Page 1

CYBER SECURITY BEST PRACTICES
TO PROTECT YOUR MUNICIPALITY
Defend against ever-evolving ransomware and other
emerging threats
Six steps to a comprehensive
security strategy:
1. Assess
2. Build
3. Protect
4. Detect
5. Recover
6. Retire
Solution brief
>60%
of all ransomware attacks in 2019
were targeted at state and local
government agencies.
1
statescoop.com/report-70-percent-ofransomware-attacks-in-2019-hit-state-andlocal-governments/.
1
Protecting government agencies and the people
they serve requires more than just a patchwork of
security solutions.
Today, safeguarding confidential personal and
financial information requires agencies to have
comprehensive and proactive security. Here’s why:
• Agencies are increasingly interconnected, with
computer technology woven throughout all
facets of government—with just about everyone
and every thing sharing data.
• Public servants and citizens need reliable and
prompt access to government networks onpremises and through online portals.
• Criminals targeting government agencies are
increasing the sophistication of their attacks
while phishing, ransomware, distributed
denial-of-service (DDoS) attacks, and more are
becoming commonplace.
What agencies need is an end-to-end cyber
security solution, one that encompasses everything
from planning through deployment to end of life
with single-pane-of-glass management.
SECURITY BEST PRACTICES
HPE follows a holistic security strategy to protect
your organization’s infrastructure from “cradle to
grave.” From the hardware supply chain to your
device’s end of life, HPE provides comprehensive
security to detect and prevent unauthorized access
as well as rapid recovery from disasters. To do all of
this, we focus on six key steps throughout the life
cycle of your infrastructure:
1. Assess: Before building any cyber security
solution, you will need a plan. HPE can help you
determine exactly what solution your agency
needs to meet your specific security challenges.
Our HPE Pointnext Services experts can
provide insights and tangible action plans to
mitigate risks to your assets and applications.
We follow ISO/IEC 270022013 guidelines to
choose the right solutions for your particular
needs and threat environment.
2. Build: Today’s threats are constantly evolving
to infiltrate your network. With HPE, you can
protect your infrastructure through a secure
root of trust, available in all HPE Gen10
Page 2
Solution brief
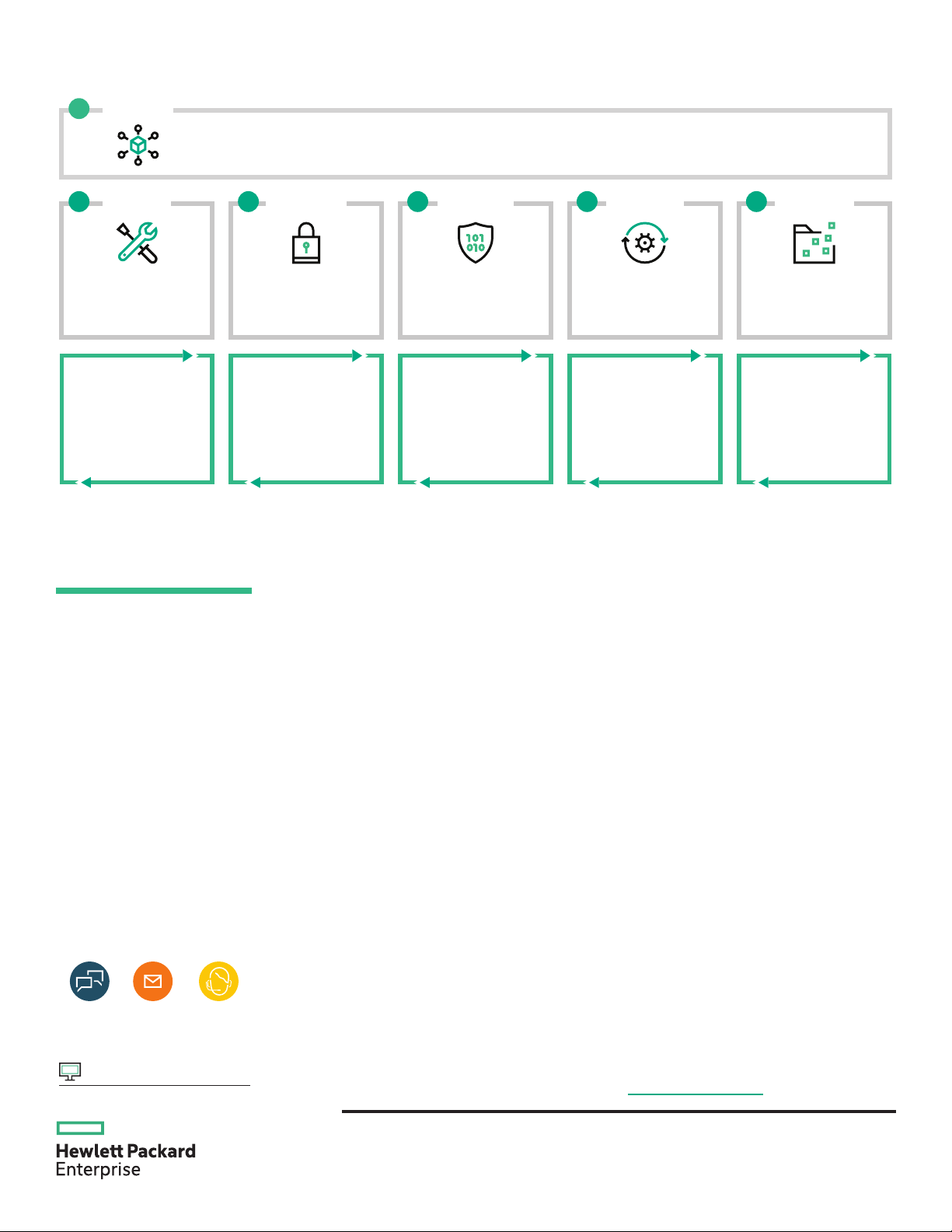
Assess
1
AN ENDTOEND SECURITY APPROACH
• Insights and tangible action plans to mitigate risks to your assets and applications
• Security controls assessment based on ISO/IEC 27002:2013
Build DetectProtect Recover Retire
2 3 4 5
Secure Silicon to
Supply Chain
Access Control and
Attack Detection
Identify Potential
User and Behavioral
Risks (UEBA)
• Silicon root of trust in
all Gen10 servers
•
Secure encryption
• DFARS-compliant
supply chain
Looking for an as-a-service oering?
Consider HPE GreenLake consumption
solutions for all phases of the security
life cycle. Experience the agility and
economics of public cloud with the
security and performance of
on-premises IT.
2
“HPE Get 6-Nines Guarantee, HPE Nimble
Storage,” September 2017.
Make the right purchase decision .
Contact our presales specialists.
Chat
Email
Call
Get updates
•
Policy-based network
access control
•
Military-grade encryption
for data storage
•
Detection of compromise
•
Full recovery capability
servers. While we carefully choose our partners
and suppliers, our encrypted root of trust
adds an additional layer of protection by
cryptographically validating the integrity of
HPE’s DFARS-compliant supply chain from
silicon to your data center.
3. Protect: Access control and threat detection
protect your HPE infrastructure with policy-based
network-access control, military-grade encryption
for data storage, intrusion detection, and full
recovery capabilities. With Aruba ClearPass, you
can easily take charge of your network, prevent
unauthorized access to sensitive information, and
further harden your network against cyberattacks.
4. Detect: HPE takes a proactive approach to
monitoring. With user and entity behavior
analytics (UEBA), our infrastructure uses AI and
machine learning to detect threats and flag any
suspicious activity.
HPE Integrated Lights-Out (iLO) can help you
configure, monitor, and update your HPE servers
seamlessly, and HPE iLO Advanced gives
even more cyber security control with runtime
firmware validation. With HPE InfoSight, you
have full visibility in a single pane of glass.
5. Recover: Get your services back online quickly.
HPE leverages on-premises and cloud-based
solutions to provide backup and rapid recovery
from cyberattacks. HPE Nimble Storage, for
example, leverages flash storage and predictive
analytics to eliminate the gap and guarantee
999999% availability, delivering the best all-
• AI and machine learning
to detect threats
• Dashboards and
proactive monitoring
and alerts
6
Backup and Restore End of Life
• On-premises and cloud-
based solutions
• Rapid recovery from
cyberattacks to resume
operations
flash capacity per terabyte in the industry—and
future-proofing design for value today and in
the future.2
6. Retire: When the time comes to retire
your hardware, HPE can help you safely
decommission or redeploy your IT assets.
HPE iLO Advanced can securely erase user
data, ensuring that your servers are wiped clean
before end of life.
• Crypto-erase data to
safely allow your
organization to
decommission or
redeploy IT assets
WHY HPE
Our holistic approach to cyber security protects
your organization throughout your infrastructure’s
life cycle. But don’t take our word for it. Marsh, a
global leader in cyber insurance, has worked with
other leading insurance companies to create the
Cyber CatalystSM program to establish a baseline for
cyber security solutions and recognize those that
are compliant. Both HPE’s exclusive root of trust
and Aruba ClearPass are certified under the Cyber
Catalyst program for their ability to reduce risk.
GET STARTED
Cyber security is a critical issue for municipalities
today, but HPE can help you navigate the risks.
Let us protect your agency—and more importantly
your citizens—with the holistic security needed to
address threats both today and tomorrow.
LEARN MORE AT
hpe.com/security
© Copyright 2020 Hewlett Packard Enterprise Development LP. The information contained herein is subject to change
without notice. The only warranties for Hewlett Packard Enterprise products and services are set forth in the express warranty
statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty.
Hewlett Packard Enterprise shall not be liable for technical or editorial errors or omissions contained herein.
a00097864enw, April 2020
 Loading...
Loading...