Page 1

StorTrends®
iTX Software
CLI (Command Line Interface)
(Version 2.7)
User’s Guide
MAN-STOR-ITX27-CLI
06/07/2010
Page 2

© Copyright 1985-2010 American Megatrends, Inc.
All rights reserved.
American Megatrends, Inc.
5555 Oakbrook Parkway
Norcross, GA 30093
This publication contains proprietary information which is protected by copyright. No part of this publication can be
reproduced, transcribed, stored in a retrieval system, translated into any language or computer language, or
transmitted in any form whatsoever without the prior written consent of the publisher, American Megatrends, Inc.
American Megatrends, Inc. acknowledges the following trademarks:
Intel and Pentium are registered trademarks of the Intel Corporation.
AMD, Athlon, and Athlon XP are trademarks of the Advanced Micro Devices Corporation.
Sun and NFS are trademarks of the Sun Microsystems Corporation.
Microsoft, Windows, Internet Explorer and MS-DOS are registered trademarks of the Microsoft Corporation and
Active Directory is a trademark of the Microsoft Corporation.
Macromedia Flash is a trademark of the Macromedia Corporation.
IBM, AT, VGA, PS/2, and OS/2 are registered trademarks and XT and CGA are trademarks of the International
Business Machines Corporation.
Digital, DEC, and OpenVMS are trademarks of Digital Equipment Corporation.
Compaq is a registered trademark of the Compaq Corporation.
Hewlett-Packard, HP, and HP-UX are registered trademarks of Hewlett-Packard Company.
Novell, NetWare, IPX, NCP, and NetWare Core Protocol are registered trademarks of the Novell Corporation.
UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open
Company Ltd.
Linux is a registered trademark of Linus Torvalds.
Red Hat is a registered trademark of the Red Hat Corporation.
Apple and AppleTalk are registered trademarks of Apple Computer Corporation.
Yellow Pages is a registered trademark in the United Kingdom of British Telecom.
Ethernet is a registered trademark of the Xerox Corporation.
802 is a registered trademark of the Institute of Electrical and Electronic Engineers, Inc. (IEEE).
Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks
and names or their products. American Megatrends, Inc. disclaims any proprietary interest in trademarks and trade
names other than its own.
Revision History
02/16/06 Created iTX 2.1 CLI document.
02/16/06 iSCSI Tape command added.
02/16/06 UPS driver config command added.
02/23/06 Synchronous replication commands added.
06/20/06 Volume and Snapshot commands updated.
06/21/06 Synchronous replication, iSCSI configuration updated.
06/23/06 Document is revised and examples are added.
07/14/06 General Server configuration section updated.
07/27/06 Updated for version 2.5.1011 and above.
08/17/06 Added Error Codes section.
04/26/07 Changed the volume chunk size.
04/26/07 Added the SRM commands.
06/28/07 Removed Tape commands.
01/16/09 Updated document and added journal and cdp commands.
12/11/09 Update the network command usage and CLI error text
01/25/10 Updated the OS Agnostic HA related commands and CLI error text
01/25/10 Updated Network Alias commands
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
ii
Page 3

01/25/10 Updated the iSCSI commands and corrected wrong format updation
03/30/10 Corrected the Create Volume usage and Get Eventlog Usage.
04/11/10 Update the create replication commands
06/07/10 Corrected the output of ‘cli main’.
06/07/10 Removed the term apple
06/07/10 Corrected set -t nfs command.
06/07/10 Corrected set raid commands.
06/07/10 Added available cache options for create raid.
06/07/10 Since alarm and cache is supported for set raid; the ‘not supported’ was removed.
06/07/10 Osinfo commands removed.
Preface
iii
Page 4

Table of Contents
Revision History ......................................................................................................................................... ii
Table of Contents ..................................................................................................................................... iv
Table of Contents ..................................................................................................................................... iv
Limited Warranty ....................................................................................................................................... v
Limitations of Liability ................................................................................................................................ v
Technical Support ...................................................................................................................................... v
Web Site ................................................................................................................................................ v
Disclaimer ................................................................................................................................................. vi
Chapter 1 Overview of CLI ..................................................................................................................... 1
Preface ...................................................................................................................................................... 1
Overview of CLI ......................................................................................................................................... 1
Accessing CLI ............................................................................................................................................ 1
Initial Setup ................................................................................................................................................ 2
Network Configuration ........................................................................................................................... 2
Volume Configuration ................................................................................................................................ 3
1. RAID Disk Creation ............................................................................................................................ 3
2. Container and Volume Configuration................................................................................................. 4
3. Enabling Share or Target ................................................................................................................... 5
Chapter 2 Command Set ........................................................................................................................ 7
Command Set ............................................................................................................................................ 7
Alert Configuration ..................................................................................................................................... 9
Date/Time Configuration .......................................................................................................................... 10
Domain Configuration .............................................................................................................................. 10
Event log Commands .............................................................................................................................. 11
Firewall Configuration .............................................................................................................................. 12
General Server Configuration .................................................................................................................. 13
Health Configuration ................................................................................................................................ 13
iSCSI Configuration ................................................................................................................................. 14
License configuration ............................................................................................................................... 16
Network Controller Configuration ............................................................................................................ 17
NAS Quota Configuration ........................................................................................................................ 18
NAS User / Group Configuration ............................................................................................................. 19
Protocol Configuration ............................................................................................................................. 20
RAID & Disk Management Commands ................................................................................................... 21
Share, Directory & ACL Configuration ..................................................................................................... 24
System Control Configuration ................................................................................................................. 26
Volume and Snapshot Commands .......................................................................................................... 26
UPS Configuration ................................................................................................................................... 29
Synchronous replication .......................................................................................................................... 30
Asynchronous Replication ....................................................................................................................... 33
Journal Volume Management ................................................................................................................. 39
Continuous Data Protection..................................................................................................................... 41
Recovery Wizard ..................................................................................................................................... 41
Storage Resource Management ............................................................................................................. 42
Local and Replicated Snapshot validation .............................................................................................. 43
Appendix A Error Codes ...................................................................................................................... 45
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
iv
Page 5
Limited Warranty
The buyer agrees that if this product proves to be defective, American Megatrends is only obligated to repair
or replace this product at American Megatrends’ discretion according to the terms and conditions of the
warranty registration software that accompanies this product. American Megatrends shall not be liable in
tort or contract for any loss or damage, direct, incidental or consequential resulting from the use of this
product. Please see the Warranty Registration Software shipped with this product for full warranty details.
Limitations of Liability
American Megatrends, Inc. shall in no event be held liable for any loss, expenses, or damages of any kind
whatsoever, whether direct, indirect, incidental, or consequential (whether arising from the design or use of
this product or the support materials provided with the product). No action or proceeding against American
Megatrends may be commenced more than two years after the delivery of product to Licensee of Licensed
Software.
Licensee agrees to defend and indemnify American Megatrends from any and all claims, suits, and liabilities
(including attorney’s fees) arising out of or resulting from any actual or alleged act or omission on the part of
Licensee, its authorized third parties, employees, or agents, in connection with the distribution of Licensed
Software to end-users, including, without limitation, claims, suits, and liability for bodily or other injuries to
end-users resulting from use of Licensee’s product not caused solely by faults in Licensed Software as
provided by American Megatrends to Licensee.
Technical Support
American Megatrends provides technical support for American Megatrends products purchased directly
from American Megatrends or from an American Megatrends-authorized reseller only.
If… Then…
You purchased this product from American Megatrends
or from a certified American Megatrends reseller,
This American Megatrends product was installed as part
of a system manufactured by a company other than
American Megatrends or you purchased an American
Megatrends product from an unauthorized reseller,
If the American Megatrends StorTrends® iTX Software fails to operate as described or you are in doubt
about a configuration option, please call technical support at 770-246-8645.
Web Site
We invite you to access the American Megatrends’ World Wide Web site at:
http://www.ami.com/
call American Megatrends’ technical support at 770246-8645. Please be prepared to specify the serial
number or CD Key of the product (if applicable).
call the technical support department of the computer
manufacturer or the unauthorized reseller. American
Megatrends does not provide direct technical support in
this case.
Preface
v
Page 6

Disclaimer
This manual describes the operation of the American Megatrends StorTrends® iTX Software. Although
efforts have been made to assure the accuracy of the information contained here, American Megatrends
expressly disclaims liability for any error in this information, and for damages, whether direct, indirect,
special, exemplary, consequential or otherwise, that may result from such error, including but not limited to
the loss of profits resulting from the use or misuse of the manual or information contained therein (even if
American Megatrends has been advised of the possibility of such damages). Any questions or comments
regarding this document or its contents should be addressed to American Megatrends at the address shown
on the inside of the front cover.
American Megatrends provides this publication “as is” without warranty of any kind, either expressed or
implied, including, but not limited to, the implied warranties of merchantability or fitness for a specific
purpose.
Some states do not allow disclaimer of express or implied warranties or the limitation or exclusion of liability
for indirect, special, exemplary, incidental or consequential damages in certain transactions; therefore, this
statement may not apply to you. Also, you may have other rights which vary from jurisdiction to jurisdiction.
This publication could include technical inaccuracies or typographical errors. Changes are periodically made
to the information herein; these changes will be incorporated in new editions of the publication. American
Megatrends may make improvements and/or revisions in the product(s) and/or the program(s) described in
this publication at any time.
Requests for technical information about American Megatrends products should be made to your American
Megatrends authorized reseller or marketing representative.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
vi
Page 7
Chapter 1 Overview of CLI
Preface
Our feature rich StorTrends® iTX comes with a built-in command line interface (CLI) that provides
extensive options to monitor and control “managed objects”. Wherever applicable, CLI follows industry
standards and uses extensible ‘tags’ for new features and objects. The command line utility can be accessed
through an in-band special console connected to the StorTrends® iTX system or out-of-band via a SSH or
telnet client. It can also be used with scripting languages to automate a set of operations.
Overview of CLI
Our CLI supports commands in excess of 140 verbs and supports XML output format. The design is very
similar to DMTF SMASH specifications and is being extended to fully comply with SMASH. Every managed
element or object has a SMASH compliant <Target> addressing conforming to the server management
instance addressing specification. The commands implemented are essentially “stateless” in nature. SMASH
compliant <Verbs> is used to select the management actions, which are complemented by extensive <Option>
attributes to control the behavior of the command. <Property> attributes can control the behavior of the
output produced by the <Verb> along with various other mapping actions to the CIM schema.
The output produced can be controlled depending on the need, For example, in automation scripting. Output
can also be made to be in the W3C standard compliant, self-descriptive XML format. The output format
includes new tags pertinent to the object management. Inherent support for multi-lingual documents and
Unicode data, along with content separation from presentation, aids in development of management
applications that have their own data representation format. CLIs used for monitoring of performance
parameters are dished out in XML tags that assist in graphing and charting, and can be right away imported
by spreadsheet applications.
Accessing CLI
The CLI can be accessed either through an in-band console connected directly to the ITX box or through the
out-of-band / remote CLP agents. It can also be accessed through a remote terminal emulation program using
SSH or Telnet. Once connected, the administrator has to login to the system to perform the operations. In a
typical console session, the user will be presented with a login screen such as:
login: cli <Enter>
password: ******* <Enter>
“cli” is the special user that has been provided with CLI access. The password is factory defaulted to
“password”. Once logged in, the system will present the user with a CLI shell as follows:
CLI>
The user can then enter the supported commands in any order. The supported commands are listed in the
next section. To close the session, the user can type the command ‘quit’. This will end the session.
Chapter One: Overview of CLI
1
Page 8

Initial Setup
Network Configuration
Once the StorTrends® iTX is installed in a new system, please ensure that the initial network configuration is
proper. The system factory defaults to DHCP setup. The configured network settings can be verified by the
following CLI commands:
CLI> get –-type or –t port
-–name or –n NIC-1
--info or -i
network <Enter>
Example: get –t port –n nic-1 –i network
This will display the NIC-1 network settings.
To configure static IP to this port:
CLI> set –-type or –t port
–-name or –n NIC-1
–-ip or –i 10.0.0.100
–-mask or –m 255.255.255.0
–-gate or –g 10.0.0.7 (optional)
--pridns or –p 10.0.0.2 (optional)
--secdns or –s 0.0.0.0 (optional)
--dnssuff or –f ami.com (optional)
network <Enter>
Example: set –t port –n nic-1 –i 10.0.0.100 –g 10.0.0.7
-p 10.0.0.2 –s 0.0.0.0 –f ami.com network
Here 10.0.0.100 is the static IP address, 255.255.255.0 is netmask and 10.0.0.7 is the network gateway.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
2
Page 9

Volume Configuration
Initial volume configuration can be done in three stages.
1. RAID Disk Creation
At the base level is the RAID CONTROLLER.
CLI> list –-type or –t controller
raid <Enter>
Example: list –t controller raid
This will list the available RAID controllers in the system. By default, Software MD will be shown as a RAID
controller with controller number “0”. If Hardware RAID controllers present, then they will take precedence
over Software MD.
CLI> list –-type or -t PD
--controllerno or -n 0
raid <Enter>
Example: list –t pd –n 0 raid
This will list the PD’s that are available for configuration in controller number zero. PD’s can be grouped
through a RAID level to form a Logical disk – LD.
CLI>create –-type or -t LD
–-stripesize or -p 64
–-diskname or -d /dev/sda (use –d 1 or –d 2…15 on a 3U)
–-diskname or –d /dev/sdb
–-diskname or –d /dev/sdc
–-diskname or –d /dev/sdd
--raidlevel or –r 0
--controllerno or –n 0
--cachemode or –m 3
raid <Enter>
Example: create –t ld –p 64 –d 1 –d 2 –r 1 –n 0 –m 2 raid
This will create a RAID 1 Logical Disk – LD with 64K-chunk size and two disks on a 3U.
Example: create –t ld –p 64 –d /dev/sda –d /dev/sdb –d
/dev/sdc –r 5 –n 0 –m 1 raid
This command will crate a RAID 5 Logical disk – LD with 64 k chunk size and three disks on a 1U box.
CLI> list –-type or –t LD
raid <Enter>
Example: list –t ld raid
This will list the available RAID LD’s present in the system.
Chapter One: Overview of CLI
3
Page 10

2. Container and Volume Configuration
Next step is the AMI DVM container creation. This can be done by the following commands:
CLI>create –-type or -t container
–-containername or -c container1
–-chunksize or –k 64
–-ldname or –l /dev/md0
volume <Enter>
Example: create –t container –c accounting –k 64 –l
/dev/sdb volume (for a 3U)
This command creates a container named “accounting” from the LD /dev/sdb.
On a 1U, LDs are created with names of /dev/mdX, with X as 0, 1, and so on. Therefore the above operation
would be accomplished by entering, for example:
Example: create –t container –c marketing –k 64 –l
/dev/md1 volume
The next step is the creation of volumes.
A NAS volume can be created by the following command:
CLI>create –-type or –t volume
–-containername or -c container1
–-volumename or -v nasvol0
–-volumesize or -z 1000 (in GB)
–-provisiontype or -p 0 (0 is thin-provisioned, 1 is exact)
–-volumetype or -e 0 (type 0 is ROW)
–-voldialect or –f 1 (dialect 1 is NAS, 0 is iSCSI)
--chunksize or –k (8 or 64 for 8KB and 64KB chunk sized volume
respectively.)
volume <Enter>
Example: create –t volume –c container1 –v volume1 –z 1000 –p 0 –
e 0 –f 1 –k 64 volume
This command creates volume “nasvol0” in container “container1” with size of 1000GB, that is thinprovisioned, Redirect-On-Write, and of NAS type with chunk size as 64KB.
Volume size should be in GBs and currently supported volume type is 0 – ROW.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
4
Page 11

Similarly a SAN volume can be created as follows:
CLI>create –-type or –t volume
–-containername or -c container1
–-volumename or -v sanvol0
–-volumesize or -z 1000
–-provisiontype or -p 0
–-volumetype or -e 0
–-voldialect or -f 0
--chunksize or –k (8 or 64 for 8KB and 64KB chunk sized volume
respectively.)
volume <Enter>
Example: create –t volume –c container1 –v volume1 –z 1000 –p 0 –
e 0 –f 1 –k 8 volume
This command creates volume “sanvol0” in container “container1” with size of 1000GB, that is thinprovisioned, Redirect-On-Write, and of SAN type with chunk size as 8KB.
3. Enabling Share or Target
To enable NAS share, use the following command syntax. Make sure the corresponding share protocol is
enabled in the system.
First, create the directory in the path before creating a share for the path.
CLI>create --path or -p container1_nasvol0/test
dir<Enter>
Example: create –p cont1_nasvol0/test dir
This command creates the subdirectory of “test” within the volume “nasvol0” in the container “cont1”.
Then create the share using the following syntax.
CLI>add –-name or -n NASShare
–-path or -p container1_nasvol0/test
–-prototype or -s cifs
–-prototype or -s nfs
share <Enter>
Example: add –n nasshare –p cont1_nasvol0/test –s cifs –s
nfs share
Note: The path specified should be of format:
“ContainerName_VolumeName/directoryName”.
To create a target, use the following commands.
CLI>add –-type or -t lun
--volumename or -v sanvol0
–-containername or -c container1
–-targetname or -n sanvol0
iscsi <Enter>
Example: add –t lun –v sanvol0 –c cont1 –n sanvol0 iscsi
Chapter One: Overview of CLI
5
Page 12

Then, to enable the target, use the syntax below:
CLI>enable –-type or –t tgt
–-targetname or -n sanvol0
iscsi <Enter>
Example: enable –t tgt –n sanvol0 iscsi
Next step is to activate a port for iSCSI traffic.
CLI>activate –-type or –t portal
–-ipaddress or -p 10.0.0.100
–-portaltag or -g 1 iscsi
Example: activate –t portal –p 10.0.0.100 –g 2 iscsi
We recommend that you assign different portal tags to the two portals if they are on different subnets.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
6
Page 13

Chapter 2 Command Set
Command Set
The CLI design being similar to the DMTF SMASH specifications follows the standard to a great extent. The
commands supported can be represented grammatically as follows:
<verb> <option> … <property> <target>
The CLI provides a wide range of command sets. These commands are grouped into modules for better
understanding. Each command is non-interactive and state-less. The <options> are supported using switches.
Our CLI accepts both short and long options for each switch to make it user-friendly. If there is any error in
the parameters entered, the CLI will display the usage of that particular command.
CLI also provides extensive online help. Each command supports a help option using ‘-h’ or
‘--help’ that will display the grammar of the command.
To get the main list of targets or modules present in CLI, the user should type the command “main” at the
CLI prompt.
The following targets will get displayed:
*****************************************************************
TARGET LIST
-----------------------------------------------------------------
1. ug 2. ups
3. dir 4. srm
5. dump 6. raid
7. ndmp 8. alert
9. iscsi 10. share
11. quota 12. system
13. volume 14. domain
15. health 16. license
17. network 18. journal
19. eventlog 20. protocol
21. firewall 22. datetime
23. timezone 24. serverinfo
25. sysupgrade 26. syncreplica
27. asyncreplica 28. recoverywizard
29. snapvalidation
For more information on the targets please use the following command
show -t/--target <targetname>
Note : Targetnames are case insensitive
Example :
show -t iscsi
*****************************************************************
The show option can also be used to show commands based on <verb>, and to display the list of targets or
verbs available.
Chapter Two: Command Set 7
Page 14

For example: To find out how the show command works, type:
CLI>show -h <Enter>
This will display the many ways the show command can be used.
(this is redundant)
For example: To display the available targets/verbs, the user has to enter:
CLI>show –d targets <Enter>
CLI>show –d verbs <Enter>
The show option can display the functions available for a target or even the functions available for a verb.
For example: To display the functions available for targets/verbs the user has to enter:
CLI>show –t <targetname> <Enter>
Example: show –t ups
CLI>show –v <verbname> <Enter>
Example: show –v list
Note: In the table below, though the <target> is given in the first column together with <verb>, it should
actually be typed at the end of command, complying with SMASH specification. Again, the target
is not case-sensitive.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
8
Page 15
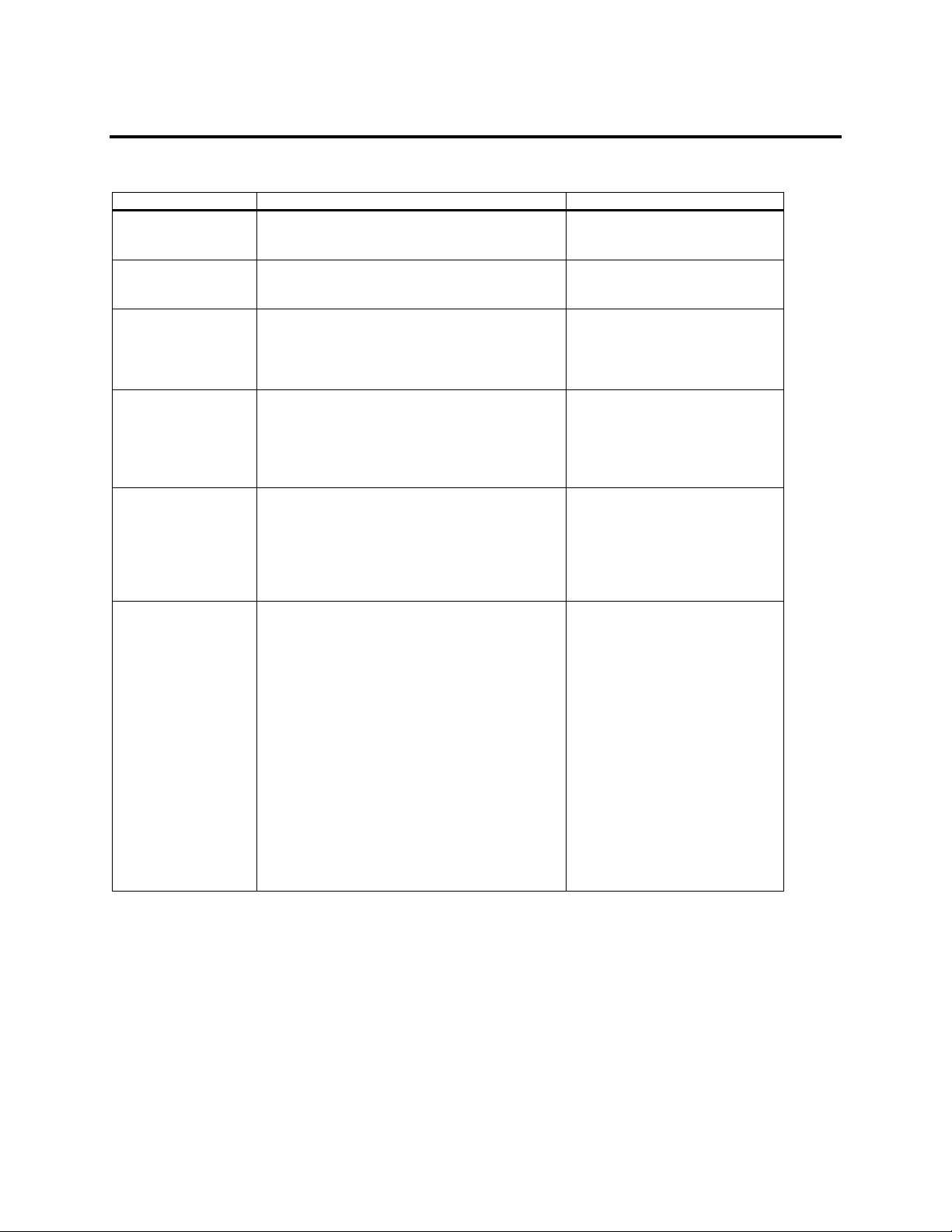
Alert Configuration
These commands configure the way alerts are generated.
Command Argument Description
get alert -t/--type snmp
For example:
get –t snmp alert
get alert -t/--type email
For example:
get –t email alert
delete alert -t/--type snmp
-v/--value <destination>
-x/--xml alert
For example:
delete -t snmp -v 10.0.3.155 -v 10.0.0.203 -x alert
delete alert -t/--type email
-v/--value <emailaddress>
-x/--xml alert
For example:
delete -t email -v sam@yahoo.com -v
yyy@ami.com -x alert
set alert -t/--type snmp
-e/--enable or
-d/--disable
-v/--value <alertmask:communityname:destination>
-x/--xml
For example: set –t snmp –e –v 1:public:10.10.10.5
-x alert
set alert -t/--type email
-e/--enable or
-d/--disable
-v/--value <alertmask:language:emailaddr>
-s/--emailserver (IP address)
-F <Fully Qualified Domain Name>
-x/--xml
For example:
1:1:sam@yahoo.com -s 10.0.0.79 -F ami.com -x
alert
set -t email -e -v
Gives the SNMP alert
configuration.
Gives the Email alert
configuration.
Deletes the SNMP specified
destination from the alert
configuration.
Deletes the specified email address
from the alert configuration.
Configures SNMP alerts.
Note:
<alertmask:communityname:destin
ation>
For example:
<1:public:10.0.0.79>
Configures Email alerts.
<alertmask:language:emailaddr>
<1:1:aaaa@ami.com>
Language
0-Unknown
1-English
2-Japanese
3-Korean
4-Chinese
Alert Mask:
1 - Information
2 - Warning
4 - Fatal
Any combination of the three alert
masks up to a maximum of seven
levels.
Chapter Two: Command Set 9
Page 16
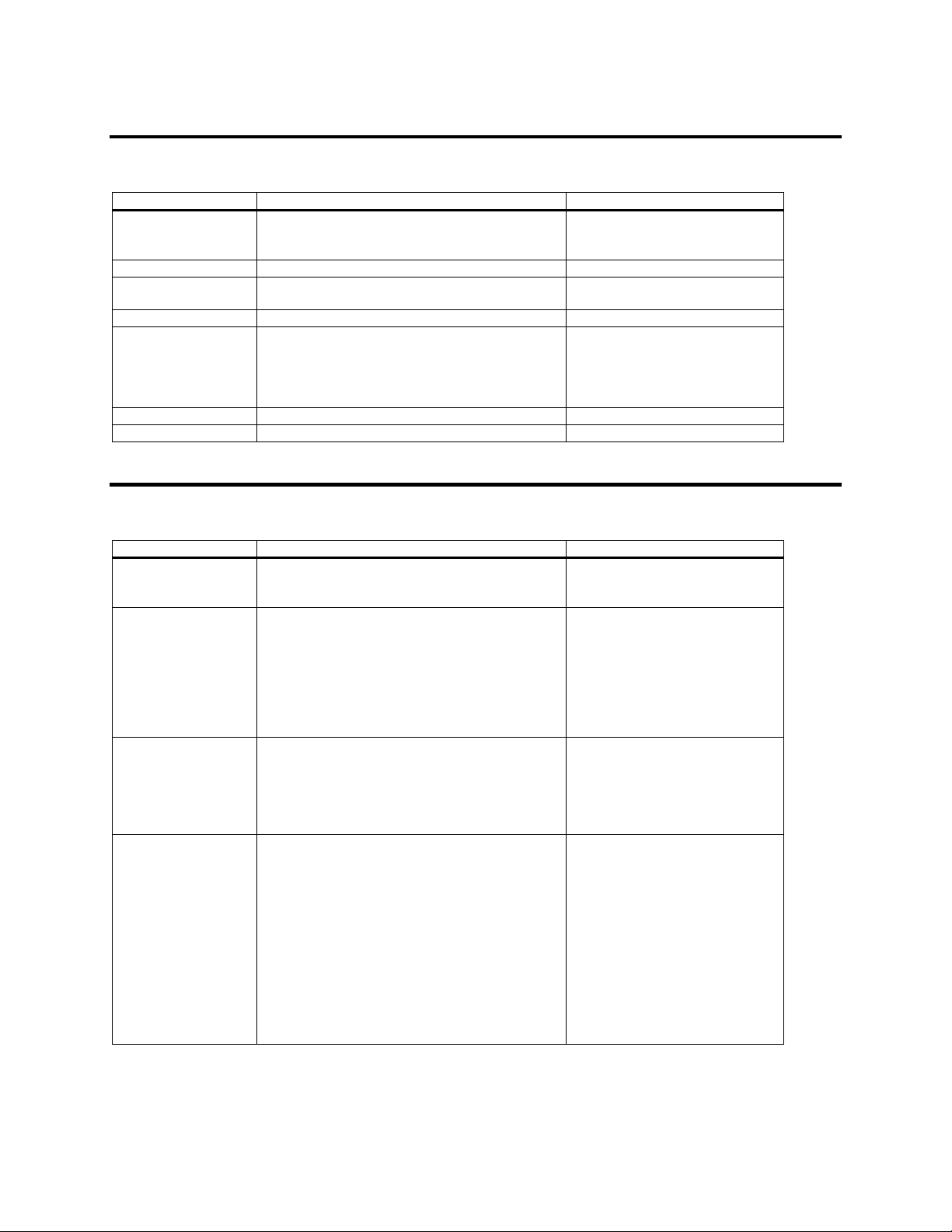
Date/Time Configuration
These commands configure the time zone and date.
Command Argument Description
set timezone -z/--zone <zone name>
-x/--xml
For example: set –z America/New_York timezone
get timezone For example: get timezone Shows the configured time zone.
set datetime -n/--ntp <FQDN of NTP server or ipaddress> Configures the NTP server to be
get timezone -c/--count Gets the number of time zones.
set datetime -d/--date <date in MM/DD/YYYY>
-t/--time <time in HH:MM:SS>
-x/--xml
For example: set –d 12/01/2006 –t 12:11:55
datetime
list timezone For example: list timezone Lists the time zones supported.
get datetime For example: get datetime Shows the date & time.
Sets the time zone of StorTrends®
iTX to given time zone.
used for time synchronization.
Sets the date and time to given
values.
Domain Configuration
These commands configure the domain server to be used for authentication.
Command Argument Description
get domain -t/--type {nis/ms}
-x/--xml
For example: get –t nis domain
set domain -t/--type{ nis }
-b/--broadcast {y/n}
-d/--domain <domainname >
-s/--server <server-1>
-s/--server <server-2>
-x/--xml
For example: set -t nis -b n -d NISSERV -s
10.0.0.215 -s 10.0.0.25 -s 10.0.0.5 domain
set domain -t/--type {ms}
-m/--mtype {wg}
-d/--domain< domainname>
-x/--xml
For example: set -t ms -m wg -d MYGROUP
domain
set domain -t/--type {ms}
-m/--mtype {/nt/ads}
-d/--domain< domainname>
-D/--nbname<netbiosname> (optional)
-i/--ip <serverip>
-I/--secip<secondary serverip> (optional)
-o/--orgname <orgName> (optional)
-u/--user <Adminname >
-p/--passwd <Adminpassword>
-x/--xml
For example: set –t ms –m ads –d domain1.com –D
domain1 –I 10.10.220.1 –u Administrator –p
password domain
Displays the domain information of
either NIS or Microsoft (MS)
domains.
Sets the NIS domain to given
domain with broadcast mode OFF
or ON. Servers can be added using
the –s/--server switch.
If broadcast is set to OFF, then no
servers are needed.
Sets the Microsoft domain type to
Workgroup.
Sets the Microsoft domain type to
NT / ADS.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
10
Page 17
Event log Commands
These commands display or clear the event log.
Command Argument Description
get eventlog -s/--section {v/s/o/h}
-o/--offset <record-offset>
-n/--recordcount <record-count>
-i/--info
-f/--fatal
-w/--warning or
-a – all eventlog
-x/--xml
For example: get –s vs –o 2 –n 20 –f –w eventlog
get eventlog -c/--count
-s/--section {v/s/o/h}
-i/--info
-f/--fatal
-w/--warning or
-a/-- all eventlog
-x/--xml
For example: cli get -s vsoh -a -c eventlog
clear eventlog Clears the complete event log.
Lists event log content matching
the given criteria.
v-Volume
s-System
o-OS
h-Health
Gets the number of events reported.
Chapter Two: Command Set 11
Page 18
Firewall Configuration
These commands configure the network firewall options.
Command Argument Description
add firewall -a/--allow or
-b/--block
-i/--ip <ipaddress>
-m/--mask <netmask>
-p/--proto {icmp}
-x/--xml
add firewall -a/--allow
-b/--block
-i/--ip <ipaddress>
-m/--mask <netmask>
-s/--sport <start-port>
-e/--eport <end-port>
-p/--proto {tcp/udp}
For example: add –a –i 10.10.1.1 –s 1200 –e 5000 –
p tcp firewall
edit firewall -a/--allow or
-b/--block
-r/--rule<ruleno>
-i/--ip <IP address>
-m/--mask <net mask>
-p/--proto { icmp}
-x/--xml
For example: edit -a -i 10.0.0.218 -r 1 -m
255.255.255.255 -p icmp -x firewall
delete firewall -a/--allow or
-b/--block
-r/--num <rule number>(obtained when viewing the
list of firewalls via the list command below)
-x/--xml
For example: delete -b -r 1 -x firewall
edit firewall -a/--allow or
-b/--block
-r/--rule<ruleno>
-i/--ip <IP address>
-m/--mask <net mask>
-s/--sport <start port>
-e/--eport <end port>
-p/--proto {tcp/udp}
-x/--xml
For example: edit -a -i 10.0.0.218 -r 1 -m
255.255.255.255 -s 2000 -e 3000 -p udp -x firewall
list firewall Lists all the blocked and allowed
get firewall -c/--count
-x/--xml
For example: get -c -x firewall
Add allowed or blocked firewall
rule with given parameters for the
ICMP protocol.
Add allowed or blocked firewall
rule with given parameters for TCP
and UDP protocols.
Modifies specified allowed or
blocked firewall rule with given
rule number to the given values for
ICMP.
Deletes allowed or blocked firewall
rule with given rule number.
Modifies specified allowed or
blocked firewall rule with given
rule number to the given values for
TCP or UDP.
firewall rules.
Retrieves the count of allowed or
blocked firewall rules.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
12
Page 19

General Server Configuration
These commands retrieve the general server information, such as build version, build date and so on. It also
allows configuration of a new server name.
Command Argument Description
get serverinfo For example: get serverinfo Displays the server information
such as server name, build version,
build date and so on.
set serverinfo -n/--name <server name>
-x/--xml
For example: set –n newitx serverinfo
set serverinfo -p/--password
–u/--user{root/cli}
-x/--xml
create dump Creates a dump of the running
Configures the name of the server.
The length of the servername
should be less than 16 characters
and the first character must be
alphabetical.
System will prompt you to enter
and confirm the new administrator
(root/cli) password.
Password length should be 32 or
less characters.
system that is useful for debugging.
The file is placed in /usr/AmiNas.
Health Configuration
These commands get the health information
Command Argument Description
get health -c/--enccount
-x/--xml
For example: get –c health
get health -i/--info –n/--enclosure
-x/--xml
For example: get –i –n 0 health
get health -s/--encstatus
–n/--enclosure (optional)
-x/--xml
For example: get –s health
get –s –n 0 health
get health -a/--
-x/--xml
For example: get –x –a health
Gets the number of enclosures
present in the system.
Gets the health information
regarding fan, voltage and
temperatures for the given
enclosure.
Gets the enclosure status for the
given enclosure or for all the
enclosures.
Gets the enclosure status for all the
enclosures.
Chapter Two: Command Set 13
Page 20

iSCSI Configuration
Note: Targetname input: Only the suffix portion of the targetname is required.
For example: “iqn.1991-10.com.ami:itx001a2b3c4d5e2006:test1” . The user needs to input only “test1”.
Command Argument Description
get iscsi -t/--type {tgtstatus}
-n/--targetname <targetsuffix>
For example: get –t tgtstatus –n target1 iscsi
get iscsi -t/--type {tgtname} Gets the iSCSI target name. This
activate iscsi -t/--type {portal}
-p/--ipaddress <Ipaddress of the target machine>
-g/--portaltag <portal tag>
For example: activate –t portal –p 10.15.1.1 –g 3
iscsi
deactivate iscsi -t/--type {portal}
-p/--ipaddress <ipaddress of the target machine>
enable iscsi -t /--type {tgt}
-n/--targetname <target suffix>
disable iscsi -t/--type {tgt}
-n/--targetname <target suffix>
For example: cli disable –t tgt –n newtgt iscsi
start iscsi To start the iSCSI service.
stop iscsi For example: stop iscsi To stop the iSCSI service.
set iscsi -t/--type {params}
-o/--choiceno {0-12}
-l/--value <value>
For example: set –t params –o 1 –l 256 iscsi.
get iscsi -t/--type {lunwritecachemode}
-v/--volumename <volume name>
-c/--containername <containername>
set iscsi -t/ --type {lunwritecachemode}
-v/--volumename <volume name>
Gives the status of the target as
enabled or disabled.
value is not configurable and is
unique to the iTX device.
For example:
iqn.1991-
10.com.ami:itx0030482c8d788a7e
Activates the specified iSCSI
portal. You have to specify a portal
tag at the time of activation of the
portal.
Deactivates the specified iSCSI
portal.
Enables the specified target.
Disables the specified target.
Sets specified iSCSI Login
negotiation parameters.
The possible values are:
1. FirstBurstLength (0-256 KB,
default=256)
2. MaxBurstLength (must be less
than #1, default=256)
3. MaxRecvDataSegmentLength
(0-256KB, default=256)
4. MaxConnections (0-4,
default=2)
5. DefaultTime2Retain (0-3600,
default=20 sec)
6. DefaultTime2Wait (03600,default=2 sec)
7. InitialR2T (0-1, default=No,0)
8. MaxOutStandingR2T (1-8,
default=1 sec)
9. ErrorRecoveryLevel (0-2,
default=2)
10. ImmediateData (0-1,
default=1,yes)
11. DataPduInOrder (0-1,
default=1,yes)
12. DataSeqInOrd (01,default=1,yes)
Gets the Write Cache mode for the
specified disk.
Sets the Write Cache mode for the
specified disk.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
14
Page 21

Command Argument Description
-c/--containername <containername>
-m/--mode {0/1/2}
For example: set –t lunwritecachemode –v v1 –c c1
0 – Write through
1 – Write back
–m 0 iscsi
add iscsi -t/--type {processor}
-n/--targetname <target suffix>
remove iscsi -t/--type {processor}
-n/--targetname <target suffix>
get iscsi -t/--type {statistics}
For example: get –t statistics iscsi
Adds the processor to the specified
target (used for backup).
Removes the processor from the
specified target.
Gets the iSCSI statistics, for
example, No. of iSCSI PDU sent
and received, payload, and
login/session failures.
get iscsi -t/--type {portalstatus}
Gets the iSCSI Portal Status.
-p/--ipaddress <ipaddress>
get iscsi -t/--type {servicestatus} Gets the iSCSI service status.
(Active/Inactive)
add iscsi -t/--type {lun}
-v/--volumename <volume name>
Adds the LUN to the specified
target.
-c/--containername <container name>
-n/--targetname <targetsuffix>
remove iscsi -t/--type {lun}
-v/--volumename <volume name>
Removes the LUN from the
specified target.
-c/--containername <container name>
-n/--targetname <target suffix>
get iscsi -t/--type {sessions}
For example: get –t sessions iscsi
remove iscsi -t/--type {session}
-s/--sessionid <session id>
Gets the current sessions details
including session id.
Terminates the session with the
given ID. To avoid automatic
reconnection by the initiator, you
will need to change the security
settings for that target prior to
termination.
list iscsi -t/--type {tgt} Gets the List of Targets available.
list iscsi -t/--type {lun}
-n/--targetname <target suffix>
get iscsi -t/--type {tgtauthsettings}
-n/--targetname <target suffix>
set iscsi -t/--type {peersecret}
-i/--initiatorname < initiatorname. (Default : none)>
-s/--peersecret
Gets the available LUNs in the
given target.
Gets the Authorization settings for
the target.
Sets the peer secret for the initiator.
You will be prompted to enter this
twice.
For example: set –t peersecret –I iqn.1991-
10.com.microsoft:newbox –s iscsi
set iscsi -t/--type {tgtauthsettings}
-n/--targetname <targetsuffix>
-u/--username <user name ‘none’ for default >
-r/--secretname <user password ‘none’ for default >
-i/--initiatorname <initiator name – ‘none’ for
default>
get iscsi -t/--type {lun}
-n/--targetname <target suffix>
Sets the Authorization settings for
the target. The secret name should
be at least 12 characters in size
This will give exclusive access to
the LUN for the specified user and
initiator for maximum security.
Gives the LUN's Information for
the specified target.
-v/--volumename<volumename>
-c/--containername<containername>
-i/--info
get iscsi -t/--type {tgtoptimizations}
-n/--targetname <target name>
Gives the Target's Optimization
settings (i.e. whether multiple
initiator logins are supported).
set iscsi -t/--type {tgtoptimizations}
-n/--targetname <target suffix>
-p/ --multiplesession {y/n}
-g/--nopinterval < nop ping internal >
Sets the Target's Optimization
settings to allow/disallow multiple
initiators logging in to a target
simultaneously.
Chapter Two: Command Set 15
Page 22

Command Argument Description
For example: set –t tgtoptimizations –n t1 –p y –g
10 iscsi
enable iscsi -t/--type { iSNSservice} Enables the iSNS Service.
disable iscsi -t/--type { iSNSservice} Disables the iSNS Service.
get iscsi -t/--type {iSNS} Gives the iSNS server's
information i.e. iSNS server IP,
server status, command
description, last status message.
set iscsi -t/--type {iSNS}
-e/--entityname <entity name>
-a /--aliasname <alias name>
enumerate iscsi -t/--type {initiator}
-n/--targetname <target suffix, ‘none’ for default>
add iscsi -t/--type {iSNSServer}
-i/--ipaddress <ip address>
remove iscsi -t/--type {iSNSServer}
-p/--ipaddress <ip address>
rescan iscsi -t/--type {iSNS} Rescan for targets and initiators.
update iscsi -t/--type {noderegistrations} Updates the nodes that are
reset iscsi Resets the iSCSI statistics.
get iscsi -t/--type {params}
-o/--choice {0-12}
set iscsi -t/--tgtname This resets the base iSCSI target
Sets the specified iSNS
information.
Gets the iSCSI initiators from the
iSNS server.
Adds a new iSNS server.
Removes an existing iSNS server.
registered with all iSNS servers
this iTX device is registered with.
Gets values of the specified iSCSI
login negotiation parameters.
name of the iTX box
This operation should be done with
utmost precaution and there should
not be any replication pairs in the
box. Logout of all existing iSCSI
sessions before running this
command
License configuration
These commands configure the License.
Command Argument Description
set license -k/--key <key>
-x/--xml
set license -f/--file <filename with path>
-x/--xml
get license -s/--serviceKey
-x/--xml
get license -l/--licenseInfo
-x/--xml
Sets the entered license key to file.
Sets the license according to the
license key given in file path.
Gets the license service key
necessary if you want to upgrade
your iTX license.
Gets the current license
information.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
16
Page 23

Network Controller Configuration
These commands configure the network ports. They can also be used to create virtual bonding network ports
(teams) for high availability and/or load balancing.
Command Argument Description
get network -t/--type {port}
-c/--count
-x/--xml
For example: get –t port –c count network
get network -t/--type {port / alias}
-n/ --name <name of the adapter >
-i/--info
-x/--xml
set network -t/--type {port}
-n/--name <Name of the NIC>
-d/--dhcp
-x/--xml
For example: set –t port –n nic-1 –d network
set network -t/--type {port / alias}
-n/--name <Name of the NIC>
-i/--ip <IP Address>
-m/--mask <net mask>
-g/--gate <Gateway> (optional)
-p/--pridns <Primary DNS> (optional)
-s/--secdns <Secondary DNS>(optional)
-f/--dnssuff <DNS suffix>(optional)
-j/--mtu <size> (optional)
get network -t/--type {adp}
-c/--count
-x/--xml
list network -t/--type {adp} Displays the available network
create network -t/--type {team}
-m/--mode {1/2/3}
-p/--pri <primary NIC>
-s/--sec <secondary NIC>
-x/--xml
Creates a team named Team-1, Team-2, and so on,
depending on available NICs in system
For example: create –t team –p nic-1 –s nic-2 –m 1
network
delete network -t/--type {team}
-n/--name <name of the Team>
-x/--xml
For example: delete –t team –n Team-1 network
get network -t/--type {team}
-i/--info
-n/--name <name of the Team>
-x/--xml
For example: get –t team –i –n Team-1 network
get network -t/--type {team}
-i/--info
-n/--name <name of the Team>
-x/--xml
list network -t/--type {adp/port}
-x/--xml
add network -t/--type alias
-n/--name <alias name>
Gets the number of ports.
Displays the given network port
information.
Configures the given network port
to work with DHCP.
Configures the specified network
port to work with the given
STATIC IP configuration.
Displays the number of network
adapters present.
adapters and their status.
Creates a network team with the
given mode. The supported modes
are:
1 – Balance Round Robin
2 – 802.3 AD (with pre-configured
switch)
3 – Balance TB
Deletes the network team with the
given name.
Displays the number of NICs
present in the given team.
Displays the given network team
information.
Displays various information for
the available network ports
including their status.
Adding an alias adapter for a
specific NIC port
Chapter Two: Command Set 17
Page 24

Command Argument Description
-p/--port <adapter name>
remove network -t/--type alias
-n/--name <alias name>
Removing an alias adapter
NAS Quota Configuration
These commands configure quotas for the NAS volumes of your iTX box.
Command Argument Description
get quota -t/--type {user }
-p/--path <volume path>
-n/--name <user name>
-x/--xml
For example: get –t user –p c0_nas0 –n user1 quota
set quota -t/--type {user }
-p/--path <volume path>
-n/--name <user name>
-q/--quotasize <size>
-f/--filecount <file count>
-x/--xml
For example: set –t user –p c0_nas0 –n user1 –q
4000 –f 400 quota
list quota -p/--path <volume path>
-x/--xml
get quota -p/--path <volume path>
-d/--default
-x/--xml
set quota -p/--path <volume path>
-q/--quotasize (KB) <quota size>
-d/--default [y/n]
-x/--xml
Displays the quota configured for
the given member.
Configures the quota size of given
member.
Size should be entered in KB.
Displays the user quota configured
for a given volume as specified in
path.
Displays the default quota
configured for the volume.
Sets the default quota limit which
should be used for a volume.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
18
Page 25

NAS User / Group Configuration
These commands allow viewing and configuration of the NAS Users and groups accounts.
Note: Known Issue: As iTX software supports enabling of ADS and NIS simultaneously, the user/group
list retrieved will be given for both instead of singly.
Command Argument Description
add ug -t/--type {user}
-u/--username <user name>
-i/--id <userid (optional)>
-p/--passwd <password(optional)>
-f/--fullname <Full name>
-x/--xml
For example: add –t user –u user1 –p password –f
“User 1” ug
add ug -t/--type {group}
-g/--groupname <group name>
-i/--id <group id (optional)>
-x/--xml
delete ug -t/--type {user}
-u/--username <username>
-x/--xml
get ug -t/--type {user/group}
-s/--section {local/ads/nis/all}
-c/--count
-x/--xml
For example: get -t user -i -u test1 ug
list ug -t/--type {user/group}
-s/--section (local/ads/nis/all)
-x/--xml
For example: list -t user -s all ug
get ug -t/--type {group}
-i/--info
-g/--groupname <groupname>
-x/--xml
For example: get –t group –I –g groupA ug
get ug -t/--type {user}
-i/--info
-u/--username <username>
-x/--xml
set ug -t/--type { user}
-u/--username <username>
-p/--passwd <password>
-f/--fullname <fullname>
-x/--xml
For exmaple: set -t user -u test1 -p test1 -f
test1 ug
list ug -t/--type {group}
-g/--groupname <groupname>
-x/--xml
delete ug -t/--type {group}
-g/--groupname <groupname>
-x/--xml
delete ug -t/--type {group}
-g/--groupname <groupname>
-u/--username <username>
-x/--xml
For example: cli delete –t group –g groupA –u
user1 ug
Adds a user. If password is not
entered in command line, it will be
prompted for.
Username is case-sensitive, must
be alphanumeric, and 8 -32
characters .
Adds a group. Group name is casesensitive, must be alphanumeric,
and 8 -32 characters.
Deletes the given user.
Displays the count of users / groups
of specified type.
Displays the specified list of users /
groups and their info.
Displays the group info.
Displays the specified user’s info.
Changes the user info to given
values for password and/or full
name.
Displays the users present in a
particular group.
Deletes the given group.
Deletes the given user from the
specified group.
Chapter Two: Command Set 19
Page 26

set ug -t/--type {group}
-g/--groupname <groupname>
-u/--username <username>
-x/--xml
Adds the given user to the specified
group. Multiple users can be added
using –u/--username switch.
(maximum of 8 users at a time)
Protocol Configuration
These commands configure the various network protocols supported.
Command Argument Description
get protocol -t/--type {cifs/nfs/http/snmp/nis/ads/https/ftp/upnp} Gets the status of cifs, nfs, http,
snmp, nis, or ads protocols.
set protocol -t/--type
{cifs/nfs/apple/http/snmp/nis/ads/https/ftp/upnp}
-d/--disable or
-e/--enable
-x/--xml
For example: set –t cifs –e protocol
get protocol -t /--type {snmp}
-n/--communityname
For example: get –t snmp –n protocol
get protocol -t/--type {cifs}
-w/--winserver
set protocol -t/--type {cifs}
-s/--winsserver <winsserver name>
-m/--mtype {wg/nt/ads}
-w/--workgroup <workgroupname>
-x/--xml
set protocol -t/--type {snmp}
-n/--communityname <communityname>
set protocol -t/--type {nfs}
-i/--ipaddress <ipaddress or “world” >
-d/--disable or
-e/--enable
-x/--xml
For example:
set -t nfs -i 10.0.0.124 -i 10.0.0.123 -e -x protocol
list protocol Lists all the protocols and
get protocol -t/--type {nfs}
-c/--count
Enables or Disables the specified
protocol.
Gets the community name for
snmp.
Gets the Wins server address.
Sets the Wins server address.
Sets the snmp community name
By default, the public community
name is supported.
Sets the nfs clients.
whether they are enabled or
disabled.
Gets the number of NFS clients
that have access to NAS shares.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
20
Page 27

RAID & Disk Management Commands
These commands allow management of disks and RAID creation.
For Hardware RAID please enter the Slotindex (For example: 1, 2,3, and so on) instead of diskname (For
example: /dev/sda, /dev/sdb) in the option for -d / --diskname <DiskInfo_OSName or slotindex>
Command Argument Description
get raid -t/--type {pd/ld/controller}
-c/--count
get raid -t/--type {controller}
-a/--alarm
-n <controllerno>
list raid -t/--type {pd/ld/controller}
list raid -t/--type {pd/enclosure}
-n <controllerno>
list raid -t/--type {spare}
get raid -t/--type {pd}
-i/--info
-n/--controllerno <controller number>
-d / --diskname <Diskname or slotindex>
get raid -t/--type {pd}
-d/--diskname <diskname or slotindex>
-n <ControllerNo>
-m/--cachemode
For example: get –t pd –d 1 –n 0 –m raid
get raid -t/--type {ld}
-l/--ldname < Logical_Osname>
-m/ --cachemode
rebuild raid -d/--diskname <diskname or slotindex>
-l/–ldname <ldname>
create raid -t/--type {ld}
-s/ --disksize <disksize optional in GB>
-p/--stripesize <stripe size 64 KB>
-d / --diskname <diskname or slotindex>
-a/--sparediskname <sparediskname> (optional)
-e/--distspare <distributedspare> (optional)
-r / --raidlevel <raid
level(0/1/3/5/6/10/1N/10N/50/60) >
-m/--cachemode <cachemode>
-b/--subdisk <subdiskcount>
-n/--controllerno <controllerno>
For example:
cli create -t ld -p 64 -d 1:5 -d 1:6 -r 0 -m
WriteThrough:ReadAhead:Cached -n 0 raid
delete raid -t/--type {ld}
-l / --ldname <drivename>
For example: delete –t ld –l /dev/md1 raid (1U)
For example: delete –t ld –l /dev/sdb raid (3U)
Displays the number of disks,
logical drives and controllers
respectively.
Displays the alarm mode and
battery status of controllers
respectively.
Displays the list of logical drives
and controllers respectively.
Displays the list of physical drives
and enclosures for controller
respectively.
Displays the list of spare disks.
Displays the information about
specified disk.
Gets the physical disk cache mode.
Gets the logical drive cache setting.
Rebuilds a logical drive with the
specified disk drive.
Creates a logical drive.
-s/ --disksize – only supported for
3U
For LSI RAID Controller - Cache
Modes Format writecache:readcache:cachemode
writecache values - WriteThrough
/ WriteBack / ForceWriteBack
readcache values ReadAheadNone / ReadAhead /
ReadAdaptive
cachemode values - Direct /
Cached
-p/ --stripesize – only 64 kb
supported for 3U
Minimum LD size: 10 GB
Deletes specified logical drive.
Chapter Two: Command Set 21
Page 28

Command Argument Description
expand raid -t/--type {ld}
-l/ -- ldname <ldname >
-d/ --diskname <diskname or slotindex(optional)>
Expands the logical drive to
specified disksize using specified
disk.
-s/--disksize <disksize in GB>
-b/--subdisk <subdiskcount (Required only for
RAID10N and RAID50)>
-e/--distspare
-n/--controllerno <controllerno (Required only for
LSI RAID controller)
For example: expand -t ld -l /dev/sdb -d 2 -s 20 raid
transform raid -t/--type {ld}
Transforms a logical drive.
-l / --ldname <ldname>
-d / --diskname <diskname or slotindex >
-r/ --raidlevel
<raid level (0/1/3/5/6/10/1N/10N/50/60)>
-s/--size <size (optional)> (enter ss for same size)
-b/--subdisk <subdiskcount (Required only for
RAID10N and RAID50)>
-e/--distspare
-n/--controllerno <controllerno (Required only for
LSI RAID controller)
For example: transform -t ld -l /dev/md0 -r 5 -d
/dev/sda -d /dev/sdb raid
blink raid -t/--type {ld/pd}
-d / --diskname<diskname or slotindex>
Blinks a disk (not supported on a
1U yet).
-n/--controllerno <controllerno>
For example: blink –t pd –l /dev/sda –n 0 raid
blink raid -t/--type {ld/pd}
-l / --ldname <ldname>
set raid -t/--type {pd}
-d / --diskname<diskname or slotindex>
-m / --cachemode
< diskcache mode>
-n/--controllerno <controllerno>
Cache Modes - pd
0 - None 1 - Read 2 - Read-Write
3 - Read-Ahead 4 - Read-Ahead-Write
For example: set –t pd –d 2 –m 1 –n 0 raid
Blinks a logical drive (not
supported on a 1U yet).
Sets the cache mode for disk (HW
RAID only).
For LSI RAID Controller - Cache
Modes Format writecache:readcache:cachemode
writecache values - WriteThrough
/ WriteBack / ForceWriteBack
readcache values ReadAheadNone / ReadAhead /
ReadAdaptive
cachemode values - Direct /
Cached
set raid -t/--type {pd}
-d / --diskname<diskname or slotindex>
-g/--makegood
-n/--controllerno <controllerno>
-x/--xml
For example: set -t pd -d 1:2 -g -n 0 raid
set raid -t/--type {controller}
Sets the alarm mode for controller
-n/--controllerno<controller no>
-a / --alarmmode <alarm mode>
Alarm Modes - controller
0 - NP 1 - Enable 2 - Disable
3 - Mute 4 - UnMute
set raid -t/--type {ld} Set the cache mode for LD
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
22
Page 29

Command Argument Description
-l / --ldname <ldname>
-m/--cachemode <cache mode>
Cache Modes - ld
0 - None 1 - Read
2 - Write 3 - Read-Write
rescan raid -n/--controllerno <controller number>
remove raid -t/--type {spare}
-d / --diskname <diskname or slotindex>
Initiates rescanning of the storage
bus connected to the controller.
Removes a drive assigned as a
spare disk or dedicated disk.
-l/ --ldname <ldname> (for dedicated spare)
-n/--controllerno <controllerno>
For example: remove -t spare -d 3 -n 0 raid
remove -t spare -l /dev/md0 -d /dev/sdb raid
add raid -t/--type {spare}
-d / --diskname or slotindex or
Adds the given drive as a global or
dedicated hot spare.
enclosurenumber:slotindexl/--ldname <ldname>(for dedicated spare)
-n/--controllerno <controllerno>
For example: add -t spare -d 1:4 -n 0 raid
upgrade raid -t/--type {controller}
-n/--controllerno <controller number>
Upgrades the firmware for
controller.
-o /--code <code>
-l/ --length <length>
upgrade raid -t/--type {pd}
-d / --diskname <diskname or slotindex>
Upgrades the firmware for a
physical disk.
-n/--controllerno <controller number>
-o /--code <code>
-l/ --length <length>
Chapter Two: Command Set 23
Page 30

Share, Directory & ACL Configuration
These commands work on NAS shares and directory.
Command Argument Description
create dir -p/--path <directory path>
-x/--xml
For example: create –p c0_nas0/new dir
list dir -p/--path <directory path>
-x/--xml
delete dir -p/--path <directory path>
-f/--force (optional)
-x/--xml
list share Displays all shares and details of
get share -t/--type {share}
-c/--count
-x/--xml
get share -t/--type {share}
-i/--info
-p/--path < path of the share >
-x/--xml
get share -t/--type {acl}
-p/--path < path of the share >
-x/--xml
add share -n/--name <name of the share >
-p/--path <path to be added>
- s/--prototype {cifs/nfs/upnp/apple/http/ftp}
-x/--xml
For example: add –n share0 –p c0_nas0/new –s cifs
–s ftp share
delete share -t/--type {share}
-n/--name <name of the share >
-x/--xml
For example: delete -t share –n share1 share
delete share -t/--type {acl}
-p <directory path>
-u/--username <username> or -g/--groupname
<groupname>
-x/--xml
For example: delete -t acl -p c0_v0/test1 -u test1
share
set share -t/--type {acl}
-x/--xml
-p/--path <directory path>
-m/--mode
<USERNAME:MODE{user/group}:PERMISSION
S:INHERITANCE:ALLOW:LEVEL>
-e/--enable or -d/--disable
-v/--voltype (0 for NT 1 for posix)
-i/--inherited (0 to not inherit 1 otherwise)share
For example:
m user1:user:agf:3:1:0 -m user2:user:agh:5:0:0 -m
group1:group:gd:3:1:1 -e -v 1 -i 0 share
set -t acl -p Cont0_Volume0/dir1 -
Creates a subdirectory with the
given complete path.
Displays all directories in the
volume.
Deletes a subdirectory with the
given complete path. The complete
path should also include the
volume path exported by the
system. The subdirectory should be
empty before deletion.
Note: the parent directory cannot
be deleted For example: c0_nas0
each.
Gets the number of shares.
Gets the share information
according to the path given.
Gets the acl permissions of a share.
Adds specified share to the system.
Note: Please make sure a directory
with the same path is made before
creating a share
Deletes a share from the system.
Deletes a acl share from the
system.
Sets the acl permission of the share
(maximum of 4 ACL permissions
can be entered at a time. And 237
acl permissions maximum per
share).
The -e/-d option is to enable or
disable ACL recursively for the
root folder and sub folders
ALLOW FOR NT
0 - Allow ACE 1 - Deny ACE
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
24
Page 31

set share -t/--type {share}
-n/--name <name of the share>
-p/--path <path of the share>
-s/--prototype <cifs/nfs/upnp/apple/http/ftp>
-x/--xml
For example: set -t share -n test1 -p
Container0_Volume0/dir1 -s cifs -s http -s upnp
share
LEVEL FOR NT
0 - Apply to all levels 1 – Apply
to first level
PERMISSIONS FOR POSIX
0 - Read Write 1 - Read Only
2 - Deny
PERMISSIONS FOR NT : The 14
bits in following order
A - Traverse Folder / Execute file
B - List Folder / Read Data
C - Read Attributes
D - Read Extended Attributes
E - Create files/ Write Data
F - Create folders / Append Data
G - Write Attributes
H - Write Extended Attributes
I - Delete Subfolders and files
J - Delete
K - Read Permissions
L - Change Permissions
m - Take Ownership
INHERITANCE FOR NT
0 - No inheritance
1 - this folder sub folders and files
2 - this folder and sub folders
3 - this folder and files
4 - subfolders and files only
5 - subfolders only
6 - files only
Sets a share properties.
Chapter Two: Command Set 25
Page 32

System Control Configuration
These commands configure the System controls.
Command Argument Description
shutdown system For example: shutdown system Shuts the system down.
get system
set system -f/--fansensors <on/off>
reboot system Reboots the system.
For example:
-t/--tempsensors <on/off>
-x/--xml
cli get -x system
Gets the auto shutdown
information.
Sets the fan sensors or temperature
sensors on or off for autoshutdown
(only temperature supported at this
release).
Volume and Snapshot Commands
These commands manage the way Containers, Volumes and Snapshots are created, or expanded. While some
of these commands are specific to either NAS or iSCSI volumes, most will work in both types of volumes.
Command Argument Description
create volume -t/--type {container}
-c/--containername<containername>
-k/--chunksize< {64} in KB>
-l/--ldname<logical device name> .....
For example: create –t container –c c0 –k 64 –l
/dev/md2 volume (1U)
For example: create –t container –c c0 –k 64 –l
/dev/sdb volume (3U)
create volume -t/--type { volume }
-c/--containername <containername>
-v/--volumename <volumename>
-z/--volumesize <volumesize in GB>
-k/-- <chunksize {64 or 8} in KB }><volumesize>
-p/--provisiontype< provisiontype {0/1/2} >
-e/--volumetype <volumetype
{0} >
-f/--voldialect <volumedialect
{0/1} >
For example:
AutoNas -k 64 -z 20 -e 0 -p 2 -f 1 volume
create volume -t/--type {snap}
-c/--containername <containername>
-v/--volumename <volumename>
-s/--snapname <snapname>
For example: create –t snap –c c0 –v v0 –s snap00
volume
create volume -t/--type {snap}
-c/--containername <containername>
-v/--volumename <volumename>
-s/--snapname <snapname>
-w/--writablesnapname<writablesnapname >
For example: create –t snap –c c0 –v v0 –s snap00
–w wsnap00 volume
create volume -t/--type { snap }
-c/--containername <containername>
-v/--volumename <volumename>
-s/--snapname <snapname>
-R/--remotesnap
create -t volume -c Cont0 -v
Creates a container.
Note:
The chunk size should be 64K
The device name should be in the
form /dev/mdx or /dev/sdx where x
can be 0,1,2,3…
Creates a Volume.
Note:
1)volumetype ([0]-ROW
2) voldialect ([[0]-ISCSI [1]-NAS)
3)provisiontype ([0]-Thin [1]-
Exact
2 – Auto(Nas Only)
As a best practice measure, it is
recommended that 20% of
container capacity be reserved (left
free) for snapshots.
Creates a read-only Snapshot.
Note: A total of 254 read-only
Snapshot can be created per
volume. And the total number of
snapshots (read-only + writable) is
992 per iTX device.
Creates a writable Snapshot over a
read-only snapshot.
Note: A total of 254 writable
Snapshot can be created per
volume. But the total number of
snapshots (read-only + writable)
should be 992 per iTX device.
Creates a snapshot on the local
target as well as the remote target if
the volume is replication enabled.
If only –R is given, only the remote
snapshot is created. If only –L is
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
26
Page 33

Command Argument Description
-L/--localsnap used, then only the local snapshot
will be created.
By default, without the switches –L
and –R, it will create the local
snapshot only.
delete volume -t/--type {container}
-c/--containername<containername>
-f/--force (optional)
Deletes the container.
-r/ option deletes all volumes
within the container recursively.
-r/--recursive (optional)
delete volume -t/--type {volume}
Deletes the specified Volume.
-c/ --containername <containername>
-v/ --volumename <volumename>
-f/--force (optional)
delete volume -t/--type {snap}
Deletes the specified Snapshot.
-c/ --containername <containername>
-v/ --volumename <volumename>
-s/ --snapname <snapname>
-f/--force (optional)
delete volume -t/--type {snap}
-c/ --containername <containername>
-v/ --volumename <volumename>
-s/ --snapname <snapname>
-L/--localsnap
-R/--remotesnap
-f/--force (optional)
For example: delete –t snap –c c0 –v v0 –s snap00
–L –R –f volume
delete volume -t/--type {volume}
-c/ --containername <containername>
Deletes the Snapshot on the local
target as well as the remote target if
the volume is replication enabled.
If –R is given, only the remote
snapshot is deleted. If –L is used,
only the local snapshot will be
deleted. By default, without the
switches –L and –R, it will delete
the local snapshot.
Deletes all the volumes within that
container.
-a/--all
-f/--force (optional)
delete volume -t/--type {snap}
-c/ --containername <containername>
Deletes all Snapshots for that
volume.
-v/ --volumename <volumename>
-a/--all
-f/--force (optional)
expand volume -t/--type {container}
-c/--containername <containername>
-l/--ldname<logical device name>
For example: expand –t container –c c0 –l /dev/sdc
Expands Container by adding the
specified LD to it.
Logical Device name eg;/dev/md0
Use:–l option
volume
expand volume -t/--type {volume}
Expands Volume.
-c/--containername <containername>
-v/--volumename <volumename>
-z/-- capacity new volume size (in GB)
For example: expand –t volume –c c0 –v v0 –z 300
volume
list volume -t/--type {container/volume/snap }
For example: list –t snap volume
List all the
Containers, Volumes, or Snapshots
in system.
list volume -t/--type {volume}
-c/--containername <containername>
list volume -t/--type { snap}
-c/--containername <containername>
-v/--volumename <volumename>
get volume -t/--type {container }
-i/ --info
List the details for all the
Volumes in specified container.
List the details about
SnapShots in specified volume and
container.
Gets the information about the
specified Container.
-c /--containername <containername>
get volume -t/--type {volume}
-i/--info
Gets the information about the
specified Volume.
Chapter Two: Command Set 27
Page 34

Command Argument Description
-c/ --containername <containername>
-v/--volumename <volumename>
get volume -t/--type {snap}
-c/--containername <containername>
-v/--volumename <volumename>
-u/--schedule
get volume -t/--type { snap}
-i/--info
-c/--containername <containername>
-v/--volumename <volumename>
-s/--snapname <snapname>
For example: get –t snap –i –c c0 –v v0 –s snap00
volume
get volume -t/--type {container}
-n /-- count
activate volume -t/--snap {snap}
-c/--containername <containername>
-v/--volumename <volumename>
-s/--snapname <snapname>
-w/--writeable(optional)
For example: activate -t snap -c Cont0 -v Volume0
-s Volume0WriteableSnap0 -w volume
deactivate volume -t/--snap {snap}
-c/--containername<containername>
-v/--volumename <volumename>
-s/ --snapname <snapname>
rollback volume -t/--snap {snap}
-c/--containername<containername>
-v/--volumename <volumename>
-s/--snapname <snapname>
freeze volume -t/--type {container/volume/snap} Freezes the UVM
set volume -t/--type {snap}
-u/--schedule
-c/--containername<containername>
-v/--volumename <volumename>
-s/-schedulesnap <scheduleduration:maxsnapshots>
-d/--description <description>
-n/--backtargetname <backuptargetname >
-p/--scheduleType 0-Windows,1-Local
[default:Windows] volume
For example: set -t snap -c Cont0 -v
Volume0ISCSILUN0 -s 5:10 -s 60:20 -d testing -n
backuptest -p 0 volume
Gets the snapshot schedule settings
for the specified volume.
Gets the information about the
specified Snapshot.
Gets the number of containers in
system.
Activates writeable Snapshot.
Deactivates the Snapshot.
Rolls back the Snapshot. Requires
disconnecting and stopping of all
I/Os.
Container/volume/snap.
Note: Yet to be implemented.
Set the Snapshot Schedule.
Note: maximum number of read
only snapshots (read-only +
writable) is 254 per volume for a
total of 992 per system.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
28
Page 35

UPS Configuration
These commands configure the UPS for power management.
Command Argument Description
get UPS -i/--info
-x/--xml
get UPS -i/--info
-m/--monitor
-x/--xml
set UPS -d/--disable
-x/--xml
set UPS -e/--enable or
-d/--disable
-b/--battery <min battery value>
-t/--timeout <mins>
-m/--mode {1}
-x/--xml
For example: set –e –b 10 –t 3 –m 1 ups
set UPS -e/--enable or
d/--disable
-b/--battery <min battery value>
-t/--timeout <mins>
-m/--mode {2}
-i/--masterip <{HostName/Master Ip>
-x/--xml
For example: set -e -b 35 -t 300 -m 2 -i 10.0.0.218
ups
config UPS -i/--info
-x/--xml
config UPS -l/--list
-x/--xml
config UPS -d/--driver <num>
-p/--port <value>
-x/--xml
For example: config –d 2 –p 1 ups
Displays the existing UPS
configuration.
Display the monitoring
configuration for the configured
UPS devices.
Disables automatic shutdown.
Sets the UPS configuration to
given values. The enable mode is
to denote the shutdown option.
Timeout should be given in
minutes. Battery is the minimum
battery value below which the
shutdown is triggered Mode checks
whether it set to master or slave.
Note:
Minimum Battery value should be
between 0 and 100 %
Timeout value should be between
0 and 1000 minutes
Sets the UPS configuration to
given values. The battery value
indicates the minimum battery
value at which the alert has to be
generated. Timeout should be
given in minutes. Mode is set to
slave and the masterip is IP
Address of the master.
Note:
Minimum Battery value should be
between 0 and 100
Timeout value should be between
0 and 1000
Displays currently configured
driver for UPS monitoring.
Displays list of available drivers.
Sets driver to use with UPS
monitoring.
Driver number is from list obtained
from –list command.
Port value:
1 – COM1
2 – COM2
u - USB
Chapter Two: Command Set 29
Page 36

Synchronous replication
These commands configure synchronous replication and High Availability using Windows DSM
(iTX 2.7v 2.x).
Command Argument Description
create syncreplica –l/--local < cont_vol_name>
-r/--remote < cont_vol_name>
-p/--priority <resync priority>
-i/--localhost <primary's IP address>
-m/--remotehost <rem host name>
-d/--mode [sync | ha]
Example: replication in local volumes
create -l c0_v0 -r c1_v1 -p 50 -i 172.16.70.70 -d
sync -m local syncreplica
Example: HA in remote volumes
create -l c0_v0 -r c1_v1 -p 50 -i 172.16.70.70 -m
172.16.70.102 –d ha syncreplica
update syncreplica –l/--local < cont_vol_name>
-p/--priority <resync priority>
-m/--remotehost <rem host name>
-x/--xmlflag <xml flag>
For example: update -l c0_v0 -p 50 -m
172.16.70.102 -x syncreplica
get syncreplica -l/--local <local-primary cont_vol_name>
For example: get –l c0_v0 syncreplica
list syncreplica -c/--container <container name>
For example: list –c c0 syncreplica
delete syncreplica -l/--local < cont_vol_name >
-f/--force (optional)
split syncreplica -l/--local <local-primary cont_vol_name> Temporarily stops replication of
join syncreplica -l/--local <cont_vol_name> Manually joins or resync the
perform syncreplica -t/--type {failover}
-l/--local <cont_vol_name>
perform syncreplica -t/--type {failback}
-l/--local <cont_vol_name>
For example: perform –t failback –l c0_v0
syncreplica
Creates a replication pair. Both the
primary and secondary volumes
should be present before this
operation.
For local volume copy, please enter
remote host as “local”. All other
parameters remain same. Default
resync priority is zero.
Specify sync for –d/--mode option
to create a synchronous replication
pair; specify ha for –d/--mode
option to create an high-availability
pair.
NOTE: management target name
for SR is the name of the virtual
target, as opposed to mtarget in
earlier versions (2.5/2.6).
Updates the given parameters of
the volpair in DDF and in module.
Displays the replication details as
available from DDF as well as
runtime.
Lists available replication pairs in
the given container.
Deletes the given synchronous
replication pair. Note : Use --force
to clean up non-operational pair
locally.
the replication pair. But at a later
time, the replication can be joined
to replicate from the place where it
stopped.
replication on the given
consistency group that was split
earlier. Also, this command should
be used to initiate a failback
resync.
Initiates failover on the given
consistency group. This command
has to be given in the secondary
target. All further I/Os will be
fielded by the secondary from now
on.
This will reinstate the initial
primary to start fielding I/Os after a
successful failback. Resync has to
be completed before activating the
failback.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
30
Page 37

High Availability (iTX27 v3.x and up )
These commands configure High Availability which is OS Agnostic
Command Argument Description
syncparams
syncreplica
managerg syncreplica -t/--type <action{create/delete/get/editalias/
create syncreplica –l/--local < cont_vol_name>
update syncreplica –l/--local < cont_vol_name>
-r/--remoteip < remote ipaddress >
-x/--xmlflag
For example:
syncparams -r 172.16.70.148 syncreplica
removealias/addalias/changeowner/forcetakeover}>
-n/--rgname <resource group name>
-a/--alias <Alias>
-r/--remoteip <remote ipaddress>
-v/--vipaddress <Virtual iapddress>
-l/--local <localipaddress>
-f/--force
-x/--xmlflag
For example:
managerg -t create -n rg0 -a Alias-1 -a Alias-2 -r
172.16.70.146 -l 172.16.70.176 syncreplica
managerg -t get syncreplica
managerg -t delete -n rg0 syncreplica
managerg -t editalias -n rg0 -v 172.16.70.10 -a
Alias-1 syncreplica
managerg -t addalias -n rg0 -a Alias-2 syncreplica
managerg -t removealias -n rg0 -a Alias-2
syncreplica
managerg -t changeowner -n rg0 syncreplica
managerg -t forcetakeover -n rg0 syncreplica
-r/--remote < cont_vol_name>
-p/--priority <resync priority>
-i/--localhost <primary's IP address>
-m/--remotehost <rem host name>
-d/--mode [hanodsm]
-g/--rgname <resource group name>
Example: HA NO DSM replication in remote
volumes
create -l c0_v0 -r c1_v1 -p 50 -i 172.16.70.70 -d
hanodsm -m 172.16.70.1
02 -t iqn.1991-
10.com.ami:itx00c09f2164459104:virtual -g rg0
syncreplica
-p/--priority <resync priority>
-m/--remotehost <rem host name>
Syncparams is used to sync the
iscsi base target names/date and
time between local and remote
machines before creating an HA
pair.
This command has to be executed
in the Primary machine before
creating the first RG between two
iTX machine.
Managerg command is used to
manage and configure Resource
Group. Action denotes the
operation to be perfomed on the
RG
This command is also used to
add/remove/edit virtual IP
configured for a specific RG.
Note: Atleast one VIP should be
present for an RG.
This command is also used the
change the original ownership of
an RG.
--forcetakeover option can be used
to takeover the RG forcefully if the
RG is in an inconsistent state but
this may result in data corruption.
--force option is used to delete an
non operational RG forcefully if
remote is dead.
Creates a replication pair. Both the
primary and secondary volumes
should be present before this
operation.
Default resync priority is 25.
Specify sync for –d/--mode option
to create a synchronous replication
pair; specify hanodsm for –d/--
mode option to create an high-
availability pair.
Updates the given parameters of
the volpair in DDF and in module.
Chapter Two: Command Set 31
Page 38

Command Argument Description
-g/--rgname <rgname>
-x/--xmlflag <xml flag>
For example:
update -l c0_v0 -p 50 -m 172.16.70.102 -x
syncreplica
Update command is used to move a
replication volume pair from
Resource group to another.
-g stands for the destination rg
name.
update -l c0_v0 -g rg0 syncreplica
get syncreplica -l/--local <local-primary cont_vol_name>
-r/--rginfo
-o/--owner
For example:
get –l c0_v0 syncreplica
get -r syncreplica
get -o syncreplica
list syncreplica -c/--container <container name>
-r/--group
For example:
list –c c0 syncreplica
list -r syncreplica
delete syncreplica -l/--local < cont_vol_name >
-f/--force (optional)
For Example:
delete -l c0_v0 syncreplica
delete -l c0_v0 -f syncreplica
delete -l c0_v0 -l c1_v2 -l c1_v2 -f syncreplica
split syncreplica -l/--local <local-primary cont_vol_name>
-g/--rgname <resource group name>
For Example:
split -l c0_v0 syncreplica
split -g rg0 syncreplica
join syncreplica -l/--local <cont_vol_name>
-g/--rgname <resource group name>
For Example:
join -l c0_v0 syncreplica
join -g rg0 syncreplica
convert syncreplica convert -c/--container <container_name> -v/--
volume <volume_name> -g/--rg <resource_group>
For Example:
convert -c c0 -v v0 -g rg0 syncreplica
Displays information about
Resource Group.
This command can be used both in
Primary & Secondary storage
systems.
It Displays the replication details as
available from DDF as well as
runtime.
Lists available replication pairs in
the given container.
It can be used to display the details
about the resource group
configured in the system and the
corresponding replication pairs.
Deletes the given synchronous
replication pair. Note: Use --force
to clean up non-operational pair
locally.
Multiple pairs (up to 64) can be
deleted at the same time by using -l
repeatedly.
Temporarily stops replication of
the replication pair. But at a later
time, the replication can be joined
to replicate from the place where it
stopped.
This command can used to stop all
the replication pairs part of the RG
Manually joins or resync the
replication on the given
consistency group that was split
earlier. Also, this command should
be used to initiate a failback
resync.
This can be used to rejoin all the
volume replication pairs part of the
RG by specigying the RG name.
This command is used to convert a
synchronous replication pair to
operate in a High Availability
mode.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
32
Page 39

Asynchronous Replication
These commands configure asynchronous replication.
Command Argument Description
create asyncreplica -t/--type <sar/jar/hasar>
-n/--name <snap assisted replication name>
-f/--volumedialect
-a/--primarycontainer <primary contName>
-l/--primaryvolume <primary volName>
-i/--primaryip <primary host IP address>
-s/--secondarycontainer <secondary contName>
-r/--secondaryvolume <secondary volName>
-m/--secondaryip <secondary host IP>
-k/--hasecondaryip <HA secondary host IP> (Only
for HA-DR)
-z/--secsnapcount <secondary snap count>
-c/--compression <zlib compression
level>(optional)
-e/--encryption (optional)
-b/--dedup (optional)
-w/--wds <bandwidth in mbps> (optional)
-u/--utilization <bandwidth utilization in
percentage>
Example: Single volume in CG
create -t sar -n name -f 1 -a c0 -l v0 -i
172.16.70.70 -s c1 -r v1 -m 172.16.70.153 -c 6 -z
10 -e asyncreplica
Example: Multiple volumes in CG
create –t sar –n name -f 0 –a c0 -l v0 -l v1 -l v2
-i 172.16.70.70 –s c1 -r v0 –r v1 -r v2 -m
172.16.70.153 -153 -c 6 -z 10 -e asyncreplica
delete asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-f/--force(optional)
Example:
delete -n name -c c0 -d 1 asyncreplica
delete -n name -c c0 –d 1 -f asyncreplica
get asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name> (optional)
-s/--compressionstats (optional)
Example:
get -n name -c c0 -d 1 asyncreplica
list asyncreplica -c/--containername <container name>
(optional only if wds enabled)
Creates a asynchronous replication
pair. Both the primary and
secondary volumes should be
present before this operation.
Note:
1) Volume Dialect
[0] - ISCSI
[1] – NAS
2) Compression Type
[0] – No compression
[1 - 9] – levels
3)
secsnapcount can take values
between 1 to 1022
4)
WDS mode is used only in Snap
Assisted Replication and HA-DR
5) This command can be issued
only in the storage system that will
be the Primary.
6) HA-DR (hasar) option can be
used only after HA is established
across all volumes of the DAR
(DR) group.
7) The HA secondary host IP is the
WAN IP of the HA pair which can
be reached from the SAR (DR)
secondary system.
Deletes the asynchronous
replication pair
-f/--force flag is optional and is
used where asynchronous
replication has to be deleted
forcefully
This command can be issued only
in the storage system that will be
the Primary.
Displays the asynchronous
replication details.
This command can be issued on
both Primary and Secondary
storage systems.
Lists available asynchronous
replication pairs in the given
Chapter Two: Command Set 33
Page 40

Command Argument Description
Example:
list -c c0 asyncreplica
container.
This command can be issued on
both Primary and Secondary
storage systems.
list asyncreplica -c/--containername <container name>
-n/--name <asynchronous replication name>
Example:
list -n name -c c0 asyncreplica
pause asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
Example:
pause -n name -c c0 –d 1 asyncreplica
Lists all the common snapshots (of
all volumes) in the asynchronous
replication pairs in the given
container.
This command can be issued on
both Primary and Secondary
storage systems.
Pauses the Asynchronous
replication until it is resumed by
resume cli.
This command can be issued in a
primary.
This command can be issued only
when the Asynchronous replication
has one of the following status
1. Paused
2. Idle
3. Active
4. Undefined
For all other status, this command
would return error.
resume asyncreplica
-n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
Example:
resume -n name -c c0 –d 1 asyncreplica
Resumes the Asynchronous
replication that was paused before.
This command can be issued in a
primary.
This command can be issued only
when the Asynchronous replication
has one of the following status
1. Paused
For all other status, this command
would return error.
failover asyncreplica
-n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
Example:
Fails over the Asynchronous
replication to the secondary.
This command can be issued only
in the secondary.
failover -n name -c c0 –d 1 asyncreplica
failbackjoin
asyncreplica
-n/--name <asynchronous name>
-c/--containername <container name>
-d/--index <system assigned name>
Example:
failbackjoin -n name -c c0 –d 1 asyncreplica
Prepares the original primary of the
Asynchronous replication for
failback.
This command can be issued only
in the primary.
failback asyncreplica -n/--name <asynchronous replication name> Fails back the Asynchronous
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
34
Page 41

Command Argument Description
-c/--containername <container name>
-d/--index <system assigned name>
Example:
failback -n name -c c0 –d 1 asyncreplica
replication to the original primary.
This command can be issued only
in the original primary acting as a
secondary.
rollbackjoin
asyncreplica
-n/--name <asynchronous replication name>
-c/--containername <container name>
-s/--snapgrouptnum <t number>
-d/--index <system assigned name>
Example:
rollback -n name -c c0 –s 30 –d 1 asyncreplica
If the status is
FAILED_DUE_TO_ROLLBACK
after a Rollback on Primary, the
replication will continue after
issuing this command on the
primary to make the secondary
ready for resuming replication.
This command can be issued in a
primary.
rollback asyncreplica
-n/--name <asynchronous replication name>
-c/--containername <container name>
-s/--snapgrouptnum <t number>
-d/--index <system assigned name>
Example:
Rolls back all the volumes of the
Asynchronous replication to a
particular set of snapshots.
This command can be issued in a
primary and/or secondary.
rollback -n name -c c0 –s 30 –d 1 asyncreplica
update asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-i/--primaryip <primary host IP address>
-m/--secondaryip <secondary host IP>
-k/--hasecondaryip <HA secondary host IP>
-t/--primarymgmttgt <primary management target
name>
-z/--secsnapcount <secondary snap count>
-u/--secondarymgmttgt <secondary management
target name>
-g/--wds <wds {0/1}>
-w/--bwutilization <bandwidth utilization in
percentage>
Update ‘priority’, ‘compression’,
‘primaryip, ‘secondaryip’,
‘hasecondaryip’
“primarymgmttgt”,
“secondarymgmttgt” fields.
Note:
1) Compression type
[0] - NO compression
[1-9] – Compression Levels
This command can be issued in a
primary.
-b/--bandwidth <bandwidth in mbps>
-f/--dedupe <deduplication {0/1}>
-y/--encryption <encryption {0/1}>
-o/--compression <compression level {0..9}>
Example:
update -n myname -d 1 -c Cont0 -o 2 –I
172.16.70.89 -m 172.16.70.90
-u iqn.1991-
10.com.ami:itx00c09f2164459105:mtarget
-t iqn.1991-
10.com.ami:itx00c09f2164459108:mtarget
-z 10 asyncreplica
update asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-f/--dedupe <deduplication {0/1}>
Update ‘deduplication’ field alone.
This command can be issued in a
primary.
Example:
update -n myname -d 1 -c Cont0 -f 1 asyncreplica
Chapter Two: Command Set 35
Page 42

Command Argument Description
update asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-z/--secsnapcount <secondary snap count>
Example:
update -n myname -d 1 -c Cont0 -z 200
asyncreplica
Update ‘secondary snap count’
field alone.
secsnapcount takes value between
1-1022
This command can be issued in a
primary.
update asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-w/--bwutilization <bandwidth utilization in
percentage>
update asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-b/--bandwidth <bandwidth in mbps>
update asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-o/--compression {0-9}
Update ‘bandwidth utilization’
field alone.
This command can be issued in a
primary.
Update ‘bandwidth’ field alone.
This command can be issued in a
primary.
Update ‘compression’ field alone.
Note:
1) Compression type
[0] - NO compression
[1-9] – Compression Levels
This command can be issued in a
primary.
update asyncreplica -n/--name <asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-i/--primaryip <primary host IP address>
update asyncreplica -n/--name < asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-m/--secondaryip <secondary host IP>
update asyncreplica -n/--name < asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-k/--hasecondaryip <secondary host IP>
update asyncreplica -n/--name < asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-t/--primarymgmttgt <primary management target
name>
update asyncreplica -n/--name < asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-u/--secondarymgmttgt <secondary management
target name>
Update ‘primaryip’ field alone.
This command can be issued in a
primary.
Update ‘secondaryip’ field alone.
This command can be issued in a
primary.
Update ‘hasecondaryip’ field alone.
This command can be issued in a
primary of a HA-DR setup.
Update ‘primarymgmttgt’ field
alone.
This command can be issued in a
primary.
Update ‘secondarymgmttgt’ field
alone.
This command can be issued in a
primary.
add asyncreplica -n/--name < asynchronous replication name>
-c/--containername <container name>
Add periodicity information for a
particular Asynchronous
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
36
Page 43
Command Argument Description
-s/-- schedule>
-d/--index <system assigned name>
Example:
add -n myname -c Cont0 -s "0-24 0-7" -d 1
asyncreplica
add -n myname -c Cont0 -s "* 0-7" -d 1
asyncreplica
add -n myname -c Cont0 -s "0-24 *" -d 1
asyncreplica
add -n myname -c Cont0 -s "* *" -d 1 asyncreplica
Replication.
Note :
1) The periodicity can be of one of
the following
a.“<start time>-<end time>
<start_day>-<end day>”
b.“<start time > <start_day>-<end
day>”
c.“<start time>-<end time>
<start_day>”
d.“<start time> <start_day>”
e.“ * *”
f.“ * <start_day>-<end day>”
g.“<start time>-<end time> *”
2) The ‘start time’ and ‘end time’
can take values from 0-24
representing the hour of the day
only.
3) The ‘start day’ and ‘end day’
can take values from 0-7
representing the day of the week
only.
4) ‘*’ indicates all hours of the day
or all days of the week based on its
position.
Note: The end_time and end_day
are not included. Meaning 15-16
means 1500-1559 Hours and 0-2
means Monday and Tuesday
5) A Maximum of 8 periodicity
information is allowed for
Asynchronous Replication pair
6) This command can be issued in
a primary.
remove asyncreplica
-n/--name < asynchronous replication name>
-c/--containername <container name>
-s/-- schedule>
-d/--index <system assigned name>
Example:
remove -n myname -c Cont0 -s "0-24 0-7" -d 1
asyncreplica
remove -n myname -c Cont0 -s "* 0-7" -d 1
asyncreplica
Remove periodicity information for
a particular Asynchronous
Replication.
Note:
1) The periodicity format should be
same as above.
2) This command can be issued in
a primary.
remove -n myname -c Cont0 -s "0-24 *" -d 1
asyncreplica
remove -n myname -c Cont0 -s "* *" -d 1
asyncreplica
set asyncreplica -t/--type snap
-c/--containername <containername>
Sets the snapshot schedule for a
CG.
Chapter Two: Command Set 37
Page 44

Command Argument Description
-n/--cgname <cgname>
-s/--schedulesnap
<scheduleduration:maxsnapshots>
-d/--description <description>
-b/--backuptargetname <backuptargetname>
-p/--scheduleType <0-Windows,1-Local>
Example:
set -t snap -c Cont0 -n mysar0 -s 5:10 -s 60:20 -d
testing -b backuptest -p 0 asyncreplica
enable asyncreplica -t hasar
-n/--name < asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-i/--ip <other HA system IP>
update asyncreplica -n/--name < asynchronous replication name>
-c/--containername <container name>
-d/--index <system assigned name>
-i/--ip <other HA system IP>
Enables HA-DR with the HA pair
system. IP addres should be the
WAN IP of HA pair that can be
reached from DR.
This command can be issued in a
primary of a HA-DR setup. Should
be used when HA was setup on an
existing SAR group.
Removes the HA- DR setup on the
given IP. It must be the IP of the
HA pair. The HA pairing should
be removed after executing this
command.
This command can be issued in a
primary of a HA-DR setup.
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
38
Page 45

Journal Volume Management
These commands configure a journal and journal file.
create
journal
create
journal
delete
journal
delete
journal
get
journal
get
journal
get
journal
get
journal
-t/--type journal
-j/--journalname <journalname>
-l/--ldname <ldname>
Example:
create -t journal -j jour0 -l /dev/sdb journal
-t/--type journalfile
-j/--journalname <journalname>
-f/--journalfilename <journalfilename>
Example
create -t journalfile -j jour0 -f jf0 -z 10 -c cont1 -v
v1 -v v2 journal
-t/--type journal
-j/--journalname <journalname>
Example:
delete -t journal -j jour0 journal
-t/--type journalfile
-c/--containername <containername>
-f/--journalfilename <journalfilename>
Example:
delete -t journalfile -c cont0 -f jf0 journal
-t/--type journal
-j/--journalname <journalname
Example:
get -t journal -j Jour0 journal
-t/--type journalfile
-c/--containername <containername>
-f/--journalfilename <journalfilename>
Example:
get -t journalfile -c Cont0 -f jf0 journal
-t/--type journalfile
-c/--containername <containername>
-v/--volumename <volumename>
Example:
get -t journalfile -c Cont0 -v vol0 -v vol1 -v vol2
journal
-t/ --type snaptable
-c/--containername <containername>
-f/--journal/CG name <journal/CG name>
Example:
Creates journal.
Minimum LD size for journal
creation is 10GB
Creates journal file.
1)Minimum LD size for journal
creation is 10GB
Deletes journal
Deletes journal file
Gets journal information
Gets journal file information
Gets journal file name for a
specific volume.
Gets information for a specific
journal file snapshot.
Chapter Two: Command Set 39
Page 46

list
journal
list
journal
list
journal
creategroup
journal
creategroup
journal
expand
journal
set
journal
get -t snaptable -c c0 -f cg0 -n 10 journal
-t/ --type journal List journal information.
-t/ --type journalfile
List journal file information.
-c/--containername <containername
-t/ --type snaptable
-c/--containername <containername>
List information for a specific
journal file snapshot.
-f/--journal/CG name <journal/CG name>
Example:
list -t snaptable -c containername -f cg0 journal
-t/--type snap
-s <contname:volumename:snapname>
-j <contname:journalfilename>
Creates group snapshot and post
event to journal
-d <volume_dialect>
Example: creategroup -t snap -s
c0:v0:Vsv0xxxxxxxxxxxxxxSchdL1RT -s
c0:v1:VsvixxxxxxxxxxxxxxSchdL1RT -j c0:jf0 -j
c0:jf1 -d 0 journal
-t/--type snap
-w
<contname:volumename:snapname:writsnapname>
Creates group writeable snapshot
and post event to journal
-d <volume_dialect>
Example:
creategroup -t snap -w
c0:v0:Vsv0xxxxxxxxxxxxxxSchdL1RT1:Vsv0xxx
xxxxxxxxxxxSchdL1WT1 -w
c0:v1:VsvixxxxxxxxxxxxxxSchdL1RT1:Vsvixxxx
xxxxxxxxxxSchdL1WT1 -d 0 journal
-t/--type journal
-j/--journalname <journalname>
-l/--ldname <ldname>
Example:
Expands journal.
1) Minimum LD size for journal
expansion is 10GB
expand -t journal -j jour0 -l /dev/sdc journal
-t/--type snap
-c/--containername <containername>
-j/--jfname <jfname>
Sets uniform scheduler settings in
journal file volumes.
-s/--schedulesnap
<scheduleduration:maxsnapshots>
-d/--description <description>
-b/--backuptargetname <backuptargetname>
-p/--scheduleType <0-Windows,1-Local>
Example:
set -t snap -c Cont0 -j mysar0 -s 5:10 -s 60:20 -d
testing -b backuptest -p 0 journal
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
40
Page 47

Continuous Data Protection
These commands are to view cdp for journal file.
rollback
cdp
review
cdp
delete
cdp
get
cdp
-c/--container <containername>
-f/--journalfile <jfname>
Example:
rollback -c c0 -f jf0 cdp
-c/--container <containername>
-f/--journalfile <jfname>
-s/--basesnap <t-number>
-t/--deltatime <deltat from basesnap>
-i/--deltaio <delta IO from deltat>
-e/--eventindex <deltaevt from basesnap>
Example:
review -c c0 -f jf0 -s 1 -t 10 -i 54 cdp
review -c c2 -f jf1 -s 1 -e 15 cdp
-c/--container <containername>
-f/--journalfile <jfname>
Example:
delete -c c0 -f jf0 cdp
-t review
-c/--container <containername>
-f/--journalfile <jfname>
Example:
get -t review -c c0 -f jf0 cdp
Recovery Wizard
These commands are used as part of recovery wizard.
get recoverywizard -c/--container <container name>
-v/--volume<volumename>
-x/--xml (optional)
-n/--tnum <writable snapshot number> (optional)
Example:
get -c c0 -v vol1 recoverywizard
get -c c0 -v vol1 -v vol2 -v vol3 -n 1 -x
recoverywizard
review
recoverywizard
-c/--container <container name>
-v/--volume<volumename>
-s/--snap<snapname>
-x/--xml (optional)
Example:
review -c c0 -v vol1 -s snapv1T1 recoverywizard
review -c c0 -v vol1 -v vol2 -v vol3 -s snap4v1T2
–s snap5v2T2 -s snap6v3T2 recoverywizard
Performs rollback on journal file.
Performs CDP Review operation
for journal file.
1) -t and -i options ignored if -e is
specified
2) Delta time and IO must not be
specified for event review
Delete a currently existing CDP
session.
Gets CDP Review Progress
operation for journal file.
Get recoverywizard lists the snaps
that have common‘t’ number
across the given set of volume(s).
Review recoverywizard activates a
set of snaps that have common ‘t’
number across the given set of
volume(s), adds them to a LUN
and enables them as a target to
which an initiator can login to
review the data.
Chapter Two: Command Set 41
Page 48
remove
recoverywizard
rollback
recoverywizard
-c/--container <container name>
-v/--volume<volumename>
-s/--snap<snapname>
-t/--tgt_name<tgt_name>
-x/--xml (optional)
Example:
remove -c c0 -v vol1 -s snap1 -t iqn.1991-
10.com.ami:itx00c09f2164459105:t08212006tgt1
recoverywizard
remove -c c0 -v vol1 -v vol2 -v vol3 –s snap4v1T2
-s snap5v2T2 -s snap6v3T2 -t iqn.1991-
10.com.ami:itx00c09f2164459105:t08222006tgt2
recoverywizard
-c/--container <container name>
-v/--volume<volumename>
-s/--snap<snapname>
-x/--xml (optional)
Example:
rollback -c c0 -v vol1 -s snap1 recoverywizard
rollback -c c0 -v vol1 -v vol2 -v vol3 –s
snap4v1T2 -s snap5v2T2 -s snap6v3T2
recoverywizard
Storage Resource Management
These commands are used as part of SRM.
list srm -q/--queue <workflow, pending, report>
-n/--num_tasks <number of tasks>
-o/--offset < offset in the queue >
-f/--filename <xml filename >
-x/--xml
Example:
list -q report -n 20 -o 5 srm
list -q pending -n 20 -o 5 srm
clear srm -q/--queue <workflow , pending, report >
-x/--xml
Example:
clear -q report srm
start srm Example:
start srm
stop srm Example:
stop srm
Remove recoverywizard disables
the target enabled in the Review
recoverywizard, removes the set of
snaps that have common ‘t’
number across the given set of
volume(s) from the LUN, and
deactivates the snapshot.
Note:
1) All Snaps have same‘t’ number.
Rollback recoverywizard rollbacks
the set of volumes to set of
snapshots.
Note:
1) All Snaps have same‘t’ number.
List the tasks in report, pending
and workflow queue of the
SRM
Clears the SRM queues such as
workflow, pending, and report
Start the Storage resource
management activity. This is by
default started in the iTX box
Stop the Storage resource
management activity
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
42
Page 49

Local and Replicated Snapshot validation
These commands are used as part of snap validation.
enable
snapvalidation
disable
snapvalidation
pause
snapvalidation
resume
snapvalidation
get
snapvalidation
list
snapvalidation
resume
snapvalidation
pause
snapvalidation
-t/--type local
-c/--containername <containername>
-v/--volumename<volumename>
-x/--xml
Example:
enable -t local -c Cont0 -v Volume0 snapvalidation
-t/--type local
-c/--containername <containername>
-v/--volumename<volumename>
-x/--xml
Example:
disable –t local -c Cont0 -v Volume0
snapvalidation
-t/--type local
-c/--containername <containername>
-v/--volumename<volumename>
-x/--xml
Example:
pause -t local -c Cont0 -v Volume0snapvalidation
-t/--type local
-c/--containername <containername>
-v/--volumename<volumename>
-x/--xml
Example:
resume –t local -c Cont0 -v Volume0snapvalidation
-t/--type local
-c/--containername <containername>
-v/--volumename<volumename>
-x/--xml
Example:
get -t local -c Cont0 -v Volume0snapvalidation
-t/--type local
-x/--xml
Example:
list -t local snapvalidation
-t/--type (SRP/HA)
-c/--containername <containername>
-v/--volumename<volumename>
-x/--xml
Example:
resume -t SRP -c Cont0 -v Volume0 snapvalidation
resume -t HA -c Cont0 -v Volume0 snapvalidation
-t/--type (SRP/HA)
-c/--containername <containername>
This will enable local NAS snap
validation for the given NAS
volume. Once enabled, it will be
in “resumed” state by default –
meaning ALL scheduled snaps will
be validated, both already present
and those that will be created new.
This will disable local NAS snap
validation for already enabled NAS
volume.
This pause validation of NAS
snapshots for already enabled NAS
volume.
This will resume validation of
NAS snapshots for already paused
(enabled) NAS volume.
This will return the status – paused
/ resumed of the given NAS
Volume for snap validation. It will
also return the list of snapshots that
are validated so far with the status
(passed / failed)
This will return the list of NAS
volumes that are enabled for NAS
snap validation, along with the
current status – paused / resumed.
This will resume replica validation
for the given volume or volumes
SRP/HA. The remote system
information will be taken from the
given replica pair itself, so no need
to add them separately.
SRP – Sync replica module
HA – High availablility module
Pauses the already running
SRP/HA replica validation of given
Chapter Two: Command Set 43
Page 50

get
snapvalidation
resume
snapvalidation
pause
snapvalidation
get
snapvalidation
-v/--volumename<volumename>
-x/--xml
Example:
pause -t SRP -c Cont0 -v Volume0 snapvalidation
pause -t HA -c Cont0 -v Volume0 snapvalidation
t/--type (SRP/HA)
-c/--containername <containername>
-v/--volumename<volumename>
-x/--xml
Example:
get -t SRP -c Cont0 -v Volume0 snapvalidation
get -t HA -c Cont0 -v Volume0 snapvalidation
-t/--type (CG)
-c/--containername<containername>
-n/--cgname <cgname>
-x/--xml
Example:
resume -t CG -c Cont0 -n CG1 snapvalidation
-t/--type (CG)
-c/--containername <containername>
-n/--cgname <cgname>
-x/--xml
Example:
pause -t CG -c Cont0 -n CG1 snapvalidation
-t/--type (CG)
-c/--containername<containername>
-n/--cgname <cgname>
-x/--xml
Example:
get -t CG -c Cont0 -n CG1 snapvalidation
set.
SRP – Sync replica module
HA – High availability module
This will return the status – paused
/ resumed as well as the list of
snapshots validated. For SRP/HA
with multiple volumes, the each
validated snap of each volume will
be returned.
SRP – Sync replica module
HA – High availability module
This will resume replica validation
for the given volume or volumes
CG. The remote system
information will be taken from the
given replica pair itself, so no need
to add them separately.
CG – Snap assisted replication
module
Pauses the already running CG
replica validation of given set.
CG – Snap assisted replication
module
This will return the status – paused
/ resumed as well as the list of
snapshots validated. For CGs with
multiple volumes, the each
validated snap of each volume will
be returned.
CG – Snap assisted replication
module
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
44
Page 51

Appendix A Error Codes
Code Description
0 Command Succeeded
1 Command Failed
2 Invalid Parameter
3 Insufficient buffer
4 Insufficient memory
5 Invalid Operation
6 Error in opening file
10 User does not exist
11 User already exists
12 Selected user is a NIS user
13 User type did not match ADS NIS and LOCAL
14 User Count in UserList is not set
15 Invalid User ID
20 Group does not exist
21 Group already exists
22 Selected group is a NIS Group
23 Group Count in GroupList is not set
24 Group type did not match ADS, NIS and LOCAL
25 Invalid Group ID
26 Not able to init CLI command list
27 Not able to init CLI error list
31 Share does not exist
32 Share already exists
33 Path does not exist
34 Share does not exist
35 Invalid share count
36 Unable to create share entry
37 Unable to delete the share entry
38 Share operations not possible on iSCSI volumes
40 Read less number of event log records, than requested.
41 Event log database is full.
42 Event log database is Empty.
43 Event is not in list
44 Corrupted event list file
45 No Matching records were found.
46 Log database is Empty.
47 Read less number of records, than requested.
51 Volume does not exist
52 Volume already exists
53 Volume is busy. Retry later.
54 Disk is not available for use by the volume
55 Disk count is invalid for the requested raid level
56 Invalid Raid level
57 Volume is not ready or Volume does not exist
58 Raid Volume is a bootable volume
59 No Raid OS volume
60 Snapshot unsupported
61 Snapshot is inactive
62 Invalid Snapshot count
63 iSCSI Volume sync error
64 Snapshot is mounted
65 Readable snapshot cannot be mounted
68 Input has missing parameters
69 Input has excess parameters
Index 45
Page 52

Code Description
70 Null parameter
71 Invalid disk channel
72 Invalid Disk
73 Invalid Username
74 Invalid password
75 Invalid groupname
76 Invalid Network port
77 Invalid Path
78 Invalid Volume Name
79 Invalid share name
80 Invalid server name
81 Invalid member type
82 Invalid member count
83 Invalid access rights
84 Invalid address
85 Retry after system reboot
86 Invalid member name
87 Invalid service type
88 Invalid service status
90 Command is not processed
91 Command not supported
92 Reply packet is not good
93 Connection to Mstor Engine is lost
94 API is returned as success. but it got excess data than requested
95 Invalid payload size
96 Invalid host name
97 Invalid RPM name
98 Error in installing RPM
99 UPnP Share Does not exists
110 File open Error
111 User Operation busy
112 Unable to delete user
113 Unable to add group
114 Group operation busy
115 Unable to update user data
116 Unable to update group data
117 Invalid group ID
118 User ID already exists
119 Group ID already exists
120 Primary group error
121 Usergroup cache empty
122 Fewer members read
150 Group or Key does not exists in the file
151 Group already exists in the file
160 Error in initializing the health monitoring interface
161 Error in reading sensor value
162 Health monitoring SDK is not initialized
163 Path is used by other share
164 Record not found
165 Record addition failed
166 Record deletion failed
167 Record update failed
168 Entry not available
169 Error in getting container list
170 Volume list is NULL
171 Snapshot list is NULL
172 Entry addition failed
174 Error in setting ACL recursively
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
46
Page 53

Code Description
175 Error in mounting the share
200 Upgrade version error
201 Upgrade package already installed
202 Upgrade package dependency failure
203 Upgrade package installation failed
204 Upgrade requires more disk space
205 Invalid package name
220 Error in upgrade operation
230 Duplicate IP address
231 Invalid IP address
232 Invalid subnet mask
233 Invalid gateway
234 Invalid DNS server
235 Failed to set IP
240 Disks are differing in geometry
241 The partition of the disks differ
250 Raid Device is busy with resync or rebuild
251 Directory is shared
252 Error in deleting directory
253 Error in creating directory
254 Directory operations are not possible on ISCSI volumes
260 Invalid IPX internal network number
261 Invalid IPX external network number
262 Invalid IPX frame type
263 Invalid CIFS workgroup
264 Invalid SNMP Trap Destination
265 Invalid SNMP community
266 Invalid domain name
267 Duplicate SNMP Trap Destination
268 Duplicate Email ID
270 ACL database error
280 Error_net_join
281 ADS domain already exists
282 NIS domain already exists
290 Invalid time
291 Invalid date
292 Sync to NTP fail
293 Invalid time zone
300 Invalid network team mode
301 Invalid network team member
302 Invalid network team name
303 Network team already exists
304 Network adapter part of team
305 Invalid network team deletion order
306 Prerequisite not met
307 Network team does not exist
310 Invalid Rule Index
311 Rule limit exceeded
312 Rule Already exists
320 EVMS API General Failure
330 Invalid License File
331 Error in trying to update Evaluation License over existing Extended License
332 Incompatible License according to the Product Type
333 Invalid Customer ID
334 Invalid version
335 Invalid license features
336 License General error
337 License file open error
Index 47
Page 54

Code Description
338 License file read write error
350 Duplicate Alias Name
351 Alias not found
352 Invalid Alias Name
353 DHCP is not supported for Alias Adapters
354 Maximum Alias Adapter count exceeded
355 Maximum Alias per NIC exceeded
500 No Target found
501 Object Not Found
502 Internal error
503 Limits exceeded for operation
504 Object does not have date
505 iSNS status returned
506 iSNS task error
507 Cannot communicate with iSNS daemon
508 Internal iSNS error
509 iSNS server signals error
510 iSNS object not found
511 iSCSI Service not running
512 Invalid Target name
513 iSNS service not running
514 Current operation failed as it needs iSCSI to be enabled on this Volume
515 Password for this user has to be between 12 and 16 characters
516 ISCSI Disk still in use
517 Too many ISNS servers
518 ISNS Server error
519 Cannot perform this operation; there are no iSNS servers
520 Unknown iSNS error
521 Cannot remove ISNS server, an operation is in progress
522 LUN serial number error
523 Error in loading SMA module
524 Error in unloading SMA module
525 Maximum number of LUNs/Volumes has been reached for this target
526 Cannot add NAS volume to target
527 Deactivate portal to change portal tag
528 LUN had been already added to target
529 Invalid LUN
550 Invalid Disk Selection
551 Invalid RAID Number
552 No RAID is Present
553 Invalid RAID Level
554 Invalid Cache Type
555 Invalid Disk Count for the RAID Level
556 Invalid Spare Disk Count
557 Invalid Disk Information
558 Selected array is part of Volume...Cannot be deleted
559 RAID Disks cannot be used as Spares
560 Size of Raid Array is greater than 2 TB
561 Distributed Spares is not supported in RAID0, RAID1 and RAID1n
562 Rebuild failed
601 Invalid controller
603 Function not supported
604 Null Controller list
605 Function not supported
606 Spare disk unsupported
607 Disk count limit exceeded
608 Error in initializing disk
609 IOCTL failure
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
48
Page 55

Code Description
610 No spare support
611 Max limit reached
612 No MD device available
613 MD creation failed
614 Add entry to configuration file failed
615 disk is not free
616 Minimum disk count
617 Error in updating configuration file
618 Error in reading from configuration file read error
619 Raid hot remove failed
620 Disk partitioning failed
621 Raid hot add failed
622 No raid array found
623 OS raid device error
624 Swap raid device error
625 Device open Error
626 Error raid creation in progress
627 Invalid Sub raid disk count
628 Error on transforming offline raid
629 Invalid raid number
631 Invalid spare disk count
632 Illegal spare type
633 Invalid raid cache type
634 Invalid raid drive size
635 Maximum raid size
636 Insufficient disk space
637 Raid cannot be shrunk
638 API failure
639 Disk is not a Spare
640 Var Log device error
642 LD Create & Expand/Transform not supported while another LD Expand/Transform is in progress
643 LD Expand/Transformation is in progress, not able to change the configuration
644 Battery Not Available
645 Cache type is not supported by the controller
701 Container count limit exceeded
702 FileSystem error
703 Volume creation error
704 DM mount error
705 Delete container error
706 Create container error
707 Duplicate device error
708 Volume Deletion error
709 DM umount error
710 NAS Volume freeze error
711 NAS Volume unfreeze error
712 Start Container failed
713 Stop Container failed
714 Invalid LD Device
715 Invalid Container chunk size
716 Resource is busy
717 Error in getting container info
718 Invalid Container name
719 Error in deactivating snap
720 Error in activating snap
721 Error in creating snap
722 Error in deleting snap
723 Error in mounting volume
724 Error in unmounting volume
Index 49
Page 56

Code Description
725 Error in mounting file system
726 Error in getting snap info
727 Error in creating writable snap
728 Error in getting volume info
729 Max space reached
730 Invalid dialect
731 Invalid Snap
732 Error in rolling back Snap
734 Error in unmounting file system
735 Error in reading metadata
736 Serial already exists
737 Invalid mount type
738 Quota operations not possible on iSCSI volumes
739 Snapshot already activated
740 Snapshot already deactivated
741 Maximum volume count limit reached
742 Error in resizing the volume
743 Unsupported option
744 Error in DM reload
745 FileSystem growth failure
746 Volume already activated
747 Volume already deactivated
748 DMsetup info error
749 No space left in container
750 Permission denied
751 Session not found
752 Max user session limit
753 Max session limit
754 Management administrator not found
760 Maximum management stations configured
800 No free space to expand
801 Volume expansion limit exceeded
802 Read only snapshot count exceeded
803 Read write snapshot count exceeded
852 License – Read only snapshot count exceeded the license count
853 License – iSCSI volume license expired/disabled
854 License - SAS hard disk license expired/disabled
855 License – SATA hard disk license expired/disabled
856 License - Enclosure count exceeded/disabled
857 License - NAS volume license expired/disabled
858 License - Container size exceeded the license limit
859 License - Invalid License Key
860 License - License Structure is missing or License is absent
861 License - Service key is missing
862 License - Updation of Evaluation time failed
863 License - Limit on the particular feature is reached
864 License - Time for the particular feature usage expired or disabled
865 License - License Structure is corrupted
866 License - Temp file creation failed
867 License - Incorrect License for the System
868 License - Error Copying files
869 License - License File Decryption Failure
870 License - License File Encryption Failure
871 License - Setting License Failure
872 License - License Key is absent, License Module is not loaded.
873 License - Incorrect System for the License Key
874 Error in WINBIND
875 Error in YPBIND
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
50
Page 57

Code Description
876 Error in BIND
877 License - HA pair creation license expired/disabled
878 License - Unable to Read the License File
879 License - License Validation Failure
880 License - New Motherboard or New Motherboard with Some External NIC cards found, For service key
generation, remove all External NIC cards from the system
881 License - Thin provision license expired/disabled, request denied.
882 License - ILM license expired/disabled, request denied.
883 License - Applying Old License File Again, request denied.
900 Replication is enabled
901 Incorrect Replication
902 Replication is enabled, secondary volume present in container
903 Replication is enabled, replication pair non-operational
904 Resource group is not owned
905 Resource group already started
906 Resource group is out of sync
907 Unable to get resource group information
908 Invalid resource group state
909 Machines chosen for HA are not identical
910 Subnet does not match in machines. All NICS should be on different subnets
911 Remote Resource group not accessible
912 Unable to set virtual ipaddress
913 Maximum of 1 Alias per NIC per RG exceeded
914 Primary Target Name already used for a different volume in secondary
915 Error in regenerating target name
916 Portal is inactive in Local/Remote
917 Replication command timed out on the remote box due to it being busy
918 No Target found for volume either in Primary/Secondary
919 Replication – Operation not permitted on Secondary
1001 Replication - General error
1002 Replication - Invalid parameters
1003 Replication - Insufficient memory for performing the operation
1004 Replication - Permission denied
1005 Replication - system busy
1006 Replication - Fatal error
1007 Replication - Master Logical drive NOT available
1008 Replication - Volume error
1009 Replication - Volume size error
1010 Replication - iSCSI target serial number error
1011 Replication - Error while accessing Container DDF
1012 Replication - Error while accessing Replication DDF
1013 Replication - Initiator error
1014 Replication - Remote device error
1015 Replication - Error while accessing tab bits
1016 Replication - iSCSI login error
1017 Replication - Error while activation
1018 Replication - Remote Volume device NOT found
1019 Replication - Remote Management device NOT found
1020 Replication - Sync replication feature is not licensed or time period expired
1021 Replication - Error in establishing MPIO Session: Please check if secondary or link to it is alive, and it's
portal is activated
1022 Replication - Error in creating HA Pair. Volume is part of a SAR pair
1023 Replication - Resource group count exceeded
1024 Replication - Resource group already present
1025 Replication - Resource group not present
1026 Replication - Failed to modify the resource group config
1027 Replication - Resource group entry not present
1028 Replication - Duplicate entry present in resource group config
Index 51
Page 58

Code Description
1029 Replication - Volume is not in sync
1030 Replication - Box owns RG but volumes are secondary
1031 Replication - Box is not the orignal owner of the RG
1032 Replication - Box does not own RG but volumes are primary
1101 Asynchronous Replication – Asynchronous Replication CG not found
1102 Asynchronous Replication – General Failure
1103 Asynchronous Replication – Duplicate Asynchronous Replication CG name
1104 Asynchronous Replication – Volume already part of Asynchronous Replication CG name
1105 Asynchronous Replication – Invalid Volume size
1106 Asynchronous Replication – Invalid Asynchronous Replication CG role
1107 Asynchronous Replication – Invalid volume count
1108 Asynchronous Replication – Volume not empty
1109 Asynchronous Replication – IOCTL error
1110 Asynchronous Replication – Error in Handshake
1111 Asynchronous Replication – Maximum CG reached
1112 Asynchronous Replication - Invalid opertion - replication not yet started - No valid snaps found
1113 Asynchronous Replication - CG config metadata area is corrupted
1114 Asynchronous Replication - Error in getting passive side CG info
1115 Asynchronous Replication - Error in getting passive side CG list
1116 Asynchronous Replication - Error in updating passive side CG info
1117 Asynchronous Replication - Error in passive side resume operation
1118 Asynchronous Replication - Error in passive side pause operation
1119 Asynchronous Replication - No common T number snapshot found
1120 Asynchronous Replication - Given T number snapshot info not available
1121 Asynchronous Replication - Given volume already part of another CG
1122 Asynchronous Replication - Remote machine unavailable
1123 Asynchronous Replication - Invalid Remote machine CG info
1124 Asynchronous Replication - Active volumes already paired with another SAR CG in this remote box
1125 Asynchronous Replication - Volumes having different scheduler settings
1126 Asynchronous Replication - Invalid Volume Chunk Size
1127 Asynchronous Replication - Unable to get the initiator name
1128 Asynchronous Replication - Unable to get mtarget name
1130 Asynchronous Replication - Minimum snapshot retention should be more than 3 per level
1131 Asynchronous Replication - Volume part of synchronous replication or HA grouping
1132 Asynchronous Replication - Invalid configuration
1200 JM – Failed to create Journal
1201 JM – Journal File count limit exceeded
1202 JM – Failed to create Journal File
1203 JM – Error in getting Journal info
1204 JM – Error in starting Journal
1205 JM – Error in stopping Journal
1206 JM – Invalid Journa Name
1207 JM – Journal Count limit exceeded
1208 JM – Failed to delete Journal
1209 JM – Journal Event Failed
1210 JM – Failed to expand Journal
1211 JM – Failed to delete Journal File
1212 JM – Error in getting Journal File Name
1213 Invalid T number
1214 JM – Journal in use
1215 JM – JournalFile size exceeded the Free Space available in Journal
1250 JM – Reached EOF
1300 Snap Validation – Info file creation error
1301 Snap Validation – Already paused
1302 Snap Validation – Already resumed
1303 Snap Validation – Config file creation error
1304 Snap Validation – Block Dedupe enabled
1305 Snap Validation – Remote side snapshot not available
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
52
Page 59

Code Description
1306 Snap Validation – Local snapshot not available
1307 Snap Validation – User snapshot validation pending
1308 Snap Validation – Snapshot already validated
1325 Read only snap count max reached
1326 Snap count per volume max reached
1327 Snap count per system max reached
1345 Duplicate Frequency/Level entered for Snapshot Schedule
1351 iSCSI MirrorConfig – Physical disk size mismatch found
1352 iSCSI MirrorConfig – Invalid physical disk mapping found
1353 iSCSI MirrorConfig – Hotspare creation failed
1354 iSCSI MirrorConfig – Logical drive creation failed
1355 iSCSI MirrorConfig – Container creation failed
1400 CDP – General error
1401 CDP – Invalid parameter
1402 CDP – Invalid Journal file name
1403 CDP – Invalid Container name
1404 CDP – Journal not present
1405 CDP – Failed to open resource
1406 CDP – Snapshot not available
1407 CDP – Memory constraint
1408 CDP – Snapshot not available in Journal
1409 CDP – CDP session for given parameters not available
1410 CDP – Failed to renew CDP session
1411 CDP – Event missing in Journal file
1412 CDP – Thread creation error
1413 CDP – Journal file overflow error
1414 CDP – Snapshot is in unstable state
1415 CDP – Failed to read from journal file
1504 Upgrading packages failed
1506 Upgrade Checksum failed
1507 Upgrade error in downloading image
1508 Upgrade image version is older than current version
1509 Upgrade image version is same as current version
1510 Insufficient disk space for upgrade
1511 Upgrade image file is corrupted
1512 Error in performing upgrade
1513 Invalid parameters in upgrade
1514 Upgrade image version is invalid
1515 License is not valid for upgrade
1516 Invald IP address or Host name
1517 Error in performing upgrade
2001 Remote Communication - General Error
2002 Remote Communication - Invalid Parameters
2003 Remote Communication - Insufficient memory for performing the operation
2004 Remote Communication - Permission Denied
2005 Remote Communication - Management Target Busy
2006 Remote Communication - Fatal Error
2010 Remote Communication - Invalid Packet Signature
2011 Remote Communication - Version Error
2012 Remote Communication - No such remote module
2013 Remote Communication - Connection Error
2014 Remote Communication - Inter-node Initiator error
2015 Remote Communication - Login Error
2016 Remote Communication - Module Connection Error
2017 Remote Communication - Remote Device Error
4096 DVM - Lib node open error
4097 DVM - Lib invalid data
4098 DVM - Device End of file
Index 53
Page 60

Code Description
4099 DVM - Device open error
4100 DVM - Device access error
4101 DVM - general error
4102 DVM - Lib DM suspend error
4103 DVM - Lib DM resume error
8192 DVM - generic error
8193 DVM - memory allocation errors
8194 DVM - IOCTL Parameter passing failures copy_from_user, copy to user etc
8195 DVM - generic invalid parameter error
8196 DVM - container name is empty / unrecognizable by DVM driver
8197 DVM - volume is empty / unrecognizable by DVM driver
8198 DVM - snapshot name is empty / unrecognizable by DVM driver
8199 DVM - Error persisting metadata to disk (or) reading metadata from disk
8200 DVM - The number of LD segments is invalid
8201 DVM - The stripe size for the LD segments is invalid
8202 DVM - Duplicate container name
8203 DVM - Too many containers in the system
8204 DVM - Failed to open the LD segment
8205 DVM - volume size specified container
8206 DVM - invalid provisioning type specified
8207 DVM - snap type specified is invalid
8208 DVM - invalid UUID specified
8209 DVM - duplicate volume name specified
8210 DVM - duplicate volume UUID specified
8211 DVM - too many volumes in the system
8212 DVM - cannot create exact provisioned volume - No space available
8213 DVM - when trying to take a snap of snapshot - assumes writ. snapshot is another ioctl
8214 DVM - duplicate snap name
8215 DVM - too many snaps in the volume or a writable snapshot already exists
8216 DVM - too many snaps in the system
8217 DVM - if the ld segment length is invalid
8218 DVM - when trying to take a "writable" snap of volume
8219 DVM - volume is in use
8220 DVM - snap is in use
8221 DVM - snap rollback bg fail
8222 DVM - compaction bg fail
8223 DVM - compaction already running
8224 DVM - cannot pause compaction
8225 DVM - cannot stop compaction
8226 DVM - log fail
8227 DVM - Container couldn't start, conflicts in vol-index with existing container-volumes
8228 DVM - Obsolete command
8229 DVM – Redundant Snapshot
8230 DVM - Operation failed on invalidated snapshot
8231 DVM – Invalid Pinned Volume
8232 DVM – Pinned Volume exists
8233 DVM – Source & Dest Volume size mismatch
8234 DVM – Destination Volume is not empty
8236 DVM - No events
StorTrends® iTX Software CLI (Command Line Interface) (Version 2.7) User’s Guide
54
 Loading...
Loading...