Page 1
2.1
Manual and
Application note
Page 2

Index
Introduction 1
CHAPTER1
Features 2
CHAPTER2
IVT - BlueSoleil software 3
CHAPTER3
Getting Started 6
CHAPTER4
BlueSoleil User Guides 38
Troubleshooting 70
FCC Caution 78
i
Page 3

i
Introduction
Bluetooth is an open specification for a cutting-edge technology that enables
short-range wireless connections between desktop and laptop computers,
personal digital assistants, cellular phones, printers, scanners, digital cameras
and even home appliances — on a globally available band (2.4GHz) for
worldwide compatibility. In a nutshell, Bluetooth unplugs your digital
peripherals and makes cable clutter a thing of the past. Now you can connect
your PDA or PC to Bluetooth™ enabled mobile phone with this Bluetooth™
adapter.
You can access e-mail & Internet no matter where you are with just a little help
from your Bluetooth™ mobile phone.
Plus, when you are back in the office, you can hook yourself up to your office
network as well as communicate with other Bluetooth™-enabled devices.
The device is designed to provide Bluetooth wireless functions on a Notebook
internal form Factor card. The Bluetooth function is based on CSR
BlueCore04-External Single Chip, This Bluetooth device is Cardbus interface or
USB compliant with USB V2.0 standard interface. It is fully support Bluetooth V1.1,
V1.2 , especially V2.0 Enhanced Data Rate. The Bluetooth application program
could be used in IVT software.
Page 4

Features
Features
y Bluetooth v2.0+EDR compliant
y USB v1.1 or Cardbus Interface
1
y Wireless access up to radius of 328 feet (100 Meters) for Class1
y Wireless access up to a radius of 32.8 feet (10 Meters) for Class2
y Connect up to 7 different enabled Bluetooth devices
y Encryption and authentication ensure safe, secure communications
y Low power consumption
Supported Profiles
y A2DP (Adv. Audio Dist. Profile)
y BIP (Basic Imaging Profile),
FAX (Fax Profile),
y
y FTP (File Transfer Profile),
y GOEP (Generic Object Exchange Profile),
y HCRP (Hard Copy Replacement Profile),
y
HID (Human Interface Device Profile),
y HSP (Headset Profile),
y OPP (Object Push Profile),
y PAN (Personal Area Network Profile),
y SDAP (Service Discovery Application Profile),
SPP (Serial Port Profile)
y
y SYNCH (Synchronization Profile),
Software & OS support
Microsoft Windows 98SE, Windows ME/2000 /XP, Mac OS 10.2.8 and above
2
Page 5

2
Welcome to BlueSoleil
Getting Started with IVT BlueSoleilTM
The following topics will help you learn more about BlueSoleil:
• Introduction
• Getting Started
• User Guides
Visit us at www.bluesoleil.com
Support: support@bluesoleil.com
3
Page 6
About BlueSoleil
BlueSoleil is Windows-based software from IVT that allows your Bluetooth®
enabled desktop or notebook computer to wirelessly connect to other
Bluetooth enabled devices. BlueSoleil allows MS Windows users to wirelessly
access a wide variety of Bluetooth enabled digital devices, such as cameras,
mobile phones, headsets, printers, and GPS receivers. You can also form
networks and exchange data with other Bluetooth enabled computers or
PDAs.
In order to connect and share services via Bluetooth wireless technology, two
devices must support the same Bluetooth Profile(s) as well as opposite device
roles (i.e., one must be the server, and the other must be the client). Bluetooth
enabled devices often support multiple profiles, and if involved in multiple
connections, can perform different device roles simultaneously.
BlueSoleil supports the following Bluetooth functions (Profiles) in the following
device roles:
Bluetooth Functions (Profiles) Client Server
AV Headphone* V V
Basic Image Profile V V
Dial-Up Networking V
Fax V
File Transfer V V
Headset* V V
Human Interface Device V
LAN access V V
Object Push V V
Personal Area Networking V V
Printer V
Serial Port V V
Synchronization V V
Notes:
• Only one Headset or AV Headphone connection can exist at a time, since
4
Page 7

there is only one virtual Bluetooth audio device.
• The Headset and AV Headphone Profiles do not work on Windows 98SE or
Windows Me.
Platforms supported by BlueSoleil include:
• Windows 98SE/ME
• Windows 2000/XP
Copyright
The information in this document is subject to change without notice. No part of
this document may be reproduced or transmitted in any form or by any means,
electronically or mechanically, for any purpose, without the express written
permission of IVT Corporation. Some parts of the content in this document
come from the Bluetooth Specification under the license.
IVT may have patents, patent applications, trademarks, copyrights, or other
intellectual property rights covering the subject matter in this document. Except
as expressly provided in any written license agreement from IVT, the
furnishing of this document does not provide any license to these patents,
trademarks, copyrights, or other intellectual property.
Copyright 2002, IVT Corporation. All rights reserved.
TM
BlueSoleil
, is a trademark of IVT Corporation.
Bluetooth is a trademark owned by Bluetooth SIG, Inc. and licensed to IVT.
Other product and company names mentioned herein may be the trademarks
of their respective owners.
5
Page 8

Getting Started
Basic operations for Bluetooth:
• Start Bluetooth
• Establish Bluetooth connection
BlueSoleil supported Bluetooth functions:
3
• AV Headphone
• Basic Imaging
• Bluetooth Synchronization
• Dial-Up Networking
• FAX
• File Transfer
• Headset
• Human Interface Device
• LAN Access
• Object Push
• Personal Area Network
• Printer
• Serial Port
For Bluetooth securities, please see:
• Bluetooth Security
6
Page 9

Start
BlueSoleil supports the following kinds of Bluetooth radio adapters: USB,
CompactFlash card (UART or BCSP).
With
The plug in and pull out of the USB dongle can be detected by BlueSoleil. You
can start BlueSoleil first and then plug in a USB dongle.
Cardbus Bluetooth just work on Windows 2000 and Windows XP
Bluetooth
1. Insert the USB dongle to your computer.
2. Start BlueSoleil.
Bluetooth
USB Dongle:
With
Cardbus Bluetooth
1. Insert the PC card to your computer and make sure the driver for the PC
card is installed correctly.
2. Start BlueSoleil.
PC card:
7
Page 10

Establish
A connection is normally initiated from the client.
• On the server side, start the service.
• On the client side, initiate the connection.
Bluetooth
Connection
Start Service on Server
If BlueSoleil provides service, please start the service:
1. Change to Service Window.
2. Right-click the service icon, select Start Service on the pop-up menu.
Initiate Connection on Client
In Main Window:
1. Single click my device, the center ball, to search the Bluetooth devices
in range.
2. Search the selected Bluetooth device service by double-clicking the
device icon.
Service button on the top of the BlueSoleil Main Window will be
highlighted if the service is supported by the device.
Enter the same Bluetooth passkey on both devices if necessary to pair
the two devices.
3. Connect.
Single-click the highlighted service button to establish the connection.
8
Page 11

Terminate
After a connection is established between a client and a server, users can
terminate it whenever he/she wants to. However, if the connection is
terminated by force while data are being transmitted, some useful data may be
lost. Please pay attention to this case.
Bluetooth
Connection
Terminate Connection on the Server
The way of terminating the connection on the server is to stop the service. This
may lead to losing data if there is data transmission going on. Accordingly, it is
recommended to terminate the connection on the client.
There are two ways to stop the service:
1. Select a started service and right click the service icon on the Service
Window. On the popup menu, select Stop Service. The service icon
turns white, and the service is stopped.
2. Select a started service. Select menu My Services | Stop Service. The
service icon turns white, and the service is stopped.
Note: The status of the active service can also be obtained by selecting the
menu item Status... from the context menu of the service icon.
Terminate Connection on the Client
On the Main Window, select the remote device first and right click the service
icon. On the popup menu, select Disconnect.
Note: For more details on how to disconnect a connection on the client, please
refer to Connect/Disconnect.
9
Page 12

Bluetooth
To modify your connection’s security settings, click My Bluetooth | Security.
BlueSoleil offers three security levels:
• Low (Security Mode 1, No security)
No security procedure is needed for connections.
• Medium (Security Mode 2, Service level enforced security)
Authentication or Authorization is requested when a specific service is
accessed by other Bluetooth enabled devices. If two devices are
connecting for the first time, or if two devices do not have a trusted
relationship, then the same passkey must be provided on both sides to
complete the Authentication. This mode allows you to assign different
access rights for each service supported by the server.
Security
• High (Security Mode 3, Link level enforced security)
If either of two devices is in Security Mode 3, Authentication is
requested whenever a connection is initiated between two Bluetooth
enabled devices. The passkey must be provided on both sides to
complete Authentication.
Note: In Security Mode 2, the user can add each authenticated device into a
trusted device list to expedite future connections.
AV Headphone
The AV Headphone Profile enables users to use a Bluetooth enabled
headphone to listen high-quality stereo music played in a computer.
Typical Usage
• Listen to music using a Bluetooth enabled AV Headphone.
10
Page 13

Steps:
1. Connect to AV Headphone.
2. Play music using media player software on your computer. Music will be
transmit wirelessly to the headphone.
Basic Imaging
The Basic Imaging Profile (BIP) enables users to receive pictures from a
Bluetooth device such as digital camera, mobile phone, or other compatible
device. It also enables remote control of shooting, display, and other imaging
functions.
Typical Usage
• Control Camera to take pictures
• Receive pictures sent from BIP-enabled digital devices
Control Camera to Take Pictures
Steps:
1. Connect to the camera. A Bluetooth Camera Controller will appear,
Figure 1.
2. Click the button to capture the image. The captured image will be
transmitted to your computer and displayed.
11
Page 14

Figure 1 Bluetooth Camera Controller
Receive Pictures
1. Assign the directory where you would like to save image files pushed
from the client device. Click My Services | Properties. Click on the Basic
Image Push tab. In the Set the image directory field, browse to select
the file location. Click OK.
2. Start the BIP service.
3. Send pictures from the remote device. For instructions, refer to the user
documentation for the remote device.
12
Page 15

Figure 2 Service Configuration
Dial-up Networking
The Bluetooth Dial-up Networking (DUN) Profile enables users to wirelessly
dial-up to Internet through a Bluetooth modem or a mobile phone that
supported the DUN Profile.
Typical Usage
• Dial-up to Internet via a Bluetooth enabled mobile phone.
• Dial-up to Internet via a Bluetooth enabled modem.
13
Page 16
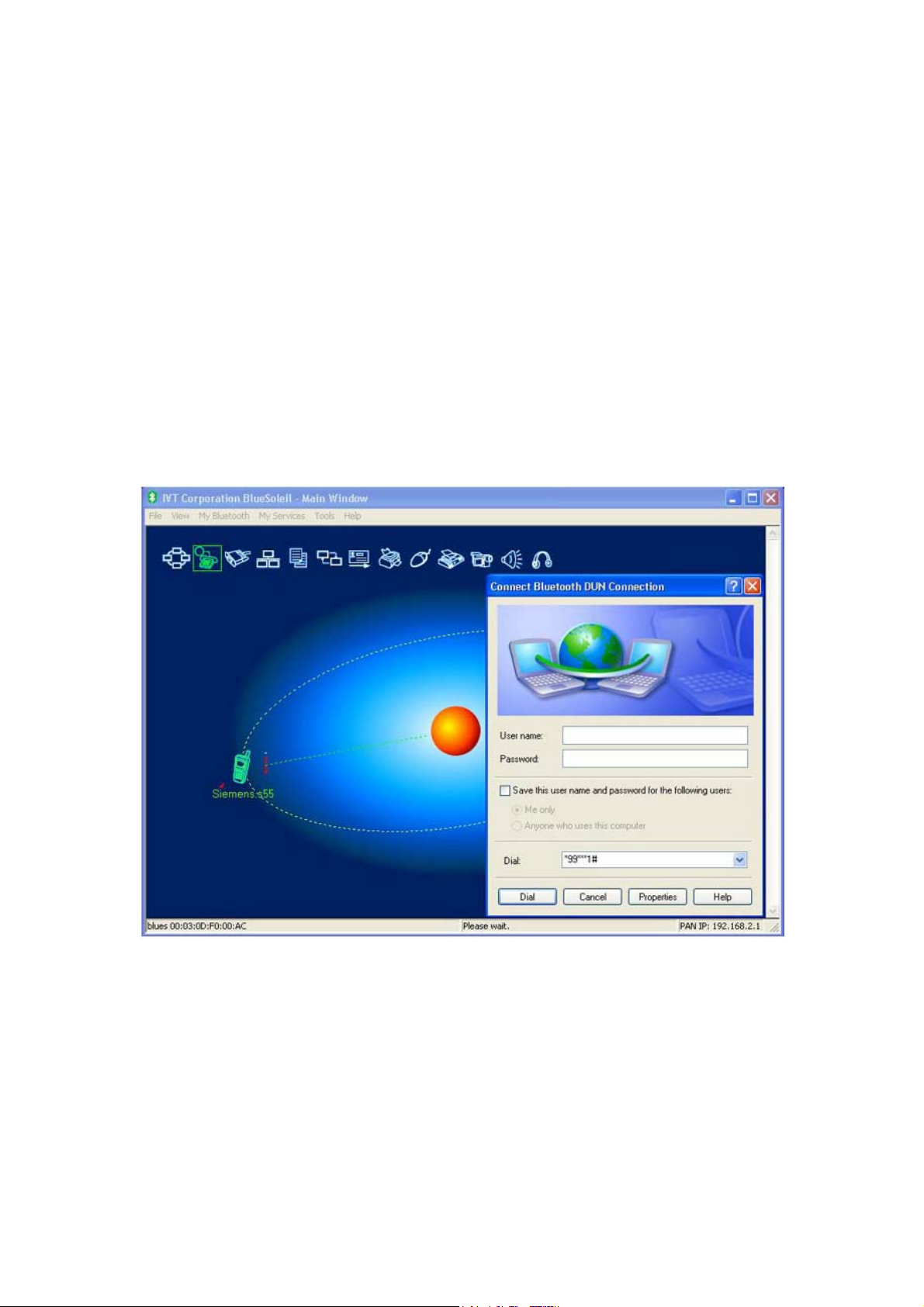
Dial-up to Internet via a
Bluetooth
mobile phone
1. Connect to the phone's Dial-Up Networking Service.
2. The Dial-Up Dialog will appear. Enter the dial-up number, User name,
and Password. Make sure the correct dial-up number is entered, then
click on the Dial button.
Note: The default dial-up number *99***1# only works with certain GPRS
phones and service providers. If necessary, enter the correct dial-up number
for your Internet Service Provider (ISP).
Figure 1 Dial-Up Dialog
Note: After you successfully connect, a screen will ask if you would like to
create a dial-up shortcut on your desktop. This would allow you to conveniently
dial up and connect by simply clicking on the shortcut, without having to
manually start BlueSoleil.
14
Page 17

FAX
The Bluetooth FAX profile enables users to send fax from a computer via a
Bluetooth enabled mobile phone or modem.
Typical Usage
• Send fax via a Bluetooth enabled mobile phone.
• Send fax via a Bluetooth enabled modem.
Send Fax via
1. Connect to the mobile phone's FAX service.
2. Use your fax software to send the message.
Send Fax via Bluetooth enabled modem
1. Connect to the modem's fax service.
2. Start your fax software. Configure your fax software for the Bluelet Fax
Modem (NOT the Bluelet Modem). Refer to your fax software’s user
documentation for instructions.
3. Use your fax software to send the message.
Bluetooth
enabled mobile phone
15
Page 18

File Transfer
The File Transfer Profile (FTP) enables users to transfer files and/or folders
between Bluetooth enabled laptops, desktops, PDAs, mobile phones, etc.
Typical Usage
• Connect to a Bluetooth enabled mobile phone and transfer files or
folders to/from the phone.
• Share a folder on your computer with other Bluetooth enabled devices.
• Access a shared folder on another Bluetooth enabled device.
Connect to a Phone
Steps:
1. Connect to the phone's FTP service.
2. The phone's folders are shown in a window. Users can
copy/paste/delete files or folders.
Share a Folder on Your Computer with other Bluetooth Enabled Devices
Steps:
1. Select the folder you would like to use for file sharing and define the
remote user privileges. Click My Services | Properties. Click on the
File Transfer tab.
Share this folder: Browse to select the folder your would like to share.
Share Permissions: Select Read and Write to allow others to copy,
paste or delete files/folders in this folder. Select Read Only to allow
others to only browse and copy files/folders from this folder.
2. Start the FTP service in BlueSoleil. Do not initiate the connection in
BlueSoleil.
16
Page 19

3. Browse your computer from the remote device. For instructions, refer to
the user documentation for the remote device. When the remote device
attempts to connect to your computer, the Bluetooth Service
Authorization screen may appear. Click Yes.
4. After successfully connecting, the remote device can browse, copy,
paste, and/or delete files on your computer, depending on the remote
folder privileges you allowed. For instructions, refer to the user
documentation for the remote device.
Access a Shared Folder on Another Bluetooth Enabled Device
1. On the remote device, designate the folder/files to share. Enable file
sharing on the remote device. For instructions, refer to the user
documentation for the remote device.
Note: If you do not enable file sharing on the remote device, BlueSoleil
will not be able to discover the device’s file sharing service.
2. Start the FTP service and initiate the connection in BlueSoleil.
3. A Remote Shared Folder screen will appear, displaying shared
files/folders on the remote device, Use the screen to browse, copy,
paste, and/or delete files, depending on your folder privileges.
17
Page 20
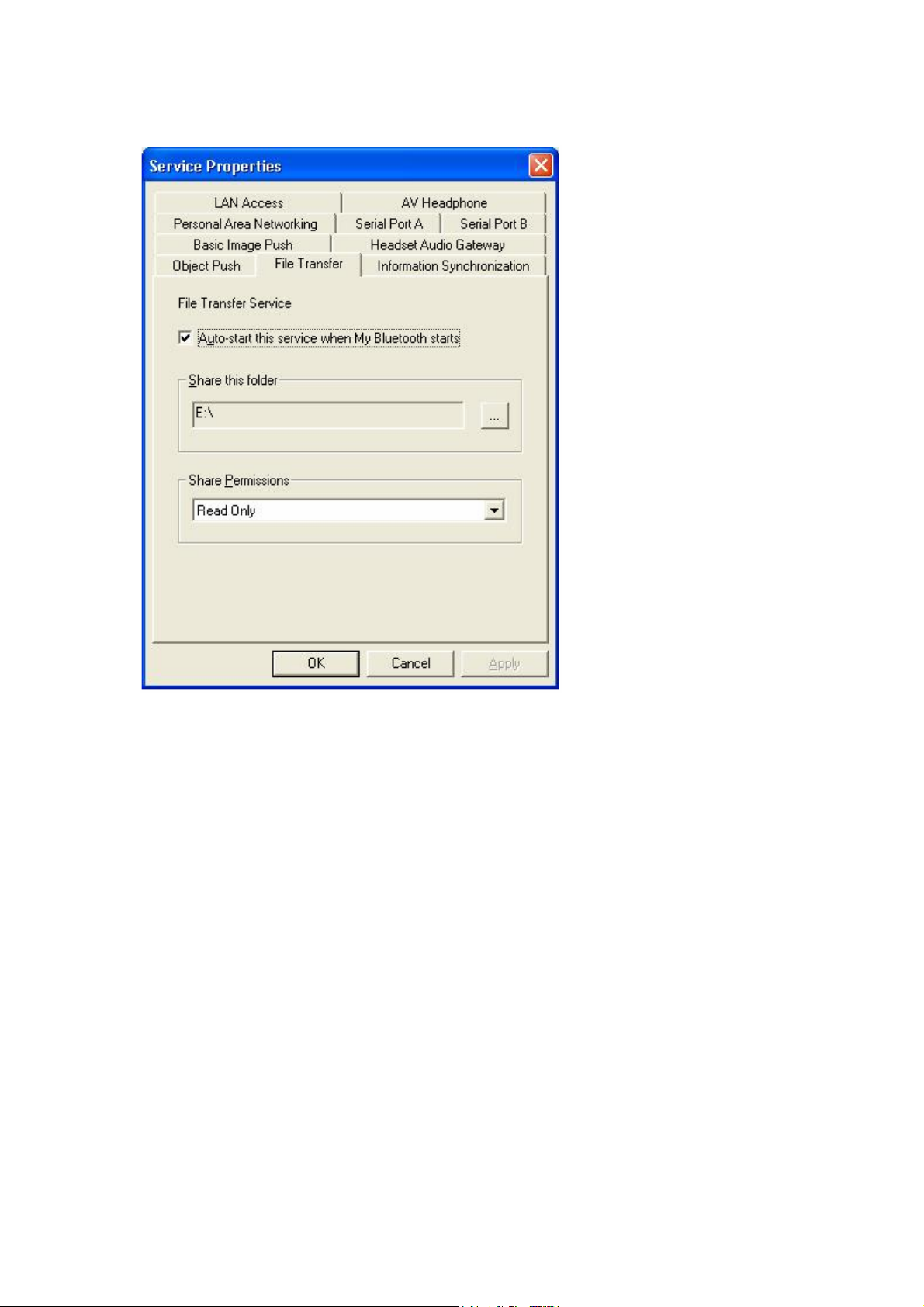
Figure 1: Service Configuration
Headset
The Headset Profile enables users to use a Bluetooth headset as wireless
earplug or microphone.
Typical Usage
• Use Headset as a device for audio input/output.
18
Page 21

Use Headset as Sound Input/Output Device
Steps:
1. Connect to the Bluetooth enabled headset.
2. Play music on your computer or chat using network meeting tools. You
may need to press a multifunction button on your headset to transmit
audio between the computer and the headset.
Note: For most Bluetooth enabled headsets, after you have successfully
connected for the first time, you can quickly reconnect to BlueSoleil by simply
pressing a multifunction button on the headset.
Human Interface Device
The Bluetooth Human Interface Device (HID) profile enables users to use
Bluetooth enabled HID Device such as keyboard, mice or joystick to control
your computer.
Typical usage
• Connect a Bluetooth enabled Mouse and a Keyboard to Your
Computer.
Connect a
Bluetooth
Mouse and a Keyboard to Your
Computer
1. Connect the Bluetooth enabled mouse to your computer.
2. Connect the Bluetooth enabled keyboard to your computer. Before you
can use BlueSoleil to connect, you may need to press a button on the
keyboard to make it discoverable.
19
Page 22

Note:
• The first time you connect the mouse or keyboard to your computer, the
Found New Hardware Wizard will automatically launch. In the first
screen of the wizard, DO NOT INSERT ANY CD and click Next. Follow
the next screens until you complete the wizard. If the wizard reappears,
cancel the wizard. You should be able to use the mouse or keyboard
with your computer.
• The Bluetooth enabled mouse/keyboard can automatically re-connect
to your computer after you successfully establish the initial connection.
LAN Access
The Bluetooth LAN Access Profile (LAP) allows users to access a Local Area
Network (LAN) via a Bluetooth enabled LAN access point.
Typical Usage
• Accesses a Local Area Networking via a Bluetooth enabled LAN access
point.
• Use your computer as a LAN Access Point.
Access a LAN via a
Bluetooth
enabled Access Point
(AP)
1. Connect to the LAN AP's LAP service.
2. In the Connect Bluetooth LAP Connection dialog, enter the user
name and password if necessary. Click Connect.
20
Page 23
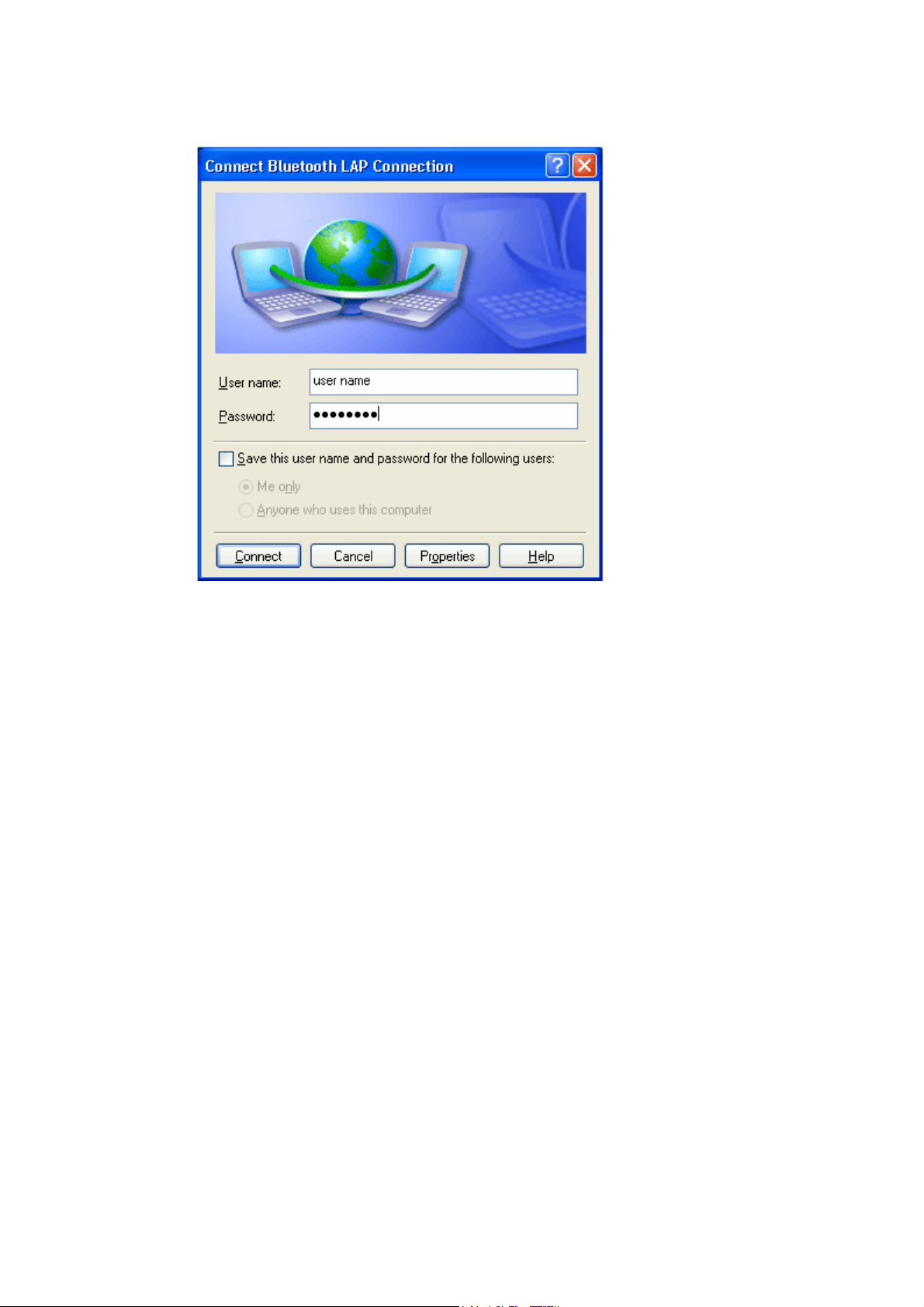
Figure 1 Connect Bluetooth LAP Connection
Use your computer as a LAN Access Point (Advanced
Users Only)
1. Start the Bluetooth LAP Access service on BlueSoleil.
2. Specify any static IP addresses for LAP clients (Alternatively, you can
use DHCP to have the system dynamically assign IP addresses).
(1) In the Network Connections window, right click Incoming
Connection, then select Properties (Figure 2).
21
Page 24
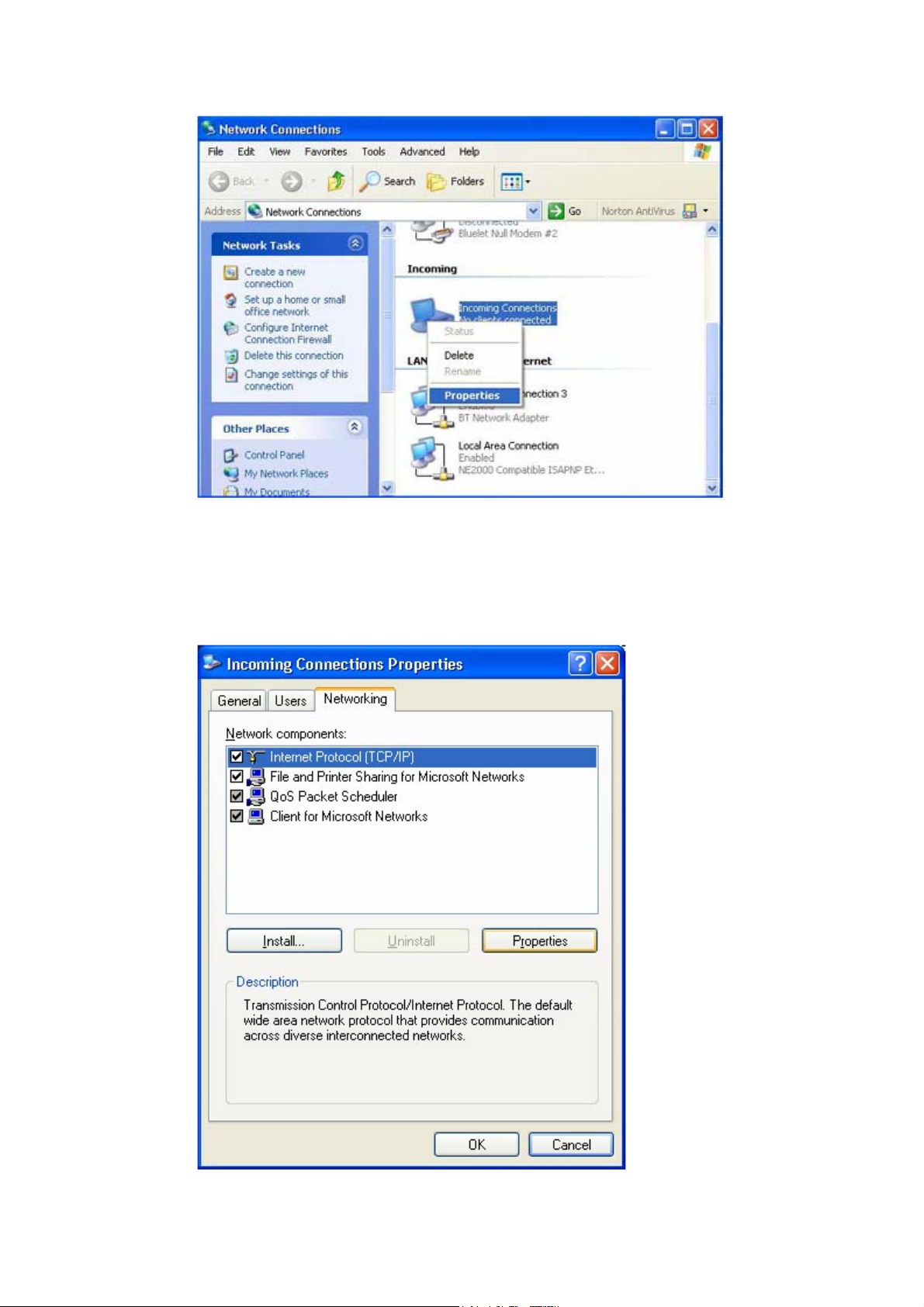
Figure 2 : Select Properties On the Pop-up Menu
(2) Select Incoming Connections Properties | Networking ->
Internet Protocol (TCP/IP), and click on the Properties button. (Figure
3)
22
Page 25

Figure 3 : Internet Protocol (TCP/IP) Network Component
(3) Select Specify TCP/IP addresses and enter the range of IP
addresses assigned to LAP clients (Figure 4).
Figure 4 : Enter the IP Addresses
Note: In order to use a Windows 98SE/Me system as an access point, you
must have already installed a Dial-up Adapter and the Windows Direct Cable
Connection component on the system.
Object Push
The Bluetooth Object Push profile (OPP) enables users to send and receive
Personal Information Management (PIM) data objects (Including messages,
notes, calendars items, and Business cards) to and from a Bluetooth enabled
PDA or mobile phone.
The objects supported:
• Contacts (*.vcf)
• Calendars (*.vcs)
• Notes (*.vnt)
• Messages (*.vmg)
23
Page 26

Typical Usage
• Push objects to a Bluetooth enabled mobile phone or PDA
• Receive objects from a Bluetooth enabled mobile phone or PDA
Note: If you would like to push PIM objects to a PDA, make sure that the PDA
is ready to receive a PIM object before you start. If necessary, enable Object
Push on the PDA. For instructions, refer the PDA’s user documentation.
Push Objects to a
Bluetooth
There are two ways to push objects:
1. From BlueSoleil Main Window:
Double-click on the mobile phone or PDA icon to browse for service
information. The Object Push Service icon should be highlighted at the
top of the screen. Right click the Object Push Service icon, and in the
pop-up menu click Send My Card. (Figure 1)
Mobile Phone
24
Page 27

Figure 1: Send Object
• Send My Card:
Send your default business card.
• Get Card:
Get the default business card of the phone.
• Send Objects:
Select some objects (PIM files in *.vcf, *.vcs, *.vnt, *.vmg) and send to
phone.
• Exchange cards:
Have your computer and the phone to exchange their default business
cards.
2. From MS Outlook:
(1) Select the contact that you would like to send.
(2) In Outlook, click on the Push button on the toolbar, or click File |
Push.
25
Page 28

Figure 2 Outlook Bluetooth Add-in
(3) The Bluetooth Neighbors screen will appear. In the device list, select
the phone or PDA that you wish to push the contact to. Click on the
Push button.
Figure 3 Select the Remote Device
26
Page 29

Receive Objects from a
Bluetooth
Phone
Steps:
1. Configure the parameters for the object push. From the Main Window,
click My Service | Properties. Click on the Object Push tab.
Figure 1: Object Push Service Configuration
2. Start Object Push service. Do not initiate a connection, only start the
service so that your computer will be ready to receive objects.
3. Send objects from the phone. For instructions, refer to your phone's
user documentation.
Notes:
27
Page 30

BlueSoleil creates a Bluetooth folder (with Inbox and Outbox subfolders)
•
in your My Documents folder for use with Object Push. The Inbox is
used to save objects received from other devices. The Outbox is used
to save objects sent out from your computer.
• Your can set your default business card by clicking My Services |
Object Push. In the Send My Business Card field, browse to select a
contact as your default business card.
Personal Area Networking
The Bluetooth Personal Area Networking (PAN) Profile enables PCs, laptops,
PDAs, and other Bluetooth enabled devices to form either of two kinds of PAN
networks. In a Group ad-hoc Network (GN), which functions as an isolated
network, multiple PAN Users (PANUs) are linked together via a GN controller.
Alternatively, a PAN can consist of multiple PANUs linked to a Network Access
Point (NAP), which provides access to external Local Area Network (LAN)
infrastructure. BlueSoleil supports all three of these device roles — GN
(controller), PANU, and NAP.
Typical Usage
• Group Ad-hoc Network (Peer-to- peer networking)
One device acts as the GN, and others function as PANU devices.
28
Page 31

These computers can visit each other or use an application based on
TCP/IP.
Figure 1: Group Ad-hoc Network
• Access a LAN via a Network Access Point (or a Computer Acting as a
NAP)
After the computers connect to the NAP, they become members of the
LAN and can directly communicate with other computers in the LAN.
Figure 2: Access LAN Via PAN-NAP
Connecting the PAN User (PANU)
1. Connect to the server's Personal Area Network service .
2. Wait for a few seconds for BlueSoleil to obtain and display your
computer's IP address.
29
Page 32

Configuring the NAP/GN
Click Bluetooth Service | Properties and click on the Personal Area
Network tab.
• Scenario 1: Group Ad-hoc Network
Select Set up Bluetooth Personal Area Network and Enable DHCP
Server (Figure 3).
A DHCP server will be started on the GN . The PANU can obtain an
IP address automatically from this DHCP server if the PANU does not
set static IP address for the BT Network Adapter.
Figure 3: Set Up Bluetooth Personal Area Network
• Scenario 2 : Access LAN via PAN-NAP
Select Access LAN Network and select a physical network adapter,
through which the NAP connects to a LAN, as the LAN Adapter (Figure
4).
30
Page 33

Figure 4: Access LAN Network
• Scenario 3 : Access Internet via NAP
Select Access Internet and select a physical network adapter, through
which the NAP connects to Internet, as the WAN Adapter (Figure 5). It
will automatically enables NAT (Network Address Translation, please
refer to Windows Help Topic) function and a DHCP server.
Note: The BT Network Adapter on the PANU side must be set to obtain an IP
address automatically. The IP address is in the form of 192.168.50.x, such as
192.168.50.1.
31
Page 34

Figure 5: Access Internet
Printer
The Bluetooth Printer Profile (HCRP) enables your compter to connect to a
Bluetooth enabled printer.
Typical Usage
• Print documents to a Bluetooth enabled Printer.
32
Page 35

Print Documents to a Bluetooth Printer
1. Connect to the printer's printer service.
2. (a) If your computer does not have the correct printer drivers installed,
BlueSoleil will prompt you to do so (Figure 1).
Figure 1 Bluetooth Printer Driver Is Not Installed
Install the driver for the printer, and remember to set the printer port to the
correct COM port number. To determine the correct COM port number, in the
Main Window, right-click on the device icon. In the pop-up menu, select Status.
(b) If the printer driver has been installed, a message indicates the Bluetooth
printer is ready (Figure 2).
Figure 2 Printer Driver Is Ready
3. Print documents using the Bluetooth enabled printer. In the application,
be sure to select the correct printer and printer port.
Serial Port
The Bluetooth Serial Port Profile (SPP) provides PCs, laptops, PDAs, GPS
receivers, cordless serial adapters, and other Bluetooth enabled devices with a
virtual serial port, enabling them to connect with each other wirelessly via
Bluetooth instead of a serial cable.
33
Page 36

BlueSoleil supports four Bluetooth Serial Ports for out-going connections and
two Bluetooth Serial Ports for incoming connections.
Typical Usage
• Connect to other Bluetooth enabled devices via the Serial Port.
Connect to a PDA
Steps:
1. Connect the PDA's Serial Port service.
2. Use ActiveSync or any software that uses a serial connection.
Note:
• Serial Port Auto-Connection function
Once a target device is assigned to a specific serial port, (e.g., COM5),
whenever an application opens that serial port, BlueSoleil will
automatically connect to the target device. Similarly, whenever an
application closes the Bluetooth serial port, BlueSoleil will stop the
connection. To check which devices are assigned to which COM ports,
click Tools | Configurations | Quick Connect...
• Some applications only allow you to use a limited range of COM port
numbers. If the application does not allow you to use a COM port
number assigned by BlueSoleil, you will not be able to use BlueSoleil
with your application.
Bluetooth
The Bluetooth Synchronization (SYNC) Profile enables users to synchronize
PIM objects on their computer with that of other Bluetooth enabled computers
as well as Bluetooth enabled mobile phones, PDAs, and other devices.
Synchronization
34
Page 37

Four kinds of objects are supported:
• Contacts (*.vcf)
• Calendars (*.vcs)
• Notes (*.vnt)
• Messages (*.vmg)
Supported Outlook versions: MS Outlook 2000, Outlook 2002 (xp), Outlook
2003.
Typical Usage
• Synchronize your computer with a Bluetooth enabled mobile phone
Synchronize with a
Bluetooth
enabled Mobile Phone
Steps:
1. Connect to the mobile phone's Synchronization service.
2. A synchronization dialog will appear (refer to Figure 1). Click on the
Start button to synchronize. Contacts, calendars, notes and emails in
MS Outlook will be synchronized with those on the phone.
35
Page 38

Figure 1:
Start To Synchronize Information
Note:
• Users can start synchronization from MS Outlook using the Bluetooth
Add-In menus and buttons installed with BlueSoleil.
• BlueSoleil can act as synchronization server. Click My Services |
Properties. Click on the Information Synchronization tab (Figure 2),
and select the type of PIM objects that you would like to synchronize.
36
Page 39

Figure 2: Service Configuration
37
Page 40

4
BlueSoleil User Guides
This chapter describes BlueSoleil User Iterface and how to do various
configurations and operations. It includes:
• BlueSoleil Environment
• Bluetooth Connection Management
• Configurations
• Bluetooth Security
For details on how to use Bluetooth profiles in BlueSoleil , please refer to
Getting Started with BlueSoleil .
BlueSoleil Environment
The BlueSoleil Graphic User Interface includes:
• Main Window
• Service Window
• Menus
Main Window
Main Window displays the local device (red ball) and the remote devices
detected in range. Connecting and disconnecting operations are conducted
here. Connections are indicated in lines between the local device and
connected remote devices.
38
Page 41

By default BlueSoleil starts with the Main Window open. To return to the Main
Windows after switching views, click View | Main Window.
The following elements are included:
• Local Bluetooth Device
• Remote Bluetooth Devices
• Bluetooth Service Buttons of Remote Device
Local
The Local Bluetooth enabled device, known as "My Device", represents the
user's computer that is running BlueSoleil.
Icon:
Operations:
• Hover mouse to display the local Bluetooth device's name or address
(if without name).
• Click on the red ball to start or stop searching for Bluetooth devices in
range.
Bluetooth
Device
• Right-click on the red ball to display a pop-up menu of related
operations (e.g., General Inquiry, My Services, Security, etc.).
Remote
Remote devices are other Bluetooth enabled devices that are in the Bluetooth
radio range of your local device. BlueSoleil uses different icons to indicated
different types of remtoe devices..
Bluetooth
39
Devices
Page 42

Icons
Icon Meanings
Remote devices can be in any of three states, which BlueSoleil indicates with
different colors.
• White- Idle. The normal state of the device.
• Yellow- Selected. you have selected the device.
• Green- Connected. The device is connected to your computer.
40
Page 43

Operations
• Single-click on the icon to select.
• Double-click on the icon to search for the services supports by the
remote Bluetooth device .
• Right-click on the icon to display a pop-up menu of related operations
(e.g. Refresh Services, Pair Devices, Connect, etc.).
Bluetooth
Service Buttons of
Remote Device
Service buttons at the top of the Main Window represent a range of Bluetooth
services potentially supported by Remote Devices .
41
Page 44

Icon Meanings
There are 3 states for the service icons, indicated by different colors.
• White- Idle. The normal state.
• Yellow- Available. The Bluetooth service is available on the selected
remote device.
• Green- Connected. The Bluetooth service is active in a connection with
the remote device.
Operations
• Hover your mouse over the service icon to display the name of the
service.
• Single-click on the service icon to connect.
• Right-click on the service icon to display a pop-up menu of related
operations.
42
Page 45

Service Window
The service Window displays the local Bluetooth services, (i.e., the Bluetooth
services supported by BlueSoleil). Use the Service Window to start and stop
services, as well as to configure service properties. To access the Service
Window, click View | Service Window.
The following elements are included:
• Local Service List
• Service Status
Local Service Status
The local service status can be viewed from the Local Service Status dialog
box.
Right click whichever local service icon in service window and select the
Status... on the pop-up menu.
The Local Service Status dialog will be displayed.
43
Page 46

Figure1: Local Service Status (e.g. Serial Port A service)
Connection:
Status: Whether the local service is connected.
Device Address: Display the Bluetooth address of remote device which
connect to the service.
Duration: The time elapsed since the connection was set up.
COM Port: The virtual Bluetooth COM ports connected by remote device.
PAN Service Status dialog is different from others.
44
Page 47

Figure2: Local Service Status (PAN)
Connection:
Status: Whether the local service is connected.
Device Name: Display the name of remote device which connects to the
service.
Duration: The time elapsed since the connection was set up.
Connection List:
Display the names and addresses of remote devices which connect to the
PAN service.
45
Page 48

Local Service List
The Local Service List displays all the Bluetooth services supported by the
local computer. Use this screen to start/stop services.
Icon Meanings
There are 3 states for the local Bluetooth services, indicated by different icon
colors.
• White- Idle. The service has not been started.
• Yellow- Started. The local Bluetooth service has been started.
• Green- Connected. Some remote device has connected to the service.
46
Page 49

Operations
• Single-click on the icon to select the service.
• Double-click on the icon to Start/Stop a service.
• Right-click to display a pop-up menu of related operations.
Menus
BlueSoleil contains the following six menus:
• File Menu
• View Menu
• My Bluetooth Menu
• My Services Menu
• Tools Menu
• Help Menu
File Menu
• Hide --- Hide the BlueSoleil window. Connections can still run when the
window is hidden.
• Always on Top --- Keep BlueSoleil window always on top.
• Exit --- Exit BlueSoleil.
Note: You can also exit BlueSoleil by right-clicking on the task tray icon at
the bottom of your screen. In the pop-up menu, click Exit.
47
Page 50

View Menu
• Main Window --- Show the BlueSoleil Main Window .
• Service Window --- Show the BlueSoleil Service Window.
• Arrange Devices --- Arrange all remote devices by Device Name,
Device Address or Device Type.
• Refresh Devices --- Refresh the list of remote devices detected by
BlueSoleil.
Note: If you select Refresh Devices, the list of previously detected devices
will not be cleared. To initiate a new device search that will first clear the list,
press F5.
My
Bluetooth
• Bluetooth Device Discovery --- Search for other Bluetooth enabled
Menu
devices in range.
• Bluetooth Service Discovery --- Browse for the services of the
selected remote device.
• Security --- Configure the security setting of the local device (e.g.
passkey requirement, data encryption, etc.).
• Properties --- Configure the properties of the local device (e.g. device
name, accessibility, etc.).
My Services Menu
• Start Service --- Start the selected local Bluetooth service.
• Stop Service --- Stop the selected local Bluetooth service.
• Status --- View the status of the selected local Bluetooth service.
48
Page 51

•
Properties --- Configure the properties of the local Bluetooth services
(e.g., automatic connections, shared file locations, etc.).
Tools Menu
• My Bluetooth Shortcuts --- Display dialog My Bluetooth Shortcuts.
(Figure 1)
(1) Connect: Connect the selected shortcut.
(2) Delete: Delete the selected shortcut.
Figure 1 My Bluetooth Shortcuts
• Find Device --- Click to find a device, by either of two search criteria.
(Figure 2)
o By Bluetooth Device Address:
Enter a Bluetooth device address, in standard format:
(xx:xx:xx:xx:xx:xx), and click on the Find button. The device with
the specified address will appear highlighted in the Main
Window.
o By Name:
Check the By Name checkbox, enter the Name of the device,
and click on the Find button. The device with the specified name
will appear highlighted in the Main Window.
49
Page 52

Figure 2 Find Device
• Add New Device --- Add a remote device by entering its Bluetooth
device address. (Figure 3)
Figure 3 Add New Bluetooth Device
• Add Device From History --- Add a remote device from history list.
(Figure 4)
(1) Add: Add the selected device to the Main Window.
(2) Delete: Delete the selected device from the history list.
50
Page 53

Figure 4 Add Device From History
• Configurations-> Quick Connect --- If desired, assign a remote
device to automatically connect with whenever an application opens a
specified Bluetooth serial port.
(1) Assign: Assign a device to the selected port.
(2) Remove: Remove the Auto-Connection device assignment for the selected
port.
Figure 5 Quick Connect
51
Page 54

•
Configurations->Unplug HID --- Remove Human Interface Devices
from BlueSoleil. (Figure 6)
Unplug: Unplug the selected HID device.
When you first connect the HID device to your computer, BlueSoleil sets
up the devices so that they will automatically reconnect in case the
connection is ever broken. After you unplug an HID device, it will no
longer automatically reconnect to your computer.
Figure 6 Unplug HID Device
• My Bluetooth Device --- Advanced hardware configuration,
recommended for advanced users only. Please refer to Hardware
Configuration for more details.
Help Menu
• Contents and Index --- Access BlueSoleil Online Help.
• About BlueSoleil --- Information about your version of BlueSoleil.
52
Page 55

Bluetooth
Connection
Management
Bluetooth Connection Management includes:
• Find Remote Devices
• Connect and Disconnect
• Connect via Shortcuts
• Remote Device Status
• Remote Device Properties
Find Remote Devices
To set up a Bluetooth connection, the remote device must be found first. There
are 3 ways to find remote devices in BlueSoleil.
Inquire Device
1. Single-click the red ball in the main window to start inquiry.
2. Bluetooth devices within the radio range will be shown around the
center ball.
3. Wait for a few seconds until the names of all the devices are obtained.
Add Device from History List
The devices which had been found or connected can be added from the
history device list directly.
1. Select menu Tools | Add Device from History.... The History dialog
box pops up.
53
Page 56

2. Select the device from the list and click button Add, the device will be
added to the main window.
Add a New Device by Entering Device Address
If the device cannot be found by Inquiring, you can enter the device address
to add the device.
1. Select menu Tools | Add New Device.... The Add New Device dialog
pops up.
2. Enter the Bluetooth device address and click button OK, the device will
be added to the main window.
Note: The device type will be unknown if add it by inputting its Bluetooth
address.
Connect and Disconnect
Connect
1. Select a remote device and double click it to browse its services.
Bluetooth passkey may be asked if security level of either side is set to
high and they are not paired devices.
After service browsing, the services the remote device supports are
highlighted by changing the color of the service buttons on the top of the
main window.
2. Single click one of the service button to connect.
After connection is setup, the remote device and the service button will
turn green.
Note: Users can right click the remote device icon or the service button to pop
up operation menu for connection.
54
Page 57

Disconnect
Method 1: Select the remote device, right click the service button. On the
popup menu, select Disconnect.
Method 2: Right click the device icon. On the pop-up menu, select Disconnect
| (the connection you want to disconnect).
Method 3: For FTP and Synchronization connection, close the operation
window, the connection will be disconnected.
Method 4: Disconnect from the remote device directly.
Method 5: If the local Bluetooth device is removed or the remote device is
powered off, all the connections will be disconnected. If the remote device
moves out of the radio range, all the connections with the remote device will
be disconnected in 1 minute.
Connect via Shortcuts
After a connection is set up, users can generate a shortcut on Windows
desktop. Users can connect later using the shortcut without device inquiry and
service browsing steps.
Shortcuts applies to Personal Area Networking, Dial-Up network, HID and AV.
Steps
1. Save shortcut
After connected, right click the device icon, select the Save
Connection as Shortcut on the popup menu.
2. Execute the shortcut on desktop.
Remote Device Status
The remote device status can be viewed from the Remote Device Status
dialog box.
55
Page 58

Right click the remote device icon and select the Status... on the popup menu.
The Remote Device Status dialog box will be displayed.
Figure 1 Remote Device Status
• Connection:
Device Name: The remote Bluetooth device's name.
Status: Whether the remote device is connected to the local device.
Duration: The time elapsed since the connection was set up.
Paired: Whether this device is paired with the local device.
Role: The Bluetooth Master/Slave role of the remote device for this
connection.
COM Port: The virtual Bluetooth COM ports used for the
connection(s), especially for DUN, FAX, SPP, and LAP.
• Activity:
The amount of the data sent and received.
56
Page 59

Radio Signal Strength:
•
This is the RSSI of the remote device. This index indicates the radio
quality between the remote device and the local device. If the radio
signal is too weak, the data transferring speed will be slow.
• Properties Button:
Display the remote device’s properties.
• Disconnect Button:
Disconnect one of the connection(s) between the remote device and the
local device.
• Unpair Button:
Remove the paired relationship between the remote device and the
local device.
Remote Device Properties
The remote device’s properties can be viewed from the Remote Device
Properties dialog box.
Right click the remote device icon and select the Properties... on the popup
menu. The Remote Device Properties dialog will be displayed.
Figure 1 Remote Device Property Dialog
57
Page 60

Device Name: The remote Bluetooth device's name.
Device Class: The remote device's device class. Bluetooth devices are
classified by device type, such as Desktop, Laptop, Headset, LAN Access
Point, and other enabled devices.
Device Address: The remote device's Bluetooth device address.
LMP Feature: The features that the remote device supports.
LMP Version: The version of the LMP firmware of the remote device.
Manufacturer: The manufacturer of the remote device.
Device Configurations
The local device configurations include:
• Local Device Hardware Configuration
• Local Device Properties Configuration
Hardware Configuration
BlueSoleil supports the following kinds of Bluetooth radio adapters: USB,
CompactFlash card (UART or BCSP).
To access the hardware configuration screens, click Tools | My Bluetooth
Device...,
• Bluetooth Device
Select the type of Bluetooth enabled device that you plan to use, either
a USB adapter or a CompactFlash (CF) card. (Figure 1).
58
Page 61

Figure 1 Select Bluetooth Device
• Advanced Configuration
The Advanced Configuration page will be enabled only if you selected
CF card in the Bluetooth Device screen. Use the Advanced
Configuration screen to configure detailed parameters including COM
Port, Baud Rate, Byte Size, Parity, Stop Bits, and Flow Control.
Figure 2 Advanced Configurations For UART Hardware Device
59
Page 62

Properties Configuration
To configure the properties of your local device, click My Bluetooth | Device
Properties…,
General
• Device Name
The local device's name, which will be shown to other Bluetooth
enabled devices.
• Device Type
The device's type of your local computer (i.e., Desktop, Laptop or
Server).
• Device Address
The address of the local device. Every Bluetooth enabled device has a
unique address.
Figure 1 General Properties Page
60
Page 63

Accessibility
Connecting Mode
• Connectable: Permits other Bluetooth enabled devices to connect with
your computer.
• Non-Connectable: Prohibits other Bluetooth enabled devices from
connecting with your computer.
Discovery Mode
• General Discoverable: Permits other Bluetooth enabled devices to
detect your computer.
• Limited Discoverable: Permits other Bluetooth enabled devices to
detect your computer with Limited Inquiry.
• Non-Discoverable: Prohibits other Bluetooth enabled devices from
detecting your computer.
Bonding Mode (Pairing Mode)
• Accepts Bonding: Allow other Bluetooth enabled devices to pair with
your computer. If the other device initiates a pairing procedure with your
computer, each device must enter the same passkey before they will be
paired.
61
Page 64

Does Not Accept Bonding: Rejects pairing attempts initiated by other
•
Bluetooth enabled devices.
Figure 2 Accessibility Properties Page
Hardware
View information about your Bluetooth hardware.
• Manufacturer: The manufacturer of the local Bluetooth device.
• HCI Version: The HCI version of the local Bluetooth device.
• HCI Revision: The HCI revision of the local Bluetooth device.
• LMP Version: The LMP version of the local Bluetooth device.
62
Page 65

LMP Subversion: The LMP subversion of the local Bluetooth device.
•
Figure 3 Hardware Properties Page
Security Configuration
Use the Security Configuration screens to specify the security settings of your
local device, it includes:
• General Security
• Paired Devices Management
• Local Services Security
Pair / Un-pair Devices
Once a remote device has paired with your computer by exchanging passkeys,
passkeys will no longer be required for further connections between your
computer and the device.
63
Page 66

How to pair with another device
• Automatically
If a passkey is required for connection, the devices will be paired
automatically the first time they successfully exchange passkeys and
connect. After a device has successfully paired with your computer, the
remote device icon in the Main Window will have a red checkmark next
to it.
• Manually
In the Main Window, right click on the device icon, and in the pop-up
menu, select Pair Device. In the Enter Bluetooth Passkey dialog,
enter the same passkey that you enter on the remote device. After a
device has successfully paired with your computer, the remote device
icon will have a red checkmark next to it.
How to un-pair with another device
• Manually
In the Main Window, right-click on the device icon, and in the pop-up
menu, select Unpair. The red checkmark next to the device icon will
disappear.
General Security
To access the security configuration screen, click My Bluetooth | Security…
Security Level
• Low
If checked, other devices will be able to access your device freely
without entering a passkey.
64
Page 67

However, if the remote device requires a passkey to connect, then both
devices need to exchange passkeys.
• Medium
The medium level is service level security, you can assign the
appropriate level of access for each specific service. For more detail,
see Local Services Security.
• High
If checked, passkeys must be exchanged for every incoming and
outgoing connection, unless the two devices have already paired in the
past.
Bluetooth
• Set Default Passkey
Use this setting to set a default passkey for all connections. BlueSoleil
will use this passkey whenever one is required.
Passkey
Data Encryption
• Enable Data Encryption
If checked, the data transmitted will be encrypted.
Paired Devices Management
To access the device security configuration screen, click My Bluetooth |
Security and click on the Devices tab.
Paired Devices List Box
This screen lists devices which have already paired with the local device.
Remove Pairing Button
65
Page 68

Click to remove the pairing relationship between the selected device and the
local device.
Authorize Services Button
Click to select which services you authorize the selected paired device to use.
A list of local services will appear. Select the services you wish to allow the
remote device to use, then click OK.
Figure 1 Authorize Services
Note:
• The screen will only list the local services that require authentication.
The local services that do not require authentication can be accessed
freely.
• The Authorization button is enabled only when the Security Level is set
to Medium.
Local Services Security
To access the local services security configuration screen, click My Bluetooth
| Security and click on the Services tab. You can only configure security for
66
Page 69

local services when the Security Level is set to Medium. (Set the Security
Level in the General Security.)
Local Services:
• Authentication
If checked, a passkey is required whenever a remote device attempts to
connect with this service.
• Encryption
If checked, data transmitted between devices for this service will be
encrypted.
Authorization Button:
Click to select the devices you wish to allow to use the selected service.
67
Page 70

In the Service Authorization screen, enter the following settings:
• Trusted Devices
Select to trust devices listed in this screen to use the selected service
on your device.
A device can freely access the service from your local device when
trusted. Click Add/Remove to edit the device list.
• Trust all devices
Connection requests will be accepted from every device.
• Prompt to user if the device is not a trusted device of this service
If a non-trusted device attempts to access the service, a dialog will
appear to allow you to accept or reject the connection.
• Reject the device to use the service if it is not a trusted device of
this service
If a non-trusted device attempts to access the service, the connection
will be rejected automatically without informing the user.
68
Page 71

Notes: If a device is trusted for a service, it may connect to this service on your
local device without informing you.
69
Page 72

Troubleshooting
Cannot start My
When the program starts, the local device address is 00:00:00:00:00:00.
Please check whether you have properly plug-in your Bluetooth USB dongle or
Bluetooth CF card and whether the device is powered up. Bluetooth USB
dongles can be detected automatically if they are in the IVT known device list
(If you are using a device of a new model, please contact IVT so that the model
can be added to the list). Some Bluetooth CF card device cannot be detected
automatically. Users need to configure the parameters in the menu Tools |
Bluetooth Device... to enable the device.
How can I find my
Bluetooth
Bluetooth
?
device information?
On the center ball, my device, right click and select Properties... on the popup
menu. In the My Bluetooth Device dialog box, there are device names,
device addresses, device manufacturers, device HCI and LMP (Link Manager
Protocol) versions and editions.
Can't find the remote device you want?
First, please check whether the remote device is in discoverable mode. If the
remote device is set to non-discoverable, other devices cannot find it. Second,
please check whether the remote device is within the radio range. Bluetooth
devices have 3 classes. Class 1 devices are high power devices. Their
transmission range are 50-100 meters. Class 2 and class 3 devices are low
power devices. Their transmission range are 10-20 meters. If you still cannot
find the remote device, you can (1) find the device from the history list, so that
70
Page 73

you can add it directly to the Main Window. Do this via Tools | Add Device
from History.... (2) If the device is not in the history list, you can also add a
new device directly by inputting the remote device address. Do this via Tools |
Add New Device....
Can't find the remote device's services?
First, please verify that whether the remote device is in connectable mode. If
the remote device is set to non-connectable, other devices cannot connect
to it.
Second, please verify whether the remote device is within the radio range.
Third, please check whether the remote device has connections already.
Currently, some Bluetooth devices do not support scatter net. That is, the
device has limitations in supporting connection among multi-devices at the
same time. It is recommended that users try to connect one to one if the
connection cannot be set up.
Fourth, please verify whether both sides have input the right Bluetooth
passkey if any side is at security level High. The Bluetooth passkey must be
the same at both sides. If both sides have set Fixed Passkey (the default
passkey) and the passkeys are different, the connection cannot be set up
because of the authentication failure.
71
Page 74

Terms
A B C D E F G H I J K L M N O P Q R S T
U V W X Y Z
A
Authentication Authentication is the process of verifying "who" is at the
other end of the link. Authentication is performed for devices. In Bluetooth this
is achieved by the authentication procedure based on the stored link key or by
pairing (entering a PIN).
Authorization Authorization is the process of deciding if device X is allowed
to access service Y. This is where the concept of "trusted" exists. Trusted
devices (authenticated and indicated as "trusted"), are allowed to access
services. Mistrusted or unknown devices may require authorization based on
user interaction before access to services is granted.
B
Bluetooth Bluetooth is an open specification for a cutting-edge technology
that enables short-range wireless connections between desktop and laptop
computers, personal digital assistants, cellular phones, printers, scanners,
digital cameras and even home appliances on a globally available band
(2.4GHz) for worldwide compatibility. In a nutshell, Bluetooth unplugs your
digital peripherals and makes cable clutter a thing of the past.
Bluetooth Authentication Bluetooth authentication is the procedure to
verify whether another Bluetooth enabled device has the right to access your
computer. During this procedure, a Bluetooth passkey is asked for on both
connection sides. If the passkeys are the same, the authentication procedure
is a success and the connection can be setup. If the passkeys are different,
then authentication fails and the connection cannot be set up.
Bluetooth Authorization Bluetooth authorization is the procedure to verify
whether you are going to allow (authorize) other Bluetooth enabled devices to
use Bluetooth services on your Bluetooth enabled devices. This procedure
functions in Bluetooth security Mode 2 and applies only to your Bluetooth
services. Every Bluetooth service in your BlueSoleil has the setting of
72
Page 75

authorization. And there is an authorization devices list for every service, which
records the devices that you have authorized. The user can change the
authorization status for each device.
Bluetooth Connection Bluetooth functions are in the model of
Client/Server. One Bluetooth device provides services, and another Bluetooth
device uses these Bluetooth services. After connection, a Bluetooth link is set
up between two devices, and the link is called a Bluetooth connection. Users
can disconnect the connection after finishing his job on Bluetooth.
Bluetooth Connection Shortcut Connection shortcut is used for saving
time in searching devices and browsing services. After a connection is
established, it can be saved as a shortcut. The shortcut can be used later to
re-establish the connection, without searching the remote Bluetooth devices
and browsing services. After a connection is setup, the connection can be
saved as a shortcut, which can be used later without searching Bluetooth
devices or browsing services.
Bluetooth Device Bluetooth devices are addressed in two ways: (1) When
referring to the local device configuration, a Bluetooth Device is the local
Bluetooth hardware which can be a USB dongles, a UART device, a PCMCIA
card or a BCSP device. The user is expected to select the interface of his
Bluetooth device in his configuration. (2) When referring to the Bluetooth
application, it is the Bluetooth system as a whole, e.g. a Bluetooth modem,
Bluetooth mobiles or a Bluetooth PDA etc. My PC together with the BlueSoleil
and the Bluetooth dongle would also be addressed as a remote Bluetooth
device by other Bluetooth devices.
Bluetooth Device Address A unique 48-bit address that distinguishes
between different Bluetooth transceivers. Every Bluetooth device has a unique
address so that other devices can find it and communicate with it. The address
appears in the form of 00:03:20:00:0D:0A.
Bluetooth Device Class According to the Bluetooth standard, every
Bluetooth device is assigned a device type, which is represented in device
class. The Bluetooth device class is three bytes in length in the form of
04:01:00. On the computer side, the class may be Server, Desktop or Laptop.
Users will be asked to select it during the first time starting.
73
Page 76

Bluetooth Device Inquiry To use Bluetooth, the user has to find the
remote device first. The searching procedure is called device inquiry. There
are two kinds of inquiry procedure, named General Inquiry and Limited Inquiry.
General Inquiry will find all the Bluetooth devices in general discoverable mode
and limited discoverable mode. Limited Inquiry will find only the devices in
limited discoverable mode.
Bluetooth Dongle A Bluetooth device which can be added onto a PC or a
notebook to make it Bluetooth enabled. Typically a USB device.
Bluetooth bonding A user initiates the bonding procedure and enters a
passkey to create a paired relationship between two devices. This differs
from the authentication procedure where the user is requested to enter a
passkey during the establishment of a link.
Bluetooth Passkey In the Bluetooth authentication procedure, a Bluetooth
passkey is requested on both connection sides. The same Bluetooth passkey
should be input on both sides. If the passkeys are the same, the authentication
procedure is successful and connections can be setup. If the passkeys are
different, the connection and authentication will fail.
Bluetooth Peripheral Device This is the implementation of the Bluetooth
Human Interface Device profile (HID). By using HID, a Bluetooth peripheral
input device such as Bluetooth mouse or keyboard can interface with the host
PC remotely.
Bluetooth Security Bluetooth security is an important part for the wireless
communication technology. Illegal access to your computer can be rejected.
There are three levels of security: Low, Medium and High. In Low level, there
is no security check. In Medium level, remote Bluetooth devices can browse
your services. Security is set on every service. The service can be set to
request or not request for authentication and authorization. If you request for
authentication, the remote device will be asked to enter the same passkey as
the one in your PC . Otherwise, the Bluetooth passkey is not asked. If
authorization is set, the remote device has to be in the authorized devices list.
If not, there will be a dialog to ask the user to confirm whether you are going to
allow a remote device to use a services of the local device.
Bluetooth Service A Bluetooth device may offer certain functions for
other Bluetooth devices to use. These functions are called Bluetooth services.
74
Page 77

For example, a Bluetooth mobile phone can offer 4 services, which include
synchronization, dial-up networking, file transfer and serial port. In BlueSoleil,
some services are started automatically and other services need to be started
manually before using. The user can also stop a service.
Bluetooth Service Browse A remote Bluetooth device can provide one or
more Bluetooth services. To use the services that the remote device provides,
the user has to find the services first. This is called service browse.
C
Connectable Bluetooth devices can be connectable or non-connectable.
When the device is connectable, other devices can connect to it.
D
DHCP The Dynamic Host Configuration Protocol (DHCP) is an Internet
protocol for automating the configuration of computers that use TCP/IP.
E
Encryption When a Bluetooth link is encrypted, data are encrypted into
unreadable data using a secret key or password before they are sent over the
air. Data are decrypted after they reach the remote device.
G
General Discoverable Bluetooth devices have 3 modes: General
discoverable, Limited discoverable and Non-discoverable mode. A Bluetooth
device will respond to a General Inquiry if it is in general discoverable or limited
discoverable mode.
H
HID A Human Interface device such as keyboard and mouse.
I
ICS Internet Connection Sharing. For more detailed information about ICS,
please refer to the help topic Internet Connection Sharing of Microsoft
Windows.
75
Page 78

L
Limited Discoverable Bluetooth devices have 3 modes: General
discoverable, Limited discoverable and Non-discoverable mode. In Limited
discoverable mode, a Bluetooth device will respond to a General Inquiry or a
Limited Inquiry.
LAN Access Point One of entities defined in the LA profiles, the LAN
Access Point acts like a router between a Bluetooth piconet and an external
network.
N
NAP (Networking Access Point) A network access point is a unit that
contains one or more Bluetooth radio devices and acts as a bridge, proxy, or
router between a Bluetooth network and some other network technology
(10baseT, GSM, etc).
NAT Network address translation, which is used to re-map IP's from one
address range to another range of network addresses.
Non-connectable A Bluetooth devices can be connectable or
non-connectable. When it is non-connectable, other devices cannot connect to
it. This is used in BlueSoleil only when the user does not want other device to
connect to their computer.
Non-discoverable Bluetooth devices have 3 modes: General discoverable,
Limited discoverable and Non-discoverable mode. In Non-discoverable mode,
a Bluetooth device will not respond to any inquiry so no device can find it.
Non-pairable A Bluetooth device can be pairable or non-pairable. When it
is non-pairable, it will not accept a bonding request from other devices;
P
Pairing Devices Pairing allows you to avoid entering access information
each time a connection is set up. Paired devices share a unique Link Key,
which they exchange each time they connect.
PIM Personal Information Management.
76
Page 79

R
Radio Signal Strength Bluetooth works on 2.4G ISM band. The radio
signal is stronger when the remote device is closer or the remote device has a
higher radio output. The radio signal is weak when the remote device is distant
or the remote device has a weak radio output. The strength of the remote
device's radio signal affects the quality of the communication of the two
Bluetooth devices. When the radio signal is weak, the Bluetooth data
transferring speed is slow. However, if the two devices are too close and the
radio signal is too strong, the Bluetooth data transferring speed is also slow
because the "sound" is too loud to "hear". The radio signal strength is always
referred to as RSSI in Bluetooth.
Remote Bluetooth Device All the other Bluetooth enabled devices are
called remote Bluetooth devices in the term of my Bluetooth device. They
could be a Bluetooth modem, Bluetooth mobiles or a Bluetooth PDA etc.
T
Trusted Device Device having unrestricted access to all services on the
server.
77
Page 80

Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class
B digital device, pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against harmful interference in a
residential installation. This equipment generates, uses and can radiate radio
frequency energy and, if not installed and used in accordance with the
instructions, may cause harmful interference to radio communications.
However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and
on, the user is encouraged to try to correct the interference by one of the
following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that to which
the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: Any changes or modifications not expressly approved by the
party responsible for compliance could void the user's authority to operate this
equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) This device may not cause harmful interference,
and (2) this device must accept any interference received, including
interference that may cause undesired operation.
The antenna(s) used for this transmitter must not be co-located or operating in
conjunction with any other antenna or transmitter.
IMPORTANT NOTE: In the event that these conditions can not be met (for example certain
laptop configurations or co-location with another transmitter), then the FCC authorization is
no longer considered valid and the FCC ID can not be used on the final product. In these
circumstances, the OEM integrator will be responsible for re-evaluating the end product
(including the transmitter) and obtaining a separate FCC authorization.
78
 Loading...
Loading...