
7402 Series
ADSL2+ Triple Play Modem/Router
User’s Manual


TTaabbllee ooff CCoonntteennttss
CHAPTER 1: INTRODUCTION..............................................................................................................1
I
NTRODUCTION TO YOUR 7402 ROUTER .....................................................................................................1
EATURES ..................................................................................................................................................1
F
7402
ADSL ROUTER APPLICATION............................................................................................................4
CHAPTER 2: INSTALLING THE ROUTER .........................................................................................5
MPORTANT NOTE FOR USING THE 7402 ADSL ROUTER.............................................................................5
I
P
ACKAGE CONTENTS..................................................................................................................................5
T
HE FRONT LEDS ......................................................................................................................................6
T
HE REAR PORTS .......................................................................................................................................7
C
ABLING ....................................................................................................................................................8
CHAPTER 3: BASIC INSTALLATION.......................................................... ............................... .........9
C
ONNECTING YOUR ROUTER.......................................................................................................................9
F
ACTORY DEFAULT SETTINGS..................................................................................................................17
Web Interface (Username and Password)...........................................................................................17
LAN Device IP Settings.......................................................................................................................17
ISP setting in WAN site .......................................................................................................................17
DHCP server................................................................................................................... ....................17
LAN and WAN Port Addresses............................................................................................................17
I
NFORMATION FROM YOUR ISP ................................................................................................................18
C
ONFIGURING WITH YOUR WEB BROWSER ..............................................................................................19
CHAPTER 4: CONFIGURATION..................................... ..................... ................ ........... ............... .....20
TATUS.....................................................................................................................................................21
S
ARP Table............................................................................................................................................21
Wireless Association Table .................................................................................................................22
Routing Table......................................................................................................................................23
DHCP Table................. ........................... .............................. .................. ..................... .......................24
PPTP Status.........................................................................................................................................25
IPSec Status..................................................................... ........... .......................... ...............................26
L2TP Status .........................................................................................................................................27
Email Status.........................................................................................................................................27
Event Log.............................................................................................................................................28
Error Log.............................................................................................................................................28
NAT Sessions. ............................................................... .......................................................................29
UPnP Portmap ....................................................................................................................................29
Q
UICK START ...........................................................................................................................................30
C
ONFIGURATION ......................................................................................................................................32
LAN (Local Area Network)..................................................................................................................32
Ethernet..........................................................................................................................................32
Ethernet Client Filter....................................................................................................................33
Wireless ..........................................................................................................................................35
Wireless Security................................................................................. ........... ........... ....................37
Wireless Client (MAC Address) Filter........................................................................................39
DHCP Server .................................................................................................................................41
WAN (Wide Area Network) .................................................................................................................42
ISP...................................................................................................................................................42
DNS.................................................................................................................................................52
ADSL..............................................................................................................................................53

System..................................................................................................................................................54
Time Zone ................................................................................. ...................... ...............................54
Remote Access............................................................................................................ ....................55
Firmware Upgrade. ................ ...................... ................... ............................... ...............................56
Backup / Restore................................................................ ..... ........... .......... .............. ....................57
Restart Router ...............................................................................................................................58
User Management..........................................................................................................................59
Firewall and Access Control...............................................................................................................60
General Settings.............................................................................................................................62
Packet Filter................................................. ......................... ............... ........................ ..................63
Intrusion Detection........................................................................................................................70
URL Filtering.................................................................................................................................72
Firewall Log....................................................................................... ............................................75
VPN (Virtual Private Networks).............................................. ........... ............. .................... ................76
PPTP (Point-to-Point Tunneling Protocol).................................................................................76
IPSec (IP Security Protocol).........................................................................................................81
L2TP (Layer Two Tunneling Protocol).......................................................................................87
QoS (Quality of Service)................................................................................ ...................... ..............112
Prioritization................................................................................................................................113
Outbound IP Throttling (LAN to WAN) ..................................................................................115
Inbound IP Throttling (WAN to LAN) .....................................................................................116
Virtual Server (“Port Forwarding”).................................................................................................120
Add Virtual Server......................................................................................................................121
Edit DMZ Host ............................................................................................................................123
Edit One-to-One NAT (Network Address Translation) ..........................................................124
Time Schedule....................................................................................................................................127
Configuration of Time Schedule ................................................................................................128
Advanced...........................................................................................................................................130
Static Routing ..............................................................................................................................130
Dynamic DNS...............................................................................................................................131
Check Emails ...............................................................................................................................132
Device Management ....................................................................................................................133
IGMP............................................................................................................................................137
S
AVE CONFIGURATION TO FLASH...........................................................................................................138
L
OGOUT .................................................................................................................................................139
CHAPTER 5: TROUBLESHOOTING............................ ..... ...... ... ...... ......... ........ ......... .... ..... .. .... ... .... .140
P
ROBLEMS STARTING UP THE ROUTER....................................................................................................140
P
ROBLEMS WITH THE WAN INTERFACE.................................................................................................140
P
ROBLEMS WITH THE LAN INTERFACE ..................................................................................................141
APPENDIX A: PRODUCT SUPPORT AND CONTACT INFORMATION............................ .......142
Chapter 1: Introduction
Introduction to your 7402 Series Router
Welcome to the BEC 7402 Series Router. The router is an “all-in-one” unit, combining an ADSL modem,
IEEE 802.11g wireless access point (optional), ADSL router with four-port 10/100M auto-crossover
Switch, and Firewall, enabling you to maximize the potential of your existing resources. The 7402 can
provide everything you need to get the machines on your network connected to the Internet over your
ADSL broadband connection. It supports the latest ADSL2/2+ technology enabling high-speed data
rates of up to 24Mbps, Its powerful QoS feature for traffic priority and bandwidth management, and
security features including multiple VPN tunnels (optional) with 3DES make the device a perfect mate to
the office user or for anyone who has the compelling needs to transmit sensitive data more securely.
With integrated 54Mbps 802.11g Access Point (optional) in this device, the router brings up the
productivity and mobility to office users.
With features such as an ADSL Quick-Start wizard and DHCP Server, you can be online in no time at all
and with a minimum of fuss and configuration, catering for first-time users to the guru requiring
advanced features and control over their Internet connection and network.
Features
The 7402 ADSL2+ Triple Play Router combines high-speed Internet access, networking, and
advanced security for office local area network. It provides:
Express Internet Access – capabl e of ADSL2/2+
The router complies with ADSL worldwide standards. It supports downstream rates up to 8Mbps
with ADSL, capable of up to 12/24 Mbps with ADSL2/2+, and upstream rates up to 1 Mbps. Users
enjoy not only high-speed ADSL services but also broadband multimedia applications such as
interactive gaming, video streaming and real-time audio much easier and faster than ever. It is
compliant with Multi-Mode standard (ANSI T1.413, Issue 2; G.dmt (ITU G.992.1); G.hs (ITU
G994.1); G.dmt.bis (ITU G.992.3); G.dmt.bisplus (ITU G.992.5)).
Wireless Ethernet 802.11g (Optional)
With integrated 802.11g Wireless Access Point in the router, the device offers a quick and easy
access among wired network, wireless network and broadband connection (ADSL) with single
device simplicity, and as a result, mobility to the users. In addition to 54 Mbps 802.11g data rate, it
also interoperates backward with existing 802.11b equipment. The Wireless Protected Access
(WPA) and Wireless Encryption Protocol (WEP) supported features enhance the security level of
data protection and access control via Wireless LAN.
Fast Ethernet Switch
A 4-port 10/100Mbps fast Ethernet switch is built in with automatic switching between MDI and
MDI-X for 10Base-T and 100Base-TX ports. An Ethernet straight or crossover cable can be used
directly for auto detection.
Multi-Protocol to Establish A Connection
Supports PPPoA (RFC 2364 - PPP over ATM Adaptation Layer 5), RFC 1483 encapsulation over
ATM (bridged or routed), PPP over Ethernet (RFC 2516) and IPoA (RFC1577) to establish a
connection with the ISP. The product also supports VC-based and LLC-based multiplexing.
Quick Installation Wizard
Supports a WEB GUI page to install this device quickly. With this wizard, end users can enter the
information easily which they get from their ISP, then surf the Internet immediately.
1
Universal Plug and Play (UPnP) and UPnP NAT Traversal
This protocol is used to enable simple and robust connectivity among stand-alone devices and
PCs from many different vendors. It makes network simple and affordable for users. UPnP
architecture leverages TCP/IP and the Web to enable seamless proximity networking in addition to
control and data transfer among networked devices. With this feature enabled, users can now
connect to Net meeting or MSN Messenger seamlessly.
Network Address Translation (NAT)
Allows multi-users to access outside resources such as the Internet simultaneously with one IP
address/one Internet access account. Many application layer gateway (ALG) are supported such
as web browser, ICQ, FTP, Telnet, E-mail, News, Net2phone, Ping, NetMeeting, IP phone and
others.
Firewall
Supports SOHO firewall with NAT technology. Automatically detects and blocks Denial of Service
(DoS) attacks. The URL blocking, packet filtering and SPI (Stateful Packet Inspection) are also
supported. The hacker’s attack will be recorded associated with timestamp in the security logging
area. More firewall functions will always be implemented through updated firmware releases.
Domain Name System (DNS) relay
Provides an easy way to map the domain name (a friendly name for users such as
www.yahoo.com
) and IP address. When local machine sets its DNS server with this router’s IP
address, every DNS conversion request packet from the PC to this router will be forwarded to the
real DNS in the outside network.
Dynamic Domain Name System (DDNS)
The Dynamic DNS service allows you to alias a dynamic IP address to a static hostname. This
dynamic IP address is the WAN IP address. For example, to use the service, you must first apply
for an account from a DDNS service like http://www.dyndns.org/
. More than 5 DDNS servers are
supported.
PPP over Ethernet (PPPoE)
Provides embedded PPPoE client function to establish a connection. Users can get greater
access speed without changing the operation concept, sharing the same ISP account and paying
for one access account. No PPPoE client software is required for local computer. The Automatic
Reconnect and Disconnect Timeout (Idle Timer) functions are provided, too.
Virtual Private Network (V PN) (O pti onal)
Allows user to make a tunnel with a remote site directly to secure the data transmission among the
connection. User can use embedded PPTP and L2TP client/server, IKE and IPSec which are
supported by this router to make a VPN connection or users can run the PPTP client in PC and the
router already provides IPSec and PPTP pass through function to establish a VPN connection if
the user likes to run the PPTP client in his local computer.
Virtual Server (“port forwarding”)
Users can specify some services to be visible from outside users. The router can detect incoming
service requests and forward either a single port or a range of ports to the specific local computer
to handle it. For example, a user can assign a PC in the LAN acting as a WEB server inside and
expose it to the outside network. Outside users can browse inside web servers directly while it is
protected by NAT. A DMZ host setting is also provided to a local computer exposed to the outside
network, Internet.
Rich Packet Filtering
Not only filters the packet based on IP address, but also based on Port numbers. It will filter
packets from and to the Internet, and also provides a higher level of security control.
2
Dynamic Host Configuration Protocol (DHCP) client and server
In the WAN site, the DHCP client can get an IP address from the Internet Service Provider (ISP)
automatically. In the LAN site, the DHCP server can allocate a range of client IP addresses and
distribute them including IP address, subnet mask as well as DNS IP address to local computers. It
provides an easy way to manage the local IP network.
Static and RIP1/2 Routing
Supports an easy static routing table or RIP1/2 routing protocol to support routing capability.
Simple Network Management Protocol (SNMP)
It is an easy way to remotely manage the router via SNMP.
Web based GUI
Supports web based GUI for configuration and management. It is user-friendly and comes with online help. It also supports remote management capability for remote users to configure and
manage this product.
Firmware Upgradeable
Device can be upgraded to the latest firmware through the WEB based GUI.
Rich management interfaces
Supports flexible management interfaces with local console port, LAN port, and WAN port. Users
can use terminal applications through the console port to configure and manage the device, or
Telnet, WEB GUI, and SNMP through LAN or WAN ports to configure and manage the device.
3
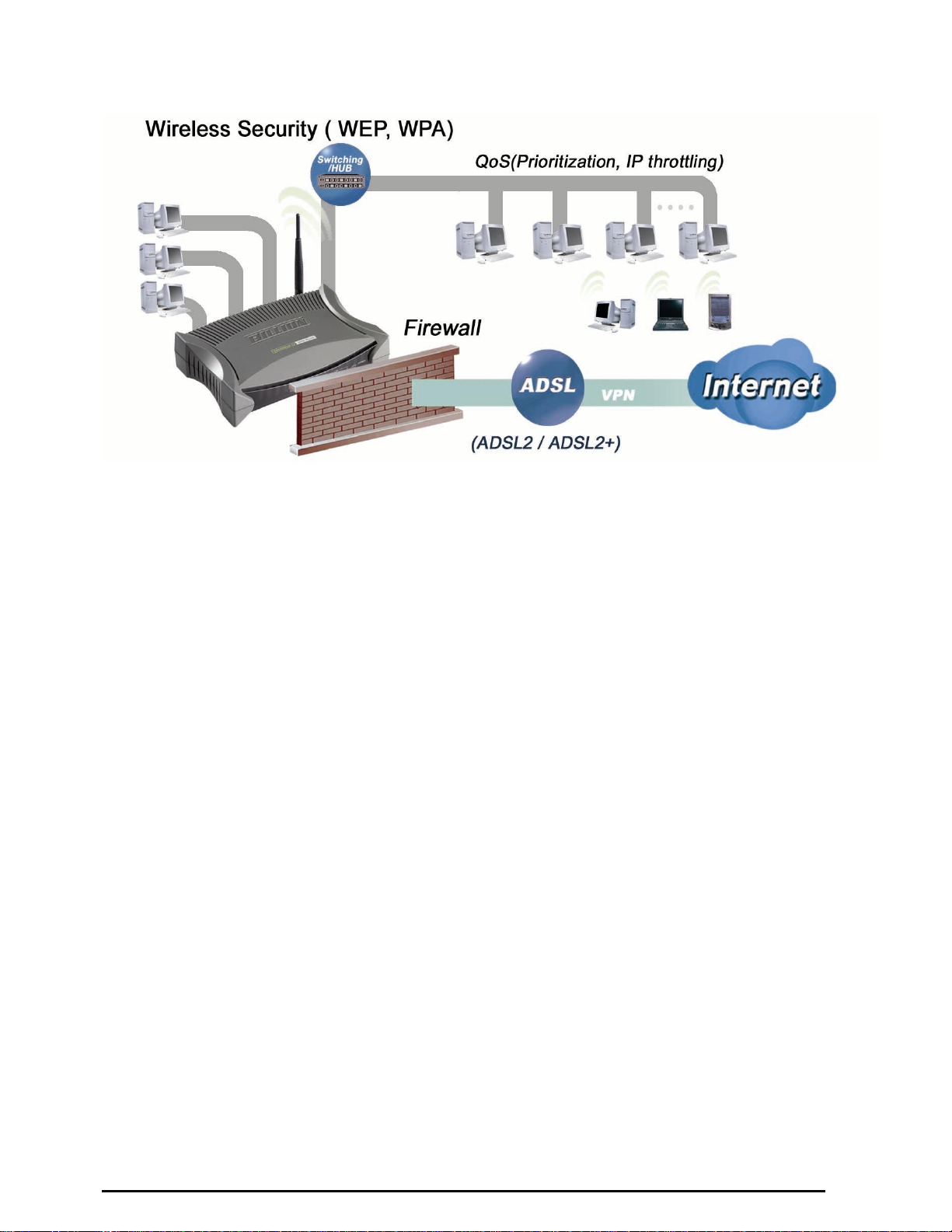
7402 ADSL Router Application
Figure 1.1 Application Diagram of 7402
Thank you for your purchase, and welcome to the world o f bro adband In tern et!
4
A
Chapter 2: Installing the Router
Important note for using the 7402 ADSL2+ Router
Warning
ttention
Package Contents
․ BEC 7402 ADSL2+ Triple Play Router
DO NOT use the 7402 in high humidity or high temperatures.
DO NOT use the same power source for the 7402 as other
equipment.
DO NOT open or repair the case yourself. If the 7402 is too hot, turn
off the power immediately and have it repaired at a qualified service
center.
Avoid using this product and all accessories outdoors.
Place the 7402 on a stable surface.
Only use the power adapter that comes with t he package. Using a
different voltage rating power adaptor may damage the router.
․ RJ-11 ADSL/telephone Cable
․ Ethernet (CAT-5 LAN) Cable
․ AC-DC power adapter (12V DC, 1A)
․ External Antenna (Wireless Router Only)
5
The Front LEDs
LAN
LED Meaning
1 PPP / MAIL
2 ADSL
LAN Port
3
1X — 4X
(RJ-45 connector)
PWR
SYS
WLAN
1 2
4
3
ADSL
PPP/MAIL
Lit steady when there is a PPPoA / PPPoE connection.
Lit and flashed periodically when there is email in the Inbox.
When lit, it indicates that the ADSL (Line) port is connected to the
DSLAM and working properly.
Lit when the LAN link is connected to an Ethernet device.
Green for 100Mbps; Orange for 10Mbps.
Blinking when data is Transmitted / Received.
4
WLAN
Lit green when the wireless connection is established.
Flashes when sending/receiving data.
5 SYS Lit when the system is ready.
6 PWR Lit when power is ON.
6
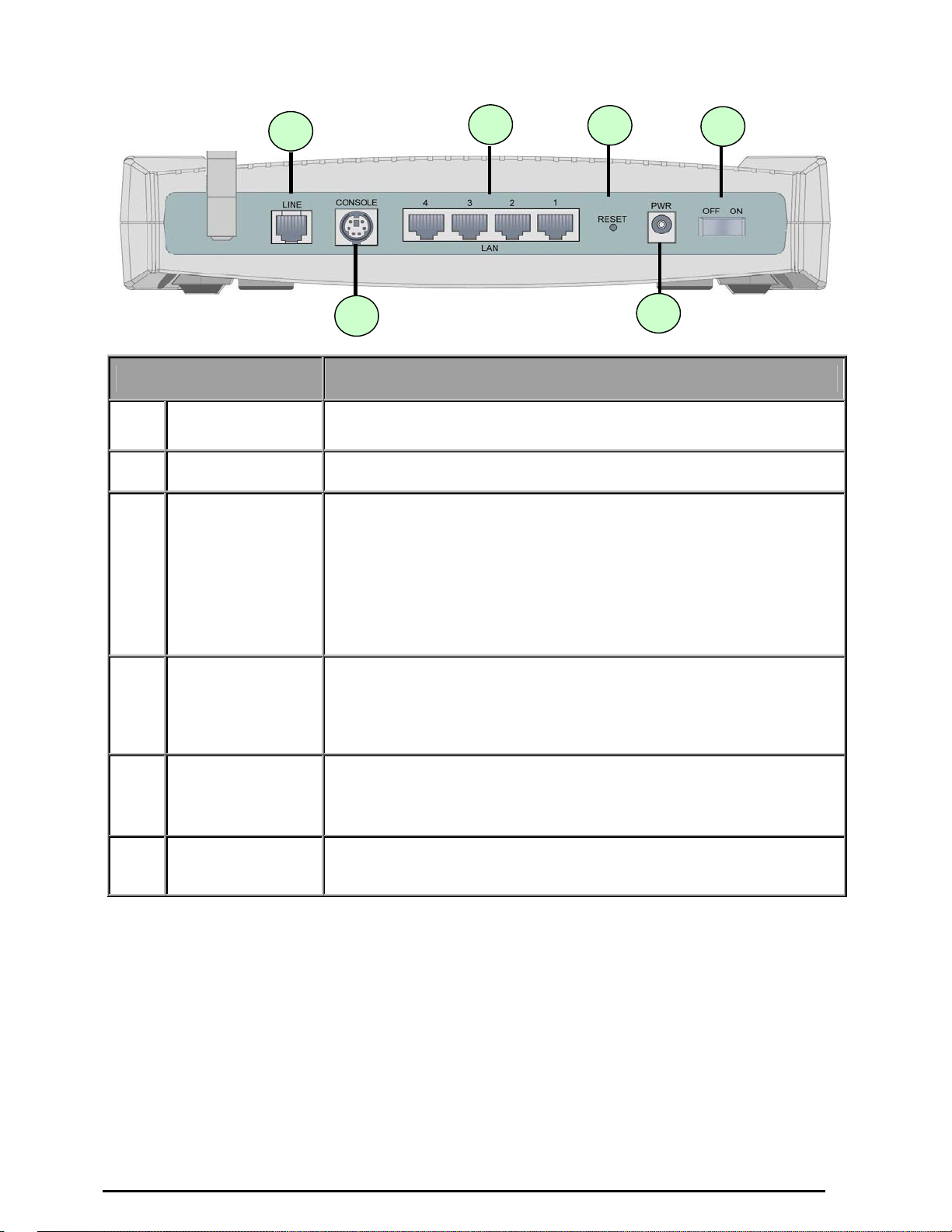
The Rear Ports
6
4
3
1
Port Meaning
Power Switch
1
PWR
2
3 RESET
LAN
4
1X — 4X
(RJ-45 connector)
5
2
Power ON/OFF switch
Connect the supplied power adapter to this jack.
After the device is powered on, press it to reset the device or restore to
factory default settings.
0-3 seconds: reset the device
6 seconds above: restore to factory default settings (this is used when
you cannot login to the router. E.g.: forgot the password)
Connect a UTP Ethernet cable (Cat-5 or Cat-5e) to one of the four
LAN ports when connecting to a PC or an office/home network of
10Mbps or 100Mbps.
5
6
CONSOLE
LINE
Connect a PS2/RS-232 cable to this port when connecting to a PC’s
RS-232 port (9-pin serial port).
Connect the supplied RJ-11 (“telephone”) cable to this port when
connecting to the ADSL/telephone network.
7

Cabling
The most common problem associated with Ethernet is bad cabling or ADSL line(s). Make sure that all
connected devices are turned on. On the front of the product is a bank of LEDs. Verify that the LAN Link
and ADSL line LEDs are lit. If they are not, verify that you are using the proper cables.
Ensure that all other devices connected to the same telephone line as your BEC router (e.g. telephones,
fax machines, analogue modems) have a line filter connected between them and the wall socket (unless
you are using a Central Splitter or Central Filter installed by a qualified and licensed electrician), and
ensure that all line filters are correctly installed and the right way around.
Missing line filters or line filters installed the wrong way around can cause problems with your ADSL
connection, including causing frequent disconnections.
8
Chapter 3: Basic Installation
7402 can be configured with your web browser. The web browser is included as a standard application
in the following operating systems: Linux, Mac OS, Windows 98/NT/2000/XP/Me, etc. The product
provides a very easy and user-friendly interface for configuration.
PCs must have an Ethernet interface installed properly and be connected to 7402 either directly or
through an external repeater hub, and have TCP/IP installed and configured to obtain an IP address
through a DHCP server or a fixed IP address that must be in the same subnet as 7402. The default IP
address of the router is 192.168.1.254 and the subnet mask is 255.255.255.0 (i.e. any attached PC must
be in the same subnet, and have an IP address in the range of 192.168.1.1 to 192.168.1.253). The best
and easiest way is to configure the PC to get an IP address automatically from 7402 using DHCP. If you
encounter any problems accessing the router’s web interface it may also be advisable to uninstall any
kind of software firewall on your PCs, as they can cause problems accessing the 192.168.1.254 IP
address of the router. Users should make their own decisions on how to best protect their network.
Please follow the steps below for your PC’s network environment installation. Before taking the first step,
please check your PC’s network components. The TCP/IP protocol stack and Ethernet network adapter
must be installed. If not, please refer to your Windows-related or other operating system manuals.
Any TCP/IP capable workstation can be used to communicate with or
through the 7402. To configure other types of workstations, please
consult the manufacturer’s documentation.
Connecting your router
1. Connect the router to a LAN (Local Area Network) and the ADSL/telephone network.
2. Power on the device.
3. Make sure the PWR and SYS LEDs are lit steadily and that the relevant LAN LED is lit.
The WLAN LED will be lit steadily.
9
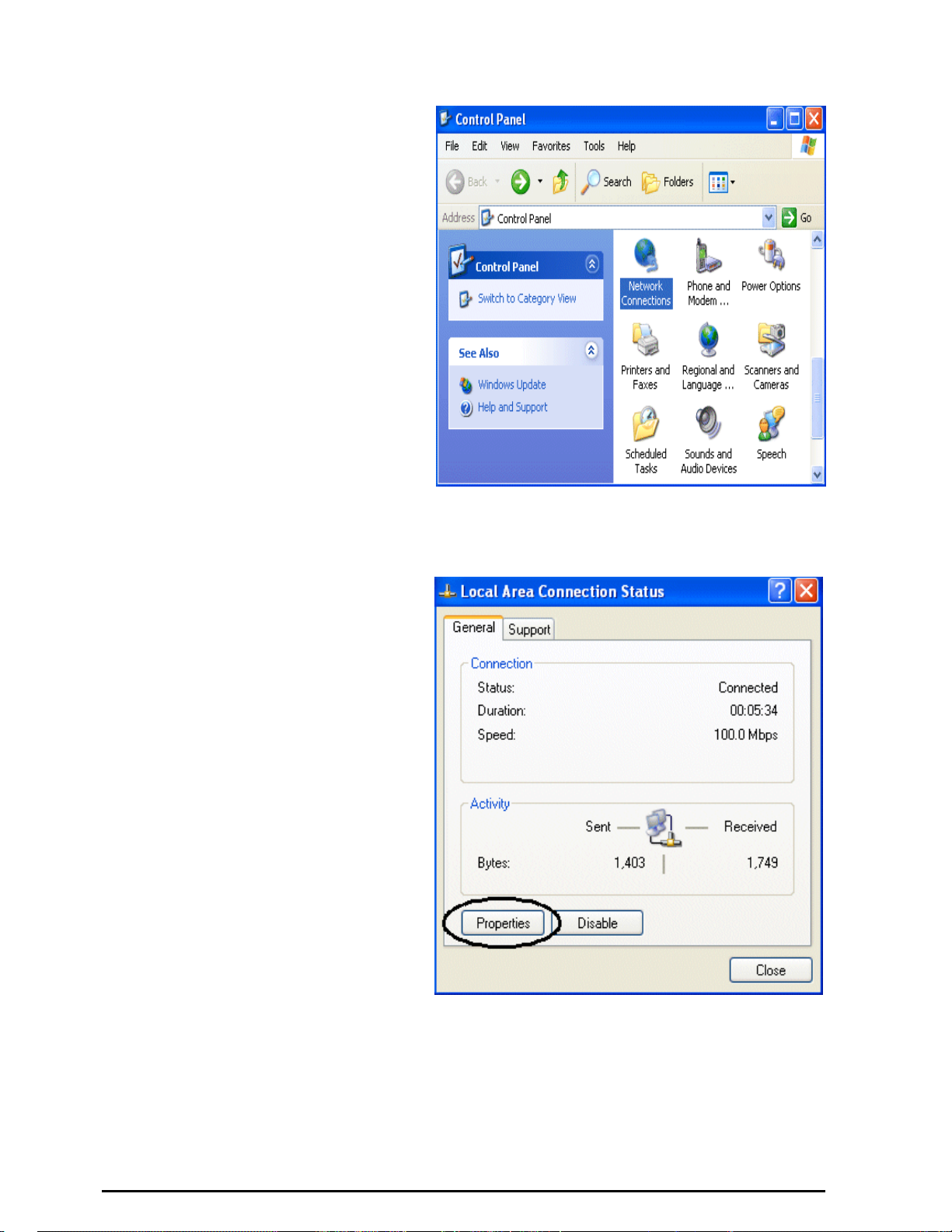
Configuring PC in Windows XP
1. Go to Start / Control Panel (in
Classic View). In the Control
Panel, double-click on Network
Connections.
2. Double-click Local Area
Connection. (See Fi gur e 3. 1)
3. In the Local Area Connection
Status window, click Properties.
(See Figure 3.2)
Figure 3.1: LAN Area Connection
Figure 3.2: LAN Connection Status
10
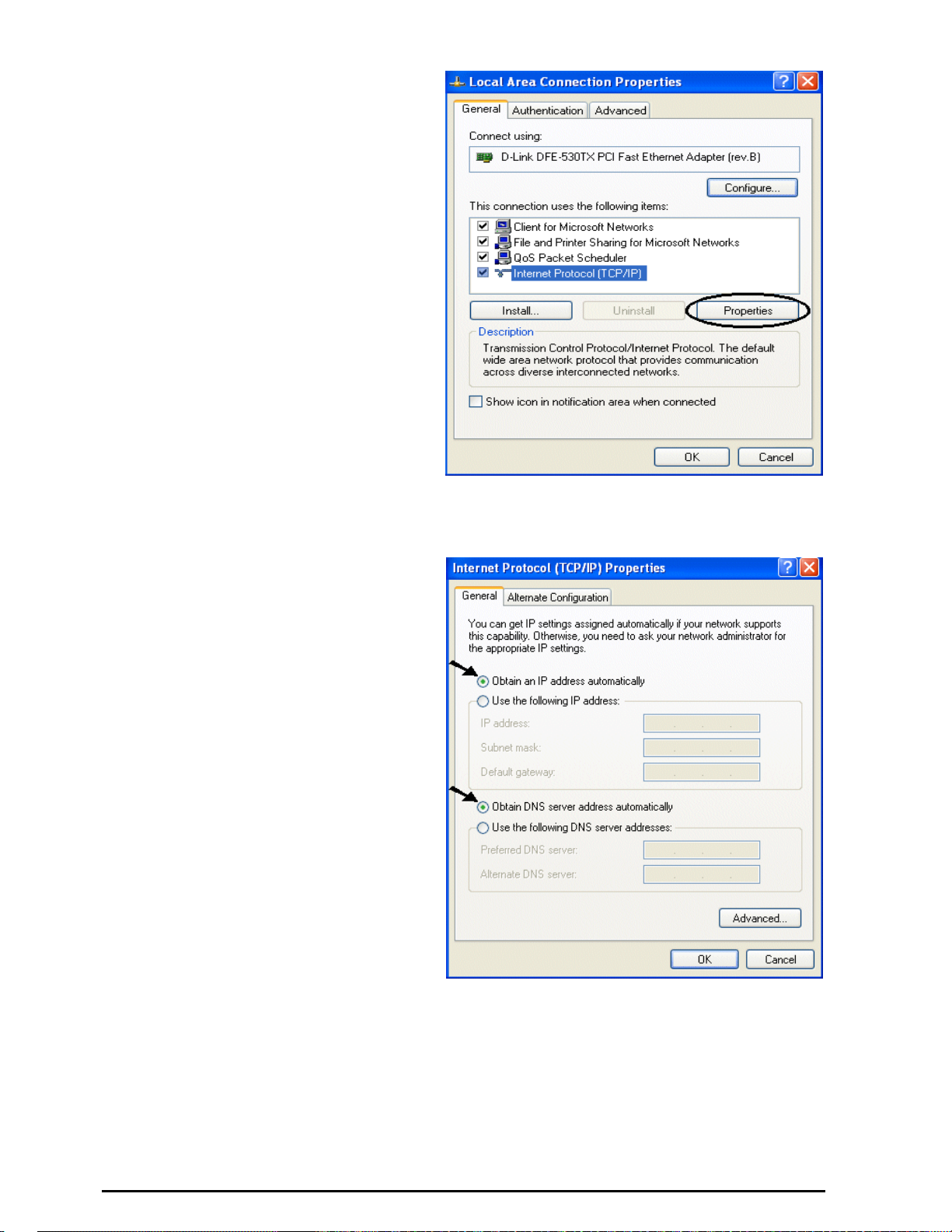
4. Select Internet Protocol (TCP/IP)
and click Properties.
(See Figure 3.3)
Figure 3.3: TCP / IP
5. Select the Obtain an IP address
automatically and the Obtain
DNS server address
automatically radio buttons.
(See Figure 3.4)
6. Click OK to finish the
configuration.
Figure 3.4: IP Address & D NS Configuration
11
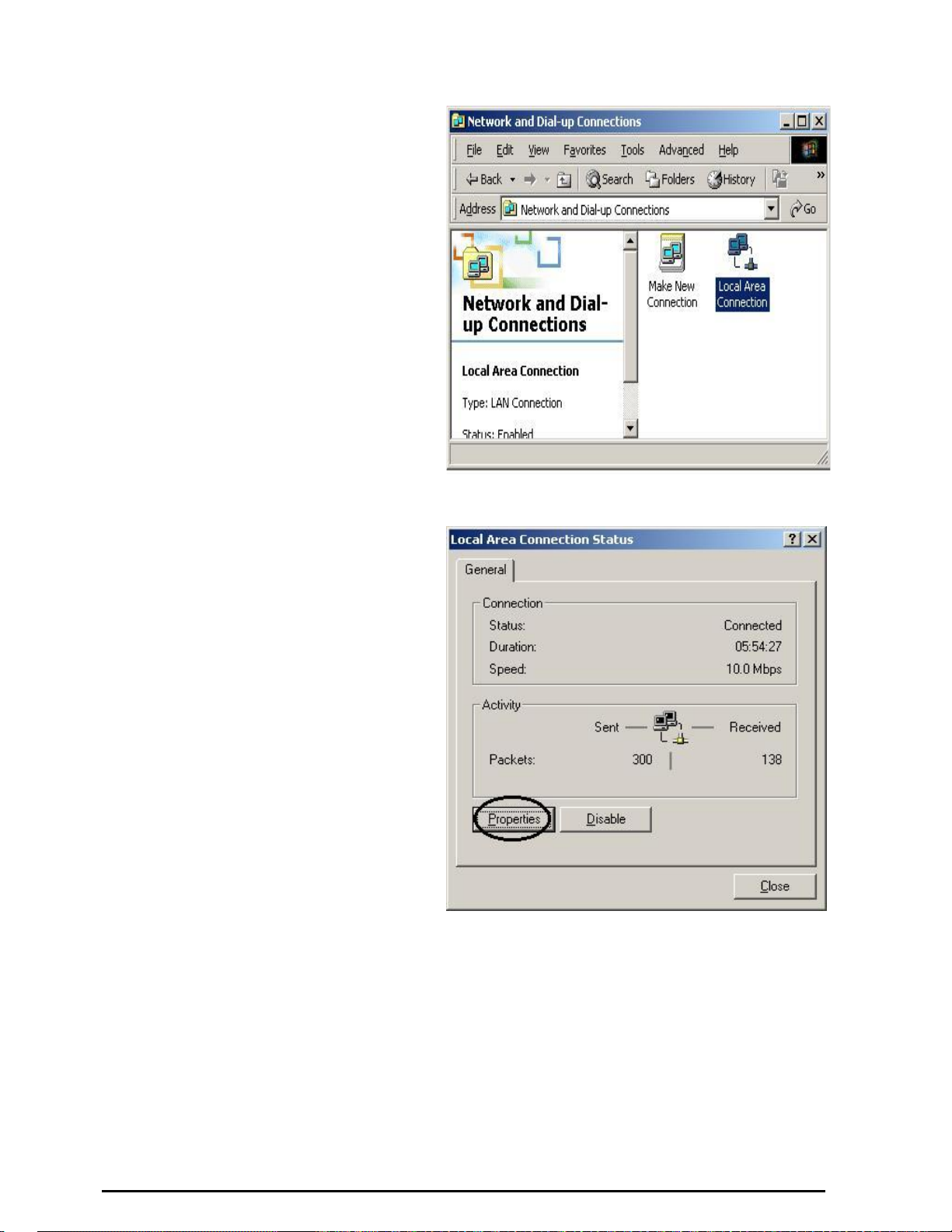
Configuring PC in Windows 2000
1. Go to Start / Settings / Control
Panel. In the Control Panel,
double-click on Network and
Dial-up Connections.
2. Double-click Local Area
Connection. (See Fi gure 3.5)
3. In the Local Area Connection
Figure 3.5: LAN Area Connection
Status window, click Properties.
(See Figure 3.6)
Figure 3.6: LAN Connection Status
12
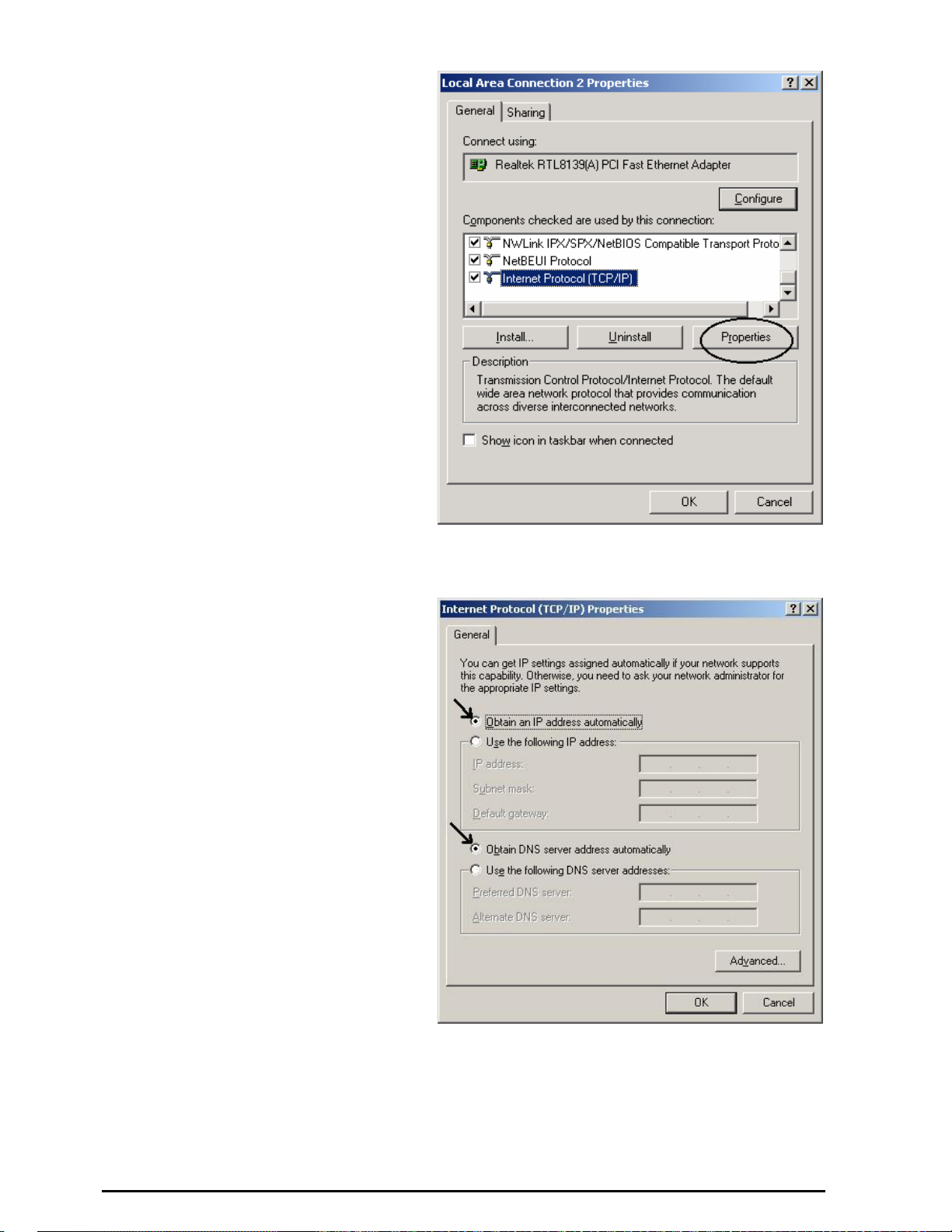
4. Select Internet Protocol
(TCP/IP) and click Properties.
(See Figure 3.7)
Figure 3.7: TCP / IP
5. Select the Obtain an IP address
automatically and the Obtain
DNS server address
automatically radio buttons.
(See Figure 3.8)
6. Click OK to finish the
configuration.
Figure 3.8: IP Address & D NS Configuration
13
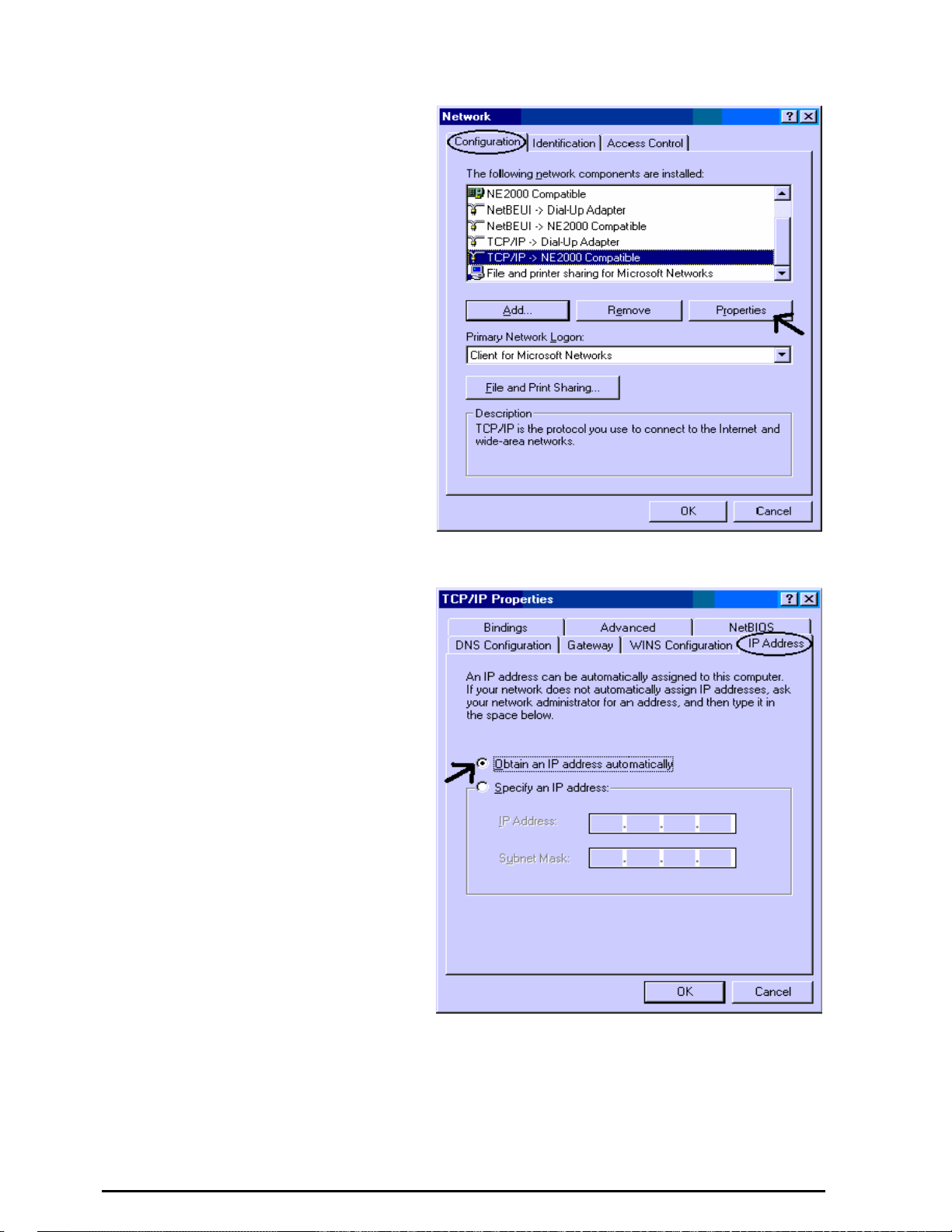
Configuring PC in Windows 95/98/ME
1. Go to Start / Settings / Control
Panel. In the Control Panel, double-
click on Network and choose the
Configuration tab.
2. Select TCP / IP -> NE2000
Compatible, or the name of your
Network Interface Card (NIC) in your
PC.
(See Figure 3.9)
3. Click Properties.
4. Select the IP Address tab. In this
page, click the Obtain an IP
address automatical ly radio button.
Figure 3.9: TCP / IP
(See Figure 3.10)
Figure 3.10: IP Address
14

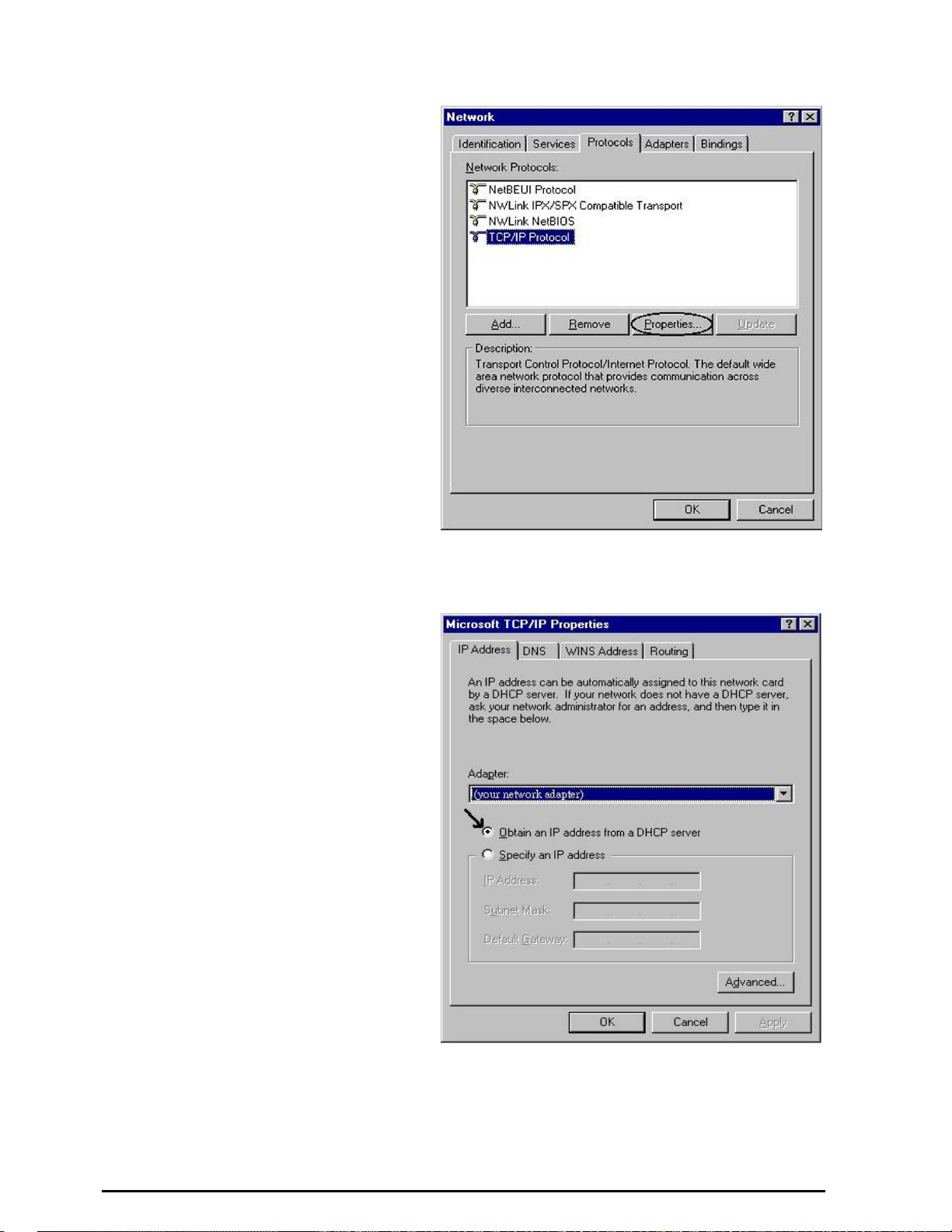
5. Then select the DNS Configurat ion
(See Figure 3.11)
tab.
6. Select the Disable DNS radio button
and click OK to finish the
configuration.
Figure 3.11: DNS Confi g uration
15
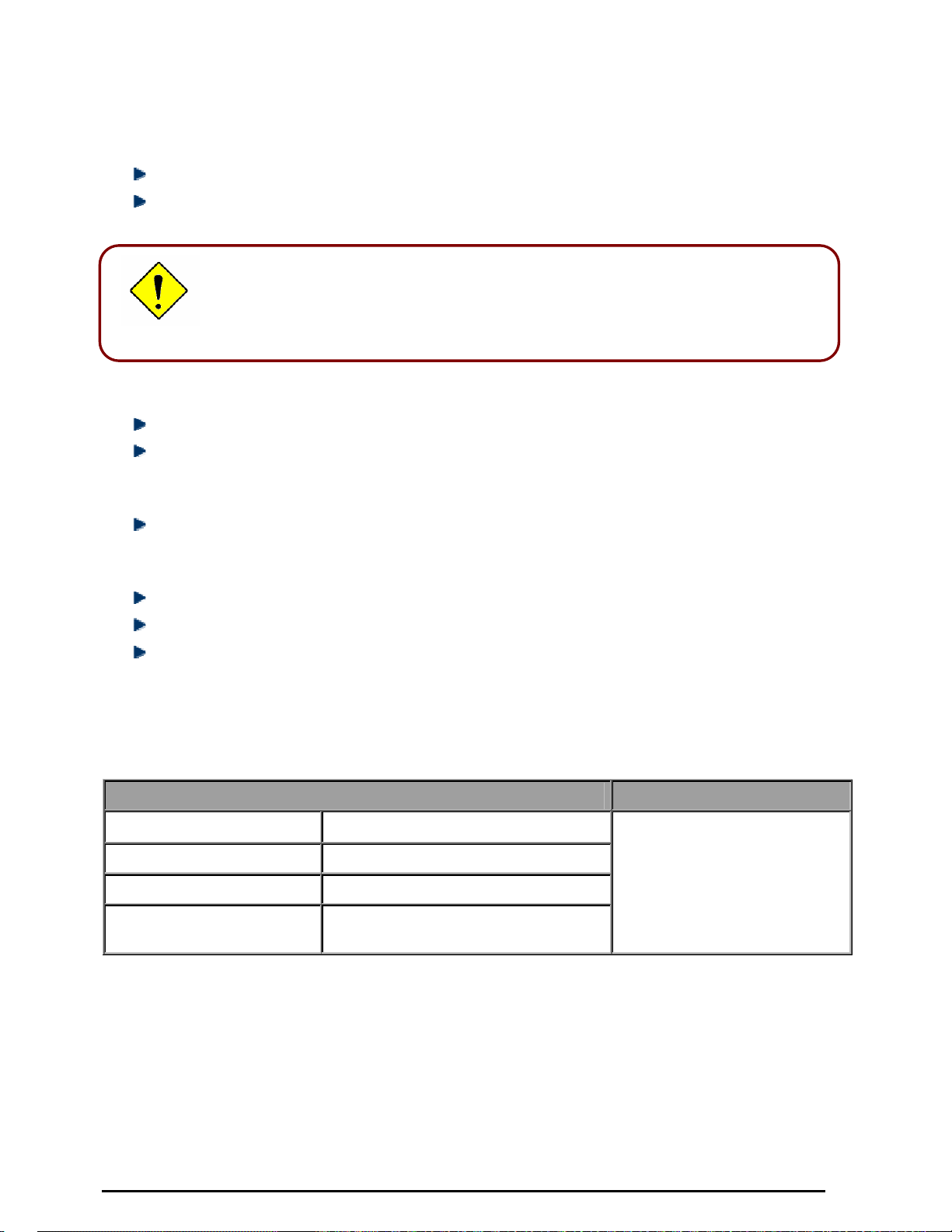
Configuring PC in Windows NT4.0
1. Go to Start / Settings / Control
Panel. In the Control Panel, double-
click on Network and choose the
Protocols tab.
2. Select TCP/IP Pr otocol and click
Properties.
3. Select the Obtain an IP address
from a DHCP serve r radio button
and click OK.
(See Figure 3.12)
Figure 3.12: TCP / IP
(See Figure 3.13)
Figure 3.13: IP Address
16
Factory Default Settings
Before configuring your, you need to know the following default settings.
Web Interface (Username and Password)
Username: admin
Password: admin
The default username and password are “admin” and “admin” respectively.
LAN Device IP Settings
IP Address: 192.168.1.254
Subnet Mask: 255.255.255.0
ISP setting in WAN site
PPPoE
If you ever forget the password to log in, you may press the RESET button up to
6 seconds to restore the factory default settings.
DHCP server
DHCP server is enabled.
Start IP Address: 192.168.1.100
IP pool counts: 100
LAN and WAN Port Addresses
The parameters of LAN and WAN ports are pre-set in the factory. The default values are shown below.
LAN Port WAN Port
IP address 192.168.1.254
Subnet Mask 255.255.255.0
DHCP server function Enabled
IP addresses for
distribution to PCs
100 IP addresses continuing from
192.168.1.100 through 192.168.1.199
The PPPoE function is enabled
to automatically get the WAN
port configuration from the ISP,
but you have to set the
username and password first.
17
Information from your ISP
Before configuring this device, you have to check with your ISP (Internet Service Provider) what kind of
service is provided such as PPPoE, PPPoA, RFC1483, or IPoA.
Gather the information as illustrated in the following table and keep it for reference
VPI/VCI, VC-based/LLC-based multiplexing, Username, Password, Service
PPPoE
PPPoA
RFC1483 Bridged VPI/VCI, VC-based/LLC-based multiplexing to use Bridged Mode.
RFC1483 Routed
Name, and Domain Name System (DNS) IP address (it can be automatically
assigned by your ISP when you connect or be set manually).
VPI/VCI, VC-based/LLC-based multiplexing, Username, Password, and
Domain Name System (DNS) IP address (it can be automatically assigned by
your ISP when you connect or be set manually).
VPI/VCI, VC-based/LLC-based multiplexing, IP address, Subnet mask,
Gateway address, and Domain Name System (DNS) IP address (it is fixed IP
address).
VPI/VCI, VC-based/LLC-based multiplexing, IP address, Subnet mask,
.
IPoA
Gateway address, and Domain Name System (DNS) IP address (it is fixed IP
address).
18
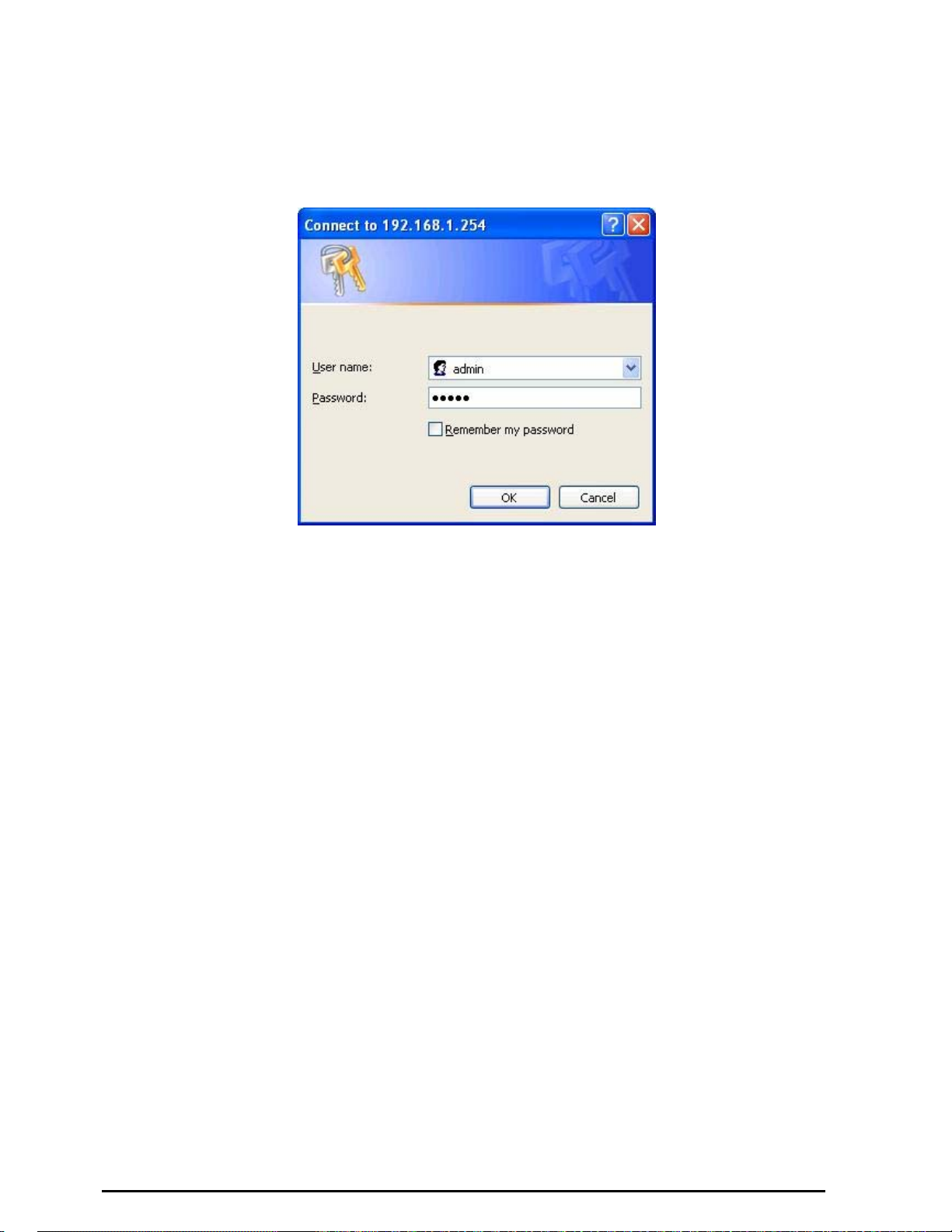
Configuring with your Web Browser
Open your web browser, enter the IP address of your router, which by default is 192.168.1.254, and click
“Go”, a user name and password window prompt will appear. The default username and password
are “admin” and “admin”. (See Figure 3.14)
Figure 3.14: User name & Password Prompt Widonw
Congratulation! You are now successfull y logon to the 7402 ADSL Router!
19
Chapter 4: Configuration
At the configuration homepage, the left navigation pane where bookmarks are provided links you directly
to the desired setup page, including:
Status (ARP Table, Wireless Association Table, Routing Table, DHCP Table, PPTP Status,
IPSec Status, L2TP Status, Email Status, Event Log, Error Log, NAT Sessions and UPnP
Portmap)
Quick Start
Configuration
(LAN, WAN, System, Firewall, VPN, QoS, Virtual Server, Time Schedule and Advanced)
Save Config to FLASH
Language (provides user interface in English and Deutsch languages)
Please see the relevant sections of this manual for detailed instructions on how to configure 7402 ADSL
Router.
20
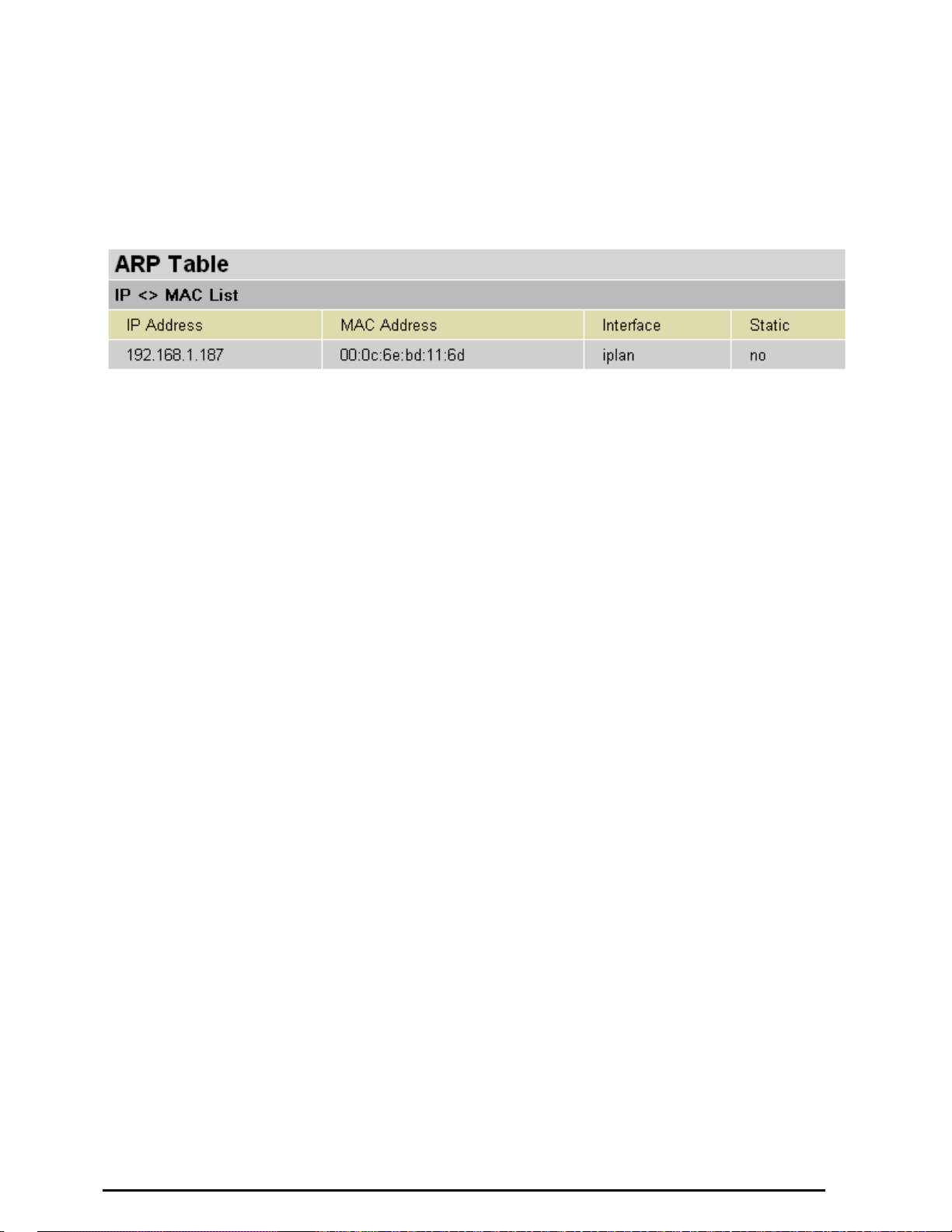
Status
ARP Table
This section displays the router’s ARP (Address Resolution Protocol) Table, which shows the mapping
of Internet (IP) addresses to Ethernet (MAC) addresses. This is useful as a quick way of determining the
MAC address of the network interface of your PCs to use with the router’s Firewall – MAC Address
Filter function. See the Firewall section of this manual for more information on this feature.
IP Address: A list of IP addresses of devices on your LAN (Local Area Network).
MAC Address: The MAC (Media Access Control) addresses for each device on your LAN.
Interface: The interface name (on the router) that this IP Address connects to.
Static: Static status of the ARP table entry:
“no” for dynamically-generated ARP table entries
“yes” for static ARP table entries added by the user
21
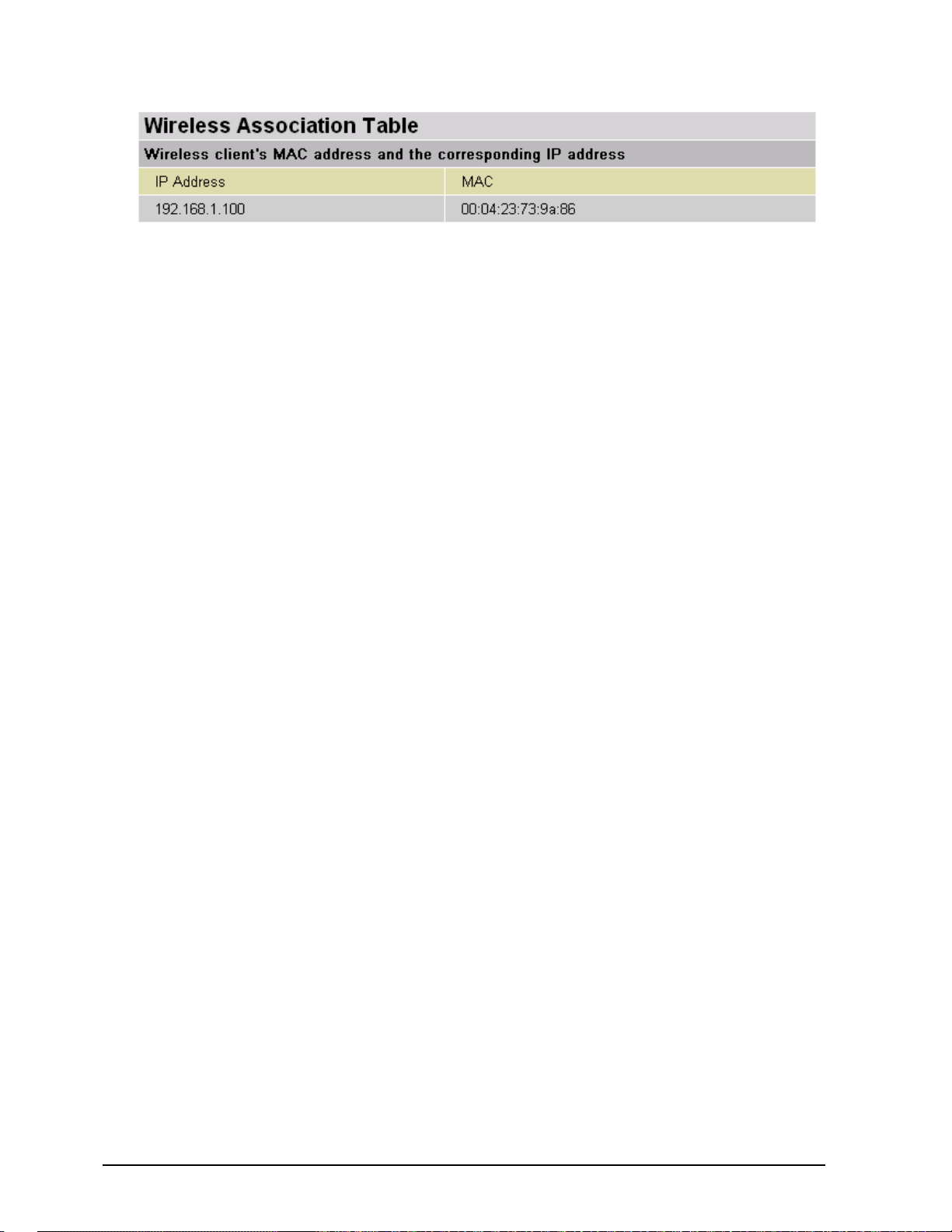
Wireless Association Table (Wireless Router Only)
IP Address: It is IP address of wireless client that joins this network.
MAC: The MAC address of wireless client
.
Chapter 4: Configuration
22
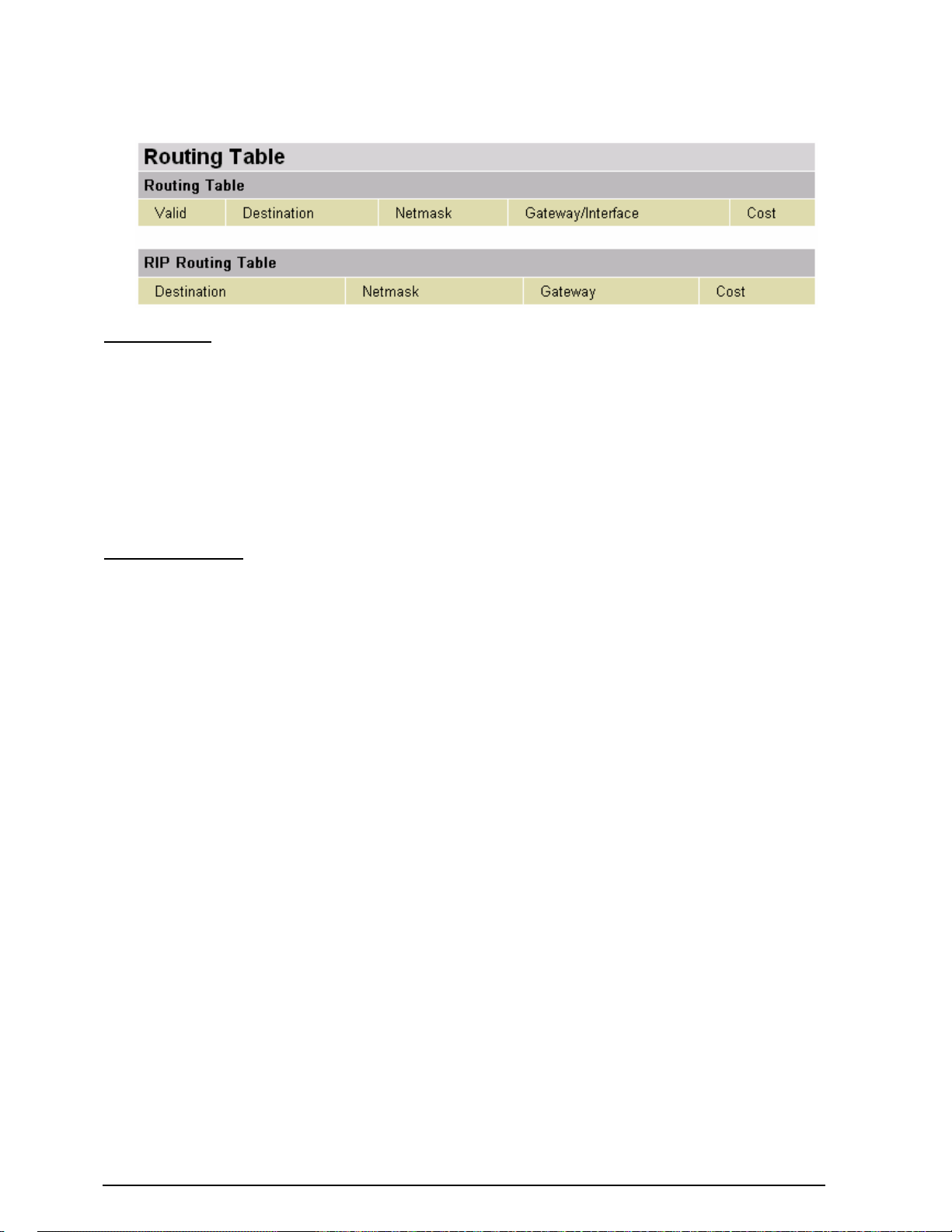
Routing Table
Routing Table
Valid: It indicates a successful routing status.
Destination: The IP address of the destination network.
Netmask: The destination netmask address.
Gateway/Interface: The IP address of the gateway or existing interface that this route will use.
Cost: The number of hops counted as the cost of the route.
RIP Routing Table
Destination: The IP address of the destination network.
Netmask: The destination netmask address.
Gateway: The IP address of the gateway that this route will use.
Cost: The number of hops counted as the cost of the route.
Chapter 4: Configuration
23
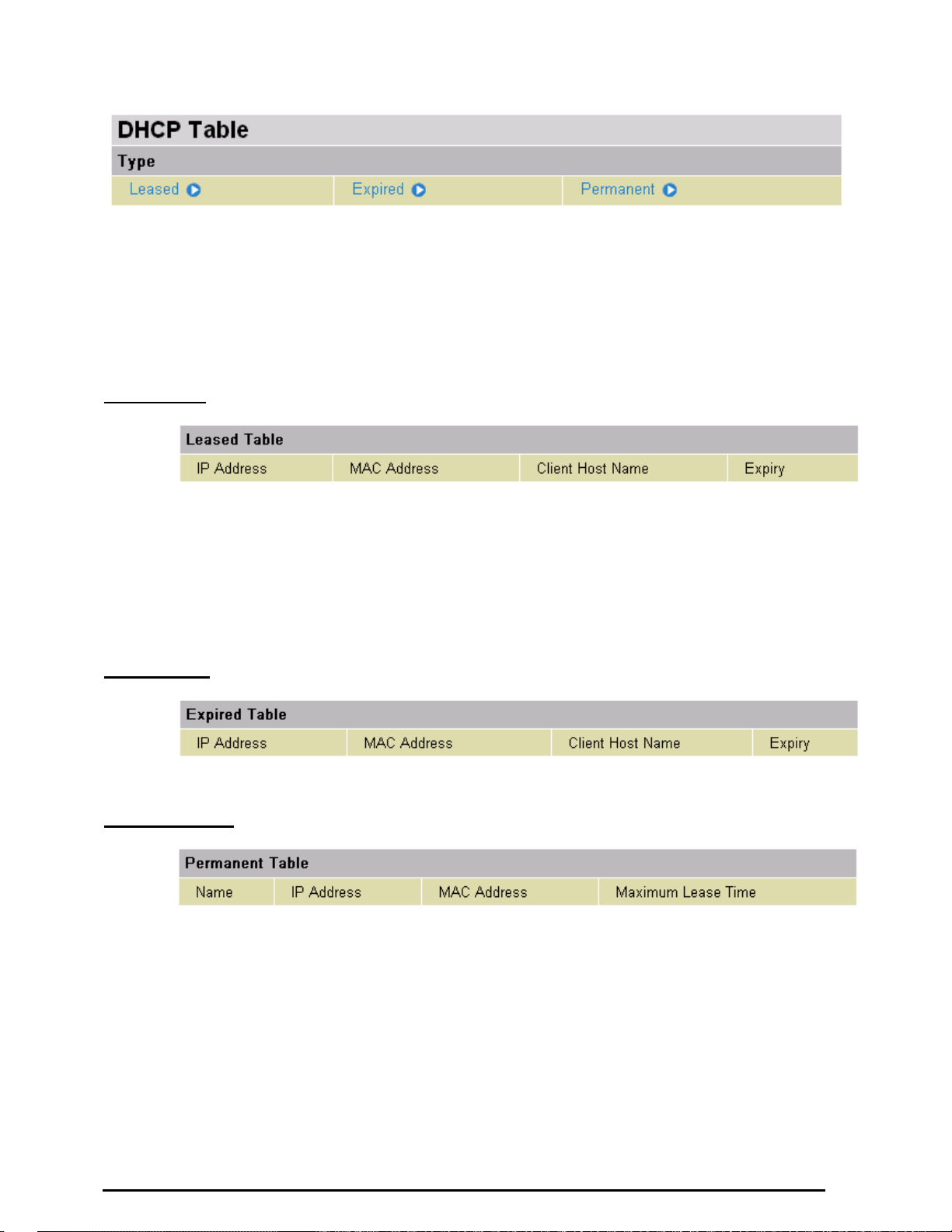
DHCP Table
Leased: The DHCP assigned IP addresses information.
IP Address: A list of IP addresses of devices on your LAN (Local Area Network).
Expired: The expired IP addresses information.
Permanent: The fixed host mapping information
Leased Table
IP Address: The IP address that assigned to client.
MAC Address: The MAC address of client.
Client Host Name: The Host Name (Computer Name) of client.
Expiry: The current lease time of client.
Expired Table
Please refer the Leased T able.
Permanent Tabl e
Name: The name you assigned to the Permanent configuration.
IP Address: The fixed IP address for the specify client.
MAC Address: The MAC Address that you want to assign the fixed IP address
Maximum Lease Time: The maximum lease time interval you allow to clients
24
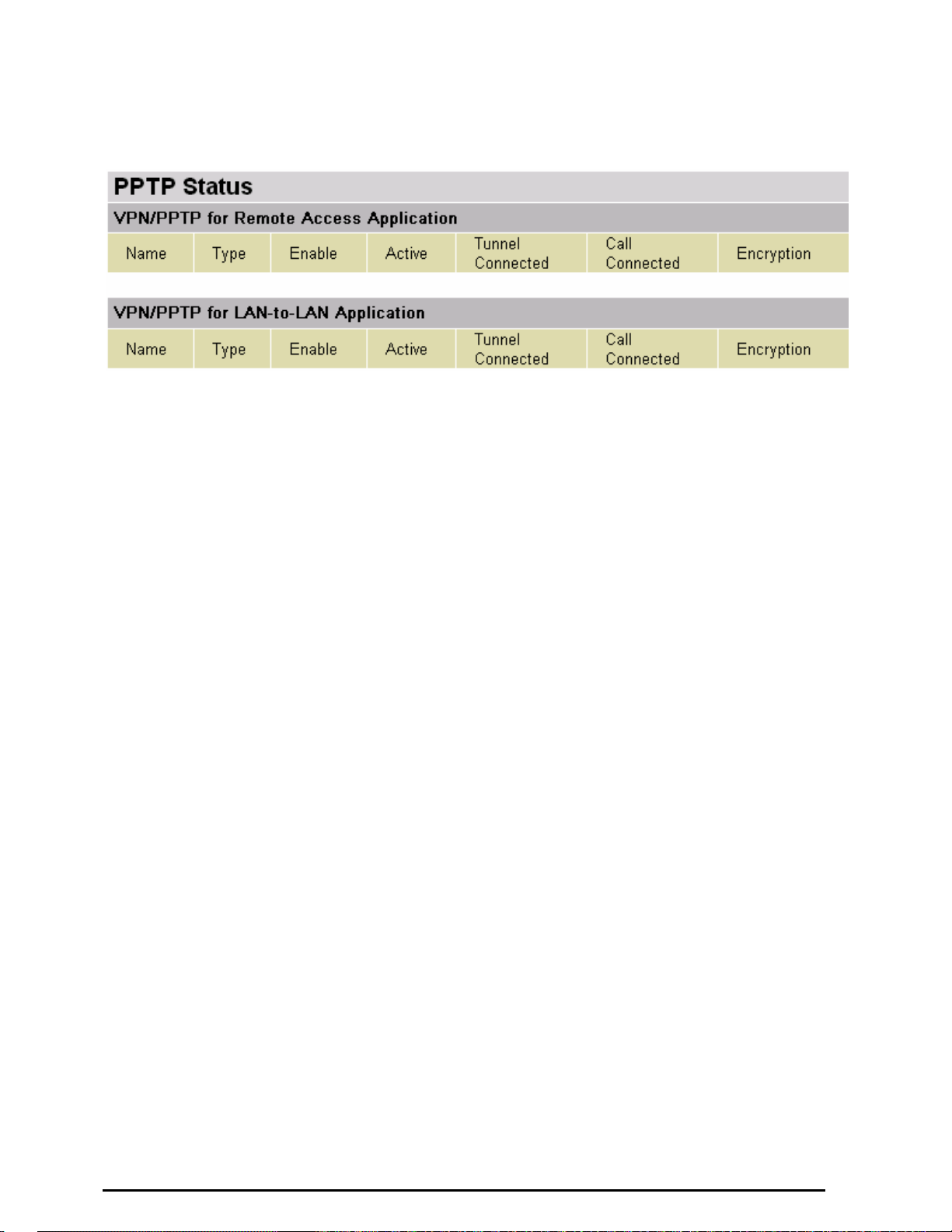
PPTP Status (VPN Router Only)
This shows details of your configured PPTP VPN Connections.
Name: The name you assigned to the particular PPTP connection in your VPN configuration.
Type: The type of connection (dial-in/dial-out).
Enable: Whether the connection is currently enabled.
Active: Whether the connection is currently active.
Tunnel Connected: Whether the VPN Tunnel is currently connected.
Call Connected: If the Call for this VPN entry is currently connected.
Encryption: The encryption type used for this VPN connection.
25
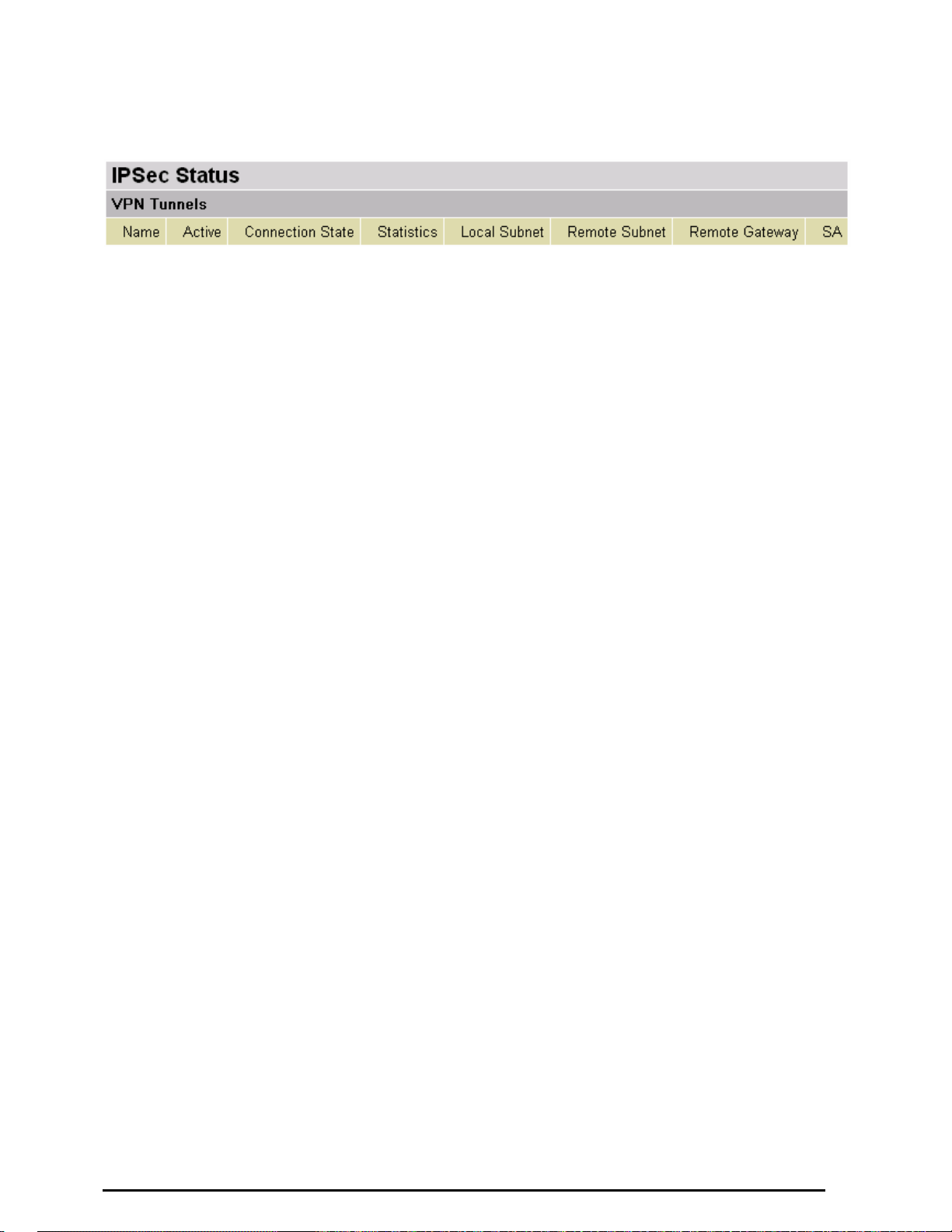
IPSec Status (VPN Router Only)
This shows details of your configured IPSec VPN Connections.
Name: The name you assigned to the particular VPN entry.
Active: Whether the VPN Connection is currently Active.
Connection State: Whether the VPN is Connected or Disconnected.
Statistics: Statistics for this VPN Connection.
Local Subnet: The local IP Address or Subnet used.
Remote Subnet: The Subnet of the remote site.
Remote Gateway: The Remote Gateway IP address.
SA: The Security Association for this VPN entry.
26

L2TP Status (VPN Router Only)
This shows details of your configured L2TP VPN Connections.
Name: The name you assigned to the particular L2TP connection in your VPN configuration.
Type: The type of connection (dial-in/dial-out).
Enable: Whether the connection is currently enabled.
Active: Whether the connection is currently active.
Tunnel Connected: Whether the VPN Tunnel is currently connected.
Call Connected: If the Call for this VPN entry is currently connected.
Encryption: The encryption type used for this VPN connection.
Email Status
Details and status for the Email Account you have configured the router to check. Please see the
Advanced section of this manual for details on this function.
27

Event Log
This page displays the router’s Event Log entries. Major events are logged to this window, such as when
the router’s ADSL connection is disconnected, as well as Firewall events when you have enabled
Intrusion or Blocking Logging in the Configuration – Firewall section of the interface. Please see the
Firewall section of this manual for more details on how to enable Firewall logging.
Error Log
Any errors encountered by the router (e.g. invalid names given to entries) are logged to this window.
28

NAT Sessions
This section lists all current NAT sessions between interface of types external (WAN) and internal (LAN).
UPnP Portmap
The section lists all port-mapping established using UPnP (Universal Plug and Play). Please see the
Advanced section of this manual for more details on UPnP and the router’s UPnP configuration options.
29

Quick Start
For detailed instructions on configuring your WAN settings, please see the WAN section of this manual.
Usually, the only details you will need for the Quick Start wizard to get you online are your login (often in
the form of u sername@ispname), your password and the encapsulation type. In additional, you have
the option to provide specific DNS as your desire, or check the Enable box to get the DNS automatically
from your ISP.
Your ISP will be able to supply all the details you need, alternatively, if you have deleted the current
WAN Connection in the WAN – ISP section of the interface, you can use the router’s PVC Scan feature
to attempt to determine the Encapsulation types offered by your ISP.
Click Start to begin scanning for encapsulation types offered by your ISP. If the scan is successful you
will then be presented with a list of supported options:
30

Select the desired option from the list and click Apply to return to the Quick Start interface to continue
configuring your ISP connection. Please note that the contents of this list will vary, depending on what is
supported by your ISP.
31

Configuration
When you click this item, you get following sub-items to configure the ADSL router.
LAN, WAN, System, Firewall, VPN, QoS, Virtual Server, Time Schedule and Advanced
These functions are described below in the following sections.
LAN (Local Area Network)
There are seven items within the LAN section: Ethernet, Ethernet Client Filter, Wireless, Wireless
Security, Wireless Client Filter, Port Setting and DHCP Server.
Ethernet
The router supports two Ethernet IP addresses in the LAN, and two different LAN subnets through
which you can access the Internet at the same time. Users usually only have one subnet in their
LAN, so there is no need to configure a Secondary IP address. The default IP address for the
router is 192.168.1.254.
RIP: RIP v1, RIP v2, and RIP v2 Multicast. Check to enable RIP function.
32

Ethernet Client Filter
The Ethernet Client Filter supports up to 16 Ethernet network machines that helps you to manage
your network control to accept traffic from specific authorized machines or can restrict unwanted
machine(s) to access your LAN.
There are no pre-define Ethernet MAC address filter rules; you can add the filter rules to meet your
requirements.
Ethernet Client Filter: Default setting is set to Disable.
Allowed: check to authorize specific device accessing your LAN by insert the MAC
Address in the space provided or click
Blocked: check to prevent unwanted device accessing your LAN by insert the MAC
Address in the space provided or click
The maximum client is 16. The MAC addresses are 6 bytes long; they are presented only in
hexadecimal characters. The number 0 - 9 and letters a - f are acceptable.
(Note: Follow the MAC Address Format xx:xx:xx:xx:xx:xx. Semicolon ( : ) must be included)
Candidates: automatically detects devices connected to the router through the Ethernet. .
→ Active PC in LAN
. Make sure your PC’s MAC is listed.
. Make sure your PC’s MAC is not listed.
33

Active PC in LAN displays a list of individual Ethernet device’s IP Address & MAC Address which
connecting to the router.
You can easily by checking the box next to the IP address to be blocked or allowed. Then, Add to
insert to the Ethernet Client Filter table. The maximum Ethernet client is 16.
34

Wireless (Wireless Rou ter Onl y )
Parameters
WLAN Service: Default setting is set to Enable. If you do not have any wireless, both 802.11g
and 802.11b, device in your network, select Disable.
Mode: The default setting is 802.11b+g (Mixed mode). If you do not know or have both 11g and
11b devices in your network, then keep the default in mixed mode. From the drop-down manual,
you can select 802.11g if you have only 11g card. If you have only 11b card, then select 802.11b.
ESSID: The ESSID is the unique name of a wireless access point (AP) to be distinguished from
another. For security propose, change the default wlan-ap to a unique ID name to the AP which is
already built-in to the router’s wireless interface. It is case sensitive and must not excess 32
characters. Make sure your wireless clients have exactly the ESSID as the device, in order to get
connected to your network. (Note: It is case sensitive and must not excess 32 characters.)
ESSID Broadcast: It is function in which transmits its ESSID to the air so that when wireless
client searches for a network, router can then be discovered and recognized. Default setting is
Enable.
Disable: If you do not want broadcast your ESSID. Any client uses “any” wireless setting
cannot discover the Access Point (AP) of your router.
Enable: Any client that using the “any” setting can discover the Access Point (AP) in
Regulation Domain: There are seven Regulation Domains for you to choose from, including
North America (N.America), Europe, France, etc. The Channel ID will be different based on this
setting.
Channel ID: Select the ID channel that you would like to use.
Connected: Representing in true or false. That it is the connection status between the system
and the build-in wireless card.
AP MAC Address: It is a unique hardware address of the Access Point.
AP Firmware Versio n: The Access Point firmware version.
35

Wireless Distribution System (WD S)
It is a wireless access point mode that enables wireless link and communication with other access point.
It is easy to be installed simply define peer’s MAC address of the connected AP. WDS takes
advantages of cost saving and flexibility which no extra wireless client device is required to bridge
between two access points and extending an existing wired or wireless infrastructure network to create a
larger network.
In addition, WDS enhances its link connection security in WEP mode, WEP key encryption must be the
same for both access points.
WDS Service: The default setting is Disable. Check Enable radio button to activate this function.
Peer WDS MAC Address: It is the associated AP’s MAC Address. It is important that your peer’s
AP must include your MAC address in order to acknowledge and communicate with each other.
(Note: For MAC Address, Semicolon ( : ) must be included)
36

Wireless Security (Wire less Router Only )
You can disable or enable with WPA or WEP for protecting wireless network.
The default mode of wireless security is disabled.
WPA Pre-Shared Key
WPA Algorithms: TKIP (Temporal Key Integrity Protocol) utilizes a stronger encryption method
and incorporates Message Integrity Code (MIC) to provide protection against hackers.
WPA Shared Key: The key for network authentication. The input format is in character style and
key size should be in the range between 8 and 63 characters.
Group Key Renewal: The period of renewal time for changing the security key automatically
between wireless client and Access Point (AP). Default value is 600 seconds.
Idle Timeout: The default idle timeout is 3600 seconds. A Timeout value base on the case of no
data traffic is send or received. If Router detects no traffic in the wireless, it will start timing the
clock and drop the session as it reaches to the defined timeout value. New session will be reestablished after the old session.
37

WEP
WEP Encryption: To prevent unauthorized wireless stations from accessing data transmitted over
the network, the router offers highly secure data encryption, known as WEP. If you require high
security for transmissions, there are two alternatives to select from: WEP 64 and WEP 128. WEP
128 will offer increased security over WEP 64.
Passphrase: This is used to generate WEP keys automatically based upon the input string and a
pre-defined algorithm in WEP64 or WEP128. You can input the same string in both the AP and
Client card settings to generate the same WEP keys. Please note that you do not have to enter
Key (0-3) as below when the Passphrase is enabled.
Default Used WEP Key: Select the encryption key ID; please refer to Key (0-3) below.
Key (0-3): Enter the key to encrypt wireless data. To allow encrypted data transmission, the WEP
Encryption Key values on all wireless stations must be the same as the router. There are four keys
for your selection. The input format is in HEX style, 5 and 13 HEX codes are required for WEP64
and WEP128 respectively, the separator is “-“. For example, using WEP64, 11-22-33-44-55 is a
valid key, whilst 1122334455 is invalid.
38

Wireless Client (MAC A ddress) F il ter (Wirel ess Router Onl y )
The MAC Address supports up to 16 wireless network machines and helps you to manage your
network control to accept traffic from specific authorized machines or to restrict unwanted
machine(s) to access your LAN.
There are no pre-define MAC Address filter rules; you can add the filter rules to meet your
requirements.
Ethernet Client Filter: Default setting is set to Disable.
Allowed: check to authorize specific device accessing your LAN by insert the MAC
Address in the space provided or click
Blocked: check to prevent unwanted device accessing the LAN by insert the MAC Address
in the space provided or click
The maximum client is 16. The MAC addresses are 6 bytes long; they are presented only in
hexadecimal characters. The number 0 - 9 and letters a - f are acceptable.
The maximum client is 16. The MAC addresses are 6 bytes long; they are presented only in
hexadecimal characters. The number 0 - 9 and letters a - f are acceptable.
(Note: Follow the MAC Address Format xx:xx:xx:xx:xx:xx. Semicolon ( : ) must be included)
Candidates: it automatically detects devices connected to the router through the Ethernet. .
→Associated Wireless Clients
. Make sure your PC’s MAC is not listed.
. Make sure your PC’s MAC is listed.
39

Associate Wireless Client displays a list of individual wireless device’s MAC Address that currently
connects to the router.
You can easily by checking the box next to the MAC address to be blocked or allowed. Then, Add
to insert to the Wireless Client (MAC Address) Filter table. The maximum Ethernet client is 16.
40

DHCP Server
You can disable or enable the DHCP (Dynamic Host Configuration Protocol) server or enable the
router’s DHCP relay functions. The DHCP protocol allows your router to dynamically assign IP
addresses to PCs on your network if they are configured to obtain IP addresses automatically.
To disable the router’s DHCP Server, check Disabled and click Next, then click Apply . When the
DHCP Server is disabled you will need to manually assign a fixed IP address to each PCs on your
network, and set the default gateway for each PCs to the IP address of the router (by default this is
192.168.1.254).
To configure the router’s DHCP Server, check DHCP Server and click Next. You can then
configure parameters of the DHCP Server including the IP pool (starting IP address and ending IP
address to be allocated to PCs on your network), lease time for each assigned IP address (the
period of time the IP address assigned will be valid), DNS IP address and the gateway IP address.
These details are sent to the DHCP client (i.e. your PC) when it requests an IP address from the
DHCP server. Click Apply to enable this function. If you check “Use Router as a DNS Server”,
the ADSL Router will perform the domain name lookup, find the IP address from the outside
network automatically and forward it back to the requesting PC in the LAN (your Local Area
Network).
If you check DHCP R elay Agent and click Next, then you will have to enter the IP address of the
DHCP server which will assign an IP address back to the DHCP client in the LAN. Use this
function only if advised to do so by your network administrator or ISP.
Click Apply to enable this function.
41

Chapte
WAN (Wide Area Network)
WAN refers to your Wide Area Network connection, i.e. your router’s connection to your ISP and the
Internet. There are two items within the WAN section: ISP, DNS and ADSL.
ISP
The factory default is PPPoE. If your ISP uses this access protocol, click Edit to input other
parameters as below. If your ISP does not use PPPoE, you can change the default WAN
connection entry by clicking Change.
A simpler alternative is to select Quick Start from the main menu on the left. Please see the Quick
Start section of the manual for more information.
r 4: Configuration
42

RFC 1483 Routed Connections
Description: Your description of this connection.
VPI and VCI: Enter the information provided by your ISP.
ATM Class: The Quality of Service for ATM layer.
NAT: The NAT (Network Address Translation) feature allows multiple users to access the Internet
through a single IP account, sharing the single IP address. If users on your LAN have public IP
addresses and can access the Internet directly, the NAT function can be disabled.
Encapsulation method: Selects the encapsulation format, the default is LLC Bridged. Select the
one provided by your ISP.
DHCP clien t: Enable or disable the DHCP client, specify if the Router can get an IP address from
the Internet Service Provider (ISP) automatically or not. Please click Obtain an IP address
automatically via DHCP client to enable the DHCP client function or click Specify an IP address
to disable the DHCP client function, and specify the IP address manually. Your ISP specifies the
setting of this item.
RIP: RIP v1, RIP v2, and RIP v2 Multicast. Check to enable RIP function.
MTU: Maximum Transmission Unit. The size of the largest datagram (excluding media-specific
headers) that IP will attempt to send through the interface.
Chapter 4: Configuration
43

RFC 1483 Bridged Connections
VPI and VCI: Enter the information provided by your ISP.
ATM Class: The Quality of Service for ATM layer.
Encapsulation method: Select the encapsulation format, this is provided by your ISP.
Ether Filter Type: Specify the type of ethernet filtering performed by the named bridge interface.
All Allows all types of ethernet packets through the port.
Ip Allows only IP/ARP types of ethernet packets through the port.
Pppoe Allows only PPPoE types of ethernet packets through the port.
Spanning Bridge I nterf ace: Enable/Disable spanning tree function of modem.
Chapter 4:Configuration
44

PPPoA Routed Connections
Description: User-definable name for the connection.
VPI/VCI: Enter the information provided by your ISP.
ATM Class: The Quality of Service for ATM layer.
NAT: The NAT (Network Address Translation) feature allows multiple users to access the Internet
through a single IP account, sharing a single IP address. If users on your LAN have public IP
addresses and can access the Internet directly, the NAT function can be disabled.
Username: Enter the username provided by your ISP. You can input up to 128 alphanumeric
characters (case sensitive). This will usually be in the format of “username@ispname” instead of
simply “username”.
Password: Enter the password provided by your ISP. You can input up to 128 alphanumeric
characters (case sensitive).
IP Address: Specify an IP address allowed to logon and access the router’s web server.. Note: IP
0.0.0.0 indicates all users who are connected to this router are allowed to logon the device and
modify data.
Authent icatio n Prot ocol T ype: Default is Chap (Auto). Your ISP will advise you whether to use
Chap or Pap.
Chapter 4:Configuration
45

Connection:
Always on: If you want the router to establish a PPPoA session when starting up and to
automatically re-establish the PPPoA session when disconnected by the ISP.
Connect to Demand: If you want to establish a PPPoA session only when there is a
packet requesting access to the Internet (i.e. when a program on your computer attempts to
access the Internet).
Idle Timeout: Auto-disconnect the broadband firewall gateway when there is no activity on the
line for a predetermined period of time.
Detail: You can define the destination port and packet type (TCP/UDP) without checking by
timer. It allows you to set which outgoing traffic will not trigger and reset the idle timer.
RIP: RIP v1, RIP v2, and RIP v2 Multicast. Check to enable RIP function.
MTU: Maximum Transmission Unit. The size of the largest datagram (excluding media-specific
headers) that IP will attempt to send through the interface.
Advanced Options (PPPoA)
LLC Header: Selects encapsulation mode, true for using LLC or false for using VC-Mux.
Create Route: This setting specifies whether a route is added to the system after IPCP (Internet
Protocol Control Protocol) negotiation is completed. If set to enabled, a route will be created which
directs packets to the remote end of the PPP link.
Specific Route: Specifies whether the route created when a PPP link comes up is a specific or
default route. If set to enabled, the route created will only apply to packets for the subnet at the
remote end of the PPP link. The address of this subnet is obtained during IPCP negotiation.
Subnet Mask: sets the subnet mask used for the local IP interface connected to the PPP transport.
If the value 0.0.0.0 is supplied, the netmask will be calculated from the class of the IP address
obtained during IPCP negotiation.
Route Mask: Sets the subnet mask used by the route that is created when a PPP link comes up. If
it is set to 0.0.0.0, the subnet mask is determined by the IP address of the remote end of the link.
The class of the IP address is obtained during IPCP (Internet Protocol Control Protocol)
negotiation.
MRU: Maximum Receive Unit. This is negotiated during the LCP protocol stage.
Discover Primary / Secondary DNS: This setting enables/disables whether the
primary/secondary DNS server address is requested from a remote PPP peer using IPCP. The
default setting for this command is enabled.
Give DNSto Relay: Controls whether the PPP Internet Protocol Control Protocol (IPCP) can
request the DNS server IP address for a remote PPP peer. Once IPCP has discovered the DNS
server IP address, it automatically gives the address to the local DNS relay so that a connection
can be established.
Give DNSto Client: Controls whether the PPP Internet Protocol Control Protocol (IPCP) can
request a DNS server IP address for a remote PPP peer. Once IPCP has discovered the DNS
server IP address, it automatically gives the address to the local DNS client so that a connection
can be established.
Give DNSto DHCP Server: Similar to the above, but gives the DNS server address to the DHCP
server.
Chapter 4:Configuration
46

Discover Primary NBNS / Discover Secondary NBNS: This setting enables/disables whether
the primary/secondary NBNS server address is requested from a remote PPP peer using IPCP.
The default setting for this command is disabled.
Discover Subnet Mask: Specifies if the subnet mask given by IPCP negotiation process is to be
used.
Give Subnet Mask To DHCP Server: Enable to change your DHCP Server settings by using the
given information in IPCP negotiation process.
Chapter 4:Configuration
47

IPoA Routed Connections
Description: User-definable name for the connection.
VPI/VCI: Enter the information provided by your ISP.
ATM Class: The Quality of Service for ATM layer.
NAT: The NAT (Network Address Translation) feature allows multiple users to access the Internet
through a single IP account, sharing a single IP address. If users on your LAN have public IP
addresses and can access the Internet directly, the NAT function can be disabled.
DHCP clien t: Enable or disable the DHCP client, specifying if the router can obtain an IP address
from the Internet Service Provider (ISP) automatically or not. Please click Obtain an IP address
automatically via DHCP client to enable the DHCP client function or click Specify an IP address
to disable the DHCP client function, and specify the IP address manually. Your ISP specifies the
setting of this item.
RIP: RIP v1, RIP v2, and RIP v2 Multicast. Check to enable RIP function.
MTU: Maximum Transmission Unit. The size of the largest datagram (excluding media-specific
headers) that IP will attempt to send through the interface.
Chapter 4:Configuration
48

PPPoE Connections
Description: A user-definable name for this connection.
VPI/VCI: Enter the information provided by your ISP.
ATM Class: The Quality of Service for ATM layer.
NAT: The NAT (Network Address Translation) feature allows multiple users to access the Internet
through a single ISP account, sharing a single IP address. If users on your LAN have public IP
addresses and can access the Internet directly, the NAT function can be disabled.
Username: Enter the username provided by your ISP. You can input up to 128 alphanumeric
characters (case sensitive). This will usually be in the format of “username@ispname” instead of
simply “username”.
Password: Enter the password provided by your ISP. You can input up to 128 alphanumeric
characters (case sensitive).
Service Name: This item is for identification purposes. If it is required, your ISP will provide you
the information. Maximum input is 20 alphanumeric characters.
IP Address: specify if the Router can get an IP address from the Internet Server Provider (ISP)
automatically or not. Please click Obtain an IP address automatically via DHCP client to enable the
DHCP client function or click Specify an IP address to disable the DHCP client function, and
specify the IP address manually. The setting of this item is specified by your ISP.
Authent ication P rotocol: Default is Chap(Auto). Your ISP will advise you whether to use Chap
or Pap.
Chapter 4:Configuration
49

Connection:
Always on: If you want the router to establish a PPPoE session when starting up and to
automatically re-establish the PPPoE session when disconnected by the ISP.
Connect to Demand: If you want to establish a PPPoE session only when there is a
packet requesting access to the Internet (i.e. when a program on your computer attempts to
access the Internet).
Idle Timeout: Auto-disconnect the broadband firewall gateway when there is no activity on the line
for a predetermined period of time.
Detail: You can define the destination port and packet type (TCP/UDP) without checking by
timer. It allows you to set which outgoing traffic will not trigger and reset the idle timer.
RIP: RIP v1, RIP v2, and RIP v2 Multicast. Check to enable RIP function.
MTU: Maximum Transmission Unit. The size of the largest datagram (excluding media-specific
headers) that IP will attempt to send through the interface.
Advanced Options (PPPoE)
LLC Header: Selects encapsulation mode, true for using LLC or false for using VC-Mux.
Create Route: This setting specifies whether a route is added to the system after IPCP (Internet
Protocol Control Protocol) negotiation is completed. If set to enabled, a route will be created which
directs packets to the remote end of the PPP link.
Specific Route: Specifies whether the route created when a PPP link comes up is a specific or
default route. If set to enabled, the route created will only apply to packets for the subnet at the
remote end of the PPP link. The address of this subnet is obtained during IPCP negotiation.
Subnet Mask: sets the subnet mask used for the local IP interface connected to the PPP transport.
If the value 0.0.0.0 is supplied, the netmask will be calculated from the class of the IP address
obtained during IPCP negotiation.
Route Mask: Sets the subnet mask used by the route that is created when a PPP link comes up. If
it is set to 0.0.0.0, the subnet mask is determined by the IP address of the remote end of the link.
The class of the IP address is obtained during IPCP (Internet Protocol Control Protocol)
negotiation.
MRU: Maximum Receive Unit. This is negotiated during the LCP protocol stage.
Discover Primary / Secondary DNS: This setting enables/disables whether the
primary/secondary DNS server address is requested from a remote PPP peer using IPCP. The
default setting for this command is enabled.
Give DNS to Relay: Controls whether the PPP Internet Protocol Control Protocol (IPCP) can
request the DNS server IP address for a remote PPP peer. Once IPCP has discovered the DNS
server IP address, it automatically gives the address to the local DNS relay so that a connection
can be established.
Give DNS to Client: Controls whether the PPP Internet Protocol Control Protocol (IPCP) can
request a DNS server IP address for a remote PPP peer. Once IPCP has discovered the DNS
server IP address, it automatically gives the address to the local DNS client so that a connection
can be established.
Give DNS to DHCP Server: Similar to the above, but gives the DNS server address to the DHCP
server.
Chapter 4:Configuration
50

Discover Primary NBNS / Discover Secondary NBNS: This setting enables/disables whether
the primary/secondary NBNS server address is requested from a remote PPP peer using IPCP.
The default setting for this command is disabled.
Discover Subnet Mask: Specifies if the subnet mask given by IPCP negotiation process is to be
used.
Give Subnet Mask To DHCP Server: Enable to change your DHCP Server settings by using the
given information in IPCP negotiation process.
Chapter 4:Configuration
51

DNS
A Domain Name System (DNS) contains a mapping table for domain name and IP addresses. On
the Internet, every host has a unique and user-friendly name (domain name) such as
www.helloworld.com and an IP address. An IP address is a 32-bit number in the form of
xxx.xxx.xxx.xxx, for example 192.168.1.254. You can think of an IP address as a telephone
number for devices on the Internet, and the DNS will allow you to find the telephone number for
any particular domain name. As an IP Address is hard to remember, the DNS converts the friendly
name into its equivalent IP Address.
You can obtain a Domain Name System (DNS) IP address automatically if your ISP has provided it
when you logon, check the Enable box. Usually when you choose PPPoE or PPPoA as your WAN
- ISP protocol, the ISP will provide the DNS IP address automatically. You may leave the
configuration field blank.
Alternatively, your ISP may provide you with an IP address of their DNS. If this is the case, you
must enter the DNS IP address manually.
If you choose one of the other three protocols ─ RFC1483 Routed/Bridged and IPoA check with
your ISP, it may provide you with an IP address for their DNS server. You must enter the DNS IP
address if you set the DNS of your PC to the LAN IP address of this router.
Chapter 4:Configuration
52

ADSL
Connect Mode: The default setting is Multimode. This mode will automatically detect your ADSL
line code, G.dmt, G.lite, and T1.413. But in some area, multimode cannot detect the ADSL line
code well. If it is the case, please adjust the ADSL line code to G.dmt or T1.413 first. If it still fails,
please try the other values such as ALCTL, ADI, etc.
Activate Line: Aborting (false) your ADSL line and making it active (true) again for taking effect
with setting of Connect Mode.
Coding Gain: Configure the ADSL coding gain from 0 dB to 7dB, or automatic.
Tx Attenuation: Setting ADSL transmission gain, the value is between 0~12.
DSP Fi rmw are Ve rsi on : Current ADSL line code firmware version.
Connected: Display current ADSL line sync status.
Operational Mode: Display current ADSL mode standard (Operational Mode) your Router is using
when ADSL line has sync.
Annex Type: ADSL Annex A, which works over a standard telephone line. Annex B, which works
over an ISDN line.
Upstream: Display current upstream rate of your ADSL line.
Downstream: Display current downstream rate of your ADSL line.
Chapter 4:Configuration
53

System
There are six items within the System section: Time Zone, Remote Access, Firmware Upgrade,
Backup/Restore, Resta rt and User Management.
Time Zone
The router does not have a real time clock on board; instead, it uses the Simple Network Time
Protocol (SNTP) to get the current time from an SNTP server outside your network. Choose your
local time zone, click Enable and click the Apply button. After a successful connection to the
Internet, the router will retrieve the correct local time from the SNTP server you have specified. If
you prefer to specify an SNTP server other than those in the list, simply enter its IP address as
shown above. Your ISP may provide an SNTP server for you to use.
Daylight Saving is also known as Summer Time Period. Many places in the world adapt it during
summer time to move one hour of daylight from morning to the evening in local standard time.
Check Automatic box to auto set your local time.
Resync Period (in minutes) is the periodic interval the router will wait before it re-synchronizes the
router’s time with that of the specified SNTP server. In order to avoid unnecessarily increasing the
load on your specified SNTP server you should keep the poll interval as high as possible – at the
absolute minimum every few hours or even days.
Chapter 4:Configuration
54

Remote Access
To temporarily permit remote administration of the router (i.e. from outside your LAN), select a time
period the router will permit remote access for and click Enable. You may change other
configuration options for the web administration interface using Device Management options in
the Advanced section of the GUI.
If you wish to permanently enable remote access, choose a time period of 0 minutes. This setting
cannot be saved into flash when timer set to zero.
Chapter 4:Configuration
55

Firmware Upgrade
Your router’s “firmware” is the software that allows it to operate and provides all its functionality.
Think of your router as a dedicated computer, and the firmware as the software it runs. Over time
this software may be improved and modified, and your router allows you to upgrade the software it
runs to take advantage of these changes.
Clicking on Browse will allow you to select the new firmware image file you have downloaded to
your PC. Once the correct file is selected, click Upgrade to update the firmware in your router.
Warning
DO NOT power down the router or interrupt the firmware upgrading while it is
still in process. Improper operation could damage the router.
Chapter 4: Configuration
56

Backup / Restore
These functions allow you to save and backup your router’s current settings to a file on your PC, or
to restore a previously saved backup. This is useful if you wish to experiment with different settings,
knowing that you have a backup handy in the case of any mistakes. It is advisable to backup your
router’s settings before making any significant changes to your router’s configuration.
Press Backup to select where on your local PC to save the settings file. You may also change the
name of the file when saving if you wish to keep multiple backups.
Press Browse to select a file from your PC to restore. You should only restore settings files that
have been generated by the Backup function, and that were created when using the current
version of the router’s firmware. Settings files saved to your PC should not be manually
edited in any way.
After selecting the settings file you wish to use, pressing Restore will load those settings into the
router.
Chapter 4:Configuration
57

Restart Router
Click Restart with option Current Settings to reboot your router (and restore your last saved
configuration).
If you wish to restart the router using the factory default settings (for example, after a firmware
upgrade or if you have saved an incorrect configuration), select Factory Default Settings to reset
to factory default settings.
You may also reset your router to factory settings by holding the small Reset pinhole button on the
back of your router in for 10-12 seconds whilst the router is turned on.
Chapter 4: Configuration
58

User Management
In order to prevent unauthorized access to your router’s configuration interface, it requires all users
to login with a password. You can set up multiple user accounts, each with their own password.
You are able to Edit existing users and Create new users who are able to access the device’s
configuration interface. Once you have clicked on Edit, you are shown the following options:
You can change the user’s password, whether their account is active and Valid, as well as add a
comment to each user account. These options are the same when creating a user account, with
the exception that once created you cannot change the username. You cannot delete the default
admin account, however you can delete any other created accounts by clicking Delete when
editing the user.
You are strongly advised to change the password on the default “admin” account when you
receive your router, and any time you reset your configuration to Factory Defaults.
Chapter 4: Con f ig u rati on
59

Firewall and Access Contro l
Your router includes a full SPI (Stateful Packet Inspection) firewall for controlling Internet access from
your LAN, as well as helping to prevent attacks from hackers. In addition to this, when using NAT
(Network Address Translation. Please see the WAN configuration section for more details on NAT) the
router acts as a “natural” Internet firewall, as all PCs on your LAN will use private IP addresses that
cannot be directly accessed from the Internet.
Firewall: Prevents access from outside your network. The router provides three levels of security
support:
NAT natural firewall: This masks LAN users’ IP addresses which are invisible to outside users on the
Internet, making it much more difficult for a hacker to target a machine on your network. This natural
firewall is on when NAT function is enabled.
When using Virtual Servers your PCs will be exposed to the degree
specified in your Virtual Server settings provided the ports specified are
opened in your firewall packet filter settings.
Firewall Security and Policy (General Settings): Inbound direction of Packet Filter rules to prevent
unauthorized computers or applications accessing your local network from the Internet.
Intrusion Detection: Enable Intrusion Detection to detect, prevent and log malicious attacks.
Access Control: Prevents access from PCs on your local network:
Firewall Security and Policy (General Settings): Outbound direction of Packet Filter rules to prevent
unauthorized computers or applications accessing the Internet.
URL Filter: To block PCs on your local network from unwanted websites.
Chapter 4: Con f ig u rati on
60

You can find six items under the Firewall section: General Settings, Packet Filter, Intrusion
Detection, URL Filter and Firewall Log.
Chapter 4: Con f ig u rati on
61

General Settings
You can choose not to enable Firewall, to add all filter rules by yourself, or enable the Firewall
using preset filter rules and modify the port filter rules as required. The Packet Filter is used to filter
packets based-on Applications (Port) or IP addresses.
There are four options when you enable the Firewall, they are:
All blocked/User-defined: no pre-defined port or address filter rules by default, meaning that
all inbound (Internet to LAN) and outbound (LAN to Internet) packets will be blocked. Users
have to add their own filter rules for further access to the Internet.
High/Medium/Low security level: the predefined port filter rules for High, Medium and Low
security are displayed in Port Filters of Packet Filter.
Select either High, Medium or Low security level to enable the Firewall. The only difference
between these three security levels is the preset port filter rules in the Packet Filter. Firewall
functionality is the same for all levels; it is only the list of preset port filters that changes between
each setting. For more detailed on level of preset port filter information, refer to Table 1:
Predefined Port Filter.
If you choose of the preset security levels and then add custom filters, you may temporarily disable
the firewall and recover your custom filter settings by re-selecting the same security level.
The “Block WAN Request” is a stand-alone function and not relate to whether security enable or
disable. Mostly it is for preventing any scan tools from WAN site by hacker.
Any remote user who is attempting to perform this action may result in blocking
all the accesses to configure and manage of the device from the Internet.
Chapter 4: Con f ig u rati on
62

Packet Filter
This function is only available when the Firewall is enabled and one of these four security levels is
chosen (All blocked, High, Medium and Low). The predefined port filter rules in the Packet Filter
must modify accordingly to the level of Firewall, which is selected. See Table1: Predefined Port
Filter for more detailed information.
63
Chapter 4: Con f ig u rati on

Example: Predefined Port F il ters Rul es
The predefined port filter rules for High, Medium and Low security levels are listed. See Table 1.
(Note: Firewall – All Blocked/User-defined, you must define and create the port filter rules
yourself. No predefined rule is set)
Table 1: Predefined Port Filter
Port Number Firewall - High Firewall - Medium Firewall – Low
Application Protocol
Start End Inbound Outbound Inbound Outbound Inbound Outbound
HTTP(80) TCP(6) 80 80 NO YES NO YES NO YES
DNS (53) UDP(17) 53 53 NO YES NO YES YES YES
DNS (53) TCP(6) 53 53 NO YES NO YES YES YES
FTP(21) TCP(6) 21 21 NO NO NO YES NO YES
Telnet(23) TCP(6) 23 23 NO NO NO YES NO YES
SMTP(25) TCP(6) 25 25 NO YES NO YES NO YES
POP3(110) TCP(6) 110 110 NO YES NO YES NO YES
NEWS(119) TCP(6) 119 119 NO NO NO YES NO YES
RealAudio
(7070)
UDP(17)
7070 7070 NO NO YES YES YES YES
PING ICMP(1) N/A N/A NO YES NO YES NO YES
H.323(1720) TCP(6) 1720 1720 NO NO NO YES YES YES
T.120(1503) TCP(6) 1503 1503 NO NO NO YES YES YES
SSH(22) TCP(6) 22 22 NO NO NO YES YES YES
NTP(123) UDP(17) 123 123 NO YES NO YES NO YES
HTTPS(443) TCP(6) 443 443 NO NO NO YES NO YES
ICQ (5190) TCP(6) 5190 5190 NO NO NO NO YES YES
Inbound: Internet to LAN
Outbound: LAN to Internet.
Chapter 4: Con f ig u rati on
64

Packet Filter – Add TCP/UDP Filter
Rule Name: A user-defined name for identifying the application.
Time Schedule: It is self-defined time period. You may specify a time schedule for your
prioritization policy. For setup and detail, refer to Time Schedule section
Source IP Address(es) / Destination IP Address(es): This is the Address-Filter used to allow or
block traffic to/from particular IP address(es). Selecting the Subnet Mask of the IP address range
you wish to allow/block the traffic to or form; set IP address and Subnet Mask to 0.0.0.0 to inactive
the Address-Filter rule.
Tip: To block access,. to/from a single IP address, enter that IP address as the Host IP Address
and use a Host Subnet Mask of “255.255.255.255”.
Type: It is the packet protocol type used by the application, select either TCP or UDP.
Source Port: This Port or Port Ranges defines the port allowed to be used by the Remote/WAN to
connect to the application. Default is set from range 0 ~ 65535. It is recommended that this option
be configured by an advanced user.
Destination Port: This is the Port or Port Ranges that defines the application.
Inbound / Outbound: Select Allow or Block the access to the Internet (“Outbound”) or from the
Internet (“Inbound”).
Click Apply button to apply your changes.
Chapter 4: Con f ig u rati on
65

Packet Filter – Add Raw IP Filter
Rule Name: A user-defined name for identifying the rule.
Time Schedule: It is self-defined time period. You may specify a time schedule for your
prioritization policy. For setup and detail, refer to Time Schedule section
Protocol Number: Insert the port number, i.e. GRE 47.
Inbound / Outbound: Select Allow or Block the access to the Internet (“Outbound”) or from the
Internet (“Inbound”).
Click Apply button to apply your changes.
Chapter 4: Con f ig u rati on
66

Example: Configuring yo ur fire wall to allow for a publicly accessible web server on your LAN
The predefined port filter rule for HTTP (TCP port 80) is the same no matter whether the firewall is set to
a high, medium or low security level. To setup a web server located on the local network when the
firewall is enabled, you have to configure the Port Filters setting for HTTP.
As you can see from the diagram below, when the firewall is enabled with one of the three presets
(Low/Medium/High), inbound HTTP access is not allowed which means remote access through HTTP to
your router is not allowed.
(Note: Inbound indicates accessing from Internet to LAN and Outbound is from LAN to the Internet)
Chapter 4: Con f ig u rati on
67

Configuring Packet Fi lter :
1. Click Port Filters. You will then be presented with the predefined port filter rules screen (in this
case for the low security level), shown below:
Note: You may click Edit the predefined rule instead of Delete it. This is an example to show to
how you add a filter on your own.
Click Delete
2. Click Delete to delete the existing HTTP rule.
3. Click Add TCP/UDP Filter.
4. Input the Rule Name, Time Schedule, Source/Destination IP, Type, Source/Destination Port,
Inbound and Outbound.
Example:
Application: Cindy_HTTP
Time Schedule: Always O n
Source / Destination IP Address(es): 0.0.0.0 (I do not wish to active the address-filter, instead I
use the port-filter)
Type: TCP (Please refer t o T able1: Predefined Port F ilter)
Source Port: 0-65535 (I allow all ports to connect with the application))
Redirect Port: 80-80 (This is Port defined for HTTP)
Inbound / Outbound: Allow
Click Add TCP/UDP Filter
Chapter 4: Configuration
68

5. The new port filter rule for HTTP is shown below:
7. Configure your Virtual Server (“port forwarding”) settings so that incoming HTTP requests on port 80
will be forwarded to the PC running your web server:
Note: For how to configure the HTTP in Virtual Server, go to Add Virtual Ser ver in Virtual
Server section for more details.
.
Chapter 4: Con f ig u rati on
69

Intrusion Detection
The router’s Intrusion Detection System (IDS) is used to detect hacker attacks and intrusion
attempts from the Internet. If the IDS function of the firewall is enabled, inbound packets are
filtered and blocked depending on whether they are detected as possible hacker attacks, intrusion
attempts or other connections that the router determines to be suspicious.
Blacklist: If the router detects a possible attack, the source IP or destination IP address will be
added to the Blacklist. Any further attempts using this IP address will be blocked for the time
period specified as the Block Duration. The default setting for this function is false (disabled).
Some attack types are denied immediately without using the Blacklist function, such as Land
attack and Echo/CharGe n scan.
Intrusion Detection: If enabled, IDS will block Smurf attack attempts. Default is false.
Block Duration:
Victim Protection Block Duration: This is the duration for blocking Smurf attacks.
Default value is 600 seconds.
Scan Attack Block Duration: This is the duration for blocking hosts that attempt a
possible Scan attack. Scan attack types include X’mas scan, IMAP SYN/FIN scan and
similar attempts. Default value is 86400 seconds.
DoS Attack Block Duration: This is the duration for blocking hosts that attempt a
possible Denial of Service (DoS) attack. Possible DoS attacks this attempts to block
include Ascend Kill and WinNuke. Default value is 1800 seconds.
Max TCP Open Handshaking Count: This is a threshold value to decide whether a SYN Flood
attempt is occurring or not. Default value is 100 TCP SYN per seconds.
Max PING Count: This is a threshold value to decide whether an ICMP Echo Storm is occurring or
not. Default value is 15 ICMP Echo Requests (PING) per second.
Chapter 4: Con f ig u rati on
70

Max ICMP Count: This is a threshold to decide whether an ICMP flood is occurring or not. Default
value is 100 ICMP packets per seconds except ICMP Echo Requests (PING).
For SYN Flood, ICMP Echo Storm and ICMP flood, IDS will just warn the user in the Event Log. It
cannot protect against such attacks.
Table 2: Hacker attack ty pes recogni zed by the IDS
Intrusion Name Detect Parameter Blacklist
Ascend Kill Ascend Kill data Src IP DoS Yes Yes
TCP
WinNuke
Smurf
Land attack SrcIP = DstIP Yes Yes
Echo/CharGen Scan
Echo Scan
CharGen Scan
X’mas Tree Scan TCP Flag: X’mas Src IP Scan Yes Yes
IMAP
SYN/FIN Scan
SYN/FIN/RST/ACK
Scan
Net Bus Scan
Back Orifice Scan
SYN Flood
ICMP Flood
ICMP Echo
Src IP: Source IP Src Port: Source Port
Dst Port: Destination Port Dst IP: Destination IP
Port 135, 137~139,
Flag: URG
ICMP type 8
Des IP is broadcast
UDP Echo Port and
CharGen Port
UDP Dst Port =
Echo(7)
UDP Dst Port =
CharGen(19)
TCP Flag: SYN/FIN
DstPort: IMAP(143)
SrcPort: 0 or 65535
TCP,
No Existing session
And Scan Hosts
more than five.
TCP
No Existing session
DstPort = Net Bus
12345,12346, 3456
UDP, DstPort =
Orifice Port (31337)
Max TCP Open
Handshaking Count
(Default 100 c/sec)
Max ICMP Count
(Default 100 c/sec)
Max PING Count
(Default 15 c/sec)
Src IP DoS Yes Yes
Dst IP
Src IP Scan Yes Yes
Src IP Scan Yes Yes
Src IP Scan Yes Yes
Src IP Scan Yes Yes
SrcIP Scan Yes Yes
SrcIP Scan Yes Yes
Type of Block
Duration
Victim
Protection
Yes Yes
Yes
Yes
Yes
Drop Packet Show Log
Yes Yes
Chapter 4: Con f ig u rati on
71

URL Filtering
URL (Uniform Resource Locator – e.g. an address in the form of http://www.abcde.com
http://www.example.com
particular websites by their URL. There are no pre-defined URL filter rules; you can add filter rules
to meet your requirements.
) filter rules allow you to prevent users on your network from accessing
or
Enable/Disable: To enable or disable URL Filter feature.
Block Mode: A list of the modes that you can choose to check the URL filter rules. The default is
set to Disabled.
Disabled: No action will be performed by the Block Mode.
Alw a ys O n: Action is enabled. URL filter rules will be monitoring and checking at all hours
of the day.
TimeSlot1 ~ TimeSlot16: It is self-defined time period. You may specify the time period to
check the URL filter rules, i.e. during working hours. For setup and detail, refer to Time
Schedule section.
Keywords Filtering: Allows blocking by specific keywords within a particular URL rather than
having to specify a complete URL (e.g. to block any image called “advertisement.gif”). When
enabled, your specified keywords list will be checked to see if any keywords are present in URLs
accessed to determine if the connection attempt should be blocked. Please note that the URL filter
blocks web browser (HTTP) connection attempts using port 80 only.
Chapter 4: Con f ig u rati on
72

For example, if the URL is http://www.abc.com/abcde.html, it will be dropped as the keyword
“abcde” occurs in the URL.
Domains Filtering: This function checks the domain name only, not the IP address, in URLs
accessed against your list of domains to block or allow. If it is matched, the URL request will
be sent (Trusted) or dropped (Forbidden). For this function to be activated, both check-boxes
must be checked. The checking procedure is:
1. Check the domain in the URL to determine if it is in the trusted list. If yes, the
connection attempt is sent to the remote web server.
2. If not, check if it is listed in the forbidden list, and if present then the connection attempt
is dropped.
3. If the packet does not match either of the above two items, it is sent to the remote web
server.
4. Please be note that the domain only should be specified, not the full URL. For example
to block traffic to www.sex.com
the example below, the URL request for www.abc.com
server because it is listed in the trusted list, whilst the URL request for www.sex
www.sex.com
will be dropped, because sex.com is in the forbidden list.
, enter “sex” or “sex.com” instead of “www.sex.com”. In
will be sent to the remote web
or
Restrict URL Features: This function enhances the restriction to your URL rules.
Chapter 4: Con f ig u rati on
73

Example: Andy wishes to disable all WEB traffic except for ones listed in the trusted domain,
which would prevent Bobby from accessing other web sites.
Andy selects both functions in the Domain Filtering and thinks that it will stop Bobby. But Bobby
knows this function, Domain Filtering, ONLY disables all WEB traffic except for Trusted Domain,
BUT not its IP address. If this is the situation, Block surfing by IP address function can be
handy and helpful to Andy. Now, Andy can prevent Bobby from accessing other sites.
Block Java Applet: This function can block Web content that includes the Java Applet. It is
to prevent someone who wants to damage your system via standard HTTP protocol.
Block surfing by IP address: Preventing someone who uses the IP address as URL for
skipping Domains Fi ltering function. Activates only and if Domain Filtering enabled.
Chapter 4: Con f ig u rati on
74

Firewall Log
Firewall Log display log information of any unexpected action with your firewall settings.
Check the Enable box to activate the logs.
Log information can be seen in the Status – Event Log after enabling.
Chapter 4: Con f ig u rati on
75

VPN (Virtual Private Networks) (VPN Router Only)
Virtual Private Networks is ways to establish secured communication tunnels to an organization’s
network via the Internet. Your router supports three main types of VPN (Virtual Private Network), PPTP,
IPSec and L2TP.
PPTP (Point-to-Point Tunneling Protocol)
There are two types of PPTP VPN supported; Remote Access and LAN-to-LAN (please refer
below for more information.). Click Create to configure a new VPN connection.
After you have created PPTP connection, account status will be displayed. (See example above).
Enable / Disable: This function activates or deactivates the PPTP connection. To wish
interrupting the tunnel, check Disable radio button and click Apply button to deactivate the
connection.
Name: This is the user-defined name of the connection.
Type: This refers to your router operates as a client or a server, Dialout or Dialin in respectively.
Status: It informs your PPTP tunnel connection condition.
Chapter 4: Configuration
76

PPTP Connection - Remote Access
Connection Name: A user-defined name for the connection (e.g. “connection to office”).
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote VPN
server, e.g. your office server), check Dial In operates as a VPN server.
When configuring your router as a Client, enter the remote Server IP Address (or Domain
Name) you wish to connection to.
When configuring your router as a server, enter the Private IP Address Assigned to Dial
in User address.
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you
are a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by your Host. If you
are a Dial-In user (server), enter your own password.
PPP Authentication Type: Default is Auto if you want the router to determine the authentication
type to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or
PAP (Password Authentication Protocol) if you know which type the server is using (when acting
as a client), or else the authentication type you want clients connecting to you to use (when acting
as a server). When using PAP, the password is sent unencrypted, whilst CHAP encrypts the
password before sending, and also allows for challenges at different periods to ensure that an
intruder has not replaced the client.
Data Encryption: Data sent over the VPN connection can be encrypted by an MPPE algorithm.
Default is Auto, so that this setting is negotiated when establishing a connection, or else you can
manually Enable or Disable encryption.
Key Length: The data can be encrypted by MPPE algorithm with 40 bits or 128 bits. Default is
Auto, it is negotiated when establishing a connection. 128 bit keys provide stronger encryption
than 40 bit keys.
Mode: You may select Stateful or Stateless mode. The key will be changed every 256 packets
when you select Stateful mode. If you select Stateless mode, the key will be changed in each
packet.
Chapter 4: Con f ig u rati on
77

Idle Ti me: Auto-disconnect the VPN connection when there is no activity on the connection for a
predetermined period of time. 0 means this connection is always on.
Active as default route: Enables the default route.
Click Apply button to apply your changes.
Chapter 4: Con f ig u rati on
78

PPTP Connection - LAN to LAN
Connection Name: A user-define description of the connection.
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote VPN
server, e.g. your office server), check Dial In operates as a VPN server.
When configuring your router as a Client, enter the remote Server IP Address (or
Hostname) you wish to connection to.
When configuring your router as a server, enter the Private IP Address Assigned to Dial
in User address.
Peer Network IP: Enter Peer network IP address.
Netmask: Enter the subnet mask of peer network based on the Peer Network IP setting.
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you
are a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by the your Host. If you
are a Dial-In user (server), enter your own password.
PPP Authentication Type: Default is Auto if you want the router to determine the authentication
type to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or
PAP (Password Authentication Protocol) if you know which type the server is using (when acting
as a client), or else the authentication type you want clients connecting to you to use (when acting
as a server). When using PAP, the password is sent unencrypted, whilst CHAP encrypts the
password before sending, and also allows for challenges at different periods to ensure that the
client has not been replaced by an intruder.
Data Encryption: Data sent over the VPN connection can be encrypted by an MPPE algorithm.
Default is Auto, so that this setting is negotiated when establishing a connection, or else you can
manually Enable or Disable encryption.
Key Length: The data can be encrypted by MPPE algorithm with 40 bits or 128 bits. Default is
Auto, it is negotiated when establishing a connection. 128 bit keys provide stronger encryption
than 40 bit keys.
Chapter 4: Con f ig u rati on
79

Mode: You may select Stateful or Stateless mode. The key will be changed every 256 packets
when you select Stateful mode. If you select Stateless mode, the key will be changed in each
packet.
Idle Ti me: Auto-disconnect the VPN connection when there is no activity on the connection for a
predetermined period of time. 0 means this connection is always on.
Click Apply button to apply your changes.
Chapter 4: Con f ig u rati on
80

IPSec (IP Security Pro t oco l)
Click Create to create a new IPSec VPN connection account.
After you have created the IPSec connection, account information will be displayed. (See example
above).
Enable / Disable: This function activates or deactivates the IPSec connection. To wish
interrupting the tunnel, check Disable radio button and click Apply button to deactivate the
connection.
Name: This is the user-defined name of the connection.
Local Subnet: Displays IP address and subnet of the local network.
Remote Subnet: Displays IP address and subnet of the remote network.
Remote Gateway: This is the IP address or Domain Name of the remote VPN device that is
connected and established a VPN tunnel.
IPSec Proposal: This is selected IPSec security method.
Chapter 4: Con f ig u rati on
81

Configure a new VPN Con nection
Connection Name: A user-defined name for the connection (e.g. “connection to office”).
Local:
Network: Set the IP address, subnet or address range of the local network.
Single Address: The IP address of the local host.
Subnet: The subnet of the local network. For example, IP: 192.168.1.0 with netmask
255.255.255.0 specifies one class C subnet starting from 192.168.1.1 (i.e. 192.168.1.1
through to 192.168.1.254).
IP Range: The IP address range of the local network. For example, IP: 192.168.1.1, end
IP: 192.168.1.10
Remote:
Secure Gateway Address (or Domain Name): The IP address or hostname of the remote
VPN device that is connected and establishes a VPN tunnel.
Network: Set the IP address, subnet or address range of the remote network.
Proposal: Select the IPSec security method. There are two methods of checking the
authentication information, AH (authentication header) and ESP (Encapsulating Security Payload).
Use ESP for greater security so that data will be encrypted and authenticated. Using AH data will
be authenticated but not encrypted.
Authentication: Authentication establishes the integrity of the datagram and ensures it is not
tampered with in transmit. There are three options, Message Digest 5 (MD5), Secure Hash
Algorithm (SHA1) or NONE. SHA1 is more resistant to brute-force attacks than MD5, however
it is slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
Chapter 4: Con f ig u rati on
82

SHA1: A one-way hashing algorithm that produces a 160−bit hash.
Encryption: Select the encryption method from the pull-down menu. There are several
options, DES, 3DES, AES (128, 192 and 256) and NULL. NULL means it is a tunnel only with
no encryption. 3DES and AES are more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an
encryption method.
AES: Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as
encryption method.
Perfect Forward Secrecy: Choose whether to enable PFS using Diffie-Hellman public-key
cryptography to change encryption keys during the second phase of VPN negotiation. This
function will provide better security, but extends the VPN negotiation time. Diffie-Hellman is a
public-key cryptography protocol that allows two parties to establish a shared secret over an
unsecured communication channel (i.e. over the Internet). There are three modes, MODP 768-bit,
MODP 1024-bit and MODP 1536-bit. MODP stands for Modular Exponentiation Groups.
Pre-shared Key: This is for the Internet Key Exchange (IKE) protocol, a string from 4 to 128
characters. Both sides should use the same key. IKE is used to establish a shared security policy
and authenticated keys for services (such as IPSec) that require a key. Before any IPSec traffic
can be passed, each router must be able to verify the identity of its peer. This can be done by
manually entering the pre-shared key into both sides (router or hosts).
Select the Apply button to apply your changes.
Chapter 4: Con f ig u rati on
83

Advanced Option
This function is only available after completed creating an IPSec account. Click Advanced Option
to change the following settings:
IKE (Internet key Exchange) Mode: Select IKE mode to Main mode or Aggressive mode. This
IKE provides secured key generation and key management.
IKE Proposal:
Hash Function: It is a Message Digest algorithm which coverts any length of a message into a
unique set of bits. It is widely used MD5 (Message Digest) and SHA-1 (Secure Hash Algorithm)
algorithms.
SHA1 is more resistant to brute-force attacks than MD5, however it is slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
SHA1: A one-way hashing algorithm that produces a 160−bit hash
Encryption: Select the encryption method from the pull-down menu. There are several options,
DES, 3DES and AE S (1 28, 192 and 256). 3DES and AES are more powerful but increase latency.
Chapter 4: Con f ig u rati on
84

DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an
encryption method.
AES: Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as
encryption method.
Diffie-Hellman Group: It is a public-key cryptography protocol that allows two parties to establish
a shared secret over an unsecured communication channel (i.e. over the Internet). There are three
modes, MODP 768-bit, MODP 1024-bit and MODP 1536-bit. MODP stands for Modular
Exponentiation Groups.
Local ID:
Type: Specify local ID type.
Content: Input ID’s information, like domain name www.ipsectest.com
.
Remote ID:
Type: Specify Remote ID type.
Identifier: Input remote ID’s information, like domain name www.ipsectest.com
.
SA Lifetime: Specify the number of minutes that a Security Association (SA) will stay active
before new encryption and authentication key will be exchanged. There are two kinds of SAs, IKE
and IPSec. IKE negotiates and establishes SA on behalf of IPSec, an IKE SA is used by IKE.
Phase 1 (IKE): To issue an initial connection request for a new VPN tunnel. The range can be
from 5 to 15,000 minutes, and the default is 240 minutes.
Phase 2 (IPSec): To negotiate and establish secure authentication. The range can be from 5 to
15,000 minutes, and the default is 60 minutes.
A short SA time increases security by forcing the two parties to update the keys. However, every
time the VPN tunnel re-negotiates, access through the tunnel will be temporarily disconnected.
PING for Keepalive: It is used to detect IPSec tunnel connection failure. Connection failure is
defined as abort or in NO response state. In such event Ping to Keepalive takes proper action to
ensure the connection quality of IPSec.
PING to the IP: It is able to IP Ping the remote PC with the specified IP address and alert when
the connection fails. Once alter message is received, Router will drop this tunnel connection. Re-
establish of this connection is required. Default setting is 0.0.0.0 which disables the function.
Internal: This sets the time interval between Pings to the IP function to monitor the connection
status. Default interval setting is 10 seconds. Time interval can be set from 0 to 3600 second, 0
second disables the function.
Chapter 4: Con f ig u rati on
85

Ping to the IP Internal (sec)
Ping to the IP Action
0.0.0.0 0 No
0.0.0.0 2000 No
xxx.xxx.xxx.xxx (A valid IP Address) 0 No
xxx.xxx.xxx.xxx(A valid IP Address) 2000 Yes, activate it in every 2000
second.
Disconnection Time after no traffic: It is the NO Response time clock. When no traffic stage
time is beyond the Disconnection time set, Router will automatically halt the tunnel connection and
re-establish it base on the Reconnection Time set. Default setting is 1200 seconds; 180
seconds is minimum time interval for this function.
Reconnection Time: It is the reconnecting time interval after NO TRAFFIC is initiated. Default
setting is 15 minutes; 3 min u te s is minimum time interval for this function.
Select the Apply button to update the settings.
Chapter 4: Con f ig u rati on
86

Chapte
L2TP (Layer Two Tunneling Protocol)
Two types of L2TP VPN are supported, Remote Access and LAN-to-LAN (please refer below for
more information.). Click Create to create a new VPN connection account.
After you have created L2TP connection, account status will be displayed. (See example above).
Enable / Disable: This function activates or deactivates the L2TP connection. To wish
interrupting the tunnel, check Disable radio button and click Apply button to deactivate the
connection.
Name: This is the user-defined name of the connection.
Type: This refers to your router operates as a client or a server, Dialout or Dialin in respectively.
Status: It informs your L2TP tunnel connection condition.
r 4: Configuration
87

L2TP Connection - Remote Access
Connection Name: This allows you to identify this particular connection, e.g. “Connection to
office”.
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote VPN
server, e.g. your office server), check Dial In operates as a VPN server.
When configuring your router as a Client, enter the remote Server IP Address (or
Hostname) you wish to connection to.
When configuring your router as a server, enter the Private IP Address Assigned to
Dial in User address.
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you
are a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by your Host. If you
are a Dial-In user (server), enter your own password.
PPP Authentication Type: Default is Auto if you want the router to determine the authentication
type to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or
PAP (Password Authentication Protocol) if you know which type the server is using (when acting
as a client), or else the authentication type you want clients connecting to you to use (when acting
as a server). When using PAP, the password is sent unencrypted, whilst CHAP encrypts the
password before sending, and also allows for challenges at different periods to ensure that the
client has not been replaced by an intruder.
Idle Ti me: Auto-disconnect the VPN connection when there is no activity on the connection for a
predetermined period of time. 0 means this connection is always on.
Click Apply after changing settings.
IPSec: Enable for enhancing your LT2P VPN security.
Chapter 4: Configuration
88

Chapte
Authentication: Authentication establishes the integrity of the datagram and ensures it is not
tampered with in transmit. There are three options, Message Digest 5 (MD5), Secure Hash
Algorithm (SHA1) or NONE. SHA1 is more resistant to brute-force attacks than MD5, however it is
slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
SHA1: A one-way hashing algorithm that produces a 160−bit hash.
Encryption: Select the encryption method from the pull-down menu. There are four options, DES,
3DES, AES and NONE. NONE means it is a tunnel only with no encryption. 3DES and AES are
more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DE S: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an
encryption method.
AES: Stands for Advanced Encryption Standards, it uses 128 bits as an encryption
method.
Perfect Forward Secrecy: Choose whether to enable PFS using Diffie-Hellman public-key
cryptography to change encryption keys during the second phase of VPN negotiation. This function
will provide better security, but extends the VPN negotiation time. Diffie-Hellman is a public-key
cryptography protocol that allows two parties to establish a shared secret over an unsecured
communication channel (i.e. over the Internet). There are three modes, MODP 768-bit, MODP
1024-bit and MODP 1536-bit. MODP stands for Modular Exponentiation Groups.
Pre-shared Key: This is for the Internet Key Exchange (IKE) protocol, a string from 4 to 128
characters. Both sides should use the same key. IKE is used to establish a shared security policy
and authenticated keys for services (such as IPSec) that require a key. Before any IPSec traffic can
be passed, each router must be able to verify the identity of its peer. This can be done by manually
entering the pre-shared key into both sides (router or hosts).
Remote Host Name (Optional): Enter hostname of remote VPN device. It is a tunnel identifier
from the Remote VPN device matches with the Remote hostname provided. If remote hostname
matches, tunnel will be connected; otherwise, it will be dropped.
Cautious: This is only when the router performs as a VPN server. This option should be used by
advanced users only.
Local Host Name (Optional): Enter hostname of Local VPN device that is connected / establishes
a VPN tunnel. As default, Router’s default Hostname is home.gateway.
Tunnel Authentication: This enables router to authenticate both the L2TP remote and L2TP host.
This is only valid when L2TP remote supports this feature.
Secret: The secure password length should be 16 characters which may include numbers and
characters.
r 4: Configuration
89

L2TP Connection - LAN to LAN
Connection Name: A user-define description of the connection.
Type: Check Dial Out if you want your router to operate as a client (connecting to a remote VPN
server, e.g. your office server), check Dial In operates as a VPN server.
When configuring your router establish the connection to a remote LAN, enter the remote
Server IP Address (or Hostname) you wish to connection to.
When configuring your router as a server to accept incoming connections, enter the
Private IP Address Assigned to Dial in User address.
Peer Network IP: Enter Peer network IP address.
Netmask: Enter the subnet mask of peer network based on the Peer Network IP setting.
Username: If you are a Dial-Out user (client), enter the username provided by your Host. If you are
a Dial-In user (server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided by the your Host. If you
are a Dial-In user (server), enter your own password.
PPP Authentication Type: Default is Auto if you want the router to determine the authentication
type to use, or else manually specify CHAP (Challenge Handshake Authentication Protocol) or PAP
(Password Authentication Protocol) if you know which type the server is using (when acting as a
client), or else the authentication type you want clients connecting to you to use (when acting as a
server). When using PAP, the password is sent unencrypted, whilst CHAP encrypts the password
before sending, and also allows for challenges at different periods to ensure that the client has not
been replaced by an intruder.
Chapter 4: Configuration
90

Chapte
Idle Tim e: Auto-disconnect the VPN connection when there is no activity on the connection for a
predetermined period of time. 0 means this connection is always on. Click Apply after changing
settings.
IPSec: Enable for enhancing your LT2P VPN security.
Authentication: Authentication establishes the integrity of the datagram and ensures it is not
tampered with in transmit. There are three options, Message Digest 5 (MD5), Secure Hash
Algorithm (SHA1) or NONE. SHA-1 is more resistant to brute-force attacks than MD5, however it is
slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
SHA1: A one-way hashing algorithm that produces a 160−bit hash.
Encryption: Select the encryption method from the pull-down menu. There are four options, DES,
3DES, AES and NONE. NONE means it is a tunnel only with no encryption. 3DES and AES are
more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an
encryption method.
AES: Stands for Advanced Encryption Standards, it uses 128 bits as an encryption
method.
Perfect Forward Secrecy: Choose whether to enable PFS using Diffie-Hellman public-key
cryptography to change encryption keys during the second phase of VPN negotiation. This function
will provide better security, but extends the VPN negotiation time. Diffie-Hellman is a public-key
cryptography protocol that allows two parties to establish a shared secret over an unsecured
communication channel (i.e. over the Internet). There are three modes, MODP 768-bit, MODP
1024-bit and MODP 1536-bit. MODP stands for Modular Exponentiation Groups.
Pre-shared Key: This is for the Internet Key Exchange (IKE) protocol, a string from 4 to 128
characters. Both sides should use the same key. IKE is used to establish a shared security policy
and authenticated keys for services (such as IPSec) that require a key. Before any IPSec traffic can
be passed, each router must be able to verify the identity of its peer. This can be done by manually
entering the pre-shared key into both sides (router or hosts).
Remote Host Name (Optional): Enter hostname of remote VPN device. It is a tunnel identifier
from the Remote VPN device matches with the Remote hostname provided. If remote hostname
matches, tunnel will be connected; otherwise, it will be dropped.
Cautious: This is only when the router performs as a VPN server. This option should be used by
advanced users only.
Local Host Name (Optional): Enter hostname of Local VPN device that is connected / establishes
a VPN tunnel. As default, Router’s default Hostname is home.gateway.
Tunnel Authentication: This enables router to authenticate both the L2TP remote and L2TP host.
This is only valid when L2TP remote supports this feature.
Secret: The secure password length should be 16 characters which may include numbers and
characters.
91
r 4: Configuration

Example: Configuring a Remote Access PPTP VPN Di al-in Connecti on
A remote worker establishes a PPTP VPN connection with the head office using Microsoft's VPN
Adapter (included with Windows 2000/ME, etc.). The router is installed in the head office, connected to a
couple of PCs and Servers.
Dial-in
Chapter 4: Configuration
92

Chapte
Configuring PPTP VPN in the Office
The input IP address 192.168.1.200 will be assigned to the remote worker. Please make sure this IP is
not used in the Office LAN.
Item Function Description
1 Connection Name VPN_PPTP Given a name of PPTP connection
Dial in Check Dial in
Private IP Address
2
Assigned to Dialing
User
Username username
3
Password 123456
Auth.Type Chap(Auto)
Data Encryption Auto
4
Key Length Auto
Mode stateful
5 Idle Time 0
192.168.1.200 An assigned IP address for the remote worker
Input username & password to authenticate
remote worker
Keep as default value in most of the cases,
PPTP server & client will determine the value
automatically. Refer to manual for details if you
want to change the setting.
The connection will be disconnected when there
is no traffic in a predefined period of time. Idle
time 0 means the connection is always on.
r 4: Configuration
93

Example: Configuring a Remote Access PPTP VPN Di al-out Connec tion
A company’s office establishes a PPTP VPN connection with a file server located at a separate location.
The router is installed in the office, connected to a couple of PCs and Servers.
Dial-out
Chapter 4: Configuration
94

Chapte
Configuring the PPTP VPN in the Office
You can either input the IP address (69.1.121.33 in this case) or hostname to reach the server.
Item Function Description
1 Connection Name VPN_PPTP Given name of PPTP connection
Dial out Check Dial out
2
Server IP Address
(or Hostname)
Username username
3
Password 123456
Auth.Type Chap(Auto)
Data Encryption Auto
4
Key Length Auto
Mode stateful
5 Idle Time 0
69.121.1.33 An Dialed server IP
A given username & password
Keep as default value in most of the cases,
PPTP server & client will determine the value
automatically. Refer to manual for details if you
want to change the setting.
The connection will be disconnected when
there Is no traffic in a predefined period of time.
Idle time 0 means the connection is always on.
r 4: Configuration
95

Example: Configuring a LAN-to-LAN PPTP VPN Connection
The branch office establishes a PPTP VPN tunnel with head office to connect two private networks over
the Internet.. The routers are installed in the head office and branch office accordingly.
Both office LAN networks MUST in different subnet with LAN to LAN
application.
Chapter 4: Configuration
96
 Loading...
Loading...