Avaya IP Office, IP Office ContactStore System Admin User Manual

IP Office
ContactStore System Admin
40DHB0002USEU Issue 1 (2nd September 2004)


ContactStore System Admin Page iii
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Table of Contents
Legal............................................................................................................................................ 5
Preface ........................................................................................................................................ 9
About This Guide ................................................................................................................................... 9
Intended audience ........................................................................................................................ 9
Conventions used in this guide................................................................................................... 11
Additional resources........................................................................................................................ 12
Chapter 1 .................................................................................................................................. 13
Chapter 1: System Operation ................................................................................................................... 13
System overview......................................................................................................................... 14
ContactStore recordings............................................................................................................. 15
Recording files............................................................................................................................ 15
Audio compression ..................................................................................................................... 15
ContactStore internal database ..................................................................................................15
Stored details.............................................................................................................................. 16
Chapter2 ................................................................................................................................... 17
Chapter 2: Essential Administrative Tasks .............................................................................................. 17
Distributing user instructions....................................................................................................... 18
Backing up your Server .............................................................................................................. 18
Call details database backup...................................................................................................... 18
Using third-party system management tools .............................................................................. 18
Daily preventative maintenance procedures............................................................................... 18
Weekly tasks............................................................................................................................... 20
Monthly tasks.............................................................................................................................. 21
Chapter3 ................................................................................................................................... 23
Chapter 3: Using the System Administration Pages................................................................................. 23
System Administration overview ..................................................................................................... 24
Key points................................................................................................................................... 24
Accessing the System Administration pages .................................................................................. 26
Setting and changing your password.......................................................................................... 27
System Settings ................................................................................................................................... 29
Server Settings................................................................................................................................ 29
Security ........................................................................................................................................... 30
User Security .............................................................................................................................. 31
Creating a new user account........................................................................................................... 31
Editing an existing user account...................................................................................................... 34
Status .............................................................................................................................................. 34
Alarms and Events...................................................................................................................... 35
Viewing alarms and events ............................................................................................................. 36
Clearing all events........................................................................................................................... 36
System Overview ............................................................................................................................ 36
Chapter 4 .................................................................................................................................. 39
Chapter 4: Using Search and Replay ....................................................................................................... 39
Search and Replay page overview ............................................................................................. 39
Configuring your browser............................................................................................................ 39
Adding ContactStore to a Microsoft Internet Explorer zone........................................................ 39
Accessing the Search and Replay page ......................................................................................... 40
Searching for calls........................................................................................................................... 42
Searching for calls by date and time........................................................................................... 42
Searching more selectively......................................................................................................... 43
Viewing results ................................................................................................................................ 44
Playing a call ................................................................................................................................... 45
Chapter 5 .................................................................................................................................. 47

Table Of Contents
ContactStore System Admin Page iv
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Chapter 5: Archiving Recordings.............................................................................................................. 47
Overview of DVD+RW archival ....................................................................................................... 48
Supported drives......................................................................................................................... 48
DVD+RW media control and care .............................................................................................. 48
Archival procedures......................................................................................................................... 48
Loading a disk............................................................................................................................. 49
Changing disks ........................................................................................................................... 49
Labeling a disk............................................................................................................................ 49
Verifying recorded disks ............................................................................................................. 49
Reusing old disks........................................................................................................................ 50
Appendix A ............................................................................................................................... 51
Appendix A: Support and Troubleshooting............................................................................................... 51
Troubleshooting resources.............................................................................................................. 52
System Administration page problems............................................................................................ 53
Email alarm problems ................................................................................................................. 53
ContactStore to VMPro problems ............................................................................................... 54
Search and Replay problems .......................................................................................................... 54
Contacting technical support ...................................................................................................... 57
AppendixB ................................................................................................................................ 59
Appendix B: Alarms .................................................................................................................................. 59
Glossary.................................................................................................................................... 62

ContactStore System Admin Page 5
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Legal
© 2004 Witness Systems, Inc.
All Rights Reserved.
Notice
While reasonable efforts were made to ensure that the information in this document was complete and accurate at the time of printing, Witness
Systems, Inc. and Avaya Inc. can assume no liability for any errors. Changes and corrections to the information in this document may be
incorporated in future releases.
Preventing toll fraud
"Toll fraud" is the unauthorized use of your telecommunications system by an unauthorized party (for example, anyone who is not a corporate
employee, agent, subcontractor, or person working on your company's behalf). Be aware that there may be a risk of toll fraud associated with
your system and that, if toll fraud occurs, it can result in substantial additional charges for your telecommunications services.
Avaya fraud intervention
If you suspect that you are being victimized by toll fraud and you need technical assistance or support, call Technical Service Center Toll Fraud
Intervention Hotline at +1-800-643-2353 for the United States and Canada. For additional support telephone numbers, see the Avaya Web site:
http://www.avaya.com
Select Support, then select Escalation Lists. This Web site includes telephone numbers for escalation within the United States. For escalation
telephone numbers outside the United States, select Global Escalation List.
Providing telecommunications security
Telecommunications security (of voice, data, and video communications) is the prevention of any type of intrusion to (that is, either unauthorized
or malicious access to or use of) your company's telecommunications equipment by some party. Your company's "telecommunications
equipment" includes both this Avaya product and any other voice/data/video equipment that could be accessed via this Avaya product (that is,
"networked equipment"). An "outside party" is anyone who is not a corporate employee, agent, subcontractor, or person working on your
company's behalf. Whereas, a "malicious party" is anyone (including someone who may be otherwise authorized) who accesses your
telecommunications equipment with either malicious or mischievous intent. Such intrusions may be either to/through synchronous (timemultiplexed and/or circuit-based) or asynchronous (character-, message-, or packet-based) equipment or interfaces for reasons of:
• Use (of capabilities special to the accessed equipment)
• Theft (such as, of intellectual property, financial assets, or toll-facility access)
• Eavesdropping (privacy invasions to humans)
• Mischief (troubling, but apparently innocuous, tampering)
• Harm (such as harmful tampering, data loss or alteration, regardless of motive or intent)
Be aware that there may be a risk of unauthorized intrusions associated with your system and/or its networked equipment. Also realize that, if
such an intrusion should occur, it could result in a variety of losses to your company (including, but not limited to, human and data privacy,
intellectual property, material assets, financial resources, labor costs, and legal costs).
Responsibility for your company's telecommunications security
The final responsibility for securing both this system and its networked equipment rests with you, an Avaya customer's system administrator,
your telecommunications peers, and your managers. Base the fulfillment of your responsibility on acquired knowledge and resources from a
variety of sources, including, but not limited to:
• Installation documents
• System administration documents
• Security documents
• Hardware-/software-based security tools
• Shared information between you and your peers
• Telecommunications security experts
To prevent intrusions to your telecommunications equipment, you and your peers should carefully program and configure your Avaya-provided
telecommunications systems and their interfaces. Your Avaya-provided software applications, as well as their underlying hardware/software
platforms and interfaces. Any other equipment networked to your Avaya products.
Warranty
Avaya Inc. provides a limited warranty on this product. Refer to your sales agreement to establish the terms of the limited warranty. In addition,
Avaya's standard warranty language, as well as information regarding support for this product, while under warranty, is available through the
following Web site:
http://www.avaya.com/support
Link disclaimer
Avaya Inc. is not responsible for the contents or reliability of any linked Web sites and does not necessarily endorse the products, services, or
information described or offered within them. We cannot guarantee that these links will work all of the time and we have no control over the
availability of the linked pages.
Trademarks
Avaya and IP Office are trademarks of Avaya Inc.

Legal
ContactStore System Admin Page 6
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
eQuality® is a registered trademark, and Quality is a trademark of
Witness Systems, Inc.
All other trademarks identified by the ® or ™ are registered trademarks or trademarks of their respective owners.
Third-party software license agreements
Witness Systems, Inc. ("Witness Systems")
© 2004 Witness Systems, Inc.
All rights reserved, worldwide.
All materials (regardless of form, and including, without limitation, software applications, documentation, and any other information relating to
Witness Systems, its products or services "Witness Materials") are the exclusive property of Witness Systems, and subject to the clickwrap
license agreement terms and conditions presented to you during installation of the Witness Materials. Only expressly authorized individuals
under obligations of confidentiality are permitted to access, review and use the Witness Materials. By accessing, reviewing and/or using the
Witness Materials, you expressly agree to (i) the terms and conditions contained in the Witness Systems clickwrap license agreement, (ii) not
disclose these materials to any third party except as expressly authorized by Witness Systems, and (iii) protect the Witness Materials as
confidential and trade secret information. Any unauthorized review, retransmission, dissemination or other use of the Witness Materials is strictly
prohibited. If you are not authorized to access, review or use the Witness Materials, please return the Witness Materials in their entirety (and
any copies) from where they were obtained. EXCEPT AS OTHERWISE EXPRESSLY PROVIDED IN THE WITNESS SYSTEMS CLICKWRAP
LICENSE AGREEMENT, ALL WITNESS MATERIALS ARE PROVIDED "AS IS" AND WITHOUT WARRANTY OF ANY KIND. WITNESS
SYSTEMS DOES NOT MAKE AND EXPRESSLY DISCLAIMS ALL WARRANTIES AND REPRESENTATIONS WITH RESPECT TO THE
WITNESS MATERIALS (AND ANY COPIES OF THE SAME) PROVIDED HEREUNDER OR OTHERWISE, WHETHER ORAL OR WRITTEN,
EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY, ACCURACY, NONINFRINGEMENT, SYSTEM INTEGRATION, AND FITNESS FOR A PARTICULAR PURPOSE. EXCEPT AS OTHERWISE EXPRESSLY
PROVIDED IN THE WITNESS SYSTEMS CLICKWRAP LICENSE AGREEMENT, NEITHER WITNESS SYSTEMS NOR ITS AFFILIATES
OFFICERS, DIRECTORS, EMPLOYEES, SHAREHOLDERS, AGENTS, SUPPLIERS, OR REPRESENTATIVES SHALL BE LIABLE TO YOU
OR ANY THIRD PARTY FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY OR CONSEQUENTIAL DAMAGES
WHETHER FORESEEABLE OR UNFORESEEABLE, THAT MAY ARISE OUT OF OR IN CONNECTION WITH THIS AGREEMENT EVEN IF
WITNESS SYSTEMS HAS BEEN NOTIFIED OF THE POSSIBILITY OR LIKELIHOOD OF SUCH DAMAGES OR COSTS OCCURRING, AND
WHETHER SUCH LIABILITY IS BASED ON CONTRACT, TORT, NEGLIGENCE, STRICT LIABILITY, PRODUCTS LIABILITY OR
OTHERWISE.
Castor software
Castor Copyright 2000-2002 (C) Intalio Inc. All Rights Reserved.
Redistribution and use of this software and associated documentation ("Software"), with or without modification, are permitted provided that the
following conditions are met:
• Redistributions of source code must retain copyright statements and notices. Redistributions must also contain a copy of this document.
• Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
• The name "ExoLab" must not be used to endorse or promote products derived from this Software without prior written permission of Intalio
Inc. For written permission, please contact info@exolab.org.
• Products derived from this Software may not be called "Castor" nor may "Castor" appear in their names without prior written permission of
Intalio Inc. Exolab, Castor and Intalio are trademarks of Intalio Inc.
• Due credit should be given to the ExoLab Project
(http://www.exolab.org/).
THIS SOFTWARE IS PROVIDED BY INTALIO AND CONTRIBUTORS "AS IS" AND ANY EXPRESSED OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL INTALIO OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING
IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
JBoss
JBoss is licensed under GPL license. See http://www.gnu.org for details.
JBoss and JBoss Group are a registered trademark and servicemark of Mark Fleury under operation by the JBoss Group, LCC.
Apache
This product includes software developed by the Apache Software Foundation (http://www.apache.org/).
The Apache Software License, Version 1.1
Copyright (c) 2000 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
• Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
• Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
• The end-user documentation included with the redistribution, if any, must include the following acknowledgment: "This product includes
software developed by the Apache Software Foundation (http://www.apache.org/)." Alternately, this acknowledgment may appear in the
software itself, if and wherever such third-party acknowledgments normally appear.

Legal
ContactStore System Admin Page 7
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
• The names "Apache" and "Apache Software Foundation" must not be used to endorse or promote products derived from this software
without prior written permission. For written permission, please contact apache@apache.org.
• Products derived from this software may not be called "Apache," nor may "Apache" appear in their name, without prior written permission of
the Apache Software Foundation.
THIS SOFTWARE IS PROVIDED ''AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE APACHE SOFTWARE FOUNDATION OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on behalf of the Apache Software Foundation. For more information
on the Apache Software Foundation, please see
http://www.apache.org/.
Portions of this software are based upon public domain software originally written at the National Center for Supercomputing Applications,
University of Illinois, Urbana-Champaign.
Avaya support
For support please contact with your system maintainer.

ContactStore System Admin Page 9
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Preface
About This Guide
The ContactStore for IP Office System Administration Guide provides details of the ContactStore for IP
Office operation, as well as other information needed for server maintenance and updating. This guide
also includes instructions for searching and replaying recordings, archiving recordings, and system
troubleshooting.
Intended audience
This document is intended to be used by the Administrator of the ContactStore.
Summary of information included in this guide
This guide provides the following information:
Chapter title Description
Chapter 1:
System Operation
This chapter provides an in-depth look at the
ContactStore for IP Office features, functions, and
limitations.
Chapter 2:
Essential Administrative
Tasks
This chapter provides an overview of procedures that
you should complete to ensure that the system is
operating optimally.
Chapter 3:
Using the System
Administration Pages
This chapter describes how to use the System
Administration web pages to maintain, update, and
monitor your system.
Chapter 4:
Using Search and Replay
This chapter discusses the Search and Replay
application.
Chapter 5:
Archiving Recordings
This chapter describes ContactStore’s internal
DVD+RW archival option.
Appendix A:
Troubleshooting
This appendix describes how to diagnose and correct
problems with ContactStore.
Appendix B:
Alarms
This appendix lists the alarm conditions that may be
reported and offers suggestions for clearing the alarms.
Glossary
The glossary defines the terms you need to understand
ContactStore.
Index
The index lists topics that you can use to access
information in the guide quickly.

preface
ContactStore System Admin Page 10
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
preface
ContactStore System Admin Page 11
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
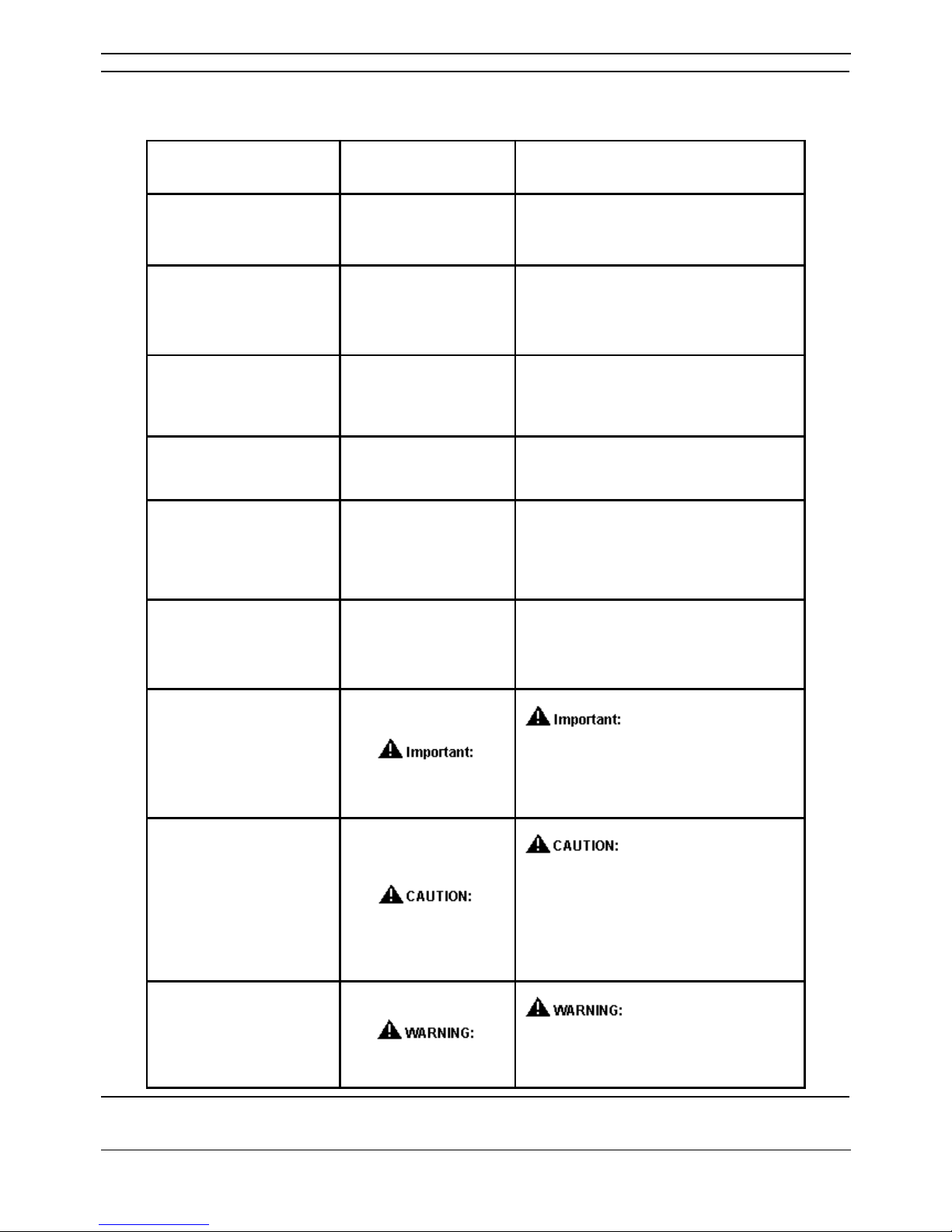
Conventions used in this guide
The following table shows how user input, output and instructions are highlighted in this guide, as well as
special notations that you will see as you use this guide.
To show... This style is used For example...
Information shown on
screen
Fixed width
You should see the prompt below:
login:
Characters that you
should type exactly as
shown
Fixed width, bold
Enter the following command:
mount
/mnt/cdrom
Characters that you
should replace with
appropriate information
Fixed width, bold
italic
Browse to the new server by entering
http://servername:8080
Menu selections,
buttons and tabs
Bold
Click on the Install button.
Helpful hints that can
improve the efficiency or
effectiveness of your
work
Tip:
Tip:
Use a photocopy of the Header List
Worksheet to plan each header list.
Important details that we
want to make sure that
you do not overlook
Note:
Note:
Media Encryption may or may not
show up on this form.
Advice that can help you
avoid undesirable
results
If the network does not meet the three
conditions listed, there will be no
media resources.
Situations that can
result in:
• Harm to software
• Loss of data
• An interruption in
service
Perform this procedure only after
normal business hours. This
procedure restarts all links on the
interface, and can cause a temporary
loss of service.
Situations that can
result in harm to
hardware or equipment
A fractured or broken ferrite is not
effective for EMC control.

preface
ContactStore System Admin Page 12
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Additional resources
The following guides contain additional information you may find helpful.
• ContactStore for IP Office Prerequisites Guide
• ContactStore for IP Office Installation Guide
• ContactStore for IP Office Search and Reply Instructions
• Avaya IP Office 3.0 Manager Application
• Avaya IP Office 3.0 Voicemail Pro Installation
• Avaya IP Office 3.0 Licence & Feature Key Guide
• Avaya IP Office Installation Manual
Note:
Avaya IP Office documentation is available through the Avaya online support Web site,
http://support.avaya.com.

ContactStore System Admin Page 13
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Chapter 1
Chapter 1: System Operation
It is important to understand how the ContactStore operates so that you can best maintain and update it.
This chapter takes you from an overview diagram through to a detailed discussion of the operation of the
system.
Chapter1
ContactStore System Admin Page 14
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
System overview
ContactStore for IP Office complements the voice recording capabilities of Voicemail Pro (“VMPro”). It
stores and catalogs the recordings so that they are easily accessible for later retrieval. Any recordings
that you instruct VMPro to “send to the Voice Recording Library” are placed in a folder that is visible to
ContactStore. ContactStore checks this folder every few seconds and if it finds a new recording file
there, it:
• Reads the information about the recording from the file
• Compresses the audio to 16kbps G.726 format
• Stores the resultant file to hard disk
• Updates its integral database with details of the recording
• Deletes the original .wav file from the handover directory.
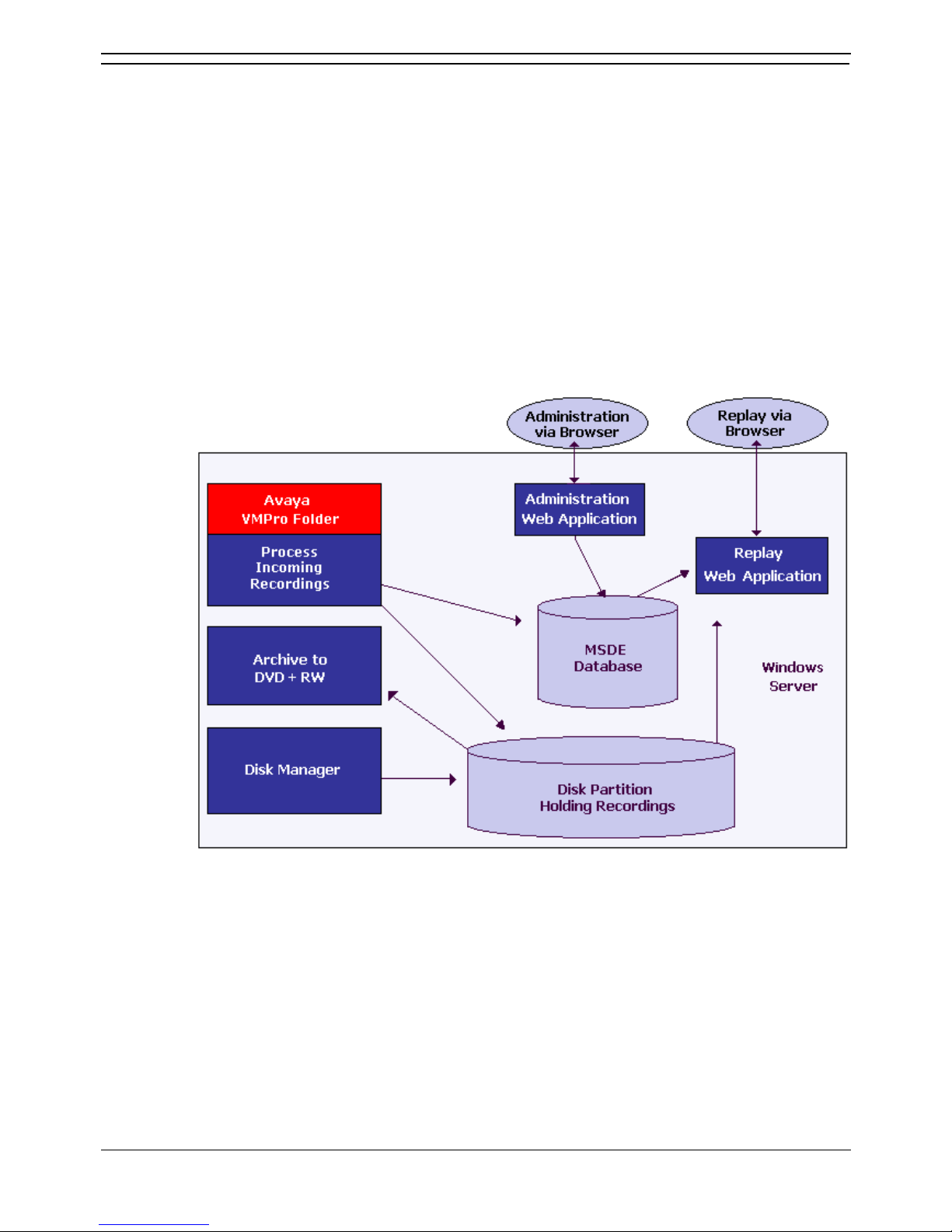
ContactStore for IP Office components
ContactStore is designed to run on the same server as VMPro. The ContactStore application contains
several distinct components as shown in the following figure:
The major functional components of the ContactStore server are:
• A folder into which VMPro deposits .wav files as recordings complete.
• A file path into which call contents and derived files are written as industry standard .wav and
.xml files.
• An MSDE database into which details of all recorded calls are inserted.
• A browser-based call search and replay application.
• A browser-based system configuration and status monitoring application.
• Disk space management - Oldest recordings are automatically deleted as needed.
• Optional archive management - Recordings are automatically written to a DVD+RW drive.
The rest of this chapter provides details about these components.
Chapter1
ContactStore System Admin Page 15
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
ContactStore recordings
ContactStore stores recorded calls in specific formats with certain security in place. As you use the
ContactStore, you need to be aware that access to recordings is strictly controlled according to the
security constraints you configure within the System Administration pages. Each recording has an
owner; the call owner is the number of the station that recorded the call.
You can specify to which stations each user has replay rights; the user can search for and replay all calls
“owned” by those stations. Typically an individual may be given rights to replay calls owned by their
station number while managers may have rights to the station numbers of all of their staff.
Recording files
Calls are stored in an industry standard .wav file.
When each call is completed and as each recording becomes available, ContactStore compresses the
audio if necessary, and updates the database with a record of the call. These files are stored in a
hierarchy of folders beneath a root path, which defaults to \calls beneath the path in which you installed
the software.
Every recording results in:
• One .wav file
• One .xml file
Other file types may also be present as described below.
You should always back up both .xml and .wav files to ensure a complete record of the content and
context of your recordings. When in use, the integral DVD archiver automatically backs up these files.
WAV files
The .wav files contain the actual audio of the recording. You can double-click some .wav files to play
them directly. Others are in audio formats that are not directly supported by Microsoft's Media Player;
these must be converted into a supported format before they can be played. Since ContactStore's
Search and Replay application does this conversion automatically, you do not need to access these files
directly.
XML files
The. xml files contain details about the recorded calls. Although most users typically search against the
ContactStore’s database of calls, you can view these files directly in a browser if required.
Within each .xml file there are:
• All the details known about this recording. Most of the information, but not all, will be inserted into
the calls database. Some of the information is only of interest for diagnostic and maintenance
purposes.
• A link to the final audio file
• Start and end time
Audio compression
ContactStore uses the G.726 16kbps ADPCM compression standard, which provides the best
compromise between storage capacity and CPU loading.
ContactStore is designed to perform compression as a background task, which does not impact your
ability to record, search or play other calls. It takes approximately 1 minute to compress a two hour
recording; there is a delay (from a few seconds to a few minutes) between completion of a recording and
its availability in the Search and Replay application.
ContactStore internal database
If you have retained all of the .xml and .wav files as described above, then you have kept all of the
details about the recordings you have made. However, the system uses Microsoft's MSDE database to
hold this information in more readily accessible forms. This database is located on the ContactStore
server.

Chapter1
ContactStore System Admin Page 16
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
To avoid having to repopulate these databases in the event of corruption or disk failure, ContactStore
automatically backs up the database content to a path you specify. A full backup is performed weekly
with daily incremental backups.
Stored details
The database stores details of the recordings as well as details of the ContactStore configuration.
Recording details
The call details database is stored beneath the location into which you installed ContactStore, under the
/MSSQL sub-directory and occupies approximately 1KB per call.
To allow you to search for calls easily, the details of the recordings are normally inserted into this
database. It contains one record for each call recorded and additional records for each party on the call
and the owner of the call. The information stored for each call is:
• A unique reference for the recording
• The start date and time
• The duration of the recording
• The name and number of the parties on the call—where this was available to IP Office (through
ANI, CLI or DNIS) at the time of the call.
• The direction of the call (incoming, outgoing, or internal)
• The owner of the recording.
• The target or dialed number, which may be different from the number that actually took the call.
Configuration details
Several tables hold details of system configuration, such as file paths, timeouts and user authorization
rights.
ContactStore System Admin Page 17
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Chapter2
Chapter 2: Essential Administrative Tasks
This chapter provides an overview of procedures that you should complete to ensure that the recording
solution is operating optimally and that recordings can be easily found and replayed when required.
This section includes routine operations such as:
• Distributing instructions to your users
• Including the ContactStore server in routine system monitoring with third-party software
• Performing daily, weekly and monthly preventative maintenance procedures and archive
management procedures
It also addresses what do if your switch or recording system changes.
Note: For comprehensive instructions on system administration, you should attend the IP Office
Advanced Applications Workshop, course code AVA00484H00. Course details and registration are
available through the following website. www.avaya-learning.com
The System Administrator is responsible for completing the maintenance procedures
outlined in this chapter. Avaya is not responsible for lost data.
Chapter2
ContactStore System Admin Page 18
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Distributing user instructions
A template document “ContactStore IP Office User Guide.doc” is included on the Installation CD. This
document provides basic instructions for end users of the system, specifically, those who will make and
replay recordings using it.
Customize this document as follows:
• Replace the URL in the document with the URL of your ContactStore.
• Check the document itself for additional customization instructions.
Backing up your Server
You are strongly advised to install and configure an automated backup tool to provide a recoverable
image of your server. You should back up the partitions onto which you have installed ContactStore, as
well as the operating system partition(s).
Call details database backup
If you configure a Database backup path using the Administration pages, ContactStore will automatically
write a backup of the database each night. The backup occurs just after 1am every morning. On Sunday
mornings a full backup is made; on other days an incremental backup is added to this file. Each week,
the previous week’s backup file is renamed from ContactStore.dump to ContactStore.old and the
previous week’s file is deleted.
Therefore, you need to archive ContactStore.dump file every night, either before 1am or after 2am, to
avoid colliding with the database backup. If you specify a fileshare on a remote computer, you will need
to configure a fileshare to allow access to a user account and then set the ContactStore service to 'Run
as...' that user. To allow ContactStore to function, you must ensure this user account has at least the
same access rights as the local system account which the service uses by default.
Using third-party system management tools
You should consider including the monitoring of ContactStore components within your other system
management regimes such as:
• Microsoft System Management Server (SMS)
• CA Unicenter
• HP OpenView
As a minimum, these tools should monitor the health and accessibility of the servers on the network.
Ideally, you should also monitor the services' web log files.
The information contained in this guide was correct at the time of publication. These are
industry standard tools and licenses. Avaya is not responsible for any problems that may be encountered
when using these products.
Daily preventative maintenance procedures
Unless you have fully automated alerting of these conditions, the following procedures should be carried
out at the start of each day:
• Alarms . Check the Alarms and Events page for new problems.
• Disk capacity. Check the available disk space daily for the partition on which your recordings
are stored until the disk has filled and starts to wrap. Past that point, the amount of free space
should stay close to 1GB.
• ContactStore is designed to run with the partition holding the recordings almost full. This
maximizes the number of recordings that are available online to you.
• Unless you have explicitly disabled disk management, the ContactStore's disk manager thread
will delete files on a FIFO (First In First Out) basis to preserve the specified amount of free space.
• Web Logs. Check the contents of the web log files and examine any errors logged since the
previous check. The default installation location for the web logs is in the sub-folder \logs.
Chapter2
ContactStore System Admin Page 19
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
While the above directory holds the ContactStore's log files (csipo.log), you may also want to check for
server errors in \tomcat5024\logs.
Look at all error and warning messages, not just those generated by the ContactStore services.
• System Status. Some problems are not easily trapped automatically; check the system status
regularly via the System Overview page. Verify that all figures are in line with expectations and
investigate any anomalies, such as no recordings today.
The table below summarizes the values to check and what constitutes an abnormal reading.
Variable Check this value... If not, it probably indicates that...
ContactStore Server
Calls recorded today >0
Either no one is using recording or
there is a major problem.
Age of oldest call
Is the date you
installed the
system or within
acceptable bounds
once your disk has
filled.
The disk is filling too rapidly forcing
calls to be overwritten that are younger
than your planned retention period.
Archival (only shows if drive is configured)
Current Media Label Is a valid label
Drive is empty, disk is corrupt, or drive
is broken.
Remaining Space Is 0.1GB or higher The disk should be changed.
• Confirm recording and replay. To confirm recording and replay:
- Check the daily recording count as listed in the table to verify that calls are being uploaded into the
database.
- Use the Search and Replay page to select the most recent calls to verify that calls are accessible.
- Confirm that the start time of these calls is as you would expect. Verify that the start time corresponds
to the most recent calls made on the extensions being recorded.
- Confirm that these calls are playable and that audio quality is good.
• Archive. If using DVD+RW archive, check the current disk's available capacity. Change the disk
if capacity is less than 0.8GB of the total disk. Total disk capacity allowed is 7.0GB. However,
due to limitations in the DVD+RW writing, the last 0.6GB is not available for individual files to be
written to and hence cannot be used by ContactStore.
Be sure that the disks are not filled completely; there is then an indeterminate time before they are
changed during which calls cannot be written to removable media.
If you change them before they fill, then calls are written to removable media as soon as a reasonable
volume of recordings is available (100MB) or 24 hours have elapsed since the oldest unarchived call
started.

Chapter2
ContactStore System Admin Page 20
IP Office 40DHB0002USEU Issue 1 (2nd September 2004)
Weekly tasks
As you become confident of the normal operation of your recorder, you can reduce the frequency of the
daily tasks. For example, if you know that the rate at which your disk is filling is much less than the
available space, you can check it weekly.
Perform the following tasks each week:
• Disk capacity-main recording store. When ContactStore is first installed, the disk is almost
empty. As it gradually fills, you should note the rate at which it is being used (at least weekly) and
extrapolate to estimate when the disk will be full. At this point, the ContactStore will begin
deleting the oldest calls to make room for new ones.
If this happens to calls that are younger than planned, check the configuration of the ContactStore to
ensure the correct calls only are being recorded. Add additional disk capacity to the partition before it
fills.
• Disk capacity check-all partitions. Check the available space on any other disk partitions. Verify
that these other drives have sufficient space. Ideally, set up an alert to warn you if they drop below
100MB. Accumulated temporary files or log files that may need to be manually purged can cause
this drop in available space.
When purging files, remember that files you delete go to the Recycle Bin directory and that the space
they occupy is not freed until you click Empty Recycle Bin.
• Call detail database purging. If you have enabled automatic purging of aged call detail
records, you should still monitor the size of the calls database during the first few months of use
so that you can predict how large it will get by the time old records begin to be purged.
Many customers plan never to purge call detail records; they add disk capacity every year or two as the
database grows. If you do this, you should upgrade your server every few years to compensate for the
increasing size of the database and the reduction in search and update speed.
• Complete Server Backup. Changes to system configuration that affect user access rights are
stored in the MSDE database, so they are backed up along with the call detail records.
If you are not using RAID arrays, Avaya strongly recommends that you take a ghost image of the
ContactStore server (or at least of the partitions on which your operating system and program files are
installed) to allow for easy restoration in the event of catastrophic system failure.
 Loading...
Loading...