Page 1
DATA SHEET
WEB CONTENT CLASSIFICATION (WEBCC) BUNDLE
(URL Filtering, IP Reputation, and Geolocation Filtering)
Aruba’s WebCC service bundle is a subscription-based license
available for ArubaOS controller-managed networks and Aruba
Central cloud-managed APs. WebCC complements the
application visibility and user-role based access control
included within Policy Enforcement Firewall (PEF) for Dynamic
Segmentation.
The WebCC bundle includes URL ltering, IP reputation, and
geo-location ltering. The web dictionaries are continuously
updated to provide up-to-date policy enforcement and
rate-limiting actions.
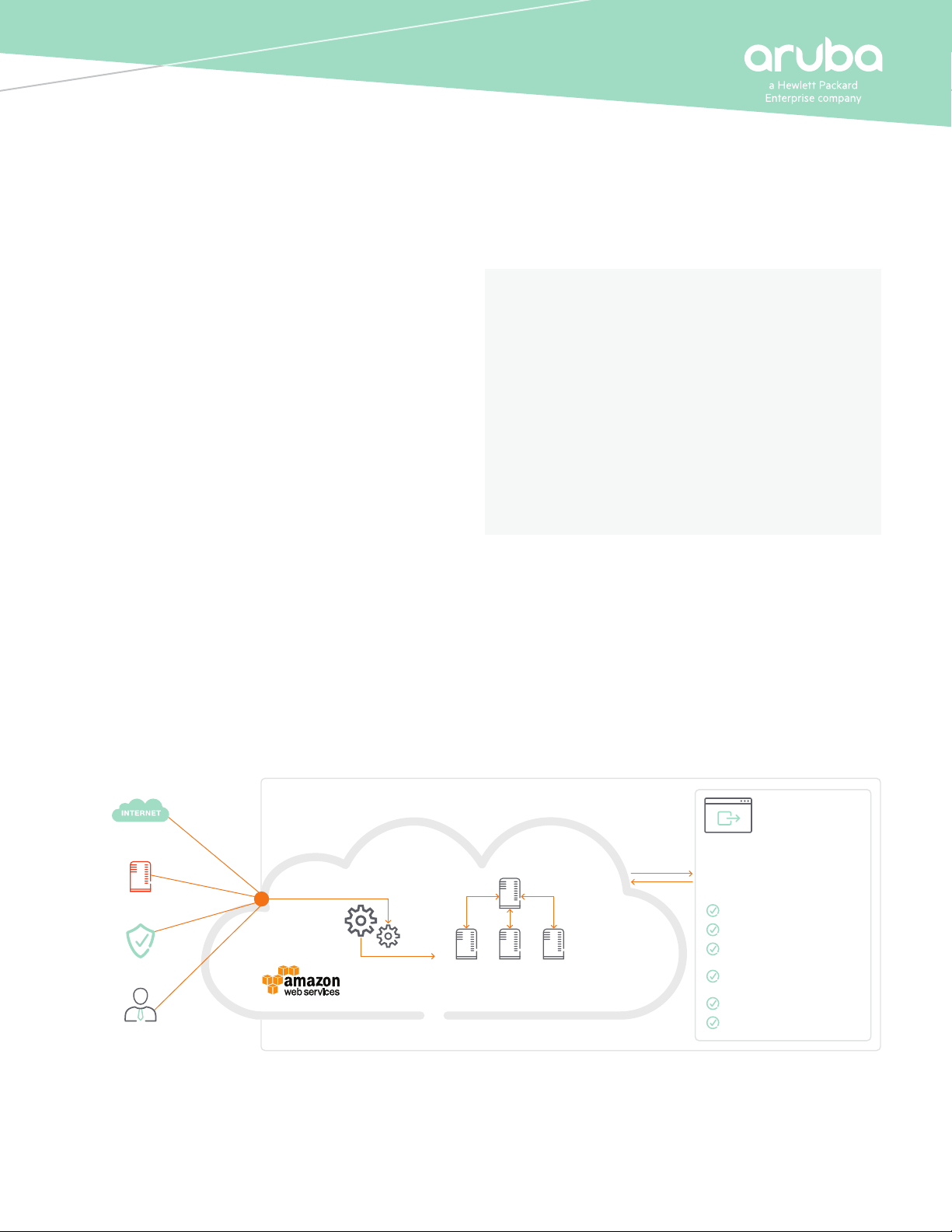
URL FILTERING
The solution involves extracting the hostnames and URLs that
users are browsing using the Aruba DPI engine.
The URLs are then looked up in a locally-cached database that
contains commonly used and recently accessed web sites. If the
user’s site is not on the list, the network makes a request for the
category, classication, and reputation of the web site from the
threat intelligence engine that classies and scores an average of
2500+ URLs per second.
FEATURES AND BENEFITS
• Enhances policy enforcement with an expanded
library of denitions
• Deploys an automated algorithm to identify
suspicious IPs
• Examines and correlates by the IP
• Applies built-in rules to test the IP
• Determines if and how long to restrict the IP
• Releases the restrictions on the IP but keeps it
under watch
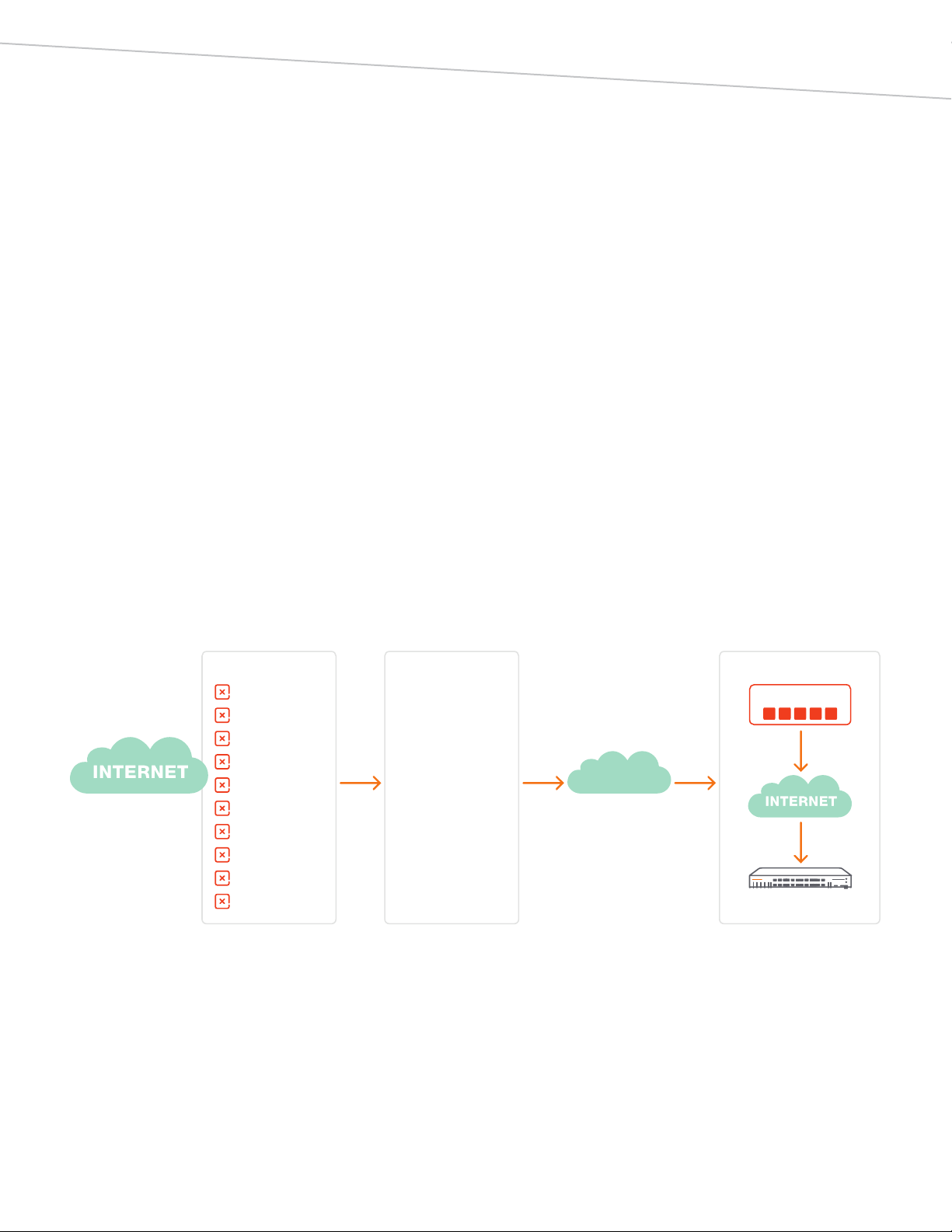
IP REPUTATION
The IP Reputation helps augment security posture by adding
a dynamic IP reputation service to existing defenses. This
service provides a real time feed of known malicious IP
addresses broken down into 10 categories so IT security
administrators can easily identify threats by type. These
categories are: Windows Exploits, Web Attacks, Phishing,
Botnets, Denial of Ser vice, Scanners, Proxies, Reputation,
Spam Sources, and Mobile Threats.
Internet
Sensor Network
Global Threat Databases
Security Partners
Customers (Millions)
THREAT INTELLIGENCE PLATFORM
Contextual Database
Capture
Classify
Analyze
Publish
URLs (Billions)
Domains (Millions)
IPs (Billions)
File MobileInternet
Behaviors (Billions)
Apps (Millions)
Connected Sensors (Millions)
URL FILTERING
83+ Site Categories, such as
Shopping, Job Search, Sports,
Pornography, as well as various
threat categories including:
Bot Nets
Malware Sites
Phishing and
Other Frauds
Proxy Avoidance
and Anonymizers
Spam URLs
Spyware and Adware
figure 1.0_071916_webcc-dsa
Page 2
DATA SHEET
WEB CONTENT CLASSIFICATION (WEBCC) BUNDLE
Security is increased with this service as the time required to
identify new and existing IP threats is drastically reduced. Not
only does the service decrease the time it takes to research
IP addresses, it also provides visibility into the types of
threats, as well as historical and geolocation data to help
security admins make better threat decisions.
The service uses a big data architecture to provide the most
comprehensive and accurate threat intelligence available
today, including up-to-the-minute intelligence on IPs of
emerging threats. This includes a dynamic list of
approximately 12 million dangerous IPs at any given time.
This intelligence can be used to block trac from TOR
nodes, proxies, botnets, and other malicious actors. In
addition, customers can also access a rich set of meta data
for investigative purposes. For example, proxies have been
used for more than just obfuscation but also to launch
short span DDoS attacks. Similarly, botnet command and
control contains BOT IPs and also the originating central
server IP. This insight can help security administrators
better understand incoming threats so they can take
proactive measures.
The service analyzes and correlates data to create a predictive
risk score, which falls into one of ve rating bands ranging
from trustworthy to malicious. The IP Reputation Index
provides scores ranging from 1 to 100, with tiers split into
Trustworthy, Low Risk, Moderate Risk, Suspicious, and High
Risk (see chart below). Numerically lower scores (higher risk)
indicate IPs that are more likely to be or become bad and are
monitored at a greater frequency than trustworthy IPs.
The reputation tiers allows for enterprises to nely tune their
security settings based on risk tolerance and business needs.
For example, a highly security conscious bank may choose to
block any thing with a score lower than 80, while others may
choose to accept trac from IPs with scores higher than 60,
as long as the site being accessed is aliated with a partner.
GEOLOCATION FILTERING
The Geolocation ltering service allows an organization to
associate source/destination IP addresses with location.
PEF can be leveraged to apply policies to permit or drop
inbound or outbound communications with certain known
malicious countries.
All IPv4 and
Active IPv6 IPs
KEY THREAT TYPES
Windows Exploits
Web Attacks
Phishing
Botnets
Denial of Service
Scanners
Proxies
Reputation
Spam Sources
Mobile Threats
SENSOR NETWORK IP REPUTATION SERVICE
Threat IPs
Semi-open Proxy Farms
Exploit Honeypots
Native User Simulation
Web App Honeypots
Spam Traps
Third-party Sources
Threat Correlation
5 minutes
Aruba Mobility Controller
figure 2.0_071916_webcc-dsa
Page 3
DATA SHEET
WEB CONTENT CLASSIFICATION (WEBCC) BUNDLE
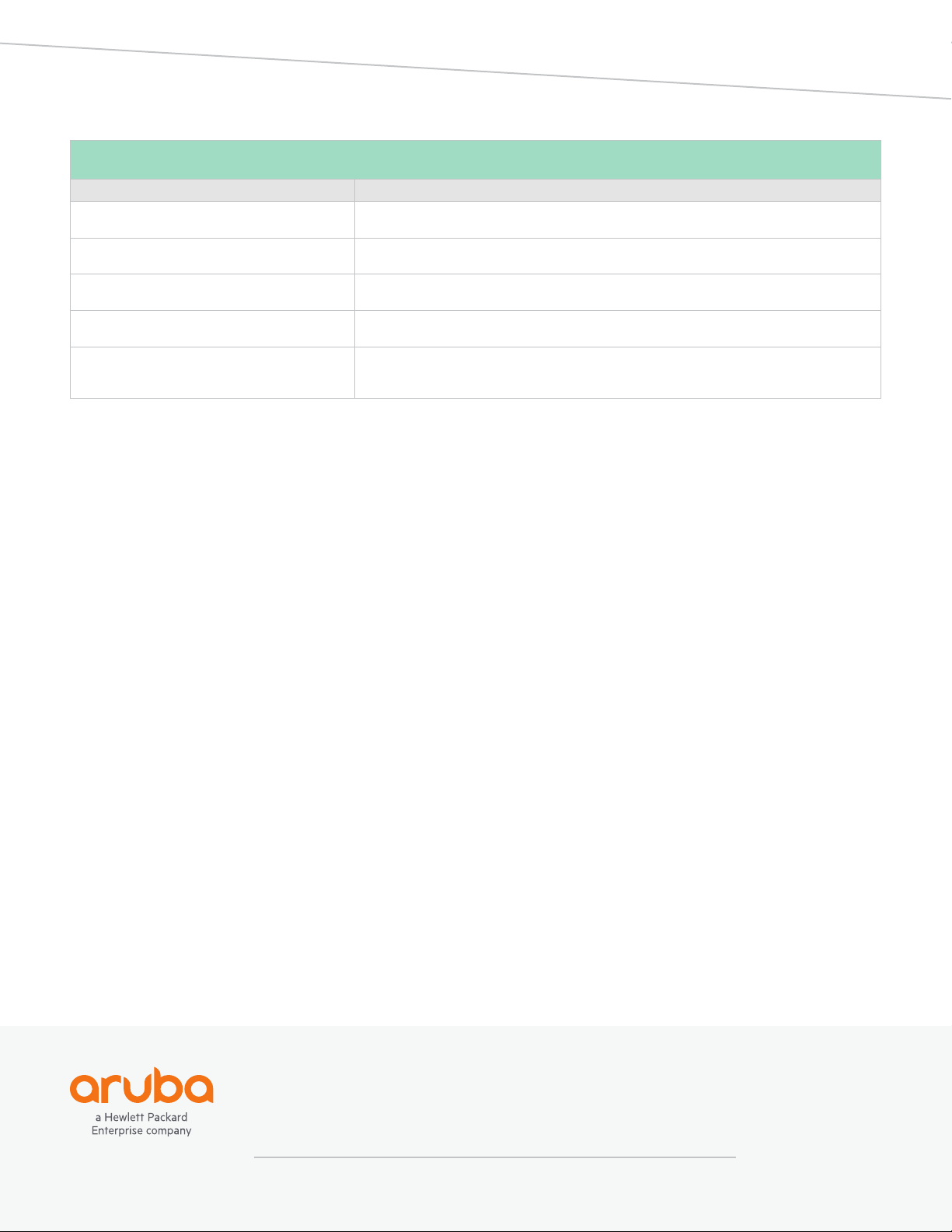
ORDERING INFORMATION*
Part Number Description
SUB1-WebCC 1 year subscription license for Aruba Mobility Controller WebCC Feature license per Access
Point. The supported controllers include 70xx and 72xx running ArubaOS 6.5 and beyond.
SUB3-WebCC 3 year subscription license for Aruba Mobility Controller WebCC Feature license per Access
Point. The supported controllers include 70xx and 72xx running ArubaOS 6.5 and beyond.
SUB5-WebCC 5 year subscription license for Aruba Mobility Controller WebCC Feature license per Access
Point. The supported controllers include 70xx and 72xx running ArubaOS 6.5 and beyond.
SUB7-WebCC 7 year subscription license for Aruba Mobility Controller WebCC Feature license per Access
Point. The supported controllers include 70xx and 72xx running ArubaOS 6.5 and beyond.
SUB10-WebCC 10 year subscription license for Aruba Mobility Controller WebCC Feature license per
Access Point. The supported controllers include 70xx and 72xx running ArubaOS 6.5
and beyond.
*For Aruba Central ordering information, please refer to the Aruba Central datasheet
© Copyright 2019 Hewlett Packard Enterprise Development LP. The information contained herein is subject to change without
notice. The only warranties for Hewlett Packard Enterprise products and services are set forth in the express warranty statements
accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Hewlett
Packard Enterprise shall not be liable for technical or editorial errors or omissions contained herein.
DS_WebCC_SK_051719 a00073443enw
Contact Us Share
 Loading...
Loading...