AirMagnet AM-5020-11AG User Manual

AirMagnet AM-5020-1 1AG
User Guide
Part Number: UG-AM-5020
© 2004 AirMagnet®, Inc. All rights reserved. 1

Table of Contents
Table of Contents............................................................................................................................ 2
Definitions and Terminology.......................................................................................................... 3
References....................................................................................................................................... 5
Introduction..................................................................................................................................... 6
Expert Analysis Functions Enabled by Sensor............................................................................... 8
Enforce Security Policy ............................................................................................................ 8
Detect Wireless Intruders and Attacks...................................................................................... 8
Lock In Network Performance.................................................................................................. 9
Ensure Network Reliability....................................................................................................... 9
Centralizing System Management............................................................................................ 9
Enable Flexible Configuration and User Access ...................................................................... 9
Enable Graphics User Interface from Anywhere in the Network............................................. 9
Enable Remote Troubleshooting and Active Tools................................................................. 10
Low Overhead On Operational Network................................................................................10
AirMagnet Sensor Operation Modes............................................................................................ 11
Configuration Mode................................................................................................................ 11
Analysis Mode........................................................................................................................ 11
Active Control Mode .............................................................................................................. 12
Hardware Specifications............................................................................................................... 13
Mechanical.............................................................................................................................. 13
Environmental......................................................................................................................... 13
Power ...................................................................................................................................... 13
Radio Frequency..................................................................................................................... 14
Effective Data Rates ............................................................................................................... 15
Physical Interfaces.................................................................................................................. 15
Internal.................................................................................................................................... 15
Compliance............................................................................................................................. 15
Sensor Powering Options.............................................................................................................. 16
AC Power................................................................................................................................ 16
Power-over-Ethernet (POE) Injector...................................................................................... 16
Appendix A: FIPS-Required Features............................................................ 17
Use of TLS Protocol for Secure Communication................................................................... 17
Limited Logon Attempts......................................................................................................... 17
Length of Password Word....................................................................................................... 17
Automatic Self Checking and Module Integrity Checking..................................................... 17
Change of Shared Secret Key via Secure Communication..................................................... 18
Password Encrypted in FIPS-Approved Algorithms .............................................................. 18
Securing the Sensor with the Tampering-Proof Tape ............................................................. 18
Periodical Inspection of the Module for Evidence of Tampering........................................... 18
© 2004 AirMagnet®, Inc. All rights reserved. 2

Definitions and Terminology
802.3
802.11 a
802.11 b
802.11 g
802.11 e
802.1x
ACK Acknowledgement frame
AGC Automatic Gain Control
AID Association Identifier
BCC Binary Convolutional Code
BPSK Binary Phase Shift Keying
CF-End Contention-Free End
CFP Contention-Free Period
CF-Poll Contention-Free Poll
CTS Clear to Send
DA Destination Address
dB Decibels
DBPSK Differential Binary Phase Shift Keying
DCF Distributed Coordination Function
DIFS Distributed Interframe Space
DPSK Differential Phase Shift Keying
DQPSK Differential Quadrature Phase Shift Keying
DS Distribution System
DSSS Direct Sequence Spread Spectrum
EIFS Extended Interframe Space
ESS Extended Service Set
ETSI European Telecommunications Standards Institute
FCC Federal Communications Commission
FCS Frame Check Sequence
FFT Fast Fourier Transform
GFSK Gaussian Frequency Shift Key
GPS Global Positioning System
HR/DSSS High Rate Direct Sequence Spread Spectrum
I/Q Interphase/Quadrature
IAPP Inter-Access Point Protocol
ICI Interchip Interference
ICV Integrity Check Value
IEEE Institute of Electrical and Electronics Engineers
IPSEC VPN
IR Infrared ISI Intersymbol interference
ISM Industrial, Scientific, and Medical
LBT Listen Before Talk
L2TP VPN Layer 2 Tunneling Protocol VPN
© 2004 AirMagnet®, Inc. All rights reserved. 3

LEAP
LLC Logical Link Control
MIB Management Information Base
MIC Message Integrity Check
MKK Ministry of Telecommunications
MMACS Multimedia Mobile Access Communication System
MPDU MAC Protocol Data Unit
MSDU MAC Service Data Unit
NAV Network Allocation Vector
OFDM Orthogonal Frequency Domain Multiplexing
PBCC Packet Binary Convolutional Coding PC Point Coordinator
PCF Point Coordination Function
PEAP
PHY Physical Layer
PIFS Priority Interframe Space
PLCP Physical Layer Convergence Procedure
PMD Physical Medium Dependent
POE Power over Ethernet
PPDU PLCP Protocol Data Unit PFSF PLCP Signaling Field
PPTP VPN Point to Multiple Point Virtual Private Network
PS Poll Power Save Poll
QAM Quadrature Amplitude Modulation
QPSK Quadrature Phase Shift Keying
RA Receiver Address
RF Radio Frequency
RFID Radio Frequency ID
RSADSI RSA Data Security, Inc.
RTS Request to Send
SA Source Address
SFD Start of Frame Delimiter
SIFS Short Interframe Space
SNR Signal to Noise Ratio
SSH VPN
SSID Service Set Identity
STA Station
TA Transmitter Address
TBT Target Beacon Transmission Time
TIM Traffic Indication Map
TKIP
TLS
TSF Timer Synchronization Factor
TTLS
TU Time Units
WEP
WLAN Wireless LAN
WPA
© 2004 AirMagnet®, Inc. All rights reserved. 4

References
http://www.airmagnet.com for the following referenced documents:
Visit
Reference 1 AirMagnet Enterprise Datasheet
Reference 2 AirMagnet Enterprise FAQ
Reference 3 AirMagnet Guided Tour
Reference 4 AirMagnet Impact Study
© 2004 AirMagnet®, Inc. All rights reserved. 5
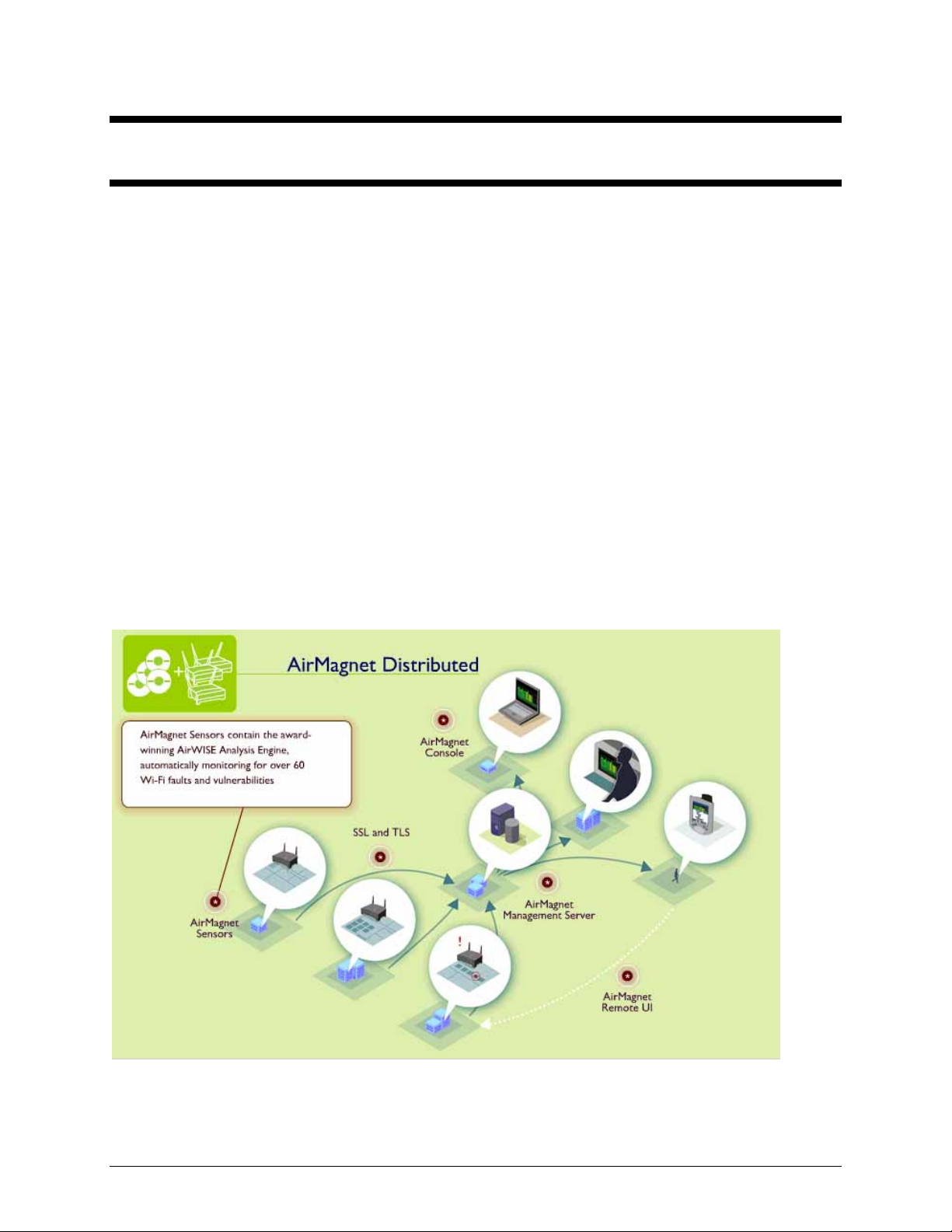
Introduction
The AirMagnet AM-5020-11AG Sensor provides 24x7 remote monitoring and troubleshooting of
802.11 wireless networks. Sensors are deployed near clusters of access points, and provide
security assessment, performance monitoring, network fault detection and remote
troubleshooting functions. Management staff can easily monitor the security measures in use on
every station and access point device to insure compliance with established policies, and also
automatically scan for dozens of wireless network attacks.
These analysis functions can be monitored and controlled from both centralized and distributed
operations centers. These centers can be located in the building, on the campus, or anywhere in
the world without requiring high travel costs or excessive delay of sending IT expert staff to
remote locations.
Figure 1 shows a complete network including the AM-5020-11AG AirMagnet Sensor.
Companion software functions available for the complete AirMagnet Enterprise system include
the following:
AirMagnet Enterprise Server – provides the dynamic operations control function to the entire
network of bound sensors including sensor activation/deactivation, upgrade of sensor software,
and collection of alerts, data, and statistics for all stations and access points within wireless
segments monitored by the sensors.
Figure 1: WLAN Network with AM-5020-11AG AirMagnet SmartEdge Sensors Installed
AirMagnet Enterprise Console – provides the graphical user interface into the server from any
© 2004 AirMagnet®, Inc. All rights reserved. 6
 Loading...
Loading...