Page 1

Avira Premium Security Suite
User Manual
Page 2

Trademarks and Copyright
Trademarks
AntiVir is a registered trademark of Avira GmbH.
Windows is a registered trademark of the Microsoft Corporation in the United States and other countries.
All other brand and product names are trademarks or registered trademarks of their respective owners.
Protected trademarks are not marked as such in this manual. This does not mean, however that they may be used freely.
Copyright information
Code provided by third party providers was used for Avira Premium Security Suite. We thank the copyright owners for
making the code available to us. For detailed information on copyright, please refer to Third Party Licenses in the Program
Help of Avira Premium Security Suite.
Page 3

ii
Table of Contents
1 Introduction ............................................................................................................ 1
2 Icons and emphases .................................................................................................. 2
3 Product information ................................................................................................ 3
3.1 Delivery scope ......................................................................................................................3
3.2 System requirements ...........................................................................................................4
3.3 Licensing and Upgrade ........................................................................................................4
4 Installation and uninstallation ................................................................................. 6
4.1 Installation ..........................................................................................................................6
4.2 Change installation .......................................................................................................... 11
4.3 Installation modules ......................................................................................................... 12
4.4 Uninstallation ................................................................................................................... 13
5 Overview of Premium Security Suite....................................................................... 14
5.1 User interface and operation ............................................................................................ 14
5.1.1 Control Center .................................................................................................... 14
5.1.2 Configuration ...................................................................................................... 17
5.1.3 Tray icon .............................................................................................................. 20
5.2 How to...? .......................................................................................................................... 21
5.2.1 Activate product .................................................................................................. 21
5.2.2 Perform automatic updates ................................................................................ 22
5.2.3 Start a manual update ......................................................................................... 23
5.2.4 On-demand scan: Using a scan profile to scan for viruses and malware ........... 23
5.2.5 On-demand scan: Scan for viruses and malware using Dragamp;Drop ............. 25
5.2.6 On-demand scan: Scan for viruses and malware via the context menu ............. 25
5.2.7 On-demand scan: Automatically scan for viruses and malware ......................... 26
5.2.8 On-demand scan: Targeted scan for Rootkits and active malware .................... 27
5.2.9 React to detected viruses and malware ............................................................... 27
5.2.10 Quarantine: Handling quarantined files (*.qua) ................................................. 31
5.2.11 Quarantine: Restore the files in quarantine ....................................................... 33
5.2.12 Quarantine: Move suspicious files to quarantine ............................................... 34
5.2.13 Scan profile: Amend or delete file type in a scan profile .................................... 34
5.2.14 Scan profile: Create desktop shortcut for scan profile ....................................... 34
5.2.15 Events: Filter events ........................................................................................... 35
5.2.16 MailGuard: Exclude email addresses from scan ................................................. 35
5.2.17 MailGuard: Train the anti-spam module ............................................................ 36
5.2.18 FireWall: Select the security level for the FireWall ............................................. 36
5.2.19 Backup: Create backups manually....................................................................... 37
5.2.20 Backup: Create automatic data backups ............................................................. 38
Page 4

Table of Contents
iii
6 Scanner .................................................................................................................. 42
7 Updates .................................................................................................................. 43
8 Avira FireWall :: Overview ...................................................................................... 44
9 Backup ................................................................................................................... 45
10 FAQ, Tips ............................................................................................................... 46
10.1 Help in case of a problem ................................................................................................. 46
10.2 Shortcuts .......................................................................................................................... 50
10.2.1 In dialog boxes .................................................................................................... 50
10.2.2 In the help ........................................................................................................... 51
10.2.3 In the Control Center .......................................................................................... 51
10.3 Windows Security Center ................................................................................................. 53
10.3.1 General ................................................................................................................ 53
10.3.2 The Windows Security Center and your AntiVir program ................................. 53
11 Viruses and more.................................................................................................... 56
11.1 Extended threat categories .............................................................................................. 56
11.2 Viruses and other malware ............................................................................................... 58
12 Info and Service ..................................................................................................... 62
12.1 Contact address ................................................................................................................ 62
12.2 Technical support ............................................................................................................. 62
12.3 Suspicious file ................................................................................................................... 62
12.4 Reporting false positives .................................................................................................. 63
12.5 Your feedback for more security ...................................................................................... 63
13 Reference: Configuration options ........................................................................... 64
13.1 Scanner ............................................................................................................................. 64
13.1.1 Scan ..................................................................................................................... 64
13.1.1.1. Action on detection ...................................................................................... 66
13.1.1.2. Exceptions .................................................................................................... 69
13.1.1.3. Heuristics ..................................................................................................... 70
13.1.2 Report .................................................................................................................. 71
13.2 Guard ................................................................................................................................ 71
13.2.1 Scan ..................................................................................................................... 71
13.2.1.1. Action on detection ...................................................................................... 73
13.2.1.2. Further actions ............................................................................................. 75
13.2.1.3. Exceptions .................................................................................................... 76
13.2.1.4. Heuristics ..................................................................................................... 79
13.2.2 ProActiv ............................................................................................................... 80
13.2.2.1. Application filter: Applications to be blocked.............................................. 81
13.2.2.2. Application filter: Permitted applications ................................................... 81
13.2.3 Report .................................................................................................................. 82
13.3 MailGuard ......................................................................................................................... 83
13.3.1 Scan ..................................................................................................................... 83
13.3.1.1. Action on detection ...................................................................................... 84
13.3.1.2. Other actions ................................................................................................ 86
13.3.1.3. Heuristics ..................................................................................................... 86
13.3.1.4. AntiBot ......................................................................................................... 87
13.3.2 General ................................................................................................................ 88
13.3.2.1. Exceptions .................................................................................................... 88
13.3.2.2. Cache ............................................................................................................ 90
Page 5

Avira Premium Security Suite
iv
13.3.2.3. MailGuard .................................................................................................... 90
13.3.2.4. Footer ........................................................................................................... 91
13.3.3 Report .................................................................................................................. 91
13.4 Firewall ............................................................................................................................. 92
13.4.1 Adapter rules ....................................................................................................... 92
13.4.1.1. Incoming Rules ............................................................................................. 95
13.4.1.2. Outgoing Rules ........................................................................................... 102
13.4.2 Application rules ............................................................................................... 102
13.4.3 Trusted providers .............................................................................................. 105
13.4.4 Settings.............................................................................................................. 106
13.4.5 Popup settings ................................................................................................... 107
13.5 WebGuard ....................................................................................................................... 108
13.5.1 Scan ................................................................................................................... 109
13.5.1.1. Action on detection .................................................................................... 109
13.5.1.2. Locked requests .......................................................................................... 110
13.5.1.3. Exceptions .................................................................................................. 112
13.5.1.4. Heuristics ................................................................................................... 114
13.5.2 Report ................................................................................................................ 115
13.6 Parental controls ............................................................................................................ 116
13.7 Backup ............................................................................................................................ 118
13.7.1 Settings.............................................................................................................. 118
13.7.2 Exceptions ......................................................................................................... 118
13.7.3 Report ................................................................................................................ 120
13.8 Update ............................................................................................................................ 121
13.8.1 Start product update ......................................................................................... 121
13.8.2 Restart settings ................................................................................................. 122
13.9 General............................................................................................................................ 123
13.9.1 Threat categories ............................................................................................... 124
13.9.2 Password ........................................................................................................... 124
13.9.3 Security .............................................................................................................. 126
13.9.4 WMI ................................................................................................................... 127
13.9.5 Proxy ................................................................................................................. 127
13.9.6 Directories ......................................................................................................... 128
13.9.7 Events ................................................................................................................ 129
13.9.8 Limit reports ..................................................................................................... 129
13.9.9 Acoustic alerts ................................................................................................... 129
13.9.10 Warnings ........................................................................................................... 130
Page 6

1
1 Introduction
Your AntiVir program protects your computer against viruses, worms, Trojans, adware
and spyware and other risks. In this manual these are referred to as viruses or malware
(harmful software) and unwanted programs.
The manual describes the program installation and operation.
For further options and information, please visit our website:
http://www.avira.com
The Avira website lets you...…
– access information on other AntiVir desktop programs
– download the latest AntiVir desktop programs
– download the latest product manuals in PDF format
– download free support and repair tools
– access our comprehensive knowledge database and FAQs for troubleshooting
– access country-specific support addresses.
Your Avira Team
Page 7
2
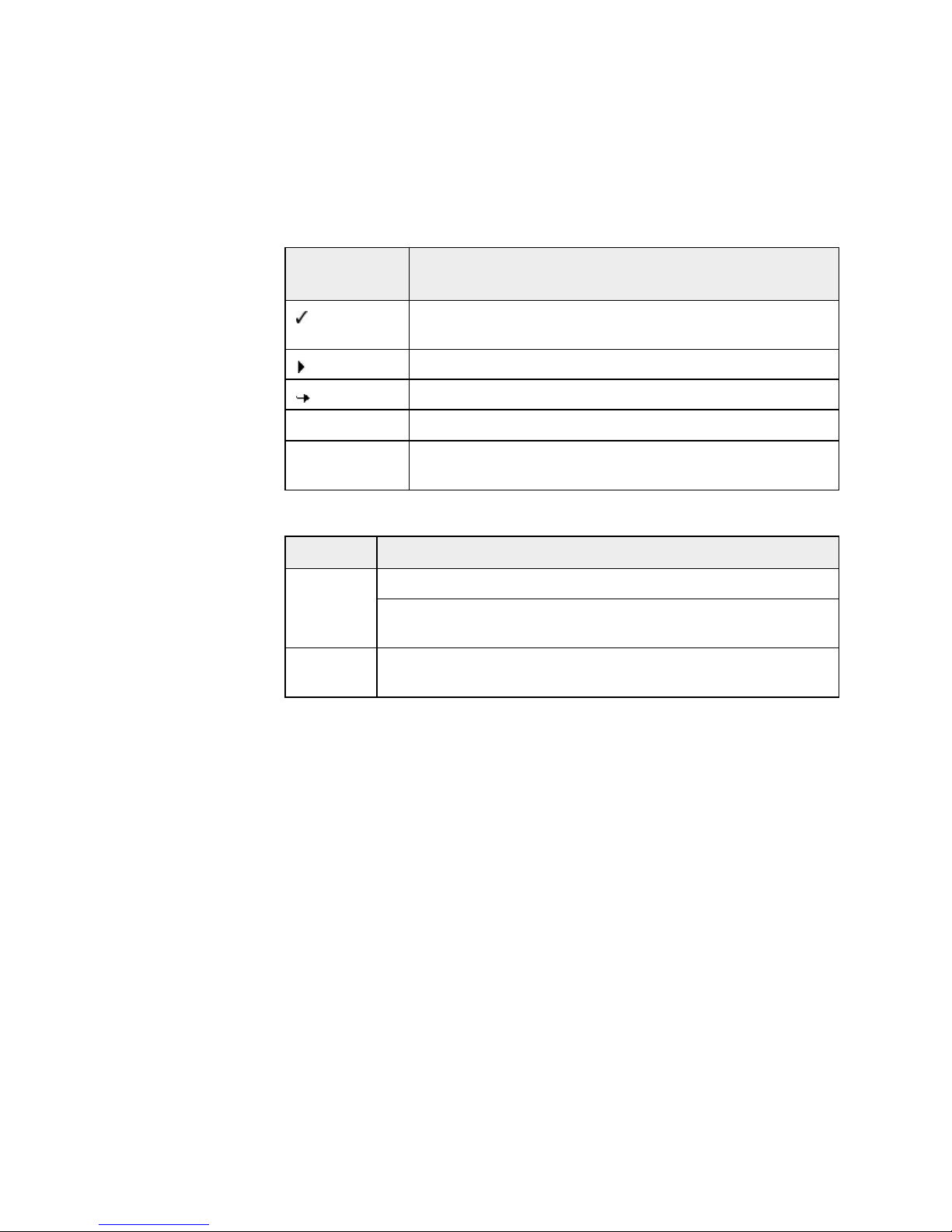
2 Icons and emphases
The following icons are used:
Icon /
designation
Explanation
Placed before a condition which must be fulfilled prior to
execution of an action.
Placed before an action step that you perform.
Placed before an event that follows the previous action.
Warning
Placed before a warning of the danger of critical data loss.
Note
Placed before a link to particularly important information or
a tip which makes your AntiVir program easier to use.
The following emphases are used:
Emphasis Explanation
Cursive
File name or path data.
Displayed software interface elements (e.g. window heading,
window field or options box).
Bold
Clicked software interface elements (e.g. menu item, section or
button).
Page 8

3
3 Product information
This chapter contains all information relevant to the purchase and use of your AntiVir
product:
– see Chapter: Delivery scope
– see Chapter: System requirements
– see Chapter: Licensing
– see Chapter: License Manager
AntiVir programs are comprehensive and flexible tools you can rely on to protect your
computer from viruses, malware, unwanted programs and other dangers.
Please note the following information:
Note
Loss of valuable data usually has dramatic consequences. Even the best virus protection
program cannot provide one hundred percent protection from data loss. Make regular
copies (Backups) of your data for security purposes.
Note
A program can only provide reliable and effective protection from viruses, malware,
unwanted programs and other dangers if it is up-to-date. Make sure your AntiVir
program is up-to-date with automatic updates. Configure the program accordingly.
3.1 Delivery scope
Your AntiVir program has the following functions:
– Control Center for monitoring, managing and controlling the entire program
– Central configuration with user-friendly standard and advanced options and
context-sensitive help
– Scanner (on-demand scan) with profile-controlled and configurable scan for all
known types of virus and malware
– Integration into the Windows Vista User Account Control allows you to carry out
tasks requiring administrator rights.
– Guard (on-access scan) for continuous monitoring of all file access attempts
– ProActiv component for the permanent monitoring of program actions (for 32-
bit system only, not available under Windows 2000)
– MailGuard (POP3 Scanner, IMAP Scanner and SMTP Scanner) for the permanent
checking of emails for viruses and malware. Checking of email attachments is
included
– WebGuard for monitoring data and files transferred from the Internet using the
HTTP protocol (monitoring of ports 80, 8080, 3128)
– Parental control component for role-based filtering of undesirable websites and
limiting Internet use
– Backup component for creating backups of your data (mirror backups)
Page 9

Avira Premium Security Suite
4
– Integrated quarantine management to isolate and process suspicious files
– Rootkit protection for detecting hidden malware installed in your computer
system (rootkits)
(Not available under Windows XP 64 bit)
– Direct access to detailed information on the detected viruses and malware via the
Internet
– Simple and quick updates to the program, virus definitions, and search engine
through Single File Update and incremental VDF updates via a web server on the
Internet
– User-friendly licensing in License Manager
– Integrated Scheduler for planning one-off or recurring jobs such as updates or
scans
– Extremely high virus and malware detection via innovative scanning technology
(scan engine) including heuristic scanning method
– Detection of all conventional archive types including detection of nested archives
and smart extension detection
– High-performance multithreading function (simultaneous high-speed scanning
of multiple files)
– Avira FireWall for protecting your computer from unauthorized access from the
Internet or another network and from unauthorized access to the
Internet/network by unauthorized users
3.2 System requirements
The system requirements are as follows:
– Computer Pentium or later, at least 266 MHz
– Operating system
– Windows XP, SP2 (32 or 64 bit) or
– Windows Vista (32 or 64 bit, SP 1)
– Windows 7 (32 or 64 bit)
– At least 150 MB of free hard disk memory space (more if using quarantine for
temporary storage)
– At least 256 MB RAM under Windows XP
– At least 1024 MB RAM under Windows Vista, Windows 7
– For the program installation: Administrator rights
– For all installations: Windows Internet Explorer 6.0 or higher
– Internet connection where appropriate (see Installation)
3.3 Licensing and Upgrade
Page 10

Product information
5
In order to be able to use your AntiVir product, you require a license. You thereby accept
the license terms.
The license is provided in the form of an activation key. The activation key is a code
comprising letters and numbers that you will receive after purchasing the AntiVir
product. The activation key contains the exact data of your license, i.e. which programs
have been licensed for which period of time.
The activation key will be sent to you by email, if you have purchased your AntiVir
program on the Internet or it is rendered on the product packaging.
In order to license your program, please enter your activation key to activate the
program. The product activation may be performed during installation. However, you
can also activate your AntiVir program after the installation in License Manager, under
Help::License management .
In License Manager, you have the option of launching an upgrade for a product from the
AntiVir desktop product family. Manual uninstallation of the old product and manual
installation of the new product is not required. When upgrading from License Manager,
you enter the activation code for the product you want to upgrade in the License
Manager input box. The new product is automatically installed.
The following product upgrades can be executed automatically via License Manager:
– Upgrade of Avira AntiVir Personal to Avira AntiVir Premium
– Upgrade of Avira AntiVir Personal to Avira Premium Security Suite
– Upgrade of Avira AntiVir Premium to Avira Premium Security Suite
Page 11

6
4 Installation and uninstallation
This chapter contains information relating to the installation and uninstallation of your
AntiVir program.
– see Chapter Installation: Conditions, Installation types, Install
– see Chapter Installation modules
– see Chapter Modification installation
– see Chapter Uninstallation: Uninstall
4.1 Installation
Before installation, check whether your computer fulfils all the minimum system
requirements. If your computer satisfies all requirements, you can install the AntiVir
program.
Note
During the installation process you have the option of creating a restore point. A
purpose of a restore point is to reset the operating system to its pre-installation status.
If you want to use this option, ensure that the operating system permits the creation of a
restore point:
Windows XP: System properties -> System restore: Disable the option Disable system
restore.
Windows Vista/Windows 7: System properties -> Computer protection: In the
Protection settings area, highlight the drive on which the system is installed and click
the Configure button. In the System protection window, enable the option System
settings and restore previous file versions.
Installation types
During installation you can select a setup type in the installation wizard:
Express
– Not all program components are installed. The following components are not
installed:
Avira AntiVir ProActiv
Avira FireWall
– The program files are installed into a specified default folder under
C:\Program Files.
– Your AntiVir program is installed with default settings. You have the option of
defining custom settings using the configuration wizard.
User-defined
– You can choose to install individual program components (see Chapter
Installation and uninstallation::Installation modules).
Page 12

Installation and uninstallation
7
– A target folder can be selected for the program files to be installed.
– You can disable Create a desktop icon and program group in the Start menu.
– Using the configuration wizard, you can define custom settings for your AntiVir
program and initiate a short system scan that is performed automatically after
installation.
Before starting installation
Close your email program. It is also recommended to end all running applications.
Make sure that no other virus protection solutions are installed. The automatic
protection functions of various security solutions may interfere with each other.
Establish an Internet connection: The Internet connection is necessary for
performing the following installation steps:
Downloading the current program file and scan engine as well as the latest virus
definition files via the installation program (for Internet-based installation)
Activating the program
Where appropriate, carrying out a update after completed installation
Keep the license key for your AntiVir program handy when you want to activate the
program.
Note
Internet-based installation:
For the Internet-based installation of the program, an installation program is provided
that loads the current program file prior to installation by the Avira GmbH web servers.
This process ensures that your AntiVir program is installed with the latest virus
definition file.
Installation with an installation package:
The installation package contains both the installation program and all necessary
program files. No language selection for your AntiVir program is available for
installation with an installation package. We recommend that you carry out an update of
the virus definition file after installation.
Note
For product activation, your AntiVir program uses the HTTP protocol and Port 80 (web
communication), as well as encryption protocol SSL and port 443, to communicate with
the Avira GmbH servers. If you are using a firewall, please ensure that the required
connections and/or incoming or outgoing data are not blocked by the firewall.
Install
The installation program runs in self-explanatory dialog mode. Every window contains a
certain selection of buttons to control the installation process.
The most important buttons are assigned the following functions:
– OK: Confirm action.
– Abort: Abort action.
– Next: Go to next step.
– Back: Go to previous step.
Installing your AntiVir program:
Page 13

Avira Premium Security Suite
8
Note
The following actions for disabling the Windows FireWall only apply to the Windows XP
operating system.
Start the installation program by double-clicking the installation file you have
downloaded from the Internet or insert the program CD.
Internet-based installation
The dialog box Welcome... appears.
Click Next to continue with the installation.
The dialog box Language selection appears.
Select the language you want to use to install your AntiVir program and confirm
your language selection by clicking Next.
The dialog box Download appears. All files necessary for installation are
downloaded from the Avira GmbH web servers. The Download window closes after
conclusion of the download.
Installation with an installation package
The installation wizard opens with the dialog box Avira Premium Security Suite.
Click Accept to begin the installation.
The installation file is extracted. The installation routine is started.
The dialog box Welcome... appears.
Click Next.
Continuing Internet-based installation and installation with an installation package
The dialog box with the license agreement appears.
Confirm that you accept the license agreement and click Next.
The dialog box Generate serial number appears.
Where appropriate, confirm that a random serial number has been generated and
transmitted during update, and click Next.
The dialog box Select installation type appears.
Enable the option Express or User-defined. If you want to create a restore point,
enable the Creating system restore point option. Click Next to confirm your
settings.
User-defined installation
The dialog box Select destination directory appears.
Confirm the specified destination directory by clicking Next.
- OR -
Use the Browse button to select a different destination directory and confirm by
clicking Next.
The dialog box Install components appears:
Enable or disable the required components and confirm by clicking Next.
If you have chosen to install the ProActiv component, the AntiVir ProActiv
Community window appears. You have the option of confirming participation in the
Avira AntiVir ProActiv Community: If this option is enabled, Avira AntiVir ProActiv
sends data on suspicious programs detected by the ProActiv component to the Avira
Malware Research Center. The data is used only for an advanced online scan and to
expand and refine detection technology. You can use the further information link to
Page 14

Installation and uninstallation
9
obtain more details on the expanded online scan.
Enable or disable participation in the AntiVir ProActiv Community and confirm by
clicking Next.
In the following dialog box you can decide whether to create a desktop shortcut
and/or a program group in the Start menu.
Click Next.
Skip the following section "Express installation".
Express installation
The AntiVir ProActiv Community window appears. You have the option of
confirming participation in the Avira AntiVir ProActiv Community: If this option is
enabled, Avira AntiVir ProActiv sends data on suspicious programs detected by the
ProActiv component to the Avira Malware Research Center. The data is used only for an
advanced online scan and to expand and refine detection technology. You can use the
further information link to obtain more details on the expanded online scan.
Enable or disable participation in the AntiVir ProActiv Community and confirm by
clicking Next.
Resume: Express installation und user-defined installation
The license wizard is opened.
You have the following options to activate the program.
• Enter an activation key.
By entering your activation key, your AntiVir program is activated with your
license.
• Select the option Product testing
If you select Product testing an evaluation license to activate the program will
be generated during the activation process. You can test the AntiVir program
with its complete range of functions for a certain period of time.
Note
By using the option Valid hbedv.key license file available you can load a valid license
file. During product activation with a valid activation key the license key is generated
and saved in the program directory of your AntiVir program. Use this option if you have
already activated a product and want to re-install your AntiVir program.
Note
In some sales versions of AntiVir products, an activation key has already been included
in the product. For this reason the activation need not be entered. If and when
necessary, the activation key is displayed in the license wizard.
Note
In order to activate the program, a connection to the Avira GmbH servers is established.
Under Proxy settings you can configure the Internet link by a proxy server.
Select an activation process and click Next to confirm.
Product activation
A dialog box will be opened in which you can enter your personal data.
Enter your data and click Next
Your data is transmitted to the Avira GmbH servers and scanned. Your AntiVir
program is activated by means of your license.
Page 15

Avira Premium Security Suite
10
Your license data will be displayed in the next window.
Click Next.
Skip the following chapter on "Activate by selecting the option Valid hbedv.key
available ".
Select the option "Valid hbedv.key available"
A box will be opened for loading the license file.
Select the license file hbedv.key with your license data for the program, and click
Open
Your license data will be displayed in the next window.
Click Next
Continuation after completed activation or loading of the license file
The program features will be installed. Installation progress is displayed in the
dialog box.
In the following dialog box you can choose whether to open the Readme file after
installation is completed and whether to restart your computer.
Agree where appropriate and complete the installation by clicking Finish.
The installation wizard is closed.
Resume: User-defined installation
Configuration wizard
If you choose user-defined installation, the configuration wizard is opened in the
following step. The configuration wizard enables you to define custom settings for your
AntiVir program.
Click Next in the welcome window of the configuration wizard to begin
configuration of the program.
The Configure AHeAD dialog box enables you to select a detection level for the
AHeAD technology. The detection level selected is used for the Scanner (On-demand
scan) and Guard (On-access scan) AHeAD technology settings.
Select a detection level and continue the installation by clicking Next.
In the following dialog box Select extended threat categories, you can adapt the
protective functions of your AntiVir program to the threat categories specified.
Where appropriate, activate further threat categories and continue the installation
by clicking Next.
If you have selected the AntiVir FireWall installation module, the FireWall
security level dialog box appears. You can define whether the Avira FireWall should
permit external access to enabled resources as well as network access by applications of
trusted companies.
Enable the required options and continue the configuration by clicking Next.
If you have selected the AntiVir Guard installation module, the Guard start mode
dialog box appears. You can stipulate the Guard start time. At each computer reboot, the
Guard will be started in the start mode specified.
Note
The specified Guard start mode is saved in the registry and cannot be changed via the
Configuration.
Page 16
Installation and uninstallation
11
Enable the required option and continue the configuration by clicking Next.
If you have selected the AntiVir WebGuard installation module, theEnable
parental controls dialog box appears. You can stipulate the Guard start time. At each
computer reboot, the Guard will be started in the start mode specified. You have the
option of assigning different roles – child, young person, adult – to computer users for
Internet use. You can disable parental controls.
Define the required parental control settings and continue the configuration by
clicking Next.
In the following Assign password dialog box, you can password protect the
Configuration from unauthorized access. This is particularly recommended if parental
control is enabled.
In the following System scan dialog box, a short system scan can be enabled or
disabled. The short system scan is performed after the configuration has been completed
and before the computer is rebooted, and scans running programs and the most
important system files for viruses and malware.
Enable or disable the Short system scan option and continue the configuration by
clicking Next.
In the following dialog box, you can complete the configuration by clicking Finish
Click Finish to complete the configuration.
The specified and selected settings are accepted.
If you have enabled the Short system scan option, the Luke Filewalker window
opens. The Scanner performs a short system scan.
Resume: Express installation und user-defined installation
If you selected the Restart computer option in the final installation wizard, the
computer reboots.
After the computer restart the Readme file is displayed if you selected the Show
Readme.txt option in the installation wizard.
After a successful installation, we recommend that you check the program is up-to-date
in the Control Center under Overview::Status.
Where appropriate, perform an update to ensure the virus definition file is up-to-
date.
Then perform a complete system scan.
4.2 Change installation
You have the option of adding or removing individual program components of the
current AntiVir program installation (see Chapter Installation and
uninstallation::Installation modules)
If you wish to add or remove modules of the current installation, you can use the option
Add or Remove Programs in the Windows control panel to Change/Remove
programs.
Select your AntiVir program and click Change. In the welcome dialog of the program,
select the option Modify. You will be guided through the installation changes.
Page 17

Avira Premium Security Suite
12
4.3 Installation modules
In a user-defined installation or a change installation, the following installation modules
can be selected, added or removed.
– Premium Security Suite
This module contains all components required for successful installation of your
AntiVir program.
– AntiVir Guard
The AntiVir Guard runs in the background. It monitors and repairs, if possible,
files during operations such as open, write and copy in on-access mode.
Whenever a user carries out a file operation (e.g. load document, execute, copy),
the AntiVir program automatically scans the file. Renaming a file does not trigger
a scan by AntiVir Guard.
– AntiVir ProActiv
The ProActiv component monitors application actions and alerts users to
suspicious application behavior. This behavior-based recognition enables you to
protect yourself against unknown malware. The ProActiv component is
integrated into AntiVir Guard.
– AntiVir MailGuard
MailGuard is the interface between your computer and the email server from
which your email program (email client) downloads emails. MailGuard is
connected as a so-called proxy between the email program and the email server.
All incoming emails are routed through this proxy, scanned for viruses and
unwanted programs and forwarded to your email program. Depending on the
configuration, the program processes the affected emails automatically or asks
the user for a certain action. In addition, the MailGuard can reliably protect you
against spam emails.
– AntiVir WebGuard
When surfing the Internet, you are using your web browser to request data from
a web server. The data transferred from the web server (HTML files, script and
image files, Flash files, video and music streams, etc.) will normally be moved
directly into the browser cache for display in the web browser, meaning that an
on-access scan as performed by AntiVir Guard is not possible. This could allow
viruses and unwanted programs to access your computer system. WebGuard is
what is known as an HTTP proxy which monitors the ports used for data transfer
(80, 8080, 3128) and scans the transferred data for viruses and unwanted
programs. Depending on the configuration, the program may process the affected
files automatically or prompt the user for a specific action.
– Avira FireWall:
Avira FireWall controls communication to and from your computer. It permits or
denies communications based on security policies.
– AntiVir Rootkit Protection
AntiVir Rootkit Protection checks whether software is already installed on your
computer that can no longer be detected with conventional methods of malware
protection after penetrating the computer system.
Page 18

Installation and uninstallation
13
– Shell Extension
The Shell Extension generates an entry ‘Scan selected files with AntiVir’ in the
context menu of the Windows Explorer (right-hand mouse button). With this
entry you can directly scan files or directories.
– Backup
The Backup component lets you create mirror backups of your data manually and
automatically.
4.4 Uninstallation
If you wish to remove the AntiVir program from your computer, you can use the option
Add or Remove Programs to Change/Remove programs in the Windows Control
Panel.
To uninstall your AntiVir program (e.g. in Windows XP and Windows Vista):
Open the Control Panel via the Windows Start menu.
Double click on Programs (Windows XP: Software).
Select your AntiVir program in the list and click Remove.
You will be asked if you really want to remove the program.
Click Yes to confirm.
You will be asked if you want to re-enable Windows FireWall (the Avira FireWall
is disabled).
Click Yes to confirm.
All components of the program are removed.
Click on Finish to complete uninstallation.
Where appropriate, a dialog box appears recommending that your computer be
restarted.
Click Yes to confirm.
The AntiVir program is uninstalled and all directories, files and registry entries
for the program are deleted when your computer is restarted.
Page 19
14
5 Overview of Premium Security Suite
This chapter contains an overview of the functionality and operation of your AntiVir
program.
– see Chapter Interface and operation
– see Chapter How to...?
5.1 User interface and operation
You operate your AntiVir program via three program interface elements:
– Control Center: monitoring and controlling the AntiVir program
– Configuration: Configuring the AntiVir program
– Tray Icon in the system tray of the taskbar: Opening the Control Center and
other functions
5.1.1 Control Center
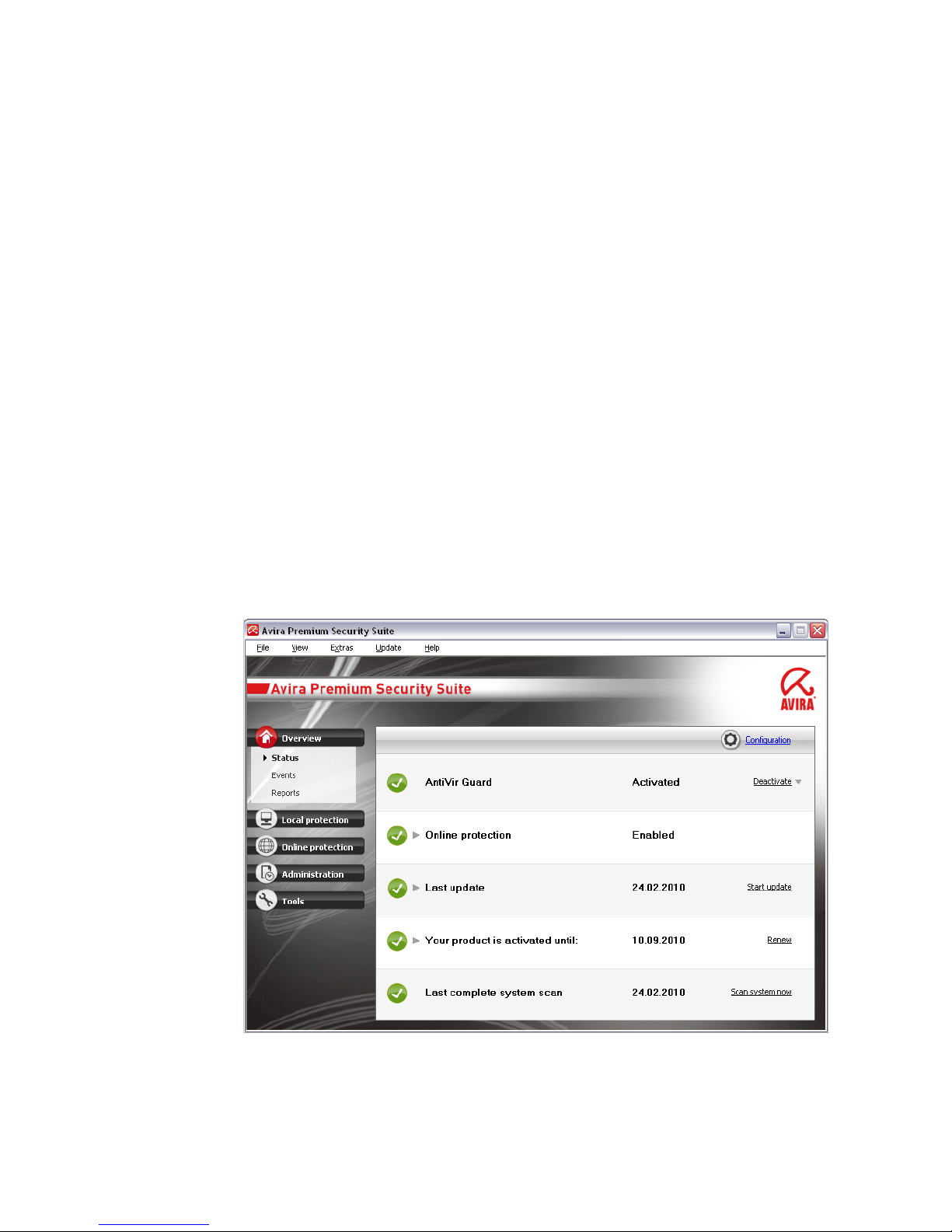
The Control Center is designed to monitor the protection status of your computer
systems and control and operate the protection components and functions of your
AntiVir program.
The Control Center window is divided into three areas: The Menu bar, the Navigation
bar and the detail window View:
– Menu bar: In the Control Center menu bar, you can access general program
functions and information on the program.
Page 20

Overview of Premium Security Suite
15
– Navigation area: In the navigation area, you can easily swap between the
individual sections of the Control Center. The individual sections contain
information and functions of the program components and are arranged in the
navigation bar according to activity. Example: Activity Overview - Section Status.
– View: This window shows the section selected in the navigation area. Depending
on the section, you will find buttons to execute functions and actions in the
upper bar of the detail window. Data or data objects are displayed in lists in the
individual sections. You can sort the lists by clicking in the box defining how you
wish to sort the list.
Starting and closing of Control Center
To start the Control Center the following options are available:
– Double-click the program icon on your desktop
– Via the program entry in the Start | Programs menu.
– Via the Tray Icon of your AntiVir program.
Close the Control Center via the menu command Close in the menu File or by clicking
on the close tab in the Control Center.
Operate Control Center
To navigate in the Control Center
Select an activity in the navigation bar.
The activity opens and other sections appear. The first section of the activity is
selected and displayed in the view.
If necessary, click another section to display this in the detail window.
- OR -
Select a section via the View menu.
Note
You can activate the keyboard navigation in the menu bar with the help of the [ALT] key.
If navigation is activated, you can move within the menu with the arrow keys. With the
Return key you activate the active menu item.
To open or close menus in the Control Center, or to navigate within the menus, you can
also use the following key combinations: [Alt] + underlined letter in the menu or menu
command. Hold down the [Alt] key if you want to access a menu, a menu command or a
submenu.
To process data or objects displayed in the detail window:
highlight the data or object you wish to edit.
To highlight multiple elements (elements in columns), hold down the control key or
the shift key while selecting the elements.
Click the appropriate button in the upper bar of the detail window to edit the object.
Control Center overview
– Overview: In Overview you will find all sections with which you can monitor
the functioning of your AntiVir program.
Page 21

Avira Premium Security Suite
16
• The Status section lets you see at a glance which program modules are active and
provides information on the last update performed. You can also see whether you
own a valid license.
• The Events section enables you to view events generated by certain program
modules.
• Die Reports section enables you to view the results of actions performed.
– Local protection: InLocal protection you will find the components for
checking the files on your computer system for viruses and malware.
• The Scan section enables you to easily configure and start an on-demand scan.
Predefined profiles enable you to run a scan with already adapted standard
options. In the same way it is possible to adapt the scan for viruses and unwanted
programs to your personal requirements with the help of manual selection (not
saved) or by creating user-defined profiles.
• The Guard section displays information on scanned files, as well as other
statistical data, which can be reset at any time, and enables access to the report
file. More detailed information on the last virus or unwanted program detected
can be obtained practically "at the push of a button".
– Online protection: In Online protection you will find the components to
protect your computer system against viruses and malware from the Internet,
and against unauthorized network access.
• The MailGuard section shows you all the emails scanned by MailGuard, their
properties and other statistical data. You can also train the anti-spam filter and
exclude email addresses from future scanning for malware or spam. Emails can
also be deleted from the MailGuard buffer.
• The WebGuard section displays information on scanned URLs and detected
viruses, as well as other statistical data, which can be reset at any time and
enables access to the report file. More detailed information on the last virus or
unwanted program detected can be obtained practically "at the push of a button".
• The FireWall section enables you to configure the basic settings for the Avira
FireWall. In addition, the current data transfer rate and all active applications
using a network connection are displayed.
– Management: In Management you will find tools for isolating and managing
suspicious or infected files, and for planning recurring tasks.
• The Quarantine section contains the so-called quarantine manager. This is the
central point for files already placed in quarantine or for suspect files that you
would like to place in quarantine. It is also possible to send a selected file to the
Avira Malware Research Center by email.
• The Scheduler section enables you to configure scheduled scanning and update
jobs as well as backup jobs and to adapt or delete existing jobs.
– Tools: In Tools you will find other data security tools.
• In the Backup section, you can create backups of your data easily and quickly and
initiate backup jobs.
Page 22
Overview of Premium Security Suite
17
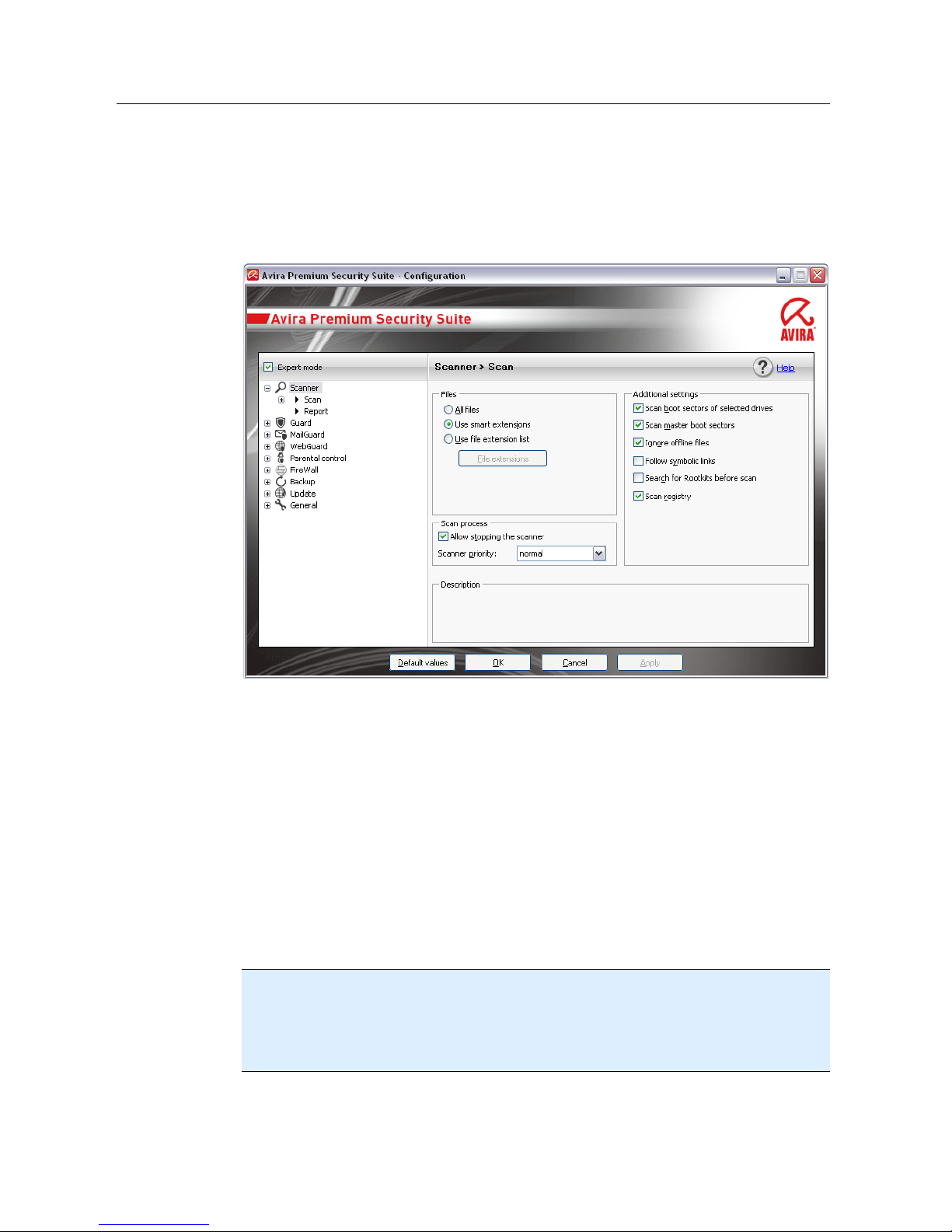
5.1.2 Configuration
You can define settings for your AntiVir program in the Configuration. After
installation, your AntiVir program is configured with standard settings, ensuring
optimal protection for your computer system. However, your computer system or your
specific requirements for your AntiVir program may mean you need to adapt the
protective components of the program.
The Configuration opens a dialog box: You can save your configuration settings via the
OK or Apply buttons, delete your settings by clicking the Cancel button or restore your
default configuration settings using the Default values button. You can select individual
configuration sections in the left-hand navigation bar.
Accessing the Configuration
You have several options for accessing the configuration:
– via the Windows control panel.
– via the Windows Security Center - from Windows XP Service Pack 2.
– Via the Tray Icon of your AntiVir program.
– in the Control Center via the menu item Extras | Configuration.
– in the Control Center via the Configuration button.
Note
If you are accessing configuration via the Configuration button in the Control Center,
go to the Configuration register of the section which is active in the Control Center.
Expert mode must be activated to select individual configuration registers. In this case, a
dialog appears asking you to activate expert mode.
Configuration operation
Page 23

Avira Premium Security Suite
18
Navigate in the configuration window as you would in Windows Explorer:
Click an entry in the tree structure to display this configuration section in the detail
window.
Click the plus symbol in front of an entry to expand the configuration section and
display configuration subsections in the tree structure.
To hide configuration subsections, click on the minus symbol in front of the
expanded configuration section.
Note
To enable or disable Configuration options and use the buttons, you can also use the
following key combinations: [Alt] + underlined letter in the option name or button
description.
Note
All configuration sections are only displayed in expert mode. Activate expert mode to
view all configuration sections. Expert mode can be protected by a password that must
be defined during activation.
If you want to confirm your Configuration settings:
Click OK.
The configuration window is closed and the settings are accepted.
- OR -
Click Accept.
The settings are applied. The configuration window remains open.
If you want to finish configuration without confirming your settings:
Click Cancel.
The configuration window is closed and the settings are discarded.
If you want to restore all configuration settings to default values:
Click Restore defaults.
All settings of the configuration are restored to default values. All amendments
and custom entries are lost when default settings are restored.
Overview of configuration options
The following configuration options are available:
– Scanner: Configuration of on-demand scan
Scan options
Action on detection
File scan options
On-demand scan exceptions
On-demand scan heuristics
Report function setting
– Guard: Configuration of on-access scan
Scan options
Action on detection
Page 24

Overview of Premium Security Suite
19
On-access scan exceptions
On-access scan heuristics
Report function setting
– MailGuard: Configuration of MailGuard
Scan options: Enable the monitoring of POP3 accounts, IMAP accounts, outgoing
emails (SMTP)
Actions on malware
MailGuard scan heuristics
AntiBot function: Permitted SMTP servers, permitted email senders
MailGuard scan exceptions
Configuration of cache, empty cache
Configuration of the anti-spam training database, empty training database
Configuration of a footer in sent emails
Report function setting
– WebGuard: Configuration of WebGuard
Scan options, enabling and disabling the WebGuard
Action on detection
Blocked access: Unwanted file types and MIME types, Web filter for known
unwanted URLS (malware, phishing, etc.)
WebGuard scan exceptions: URLs, file types, MIME types
WebGuard heuristics
Parental control function: Role-based filter and role-based time limitation of
Internet use
Report function setting
– FireWall: Configuration of the FireWall
Adapter rule setting
User-defined application rule settings
List of trusted providers (exceptions for network access by applications)
Expanded settings: Timeout for rules, lock Windows host file, stop Windows
FireWall, notifications
Popup settings (alerts for network access by applications)
– Backup:
Backup component setting (incremental backup, scan for viruses during backup)
Exceptions: Defining files for saving
Report function setting
– General:
Extended risk categories for on-demand and on-access scan
Password protection for access to the Control Center and the Configuration
Page 25

Avira Premium Security Suite
20
Security: Update status display, complete system scan status display, product
protection
WMI: Enable WMI support
Event log configuration
Configuration of report functions
Setting of directories used
Update: Configuration of connection to download server, set-up of product updates
Configuration of acoustic alerts when malware is detected
5.1.3 Tray icon
After installation, you will see the tray icon of your AntiVir program in the system tray
of the taskbar:
Icon Description
AntiVir Guard is enabled and the FireWall is enabled
AntiVir Guard is disabled and the FireWall is disabled
The tray icon displays the status of the Guard and the FireWall service.
Central functions of your AntiVir program can be quickly accessed via the context menu
of the tray icon. To open the context menu, click the tray icon with the right-hand mouse
button.
Entries in the context menu
– Activate AntiVir Guard: Enables or disables the AntiVir Guard.
– Enable AntiVir MailGuard:. Enables or disables the AntiVir MailGuard.
– Enable AntiVir WebGuard: Enables or disables the AntiVir WebGuard.
– FireWall:
– Enable FireWall: Enables or disables the FireWall
– Block all traffic: Enabled: Blocks all data transfers except transfers to the host
computer system (Local Host/IP 127.0.0.1).
– Enable game mode: Enables or disables the mode:
Enabled: When activated, all defined adapter and application rules apply.
Applications for which no rule is defined are permitted network access and no
pop-up window is opened.
– Start AntiVir: Opens the Control Center.
– Configure AntiVir: Opens the Configuration
– Start update Starts an update.
– Help: opens the Online Help.
– About Premium Security Suite: Opens a dialog box with information on your
AntiVir program: Product information, Version information, License
information.
– Avira on the Internet: Opens the Avira web portal on the Internet. The
condition for this is that you have an active connection to the Internet.
Page 26

Overview of Premium Security Suite
21
5.2 How to...?
5.2.1 Activate product
To activate your AntiVir product, you have the following options:
• Activation with a valid full license
To activate the program with a full license, you need a valid activation key, which
holds data of the license you have purchased. You have received the activation
key from us either by email or it has been printed on the product packaging.
• Activation with an evaluation license
Your AntiVir program is activated with an automatically generated evaluation
license, with which you can test the AntiVir program with its complete range of
function for a limited period of time.
Note
For product activation or for a test license you need an active Internet link.
If no connection can be established to the servers of Avira GmbH, please check the
settings of the firewall used: Connections via the HTTP protocol and port 80 (web
communication) and via the encryption protocol SSL and port 443 are used for product
activation. Make sure that your firewall does not block incoming and outgoing data. First
of all check whether you can access web pages with your web browser.
The following describes how to activate your AntiVir program:
If you have not yet installed your AntiVir program:
Install your AntiVir program.
During the installation process you will be asked to select an activation option
• Activate product
= Activation with a valid full license
• Test product
= Activation with an evaluation license
Enter the activation key for an activation with a full license.
Acknowledge the selection of the activation procedure by clicking Next.
If and when necessary, enter your personal data for registration and acknowledge by
clicking Next.
Your license data will be displayed in the next window. Your AntiVir program has
been enabled.
Continue to install.
If you have already installed your AntiVir program:
In the Control Center, select the menu item Help:: License management.
The license wizard opens, in which you can select an activation option. The next
steps of product activation are identical with the procedure described above.
Page 27
Avira Premium Security Suite
22
5.2.2 Perform automatic updates
To create a job with the AntiVir Scheduler to update your AntiVir program automatically:
In the Control Center, select the section Management :: Scheduler.
Click the
Create new job with the wizard icon.
The dialog box Name and description of job appears.
Give the job a name and, where appropriate, a description.
Click Next.
The dialog box Type of job is displayed.
Select Update job from the list.
Click Next.
The dialog box Time of job appears.
Select a time for the update:
• Immediately
• Daily
• Weekly
• Interval
• Single
• Login
Note
We recommend regular and frequent updates. The recommended update interval is: 2
hours.
Where appropriate, specify a date according to the selection.
Where appropriate, select additional options (availability depends on type of job):
• Also start job when Internet connection is established
In addition to the defined frequency, the job is performed when an Internet
connection is set up.
• Repeat job if the time has already expired
Past jobs are performed that could not be performed at the required time, for
example because the computer was switched off.
Click Next.
The dialog box Select display mode appears.
Select the display mode of the job window:
• Minimize: progress bar only
• Maximize: Entire job window
• Hide: No job window
Click Finish.
Your newly created job appears on the start page of the Manager :: Scan section
with the status activated (check mark).
Where appropriate, deactivate jobs that are not to be performed.
Page 28

Overview of Premium Security Suite
23
Use the following icons to further define your jobs:
View properties of a job
Modify job
Delete job
Start job
Stop job
5.2.3 Start a manual update
You have various options for starting an update manually: When an update is started
manually, the virus definition file and scan engine are always updated. A product update
can only take place if you have activated the option Download and automatically
install product updates in the configuration under General :: Update
To start an update of your AntiVir program manually:
With the right-hand mouse button, click the AntiVir tray icon in the taskbar.
A context menu appears.
Select Start update.
The Updater dialog box appears.
- OR -
In the Control Center, select the section Overview :: Status.
In the Last update field, click on the Start update link.
The Updater dialog box appears.
- OR -
In the Control Center, in the Update menu, select the menu command Start update.
The Updater dialog box appears.
Note
We recommend regular automatic updates. The recommended update interval is: 2
hours.
Note
You can also carry out a manual update directly via the Windows security center.
5.2.4 On-demand scan: Using a scan profile to scan for viruses and
malware
A scan profile is a set of drives and directories to be scanned.
The following options are available for scanning via a scan profile:
– Use predefined scan profile
if the predefined scan profile corresponds to your requirements.
– Customize and apply scan profile (manual selection)
Page 29

Avira Premium Security Suite
24
if you want to scan with a customized scan profile.
– Create and apply new scan profile
if you want to create your own scan profile.
Depending on the operating system, various icons are available for starting a scan
profile:
– In Windows XP and 2000:
This icon starts the scan via a scan profile.
– In Windows Vista:
In Microsoft Windows Vista, the Control Center only has limited rights at the
moment, e.g. for access to directories and files. Certain actions and file accesses can
only be performed in the Control Center with extended administrator rights. These
extended administrator rights must be granted at the start of each scan via a scan
profile.
This icon starts a limited scan via a scan profile. Only directories and files that
Windows Vista has granted access rights to are scanned.
This icon starts the scan with extended administrator rights. After
confirmation, all directories and files in the selected scan profile are scanned.
To scan for viruses and malware with a scan profile:
Go to Control Center and select the section Local protection::Scan.
Predefined scan profiles appear.
Select one of the predefined scan profiles.
-OR-
Adapt the scan profile Manual selection.
-OR-
Create a new scan profile
Click the icon (Windows XP:
or Windows Vista: ).
The Luke Filewalker window appears and an on-demand scan is started.
When the scan is completed, the results are displayed.
If you want to adapt a scan profile:
In the scan profile, expand Manual Selection the file tree so that all the drives and
directories you want to scan are open.
• Click the + icon: The next directory level is displayed.
• Click the - icon: The next directory level is hidden.
Highlight the nodes and directories you want to scan by clicking on the
relevantboxof the appropriate directory level.
The following options are available for selecting directories:
• Directory, including sub-directories (black check mark)
Page 30

Overview of Premium Security Suite
25
• Directory excluding sub-directories (green check mark)
• Sub-directories of one directory only (grey check mark, sub-directories have black
check marks)
• No directory (no check mark)
If you want to create a new scan profile:
Click the icon
Create new profile.
The profile New profile appears below the profiles previously created.
Where appropriate, rename the scan profile by clicking on the icon
.
Highlight the nodes and directories to be saved by clicking the check box of the
respective directory level.
The following options are available for selecting directories:
• Directory, including sub-directories (black check mark)
• Directory excluding sub-directories (green check mark)
• Sub-directories of one directory only (grey check mark, sub-directories have black
check marks)
• No directory (no check mark)
5.2.5 On-demand scan: Scan for viruses and malware using
Dragamp;Drop
To scan for viruses and malware systematically using Drag&Drop:
The Control Center of your AntiVir program has been opened.
Highlight the file or directory you want to scan.
Use the left-hand mouse button to drag the highlighted file or directory into the
Control Center.
The Luke Filewalker window appears and an on-demand scan is started.
When the scan is completed, the results are displayed.
5.2.6 On-demand scan: Scan for viruses and malware via the context
menu
To scan for viruses and malware systematically via the context menu:
Click with the right-hand mouse button (e.g. in Windows Explorer, on the desktop or
in an open Windows directory) on the file or directory you want to scan.
The Windows Explorer context menu appears.
Select Scan selected files with AntiVir in the context menu.
The Luke Filewalker window appears and an on-demand scan is started.
When the scan is completed, the results are displayed.
Page 31

Avira Premium Security Suite
26
5.2.7 On-demand scan: Automatically scan for viruses and malware
Note
After installation, the scan job Full system scan is created in the Scheduler: A complete
system scan is automatically performed at a recommended interval.
To create a job to automatically scan for viruses and malware:
In the Control Center, select the section Management:: Scheduler.
Click the icon
.
The dialog box Name and description of job appears.
Give the job a name and, where appropriate, a description.
Click Next.
The dialog box Type of job appears.
Select Scan job.
Click Next.
The dialog box Select profile appears.
Select the profile to be scanned.
Click Next.
The dialog box Time of job appears.
Select a time for the scan:
• Immediately
• Daily
• Weekly
• Interval
• Single
• Login
Where appropriate, specify a date according to the selection.
Where appropriate, select the following additional options (availability depends on
job type):
• Repeat job if the time has already expired
Past jobs are performed that could not be performed at the required time, for
example because the computer was switched off.
Click Next.
The dialog box Select display mode appears.
Select the display mode of the job window:
• Minimize: progress bar only
• Maximize: Entire job window
• Hide: No job window
Select the Shut down computer option if you want the computer to shut down
automatically when the scan is finished. This option is only available if the display
mode is set to minimized or maximized.
Page 32

Overview of Premium Security Suite
27
Click Finish.
Your newly created job appears on the start page of the Manager :: Scheduler
section with the status activated (check mark).
Where appropriate, deactivate jobs that are not to be performed.
Use the following icons to further define your jobs:
View properties of a job
Modify job
Delete job
Start job
Stop job
5.2.8 On-demand scan: Targeted scan for Rootkits and active malware
To scan for active rootkits, use the predefined scan profile Scan for Rootkits and active
malware.
To scan for active rootkits systematically:
Go to Control Center and select the section Local protection:: Scanner.
Predefined scan profiles appear.
Select the predefined scan profile Scan for Rootkits and active malware.
Where appropriate, highlight other nodes and directories to be scanned by clicking
the check box of the directory level.
Click the icon (Windows XP:
or Windows Vista: ).
The Luke Filewalker window appears and an on-demand scan is started.
When the scan is completed, the results are displayed.
5.2.9 React to detected viruses and malware
For the individual protection components of your AntiVir program, you can define how
your AntiVir program reacts to a detected virus or unwanted program in the
Configuration under the section Action on detection.
No configurable action options are available for the ProActiv component of the Guard:
Notification of a detection is always given in the Guard: Suspicious application behavior
window.
Action options for the Scanner:
– Interactive
Page 33

Avira Premium Security Suite
28
In interactive action mode, the results of the Scanner scan are displayed in a dialog
box. This option is enabled as the default setting.
In the case of Scanner scan, you will receive an alert with a list of the affected files
when the scan is complete. You can use the content-sensitive menu to select an
action to be executed for the various infected files. You can execute the standard
actions for all infected files or cancel the Scanner.
– Automatic
In automatic action mode, when a virus or unwanted program is detected the action
you selected in this area is executed automatically.
Action options for the Guard:
– Interactive
In interactive action mode, data access is denied and a desktop notification is
displayed. In the desktop notification you can remove the malware detected or
transfer the malware to the Scanner component using the Details button for further
virus management. The Scanner opens a window containing notification of the
detection, which gives you various options for managing the affected file via a
context menu (see Detection::Scanner):
– Automatic
In automatic action mode, when a virus or unwanted program is detected, the action
you selected in this area is executed automatically.
Action options for MailGuard, WebGuard:
– Interactive
In interactive action mode, if a virus or unwanted program is detected, a dialog box
appears in which you can select what to do with the infected object. This option is
enabled as the default setting.
– Automatic
In automatic action mode, when a virus or unwanted program is detected the action
you selected in this area is executed automatically.
In interactive action mode, you can react to detected viruses and unwanted programs by
selecting an action for the infected object in the alert and executing the selected action
by clicking Confirm.
The following actions for handling infected objects are available for selection:
Note
Which actions are available for selection depends on the operating system, the
protection components (AntiVir Guard, AntiVir Scanner, AntiVir MailGuard, AntiVir
WebGuard) reporting the detection, and the type of malware detected.
Actions of the Scanner and the Guard (not ProActiv detections):
– Repair
The file is repaired.
This option is only available if the infected file can be repaired.
– Move to quarantine
The file is packaged into a special format (*.qua) and moved to the Quarantine
directory INFECTED on your hard disk, so that direct access is no longer possible.
Files in this directory can be repaired in Quarantine at a later data or, if necessary,
sent to Avira GmbH.
Page 34

Overview of Premium Security Suite
29
– Delete
The file will be deleted. This process is much quicker than overwrite and delete. If a
boot sector virus is detected, this can be deleted by deleting the boot sector. A new
boot sector is written.
– Overwrite and delete
The file is overwritten with a default template and then deleted. It cannot be
restored.
– Rename
The file is renamed with a *.vir extension. Direct access to these files (e.g. with
double-click) is therefore no longer possible. Files can be repaired and given their
original name at a later time.
– Ignore
No further action is taken. The infected file remains active on your computer.
Warning
This could result in loss of data and damage to the operating system! Only select the
Ignore option in exceptional cases.
– Always ignore
Action option for Guard detections: No further action is taken by Guard. Access to
the file is permitted. All further access to this file is permitted and no further
notifications will be provided until the computer is restarted or the virus definition
file is updated.
– Copy to quarantine
Action option for a rootkit detection: The detection is copied to quarantine.
– Repair boot sector | Download repair tool
Action options when infected boot sectors are detected: A number of options are
available for repairing infected diskette drives. If your AntiVir program is unable to
perform the repair, you can download a special tool for detecting and removing boot
sector viruses.
Note
If you carry out actions on running processes, the processes in question are terminated
before the actions are performed.
Actions of the Guard for detections made by the ProActiv component
(notification of suspicious actions of an application):
– Trusted program
The application continues to run. The program is added to the list of permitted
applications and is excluded from monitoring by the ProActiv component. When
adding to the list of permitted applications, the monitoring type is set to Content.
This means that the application is only excluded from monitoring by the ProActiv
component if the content remains unchanged (see
Configuration::Guard::ProActiv::Application filter: Permitted applications).
– Block program once
The application is blocked, i.e. the application is terminated. The actions of the
application continue to be monitored by the ProActiv component.
– Always block this program
Page 35

Avira Premium Security Suite
30
The application is blocked, i.e. the application is terminated. The program is added to
list of blocked applications and can no longer be run (see
Configuration::Guard::ProActiv::Application filter: Applications to be blocked).
– Ignore
The application continues to run. The actions of the application continue to be
monitored by the ProActiv component.
MailGuard actions: Incoming emails
– Move to quarantine
The email including all attachments is moved to quarantine. The affected email is
deleted. The body of the text and any attachments of the email are replaced by a
default text.
– Delete
The affected email is deleted. The body of the text and any attachments of the email
are replaced by a default text.
– Delete attachment
The infected attachment is replaced by a default text. If the body of the email is
affected, it is deleted and also replaced by a default text. The email itself is delivered.
– Move attachment to quarantine
The infected attachment is placed in quarantine and then deleted (replaced by a
default text). The body of the email is delivered. The affected attachment can later be
delivered via the quarantine manager.
– Ignore
The affected email is delivered.
Warning
This could allow viruses and unwanted programs to access your computer system. Only
select the Ignoreoption in exceptional cases. Disable the preview in your mail client,
never open any attachments with a double click!
MailGuard actions: Outgoing emails
– Move mail to quarantine (do not send)
The email, together with all attachments, is copied to Quarantine and is not sent.
The email remains in the outbox of your email client. You receive an error message in
your email program. All other emails sent from your email account will be scanned
for malware.
– Block sending of mails (do not send)
The email is not sent and remains in the outbox of your email client. You receive an
error message in your email program. All other emails sent from your email account
will be scanned for malware.
– Ignore
The affected email is sent.
Warning
Viruses and unwanted programs can penetrate the computer system of the email
recipient in this way.
WebGuard actions:
Page 36

Overview of Premium Security Suite
31
– Deny access
The website requested from the web server and/or any data or files transferred are
not sent to your web browser. An error message to notify you that access has been
denied is displayed in the web browser.
– Move to quarantine
The website requested from the web server and/or any data or files transferred are
moved to quarantine. The affected file can be recovered from quarantine manager if
it has an informative value or - if necessary - sent to the Avira Malware Research
Center.
– Ignore
The website requested from the web server and/or the data and files that were
transferred are forwarded on by WebGuard to your web browser.
Warning
This could allow viruses and unwanted programs to access your computer system. Only
select the Ignoreoption in exceptional cases.
Note
We recommend that you move any suspicious file that cannot be repaired to quarantine.
Note
You can also send files reported by the heuristic to us for analysis.
For example, you can upload these files to our website:http://www.avira.com/sampleupload
You can identify files reported by the heuristic from the designation HEUR/ or
HEURISTIC/ that prefixes the file name, e.g.: HEUR/testfile.*.
5.2.10 Quarantine: Handling quarantined files (*.qua)
To handle quarantined files:
In the Control Center, select the section Management :: Quarantine section.
Check which files are involved, so that, if necessary, you can reload the original back
onto your computer from another location.
If you want to see more information on a file:
Highlight the file and click on
.
The dialog box Properties appears with more information on the file.
If you want to rescan a file:
Scanning a file is recommended if the virus definition file of your AntiVir program has
been updated and a false positive report is suspected. This enables you to confirm a false
positive with a rescan and restore the file.
Highlight the file and click on
.
The file is scanned for viruses and malware using the on-demand scan settings.
After the scan, the dialog Scan statistics appears which displays statistics on the
status of the file before and after the rescan.
To delete a file:
Page 37

Avira Premium Security Suite
32
Highlight the file and click on
.
If you want to upload the file to a Avira Malware Research Center web server for analysis:
Highlight the file you want to upload.
Click on
.
A dialog opens with a form for inputting your contact data.
Enter all the required data.
Select a type: Suspicious file or False positive.
Click OK.
The file is uploaded to a Avira Malware Research Center web server in
compressed form.
Note
In the following cases, analysis by the Avira Malware Research Center is recommended:
Heuristic hits (Suspicious file): During a scan, a file has been classified as suspicious
by your AntiVir program and moved to quarantine: Analysis of the file by the Avira
Malware Research Center has been recommended in the virus detection dialog box or in
the report file generated by the scan.
Suspicious file: You consider a file to be suspicious and have therefore moved this file
to quarantine, but a scan of the file for viruses and malware is negative.
False positive: You assume that a virus detection is a false positive: Your AntiVir
program reports a detection in a file, which is very unlikely to have been infected by
malware.
Note
The size of the files you upload is limited to 20 MB uncompressed or 8 MB compressed.
Note
You can only upload one file at a time.
If you want to copy a quarantined object from quarantine to another directory:
Highlight the quarantined object and click on
.
A scan dialog opens from which you can select a directory.
Select a directory where you want to save a copy of the quarantined object and
confirm your selection.
The selected quarantined object is saved to the selected directory.
Note
The quarantined object is not identical to the restored file. The quarantined object is
encrypted and cannot be executed or read in its original format.
If you want to export the properties of a quarantined object to a text file:
Highlight the quarantined object and click on
.
A text file opens containing the data from the selected quarantined object.
Save the text file.
You can also restore the files in quarantine:
– see Chapter: Quarantine: Restoring files in quarantine
Page 38

Overview of Premium Security Suite
33
5.2.11 Quarantine: Restore the files in quarantine
Different icons control the restore procedure, depending on the operating system:
– In Windows XP and 2000:
This icon restores the files to their original directory.
This icon restores the files to a directory of your choice.
– In Windows Vista:
In Microsoft Windows Vista, the Control Center only has limited rights at the
moment, e.g. for access to directories and files. Certain actions and file accesses can
only be performed in the Control Center with extended administrator rights. These
extended administrator rights must be granted at the start of each scan via a scan
profile.
This icon restores the files to a directory of your choice.
This icon restores the files to their original directory. If extended administrator
rights are necessary to access this directory, a corresponding request appears.
To restore files in quarantine:
Warning
This could result in loss of data and damage to the operating system of the computer!
Only use the function Restore selected object in exceptional cases. Only restore files that
could be repaired by a new scan.
File rescanned and repaired.
In the Control Center, select the section Management :: Quarantine section.
Note
Emails and email attachments can only be restored using the option if the file
extension is *.eml.
To restore a file to its original location:
Highlight the file and click the icon (Windows 2000/XP:
, Windows Vista ).
This option is not available for emails.
Note
Emails and email attachments can only be restored using the option if the file
extension is *.eml.
A message appears asking if you want to restore the file.
Click Yes.
The file is restored to the directory it was in before it was moved to quarantine.
To restore a file to a specified directory:
Highlight the file and click on
.
A message appears asking if you want to restore the file.
Page 39

Avira Premium Security Suite
34
Click Yes.
The Windows default window for selecting the directory appears.
Select the directory to restore the file to and confirm.
The file is restored to the selected directory.
5.2.12 Quarantine: Move suspicious files to quarantine
To move a suspect file to quarantine manually:
In the Control Center, select the section Management :: Quarantine section.
Click on
.
The Windows default window for selecting a file appears.
Select the file and confirm.
The file is moved to quarantine.
You can scan files in quarantine with the AntiVir Scanner:
• see Chapter: Quarantine: Handling quarantined files (*.qua)
5.2.13 Scan profile: Amend or delete file type in a scan profile
To stipulate additional file types to be scanned or exclude specific file types from the
scan in a scan profile (only possible for manual selection and customized scan profiles):
In the Control Center, go to the Local protection:: Scan section.
With the right-hand mouse button, click on the scan profile you want to edit.
A context menu appears.
Select File filter.
Expand the context menu further by clicking on the small triangle on the right-hand
side of the context menu.
The entries Default, Scan all files and User-defined appear.
Select User-defined.
The File extensions dialog box appears with a list of all file types to be scanned
with the scan profile.
If you want to exclude a file type from the scan:
Highlight the file type and click Delete.
If you want to add a file type to the scan:
Highlight the file type.
Click Add and enter the file extension of file type into the input box.
Use a maximum of 10 characters and do not enter the leading dot. Wildcards (*
and ? ) are allowed as replacements.
5.2.14 Scan profile: Create desktop shortcut for scan profile
You can start an on-demand scan directly from your desktop via a desktop shortcut to a
scan profile without accessing your AntiVir program’s Control Center.
To create a desktop shortcut to the scan profile:
Page 40

Overview of Premium Security Suite
35
In the Control Center, go to the Local protection:: Scan section.
Select the scan profile for which you want to create a shortcut.
Click the icon
.
The desktop shortcut is created.
5.2.15 Events: Filter events
Events that have been generated by program components of your AntiVir program are
displayed in the Control Center under Overview::Events (analogous to the event
display of your Windows operating system). The program components are:
– Updater
– Scheduler
– Guard
– MailGuard
– Scanner
– FireWall
– WebGuard
– Backup
– Helper Service
– ProActiv
The following event types are displayed:
– Information
– Warning
– Error
– Detection
To filter displayed events:
In the Control Center, select the section Overview :: Events.
Check the box of the program components to display the events of the activated
components.
- OR -
Uncheck the box of the program components to hide the events of the deactivated
components.
Check the event type box to display these events.
- OR -
Uncheck the event type box to hide these events.
5.2.16 MailGuard: Exclude email addresses from scan
To define which email addresses (senders) are excluded from the MailGuard scan (white
listing):
Go to Control Center and select the section Online protection :: MailGuard.
Page 41

Avira Premium Security Suite
36
The list shows incoming emails.
Highlight the email you want to exclude from the MailGuard scan.
Click the appropriate icon to exclude the email from the MailGuard scan:
In future, the selected email address will no longer be scanned for viruses and
unwanted programs.
In the future, the selected email address will no longer be scanned for spam.
The email sender address is included in the exclusion list and no longer scanned
for viruses, malware or spam .
Warning
Only exclude email addresses from the MailGuard scan if the senders are completely
trustworthy.
Note
In the Configuration, under MailGuard :: General :: Exceptions, you can add other email
addresses to the exclusion list or remove email addresses from the exclusion list.
5.2.17 MailGuard: Train the anti-spam module
The anti-spam module contains a training database. Your individual categorization
criteria are recorded in this training database. Over time, the internal filters, algorithms
and evaluation criteria for spam adapt themselves to your personal criteria.
To categorize emails for the training database:
Go to Control Center and select the section Online protection:: MailGuard.
The list shows incoming emails.
Highlight the email you want to categorize.
Click the appropriate icon to identify the email as either spam
or wanted, i.e.
'good' Email
.
The email is entered into the training database and applied to the next spam
recognition process.
Note
You can delete the training database in the configuration under MailGuard :: General ::
AntiSpam.
5.2.18 FireWall: Select the security level for the FireWall
There are various security levels to choose from. Depending on which you choose, you
have different adapter rule configuration options.
The following security levels are available:
– Low
• Flooding and port scan are detected.
– Medium
Page 42

Overview of Premium Security Suite
37
• Suspicious TCP and UDP packages are discarded.
• Flooding and port scan are prevented.
– High
• Computer is not visible on the network.
• Connections from outside are blocked.
• Flooding and port scan are prevented.
– User
• User-defined rules: If this security level is selected, the program automatically
recognizes that the adapter rules have been modified.
Note
The default security level setting for all predefined rules of the Avira FireWall is High
To define the security level for the FireWall:
Go to the Control Center and select the section Online protection :: FireWall.
Move the slider to the required security level.
The selected security level is applied immediately.
5.2.19 Backup: Create backups manually
The backup tool in the Control Center lets you back up your personal data quickly and
easily. In Avira Backup you can create so-called mirror backups which let you save and
store your most recent data using a minimum of resources. Avira Backup lets you scan
your data for viruses and malware during the backup process. Infected files are not
saved.
Note
In contrast to version backups, mirror backups do not save individual backup versions.
The mirror backup contains the data stock at the time of the last backup. If, however,
files from the saved data stock are deleted, no match takes place in the following backup,
i.e. the deleted files are still available in the backup.
Note
With the default settings of Avira Backup only modified files are saved, and files are
scanned for viruses and malware. You can change these settings in the configuration
under Backup::Settings.
To save your data using the backup tool:
In the Control Center, select the Tools::Backup section.
Preset backup profiles appear.
Select one of the preset backup profiles.
-OR-
Adapt the backup profile Manual selection.
-OR-
Create a new backup profile
Enter a save location for the selected profile in the Destination directory box.
The save location for the backup can be a directory on your computer, on a
connected network drive or a removable disk such as a USB stick or diskette.
Page 43

Avira Premium Security Suite
38
Click the icon
.
The window Avira Backup appears and the backup starts. The status and results
of the backup are displayed in the backup window.
If you want to modify a backup profile:
In the scan profile, expand the Manual Selection file tree so that all drives and
directories to be saved are open:
• Click the + icon: The next directory level is displayed.
• Click the - icon: The next directory level is hidden.
Highlight the nodes and directories to be saved by clicking the box of the respective
directory level:
The following options are available for selecting directories:
• Directory, including sub-directories (black check mark)
• Directory excluding sub-directories (green check mark)
• Sub-directories of one directory only (grey check mark, sub-directories have black
check marks)
• No directory (no check mark)
If you want to create a new backup profile:
Click the icon
Create new profile.
The profile New profile appears below the profiles previously created.
Where appropriate, give the backup profile a name by clicking on the icon
.
Highlight the nodes and directories to be saved by clicking the check box of each
directory level.
The following options are available for selecting directories:
• Directory, including sub-directories (black check mark)
• Directory excluding sub-directories (green check mark)
• Sub-directories of one directory only (grey check mark, sub-directories have black
check marks)
• No directory (no check mark)
5.2.20 Backup: Create automatic data backups
This shows you how to initiate a job to create automatic data backups:
In the Control Center, select the Management::Scheduler section.
Click the icon
.
The dialog box Name and description of job appears.
Give the job a name and, where appropriate, a description.
Click Next.
The dialog box Type of job appears.
Select Backup job.
Page 44

Overview of Premium Security Suite
39
Click Next.
The dialog box Select profile appears.
Select the profile to be scanned.
Note
Only backup profiles for which a save location has been stipulated are displayed.
Click Next.
The dialog box Time of job appears.
Select a time for the scan:
• Immediately
• Daily
• Weekly
• Interval
• Single
• Login
• Plug&Play
A backup is always created for the Plug&Play event if the removable disk selected
as the save location of the backup profile is connected to the computer. The
backup event Plug&Play requires a USB stick to be entered as a save location.
Where appropriate, specify a date according to the selection.
Where appropriate, select the following additional options (availability depends on
job type):
• Repeat job if the time has already expired
Past jobs are performed that could not be performed at the required time, for
example because the computer was switched off.
Click Next.
The dialog box Select display mode appears.
Select the display mode of the job window:
• Minimize: progress bar only
• Maximize: entire backup window
• Hide: no backup window
Click Finish.
Your newly created job appears on the start page of the Manager :: Scheduler
section with the status activated (check mark).
Where appropriate, deactivate jobs that are not to be performed.
Use the following icons to further define your jobs:
View properties of a job
Modify job
Delete job
Page 45

Avira Premium Security Suite
40
Start job
Stop job
Page 46

41
Page 47

Avira Premium Security Suite
42
6 Scanner
With the Scanner component, you can carry out targeted scans (on-demand scans) for
viruses and unwanted programs. The following options are available for scanning for
infected files:
– On-demand scan via context menu
The on-demand-scan via the context menu (right-hand mouse button - entry
Scan selected files with AntiVir) is recommended if, for example, you wish to
scan individual files and directories. Another advantage is that it is not necessary
to first start the Control Center for an on-demand scan via the context menu.
– On-demand scan via drag & drop
When a file or directory is dragged into the program window of the Control
Center, the Scanner scans the file or directory and all sub-directories it contains.
This procedure is recommended if you wish to scan individual files and
directories that you have saved, for example, on your desktop.
– On-demand scan via profiles
This procedure is recommended if you wish to regularly scan certain directories
and drives (e.g. your work directory or drives on which you regularly store new
files). You do not then need to select these directories and drives again for every
new scan, you simply select using the relevant profile.
– On-demand scan via the Scheduler
The Scheduler enables you to carry out time-controlled scans.
Special processes are required when scanning for rootkits, boot sector viruses, and when
scanning active processes. The following options are available:
– Scan for rootkits via the scan profile Scan for Rootkits and active malware
– Scan active processes via the scan profile Active processes
– Scan for boot sector viruses via the menu command Scan for boot sector
viruses in the Extras menu
Page 48

43
7 Updates
The effectiveness of anti-virus software depends on how up-to-date the program is, in
particular the virus definition file and the scan engine. To carry out regular updates, the
Updater component is integrated into your AntiVir. The Updater ensures that your
AntiVir program is always up-to-date and able to deal with the new viruses that appear
every day. Updater updates the following components:
– Virus definition file:
The virus definition file contains the virus patterns of the harmful programs which
are used by your AntiVir program to scan for viruses and malware and repair
infected objects.
– Scan engine:
The scan engine contains the methods used by your AntiVir program to scan for
viruses and malware.
– Program files (product update):
Update packages for product updates make extra functions available to the
individual program components.
An update checks whether the virus definition file and scan engine are up-to-date and if
necessary implements an update. Depending on the settings in the configuration, the
Updater also carries out a product update or informs you of the product updates
available. After a product update, you may have to restart your computer system. If only
the virus definition file and scan engine are updated, the computer does not have to be
restarted.
Note
For security reasons, the Updater checks whether the Windows hosts file of your
computer was altered, whether the Update URL, for example, was manipulated by
malware and is diverting the Updater to unwanted download sites. If the Windows hosts
file has been manipulated, this is shown in the Updater report file.
An update is automatically performed in the following interval: 2 hours. You can edit or
disable the automatic update through the configuration (Configuration::Update).
In the Control Center under Scheduler, you can create additional update jobs that are
performed by Updater at the specified intervals. You also have the option to start an
update manually:
– In the Control Center: in the Update menu and in the Status section
– via the context menu of the tray icon
Updates can be obtained from the Internet via a Web server of the manufacturer. The
existing network connection is the default connection to the download servers of Avira
GmbH. You can change this default setting in the Configuration under General :: Update.
Page 49

44
8 Avira FireWall :: Overview
Avira FireWall monitors and regulates incoming and outgoing data traffic on your
computer system and protects you from a wide range of attacks and threats from the
Internet: Incoming or outgoing data traffic or listening to ports will be allowed or denied
based on security guidelines. You will receive a desktop notification if Avira FireWall
denies network activity and thus blocks network connections. The following options are
available for Avira FireWall settings:
– by setting a security level in the Control Center
You can define a security level in the Control Center. The low, medium and high
security levels each contain several complementary security rules based on packet
filters. These security rules are saved as predefined adapter rules in the
Configuration under FireWall::Adapter rules.
– by saving actions in the Network event window
When an application first tries to create a network or Internet connection, the
Network Event popup window appears. The Network Event window allows the user to
choose whether the network activity of the application is allowed or denied. If the
Save Action for this application option is enabled, the action is created as an
application rule and is saved in the configuration under FireWall::Application Rules.
Saving the actions in the Network event window gives you a set of rules for the
network activities of applications.
Note
For applications from trusted providers, network access is allowed by default unless an
adapter rule prohibits network access. You have the option of removing providers from
the list of trusted providers.
– by creating adapter and application rules in the Configuration
You can alter predefined adapter rules or create new adapter rules in the
Configuration. The security level of the FireWall is automatically set to the value
User if you add or change adapter rules.
Application rules allow you to define monitoring rules specified for applications:
You can use simple application rules to define whether all network activities of a
software application are to be denied or allowed or whether they are to be handled by
means of the Network Event popup window.
In the advanced configuration of the Application rules setting you can define different
packet filters for an application, which are executed as specified application rules.
Note
There are two different modes for application rules: Privileged and Filtered. For
application rules in filtered mode, the relevant adapter rules are prioritized, i.e. relevant
adapter rules are executed after the application rule. It is therefore possible that network
access may be denied due to a high security level or corresponding adapter rules. For
application rules in privileged mode, adapter rules are ignored. If applications are allowed
in privileged mode, the application is always granted network access.
Page 50

45
9 Backup
There are various options available to you for creating a backup of your data:
Backup via the backup tool
You can use the backup tool to select or create backup profiles and start a backup of a
selected profile manually.
Backup via a backup job in Scheduler
Scheduler gives you the option of creating scheduled or event-controlled backup jobs.
Scheduler automatically executes the backup jobs. This process is particularly useful if
you want to make regular backups of specific data.
Page 51

46
10 FAQ, Tips
This chapter contains important information on troubleshooting and further tips on
using your AntiVir program.
see Chapter Troubleshooting
see Chapter Keyboard commands
see Chapter Windows Security Center
10.1 Help in case of a problem
Here you will find information on causes and solutions of possible problems.
– The error message The license file cannot be opened appears.
– AntiVir MailGuard does not work.
– There is no network connection available in a virtual machine (e.g. VMWare,
Virtual PC, ...) if Avira FireWall is installed on the host machine and the security
level of Avira FireWall is set to medium or high.
– Virtual Private Network (VPN) Connection is blocked, if the security level of
Avira FireWall is set to medium or high.
– An email sent via a TSL connection has been blocked by MailGuard.
– Webchat is not operational: Chat messages will not be displayed
The error message
The license file cannot be opened
appears.
Reason: The file is encrypted.
To activate the license, you do not need to open the file, but rather you save it in
the program directory.
The error message
Connection failed while downloading the file ...
appears
when attempting to start an update.
Reason: Your Internet connection is inactive. No connection to the web server on the
Internet can therefore be established.
Test whether other Internet services such as WWW or email work. If not, re-
establish the Internet connection.
Reason: The proxy server cannot be reached.
Check whether the login for the proxy server has changed and adapt it to your
configuration if necessary.
Reason: The update.exe file is not fully approved by your personal firewall.
Ensure that the update.exe file is fully approved by your personal firewall.
Otherwise:
Page 52

FAQ, Tips
47
Check your settings in the Configuration (expert mode) under
General::UpdateYour settings.
Viruses and malware cannot be moved or deleted.
Reason: The file was loaded by windows and is active.
Update your AntiVir product.
If you use the Windows XP operating system, deactivate System Restore.
Start the computer in Safe Mode.
Start the AntiVir program and the Configuration (expert mode).
Select Scanner::Scan::Files::All files and confirm the window with OK.
Start a scan of all local drives.
Start the computer in Normal Mode.
Carry out a scan in Normal Mode.
If no other viruses or malware have been found, activate System Restore if it is
available and to be used.
The status of the tray icon is disabled.
Reason: AntiVir Guard is disabled.
In the Control Center in the section Overview::Status in the AntiVir Guard area,
click on the Enable link.
Reason: AntiVir Guard is blocked by a firewall.
Define a general approval for AntiVir Guard in the configuration of your firewall.
AntiVir Guard only works with the address 127.0.0.1 (localhost). An Internet connection
is not established. The same applies to AntiVir MailGuard.
Otherwise:
Check the startup type of the AntiVir Guard service. If necessary, enable the
service: In the taskbar, select "Start | Settings | Control Panel". Start the configuration
panel "Services" with a double-click (under Windows 2000 and Windows XP the services
applet is located in the sub-directory "Administrative Tools"). Find the entry Avira
AntiVir Guard. "Automatic" must be entered as the startup type and "Started" as the
status. If necessary, start the service manually by selecting the relevant line and the
button "Start". If an error message appears, please check the event display.
The computer is extremely slow when I perform a data back-up.
Reason: During the backup procedure, AntiVir Guard scans all files being used by the
backup procedure.
Select Guard::Scan::Exceptions in the Configuration (expert mode) and enter the
process names of the back-up software.
My firewall reports AntiVir Guard and AntiVir MailGuard immediately after
activation.
Reason: Communication with AntiVir Guardand AntiVir MailGuardoccurs via the TCP/IP
Internet protocol. A firewall monitors all connections via this protocol.
Page 53

Avira Premium Security Suite
48
Define a general approval for AntiVir Guard and AntiVir MailGuard. AntiVir
Guard only works with the address 127.0.0.1 (localhost). An Internet connection is not
established. The same applies to AntiVir MailGuard.
AntiVir MailGuard does not work.
Please check correct functioning of AntiVir MailGuard with the aid of the following
checklists if problems occur with AntiVir MailGuard.
Checklist
Check whether your mail client logs in on the server via Kerberos, APOP or RPA.
These verification methods are currently not
supported.
Check whether your mail client reports to the server through SSL (also often
called TSL – Transport Layer Security). AntiVir MailGuard does not support SSL and
therefore terminates any encrypted SSL connections. If you want to use encrypted SSL
connections without having them protected by MailGuard, you will have to use a port
that is not monitored by MailGuard for the connection. The ports monitored by
MailGuard can be configured in the configuration under MailGuard::Scan.
Is the AntiVir MailGuard service active? If necessary, enable the service: In the
taskbar, select "Start | Settings | Control Panel". Start the configuration panel "Services"
with a double-click (under Windows 2000 and Windows XP the services applet is located
in the sub-directory "Administrative Tools"). Find the entry Avira AntiVir MailGuard.
"Automatic" must be entered as the startup type and "Started" as the status. If necessary,
start the service manually by selecting the relevant line and the button "Start". If an
error message appears, please check the event display. If this is not successful, you may
have to completely uninstall the AntiVir program via "Start | Settings | Control Panel |
Add or Remove Programs", restart the computer and then reinstall your AntiVir
program.
General
POP3 connections encrypted via SSL (Secure Sockets Layer, also frequently
referred to as TLS (Transport Layer Security)) cannot currently be protected and are
ignored.
Verification to the mail server is currently only supported via "passwords".
"Kerberos" and "RPA" are not currently supported.
Your AntiVir program does not check outgoing emails for viruses and unwanted
programs.
Note
We recommend regularly installing Microsoft updates to close any gaps in security.
There is no network connection available in a virtual machine (e.g. VMWare,
Virtual PC, ...) if Avira FireWall is installed on the host machine and the
security level of Avira FireWall is set to medium or high.
If Avira FireWall is installed on a computer on which a virtual machine (for example
VMWare, virtual PC, etc.) is also running, the firewall will block all network connections
for the virtual machine when the security level of the Avira FireWall is set to medium or
high. If the security level is set to low, the FireWall works as expected.
Page 54

FAQ, Tips
49
Reason: The virtual machine emulates a network card by means of software. This
emulation encapsulates the data packages of the guest system in special packages (UDP
packages) and routes them via the external gateway back to the host system. Avira
FireWall rejects these packages coming from outside, starting from security level
medium.
To avoid this behavior do the following:
Go to Control Center and select the section Online protection :: FireWall.
Click the Configuration link.
The Configuration dialog box is displayed. You are in the configuration section
Application rules.
Activate the Expert mode option.
Select the configuration section Adapter rules.
Click add rule.
Select UDP in the section Incoming rules.
Type the name of the rule in the Section Name of the rule .
Click OK.
Check if the rule is directly above the rule Deny all IP packets.
Warning
This rule is potentially dangerous because it will allow UDP packets without any filtering!
After working with the virtual machine change to your previous security level.
Virtual Private Network (VPN) Connection is blocked, if the security level of
Avira FireWall is set to medium or high.
Reason: This problem is caused by the last rule Deny all IP packets which discards all
packets that do not comply with any of the rules above it. The type of packages
dispatched by the VPN software (so-called GRE packets) do not fit into the other
categories and therefore they are filtered by this rule.
Replace the rule Deny all IP packets with two new rules which will deny the TCP and
UPD packets. In this way there is the possibility to allow packets of other protocols.
An email sent via a TSL connection has been blocked by MailGuard.
Reason: Transport Layer Security (TLS: encryption protocol for data transfers on the
Internet) is not supported by MailGuard at this time. The following options are available
for sending the email:
Use a different port from port 25, which is used by SMTP. This will bypass
monitoring by MailGuard.
Turn off the TSL encrypted connection and disable TSL support in your email
client.
Disable (temporarily) monitoring of outgoing emails by MailGuard in the
configuration under MailGuard::Scan.
Webchat is not operational: Chat messages are not displayed; data are being
loaded in the browser.
Page 55

Avira Premium Security Suite
50
This phenomenon may occur during chats, which are based on the HTTP protocol with
'transfer-encoding= chunked’.
Reason: WebGuard checks the data sent completely for viruses and undesired programs
first of all, before the data are loaded into the web browser. During a data transfer with
‘transfer-encoding= chunked’, WebGuard cannot determine the message length or the
data volume.
Enter the configuration of the URL of the web chats as an exception (see
Configuration: WebGuard::Exceptions).
10.2 Shortcuts
Keyboard commands - also called shortcuts - offer a fast possibility to navigate through
the program, to retrieve individual modules and to start actions.
Below we provide you with an overview of the available keyboard commands. Please find
further indications regarding the functionality in the corresponding chapter of the help.
10.2.1 In dialog boxes
Shortcut Description
Ctrl + Tab
Ctrl + Page
down
Navigation in the Control Center
Go to next section.
Ctrl + Shift +
Tab
Ctrl + Page up
Navigation in the Control Center
Go to previous section.
← ↑ → ↓
Navigation in the configuration sections
First, use the mouse to set the focus on a configuration
section.
Tab Change to the next option or options group.
Shift + Tab Change to the previous option or options group.
← ↑ → ↓
Change between the options in a marked drop-down list or
between several options in a group of options.
Space Activate or deactivate a check box, if the active option is a
check box.
Alt + underlined
letter
Select option or start command.
Alt + ↓
F4
Open selected drop-down list.
Esc Close selected drop-down list.
Cancel command and close dialog.
Page 56

FAQ, Tips
51
Enter Start command for the active option or button.
10.2.2 In the help
Shortcut Description
Alt + Space Display system menu.
Alt + Tab Shift between the help and the other opened windows.
Alt + F4 Close help.
Shift + F10 Display context menu of the help.
Ctrl + Tab Go to next section in the navigation window.
Ctrl + Shift +
Tab
Go to previous section in the navigation window.
Page up Change to the subject, which is displayed above in the
contents, in the index or in the list of the search results.
Page down Change to the subject, which is displayed below the current
subject in the contents, in the index or in the list of the search
results.
Page up
Page down
Browse through a subject.
10.2.3 In the Control Center
General
Shortcut Description
F1 Display help
Alt + F4 Close Control Center
F5 Refresh
F8 Open configuration
F9 Start update
Scan section
Shortcut Description
F2 Rename selected profile
F3 Start scan with the selected profile
F4 Create desktop link for the selected profile
Ins Create new profile
Del Delete selected profile
Page 57

Avira Premium Security Suite
52
FireWall section
Shortcut Description
Return Properties
Quarantine section
Shortcut Description
F2 Rescan object
F3 Restore object
F4 Send object
F6 Restore object to...
Return Properties
Ins Add file
Del Delete object
Scheduler section
Shortcut Description
F2 Edit job
Return Properties
Ins Insert new job
Del Delete job
Reports section
Shortcut Description
F3 Display report file
F4 Print report file
Return Display report
Del Delete report(s)
Events section
Shortcut Description
F3 Export event(s)
Return Show event
Del Delete event(s)
Page 58

FAQ, Tips
53
10.3 Windows Security Center
- Windows XP Service Pack 2 or higher -
10.3.1 General
The Windows Security Center checks the status of a computer for important security
aspects.
If a problem is detected with one of these important points (e.g. an outdated anti-virus
program), the Security Center issues an alert and gives recommendations on how to
protect your computer better.
10.3.2 The Windows Security Center and your AntiVir program
FireWall
You may receive the following information from the Security Center with regard to your
firewall:
– FireWall ACTIVE / FireWall on
– FireWall INACTIVE / FireWall off
FireWall ACTIVE / FireWall off
After installing your AntiVir program and turning off Windows Firewall, you will receive
the following message:
FireWall INACTIVE / FireWall off
You will receive the following message as soon as you disable the Avira FireWall:
Note
You can enable or disable the Avira FireWall via the Status tab in the Control Center.
Warning
If you turn the Avira FireWall off, your computer is no longer prevented by unauthorized
users from gaining access to it through a network or the Internet.
Virus protection software / Protection against malicious software
Page 59

Avira Premium Security Suite
54
You may receive the following information from the Windows Security Center with
regard to your virus protection:
Virus protection NOT FOUND
Virus protection OUT OF DATE
Virus protection ON
Virus protection OFF
Virus protection NOT MONITORED
Virus protection NOT FOUND
This information of the Windows Security Center appears when the Windows Security
Center has not found any anti-virus software on your computer.
Note
Install your AntiVir program on your computer to protect it against viruses and other
unwanted programs!
Virus protection OUT OF DATE
If you have already installed Windows XP Service Pack 2 or Windows Vista and then
install your AntiVir program or you install Windows XP Service Pack 2 or Windows Vista
on a system on which your AntiVir program has already been installed, you will receive
the following message:
Note
In order for the Windows Security Center to recognize your AntiVir program as up-todate, an update must be performed after installation. Update your system by carrying
out an update.
Virus protection ON
After installation of your AntiVir program and a subsequent update, you will receive the
following message:
Page 60

FAQ, Tips
55
Your AntiVir program is now up-to-date and the AntiVir Guard is enabled.
Virus protection OFF
You receive the following message if you disable the AntiVir Guard or stop the Guard
service.
Note
You can enable or disabled AntiVir Guard in the Overview::Status section of the Control
Center. You can also see that the AntiVir Guard is enabled if the red umbrella in your
taskbar is open.
Virus protection NOT MONITORED
If you receive the following message from the Windows Security Center, you have
decided that you want to monitor your anti-virus software yourself.
Note
This function is not supported by Windows Vista.
Note
The Windows Security Center is supported by your AntiVir program. You can enable this
option at any time via the "Recommendations...." button.
Note
Even if you have installed Windows XP Service Pack 2 or Windows Vista, you still require
a virus protection solution. Although Windows XP Service Pack 2 monitors your antivirus software, it does not contain any anti-virus functions itself. Therefore you would
not be protected against viruses and other malware without an additional anti-virus
solution!
Page 61

56
11 Viruses and more
11.1 Extended threat categories
Dialer (DIALER)
Certain services available in the Internet have to be paid for. They are invoiced in
Germany via dialers with 0190/0900 numbers (or via 09x0 numbers in Austria and
Switzerland; in Germany, the number is set to change to 09x0 in the medium term).
Once installed on the computer, these programs guarantee a connection via a suitable
premium rate number whose scale of charges can vary widely.
The marketing of online content via your telephone bill is legal and can be of advantage
to the user. Genuine dialers leave no room for doubt that they are used deliberately and
intentionally by the user. They are only installed on the user’s computer subject to the
user’s consent, which must be given via a completely unambiguous and clearly visible
labeling or request. The dial-up process of genuine dialers is clearly displayed. Moreover,
genuine dialers tell you the incurred costs exactly and unmistakably.
Unfortunately there are also dialers which install themselves on computers unnoticed,
by dubious means or even with deceptive intent. For example they replace the Internet
user’s default data communication link to the ISP (Internet Service Provider) and dial a
cost-incurring and often horrendously expensive 0190/0900 number every time a
connection is made. The affected user will probably not notice until his next phone bill
that an unwanted 0190/0900 dialer program on his computer has dialed a premium rate
number with every connection, resulting in dramatically increased costs.
We recommend that you ask your telephone provider to block this number range directly
for immediate protection against undesired dialers (0190/0900 dialers).
Your AntiVir program can detect the familiar dialers by default.
If the option Dialers is enabled with a check mark in the configuration under Extended
threat categories, you receive a corresponding alert if a dialer is detected. You can now
simply delete the potentially unwanted 0190/0900 dialer. However, if it is a wanted dialup program, you can declare it an exceptional file and this file is then no longer scanned
in future.
Games (GAMES)
There is a place for computer games - but it is not necessarily at work (except perhaps in
the lunch hour). Nevertheless, with the wealth of games downloadable from the
Internet, a fair bit of mine sweeping and Patience playing goes on among company
employees and civil servants. You can download a whole array of games via the Internet.
Email games have also become more popular: numerous variants are circulating, ranging
from simple chess to "fleet exercises" (including torpedo combats): The corresponding
moves are sent to partners via email programs, who answer them.
Page 62

Viruses and more
57
Studies have shown that the number of working hours devoted to computer games has
long reached economically significant proportions. It is therefore not surprising that
more and more companies are considering ways of banning computer games from
workplace computers.
Your AntiVir program recognizes computer games. If the Games option is enabled with
a check mark in the configuration under Threat categories, you receive a corresponding
alert if your AntiVir program detects a game. The game is now over in the truest sense of
the word, because you can simply delete it.
Jokes (JOKES)
Jokes are merely intended to give someone a fright or provide general amusement
without causing harm or reproducing. When a joke program is loaded, the computer will
usually start at some point to play a tune or display something unusual on the screen.
Examples of jokes are the washing machine in the disk drive (DRAIN.COM) or the screen
eater (BUGSRES.COM).
But beware! All symptoms of joke programs may also originate from a virus or Trojan. At
the very least users will get quite a shock or be thrown into such a panic that they
themselves may cause real damage.
Thanks to the extension of its scanning and identification routines, your AntiVir
program is able to detect joke programs and eliminate them as unwanted programs if
required. If the option Jokes is enabled with a check mark in the configuration under
Threat categories, a corresponding alert is issued if a joke program is detected.
Security Privacy Risk (SPR)
Software that may be able to compromise the security of your system, initiate unwanted
program activities, damage your privacy or spy on your user behavior and could
therefore be unwanted.
Your AntiVir program detects "Security Privacy Risk" software. If the option Security
Privacy Risk is enabled with a check mark in the configuration under Extended threat
categories, you receive a corresponding alert if your AntiVir program detects such
software.
Backdoor Clients (BDC)
In order to steal data or manipulate computers, a backdoor server program is smuggled
in unknown to the user. This program can be controlled by a third party using backdoor
control software (client) via the Internet or a network.
Your AntiVir program recognizes "Backdoor control software". If the Backdoor control
software (BDC) option is enabled with a check mark in the configuration under
Extended threat categories, you receive a corresponding alert if your AntiVir program
detects such software.
Adware/Spyware (ADSPY)
Software that displays advertising or software that sends the user’s personal data to a
third party, often without their knowledge or consent, and for this reason may be
unwanted.
Page 63

Avira Premium Security Suite
58
Your AntiVir program recognizes "Adware/Spyware". If the option Adware/Spyware
(ADSPY) is enabled with a check mark in the configuration under Extended threat
categories, you receive a corresponding alert if your AntiVir program detects adware or
spyware.
Unusual Runtime Packers (PCK)
Files that have been compressed with an unusual runtime packer and that can therefore
be classified as potentially suspicious.
Your AntiVir program recognizes "Unusual runtime packers". If the option Unusual
runtime packers is enabled with a check mark in the configuration under Extended
threat categories, you receive a corresponding alert if your AntiVir program detects such
packers.
Double Extension Files (HEUR-DBLEXT)
Executable files that hide their real file extension in a suspicious way. This camouflage
method is often used by malware.
Your AntiVir program recognizes "Double Extension Files". If the option Double
Extension files (HEUR-DBLEXT) is enabled with a check mark in the configuration
under Extended threat categories, you receive a corresponding alert if your AntiVir
program detects such files.
Phishing
Phishing, also known as brand spoofing is a clever form of data theft aimed at customers
or potential customers of Internet service providers, banks, online banking services,
registration authorities.
When submitting your email address on the Internet, filling in online forms, accessing
newsgroups or websites, your data can be stolen by "Internet crawling spiders" and then
used without your permission to commit fraud or other crimes.
Your AntiVir program recognizes "Phishing". If the option Phishing is enabled with a
check mark in the configuration under Extended threat categories, you receive a
corresponding alert if your AntiVir program detects such behavior.
Application (APPL)
The term APPL refers to an application which may involve a risk when used or is of
dubious origin.
Your AntiVir program recognizes "Application (APPL)". If the option Application
(APPL) is enabled with a check mark in the configuration under Extended threat
categories, you receive a corresponding alert if your AntiVir program detects such
behavior.
11.2 Viruses and other malware
Adware
Page 64

Viruses and more
59
Adware is software that presents banner ads or in pop-up windows through a bar that
appears on a computer screen. These advertisements usually cannot be removed and are
consequently always visible. The connection data allow many conclusions on the usage
behavior and are problematic in terms of data security.
Backdoors
A backdoor can gain access to a computer by bypassing the computer access security
mechanisms.
A program that is being executed in the background generally enables the attacker
almost unlimited rights. User's personal data can be spied with the backdoor's help.. But
are mainly used to install further computer viruses or worms on the relevant system.
Boot viruses
The boot or master boot sector of hard disks is mainly infected by boot sector viruses.
They overwrite important information necessary for the system execution. One of the
awkward consequences: the computer system cannot be loaded any more…
Bot-Net
A bot-net is defined as a remote network of PCs (on the Internet) that is composed of
bots that communicate with each other. A bot-net can comprise a collection of cracked
machines running programs (usually referred to as worms, Trojans) under a common
command and control infrastructure. Bot-nets serve various purposes, including denialof-service attacks etc., usually without the affected PC user's knowledge. The main
potential of bot-nets is that the networks can achieve grow to thousands of computers
and their total bandwidth exceeds most conventional Internet accesses.
Exploit
An exploit (security gap) is a computer program or script that takes advantage of a bug,
glitch or vulnerability leading to privilege escalation or denial of service on a computer
system. One form of exploitation for example is an attack from the Internet with the
help of manipulated data packages. Programs can be infiltrated in order to obtain higher
access.
Hoaxes
For several years, Internet and other network users have received alerts about viruses
that are purportedly spread via email. These alerts are spread via email with the request
that they should be sent to the highest possible number of colleagues and to other users,
in order to warn everyone against the "danger".
Honeypot
A honeypot is a service (program or server) installed in a network. Its function is to
monitor a network and log attacks. This service is unknown to the legitimate user because of this reason he is never addressed. If an attacker examines a network for the
weak points and uses the services which are offered by a honeypot, it is logged and an
alert is triggered.
Page 65

Avira Premium Security Suite
60
Macro viruses
Macroviruses are small programs that are written in the macro language of an
application (e.g. WordBasic under WinWord 6.0) and that can normally only spread
within documents of this application. Because of this, they are also called document
viruses. In order to be active, they need that the corresponding applications are activated
and that one of the infected macros has been executed. Unlike "normal" viruses, macro
viruses consequently do not attack executable files but they do attack the documents of
the corresponding host application.
Pharming
Pharming is a manipulation of the host file of web browsers to divert enquiries to
spoofed websites. This is a further development of classic phishing. Pharming fraudsters
operate their own large server farms on which fake websites are stored. Pharming has
established itself as an umbrella term for various types of DNS attacks. In the case of a
manipulation of the host file, a specific manipulation of a system is carried out with the
aid of a Trojan or virus. The result is that the system can now only access fake websites,
even if the correct web address is entered.
Phishing
Phishing means angling for personal details of the Internet user. Phishers generally send
their victims apparently official letters such as emails that are intended to induce them
to reveal confidential information to the culprits in good faith, in particular user names
and passwords or PINs and TANs of online banking accounts. With the stolen access
details, the phishers can assume the identities of the victims and carry out transactions
in their name. What is clear is that: banks and insurance companies never ask for credit
card numbers, PINs, TANs or other access details by email, SMS or telephone.
Polymorph viruses
Polymorph viruses are the real masters of disguise. They change their own programming
codes - and are therefore very hard to detect.
Program viruses
A computer virus is a program that is capable of attaching itself to other programs after
being executed and cause an infection. Viruses multiply themselves unlike logic bombs
and Trojans. In contrast to a worm, a virus always requires a program as host, where the
virus deposits its virulent code. The program execution of the host itself is not changed
as a rule.
Rootkit
A rootkit is a collection of software tools that are installed after a computer system has
been infiltrated to conceal logins of the infiltrator, hide processes and record data generally speaking: to make themselves invisible. They attempt to update already
installed spy programs and reinstall deleted spyware.
Script viruses and worms
Page 66

Viruses and more
61
Such viruses are extremely easy to program and they can spread - if the required
technology is on hand - within a few hours via email round the globe.
Script viruses and worms use one of the script languages, such as Javascript, VBScript
etc., to insert themselves in other, new scripts or to spread themselves by calling
operating system functions. This frequently happens via email or through the exchange
of files (documents).
A worm is a program that multiplies itself but that does not infect the host. Worms
cannot consequently form part of other program sequences. Worms are often the only
possibility to infiltrate any kind of damaging programs on systems with restrictive
security measures.
Spyware
Spyware are so called spy programs that intercept or take partial control of a computer's
operation without the user's informed consent. Spyware is designed to exploit infected
computers for commercial gain.
Trojan horses (short Trojans)
Trojans are pretty common nowadays. Trojans include programs that pretend to have a
particular function, but that show their real image after execution and carry out a
different function that, in most cases, is destructive. Trojan horses cannot multiply
themselves, which differentiates them from viruses and worms. Most of them have an
interesting name (SEX.EXE or STARTME.EXE) with the intention to induce the user to
start the Trojan. Immediately after execution they become active and can, for example,
format the hard disk. A dropper is a special form of Trojan that 'drops' viruses, i.e.
embeds viruses on the computer system.
Zombie
A zombie PC is a computer that is infected with malware programs and that enables
hackers to abuse computers via remote control for criminal purposes. On command, the
affected PC starts denial-of-service (DoS) attacks, for example, or sends spam and
phishing emails.
Page 67

62
12 Info and Service
This chapter contains information on how to contact us.
see Chapter Contact address
see Chapter Technical support
see Chapter Suspicious files
see Chapter Report false positives
see Chapter Your feedback for more security
12.1 Contact address
If you have any questions or requests concerning the AntiVir product range, we will be
pleased to help you. For our contact addresses, please refer to the Control Center under
Help :: About Avira Premium Security Suite.
12.2 Technical support
Avira support provides reliable assistance in answering your questions or solving a
technical problem.
All necessary information on our comprehensive support service can be obtained from
our website:
http://www.avira.com/premium-suite-support
So that we can provide you with fast, reliable help, you should have the following
information ready:
– License information. You can find the program interface under the menu item
Help :: About Avira Premium Security Suite :: License information
– Version information. You can find the program interface under the menu item
Help :: About Avira Premium Security Suite:: Version information.
– Operating system version and any Service Packs installed.
– Installed software packages, e.g. anti-virus software of other vendors.
– Exact messages of the program or of the report file.
12.3 Suspicious file
Viruses that may not yet be detected or removed by our products or suspect files can be
sent to us. We provide you with several ways of doing this.
Page 68

Info and Service
63
– Identify the file in the quarantine manager of the Control Center and select the
item Send file via the context menu or the corresponding button.
– Send the required file packed (WinZIP, PKZip, Arj etc.) in the attachment of an
email to the following address:
virus-premium-suite@avira.com
As some email gateways work with anti-virus software, you should also provide
the file(s) with a password (please remember to tell us the password).
You can also send us the suspicious file via our website: http://www.avira.com/sampleupload
12.4 Reporting false positives
If you believe that your AntiVir program is reporting a detection in a file that is most
likely "clean", send the relevant file packed (WinZIP, PKZip, Arj etc.) as an email
attachment to the following address:
– virus-premium-suite@avira.com
As some email gateways work with anti-virus software, you should also provide the
file(s) with a password (please remember to tell us the password).
12.5 Your feedback for more security
At Avira, our customers’ security is paramount. For this reason, we don't just have an inhouse expert team that tests the quality and security of every Avira GmbH solution
before the product is released. We also attach great importance to the indications
regarding security relevant gaps that could develop and we treat those seriously.
If you think you have detected a security gap in one of our products, please send us an
email to the following address:
vulnerabilities-premium-suite@avira.com
Page 69

64
13 Reference: Configuration options
The configuration reference documents all available configuration options.
13.1 Scanner
The Scanner section of the Configuration is responsible for the configuration of the ondemand scan.
13.1.1 Scan
Here you define the basic behavior of the scan routine for an on-demand scan. If you
select certain directories to be scanned with an on-demand scan, depending on the
configuration the Scanner scans:
– with a certain scanning power (priority),
– also boot sectors and main memory,
– certain or all boot sectors and the main memory,
– all or selected files in the directory.
Files
The Scanner can use a filter to scan only those files with a certain extension (type).
All files
If this option is enabled, all files are scanned for viruses or unwanted programs,
irrespective of their content and file extension. The filter is not used.
Note
If All files is enabled, the button File extensions cannot be selected.
Smart Extensions
If this option is enabled, the selection of the files scanned for viruses or unwanted
programs is automatically chosen by the program. This means that your AntiVir program
decides whether the files are scanned or not based on their content. This procedure is
somewhat slower than Use file extension list, but more secure, since not only on the
basis of the file extension is scanned. This option is enabled as the default setting and is
recommended.
Note
If Smart Extensions is enabled, the button File extensions cannot be selected.
Use file extension list
If this option is enabled, only files with a specified extension are scanned. All file types
that may contain viruses and unwanted programs are preset. The list can be edited
manually via the button "
File extension".
Page 70

Reference: Configuration options
65
Note
If this option is enabled and you have deleted all entries from the list with file
extensions, this is indicated with the text "No file extensions" under the button File
extensions.
File extensions
With the aid of this button, a dialog box is opened in which all file extensions are
displayed that are scanned in "Use file extension list" mode. Default entries are set for
the extensions, but entries can be added or deleted.
Note
Please note that the default list may vary from version to version.
Additional settings
Scan boot sectors of selected drives
If this option is enabled, the Scanner scans the boot sectors of the drives selected for the
on-demand scan. This option is enabled as the default setting.
Scan master boot sectors
If this option is enabled, the Scanner scans the master boot sectors of the hard disk(s)
used in the system.
Ignore offline files
If this option is enabled, the direct scan ignores so-called offline files completely during a
scan. This means that these files are not scanned for viruses and unwanted programs.
Offline files are files that were physically moved by a so-called Hierarchical Storage
Management System (HSMS) from the hard disk onto a tape, for example. This option is
enabled as the default setting.
Integrity checking of system files
When this option is enabled, the most important Windows system files are subjected to
a particularly secure check for changes by malware during every on-demand scan. If an
amended file is detected, this is reported as suspect. This function uses a lot of computer
capacity. That is why the option is disabled as the default setting.
Important
This option is only available with Windows Vista and higher.
Note
This option should not be used if you are using third-party tools that modify system files
and adapt the boot or start screen to your own requirements. Examples of such tools are
skinpacks, TuneUp utilities or Vista Customization.
Optimized scan
When the option is enabled, the processor capacity is optimally utilized during a Scanner
scan. For performance reasons, an optimized scan is only logged on standard level.
Note
This option is only available on multi-processor systems. If
Follow symbolic links
If this option is enabled, Scanner performs a scan that follows all symbolic links in the
scan profile or selected directory and scans the linked files for viruses and malware. This
option is not supported by Windows 2000 and has been deactivated.
Page 71

Avira Premium Security Suite
66
Important
The option does not include any shortcuts, but refers exclusively to symbolic links
(generated by mklink.exe) or Junction Points (generated by junction.exe) that are
transparent in the file system.
Search for Rootkits before scan
If this option is enabled and a scan is started, the Scanner scans the Windows system
directory for active rootkits in a so-called shortcut. This process does not scan your
computer for active rootkits as comprehensively as the scan profile "Scan for rootkits",
but it is significantly quicker to perform.
Important
The rootkit scan is not available for Windows XP 64 bit !
Scan Registry
If this option is enabled, the Registry is scanned for references to malware.
Scan process
Allow stopping the Scanner
If this option is enabled, the scan for viruses or unwanted programs can be terminated at
any time with the button "Stop" in the "Luke Filewalker" window. If you have disabled
this setting, the
Stop button in the "Luke Filewalker" window has a gray background.
Premature ending of a scan process is thus not possible! This option is enabled as the
default setting.
Scanner priority
With the on-demand scan, the Scanner distinguishes between priority levels. This is only
effective if several processes are running simultaneously on the workstation. The
selection affects the scanning speed.
Low
The Scanner is only allocated processor time by the operating system if no other process
requires computation time, i.e. as long as only the Scanner is running, the speed is
maximum. All in all, work with other programs is optimal: The computer responds more
quickly if other programs require computation time while the Scanner continues running
in the background. This option is enabled as the default setting and is recommended.
Medium
The Scanner is executed with normal priority. All processes are allocated the same
amount of processor time by the operating system. Under certain circumstances, work
with other applications may be affected.
High
The Scanner has the highest priority. Simultaneous work with other applications is
almost impossible. However, the Scanner completes its scan at maximum speed.
13.1.1.1. Action on detection
Action on detection
You can define the actions to be performed by Scanner when a virus or unwanted
program is detected.
Interactive
Page 72

Reference: Configuration options
67
If this option is enabled, the results of the Scanner scan are displayed in a dialog box.
When carrying out a scan with the Scanner, you will receive an alert with a list of the
affected files at the end of the scan. You can use the content-sensitive menu to select an
action to be executed for the various infected files. You can execute the standard actions
for all infected files or cancel the Scanner.
Note
The action Move to quarantine is preselected by default in the Scanner notification.
Further actions can be selected via a context menu.
Click here for more information.
Automatic
If this option is enabled, no dialog box in case of a virus detection appears. The Scanner
reacts according to the settings you predefine in this section as primary and secondary
action.
Backup to quarantine
If this option is enabled, the Scanner creates a backup copy before carrying out the
requested primary or secondary action. The back-up copy is saved in Quarantine, where
the file can be restored if it is of informative value. You can also send the backup copy to
the Avira Malware Research Center for further investigation.
Primary action
Primary action is the action performed when the Scanner finds a virus or an unwanted
program. If the option "repair" is selected but the affected file cannot be repaired, the
action selected under "Secondary action" is performed.
Note
The option Secondary action can only be selected if the setting repair was selected
under Primary action.
Repair
If this option is enabled, the Scanner repairs affected files automatically. If the Scanner
cannot repair an affected file, it carries out the action selected under Secondary action.
Note
An automatic repair is recommended, but means that the Scanner modifies files on the
workstation.
delete
If this option is enabled, the file is deleted. This process is much faster than "overwrite
and delete".
overwrite and delete
If this option is enabled, the Scanner overwrites the file with a default pattern and then
deletes it. It cannot be restored.
rename
If this option is enabled, the Scanner renames the file. Direct access to these files (e.g.
with double-click) is therefore no longer possible. Files can later be repaired and given
their original names again.
Ignore
If this option is enabled, access to the file is allowed and the file is left as it is.
Warning
The affected file remains active on your workstation! It may cause serious damage on
your workstation!
Quarantine
Page 73

Avira Premium Security Suite
68
If this option is enabled, the Scanner moves the file to the quarantine. These files can
later be repaired or - if necessary - sent to the Avira Malware Research Center.
Secondary action
The option "Secondary action" can only be selected if the setting repair was selected
under "Primary action". With this option it can now be decided what is to be done with
the affected file if it cannot be repaired.
delete
If this option is enabled, the file is deleted. This process is much faster than "overwrite
and delete".
overwrite and delete
If this option is enabled, the Scanner overwrites the file with a default pattern and then
deletes (wipes) it. It cannot be restored.
rename
If this option is enabled, the Scanner renames the file. Direct access to these files (e.g.
with double-click) is therefore no longer possible. Files can later be repaired and given
their original names again.
Ignore
If this option is enabled, access to the file is allowed and the file is left as it is.
Warning
The affected file remains active on your workstation! It may cause serious damage on
your workstation!
Quarantine
If this option is enabled, the Scanner moves the file to Quarantine. These files can later
be repaired or - if necessary - sent to the Avira Malware Research Center.
Note
If you have selected Delete or Overwrite and Delete as the primary or secondary
action, you should note the following: In the case of heuristic hits, the affected files are
not deleted, but are instead moved to quarantine.
When scanning archives, the Scanner uses a recursive scan: Archives in archives are also
unpacked and scanned for viruses and unwanted programs. The files are scanned,
decompressed and scanned again.
Scan archives
If this option is enabled, the selected archives in the archive list are scanned. This option
is enabled as the default setting.
All archive types
If this option is enabled, all archive types in the archive list are selected and scanned.
Smart Extensions
If this option is enabled, the Scanner detects whether a file is a packed file format
(archive), even if the file extension differs from the usual extensions, and scans the
archive. However every file must be opened for this, which reduces the scanning speed.
Example: If a *.zip archive has the file extension *.xyz, the Scanner also unpacks this
archive and scans it. This option is enabled as the default setting.
Note
Only those archive types marked in the archive list are supported.
Page 74

Reference: Configuration options
69
Recursion depth
Unpacking and scanning recursive archives can require a great deal of computer time and
resources. If this option is enabled, you limit the depth of the scan in multi-packed
archives to a certain number of packing levels (maximum recursion depth). This saves
time and computer resources.
Note
In order to find a virus or an unwanted program in an archive, the Scanner must scan up
to the recursion level in which the virus or the unwanted program is located.
Maximum recursion depth
In order to enter the maximum recursion depth, the option Limit recursion depth must
be enabled.
You can either enter the requested recursion depth directly or by means of the right
arrow key on the entry field. The permitted values are 1 to 99. The standard value is 20
which is recommended.
Default values
The button restores the pre-defined values for scanning archives.
Archives
In this display area you can set which archives the Scanner should scan. For this, you
must select the relevant entries.
13.1.1.2. Exceptions
File objects to be omitted for the Scanner
The list in this window contains files and paths that should not be included by the
Scanner in the scan for viruses or unwanted programs.
Please enter as few exceptions as possible here and really only files that, for whatever
reason, should not be included in a normal scan. We recommend that you always scan
these files for viruses or unwanted programs before they are included in this list!
Note
The entries in the list must not result in more than 6000 characters in total.
Warning
These files are not included in a scan!
Note
The files included in this list are recorded in the report file. Please check the report file
from time to time for unscanned files, as perhaps the reason you excluded a file here no
longer exists. In this case you should remove the name of this file from this list again.
Input box
In this input box you can enter the name of the file object that is not included in the ondemand scan. No file object is entered as the default setting.
Page 75

Avira Premium Security Suite
70
The button opens a window in which you can select the required file or the required
path.
When you have entered a file name with its complete path, only this file is not scanned
for infection. If you have entered a file name without a path, all files with this name
(irrespective of the path or drive) are not scanned.
Add
With this button, you can add the file object entered in the input box to the display
window.
Delete
The button deletes a selected entry from the list. This button is inactive if no entry is
selected.
Note
If you add a complete partition to the list of the file objects, only those files that are
saved directly under the partition will be excluded from the scan, which does not apply
to files in sub-directories on the corresponding partition:
Example: File object to be skipped: D:\ = D:\file.txt will be excluded from the
scan of the Scanner, D:\folder\file.txt will not be excluded from the scan.
13.1.1.3. Heuristics
This configuration section contains the settings for the heuristic of the scan engine.
AntiVir products contain very powerful heuristics that can proactively uncover unknown
malware, i.e. before a special virus signature to combat the damaging element has been
created and before a virus guard update has been sent. Virus detection involves an
extensive analysis and investigation of the affected codes for functions typical of
malware. If the code being scanned exhibits these characteristic features, it is reported as
being suspicious. This does not necessarily mean that the code is in fact malware. False
positives do sometimes occur. The decision on how to handle affected code is to be made
by the user, e.g. based on his or her knowledge of whether the source of the code is
trustworthy or not.
Macrovirus heuristics
Macrovirus heuristics
Your AntiVir product contains a highly powerful macrovirus heuristic. If this option is
enabled, all macros in the relevant document are deleted in the event of a repair,
alternatively suspect documents are only reported, i.e. you receive an alert. This option is
enabled as the default setting and is recommended.
Advanced Heuristic Analysis and Detection (AHeAD)
enable AHeAD
Your AntiVir program contains a very powerful heuristic in the form of AntiVir AHeAD
technology, which can also detect unknown (new) malware. If this option is enabled, you
can define how "aggressive" this heuristic should be. This option is enabled as the default
setting.
Low detection level
Page 76

Reference: Configuration options
71
If this option is enabled, slightly less unknown malware is detected, the risk of false
alerts is low in this case.
Medium detection level
This option is enabled as the default setting if you have selected the use of this heuristic.
High detection level
If this option is enabled, significantly more unknown malware is detected, but there are
also likely to be false positives.
13.1.2 Report
The Scanner has a comprehensive reporting function. You thus obtain precise
information on the results of an on-demand scan. The report file contains all entries of
the system as well as alerts and messages of the on-demand scan.
Note
To enable you to establish what actions the Scanner has performed when viruses or
unwanted programs have been detected, a report file should always be created.
Reporting
Off
If this option is enabled, the Scanner does not report the actions and results of the ondemand scan.
Default
When this option is activated, the Scanner logs the names of the files concerned with
their path. In addition, the configuration for the current scan, version information and
information on the licensee is written in the report file.
Advanced
When this option is activated, the Scanner logs alerts and tips in addition to the default
information.
Complete
When this option is activated, the Scanner also logs all scanned files. In addition, all files
involved as well as alerts and tips are included in the report file.
Note
If you have to send us a report file at any time (for troubleshooting), please create this
report file in this mode.
13.2 Guard
The Guard section of the configuration is responsible for the configuration of the onaccess scan.
13.2.1 Scan
Page 77

Avira Premium Security Suite
72
You will normally want to monitor your system constantly. To this end, use the Guard (=
on-access Scanner). You can thus scan all files that are copied or opened on the computer
"on the fly", for viruses and unwanted programs.
Scan mode
Here the time for scanning of a file is defined.
Scan when reading
If this option is enabled, the Guard scans the files before they are read or executed by the
application or the operating system.
Scan when writing
If this option is enabled, the Guard scans a file when writing. You can only access the file
again after this process has been completed.
Scan when reading and writing
If this option is enabled, the Guard scans files before opening, reading and executing and
after writing. This option is enabled as the default setting and is recommended.
Files
The Guard can use a filter to scan only those files with a certain extension (type).
All files
If this option is enabled, all files are scanned for viruses or unwanted programs,
irrespective of their content and their file extension.
Note
If All files is enabled, the File extensions button cannot be selected.
Smart Extensions
If this option is enabled, the selection of the files scanned for viruses or unwanted
programs is automatically chosen by the program. This means that the program decides
whether the files are scanned or not based on their content. This procedure is somewhat
slower than Use file extension list, but more secure, since not only on the basis of the file
extension is scanned.
Note
If Smart Extensions is enabled, the File extensions button cannot be selected.
Use file extension list
If this option is enabled, only files with a specified extension are scanned. All file types
that may contain viruses and unwanted programs are preset. The list can be edited
manually via the "
File extensions" button. This option is enabled as the default setting
and is recommended.
Note
If this option is enabled and you have deleted all entries from the list with file
extensions, this is indicated with the text "No file extensions" under the File extensions
button.
File extensions
With the aid of this button, a dialog box is opened in which all file extensions are
displayed that are scanned in "Use file extension list" mode. Default entries are set for
the extensions, but entries can be added or deleted.
Page 78

Reference: Configuration options
73
Note
Please note that the file extension list may vary from version to version.
Archives
Scan archives
If this option is enabled, then archives will be scanned. Compressed files are scanned,
then decompressed and scanned again. This option is deactivated by default. The archive
scan is restricted by the recursion depth, the number of files to be scanned and the
archive size. You can set the maximum recursion depth, the number of files to be
scanned and the maximum archive size.
Note
This option is deactivated by default, since the process puts heavy demands on the
computer's performance. It is generally recommended that archives be checked using an
on-demand scan.
Maximum recursion depth
When scanning archives, the Guard uses a recursive scan: Archives in archives are also
unpacked and scanned for viruses and unwanted programs. You can define the recursion
depth. The default value for the recursion depth is 1 and is recommended: all archives
that are directly located in the main archive are scanned.
Maximum number of files
When scanning archives, you can restrict the scan to a maximum number of files in the
archive. The default value for the maximum number of files to be scanned is 10 and is
recommended.
Maximum size (KB)
When scanning archives, you can restrict the scan to a maximum archive size to be
unpacked. The standard value of 1000 KB is recommended.
13.2.1.1. Action on detection
Action on detection
You can define the actions to be performed by Guard when a virus or unwanted program
is detected.
Interactive
If this option is enabled, a desktop notification appears when Guard detects a virus or
unwanted program. You have the option of removing the detected malware or accessing
other possible virus treatment actions via the 'Details' button. The actions are displayed
in a dialog box. The actions will be displayed in a dialog box. This option is enabled as the
default setting.
Click here for more information.
Automatic
If this option is enabled, no dialog box in case of a virus detection appears. Guard reacts
according to the settings you predefine in this section as primary and secondary action.
Backup to quarantine
Page 79

Avira Premium Security Suite
74
If this option is enabled, the Guard creates a backup copy before carrying out the
requested primary or secondary action. The backup copy is saved in quarantine. It can be
restored via the quarantine manager if it is of informative value. You can also send the
backup copy to the Avira Malware Research Center. Depending on the object, more
selection options are available in the quarantine manager .
Primary action
Primary action is the action performed when the Guard finds a virus or an unwanted
program. If the "repair" option is selected but the affected file cannot be repaired, the
action selected under "Secondary action" is performed.
Note
The Secondary action option can only be selected if the repair setting was selected under
Primary action.
repair
If this option is enabled, the Guard repairs affected files automatically. If the Guard
cannot repair an affected file, it carries out the action selected under Secondary action.
Note
An automatic repair is recommended, but means that the Guard modifies files on the
workstation.
delete
If this option is enabled, the file is deleted. This process is much faster than "overwrite
and delete".
overwrite and delete
If this option is enabled, the Guard overwrites the file with a default pattern and then
deletes it. It cannot be restored.
rename
If this option is enabled, the Guard renames the file. Direct access to these files (e.g. with
double-click) is therefore no longer possible. Files can later be repaired and given their
original names again.
Ignore
If this option is enabled, access to the file is allowed and the file is left as it is.
Warning
The affected file remains active on your workstation! It may cause serious damage on
your workstation!
Deny access
If this option is enabled, the Guard only enters the detection in the report file if the
report function is enabled. In addition, the Guard writes an entry in the Event log, if this
option is enabled.
Quarantine
If this option is enabled, the Guard moves the file to Quarantine. The files in this
directory can later be repaired or - if necessary - sent to the Avira Malware Research
Center.
Secondary action
The option "Secondary action" can only be selected if the "Repair" option was selected
under "Primary action". With this option it can now be decided what is to be done with
the affected file if it cannot be repaired.
delete
Page 80

Reference: Configuration options
75
If this option is enabled, the file is deleted. This process is much faster than "overwrite
and delete".
overwrite and delete
If this option is enabled, the Guard overwrites the file with a default pattern and then
deletes it. It cannot be restored.
rename
If this option is enabled, the Guard renames the file. Direct access to these files (e.g. with
double-click) is therefore no longer possible. Files can later be repaired and given their
original names again.
Ignore
If this option is enabled, access to the file is allowed and the file is left as it is.
Warning
The affected file remains active on your workstation! It may cause serious damage on
your workstation!
Deny access
If this option is enabled, the Guard only enters the detection in the report file if the
report function is enabled. In addition, the Guard writes an entry in the Event log, if this
option is enabled.
Quarantine
If this option is enabled, the Guard moves the file to Quarantine. The files can later be
repaired or - if necessary - sent to the Avira Malware Research Center.
Note
If you have selected Delete or Overwrite and Delete as the primary or secondary
action, please note the following: In the case of heuristic hits, the affected files are not
deleted, but are instead moved to quarantine.
13.2.1.2. Further actions
Notifications
Event log
Use event log
If this option is enabled, an entry is added to the Windows event log for every detection.
The events can be called up in the Windows event viewer. This option is enabled as the
default setting.
Autostart
Block autostart function
Page 81

Avira Premium Security Suite
76
When this option is enabled, the execution of the Windows Autostart function is blocked
on all connected drives, including USB sticks, CD and DVD drives and network drives.
With the Windows Autostart function, files on data media or network drives are read
immediately on loading or connection, and files can therefore be started and copied
automatically. This functionality carries with it a high security risk, however, as malware
and unwanted programs can be installed with the automatic start. The Autostart
function is especially critical for USB sticks as data on a stick can be changed at any time.
Exclude CDs and DVDs
When this option is enabled, the Autostart function is permitted on CD and DVD drives.
Warning
Only disable the Autostart function for CD and DVD drives if you are sure you are only
using trusted data media.
13.2.1.3. Exceptions
With these options you can configure exception objects for the Guard (on-access scan).
The relevant objects are then not included in the on-access scan. The Guard can ignore
file accesses to these objects during the on-access scan via the list of processes to be
omitted. This is useful, for example, with databases or backup solutions.
Please note the following when specifying processes and file objects to be omitted: The
list is processed from top to bottom. The longer the list is, the more processor time is
required for processing the list for each access. Therefore, keep the list as short as
possible.
Processes to be omitted by the Guard
All file accesses of processes in this list are excluded from monitoring by Guard.
Input box
In this field, enter the name of the process that is to be ignored by the real-time scan. No
process is entered as the default setting.
Note
You can enter up to 128 processes.
Note
When entering the process, Unicode symbols are accepted. You can therefore enter
process or directory names containing special symbols.
Note
You have the option of excluding processes from monitoring by the Guard without full
path details.
application.exe
This however only applies to processes where the executable files are located on hard
disk drives.
Do not specify any exceptions for processes where the executable files are located on
dynamic drives. Dynamic drives are used for removable disks, such as CDs, DVDs or USB
sticks.
Note
Drive information must be entered as follows: [Drive letter]:\
The colon symbol (:) is only used to specify drives.
Page 82

Reference: Configuration options
77
Note
When specifying the process, you can use the wildcards* (any number of characters) and
?? (a single character).
C:\Program Files\Application\application.exe
C:\Program Files\Application\applicatio?.exe
C:\Program Files\Application\applic*.exe
C:\Program Files\Application\*.exe
To avoid the process being excluded globally from monitoring by Guard, specifications
exclusively comprising the following characters are invalid: * (asterisk), ? (question
mark), / (forward slash), \ (backslash), . (dot), : (colon).
Note
The specified path and file name of the process should contain a maximum of 255
characters. The entries in the list must not result in more than 6000 characters in total.
Warning
Please note that all file accesses by processes recorded in the list are excluded from the
scan for viruses and unwanted programs! The Windows Explorer and the operating
system itself cannot be excluded. A corresponding entry in the list is ignored.
The button opens a window in which you can select an executable file.
Processes
The "Processes" button opens the" Process selection" window in which the running
processes are displayed.
Add
With this button, you can add the process entered in the input box to the display
window.
Delete
With this button you can delete a selected process from the display window.
File objects to be omitted by the Guard
All file accesses to objects in this list are excluded from monitoring by the Guard.
Input box
In this box you can enter the name of the file object that is not included in the on-access
scan. No file object is entered as the default setting.
Note
When specifying file objects to be omitted, you can use the wildcards* (any number of
characters) and ?? (a single character): Individual file extensions can also be excluded
(including wildcards):
C:\Directory\*.mdb
*.mdb
*.md?
*.xls*
C:\Directory\*.log
Note
Directory names must end with a backslash \, otherwise a file name is assumed.
Note
The entries in the list must have no more than 6000 characters in total.
Page 83

Avira Premium Security Suite
78
Note
If a directory is excluded, all its sub-directories are automatically also excluded.
Note
For each drive you can specify a maximum of 20 exceptions by entering the complete
path (starting with the drive letter).
For example: C:\Program Files\Application\Name.log
The maximum number of exceptions without a complete path is 64.
For example: *.log
Note
In case of dynamic drives that are mounted as a directory on another drive, the alias of
the operating system for the integrated drive in the list of the exceptions has to be used:
e.g. \Device\HarddiskDmVolumes\PhysicalDmVolumes\BlockVolume1\
If you use the mount point itself, for example, C:\DynDrive, the dynamic drive will be
scanned nonetheless. You can determine the alias of the operating system to be used
from the Guard report file.
The button opens a window in which you can select the file object to be excluded.
Add
With this button, you can add the file object entered in the input box to the display
window.
Delete
With this button you can delete a selected file object from the display window.
Please note the further information when specifying exceptions:
Note
In order to also exclude objects when they are accessed with short DOS file names (DOS
name convention 8.3), the relevant short file name must also be entered in the list.
Note
A file name that contains wildcards may not be terminated with a backslash.
For example:
C:\Program Files\Application\applic*.exe\
This entry is not valid and not treated as an exception!
Note
You can locate the path Guard uses to scan for infected files in the Guard report file.
Indicate exactly the same path in the list of exceptions. Proceed as follows: Set the
protocol function of the Guard to Complete in the configuration under Guard::Report.
Now access the files, folders, mounted drives with the activated Guard. You can now read
the path to be used from the Guard report file. The report file can be accessed in the
Control Center under Local protection::Guard.
Examples for processes to be excluded:
– application.exe
The application.exe process is excluded from the Guard scan, irrespective of which
hard disk drive it is located on and which directory it is in.
– C:\Program Files1\Application.exe
Page 84

Reference: Configuration options
79
The process for the file application.exe, which is located under the path C:\Program
Files1, is excluded from the Guard scan.
– C:\Program Files1\*.exe
All processes for executable files located under the path C:\Program Files1 are
excluded from the Guard scan.
Examples for files to be excluded:
– *.mdb
All files with the extension 'mdb’ are excluded from the Guard scan
– *.xls*
All files with a file extension beginning 'xls’ are excluded from the Guard scan, e.g.
files with the extensions .xls and .xlsx.
– C:\Directory\*.log
All log files with the extension 'log’, located under the path C:\Directory, are
excluded from the Guard scan.
13.2.1.4. Heuristics
This configuration section contains the settings for the heuristic of the scan engine.
AntiVir products contain very powerful heuristics that can proactively uncover unknown
malware, i.e. before a special virus signature to combat the damaging element has been
created and before a virus guard update has been sent. Virus detection involves an
extensive analysis and investigation of the affected codes for functions typical of
malware. If the code being scanned exhibits these characteristic features, it is reported as
being suspicious. This does not necessarily mean that the code is in fact malware. False
positives do sometimes occur. The decision on how to handle affected code is to be made
by the user, e.g. based on his or her knowledge of whether the source of the code is
trustworthy or not.
Macrovirus heuristics
Macrovirus heuristics
Your AntiVir product contains a highly powerful macrovirus heuristic. If this option is
enabled, all macros in the relevant document are deleted in the event of a repair,
alternatively suspect documents are only reported, i.e. you receive an alert. This option is
enabled as the default setting and is recommended.
Advanced Heuristic Analysis and Detection (AHeAD)
enable AHeAD
Your AntiVir program contains a very powerful heuristic in the form of AntiVir AHeAD
technology, which can also detect unknown (new) malware. If this option is enabled, you
can define how "aggressive" this heuristic should be. This option is enabled as the default
setting.
Low detection level
Page 85

Avira Premium Security Suite
80
If this option is enabled, slightly less unknown malware is detected, the risk of false
alerts is low in this case.
Medium detection level
This option is enabled as the default setting if you have selected the use of this heuristic.
High detection level
If this option is enabled, significantly more unknown malware is detected, but there are
also likely to be false positives.
13.2.2 ProActiv
Avira AntiVir ProActiv protects you from new and unknown threats for which there are
not yet any virus definitions or heuristics available. ProActiv technology is integrated
into the Guard component and observes and analyzes the program actions performed.
The behavior of the program is checked against typical malware action patterns: Type of
action and action sequences. If a program exhibits behavior typical of malware, this is
treated as a virus detection : You have the option of blocking the program or ignoring
the notification and continuing to use the program. You can classify the program as
trusted and add it to the application filter for permitted programs. You have the option
of adding the program to the application filter for blocked programs using the Always
block command.
The ProActiv component uses rule sets developed by the Avira Malware Research Center
to identify suspicious behavior. The rule sets are supplied by Avira GmbH databases.
Avira AntiVir ProActiv sends information on any suspicious programs detected to the
Avira databases for logging. You have the option of disabling data transmission to the
Avira databases
Note
ProActiv technology is not yet available for 64 bit systems! Windows 2000 does not
support ProActiv components.
General
Enabling Avira AntiVir ProActiv
If this option is enabled, programs on your computer system are monitored and checked
for suspicious actions. You will receive a message if typical malware behavior is detected.
You can block the program or select "Ignore" to continue to use the program. The
monitoring process excludes: Programs classified as trusted, trusted and signed
programs included by default in the permitted applications filter, and all programs which
you have added to the application filter for permitted programs.
Participating in the AntiVir ProActiv Community enhances your computer’s security.
If this option is enabled, Avira AntiVir ProActiv sends data on suspicious programs and,
in certain cases, suspicious program files (executable files) to the Avira Malware
Research Center for advanced online scanning. After evaluation, these data are added to
the ProActiv behavioral analysis rule sets. In this way, you become part of the Avira
ProActiv community and contribute to the continuous improvement and refinement of
the ProActiv security technology. No data are sent if this option is disabled. This has no
effect on ProActiv functionality.
Click here for further information
With this link you can access an Internet page where you can obtain detailed information
on the advanced online scan. All data transmitted during an advanced online scan is
included on the Internet page.
Page 86

Reference: Configuration options
81
13.2.2.1. Application filter: Applications to be blocked
Under Application filter: Applications to be blocked you can enter applications which you
classify as harmful and which you want Avira AntiVir ProActiv to block by default. The
applications added cannot be executed on your computer system. You can also add
programs to the application filter for blocking via Guard notifications of suspicious
program behavior, by selecting theAlways block this program option.
Applications to be blocked
Applications
The list contains all applications which you have classified as harmful which you have
entered via the configuration or by notifying the ProActiv component. The applications
on the list are blocked by Avira AntiVir ProActiv and cannot be executed on your
computer system. An operating system message appears when a blocked program starts
up. The applications to be blocked are identified by Avira AntVir ProActiv on the basis of
the path specified and the file name, and are blocked irrespective of their content.
Input box
Enter the application you want to block in this box. To identify the application, the full
path, file name and file extension must be specified. The path must either show the drive
on which the application is located or start with an environment variable.
The button opens a window in which you can select the application to be blocked.
Add
With the "Add" button you can transfer the application specified in the input box to the
list of applications to be blocked.
Note
Applications required for the proper operation of the operating system cannot be added.
Delete
The "Delete" button lets you remove a highlighted application from the list of
applications to be blocked.
13.2.2.2. Application filter: Permitted applications
The section Application filter: Permitted applicationslists the applications excluded from
monitoring by the ProActiv component: signed programs classified as trusted and
included in list by default, all applications classified as trusted and added to the
application filter: You can add permitted applications to the list in Configuration. You
also have the option of adding applications to suspicious program behavior via Guard
notifications by using the Trusted program option in the Guard notification.
Applications to be skipped
Page 87

Avira Premium Security Suite
82
Applications
The list contains applications excluded from monitoring by the ProActiv component. In
the default installation settings, the list contains signed applications from trusted
producers. You have the option of adding applications that you consider to be
trustworthy via the configuration or via Guard notifications. The ProActiv component
identifies applications using the path, the file name and the content. We recommend
checking the content as malcode can be added to a program through changes such as
updates. You can determine whether a contents check should be performed from the
type specified: For the "Contents" type, the applications specified by path and file name
are checked for changes to the file content before they are excluded from monitoring by
the ProActiv component. If the file contents have been modified, the application is again
monitored by the ProActiv component. For the "Path" type, no contents check is
performed before the application is excluded from monitoring by the Guard. To change
the exclusion type, click on the type displayed.
Warning
Only use the Path type in exceptional cases. Malcode can be added to an application
through an update. The originally harmless application is now malware.
Note
Some trusted applications, including for example all application components of your
AntiVir program, are by default excluded from monitoring by the ProActiv component
even though they are not included in the list.
Input box
In this box you enter the application to be excluded from monitoring by the ProActiv
component. To identify the application, the full path, file name and file extension must
be specified. The path must either show the drive on which the application is located or
start with an environment variable.
The button opens a window in which you can select the application to be excluded.
Add
With the "Add" button you can transfer the application specified in the input box to the
list of applications to be excluded.
Delete
The "Delete" button lets you remove a highlighted application from the list of
applications to be excluded.
13.2.3 Report
Guard includes an extensive logging function to provide the user or administrator with
exact notes about the type and manner of a detection.
Reporting
This group allows for the content of the report file to be determined.
Off
Page 88

Reference: Configuration options
83
If this option is enabled, then Guard does not create a log.
It is recommended that you should turn off the logging function only in exceptional
cases, such as if you are executing trials with multiple viruses or unwanted programs.
Default
If this option is enabled, Guard records important information (concerning detections,
alerts and errors) in the report file, with less important information ignored for
improved clarity. This option is enabled as the default setting.
Advanced
If this option is enabled, Guard logs less important information to the report file as well.
Complete
If this option is enabled, Guard logs all available information in the report file, including
file size, file type, date, etc.
Limit report file
Limit size to n MB
If this option is enabled, the report file can be limited to a certain size; possible values:
Permitted values are between 1 and 100 MB. Around 50 kilobytes of extra space are
allowed when limiting the size of the report file to minimize the use of system resources.
If the size of the log file exceeds the indicated size by more than 50 kilobytes, then old
entries are deleted until the indicated size minus 50 kilobytes is reached.
Backup report file before shortening
If this option is enabled, the report file is backed up before shortening.
Write configuration in report file
If this option is enabled, the configuration of the on-access scan is recorded in the report
file.
Note
If you have not specified any report file restriction, a new report file is automatically
created when the report file reaches 100MB. A backup of the old report file is created. Up
to three backups of old report files are saved. The oldest backups are deleted first.
13.3 MailGuard
The MailGuard section of the Configuration is responsible for the configuration of the
MailGuard.
13.3.1 Scan
Use MailGuard to scan incoming emails for viruses and malware and for spam. Outgoing
emails can be scanned for viruses and malware by MailGuard. Outgoing emails which are
spam sent from an unknown bot on your computer can be blocked by MailGuard to
prevent spam.
Scan
Turn on MailGuard
Page 89

Avira Premium Security Suite
84
If this option is enabled, email traffic is monitored by MailGuard. MailGuard is a proxy
server which checks data traffic between the email server you use and the email client
program on your computer system: incoming emails are scanned for malware by default.
If this option is disabled, the MailGuard service is still started, but monitoring by
MailGuard is disabled.
Scan incoming emails
If this option is enabled, incoming emails are scanned for viruses and malware and for
spam . MailGuard supports POP3 and IMAP protocols. Enable the inbox account used by
your email client to receive emails for monitoring by MailGuard.
Monitor POP3 accounts
If this option is enabled, the POP3 accounts are monitored on the specified ports.
Monitored ports
In this field you should enter the port to be used as the inbox by the POP3 protocol.
Multiple ports are separated by commas.
Default
This button resets the specified port to the default POP3 port.
Monitor IMAP accounts
If this option is enabled, the IMAP accounts are monitored on the specified ports.
Monitored ports
In this field you should enter the port to be used as the inbox by the IMAP protocol.
Multiple ports are separated by commas.
Default
This button resets the specified port to the default IMAP port.
Scan outgoing emails (SMTP)
If this option is enabled, outgoing emails are scanned for viruses and malware. Emails
which are spam sent by unknown bots are blocked.
Monitored ports
In this field you should enter the port to be used as the outbox by the SMTP protocol.
Multiple ports are separated by commas.
Default
This button resets the specified port to the default SMTP port.
Note
To verify the protocols and ports used, call up the properties of your email accounts in
your email client program. Default ports are mostly used.
13.3.1.1. Action on detection
This configuration section contains settings for actions performed when MailGuard
finds a virus or unwanted program in an email or in an attachment.
Note
These actions are performed both when a virus is detected in incoming emails and when
a virus is detected in outgoing emails.
Action on detection
Page 90

Reference: Configuration options
85
Interactive
If this option is enabled, a dialog box appears when a virus or unwanted program is
detected in an email or attachment in which you can choose what is to be done with the
email or attachment concerned. This option is enabled as the default setting.
Show progress bar
If this option is enabled, the MailGuard shows a progress bar during downloading of
emails. This option can only be enabled if the option Interactive has been selected.
Automatic
If this option is enabled, you are no longer notified when a virus or unwanted program is
found. MailGuard reacts according to the settings you define in this section.
Primary action
The Primary action is the action performed when the MailGuard finds a virus or an
unwanted program in an email. If the option "Ignore email" is selected, it is also
possible, under "Affected attachments", to select the process for dealing with a virus or
unwanted program detected in an attachment.
Delete email
If this option is enabled, the affected email is automatically deleted if a virus or
unwanted program is found. The body of the email is replaced by the default text given
below. The same applies to all attachments included; these are also replaced by a default
text.
Isolate email
If this option is enabled, the complete email including all attachments is placed in
Quarantine if a virus or unwanted program is found. If required, it can later be restored.
The affected email itself is deleted. The body of the email is replaced by the default text
given below. The same applies to all attachments included; these are also replaced by a
default text.
Ignore email
If this option is enabled, the affected email is ignored despite detection of a virus or
unwanted program. However, you can decide what is to be done with the affected
attachment:
Affected attachments
The option "Affected attachments" can only be selected if the setting "Ignore email"
has been selected under "Primary action". With this option it is now possible to decide
what is to be done if a virus or unwanted program is found in an attachment.
delete
If this option is enabled, the affected attachment is deleted if a virus or unwanted
program is found and replaced by a default text.
Isolate
If this option is enabled, the affected attachment is placed in Quarantine and then
deleted (replaced by a default text). If required, the affected attachment(s) can later be
restored.
Ignore
If this option is enabled, the attachment is ignored despite detection of a virus or
unwanted program and delivered.
Warning
If you select this option, you have no protection against viruses and unwanted programs
by the MailGuard. Only select this item if you are certain you know what you are doing.
Disable the preview in your email program, never open attachments by double-clicking!
Page 91

Avira Premium Security Suite
86
13.3.1.2. Other actions
This configuration section contains other settings for actions performed when
MailGuard finds a virus or unwanted program in an email or in an attachment.
Note
These actions are performed exclusively when a virus is detected in incoming emails.
Default text for deleted and moved emails
The text in this box is inserted in the email as a message instead of the affected email.
You can edit this message. A text may contain a maximum of 500 characters.
You can use the following key combination for formatting:
inserts a line break.
Default
The button inserts a pre-defined default text in the edit box.
Default text for deleted and moved attachments
The text in this box is inserted in the email as a message instead of the affected
attachment. You can edit this message. A text may contain a maximum of 500
characters.
You can use the following key combination for formatting:
inserts a line break.
Default
The button inserts a pre-defined default text in the edit box.
13.3.1.3. Heuristics
This configuration section contains the settings for the heuristic of the scan engine.
AntiVir products contain very powerful heuristics that can proactively uncover unknown
malware, i.e. before a special virus signature to combat the damaging element has been
created and before a virus guard update has been sent. Virus detection involves an
extensive analysis and investigation of the affected codes for functions typical of
malware. If the code being scanned exhibits these characteristic features, it is reported as
being suspicious. This does not necessarily mean that the code is in fact malware. False
positives do sometimes occur. The decision on how to handle affected code is to be made
by the user, e.g. based on his or her knowledge of whether the source of the code is
trustworthy or not.
Macrovirus heuristics
Activate macrovirus heuristics
Your AntiVir product contains a highly powerful macrovirus heuristic. If this option is
enabled, all macros in the relevant document are deleted in the event of a repair,
alternatively suspect documents are only reported, i.e. you receive an alert. This option is
enabled as the default setting and is recommended.
Page 92

Reference: Configuration options
87
Advanced Heuristic Analysis and Detection (AHeAD)
enable AHeAD
Your AntiVir program contains a very powerful heuristic in the form of AntiVir AHeAD
technology, which can also detect unknown (new) malware. If this option is enabled, you
can define how "aggressive" this heuristic should be. This option is enabled as the default
setting.
Low detection level
If this option is enabled, slightly less unknown malware is detected, the risk of false
alerts is low in this case.
Medium detection level
This option is enabled as the default setting if you have selected use of this heuristic.
This option is enabled as the default setting and is recommended.
High detection level
If this option is enabled, significantly more unknown malware is detected, but there are
also likely to be false positives.
13.3.1.4. AntiBot
The AntiBot function of MailGuard prevents your computer from becoming part of a socalled bot-net and being used to send out spam emails: To send spam via a bot-net, an
attacker usually infects a number of computers with a bot that then connects to an IRC
server, opens a particular channel and waits for the command to send the spam emails.
To distinguish spam emails from an unknown bot from genuine emails, MailGuard
checks if the SMTP server and email sender for an outgoing email are included in the
lists of permitted servers and senders. If this is not the case, the outgoing emails are
blocked, i.e. the email is not sent. The blocked email is displayed in a dialog box.
Note
The AntiBot function can only be used, if the MailGuard scan of outgoing emails is
enabled (see the option Scan outgoing emails under MailGuard :: Scan).
Permitted Servers
All servers in this list are authorized by MailGuard to send emails: Emails sent to these
servers are not blocked by MailGuard. If no servers are included in the list, the SMTP
server used to send outgoing emails is not scanned. If the list is populated, MailGuard
blocks emails sent to any SMTP server not included in the list.
Input box
Enter the host name or IP address of the SMTP server you use to send your emails in this
box.
Note
You can find details of the SMTP server used by your email program to send emails in
your email program under the date the user account was created.
Add
You can use this button to include servers specified in the input box in the list of
permitted servers.
Delete
This button deletes a highlighted entry from the list of permitted servers. This button is
inactive if no entry is selected.
Clear all
Page 93

Avira Premium Security Suite
88
This button deletes all entries from the list of permitted servers.
Permitted Sender(s)
All senders in this list are authorized by MailGuard to send emails: Emails sent from this
email address are not blocked by MailGuard. If no senders are included the list, the email
address used to send outgoing emails is not scanned. If the list is populated, MailGuard
blocks emails from senders not included in the list.
Input box
Enter your email sender address(es) in this box.
Add
You can use this button to include senders specified in the input box in the list of
permitted senders.
Delete
This button deletes a highlighted entry from the list of permitted senders. This button is
inactive if no entry is selected.
Clear all
This button deletes all entries from the list of permitted senders.
13.3.2 General
13.3.2.1. Exceptions
Scanning exceptions
This table shows you the list of email addresses excluded from scanning by AntiVir
MailGuard (white list).
Note
The list of exceptions is used exclusively by MailGuard with regard to incoming emails.
Status
Icon Description
This email address will no longer be scanned for spam.
This email address will no longer be scanned for malware.
This email address will not be scanned for malware or spam.
Email address
Email that is no longer to be scanned.
Malware
When this option is enabled, the email address is no longer scanned for malware.
Spam
Page 94

Reference: Configuration options
89
When this option is enabled, the email address is no longer scanned for spam.
Up
You can use this button to move a highlighted email address to a higher position. If no
entry is highlighted or the highlighted address is at the first position in the list, this
button is not enabled.
Down
You can use this button to move a highlighted email address to a lower position. If no
entry is highlighted or the highlighted address is at the last position in the list, this
button is not enabled.
Input box
In this box you enter the email address that you want to add to the list of email
addresses not to be scanned. Depending on your settings, the email address will no
longer be scanned in future by the MailGuard.
Note
You can use wildcards when entering email addresses: * for any number of characters
and ? for one character only. Wildcards can, however, by used exclusively for email
addresses that are not scanned for spam. You will receive an error message if you
attempt to exclude an address containing wildcards from the malware scan by checking
the Malware exclusion list box. Please note that when entering addresses with
wildcards, the specified character sequence must be consistent with the structure of an
email address (*@*.*).
Warning
Please note the examples given for the use of wildcards. Only use wildcards selectively
and be careful which email addresses containing wildcards you include in the spam white
list.
Examples: Use of wildcards in email addresses (spam white list)
– virus@avira.* / = all emails with this address and any top level domain:
virus@avira.de, virus@avira.com, virus@avira.net, etc.
– *@avira.com = all emails sent from the domain avira.com: info@avira.com,
virus@avira.com, contakt@avira.com, employee@avira.com
– info@*.com = all email addresses with the top level domain com and the
address info: the second level domain can be anything: info@name1.com,
info@name2.com,...
Add
With this button you can add the email address entered in the input box to the list of
email addresses not to be scanned.
Delete
This button deletes a highlighted email address from the list.
Import Outlook address book
With this button you import the email addresses from the address book of the MS
Outlook email program into the list of exceptions. Imported email addresses are not
scanned for spam.
Import Outlook Express address book
Use this button to import the email address from the address book of the MS Outlook
Express email program into the list of exceptions. Imported email addresses are not
scanned for spam.
Page 95

Avira Premium Security Suite
90
13.3.2.2. Cache
Cache
The MailGuard cache contains data regarding the scanned emails that is displayed as
statistical data in the Control Center under MailGuard. Copies of incoming emails are
also deposited in the cache. The emails can also be used for the anti-spam module's
training functions (Good email – use for training, Spam – use for training).
Note
The anti-spam module must be activated for incoming emails to be backed up in the
cache.
Maximum number of emails to be stored in the cache
This field is used to set the maximum number of emails that are stored by MailGuard in
the cache. Emails are deleted oldest first.
Maximum storage period of an email in days
The maximum storage period of an email in days is entered in this box. After this time,
the email is removed from the cache.
Empty Cache
Click on this button to delete the emails stored in the cache.
13.3.2.3. MailGuard
AntiSpam
The AntiVir MailGuard service checks e-mails and their attachments for viruses and
unwanted programs. In addition, it can reliably protect you against spam emails.
AntiSpam
Enable AntiSpam module
Enabling this option activates the anti-spam function of MailGuard.
Mark email subject
If this option is enabled, a note is added to the original subject line when a spam email is
detected.
Simple
If a spam or phishing email is received, an addendum [SPAM] or [Phishing] is added.
This option is enabled as the default setting.
Detailed
The subject line of a spam of phishing email is prefixed by an addendum drawing
attention to the likelihood that the respective message is spam.
Enable logging
If this option is enabled, MailGuard creates a special anti-spam report file.
Use real-time black lists
Page 96

Reference: Configuration options
91
When this option is enabled, a so-called "black list" is queried in real time, which
provides additional information to classify emails of dubious origin as spam.
Timeout: n second(s)
If the information of a black list is not available after n seconds, the attempt to query the
black list is aborted.
Clear training database
Click on the button to delete the training database.
Automatically add recipients of outgoing mails to white list
If this option is enabled, the recipient addresses of outgoing emails are automatically
added to the spam whitelist (list of emails not scanned for spam, defined in MailGuard::
General :: Exceptions). Incoming emails sent from addresses on the spam white list are
not scanned for spam. They are, however, scanned for viruses and malware. This option
is disabled as the default setting.
Note
This option can only be enabled if the MailGuard scan of outgoing emails is enabled (see
the option Scan outgoing emails under MailGuard :: Scan).
13.3.2.4. Footer
Under Footer you can configure an email footer which is displayed in the emails you
send. This function requires activation of the MailGuard scan of outgoing emails (see
option Scan outgoing emails (SMTP) under Configuration::MailGuard::Scan) . You can use
the defined AntiVir MailGuard footer to confirm the sent email has been scanned by a
virus protection program. You also have the option of inserting text yourself for a userdefined footer. If you use both footer options, the user-defined text is preceded by the
AntiVir MailGuard footer.
Footer for emails to be sent
Attach AntiVir MailGuard footer
If this option is enabled, the AntiVir MailGuard footer is displayed beneath the message
text of the sent email. The AntiVir MailGuard footer confirms that the sent email has
been scanned for viruses and unwanted programs by AntiVir MailGuard and does not
originate from an unknown bot. The AntiVir MailGuard footer contains the following
text: "Scanned with AntiVir MailGuard [product version] [initials and version number of
search engine] [initials and version number of virus definition file]".
Attach this footer
If this option is enabled, the text which you insert into the input box is displayed as a
footer in sent emails.
Input box
In this input box, you can insert a text which is displayed as a footer in sent emails.
13.3.3 Report
MailGuard includes an extensive logging function to provide the user or administrator
with exact notes about the type and manner of a detection.
Page 97

Avira Premium Security Suite
92
Reporting
This group allows for the content of the report file to be determined.
Off
If this option is enabled, then MailGuard does not create a log.
It is recommended that you should turn off the logging function only in exceptional
cases, such as if you are executing trials with multiple viruses or unwanted programs.
Default
If this option is enabled, MailGuard records important information (concerning
detections, alerts and errors) in the report file, with less important information ignored
for improved clarity. This option is enabled as the default setting.
Advanced
If this option is enabled, MailGuard logs less important information to the report file as
well.
Complete
If this option is enabled, MailGuard logs all information to the report file.
Limit report file
Limit size to n MB
If this option is enabled, the report file can be limited to a certain size; possible values:
Permitted values are between 1 and 100 MB. Around 50 kilobytes of extra space are
allowed when limiting the size of the report file to minimize the use of system resources.
If the size of the log file exceeds the indicated size by more than 50 kilobytes, then old
entries are deleted until the indicated size minus 50 kilobytes is reached.
Backup report file before shortening
If this option is enabled, the report file is backed up before shortening.
Write configuration in report file
If this option is enabled, the MailGuard configuration is recorded in the report file.
Note
If you have not specified any report file restriction, a new report file is automatically
created when the report file reaches 100MB. A backup of the old report file is created. Up
to three backups of old report files are saved. The oldest backups are deleted first.
13.4 Firewall
The FireWall section of Configuration is responsible for configuration of the Avira
FireWall.
13.4.1 Adapter rules
In the Avira FireWall, an adapter represents a software simulated hardware device (e.g.
miniport, bridge connection, etc.) or a real hardware device (e.g. network card).
Page 98

Reference: Configuration options
93
The Avira FireWall displays the adapter rules of all existing adapters on your computer
for which a driver was installed.
A predefined adapter rule depends on the security level. You can change the security
level in the Online protection :: You can change the FireWall settings in the Control
Center or define your own adapter rules. If you have defined your own adapter rules, in
the FireWall section of the Control Center, the security level is set to custom.
Note
The default security level setting for all predefined rules of the Avira FireWall is
Medium.
ICMP protocol
The Internet Control Message Protocol (ICMP) is used to exchange error and
information messages on networks. The protocol is also used for status messages with
ping or tracer.
With this rule, you can define the incoming and outgoing blocked message types, the
behavior in case of flooding and the reaction to fragmented ICMP packets. This rule
serves for preventing so-called ICMP flood attacks, which results in an increase of the
CPU load of the attacked machine as it responds to every packet.
Predefined rules for the ICMP protocol
Setting: Low Setting:
Medium
Setting: High
Incoming blocked types: no
type.
Outgoing blocked types: no
type.
Assume flooding if delay
between packets is less than
50 ms.
Reject fragmented ICMP
packets.
Same rule as for
the low level.
Incoming blocked types:
several types
Outgoing blocked types:
several types
Assume flooding if delay
between packets is less than
50 ms.
Reject fragmented ICMP
packets.
Incoming blocked types: no types/several types
With a mouse click on the link a list of ICMP packet types is displayed. From this list you
can specify the desired incoming ICMP message types you want to block.
Outgoing blocked types: no types/several types
With a mouse click on the link a list of ICMP packet types is displayed. From this list you
can select the desired outgoing ICMP message types you want to block.
Flooding
With a mouse click on the link, a dialog box is displayed where you can enter the
maximum allowed ICMPA delay.
Fragmented ICMP packets
With a mouse click on the link, you have the choice to reject or not to reject fragmented
ICMP packets.
Page 99

Avira Premium Security Suite
94
TCP port scan
With this rule, you can define when a TCP port scan is assumed by the FireWall and what
should be done in this case. This rule serves for preventing so-called TCP port scan
attacks that result in a detection of open TCP ports on your computer. This kind of
attack is used to search a computer for weak spots and is often followed by more
dangerous attack types.
Predefined rules for the TCP port scan
Setting: Low Setting: Medium Setting: High
Assume a TCP port scan if
50 or more ports were
scanned in 5,000
milliseconds.
When detected, log
attacker's IP and don't
add rule to block the
attack.
Assume a TCP port scan if
50 or more ports were
scanned in 5,000
milliseconds.
When detected, log
attacker's IP and add rule
to block the attack.
Same rule as for medium
level.
Ports
With a mouse click on the link a dialog box appears in which you can enter the number of
ports that must have been scanned so that a TCP port scan is assumed.
Port scan time window
With a mouse click on this link a dialog box appears in which you can enter the time span
for a certain number of port scans, so that a TCP port scan is assumed.
Report file
With a mouse click on the link you have the choice to log or not to log the attacker's IP
address.
Rule
With a mouse click on the link you have the choice to add or not to add the rule to block
the TCP port scan attack.
UDP port scan
With this rule, you can define when a UDP port scan is assumed by the FireWall and
what should be done in this case. This rule prevents so-called UDP port scan attacks that
result in a detection of open UDP ports on your computer. This kind of attack is used to
search a computer for weak spots and is often followed by more dangerous attack types.
Predefined rules for the UDP port scan
Setting: Low Setting: Medium Setting: High
Assume a UDP port scan
if 50 or more ports were
scanned in 5,000
milliseconds.
When detected,log
attacker's IP and don't
Assume a UDP port scan
if 50 or more ports were
scanned in 5,000
milliseconds.
When detected, log
attacker's IP and add rule
Same rule as for medium
level.
Page 100

Reference: Configuration options
95
add rule to block the
attack.
to block the attack.
Ports
With a mouse click on the link a dialog box appears in which you can enter the number of
ports that must have been scanned so that a UDP port scan is assumed.
Port scan time window
With a mouse click on this link a dialog box appears in which you can enter the time span
for a certain number of port scans, so that a UDP port scan is assumed.
Report file
With a mouse click on the link you have the choice to log or not to log the attacker's IP
address.
Rule
With a mouse click on the link you have the choice to add or not to add the rule to block
the UDP port scan attack.
13.4.1.1. Incoming Rules
Incoming rules are defined to control incoming data traffic by the Avira FireWall.
Note
When a packet is filtered the corresponding rules are applied successively, therefore the
rule order is very important. Change the rule order only if you are completely aware of
what you are doing.
Predefined rules for the TCP data traffic data monitor
Setting: Low Setting: Medium Setting: High
No incoming data
traffic is blocked by
the Avira FireWall.
– Allow established
TCP connections
on 135
Allow TCP
packets from
address 0.0.0.0
with mask
0.0.0.0 if local
ports in {135}
and remote ports
in {0-65535}.
Apply forpackets
of existing
connections.
Don't log when
packet matches
rule.
Advanced:
Discard packets
that have
following bytes
– Monitor
established TCP
data traffic
Allow TCP
packets from
address 0.0.0.0
with mask
0.0.0.0 if local
ports in {0-
65535} and
remote ports in
{0-65535}.
Apply forpackets
of existing
connections.
Don't log when
packet matches
rule.
Advanced:
Discard packets
that have
 Loading...
Loading...