Page 1

TCG
220
-
E
27
USER MANUAL
Page 1 / 59
Page 2

SAFETY INSTRUCTIONS AND REGULATORY NOTICES ........................................................... 4
Chapter 1: Connections and Setup ........................................................................................ 9
Cable Modem Overview ................................................................................................ 9
Front Panel ........................................................................................................... 9
Rear Panel .......................................................................................................... 11
Top Side Panel for WPS ........................................................................................ 12
Relationship among the Devices .................................................................................. 13
What the Modem Does ......................................................................................... 13
What the Modem Needs to Do Its Job ..................................................................... 13
Contact Your Local Cable Company ........................................................................ 14
Connecting the Wireless Voice Gateway to a Single Computer .......................................... 14
Attaching the Cable TV Wire to the Wireless Voice Gateway ....................................... 15
Installation procedure for connecting to the Ethernet interface ................................... 16
Chapter 2: WEB Configuration ............................................................................................ 17
Accessing the Web Configuration ................................................................................. 17
Overview Web Page Group .......................................................................................... 19
Overview ............................................................................................................ 19
Internet Web Page Group ........................................................................................... 20
Advanced ........................................................................................................... 20
Port Mapping ...................................................................................................... 22
Parental Control ................................................................................................... 23
Firewall .............................................................................................................. 24
Firewal event log ................................................................................................. 25
DMZ Host ........................................................................................................... 26
Dynamic DNS ...................................................................................................... 27
UPnP ................................................................................................................. 28
MAC base Passthrough ......................................................................................... 29
Bridge Mode ....................................................................................................... 30
Diagnostic .......................................................................................................... 31
eRouter Reset ..................................................................................................... 32
Page 2 / 59
Page 3

Wi-Fi Web Page Group ............................................................................................... 33
General .............................................................................................................. 33
Schedule ............................................................................................................ 36
WPS .................................................................................................................. 37
MAC Filter ........................................................................................................... 38
Guest Network .................................................................................................... 39
Wi-Fi Clients ........................................................................................................ 42
Reset ................................................................................................................. 43
Wi-Fi insight ........................................................................................................ 44
Settings Web Page Group ........................................................................................... 45
Language ........................................................................................................... 45
Password ............................................................................................................ 46
Initial Scan ......................................................................................................... 47
Configuration ...................................................................................................... 48
LAN ................................................................................................................... 49
Remote Access .................................................................................................... 50
Status Web Page Group .............................................................................................. 51
Status ................................................................................................................ 51
Voice Status ........................................................................................................ 52
Upstream ........................................................................................................... 53
Downstream ....................................................................................................... 54
Event log ............................................................................................................ 55
Chapter 3: Additional Information ....................................................................................... 56
Frequently Asked Questions ........................................................................................ 56
General Troubleshooting ............................................................................................. 57
Service Information ................................................................................................... 58
Federal Communication Commission Interference Statement ............................................ 59
Page 3 / 59
Page 4
SAFETY INSTRUCTIONS AND REGULATORY NOTICES
Explanation of risk levels
Explanation of pictorial warning ind
ications and warning labels
Product Safety Notice
Before installing or using the product, read these instructions carefully. Be sure to comply
strictly precautions.
This indication is given where there is an immediate danger of death
or serious injury if the person in charge or any third party mishandles
DANGER
WARNING
the machine or does not avoid the dangerous situation when
operating or maintaining the machine.
This indication is given where there is a potentiality for death or
serious injury if the person in charge or any third party mishandles
the machine or does not avoid the dangerous situation when
operating or maintaining the machine.
CAUTION
Prohibited
Caution
This indication is given where there is a danger of medium to minor
injury if the person in charge or any third party mishandles the
machine or does not avoid the dangerous situation when operating
or maintaining the machine.
It is used to prohibit its conduct in handling products.
Specific prohibited contents are indicated by pictures and sentences in or
near the figure symbol.
It is used to call attention to ignition, electric shock, high temperature,
etc. in the handling of products.
Specific notes content is indicated by a picture or sentence in or near the
figure symbol.
Used to force actions based on instructions in the handling of products.
Specific instruction content is indicated by a picture or sentence in or near
the figure symbol.
Instruction
Page 4 / 59
Page 5
LIMITATIONS OF LIABILITY
Instruction
This equipment has been designed for domestic use inside a building. In some
environments or circumstances, the use of wireless devices may be prohibited by
the owner of the building or responsible representatives of the organization. If in
doubt about the policy applying to the use of wireless devices in an organization
where a specific environment (e.g. airports), you should ask for permission to use
the device before turn it on. ASKEY assumes no liability for non-compliance with
regulations on the installation site, and radio interference created vis-à-vis third
parties and due to non-compliance with national regulations for this application.
DANGER
Do not overload wall outlet or extension cords as this may increase the
risk of electric shock or fire. If the power cord is frayed, replace it with a
new one.
Instruction
Instruction
Unplug the
power plug
Do not attempt to connect with any computer accessory or electronic
product without instructions from qualified service personnel. This may
result in risk of electronic shock or fire.
WARNING
Proper ventilation is necessary to prevent the product overheating. Do not
block or cover the slots and openings on the product, which are intended
for ventilation and proper operation.
When the product is expected to be not in use for a period of time,
unplug the power cord of the product to prevent it from the damage of
storm or sudden increases in rating.
Accidental penetrations of small metal objects (such as pins, paper clips,
etc.) disconnect the equipment from the mains as soon as possible (risk
of electric shock) and contact your Customer Service to find out how to
proceed. Do not reconnect the product as a foreign object has not been
Unplug the
eliminated. Unplug the product immediately if you notice it exudes a smell
Page 5 / 59
Page 6
power plug
of burning or smoke. You should
never open the unit yourself because
Prohibited
Water wet
prohibition
Instruction
you could be electrocuted.
Do not place the product near any source of heat or expose it to direct
sunlight.
Do not expose the product to moisture. Never spill any liquid on the
product.
Avoid connecting or using this product during a lightning storm.
Disturbances transmitted through the grid and / or telephone can cause
electric shock in the product and people.
Instruction
Instruction
CAUTION
Use only power adapter supplied with the product. This appliance is
designed to operate in the rated voltage 100~240 VAC.
Do not place this product on unstable stand or table.
This product is designed for stationary use in an office or a room in the
home for a maximum ambient temperature of 45 ° C (113 ° F).
Instruction
To allow the disconnection of the device in case of problems, make sure
the base of the outlet you plug the power cord is easily accessible and is
located as close as possible to the equipment.
Instruction
Page 6 / 59
Page 7

Instruction
Be sure to
connect the
ground wire
Leave 7cm to 10cm around the appliance to ensure that proper
ventilation gets to it.
The screen of the coaxial cable is intended to be connected to earth in
the building installation.
Do not attempt to disassemble or open covers of this unit by yourself. Nor
should you attempt to service the product by yourself, which may void
the user’s authority to operate it. Contact qualified service personnel
under the following conditions:
1. If the power cord or plug is damaged or frayed.
2. If liquid has been spilled into the product.
3. If the product has been exposed to rain or water.
Disassembly
prohibited
Unplug the
power plug
4. If the product does not operate normally when the operating
instructions are followed.
5. If the product has been dropped or the cabinet has been
damaged.
6. If the product exhibits a distinct change in perform
ance.
7. If a cable is damaged or frayed provided.
8. If the unit is dropped or damaged in any way.
9. If there is a noticeable signs of overheating
Power off and unplug this product from the wall outlet when it is not in
use or before cleaning. Pay attention to the temperature of the power
adapter. The temperature might be high.
Do not store the Cable Modem product in excessively hot, cold or damp
conditions. Operation Environmental:
Instruction
‧ Operation Temperature: 0°C ~ 45°C
‧ Storage Temperature: -20°C ~ +70°C
To clean the appliance, use a dry, clean soft cloth with no cleaning
solvent or abrasive products. Clean the ventilation openings regularly.
Page 7 / 59
Page 8

Instruction
Under normal use condition the user shall keep at least 20cm from the
Cable Modem product.
Instruction
Page 8 / 59
Page 9
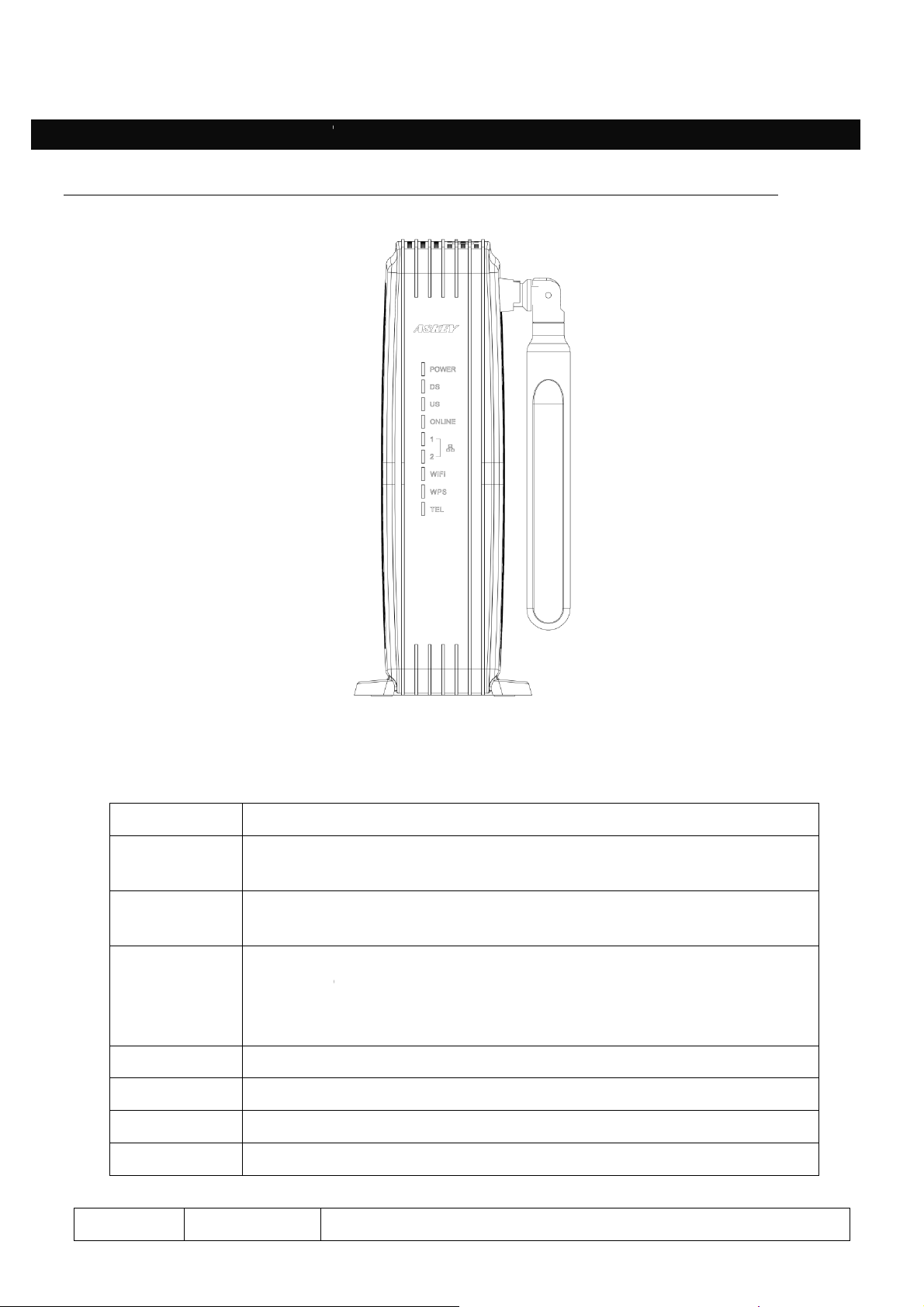
CHAPTER 1: CONNECTIO
Cable Modem Overview
The following illustration shows the front panel of the
POWER
Indicates the
Indicates the status of
d
Indicates the status of
etwork (
Displays the status of your cable connection.
connection is detectedand fully lit when the modem has
established a connection with the network and data can be
transferred
LAN1 / 2
In
dicates the state of Ethernet ports
WI-FI Indicates the traffic on the wireless network
WPS
Indicates the status of
TEL
Indicates the status of the telephon
LED
Status
power
status.
d
ata reception by the cable modem from the
d
ata transmission by the cable modem to
The light is off when
the WPS.
e.
Description
Front Panel
NS AND SETUP
Fig.1-1 Front Panel
TCG220-E27:
DS
US
ONLINE
network (
the n
no cable
ownstream traffic)
upstream traffic)
LED from top to bottom.
Page 9 / 59
Page 10
POWER
ON
The device is on.
Flash
Scanning Downstream and trying to link.
Flash
Scanning Upstream and trying to link.
ON
The device is ready for use. Now you can link to the internet.
ON
LAN port is connected to the PC.
ON
Wi-Fi is enabled.
Flash
WPS process is running or connects fail.
ON
Phone is ready registration for use.
OFF
The device boot fail or no power.
DS
US
ONLINE
LAN
WI-FI
ON
OFF
ON
OFF
OFF
FLASH
OFF
FLASH
OFF
FLASH
Downstream link OK.
Downstream is not linked.
Upstream link OK.
Upstream is not linked.
The device is not link to the internet yet or not registration.
The device is in registration process.
LAN port is not connected to the PC.
Traffic on the LAN is working.
Wi-Fi is disabled.
Wi-Fi traffic is working.
WPS
ON
OFF
TEL
OFF
FLASH
WPS connect success.
WPS is not running.
Phone is not able to use.
Phone interface is in registration process.
Table1-1 LED behavior
Page 10 / 59
Page 11
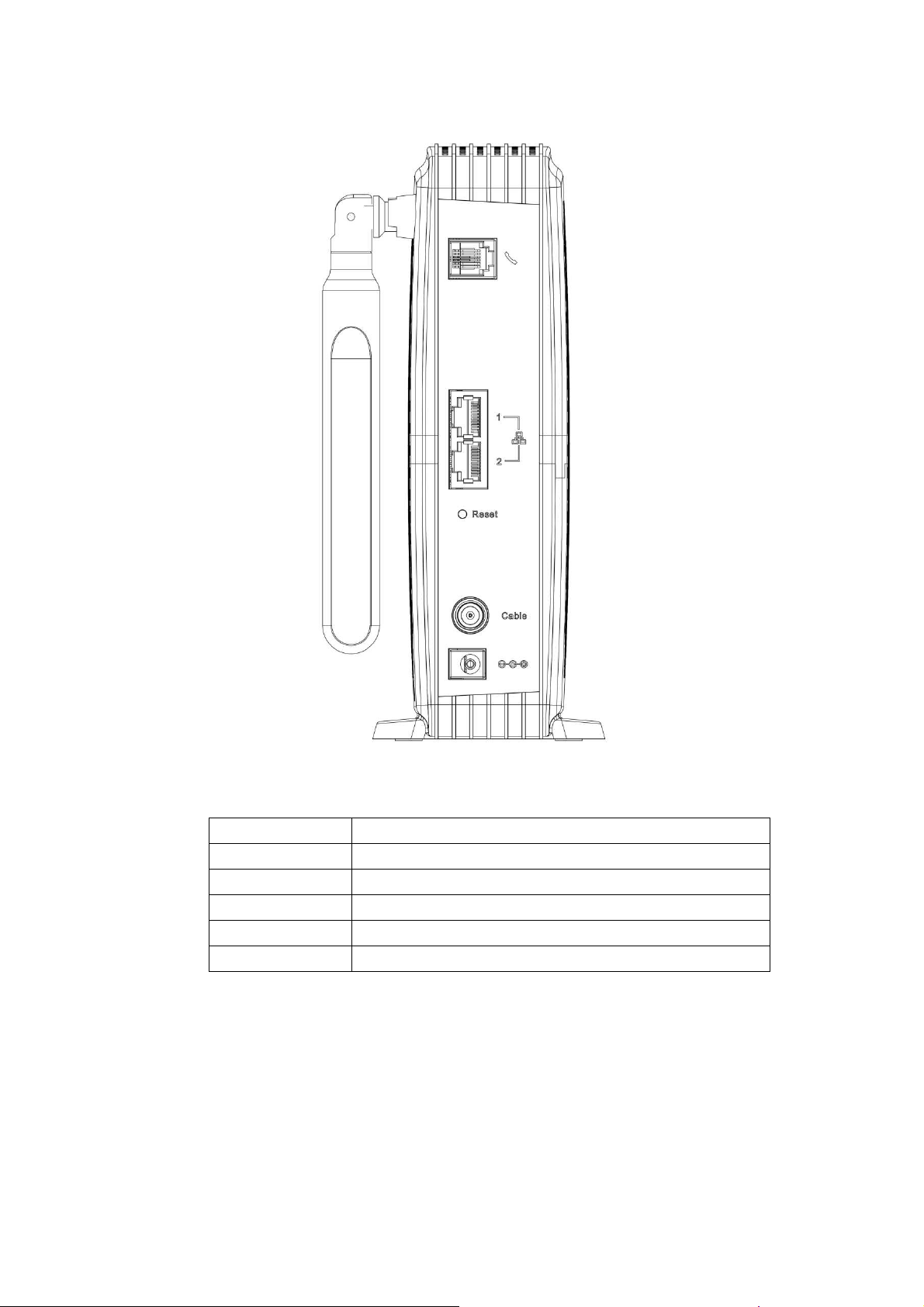
Rear Panel
Slot
Description
TEL Telephony RJ
-
11 connector
LAN1 / 2
Ethernet 10/100/1000 Base
-
T RJ
-
45 connector
R
eset
Reset/Reboot this
Cable modem
C
able
F-
Connector
12VDC
12V
DC-IN Power connector.
Fig.1-2 Rear Panel
Table1-2 Rear Panel description
Page 11 / 59
Page 12

Top Side Panel for WPS
Fig.1-3 Top Side Panel
The button is on the Top Side panel of TCG220-E27, you can long press button
(more than 5 sec) enables scanning for available WPS client device.
Page 12 / 59
Page 13

Relationship among the Devices
This illustration shows a cable company that offers
PacketCable
The Wireless Voice Gateway provides high
quality telephone voice and fax/modem services over residential, commercial, and
education subscribers on public and private networks via an existing CATV infrastructure. It
PacketCable
based voice communications. The IP traffic can transfer between the Wireless Voice Gateway
compliant head
upstream and downstream communications.
Needs to Do Its Job
The Right Cable Company:
TV industry
The Internet/Telephony Service Provider (ISP/TSP):
you access to an Internet Service Provider (ISP) and Telephony Service Provider (TSP).
The ISP is your gateway to the Internet and provides you with a pipeline to access
Internet content on the World Wide Web (WWW). The TSP provides you with telephony
ess to other modems or other telephony services over the Public Switched Telephone
Check with your cable company to make sure you have everything you need to begin; they’ll
know if you need to install special software or re
DOCSIS
speed Internet access as well
equipment and provide the IP
end equipment. The data security secures
Make sure your local cable company provides data services
compliant technology.
Your cable company provides
omputer to make your cable
PacketCable/Euro-
What the Modem Does
toll-
DOCSIS/Euro-
compliant voice/data services.
Fig.1-4 Connection overview
-
and
as cost-effective,
can inter-operate with the
and DOCSIS/Euro-DOCSIS
What the Modem
that use cable
acc
Network (PSTN).
internet service work for you.
compliant head-end
-
-standard DOCSIS/Euro-DOCSIS
-configure your c
-
Page 13 / 59
Page 14
Contact Your Local Cable Company
You will need to contact your cable company to establish an Internet account before you can
use your gateway. You should have the following information ready (which you will find on the
sticker on the gateway):
• The serial number
• The model number
• The Cable Modem (CM) Media Access Control (MAC) address
• The Terminal Adapter (EMTA) MAC address
• Security information: Service Set Identifier (SSID),
Encryption key / passphrase
(WPA2/PSK by default), channel number. Default values are indicated underneath the
modem on the sticker.
Please check the following with the cable company
The cable service to your home supports DOCSIS/Euro-DOCSIS compliant two-way
modem access.
Your internet account has been set up. (The Media Terminal Adapter will provide data
service if the cable account is set up but no telephony service is available.)
You have a cable outlet near your PC and it is ready for Cable Modem service.
Note: It is important to supply power to the modem at all times. Keeping your modem
plugged in will keep it connected to the Internet. This means that it will always be ready
whenever you need.
Important Information
Your cable company should always be consulted before installing a new cable outlet. Do not
attempt any rewiring without contacting your cable company first.
Please verify the following on the Wireless Voice Gateway
The Power LED should be lighted when plug-in the power supply.
Connecting the Wireless Voice Gateway to a Single Computer
This section of the manual explains how to connect your Wireless Voice Gateway to the
Ethernet port on your computer and install the necessary software. Please refer to Figure 1-6
to help you connect your Digital Cable Modem for the best possible connection.
Page 14 / 59
Page 15
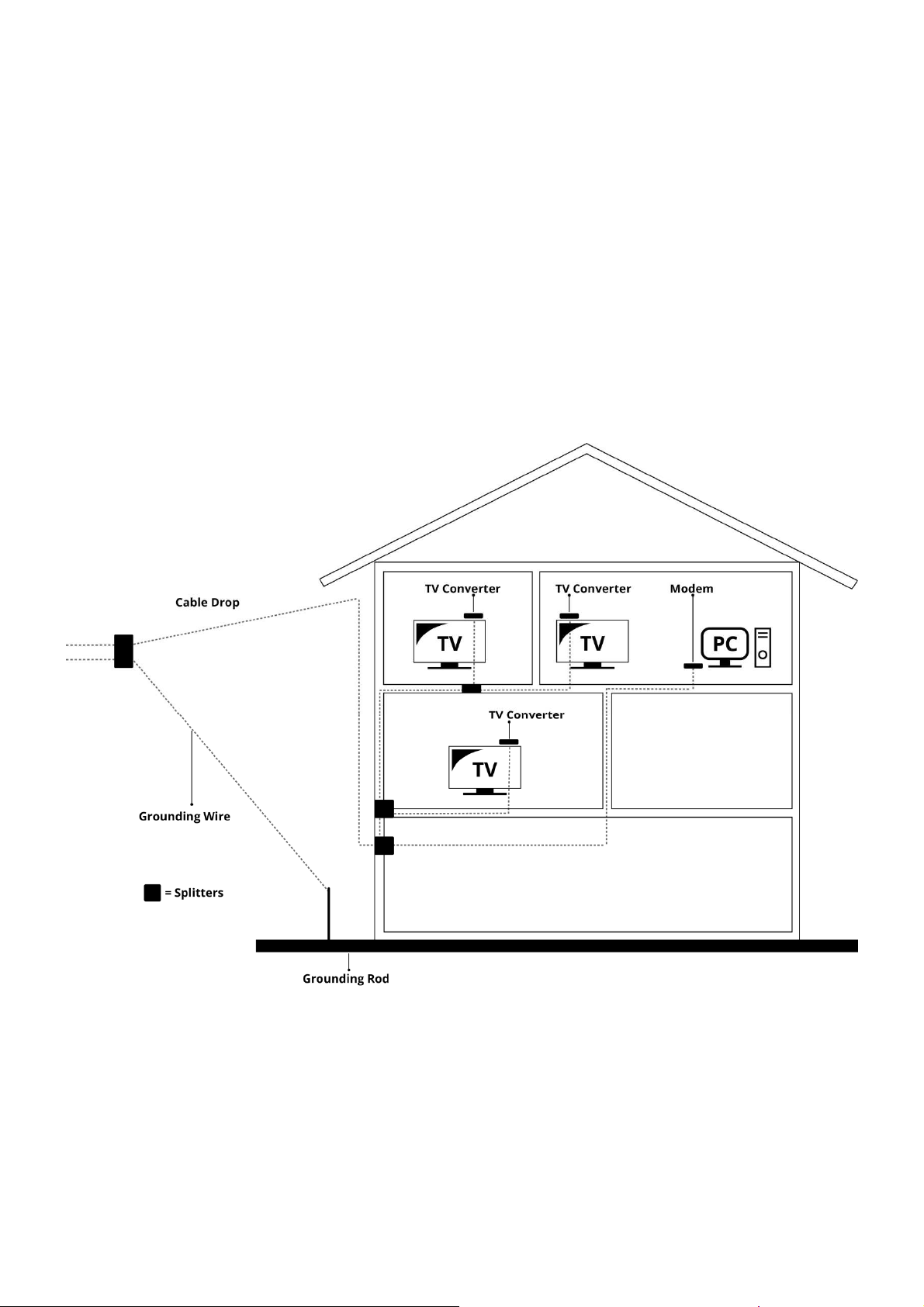
Attaching the Cable TV Wire to the Wireless Voice Gateway
1. Locate the Cable TV wire. You may find it one of three ways:
a. Connected directly to a TV, a Cable TV converter box, or VCR. The line will be
connected to the jack, which should be labeled either IN, CABLE IN, CATV, CATV IN,
etc.
b. Connected to a wall-mounted cable outlet.
c. Coming out from under a baseboard heater or other location. See Figure 1-5 for the
wiring example.
Notes:For optimum performance, be sure to connect your Wireless Voice Gateway to the first
point the cable enters your home. The splitter must be rated for at least 1GHz.
Fig.1-5Basic Home Wiring
Page 15 / 59
Page 16
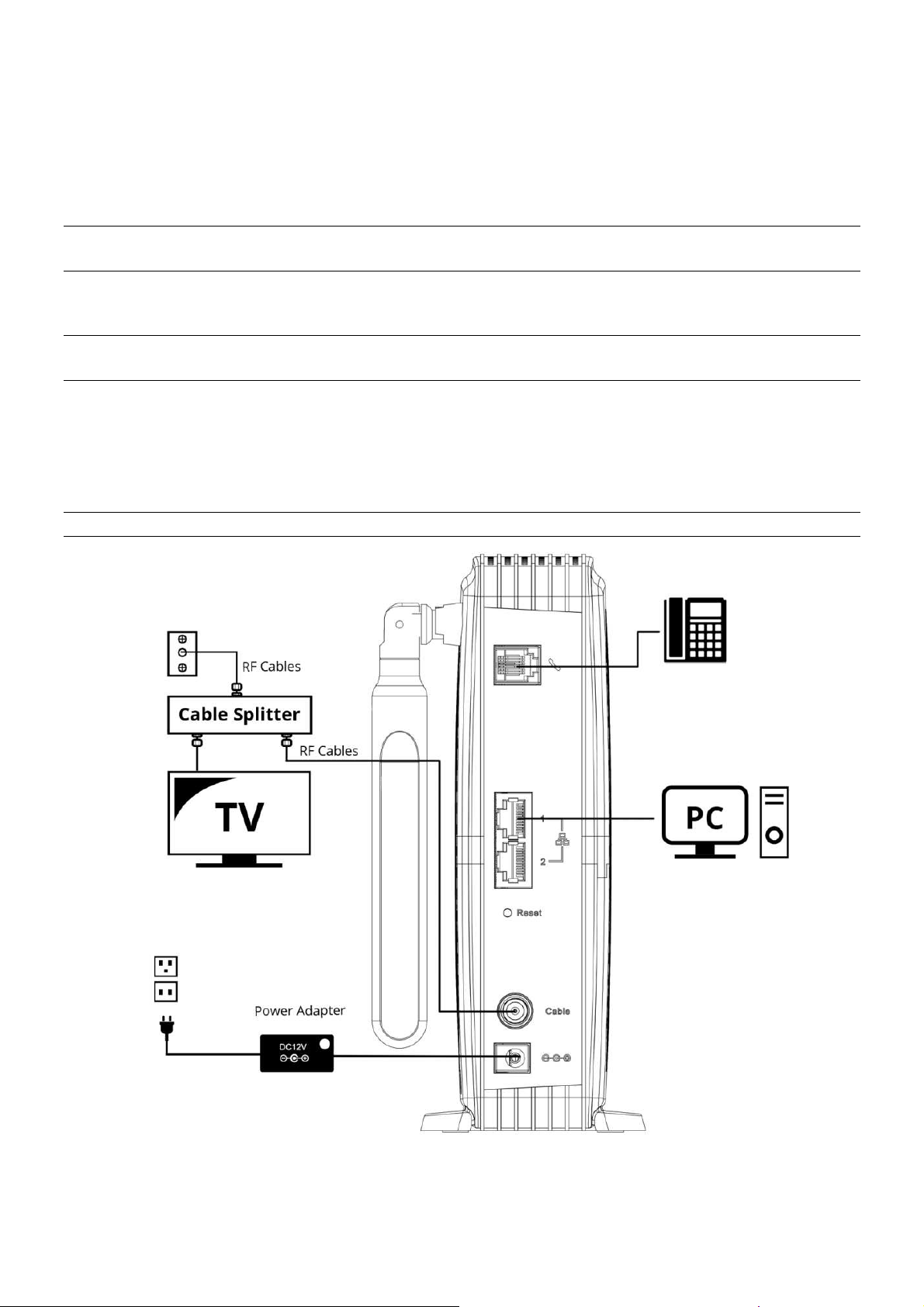
Installation procedure for connecting to the Ethernet interface
Follow these steps for proper installation.(Please refer to Fig. 1-6)
Plug the coaxial cable to the cable wall outlet and the other end to the modem’scable
connector.
Note: To ensure a fast registration of the modem, the coaxial cable must be connected to
the modem before it is powered on.
Plug the power adapter into the socket of the cable modem and two-pin plug in the AC
outletto power on the modem.
Note: Only use the poweradapter that comes with the modem. Using another power adapter
can cause damage to the product, and will void the warranty.
Connect an Ethernet cable (direct connection, see below) to the Ethernet port at the back of
the computer, and the other end to the ETHERNET port on the rear panel of the cable
modem. The modem will seek the appropriate cable signal on the cable television network
and go through the initial registration process on its own. The modem is ready for data
transfer after the green LED "Online" is lit continuously.
Note: the button "Reset" at the back of the modem is used primarily for maintenance.
Fig.1-6 Connect to the Modem
Page 16 / 59
Page 17

CHAPTER 2: WEB CONFIGURATION
To make sure that you can access the Internet successfully, please check the following first.
1. Make sure the connection (through Ethernet) between the Wireless Voice Gateway and
your computer is OK.
2. Make sure the TCP/IP protocol is set properly.
3. Subscribe to a Cable Company.
Accessing the Web Configuration
The Wireless Voice Gateway offers local management capability through a built-in HTTP
server and a number of diagnostic and configuration web pages. You can configure the
settings on the web page and apply them to the device.
Once your host PC is properly configured; please proceed as follows:
1. Start your web browser and type the private IP address of the Wireless Voice Gateway
on the URL field: 192.168.100.1 or 192.168.1.1
2. After connecting to the device, you will be prompted to enter username and password.
By default, the username is "admin" and password is "Cl@r0".
Fig.2-1 Login dialogue
Note: If forget your username and password, you may Press "Reset" button on the rear
panel more than 5seconds to restore the username and password to default.
Page 17 / 59
Page 18

If you login successfully, the main page will appear. “
You can change the display language to “English” or “Español” on the top of the page.
Fig. 2-2 Switch Language
Page 18 / 59
Page 19

Overview Web Page Group
The Overview page is the start page. You could
, ETHERNET and VoIP connection status. You could click the icons
s.
Overview
Setting, Status)
This page display Wi-Fi
, and will lead
switch to other page
to Wi-Fi, LAN and VoIP status pages.
(e.g., Internet, Wi-Fi,
Fig.2-3 Overview
Page 19 / 59
Page 20

Internet Web Page Group
Advanced
This page allows you to configuration of advanced features of the Wireless Voice Gateway.
Fig.2-4 Internet\Advanced
WAN Blocking
prevents others on the WAN side from being able to ping your gateway.
With WAN Blocking enabled, your gateway will not respond to pings it receives,
effectively “hiding” your gateway.
Ipsec PassThrough enables IpSec type packets to pass WAN LAN. IpSec (IP
Security) is a security mechanism used in Virtual Private Networks (VPNs).
PPTP PassThrough enables PPTP type packets to pass WAN LAN. PPTP (Point to
Point Tunneling Protocol) is another mechanism sometimes used in VPNs.
Page 20 / 59
Page 21

NAT ALGenable NAT ALG (application layer gateways) allows customized NAT traversal
filters to be plugged into the gateway to support address and port translation for certain
application layer "control/data" protocols such as SIP , Wake on LAN file transfer in IM
applications etc. In order for these protocols to work through NAT or a firewall, either
the application has to know about an address/port number combination that allows
incoming packets, or the NAT has to monitor the control traffic and open up port
mappings (firewall pinhole) dynamically as required. Legitimate application data can thus
be passed through the security checks of the firewall or NAT that would have otherwise
restricted the traffic for not meeting its limited filter criteria.
Page 21 / 59
Page 22

Port Mapping
This page allows configuration of Port Forwarding and Port Triggering.
Fig.2-5 Internet\Port Mapping
Port ForwardingF
or LAN WAN communications, the gateway normally only allows you
to originate an IP connection with a PC on the WAN; it will ignore attempts of the WAN PC
to originate a connection onto your PC. This protects you from malicious attacks from
outsiders. However, sometimes you may wish for anyone outside to be able to originate a
connection to a particular PC on your LAN if the destination port (application) matches one
you specify.
Port TriggeringSome Internet activities, such as interactive gaming, require that a PC on
the WAN side of your gateway be able to originate connections during the game with your
game playing PC on the LAN side. Port triggering is an elegant mechanism that does this
work for you, each time you play the game.
Page 22 / 59
Page 23

Parental Control
This page allows you to set the time limit for a client’s network usage.
Fig.2-6 Internet\Parental Control
Page 23 / 59
Page 24

Firewall
This page allows you to enable/disable, and you can choose “Off”, “Low”, “Medium”,
“High” firewall protection.
The Low setting does not block any services/ports, however it does protect against invalid
packets and well known attacks. The Medium setting will cause the firewall to drop a packet
unless it is on a specific port of allowed services. The High setting is similar to medium, but
allows access to even fewer services. The Off setting allows all traffic to pass.
IP Flood Detection if you switch this button to ON, cm will show the attack of IP flood on
the “firewall event log” page.
Fig.2-7 Internet\Firewall
Page 24 / 59
Page 25

Firewal event log
This page displays all Firewall event logs.
Fig.2-8 Internet\Firewall event log
Page 25 / 59
Page 26

DMZ Host
Use this page to designate one PC on your LAN that should be left accessible to all PCs from
the WAN side, for all ports. e.g., if you put an HTTP server on this machine, anyone will be
able to access that HTTP server by using your gateway IP address as the destination.
Fig.2-9 Internet\DMZ Host
Page 26 / 59
Page 27

Dynamic DNS
This page allows to setup for Dynamic DNS server.
Fig.2-10 Internet\Dynamic DNS
Dynamic DNS-
Turn “ON” to enable the dynamic DNS function.
Provider- Choose Provider to enable the basic setting.
Domain Name- The domain name that you registered with your DDNS provider.
Account / Email- The account that is registered with your DDNS provider.
Password- The password that you registered with your DDNS provider
DDNS Status- It shows the DDNS service status whether it is enabled or disabled.
Click Apply to save the changes.
Page 27 / 59
Page 28

UPnP
Enable IGD UPnP to allow any local UPnP control point to perform a variety of actions,
include retrieving the external IP address of the device, enumerate existing port mappings,
and add or remove port mappings.
Fig.2-11 Internet\UPnP
Page 28 / 59
Page 29

MAC base Passthrough
This page allows you configure passthrough CPEs via MAC address. (bypass NAT)
Fig.2-12 Internet\MAC base Passthrough
Page 29 / 59
Page 30

Bridge Mode
Switch this to ON, DHCP is disabled and all ip addresses are given out by Headend server.
Fig.2-13 Internet\Bridge Mode
Page 30 / 59
Page 31

Diagnostic
This page offers basic diagnostic tools for you to use when connectivity problems occur.
When youping an Internet device, you send a packet to its TCP/IP stack, and it sends one
back to yours. To usethe ping Test, enter the information needed and press Start Test; the
Result will be displayed in thelower part of the window. Press Abort Test to stop, and Clear
Results to clear the result contents.
Note: Firewalls may cause pings to fail but still provide you TCP/IP access to selected devices
behindthem. Keep this in mind when ping a device that may be behind a firewall. Ping is
most useful toverify connectivity with PCs which do not have firewalls, such as the PCs on
your LAN side.
Fig.2-14 Internet\Diagnostic
Page 31 / 59
Page 32

eRouter Reset
This page allows resetting eRouter.
Fig.2-15 Internet\eRouter Reset
Page 32 / 59
Page 33

Wi-Fi Web Page Group
General
This page allows configuration of the 2.4GHz and 5GHz wireless features.These must match
the settings you make on your wireless-equipped PC on the LAN side.
Fig. 2-16 Wi-Fi\General
Page 33 / 59
Page 34

2.4GWi-Fi Network / 5GWi-Fi Network:It may help you to Enable or Disable the
2.4GHz / 5GHz wireless function.
Current Channel: The channel that you choose will be displayed in this field.
Current Bandwidth:The bandwidth that you choose will be displayed in this field.
Wi-Fi Name (SSID):The SSID for 2.4GHz / 5GHz wireless function.
Interface Type: There are three different modes can be selected. 2.4GHz can be
selected 802.11b/g, 802.11b/g/n and 802.11n only; 5GHz can be selected 802.11a,
802.11a/n/ac and 802.11n/ac only.
Sideband (40MHz only):
There is“Lower” and “Upper” can be selected if Bandwidth 40
MHz was enabled.
Channel: In 802.11 Band 2.4GHz, there are 1 to 11 channels. In 802.11 Band 5GHz,
there are 36, 44, 52, 60, 64, 100, 104, 108, 116, 124, 128, 132, 149, 157channels for all
country. Choose the one that is suitable for this device.
Bandwidth: Select wireless channel width 20/40 MHz is for 2.4GHz Wi-Fi default value,
and 20/40/80 MHz is for 5GHz Wi-Fi default value. (Bandwidth taken by wireless
signals of this access point.)
OBSS Coexistence:Overlapping BBS coexistence, here to control this function Enable or
Disable, default is enabled.
Output Power: This setting decides the output power of this device. You may use it to
economize on electricity by selecting lower percentage of power output. Control the
range of the AP by adjusting the radio output power.
Broadcast SSID:
Broadcasting the SSID causes the name of your network to appear in
the list of available networks.
Wi-Fi Protection: ThemethodofWi-Fi protectioncanbeOFF, WEP-64, WEP-128,WPA/TKIP,
WPA/TKIP+AES, WPA2/AES, WPA2/TKIP+AESorWPA+WPA2/TKIP+AES.
Network key: The network key is the password that you use to authenticate with your
router.
Page 34 / 59
Page 35

802.11x Authentication introduction
If you enable the 802.11x authentication function, you will have to offer the following
information-
WEP-64 / WEP-128(Wired Equivalent Privacy):
WEP-64/ WEP-128 is a simple security protocol for wireless networks that encrypts
transmitted data. The WEP key can be entered as a string of
10 hexadecimal characters (0–9 and A–F).
WPA (Wi-Fi Protected Access)/WPA2:
It must be used in conjunction with an authentication server such as RADIUS to
provide centralized access control and management. It can provide stronger
encryption and authentication solution than none WPA modes. WPA2 is the second
generation of WPA security.
WPA/WPA2 Encryption:
here are two types that you can choose,AES, TKIP+AES.
T
TKIP takes the original master key only as a starting point and derives its
encryption keys mathematically from this mater key. Then it regularly changes
and rotates the encryption keys so that the same encryption key will never be
used twice
AES provides security between client workstations operating in ad hoc mode. It
uses a mathematical ciphering algorithm that employs variable key sizes of 128,
192 or 256 bits.
Page 35 / 59
Page 36

Schedule
Schedule the times when you want the Wi-Fi of your router to be turned on or off. When it is
turned back on, you return to your chosen Wi-Fi settings.
Fig.2-17 Wi-Fi\Schedule
Page 36 / 59
Page 37

WPS
Thispageallows youtoconfigureWPSsetting.WiFiProtectedSetupTM(WPS)isaneasyandsecurewayofconfiguringandconnectingyourWirelessaccesspoint.I
nthiscase,theWireless Voice
GatewayistheAccessPoint(AP),andYourPC(orWirelessDevice)iscalledtheSTA.WhenconfiguringyourWirele
ssNetworkviaWPS,MessagesareexchangedbetweentheSTAandAPinordertoconfiguretheSecuritySettings
onbothdevices.
Fig.2-18 Wi-Fi\WPS
Page 37 / 59
Page 38

MAC Filter
By entering MAC Address, you can configure which local PCs are allowed access to the WAN.
Besides the list of MAC filter, any local PCs else would be blocked to the WAN.
Fig.2-19 Wi-Fi\MAC Filter
Page 38 / 59
Page 39

Guest Network
This page allows configuration of the 2.4GHz and 5GHz guest network.
Fig.2-20Wi-Fi\Guest Network
Page 39 / 59
Page 40

Select Wi-Fi Guest Interface Index:Select wireless guest interface index
CLARO_GUS_1 is for Wi-Fi guest interface default value.
2.4G Guest Network / 5G Guest Network:It may help you to Enable or Disable
the 2.4GHz / 5GHz wireless function.
Wi-Fi Name (SSID):The SSID for 2.4GHz / 5GHz Guest wireless function.
Broadcast SSID:Broadcasting the SSID causes the name of your network to appear in
the list of available networks.
Wi-Fi Protection:
ThemethodofWi-Fi protectioncanbeOFF, WEP-64, WEP-128, WPA/TKIP,
WPA/TKIP+AES, WPA2/AES, WPA2/TKIP+AESorWPA+WPA2/TKIP+AES.
Network key: The network key is the password that you use to authenticate with your
router.
Guest LAN Settings
A private IP address and Subnet Mask for LAN sub netting.
For example 192.168.2.1./ 255.255.255.0.
Configure the IP address numbers for the DHCP server with “Lease pool start” and
“Lease pool end”.
Configure the IP address lease time with “Lease time” for DHCP server.
Page 40 / 59
Page 41

802.11x Authentication introduction
If you enable the 802.11x authentication function, you will have to offer the following
information-
WEP-64 / WEP-128(Wired Equivalent Privacy):
WEP-64/ WEP-128 is a simple security protocol for wireless networks that encrypts
transmitted data. The WEP key can be entered as a string of
10 hexadecimal characters (0–9 and A–F).
WPA (Wi-Fi Protected Access)/WPA2:
It must be used in conjunction with an authentication server such as RADIUS to
provide centralized access control and management. It can provide stronger
encryption and authentication solution than none WPA modes. WPA2 is the second
generation of WPA security.
WPA/WPA2 Encryption:
here are two types that you can choose,AES, TKIP+AES.
T
TKIP takes the original master key only as a starting point and derives its
encryption keys mathematically from this mater key. Then it regularly changes
and rotates the encryption keys so that the same encryption key will never be
used twice
AES provides security between client workstations operating in ad hoc mode. It
uses a mathematical ciphering algorithm that employs variable key sizes of 128,
192 or 256 bits.
Page 41 / 59
Page 42

Wi-Fi Clients
This page shows all Wi-Fi clients.
Fig.2-21 Wi-Fi\Wi-Fi Clients
Page 42 / 59
Page 43

Reset
This page allows you to restore the Wi-Fi settings to factory default values.
Fig.2-22 Wi-Fi\Reset
Page 43 / 59
Page 44

Wi-Fi insight
On this page, Users can view real
information about them, including: Network Name (SSID),
time wireless networks in your area and extensive
Strength, and
mode).
Status (Security
Fig.2-23Wi-Fi\Wi-Fi insight
Page 44 / 59
Page 45

Settings Web Page Group
Language
This page allows configuration of language.Or you can choose specific language via dropdown menu in the top of the page.
You can change the display language to “English” or “Español” on the top of the page.
Fig.2-24Setting\Language
Page 45 / 59
Page 46

Password
By default, the username is "admin" and password is "Cl@r0".
When the current password is the default one, the user is strongly encouraged to change the
default web password.
The password can be a minimum of 8 characters, maximum of 20 characters and is case
sensitive. If forget your username and password, you may Press "Reset" button on the rear
panel more than 5seconds to restore the username and password to default.
Note: We are always suggesting you to modify the password. This is a basic protection
against wrongful access to the Gateway Web pages.
Fig.2-25Setting\Password
Page 46 / 59
Page 47

Initial Scan
To speed up the modem’s first time connection, enter known downstream frequency and/or
upstream channel ID information here. Then click “Apply” button to start scanning the cable
network beginning with the values supplied here.
The value is provided in Hertz. So, for 603 MHz, you must type: 603000000
Fig.2-26Setting\Initial Scan
Page 47 / 59
Page 48

Configuration
This page allows you to save your current settings locally on your PC, or restore settings
previously saved.
Fig.2-27 Setting\Configuration
Save & Restore User Configuration:
To back up the current configuration, click Save
to Computer and follow the prompts.
To restore a previous configuration, click Upload and use the navigation window to locate
the file (usually GatewaySettings.bin.) Once the file has been located, click From to
Computer to restore the settings. Once the settings are restored, the device will reboot.
Restart Router: C
Reset to Factory Settings: C
licking Restart will reboot your router.
lick Reset allows you to restore your router to factory
default settings and will also force it to restart.
Page 48 / 59
Page 49

LAN
This page allows configuration of IP addressing for all the equipment connected to your
modem.
Fig.2-28Setting\LAN
Page 49 / 59
Page 50

Remote Access
This page allows configuration of the Remote Access.
Fig.2-29Setting\Remote Access
Allow Remote Management:
It may help you to Enable or Disable the remote
access function.
Remote User Name: The user name that when you remote access able to login.
Port Number: Configure specific port number when you remote access to GUI.
Remote Password: The remote passwordthat when you remote access able to login.
IP Address: The IP address that you can use to remote access.
Page 50 / 59
Page 51

Status Web Page Group
Status
This page can find an overview of all your router parameters. This may help you in
optimizing or trouble shooting your router.
Fig.2-30Status\Status
Page 51 / 59
Page 52

Voice Status
This page displays the initialization status of the MTA containing Telephony DHCP,
Security, TFTP and Provisioning Status. The information can be useful to your cable
company’s support technician if you’re having problems.
Fig.2-31Status\Voice Status
Page 52 / 59
Page 53

Upstream
This page reports current CM’s upstream information containing Transmitter #, Channel ID,
Lock Status, Frequency, Modulation, Symbol Rate, Channel Type and Power. The information
can be useful to your cable company’s support technician if you’re having problems.
Fig.2-32 Status\Upstream
Page 53 / 59
Page 54

Downstream
This page reports current CM’s downstream information containing Receiver #, Channel ID,
Lock Status, Frequency, Modulation, SNR, and Power. The information can be useful to your
cable company’s support technician if you’re having problems.
Fig.2-33 Status\Downstream
Page 54 / 59
Page 55

Event log
This page displays the contents of the modem's event log.
Fig.2-34 Status\Event log
Page 55 / 59
Page 56

CHAPTER 3: ADDITIONAL INFORMATION
Frequently Asked Questions
Q. How do I get the system installed?
A. Installation from your cable provider is recommended. They will ensure proper cable
connection to the modem and your computer. However, your retailer may have offered a
self- installation kit, including the necessary software to communicate with your cable ISP.
Q. Once my Cable Modem is connected, how do I get access to the Internet?
A. Your local cable company provides your internet service*, offering a wide range of services
including email, chat, and news and information services, and a connection to the World
Wide Web.
Q. What do you mean by “Broadband?”
A. Simply put, it means you’ll be getting information through a “bigger pipe,” with more
bandwidth, than a standard phone line can offer. A wider, “broader” band means more
information, more quickly.
Q. What is DOCSIS and what does it mean?
A. “Data over Cable Service Interface Specifications” is the industry standard that most cable
companies are adopting as they upgrade their systems. Should you ever decide to move,
the Cable Modem will work with all upgraded cable systems that are DOCSIS-compliant.
* Monthly subscription fee applies.
** Additional equipment required. Contact your Cable Company and ISP for any restrictions or
additional fees.
Page 56 / 59
Page 57

General Troubleshooting
You can correct most problems you have with your product by consulting the troubleshooting
list that follows.
I can’t access the internet.
Check all of the connections to your Cable Modem.
Your Ethernet card may not be working. Check each product’s documentation for more
information.
The Network Properties of your operating system may
not be installed correctly or the
settings may be incorrect. Check with your ISP or cable company.
I can’t get the modem to establish an Ethernet connection.
Even new computers don’t always have Ethernet capabilities – be sure to verify that your
computer has a properly installed Ethernet card and the driver software to support it.
Check to see that you are using the right type of Ethernet cable.
The modem won’t register a cable connection.
If the modem is in Initialization Mode, the INTERNET light will be flashing. Call your Cable
Company if it has not completed this 5-step process within 30 minutes, and note which
step it is getting stuck on.
The modem should work with a standard RG-6 coaxial cable, but if you’re using a cable
other than the one your Cable Company recommends, or if the terminal connections are
loose, it may not work. Check with your Cable Company to determine whether you’re
using the correct cable.
If you subscribe to video service over cable, the ca
ble signal may not be reaching the
modem. Confirm that good quality cable television pictures are available to the coaxial
connector you are using by connecting a television to it. If your cable outlet is “dead”, call
your Cable Company.
Verify that the Cable Modem service is DOCSIS compliant by calling your cable provider.
Page 57 / 59
Page 58

Service Information
If you purchased or leased your Cable Modem directly from your cable company, then
warranty service for the Digital Cable Modem may be provided through your cable provider or
its authorized representative. For information on 1) Ordering Service, 2) Obtaining Customer
Support, or 3) Additional Service Information, please contact your cable company. If you
purchased your Cable Modem from a retailer, see the enclosed warranty card.
Page 58 / 59
Page 59

Federal Communication Commission Interference Statement
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two
conditions: (1) This device may not cause harmful interference, and (2) this device must accept
any interference received, including interference that may cause undesired operation.
This equipment has been tested and found to comply with the limits for a Class B digital device,
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable
protection against harmful interference in a residential installation. This equipment generates,
uses and can radiate radio frequency energy and, if not installed and used in accordance with
the instructions, may cause harmful interference to radio communications. However, there is
no guarantee that interference will not occur in a particular installation. If this equipment does
cause harmful interference to radio or television reception, which can be determined by turning
the equipment off and on, the user is encouraged to try to correct the interference by one of
the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that
to which the receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: Any changes or modifications not expressly approved by the party responsible for
compliance could void the user's authority to operate this equipment.
This transmitter must not be co-located or operating in conjunction with any other antenna or
transmitter.
Operations in the 5.15-5.25GHzband are restricted to indoor usage only.
Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled
environment. This equipment should be installed and operated with minimum distance 20cm
between the radiator & your body.
Page 59 / 59
 Loading...
Loading...