Avaya 8400B Plus User Manual

8400B Plus Data Module
User’s Guide
Comcode 107893323
555-020-709
Issue 2
November 1996

Copyright 1996, Avaya Inc.
All Rights Reserved
Printed in USA
Notice
While reasonable efforts were made to
ensure that the information in this document was complete and accurate at the time of printing, Avaya can
assume no responsibility for any errors. Changes and
corrections to the information contained in this document may be incorporated into future reissues.
Your Responsibility for Your Syst em’s Secu-
Toll fraud is the unauthorized use of your tele-
rity
communications system by an unauthorized party, for
example, persons other than your company’s employees, agents, subcontractors, or persons working on
your company’s behalf. Note that there may be a risk
of toll fraud associated with your telecommunications
system, and if toll fraud occurs, it can result in substantial additional charges for your telecommunications services.
You and your System Manager are responsible for the
security of your system, such as programming and
configuring your equipment to prevent unauthorized
use. The System Manager is also responsible for
reading all installation, instruction, and system administration documents provided with this product in order
to fully understand the features that can introduce risk
of toll fraud and the steps that can be taken to reduce
that risk. Avaya does not warrant that this product is
immune from or will prevent unauthorized use of common-carrier telecommunication services or facilities
accessed through or connected to it. Avaya will not be
responsible for any charges that result from such
unauthorized use.
Avaya Fraud Intervention If you suspect you are
being victimized by toll fraud and you need technical
support or assistance, call Technical Service Center
Toll Fraud Intervention Hotline at 1 800 643-2353.
Warranty Avaya provides a limited warranty on this
product. Refer to the “Limited Use Software License
Agreement” card provided with your package.
CE Compliant The CE mark on this product indi-
cates technical compliance with the European Council
EMC Directive 89/336/EEC.
Federal Communication s C ommission Statement: Part 15: Class A Statement
figuration of this equipment has been tested and found
to comply with the limits for a Class A digital device,
pursuant to Part 15 of the FCC Rules. These limits are
designed to provide reasonable protection against
harmful interference when the equipment is operated in
a commercial environment. This equipment generates,
uses, and can radiate radio-frequency energy and, if
not installed and used in accordance with the instruction manual, may cause harmful interference to radio
communications. Operation of this equipment in a residential area is likely to cause harmful interference, in
which case the user will be required to correct the interference at his or her own expense.
The US Con-
Trademarks DEFINITY is a registered trademark of
Avaya. Hayes is a registered trademark of Hayes
Microcomputer Products, Inc. Microsoft and MS-DOS
are registered trademarks of Microsoft Corporation.
Smartmodem is a trademark of Hayes Microcomputer
Products, Inc.
Ordering Information
Call: US Voice:1 800 457 1235
US Fax:1 800 457 1764
non-US Voice:+1 410 568 3680
non-US Fax:+1 410 891 0207
Write: Globalware Solutions
200 Ward Hill Avenue
Haverhill, MA 01835 USA
Order: Document No. 555-020-709
Comcode 107893323
Issue 2, November 1996
You can be placed on a Standing Order list for this and
other documents you may need. Standing Order will
enable you to automatically receive updated versions
of individual documents or document sets, billed to
account information that you provide.
Acknowledgment This document was prepared by
the Product Documentation Development group, Avaya
Inc., Middletown, NJ.

Contents
About This Document vii
■ Purpose vii
■ Organization of This Guide vii
■ How to Order Documentation ix
■ How to Comment on This Document ix
■ Conventions Used x
■ Security Issues xi
■ Lucent Technologies Fraud Intervention xv
■ Related Documentation xv
Important Safety Instructions xvii
1 Introduction 1-1
■ Overview 1-1
■ Features 1-2
■ Physical Description 1-3
2 Installation 2-1
■ About the Terminal Device 2-1
■ Selecting the Correct Installation Procedure 2-2
Issue 2 November 1996 iii

Contents
■ Hardware Installation 2-8
■ Initial System Checks 2-11
■ Installation Options 2-12
■ Changing Installation Options 2-16
■ LED Indications 2-18
■ Selecting PC Communications Packages 2-21
3 Configuration and Operation 3-1
■ Operating Modes 3-1
■ Issuing Commands 3-2
■ Configuration Parameters 3-7
■ Data Operation 3-10
■ Voice Operations 3-18
4 Troubleshooting 4-1
■ How to Use This Chapter 4-1
iv Issue 2 November 1996
Contents
A AT Command Set A-1
B Dial Modifiers B-1
C S-Registers C-1
D Isolating Problems Using Loopback Data Tests D-1
■ Data Loopback Test D-1
■ Local Loopback Test D-3
■ Local Loopback Test with Self-Test D-4
■ Remote Loopback Test D-6
■ Remote Loopback Test with Self-Test D-8
■ Loop-Around Data Test Arrangement D-10
Issue 2 November 1996 v
Contents
E Quick-Reference Summaries E-1
GL Glossary GL-1
IN Index IN-1
vi Issue 2 November 1996

About This Document
Purpose
The purpose of this guide is to provide information for installing, operating,
testing, and troubleshooting the 8400B Plus Data Module.
Organization of This Guide
The following paragraphs summarize the chapters and appendices contained in
this guide.
■ Chapter 1, “Introduction,” discusses the basic operating features of the
8400B Plus Data Module and describes the external indicators and
connectors.
■ Chapter 2, “Installation,” describes the hardware and software required
for installing the 8400B Plus Data Module, and outlines procedures for
preparing the 8400B Plus Data Module for operation.
■ Chapter 3, “Configuration and Operation,” describes how to issue
commands to your 8400B Plus Data Module. In addition, it describes
how to change, store, and recall configuration parameters, and outlines
how to create and save custom configuration profiles. It also provides
some basics on the operation of the 8400B Plus Data Module, outlines a
typical on-line data session, and discusses more advanced command
usage with example command lines. If you are not familiar with the AT
Issue 2 November 1996 vii

About This Document
command interface and you are not using your 8400B Plus Data Module
with a PC communications package, you will need to familiarize yourself
with this chapter.
■ Chapter 4, “Troubleshooting,” describes procedures for troubleshooting
problems that may be encountered while configuring and operating the
8400B Plus Data Module.
■ Appendix A, “AT Command Set,” contains an explanation of each AT
command accepted by the 8400B Plus Data Module.
■ Appendix B, “Dial Modifiers,” contains an explanation of each Dial
Modifier accepted by the 8400B Plus Data Module.
■ Appendix C, “S-Registers,” contains an explanation of each S-register
used by the 8400B Plus Data Module.
■ Appendix D, “Isolating Problems Using Loopback Data Tests,” provides
information on how to perform loopback tests and how to isolate
problems using the 8400B Plus Data Modul e.
■ Appendix E, “Quick-Reference Summaries,” contains quick-reference
summaries of AT commands, S-registers, result codes, factory-default
configuration settings, EIA/TIA-574 pin-outs, and the ASCII character
set.
A glossary and an index are provided at the rear of this guide.
viii Issue 2 November 1996
How to Order Documentation
How to Order Documentation
This document’s order number is 555-020-709. To order this document:
Call: Lucent Technologies Publications Center
Voice 1 800 457-1235
Fax 1 800 457-1764
International Voice 317 361-5353
International Fax 317 361-5355
OR
Write: Lucent Technologies Publications Center
P.O. Box 4100
Crawfordsville, IN 47933
For more information about Lucent Technologies documents, see Business
Communications Systems Publications Catalog, 555-000-010.
How to Comment on This Document
To comment on this document, please return the comment card at the back of
the document.
Issue 2 November 1996
ix
About This Document
Conventions Used
Throughout this guide, command lines that are typed are shown in
typewriter-style characters, and responses that the 8400B Plus Data Module
returns are shown in italics. The following is an example.
AT H
ENTER
OK
Note the following characteristics of the display representation:
■ The first line is a command line as it should be typed. The symbol,
ENTER
when shown, indicates that you must press the Enter or Return key to
complete the command line.
■ Spaces are used to separate commands in some examples shown in this
guide. In actual use, the spaces may be typed, but they are not required.
■ The second line in the example shows a typical response returned by the
8400B Plus Data Module.
Throughout this document, toll fraud security hazards are indicated by an
exclamation point inside a triangle and the words Security Alert.
!
Security Alert:
Security Alert indicates the presence of a toll fraud security hazard. Toll
fraud is the unauthorized use of your telecommunications system by an
unauthorized party (for example, persons other than your company’s
employees, agents, subcontractors, or persons working on your
company’s behalf). Be sure to read “Your Responsibility for Your System’s
Security” on the inside front cover of this book and ‘‘Security Issues’’ on
page xi of this section.
x Issue 2 November 1996

Security Issues
Security Issues
As a Lucent Technologies customer, you should be aware that there is an
increasing problem of telephone fraud. Telephone toll fraud can occur in many
forms, despite the numerous efforts of telephone companies and telephone
equipment manufacturers to control it. Some individuals use electronic devices
to prevent or falsify records of these calls. Others charge calls to someone
else’s number by illegally using lost or stolen calling cards, billing innocent
parties, clipping onto someone else’s line, or breaking into someone else’s
telephone equipment physically or electronically.
Today security problems are not just limited to toll fraud. There have been sharp
increases in reported incidents of hackers: criminals skilled in reprogramming
computer systems, accessing telecommunications systems through remote
administration or maintenance ports. These ports cannot be used to place
phone calls, but hackers can gain control over the setup of the system. Through
these ports, hackers create security “holes” to allow unauthorized calling — a
serious form of electronic vandalism.
Maintenance ports are their most recent target of abuse. In this scenario,
hackers find a private branch exchange (PBX) maintenance port number with
their “war dialer”; a device that randomly dials telephone numbers until a
modem or dial tone is obtained. They then “hack” the user ID and password,
sometimes just by using the PBX defau lt pas sw or ds , to enter your sys tem.
This is the most dangerous type of abuse because, once in your system, the
hackers have control over all the administrative commands. While in your
system, they have been known to:
■ Turn on Remote Access or Direct Inward System Access (DISA).
Hackers have been known to change the system at 8:00 p.m. to allow
fraudulent calls. Then, at 3:00 a.m., they reprogram the system back to
its original configuration. One company was hit three weekends in a row
before it realized what was happening.
■ Turn off Call Detail Recording (CDR) or Station Message Detail
Recording (SMDR), hack your system all weekend, then turn it back on
before Monday morning. This is especially disturbing to managers who
Issue 2 November 1996
xi

About This Document
are security conscious and check the CDR/SMDR reports every morning
looking for suspicious activity. They will not see records of the calls
because CDR/SMDR was turned off by the hackers. The administrator
may notice the absence of CDR/SMDR records for evening, night, and
weekend calls made by employees.
NETCON Data Channels
The NETCON (Network Control) data channels provide internal access to the
system management capabilities of your DEFINITY® Communications System.
If the 8400B Plus Data Module is connected to a modem, or there is a modem
pool, your system may be at risk for toll fraud.
Expert toll hackers will target the administration and maintenance capabilities of
your system. Once criminals gain access to the administration port, they are
able to change system features and parameters so that fraudulent calls can be
made. In a modem pool or NETCON modem installation, this would also permit
a hacker to transfer to a NETCON extension, get data tone, and obtain a login
prompt — permitting transfer out to make toll calls.
If the data module or modem must be connected to a NETCON administration
port, then deny access to any high-risk features or endpoints by placing them in
restricti on grou ps on the D EFINITY Communi cations System. This rest ricts th eir
accessibility from the incoming facility or endpoints that could transfer a call.
Also, use Class of Restriction to Class of Restriction (COR-to-COR) to restrict
stations from calling the NETCON data channels, so that only CORs allowed to
access the maintenance port are able to do so. For example, if voice mail
extensions have a COR of 9, and extensions assigned to NETCON channels
have a COR of 2, ensure that COR 9 does not have access to COR 2. Anyone
not authorized to use the NETCON channel should not be able to access it.
In addition, a data module or modem port used for voice mail maintenance or
administrative access is often a switch extension. It should be restricted in the
same manner as the NETCON channel.
xii Issue 2 November 1996

Security Issues
PBX Security Measures
Everyone in your company who uses the telephone system is responsible for
system security. Users and attendants need to be aware of how to recognize
and react to potential hacker activity. Informed people are more likely to
cooperate with security measures that often make the system less flexible and
more difficult to use.
Implement the following general security measures to protect your PBX, and
discourage the unauthorized use of your communications system.
■ Never program passwords or authorization codes onto auto-dial buttons.
Display phones reveal the programmed numbers, and internal abusers
can use the auto-dial buttons to originate unauthorized calls.
■ Discourage the practice of writing down passwords. If a password needs
to be written down, keep it in a secure place and never discard it while it
is active.
■ Attendants should tell their system manager if they answer a series of
calls where there is silence on the other end or the caller hangs up.
■ Users who are assigned voice mailboxes should frequently change
personal passwords and should not choose obvious passwords.
■ Advise users with special telephone privileges (such as Remote Access,
voice mail outcalling, and call forwarding off-switch) of the potential risks
and responsibilities.
■ Be suspicious of any caller who claims to be with the telephone company
and wants to check an outside line. Ask for a callback number, hang up,
and confirm the caller’s identity.
■ Never distribute the office telephone directory to anyone outside the
company; be careful when discarding it.
■ Never accept collect phone calls.
■ Never discuss your telephone system’s numbering plan with anyone
outside the company.
Issue 2 November 1996
xiii

About This Document
■ Change passwords frequently (at least quarterly). Set password
expiration times and tell users when the changes go into effect.
Changing passwords routinely on a specific date (such as the first of the
month) helps users to remember to do so.
■ Establish well-controlled procedures for resetting passwords.
■ Limit the number of invalid attempts to access a voice mail to five or less.
■ Monitor access to the dial-up mainte nan ce port. C han ge the acces s
password regularly and issue it only to authorized personnel. Consider
using the Remote Port Security Device (RPSD) — a Lucent
Technologies product that helps protect your administration and
maintenance ports from unauthorized access.
■ Create a PBX system management policy concerning employee turnover
and include these actions:
— Delete all unused voice mailboxes in the voice mail system.
— If an employee is terminated, immediately delete any voice
mailboxes belonging to that employee.
— If a terminated employee had Remote Access calling privileges
and a personal authorization code, remove the authorization code
immediately.
— If barrier codes and/or authorization codes were shared by the
terminated employee, these should be changed immediately.
Notify the remaining users as well.
— If the terminated employee had access to the system
administration interface, their login ID should be removed (G3V3
or later). Any associated passwords should be changed
immediately.
■ Back up system files regularly to ensure a timely recovery should it be
required. Schedule regular, off-site backups.
■ Keep the attendant console and supporting documentation in an office
that is secured with a changeable combination lock. Provide the
combination only to those individuals having a real need to enter the
office.
xiv Issue 2 November 1996
Lucent Technologies Fraud Intervention
■ Keep telephone wiring closets and equipment rooms locked.
■ Keep telephone logs and printed reports in locations that only authorized
personnel can enter.
■ Design distributed reports so they do not reveal password or trunk
access code information.
Lucent Technologies Fraud
Intervention
If you suspect you are being victimized by toll fraud and you need technical
support or assistance, call Technical Service Center Toll Fraud Intervention
Hotline at 1 800 643-2353.
Related Documentation
For additional information about securing against toll fraud, refer to the following
document:
Document # Document Title
555-025-600 BCS Products Security Handbook
In addition, the following manuals may provide helpful information while
installing and using the 8400B Plus Data Module. Since each user may have
different equipment and software preferences or availability, only generic titles
are given for the manuals.
If you are using a terminal device other than a PC:
User’s guide for your terminal device. You may need information about
the configuration and capabilities of your terminal device from that
manual during the installation and preliminary operation of the 8400B
Plus Data Module.
Issue 2 November 1996
xv

About This Document
If you are using a PC as your terminal:
User’s guide for Microsoft
explanations of commands used by your PC to install, configure, and run
your PC communications package.
User’s guide for your PC communications package. You may need this
guide for information on how to configure your terminal emulation
software to access the 8400B Plus Data Module.
®
MS-DOS®. You may need this reference for
xvi Issue 2 November 1996

Important Safety Instructions
Important Safety Instructions
When using your equipment, basic safety precautions, including the following,
should always be followed to reduce the risk of fire, electric shock, and injury to
persons:
■ Read and understand all instructions.
■ Follow all warnings and instructions marked on the product.
■ This product can be hazardous if immersed in water. To avoid the
possibility of electric shock, do not use when you are wet. If you
accidentally drop it into water, do not retrieve it until you have first
unplugged the power cord from the alternating current (AC) outlet, the
line cord from the modular wall jack, and all interconnecting cords from
the terminal equipment. Do not plug the cords back in until the product
has dried thoroughly.
■ Avoid touching the product during electrical storms in your immediate
area. There is a remote risk of electric shock from lightning. Even though
protective measures may have been installed to limit electrical surges
from entering your business, absolute protection from lightning is
impossible.
■ Never push objects of any kind through housing slots as they may touch
hazardous voltage points or short out parts that could result in a risk of
electrical shock. Never spill liquid of any kind on the product.
■ Disconnect the cords on this product before cleaning. Do not use liquid
cleaners or aerosol cleaners. Use a damp cloth for cleaning.
■ Slots and openings in the housing and the back or bottom are provided
for ventilation to protect it from overheating; these openings must not be
blocked or covered. The openings should never be blocked by placing
the product on a rug or other similar surface. This product should never
be placed near or over a radiator or heat register. This product should not
be placed in a built-in installation unless proper ventilation is provided.
■ This product should be operated only from the type of power unit
indicated in this manual. If you are not sure of the type of power supply
being used, contact a qualified service person.
Issue 2 November 1996
xvii

Important Safety Instructions
■ Do not allow anything to rest on the power cord. Do not locate this
product where the cord will be abused by persons walking on it.
■ Do not overload wall outlets and extension cords as this can result in the
risk of fire or electric shock.
■ Disconnect the cords on this product and refer servicing to qualified
service personnel under the following conditions:
a. When the power supply cord or plug is damaged or frayed.
b. If liquid has been spilled into the product.
c. If the product has been exposed to rain or water.
d. If the product does not operate normally by following the operating
instructions.
e. If the product has been dropped or the housing has been
damaged.
f. If the product exhibits a distinct change in performance.
!
SAVE THESE INSTRUCTIONS
When you see this symbol on the product, refer to the instruction booklet
packed with the product for more information before proceeding.
xviii Issue 2 November 1996
Introduction
1
This chapter discusses the basic operating features of the 8400B Plus Data
Module and describes the external indicators and connectors.
The 8400B Plus Data Module is a new version of the 7400B Plus Data Module
and has been designed explicitly to work with two-wire DEFINITY Digital
Communications Protocol circuits. It is fully compatible with the 7400B Plus and
supports all of its functionality and applications.
Overview
Congratulations on the addition of the Lucent Technologies 8400B Plus Data
Module. Following our tradition of excellent quality and high reliability, we have
designed this new 8400B Plus Data Module with the latest advances in
telecommunications technology.
The 8400B Plus Data Module is a full-duplex asynchronous data module. It
provides integrated voice-data communications at the desktop over standard
twisted-pair wiring. At the desk, the 8400B Plus Data Module provides
asynchronous communication speeds ranging from 300 bps to 19.2 Kbps. The
8400B Plus Data Module’s ability to emulate a Hayes® compatible modem
interface makes it compatible with many standard PC communications
packages that use Hayes command sets. In addition, the 8400B Plus Data
Module provides a voice dial capability that allows you to initiate voice calls from
Issue 2 November 1996 1-1
Introduction
a personal computer (PC) using industry-standard ‘‘auto-dialer’’ PC
communications pac k ages .
The 8400B Plus Data Module is a data service link between a Data Terminal
Equipment (DTE) device, a two-wire telephone, and a Lucent Technologies
DEFINITY
®
Communications System G3V2 or later.
NOTE:
Unless a specific DTE device is intended, the words terminal device shall
be used throughout this guide to represent any applicable DTE device,
including a dumb terminal, or a PC with an appropriate communications
package.
Features
A terminal device is connected to the 8400B Plus Data Module using a standard
Electronics Industries Association EIA-232-D Connector cord and, if needed,
the supplied M9/F25 Adapter. The M9/F25 Adapter converts a 25-pin interface
to a 9-pin interface, adhering to the Electronics Industries Association/
Telecommunications Industry Association EIA/TIA-574 standard. A Digital
Communications Protocol (DCP) interface (using a type D8W modular
telephone cord) is used to connect the 8400B Plus Data Module to the digital
PBX.
The 8400B Plus Data Module may be optioned for use either with or without a
telephone. In the stand-alone case, the 8400B Plus Data Module supports data
service only. Otherwise, the 8400B Plus Data Module provides simultaneous
data and voice service. The 8400B Plus Data Module works with all DCP voice
terminals that support two-wire operation (such as the 8400 series voice
terminals) to provide simultaneous data and voice service.
The voice dial feature allows you to dial a voice call without touching the
telephone. Depending on your communications package, you may also store
telephone numbers on a PC and recall them for dialing, log phone calls for easy
billing, and take notes for later reference during a telephone conversation.
1-2 Issue 2 November 1996

Physical Description
In addition, the 8400B Plus Data Module can be used to automatically turn on
the speakerphone of the voice terminal when a voice call is dialed from your
terminal device.
Additional features of the 8400B Plus Data Module include the following:
■ nonvolatile, read-write memory for storing installation options, two data
options profiles, and up to four telephone numbers
■ an AT command interface that emulates a Hayes 2400 Smartmodem™
and supports the following:
— storage of the wait time for carrier detect interval (S-register S7)
— voice call origination using the ATDP command
■ automatic speed and parity adjustment
■ even, odd, mark, space or no parity
■ automatic data throughput adjustment
■ power-up self-test
■ local and remote loopback tests with test duration timers
■ voice terminal powered by the PBX is not affected if AC power is
removed from the 8400B Plus Data Module
Physical Description
The 8400B Plus Data Module is housed in a black casing, approximately
5" x 7.75" x 1.5". Its name appears on the underside of the unit. The external
features of the front and rear panels and the separate power supply units are
described in this section.
Issue 2 November 1996
1-3
Introduction
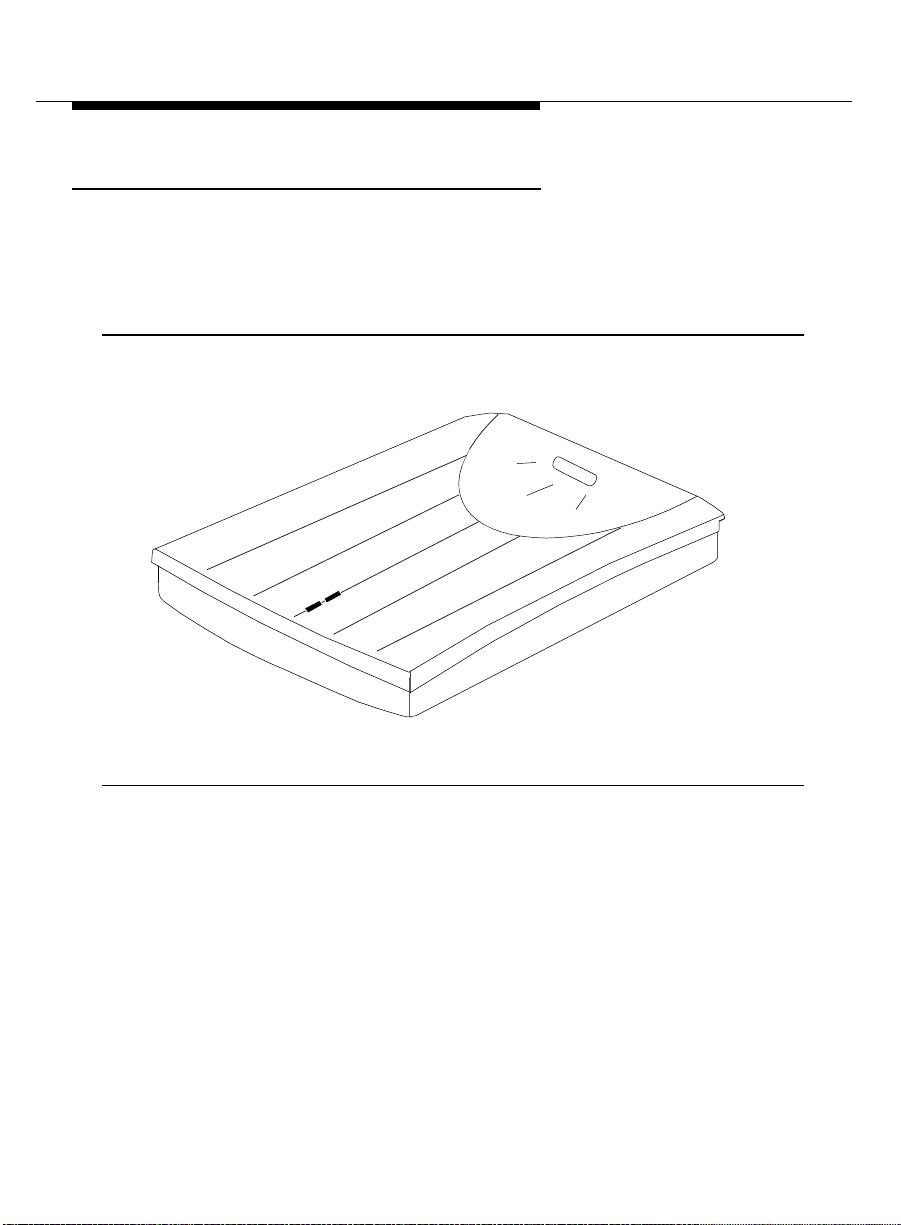
Front Panel
The front panel of the 8400B Plus Data Module is shown in Figure 1-1. One red
light emitting diode (LED) and one green LED on the front panel indicate the
status of the set during normal operation, and the result of self-tests when
initially powered.
Figure 1-1. Front Panel of the 8400B Plus Data Module
1-4 Issue 2 November 1996

Physical Description
Rear Panel
The rear panel of the 8400B Plus Data Module is shown in Figure 1-2, and the
connectors located on the rear panel are described in Table 1-1.
LINE/
PHONE
Figure 1-2. Rear Panel of the 8400B Plus Data Module
USE ONLY WITH COMMUNICATION
!
POWER
CIRCUIT POWER SOURCE
Issue 2 November 1996
1-5

Introduction
_
Table 1-1. Rear Panel Connector Descriptions
Connector Description
PHONE This connector accepts one end of the D8W telephone line
cord used to connect a two-wire voice terminal to the
8400B Plus Data Module.
LINE/
POWER
EIA
CONNECTOR
INTERFACE
This connector accepts one end of the D8W telephone
cord that connects between the 8400B Plus Data Module
and either:
■ a PBX wall jack already powered by a closet
supply, or
■ a power supply, which is connected to the PBX
wall jack.
This unlabeled connector provides an interface between
the 8400B Plus Data Module and the terminal device.
■ If the communications port on the terminal
device is a 9-pin interface, use a cord with DB9
male connectors on each end to connect the
Data Module to the terminal device.
■ If the communications port on the terminal
device is a 25-pin interface, use a 25-pin
EIA-232-D cord, plus the supplied
M9/F25 Adapter to connect the Data Module to
the terminal device.
1-6 Issue 2 November 1996
Physical Description
Power Supply Unit
A Lucent T echnologies power supply unit is shipped with each 8400B Plus Data
Module. This unit connects to a grounded AC outlet, and provides a connection
between the PBX wall jack and the 8400B Plus Data Module. The power supply
unit provides the necessary operating voltages for the 8400B Plus Data Module.
!
CAUTION:
Use the 8400B Plus Data Module only with an approved communication
circuit power source.
!
CAUTION:
Make certain that the AC outlet to which you connect the power supply is
unswitched (for example, not controlled by a wall switch or light dimmer).
Instructions for installing the power supply unit are provided in ‘‘Hardware
Installation’’ on page 2-8.
Issue 2 November 1996
1-7


Installation
2
This chapter describes the equipment required for installing the 8400B Plus
Data Module, and outlines procedures for preparing it for operation. If you are
using the 8400B Plus Data Module with a PC, you will be ready to use a PC
communications package after reading this chapter. If you are using the 8400B
Plus Data Module with a terminal, printer, or host, or you want to learn about the
AT interface and operations, read this chapter, and then continue to Chapter 3.
About the Terminal Device
The 8400B Plus Data Module operates with any asynchronous data terminal
device that has either an EIA-232-D or RS-232-C interface. If you are using a
PC as your terminal, you will need a suitable PC communications package. EIA
Connector cord and PC communications package requirements are described
in this chapter.
Y ou must set the appropriate configuration options before connecting the 8400B
Plus Data Module to a printer or plotter. To do this, connect a data terminal or
PC to the EIA Connector Interface on the 8400B Plus Data Module, change and
store the necessary configuration parameters, remove the data terminal or PC,
and then connect the printer or plotter. The configuration parameters used for
this type of operation are described in ‘‘Remote Site Use’’ on page 3-13.
Issue 2 November 1996 2-1

Installation
Selecting the Correct Installation Procedure
The 8400B Plus Data Module is available in two configurations. Before you can
successfully install the data module, you must ascertain which configuration you
have. Refer to Figure 2-1 (on page 2-3) for an illustration of the components
included with each configuration.
2-2 Issue 2 November 1996
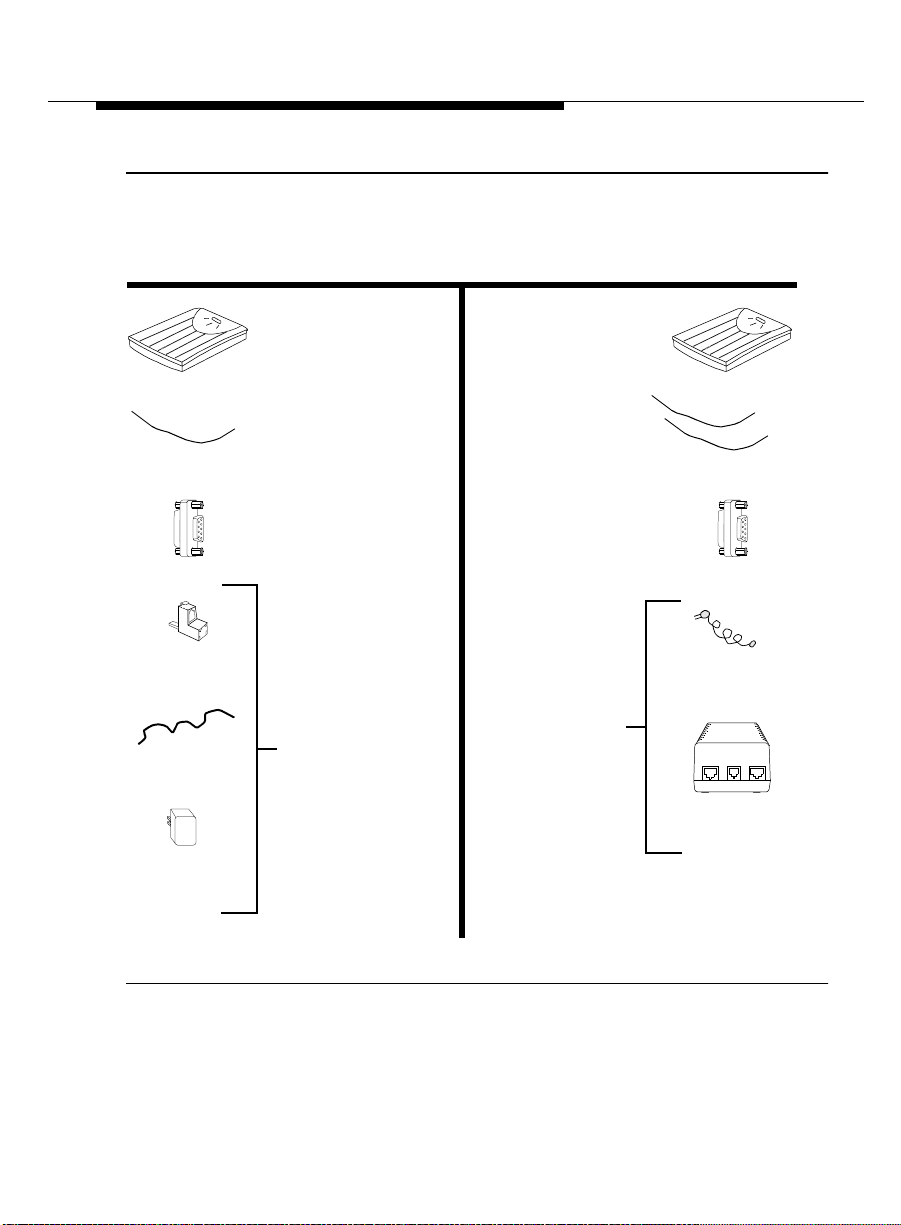
Selecting the Correct Installation Procedure
CONFIGURATIONS
United States International
400B2
Adapter
one 7-foot
D6AP 87 cord
KS-22911,L2
Power Supply
8400B Plus
Data Module
one 7-foot D8W
telephone cord
M9/F25 Adapter
DEFINITY
Adjunct Power Kit,
containing:
8400B Plus
Data Module
two 7-foot D8W
telephone cords
M9/F25 Adapter
MSP-1
Power Supply
Kit, containing:
one power
cord
LINEPHONE
OTHER
-7 +8
-2
+5
MSP-1
Power S upply
Figure 2-1. Components of the US Configuration and the International
Configuration
Issue 2 November 1996
2-3

Installation
What You Need
To install and operate the 8400B Plus Data Module, you will need the following
items:
■ an asynchronous data terminal or PC with a terminal emulation program
and EIA cord
■ (optional) a two-wire DCP voice terminal with D8W cord
Figure 2-2 illustrates a standard US Configuration, using a telephone and
separate power supply.
Figure 2-3 illustrates a standard International Configuration, using a telephone
and separate power supply.
The US Configuration may be installed using the Lucent Technologies 1145A or
Lucent Technologies 1145B1 closet power supply. The International
Configuration may be installed using the Lucent Technologies 1145B1 closet
power supply. Both configurations are shown in Figure 2-4. This type of
installation eliminates the need for the separate power supply.
2-4 Issue 2 November 1996
 Loading...
Loading...