Page 1

BiGuard 30
iBusiness Security Gateway SMB
User’s Manual
Version Release 7.01 (FW:1.06p)
Page 2

BiGuard 30 User’s Manual
(Updated March 28, 2007)
Copyright Information
© 2007 Billion Electric Corporation, Ltd.
The contents of this publication may not be reproduced in whole or in part,
transcribed, stored, translated, or transmitted in any form or any means, without
the prior written consent of Billion Electric Corporation.
Published by Billion Electric Corporation. All rights reserved.
Disclaimer
Billion does not assume any liability arising out of the application of use of any
products or software described herein. Neither does it convey any license under its
patent rights nor the patent rights of others. Billion reserves the right to make
changes in any products described herein without notice. This publication is subject
to change without notice.
Trademarks
Mac OS is a registered trademark of Apple Computer, Inc.
Windows 98, Windows NT, Windows 2000, Windows Me and Windows XP are
registered trademarks of Microsoft Corporation.
2
Page 3
Safety Warnings
Your BiGuard 30 is built for reliability and long service life. For your safety,
be sure to read and follow the following safety warnings.
• Read this installation guide thoroughly before attempting to set up your BiGuard
30.
• Your BiGuard 30 is a complex electronic device. DO NOT open or attempt to
repair it yourself. Opening or removing the covers can expose you to high
voltage and other risks. In the case of malfunction, turn off the power
immediately and have it repaired at a qualified service center. Contact your
vendor for details.
• Connect the power cord to the correct supply voltage.
• Carefully place connecting cables to avoid people from stepping or tripping on
them. DO NOT allow anything to rest on the power cord and DO NOT place the
power cord in an area where it can be stepped on.
• DO NOT use BiGuard 30 in environments with high humidity or high
temperatures.
• DO NOT use the same power source for BiGuard 30 as other equipment.
• DO NOT use your BiGuard 30 and any accessories outdoors.
• If you wall mount your BiGuard 30, make sure that no electrical, water or gas
pipes will be damaged during installation.
• DO NOT install or use your BiGuard 30 during a thunderstorm.
• DO NOT expose your BiGuard 30 to dampness, dust, or corrosive liquids.
• DO NOT use your BiGuard 30 near water.
• Be sure to connect the cables to the correct ports.
• DO NOT obstruct the ventilation slots on your BiGuard 30 or expose it to direct
sunlight or other heat sources. Excessive temperatures may damage your
device.
• DO NOT store anything on top of your BiGuard 30.
• Only connect suitable accessories to your BiGuard 30.
• Keep packaging out of the reach of children.
• If disposing of the device, please follow your local regulations for the safe
disposal of electronic products to protect the environment.
3
Page 4

Table of Contents
Chapter 1: Introduction
1.1 Overview
1.2 Product Highlights
1.2.1 Increased Bandwidth, Scalability and Resilience
1.2.2 Virtual Private Network Support
1.2.3 Advanced Firewall Security
1.2.4 Intelligent Bandwidth Management
1.3 Package Contents
1.3.1 Front Panel
1.3.2 Rear Panel
1.3.3 Rack Mounting
1.3.4 Cabling
Chapter 2: Router Applications
2.1 Overview
2.2 Bandwidth Management with QoS
2.2.1 QoS Technology
2.2.2 QoS Policies for Different Applications
2.2.3 Guaranteed / Maximum Bandwidth
2.2.4 Policy Based Traffic Shaping
2.2.5 Priority Bandwidth Utilization
2.2.6 Management by IP or MAC address
2.2.7 DiffServ (DSCP Marking)
2.2.7 DSCP (Matching)
2.3 Outbound Traffic
2.3.1 Outbound Fail Over
2.3.2 Outbound Load Balancing
2.4 Inbound Traffic
2.4.1 Inbound Fail Over
2.4.2 Inbound Load Balancing
2.5 DNS Inbound
2.5.1 DNS Inbound Fail Over
2.5.2 DNS Inbound Load Balancing
2.6 Virtual Private Networking
4
Page 5

2.6.1 General VPN Setup
2.6.2 VPN Planning - Fail Over
2.6.3 Concentrator
Chapter 3: Getting Started
3.1 Overview
3.2 Before You Begin
3.3 Connecting Your Router
3.4 Configuring PCs for TCP/IP Networking
3.4.1 Overview
3.4.2 Windows XP
3.4.2.1 Configuring
3.4.2.2 Verifying Settings
3.4.3 Windows 2000
3.4.3.1 Configuring
3.4.3.2 Verifying Settings
3.4.4 Windows 98 / ME
3.4.4.1 Installing Components
3.4.4.2 Configuring
3.4.4.3 Verifying Settings
3.5 Factory Default Settings
3.5.1 Username and Password
3.5.2 LAN and WAN Port Addresses
3.6 Information From Your ISP
3.6.1 Protocols
3.6.2 Configuration Information
3.6.2.1 Windows
3.7 Web Configuration Interface
Chapter 4: Router Configuration
4.1 Overview
4.2 Status
4.2.1 ARP Table
4.2.2 Routing Table
4.2.3 Session Table
4.2.4 DHCP Table
5
Page 6

4.2.5 IPSec Status
4.2.6 PPTP Status
4.2.7 Traffic Statistics
4.2.8 System Log
4.2.9 IPSec Log
4.3 Quick Start
4.3.1 DHCP
4.3.2 Static IP
4.3.3 PPPoE
4.3.4 PPTP
4.3.5 Big Pond
4.4 Configuration
4.4.1 LAN
4.4.1.1 Ethernet
4.4.1.2 DHCP Server
4.4.1.3 LAN Address Mapping
4.4.2 WAN
4.4.2.1 ISP Settings
4.4.2.1.1 DHCP
4.4.2.1.2 Static IP
4.4.2.1.3 PPPoE
4.4.2.1.4 PPTP
4.4.2.1.5 Big Pond
4.4.2.2 Bandwidth Settings
4.4.2.3 WAN IP Alias
4.4.3 Dual WAN
4.4.3.1 General Settings
4.4.3.2 Outbound Load Balance
4.4.3.3 Inbound Load Balance
4.4.3.4 Protocol Binding
4.4.4 System
4.4.4.1 Time Zone
4.4.4.2 Remote Access
4.4.4.3 Firmware Upgrade
4.4.4.4 Backup / Restore
4.4.4.5 Restart
4.4.4.6 Password
4.4.4.7 System Log Server
6
Page 7

4.4.4.8 Email Alert
4.4.5 Firewall
4.4.5.1 Packet Filter
4.4.5.2 URL Filter
4.4.5.3 LAN MAC Filter
4.4.5.4 Block WAN Request
4.4.5.5 Intrusion Detection
4.4.6 VPN
4.4.6.1 IPSec
4.4.6.1.1 IPSec Wizard
4.4.6.1.2 IPSec Policy
4.4.6.2 PPTP
4.4.7 QoS
4.4.8 Virtual Server
4.4.8.1 DMZ
4.4.8.2 Port Forwarding Table
4.4.9 Advanced
4.4.9.1 Static Route
4.4.9.2 Dynamic DNS
4.4.9.3 Device Management
4.4.9.4 IGMP
4.4.9.5 VLAN Bridge
4.5 Save Configuration To Flash
4.6 Logout
Chapter 5: Troubleshooting
5.1 Basic Functionality
5.1.1 Router Won’t Turn On
5.1.2 LEDs Never Turn Off
5.1.3 LAN or Internet Port Not On
5.1.4 Forgot My Password
5.2 LAN Interface
5.2.1 Can’t Access Router from the LAN
5.2.2 Can’t Ping Any PC on the LAN
5.2.3 Can’t Access Web Configuration Interface
5.2.3.1 Pop-up Windows
5.2.3.2 Javascripts
7
Page 8

5.2.3.3 Java Permissions
5.3 WAN Interface
5.3.1 Can’t Get WAN IP Address from the ISP
5.4 ISP Connection
5.5 Problems with Date and Time
5.6 Restoring Factory Defaults
Appendix A: Product Specifications
Appendix B: Customer Support
Appendix C: FCC Interference Statement
Appendix D: Network, Routing, and Firewall Basics
D.1 Network Basics
D.1.1 IP Addresses
D.1.1.1 Netmask
D.1.1.2 Subnet Addressing
D.1.1.3 Private IP Addresses
D.1.2 Network Address Translation (NAT)
D.1.3 Dynamic Host Configuration Protocol (DHCP)
D.2 Router Basics
D.2.1 Why use a Router?
D.2.2 What is a Router?
D.2.3 Routing Information Protocol (RIP)
D.3 Firewall Basics
D.3.1 What is a Firewall?
D.3.2.1 Stateful Packet Inspection
D.3.2.2 Denial of Service (DoS) Attack
D.3.2 Why Use a Firewall?
Appendix E: Virtual Private Networking
E.1 What is a VPN?
E.1.1 VPN Applications
8
Page 9

E.2 What is IPSec?
E.2.1 IPSec Security Components
E.2.1.1 Authentication Header (AH)
E.2.1.2 Encapsulating Security Payload (ESP)
E.2.1.3 Security Associations (SA)
E.2.2 IPSec Modes
9
Page 10

E.2.3 Tunnel Mode AH
E.2.4 Tunnel Mode ESP
E.2.5 Internet Key Exchange (IKE)
Appendix F: IPSec Logs and Events
F.1 IPSec Log Event Categories
F.2 IPSec Log Event Table
Appendix G: Bandwidth Management with QoS
G.1 Overview
G.2 What is Quality of Service?
G.3 How Does QoS Work?
G.4 Who Needs QoS?
G.4.1 Home Users
G.4.2 Office Users
Appendix H: Router Setup Examples
H.1 Outbound Fail Over
H.2 Outbound Load Balancing
H.3 Inbound Fail Over
H.4 DNS Inbound Fail Over
H.5 DNS Inbound Load Balancing
H.6 Dynamic DNS Inbound Load Balancing
H.7 VPN Configuration
H.7.1 LAN to LAN
H.7.2 Host to LAN
H.8 IPSec Fail Over (Gateway to Gateway)
H.9 VPN Concentrator
H.10 Protocol Binding
H.11 Intrusion Detection
H.12 PPTP Remote Access by Windows XP
H.13 PPTP Remote Access by BiGuard
10
Page 11

Chapter 1: Introduction
1.1 Overview
Congratulations on purchasing BiGuard 30 Router from Billion. Combining a router
with an Ethernet network switch, BiGuard 30 is a state-of-the-art device that
provides everything you need to get your network connected to the Internet over
your Cable or DSL connection quickly and easily. The Quick Start Wizard and DHCP
Server will get first-time users up and running with minimal fuss and configuration,
while sophisticated Quality of Service (QoS) and Load Balancing features grant
advanced users total control over their network and Internet connection.
This manual illustrates the many features and functions of BiGuard 30, and even
takes you through the various ways you can apply this versatile device to your home
or office. Take the time now to familiarize yourself with BiGuard 30.
1.2 Product Highlights
1.2.1 Increased Bandwidth, Scalability and Resilience
With integrated Dual WAN ports, BiGuard 30 combines two broadband lines such as
DSL or Cable into one Internet connection, providing optimal bandwidth sharing for
multiple PCs on your network, or allowing maximum reliability with network
redundancy. Load Balancing enables BiGuard 30 to efficiently balance network
traffic across two connections, ideal for small-to-medium businesses that require
increased bandwidth, network scalability, and resilience for mission-critical network
and Internet applications. Auto failover can also be configured to ensure smooth,
continuous service should one connection fail, providing maximum business uptime
and productivity, plus uninterrupted service for you and your customers.
1.2.2 Virtual Private Network Support
BiGuard 30 supports comprehensive IPSec & PPTP VPN protocols for businesses to
establish private encrypted tunnels over the Internet to ensure data transmission
security among multiple sites, such as a branch office or dial-up connection. IPSec
VPN is up to 30 simultaneous IPSec VPN connections are possible on BiGuard 30,
with performance of up to 30Mbps. PPTP VPN is up to 4 simultaneous PPTP VPN
11
Page 12

connections are possible on BiGuard 30, with performance of up to 10Mbps.
1.2.3 Advanced Firewall Security
Aside from intelligent broadband sharing, BiGuard 30 offers integrated firewall
protection with advanced features to secure your network from outside attacks.
Stateful Packet Inspection (SPI) determines if a data packet is permitted to enter
the private LAN. Denial of Service (DoS) prevents hackers from interrupting
network services via malicious attacks. In addition, BiGuard 30 firewall can be
configured to alert you via email should your network come under fire, offering both
tight network security and peace of mind.
1.2.4 Intelligent Bandwidth Management
BiGuard 30 utilizes Quality of Service (QoS) to give you full control over the priority
of both incoming and outgoing data, ensuring that critical data such as customer
information moves through your network, even while under a heavy load.
Transmission speeds can be throttled to make sure users are not saturating
bandwidth required for mission-critical data transfers. Priority types of upload data
can also be changed, allowing BiGuard 30 to automatically sort out actual speeds for
unmatched convenience.
1.3 Package Contents
BiGuard 30 iBusiness Security Gateway SMB
Bracket x 2 (for rack-mounting)
Screw x 4 (for rack-mounting)
Getting Started CD-ROM
Quick Start Guide
AC-DC Power Adapter (12VDC, 1A)
1.3.1 Front Panel
12
Page 13
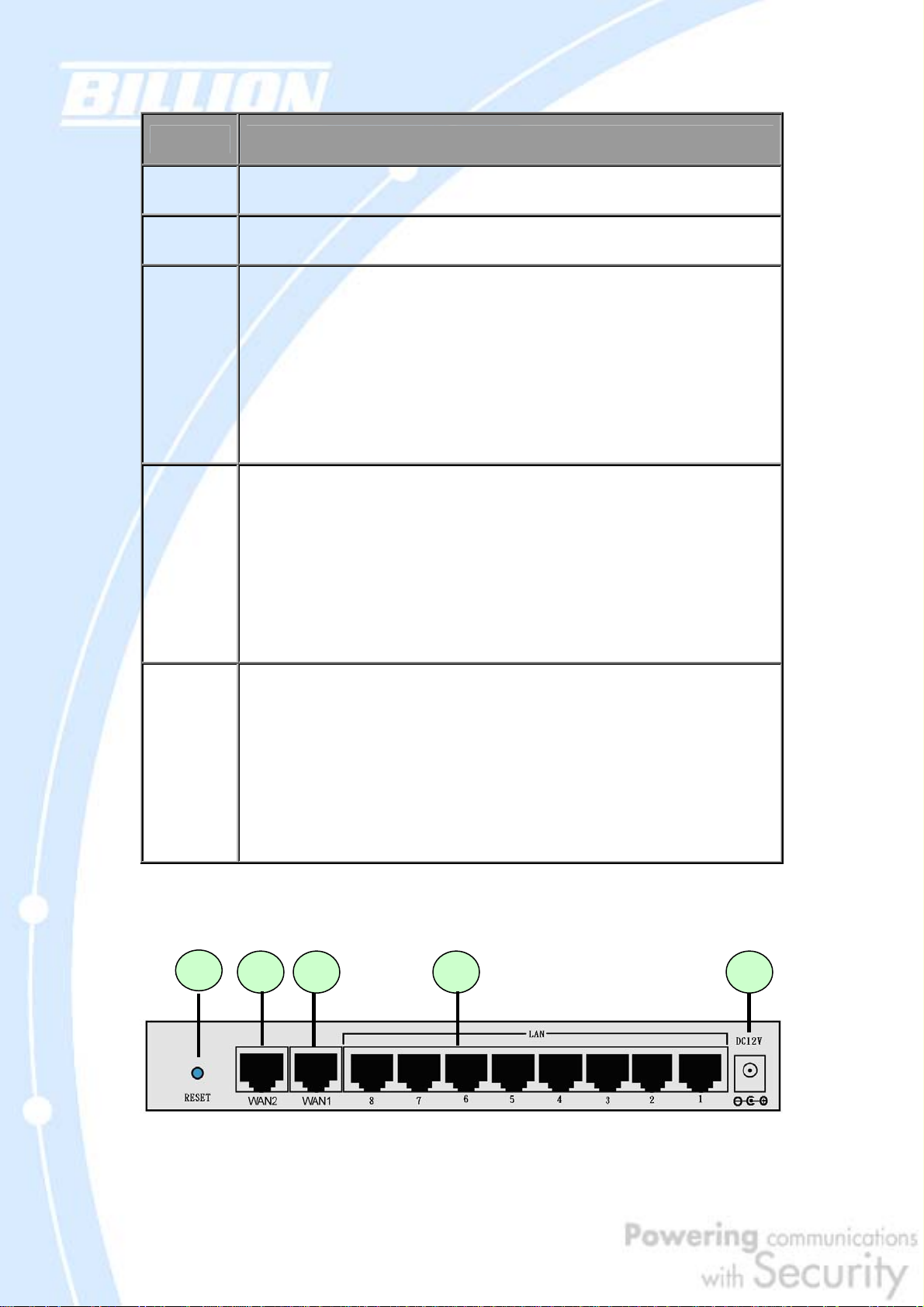
LED Function
Power
Status
LAN
1 – 8
WAN1
A solid light indicates a steady connection to a power source.
A blinking light indicates the device is writing to flash memory.
Lit when connected to an Ethernet device.
10/100M : Lit green when connected at 100Mbps.
Not lit when connected at 10Mbps.
Link/ACT: Lit when device is connected.
Blinking when data is transmitting/receiving.
Lit when connected to an Ethernet device.
10/100M : Lit green when connected at 100Mbps.
Not lit when connected at 10Mbps.
Link/ACT: Lit when device is connected.
Blinking when data is transmitting/receiving.
WAN2
Lit when connected to an Ethernet device.
10/100M : Lit green when connected at 100Mbps.
Not lit when connected at 10Mbps.
Link/ACT: Lit when device is connected.
Blinking when data is transmitting/receiving.
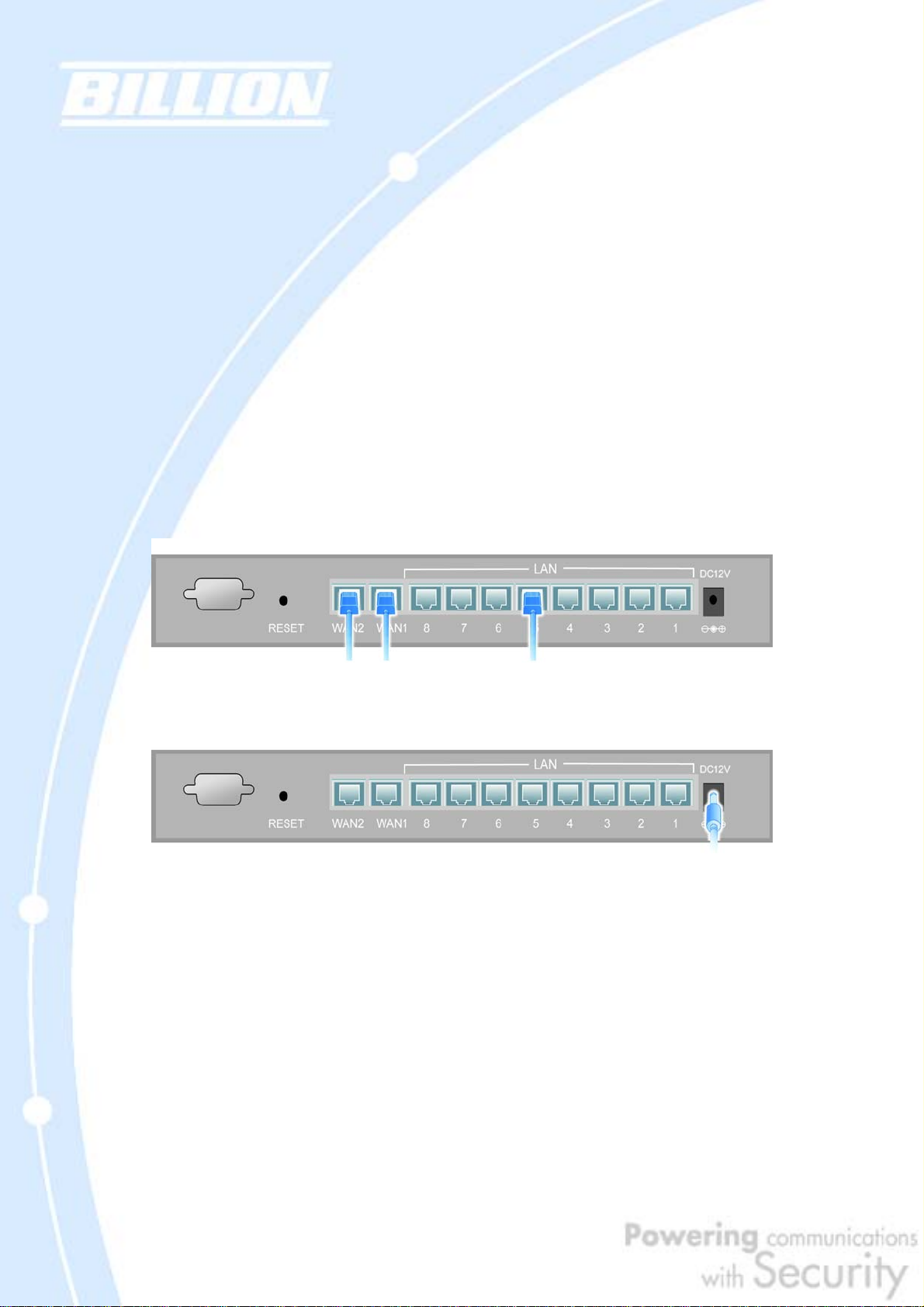
1.3.2 Rear Panel
1
2
3
4
5
13
Page 14
Port Function
To reset the device and restore factory default settings, after
1 RESET
the device is fully booted, press and hold RESET until the
Status LED begins to blink.
WAN2 10/100M Ethernet port (with auto crossover support);
2 WAN2
connect xDSL/Cable modem here.
WAN1 10/100M Ethernet port (with auto crossover support);
3 WAN1
connect xDSL/Cable modem here.
LAN
Connect a UTP Ethernet cable (Cat-5 or Cat-5e) to one of the
4
1 — 8
eight LAN ports when connecting a PC to the network.
5 DC12V Connect DC Power Adapter here. (12VDC)
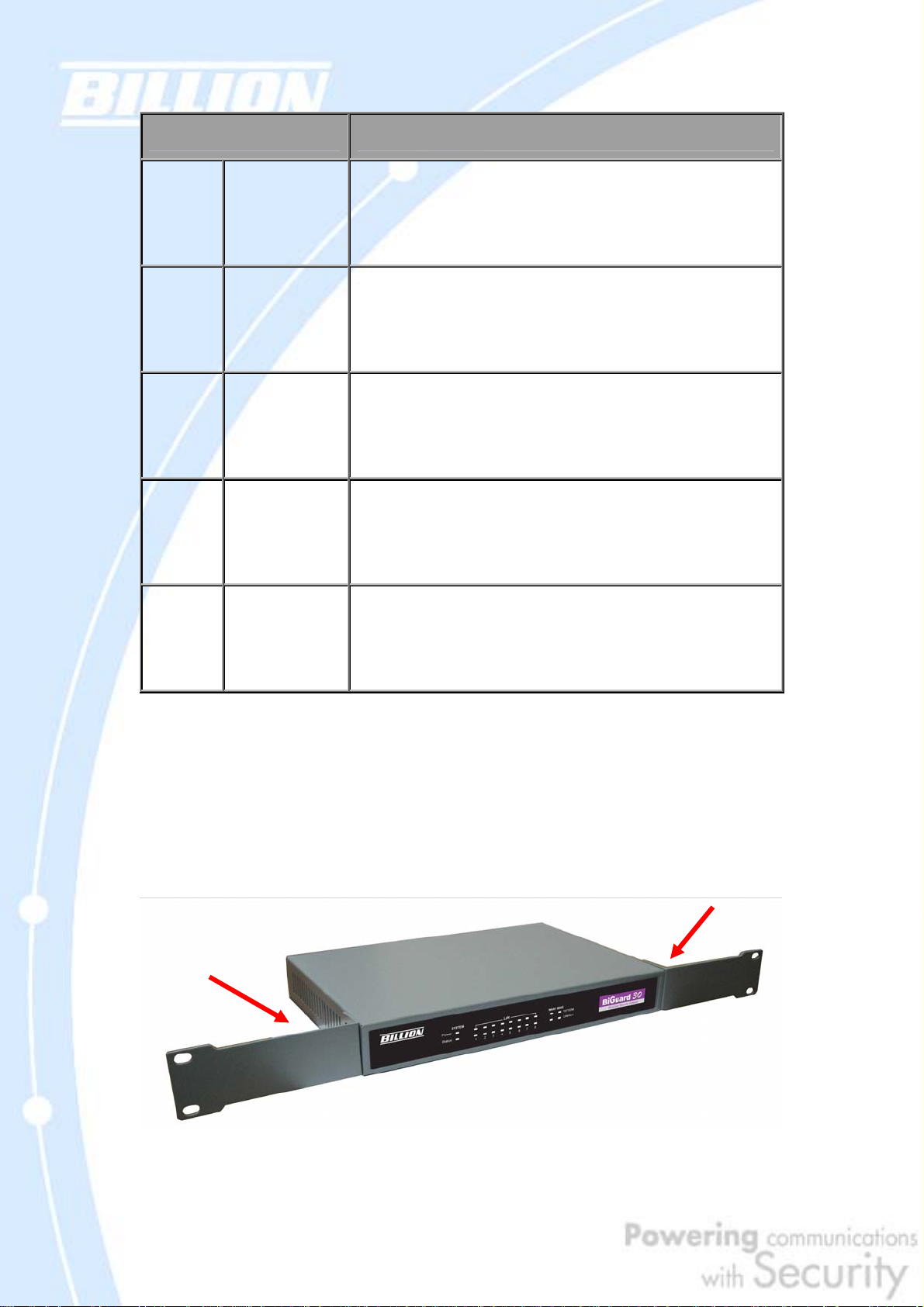
1.3.3 Rack Mounting
To rack mount BiGuard 30, carefully secure the device to your rack on both sides
using the included brackets and screws. See the diagram below for a more detailed
explanation.
14
Page 15

1.3.4 Cabling
Most Ethernet networks currently use unshielded twisted pair (UTP) cabling. The
UTP cable contains eight conductors, arranged in four twisted pairs, and terminated
with an RJ45 type connector.
One of the most common causes of networking problems is bad cabling. Make sure
that all connected devices are turned on. On the front panel of BiGuard 30, verify
that the LAN link and WAN line LEDs are lit. If they are not, check to see that you are
using the proper cabling.
15
Page 16

Chapter 2: Router Applications
2.1 Overview
Your BiGuard 30 router is a versatile device that can be configured to not only
protect your network from malicious attackers, but also ensure optimal usage of
available bandwidth with Quality of Service (QoS) and both Inbound and Outbound
Load Balancing. Alternatively, BiGuard 30 can also be set to redirect incoming and
outgoing network traffic with the Fail Over capability, ensuring minimal downtime
and increased reliability.
The following chapter describes how BiGuard 30 can work for you.
2.2 Bandwidth Management with QoS
Quality of Service (QoS) gives you full control over which types of outgoing data
traffic should be given priority by the router. By doing so, the router can ensure that
latency-sensitive applications like voice, bandwidth-consuming data like gaming
packets, or even mission critical files efficiently move through the router even under
a heavy load. You can throttle the speed at which different types of outgoing data
pass through the router. In addition, you can simply change the priority of different
types of upload data and let the router sort out the actual speeds.
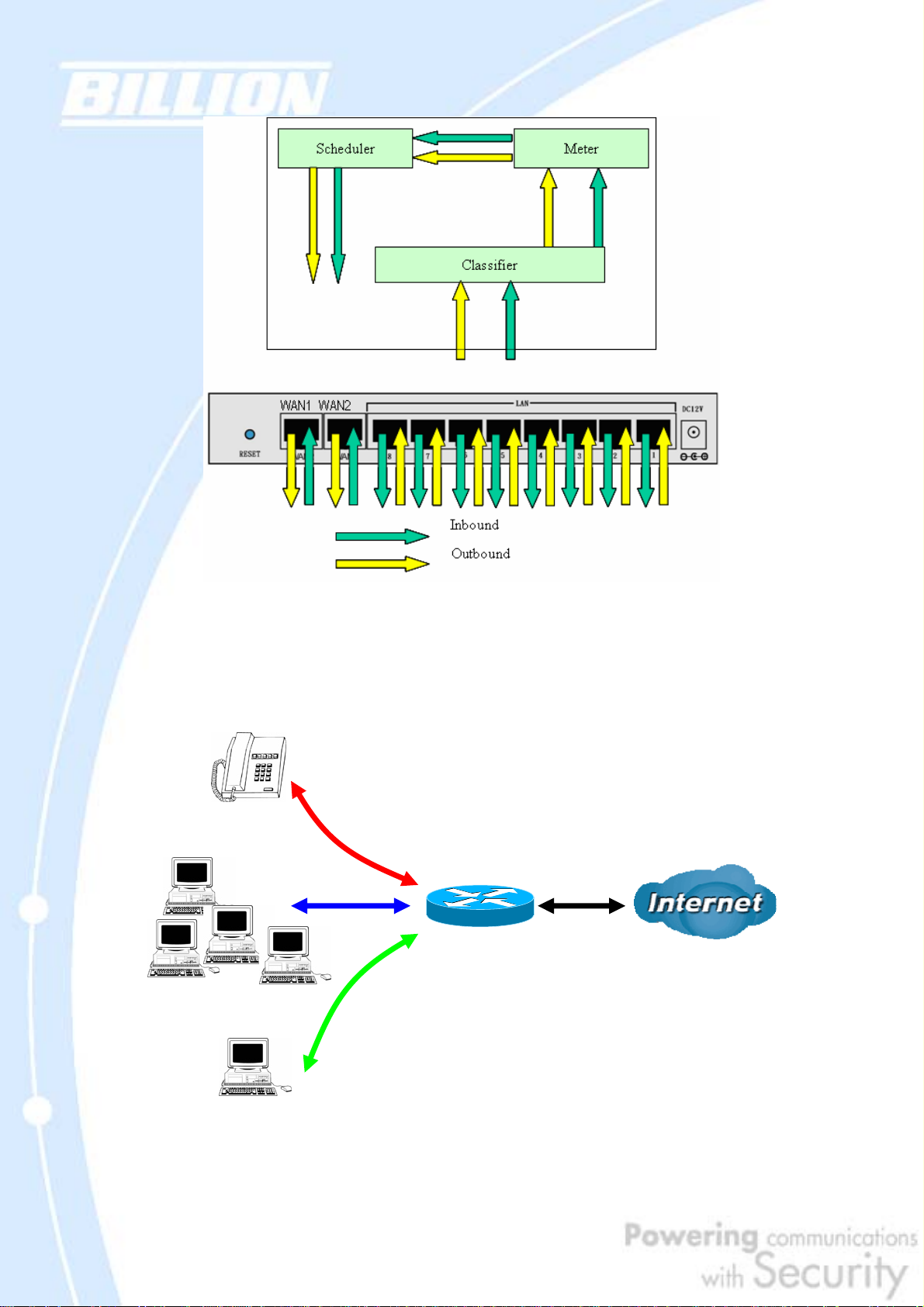
2.2.1 QoS Technology
QoS generally involves the prioritization of network traffic. QoS is comprised of
three major components: Classifier, Meter, and Scheduler. Each of these
components has a distinct role in ensuring that incoming and outgoing data is
managed according to user specifications.
The Classifier analyses incoming packets and marks each one according to
configured parameters. The Meter communicates the drop priority to the Scheduler
and measures the temporal priorities of the output stream against configured
parameters. Finally, the Scheduler schedules each packet for transmission based on
information from both the Classifier and the Meter.
16
Page 17
2.2.2 QoS Policies for Different Applications
By setting different QoS policies according to the applications you are running, you
can use BiGuard 30 to optimize the bandwidth that is being used on your network.
VoIP
Normal PCs
Restricted PC
As illustrated in the diagram above, applications such as Voiceover IP (VoIP) require
17
Page 18
low network latencies to function properly. If bandwidth is being used by other
applications such as an FTP server, users using VoIP will experience network lag
and/or service interruptions during use. To avoid this scenario, this network has
assigned VoIP with a guaranteed bandwidth and higher priority to ensure smooth
communications. The FTP server, on the other hand, has been given a maximum
bandwidth cap to make sure that regular service to both VoIP and normal Internet
applications is uninterrupted.
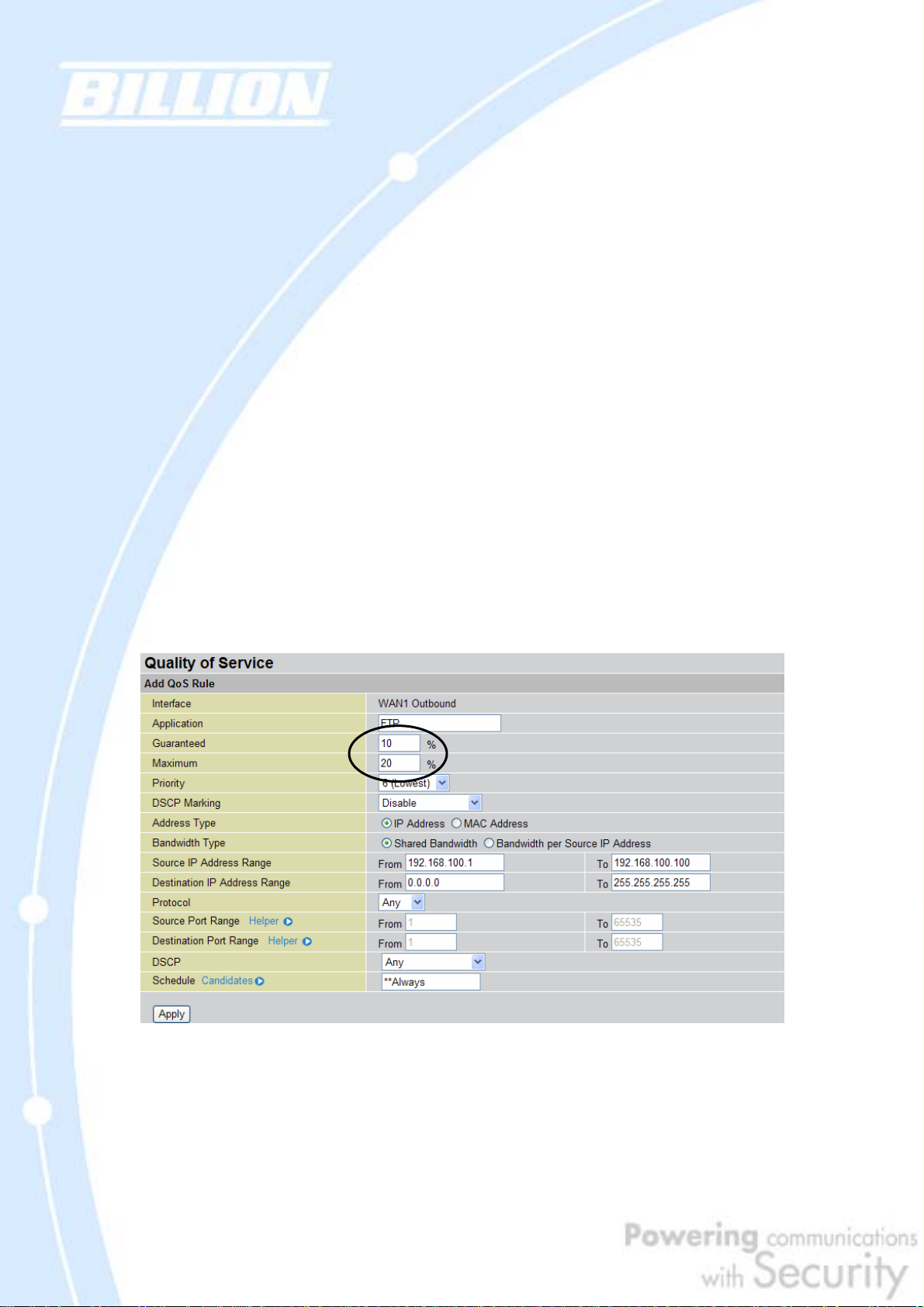
2.2.3 Guaranteed / Maximum Bandwidth
Setting a Guaranteed Bandwidth ensures that a particular service receives a
minimum percentage of bandwidth. For example, you can configure BiGuard 30 to
reserve 10% of the available bandwidth for a particular computer on the network to
transfer files.
Alternatively you can set a Maximum Bandwidth to restrict a particular application
to a fixed percentage of the total throughput. Setting a Maximum Bandwidth of 20%
for a file sharing program will ensure that no more than 20% of the available
bandwidth will be used for file sharing.
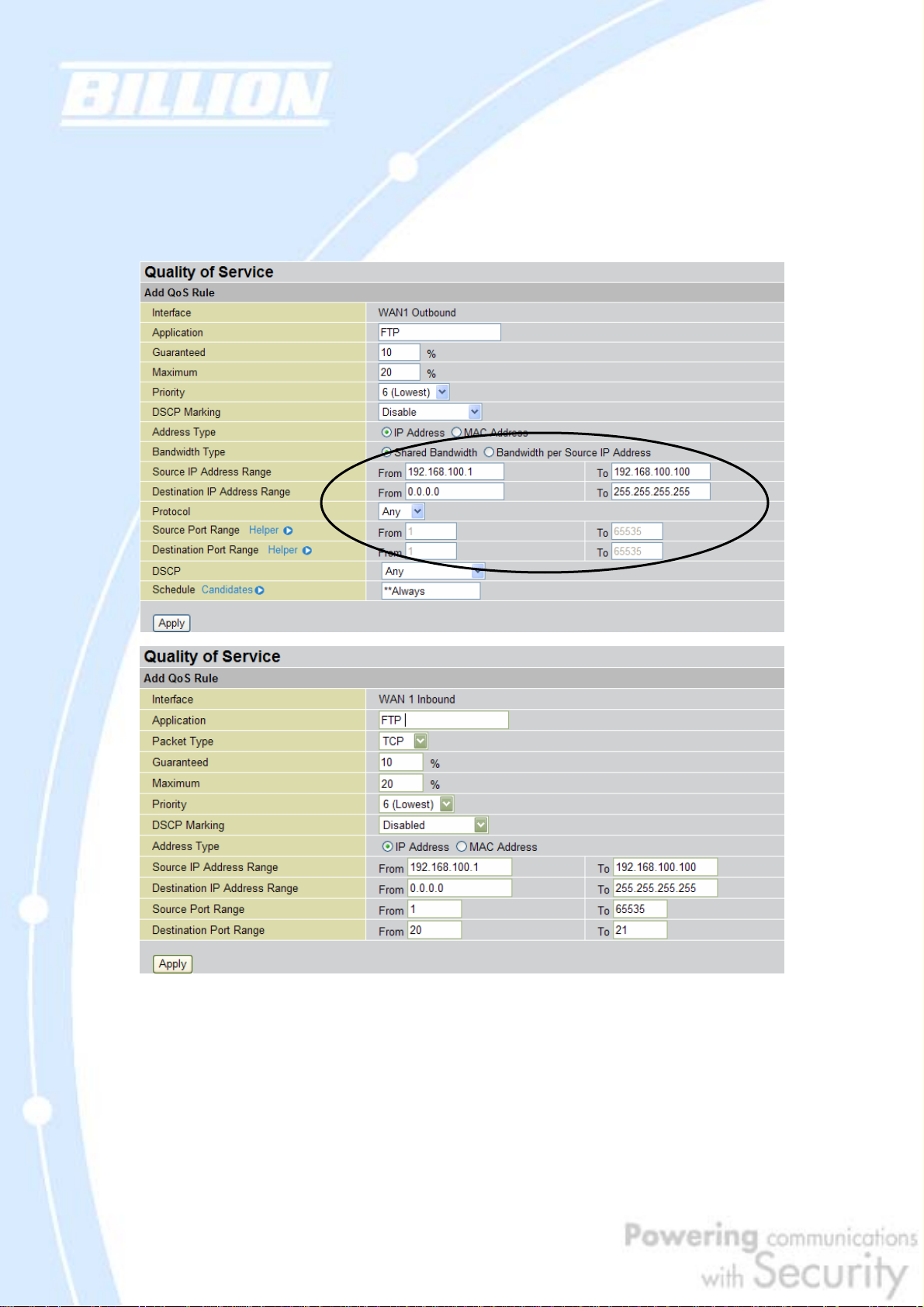
2.2.4 Policy Based Traffic Shaping
Policy Based Traffic Shaping allows you to apply specific traffic policies across a
range of IP addresses or ports. This is particularly useful for assigning different
18
Page 19
policies for different PCs on the network. Policy based traffic shaping lets you better
manage your bandwidth, providing reliable Internet and network service to your
organization.
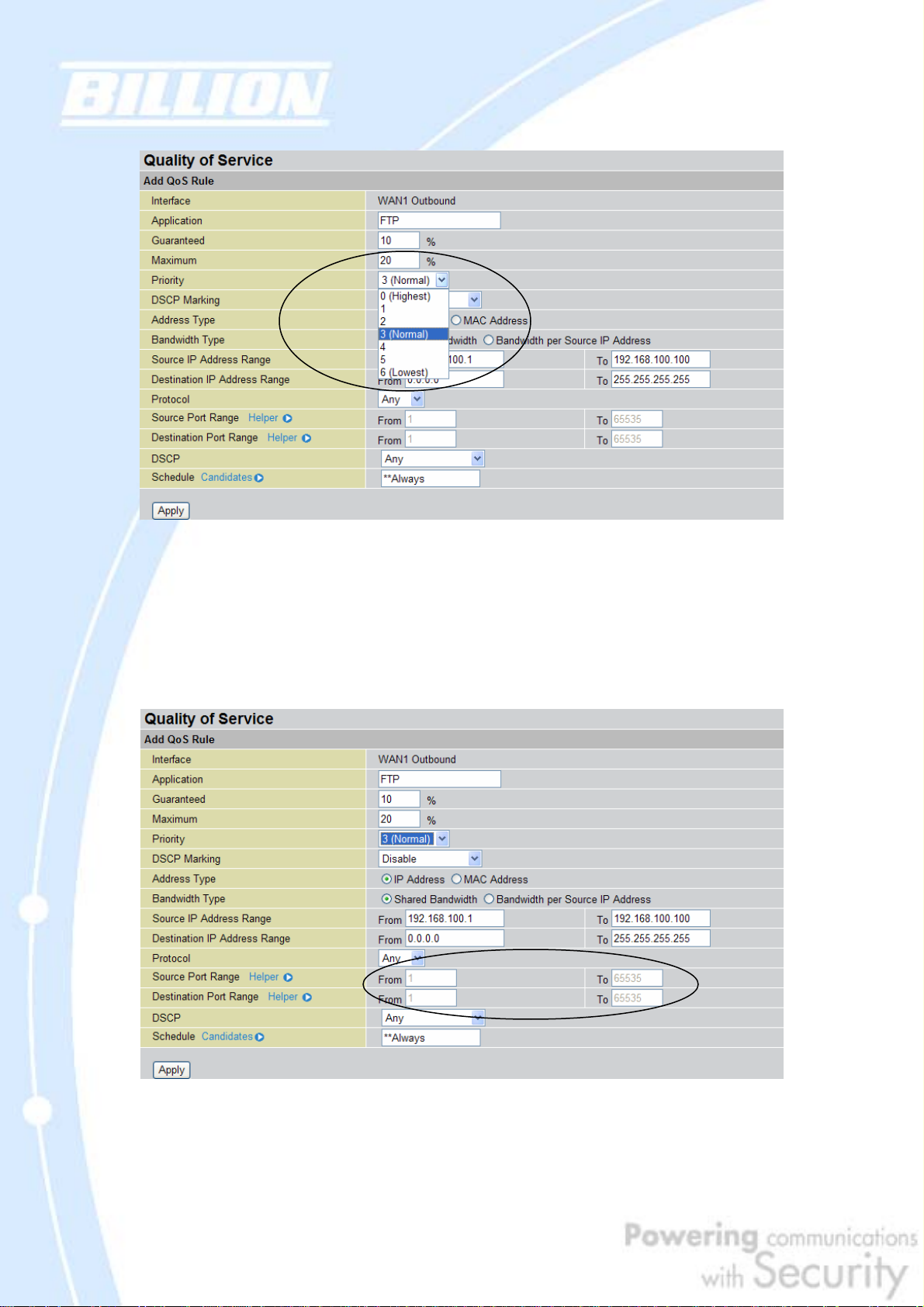
2.2.5 Priority Bandwidth Utilization
Assigning priority to a certain service allows BiGuard 30 to give either a higher or
lower priority to traffic from this particular service. Assigning a higher priority to an
application ensures that it is processed ahead of applications with a lower priority
and vice versa.
19
Page 20
2.2.6 Management by IP or MAC address
BiGuard 30 can also be configured to apply traffic policies based on a particular IP or
MAC address. This allows you to quickly assign different traffic policies to a specific
computer on the network.
2.2.7 DiffServ (DSCP Marking)
20
Page 21
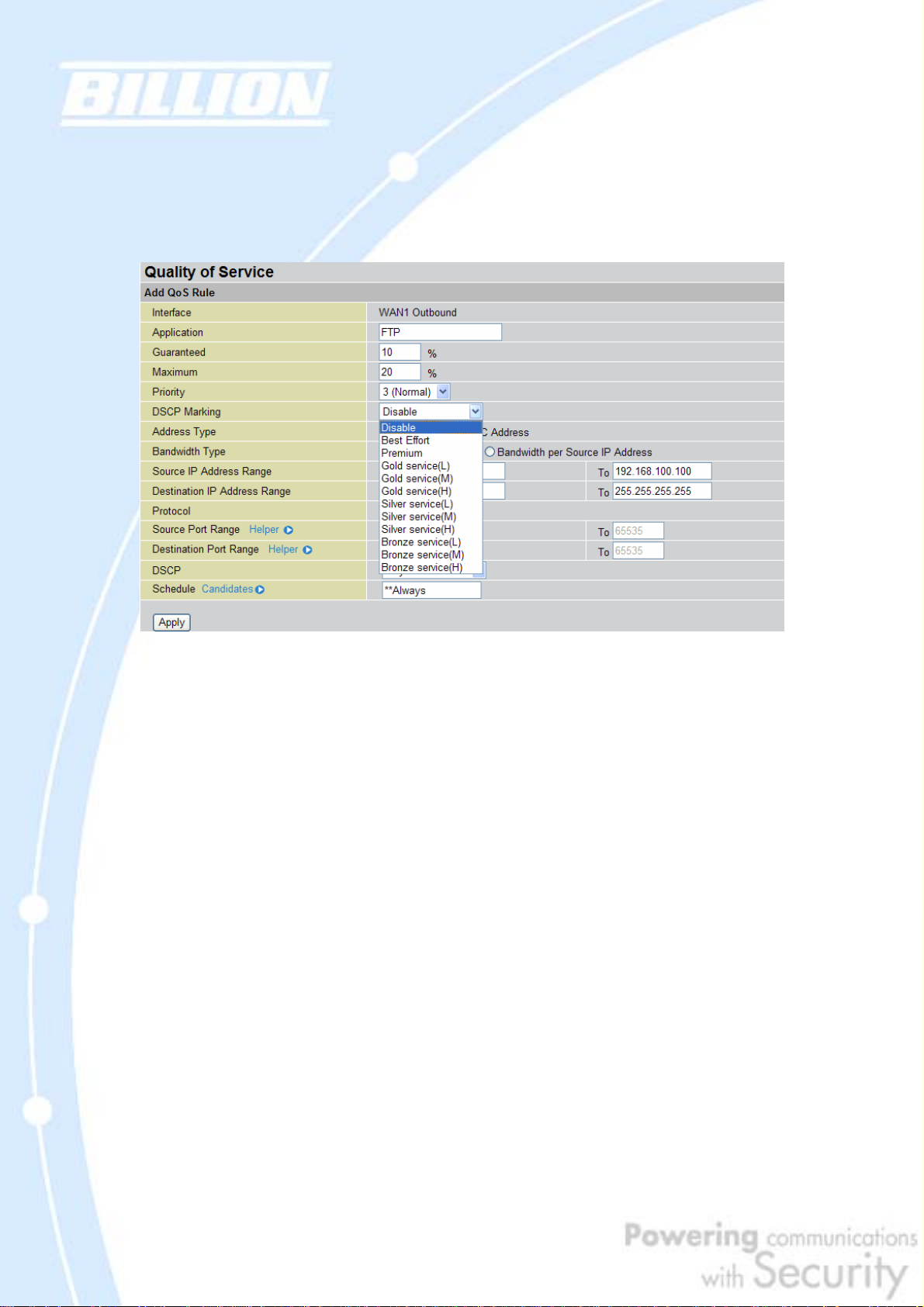
DiffServ (a.k.a. DSCP Marking) allows you to classify traffic based on IP DSCP values.
Other interfaces can match traffic based on the DSCP markings. DSCP markings are
used to decide how packets should be treated, and is a useful tool to give
precedence to varying types of data.
2.2.8 DSCP (Matching)
Just like the DSCP Marking, DSCP is used on traffics (Both inbound rules and
outbound rules have DSCP matching). DSCP matching is used to identify traffic for
the rule. (It is just like what source IP and destination IP do). When this option of the
QoS rule is selected, the QoS rule will only be applied to the packets whose DSCP
field’s IP header matches the criteria selected. These markings can be used to identify
traffic within the network.
2.3 Outbound Traffic
This section outlines some of the ways you can use BiGuard 30 to manage outbound
traffic.
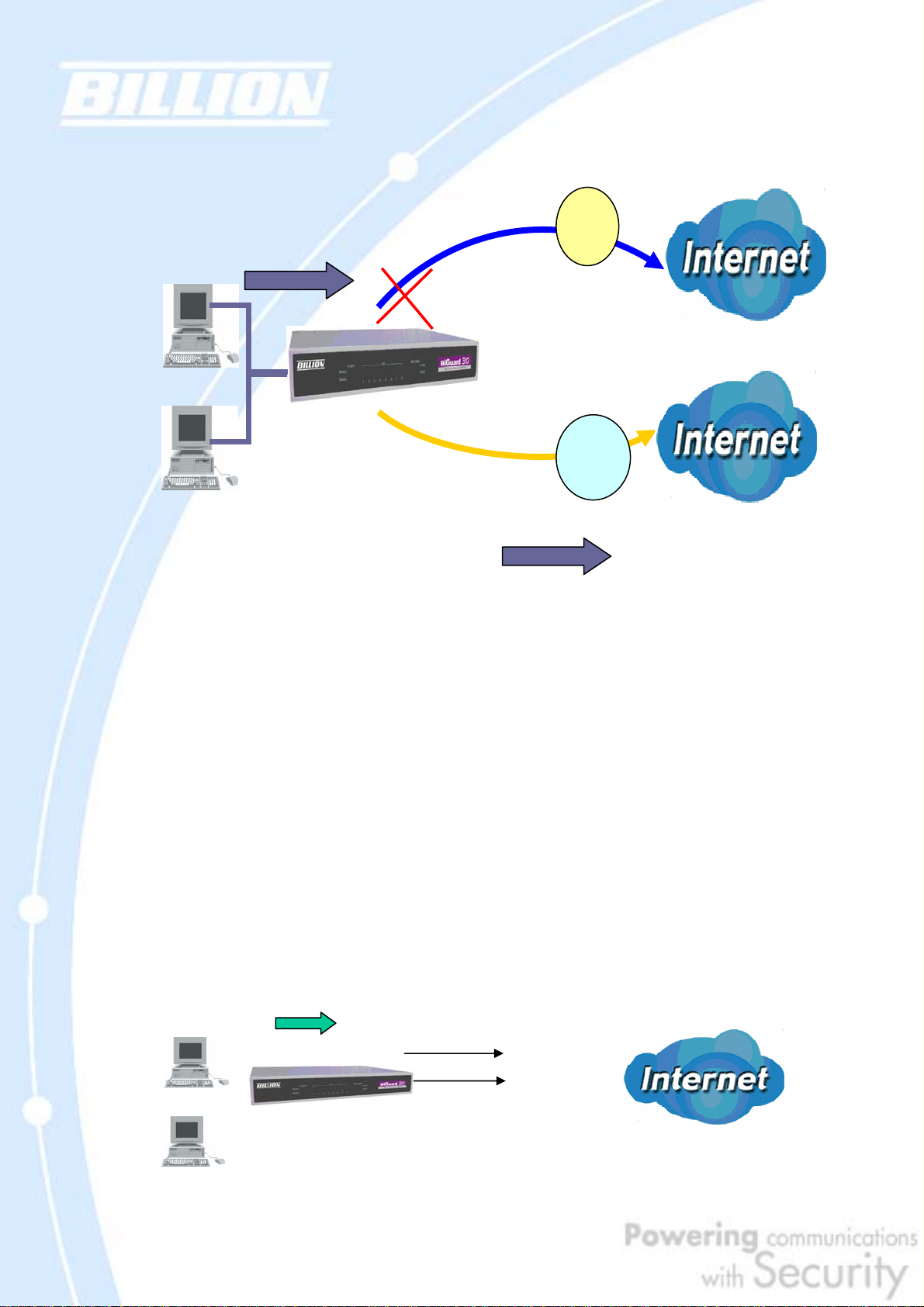
2.3.1 Outbound Fail Over
Configuring BiGuard 30 for Outbound Fail Over allows you to ensure that outgoing
traffic is uninterrupted by having BiGuard 30 default to WAN2 should WAN1 fail.
21
Page 22
230.100.100.1
1st Connection
192.168.2.2
ISP
ISP
2nd connection
192.168.2.3
In the above example, PC 1 (IP_192.168.2.2) and PC 2 (IP_192.168.2.3) are
213.10.10.2
connected to the Internet via WAN1 (IP_230.100.100.1) on BiGuard 30. Should
WAN1 fail, Outbound Fail Over tells BiGuard 30 to reroute outgoing traffic to WAN2
(IP_213.10.10.2). Configuring your BiGuard 30 for Outbound Fail Over provides a
more reliable connection for your outgoing traffic.
Please refer to appendix H for example settings.
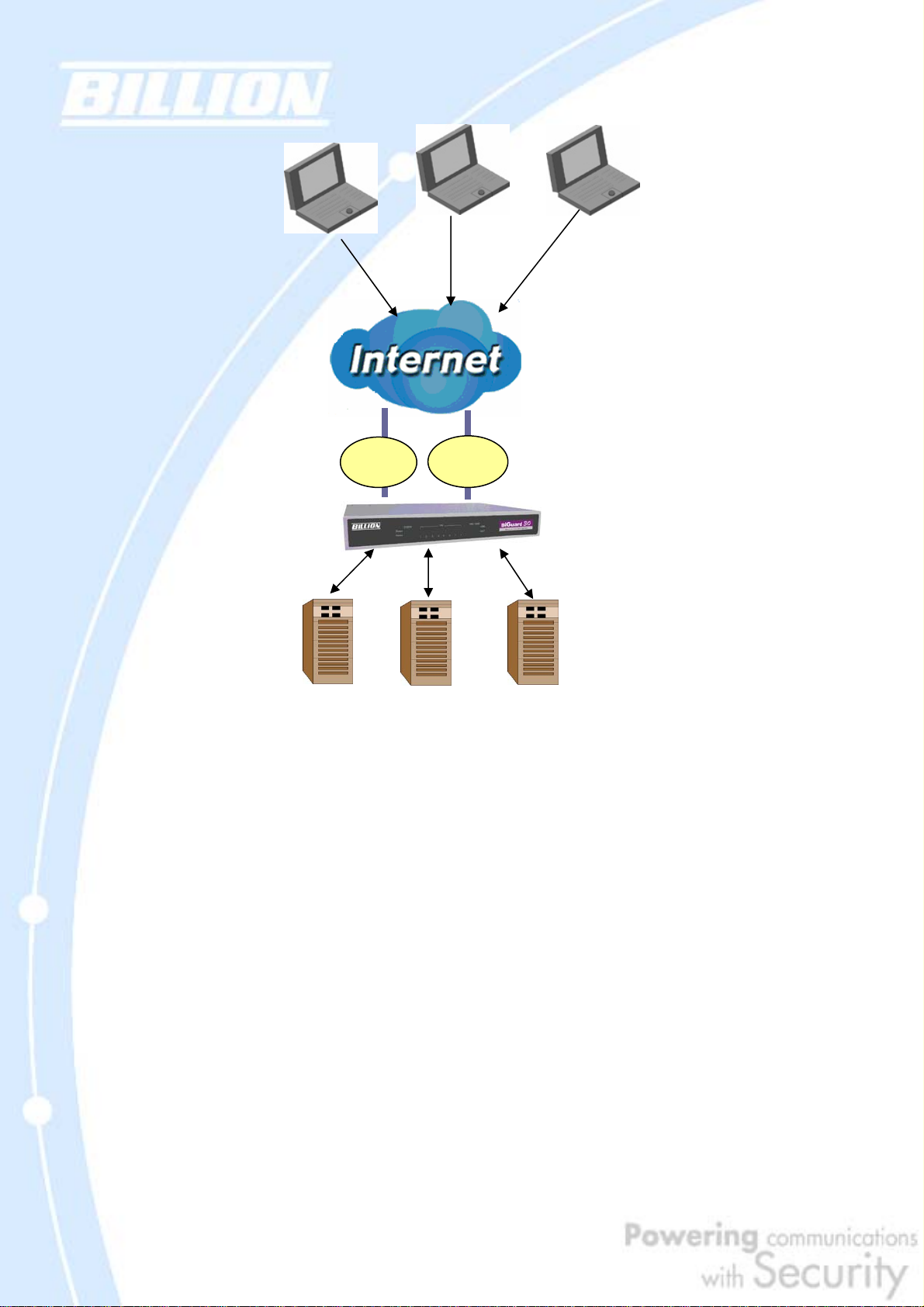
2.3.2 Outbound Load Balancing
Outbound Load Balancing allows BiGuard 30 to intelligently manage outbound
traffic based on the amount of load of each WAN connection.
192.168.2.2
230.100.100.1
ISP
192.168.2.3
213.10.10.2
22
Page 23

In the above example, PC 1 (IP_192.168.2.2) and PC 2 (IP_192.168.2.3) are
connected to the Internet via WAN1 (IP_230.100.100.1) and WAN2
(IP_213.10.10.2) on BiGuard 30. You can configure BiGuard 30 to balance the load
of each WAN port with one of two mechanisms:
1. Session (by session/by traffic/weight of link capability)
2. IP Hash (by traffic/weight of link capability)
The IP Hash mechanism will ensure that the traffic from the same source IP address
and destination IP address will go through the same WAN port. This is useful for
some server applications that need to identify the source IP address of the client.
By balancing the load between WAN1 and WAN2, your BiGuard 30 can ensure that
outbound traffic is efficiently handled by making sure that both ports are equally
sharing the load, preventing situations where one port is completely saturated by
outbound traffic.
Please refer to appendix H for example settings.
2.4 Inbound Traffic
Learn how BiGuard 30 can handle inbound traffic in the following section.
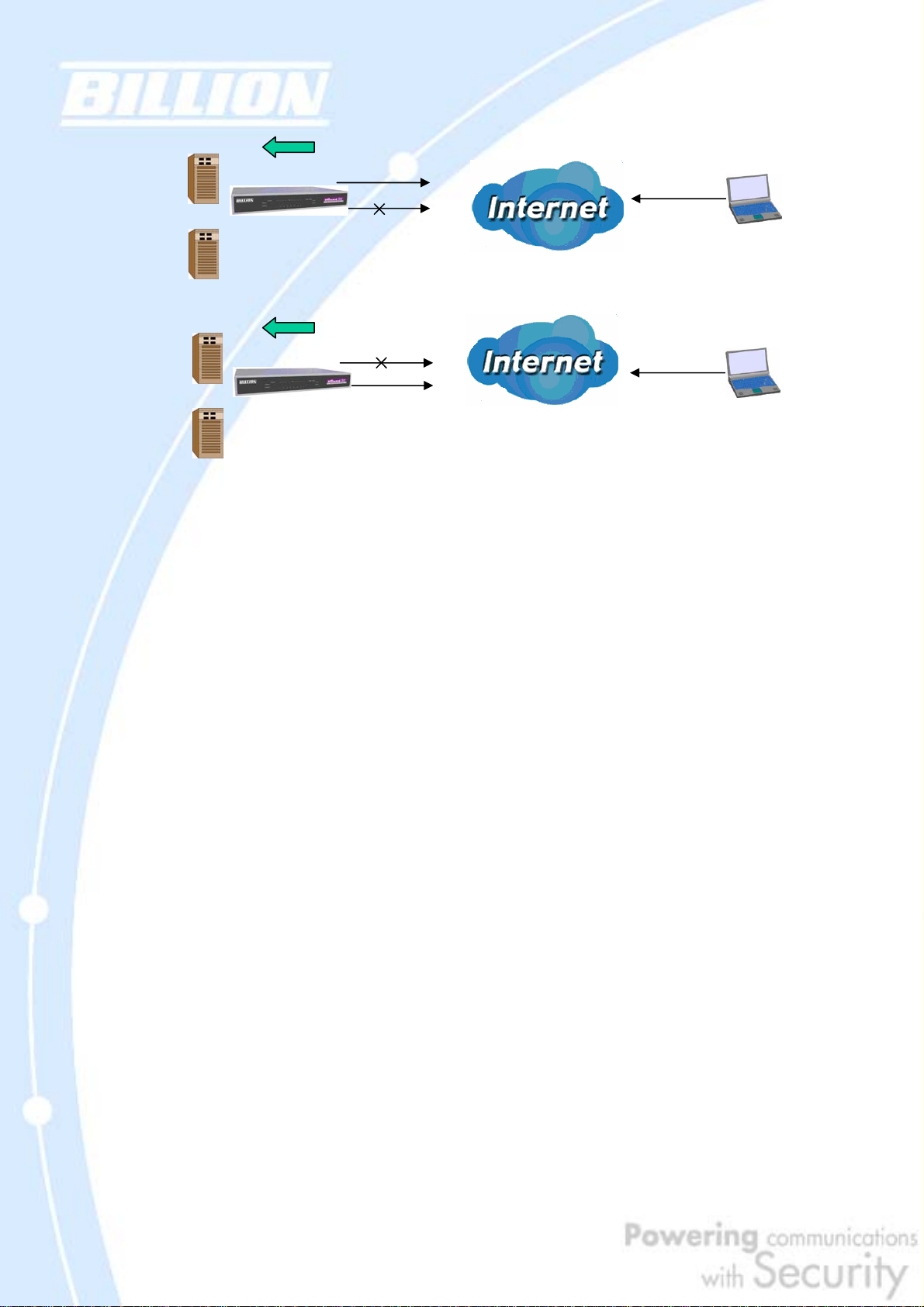
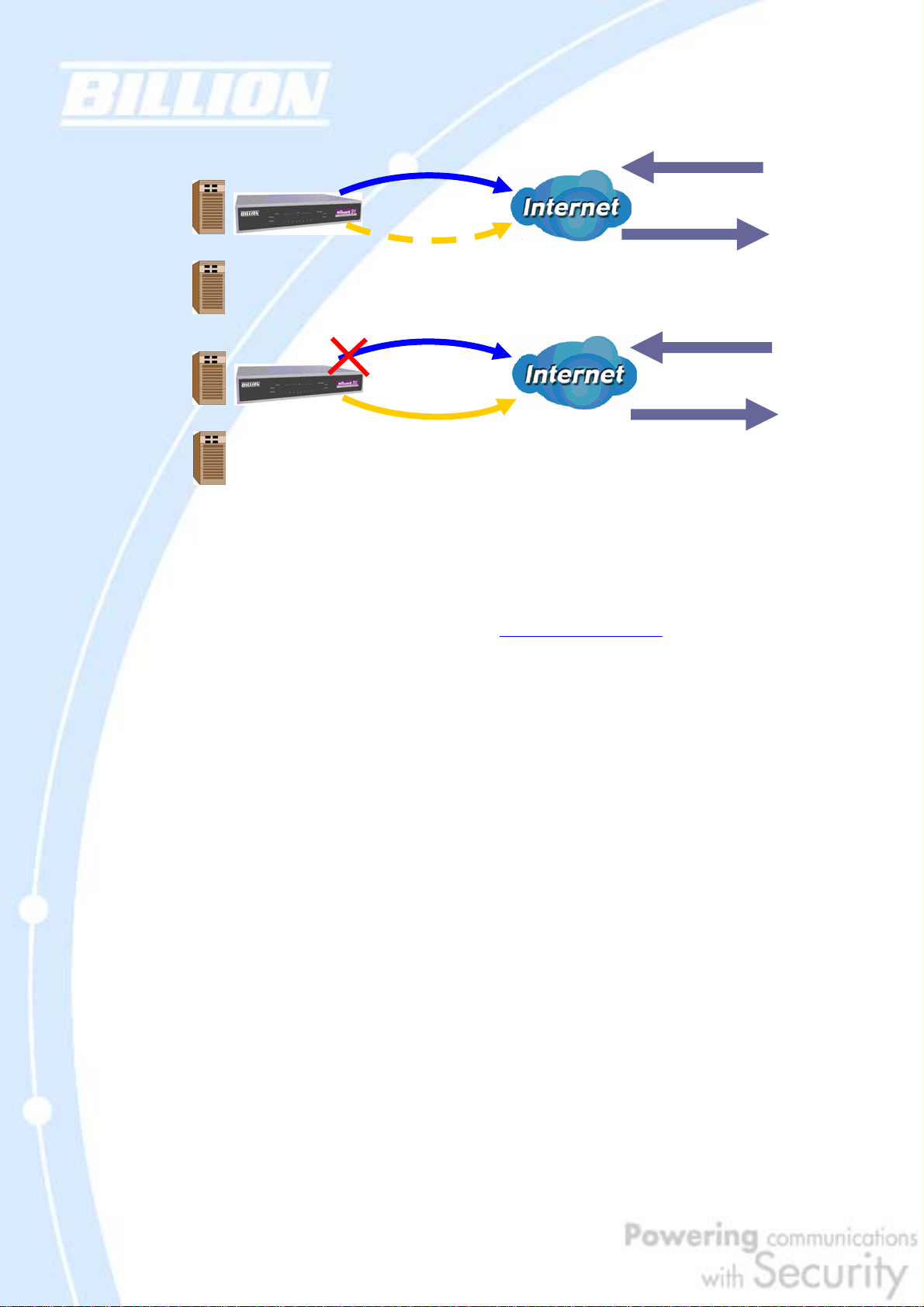
2.4.1 Inbound Fail Over
Configuring BiGuard 30 for Inbound Fail Over allows you to ensure that incoming
traffic is uninterrupted by having BiGuard 30 default to WAN2 should WAN1 fail.
23
Page 24
192.168.2.2
FTP
192.168.2.3
HTTP
192.168.2.2
FTP
192.168.2.3
HTTP
ftp.billion.dyndns.org
Before Fail Over
ftp.billion.dyndns.org
Remote Access from Internet
ftp ftp.billion.dydns.org
ftp ftp.billion.dydns.org
Remote Access from Internet
After Fail Over
In the above example, an FTP Server (IP_192.168.2.2) and an HTTP Server
(IP_192.168.2.3) are connected to the Internet via WAN1 (ftp.billion.dyndns.org)
on BiGuard 30. A remote computer is trying to access these servers via the Internet.
Under normal circumstances, the remote computer will gain access to the network
via WAN1. Should WAN1 fail, Inbound Fail Over tells BiGuard 30 to reroute incoming
traffic to WAN2 by using the Dynamic DNS mechanism. Configuring your BiGuard 30
for Inbound Fail Over provides a more reliable connection for your incoming traffic.
Please refer to appendix H for example settings.
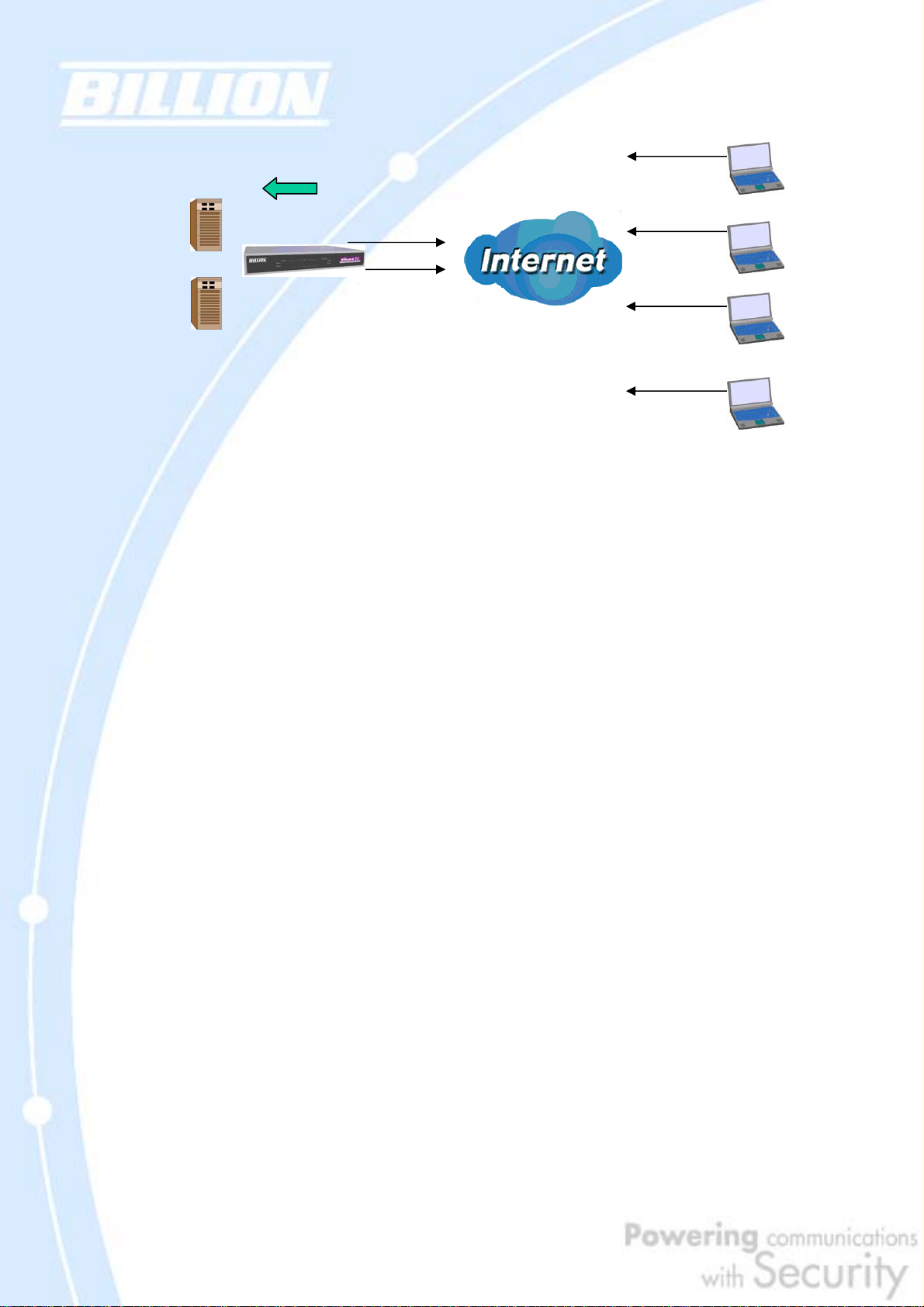
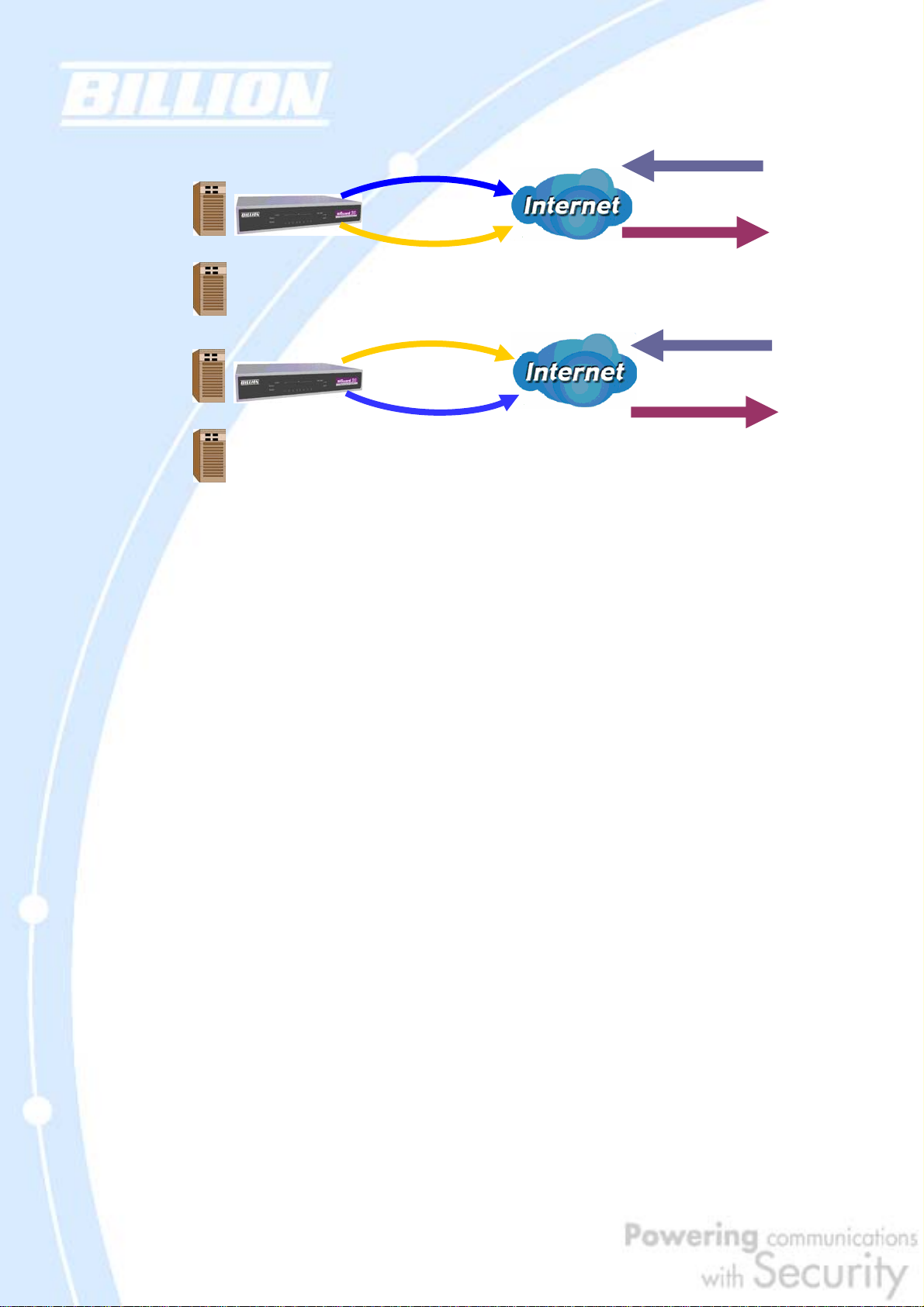
2.4.2 Inbound Load Balancing
Inbound Load Balancing allows BiGuard 30 to intelligently manage inbound traffic
based on the amount of load of each WAN connection.
24
Page 25
192.168.2.2
FTP
192.168.2.3
HTTP
www.billion3.dyndns.org
www.billion2.dyndns.org
www.billion3.dyndns.org
www.billion2.dyndns.org
Remote Access from Internet
In the above example, an FTP server (IP_192.168.2.2) and an HTTP server
(IP_192.168.2.3) are connected to the Internet via WAN1
(www.billion2.dyndns.org) and WAN2 (www.billion3.dyndns.org) on BiGuard 30.
Remote PCs are attempting to access the servers via the Internet. Using Inbound
Load Balancing, BiGuard 30 can direct incoming requests to the correct WAN port
based on group assignment. For example, a sales force can be directed to
www.billion2.dyndns.org, while the R&D group can access www.billion3.dyndns.org.
By balancing the load between WAN1 and WAN2, your BiGuard 30 can ensure that
inbound traffic is efficiently handled with both ports equally sharing the load,
preventing situations where service is slow because one port is completely
saturated by inbound traffic.
Please refer to appendix H for example settings.
2.5 DNS Inbound
Using DNS Inbound is a great way to intelligently direct network traffic.
25
Page 26
ISP
DNS Inbound is a three step process. First, a DNS request is made to the router via
a remote PC. BiGuard 30, based on settings specified by the user, will direct the
requesting PC to the correct WAN port by replying the selected WAN IP address
through the built-in DNS server. The remote PC then accesses the network via the
specified WAN port. How BiGuard 30 directs this traffic through the built-in DNS
server depends on whether it is configured for Fail Over or Load Balancing.
ISP
Learn how to make DNS Inbound on BiGuard 30 work for you in the following
section.
2.5.1 DNS Inbound Fail Over
BiGuard 30 can be configured to reply the WAN2 IP address for the DNS domain
name request should WAN1 fail.
26
Page 27
Authoritative Domain Name Server
192.168.2.2
FTP
192.168.2.3
HTTP
192.168.2.2
FTP
192.168.2.3
HTTP
Built-in DNS
Built-in DNS
200.200.200.1
1st connection
2nd connection
Before Fail Over
1st connection
nd
connection
2
100.100.100.1
www.mydomain.com
200.200.200.1
www.mydomain.com
100.100.100.1
After Fail Over
In the above example, an FTP Server (IP_192.168.2.2) and an HTTP Server
(IP_192.168.2.3) are connected to the Internet via WAN1 (IP_200.200.200.1) on
BiGuard 30. A remote computer is trying to access these servers via the Internet,
and makes a DNS request. The DNS request (www.mydomain.com
) will be sent
through WAN1 (200.200.200.1) to the built-in DNS server. The DNS server will reply
200.200.200.1 because this is the only active WAN port. Should WAN1 fail, BiGuard
30 will instead reply with WAN2’s IP address (100.100.100.1), and the remote PC
will gain access to the network via WAN2. By configuring BiGuard 30 for DNS
Inbound Fail Over, incoming requests will enjoy increased reliability when accessing
your network.
Please refer to appendix H for example settings.
2.5.2 DNS Inbound Load Balancing
DNS Inbound Load Balancing allows BiGuard 30 to intelligently manage inbound
traffic based on the amount of load of each WAN connection by assigning the IP
address with the lowest traffic load to incoming requests.
27
Page 28
2
Authoritative Domain Name Server
192.168.2.2
FTP
192.168.2.3
HTTP
192.168.2.2
FTP
192.168.2.3
HTTP
WAN 1
WAN 2
Built-in DNS
Heavy load on WAN
WAN 1
WAN 2
Built-in DNS
Heavy load on WAN 1
200.200.200.1
100.100.100.1
200.200.200.1
100.100.100.1
www.mydomain.com
DNS Reply
200.200.200.1
www.mydomain.com
DNS Reply
100.100.100.1
In the above example, an FTP server (IP_192.168.2.2) and an HTTP server
(IP_192.168.2.3) are connected to the Internet via WAN1 (IP_200.200.200.1) and
WAN2 (IP_100.100.100.1) on BiGuard 30. Remote PCs are attempting to access the
servers via the Internet by making a DNS request, entering a URL
(www.mydomain.com). Using a load balancing algorithm, BiGuard 30 can direct
incoming requests to either WAN port based on the amount of load each WAN port
is currently experiencing. If WAN2 is experiencing a heavy load, BiGuard 30
responds to incoming DNS requests with WAN1. By balancing the load between
WAN1 and WAN2, your BiGuard 30 can ensure that inbound traffic is efficiently
handled, making sure that both ports are equally sharing the load and preventing
situations where service is slow because one port is completely saturated by
inbound traffic.
Please refer to appendix H for example settings.
A typical scenario of how traffic is directed with DNS Inbound Load Balancing is
illustrated below:
28
Page 29
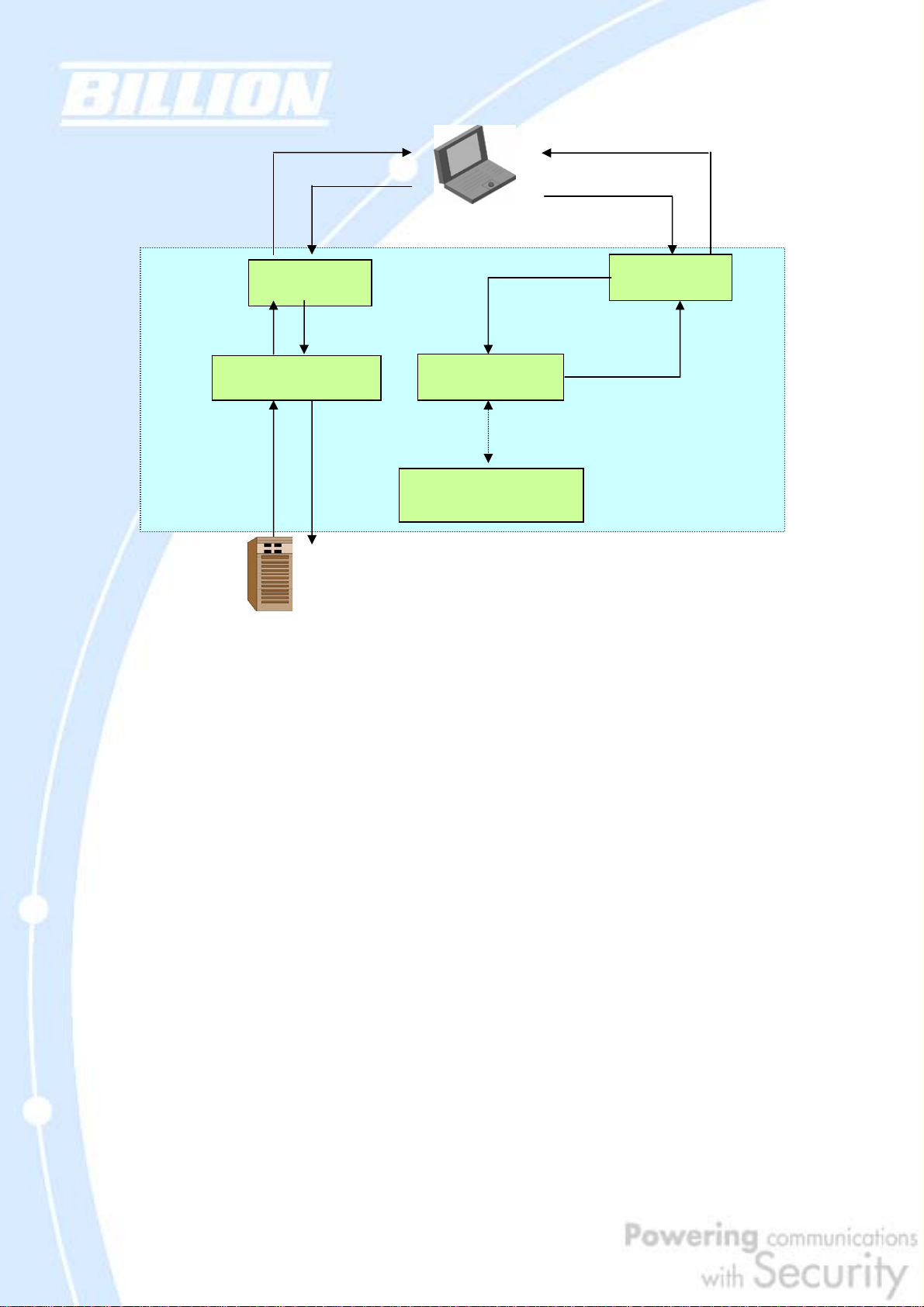
y
r
11
HTTP Repl
HTTP Request
6
WAN 1
10
7
URL Host Map
9
8
1
DNS Request
2
DNS Server
3
Bandwidth Monitor
DNS Reply
5
WAN 2
4
HTTP Serve
In the example above, the client is making a DNS request. The request is sent to the
DNS server of BiGuard 30 through WAN2 (1). WAN2 will route this request to the
embedded DNS server of BiGuard 30 (2). BiGuard 30 will analyze the bandwidth of
both WAN1 and WAN2 and decide which WAN IP to reply to the request (3). After the
decision is made, BiGuard 30 will route the DNS reply to the user through WAN2 (4).
The user will receive the DNS reply with the IP address of WAN1 (5). The browser
will initiate an HTTP request to the WAN1 IP address (6). The HTTP request will be
send to BiGuard 30’s URL Host Map (7). The Host Map will then redirect the HTTP
request to the HTTP server (8). The HTTP server will reply (9). The URL Host Map will
route the packet through WAN1 to the user (10). Finally, the client will receive an
HTTP reply packet (11).
2.6 Virtual Private Networking
A Virtual Private Network (VPN) enables you to send data between two computers
across a shared or public network in a manner that emulates the properties of a
point-to-point private link. As such, it is perfect for connecting branch offices to
headquarters across the Internet in a secure fashion.
29
Page 30
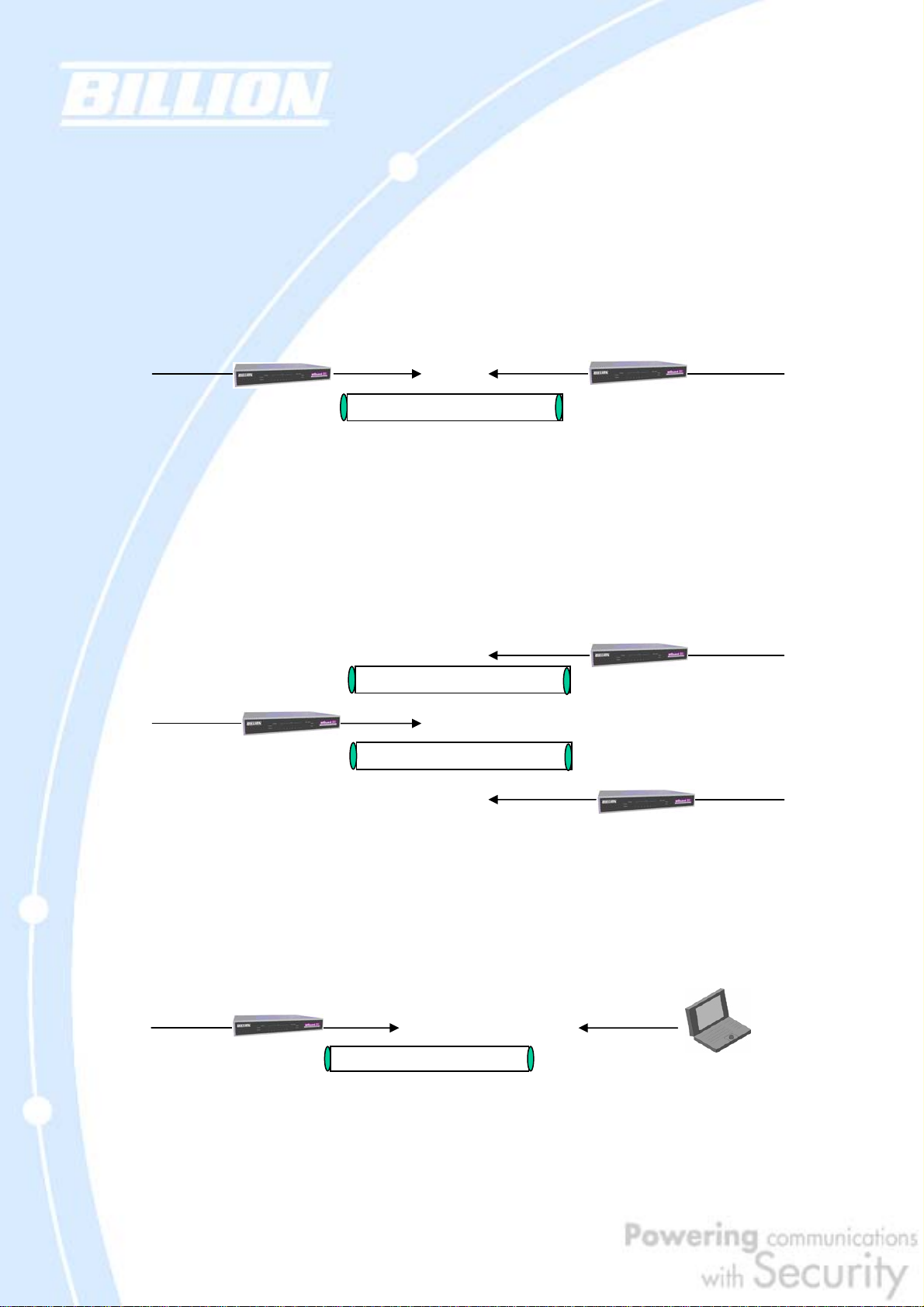
The following section discusses Virtual Private Networking with BiGuard 30.
2.6.1 General VPN Setup
There are typically three different VPN scenarios. The first is a Gateway to
Gateway setup, where two remote gateways communicate over the Internet via a
secure tunnel.
100.100.100.1
192.168.2.x
Secure Tunnel
200.200.200.1
192.168.3.x
The next type of VPN setup is the Gateway to Multiple Gateway setup, where one
gateway (Headquarters) is communicating with multiple gateways (Branch Offices)
over the Internet. As with all VPNs, data is kept secure with secure tunnels.
200.200.200.1
192.168.3.x
192.168.2.x
Secure Tunnel
100.100.100.1
Secure Tunnel
201.201.201.1
192.168.4.x
The final type of VPN setup is the Client to Gateway. A good example of where this
can be applied is when a remote sales person accesses the corporate network over
a secure VPN tunnel.
100.100.100. myID.dyndns.org
192.168.2.x
Secure Tunnel
BiGuard Client
VPN provides a flexible, cost-efficient, and reliable way for companies of all sizes to
stay connected. One of the most important steps in setting up a VPN is proper
30
Page 31

planning. The following sections demonstrate the various ways of using BiGuard 30
to setup your VPN.
2.6.2 VPN Planning - Fail Over
Configuring your VPN with Fail Over allows BiGuard 30 to automatically default to
WAN2 should WAN1 fail.
192.168.2.x
BiGuard30
biguard.billion.com
200.200.200.1
BiGuard10
192.168.3.x
Before Fail Over
192.168.2.x
BiGuard30
200.200.200.1
biguard.billion.com
BiGuard10
192.168.3.x
After Fail Over
Because the dynamic domain name biguard.billion.com is configured for both WAN1
and WAN2, the active WAN port will announce the domain name through the WAN IP
address. The remote gateway will then be able to connect to the VPN through the
domain name.
In this Gateway to Gateway example, BiGuard 30 is communicating to a remote
gateway using WAN1 through a secure VPN tunnel. Should WAN1 fail, outbound
traffic from BiGuard 30 will automatically be redirected to WAN2. This process is
completely transparent to the remote gateway, as BiGuard 30 will automatically
update the domain name (biguard.billion.com) with the WAN2 IP address.
Configuring a Gateway to Multiple Gateway setup with Fail Over is similar, as shown
below:
31
Page 32

192.168.2.x
BiGuard30
100.100.100.1
biguard.billion.com
200.200.200.1
BiGuard10
BiGuard10
192.168.3.x
192.168.4.x
Before Fail Over
100.100.100.1 192.168.3.x
192.168.2.x
BiGuard30
biguard.billion.com
200.200.200.1
Configuring BiGuard 30 for Fail Over provides added reliability to your VPN.
2.6.3 Concentrator
BiGuard10
BiGuard10
192.168.4.x
The VPN Concentrator provides an easy way for branch offices to connect to
headquarter through a VPN tunnel. All branch office traffic will be redirected to the
VPN tunnel to headquarter with the exception of LAN-side traffic. This way, all
branch offices can connect to each other through headquarter via the headquarter’s
firewall management. You can also configure BiGuard 30 to function as a VPN
Concentrator:
Please refer to appendix H for example settings.
Local subnet: 192.168.3.0
Local subnet: 0.0.0.0
Local mask: 0.0.0.0
Remote subnet: 192.168.3.0
Remote mask: 255.255.255.0
192.168.2.x
200.200.200.1
100.100.100.1
Local mask: 255.255.255.0
Remote subnet: 0.0.0.0
Remote mask: 0.0.0.0
192.168.3.x
BiGuard 10
BiGuard 30
Local subnet: 0.0.0.0
Local mask: 0.0.0.0
Remote subnet: 192.168.4.0
Remote mask: 255.255.255.0
32
201.201.201.1
BiGuard 10
Local subnet: 192.168.4.0
Local mask: 255.255.255.0
Remote subnet: 0.0.0.0
Remote mask: 0.0.0.0
192.168.4.x
Page 33

Chapter 3: Getting Started
3.1 Overview
BiGuard 30 is designed to be a powerful and flexible network device that is also easy
to use. With an intuitive web-based configuration, BiGuard 30 allows you to
administer your network via virtually any Java-enabled web browser and is fully
compatible with Linux, Mac OS, and Windows 98/Me/NT/2000/XP operating
systems.
The following chapter takes you through the very first steps to configuring your
network for BiGuard 30. Take a look and see how easy it is to get your network up
and running.
3.2 Before You Begin
BiGuard 30 is a flexible and powerful networking device. To simplify the
configuration process and increase the efficiency of your network, consider the
following items before setting up your network for the first time:
1. Plan your network
Decide whether you are going to use one or both WAN ports. For one WAN port, you
may need a fully qualified domain name either for convenience or if you have a
dynamic IP address. If you are going to use both WAN ports, determine whether you
are going to use them in fail over mode for increased network reliability or load
balancing mode for maximum bandwidth efficiency. See Chapter 2: Router
Applications for more information.
2. Set up your accounts
Have access to the Internet and locate the Internet Service Provider (ISP)
configuration information. Each BiGuard 30 WAN port must be configured separately,
whether you are using a separate ISP for each WAN port or are having the traffic of
both WAN ports routed through the same ISP.
3. Determine your network management approach
BiGuard 30 is capable of remote management. However, this feature is not active by
default. If you reset the device, remote administration must be enabled again. If
you decide to manage your network remotely, be sure to change the default
33
Page 34
password for security reason.
4. Prepare to physically connect BiGuard 30 to Cable or DSL modems and a
computer.
Be sure to also review the Safety Warnings located in the preface of this manual
before working with your BiGuard 30.
3.3 Connecting Your Router
Connecting BiGuard 30 is an easy three-step process:
1. Connect BiGuard 30 to your LAN by connecting Ethernet cables from your
networked PCs to the LAN ports on the router. Connect BiGuard 30 to your
broadband Internet connection via router’s WAN port.
2. Plug BiGuard 30 to an AC outlet with the included AC Power Adapter.
3. Ensure that the Power and WAN LEDs are solidly lit, and that on any LAN port that
has an Ethernet cable plugged in the LED is also solidly lit. The Status LED will
remain solid as the device boots. Once the boot sequence is complete, the LED will
shut off, indicating that BiGuard 30 is ready.
If the router does not power on, please refer to Chapter 5: Troubleshooting for
possible solutions.
34
Page 35

3.4 Configuring PCs for TCP/IP Networking
Now that your BiGuard 30 is connected properly to your network, it’s time to
configure your networked PCs for TCP/IP networking.
In order for your networked PCs to communicate with your router, they must have
the following characteristics:
1. Have a properly installed and functioning Ethernet Network Interface Card (NIC).
2. Be connected to BiGuard 30, either directly or through an external repeater hub
via an Ethernet cable.
3. Have TCP/IP installed and configured with an IP address.
The IP address for each PC may be a fixed IP address or one that is obtained from a
DHCP server. If using a fixed IP address, it is important to remember that it must be
in the same subnet as the router. The default IP address of BiGuard 30 is
192.168.1.254 with a subnet mask of 255.255.255.0. Using the default
configuration, networked PCs must reside in the same subnet, and have an IP
address in the range of 192.168.1.1 to 192.168.1.253. However, you’ll find that the
quickest and easiest way to configure the IP addresses for your PCs is to obtain the
IP addresses automatically by using the router as a DHCP server.
If you are unable to access the web configuration interface, check to see if you have
any software-based firewalls installed on your PCs, as they can cause problems
accessing the 192.168.1.254 IP address of BiGuard 30.
The following sections outline how to set up your PCs for TCP/IP networking. Refer
to the applicable section for your PC’s operating system.
3.4.1 Overview
Before you begin, make sure that the TCP/IP protocol and a functioning Ethernet
network adapter is installed on each of your PCs.
The following operating systems already include the necessary software
components you need to install TCP/IP on your PCs:
- Windows 95/98/Me/NT/2000/XP
35
Page 36

- Mac OS 7 and later
If you are using Windows 3.1, you must purchase a third-party TCP/IP application
package.
Any TCP/IP capable workstation can be used to communicate with or through
BiGuard 30. To configure other types of workstations, please consult the
manufacturer’s documentation.
3.4.2 Windows XP
3.4.2.1 Configuring
1. Select Start > Settings > Network Connections.
2. In the Network Connections window, right-click Local Area Connection and
select Properties.
36
Page 37

3. Select Internet Protocol (TCP/IP) and click Properties.
4a. To have your PC obtain an IP address automatically, select the Obtain an IP
37
Page 38

address automatically and Obtain DNS server address automatically radio
buttons.
4b. To manually assign your PC a fixed IP address, select the Use the followin g IP
address radio button and enter your desired IP address, subnet mask, and default
gateway in the blanks provided. Remember that your PC must reside in the same
subnet mask as the router. To designate a DNS server, select the Use the following
DNS server and fill in the preferred DNS address.
5. Click OK to finish the configuration.
38
Page 39

3.4.2.2 Verifying Settings
To verify your settings using a command prompt:
1. Click Start > Programs > Accessories > Command Prompt.
2. In the Command Prompt window, type ipconfig and then press ENTER.
If you are using BiGuard 30’s default settings, your PC should have:
39
Page 40

- An IP address between 192.168.1.1 and 192.168.1.253
- A subnet mask of 255.255.255.0
To verify your settings using the Windows XP GUI:
1. Click Start > Settings > Network Connections.
40
Page 41

2. Right click one of the network connections listed and select Status from the
pop-up menu.
3. Click the Support tab.
41
Page 42

If you are using BiGuard 30’s default settings, your PC should:
- Have an IP address between 192.168.1.1 and 192.168.1.253
- Have a subnet mask of 255.255.255.0
3.4.3 Windows 2000
3.4.3.1 Configuring
1. Select Start > Settings > Control Panel.
42
Page 43

2. In the Control Panel window, double-click Network and Dial-up Connections.
3. In Network and Dial-up Connections, double-click Local Area Connection.
43
Page 44

4. In the Local Area Connection window, click Properties.
5. Select Internet Protocol (TCP/IP) and click Properties.
44
Page 45

6a. To have your PC obtain an IP address automatically, select the Obtain an IP
address automatically and Obtain DNS server address automatically radio
buttons.
6b. To manually assign your PC a fixed IP address, select the Use the following IP
address radio button and enter your desired IP address, subnet mask, and default
gateway in the blanks provided. Remember that your PC must reside in the same
subnet mask as the router. To designate a DNS server, select the Use the following
DNS server and fill in the preferred DNS address.
45
Page 46

7. Click OK to finish the configuration.
3.4.3.2 Verifying Settings
1. Click Start > Programs > Accessories > Command Prompt.
46
Page 47

2. In the Command Prompt window, type ipconfig and then press ENTER.
If you are using BiGuard 30’s default settings, your PC should have:
- An IP address between 192.168.1.1 and 192.168.1.253
- A subnet mask of 255.255.255.0
47
Page 48

3.4.4 Windows 98 / Me
3.4.4.1 Installing Components
To prepare Windows 98/Me PCs for TCP/IP networking, you may need to manually
install TCP/IP on each PC. To do this, follow the steps below. Be sure to have your
Windows CD handy, as you may need to insert it during the installation process.
1. On the Windows taskbar, select Start > Settings > Control Panel.
2. Double-click the Network icon. The Network window displays a list of installed
components.
48
Page 49

You must have the following installed:
49
Page 50

- An Ethernet adapter
- TCP/IP protocol
- Client for Microsoft Networks
If you need to install a new Ethernet adapter, follow these steps:
a. Click Add.
b. Select Adapter, then Add.
c. Select the manufacturer and model of your Ethernet adapter, then click OK.
50
Page 51

If you need TCP/IP:
a. Click Add.
b. Select Protocol, then click Add.
51
Page 52

c. Select Microsoft. Æ TCP/IP, then OK.
If you need Client for Microsoft Networks:
a. Click Add.
52
Page 53

b. Select Client, then click Add.
c. Select Microsoft. Æ Client for Microsoft Networks, and then click OK.
3. Restart your PC to apply your changes.
3.4.4.2 Configuring
1. Select Start > Settings > Control Panel.
53
Page 54

2. In the Control Panel, double-click Network and choose the Configuration tab.
54
Page 55

3. Select TCP / IP > ASUSTek or the name of any Network Interface Card (NIC) in
your PC and click Properties.
4. Select the IP Address tab and click the Obtain an IP address automatically
radio button.
55
Page 56

5. Select the DNS Configuration tab and select the Disable DNS radio button.
6. Click OK to apply the configuration.
56
Page 57

3.4.4.3 Verifying Settings
To check the TCP/IP configuration, use the winipcfg.exe utility:
1. Select Start > Run.
2. Type winipcfg, and then click OK.
3. From the drop-down box, select your Ethernet adapter.
57
Page 58

The window is updated to show your settings. Using the default BiGuard 30 settings,
your PC should have:
- An IP address between 192.168.1.1 and 192.168.1.253
- A subnet mask of 255.255.255.0
- A default gateway of 192.168.1.254
3.5 Factory Default Settings
Before configuring your BiGuard 30, you need to know the following default
settings:
Web Interface:
Username: admin
Password: admin
LAN Device IP Settings:
IP Address: 192.168.1.254
Subnet Mask: 255.255.255.0
58
Page 59

ISP setting in WAN site:
Obtain an IP Address automatically (DHCP Client)
DHCP server:
DHCP server is enabled.
Start IP Address: 192.168.1.100
End IP Address: 192.168.1.199
3.5.1 User Name and Password
The default user name and password are "admin" and "admin" respectively.
If you ever forget your user name and/or password, you can restore your BiGuard
30 to its factory settings by holding the Reset button on the back of your router until
the Status LED begins to blink. Please note that doing this will also erase any
previous router settings that you have made. The Status LED will remain solid as the
device boots. Once the boot sequence is complete, the LED will shut off, indicating
that BiGuard 30 is ready.
3.5.2 LAN and WAN Port Addresses
The default values for LAN and WAN ports are shown below:
LAN Port WAN Port
IP address
192.168.1.254
The DHCP Client is enabled to
automatically get the WAN port
Subnet Mask
DHCP server
255.255.255.0
Enabled
configuration from the ISP.
function
IP addresses for
100 IP addresses continuing
distribution to
PCs
from 192.168.1.100 through
192.168.1.199
3.6 Information From Your ISP
3.6.1 Protocols
59
Page 60

Before configuring this device, you have to check with your ISP (Internet Service
Pr ovider) to find out what kind of s ervice is provided such as DHCP, Static IP, PPPoE,
or PPTP. The following table outlines each of these protocols:
Configure this WAN interface to use DHCP client protocol to get an IP
DHCP
address from your ISP automatically. Your ISP provides an IP address to
the router dynamically when logging in.
Configure this WAN interface with a specific IP address. This IP address
Static IP
should be provided by your ISP.
PPPoE (PPP over Ethernet) is known as a dial-up DSL or cable service. It
is designed to integrate the broadband services into the current widely
PPPoE
deployed, easy-to-use, and low-cost dial-up-access networking
infrastructure.
If your ISP provides a PPTP connection, you can use the PPTP protocol
PPTP
to establish a connection to your ISP.
Big Pond
If your account uses PPP over Ethernet (PPPoE), you will need to enter your login
The Big Pond login for Telstra cable in Australia.
name and password when configuring your BiGuard 30. After the network and
firewall are configured, BiGuard 30 will login automatically, and you will no longer
need to run the login program from your PC.
3.6.2 Configuration Information
If your ISP does not dynamically assign configuration information but instead uses
fixed configurations, you will need the following basic information from your ISP:
- An IP address and subnet mask
- A gateway IP address
- One or more domain name server (DNS) IP addresses
Depending on your ISP, a host name and domain suffix may also be provided. If any
of these items are dynamically supplied by the ISP, your BiGuard 30 will
automatically acquire them.
60
Page 61

If an ISP technician configured your computer or if you configured it using
instructions provided by your ISP, you need to copy the configuration information
from your PC’s Network TCP/IP Properties window before reconfiguring your
computer for use with BiGuard 30. The following sections describe how you can
obtain this information.
3.6.2.1 Windows
This section uses illustrations from Windows XP. However, other versions of
Windows will follow a similar procedure. Have your Windows CD handy, as it may be
required during the configuration process.
1. Select Start > Settings > Control Panel.
2. Double-click the Network icon.
61
Page 62

3. In the Network Connections window, right-click Local Area Connection and
select Properties.
4. Select Internet Protocol (TCP/IP) and click Properties.
62
Page 63

5. If an IP address, subnet mask and a Default gateway are shown, write down
the information. If no address is present, your account’s IP address is dynamically
assigned. Click the Obtain an IP address automatically radio button.
6. If any DNS server addresses are shown, write them down. Click the Obtain DNS
63
Page 64

server address automatically radio button.
7. Click OK to save your changes.
64
Page 65

3.7 Web Configuration Interface
BiGuard 30 includes a Web Configuration Interface for easy administration via
virtually any browser on your network. To access this interface, open your web
browser, enter the IP address of your router, which by default is 192.168.1.254, and
click Go. A user name and password window prompt will appear. Enter your user
name and password (the default user name and password are "admin" and "admin")
to access the Web Configuration Interface.
If the Web Configuration Interface appears, congratulations! You are now ready to
configure your BiGuard 30. If you are having trouble accessing the interface, please
refer to Chapter 5: Troubleshooting for possible resolutions.
65
Page 66

Chapter 4: Router Configuration
4.1 Overview
The Web Configuration Interface makes it easy for you to manage your network via
any PC connected to it. On the Web Configuration homepage, you will see the
navigation pane located on the left hand side. From it, you will be able to select
various options used to configure your router.
1. Click Apply if you would like to apply the settings on the current screen to the
device. The settings will be effective immediately, however the configuration is not
saved yet and the settings will be erased if you power off or restart the device.
2. Click SAVE CONFIG to save the current settings permanently to the device.
3. Click RESTART to restart the device. There are two options to restart the device.
- Select Current Settings if would like to restart using the current configuration.
- Select Factory Default Settings if you would like to restart using the factory
default configuration.
4. To exit the router’s web interface, click LOGOUT. Please ensure that you have
saved your configuration settings before you logout. Be aware that the router is
restricted to only one PC accessing the web configuration interface at a time. Once
a PC has logged into the web interface, other PCs cannot gain access until the
current PC has logged out. If the previous PC forgets to logout, the second PC can
66
Page 67

access the page after a user-defined period (5 minutes by default).
The following sections will show you how to configure your router using the Web
Configuration Interface.
4.2 Status
The Status menu displays the various options that have been selected and a number
of statistics about your BiGuard 30. In this menu, you will find the following
sections:
- ARP Table
- Routing Table
- Session Table
- DHCP Table
- IPSec Status
- PPTP Status
- Traffic Statistics
- System Log
- IPSec Log
4.2.1 ARP Table
The Address Resolution Protocol (ARP) Table shows the mapping of Internet (IP)
addresses to Ethernet (MAC) addresses. This is a quick way to determine the MAC
address of your PC’s network interface to use with the router’s Firewall – MAC
Address Filter function. See the Firewall section of this chapter for more
information on this feature.
67
Page 68
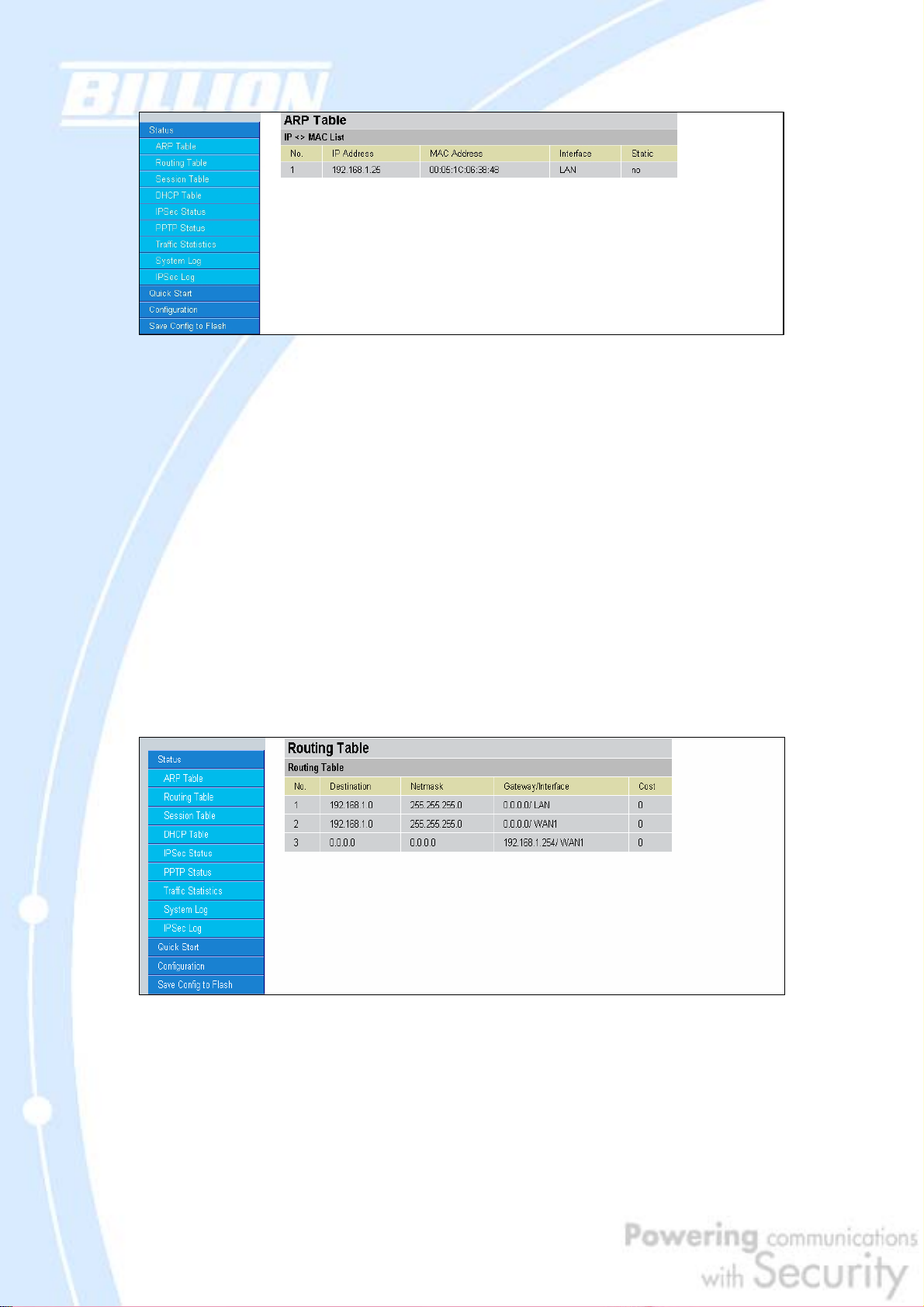
No.: Number of the list.
IP Address: A list of IP addresses of devices on your LAN.
MAC Address: The Media Access Control (MAC) addresses for each device on your
LAN.
Interface: The interface name (on the router) that this IP address connects to.
Static: Static status of the ARP table entry.
NO indicates dynamically-generated ARP table entries.
YES indicates static ARP table entries added by the user.
4.2.2 Routing Table
The Routing Table displays the current path for transmitted packets. Both static and
dynamic routes are displayed.
No.: Number of the list.
Destination: The IP address of the destination network.
Netmask: The destination netmask address.
Gateway/Interface: The IP address of the gateway or existing interface that this
route will use.
Cost: The number of hops counted as the cost of the route.
68
Page 69

4.2.3 Session Table
The NAT Session Table displays a list of current sessions for both incoming and
outgoing traffic with protocol type, source IP, source port, destination IP and
destination port, each page shows 10 sessions.
No.: Number of the list.
Protocol: Protocol type of the Session.
From IP: Source IP of the session.
From port: source port of the session.
To IP: Destination IP of the session.
To port: Destination port of the session.
Sessions:
Filter: when the presented field is filled, please click Filter button.
From IP: please input the source IP you would like to filter.
From port: please input the source port you would like to filter.
To IP: please input the destination IP you would like to filter.
To port: please input the destination port you would like to filter.
First: To the first page.
Previous: To the previous page.
Next: To the next page.
Last: To the last page.
Jump to the session: please input the session number you would like to see and
press “GO”
4.2.4 DHCP Table
The DHCP Table displays a list of IP addresses that have been assigned to PCs on
69
Page 70

your network via Dynamic Host Configuration Protocol (DHCP).
No.: Number of the list.
IP Address: A list of IP addresses of devices on your LAN.
Device Name: The host name (computer name) of the client.
MAC Address: The MAC address of client.
4.2.5 IPSec Status
The IPSec Status window displays the status of the IPSec Tunnels that are currently
configured on your BiGuard 30.
Name: The name you assigned to the particular IPSec entry.
Enable: Whether the IPSec connection is currently Enable or Disable.
Status: Whether the IPSec is Active, Inactive or Disable.
Local Subnet: The local IP address or subnet used.
Remote Subnet: The subnet of the remote site.
Remote Gateway: The remote gateway IP address.
SA: The Security Association for this IPSec entry.
Action: Manually connect or drop the tunnel.
70
Page 71

4.2.6 PPTP Status
The PPTP Status window displays the status of the PPTP Tunnels that are currently
configured on your BiGuard 30.
Name: The name you assigned to the particular PPTP entry.
Enable: Whether the PPTP connection is currently Enable or Disable.
Status: Whether the PPTP is Active, Inactive or Disable.
Type: Whether the Connection type is Remote Access or LAN to LAN
Peer Network: The Remote subnet for LAN to LAN as connection type.
Connect by: The remote address when connected.
Action: Manually drop the tunnel.
4.2.7 Traffic Statistics
The Traffic Statistics window displays both sent and received sent data (in Bytes/sec)
over a one hour duration. The line in red represents WAN1, while the line in blue
represents WAN2.
71
Page 72

WAN1: Transmitted (Tx) and Received (Rx) bytes and packets for WAN1.
WAN2: Transmitted (Tx) and Received (Rx) bytes and packets for WAN2.
Display: Allows you to change the units of measurement for the traffic graph.
4.2.8 System Log
This window displays BiGuard 30’s System Log entries. Major events are logged on
this window.
Refresh: Refresh the System Log.
Clear Log: Clear the System Log.
Send Log: Send the System Log to your email account. You can set the email
address in Configuration > System > Email Alert. See the Email Alert section
for more details.
4.2.9 IPSec Log
This page displays the router’s IPSec Log entries. Major events are logged to this
window.
72
Page 73

Refresh: Refresh the IPSec Log.
Clear Log: Clear the IPSec Log.
Send Log: Send IPSec Log to your email account. You can set the email address in
Configuration > System > Email Alert. See the Email Alert section for more
details.
Please refer to Appendix F: IPSec Log Events for more information on log events.
4.3 Quick Start
The Quick Start menu allows you to quickly configure your network for Internet
access using the most basic settings.
Connection Method: Select your router’s connection to the Internet. Selections
include Obtain an IP Address Automatically, Static IP Settings, PPPoE
Settings, PPTP Settings, and Big Pond Settings.
4.3.1 DHCP
The following is information regarding your ISP that you will need to enter in order
to properly configure your Internet connection. If you select to Obtain an IP
Address Automatically, these will be automatically set for you, provided that your
ISP dynamically assigns an IP address.
73
Page 74

4.3.2 Static IP
IP assigned by your ISP: Enter the assigned IP address from your IP.
IP Subnet Mask: Enter your IP subnet mask.
ISP Gateway Address: Enter your ISP gateway address.
Primary DNS: Enter your primary DNS.
Secondary DNS: Enter your secondary DNS.
Click Apply to save your changes. To reset to defaults, click Reset.
4.3.3 PPPoE
Username: Enter your user name.
Password: Enter your password.
Retype Password: Retype your password.
Connection: Select whether the connection should Always Connect or Trigger on
Demand. If you want the router to establish a PPPoE session when starting up and
to automatically re-establish the PPPoE session when disconnected by the ISP,
select Always Connect. If you want to establish a PPPoE session only when there
is a packet requesting access to the Internet (i.e. when a program on your computer
attempts to access the Internet), select Trigger on Demand .
Idle Time: Auto-disconnect the router when there is no activity on the line for a
predetermined period of time. Select the idle time from the d rop do wn menu. A ctiv e
if Trigger on Demand is selected.
Click Apply to save your changes. To reset to defaults, click Reset.
74
Page 75

4.3.4 PPTP
Username: Enter your user name.
Password: Enter your password.
Retype Password: Retype your password.
PPTP Client IP: Enter the PPTP Client IP provided by your ISP.
PPTP Client IP Netmask: Enter the PPTP Client IP Netmask provided by your ISP.
PPTP Client IP Gateway: Enter the PPTP Client IP Gateway provided by your ISP.
PPTP Server IP: Enter the PPTP Server IP provided by your ISP.
Connection: Select whether the connection should Always Connect or Trigger on
Demand. If you want the router to establish a PPTP session when starting up and to
automatically re-establish the PPTP session when disconnected by the ISP, select
Always Connect. If you want to establish a PPTP session only when there is a
packet requesting access to the Internet (i.e. when a program on your computer
attempts to access the Internet), select Trigger on Demand .
Idle Time: Auto-disconnect the router when there is no activity on the line for a
predetermined period of time. Select the idle time from the d rop do wn menu. A ctiv e
if Trigger on Demand is selected.
Click Apply to save your changes. To reset to defaults, click Reset.
4.3.5 Big Pond
75
Page 76

Username: Enter your user name.
Password: Enter your password.
Retype Password: Retype your password.
Login Server: Enter the IP of the Login server provided by your ISP.
Click Apply to save your changes. To reset to defaults, click Reset.
For detailed instructions on configuring WAN settings, please refer to the WAN
section of this chapter.
4.4 Configuration
The Configuration menu allows you to set many of the operating parameters of
BiGuard 30. In this menu, you will find the following sections:
- LAN
- WAN
- Dual WAN
- System
- Firewall
- VPN
- QoS
- Virtual Server
- Advanced
These items are described below in the following sections.
76
Page 77
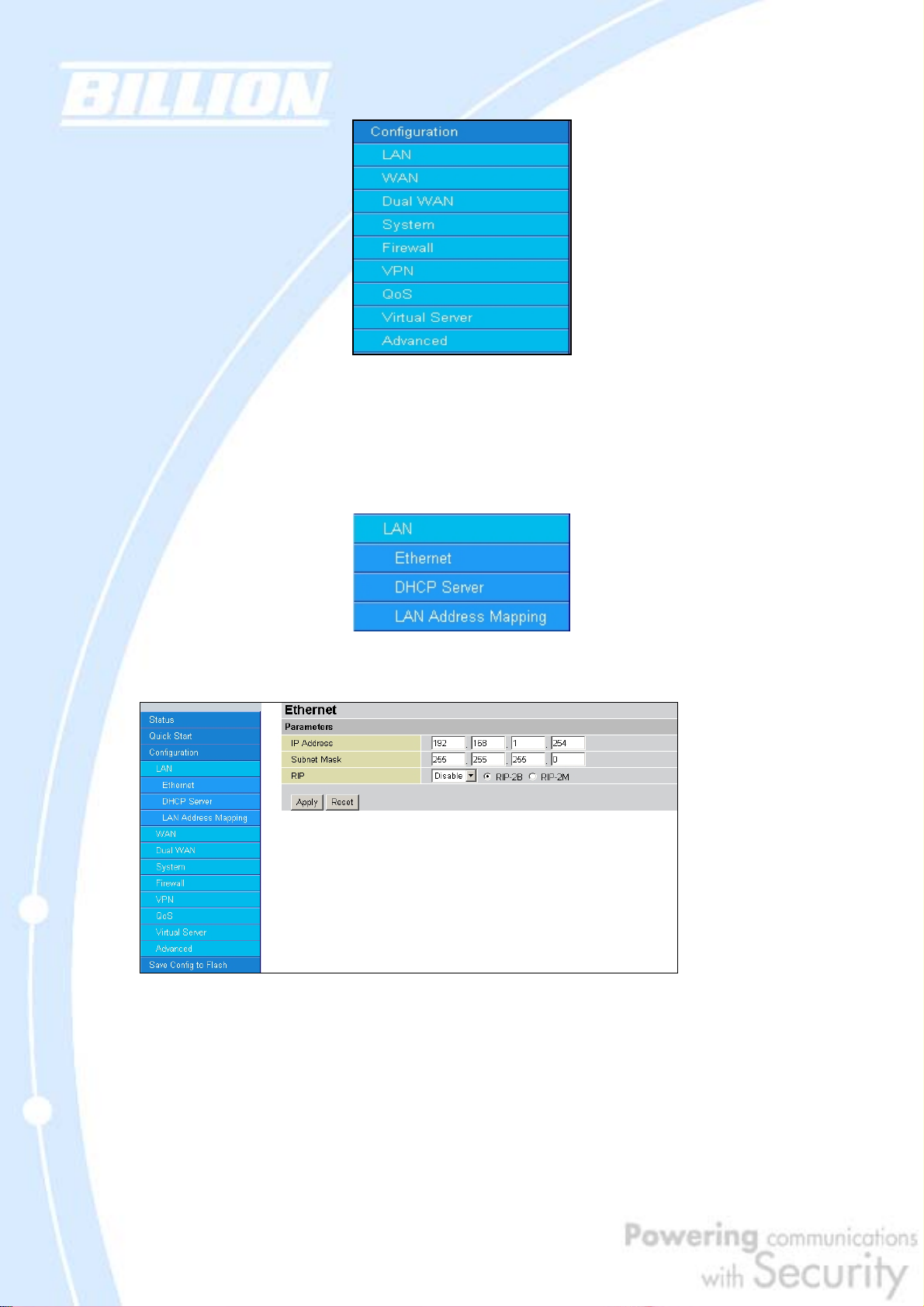
4.4.1 LAN
There are three items within this section: Ethernet, DHCP Server and LAN
Address Mapping.
4.4.1.1 Ethernet
IP Address: Enter the internal LAN IP address for BiGuard 30 (192.168.1.254 by
default).
Subnet Mask: Enter the subnet mask (255.255.255.0 by default).
RIP: RIP v2 Broadcast and RIP v2 Multicast. Check to enable RIP.
77
Page 78
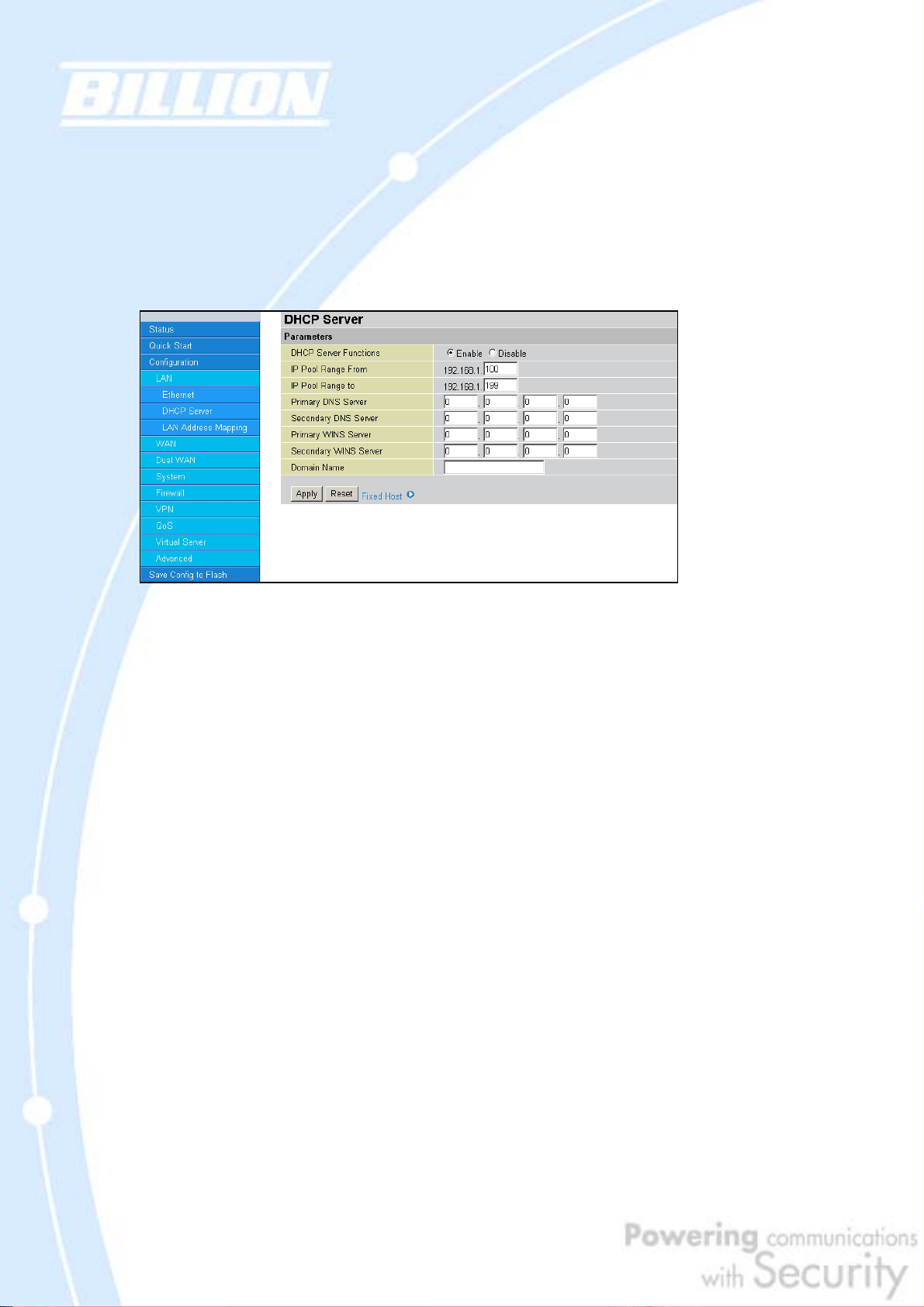
4.4.1.2 DHCP Server
In this menu, you can disable or enable the Dynamic Host Configuration Protocol
(DHCP) server. The DHCP protocol allows your BiGuard 30 to dynamically assign IP
addresses to PCs on your network if they are configured to automatically obtain IP
addresses.
To disable the router’s DHCP Server, select the Disable radio button, and then click
Apply. When the DHCP Server is disabled, you will need to manually assign a fixed
IP address to each PC on your network, and set the default gateway for each PC to
the IP address of the router (192.168.1.254 by default).
To configure the router’s DHCP Server, select the Enable radio button, and then
configure parameters of the DHCP Server including the IP Pool (starting IP address
and ending IP address to be allocated to the PCs on your network), DNS Server,
WINS Server, and Domain Name. These details are sent to each DHCP client when
they request an IP address from the DHCP server. Click Apply to enable this
function.
Fixed Host allows specific computer/network clients to have a reserved IP address.
78
Page 79

Name: Enter the name you want to give for the IP+Mac Address Fixed Host
account.
Active: Select whether you want to Enable or Disable this particular Fixed Host
account.
IP Address: Enter the IP address that you want to reserve for the above MAC
address.
MAC Address: Enter the MAC address of the PC or server you wish to be assigned
a reserved IP.
Candidates: You can also select the Candidates which are referred from the ARP
table for automatic input.
Click the Apply button to add the configuration into the Host Table.
4.4.1.3 LAN Address Mapping
LAN Address Mapping is a function that can support multiple subnet and also
multiple NAT, you can specify a subnet and LAN Gateway IP Address and select
associated WAN IP Address specified in WAN IP Alias in Configuration -> WAN ->
WAN IP Alias.
79
Page 80

Please click Create to create a LAN Address Mapping rule.
Name: Please input the name of the rule.
IP Address: Please input the LAN Gateway IP Address you would like to use.
Netmask: Please input the Netmask you would like to use.
WAN IP Address: Please click Candidates to select the WAN IP address you would
like to use from WAN Alias list.
Click the Apply button to add the configuration into the LAN Address Mapping.
4.4.2 WAN
WAN refers to your Wide Area Network connection. In most cases, this means your
router’s connection to the Internet through your ISP. BiGuard30 features Dual WAN
capability
. There are three items within this section:
80
Page 81

The WAN menu contains two items: ISP Settings, Bandwidth Settings and WAN
IP Alias.
4.4.2.1 ISP Settings
This WAN Service Table displays the different WAN connections that are configured
on BiGuard 30. To edit any of these connections, click Edit. You will be taken to the
following menu.
81
Page 82

Connection Method: Select how your router will connect to the Internet. Selections
include Obtain an IP Address Automatically, Static IP Settings, PPPoE
Settings, PPTP Settings, and Big Pond Settings. For each WAN port, the factory
default is DHCP. If your ISP does not use DHCP, select the correct connection
method and configure the connection accordingly. Configurable items will vary
depending on the connection method selected.
4.4.2.1.1 DHCP
Host Name: Some ISPs authenticate logins using this field.
MAC Address: If your ISP requires you to input a WAN Ethernet MAC, check the
checkbox and enter your MAC address in the blanks below.
Candidates: You can also select the MAC address from the list in the Candidates.
DNS: If your ISP requires you to manually setup DNS settings, check the checkbox
82
Page 83

and enter your primary and secondary DNS.
RIP: To activate RIP, select Send, Receive, or Both from the drop down menu. To
disable RIP, select Disable from the drop down menu.
MTU: Enter the Maximum Transmission Unit (MTU) for your network.
Network Address Translation: Enables or Disables the NAT function. To apply this
interface as router mode please select Disable. Due to default firewall feature, if you
would like to use router mode, you have to input the packet filter rules you would
like to forward in Configuration -> Firewall -> Packet filter
Click Apply to save your changes. To reset to defaults, click Reset.
4.4.2.1.2 Static IP
IP assigned by your ISP: Enter the static IP assigned by your ISP.
IP Subnet Mask: Enter the IP subnet mask provided by your ISP.
ISP Gateway Address: Enter the ISP gateway address provided by your ISP.
MAC Address: If your ISP requires you to input a WAN Ethernet MAC, check the
checkbox and enter your MAC address in the blanks below.
Candidates: You can also select the MAC address from the list in the Candidates.
Primary DNS: Enter the primary DNS provided by your ISP.
Secondary DNS: Enter the secondary DNS provided by your ISP.
RIP: To activate RIP, select Send, Receive, or Both from the drop down menu. To
disable RIP, select Disable from the drop down menu.
MTU: Enter the Maximum Transmission Unit (MTU) for your network.
Network Address Translation: Enables or Disables the NAT function. To apply this
interface as router mode please select Disable. Due to default firewall feature, if you
83
Page 84

would like to use router mode, you have to input the packet filter rules you would
like to forward in Configuration -> Firewall -> Packet filter
Click Apply to save your changes. To reset to defaults, click Reset.
4.4.2.1.3 PPPoE
Username: Enter your user name.
Password: Enter your password.
Retype Password: Retype your password.
Connection: Select whether the connection should Always Connect or Trigger on
Demand. If you want the router to establish a PPPoE session when starting up and
to automatically re-establish the PPPoE session when disconnected by the ISP,
select Always Connect. If you want to establish a PPPoE session only when there
is a packet requesting access to the Internet (i.e. when a program on your computer
attempts to access the Internet), select Trigger on Demand .
Idle Time: Auto-disconnect the router when there is no activity on the line for a
predetermined period of time. Select the idle time from the d rop do wn menu. A ctiv e
if Trigger on Demand is selected.
IP Assigned by your ISP: If your IP is dynamically assigned by your ISP, select the
Dynamic radio button. If your IP assigns a static IP address, select the Static radio
button, and input your IP address in the blank provided.
84
Page 85

MAC Address: If your ISP requires you to input a WAN Ethernet MAC, check the
checkbox and enter your MAC address in the blanks below.
Candidates: You can also select the MAC address from the list in the Candidates.
DNS: If your ISP requires you to manually setup DNS settings, check the checkbox
and enter your primary and secondary DNS.
RIP: To activate RIP, select Send, Receive, or Both from the drop down menu. To
disable RIP, select Disable from the drop down menu.
MTU: Enter the Maximum Transmission Unit (MTU) for your network.
Network Address Translation: Enables or Disables the NAT function. To apply this
interface as router mode please select Disable. Due to default firewall feature, if you
would like to use router mode, you have to input the packet filter rules you would
like to forward in Configuration -> Firewall -> Packet filter
Click Apply to save your changes. To reset to defaults, click Reset.
4.4.2.1.4 PPTP Settings
Username: Enter your user name.
Password: Enter your password.
Retype Password: Retype your password.
PPTP Client IP: Enter the PPTP Client IP provided by your ISP.
PPTP Client IP Netmask: Enter the PPTP Client IP Netmask provided by your ISP.
85
Page 86

PPTP Client IP Gateway: Enter the PPTP Client IP Gateway provided by your ISP.
PPTP Server IP: Enter the PPTP Server IP provided by your ISP.
Connection: Select whether the connection should Always Connect or Trigger on
Demand. If you want the router to establish a PPTP session when starting up and to
automatically re-establish the PPTP session when disconnected by the ISP, select
Always Connect. If you want to establish a PPTP session only when there is a
packet requesting access to the Internet (i.e. when a program on your computer
attempts to access the Internet), select Trigger on Demand .
Idle Time: Auto-disconnect the router when there is no activity on the line for a
predetermined period of time. Select the idle time from the d rop do wn menu. A ctiv e
if Trigger on Demand is selected.
IP Assigned by your ISP: If your IP is dynamically assigned by your ISP, select the
Dynamic radio button. If your IP assigns a static IP address, select the Static radio
button. This will take you to another page for inputting the IP address information.
MAC Address: If your ISP requires you to input a WAN Ethernet MAC, check the
checkbox and enter your MAC address in the blanks below.
Candidates: You can also select the MAC address from the list in the Candidates.
DNS: If your ISP requires you to manually setup DNS settings, check the checkbox
and enter your primary and secondary DNS.
RIP: To activate RIP, select Send, Receive, or Both from the drop down menu. To
disable RIP, select Disable from the drop down menu.
MTU: Enter the Maximum Transmission Unit (MTU) for your network.
Network Address Translation: Enables or Disables the NAT function. To apply this
interface as router mode please select Disable. Due to default firewall feature, if you
would like to use router mode, you have to input the packet filter rules you would
like to forward in Configuration -> Firewall -> Packet filter
Click Apply to save your changes. To reset to defaults, click Reset.
4.4.2.1.5 Big Pond Settings
86
Page 87

Username: Enter your user name.
Password: Enter your password.
Retype Password: Retype your password.
Login Server: Enter the IP of the Login server provided by your ISP.
MAC Address: If your ISP requires you to input a WAN Ethernet MAC, check the
checkbox and enter your MAC address in the blanks below.
Candidates: You can also select the MAC address from the list in the Candidates.
DNS: If your ISP requires you to manually setup DNS settings, check the checkbox
and enter your primary and secondary DNS.
RIP: To activate RIP, select Send, Receive, or Both from the drop down menu. To
disable RIP, select Disable from the drop down menu.
MTU: Enter the Maximum Transmission Unit (MTU) for your network.
Network Address Translation: Enables or Disables the NAT function. To apply this
interface as router mode please select Disable. Due to default firewall feature, if you
would like to use router mode, you have to input the packet filter rules you would
like to forward in Configuration -> Firewall -> Packet filter
Click Apply to save your changes. To reset to defaults, click Reset.
A simpler alternative is to select Quick Start from the main menu. Please see the
Quick Start section of this chapter for more information.
4.4.2.2 Bandwidth Settings
Under Bandwidth Settings, you can easily configure both inbound and outbound
87
Page 88

bandwidth for each WAN port.
WAN1: Enter your ISP inbound and outbound bandwidth for WAN1.
WAN2: Enter your ISP inbound and outbound bandwidth for WAN2.
NOTE: These values entered here are referenced by both QoS and Load Balancing
functions.
4.4.2.3 WAN IP Alias
WAN IP Alias allows you to input additional WAN IP addresses. WAN IP Alias can be
used for Multiple NAT settings, including LAN Address Mapping settings and Virtual
Server settings.
Please click Create to create a LAN Address Mapping rule.
88
Page 89
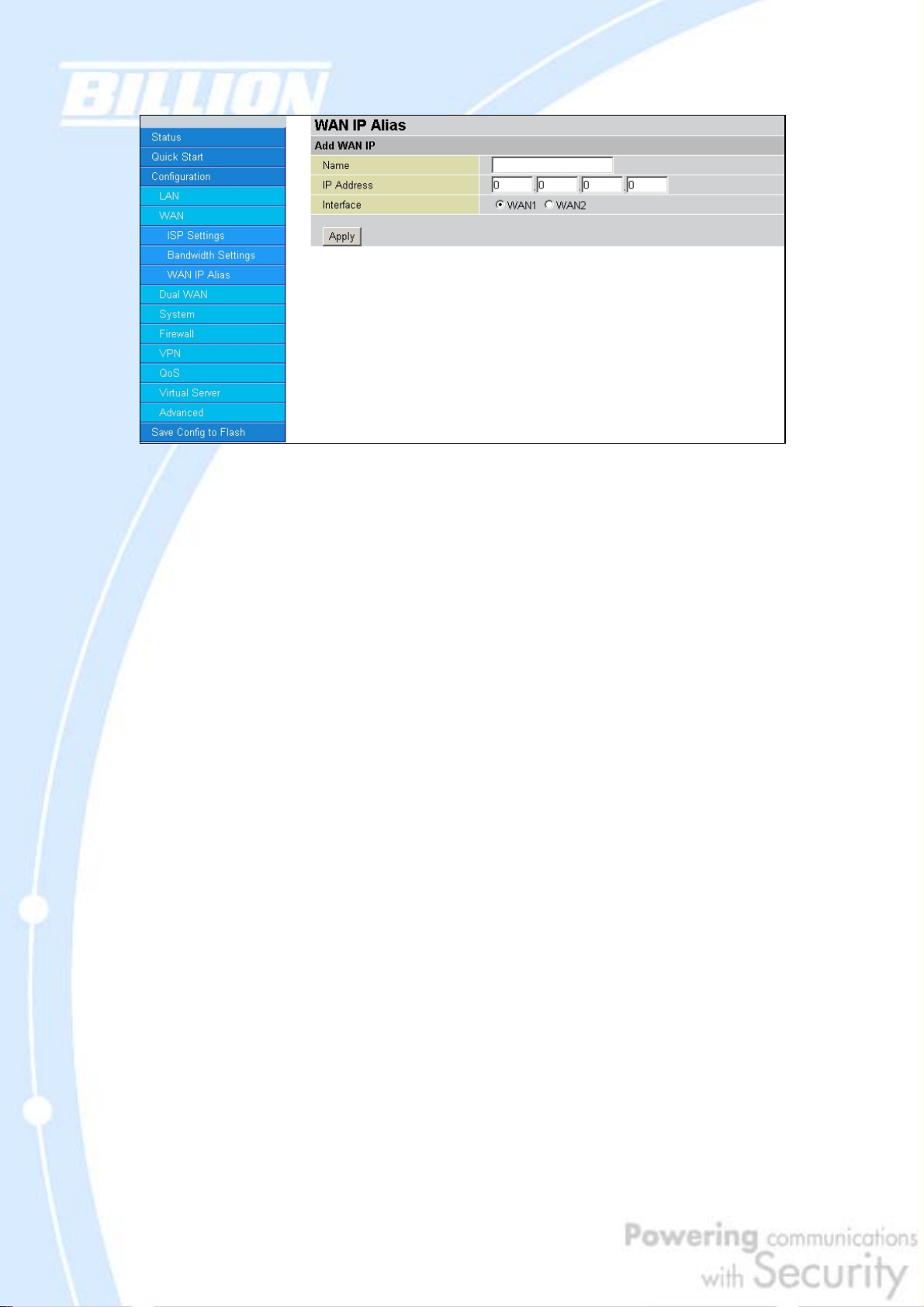
Name: Please input the name of the rule.
IP Address: Please input the additional WAN IP address you would like to use.
Interface: Please select the WAN Interface that you would like to add the additional
WAN IP to.
Click the Apply button to add the configuration into the WAN IP Alias.
4.4.3 Dual WAN
In this section, you can setup the fail over or load balance function, outbound load
balance or inbound load balance function, or setup specific protocol to bind with
specific WAN port. In this menu are the following sections: General Settings,
Outbound Load Balance, Inbound Load Balance, and Protocol Binding.
4.4.3.1 General Settings
89
Page 90

Mode: You can select Load Balance or Fail Over.
Service Detection: Enables or disables the service detection feature. For fail over,
the service detection function is enabled. For load balance, user is able to enable or
disable it.
Connectivity Decision: Establishes the number of times probing the connection has
to fail before the connection is judged as failed.
Probe Cycle: The number of seconds between each probe.
Probe WAN1: Determines if WAN1 is a gateway or host. If host is selected, please
enter the IP address.
Probe WAN2: Determines if WAN2 is a gateway or host. If host is selected, please
enter the IP address.
Fail back to WAN1 when possible: Enables or disables fail back to WAN1. This
function only applies to fail over.
Click Apply to save your changes.
4.4.3.2 Outbound Load Balance
90
Page 91

Outbound Load Balancing on BiGuard 30 can be based on one of two methods:
1. By session mechanism
2. By IP address hash mechanism
Choose one by clicking the corresponding radio button.
Based on Session Mechanism: The source IP address and destination IP address
might go through WAN1 or WAN2 according to policy settings in this mechanism.
You can choose this mechanism if the applications the users use will not tell the
difference of the WAN IP addresses. (some applications in the Internet need to
identify the source IP address, e.g. Back, Forum, …)
Balance by Session (Round Robin): Balances session traffic based on a round
robin method.
Balance by Session (weight of length capacity): Balances session traffic based
on weight of length capacity.
Balance by Session weight: Balances session traffic based on a weight ratio.
Enter the desired ratio in the blanks provided.
Balance by Traffic (weight of length capacity): Balances traffic based on weight
of link capacity.
Balance by Traffic weight: Balances traffic based on a traffic weight ratio. Enter
the desired ratio into the blanks provided.
Based on IP hash mechanism: The source IP address and destination IP address will
go through specific WAN port (WAN1 or WAN2) according to policy settings in this
mechanism. This will assure that some applications will work when it would like to
91
Page 92

authenticate the source IP address.
Balance by weight of link capacity: Uses an IP hash to balance traffic based on
weight of link bandwidth capacity.
Balance by weight: Uses an IP hash to balance traffic based on a ratio. Enter
the desired ratio into the blanks provided.
Click Apply to save your changes.
4.4.3.3 Inbound Load Balance
Function: Used to enable or disable inbound load balancing.
DNS Server 1: DNS Server 1 settings including Host URL mappings.
DNS Server 2: DNS Server 2 settings including Host URL mappings.
To edit server settings, click Edit. The following example illustrates DNS Server 1
settings. DNS Server 2 settings follow a similar procedure.
92
Page 93

SOA:
Domain Name: The domain name of DNS Server 1. It is the name that you
register on DNS organization. You have to fill-out the Fully Qualified Domain Name
(FQDN) with an ending character (a dot) for this text field.(ex:abc.com.).When you
enter the following domain name, you can only input different chars without an
ending dot, its name is then added with domain name, and it becomes FQDN.
Primary Name Server: The name assigned to the Primary Name Server.
(e.g:aaa, its FQDN is aaa.abc.com.)
Admin. Mail Box: The administrator’s email account.(e.g:admin@abc.com.)
Serial Number: It is the version number that keeps in the SOA record.
Refresh Interval: The interval refreshes are done. Denoted in seconds.
Retry Interval: The interval retries are done. Denoted in seconds.
Expir ation Ti m e: The le n g th of ti m e that ca n elapse b e f ore the z one is n o longer
authoritative. Denoted in seconds.
Minimum TTL: The minimum time to live. Denoted in seconds.
NS Record
Name Server: The name of the Primary Name Server.
MX Record
Mail Exchanger: The name of the mail server.
IP Address: The mail server IP address.
Click Apply to save your changes.
93
Page 94

To edit the Host Mapping URL list, click Edit. This will open the Host Mapping URL
table, which lists the current Host Mapping URLs.
To add a host mapping URL to the list, click Create.
Domain Name: The domain name of the local host.
Host URL: The URL to be mapped.
Private IP Address: The IP address of the local host.
Helper: You could also select the application type you would like to apply for
automatic input.
94
Page 95

Port Range: The port range of all incoming packets are accepted and processed by
a local host with the specified private IP address.
Candidates: You can also select the Candidates which are referred from the ARP
table for automatic input.
Name1: The Alias Host URL
Name2: The Alias Host URL
Click Apply to save your changes.
4.4.3.4 Protocol Binding
Protocol Binding lets you direct specific traffic to go out from a specific WAN port.
Click the Create button to create a new policy entry. Policies entered would tell
specific types of Internet traffic from a particular range of IPs to go to a particular
range of IPs with ONE WAN port, rather than using both of the WAN ports with load
balancing.
(NOTE: If any policies are added in the Protocol Binding section, please note that it
would take precedence over the settings that are already configured in the Load
Balance Setting section.)
The Protocol Binding Table lists any protocol binding that has been configured. To
add a new binding, click
Create.
95
Page 96

Interface: Choose which WAN port to use: WAN1, WAN2
Packet Type: The particular protocol of Internet traffic for the specified policy.
Choose from TCP, UDP, or Any.
Source IP Range:
All Source IP: Click it to specify all source IPs.
Specified Source IP: Click to specify a specific source IP address and source IP
netmask.
Source IP Address: If Specified Source IP was chosen, here’s where the IP can be
entered.
Source IP Netmask: If Specified Source IP was chosen, here’s where the subnet
mask can be entered.
Destination IP Range:
All Destination IP: Click it to specify all source IPs.
Specified Destination IP: Click to specify a specific destination IP address and
Destination IP Netmask.
Destination IP Address: If Specified Destination IP was chosen, here’s where the IP
can be entered.
Destination IP Netmask: If Specified Destination IP was chosen, here’s where the
subnet mask can be entered.
Port Range: The range of ports for the specified policy (if you only want to use one
port, enter the same value in both boxes).
Click Apply to save your changes.
96
Page 97

4.4.4 System
The System menu allows you to adjust a variety of basic router settings, upgrade
firmware, set up remote access, and more. In this menu are the following sections:
Time Zone, Remote Access, Firmware Upgrade, Backup/Restore, Restart,
Password, System Log and E-mail Alert.
4.4.4.1 Time Zone
BiGuard does not use an onboard real time clock; instead, it uses the Network Time
Protocol (NTP) to acquire the current time from an NTP server outside your network.
Simply choose your local time zone, enter NTP Server IP Address, and click Apply.
After connecting to the Internet, BiGuard 30 will retrieve the correct local time from
the NTP server you have specified. Your ISP may provide an NTP server for you to
use.
97
Page 98

Time Zone: Select Enable or Disable this function.
Local Time Zone(+-GMT Time): Please select the time zone that belongs to your
area.
NTP Server Address: Please input the NTP server address you would like to use.
Daylight Saving: To have BiGuard 30 automatically adjust for Daylight Savings Time,
please check the Automatic checkbox.
Resync Period: Please input the resync circle of time zone update.
Click Apply to apply the rule, Click Cancel to discard the changes.
4.4.4.2 Remote Access
To allow remote users to configure and manage BiGuard 30 through the Internet,
select the Enable radio button. To deactivate remote access, select the Disable radio
button. This function also enables you to grant access from any PC or from a specific
IP address. Click Apply to save your settings.
NOTE: When enabling remote access, please make sure to change the default
administration password for security reason.
Action: Select Enable or Disable remote access function.
HTTPS Port: Please input the remote access HTTPS port you would like to
use.(default is 443)
Click Apply to apply your settings.
Click Create to add a Remote Access Table to specify the allowed remote access
addresses.
98
Page 99

Allow Remote Access By:
Everyone: Please check if you allow any IP addresses for the remote user to access.
Only the PC: Please specify the IP Address that is allowed to access.
PC from the subnet: Please specify the subnet that is allowed to access.
4.4.4.3 Firmware Upgrade
Upgrading your BiGuard 30’s firmware is a quick and easy way to enjoy increased
99
Page 100

functionality, better reliability, and ensure trouble-free operation. To upgrade your
firmware, simply visit Billion’s website (http://www.billion.com
latest firmware image file for BiGuard 30. Next, click Browse and select the newly
downloaded firmware file. Click Upgrade to complete the update.
NOTE: DO NOT power down the router or interrupt the firmware upgrade while it is
still in process. Interrupting the firmware upgrade process could damage the router.
) and download the
4.4.4.4 Backup / Restore
This feature allows you to save and backup your router’s current settings, or restore
a previously saved backup. This is useful if you wish to experiment with different
settings, knowing that you have a backup handy. It is advisable to backup your
router’s settings before making any significant changes to your router’s
configuration.
To backup your router’s settings, click Backup and select where to save the settings
backup file. You may also change the name of the file when saving if you wish to
keep multiple backups. Click OK to save the file.
100
 Loading...
Loading...