................................................................................................................................................135
15. Advanced Configuration .........................................................................................................................................................................................136
15.1 Custom Scripting...........................................................................................................................................................................................136
15.1.1 Custom Script to Run When Booting ..............................................................................................................................................136
15.1.2 Running Custom Scripts When Alerts are Triggered ......................................................................................................................136
15.1.3 Example Script—Power Cycling on Pattern Match .........................................................................................................................137
15.1.4 Example Script—Multiple Email Notifications on Each Alert ..........................................................................................................137
15.1.5 Deleting Configuration Values from the CLI ...................................................................................................................................138
15.1.6 Power Cycle Any Device When a Ping Request Fails ......................................................................................................................140
15.1.7 Running Custom Scripts When a Configurator is Invoked.............................................................................................................141
15.1.8 Backing Up the Configuration and Restoring Using a Local USB Stick .........................................................................................141
15.1.9 Backing Up the Configuration Off-Box............................................................................................................................................142
15.2 Advanced Portmanager................................................................................................................................................................................143
15.2.1 Portmanager Commands..................................................................................................................................................................143
15.2.2 External Scripts and Alerts.................................................................................................................................................................144
15.3 Raw Access to Serial Ports ............................................................................................................................................................................145
15.3.1 Access to Serial Ports .........................................................................................................................................................................145
15.3.2 Accessing the Console/Modem Port................................................................................................................................................145
15.4 IP Filtering.......................................................................................................................................................................................................145
15.5 Modifying SNMP Configuration...................................................................................................................................................................146
15.6 Secure Shell (SSH) Public Key Authentication .............................................................................................................................................147
15.6.1 SSH Overview.....................................................................................................................................................................................147
15.6.2 Generating Public Keys (Linux) .........................................................................................................................................................147
15.6.3 Installing the SSH Public/Private Keys (Clustering) ...........................................................................................................................148
................................................................................131
7
724-746-5500 | blackbox.com
7
Page 8

8
1101 and 1102 Secure Device Servers
15.6.4 Installing SSH Public Keys Authentication (Linux)............................................................................................................................148
15.6.5 Generating Public/Private Keys for SSH (Windows) ........................................................................................................................150
15.6.6 Fingerprinting.....................................................................................................................................................................................151
15.6.7 SSH Tunneled Serial Bridging............................................................................................................................................................152
15.6.8 SDT Connector Public Key Authentication ......................................................................................................................................153
15.7 Secure Sockets Layer (SSL) Support .............................................................................................................................................................154
15.8 HTTPS .............................................................................................................................................................................................................154
15.8.1 Generating an Encryption Key..........................................................................................................................................................154
15.8.2 Generating a Self-Signed Certificate with OpenSSL .......................................................................................................................154
15.8.3 Installing the Key and Certificate......................................................................................................................................................155
15.8.4 Launching the HTTPS Server.............................................................................................................................................................155
15.9 Power Strip Control.......................................................................................................................................................................................155
15.9.1 The PowerMan Tool ..........................................................................................................................................................................155
15.9.2 The pmpower Tool ............................................................................................................................................................................156
15.9.3 Adding New RPC Devices .................................................................................................................................................................157
15.10 IPMtool ...................................................................................................................................................................................................157
15.11 Custom Development Kit (CDK) ..........................................................................................................................................................160
15.12 Scripts for Managing Slaves..................................................................................................................................................................160
Appendix. Linux Commands and Source Code ...........................................................................................................................................................161
8
724-746-5500 | blackbox.com
Page 9

1. Specifications
CPU: MIcrel KS8695P controller
Memory: 16 MB SDRAM, 8 MB Flash
Serial Baud Rates: 2400 to 115,200 bps
Connectors: LES1101A: (1) DB9 RS-232 serial, (1) RJ-45 10/100BASE-T Ethernet;
LES1102A: (2) DB9 RS-232 serial, (1) RJ-45 10/100BASE-T Ethernet
Indicators: LES1101A: (4) LEDs: Power, Activity, On RJ-45: Connectivity, Activity
LES1102A: (5) LEDs: Power, Serial 1, Serial 2, On RJ-45: Connectivity, Activity
Temperature Tolerance: Operating: 41 to 122° F (5 to 50° C);
Storage: -20 to +140° F (-30 to +60° C)
Humidity Tolerance: 5 to 90%
Power: (1) 12-VDC universal input external wallmount power supply,100–240 VAC, 50/60 Hz
Size: LES1101A: 4”H x 1.75”W x 1”D (10.2 x 4.5 x 2.5 cm);
LES1102A: 3.9”H x 2.8”W x 1”D (10 x 7.2 x 2.5 cm)
Weight: LES1101A: 0.25 lb. (0.11 kg);
LES1102A: 1 lb. (0.45 kg)
Chapter 1: Specifications
724-746-5500 | blackbox.com
9
Page 10

1101 and 1102 Secure Device Servers
2. Overview
2.1 Introduction
This User’s Manual walks you through installing and configuring your Black Box Secure Device Servers (LES1101A or LES1102A). Each of these
products is referred to generically in this manual as a “console server.”
Once configured, you will be able to use your console server to securely monitor access and control the computers, networking devices,
telecommunications equipment, power supplies, and operating environments in your data room or communications centers. This manual guides
you in managing this infrastructure locally (across your operations or management LAN or through the local serial console port), and remotely
(across the Internet or private network).
2.2 Manual Organization
This manual contains the following chapters:
• Chapter 1. Specifications: Lists the general specifications for the console servers.
• Chapter 2, Overview: An overview of the features of console server and information on this manual.
• Chapter 3, Installation: Physical installation of the console server and how to interconnect controlled devices.
• Chapter 4, System Configuration: Describes the initial installation and configuration using the Management Console. Covers configuration of the
console server on the network and the services that will be supported.
• Chapter 5, Serial Port and Network Host: Covers configuring serial ports and connected n etwork hosts, and setting up Users and Groups.
• Chapter 6, Secure Tunneling (SDT): Covers secure remote access using SSH and configuring for RDP, VNC, HTTP, HTTPS, etc. access to network
and serially connected devices.
• Chapter 7, Alerts and Logging: Explains how to set up local and remote event/data logs and how to trigger SNMP and email alerts.
• Chapter 8, Power Management: Describes how to manage USB, serial, and network attached power strips and UPS supplies including Network
UPS Tool (NUT) operation and IPMI power control.
• Chapter 9, Authentication: Access to the console server requires usernames and passwords that are locally or externally authenticated.
• Chapter 10, Nagios Integration: Describes how to set Nagios central management with SDT extensions and configure the console server as
a distributed Nagios server.
• Chapter 11, System Management: Covers access to and configuration of services that will run on the console server
.
• Chapter 12, Status Reports: View a dashboard summary and detailed status and logs of serial and network connected devices (ports,
hosts, power, and environment)
• Chapter 13, Management: Includes port controls that Users can access.
• Chapter 14, Basic Configuration: Command line installation and configuration using the config command.
• Chapter 15, Advanced Config: More advanced command line configuration activities where you will need to use Linux commands.
The latest update of this manual can be found online at www.Black Box.com/download.html
• Appendix: Linux Commands and Source Code.
2.3 Types of Users
The console server supports two classes of users:
First, there are the administrative users who will be authorized to configure and control the console server; and to access and control all the
connected devices. These administrative users will be set up as members of the admin user group and any user in this class is referred to generically
in this manual as the Administrator. An Administrator can access and control the console server using the config utility, the Linux command line, or
the browser-based Management Console. By default, the Administrator has access to all services and ports to control all the serial connected devices
and network connected devices (hosts).
The second class of users are those who have been set up by the Administrator with specific limits of their access and control authority. These users
are set up as members of the users user group (or some other user groups the Administrator may have added). They are only authorized to perform
specified controls on specific connected devices and are referred to as Users. These Users (when authorized) can access serial or network connected
10
724-746-5500 | blackbox.com
Page 11

Chapter 2: Overview
devices; and control these devices using the specified services (for example, Telnet, HHTPS, RDP, IPMI, Serial over LAN, Power Control). An
authorized User also has a limited view of the Management Console and can only access authorized configured devices and review port logs.
In this manual, when the term user (lower case) is used, it refers to both the above classes of users. This document also uses the term remote users
to describe users who are not on the same LAN segment as the console server. These remote users may be Users, who are on the road connecting
to managed devices over the public Internet, or it may be an Administrator in another office connecting to the console server itself over the
enterprise VPN, or the remote user may be in the same room o r the same office but connected on a separate VLAN than the console server.
2.4 Management Console
The Management Console provides a view of the console server and all the connected devices.
Administrators can use any browser to log into the Management Console either locally or from a remote location. They can then use Management
Console to manage the console server, the users, the serial ports and serially connected devices, network connected hosts, and connected power
devices; and to view associated logs and con figure alerts.
1 2 3
Figure 2-1. Login screen for the management console.
A User can also use the Management Console, but has limited menu access to control select devices, review their logs, and access them using the
built-in java terminal or control power to them.
The console server runs an embedded Linux® operating system, and experienced Linux and UNIX® users may prefer to configure it at the
command line. To get command line access, connect through a terminal emulator or communications program to the console serial port; connect
via ssh or telnet through the LAN; or connect through an SSH tunneling to the console server.
1 2 3
2.5 Hardware Description
2.5.1 LES1101A Front Panel
Figure 2-2 shows the front panel of the LES1101A. Table 2-1 describes its components.
724-746-5500 | blackbox.com
1 2 3
5 4
Figure 2-2. LES1101A front panel.
11
Page 12

1101 and 1102 Secure Device Servers
Table 2-1. LES1101A front-panel components.
Number Component Description
` 1 Barrel connector Power
2 RJ-45 connector Links to 10/100 Mbps Ethernet
3 J1 jumper Selects RS-232, RS-485, RS-422
4 RJ-45 LED Ethernet Connectivity LED
5 RJ-45 Ethernet Activity
2.5.2 LES1101A Back Panel
Figure 2-3 shows the LES1101A back panel. Table 2-2 describes its components.
6
Figure 2-3. LES1101A back panel.
Table 2-2. LES1101A back-panel components.
Number Component Description
6 DB9 connector Serial connector (RS-232, RS-485, RS-422)
12
724-746-5500 | blackbox.com
Page 13

2.5.3 LES1102A Front Panel
Figure 2-4 shows the front panel of the LES1102A. Table 2-3 describes its components.
1 2 3
Chapter 2: Overview
Figure 2-4. LES1102A front panel.
Table 2-3. LES1102A front-panel components.
Number Component Description
1 Barrel connector Power
2 8-position Phoenix connector Port 2 (RS-422/485)
3 RJ-45 connector Links to 10/100 Mbps Ethernet
4 RJ-45 LED (left side of connector) Ethernet Connectivity LED
5 RJ-45 LED (right side of connector) Ethernet Activity LED
4 5
2.5.4 LES1102A Back Panel
Figure 2-5 shows the LES1102A back panel. Table 2-4 describes its components.
6 7
Figure 2-5. LES1102A back panel.
Table 2-4. LES1102A back-panel components.
Number Component Description
6 DB9 connector Port 1 RS-232
7 DB9 connector Port 2 RS-232
724-746-5500 | blackbox.com
13
Page 14

1101 and 1102 Secure Device Servers
2.6 What’s Included
Your package should include the following items. If anything is missing or damaged, contact Black Box Technical Support at 724-746-5500 or
info@blackbox.com
2.6.1 LES1101A
• 1101 Secure Device Server
• Universal input 12-VDC wallmount power supply
• Printed Quick Start Guide
• CD-ROM containing this user’s manual
2.6.2 LES1102A
• 1101 Secure Device Server
• (2) UTP cables
• (2) DB9 F to RJ-45 S adapters
• Universal input 12-VDC wallmount power supply
• Printed Quick Start Guide
• CD-ROM containing this user’s manual
.
14
724-746-5500 | blackbox.com
Page 15

Chapter 3: Installation
3. Installation
Make sure you have everything listed in Chapter 2, Section 2.6 for your 1101 or 1102 Secure Device Server.
3.1 Power Connection
The LES1101A or LES1102A models are each supplied with an external DC wall mount power supply. This power supply comes with a selection of
wall socket adapters for each geographic region (North American, Europe, UK, Japan or Australia) and will operate with 100-240 VAC, 50/60 Hz
input, 7.2 watts maximum.
Plug in the DC power cable. The 12V DC connector from the power supply unit plugs into the DC power socket on the side of the console server
casing.
Plug in the power supply AC power cable and turn on the AC power. Confirm that the console server Power LED (PWR) is lit.
NOTE: When you first apply power to the LES1101A or LES1102A the Local and Serial LEDs will flash alternately.
The LES1102A can also be powered directly from any +9V DC to +48V DC power source by connecting the DC power lines to the IN-GND and
VIN+ screw jacks.
Power connector
+9 to +48 VDC 1 GND
Figure 3-1. Power connector.
3.2 Network Connection
The RJ-45 LAN ports are located on the side of the LES1101A and LES1102A units.
All physical connections are made using industry standard CAT5 cabling and connectors. Make sure you only connect the LAN port to an Ethernet
network that supports 10BASE-T/100BASE-T.
The first time you configure the console server, you must connect a PC or workstation to the console server’s network port.
3.3 Serial Port Connection
The LES1102A has two DB9 serial ports (Ports 1–2). By default, Port 1 is configured in Local Console (modem) mode. The LES1101A also has one
DB9 serial port that‘s configured by default in Local Console (modem) mode.
The serial ports are all set by default in RS-232 mode. The RS-232 pinout standards for the DB9 connector are described in Table 3-1.
724-746-5500 | blackbox.com
15
Page 16

1101 and 1102 Secure Device Servers
Table 3-1. RS-232 DB9 connector pinouts.
3.3.1 Non RS-232 Serial Port Pinouts— LES1102A
Port 2 on the LES1102A can also be software selected to be an RS-485 or RS-422 port connected through the screw terminal block (pinout shown
in Table 3-2.
Signal Pin Definition
CD 1 Received Line Signal Detector
RXD 2 Received Data
TXD 3 Transmitted Data
DTR 4 Data Terminal Ready
GND 5 Signal Ground
DSR 6 Data Set Ready
RTS 7 Request To Send
CTS 8 Clear To Send
RI 9 Ring Indicator
Table 3-2. Non RS-232 serial port pinout for the LES1102A.
1 +V DC IN
2 GND
3 RX+
4 RX5 TX+
6 TX-
7 +3.3V DC OUT
8 GND
RS-422 uses a full-duplex transmit on TX+/TX- pair, receive on RX+/RX- pair.
RS-485 uses half-duplex over single pair. The LES1102A supports half duplex “party-line” communications over a 2-wire RS-485 bus (D+/D-). This is
enabled by choosing the RS-485 option (instead of RS-232 or RS-422) for “Signaling Protocol” from the “Serial Port: Configuration” link on the
16
724-746-5500 | blackbox.com
Figure 3-2. Front panel of the LES1102A showing pinout connections on the left side.
Page 17

Chapter 3: Installation
Web management console. Two short cable loops are also required between the RX+/TX+ pins and RX-/TX- pins. This is because the LES1102A uses
universal differential transceivers that support 4-wire (RS-422) and 2-wire (RS-485) operation.
In RS-485 mode, Port 2 on the LES1102A listens on the 2-wire bus for receive data until it is required to send data. In RS-485 send mode, it stops
receiving, enables its transmitters when there is data to be sent, transmits the data, and returns to receive mode. This eliminates the possibility of
collisions with other devices that share the RS-485 bus and avoids receiving stale echoed data.
1 +3V
2 GND
3 RX+
4 RX-
D+
D-
5 TX+
6 TX7 +VIN
8 GND
Figure 3-3. RS-485 wiring diagram for LES1102A.
3.3.2 Non RS-232 Serial Port Pinouts— LES1101A
The one DB9 serial port on the LES1101A can be used as an RS-232, RS-485 or RS-422 port. By default, the LES1101A is configured in RS-232
mode (with a vertical jumper in place on the left hand J1 pins).
Figure 3-4. RS-232 configuration for the DB9 port on the LES1101A.
To set the port in RS-422 or RS-485 mode, you must remove the J1 jumper and then configure the Signaling Protocol using the Management
Console.
The DB9 pinout is shown in Table 3-3.
Table 3-3. DB9 pinout for LES1101A.
Pin: Mode: RS232 RS422 RS485
1 DCD DCD+ 2 RXD RX - 3 TXD TX + D+
4 DTR DTR+ 5 GND GND GND
6 DSR RX + 7 RTS TX - D8 CTS DCD- 9 - DTR- -
724-746-5500 | blackbox.com
17
Page 18

1101 and 1102 Secure Device Servers
4. System Configuration
This chapter provides step-by-step instructions for the console server’s initial configuration, and for connecting it to the Management or Operational
LAN. Th e Administrator must:
• Activate the Management Console.
• Change the Administrator password.
• Set the IP address console server’s principal LAN port.
• Select the network services that will be supported.
This chapter also discusses the communications software tools that the Administrator may use to access the console server.
4.1 Management Console Connection
Your console server is configured with a default IP Address 192.168.0.1 Subnet Mask 255.255.255.0
• Directly connect a PC or workstation to the console server.
NOTE: For initial configuration we recommend that you connect the console server directly to a single PC or workstation. However, if you choose to
connect your LAN before completing the initial setup steps:
• make sure that there are no other devices on the LAN with an address of 192.168.0.1
• make sure that the console server and the PC/workstation are on the same LAN segment, with no interposed router appliances.
4.1.1 Connected PC/Workstation Setup
To configure the console server with a browser, the connected PC/workstation should have an IP address in the same range as the console server
(for example, 192.168.0.100):
• To configure the IP Address of your Linux or Unix PC/workstation, simply run ifconfig
• For Windows PCs (Win9x/Me/2000/XP, Windows NT, Windows Vista, Windows 7):
- Click Start -> (Settings ->) Control Panel and double click Network Connections (for 95/98/Me, double click Network).
- Right click on Local Area Connection and select Properties.
- Select Internet Protocol (TCP/IP) and click Properties.
- Select Use the following IP address and enter the following details:
-
IP address: 192.168.0.100
Subnet mask: 255.255.255.0
If you want to retain your existing IP settings for this network connection, click Advanced and Add the above as a secondary IP connection.
If it is not convenient to change your PC/workstation network address, you can use the ARP-Ping command to reset the console server IP address.
To do this from a Windows PC:
• Click Start -> Run (or select All Programs then Accessories then Run).
• Type cmd and click OK to bring up the command line.
• Type arp –d to flush the ARP cache.
• Type arp –a to view the current ARP cache (this should be empty).
18
724-746-5500 | blackbox.com
Page 19

Chapter 4: System Configuration
Figure 4-1. Run screen.
Now add a static entry to the ARP table and ping the console server to assign the IP address to the console server. In the example below, a console
server has a MAC Address 00:13:C6:00:02:0F (designated on the label on the bottom of the unit) and we are setting its IP address to
192.168.100.23. Also the PC/workstation issuing the arp command must be on the same network segment as the console server (that is, have an IP
address of 192.168.100.xxx)
• Type arp -s 192.168.100.23 00-13-C6-00-02-0F (Note for UNIX the syntax is: arp -s 192.168.100.23 00:13:C6:00:02:0F).
• Type ping -t 192.18.100.23 to start a continuous ping to the new IP Address.
• Turn on the console server and wait for it to configure itself with the new IP address. It will start replying to the ping at this point.
• Type arp –d to flush the ARP cache again.
4.1.2 Browser connection
Activate your preferred browser on the connected PC/workstation and enter https://192.168.0.1 The Management Console supports all current
versions of the popular browsers (Internet Explorer, Mozilla Firefox, Chrome, and more).
724-746-5500 | blackbox.com
19
Page 20

1101 and 1102 Secure Device Servers
You will be prompted to log in. Enter the default administration
username and administration password:
Username: root
Password: default
Figure 4-2. Login screen.
NOTE: Console servers are factory configured with HTTPS access enabled and HTTP access disabled.
Figure 4-3. Management console welcome screen.
A Welcome screen, which lists four initial installation configuration steps, will be displayed:
1. Change the default administration password on the System/Administration page (Chapter 4).
2. Configure the local network settings on the System/IP page (Chapter 4).
3. Configure port settings and enable them on the Serial & Network/Serial Port page (Chapter 5).
4. Configure users with access to serial ports on the Serial & Network/Users page (Chapter 4).
After completing each of the above steps, you can return to the configuration list by clicking in the top left corner of the screen on the Black Box
logo.
NOTE: If you are not able to connect to the Management Console at 192.168.0.1 or if the default Username/Password were not accepted,
then reset your console server (refer to Chapter 11).
4.2 Administrator Password
For security reasons, only the administrator user named root can initially log into your console server. Only people who know the root password can
access and reconfigure the console server itself. However, anyone who correctly guesses the root password could gain access (and the default root
password is default). To avoid this, enter and confirm a new root password before giving the console server any access to, or control of, your
computers and network appliances.
NOTE: We recommend that you set up a new Administrator user as soon as convenient and log in as this new user for all ongoing
administration functions (rather than root). This Administrator can be configured in the admin group with full access privileges
through the Serial & Network: Users & Groups menu as detailed in Chapter 5.
20
724-746-5500 | blackbox.com
Page 21

Chapter 4: System Configuration
Figure 4-4. System: Administration screen.
1. Select System: Administration.
2. Enter a new System Password then re-enter it in Confirm System Password. This is the new password for root, the main administrative
user account, so choose a complex password, and keep it safe.
3. At this stage, you may also wish to enter a System Name and System Description for the console server to give it a unique ID and make it
simple to identify.
NOTE: The System Name can contain from 1 to 64 alphanumeric characters (however you can also use the special characters “-”, “_”,
and “.” ) There are no restrictions on the characters that can be used in the System Description or the System Password (each can contain
up to 254 characters). However, only the first eight System Password characters are used to make the password hash.
4. Click Apply. Since you have changed the password, you will be prompted to log in again. This time, use the new password.
NOTE: If you are not confident that your console server has the current firmware release, you can upgrade. Refer to Upgrade Firmware—
Chapter 11.
4.3 Network IP Address
The next step is to enter an IP address for the principal Ethernet (LAN/Network/Network1) port on the console server; or enable its DHCP client so
that it automatically obtains an IP address from a DHCP server on the network it will connect to.
On the System: IP menu, select the Network Interface page, then check dhcp or static for the Configuration Method.
If you selected Static, you must manually enter the new IP Address, Subnet Mask, Gateway, and DNS server details. This selection automatically
disables the DHCP client.
724-746-5500 | blackbox.com
21
Page 22

1101 and 1102 Secure Device Servers
Figure 4-5. IP Settings screen.
If you selected DHCP, the console server will look for configuration details from a DHCP server on your management LAN. This selection
automatically disables any static address. The console server MAC address is printed on a label on the base plate.
NOTE: In its factory default state (with no Configuration Method selected) the console server has its DHCP client enabled, so it automatically
accepts any network IP address assigned by a DHCP server on your network. In this initial state, the console server will then respond to
both its Static address (192.168.0.1) and its newly assigned DHCP address.
By default, the console server LAN port auto-detects the Ethernet connection speed. You can use the Media menu to lock the Ethernet to 10 Mbps
or 100 Mbps, and to Full Duplex (FD) or Half Duplex (HD).
NOTE: If you changed the console server IP address, you may need to reconfigure your PC/workstation so it has an IP address that is in the same
network range as this new address.
Click Apply.
Enter http://new IP address to reconnect the browser on the PC/workstation that is connected to the console server.
IPv6 configuration
You can also configure the console server management LAN for IPv6 operation:
• On the System: IP menu, select the General Settings page and check Enable IPv6.
• Then, configure the IPv6 parameters on the Network Interface page.
4.4 System Services
The Administrator can access and configure the console server and connect to the managed devices using a range of access protocols (services). The
factory default enables HTTPS and SSH access to the console server and disables HTTP and Telnet.
A User or Administrator can also use nominated enabled services to connect through the console server to attached serial and network connected
managed devices.
The Administrator can simply disable any of the services, or enable others.
22
724-746-5500 | blackbox.com
Page 23

Chapter 4: System Configuration
Figure 4-6. System: Services screen.
Select the System: Services option, then select/deselect for the service to be enabled/disabled. The following access protocol options are available:
• HTTPS: This ensures secure browser access to all the Management Console menus. It also allows appropriately configured Users secure
browser access to selected Management Console Manage menus. If you enable HTTPS, the Administrator will be able to use a secure
browser connection to the Console server’s Management Console. For information on certificate and user client software configuration,
refer to Chapter 9—Authentication. By default, HTTPS is enabled, and we recommend that that you only use HTTPS access if the console
server will be managed over any public network (for example, the Internet).
• HTTP: By default HTTP is disabled. We recommend that the HTTP service remain disabled if the console server will be remotely accessed
over the Internet.
• Telnet: This gives the Administrator Telnet access to the system command line shell (Linux commands). This may be suitable for a local
direct connection over a management LAN. By default, Telnet is disabled. We recommend that this service remain disabled if you will
remotely administer the console server.
• SSH: This service provides secure SSH access to the Linux command line shell. We recommend that you choose SSH as the protocol where
the Administrator connects to the console server over the Internet or any other public network. This will provide authenticated
communications between the SSH client program on the remote PC/workstation and the SSH sever in the conso le server. By default SSH is
enabled. For more information on SSH configuration refer Chapter 9—Authentication.
You can configure related service options at this stage:
• Ping: This allows the console server to respond to incoming ICMP echo requests. Ping is enabled by default. For security reasons, you
should disable this service after initial configuration.
And there are some serial port access parameters that you can configure on this menu:
724-746-5500 | blackbox.com
23
Page 24

1101 and 1102 Secure Device Servers
• Base: The console server uses specific default ranges for the TCP/IP ports for the various access services that Users and Administrators can
use to access devices attached to serial ports (as covered in Chapter 4—Configuring Serial Ports). The Administrator can also set alternate
ranges for these services, and these secondary ports will then be used in addition to the defaults.
The default TCP/IP base port address for telnet access is 2000, and the range for telnet is IP Address: Port (2000 + serial port #),
that is, 2001–2002. If the Administrator sets 8000 as a secondary base for telnet, then serial port #2 on the console server can be
accessed via telnet at IP Address:2002 and at IP Address:8002.
The default base for SSH is 3000; for Raw TCP is 4000; and for RFC2217 it is 5000.
Click Apply. As you apply your services selections, the screen will be updated with a confirmation message:
Message Changes to configuration succeeded.
4.5 Communications Software
You have configured access protocols for the Administrator client to use when connecting to the console server. User clients (who you may set up
later) will also use these protocols when accessing con sole server serial attached devices and network attached hosts. You will need to have
appropriate communications software tools set up on the Administrator (and User) PC/workstation.
Black Box provides the SDT Connector Java applet as the recommended client software tool. You can use other generic tools such as PuTTY and
SSHTerm. These tools are all described below as well.
4.5.1 SDT Connector
Each console server has an unlimited number of SDT Connector licenses to use with that console server.
LES1102A
LAN
SDT connector
(RDP/VNC/Telnet/
HTTP client
RDP/VNC/Telnet/HTTP sessions
forwarded to
devices/computers/service processors
SDT Connector is a lightweight tool that enables Users and Administrators to securely access the console server and the various computers, network
devices, and appliances that may be serially or network connected to the console server.
SDT Connector is a Java applet that couples the trusted SSH tunneling protocol with popular access tools such as Telnet, SSH, HTTP, HTTPS, VNC,
and RDP to provide point-and-click secure remote management access to all the systems and devices being managed.
Information on using SDT Connector for browser access to the console server’s Management Console, Telnet/SSH access to the console server
command line, and TCP/UDP connecting to hosts that are network connected to the console server is in Chapter 6—Secure Tunneling .
SDT Connector can be installed on Windows 2000, XP, 2003, Windows Vista, Windows NT PCs, and on most Linux, UNIX, and Solaris computers.
SSH encrypted
on the LAN
tunnel
Network
appliance
Figure 4-7. SDT connector application.
Database
server
Web
server
PCs
24
724-746-5500 | blackbox.com
Page 25

Chapter 4: System Configuration
4.5.2 PuTTY
You can also use communications packages like PuTTY to connect to the console server command line (and to connect serially attached devices as
covered in Chapter 5). PuTTY is a freeware implementation of Telnet and SSH for Windows and UNIX platforms. It runs as an executable application
without needing to be installed onto your system. PuTTY (the Telnet and SSH client itself) can be downloaded from
http://www.tucows.com/preview/195286.html
To use PuTTY for an SSH terminal session from a Windows
client, enter the console server’s IP address as the ”Host
Name (or IP address).”
To access the console server command line, select “SSH” as
the protocol, and use the default IP Port 22.
Click “Open” and the console server login prompt will
appear. (You may also receive a “Security Alert” that the
host’s key is not cached. Choose “yes” to continue.)
Using the Telnet protocol is similarly simple, but you use the
default port 23.
Figure 4-8. PuTTY screen.
4.5.3 SSHTerm
Another popular communications package you can use is SSHTerm, an open source package that you can download from
http://sourcefo rge.net/projects/sshtools
To use SSHTerm for an SSH terminal session from a Windows Client, simply Select the “File” option and click on “New Connection.”
A new dialog box will appear for your “Connection Profile.” Type in the host
name or IP address (for the console server unit) and the TCP port that the SSH
session will use (port 22). Then type in your username, choose password
authentication, and click connect.
You may receive a message about the host key fingerprint. Select “yes” or
“always” to continue.
The next step is password authentication. The system prompts you for your
username and password from the remote system. This logs you on to the
console server
Figure 4-9. Connection Profile screen.
724-746-5500 | blackbox.com
25
Page 26

1101 and 1102 Secure Device Servers
5. Serial Port, Host, Device, and User Configuration
The Black Box LES1101A and LES1102A console server enables access and control of serially attached devices and network attached devices (hosts).
The Administrator must configure access privileges for each of these devices, and specify the services that can be used to control the devices. The
Administrator can also set up new users and specify each user’s individual access and control privileges.
LAN
Network connected
(HTTP, HTTPS, IPMI,
ALOM, SOL, VNC,
RDP, SSH, X, Telnet)
Figure 5-1. Configuration.
This chapter covers each of the steps in configuring hosts and serially attached devices:
Configure Serial Ports
Users & Groups
Authentication—
Network Hosts
Configuring Trusted Networks
Cascading and Redirection of Serial Console Ports.
Connecting to Power (UPS PDU and IPMI) and Environmental Monitoring (EMD) devices.
Managed Devices—presents a consolidated view of all the connections.
—setting up the protocols to be used in accessing serially-connected devices.
—setting up users and defining the access permissions for each of these users.
covered in more detail in Chapter 9.
—configuring access to network connected devices (referred to as hosts).
—nominate user IP addresses.
LES1102A
Serial connected
Linux, Solaris,
Windows, UNIX, BSD
servers
VoIP PBX switch,
router, firewall,
power strip, UPS
5.1 Configure Serial Ports
To configure a serial port, you must first set the Common Settings (the protocols and the RS-232 parameters (such as baud rate) that will be used
for the data connection to that port.
Select what mode the port is to operate in. You can set each port to support one of five operating modes:
1. Console Server Mode is the default and this enables general access to serial console port on the serially attached devices.
2. Device Mode sets the serial port up to communicate with an intelligent serial controlled PDU or UPS.
3. SDT Mode enables graphical console access (with RDP, VNC, HTTPS, etc.) to hosts that are serially connected.
4. Terminal Server Mode sets the serial port to wait for an incoming terminal login session.
5. Serial Bridge Mode enables transparently interconnects two serial port devices over a network.
26
724-746-5500 | blackbox.com
Page 27

Chapter 5: Serial Port, Host, Device, and User Configuration
Figure 5-2. Serial port screen.
Select Serial & Network: Serial Port and you will see the current labels, modes, logging levels, and RS-232 protocol options that are currently set up
for each serial port.
By default, each serial port is set in Console Server mode. To reconfigure the port, click Edit.
When you have reconfigured the common settings (Chapter 5.1.1) and the mode (Chapters 5.1.2–5.1.6) for each port, you can set up any remote
syslog (Chapter 5.1.7), then click Apply.
NOTE: If you want to set the same protocol options for multiple serial ports at once, click Edit Multiple Ports and select which ports you want to
configure as a group.
If the console server has been configured with distributed Nagios monitoring enabled, then you will also be presented with Nagios Settings options
to enable nominated services on the Host to be monitored (refer Chapter 10—Nagios Integration).
5.1.1 Common Settings
There are a number of common settings that you can set for each serial port. These are independent of the mode in which the port is being used.
Set these serial port parameters to match the serial port parameters on the device you attach to that port.
Figure 5-3. Edit multiple ports screen.
Specify a label for the port.
Select the appropriate Baud Rate, Parity, Data Bits, Stop Bits, and Flow Control for each port. (Note: The RS-485/RS-422 option is not relevant for
console servers.)
724-746-5500 | blackbox.com
27
Page 28

1101 and 1102 Secure Device Servers
Before proceeding with further serial port configuration, connect the ports to the serial devices they will be controlling, and make sure they have
matching settings.
NOTE: The serial ports are all set at the factory to RS-232: 9600 baud, no parity, 8 data bits, 1 stop bit, and Console server Mode. You can
5.1.2 Console Server Mode
Select Console Server Mode to en able remote management access to the serial console that is attached to this serial port:
change the baud rate to 2400–230400 baud using the management console. You can configure lower baud rates (50, 75, 110, 134,
150, 200, 300, 600, 1200, 1800 baud) from the command line. Refer to Chapter 14— Basic Configuration (Linux Commands).
Figure 5-4. Console Server settings screen.
Logging Level: This specifies the level of information to be logged and monitored (referto Chapter 7— Alerts and Logging).
Telnet: Wh en the Telnet service is enabled on the console server, a Telnet client on a User or Administrator’s computer can connect to a serial device
attached to this serial port on the console server. The Telnet communications are unencrypted, so this protocol is generally recommended only for
local connections.
With Win2000/XP/NT you can run telnet from the command prompt (cmd.exe). Vista and Windows 7 include a Telnet client and server, but they are
not enabled by default. To enable Telnet:
• Log in as Admin and go to Start/Control Panel/Programs and Features.
• Select Turn Windows features on or off, check the Telnet Client, and click OK.
28
724-746-5500 | blackbox.com
Page 29

Chapter 5: Serial Port, Host, Device, and User Configuration
Figure 5-5. Windows features screen.
If the remote communications are tunneled with SDT Connector, then you can use Telnet to securely access these attached devices (refer to the
Note below).
NOTE: In Console Server mode, Users and Administrators can use SDT Connector to set up secure Telnet connections that are SSH tunneled from
their client PC/workstations to the serial port on the console server. SDT Connector can be installed on Windows 2000, XP, 2003, Vista,
and Windows 7 PCs and on most Linux platforms. You can also set up secure Telnet connections with a simple point-and-click.
To use SDT Connector to access consoles on the console server serial ports, you configure SDT Connector with the console server as a
gateway, then configure it as a host. Next, you enable Telnet service on Port (2000 + serial port #) i.e. 2001–2002. Refer to Chapter 6 for
more details on using SDT Connector for Telnet and SSH access to devices that are attached to the console server serial ports.
You can also use standard communications packages like PuTTY to set a direct Telnet (or SSH) connection to the serial ports (refer to the Note
below).
NOTE: PuTTY also supports Telnet (and SSH), and the procedure to set up a Telnet session is simple. Enter the console server’s IP address as the
“Host Name (or IP address).” Select “Telnet” as the protocol and set the “TCP port” to 2000 plus the physical serial port number (that is,
2001 to 2002).
Click the “Open” button. You may then receive a “Security Alert” that the host‘s key is not cached. Choose “yes” to continue. You will
then be presented with the login prompt of the remote system connected to the serial port chosen on the console server. Login as normal
and use th e host serial console screen.
724-746-5500 | blackbox.com
29
Page 30

1101 and 1102 Secure Device Servers
Figure 5-6. PuTTY Configuration screen.
PuTTY can be downloaded at http://www.tucows.com/preview/195286.html
SSH: We recommend that you use SSH as the protocol where the User or Administrator connects to the console server (or connects through the
console server to the attached serial consoles) over the Internet or any other public network. This will provide authenticated SSH communications
between the SSH client program on the remote user’s computer and the console server, so the user’s communication with the serial device attached
to the console server is secure.
For SSH access to the consoles on devices attached to the console server serial ports, you can use SDT Connector. Configure SDT Connector with
the console server as a gateway, then as a host, and enable SSH service on Port (3000 + serial port #) i.e. 3001-3002. Chapter 6—Secure Tunneling
has more information on using SDT Connector for SSH access to devices that are attached to the console server serial ports.
You can also use common communications packages, like PuTTY or SSHTerm to SSH connect directly to port address IP Address _ Port (3000 +
serial port #), for example, 3001–3002.
SSH connections can be configured using the standard SSH port 22. Identify the the serial port that’s accessed by appending a descriptor to the
username. This syntax supports:
<username>:<portXX>
<username>:<port label>
<username>:<ttySX>
<username>:<serial>
For a User named “fred” to access serial port 2, when setting up the SSHTerm or the PuTTY SSH client, instead of typing username = fred and ssh
port = 3002, the alternate is to type username = fred:port02 (or username = fred:ttyS1) and ssh port = 22.
Or, by typing username=fred:serial and ssh port = 22. A port selection option appears to the User:
This syntax enables Users to set up SSH tunnels to all serial ports with only opening a single IP port 22 in their firewall/gateway.
30
724-746-5500 | blackbox.com
Figure 5-7. Port Selection option.
Page 31
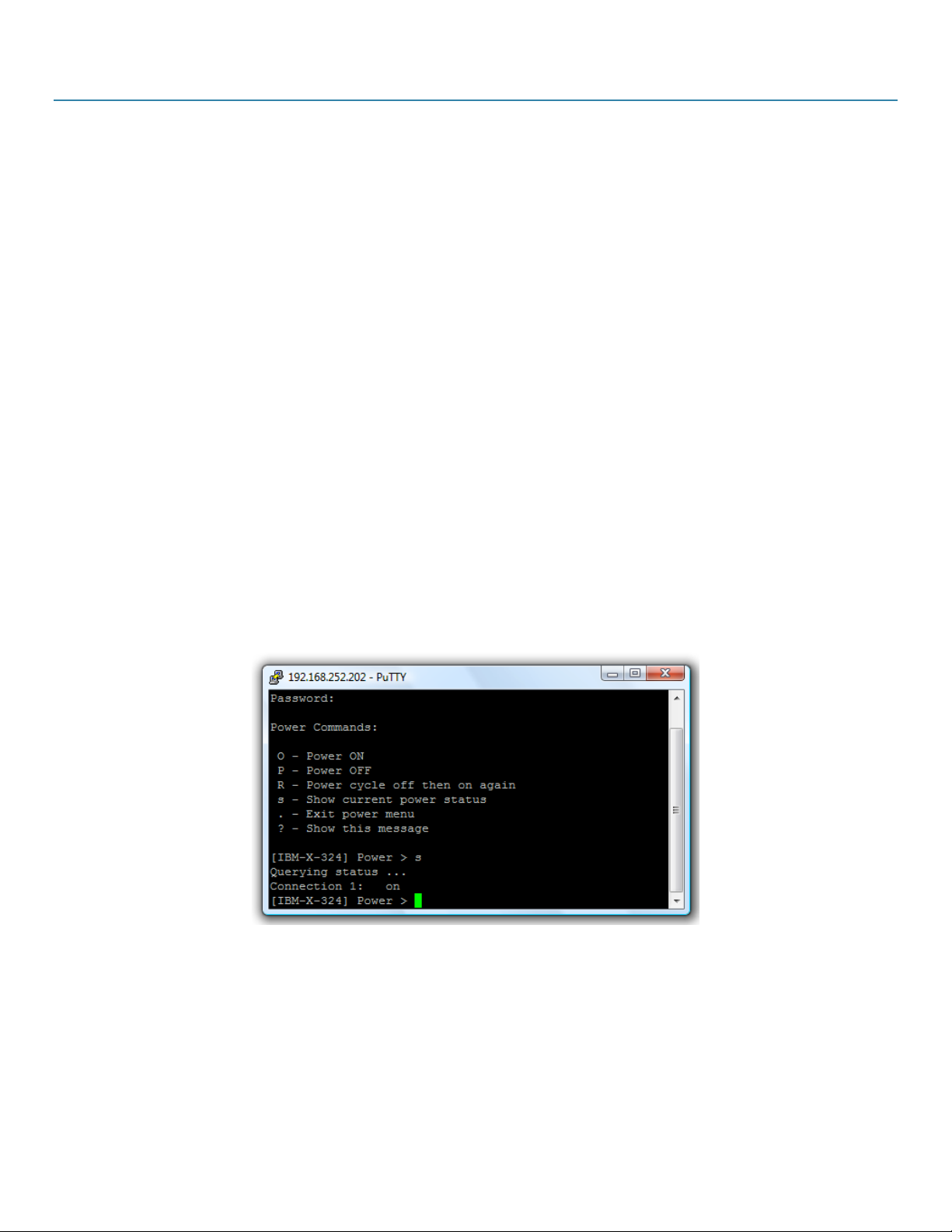
Chapter 5: Serial Port, Host, Device, and User Configuration
TCP: RAW TCP allows connections directly to a TCP socket. Communications programs like PuTTY also support RAW TCP. You would usually access
this protocol via a custom application.
For RAW TCP, the default port address is IP Address _ Port (4000 + serial port #) for example, 4001–4002.
RAW TCP also enables the serial port to be tunneled to a remote console server, so two serial port devices can transparently interconnect over a
network (see Chapter 5.1.6—Serial Bridging).
RFC2217 Selecting RFC2217 enables serial port redirection on that port. For RFC2217, the default port address is IP Address _ Port (5000 + serial
port #), that is, 5001– 5002.
Special client software is available for Windows UNIX and Linux that supports RFC2217 virtual com ports, so a remote host can monitor and
manage remote serially attached devices, as though they were connected to the local serial port (see Chapter 5.6—Serial Port Redirection for
details).
RFC2217 also enables the serial port to be tunneled to a remote console server, so two serial port devices can transparently interconnect over a
network (see Chapter 5.1.6—Serial Bridging).
Unauthenticated Telnet: Selecting Unauthenticated Telnet enables telnet access to the serial port without requiring the user to provide credentials.
When a user accesses the console server to telnet to a serial port, he normally is given a login prompt. With unauthenticated telnet, the user
connects directly through to a port with any console server login. This mode is mainly used when you have an external system (such as conserver)
managing user authentication and access privileges at the serial device level.
For Unauthenticated Telnet, the default port address is IP Address _ Port (6000 + serial port #) i.e. 6001 – 6002.
Accumulation Period: By default, once a connection is established for a particular serial port (such as a RFC2217 redirection or Telnet connection to
a remote computer) then any incoming characters on that port are forwarded over the network on a character by character basis. The accumulation
period changes this by specifying a period of time that incoming characters will be collected before then being sent as a packet over the network.
Escape Character: This enables you to change the character used for sending escape characters. The default is ~.
Power Menu: This setting enables the shell power command. A user can control the power connection to a Managed Device from command line
when he is connected to the device via telnet or ssh. To operate, the Managed Device must be set up with both its Serial port connection and
Power connection configured. The command to bring up the power menu is ~p
Figure 5-8. PuTTY screen.
Single Connection: This setting limits the port to a single connection> If multiple users have access privileges for a particular port, only one user at a
time can access that port (that is, port “snooping” is not permitted).
5.1.3 SDT Mode
This setting allows port forwarding of RDP, VNC, HTPP, HTTPS, SSH, Telnet, and other LAN protocols through to computers that are locally
connected to the console server by their serial COM port. Port forwarding requires that you set up a PPP link over this serial port.
724-746-5500 | blackbox.com
31
Page 32

1101 and 1102 Secure Device Servers
Figure 5-9. SDT settings.
For configuration details, refer to Chapter 6.4—Using SDT Connector to Telnet or SSH connect to devices that are serially attached to the console
server.
5.1.4 Device (RPC, UPS, EMD) Mode
This mode configures the selected serial port to communicate with a serial controlled Uninterruptable Power Supply (UPS), Remote Power
Controller/Power Distribution Unit (RPC) or Environmental Monitoring Device (EMD).
Figure 5-10. Device settings screen.
Select the desired Device Type (UPS, RPC or EMD)
Proceed to the appropriate device configuration page (Serial & Network: UPS Connections, RPC Connection or Environmental) as detailed in
Chapter 8—Power Management.
5.1.5 Terminal Server Mode
Select Terminal Server Mode and the Terminal Type (vt220, vt102, vt100, Linux, or ANSI) to enable a getty on the selected serial port.
Figure 5-11. Terminal server settings screen.
The getty will then configure the port and wait for a connection to be made. An active connection on a serial device is usually indicated by the Data
Carrier Detect (DCD) pin on the serial device being raised. When a connection is detected, the getty program issues a login: prompt, and then
invokes the login program to handle the actual system login.
NOTE: Selecting Terminal Server mode will disable Port Manager for that serial port, so data is no longer logged for alerts, etc.
5.1.6 Serial Bridging Mode
With serial bridging, the serial data on a nominated serial port on one console server is encapsulated into network packets and then transported
over a network to a second console server. It is then represented on its serial port again as serial data. The two console servers effectively act as a
virtual serial cable over an IP network.
One console server is configured as the Server. Set the Server serial port to be bridged in Console Server mode with either RFC2217 or RAW
enabled (as described in Chapter 5.1.2—Console Server Mode).
For the Client console server, the serial port to bridge must be set in Bridging Mode:
32
724-746-5500 | blackbox.com
Page 33

Chapter 5: Serial Port, Host, Device, and User Configuration
Figure 5-12. Serial bridge settings.
Select Serial Bridging Mode and specify the IP address of the Server console server and the TCP port address of the remote serial port (for RFC2217
bridging this will be 5001–5002).
By default, the bridging client will use RAW TCP. Select RFC2217 if this is the console server mode you have specified on the server console server.
LES1102A
COM port
connected control
PC
Figure 5-13. Serial bridging mode application.
You may secure the communications over the local Ethernet by enabling SSH. You will need to generate and upload keys (refer to Chapter 15—
Advanced Configuration).
Local Ethernet LAN
LES1102A
Serially connected device
(for example, security
appliance)
5.1.7 Syslog
In addition to built-in logging and monitoring (which can be applied to serial-attached and network-attached management accesses, as covered in
Chapter 7—Alerts and Logging), you can also configure the console server to support the remote syslog protocol on a per serial port basis:
Select the Syslog Facility/Priority fields to enable logging of traffic on the selected serial port to a syslog server; and to appropriately sort and action
those logged messages (that is, redirect them/send alert email etc.).
Figure 5-14. Syslog setting screen.
For example, if the computer attached to serial port 3 should never send anything out on its serial console port, the Administrator can set the Facility
for that port to local0 (local0 .. local1 are for site local values), and the Priority to critical. At this priority, if the console server syslog server does
receive a message, it will automatically raise an alert. Refer to Chapter 7—Alerts and Logging.
724-746-5500 | blackbox.com
33
Page 34

1101 and 1102 Secure Device Servers
5.2 Add/ Edit Users
The Administrator uses this menu selection to set up, edit, and delete users, and to define the access permissions for each of these users.
Figure 5-15. Users and Groups screen.
Users can be authorized to access specified console server serial ports and specified network-attached hosts. These users can also be given full
Administrator status (with full configuration and management and access privileges).
To simplify user set up, they can be configured as members of Groups. There are two Groups set up by default (admin and user).
1. Members of the admin group have full Administrator privileges. The admin user (Administrator) can access the console server using any of
the services that are enabled in System: Services. For example, if only HTTPS has been enabled, then the Administrator can only access
the console server using HTTPS. Once logged in, they can reconfigure the console server settings (for example, to enabled HTTP/Telnet for
future access). They can also access any of the connected Hosts or serial port devices using any of the services that have been enabled
for these connections. The Administrator can reconfigure the access services for any Host or serial port. Only trusted users should have
Administrator access.
NOTE: For convenience, the SDT Connector “Retrieve Hosts” function retrieves and auto-configures checked serial ports and checked hosts only,
even for admin group users.
2. Members of the user group have limited access to the console server and connected Hosts and serial devices. These Users can access only
the Management section of the Management Console menu and they have no command line access to the console server. They also can
only access those Hosts and serial devices that are checked for them, using services that are enabled.
3. The Administrator can also set up additional Groups with specific serial port and host access permissions (same as Users). However, users
in these additional groups don’t have any access to the Management Console menu or any command line access to the console server
itself. Finally, the Administrator can also set up users who are not a member of any Groups. They will have the same access as users in
the additional groups.
To set up new Groups and new users, and to classify users as members of particular Groups:
Select Serial & Network: Users & Groups to display the configured Groups and Users.
Click Add Group to add a new Group.
Add a Group name and Description for each new Group, then nominate the Accessible Hosts, Accessible Ports, and Accessible RPC Outlets(s) that
you want any users in this new Group to be able to access.
Click Apply.
34
724-746-5500 | blackbox.com
Page 35

Chapter 5: Serial Port, Host, Device, and User Configuration
Figure 5-16. Add a new user screen.
Click Add User to add a new user.
Add a Username and a confirmed Password for each new user. You may also include information related to the user (for example, contact details)
in the Description field.
NOTE: The User Name can contain from 1 to 127 alphanumeric characters (you can also use the special characters “-”, “_”, and “.” ).
There are no restrictions on the characters that you can use in the user Password (each can contain up to 254 characters). Only the first
eight Password characters are used to make the password hash.
Specify which Group (or Groups) you want the user to join.
Check specific Accessible Hosts and/or Accessible Ports to nominate the serial ports and network connected hosts you want the user to have access
privileges to.
If there are configured RPCs, you can check Accessible RPC Outlets to specify which outlets the user is able to control (that is, Power On/Off).
Click Apply. The new user can now access the Network Devices, Ports, and RPC Outlets you nominated as accessible. Plus, if the user is a Group
member, he can also access any other device/port/outlet that was set up as accessible to the Group.
NOTE: There are no specific limits on the number of users you can set up, nor on the number of users per serial port or host. Multiple
users (Users and Administrators) can control/monitor one port or host.
There are no specific limits on the number of Groups. Each user can be a member of a number of Groups (they take on the cumulative
access privileges of each of those Groups). A user does not have to be a member of any Groups (but if the User is not even a member of
the default user group. then he will not be able to use the Management Console to manage ports).
The time allowed to re-configure increases as the number and complexity increases. We recommend that you keep the aggregate
number of users and groups under 250.
The Administrator can also edit the access settings for any existing users:
Select Serial & Netwo rk: Users & Groups and click Edit for the User to be modified.
NOTE: For more information on enabling the SDT Connector so each user has secure tunneled remote RPD/VNC/Telnet/HHTP/HTTPS/SoL
access to the network connected hosts, refer to Chapter 6.
724-746-5500 | blackbox.com
35
Page 36

1101 and 1102 Secure Device Servers
5.3 Authentication
Refer to Chapter 9.1—Authentication Configuration for authentication configuration details.
5.4 Network Hosts
To access a locally networked computer or device (referred to as a Host), you must identify the Host and specify the TCP or UDP ports/services that
will be used to control that Host.
Selecting Serial & Network: Network Hosts presents all the network connected Hosts that have been enabled for access, and the related access TCP
ports/services.
Click Add Host to enable access to a new Host (or select Edit to update the settings for an existing Host).
Figure 5-17. Network hosts screen.
Enter the IP Address or DNS Name and a Host Name (up to 254 alphanumeric characters) for the new network connected Host (and optionally
enter a Description).
Add or edit the Permitted Services (or TCP/UDP port numbers) that are authorized to be used in controlling this host. Only these permitted services
will be forwarded through by SDT to the Host. All other services (TCP/UDP ports) will be blocked.
The Logging Level specifies the level of information to be logged and monitored for each Host access (refer to Chapter 7—Alerts and Logging).
If the Host is a PDU or UPS power device or a server with IPMI power control, then specify RPC (for IPMI and PDU) or UPS and the Device Type. The
Administrator can then configure these devices and enable which users have permission to remotely cycle power, etc. (refer to Chapter 8).
Otherwise, leave the Device Type set to None.
If the console server has been configured with distributed Nagios monitoring enabled, then you will also be presented with Nagios Settings options
to enable nominated services on the Host to be monitored (refer to Chapter 10—Nagios Integration).
Click Apply. This will create the new Host and also create a new Managed Device (with the same name).
36
724-746-5500 | blackbox.com
Page 37

Chapter 5: Serial Port, Host, Device, and User Configuration
5.5 Trusted Networks
The Trusted Networks facility gives you an option to nominate specific IP addresses where users (Administrators and Users) must be located to
access console server serial ports.
Select Serial & Network: Trusted Networks. To add a new trusted network, select Add Rule.
Figure 5-18. Trusted networks screen.
Select the Accessible Port(s) that the new rule is to be applied to.
Then, enter th e Network Address of the subnet to be permitted access.
Then, specify the range of addresses that are to be permitted by entering a Network Mask for that permitted IP range, for example:
To permit all the users located with a particular Class C network (for example, 204.15.5.0) connection to the nominated port then you would add
the following Trusted Network New Rule:
Network Address 204.15.5.0
Network Mask 255.255.255.0
If you want to permit only the one user who is located at a specific IP address (for example, 204.15.5.13 say) to connect:
Network Address 204.15.5.0
Network Mask 255.255.255.255
If, however, you want to allow all the users operating from within a specific range of IP addresses (for example, any of the thirty addresses from
204.15.5.129 to 204.15.5.158) to be permitted connection to the nominated port:
Host /Subnet Address 204.15.5.128
Subnet Mask 255.255.255.224
Click Apply.
.
NOTE: The above Trusted Networks will limit Users and Administrators access to the console serial ports. They do not restrict access to the
console server itself or to attached hosts. To change the default settings for this access, you will to need to edit the IPtables rules as
described in Chapter 15—Advanced Configuration.
5.6 Serial Port Redirection
To allow an application on a client PC to access the virtual serial ports on the console server, you need to run client software (to redirect the local
serial port traffic to remote console server serial port).
There’s a selection of commercial software available including Serial to Ethernet from Eltima (www.eltima.com
Redirector from Tactical Software
(www.tacticalsoftware.com/products/serialip.htm).
724-746-5500 | blackbox.com
) and Serial/IP™ COM Port
37
Page 38

1101 and 1102 Secure Device Servers
Serial device
applications
Serial/IP
redirector virtual
COM ports
Figure 5-19. Serial Port redirection.
This serial port redirector software is loaded in your desktop PC, and it allows you to use a serial device that’s connected to the remote console
server as if it were connected to your local serial port.
5.7 Managed Devices
Managed Devices presents a consolidated view of all the connections to a device that you can access and monitor through the console server. To
view the connections to the devices:
Select Serial & Network: Managed Devices.
LES1102A
LES1101A
LES1102A
Remote Serial
Device servers
Retail data
systems
Building
automation
systems
Controllers
Sensors
Figure 5-20. Managed Devices screen.
This screen displays all the Managed Devices with their Description/Notes. It also lists all the configured Connections, that is, Serial Port # (if serially
connected) or USB if USB connected; IP Address (if network connected); Power PDU/outlet details (if applicable), and any UPS connections. Devices
such as servers will commonly have more than one power connection (for example, dual power supplied) and more than one network connection
(for example, for BMC/service processor).
All Users can view (but not edit) these Managed Device connections by selecting Manage: Devices. The Administrator user can edit and add/delete
these Managed Devices and their connections.
To edit an existing device and add a new connection:
• Select Edit on the Serial & Network: Managed Devices and click Add Connection.
38
724-746-5500 | blackbox.com
Page 39

Chapter 5: Serial Port, Host, Device, and User Configuration
• Select the connection type for the new connection (Serial, Network Host, UPS, or RPC) and then select the specific connection from the
presented list of configured unallocated hosts/ports/outlets.
To add a new network-connected Managed Device:
The Administrator adds a new network-connected Managed Device using Add Host on the Serial & Network: Network Host menu. This
automatically creates a corresponding new Managed Device (as covered in Section 5.4—Network Hosts).
When adding a new network-connected RPC or UPS power device, you set up a Network Host, designate it as RPC or UPS, then go to RPC
Connections (or UPS Connections) to configure the relevant connection. A corresponding new Managed Device (with the same Name /Description
as the RPC/UPS Host) is not created until you complete this connection step (refer Chapter 8—Power Management).
NOTE: The outlet names on this newly created PDU will by default be “Outlet 1” and “Outlet 2.” When you connect a particular Managed
To add a new serially connected Managed Device:
• Configure the serial port using the Serial & Network: Serial Port menu (refer to Section 5.1—Configure Serial Port).
• Select Serial & Network: Managed Devices and click Add Device.
• Enter a Device Name and Description for the Managed Device.
Device (that draws power from the outlet), then the outlet will take the powered Managed Device’s name.
Figure 5-21. Add a new device screen.
• Click Add Connection and select Serial and the Port that connects to the Managed Device.
• To add a UPS/RPC power connection or network connection or another serial connection, click Add Connection.
• Click Apply.
NOTE: To set up a new serially connected RPC UPS or EMD device, config ure the serial port, design ate it as a Device, then enter a Name and
Description for that device in the Serial & Network: RPC Connections (or UPS Connections or Environmental). When applied, this will
automatically create a corresponding new Managed Device with the same Name /Description as the RPC/UPS Host (refer to Chapter 8—
Power Management).
All the outlet names on the PDU will by default be “Outlet 1” and “Outlet 2.” When you connect a particular Managed Device (that
draws power from the outlet), then the outlet will take the name of the powered Managed Device.
724-746-5500 | blackbox.com
39
Page 40

1101 and 1102 Secure Device Servers
6. Secure SSH Tunneling and SDT Connector
Each Black Box console server has an embedded SSH server and uses SSH tunneling so remote users can securely connect through the console
server to Managed Devices—using text-based console tools (such as SSH, telnet, SoL) or graphical tools (such VNC, RDP, HTTPS, HTTP, X11,
VMware, DRAC, iLO).
The Managed Devices you access can be located on the same local network as the console server or they can be attached to the console server via a
serial port. The remote User/Administrator connects to the console server thru an SSH tunnel via dial-up, wireless or ISDN modem; a broadband
Internet connection; the enterprise VPN network; or the local network.
Secure Local
Management
LES1102A
Secure Remote
Management
Serial
connected
Figure 6-1. Secure network.
To set up the secure SSH tunnel from the client PC to the console server, install and launch SSH client software on the User/Administrator’s PC,
Black Box recommends that you use the SDT Connector client software supplied with the console server. SDT Connector is simple to install and
auto-configure and it provides all your users with point-and-click access to all the systems and devices in the secure network. With one click, SDT
Connector sets up a secure SSH tunnel from the client to the selected console server, then establishes a port forward connection to the target
network connected host or serial connected device. Next, it executes the client application that it uses in communicating with the host.
This chapter details the basic SDT Connector operations:
• Configuring the console server for SSH tunneled access to network attached hosts and setting up permitted Services and user access
(Section 6.1).
• Setting up the SDT Connector client with gateway, host, service, and client application details, and making connections between the
Client PC and hosts connected to the console server (Section 6.2).
• Using SDT Connector to access the Management Console via a browser (Section 6.3).
• Using SDT Connector to Telnet or SSH connect to devices that are serially attached to the console server (Section 6.4).
The chapter then covers more advanced SDT Connector and SSH tunneling topics:
• Using SDT Connector for out-of-band access (Section 6.5).
• Automatic importing and exporting configurations (Section 6.6).
• Configuring Public Key Authentication (Section 6.7).
• Setting up a SDT Secure Tunnel for Remote Desktop (Section 6.8).
• Setting up a SDT Secure Tunnel for VNC (Section 6.9).
40
724-746-5500 | blackbox.com
Page 41
Chapter 6: Secure SSH Tunneling and SDT Connector
• Using SDT to IP connect to hosts that are serially attached to the console server (Section 6.10).
6.1 Configuring for SSH Tunneling to Hosts
To set up the console server to SSH tunnel to access a network attached host:
Add the new host and the permitted services using the Serial & Network: Network Hosts menu as detailed in Network Hosts (Chapter 5.4). Only
these permitted services will be forwarded through by SSH to the host. All other services (TCP/UDP ports) will be blocked.
NOTE: Following are some of the TCP Ports used by SDT in the console server:
Add the new Users using Serial & Network: Users & Groups menu as detailed in Network Hosts (Chapter 5.4). Users can be authorized to access the
console server ports and specified network attached hosts. To simplify configuration, the Administrator can first set up Groups with group access
permissions, then Users can be classified as members of particular Groups.
6.2 SDT Connector Client Configuration
The SDT Connector client works with all Black Box console servers. Each of these remote console servers has an embedded OpenSSH based server
that you can configure to port forward connections from the SDT Connector client to hosts on their local network (as detailed in the previous
chapter). You can also pre-configure the SDT Connector with the access tools and applications that are available to run when you’ve established
access to a particular host.
SDT Connector can connect to the console server using an alternate OoB access. It can also access the console server itself and access devices
connected to serial ports on the console server.
6.2.1 SDT Connector installation
The SDT Connector set up program (SDTConnector Setup-1.n.exe or sdtcon-1.n.tar.gz) is included on the CD supplied with your Black Box console
server.
Run the set-up program.
22 SSH (All SDT Tunneled connections)
23 Telnet on local LAN (forwarded inside tunnel)
80 HTTP on local LAN (forwarded inside tunnel)
3389 RDP on local LAN (forwarded inside tunnel)
5900 VNC on local LAN (forwarded inside tunnel)
73XX RDP over serial from local LAN – where XX is the serial port number (that is, 7301 to 7302 on a 2-port console server)
79XX VNC over serial from local LAN – where XX is the serial port number
Figure 6-2. SDT connector setup window.
NOTE: For Windows clients, the SDTConnectorSetup-1.n.exe application will install the SDT Connector 1.n.exe and the config file
defaults.xml. If there is already a config file on the Windows PC, then it will not be overwritten. To remove an earlier config file, run the
regedit command and search for “SDT Connector,” then remove the directory with this name.
For Linux and other Unix clients, SDTConn ector.tar.gz application will install the sdtcon-1.n.jar and the con fig file defaults.xml.
724-746-5500 | blackbox.com
41
Page 42

1101 and 1102 Secure Device Servers
Once the installer completes you will have a working SDT Connector client installed on your machine and an icon on your desktop:
Figure 6-3. SDT connector icon.
Click the SDT Connector icon on your desktop to start the client.
NOTE: SDT Connector is a Java application, so it must have a Java Runtime Environment (JRE) installed. You can download this for free from
http://java.sun.com/j2se/. It installs on Windows 2000, XP, 2003, Vista, and 7 PCs and on most Linux platforms. Solaris platforms are also
supported, but they must have Firefox installed. SDT Connector can run on any system with Java 1.4.2 and above installed, but it assumes
the web browser is Firefox, and that xterm -e telnet opens a telnet window.
To operate SDT Connector, you first need to add new gateways to the client software by entering the access details for each console server (refer to
Section 6.2.2). Then, let the client auto-configure all host and serial port connections from each console server (refer to Section 6.2.3). Finally, pointand-click to connect to the Hosts and serial devices (refer to Section 6.2.4).
Or, you can manually add network connected hosts (refer to Section 6.2.5) and manually configure new services to use to access the console server
and the hosts (refer to Section 6.2.6). Then, manually configure clients to run on the PC that will use the service to connect to the hosts and serial
port devices (refer to Section 6.2.).
6.2.2 Configuring a New Console Server Gateway in the SDT Connector Client
To create a secure SSH tunnel to a new console server:
Click the New Gateway
Enter the IP or DNS Address of the console server and the SSH port that you will use (typically 22).
NOTE: If SDT Connector is connecting to a remote console server through the public Internet or routed network you will need to:
• Determine the public IP address of the console server (or of the router/ firewall that connects the console server to the Internet) as
assigned by the ISP. One way to find the public IP address is to access http://checkip.dyndns.org/ or http://www.whatismyip.com/ from a
computer on the same network as the console server and note the reported IP address.
• Set port forwarding for TCP port 22 through any firewall/NAT/router that is located between SDT Connector and the console server so it
points to the console server. http://www.portforward.com has port forwarding instructions for a range of routers. Also, you can use th e
Open Port Check tool from http://www.canyouseeme.org to check if port forwarding through local firewall/NAT/router devices has been
properly configured.
Enter the Username and Password of a user on the gateway that is enabled to connect via SSH and/or create SSH port redirections.
icon or select the File: New Gateway menu option.
Figure 6-4. New Gateway menu option.
42
724-746-5500 | blackbox.com
Page 43

Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-5. New SDT Gateway screen.
Or, enter a Descriptive Name to display instead of the IP or DNS address, and any Notes or a Description of this gateway (such as its firmware
version, site location, or anything special about its network configuration).
Click OK and an icon for the new gateway will now appear in the SDT Connector home page.
NOTE: For an SDT Connector user to access a console server (and then access specific hosts or serial devices connected to that console server),
that user must first be setup on the con sole server, and must be authorized to access the specific ports/hosts (refer to Chapter 6). Only
these permitted services will be forwarded through by SSH to the Host. All other services (TCP/UDP ports) will be blocked.
6.2.3 Auto-configure SDT Connector Client with the User’s Access Privileges
Each user on the console server has an access profile that was configured with those specific connected hosts and serial port devices the user has
authority to access, and a specific set of the enabled services for each of these. You can upload this configuration automatically into the SDT
Connector client:
Figure 6-6. Gateway actions.
Click on the new gateway icon and select Retrieve Hosts. This will:
• configure access to network connected Hosts that the user is authorized to access and set up (for each of these Hosts) the services (for
example, HTTPS, IPMI2.0) and the related IP ports being redirected.
• configure access to the console server itself (this is shown as a Local Services host).
• configure access with the enabled services for the serial port devices connected to the console server.
724-746-5500 | blackbox.com
43
Page 44

1101 and 1102 Secure Device Servers
Figure 6-7. Hosts.
NOTE: The Retrieve Hosts function will auto-configure all user classes (that is, they can be members of user or admin or some other group or no
group. SDT Connector will not auto-configure the root (and we recommend that you only use this account for initial config and to add an
initial admin account to the console server).
6.2.4 Make an SDT Connection through the Gateway to a Host
Simply point at the host to be accessed and click on the service to use to access that host. The SSH tunnel to the gateway is then automatically
established, the appropriate ports redirected through to the host, and the appropriate local client application is launched pointing at the local
endpoint of the redirection.
Figure 6-8. Services.
NOTE: You can configure the SDT Connector client with an unlimited number of Gateways (that is, console servers). You can configure each
Gateway to port forward to an unlimited number of locally networked Hosts. There is no limit on the number of SDT Connector clients
that can be configured to access the one Gateway. Nor are there limits on the number of Host connections that an SDT Connector client
can concurrently have open through the one Gateway tunnel.
There is a limit on the number of SDT Connector SSH tunnels that can be open at the same time on a particular Gateway (console
server). Each Gateway (console server) can support at least 50 such concurrent connections. At any time, you could have up to 50 users
securely controlling an unlimited number of Managed Devices at a remote site through the on-site console server Gateway.
6.2.5 Manually Adding Hosts to the SDT Connector Gateway
For each gateway, you can manually specify the network connected hosts that you will access through that console server; and for each host,
specify the services that you will use to communicate with the host.
Select the newly added gateway and click the Host icon
New Host).
44
724-746-5500 | blackbox.com
to create a host that will be accessible via this gateway. (Alternatively, select File:
Page 45
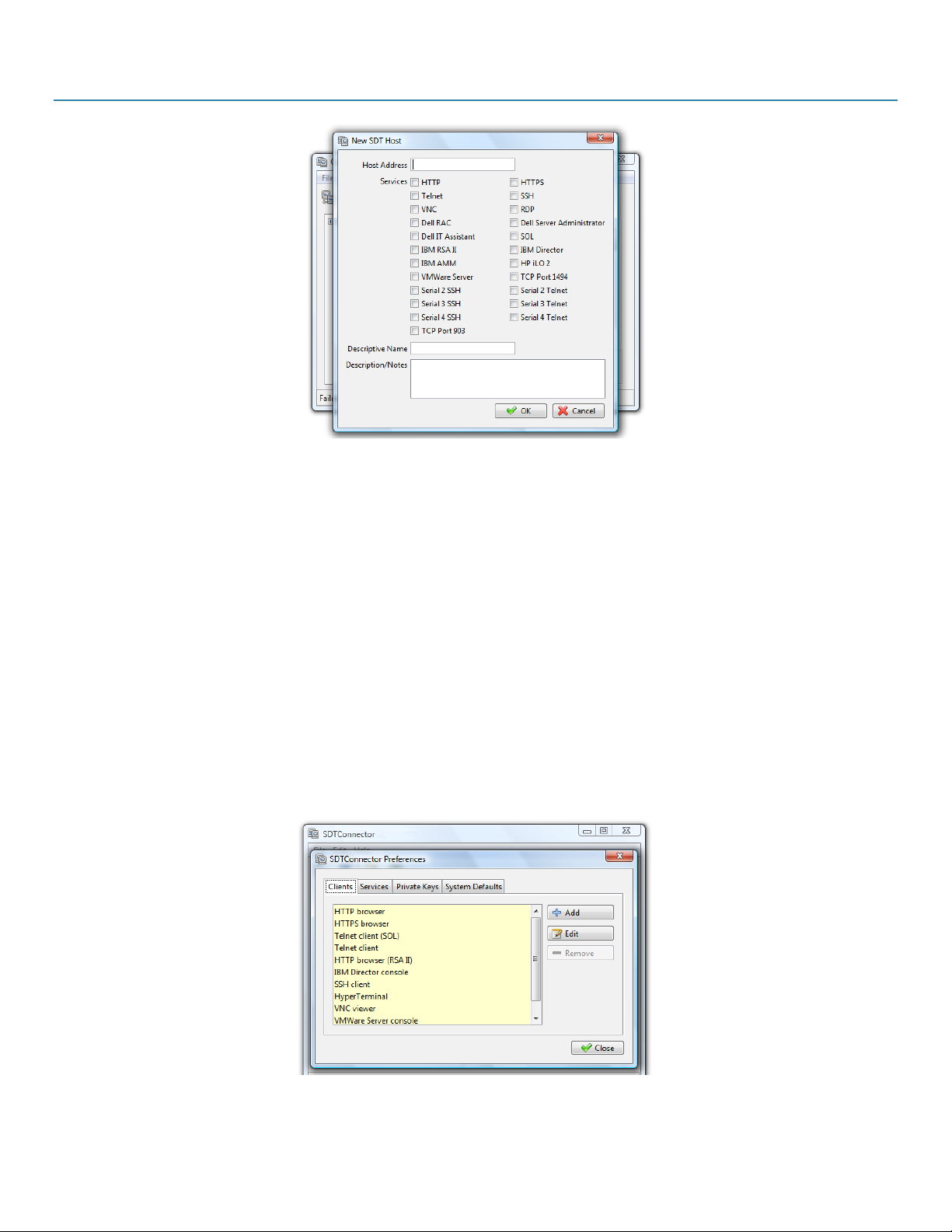
Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-9. New SDT Host screen.
Enter the IP or DNS Host Address of the host (if this is a DNS address, it must be able to be resolved by the gateway).
Select which Services to use to access the new host. A range of service options are pre-configured in the default SDT Connector client (RDP, VNC,
HTTP, HTTPS, Dell RAC, VMware, etc.). If you want to add new services to the range, then proceed to the next section (Adding a new service) then
return here.
Or, enter a Descriptive Name for the host to display instead of the IP or DNS address, and any Notes or a Description of this host (such as its
operating system/release, or anything special about its configuration).
Click OK.
6.2.6 Manually Adding New Services to the New Hosts
To extend the range of services that you can use when accessing hosts with SDT Connector:
Select Edit: Preferences and click the Services tab. Click Add.
Enter a Service Name and click Add.
Under the General tab, enter the TCP Port that this service runs on (for example, 80 for HTTP). Or, select the client to use to access the local
endpoint of the redirection.
Figure 6-10. Clients.
724-746-5500 | blackbox.com
45
Page 46

1101 and 1102 Secure Device Servers
Select which Client application is associated with the new service. A range of client application options are pre-configured in the default SDT
Connector (RDP client, VNC client, HTTP browser, HTTPS browser, Telnet client, etc.). If you want to add new client applications to this range,
proceed to the next section (Adding a new client), then return here.
Figure 6-11. Select client.
Click OK, then Close.
A service typically consists of a single SSH port redirection and a local client to access it. It may consist of several redirections, and some or all may
have clients associated with them.
An example is the Dell RAC service. The first redirection is for the HTTPS connection to the RAC server— it has a client associated with it (web
browser) that it launches immediately when you click the button for this service.
The second redirection is for the VNC service that you may choose to later launch from the RAC web console. It automatically loads in a Java client
served through the web browser, so it does not need to have a local client associated with it.
Figure 6-12. Edit Service.
On the Add Service screen, you can click Add as many times as needed to add multiple new port redirections and associated clients.
You may also specify Advanced port redirection options:
Enter the local address to bind to when creating the local endpoint of the redirection. It is not usually necessary to change this from “localhost.”
Enter a local TCP port to bind to when creating the local endpoint of the redirection. If you leave this blank, a random port is selected.
46
724-746-5500 | blackbox.com
Page 47

Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-13. Edit port redirection.
NOTES: SDT Connector can also tunnel UDP services. SDT Connector tunnels the UDP traffic through the TCP SSH redirection, so it is a “tunnel
within a tunnel.”
Enter the UDP port where the service is running on the host. This will also be the local UDP port that SDT Connector binds as the
local endpoint of the tunnel.
For UDP services, you still need to specify a TCP port under General. This will be an arbitrary TCP port that is not in use on the
gateway. An example of this is the SOL Proxy service. It redirects local UDP port 623 to remote UDP port 623 over the arbitrary TCP port
6667.
6.2.7 Adding a Client Program to be Started for the New Service
Clients are local applications that you may launch when a related service is clicked. To add to the pool of client programs:
Select Edit: Preferences and click the Client tab. Click Add.
Figure 6-14. Add Client screen.
Enter a Name for the client. Enter the Path to the executable file for the client (or click Browse to locate the executable).
724-746-5500 | blackbox.com
47
Page 48

1101 and 1102 Secure Device Servers
Enter a Command Line associated with launching the client application. SDT Connector typically launches a client using command line arguments to
point it at the local endpoint of the redirection. There are three special keywords for specifying the command line format. When launching the
client, SDT Connector substitutes these keywords with the appropriate values:
%path% is path to the executable file, that is, the previous field.
%host% is the local address to which the local endpoint of the redirection is bound, that is, the Local Address field for the Service redirection
Advanced options.
%port% is the local port to which the local endpoint of the redirection is bound, that is, the Local TCP Port field for the Service redirection
Advanced options. If this port is unspecified (that is, “Any”), the appropriate randomly selected port will be substituted.
For example SDT Connector is preconfigured for Windows installations with a HTTP service client that will connect with the local browser that the
local Windows user has configured as the default. Otherwise, the default browser used is Firefox.
Figure 6-15. HTTP browser client.
Also some clients are launched in a command line or terminal window. The Telnet client is an example of this so the “Path to client executable file”
is telnet and the “Command line format for client executable” is cmd /c start %path% %host% %port%.
Figure 6-16. Telnet client.
Click OK.
48
724-746-5500 | blackbox.com
Page 49

Chapter 6: Secure SSH Tunneling and SDT Connector
6.3 SDT Connector to Management Console
You can also configure SDT Connector for browser access to the console server’s Management Console —and for Telnet or SSH access to the
command line. For these connections to the console server itself, you must configure SDT Connector to access the Gateway itself by setting the
Gateway (console server) up as a host, and then configuring the appropriate services:
Launch SDT Connector on your PC. Assuming you have already set up the console server as a Gateway in your SDT Connector client (with
username/ password etc.), select this newly added Gateway and click the Host icon to create a host. Or, select File -> New Host.
Enter 127.0.0.1 as the Host Address and provide details in Descriptive Name/Notes. Click OK.
Figure 6-17. Edit SDT host screen.
Click the HTTP or HTTPS Services icon to access the Management Console, and/or click SSH or Telnet to access the command line console.
NOTES: To enable SDT access to the console, you must also configure the console server to allow the port forwarded network access to
itself:
Browse to the console server and select Network Hosts from Serial & Network, click Add Host, and in the IP Address/DNS Name field enter
127.0.0.1 (this is the Black Box network loopback address). Then, enter Loopback in Description.
Remove all entries under Permitted Services except for those that you will use to access the Management Console (80/http or 443/https)
or the command line (22/ssh or 23/telnet). Scroll to the bottom and click Apply.
Administrators by default have gateway access privileges. For Users to access the console server Management Console, you will need to
give those Users the required access privileges. Select Users & Groups from Serial & Network. Click Add User. Enter a Username,
Description and Password/Confirm. Select 127.0.0.1 from Accessible Host(s) and click Apply.
6.4 SDT Connector—Telnet or SSH Connect to Serially Attached Devices
You can also use SDT Connector to access text consoles on devices that are attached to the console server serial ports. For these connections, you
must configure the SDT Connector client software with a Service that will access the target gateway serial port, and then set the gateway up as a
host:
Launch SDT Connector on your PC. Select Edit -> Preferences and click the Services tab. Click Add.
Enter "Serial Port 2" in Service Name and click Add.
Select Telnet client as the Client. Enter 2002 in TCP Port. Click OK, then Close and Close again.
724-746-5500 | blackbox.com
49
Page 50

1101 and 1102 Secure Device Servers
Figure 6-18. Add port redirection.
Assuming you have already set up the target console server as a gateway in your SDT Connector client (with username/password etc), select this
gateway and click the Host icon to create a host. Or, select File -> New Host.
Enter 127.0.0.1 as the Host Address and use Serial Port 2 for descriptive name. In Description/notes, enter something such as Loopback ports, or
Local serial ports. Click OK.
Click Serial Port 2 icon for Telnet access to the serial console on the device attached to serial port #2 on the gateway.
To enable SDT Connector to access the devices connected to the gateway’s serial ports, you must also configure the Console server itself to allow
port forwarded network access to itself, and enable access to the nominated serial port:
Browse to the Console server and select Serial Port from Serial & Network.
Click Edit next to selected Port # (for example, Port 2 if the target device is attached to the second serial port). Make sure the port’s serial
configuration is appropriate for the attached device.
Scroll down to Console server Setting and select Console server Mode. Check Telnet (or SSH) and scroll to the bottom and click Apply.
Select Network Hosts from Serial & Network and click Add Host.
In the IP Address/DNS Name field enter 127.0.0.1 (this is the Black Box network loopback address) and enter Loopback in Description.
Remove all entries under Permitted Services, select TCP, and enter 200n in Port. (This configures the Telnet port enabled in the previous step, so for
Port 2 you would enter 2002.)
Click Add, then scroll to the bottom and click Apply.
Administrators by default have gateway and serial port access privileges; however for Users to access the gateway and the serial port, you will need
to give those Users the required access privileges. Select Users & Groups from Serial & Network. Click Add User. Enter a Username, Description, and
Password/Confirm. Select 127.0.0.1 from Accessible Host(s) and select Port 2 from Accessible Port(s). Click Apply.
6.5 Using SDT Connector for Out-of-Band Connection to the Gateway
You can also set up SDT Connector to connect to the console server (gateway) out-of-band (OoB). OoB access uses an alternate path for connecting
to the gateway to that used for regular data traffic. OoB access is useful for when the primary link into the gateway is unavailable or unreliable.
Typically, a gateway’s primary link is a broadband Internet connection or Internet connection via a LAN or VPN, and the secondary out-of-band
connectivity is provided by a dial-up or wireless modem directly attached to the gateway. Out-of-band access enables you to access the hosts and
serial devices on the network, diagnose any connectivity issues, and restore the gateway's primary link.
In SDT Connector, to configure OoB access, you provide the secondary IP address of the gateway, and tell SDT Connector how to start and stop the
OoB connection. You can start an OoB connection by initiating a dial up connection, or adding an alternate route to the gateway. SDT Connector
allows for maximum flexibility. It allows you to provide your own scripts or commands for starting and stopping the OoB connection.
50
724-746-5500 | blackbox.com
Page 51

Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-19. Out-of-band access.
To con figure SDT Conn ector for OoB access:
When adding a new Gateway or editing an existing Gateway select the Out Of Band tab.
Enter the secondary, OoB IP address of the gateway (for example, the IP address it is using when dialed in directly). You also may modify the
gateway’s SSH port if it's not using the default of 22.
Enter the command or path to a script to start the OoB connection in Start Command.
To initiate a pre-configured dial-up connection under Windows, use the following Start Command:
cmd /c start "Starting Out of Band Connection" /wait /min rasdial network_connection login password
where network_connection is the name of the network connection as displayed in Control Panel -> Network Connections, login is the
dial-in username, and password is the dial-in password for the connection.
To initiate a pre-configured dial-up connection under Linux, use the following Start Command:
pon network_connection
where network_connection is the name of the connection.
Enter the command or path to a script to stop the OoB connection in Stop Command.
To stop a pre-configured dial-up connection under Windows, use the following Stop Command:
cmd /c start "Stopping Out of Band Connection" /wait /min rasdial network_connection /disconnect
where network connection is the name of the network connection as displayed in Control Panel -> Network Connections.
To stop a pre-configured dial-up connection under Linux, use the following Stop Command:
poff network_connection
To make the OoB connection using SDT Connector:
Select the console server and click Out Of Band. The status bar will change color to indicate that this console server is now accessed using the OoB
link rather than the primary link.
724-746-5500 | blackbox.com
51
Page 52

1101 and 1102 Secure Device Servers
Figure 6-20. OoB connection using SDT connector.
When you connect to a service on a host behind the console server, or to the console server itself, SDT Connector will initiate the OoB connection
using the provided Start Command. The OoB connection does not stop (using the provided Stop Command) until you click off Out Of Band under
Gateway Actions; then the status bar will return to its normal color.
6.6 Importing (and Exporting) Preferences
To enable the distribution of pre-configured client config files, SDT Connector has an Export/Import facility:
• To save a configuration.xml file (for backup or for importing into other SDT Connector clients), select File -> Export Preferences and select the
location where you want to save the configuration file.
• To import a configuration, select File -> Import Preferences and select the .xml configuration file to install.
Figure 6-21. Import preferences option.
6.7 SDT Connector Public Key Authentication
SDT Connector can authenticate against an SSH gateway using your SSH key pair instead of requiring you to enter your password. This is known as
public key authentication.
To use public key authentication with SDT Connector, first you must add the public part of your SSH key pair to your SSH gateway:
Make sure the SSH gateway allows public key authentication, this is typically the default behavior.
If you do not already have a public/private key pair for your client PC (the one running SDT Connector), generate them now using ssh-keygen,
PuTTYgen or a similar tool. You may use RSA or DSA; however, leave the passphrase field blank:
Upload the public part of your SSH key pair (this file is typically named id_rsa.pub or id_dsa.pub) to the SSH gateway, or otherwise add to
.ssh/authorized keys in your home directory on the SSH gateway.
Next, add the private part of your SSH key pair (this file is typically named id_rsa or id_dsa) to SDT Connector. Click Edit -> Preferences -> Private
Keys -> Add, locate the private key file, and click OK.
You do not have to add the public part of your SSH key pair, the private key calculates it.
52
PuTTYgen: http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
OpenSSH: http://www.openssh.org/
OpenSSH (Windows): http://sshwindows.sourceforge.net/download/
724-746-5500 | blackbox.com
Page 53

Chapter 6: Secure SSH Tunneling and SDT Connector
SDT Connector will now use public key authentication when connecting through the SSH gateway (console server). You may have to restart SDT
Connector to shut down any existing tunnels that were established using password authentication.
If you have a host behind the console server that you connect to by clicking the SSH button in SDT Connector, you may also want to configure
access to it for public key authentication as well. This configuration is entirely independent of SDT Connector and the SSH gateway. You must
configure the SSH client that SDT Connector launches (for example, Putty, OpenSSH) and the host’s SSH server for public key authentication.
Essentially what you are using is SSH over SSH, and the two SSH connections are entirely separate.
6.8 Setting up SDT for Remote Desktop Access
The Microsoft Remote Desktop Protocol (RDP) enables the system manager to securely access and manage remote Windows computers—to
reconfigure applications and user profiles, upgrade the server’s operating system, reboot the machine, etc. Black Box’s Secure Tunneling uses SSH
tunneling, so this RDP traffic is securely transferred through an authenticated and encrypted tunnel.
SDT with RDP also allows remote Users to connect to Windows XP, Vista, Server2003, and Server 2008 computers and to Windows 2000 Terminal
Servers; and to access to all of the applications, files, and network resources (with full graphical interface just as though they were in front of the
computer screen at work). To set up a secure Remote Desktop connection, enable Remote Desktop on the target Windows computer that you
want to access and configure the RPD client software on the client PC.
6.8.1 Enable Remote Desktop on the Target Windows Computer to be Accessed
To enable Remote Desktop on the Windows computer being accessed:
Open System in the Control Panel and click the Remote tab.
Figure 6-22. System Properties screen.
Check Allow users to connect remotely to this computer.
Click Select Remote Users.
724-746-5500 | blackbox.com
53
Page 54

1101 and 1102 Secure Device Servers
Figure 6-23. Remote Desktop Users dialog box.
To set the user(s) who can remotely access the system with RDP, click Add on the Remote Desktop Users dialog box.
NOTE: If you need to set up new users for Remote Desktop access, open User Accounts in the Control Panel and follow the steps to nominate
the new user’s name, password, and account type (Administrator or Limited).
NOTE: With Windows XP Professional and Vista, you have only one Remote Desktop session and it connects directly to the Windows root
console. With Windows Server 2008, you can have multiple sessions (and with Server 2003 you have three sessions— the console session
and two other general sessions). More than one user can have active sessions on a single computer.
When the remote user connects to the accessed computer on the console session, Remote Desktop automatically locks that computer (no
other user can access the applications and files). When you come back to your computer at work, you can unlock it by typing
CTRL+ALT+DEL.
6.8.2 Configure the Remote Desktop Connection Client
Now that you have the Client PC securely connected to the console server (either locally, or remotely—through the enterprise VPN, or a secure SSH
internet tunnel, or a dial-in SSH tunnel), you can establish the Remote Desktop connection from the Client. Simply enable the Remote Desktop
Connection on the remote client PC, then point it to the SDT Secure Tunnel port in the console server:
On a Windows client PC:
Click Start. Point to Programs, then to Accessories, then Communications, and click Remote Desktop Connection.
54
724-746-5500 | blackbox.com
Figure 6-24. Remote Desktop Connection.
Page 55

Chapter 6: Secure SSH Tunneling and SDT Connector
In Computer, enter the appropriate IP Address and Port Numb er:
Where there is a direct local or enterprise VPN connection, enter the IP Address of the console server, and the Port Number of the SDT Secure
Tunnel for the console server serial port that you attach to the Windows computer you want to control. For example, if the Windows computer is
connected to serial Port 2 on a console server located at 192.168.0.50, then you would enter 192.168.0.50:7302.
Where there is an SSH tunnel (over a dial up PPP connection or over a public internet connection or private network connection), simply enter the
localhost as the IP address, 127.0.0.1. For Port Number, enter the source port you created when setting SSH tunneling /port forwarding (in Section
6.1), for example:1234.
Click Option. In the Display section, specify an appropriate color depth (for example, for a modem connection we recommend that you not use over
256 colors). In Local Resources, specify the peripherals on the remote Windows computer that are to be controlled (printer, serial port, etc.).
Figure 6-25. Remote Desktop Connection, General tab.
Click Connect.
NOTES: The Remote Desktop Connection software is pre-installed with Windows XP, Vista, and Server 2003/2008. For earlier Windows PCs, you
need to download the RDP client:
Go to the Microsoft Download Center site http://www.microsoft.com/downloads/details.aspx?familyid=80111F21-D48D-426E-96C208AA2BD23A49&displaylang=en and click the Download button
This software package will install the client portion of Remote Desktop on Windows 95, Windows 98 and 98 Second Edition, Windows
Me, Windows NT 4.0, and Windows 2000. When run, this software allows these older Windows platforms to remotely connect to a
computer running current Windows.
On a Linux or UNIX client PC:
Launch the open source rdesktop client:
rdesktop -u windows-user-id -p windows-password -g 1200x950 ms-windows-terminal-server-host-name
Option Description
-a Color depth: 8, 16, 24
-r Device redirection. (Redirect sound on remote machine to local device. -0 –r sound (MS/Windows 2003)
-g Geometry: width x height or 70% screen percentage
-p Use –p to receive password prompt
724-746-5500 | blackbox.com
55
Page 56

1101 and 1102 Secure Device Servers
You can use GUI front end tools like the GNOME Terminal Services Client tsclient to configure and launch the rdesktop client. (Using tsclient also
enables you to store multiple configurations of rdesktop for connection to many servers.)
Figure 6-26. RDP protocol.
NOTE: The rdesktop client is supplied with Red Hat 9.0:
rpm -ivh rdesktop-1.2.0-1.i386.rpm
For Red Hat 8.0 or other distributions of Linux; download source, untar, configure, make, make, then install.
rdesktop currently runs on most UNIX based platforms with the X Window System and can be downloaded from http://www.rdesktop.org/
On a Macintosh client:
Download Microsoft's free Remote Desktop Connection client for Mac OS X
http://www.microsoft.com/mac/otherproducts/otherproducts.aspx?pid=remotedesktopclientSDT SSH Tunnel for VNC
6.9 SDT SSH Tunnel for VNC
With SDT and Virtual Network Computing (VNC), Users, and Administrators can securely access and control Windows 98/NT/2000/XP/2003, Linux,
Macintosh, Solaris, and UNIX computers. There’s a range of popular free and commercial VNC software available (UltraVNC, RealVNC, TightVNC).
To set up a secure VNC connection, install and configure the VNC Server software on the computer the user will access, then install and configure
the VNC Viewer software on the Viewer PC.
6.9.1 Install and Configure the VNC Server on the Computer to be Accessed
Virtual Network Computing (VNC) software enables users to remotely access computers running Linux, Macintosh, Solaris, UNIX, all versions of
Windows, and most other operating systems.
For Microsoft Windows servers (and clients):
Windows does not include VNC software, so you will need to download, install, and activate a third party VNC Server software package:
56
724-746-5500 | blackbox.com
Page 57

Chapter 6: Secure SSH Tunneling and SDT Connector
RealVNC http://www.realvnc.com is fully cross-platform, so a desktop running on a Linux
machine may be displayed on a Windows PC, on a Solaris machine, or on any number of
other architectures. There is a Windows server, allowing you to view the desktop of a remote
Windows machine on any of these platforms using exactly the same viewer. RealVNC was
founded by members of the AT&T team who originally developed VNC.
For Linux servers (and clients):
Most Linux distributions now include VNC Servers and Viewers and they generally can be launched from the (Gnome/KDE etc) front end; for
example, with Red Hat Enterprise Linux 4 there’s VNC Server software and a choice of Viewer client software, and to launch:
Select the Remote Desktop entry in the Main Menu -> Preferences menu.
Click the Allow other users… checkbox to allow remote users to view and control your desktop.
UltraVNC http://ultravnc.com is easy to use, fast, and free VNC software that has pioneered
and perfected features that the other flavors have consistently refused or been very slow to
implement for cross platform and minimalist reasons. UltraVNC runs under Windows
operating systems (95, 98, Me, NT4, 2000, XP, 2003). Download UltraVNC from
Sourceforge's UltraVNC file list.
TightVNC http://www.tightvnc.com is an enhanced version of VNC. It has added features such
as file transfer, performance improvements, and read-only password support. They have just
recently included a video drive much like UltraVNC. TightVNC is still free, cross-platform
(Windows Unix, and Linux), and compatible with the standard (Real) VNC.
Figure 6-27. Remote Desktop Preferences screen.
To set up a persistent VNC server on Red Hat Enterprise Linux 4:
• Set a password using vncpasswd
• Edit /etc/sysconfig/vncservers
• Enable the service with chkconfig vncserver on
• Start the service with service vncserver start
724-746-5500 | blackbox.com
57
Page 58

1101 and 1102 Secure Device Servers
• Edit /home/username/.vnc/xstartup if you want a more advanced session than just twm and an xterm.
For Macintosh servers (and clients):
OSXvnc http://www.redstonesoftware.com/vnc.html is a robust, full-featured VNC server for Mac OS X that allows any VNC client to remotely view
and/or control the Mac OS X machine. OSXvnc is supported by Redstone Software.
Most other operating systems (Solaris, HPUX, PalmOS etc) either come with VNC bundled, or have third-party VNC software that you can
download.
6.9.2 Install, Configure, and Connect the VNC Viewer
VNC is truly platform-independent so a VNC Viewer on any operating system can connect to a VNC Server on any other operating system. There
are Viewers (and Servers) from a wide selection of sources (for example, UltraVNC, TightVNC, or RealVNC) for most operating systems. There are
also a wealth of Java viewers available so that any desktop can be viewed with any Java-capable browser (http://en.wikipedia.org/wiki/VNC lists
many of the VNC Viewers sources).
Install the VNC Viewer software and set it up for the appropriate speed connection.
NOTE: To make VNC faster, when you set up the Viewer:
(Refer to http://doc.uvnc.com for detailed configuration instructions)
To establish the VNC connection, first configure the VNC Viewer, entering the VNC Server IP address.
When the Viewer PC is connected to the console server thru an SSH tunnel (over the public Internet, or a dial-in connection, or private network
connection), enter localhost (or 127.0.0.1) as the IP VNC Server IP address; and the source port you entered when setting SSH tunneling /port
forwarding (in Section 6.2.6), for example:1234
Set encoding to ZRLE (if you have a fast enough CPU).
Decrease color level (e.g. 64 bit).
Disable the background transmission on the Server or use a plain wallpaper.
Figure 6-28. VNC server.
When the Viewer PC is connected directly to the console server (that is, locally or remotely through a VPN or dial in connection); and the VNC Host
computer is serially connected to the console server; enter the IP address of the console server unit with the TCP port that the SDT tunnel will use.
The TCP port will be 7900 plus the physical serial port number (that is, 7901 to 7902, so all traffic directed to port 79xx on the console server is
tunneled thru to port 5900 on the PPP connection on serial Port xx). For a Windows Viewer PC using UltraVNC connecting to a VNC Server
attached to Port 1 on a console server, it is located at 192.168.0.1.
58
724-746-5500 | blackbox.com
Page 59

Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-29. IP address of console server unit.
To establish the VNC connection, simply activate the VNC Viewer software on the Viewer PC and enter the password.
Figure 6-30. VNC authentication.
NOTE: For general background reading on Remote Desktop and VNC access we recommend the following:
The Micro soft Remote Desktop How-To .
http://www.microsoft.com/windowsxp/using/mobility/getstarted/remoteintro.mspx
The Illustrated Network Remote Desktop help page.
http://theillustratednetwork.mvps.org/RemoteDesktop/RemoteDesktopSetupandTroubleshooting.html
What is Remote Desktop in Windows XP and Windows Server 2003? by Daniel Petri. http://www.petri.co.il/what's_remote_desktop.htm
Frequently Asked Questions about Remote Desktop. http://www.microsoft.com/windowsxp/using/mobility/rdfaq.mspx
Secure remote access of a home network using SSH, Remote Desktop, and VNC for the home user
http://theillustratednetwork.mvps.org/RemoteDesktop/SSH-RDP-VNC/RemoteDesktopVNCandSSH.html
Taking your desktop virtual with VNC, Red Hat magazine. http://www.redhat.com/magazine/006apr05/features/vnc/ and
http://www.redhat.com/magazine/007may05/features/vnc/
Wikipedia general background on VNC http://en.wikipedia.org/wiki/VNC.
6.10 Using SDT to IP Connect to Hosts that are Serially Attached to the Gateway
Network (IP) protocols like RDP, VNC, and HTTP can also be used for connecting to host devices that are serially connected through their COM port
to the console server. To do this you must:
establish a PPP connection (Section 6.7) between the host and the gateway, then
set up Secure Tunneling—Ports on the console server (Section 6.7), then
configure SDT Connector to use the appropriate network protocol to access IP consoles on the host devices that are attached to the
Console server serial ports (Section 6.7)
724-746-5500 | blackbox.com
59
Page 60

1101 and 1102 Secure Device Servers
6.10.1 Establish a PPP Connection between the Host COM Port and Console Server
(This step is only necessary for serially connected computers.)
First, physically connect the COM port on the host computer you want to access to the serial port on the console server, then:
For non Windows (Linux, UNIX, Solaris, etc.) computers, establish a PPP connection over the serial port. The online tutorial
http://www.yolinux.com/TUTORIALS/LinuxTutorialPPP.html presents a selection of methods for establishing a PPP connection for Linux.
For Windows XP and 2003 computers, follow the steps below to set up an advanced network connection between the Windows computer,
through its COM port to the console server. Both Windows 2003 and Windows XP Professional allow you to create a simple dial in service which
can be used for the Remote Desktop/VNC/HTTP/X connection to the console server:
Open Network Connections in Control Panel and click the New Connection Wizard.
Figure 6-31. New Connection Wizard screen.
Select Set up an advanced connection and click Next.
On the Advanced Connection Options screen, select Accept Incoming Connections and click Next.
Select the Connection Device (i.e. the serial COM port on the Windows computer that you cabled through to the console server). By default, select
COM1. The COM port on the Windows computer should be configured to its maximum baud rate. Click Next.
On the Incoming VPN Connection Options screen, select Do not allow virtual private connections and click Next.
60
724-746-5500 | blackbox.com
Page 61

Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-32. User permissions.
Specify which Users will be allowed to use this connection. This should be the same Users who were given Remote Desktop access privileges in the
earlier step. Click Next.
On the Network Connection screen, select TCP/IP and click Properties.
Figure 6-33. Incoming TCP/IP properties.
Select Specify TCP/IP addresses on the Incoming TCP/IP Properties screen, select TCP/IP. Nominate a From: and a To: TCP/IP address, and click Next.
NOTES: You can choose any TCP/IP addresses so long as they are addresses that are not used anywhere else on your network. The From: address
will be assigned to the Windows XP/2003 computer and the To: address will be used by the console server. For simplicity, use the IP
address as shown in the illustration above:
From: 169.134.13.1
To: 169.134.13.2
Or, you can set the advanced connection and access on the Windows computer to use the console server defaults:
Specify 10.233.111.254 as the From: address
Select Allow calling computer to specify its own address
Also, you could use the console server default username and password when you set up the new Remote Desktop User and gave this
User permission to use the advance connection to access the Windows computer:
724-746-5500 | blackbox.com
61
Page 62
1101 and 1102 Secure Device Servers
NOTES (continued): The console server default Username is portXX where XX is the serial port number on the console server.
When the PPP connection has been set up, a network icon will appear in the Windows task bar.
NOTE: The above notes describe setting up an incoming connection for Windows XP. The steps are similar for Vista and Windows Server
2003/2008, but the set up screens present slightly differently:
The default Password is portXX
To use the defaults for a RDP connection to the serial port 2 on the console server, you would have set up a Windows
user named port02.
Figure 6-34. Users tab.
You need to put a check in the box for Always allow directly connected devices such as palmtop.
The option to Set up an advanced connection is not available in Windows 2003 if RRAS is configured. If RRAS has been configured, you can enable
the null modem connection for the dial-in configuration.
For earlier version Windows computers, follow the steps in Section B, above. To get to the Make New Connection button:
For Windows 2000, click Start, and select Settings. At the Dial-Up Networking Folder, click Network and Dial-up Connections, and click Make New
Connection. You may need to first set up a connection over the COM port using Connect directly to another computer before proceeding to Set up
an advanced connection.
For Windows 98, double click My Computer on the Desktop, then open Dial-Up Networking and double click.
6.10.2 Set up SDT Serial Ports on Console Server
To set up RDP (and VNC) forwarding on the console server Serial Port that is connected to the Windows computer COM port:
Select the Serial & Network: Serial Port menu option and click Edit (for the particular Serial Port that is connected to the Windows computer COM
port).
On the SDT Settings menu, select SDT Mode (this will enable port forwarding and SSH tunneling) and enter a Username and User Password.
62
724-746-5500 | blackbox.com
Page 63
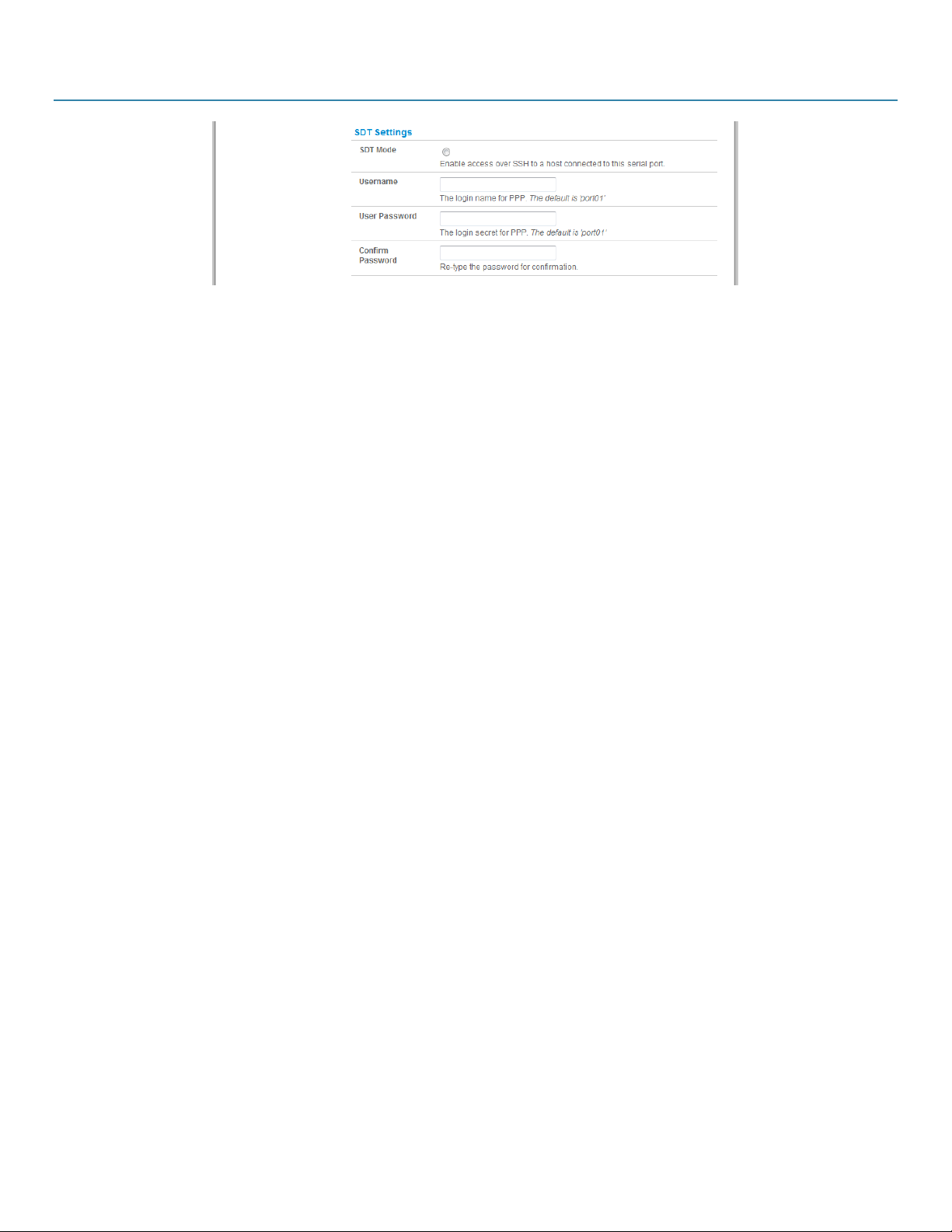
Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-35. SDT settings screen.
NOTE: When you enable SDT, it will override all other Configuration protocols on that port.
NOTE: If you leave the Username and User Password fields blank, they default to portXX and portXX where XX is the serial port number. The
default username and password for Secure RDP over Port 2 is port02.
Make sure the console server Common Settings (Baud Rate, Flow Control) are the same as those set up on the Windows computer COM port and
click Apply.
RDP and VNC forwarding over serial ports is enabled on a Port basis. You can add Users who can have access to these ports (or reconfigure User
profiles) by selecting Serial & Network: User & Groups menu tag—as described earlier in Chapter 5, Configuring Serial Ports.
6.10.3 Setup SDT Connector to SSH Port Forward over the Console Server Serial Port
In the SDT Connector software running on your remote computer, specify the gateway IP address of your console server and a username/password
for a user you set up on the console server that has access to the desired port.
Next, add a New SDT Host. In the Host address, put portxx, where xx = the port you are connecting to. Example: for port 1 you would have a Host
Address of: port01. Then select the RDP Service check box.
6.11 SSH Tunneling Using other SSH Clients (for example, PuTTY)
As covered in the previous sections of this chapter, we recommend that you use the SDT Connector client software that is supplied with the console
server. There’s also a wide selection of commercial and free SSH client programs that can provide the secure SSH connections to the console servers
and secure tunnels to connected devices:
PuTTY is a complete (though not very user friendly) freeware implementation of SSH for Win32 and UNIX platforms.
SSHTerm is a useful open source SSH communications package.
SSH Tectia is leading end-to-end commercial communications security solution for the enterprise.
Reflection for Secure IT (formerly F-Secure SSH) is another good commercial SSH-based security solution.
For example, the steps on the next page show how to establish an SSH tunneled connection to a network connected device using the PuTTY client
software.
724-746-5500 | blackbox.com
63
Page 64

1101 and 1102 Secure Device Servers
Figure 6-36. PuTTY Configuration screen.
In the Session menu, enter the IP address of the console server in the Host Name or IP address field.
For dial-in connections, this IP address will be the Local Address that you assigned to the console server when you set it up as the Dial-In PPP Server.
For Internet (or local/VPN connections) connections, this will be the console server’s public IP address.
Select the SSH Protocol, and the Port will be set as 22.
Go to the SSH -> Tunnels menu and in Add new forwarded port enter any high unused port number for the Source port, for example, 54321.
Set the Destination: IP details.
If your destination device is network-connected to the console server and you are connecting using RDP, set the Destination as <Managed Device IP
address/DNS Name>:3389. For example, if when setting up the Managed Device as Network Host on the console server, you specified its IP address
to be 192.168.253.1 (or its DNS Name was accounts.myco.intranet.com), then specify the Destination as 192.168.523.1:3389 (or
accounts.myco.intranet.com:3389 ). Only devices that are configured as networked Hosts can be accessed using SSH tunneling (except by the
“root” user who can tunnel to any IP address the console server can route to).
64
724-746-5500 | blackbox.com
Page 65

Chapter 6: Secure SSH Tunneling and SDT Connector
Figure 6-37. Set destination.
If your destination computer is serially connected to the console server, set the Destination as <port label>:3389. For example, if the Label you
specified on the serial port on the console server is win2k3, then specify the remote host as win2k3:3389. Or, you can set the Destination as
portXX:3389 (where XX is the SDT enabled serial port number). For example, if port 2 is on the console server is to carry the RDP traffic, then specify
port02:3389.
NOTE: http://www.jfitz.com/tips/putty_config.html has useful examples on configuring PuTTY for SSH tunneling.
Select Local and click the Add button.
Click Open to SSH connect the Client PC to the console server. You will now be prompted for the Username/Password for the console server user.
Figure 6-38. Enter username and password.
If you are connecting as a User in the “users” group, then you can only SSH tunnel to Hosts and Serial Ports where you have specific access
permission.
If you are connecting as an Administrator (in the “admin” group), then you can connect to any configured Host or Serial Ports (that has SDT
enabled).
To set up the secure SSH tunnel for a HTTP browser connection to the Managed Device, specify port 80 (instead of port 3389 that was used for
RDP) in the Destination IP address.
To set up the secure SSH tunnel from the Client (Viewer) PC to the console server for VNC, follow the steps above, but when you configure the
VNC port redirection, specify port 5900 in the Destination IP address.
724-746-5500 | blackbox.com
65
Page 66

1101 and 1102 Secure Device Servers
NOTE: How secure is VNC? VNC access generally allows access to your whole computer, so security is very important. VNC uses a random
challenge-response system to provide the basic authentication that allows you to connect to a VNC server. This is reasonably secure and
the password is not sent over the network.
Once connected, all subsequent VNC traffic is unencrypted. A malicious user could snoop your VNC session. There are also VNC scanning
programs available, which will scan a subnet looking for PCs that are listening on one of the ports that VNC uses.
Tunneling VNC over a SSH connection ensures all traffic is strongly encrypted. No VNC port is ever open to the internet, so anyone
scanning for open VNC ports will not be able to find your computers. When tunneling VNC over a SSH connection, the only port that
you’re opening on your console server is the SDT port 22.
Sometimes it may be prudent to tunnel VNC through SSH even when the Viewer PC and the console server are both on the same local
network.
66
724-746-5500 | blackbox.com
Page 67

Chapter 7: Alerts and Logging
7. Alerts and Logging
This chapter describes the alert generation and logging features of the console server. The Alert facility monitors the serial ports, all logins, and the
power status, and sends emails, SMS, Nagios, or SNMP alerts when specified trigger events occur.
First, enable and configure the service that will be used to carry the alert (Section 7.1).
Then, specify the alert trigger condition and the actual destination to which that particular alert will be sent (Section 7.2).
All console server models can maintain log records of all access and communications with the console server and with the attached serial devices. A
log of all system activity is also maintained, as is a history of the status of any attached environmental monitors.
Some models also log access and communications with network attached hosts and maintain a history of the UPS and PDU power status.
If port logs are to be maintained on a remote server, then configure the access path to this location (Section 7.3).
Then you need to activate and set the desired levels of logging for each serial (Section 7.4) and/or network port (Section 7.5) and/or power UPS
(refer to Chapter 8).
7.1 Configure SMTP/SMS/SNMP/Nagios Alert Service
The Alerts facility monitors nominated ports/hosts/UPSs/PDUs/EMDs, etc. for trigger conditions. When triggered, the facility sends an alert
notification over the nominated alert service. Before setting up the alert trigger, configure these alert services:
7.1.1 Email Alerts
The console server uses SMTP (Simple Mail Transfer Protocol) for sending the email alert notifications. To use SMTP, the Administrator must
configure a valid SMTP server for sending the email:
Select Alerts & Logging: SMTP &SMS
Figure 7-1. SMTP and SMS screen.
In the SMTP Server field, enter the outgoing mail Server’s IP address.
If this mail server uses a Secure Connection, specify its type.
You may enter a Sender email address which will appear as the “from” address in all email notifications sent from this console server. Many SMTP
servers check the sender’s email address with the host domain name to verify the address as authentic. So it may be useful to assign an email
address for the console server such as consoleserver2@mydomain.com
724-746-5500 | blackbox.com
67
Page 68

1101 and 1102 Secure Device Servers
You may also enter a Username and Password if the SMTP server requires authentication.
You can specify the specific Subject Line that will be sent with the email.
Click Apply to activate SMTP.
7.1.2 SMS Alerts
The console server uses email-to-SMS services to send SMS alert notifications to mobile devices. Sending SMS via email using SMTP (Simple Mail
Transfer Protocol) is much faster than sending text pages via a modem using the TAP Protocol. Almost all mobile phone carriers provide an SMS
gateway service that forwards email to mobile phones on their networks. There’s also a wide selection of SMS gateway aggregators that provide
email to SMS forwarding to phones on any carriers. To use SMTP SMS, the Administrator must configure a valid SMTP server for sending the email:
Figure 7-2. SMTP SMS Server screen.
In the SMTP SMS Server field in the Alerts & Logging: SMTP &SMS menu, enter the IP address of the outgoing mail Server (and Secure
Connection if applicable).
You may enter a Sender email address, which will appear as the “from” address in all email notifications sent from this console server. Some SMS
gateway service providers only forward email to SMS when the email has been received from authorized senders. You might need to assign a
specific authorized email address for the console server.
You may also enter a Username and Password, because some SMS gateway service providers use SMTP servers which require authentication.
You can specify the specific Subject Line that will be sent with the email. Generally, the email subject will contain a truncated version of the alert
notification message (which is contained in full in the body of the email). However some SMS gateway service providers require blank subjects or
require specific authentication headers to be included in the subject line.
Click Apply to activate SMTP.
7.1.3 SNMP Alerts
The Administrator can configure the Simple Network Management Protocol (SNMP) agent that resides on the console server to send SNMP trap
alerts to an NMS management application:
Select Alerts & Logging: SNMP
Enter the SNMP transport protocol. SNMP is generally a UDP-based protocol, though infrequently, it uses TCP instead.
Enter the IP address of the SNMP Manager and the Port to use for connecting (default = 162)
Select the version being used. The console server SNMP agent supports SNMP v1, v2, and v3.
Enter the Community name for SNMP v1 or 2c. An SNMP community is the group that devices and management stations running SNMP belong
to. It helps define where information is sent. SNMP default communities are private for Write (and public for Read).
68
724-746-5500 | blackbox.com
Page 69

Chapter 7: Alerts and Logging
To configure for SNMP v3, you will need to enter an ID and authentication password and contact information for the local Administrator (in the
Security Name).
Click Apply to activate SNMP.
Figure 7-3. SNMP alerts.
NOTE: All console servers have the snmptrap daemon to send traps/notifications to remote SNMP servers on defined trigger events as
detailed above. They also accept SNMP requests from remote SNMP management servers and provides information on network
interface, running processes, etc. (refer to Chapter 15.5—Modifying SNMP Configuration for more details).
7.1.4 Nagios Alerts
To notify the central Nagios server of Alerts, NSCA must be enabled under System: Nagios and Nagios must be enabled for each applicable host
or port under Serial & Network: Network Hosts or Serial & Network: Serial Ports (refer to Chapter 10).
7.2 Activate Alert Events and Notifications
The Alert facility monitors the status of th e console server and connected devices. When an alert event is triggered, the Alert facility notifies a
nominated email address or SMS gateway, or the configured SNMP or Nagios server. The data stream from nominated serial ports can be
monitored for matched patterns or flow control status changes can be configured to trigger alerts, as can user connections to serial ports and Hosts,
or power events.
Figure 7-4. Add alert button.
724-746-5500 | blackbox.com
69
Page 70

1101 and 1102 Secure Device Servers
Select Alerts & Logging: Alerts, which will display all the alerts currently configured. Click Add Alert.
7.2.1 Add a New Alert
The first step is to specify the alert service that th is event will use for sending notification, who to notify there, and what port/host/device is to be
monitored:
Figure 7-5. Add a new alert screen.
At Add a New Alert, enter a Description for this new alert.
Nominate the email address for the Email Recipient(s) and/or the SMS Recipient(s) to be notified of the alert. For multiple recipients, enter
comma separated addresses.
Activate SNMP notification if an SNMP trap is to be sent for this event.
Activate Nagios notification to use it for this event. In a SDT Nagios centrally managed environment, you can check the Nagios alert option. On the
trigger condition (for matched patterns, logins, power events, and signal changes), an NSCA check “warning” result will be sent to the central
Nagios server. This condition is displayed on the Nagios status screen and triggers a notification, which can cause the Nagios central server itself to
send out an email or an SMS, page, etc.
7.2.2 Configuring General Alert Types
Next, you must select the Alert Type (Connection, Signal, Pattern Match, UPS Power Status, and Power Sensor) to monitor. You can
configure a selection of different Alert types and any number of specific triggers.
Connection Alert—This alert will be triggered when a user connects or disconnects from the applicable Host or Serial Port, or when a Slave
connects or disconnects from the applicable UPS (and you must specify the applicable connections to Apply Alert To).
70
724-746-5500 | blackbox.com
Page 71

Chapter 7: Alerts and Logging
Figure 7-6. General alert types.
Serial Port Signal Alert—This alert will be triggered when the specified signal changes state and applies to serial ports only. You must specify the
particular Signal Type (DSR, DCD or CTS) trigger condition and the Applicable Ports(s).
Figure 7-7. Serial port signal alert.
Serial Port Pattern Match Alert—This alert will be triggered if a regular expression is found in the serial ports character stream that matches the
regular expression you enter in the Pattern field. This alert type will only be applied to serial ports selected as Applicable Ports(s).
724-746-5500 | blackbox.com
71
Page 72

1101 and 1102 Secure Device Servers
Figure 7-8. Serial port pattern match alert.
UPS Power Status Alert— This alert will be triggered when the UPS power status changes between on line, on battery, and low battery. This
status will only be monitored on the Applicable UPS(es) you select.
Power Alert—(next section).
7.2.3 Configuring Power Alert Type
This alert type monitors UPSes, RPCs, and power devices.
Figure 7-9. Power alert.
Select Power Alert to activate.
Specify which Sensor Type to alert on (Power Load and Battery Charge).
Set the levels at which Critical and/or Warning alerts are to be sent. You can also specify High and/or Low Set Points for sending alerts and the
Hysteresis to be applied before resetting the alerts.
NOTE: Specify the Set Point values in amps (current) for power load and % (percentage) for battery charge.
Specify the applicable UPSes, RPCs (and RPC outlets) to Apply Alert To.
72
724-746-5500 | blackbox.com
Page 73

Chapter 7: Alerts and Logging
7.3 Remote Log Storage
Before activating Serial or Network Port Logging on any port or UPS logging, you must specify where those logs are to be saved:
Select the Alerts & Logging: Port Log menu option and specify the Server Type to use, and the details to enable log server access.
Figure 7-11. Remote log storage.
7.4 Serial Port Logging
In Console Server mode, activity logs of all serial port activity can be maintained. These records are stored on an off-server, or in the Advanced
Console Server flash memory. To specify which serial ports have activities recorded and to what level data is to be logged:
Select Serial & Network: Serial Port and Edit the port to be logged.
Specify the Logging Level of for each port as:
Level 0 Turns off logging for the selected port.
Level 1 Logs all connection events to the port.
Level 2 Logs all data transferred to and from the port, all changes in hardware flow control status, and all User connection events.
Click Apply.
NOTE: A cache of the most recent 8K of logged data per serial port is maintained locally (in addition to the Logs that are transmitted for
remote/USB flash storage). To view the local cache of logged serial port data, select Manage: Port Logs.
7.5 Network TCP or UDP Port Logging
The console server can be configured to log access to and communications with network attached Hosts.
For each Host, when you set up the Permitted Services that you authorize to use, you also must set up the level of logging to maintain for each
service.
Specify the logging level to maintain for that particular TDC/UDP port/service, on that particular Host:
Level 0 Turns off logging for the selected TDC/UDP port to the selected Host.
Level 1 Logs all connection events to the port.
724-746-5500 | blackbox.com
73
Page 74

1101 and 1102 Secure Device Servers
Level 2 Logs all data transferred to and from the port.
Click Add then click Apply.
74
724-746-5500 | blackbox.com
Page 75

Chapter 8: Power Management
8. Power Management
Black Box console servers manage embedded software that you can use to manage connected Power Distribution Systems (PDUs), IPMI devices, and
Uninterruptible Power Supplies (UPSs) supplied by a number of vendors.
8.1 Remote Power Control (RPC)
The console server Management Console monitors and controls Remote Power Control (RPC) devices using the embedded PowerMan and Network
UPS Tools open source management tools and the Black Box power management software. RPCs include power distribution units (PDUs) and IPMI
power devices.
You can control serial PDUs invariably using their command line console, so you could manage the PDU through the console server using a remote
Telnet client. Also, you could use proprietary software tools supplied by the vendor. This generally runs on a remote Windows PC, and you could
configure the console server serial port to operate with a serial COM port redirector in the PC (as detailed in Chapter 5).
Similarly, you can control network-attached PDUs with a browser (for example, with SDT as detailed in Chapter 6.3), an SNMP management
package, or using the vendor-supplied control software. Servers and network-attached appliances with embedded IPMI service processors or BMCs
invariably have their own management tools (like SoL) that provide secure management when connected with SDT Connector.
For simplicity, you can now control all these devices through one window using the Management Console’s RPC remote power control tools.
8.1.1 RPC Connection
Serial and network connected RPCs must first be connected to, and configured to communicate with, the console server:
For serial RPCs, conn ect the PDU to th e selected serial port on the console server. From the Serial and Network: Serial Port menu, configure the
Common Settings of that port with the RS-232 properties, etc. required by the PDU (refer to Chapter 5.1.1 Common Settings). Then select RPC as
the Device Type.
For each network-connected RPC, go to Serial & Network: Network Hosts menu and configure the RPC as a connected Host by specifying it as
Device Type: RPC and clicking Apply (refer to Section 5.4, Network Hosts).
Figure 8-1. Select RPC connections menu.
Select the Serial & Network: RPC Connections menu. This will display all the RPC connections that have already been configured.
724-746-5500 | blackbox.com
75
Page 76
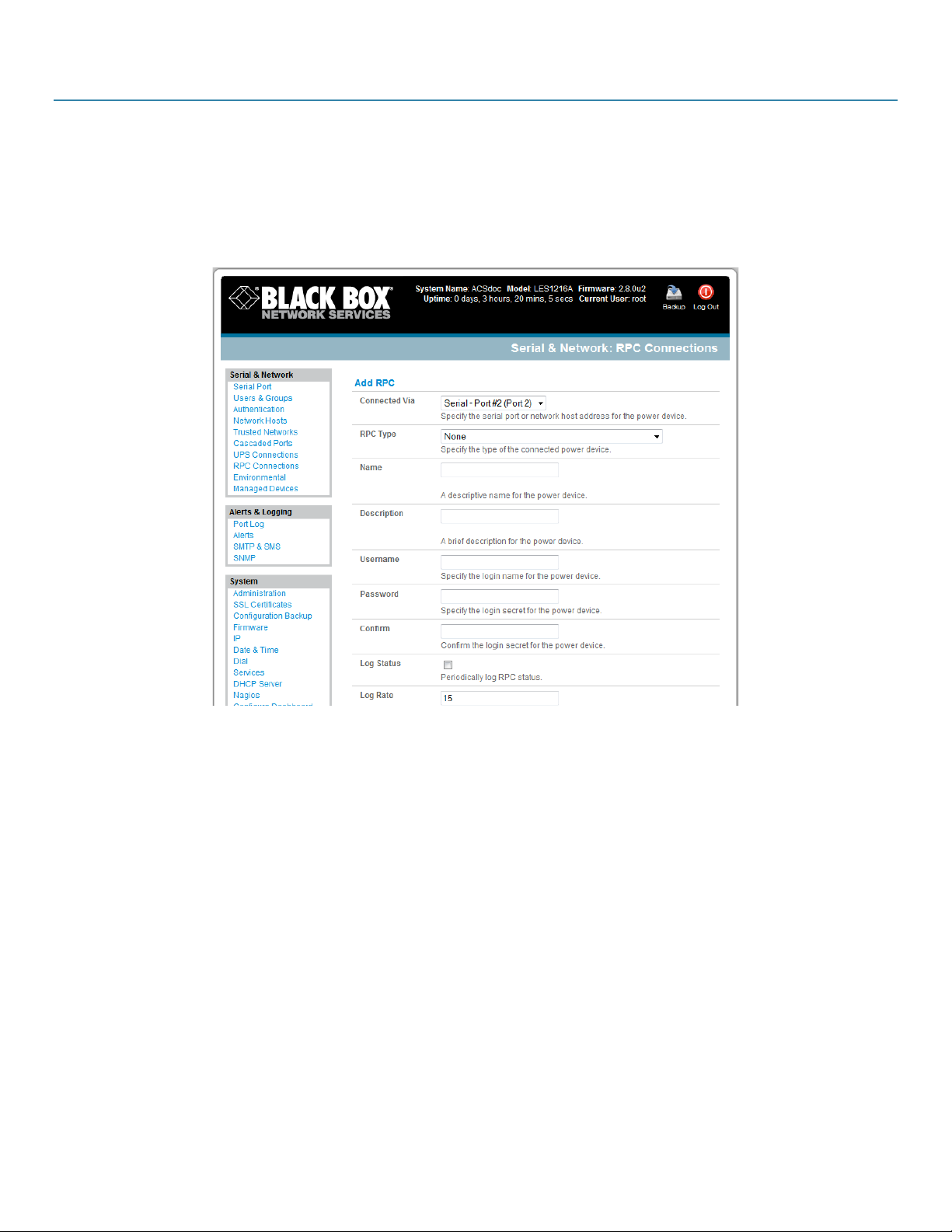
1101 and 1102 Secure Device Servers
Click Add RPC.
Connected Via presents a list of serial ports and network Host connections that you have set up with device type RPC (but have yet to connect to a
specific RPC device):
When you select Connect Via for a Network RPC connection, then the corresponding Host Name/Description that you set up for that connection
will be entered as the Name and Description for the power device.
Or, if you select to Connect Via a Serial connection, enter a Name and Description for the power device.
Figure 8-2. Add RPC screen.
Select the appropriate RPC Type for the PDU (or IPMI) being connected:
If you are connecting to the RPC via the network, you will be presented with the IPMI protocol options and the SNMP RPC Types currently
supported by the embedded Network UPS Tools.
If you are connecting to the RPC by a serial port, you will be presented with all the serial RPC types currently supported by the embedded
PowerMan and the Black Box power manager:
76
724-746-5500 | blackbox.com
Page 77

Chapter 8: Power Management
Figure 8-3. RPC descriptions.
Enter the Username and Password used to login into the RPC (Note th at th ese login credentials are not related to the Users and access privileges
you configured in Serial & Networks: Users & Groups).
If you selected SNMP protocol, enter the SNMP v1 or v2c Community for Read/Write access (by default this would be “private”).
Check Log Status and specify the Log Rate (minutes between samples) if you want the status from this RPC to be logged. View these logs from
the Status: RPC Status screen.
Click Apply.
For SNMP PDUs, the console server probes the configured RPC to confirm the RPC Type matches and reports the number of outlets it finds that can
be controlled. If unsuccessful, it will report Unable to probe outlets and you’ll need to check the RPC settings or network/serial connection.
For serially connected RPC devices, a new Managed Device (with the same name as given to the RPC) will be created. The console server will then
configure the RPC with the number of outlets specified in the selected RPC Type or will query the RPC itself for this information.
NOTE: The Black Box console servers support most popular network and serial PDUs. If your PDU is not on the default list, then you can add
support directly (as covered in Chapter 15—Advanced Configurations) or add the PDU support to either the Network UPS Tools or
PowerMan open source projects.
Configure IPMI service processors and BMCs so that all authorized users can use the Management Console to remotely cycle power and
reboot computers, even when their operating system is unresponsive. To set up IPMI power control, the Administrator first enters the IP
address/domain name of the BMC or service processor (for example, a Dell DRAC) in Serial & Network: Network Hosts, then in Serial &
Network: RPC Connections specifies the RPC Type to be IPMI1.5 or 2.0.
8.1.2 RPC Access Privileges and Alerts
You can now set PDU and IPMI alerts using Alerts & Logging: Alerts (refer to Chapter 7). You can also assign which user can access and control
which particular outlet on each RPC using Serial & Network: User & Groups (refer to Chapter 5).
8.1.3 User Power Management
The Power Manager en ables both Users and Administrators to access and control the configured serial and network attached PDU power strips, and
servers with embedded IPMI service processors or BMCs.
Select the Manage: Power and the particular Target power device to be controlled (and the Outlet to be controlled if the RPC supports outlet level
control).
724-746-5500 | blackbox.com
77
Page 78

1101 and 1102 Secure Device Servers
The outlet status is displayed and you can initiate the Action you want to take by selecting the appropriate icon:
Turn ON
Turn OFF
Cycle
Status
You will only be presented with icons for those operations that are supported by the Target you have selected.
Figure 8-4. Selected operations supported by target.
8.1.4 RPC Status
You can monitor the current status of your network and serially connected PDUs and IPMI RPCs.
Select the Status: RPC Status menu and a table with the summary status of all connected RPC hardware will be displayed.
Click on View Log or select the RPCLogs menu and you will be presented with a table of the history and detailed graphical information on the
selected RPC.
Click Manage to query or control the individual power outlet. This will take you to the Manage: Power screen.
8.2 Uninterruptible Power Supply Control (UPS)
You can configure all Black Box console servers to manage locally and remotely connected UPS hardware using Network UPS Tools.
Network UPS Tools (NUT) is a group of open source programs that provide a common interface for monitoring and administering UPS hardware.
These programs ensure safe shutdowns of the systems that are connected. NUT is built on a networked model with a layered scheme of drivers,
server, and clients (covered in some detail in Chapter 8.2.6).
78
724-746-5500 | blackbox.com
Page 79

Chapter 8: Power Management
LES1102A
Multiple local (serial USB
networked) UPSes
Managed UPS
Multiple remote
UPSes
Figure 8-5. Connecting to remote UPS.
LES1102A
Remote UPS
8.2.1 Managed UPS Connections
A Managed UPS is a UPS that is directly connected as a Managed Device to the console server. You can connect it via serial or USB cable or by the
network. The console server becomes the master of this UPS, and runs a upsd server to allow other computers that are drawing power through the
UPS (slaves) to monitor the UPS status and take appropriate action, such as shutdown when the UPS battery is low.
Serial, USB, or
network
connections
Managed
UPS
Figure 8-6. Managed UPS connections.
The console server may or may not be drawing power itself through the Managed UPS. When the UPS’s battery power reaches critical, the console
server signals and waits for slaves to shut down, then powers off the UPS.
724-746-5500 | blackbox.com
79
Page 80

1101 and 1102 Secure Device Servers
Serial and network connected UPSes must first be connected to, and configured to communicate with the console server:
For serial UPSes attach the UPS to the selected serial port on the console server. From the Serial and Network: Serial Port menu, configure the
Common Settings of that port with the RS-232 properties, etc. required by the UPS (refer to Chapter 5.1.1—Common Settings). Then select UPS
as the Device Type.
For each network connected UPS, go to the Serial & Network: Network Hosts menu and configure the UPS as a connected Host by specifying it
as Device Type: UPS and clicking Apply.
No such configuration is required for USB connected UPS hardware.
Figure 8-7. UPS connections.
Select the Serial & Network: UPS Connections menu. The Managed UPSes section will display all the UPS connections that have already been
configured.
Click Add Managed UPS.
80
724-746-5500 | blackbox.com
Page 81

Chapter 8: Power Management
Figure 8-8. Add managed UPS screen.
Select if the UPS will be Connected Via USB, over a pre-configured serial port, or via SNMP/HTTP/HTTPS over the preconfigured network Host
connection.
When you select a network UPS connection, then the corresponding Host Name/Description that you set up for that connection will be entered as
the Name and Description for the power device. Or, if you selected to Connect Via a USB or serial connection then you will need to enter a
Name and Description for the power device (and these details will also be used to create a new Managed Device entry for the serial/USB
connected UPS devices).
Enter the login details. This Username and Password is used by slaves of this UPS (that is, other computers that are drawing power through this
UPS) to connect to the console server to monitor the UPS status so they can shut themselves down when battery power is low. Monitoring will
typically be performed using the upsmon client running on the slave server (refer to Section 8.2.3)
NOTE: These login creden tials are not related to the Users and access privileges you configured in Serial & Networks: Users & Groups.
If you have multiple UPSes and require them to be shut down in a specific order, specify the Shutdown Order for this UPS. This is a whole positive
number, or -1. 0s shut down first, then 1s, 2s, etc. -1s are not shut down at all. Defaults to 0.
Select the Driver that you will use to communicate with the UPS. Most console servers are preconfigured so the drop down menu presents a full
selection of drivers from the latest Network UPS Tools (NUT version 2.4).
724-746-5500 | blackbox.com
81
Page 82

1101 and 1102 Secure Device Servers
Click New Options in Driver Options if you need to set driver-specific options for your selected NUT driver and hardware combination (more
details at http://www.networkupstools.org/doc
).
Figure 8-9. New option screen.
Check Log Status and specify the Log Rate (minutes between samples) if you want the status from this UPS to be logged. You can view these logs
from the Status: UPS Status screen.
If you have enabled Nagios services, then you will presented with an option for Nagios monitoring. Check Enable Nagios to enable this UPS to be
monitored using Nagios central management.
Check Enable Shutdown Script if this is the UPS providing power to the console server itself and if a critical power failure occurs, you can perform
any "last gasp" actions on the console server before power is lost. Place a custom script in /etc/config/scripts/ups-shutdown (you may use the
provided /etc/scripts/ups-shutdown as a template). This script only runs when then UPS reaches critical battery status.
Click Apply.
NOTE: You can also customize the upsmon, upsd, and upsc settings for this UPS hardware directly from the command line.
8.2.2 Remote UPS Management
A Remote UPS is a UPS that is connected as a Managed Device to a remote console server that is monitored (but not managed) by your console
server.
You can configure the upsc and upslog clients in the Black Box console server to monitor remote servers that are running Network UPS Tools
managing their locally connected UPSes. These remote servers might be other Black Box console servers or generic Linux servers running NUT. You
can centrally monitor all these distributed UPSes (which may be spread in a row in a data center, around a campus property, or across the country)
through the one central console server window. To add a Remote UPS:
Select the Serial & Network: UPS Connections menu. The Remote UPSes section will display all the remote UPS devices being monitored.
Click Add Remote UPS.
Figure 8-10. Add remote UPS screen.
Enter the Name of the particular remote UPS that you want to remotely monitor. This name must be the name that the remote UPS was
configured with on the remote console server (becau se the remote console server may itself have multiple UPSes attached that it manages locally
with NUT). Optionally, enter a Description.
82
724-746-5500 | blackbox.com
Page 83

Chapter 8: Power Management
Enter the IP Address or DNS name of the remote console server* that is managing the remote UPS. (*This may be another Black Box console server
or it may be a generic Linux server running Network UPS Tools.)
NOTE: An example where centrally monitor remotely distributed UPSes is useful is a campus or large business site where there’s a multitude of
Check Log Status and specify the Log Rate (minutes between samples) if you want the status from this UPS to be logged. You can view these logs
from the Status: UPS Status screen.
Check Enable Shutdown Script if this remote UPS is the UPS providing power to the console server itself. If the UPS reaches critical battery status,
the custom script in /etc/config/scripts/ups-shutdown runs, enabling you to perform any
Click Apply.
8.2.3 Controlling UPS Powered Computers
One of the advantages of having a Managed UPS is that you can configure computers that draw power through that UPS to shut down gracefully if
you have UPS problems.
For Linux computers, set up upsmon on each computer and direct them to monitor the console server that is managing their UPS. This will set the
specific conditions that will be used to initiate a power down of the computer. Non-critical servers may be powered down some seconds after the
UPS starts running on battery. In contrast, more critical servers may not be shut down until a low battery warning is received). Refer to the online
NUT documentation for details on how to do this:
http://eu1.networkupstools.org/doc/2.2.0/INSTALL.html
http://linux.die.net/man/8/upsmon
An example upsmon.conf entry might look like:
MONITOR managedups@192.168.0.1 1 username password slave
- managedups is the UPS Name of the Managed UPS
- 192.168.0.1 is the IP address of the Black Box console server
- 1 indicates the server has a single power supply attached to this UPS
- username is the Username of the Managed UPS
- password is the Password of the Manager UPS
There are NUT monitoring clients available for Windows computers (WinNUT).
If you have an RPC (PDU), you can shut down UPS powered computers and other equipment if if the they don’t have a client running (for example,
communications, and surveillance gear). Set up a UPS alert and using this to trigger a script that controls a PDU to shut off the power (refer to
Chapter 15).
8.2.4 UPS Alerts
You can set UPS alerts using Alerts & Logging: Alerts (refer to Chapter 7— Alerts & Logging).
8.2.5 UPS Status
You can monitor the current status of your network, serially or USB connected Managed UPSes, and any configured Remote UPSes.
Select the Status: UPS Status menu and a table with the summary status of all connected UPS hardware displays.
Click on any particular UPS System name in the table and more detailed graphical information on the selected UPS System appears.
computer and other equipment sites spread afar, each with th eir own UPS supply … and many of these (particularly the smaller sites) will
be USB or serially connected.
Having a console server at these remote sites would enable the system manager to centrally monitor the status of the power supplies at all
sites, and centralize alarms. So he/she can be warned to initiate a call-out or shut-down.
“last gasp” actions.
724-746-5500 | blackbox.com
83
Page 84

1101 and 1102 Secure Device Servers
Figure 8-11. UPS graph.
Click on any particular All Data for any UPS System in the table for more status and configuration information about the selected UPS System.
Select UPS Logs and you will be presented with the log table of the load, battery charge level, temperature, and other status information from all
the Managed and Monitored UPS systems. This information will be logged for all UPSes that were configured with Log Status checked. The
information is also presented graphically.
Figure 8-12. Log table.
8.2.6 Overview of Network UPS Tools (NUT)
NUT is built on a networked model with a layered scheme of drivers, server and clients. Configure NUT using the Management Console as
described above, or configure the tools and manage the UPSes directly from the command line. This section provides an overview of NUT. You can
find full documentation at http://www.networkupstools.org/doc.
84
724-746-5500 | blackbox.com
Page 85

Chapter 8: Power Management
LES1102A
Monitor log graph and client
NUT upsc client
Local NUT upsd server
NUT serial/USB/SNMP UPS drivers
LES1102A
NUT upsd server
Multiple local
UPSes
Multiple
remote UPSes
NUT is built on a networked model with a layered scheme of drivers, server and clients:
The driver programs talk directly to the UPS equipment and run on the same host as the NUT network server (upsd). Drivers are provided for a wide
assortment of equipment from most of the popular UPS vendors and understand the specific language of each UPS. They communicate with serial,
USB, and SNMP network connected UPS hardware and map the communications back to a compatibility layer. This means both an expensive
“smart” protocol UPS and a simple “power strip” model can be handled transparently.
The NUT network server program upsd is responsible for passing status data from the drivers to the client programs via the network. upsd can
cache the status from multiple UPSes and then serve this status data to many clients. upsd also contains access control features to limit the abilities
of the clients (only authorized hosts may monitor or control the UPS hardware).
There are a number of NUT clients that connect to upsd to check on the status of the UPS hardware and do things based on the status. These
clients can run on the same host as the NUT server or they can communicate with the NUT server over the network (enabling them to monitor any
UPS anywhere):
The latest release of NUT (2.4) also controls PDU systems. It can do this either natively using SNMP or through a binding to
source software from Livermore Labs that also is embedded in Black Box console servers).
These NUT clients and servers all are embedded in each Black Box console server (with a Management Console presentation layer added) —and
they also are run remotely on distributed console servers and other remote NUT monitoring systems. This layered distributed NUT architecture
enables:
Multiple manufacturer support: NUT can monitor UPS models from 79 different manufacturers—and PDUs from a growing number of vendors—
with a unified interface.
Multiple architecture support: NUT can manage serial and USB connected UPS models with the same common interface. Network-connected USB
and PDU equipment can also be monitored using SNMP.
Multiple clients monitoring one UPS: Multiple systems may monitor a single UPS using only their network connections. There is a wide selection of
client programs that support monitoring UPS hardware via NUT (Big Sister, Cacti, Nagios, and more).
The upsc client provides a quick way to poll the status of a UPS server. Use it inside shell scripts and other programs that need UPS data
but don't want to include the full interface.
The upsmon client enables servers that draw power through the UPS to shutdown gracefully when the battery power reaches critical.
There are also logging clients (upslog) and third party interface clients (Big Sister, Cacti, Nagios, Windows, and more.
Refer to
.)
Figure 8-13. NUT.
UPS drivers
(open
724-746-5500 | blackbox.com
85
Page 86

1101 and 1102 Secure Device Servers
Central management of multiple NUT servers: A central NUT client can monitor multiple NUT servers that may be distributed throughout the data
center, across a campus, or around the world.
NUT supports the more complex power architectures found in data centers, communications centers, and distributed office environments where
many UPSes from many vendors power many systems with many clients. Each of the larger UPSes power multiple devices, and many of these
devices are in turn dual powered.
86
724-746-5500 | blackbox.com
Page 87

Chapter 9: Authentication
9. Authentication
The console server is a dedicated Linux computer with a myriad of popular and proven Linux software modules for networking, secure access
(OpenSSH), and communications (OpenSSL), and sophisticated user authentication (PAM, RADIUS, TACACS+, and LDAP).
This chapter details how the Administrator can use the Management Console to establish remote AAA authentication for all connections to the
console server and attached serial and network host devices.
This chapter also covers how to establish a secure link to the Management Console using HTTPS and using OpenSSL and OpenSSH to establish a
secure Administration connection to the console server.
9.1 Authentication Configuration
Authentication can be performed locally, or remotely using an LDAP, Radius, or TACACS+ authentication server. The default authentication method
for the console server is Local.
Figure 9-1. Authentication screen.
Any authentication method that is configured will be used for authentication of any user who attempts to log in through Telnet, SSH, or the Web
Manager to the console server and any connected serial port or network host devices.
You can configure the console server to the default (Local) or using an alternate authentication method (TACACS, RADIUS, or LDAP). Optionally,
you can select the order in which local and remote authentication is used:
Local TACACS /RADIUS/LDAP: Tries local authentication first, falling back to remote if local fails.
TACACS /RADIUS/LDAP Local: Tries remote authentication first, falling back to local if remote fails.
TACACS /RADIUS/LDAP Down Local: Tries remote authentication first, falling back to local if the remote authentication returns an error condition
(for example, if the remote authentication server is down or inaccessible).
9.1.1 Local Authentication
Select Serial and Network: Authentication and check Local.
Click Apply.
9.1.2 TACACS Authentication
Perform the following procedure to configure the TACACS+ authentication method to use whenever the console server or any of its serial ports or
hosts is accessed:
Select Serial and Network: Authentication and check TACAS or LocalTACACS or TACACSLocal or TACACSDownLocal
724-746-5500 | blackbox.com
87
Page 88

1101 and 1102 Secure Device Servers
Figure 9-2. TACACS screen.
Enter the Server Address (IP or host name) of the remote Authentication/Authorization server. Multiple remote servers may be specified in a
comma-separated list. Each server is tried in succession.
In addition to multiple remote servers, you can also enter separate lists of Authentication/Authorization servers and Accounting servers. If no
Accounting servers are specified, the Authentication/Authorization servers are used instead.
Enter the Server Password.
Click Apply. TACAS+ remote authentication will now be used for all u ser access to console server and serially or network attached devices.
TACACS+
The Terminal Access Controller Access Control System (TACACS+) security protocol is a recent protocol developed by Cisco. It provides detailed
accounting information and flexible administrative control over the authentication and authorization processes. TACACS+ allows for a single access
control server (the TACACS+ daemon) to provide authentication, authorization, and accounting services independently. Each service can be tied into
its own database to take advantage of other services available on that server or on the network, depending on the capabilities of the daemon.
There is a draft RFC detailing this protocol. You can find further information on configuring remote TACACS+ servers at the following sites:
http://www.cisco.com/en/US/tech/tk59/technologies_tech_note09186a0080094e99.shtml
http://www.cisco.com/en/US/products/sw/secursw/ps4911/products_user_guide_chapter09186a00800eb6d6.html
http://cio.cisco.com/univercd/cc/td/doc/product/software/ios113ed/113ed_cr/secur_c/scprt2/sctplus.htm
9.1.3 RADIUS Authentication
Perform the following procedure to configure the RADIUS authentication method to use whenever the console server or any of its serial ports or
hosts is accessed:
Select Serial and Network: Authentication and check RADIUS or LocalRADIUS or RADIUSLocal or RADIUSDownLocal.
Figure 9-3. RADIUS screen.
Enter the Server Address (IP or host name) of the remote Authentication/ Authorization server. Multiple remote servers may be specified in a
comma-separated list. Each server is tried in succession.
In addition to multiple remote servers, you can also enter separate lists of Authentication/Authorization servers and Accounting servers. If no
Accounting servers are specified, the Authentication/Authorization servers are used instead.
Enter the Server Password.
Click Apply. RADIUS remote authentication will now be used for all user access to console server and serially or network-attached devices.
88
724-746-5500 | blackbox.com
Page 89

Chapter 9: Authentication
RADIUS: The Remote Authentication Dial-In User Service (RADIUS) protocol was developed by Livingston Enterprises as an access server
authentication and accounting protocol. The RADIUS server can support a variety of methods to authenticate a user. When it is provided with the
username and original password given by the user, it can support PPP, PAP, or CHAP, UNIX login, and other authentication mechanisms. You can
find further information on configuring remote RADIUS servers at the following sites:
http://www.microsoft.com/technet/prodtechnol/windowsserver2003/library/DepKit/d4fe8248-eecd-49e4-88f6-9e304f97fefc.mspx
http://www.cisco.com/en/US/tech/tk59/technologies_tech_note09186a00800945cc.shtml
http://www.freeradius.org/
9.1.4 LDAP Authentication
Perform the following procedure to configure the LDAP authentication method to use whenever the console server or any of its serial ports or hosts
is accessed:
Select Serial and Network: Authentication and check LDAP or LocalLDAP or LDAPLocal or LDAPDownLocal
Figure 9-4. LDAP screen.
Enter the Server Address (IP or host name) of the remote Authentication server. Multiple remote servers may be specified in a comma-separated
list. Each server is tried in succession.
Enter the Server Password.
NOTE: To interact with LDAP requires that the user account exist on our console server to work with the remote server. (You can't just create the
user on your LDAP server and not tell the console server about it.) You need to add the user account.
Click Apply. LDAP remote authentication will now be used for all user access to console server and serially or network attached devices.
LDAP: The Lightweight Directory Access Protocol (LDAP) is based on the X.500 standard, but is significantly simpler and more readily adapted to
meet custom needs. The core LDAP specifications are all defined in RFCs. LDAP is a protocol used to access information stored in an LDAP server.
You can find further information on configuring remote RADIUS servers at the following sites:
http://www.ldapman.org/articles/intro_to_ldap.html
http://www.ldapman.org/servers.html
http://www.linuxplanet.com/linuxplanet/tutorials/5050/1/
http://www.linuxplanet.com/linuxplanet/tutorials/5074/4/
9.1.5 RADIUS/TACACS User Configuration
Users may be added to the local console server appliance. If they are not added and they log in via remote AAA, a user will be added for them. This
user will not show up in the Black Box configurators unless they are specifically added, at which point they are transformed into a completely local
user. The newly added user must authenticate from the remote AAA server, and will have no access if it is down.
If a local user logs in, they may be auth enticated/authorized from the remote AAA server, depending on the chosen priority of the remote AAA. A
local user’s authorization is the union of local and remote privileges.
Example 1: User Tim is locally added, and has access to ports 1 and 2. He is also defined on a remote TACACS server, which says he has access to
ports 3 and 4. Tim may log in with either his local or TACACS password, and will have access to ports 1 through 4. If TACACS is down, he will need
to use his local password, and will only be able to access ports 1 and 2.
724-746-5500 | blackbox.com
89
Page 90

1101 and 1102 Secure Device Servers
Example 2: User Ben is only defined on the TACACS server, which says he has access to ports 5 and 6. When he attempts to log in, a new user will
be created for him, and he will be able to access ports 5 and 6. If the TACACS server is down he will have no access.
Example 3: User Paul is defined on a RADIUS server only. He has access to all serial ports and network hosts.
Example 4: User Don is locally defined on an appliance using RADIUS for AAA. Even if Don is also defined on the RADIUS server, he will only have
access to those serial ports and network hosts he has been authorized to use on the appliance.
If a “no local AAA” option is selected, then root will still be authenticated locally.
You can add remote users to the admin group via either RADIUS or TACACS. Users may have a set of authorizations set on the remote TACACS
server. Users automatically added by RADIUS will have authorization for all resources, whereas those added locally will still need their authorizations
specified.
LDAP has not been modified, and will still need locally defined users.
9.2 PAM (Pluggable Authentication Modules)
The console server supports RADIUS, TACACS+, and LDAP for two-factor authentication via PAM (Pluggable Authentication Modules). PAM is a
flexible mechanism for authenticating users. A number of new ways of authenticating users have become popular. The challenge is that each time a
new authentication scheme is developed, you need to rewrite all the necessary programs (login, ftpd, etc.) to support it.
PAM provides a way to develop programs that are independent of authentication scheme. These programs need “authentication modules” to be
attach ed to them at run-time in order to work. Which authentication module is attached depends on the local system setup and is at the discretion
of the local Administrator.
The console server family supports PAM with the following modules added for remote authentication:
RADIUS - pam_radius_auth (
TACACS+ - pam_tacplus (
LDAP - pam_ldap (
Further modules can be added as required.
Changes may be made to files in /etc/config/pam.d/ that will persist, even if the authentication configurator runs.
Users added on demand: When a user attempts to log in, but does not already have an account on the console server, a new user account will be
created. This account will have no rights, and no password set. It will not appear in the Black Box configuration tools. Automatically added accounts
will not be able to log in if the remote servers are unavailable. RADIUS users are currently assumed to have access to all resources, so they will only
be authorized to log in to the console server. RADIUS users will be authorized each time they access a new resource.
Admin rights granted over AAA: Users may be granted Administrator rights via networked AAA. For TACACS a priv-lvl of 12 or above indicates
an Administrator. For RADIUS, Administrators are indicated via the Framed Filter ID. (See the example configuration files below for example.)
Authorization via TACACS for both serial ports and host access: Permission to access resources may be granted via TACACS by indicating a
Black Box Appliance and a port or networked host the user may access. (See the example configuration files below.)
TACACS Example:
user = tim {
service = raccess {
priv-lvl = 11
port1 = les1102/port02
port2 = 192.168.254.145/port05
}
global = cleartext mit
}
RADIUS Example:
paul Cleartext-Password := "luap"
Service-Type = Framed-User,
Fall-Through = No,
Framed-Filter-Id=":g roup_name=admin"
]
The list of groups may include any number of entries separated by a comma. If the admin group is included, the user will be made an Administrator.
If there is alread y a Framed-Filter-Id, simply add the list of group_names after the existing entries, including the separating colon “:”.
)
)
)
90
724-746-5500 | blackbox.com
Page 91

Chapter 9: Authentication
9.3 SSL Certificate
The console server uses the Secure Socket Layer (SSL) protocol for encrypted network traffic between itself and a connected user. When establishing
the connection, the console server has to expose its identity to the user’s browser using a cryptographic certificate. The default certificate that comes
with the console server device upon delivery is for testing purposes only.
The System Administrator should not rely on the default certificate as
the secured global access mechanism for use through Internet.
Activate your preferred browser and enter https:// IP address. Your browser may respond with a message that verifies the security certificate is valid
but notes that it is not necessarily verified by a certifying authority. To proceed, you need to click yes if you are using Internet Explorer or select
accept this certificate p ermanently (or temporarily) if you are using Mozilla Firefox.
You will then be prompted for the Administrator account and password as normal.
We recommend that you generate and install a new base64 X.509 certificate that is unique for a particular console server.
To do this, the console server must be enabled to generate a new cryptographic key and the associated Certificate Signing Request (CSR) that need s
to be certified by a Certification Authority (CA). A certification authority verifies that you are the person who you claim you are, and signs and issues
a SSL certificate to you. To create and install a SSL certificate for the console server:
Figure 9-5. SSL certificates screen.
724-746-5500 | blackbox.com
91
Page 92

1101 and 1102 Secure Device Servers
Select System: SSL Certificate and fill out the field s as explained below:
Common name
This is the network name of the console server once it is installed in the network (usually the fully qualified domain name). It is identical to the name
that is used to access the console server with a web browser (without the “http://” prefix). In case the name given here and the actual network
name differ, the browser will pop up a security warning when the console server is accessed using HTTPS.
Organizational Unit
Use this field to specify which department within an organization the console server belongs to.
Organization
The name of the organization that the console server belongs to.
Locality/City
The city where the organization is located.
State/Province
The state or province where the organization is located.
Country
The country where the organization is located. This is the two-letter ISO code, for example, DE for Germany, or US for the USA. (Note: Enter the
country code in CAPITAL LETTERS.)
Email
The email address of a contact person that is responsible for the console server and its security.
Challenge Password
Some certification authorities require a challenge password to authorize later changes on the certificate (for example, revocation of the certificate).
The password must be at least 4 characters long.
Confirm Challenge Password
Confirmation of the Challenge Password.
Key length
This is the length of the generated key in bits. 1024 Bits are supposed to be sufficient for most cases. Longer keys may result in slower response
time of the console server when establishing a connection.
Once this is done, click on the button Generate CSR which will initiate the Certificate Signing Request generation. The CSR can be downloaded to
your administration machine with the Download button.
Send the saved CSR string to a Certification Authority (CA) for certification. You will get the new certificate from the CA after a more or less
complicated traditional authentication process (depending on the CA).
Upload the certificate to the console server using the Upload button as shown on the next page.
92
724-746-5500 | blackbox.com
Page 93

Chapter 9: Authentication
Figure 9-6. Upload button.
After completing these steps, the console server has its own certificate that is used for identifying the console server to its users.
NOTE: You can find information on issuing certificates and configuring HTTPS from the command line in Chapter 14.
724-746-5500 | blackbox.com
93
Page 94

1101 and 1102 Secure Device Servers
10. Nagios Integration
Nagios is a powerful, highly extensible open source tool for monitoring network hosts and services. The core Nagios software
package will typically be installed on a server or virtual server, the central Nagios server.
Console servers operate in conjunction with a central/upstream Nagios server to distribute and monitor attached network hosts
and serial devices. They embed the NSCA (Nagios Service Checks Acceptor) and NRPE (Nagios Remote Plug-in Executor) addons—this allows them to communicate with the central Nagios server, so you won’t need a dedicated slave Nagios server at
remote sites.
Even if distributed monitoring is not required, the console servers can be deployed locally alongside the Nagios monitoring host
server, to provide additional diagnostics and points of access to managed devices.
Central site (Nagios
server)
LES1102A
Network
Remote site
Managed hosts and
services
Figure 10-1. Nagios application.
SDT for Nagios extends the capabilities of the central Nagios server beyond monitoring, enabling it to be used for central
management tasks. It incorporates the SDT Connector client, enabling point-and-click access and control of distributed
networks of console servers and their attached network and serial hosts, from a central location.
NOTE: If you have an existing Nagios deployment, you may want to use the console server gateways in a distributed
monitoring server capacity only. If this case and you are already familiar with Nagios, skip ahead to Section 10.3.
10.1 Nagios Overview
Nagios provides central monitoring of the hosts and services in your distributed network. Nagios is freely downloadable, open
source software. This section offers a quick background of Nagios and its capabilities. A complete overview, FAQ, and
comprehensive documentation are available at: http://www.nagios.org
Nagios does take some time to install and configure; however, once Nagios is up and running however, it provides an
outstanding network monitoring system.
With Nagios you can:
Display tables showing the status of each monitored server and network service in real time.
Use a wide range of freely available plug-ins to make detailed checks of specific services—for example, don't just check that a
database is accepting network connections, check that it can actually validate requests and return real data.
Display warnings and send warning e-mails, pager, or SMS alerts when a service failure or degradation is detected.
Assign contact groups who are responsible for specific services in specific time frames.
94
Page 95

Chapter 10: Nagios Integration
10.2 Central Management and Setting Up SDT for Nagios
The Black Box Nagios solution has three parts: the Central Nagios server, Distributed Black Box console servers, and the SDT for Nagios software.
Client
Central Nagios
server
LES1102A
Distributed console
servers
LES1102A
Figure 10-2. Nagios setup.
Central Nagios server
• A vanilla Nagios 2.x or 3.x installation (typically on a Linux server) generally running on a blade, PC, virtual machine, etc. at a central location.
Runs a web server that displays the Nagios GUI.
• Imports configuration from distributed console servers using the SDT for Nagios Configuration Wizard.
Distributed console servers
• Black Box console servers.
• Serial and network hosts are attached to each console server.
• Each runs Nagios plug-ins, NRPE, and NSCA add-ons, but not a full Nagios server.
Clients
• Typically a client PC, laptop, etc., running Windows, Linux, or Mac OS X.
• Runs SDT Connector client software 1.5.0 or later.
• Possibly remote to the central Nagios server or distributed console servers (i.e. a road warrior).
• May receive alert emails from the central Nagios server or distributed console servers.
• Connects to the central Nagios server web UI to view status of monitored hosts and serial devices.
• Uses SDT Connector to connect through the console servers to manage monitored hosts and serial devices.
SDT Nagios setup involves the following steps:
1. Install Nagios and the NSCA and NRPE add-ons on the central Nagios server (Section 10.2.1—Set up central Nagios server).
Configure each Black Box distributed console server for Nagios monitoring, alerting, and SDT Nagios integration (Section 10.2.2— Set up
distributed Black Box servers)
.
724-746-5500 | blackbox.com
95
Page 96

1101 and 1102 Secure Device Servers
2. Run the SDT for Nagios Configuration Wizard on the central Nagios server (Section 10.2.1— Set up SDT Nagios on central Nagios server)
and perform any additional configuration tasks.
3. Install SDT Connector on each client..
10.2.1 Setup Central Nagios Server
SDT for Nagios requires a central Nagios server running Nagios 2.x or 3.x. Nagios 1.x is not supported. The Nagios server software is available for
most major distributions of Linux using the standard package management tools. Your distribution will have documentation available on how to
install Nagios. This is usually the quickest and simplest way to get up and running.
Note that you will need the core Nagios server package, and at least one of the NRPE or NSCA add-ons. NSCA is required to use the alerting
features of the Black Box distributed hosts; installing both NRPE and NSCA is recommended.
You will also require a web server such as Apache to display the Nagios web UI (and this may be installed automatically depending on the Nagios
packages).
Or, you may wish to download the Nagios source code directly from the Nagios website, and build and install the software from scratch. The Nagios
website (http://www.nagios.org
Once you are able to browse to your Nagios server and see its web UI and the local services it monitors by default, you are ready to continue.
10.2.2 Setup Distributed Console Servers
This section provides a brief walkthrough on configuring a single console server to monitor the status of one attached network host (a Windows IIS
server running HTTP and HTTPS services) and one serially attached device (the console port of a network router), and to send alerts back to the
Nagios server when an Administrator connects to the router or server.
This walkthrough provides an example, but details of the configuration options are described in the next section. This walkthrough also assumes the
network host and serial devices are already physically connected to the console server. The first step is to set up the Nagios features on the console
server:
) has several Quick Start Guides that walk through this process.
Figure 10-3. Nagios screen.
Browse the Black Box console server and select System: Nagios on the console server Management Console. Check Nagios service Enabled.
Enter the Host Name and the Nagios Host Address (for example, IP address) that the central Nagios server will use to contact the distributed Black
Box console server.
Enter the IP address that the distributed Black Box console server will use to contact the central Nagios server in Nagios Server Address.
Enter the IP address that the clients running SDT Connector will use to connect through the distributed Black Box servers in SDT Gateway address.
Check Prefer NRPE, NRPE Enabled, and NRPE Command Arguments.
Check NSCA Enabled, choose an NSCA Encryption Method and enter and confirm an NSCA Secret. Remember these details because you will need
them later on. For NSCA Interval, enter: 5.
96
724-746-5500 | blackbox.com
Page 97

Chapter 10: Nagios Integration
Click Apply.
Next, you must configure the attached Window network host and specify the services you will be checking with Nagios (HTTP and HTTPS):
Select Network Hosts from the Serial & Network menu and click Add Host.
Enter the IP Address/DNS Name of the network server, for example: 192.168.1.10 and enter a Description, for example: Windows 2003 IIS Server.
Remove all Permitted Services. This server will be accessible using Terminal Services, so check TCP, Port 3389 and log level 1 and click Add. Remove
and re-add the service to enable logging.
Figure 10-4. Nagios settings screen.
Scroll down to Nagios Settings and check Enable Nagios.
Click New Check and select Check Ping. Click check-host-alive.
Click New Check and select Check Permitted TCP. Select Port 3389
Click New Check and select Check TCP. Select Port 80.
Click New Check and select Check TCP. Select Port 443.
Click Apply.
Similarly, you now must configure the serial port to the router to be monitored by Nagios:
Select Serial Port from the Serial & Network menu.
Locate the serial port that has the router console port attached and click Edit.
Make sure the serial port settings under Common Settings are correct and match the attached router’s console port.
Click Console server Mode, and select Logging Level 1.
Check Telnet (SSH access is not required, as SDT Connector is used to secure the otherwise insecure Telnet connection).
Scroll down to Nagios Settings and check Enable Nagios.
Check Port Log and Serial Status.
Click Apply.
Now you can set the console server to send alerts to the Nagios server:
Select Alerts from the Alerts & Logging menu and click Add Alert.
In Description enter: Administrator connection.
Check Nagios (NSCA ).
In Applicable Ports check the serial port that has the router console port attached. In Applicable Hosts check the IP address/DNS name of the IIS
server.
Click Connection Alert.
Click Apply.
724-746-5500 | blackbox.com
97
Page 98

1101 and 1102 Secure Device Servers
Finally, you need to add a User for the client running SDT Connector:
Select Users & Groups from the Serial & Network menu.
Click Add User.
In Username, enter: sdtnagiosuser, then enter and confirm a Password.
In Accessible Hosts click the IP address/DNS name of the IIS server, and in Accessible Ports click the serial port that has the router console port
attached.
Click Apply.
10.3 Configuring Nagios Distributed Monitoring
To activate th e console server Nagios distributed monitoring:
Nagios integration must be enabled and a path established to the central/upstream Nagios server.
If the console server is to periodically report on Nagios monitored services, then the NSCA client embedded in the console server must be
configured—the NSCA program enables scheduled check-ins with the remote Nagios server and is used to send passive check results across the
network to the remote server.
If the Nagios server is to actively request status updates from the console server, then the NRPE server embedded in the console server must be
configured— the NRPE server is the Nagios daemon for executing plug-ins on remote hosts.
Each of the Serial Ports and each of the Hosts connected to the console server that you want to monitor must have Nagios enabled and any specific
Nagios checks configured.
Configure the central/upstream Nagios monitoring host.
10.3.1 Enable Nagios on the Console Server
Select System: Nagios on the console server Management Console and tick the Nagios service Enabled.
Enter the Nagios Host Name that the Console server will be referred to in the Nagios central server—this will be generated from local System Name
(entered in System: Administration) if unspecified.
In Nagios Host Address enter the IP address or DNS name that the upstream Nagios server will use to reach the console server— if unspecified this
will default to the first network port’s IP (Network (1) as entered in System: IP).
In Nagios Server Address enter the IP address or DNS name that the console server will use to reach the upstream Nagios monitoring server.
Check the Disable SDT Nagios Extensions option if you want to disable the SDT Connector integration with your Nagios server at the head end—
this would only be checked if you want to run a vanilla Nagios monitoring.
If not, enter the IP address or DNS name that the SDT Nagios clients will use to reach the console server in SDT Gateway Address.
When NRPE and NSCA are both enabled, NSCA is preferred method for communicating with the upstream Nagios server— check Prefer NRPE to
use NRPE whenever possible (that is, for all communication except for alerts).
98
724-746-5500 | blackbox.com
Page 99

10.3.2 Enable NRPE Monitoring
Chapter 10: Nagios Integration
LES1102A
Serial
Nagios
Nagios monitoring host Remote Console server
Enabling NRPE allows you to execute plug-ins (such as check_tcp and check_ping) on the remote Console server to monitor serial or network
attached remote servers. This will offload CPU load from the upstream Nagios monitoring machine. This is especially valuable if you are monitoring
hundreds or thousands of hosts. To enable NRPE:
Select System: Nagios and check NRPE Enabled
Enter the details for the user connection to the upstream Nagios monitoring server and again refer to the sample Nagios configuration example
below for details about how to configure specific NRPE checks.
By default, the console server will accept a connection between the upstream Nagios monitoring server and the NRPE server with SSL encryption,
without SSL, or tunneled through SSH. The security for the connection is configured at the Nagios server.
check_
nrpe
NRPE
Figure 10-5. NRPE monitoring structure.
Network
Remote managed devices
10.3.3 Enable NSCA Monitoring
Tunneled SSH
LES1102A
Program/script send_ncsa
Nagios
Nagios monitoring host Remote Console server Remote managed devices
NSCA is the mechanism that allows you to send passive check results from the remote console server to the Nagios daemon running on the
monitoring server. To enable NSCA:
Select System: Nagios and check NSCA Enabled.
Select the Encryption to be used from the drop down menu, then enter a Secret password and specify a check Interval.
724-746-5500 | blackbox.com
NSCA
Figure 10-6. NCSA monitoring structure.
99
Page 100

1101 and 1102 Secure Device Servers
Refer to the sample Nagios configuration section below for some examples of configuring specific NSCA checks.
10.3.4 Configure Selected Serial Ports for Nagios Monitoring
The individual Serial Ports connected to the console server to be monitored must be configured for Nagios checks. See Chapter 10 for details on
enabling Nagios monitoring for Hosts that are network connected to the console server. To enable Nagios to monitor a device connected to the
console server serial port:
Select Serial & Network: Serial Port and click Edit on the serial Po rt # you want to monitor.
Select Enable Nagios, specify the name of the device on the upstream server and determine the check you want to run on this port. Serial Status
monitors the handshaking lines on the serial port and Check Port monitors the data logged for the serial port.
10.3.5 Configure Selected Network Hosts for Nagios Monitoring
The individual Network Hosts connected to the console server that you want to monitor must also be configured for Nagios checks:
Select Serial & Network: Network Port and click Edit on the Network Host you want to monitor.
Select Enable Nagios, specify the name of the device as it will appear on the upstream Nagios server.
Click New Check to add a specific check which will be run on this host.
Select Check Permitted TCP/UDP to monitor a service that you have previously added as a Permitted Service.
Select Check TCP/UDP to specify a service port that you want to monitor, without allowing external (SDT Connector) access.
Select Check TCP to monitor.
The Nagios Check nominated as the check-host-alive check is the check used to determine whether the network host itself is up or down.
Typically this will be Check Ping—although in some cases the host will be configured not to respond to pings.
If no check-host-alive check is selected, the host will always be assumed to be up.
You may deselect check-host-alive by clicking Clear check-host-alive.
If required, customize the selected Nagios Checks to use custom arguments.
Click Apply.
10.3.6 Configure the Upstream Nagios Monitoring Host
Refer to the Nagios documentation (http://www.nagios.org/docs/
The section entitled Distributed Monitoring steps through what you need to do to configure NSCA on the upstream server (under Central Server
Configuration).
NRPE Documentation was recently added that steps through configuring NRPE on the upstream server
http://nagios.sourceforge.net/docs/nrpe/NRPE.pdf
At this stage, Nagios at the upstream monitoring server is configured, and individual serial port and network host connections on the console server
are configured for Nagios monitoring. If NSCA is enabled, each selected check will be executed once over the period of the ch eck interval. If NRPE is
enabled, then the upstream server will be able to request status updates under its own scheduling.
.
10.4 Advanced Distributed Monitoring Configuration
10.4.1 Sample Nagios Configuration
An example configuration for Nagios is listed below. It shows how to set up a remote Console server to monitor a single host, with both network
and serial connections. For each check it has two configurations, one each for NRPE and NSCA. In practice, these would be combined into a single
check which used NSCA as a primary method, falling back to NRPE if a check was late— for details, see the Nagios documentation
(http://www.nagios.org/docs/
.
; Host definitions
;
; Black Box console server
define host{
use generic-host
) on Service and Host Freshness Checks
) for configuring the upstream server:
100
724-746-5500 | blackbox.com
 Loading...
Loading...