Page 1

Wireless G 2.4GHz 500mW Outdoor AP
Model: APO1000/APO1010
User’s Manual
V.1.0
Page 2

Table of Contents
CHAPTER 1. SYSTEM OVERVIEW.............................................................................................................................1
1.1 INTRODUCTION........................................................................................................................................................1
1.2 SYSTEM CONCEPT .................................................................................................................................................. 2
1.3 APPLICATIONS IN WIRELESS NETWORK..................................................................................................................3
1.4 PRODUCT BENEFIT..................................................................................................................................................8
1.5 SPECIFICATION........................................................................................................................................................ 9
CHAPTER 2. BASIC INSTALLATION.......................................................................................................................12
2.1 HARDWARE INSTALLATION.....................................................................................................................................12
2.1.1 Package Contents......................................................................................................................................12
2.1.2 Panel Function Descriptions.....................................................................................................................13
2.1.3 Hardware Installation Steps ......................................................................................................................15
2.2 WEB MANAGEMENT INTERFACE INSTRUCTIONS...................................................................................................16
CHAPTER 3. AP MODE CONFIGURATION.............................................................................................................18
3.1 EXTERNAL NETWORK CONNECTION.....................................................................................................................18
3.1.1 Network Requirement................................................................................................................................18
3.1.2 Configure LAN IP........................................................................................................................................19
3.2 WIRELESS LAN NETWORK CREATION..................................................................................................................21
3.2.1 Wireless General Setup.............................................................................................................................21
3.2.2 Wireless Advanced Setup.........................................................................................................................22
3.2.3 Create Virtual AP(VAP)..............................................................................................................................25
3.2.3.1 Virtual AP Overview...............................................................................................................................................25
3.2.3.2 Virtual AP Setup.....................................................................................................................................................26
3.2.4 MAC Filter Setup........................................................................................................................................ 32
3.3 WIRELESS NETWORK EXPANSION........................................................................................................................33
3.4 SYSTEM MANAGEMENT .........................................................................................................................................36
3.4.1 Configure Management.............................................................................................................................36
3.4.2 Configure System Time............................................................................................................................. 38
3.4.3 Configure UPnP..........................................................................................................................................39
3.4.4 Configure SNMP Setup.............................................................................................................................40
3.4.5 Backup / Restore and Reset to Factory..................................................................................................42
3.4.6 Firmware Upgrade......................................................................................................................................43
3.4.7 Network Utility.............................................................................................................................................44
3.4.8 Reboot.......................................................................................................................................................... 45
3.5 SYSTEM STATUS ....................................................................................................................................................46
3.5.1 System Overview........................................................................................................................................46
3.5.2 Associated Clients Status..........................................................................................................................48
3.5.3 WDS Link Status.........................................................................................................................................49
3.5.4 Extra Information........................................................................................................................................50
3.5.5 Event Log.....................................................................................................................................................52
CHAPTER 4. WDS MODE CONFIGURATION.........................................................................................................53
4.1 EXTERNAL NETWORK CONNECTION.....................................................................................................................53
4.1.1 Network Requirement................................................................................................................................53
4.1.2 Configure LAN IP........................................................................................................................................54
4.2 WIRELESS NETWORK EXPANSION........................................................................................................................56
4.2.1 Wireless General Setup.............................................................................................................................56
4.2.2 Wireless Advanced Setup.........................................................................................................................57
4.2.3 WDS Setup..................................................................................................................................................60
4.3 SYSTEM MANAGEMENT .........................................................................................................................................63
4.3.1 Configure Management.............................................................................................................................63
4.3.2 Configure System Time............................................................................................................................. 65
4.3.3 Configure UPnP..........................................................................................................................................66
4.3.4 Configure SNMP Setup.............................................................................................................................67
1
Page 3

4.3.5 Backup / Restore and Reset to Factory..................................................................................................69
4.3.6 Firmware Upgrade......................................................................................................................................70
4.3.7 Network Utility.............................................................................................................................................71
4.3.8 Reboot.......................................................................................................................................................... 72
4.4 SYSTEM STATUS ....................................................................................................................................................73
4.4.1 System Overview........................................................................................................................................73
4.4.2 WDS Link Status.........................................................................................................................................75
4.4.3 Extra Information........................................................................................................................................76
4.4.4 Event Log.....................................................................................................................................................78
CHAPTER 5. CPE MODE CONFIGURATION..........................................................................................................79
5.1 EXTERNAL NETWORK CONNECTION.....................................................................................................................79
5.1.1 Network Requirement................................................................................................................................79
5.1.2 Configure WAN Setup................................................................................................................................81
5.1.3 Configure DDNS Setup..............................................................................................................................84
5.1.4 Configure LAN IP........................................................................................................................................85
5.2 ACCESS POINT ASSOCIATION................................................................................................................................87
5.2.1 Wireless General Setup.............................................................................................................................87
5.2.2 Wireless Advanced Setup.........................................................................................................................90
5.2.3 Site Survey..................................................................................................................................................93
5.3 SYSTEM MANAGEMENT .........................................................................................................................................94
5.3.1 Configure Management.............................................................................................................................94
5.3.2 Configure System Time............................................................................................................................. 96
5.3.3 Configure UPnP..........................................................................................................................................97
5.3.4 Configure SNMP Setup.............................................................................................................................98
5.3.5 Backup / Restore and Reset to Factory................................................................................................100
5.3.6 Firmware Upgrade....................................................................................................................................101
5.3.7 Network Utility...........................................................................................................................................102
5.3.8 Reboot........................................................................................................................................................ 103
5.4 ACCESS CONTROL LIST.......................................................................................................................................104
5.4.1 IP Filter Setup............................................................................................................................................104
5.4.2 MAC Filter Setup...................................................................................................................................... 106
5.5 RESOURCE SHARING ..........................................................................................................................................107
5.5.1 DMZ............................................................................................................................................................107
5.5.2 Virtual Server (Port Forwarding).............................................................................................................108
5.6 SYSTEM STATUS .................................................................................................................................................. 110
5.6.1 System Overview...................................................................................................................................... 110
5.6.2 DHCP Clients............................................................................................................................................ 113
5.6.3 Extra Info.................................................................................................................................................... 114
5.6.4 Event Log................................................................................................................................................... 116
CHAPTER 6. CLIENT BRIDGE + UNIVERSAL REPEATER CONFIGURATION............................................ 117
6.1 EXTERNAL NETWORK CONNECTION...................................................................................................................117
6.1.1 Network Requirement.............................................................................................................................. 117
6.1.2 Configure LAN IP...................................................................................................................................... 118
6.2 ACCESS POINT ASSOCIATION..............................................................................................................................120
6.2.1 Configure Wireless General Setting...................................................................................................... 120
6.2.2 Wireless Advanced Setup.......................................................................................................................122
6.2.3 Site Survey................................................................................................................................................125
6.3 WIRELESS LAN NETWORK CREATION................................................................................................................126
6.3.1 AP Setup....................................................................................................................................................126
6.3.2 MAC Filter Setup...................................................................................................................................... 132
6.4 SYSTEM MANAGEMENT .......................................................................................................................................133
6.4.1 Configure Management........................................................................................................................... 133
6.4.2 Configure System Time........................................................................................................................... 135
6.4.3 Configure UPnP........................................................................................................................................136
6.4.4 Configure SNMP Setup...........................................................................................................................137
6.4.5 Backup / Restore and Reset to Factory................................................................................................139
2
Page 4

6.4.6 Firmware Upgrade....................................................................................................................................140
6.4.7 Network Utility...........................................................................................................................................141
6.4.8 Reboot........................................................................................................................................................ 142
6.5 SYSTEM STATUS ..................................................................................................................................................143
6.5.1 System Overview......................................................................................................................................143
6.5.2 Associated Clients Status........................................................................................................................146
6.5.3 DHCP Clients............................................................................................................................................ 147
6.5.4 Extra Information...................................................................................................................................... 148
6.5.5 Event Log...................................................................................................................................................150
CHAPTER 7. COMMAND LINE INTERFACE(CLI) ...............................................................................................151
7.1 ACCESSING THE CLI WITH TELNET.....................................................................................................................151
7.2 USING THE CLI....................................................................................................................................................152
APPENDIX A. WINDOWS TCP/IP SETTINGS.....................................................................................................154
APPENDIX B. WEB GUI VALID CHARACTERS ................................................................................................156
APPENDIX C. NETWORK MANAGER PRIVILEGES........................................................................................160
APPENDIX D. ENABLING UPNP IN WINDOWS XP..........................................................................................161
TECHNICAL SUPPORT............................................................................................................................................. 163
3
Page 5

4
Page 6

Chapter 1. System Overview
1.1 Introduction
The 802.11 b/g compliant Airlink101® APO1000/APO1010 is an outdoor wireless access point that can be used for five
different purposes in three different mod es. In the AP mode, it can be deployed either as traditional fixed wireless Access
Point(AP), or combination of AP and WDS(AP+WDS). In the WDS mode, it’s only used to expand or bridge Ethernet networks
and deployed as a main base, relay based or remote base station. In the CPE (Customer Premises Equipment) mode, it
connects to Wireless Internet Service Provider’s (WISP) outdoor network via wireless WAN gateway to access to Internet. In
the Client Bridge + Universal Repeater mode, it connects to Wireless Internet Service Provider’s (WISP) outdoor network via
wireless or wired bridge to access to Internet
The die-cast sealed APO1000/APO1010 is compact in size and compliant with IP68 weatherproof standard. It comes with a
mounting kit to mount on pole or wall. It is suitable for both indoor and outd oor usage with its 500mW output power, which is
higher than a typical indoor AP (100mW).
Features:
1. Access Point : It can be deployed as a traditional fixed wireless Access Point
2. Repeater: To expand wireless service by repeating prior AP
3. WDS : It can be used to expand Ethernet network via wireless WDS Link
4. AP+WDS: Not only to extend Ethernet network, but also provide wireless access to the expanded network
5. CPE (Customer Premises Equipment): It is a wireless gateway with NAT and DHCP Server functions to connects to
Wireless Internet Service Provider's (WISP)
6. Client Bridge + Universal Repeater : It is a wireless repeater or bridge to connects to Wireless Internet Service
Provider's (WISP)
1
Page 7
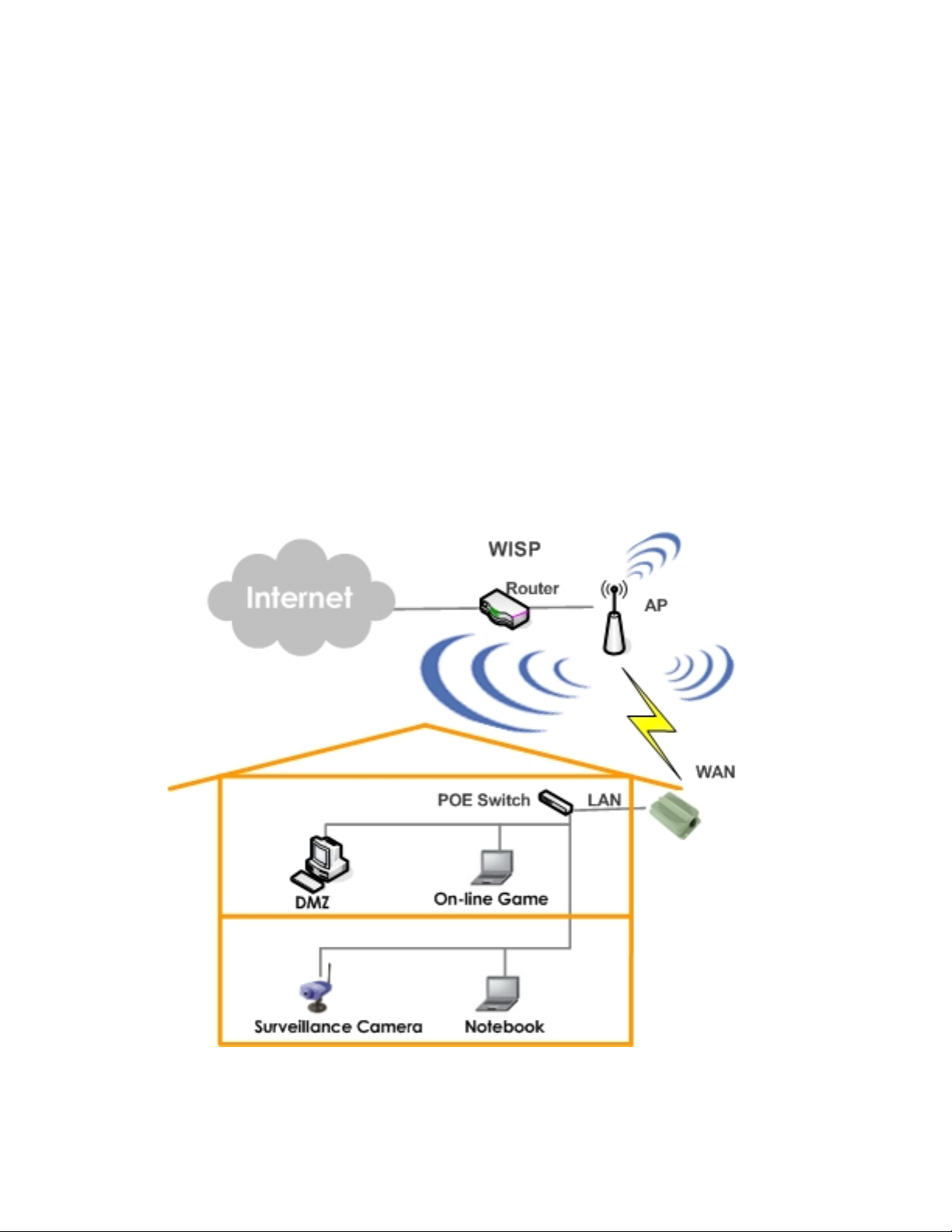
1.2 System Concept
The APO1000/APO1010 is not only designed and used as traditional outdoor AP, but also with rich features t ailored for WISP
applications. The two-level management capability and access control ease WISP and owners to maintain and manage
wireless network in a more controllable fashion. Main applications are listed as follows with illustration:
1. Wireless CPE for Multi Dwelling Unit/Multi Tenant Unit (MDU/MTU) complexes includi ng apartments, dormitories, and
office complexes.
2. Outdoor Access Point for school campuses, enterprise campuses, or manufacture plants.
3. Indoor Access Point for hotels, factories, or warehouses where industrial grade devices are preferred.
4. Public hotspot operation for café, parks, convention centers, shopping malls, or airports.
5. Wireless coverage for indoor and outdoor grounds in private resorts, home yards, or gulf course communities.
APO1000/
APO1010
2
Page 8
1.3 Applications in Wireless Network
APO1000/APO1010 is a multiple mode system which can be configured either as a wireless gateway or an access point as
desired. It also can be used as WDS link for Ethernet network expansion. This se ction depicts different applications in AP
Mode, WDS Mode, and CPE Mode and Client Bridge + Universal Repeater Mode.
Configuration in AP Mode (including Access Point + WDS)
An access point can be either a main, relay or remote base station. A main base station is typically connected to a wired
network via the Ethernet port. A relay base station relays data between main base stations and relay stations or remote
base stations with clients. A remote base station is the end point to accept connections from wireless clients and pass
data upwards to a network wirelessly.
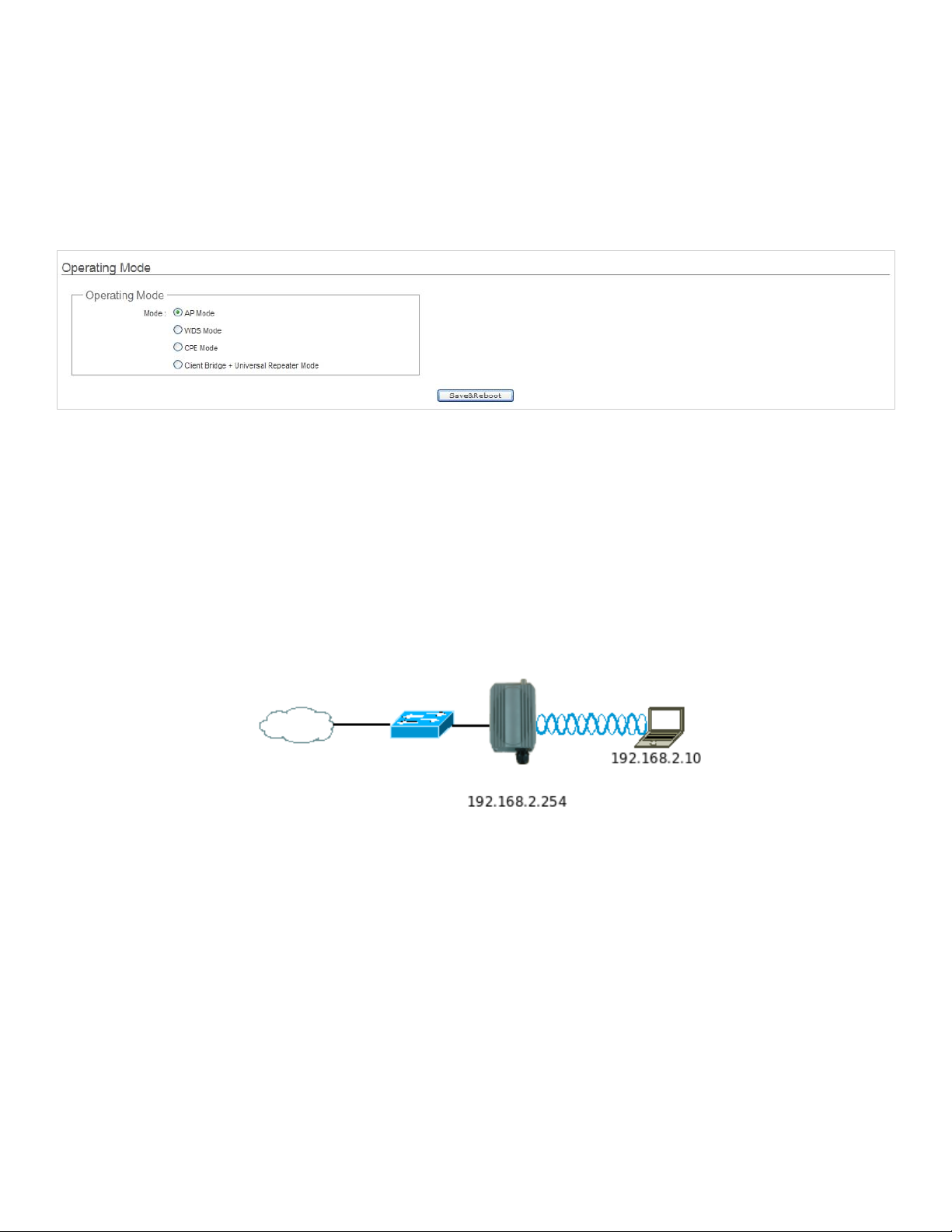
Î Example 1 : Access Point without WDS
9 It can be deployed as a tradition fixed wireless Access Point
APO1000/APO1010
Î Example 2 : Access Point with WDS
9 It can be deployed as a tradition fixed wireless Access Point and provides WDS link to expand network
3
Page 9
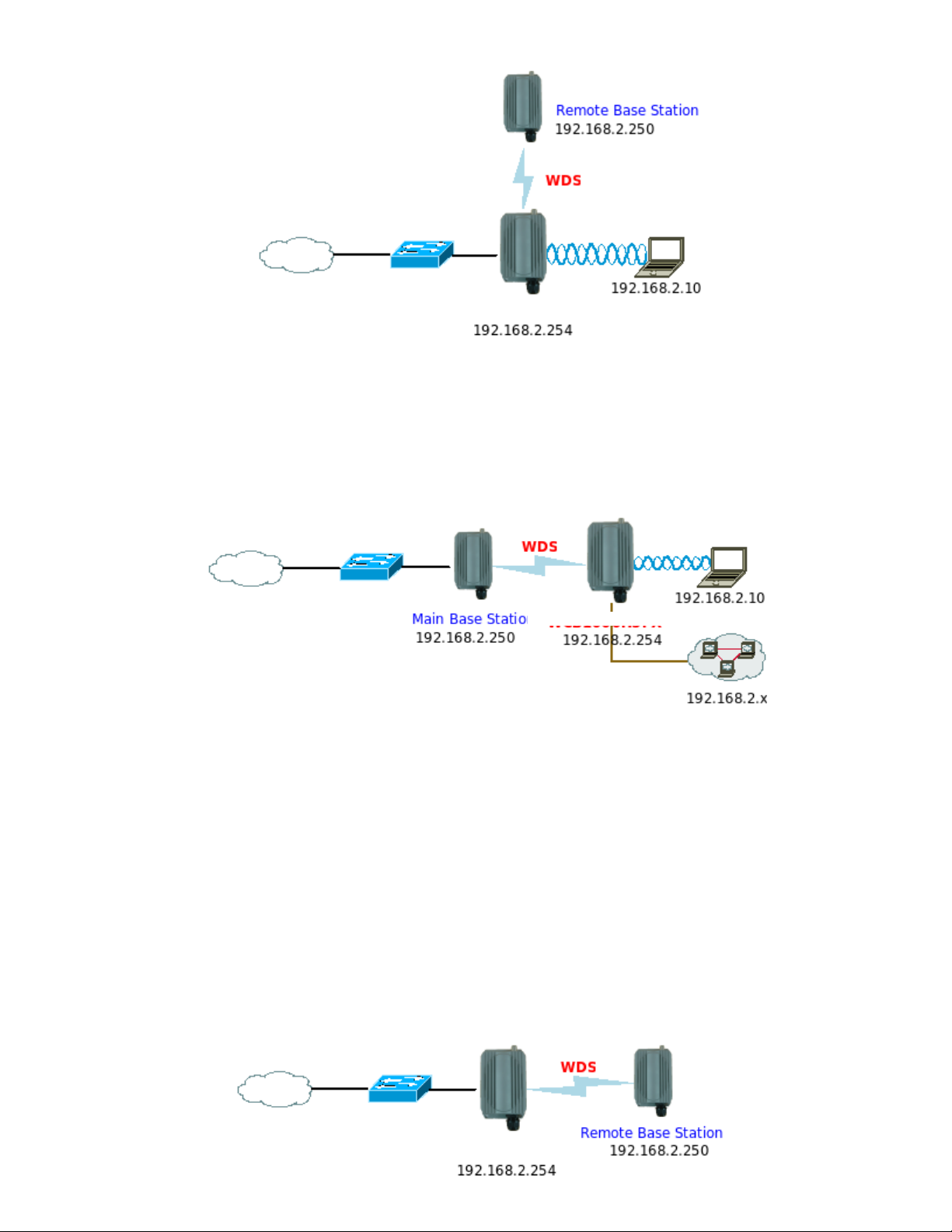
Configuration in WDS Mode (Pure WDS)
An access point can be either a main, relay or remote base station. A main base station is typically connected to a wired
network via the Ethernet port. A relay base station relays data between main base stations and relay stations or remote
base stations with clients. A remote base station is the end point to accept connections from wireless clients and pass
data upwards to a network wirelessly. In this mode, it can support single or multiple WDS links and no wireless clients
can associate with it though.
Î Example 1 : Point-to-Point
APO1000/APO1010
4
Page 10
APO1000/APO1010
5
Page 11
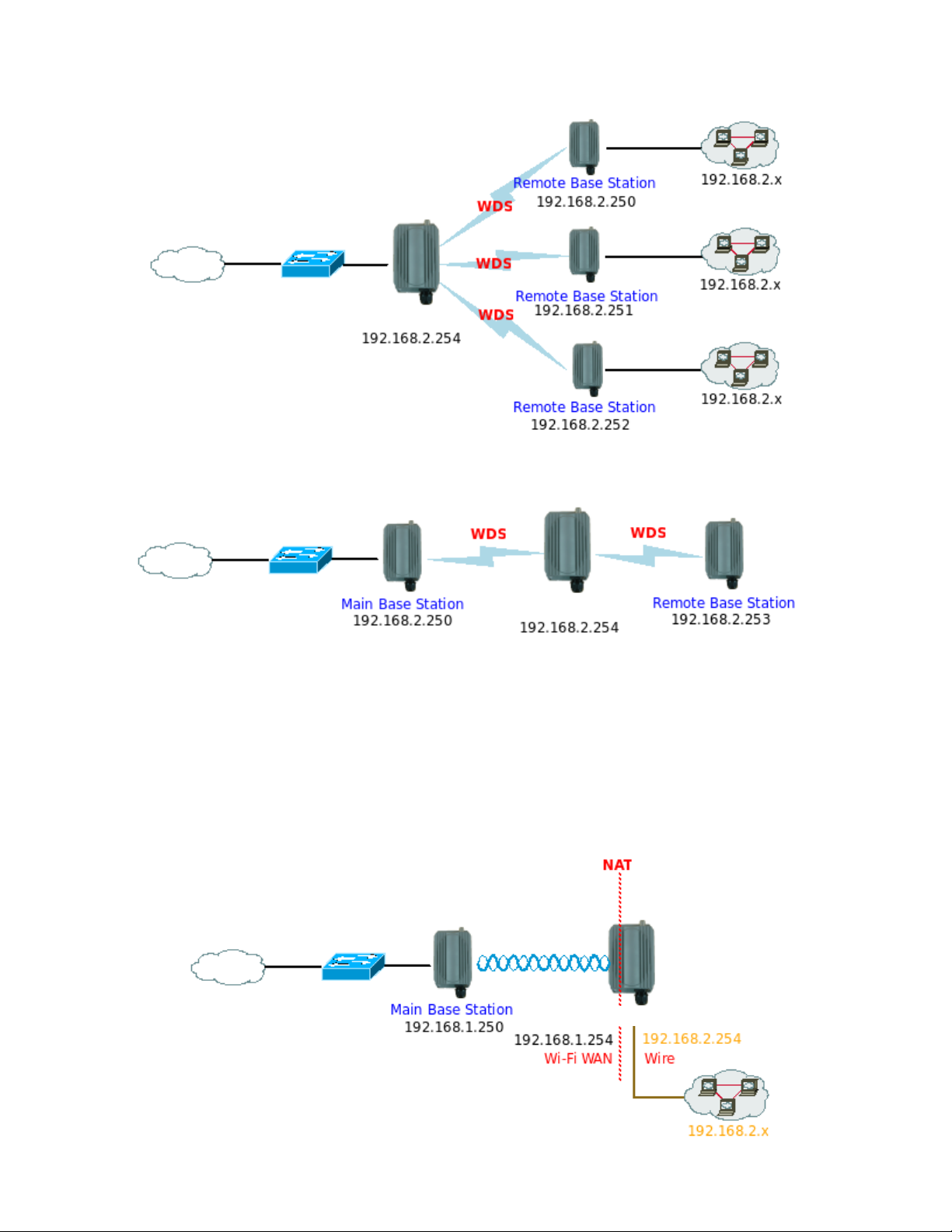
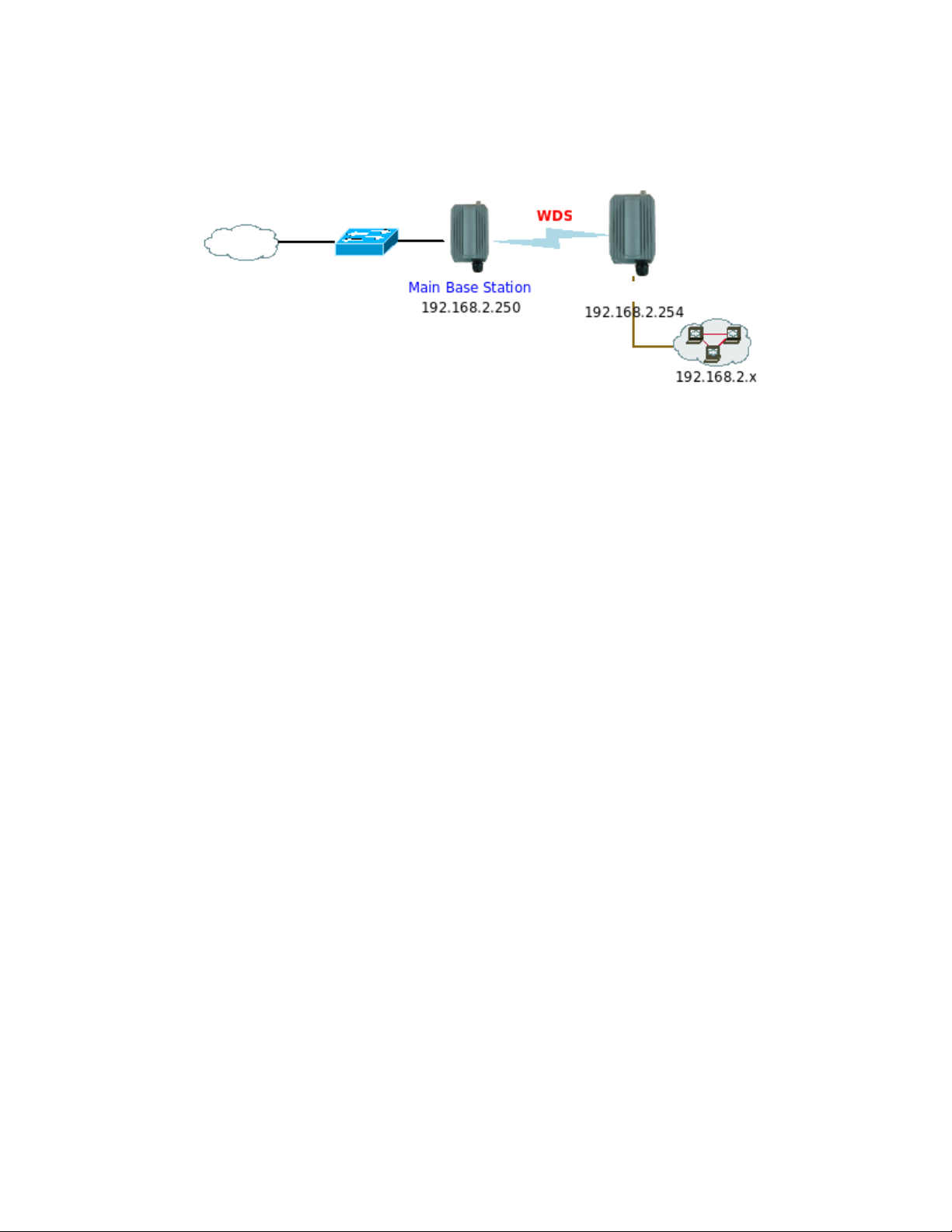
Î Example 2 : Point-to-Multi-Point
APO1000/APO1010
Î Example 3 : Multi-Point Repeating bridge
APO1000/APO1010
Configuration in CPE Mode
It can be used as an Outdoor Customer Premises Equipment (CPE) to receive wireless signal over last mile application ,
helping WISPs deliver wireless broadband Internet service to residents and business cu stomers. In the CPE mode,
APO1000/APO1010 is a gateway enabled with NAT and DHCP Server functions. The wired clients connected to
APO1000/APO1010 are in different subnet from those connected to Main Base Station, and, in CPE mode, it does not
accept wireless association from wireless clients.
APO1000/APO1010
6
Page 12
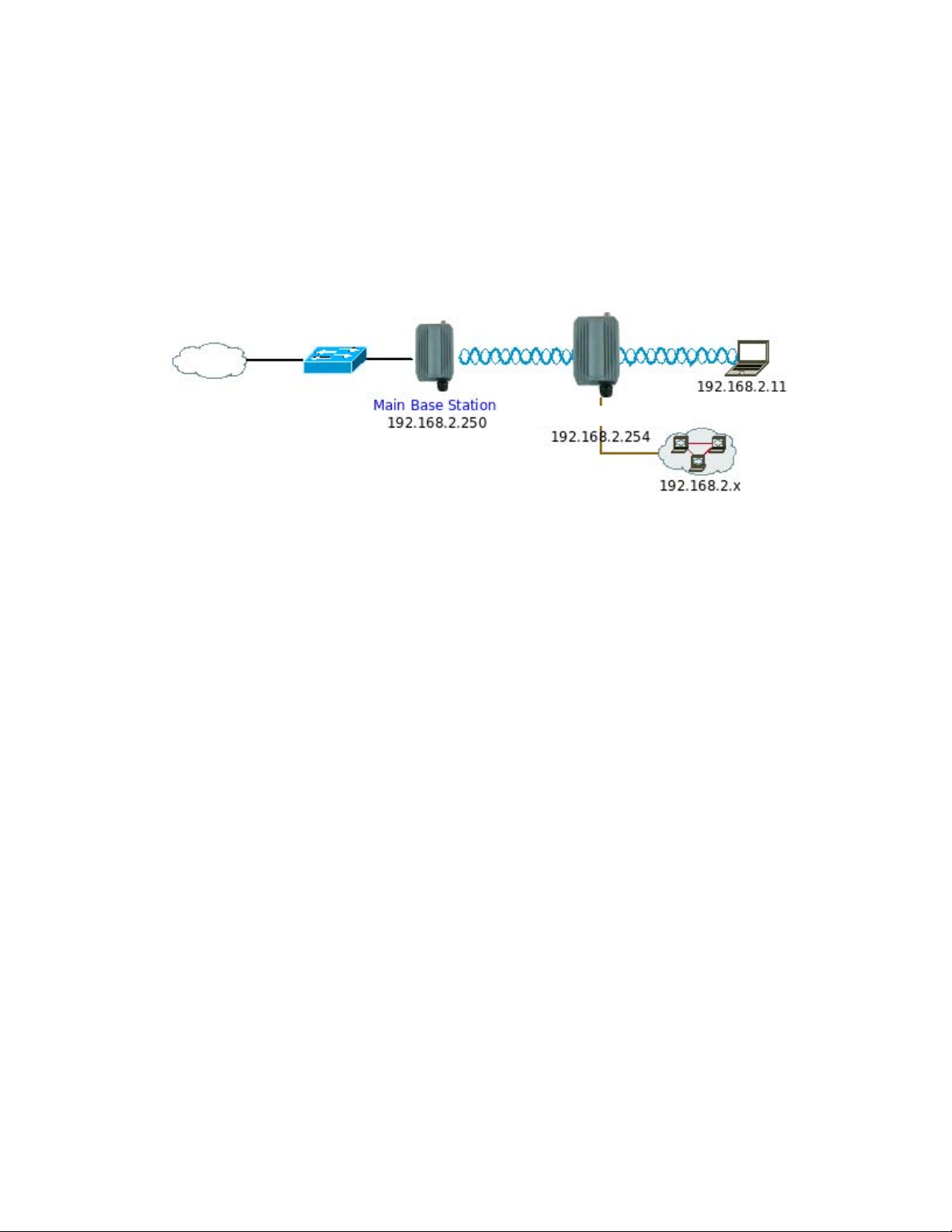
Configuration in Client Bridge + Universal Repeater Mode
It can be used as an Client Bridge + Universal Repeater to receive wireless signal over last mile applications, helping
WISPs deliver wireless broadband Internet service to new residential and business customers. In this mod e,
APO1000/APO1010 is enabled with DHCP Server functions. The wired clients of APO1000/APO1010 are in the same
subnet from Main Base Station and it accepts wireless connections from client devices.
APO1000/APO1010
7
Page 13

1.4 Product Benefit
500mW at 2.4Ghz Output Power
Topology : Point to Point ; Point to Multi Point
Operation Modes :
Î Access Point Mode : Pure Access Point Function and Access Point /Bridge(WDS) Function
Î WDS Mode
Î CPE Mode (Router Client )
Î Client Bridge + Universal Repeater Mode
Security with WEP, WPA/WPA2-PSK, and WPA/WPA2-RADIUS
Over load current protection
Integrated Power over Ethernet (PoE)
8 Multiple B-SSID capability
Business-class security and central management
Weather-Proof Housing
VLAN tag over WDS
Client Isolation through Layer 2 VLAN technology
Two administrator accounts for manager authorities
APO1000/APO1010 outdoor high power WiFi Bridge is the point of connection to Wireless Outdoor Network for service
provider deploying last mile services to business or residential broadband subscribers.. Network administrators can create
multiple subscriber service tier using per-subscriber rate limiting features, and manage centrally. APO1000/APO1010 outdoor
bridge utilizes a 500mW output Tx Power to connect to the WiFi mesh or WDS infrastructure and provides the subscriber with
an Ethernet connection for a local access.
APO1000/APO1010 outdoor high power Bridge support s four operational mode s, the AP mode, the WDS mode, the CPE
mode and the Client Bridge + Universal Repeater mode, respectively with built-in remote management features.
8
Page 14

1.5 Specification
Wireless Architecture Mode
Î AP Mode
9 Pure AP Mode
• It can be deployed as a tradition fixed wireless Access Point
• It allow wireless clients or Stations(STA ) to access
9 AP/WDS Mode
• This enables the wireless interconnection of Access Point in an IEEE802.11 network .and accept wireless
clients at the same time
Î WDS Mode
9 This enables the wireless interconnection of Access Point in an IEEE802.11 n etwork.
9 It allows a wireless network to be expanded using multiple access point without the need for a wired backbone
to link them.
9 This also be referred to as repeater mode.
9 It can’t allow wireless clients or Stations (STA) to associate.
Î CPE Mode
9 WiFi connection as WAN , in CPE mode , the device run as DHCP server to assign IP address to clients out of a
private IP address pool behind a NAT
Î Client Bridge + Universal RepeaterMode
9 A wireless repeater and bridge with DHCP server enabled, clients on the same subnet as host AP(Primary
Router).
6. Networking
Î Support Static IP, Dynamic IP(DHCP Client) and PPPoE on WiFi WAN Connection
Î Support PPTP/L2TP/IP Sec Pass Through
Î PPPoE Reconnect – Always On , On demand, Manual
Î MAC Cloning
Î DHCP Server
Î 802.3 Bridging
Î Masquerading (NAT)
Î Proxy DNS
Î Dynamic DNS
Î NTP Client
Î Virtual DMZ
Î Virtual Server (IP / Port Forwarding)
9
Page 15

Î Support MAC Filter
Î Support IP Filter
Î Bandwidth traf fic Shaping
7. Wireless Feature
Î Transmission power control : 9 Levels
Î Channel selection : Manual or Auto
Î No of associated clients per AP : 32
Î Setting for max no associated clients : Yes
Î No. of ESSID (Virtual AP) : 8
Î No. of Max. WDS setting : 8
Î Preamble setting : Short/ Long
Î Setting for 802.11b/g mix, 802.11b only or 802.11g only
Î Setting for transmission speed
Î Dynamic Wireless re-transmission
Î IEEE802.11f IAPP (Inter Access Point Protocol), hand over users to another AP
Î IEEE 802.11i Preauth (PMKSA Cache )
Î IEEE 802.11h -Transmission Power Control
Î IEEE 802.11d -Multi country roaming
Authentication/ Encryption (Wireless Security)
Î Layer 2 User Isolation
Î Blocks client to client discovery within a specified VLAN
Î WEP 64/ 128/ 152 Bits
Î EAP-TLS + Dynamic WEP
Î EAP-TTLS + Dynamic WEP
Î PEAP/ MS-PEAP+Dynamic WEP
Î WPA (PSK +TKIP)
Î WPA (802.1x certification + TKIP)
Î 802.11i WPA2 (PSK + CCMP/ AES)
Î 802.11i WPA2 (802.1x certification + CCMP/ AES)
Î Setting for TKIP/ CCMP/ AES key’s refreshing period
Î Hidden ESSID support
Î Setting for “Deny ANY “ connection request
Î MAC Address filtering (MAC ACL)
10
Page 16

Î No. of registered RADIUS servers : 2
Î VLAN assignment on BSSID
Î Support VLAN tag over WDS
Quality of Service
Î DiffServ/ ToS
Î IEEE802.1p/ CoS
Î IEEE 802.1Q Tag VLAN priority control
Î IEEE802.11e WMM
System Administration
Î Intuitive Web Management Interface
Î Password Protected Access
Î Firmware upgrade via Web
Î Reset to Factory Defaults
Î Profiles Configuration Backup and Restore
Î Two administrator accounts
Î Remote Link Test
Î Full Statistics and Status Reporting
Î SNMP Traps to a list of IP Address
Î NTP T ime Synchronization
Î Even Log
Î Support SNMP v1,v2c, v3
Î Support MIB II
Î CLI access via Telnet and SSH
Î Administrative Access : HTTP/ HTTPS
Î UPnP (Universal Plug and Play)
11
Page 17
Chapter 2. Basic Installation
2.1 Hardware Installation
2.1.1 Package Contents
The standard package contents of APO1000/APO1010:
APO1000/APO1010 x 1
Quick Installation Guide x 1
CD-ROM (with User Manual and QIG) x 1
PSE with AC Cable x 1
Mounting Kit x 1
It is highly recommended to use all the supplies in the package instead of substit uting any components by other
suppliers to guarantee best performance.
12
Page 18

2.1.2 Panel Function Descriptions
¾ APO1000
Front Panel Rear Panel
1. Reset Button : System reboot button press until LED flashed and rel ease for system reboot or for reset
to factory default press, LED flashes keep pressing until LED becom es static
2. Power : Red LED ON indicates power on, and OFF indicates power off
3. Signal Strength : Yellow LED ON indicates Low Signal (CPE Mode)
4. Signal Strength : Green LED ON indicates Normal Signal (CPE Mode) or (WDS Mode only)
5. Signal Strength : Green LED ON indicates High Signal (CPE Mode) or (AP Mode only)
6. WLAN : Green LED BLINKING indicates Wireless ON, and BL INKING quickly indicates Wireless
Transmit quickly.
7. Ethernet : Green LED ON indicates connection, OFF indicates no connection
8. PoE Connector : For connecting to PSE
9. N-Type Conn ector : For connecting to N-Ty pe antenna
In CPE Mode, the LED 3 ON indicates the signal Low ( Signal <= 10 RSSI); the LED 3 and 4 ON indicate the
signal Normal (10 < Signal <=40 RSSI); the LED 3, 4 and 5 ON indicate the signal High ( Signal > 40 ).
Only LED 4 ON indicates the operating mode is WDS Mode; only LED 5 ON indicates the operating mode is
AP Mode.
13
Page 19

¾ APO1010
Front Panel Rear Panel
1. Reset Button : System reboot button press until LED flashed and rel ease for system reboot or for reset
to factory default press, LED flashes keep pressing until LED becom es static
2. Power : Red LED ON indicates power on, and OFF indicates power off
3. Signal Strength : Yellow LED ON indicates Low Signal (CPE Mode)
4. Signal Strength : Green LED ON indicates Normal Signal (CPE Mode) or (WDS Mode only)
5. Signal Strength : Green LED ON indicates High Signal (CPE Mode) or (AP Mode only)
6. WLAN : Green LED BLINKING indicates Wireless ON, and BL INKING quickly indicates Wireless
Transmit quickly.
7. Ethernet : Green LED ON indicates connection, OFF indicates no connection
8. PoE Connector : For connecting to PSE
In CPE Mode, the LED 3 ON indicates the signal Low ( Signal <= 10 RSSI); the LED 3 and 4 ON indicate the
signal Normal (10 < Signal <=40 RSSI); the LED 3, 4 and 5 ON indicate the signal High ( Signal > 40 ).
Only LED 4 ON indicates the operating mode is WDS Mode; only LED 5 ON indicates the operating mode is
AP Mode.
14
Page 20
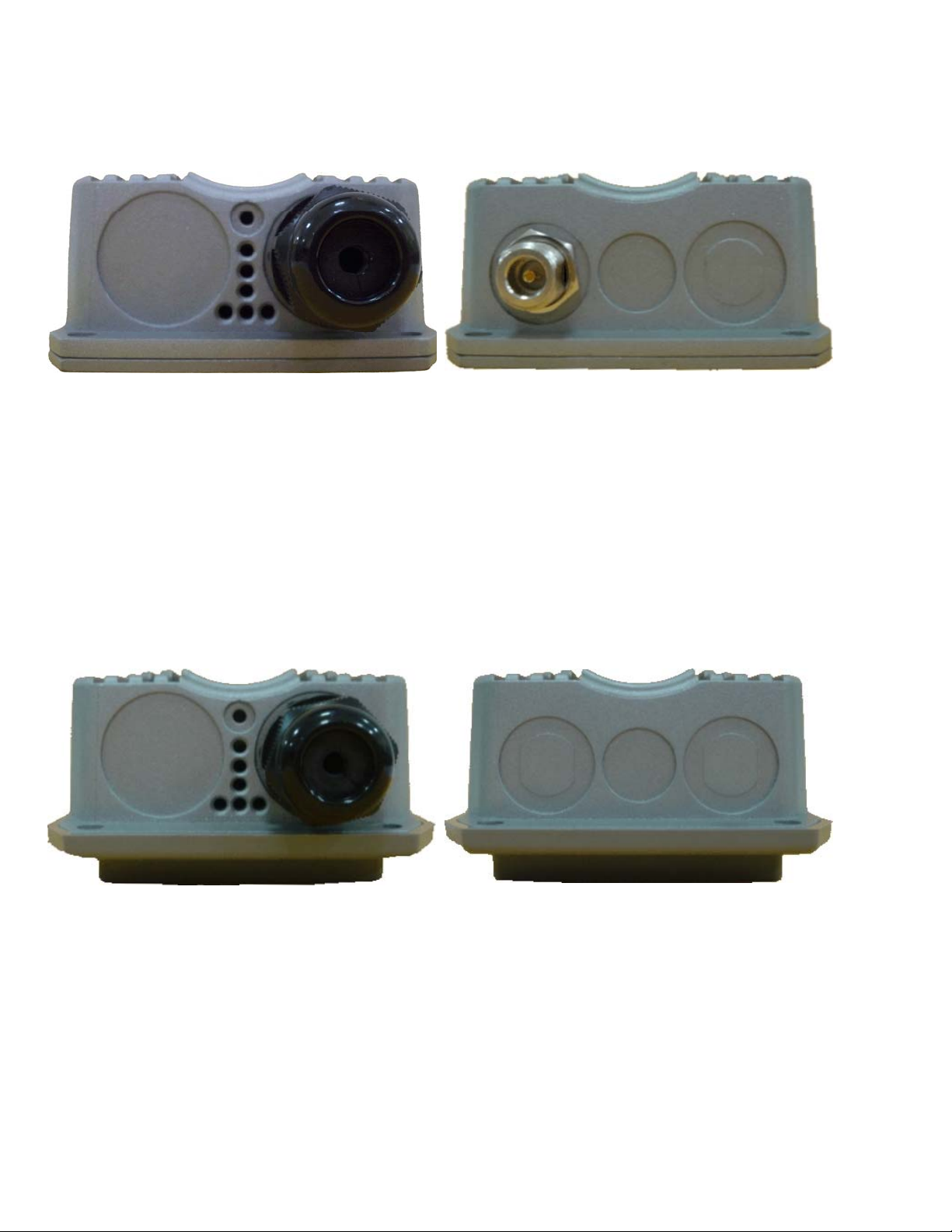
2.1.3 Hardware Installation Steps
Please follow the steps mentioned below to install the hardwa re of APO1000/APO1010:
¾ APO1000
Front Panel Rear Panel
Î Connect N-type antenna to the N-type connector on the rear panel.
Î Connect Power Injector to the PoE connector on the front panel.
Î Connect an Ethernet cable to the Power Injector and the other end to a computer.
Î Source power to Power Injector in order to supply power to APO1000.
¾ APO1010
Front Panel Rear Panel
Î Connect Power Injector to the PoE connector on the front panel.
Î Connect an Ethernet cable to the Power Injector and the other end to a computer.
Î Source power to Power Injector in order to supply power to APO1010.
15
Page 21
2.2 Web Management Interface Instructions
APO1000/APO1010 supports web-based config uration. Upon the completion of hardware installation, APO1000/APO1010
can be configured through a COMPUTER by using its web browser such as Internet Explorer or Mozilla Firefox.
1. Default IP Address : 192. 168.2.254
2. Default IP Netmask : 255.255.255.0
3. Default User Name and Password :
The default user name and password for both root manager account and admin manager account are as follows:
Mode CPE Mode AP Mode WDS Mode
Management Account
User Name
Password
Root
Account
root admin root root root
default admin default default default
Admin
Account
Root
Account
Root
Account
Client Bridge +
Universal Repeater Mode
Root
Account
Step
IP Segment Set-up for Administrator's Computer
Set the IP segment of the administrator's computer to be in the same range as APO1000/APO1010 for accessing the
system. Do not duplicate the IP Address used here with IP Address of APO1000/APO1010 or any other device within the
network
Example of Segment :
The valid range is 1 ~ 254 and 192.168.2.254 shall be avoided because it is already assigned to APO1000/APO1010.
192.168.2.10 is used in the example below.
Î IP Address : 192.168.2.10
Î IP Netmask : 255.255.255.0
Launch Web Browser
Launch web browser to access the web management interface of system by entering the default IP Address,
http://192.168.2.254
, in the URL field, and then press Enter.
System Login
16
Page 22
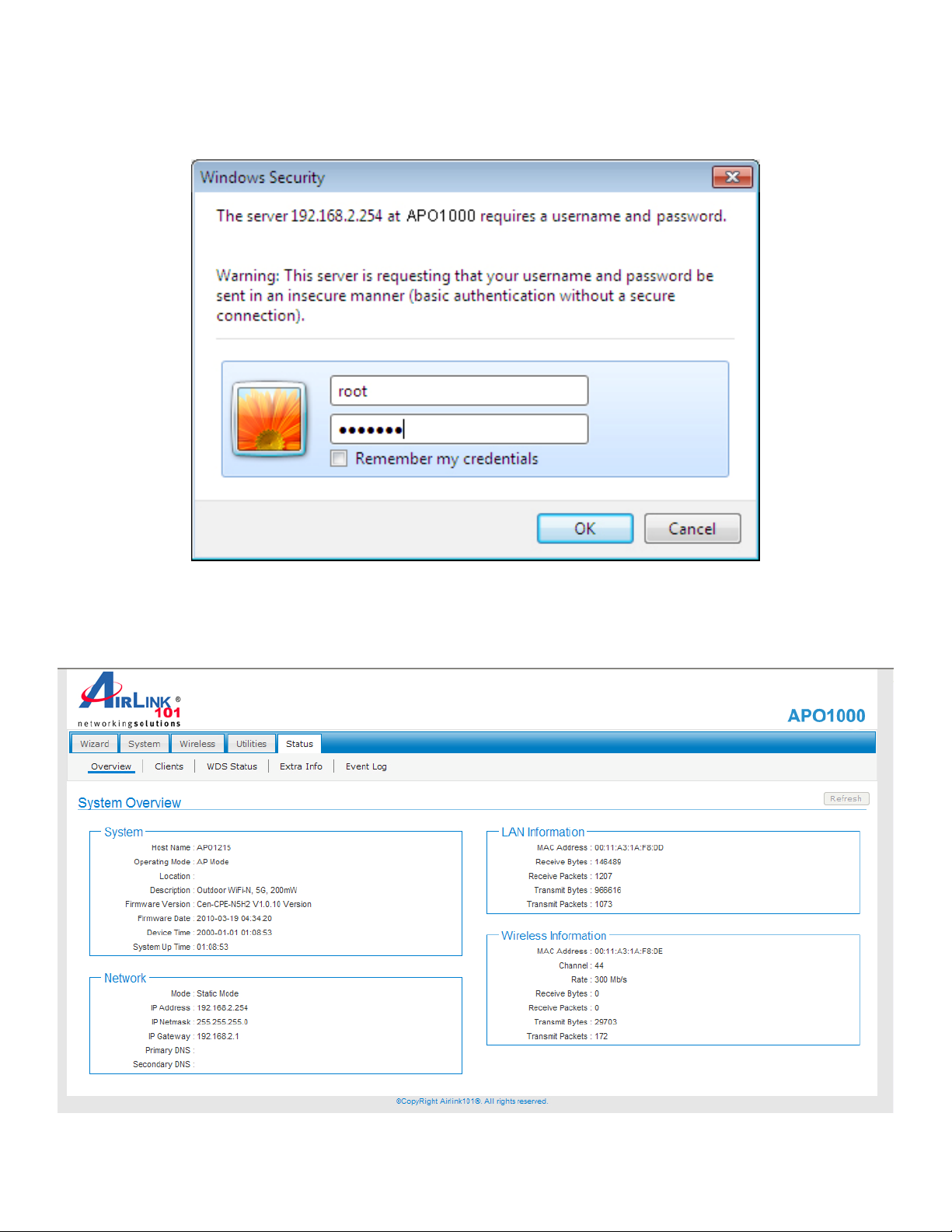
The network manager Login Page then appears.
Enter “root” for user name and “default” for password, and then click OK to login to the system; the root manager
account is used as an example here.
Login Success
System Overview page will appear after successful login.
17
Page 23
Chapter 3. AP Mode Configuration
When AP mode is chosen, the system can be configured as an Access Point. This section provides detailed explanation for
users to configure in the AP mode with help of illustrations. In the AP mode, functions listed in the table below are also
available from the Web-based GUI interface.
Option System Wireless Utilities Status
Operating Mode General Settings Profiles Settings System Overview
LAN Advanced Settings Firmware Upgrade Clients
Functions
Management Virtual AP Network Utility WDS List
Time Server WDS Setup Reboot Extra Info
SNMP Event Log
UPNP
Table 3-1: AP Mode Functions
3.1 External Network Connection
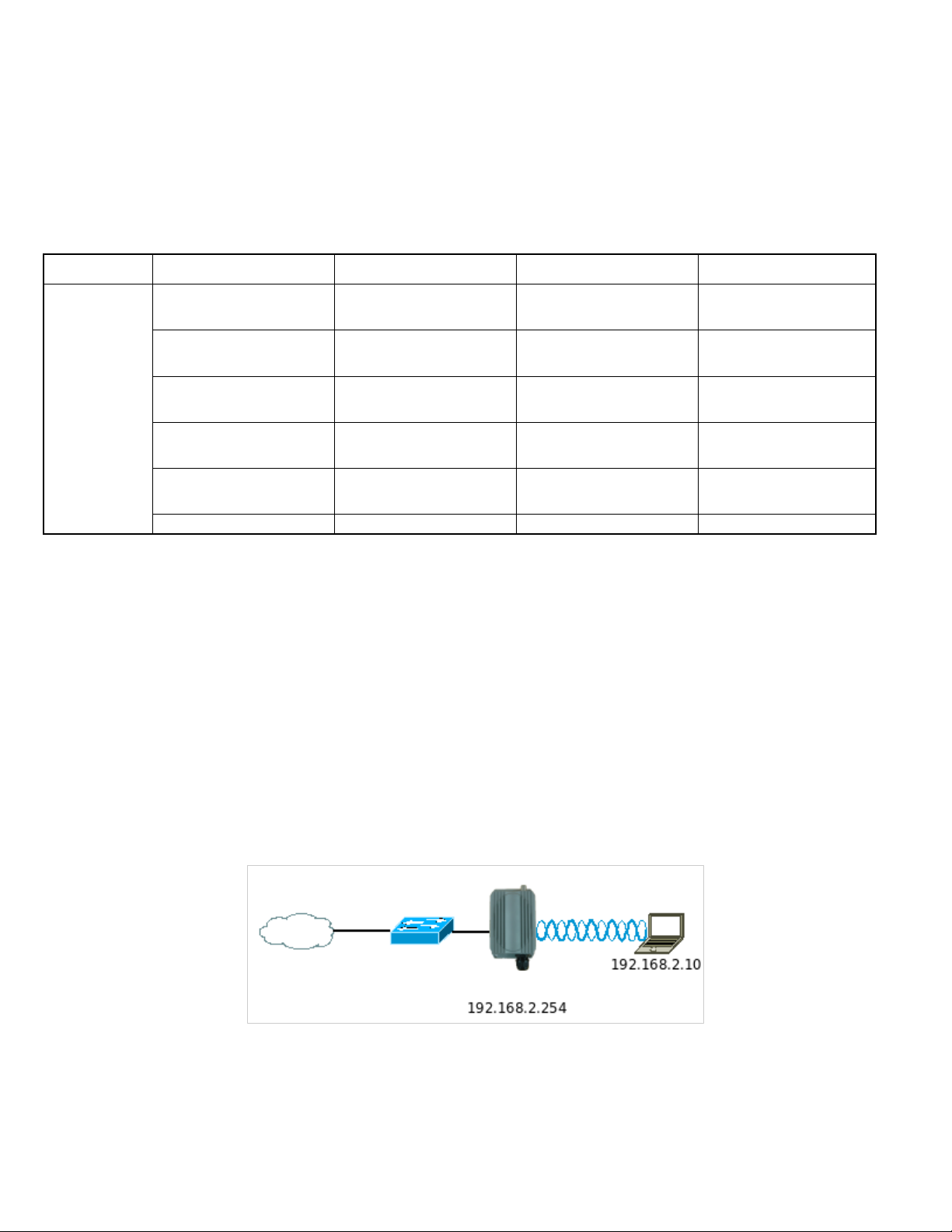
3.1.1 Network Requirement
Normally, APO1000/APO1010 connects to a wired LAN and provides a wireless con nection point to associate with wireless
client as shown in Figure 3-1. Then, Wireless clients could access to LAN or Internet by associating themselves with
APO1000/APO1010 set in AP mode.
Figure 3-1 Access Point on a Wired LAN Configuration
APO1000/APO1010
18
Page 24
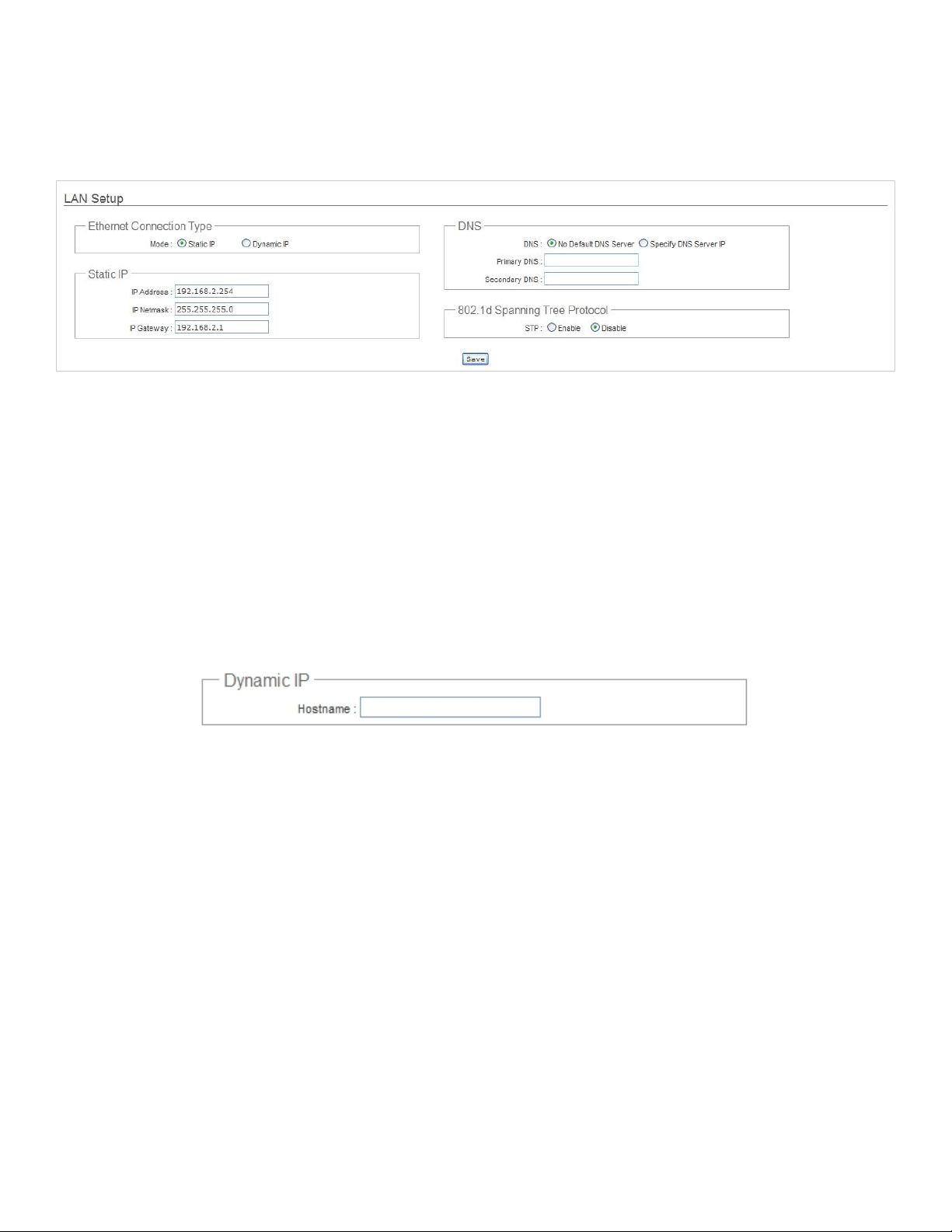
3.1.2 Configure LAN IP
Here are the instructions to setup the local IP Address and Netmask.
Please click on System -> LAN and follow the below setting.
Mode : Check either “Static IP” or “Dynamic IP” button as desired to set up the system IP of LAN port .
Î Static IP : The administrator can manually setup the LAN IP address when static IP is preferred.
9 IP Address : The IP address of the LAN port; default IP address is 192.168.1.254
9 IP Netmask : The Subnet mask of the LAN port; default Netmask is 255.255.255.0
9 IP Gateway : The default gateway of the LAN port; default Gateway is 192.168.1.1
Î Dynamic IP : This configuration type is applicable when the APO1000/APO1010 is connected to a network with
presence of a DHCP server. All related IP information will be provided by the DHCP server automatically.
9 Hostname : The Hostname of the LAN port
DNS : Check either “No Default DNS Server” or “Specify DNS Server IP” button as desired to set up the system DNS.
Î Primary : The IP address of the primary DNS server.
Î Secondary : The IP address of the secondary DNS server.
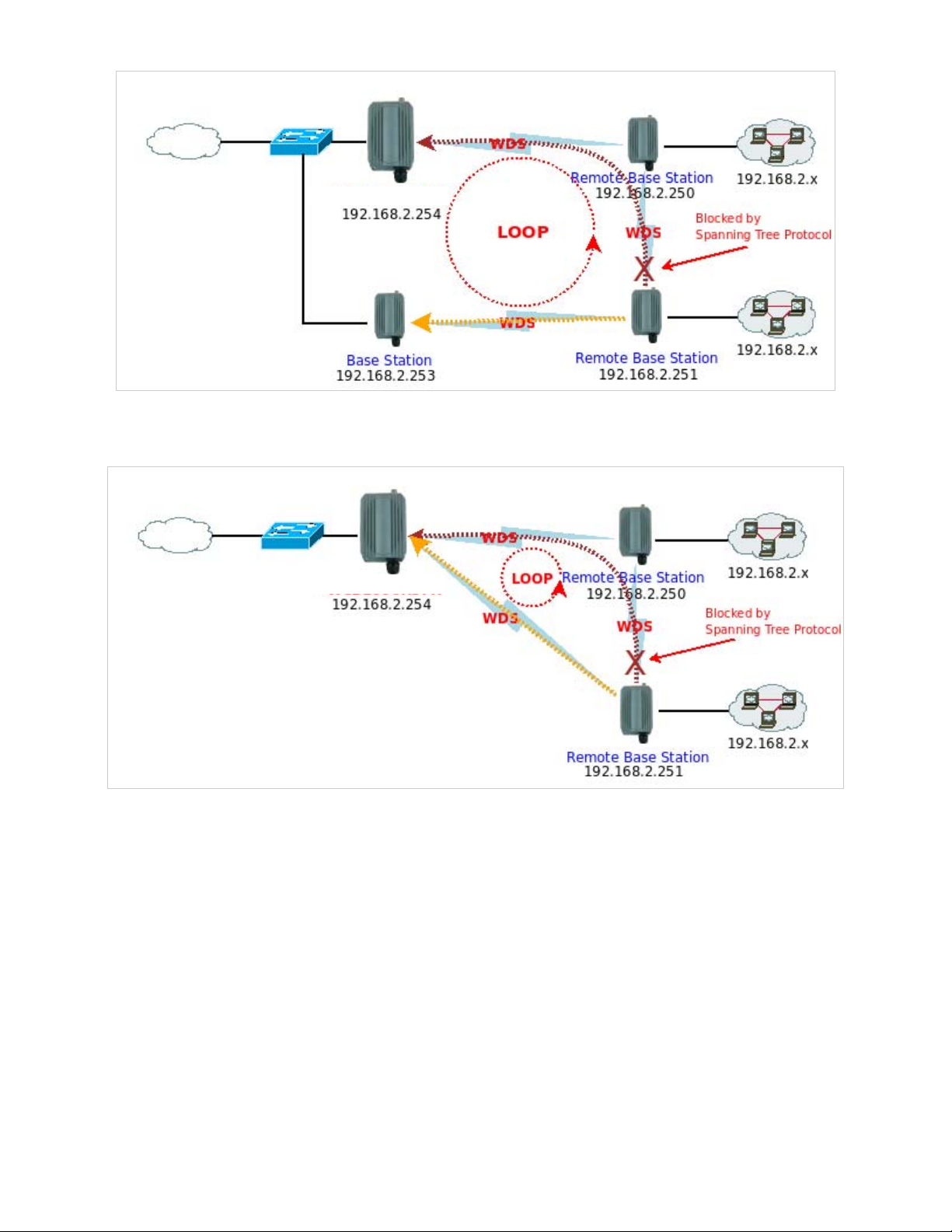
802.1d Spanning Tree
The spanning tree network protocol provides a loop free topology for a bridged LAN between LAN interface and 8 WDS
interfaces from wds0 to wds7. The Spanning Tree Protocol, which is also referred to as STP, is defined in the IEEE
Standard 802.1d.
19
Page 25
APO1000/APO1010
APO1000/APO1010
Click Save button to save your changes. Click Reboot button to activate your changes
20
Page 26
3.2 Wireless LAN Network Creation
The network manager can configure related wireless settings, General Settings, Advanced Settings, Virtual AP(VAP)
Setting, Security Settings, and MAC Filter Settings.
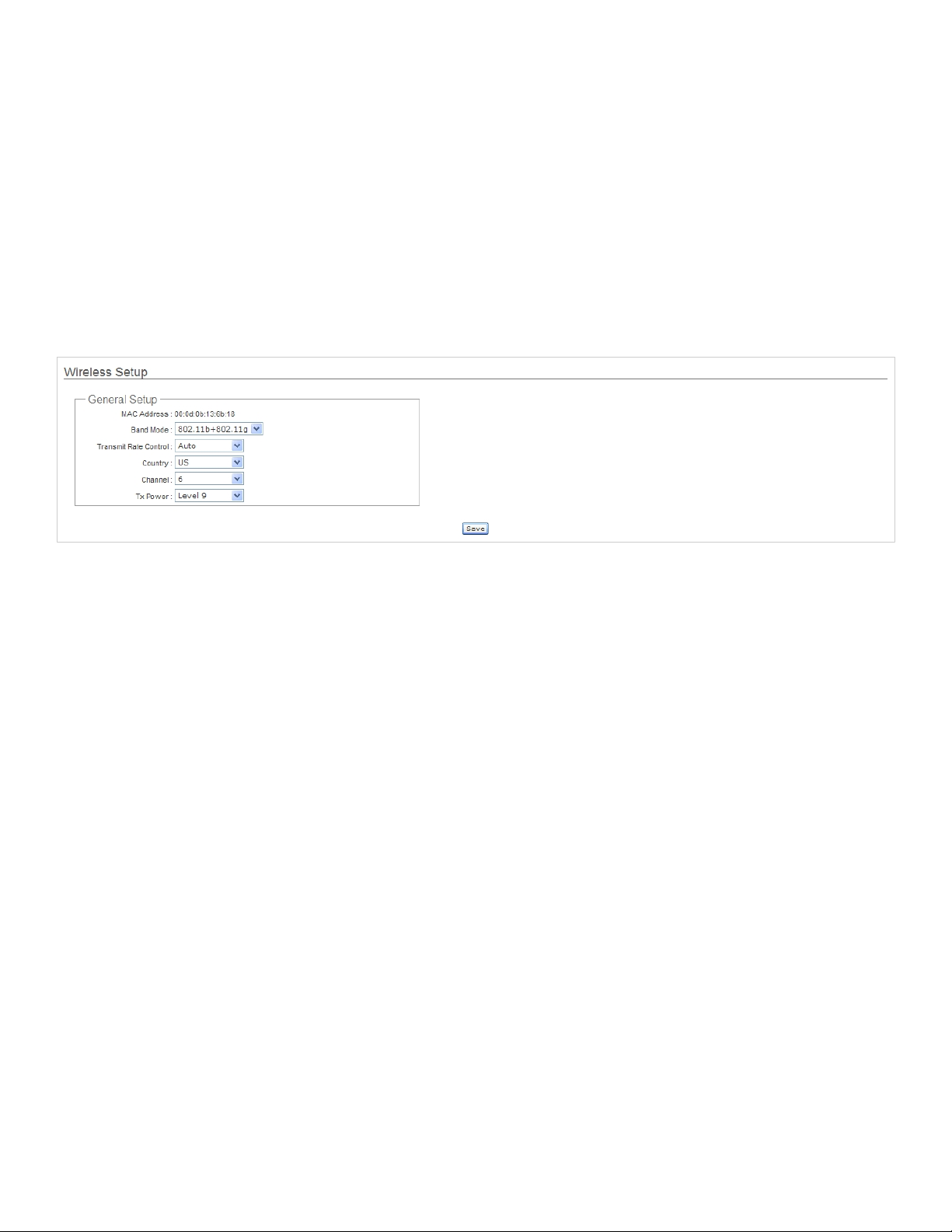
3.2.1 Wireless General Setup
The administrator can change the data transmission, channel and output power settings for the system. Please click on
Wireless -> General Setup and follow the below setting.
MAC address : The MAC address of the Wireless interface is displayed here.
Band Mode : Select an appropriate wireless band; bands available are 801.11b, 802.1 1g and 802.11b+802.11g.
Transmit Rate Control : Select the desired rate from the drop-down list; the options are auto or ranging from 1 to
54Mbps for the 802.11g and 802.11b/g modes, or 1 to 11Mbps for the 802.11b mode.
Country : Select the desired Country code from the drop-down list; the options are US, ETSI or Japan.
Channel : The channel range will be changed by selecting different country code. The channel range from 1 to 11 for US
country code, or 1 to 13 for ETSI country code, or 1 to 14 for JP country code.
Tx Power : You can adjust the output power of the system to get the appropriate coverage for your wireless network.
Select the LEVEL 1 to LEVEL 9 that you need for your environment. If you are not sure from which setting to choose,
then use the default LEVEL 9 setting.
Click Save button to save your changes. Click Reboot button to activate your changes. The items in this page are for AP's RF
general settings and will be applied to all VAPs.
21
Page 27
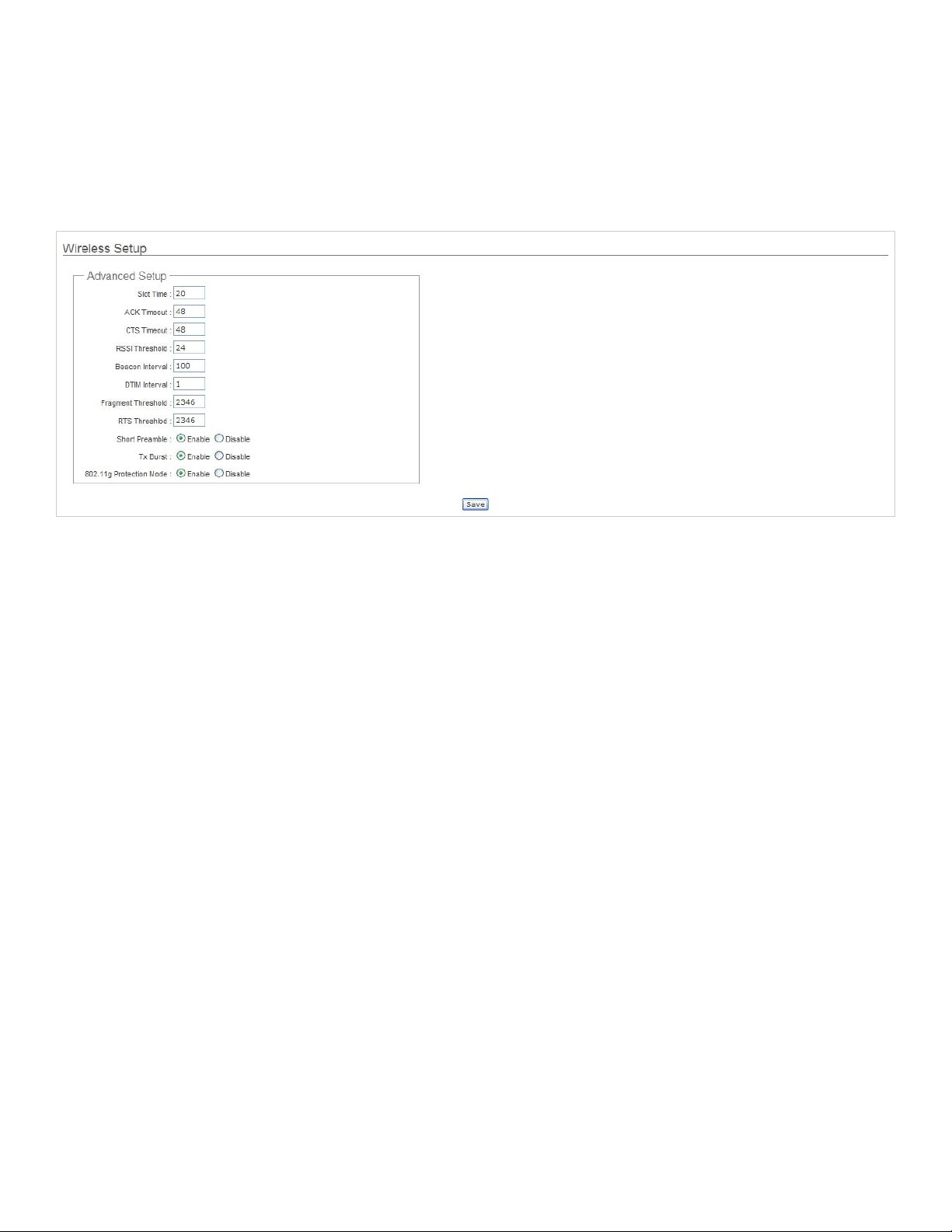
3.2.2 Wireless Advanced Setup
To achieve optimal wireless performance, it is necessary to tweak advance setting per requirements properly, not necessary
higher the better or lower.
The administrator can change the RTS threshold and fragmentation threshold settings for the system. Please click on
Wireless -> Advanced Setup and follow the below setting.
Slot Time : Slot time is in the range of 1~1489 and set in unit of microsecond. The default value is 20 microsecond.
Slot time is the amount of time a device waits after a collision before retransmitting a p acket. Reducing the slot time
decreases the overall back-off, which increases throughput. Back-off, which is a multiple of the slot time, is the random
length of time a station waits before sending a packet on the LAN. For a sender and receiver own right of the channel the
shorter slot time help manage shorter wait time to re-transmit from collision because of hidden wireless clients or other
causes. When collision sources can be removed soo ner and other send ers attempting to send are listening the
channel(CSMA/CA) the owner of the channel should continue ownership and finish their transmission and relea se the
channel. Then, following ownership of the channel will be sooner for the new pair due to shorter slot time. However, when
long duration of existing collision sources and shorter slot time exist the owners might experience subsequent collisions.
When adjustment to longer slot time can’t improve performance then RTS/CTS could supplement and help improve
performance.
ACK Timeout : ACK timeout is in the range of 1~372 and set in unit of microsecond. The default value is 48
microsecond.
All data transmission in 802.11b/g request an “Acknowledgement” (ACK) send by receiving radio. The transmitter will
resend the original packet if correspondent ACK failed to arrive within specific time interval, also refer to as “ACK
Timeout”.
ACK Timeout is adju stable due to the fact that distance between two radio links may vary in different deployment. ACK
Timeout makes significant influence in performance of long distance radio link. If ACK T i meout is set too short, transmitter
will start to “Resend” packet before ACK is received, and throughputs become low due to excessively high retransmission.
ACK Timeout is best dete rmined by distance between the radios, data rate of average environment. The Timeout value is
calculated based on round-trip time of packet with a little tolerance, So, if experiencing re-transmissions or p oor
22
Page 28
performance the ACK Timeout could be made longer to accommodate.
RTS/CTS
Adjustment of RTS Threshold can be done to turn on RTS. CTS Timeout will take effect only when RTS is turned on.
Unlike wired Ethernet, radio transmission may begin with a RTS (Request to Send) frame, and receiver re sponds with a CTS
(Clear to Send) frame. The RTS/CTS mech anism is called Channel Cleaning, all stations that received CTS will back off for
certain period of time, multiple of the slot time.
Each CTS packet has a NAV (Network Allocation Vector) number n, the channel is reserved for sender and receiver for
additional n-millisecond. The NAV guarantees the channel is free of interference in next n-millisecond. The last packet of ACK
will set NAV to zero, indicated that connection is done and free the channel to others.
CTS Timeout : CTS Timeout is in the range of 1~744 and set in unit of microsecond. The default value is 48
microsecond.
CTS Timeout will take effect only when RTS is turned on. Adjustment of RTS Threshold can be done to turn on RTS.
When hidden wireless stations are present in the wireless network RTS can be considered to turn on to minimize
collisions and increase performance. Ensure CTS timeout is long enough to avoid frequent re-transmission of RTS.
Slot Time and ACK/CTS Timeout settings for long distance links. It is important to tweak settings to achieve the
optimal result based on requirement.
RSSI Threshold : RSSI Threshold is in the range of -128~127.The default value is 24.
RSSI is defined as Received Signal Strength Indication, when the received signal strength from peer is below this
threshold, the peer will be consider as disconnected. Set the threshold higher will make roaming happen earlier, set lower
will allow weak signal peer to connect. In normal situation, the longer distance the lower signal strength will be sensed
between peers people could consider to lower RSSI threshold to have bigger coverage from the AP or AP client
perspective. If it doesn’t work well then people could consider to jack up RSSI threshold to have stable smaller coverage
and leave AP clients in longer distance to associate with closer AP.
Beacon Interval : Beacon Interval is in the range of 1~5000 and set in unit of millisecond. The default value is 100
msec.
Access Point (AP) in IEEE 802.11 will send out a special approximated 50-byte frame, called “Beacon”. Beacon is
broadcast to all the stations, provides the basic information of AP such as SSID, channel, encryption keys, signal
strength, time stamp, support data rate.
All the radio stations received beacon recognizes the existence of such AP, and may proceed next actions if the
information from AP matches the requirement. Beacon is sent on a periodic basis, the time interval can be adjusted.
By increasing the beacon interval, you can reduce the number of beacons and associated overhead, but that will likely
delay the association and roaming process because stations scanning for available access points may miss the beacons.
You can decrease the beacon interval, which increases the rate of beacons. This will make the association and roaming
process very responsive; however, the network will incur additional overhead and throughput will go down.
23
Page 29

DTIM Interval : The DTIM interval is in the range of 1~15. The default is 15.
DTIM is defined as Delivery Traffic Indication Message. It is used to notify the wireless stations, which support power
saving mode, when to wake up to receive multicast frame. DTIM is necessary and critical in wireless environment as a
mechanism to fulfill power-saving synchronization.
A DTIM interval is a count of the number of beacon frames that must occur before the access point sends the buffered
multicast frames. For instance, if DTIM Interval is set to 3, then the Wi-Fi clients will expect to receive a multicast frame
after receiving three Beacon frame. The higher DTIM interval will help power saving and possibly decrease wireless
throughput in multicast applications.
Fragment Threshold : The Fragment Threshold is in the range of 256~2346 byte. The default is 2346 byte.
Each Wi-Fi packet can be divided into smaller packets, marked with a sequential fragment number and re-assemble in
the receiving ends. The purpose is to make a short frame, instead of long frame, transmitting by radio in a heavy noisy
environment. Because of sending smaller frames, corruptions are much less likely to occur. The pros is obvious, the cons
is the overhead for transmission. So, in a clean environment, higher fragment threshold can be an option to increase
throughput.
Fragmentation will be triggered by setting the Fragment Threshold, usually in Byte-length. Only when the frame size is
over the Threshold, fragmentation will take place automatically.
RTS Threshold : RTS Threshold is in the range of 1~2346 byte. The default is 2346 byte.
The main purpose of enabling RTS by changing RTS threshold is to reduce possible collisions due to hidden wireless
clients. RTS in AP will be enabled automatically if the packet size is larger than the Threshold value. By default, RTS is
disabled in a normal environment supports non-jumbo frames.
Short Preamble : By default, it’s “Enable”. To Disable is to use Long 128-bit Preamble Synchronization field.
The preamble is used to signal "here is a train of data coming" to the receiver. The short preamble provides 72-bit
Synchronization field to improve WLAN transmission efficiency with less overhead.
Tx Burst : By default, it’s “Enable”. To Disable is to deactivate Tx Burst.
With TX burst enabled, AP will send many packets in a burst, without collision detection and RTS/CTS for each packet.
TX Burst have better throughput but cause interference with other APs in channel.
802.11g Protection Mode : By default, it’s “Enable”. To Disable is to deactivate 802.11g Protection Mode.
Protection mode use RTS/CTS to prevent interference with other APs and 802.11b peers, and disabling it will save
transmission time used by RTS/CTS. RTS/CTS threshold is effective only when 802.11g protection mode is made
enable.
Click Save button to save your changes. Click Reboot button to activate your changes. The items in this page are for AP's RF
advanced settings and will be applied to all VAPs.
24
Page 30
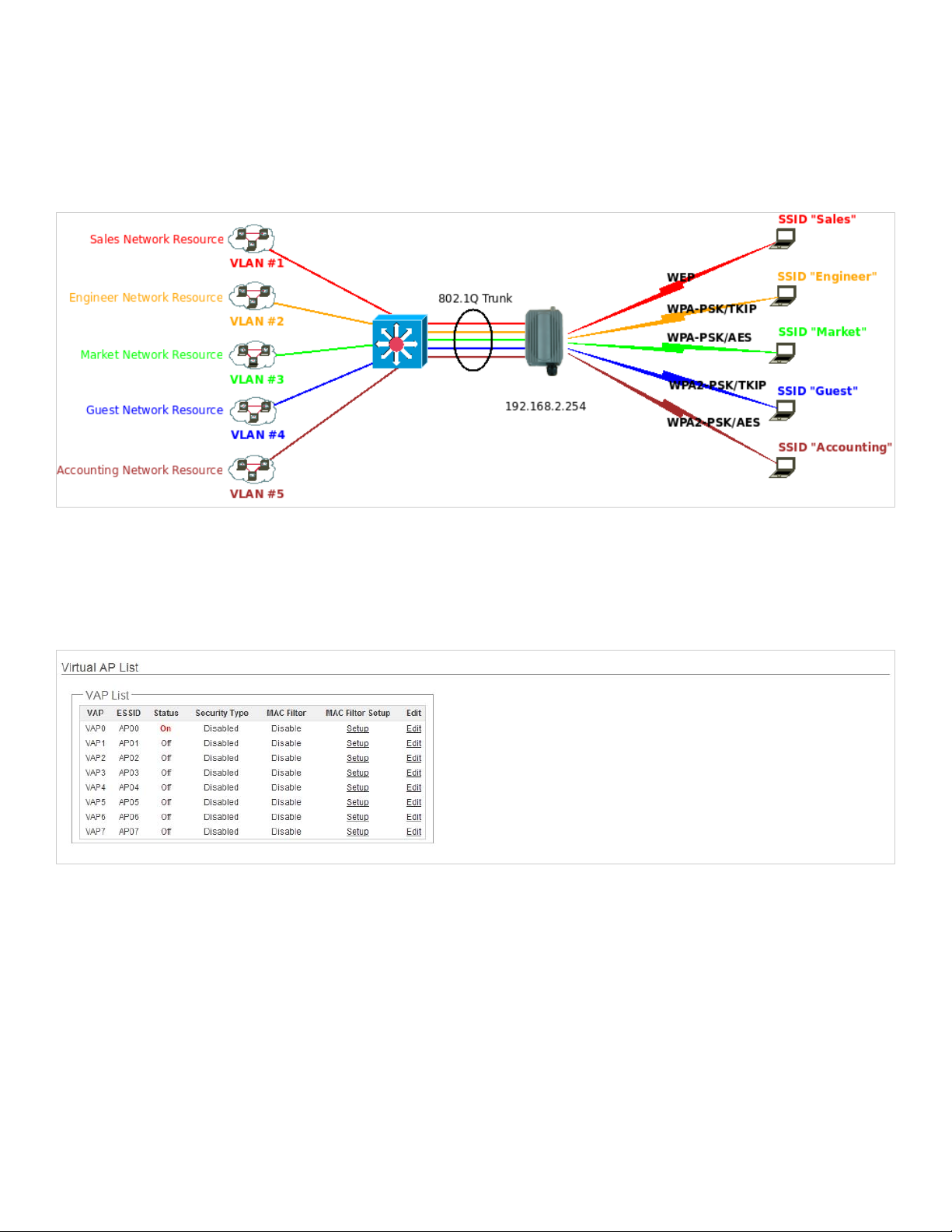
3.2.3 Create Virtual AP(VAP)
The APO1000/APO1010 support broadcasting multiple SSIDs, allowing the creation of Virtual Access Points, partitioning a
single physical access point into 8 logical access points, ea ch of which can have a different set of security, VLAN t ag(ID) and
network settings. Figure 3-2 shows multiple SSIDs with different security type and VLAN settings.
APO1000/APO1010
Figure 3-2 Multiple SSIDs with different Security Type and VLAN Tag
3.2.3.1 Virtual AP Overview
The administrator can view all of the Virtual AP's settings via this page.
Please click on Wireless -> Virtual AP Setup and the Virtual AP Overview Page appears.
VAP : Indicate the system's available Virtual AP
ESSID : Indicate the ESSID of the respective Virtual AP
Status : Indicate the Status of the respective Virtual AP. The VAP0 always On
Security Type : Indicate an used security type of the respective Virtual AP
MAC Filter : Indicate an used MAC filter of the respective Virtual AP
MAC Filter Setup : Click “Setup” button to configure Virtual AP's MAC filter.
VAP Edit : Click “Edit” button to configure Virtual AP's settings, including security type.
25
Page 31

3.2.3.2 Virtual AP Setup
For each Virtual AP, administrators can configure SSID, VLAN ID(Tag), SSID broadcasting, Maximum number of client
associations, security type settings.
Click Edit button on the VAP Edit column, and then a Virtual AP setup page appears.
ESSID : Extended Service Set ID, When clients are browsing for available wireless networks, this is the SSID that will
appear in the list. ESSID will determine the service type available to AP clients associated with the specified VAP.
Enable VAP : By default, it’s “Disable” for VAP1 ~ VAP7. The VAP0 always enabled.
Select “Enable” to activate VAP or click “Disable” to deactivate this function
Hidden SSID : By default, it’s “Disable”.
Enable this option to stop the SSID broadcast in your network. When disabled, people could easily obtain the SSID
information with the site survey software and get access to the network if security is not turned on. When enabled,
network security is enhanced. It’s suggested to enable it after AP security settings are archived and setting of AP clients
could make to associate to it.
Client Isolation : By default, it’s “Disable”.
Select “Enable”, all clients will be isolated from each other, which m eans they can’t reach each other.
WMM : By default, it’s “Disable”.
Select “Enable”, then packets with WMM QoS will take higher priority.
WMM prioritizes traffic according to four Access Categories (AC) - voice, video, best effort, and background. However, it
does not provide guaranteed throughput. Packets with QoS header including Diffserv/IP ToS and 802.1p will be mapped
into 4 Access Categories of WMM, packets without QoS header will be assigned to the Best Effort queue. Please refer to
the table below for mapping from 802.1p and ToS mapping to WMM:
Queue
Data Transmitted
Clients to AP
AC_BK Background.
IP
ToS
0x08
0x20
802.1P
Priority
Priority Description
1, 2 Low
AC_BE Best Effort 0, 3 Medium
AC_VI Video
0x28
0xa0
4, 5 High
High throughput. Bulk data that requires maximum
throughput and is not time-sensitive is sent to this queue
(FTP data, for example).
Medium throughput and delay. Most traditional IP data is
sent to this queue
Minimum delay. Time-sensitive video data is automatically
sent to this queue
26
Page 32

0x30
AC_VO Voice
0xe0
0x88
6, 7 High
Time-sensitive data like VoIP and streaming media are
automatically sent to this queue
0xb8
IAPP Support : By default, it’s “Disable”.
Inter Access-Point Protocol is designed to enforce unique association throughout an ESS(Extended Service Set) and to
enforce secure exchange of station's security context between current access point (AP) and new AP during hand off
period.
IAPP supported only for WPA-PSK/WPA2-PSK, WPA-Enterprise/WPA2-Enterprise and 802.1X security type.
Maximum Clients : The default value is 32. You can enter the number of wireless clients that can associ ate to a
particular SSID. When the number of client is set to 5, only 5 clients at most are allowed to connect to this VAP.
VLAN ID(Tag) : By default, it’s selected “Disable”.
This system supports tagged Virtual LAN(VLAN). A valid number of 0 to 4094 can be entered after it’s enabled. If your
network utilize VLANs you could tie a VLAN ID to a specific SSID, and packets from/to wireless clients belonging to that
SSID will be tagged with that VLAN ID. This enables security of wireless applications by applying VLAN ID.
Security Type : Select the desired security type from the drop-down list; the options are Disable, WEP, WPA-PSK,
WPA2-PSK, WPA-Enterprise, WPA2-Enterprise and WEP 802.1X.
Î Disable : Data are unencrypted during transmission when this option is selected.
Î WEP : Wired Equivalent Privacy(WEP) is a dat a encryption mechanism based on a 64-bit, 128-bit or 152-bit shared
key.
9 Key Length : The available options are 64 bits, 128 bits or 152 bits.
9 WEP auth Method : Enable the desired option among Open system and Shared.
9 Key Index : key index is used to designate the WEP key during data transmission. 4 different WEP keys can be
entered at the same time, but only one is chosen.
9 WEP Key # : Enter HEX or ASCII format WEP key value; the system supports up to 4 sets of WEP keys.
27
Page 33

Key Length Hex ASCII
64-bit 10 characters 5 characters
128-bit 26 characters 13 characters
152-bit 32 characters 16 characters
Î WPA-PSK/WPA2-PSK : WPA or WPA2 Algorithms enable the sy stem to access the network by using the WPA-PSK
protected access.
9 Cipher Suite : By default, it is TKIP. Select either AES or TKIP cipher suites
9 Group Key Update Period : By default, it is 600 seconds. This time interval for rekeying GTK,
broadcast/multicast encryption keys, in seconds. Entering the time-length is required.
9 Master Key Update Period : By default, it is 83400 seconds. This time interval for rekeying GMK, master key to
generate GTKs, in seconds. Enter the time-length required.
9 Key Type : Select either ASCII or HEX format for the Pre-shared Key.
9 Pre-shared Key : Enter the pre-shared key; the format shall go with the selected key type.
Pre-shared key can be entered with either a 256-bit secret in 64 HEX digits format, or 8 to 63 ASCII characters.
Î WPA-Enterprise/WPA2-Enterprise: The RADIUS authentication and encryption will apply if either one is selected.
9 WPA General Settings :
• Cipher Suite : By default, it is TKIP. Select either AES or TKIP cipher suites
• Group Key Update Period : By default, it’s 600 seconds. This time interval for rekeying GTK,
broadcast/multicast encryption keys, in seconds. Entering the time-length is required.
• Master Key Update Period : By default, it’s 83400 seconds. This time interval for rekeying GMK, master
28
Page 34

key to generate GTKs, in seconds. Enter the time-length required.
• EAP Reauth Period :; By default, it’s 3600 seconds; 0 second is to disable EAP Re-authentication.
9 Main and secondary Authentication RADIUS Server Settings :
• Authentication Server : Enter the IP address of the Authentication RADIUS server.
• Port : By default, it’s 1812. The port number used to communicate with RADIUS server.
• Shared secret : A secret key used between system and RADIUS server. Supports 1 to 64 characters.
• Accounting Server : Enable or Disable accounting features in RADIUS server.
9 Main or Secondary Accounting RADIUS Server Settings :
• Accounting Server : Enter the IP address of the Accounting RADIUS server.
• Port : By default, it’s 1813. The port number used to communicate with RADIUS server.
• Shared Secret : A se cret key used between system and Accounting RADIUS server. Supports 1 to 64
characters.
Î WEP 802.1X : When WEP 802.1x Authentication is enabled, please refer to the following Dynamic WEP and
29
Page 35

RADIUS settings to complete configuration.
9 Dynamic WEP Settings :
• W
E
P Key length : The available options are 64 bits or 128 bits. The system will automatically generate WEP
encryption keys.
• WEP Key Update Period : By default, it’s 300 seconds; 0 not to rekey.
• EAP Reauth Period : By default, it’s 3600 seconds; 0 second is to disable EAP Re-authentication.
9 Main and Secondary Authentication RADIUS Server Settings :
• Authentication Server : Enter the IP address of the Authentication RADIUS server.
• Port : By default, it’s 1812. The port number used to communicate with RADIUS server.
• Shared secret : A secret key used between system and RADIUS server. Supports 1 to 64 characters.
• Accounting Server : Enable or Disable accounting features in RADIUS server.
9 Main and secondary Accounting RADIUS Server Settings :
30
Page 36

• Accounting Server : Enter the IP address of the Accounting RADIUS server.
• Port : By default, it’s 1813. The port number used to communicate with RADIUS server.
• Shared Secret : A secret key used between system and Accounting RADIUS server. Supports 1 to 64
characters.
Click Save button to save your changes. Click Reboot button to activate your changes
31
Page 37

3.2.4 MAC Filter Setup
Continued from the 3.2.3.1 Virtual AP Overview section, Click Setup button on the MAC Filter Setup column, and then a
Virtual AP MAC Filter setup page appears. The administrator can allow or reject clients to access each Virtual AP.
MAC Filter Setup : By default, it’s “Disable”. Options are Disabled, Only Deny List MAC or Only Allow List MAC.
Click Save button to save your change.
Two ways to set the MAC filter rules :
Î Only Allow List MAC.
The wireless clients in the MAC Filter List will be allowed to access to Access Point; All others will be denied.
Î Only Deny List MAC.
The wireless clients in the MAC Filter List will be denied to access to Access Point; All others will be allowed.
MAC Address : Enter MAC address (e.g. aa:bb:cc:00:00:0a) and click “Add” button, then the MAC address should
display in the MAC Filter List.
There are a maximum of 20 clients allowed in this MAC Filter List. The MAC addresses of the wireless clients can be added
and removed to the list using the Add and Delete buttons.
Click Reboot button to activate your changes
MAC Access Control is the weakest security ap proach. WPA or WPA2 security method is highly recommended.
32
Page 38

3.3 Wireless Network Expansion
The administrator could create WDS Links to expand wireless network. When WDS is enabled, access point functions as a
wireless bridge and is able to communicate with other access points via WDS links. A WDS link is bidirectional and both
side must support WDS. Access points know each other by MAC Address. In other words, each access point needs
to include MAC address of its peer. Ensure all access points are configured with the same channel and own same
security type settings.
Figure 3-3 shows Point to Multiple Points with different VLAN settings
APO1000/APO1010
Figure 3-3 Point to Multiple Points with different VLAN Tag
Please click on Wireless -> WDS Setup and follow the below setting.
Note that VLAN ID in the WDS MAC List setting will only be tagged to egress packets on the wired Ethernet port.
Ensure to match VLAN ID used on the network of the peer. WDS link won’t carry tags at all.
WMM : By default, it’s “Disable”.
Select “Enable”, then packets with WMM QoS will take higher priority.
33
Page 39

WMM prioritizes traffic according to four Access Categories (AC) - voice, video, best effort, and background. However, it
does not provide guaranteed throughput. Packets with QoS header including Diffserv/IP ToS and 802.1p will be mapped
into 4 Access Categories of WMM, packets without QoS header will be assigned to the Best Effort queue. Please refer to
the table below for mapping from 802.1p and ToS mapping to WMM:
Queue
Data Transmitted
Clients to AP
AC_BK Background.
AC_BE Best Effort 0, 3 Medium
AC_VI Video
IP
ToS
0x08
0x20
0x28
0xa0
802.1P
Priority
Priority Description
1, 2 Low
4, 5 High
High throughput. Bulk data that requires maximum
throughput and is not time-sensitive is sent to this queue
(FTP data, for example).
Medium throughput and delay. Most traditional IP data is
sent to this queue
Minimum delay. Time-sensitive video data is automatically
sent to this queue
0x30
AC_VO Voice
0xe0
0x88
6, 7 High
Time-sensitive data like VoIP and streaming media are
automatically sent to this queue
0xb8
Security Type : Option is “Disabled”, “WEP” or “AES” from drop-down list. Needs the same type to build WDS links.
Security type takes effect when WDS is enabled.
Î WEP Key : Enter HEX or ASCII WEP key at different length as shown below. This system supports up to 4 sets of
WEP keys.
9 Key Length : The available options are 64 bits, 128 bits or 152 bits.
9 WEP auth Method : Enable the desired option among Open system and Shared.
9 Key Index : key index is used to designate the WEP key during data transmission. 4 different WEP keys can be
entered at the same time, but only one is chosen.
9 WEP Key # : Enter HEX or ASCII format WEP key value; the system supports up to 4 sets of WEP keys.
34
Page 40

Key Length Hex ASCII
64-bit 10 characters 5 characters
128-bit 26 characters 13 characters
152-bit 32 characters 16 characters
Î AES Key : Enter 32 HEX characters AES key .
WDS MAC List
Î Enable : Click Enable to create WDS link.
Î WDS Peer's MAC Address : Enter the MAC address of WDS peer.
Î VLAN ID : By default, it’s disabled(spa ce ) with no VLAN ID. When desired, this system supports tagged VLA N from
0 to 4094.
Î Description : Description of WDS link.
The WDS link needs to be set at same Channel and with same Security Type.
Click Save button to save your changes. Click Reboot button to activate your changes
35
Page 41

3.4 System Management
3.4.1 Configure Management
Administrator could specify geographical location of the system via instructions in this page. Administrator could also enter
new Root and Admin passwords and allow multiple login methods.
Please click System -> Management and follow the below settings.
System Information
Î System Name : Enter a desired name or use the default one.
Î Description : Provide description of the system.
Î Location : Enter geographical location information of the system. It helps administrator to locate the system easier.
The system supports two management accounts, root and admin. The network manager is assigned with full administrative
privileges, when logging in as root user, to manage the system in all aspects. While logging in as an admin user, only subset
of privileges is granted such as basic maintenance. For example, root user can change passwords for both root and admin
account, and admin user can only manage its own. For more information about covered privileges for these two accounts,
please refer to Appendix C. Network manager Privileges.
Root Password : Log in as a root user and is allowed to change its own, plus admin user’s password.
Î New Password : Enter a new password if desired
Î Check New Password : Enter the same new password again to check.
Admin Password : Log in as a admin user and is allowed to change its own,
Î New Password : Enter a new password if desired
Î Check New Password : Enter the same new password again to check.
36
Page 42

Admin Login Methods : Only root user can enable or disable system login methods and change services port.
Î Enable HTTP : Check to select HTTP Service.
Î HTTP Port : The default is 80 and the range is between 1 ~ 65535.
Î Enable Telnet : Check to select Telnet Service
Î Telnet Port : The default is 23 and the range is between 1 ~ 65535.
Click Save button to save your changes. Click Reboot button to activate your changes
37
Page 43

3.4.2 Configure System Time
System time can be configured via this page, and manual setting or via a NTP server is supported.
Please click on System -> Time Server and follow the below setting.
Local Time : Display the current system time.
NTP Client : To synchronize the system time with NTP server.
Î Enable : Check to select NTP client.
Î Default NTP Server : Select the NTP Server from the drop-down list.
Î Time Zone : Select a desired time zone from the drop-down list.
Î Daylight saving time : Enable or disable Daylight saving.
If the system time from NTS server seem s incorrect, please verify your network settings, like default Gateway
and DNS settings
Click Save button to save your changes. Click Reboot button to activate your changes
38
Page 44

3.4.3 Configure UPnP
Universal Plug and Play(UPnP) is an architecture to enable pervasive peer-to-peer network connectivity between PCs,
intelligent devices and appliances when UPnP is supported. UPnP works on TCP/IP network to enable UPnP devices to
connect and access to each other, very well adopted in home networking environment.
UPnP : By default, it’s “Disable”. Select “Enable” or “Disable” of UPnP Service.
Click Save button to save changes and click Reboot button to activate changes
For UPnP to work in Windows XP, the “APO1000” or “APO1010”must be available in “My Network Places”.
If these devices are not available, you should verify that the correct components and services are loaded in Windows XP.
Please refer to Appendix D. Using UPnP on Windows XP
39
Page 45

3.4.4 Configure SNMP Setup
SNMP is an application-layer protocol that provides a message format for communication between SNMP manager and
agent. By enabling SNMP function, the administrator can obtain the system information remotely.
Please click on System -> SNMP Setup and follow the below setting.
SNMP v2c Enable: Check to enable SNMP v2c.
Î ro community : Set a community string to authorize read-only access.
Î rw community : Set a community string to authorize read/write access.
SNMP v3 Enable: Check to enable SNMP v3.
SNMPv3 supports the highest level SNMP security.
Î SNMP ro user : Set a community string to authorize read-only access.
Î SNMP ro password : Set a password to authorize read-only access.
Î SNMP rw user : Set a community string to authorize read/write access.
Î SNMP rw password : Set a password to authorize read/write access.
40
Page 46

SNMP Trap : Events such as cold start, interface up & down, and association & disassociation will report to an assigned
server.
Î Community : Set a community string required by the remote host computer that will receive trap messages or
notices send by the system.
Î IP : Enter the IP addresses of the remote hosts to receive trap messages.
Click Save button to save changes and click Reboot button to activate.
41
Page 47

3.4.5 Backup / Restore and Reset to Factory
Backup current configuration, restore prior configuration or reset back to factory default configuration can be executed via this
page.
Please click on Utilities -> Profile Setting and follow the below setting.
Save Settings To PC : Click Save button to save the current configuration to a local disk.
Load Settings from PC : Click Browse button to locate a configuration file to restore, and then click Upload button to
upload.
Reset To Factory Default : Click Default button to reset back to the factory default settings and expect Successful
loading message. Then, click Reboot button to activate.
42
Page 48

3.4.6 Firmware Upgrade
Firmware is the main software image that system needs to respond to requests and to manage re al time operations.
Firmware upgrades are sometimes required to include new features or bugs fix. It t akes around 8 minutes to upgrade due to
complexity of firmware. To upgrade system firmware, click Browse button to locate the new firmware, and then click Upgrade
button to upgrade.
1. To prevent data loss during firmware upgrade, please back up current settings before proceeding
2. Do not interrupt during firmware upgrade including power on/off as this may damage system.
43
Page 49

3.4.7 Network Utility
The administrator can diagnose network connectivity via the PING utility.
Please click on Utilities -> Network Utility and follow the below setting.
Ping : This utility will help ping other devices on the network to verify connectivity. Ping utility, using ICMP packets,
detects connectivity and latency between two network nodes. As result of that, packet loss and latency time are available
in the Result field while running the PING test.
Î Destination IP/Domain : Enter desired domain name, i.e. www.google.com, or IP address of the destination, and
click ping button to proceed. The ping result will be shown in the Result field.
Î Count : By default, it’s 5 and the range is from 1 to 50. It indicates numbe r of connectivity test.
44
Page 50

3.4.8 Reboot
This function allows user to restart system with existing or most current settings when chang es are made. Click Reboot
button to proceed and take around three minutes to complete.
A reminder will be available for remaini ng time to complete. If power cycle is necessary, please wait till completion of the
reboot process.
The System Overview page appears upon the completion of reboot.
45
Page 51

3.5 System Status
This section breaks down into subsections of System Overview, Associated Clients Status, WDS Link Status, Extra
Information and Event Log.
3.5.1 System Overview
Display detailed information of System, Network, LAN and Wireless in the System Overview page.
System : Display information of the system.
Î System Name : The name of the system.
Î Operating Mode : The mode currently in service.
Î Location : Deployed geographical location.
Î Description : A description of the system.
Î Firmware Version : The current installed firmware version.
Î Firmware Date : The build time of install ed firmware.
Î Device Time : The current time of the system.
Î System Up Time : The time period that system has been in service since last reboot.
Network Information : Display information of the Network.
Î Mode : Supports Static or Dynamic modes on the LAN interface.
Î IP Address : The management IP of system. By default, it’s 192.168.10.100.
Î IP Netmask : The network mask. By default, it’s 255.255.255.0.
Î IP Gateway : The gateway IP address and by default, it’s 192.168.10.1.
46
Page 52

Î Primary DNS : The primary DNS server in service.
Î Secondary DNS : The secondary DNS serve r in service.
LAN Information : Display total received and transmitted statistics on the LAN interface.
Î MAC Address : The MAC address of the LAN port.
Î Receive bytes : The total received packets in bytes on the LAN port.
Î Receive packets : The total received packets of the LAN port.
Î Transmit bytes : The total transmitted packets in bytes of the LAN port.
Î Transmit packets : The total transmitted packets of the LAN port.
Wireless VAP Information : Display total received and transmitted statistics on available Virtual AP.
Î MAC Address : The MAC address of the Wireless port. Different MAC address on each Virtual AP
Î Receive bytes :The total received packets in bytes on the Wireless port.
Î Receive packets : The total received packets on the Wireless port.
Î Transmit bytes : The total transmitted packets in bytes on the Wireless port.
Î Transmit packets : The total transmitted packets on the Wireless port.
47
Page 53

3.5.2 Associated Clients Status
It displays ESSID, on/off St atus, Security Type, total number of wireless clients associated with all Virtual AP.
VAP Information : Highlights key VAP information.
Î VAP : Available VAP from VAP0 to VAP7.
Î ESSID : Display name of ESSID for each VAP.
Î Status : On/Off
Î Security Type : Display chosen security type; WEP, WPA/WPA2-PSK, WPA/WPA2-Enterprise.
Î Clients : Display total number of wireless connections for each VA P.
VAP Clients : Display all associated clients on each Virtual AP.
Î MAC Address : MAC address of associated clients.
Î RSSI : RSSI of from associated clients..
Î Last TX Time : Last inactive time period in seconds for a wireless connection.
Î Disconnect : Click “Delete” button to manually disconnect a wireless client in a Virtual AP.
48
Page 54

3.5.3 WDS Link Status
On/Off Status, peers MAC Address, Received Signal Strength Indicator (RSSI) and Last TX Time for each WDS are available.
WDS : Maximum supported WDS links.
Status : On/Off.
MAC Address : Display MAC address of WDS peer.
RSSI : Indicate the RSSI of WDS links.
Last TX Time : Last inactive time period in seconds on WDS links.
If display “0” RSSI, you need to check WDS configuration. Things to verify are MAC Address, Channel and
Security type. Also, adjust antenna angle and Tx Power. If display unexpected RSSI, In a long distance
application, you might need to adjust Slot time, ACK/CTS timeout, and/or RT S threshold.
49
Page 55

3.5.4 Extra Information
Users could pull out information such as Route table, ARP table, MAC table, Bridge table or STP available in the drop-down
list from system. The “Refresh” button is used to retrieve latest table information.
Route table information : Select “Route t able infor m ation ” on the drop-down list to display route table.
APO1000/APO1010 could be used as a L2 or L3 device. It doesn’t support dynamic routing protocols such as RIP or
OSPF. Static routes to specific hosts, networks or default gateway are set up automatically according to the IP
configuration of system's interfaces. When used as a L2 device, it could switch packets and, as L3 device, it’s capable of
being a gateway to route packets inward and outward.
ARP table Information : Select “ARP Table Information” on the drop-down list to display ARP table.
ARP associates each IP address to a unique hardware address (MAC) of a device. It is important to have a unique IP
address as final destination to switch packets to.
Bridge table information : Select “Bridge Table information” on the drop-down list to display bridge table.
Bridge table will show Bridge ID and STP's Status on the each Ethernet bridge and its attached interfaces, the Bridge
Port should be attached to some interfaces (e.g. eth0, ath0~ath7 and ath0.wds0~ath0.wds7).
Bridge MAC information : Select “Bridge MACs Information” on the drop-down list to display MAC table.
This table displays local MAC addresses associated with wired or wireless inte rfaces, but also remember non-local MAC
addresses learned from wired or wireless interfaces.
50
Page 56

Ageing timers will be reset when existing MAC addresses in table are learned again or added when new MAC addresses
are seen from wired or wireless interfaces as well. When time runs out for a particular entry, it will be pruned from the
table. In that situation, switching packet to that particular MAC address will be dropped.
Bridge STP Information : Select “Bridge STP Information” on the drop-down list to display a list of bridge STP
information.
51
Page 57

3.5.5 Event Log
The Event log displays system events when system is up and running. Also, it becomes very useful as a troubleshooting tool
when issues are experienced in system.
Time: The date and time when the event occurred.
Facility: It helps users to identify source of events such “System” or “User”
Severity: Severity level that a specific event is associated such as “info”, “error”, “warning”, etc.
Message: Description of the event.
Click Refresh button to renew the log, or click Clear button to clear all the record.
52
Page 58

Chapter 4. WDS Mode Configuration
Please refer to illustrations of the section 1.3 for possible applications in the WDS mode. This section provides detailed
explanation for users to configure in the WDS mode with help of illustrations. In the WDS mode, functions listed in the table
below are also available from the Web-based GUI interface.
Option System Wireless Utilities Status
Operating Mode General Settings Management System Overview
LAN Advanced Settings Profiles Settings WDS Status
Functions
Time Server WDS Setup Firmware Upgrade Extra Info
SNMP Network Utility Event Log
UPnP Reboot
Table 4-1: WDS Mode Functions
4.1 External Network Connection
4.1.1 Network Requirement
You could expand your Ethernet network via WDS link. In this mode, the APO1000/APO1010 conne cts directly to a wired
LAN, and wirelessly bridges to a remote access point via a WDS link as shown in Figure 4-1. In the mode, it can’t associa t e
with any wireless clients.
F
i
g
u
r
e
4-1 Point to Point Configuration
APO1000/APO1010
53
Page 59

4.1.2 Configure LAN IP
Here are the instructions for how to setup the local IP Address and Netmask.
Please click on System -> LAN and follow the below setting.
Î Mode : Check either “Static IP” or “Dynamic IP” button as desired to set up the system IP of LAN port .
Î Static IP : The administrator can manually setup the LAN IP address when static IP is available/ prefe rred.
9 IP Address : The IP address of the LAN port; default IP address is 192.168.10.100
9 IP Netmask : The Subnet mask of the LAN port; default Netmask is 255.255.255.0
9 IP Gateway : The default gateway of the LAN port; default Gateway is 192.168.10.1
Î Dynamic IP : This configuration type is applicable when the APO1000/APO1010 is connected to a network with the
presence of a DHCP server; all related IP information will be provided by the DHCP server aut omatically.
Î Hostname : The Hostnam e of the LAN port
DNS : Check either “No Default DNS Server” or “Specify DNS Server IP” button as desired to set up the system DNS.
Î Primary : The IP address of the primary DNS server.
Î Secondary : The IP address of the secondary DNS server.
Î 802.1d Spanning Tree
The spanning tree network protocol provides a loop free topology for a bridged LAN between LAN interface and 8 WDS
interfaces from wds0 to wds7. The Spanning Tree Protocol, which is also referred to as STP, is defined in the IEEE
Standard 802.1d.
54
Page 60

APO1000/APO1010
APO1000/APO1010
Click Save button to save your changes. Click Reboot button to activate your changes
55
Page 61

4.2 Wireless Network Expansion
The network manager can configure related wireless settings, General Settings, Advanced Settings, Virtual AP Setting
and Security Settings.
4.2.1 Wireless General Setup
The administrator can change the data transmission, channel and output power settings for the system. Please click on
Wireless -> General Setup and follow the below setting.
MAC address : The MAC address of the Wireless interface is displayed here.
Band Mode : Select an appropriate wireless band; bands available are 801.11b, 802.1 1g and 802.11b+802.11g.
Transmit Rate Control : Select the desired rate from the drop-down list; the options are auto or ranging from 1 to
54Mbps for 802.11g and 802.11b/g modes, or 1 to 11Mbps for 802.11b mode.
Country : Select the desired Country code from the drop-down list; the options are US, ETSI or Japan.
Channel : The channel range will be changed by selecting different country code. The channel range from 1 to 11 for US
country code, or 1 to 13 for ETSI country code, or 1 to 14 for JP country code.
The Channel 14 for Japan only used on IEEE802.11b only
Tx Power : You can adjust the output power of the system to get the appropriate coverage for your wireless network.
Select the LEVEL 1 to LEVEL 9 you needed for your environment. If you are not sure of which setting to choose, then
keep the default setting, LEVEL 9.
Click Save button to save your changes. Click Reboot button to activate your changes. The items in this page are for AP's RF
general settings and will be applied to all WDS links.
56
Page 62

4.2.2 Wireless Advanced Setup
To achieve optimal wireless performance, it is necessary to tweak advance setting per requirements properly, not necessary
higher the better or lower.
The administrator can change the RTS threshold and fragmentation threshold settings for the system. Please click on
Wireless -> Advanced Setup and follow the below setting.
Slot Time : Slot time is in the range of 1~1489 and set in unit of microsecond. The default value is 20 microsecond.
Slot time is the amount of time a device waits after a collision before retransmitting a p acket. Reducing the slot time
decreases the overall back-off, which increases throughput. Back-off, which is a multiple of the slot time, is the random
length of time a station waits before sending a packet on the LAN. For a sender and receiver own right of the channel the
shorter slot time help manage shorter wait time to re-transmit from collision because of hidden wireless clients or other
causes. When collision sources can be removed soo ner and other send ers attempting to send are listening the
channel(CSMA/CA) the owner of the channel should continue ownership and finish their transmission and relea se the
channel. Then, following ownership of the channel will be sooner for the new pair due to shorter slot time. However, when
long duration of existing collision sources and shorter slot time exist the owners might experience subsequent collisions.
When adjustment to longer slot time can’t improve performance then RTS/CTS could supplement and help improve
performance.
ACK Timeout : ACK timeout is in the range of 1~372 and set in unit of microsecond. The default value is 48
microsecond.
All data transmission in 802.11b/g request an “Acknowledgement” (ACK) send by receiving radio. The transmitter will
resend the original packet if correspondent ACK failed to arrive within specific time interval, also refer to as “ACK
Timeout”.
ACK Timeout is adju stable due to the fact that distance between two radio links may vary in different deployment. ACK
Timeout makes significant influence in performance of long distance radio link. If ACK T i meout is set too short, transmitter
will start to “Resend” packet before ACK is received, and throughputs become low due to excessively high retransmission.
ACK Timeout is best dete rmined by distance between the radios, data rate of average environment. The Timeout value is
calculated based on round-trip time of packet with a little tolerance, So, if experiencing re-transmissions or poor
57
Page 63

performance the ACK Timeout could be made longer to accommodate.
RTS/CTS
Adjustment of RTS Threshold can be done to turn on RTS. CTS Timeout will take effect only when RTS is turned on.
Unlike wired Ethernet, radio transmission may begin with a RTS (Request to Send) frame, and receiver re sponds with a CTS
(Clear to Send) frame. The RTS/CTS mech anism is called Channel Cleaning, all stations that received CTS will back off for
certain period of time, multiple of the slot time.
Each CTS packet has a NAV (Network Allocation Vector) number n, the channel is reserved for sender and receiver for
additional n-millisecond. The NAV guarantees the channel is free of interference in next n-millisecond. The last packet of ACK
will set NAV to zero, indicated that connection is done and free the channel to others.
CTS Timeout : CTS Timeout is in the range of 1~744 and set in unit of microsecond. The default value is 48
microsecond.
CTS Timeout will take effect only when RTS is turned on. Adjustment of RTS Threshold can be done to turn on RTS.
When hidden wireless stations are present in the wireless network RTS can be considered to turn on to minimize
collisions and increase performance. Ensure CTS timeout is long enough to avoid frequent re-transmission of RTS.
Slot Time and ACK/CTS Timeout settings for long distance links. It is important to tweak settings to achieve the
optimal result based on requirement.
RSSI Threshold : RSSI Threshold is in the range of -128~127.The default value is 24.
RSSI is defined as Received Signal Strength Indication, when the received signal strength from peer is below this
threshold, the peer will be consider as disconnected. Set the threshold higher will make roaming happen earlier, set lower
will allow weak signal peer to connect.
In normal situation, the longer distance the lower signal strength will be
sensed between peers people could consider to lower RSSI threshold to have bigger coverage from the AP or
AP client perspective. If it doesn’t work well then people could consider to jack up RSSI threshold to have
stable smaller coverage and leave AP clients in longer distance to associate with closer AP.
Beacon Interval : Beacon Interval is in the range of 1~5000 and set in unit of millisecond. The default value is 100
msec.
Access Point (AP) in IEEE 802.11 will send out a special approximated 50-byte frame, called “Beacon”. Beacon is
broadcast to all the stations, provides the basic information of AP such as SSID, channel, encryption keys, signal
strength, time stamp, support data rate.
All the radio stations received beacon recognizes the existence of such AP, and may proceed next actions if the
information from AP matches the requirement. Beacon is sent on a periodic basis, the time interval can be adjusted.
By increasing the beacon interval, you can reduce the number of beacons and associated overhead, but that will likely
delay the association and roaming process because stations scanning for available access points may miss the beacons.
You can decrease the beacon interval, which increases the rate of beacons. This will make the association and roaming
process very responsive; however, the network will incur additional overhead and throughput will go down.
58
Page 64

DTIM Interval : The DTIM interval is in the range of 1~15. The default is 15.
DTIM is defined as Delivery Traffic Indication Message. It is used to notify the wireless stations, which support power
saving mode, when to wake up to receive multicast frame. DTIM is necessary and critical in wireless environment as a
mechanism to fulfill power-saving synchronization.
A DTIM interval is a count of the number of beacon frames that must occur before the access point sends the buffered
multicast frames. For instance, if DTIM Interval is set to 3, then the Wi-Fi clients will expect to receive a multicast frame
after receiving three Beacon frame. The higher DTIM interval will help power saving and possibly decrease wireless
throughput in multicast applications.
Fragment Threshold : The Fragment Threshold is in the range of 256~2346 byte. The default is 2346 byte.
Each Wi-Fi packet can be divided into smaller packets, marked with a sequential fragment number and re-assemble in
the receiving ends. The purpose is to make a short frame, instead of long frame, transmitting by radio in a heavy noisy
environment. Because of sending smaller frames, corruptions are much less likely to occur. The pros is obvious, the cons
is the overhead for transmission. So, in a clean environment, higher fragment threshold can be an option to increase
throughput.
Fragmentation will be triggered by setting the Fragment Threshold, usually in Byte-length. Only when the frame size is
over the Threshold, fragmentation will take place automatically.
RTS Threshold : RTS Threshold is in the range of 1~2346 byte. The default is 2346 byte.
The main purpose of enabling RTS by changing RTS threshold is to reduce possible collisions due to hidden wireless
clients. RTS in AP will be enabled automatically if the packet size is larger than the Threshold value. By default, RTS is
disabled in a normal environment supports non-jumbo frames.
Short Preamble : By default, it’s “Enable”. To Disable is to use Long 128-bit Preamble Synchronization field.
The preamble is used to signal "here is a train of data coming" to the receiver. The short preamble provides 72-bit
Synchronization field to improve WLAN transmission efficiency with less overhead.
Tx Burst : By default, it’s “Enable”. To Disable is to deactivate Tx Burst.
With TX burst enabled, AP will send many packets in a burst, without collision detection and RTS/CTS for each packet.
TX Burst have better throughput but cause interference with other APs in channel.
802.11g Protection Mode : By default, it’s “Enable”. To Disable is to deactivate 802.11g Protection Mode.
Protection mode use RTS/CTS to prevent interference with other APs and 802.11b peers, and disabling it will save
transmission time used by RTS/CTS. RTS/CTS threshold is effective only when 802.11g protection mode is made
enable.
Click Save button to save your changes. Click Reboot button to activate your changes. The items in this page are for AP's RF
advanced settings and will be applied to all WDS links.
59
Page 65

4.2.3 WDS Setup
The administrator could create WDS Links to expand wireless network. When WDS is enabled, access point functions as a
wireless bridge and is able to communicate with other access points via WDS links. A WDS link is bidirectional and both
side must support WDS. Access points know each other by MAC Address. In other words, each access point needs
to include MAC address of its peer. Ensure all access points are configured with the same channel and own same
security type settings.
Figure 4-2 shows Point to Multiple Points with different VLAN settings
APO1000/APO1010
Figure 4-2 Point to Multiple Points with different VLAN Tag
Please click on Wireless -> WDS Setup and follow the below setting.
Note that VLAN ID in the WDS MAC List setting will only be tagged to egress packets on the wired Ethernet port.
Ensure to match VLAN ID used on the network of the peer. WDS link won’t carry tags at all.
WMM : By default, it’s “Disable”.
Select “Enable”, then packets with WMM QoS will take higher priority.
60
Page 66

WMM prioritizes traffic according to four Access Categories (AC) - voice, video, best effort, and background. However, it
does not provide guaranteed throughput. Packets with QoS header including Diffserv/IP ToS and 802.1p will be mapped
into 4 Access Categories of WMM, packets without QoS header will be assigned to the Best Effort queue. Please refer to
the table below for mapping from 802.1p and ToS mapping to WMM:
Queue
Data Transmitted
Clients to AP
AC_BK Background.
AC_BE Best Effort 0, 3 Medium
AC_VI Video
IP
ToS
0x08
0x20
0x28
0xa0
802.1P
Priority
Priority Description
1, 2 Low
4, 5 High
High throughput. Bulk data that requires maximum
throughput and is not time-sensitive is sent to this queue
(FTP data, for example).
Medium throughput and delay. Most traditional IP data is
sent to this queue
Minimum delay. Time-sensitive video data is automatically
sent to this queue
0x30
AC_VO Voice
0xe0
0x88
6, 7 High
Time-sensitive data like VoIP and streaming media are
automatically sent to this queue
0xb8
Security Type : Option is “Disabled”, “WEP” or “AES” from drop-down list. Needs the same type to build WDS links.
Security type takes effect when WDS is enabled.
Î WEP Key : Enter HEX or ASCII WEP key at different length as shown below. This system supports up to 4 sets of
WEP keys.
9 Key Length : The available options are 64 bits, 128 bits or 152 bits.
9 WEP auth Method : Enable the desired option among Open system and Shared.
9 Key Index : key index is used to designate the WEP key during data transmission. 4 different WEP keys can be
entered at the same time, but only one is chosen.
9 WEP Key # : Enter HEX or ASCII format WEP key value; the system supports up to 4 sets of WEP keys.
Key Length Hex ASCII
64-bit 10 characters 5 characters
128-bit 26 characters 13 characters
152-bit 32 characters 16 characters
Î AES Key : Enter 32 HEX characters AES key .
61
Page 67

WDS MAC List
Î Enable : Click Enable to create WDS link.
Î WDS Peer's MAC Address : Enter the MAC address of WDS peer.
Î VLAN ID : By default, it’s disabled(spa ce ) with no VLAN ID. When desired, this system supports tagged VLA N from
0 to 4094.
Î Description : Description of WDS link.
The WDS link needs to be set at same Channel and Security Type.
Click Save button to save your changes. Click Reboot button to activate your changes
62
Page 68

4.3 System Management
4.3.1 Configure Management
Administrator could specify geographical location of the system via instructions in this page. Administrator could also enter
new Root and Admin passwords and allow multiple login methods.
Please click System -> Management and follow the below settings.
System Information
Î System Name : Enter a desired name or use the default one.
Î Description : Provide description of the system.
Î Location : Enter geographical location information of the system. It helps administrator to locate the system easier.
The system supports two management accounts, root and admin. The network manager is assigned with full administrative
privileges, when logging in as root user, to manage the system in all aspects. While logging in as an admin user, only subset
of privileges is granted such as basic maintenance. For example, root user can change passwords for both root and admin
account, and admin user can only manage its own. For more information about covered privileges for these two accounts,
please refer to Appendix C. Network manager Privileges.
Root Password : Log in as a root user and is allowed to change its own, plus admin user’s password.
Î New Password : Enter a new password if desired
Î Check New Password : Enter the same new password again to check.
Admin Password : Log in as a admin user and is allowed to change its own,
Î New Password : Enter a new password if desired
Î Check New Password : Enter the same new password again to check.
63
Page 69

Admin Login Methods : Only root user can enable or disable system login methods and change services port.
Î Enable HTTP : Check to select HTTP Service.
Î HTTP Port : The default is 80 and the range is between 1 ~ 65535.
Î Enable HTTPS : Check to select HTTPS Service
Î HTTPS Port : The default is 443 and the range is between 1 ~ 65535.
If you already have an SSL Certificate, please click “UploadKey” button to select the file and upload it.
Î Enable Telnet : Check to select Telnet Service
Î Telnet Port : The default is 23 and the range is between 1 ~ 65535.
Î Enable SSH : Check to select SSH Service
Î SSH Port : Please The default is 22 and the range is between 1 ~ 65535.
Click “GenerateKey” button to generate RSA private key. The “host key footprint” gray blank will display content
of RSA key.
Click Save button to save your changes. Click Reboot button to activate your changes
Without a valid certificate, users may encounter the following problem in IE7 when they try to access system's Web GUI
(https://192.168.2.254
). There will be a “Certificate Error”, because the browser treats system as an illegal website.
Click “Continue to this website” to access the system's Web GUI. The system's Overview page will appear.
64
Page 70

4.3.2 Configure System Time
System time can be configured via this page, and manual setting or via a NTP server i s su pported.
Please click on System -> Time Server and follow the below setting.
Local Time : Display the current system time.
NTP Client : To synchronize the system time with NTP server.
Î Enable : Check to select NTP client.
Î Default NTP Server : Select the NTP Server from the drop-down list.
Î Time Zone : Select a desired time zone from the drop-down list.
Î Daylight saving time : Enable or disable Daylight saving.
If the system time from NTS server seem s incorrect, please verify your network settings, like default Gateway
and DNS settings
Click Save button to save your changes. Click Reboot button to activate your changes
65
Page 71

4.3.3 Configure UPnP
Universal Plug and Play(UPnP) is an architecture to enable pervasive peer-to-peer network connectivity between PCs,
intelligent devices and appliances when UPnP is supported. UPnP works on TCP/IP network to enable UPnP devices to
connect and access to each other, very well adopted in home networking environment.
UPnP : By default, it’s “Disable”. Select “Enable” or “Disable” of UPnP Service.
Click Save button to save changes and click Reboot button to activate changes
For UPnP to work in Windows XP, the “APO1000” or “APO1010” must be available in “My Network Places”.
If these devices are not available, you should verify that the correct components and services are loaded in Windows XP.
Please refer to Appendix D. Using UPnP on Windows XP
66
Page 72

4.3.4 Configure SNMP Setup
SNMP is an application-layer protocol that provides a message format for communication between SNMP managers and
agents. By enabling SNMP function, the administrator can obtain the system info rmation remotely.
Please click on System -> SNMP Setup and follow the below setting.
SNMP v2c Enable : Check to enable SNMP v2c.
Î ro community : Set a community string to authorize read-only access.
Î rw community : Set a community string to authorize read/write access.
SNMP v3 Enable: Check to enable SNMP v3.
SNMPv3 supports the highest level SNMP security.
Î SNMP ro user : Set a community string to authorize read-only access.
Î SNMP ro password : Set a password to authorize read-only access.
Î SNMP rw user : Set a community string to authorize read/write access.
Î SNMP rw password : Set a password to authorize read/write access.
SNMP Trap : Events such as cold start, interface up & down, and association & disassociation will report to an assigned
server.
67
Page 73

Î Community : Set a community string required by the remote host computer that will receive trap messages or
notices send by the system.
Î IP : Enter the IP addresses of the remote hosts to receive trap messages.
Click Save button to save changes and click Reboot button to activate.
68
Page 74

4.3.5 Backup / Restore and Reset to Factory
Backup current configuration, restore prior configuration or reset back to factory default configuration can be executed via this
page.
Please click on Utilities -> Profile Setting and follow the below setting.
Save Settings to PC : Click Save button to save the current configuration to a local disk.
Load Settings from PC : Click Browse button to locate a configuration file to restore, and then click Upload button to
upload.
Reset To Factory Default : Click Default button to reset back to the factory default settings and expect Successful
loading message. Then, click Reboot button to activate.
69
Page 75

4.3.6 Firmware Upgrade
Firmware is the main software image that system needs to respond to requests and to manage re al time operations.
Firmware upgrades are sometimes required to include new features or bugs fix. It t akes around 8 minutes to upgrade due to
complexity of firmware. To upgrade system firmware, click Browse button to locate the new firmware, and then click Upgrade
button to upgrade.
1. To prevent data loss during firmware upgrade, please back up current settings before proceeding.
2. Do not interrupt during firmware upgrade including power on/off as this may damage system.
70
Page 76

4.3.7 Network Utility
The administrator can diagnose network connectivity via the PING utility.
Please click on Utilities -> Network Utility and follow the below setting.
Ping : This utility will help ping other devices on the network to verify connectivity. Ping utility, using ICMP packets,
detects connectivity and latency between two network nodes. As result of that, packet loss and latency time are available
in the Result field while running the PING test.
Î Destination IP/Domain : Enter desired domain name, i.e. www.google.com, or IP address of the destination, and
click ping button to proceed. The ping result will be shown in the Result field.
Î Count : By default, it’s 5 and the range is from 1 to 50. It indicates numbe r of connectivity test.
71
Page 77

4.3.8 Reboot
This function allows user to restart system with existing or most current settings when chang es are made. Click Reboot
button to proceed and take around three minutes to complete.
A reminder will be available for remaini ng time to complete. If power cycle is necessary, please wait till completion of the
reboot process.
The System Overview page appears upon the completion of reboot.
72
Page 78

4.4 System Status
This section breaks down into subsections of System Overview, WDS Link St atus, Extra Information a nd Event Log.
4.4.1 System Overview
Detailed information on System, Network, LAN Information and Wireless Information can be reviewed via this page.
System : Display the information of the system.
Î System Name : The name of the system.
Î Operating Mode : The mode currently in service.
Î Location : The reminding note on the g eographical location of the system.
Î Description : The reminding note of the system.
Î Firmware Version : The current firmware version installed.
Î Firmware Date : The build time of the firmware installed.
Î Device Time : The current time of the system.
Î System Up Time : The time period that system has been in service since last reboot.
Network Information : Display the information of the Network.
Î Mode : Supports Static or Dynamic modes on the LAN interface.
Î IP Address : The management IP of system. By default, it’s 192.168.10.100.
Î IP Netmask : The network mask. By default, it’s 255.255.255.0.
Î IP Gateway : The gateway IP address and by default, it’s 192.168.10.1.
Î Primary DNS : The primary DNS server in service.
Î Secondary DNS : The secondary DNS serve r in service.
73
Page 79

LAN Information : Display total received and transmitted statistics on the LAN interface.
Î MAC Address : The MAC address of the LAN port.
Î Receive bytes : The total received packets in bytes on the LAN port.
Î Receive packets : The total received packets of the LAN port.
Î Transmit bytes : The total transmitted packets in bytes of the LAN port.
Î Transmit packets : The total transmitted packets of the LAN port.
74
Page 80

4.4.2 WDS Link Status
On/Off Status, peers MAC Address, Received Signal Strength Indicator(RSSI) and Last TX Time for each WDS are available.
WDS : Maximum supported WDS links.
Status : On/Off.
MAC Address : Display MAC address of WDS peer.
RSSI : Indicate the RSSI of WDS links.
Last TX Time : Last inactive time period in seconds on WDS links.
If display “0” RSSI, you need to check WDS configuration. Things to verify are MAC Address, Channel and
Security type. Also, adjust antenna angle and Tx Power. If display unexpected RSSI, In a long distance
application, you might need to adjust Slot time, ACK/CTS timeout, and/or RT S threshold.
75
Page 81

4.4.3 Extra Information
Users could pull out information such as Route table, ARP table, MAC table, Bridge table or STP available in the drop-down
list from system. The “Refresh” button is used to retrieve latest table information.
Route table information : Select “Route t able infor m ation ” on the drop-down list to display route table.
APO1000/APO1010 could be used as a L2 or L3 device. It doesn’t support dynamic routing protocols such as RIP or
OSPF. Static routes to specific hosts, networks or default gateway are set up automatically according to the IP
configuration of system's interfaces. When used as a L2 device, it could switch packets and, as L3 device, it’s capable of
being a gateway to route packets inward and outward.
ARP table Information : Select “ARP Table Information” on the drop-down list to display ARP table.
ARP associates each IP address to a unique hardware address (MAC) of a device. It is important to have a unique IP
address as final destination to switch packets to.
Bridge table information : Select “Bridge Table information” on the drop-down list to display bridge table.
Bridge table will show Bridge ID and STP's Status on the each Ethernet bridge and its attached interfaces, the Bridge
Port should be attached to some interfaces (e.g. eth0, ath0.wds0~at h0.wds7).
Bridge MAC information : Select “Bridge MACs Information” on the drop-down list to display MAC table.
This table displays local MAC addresses associated with wired or wireless inte rfaces, but also remember non-local MAC
addresses learned from wired or wireless interfaces.
76
Page 82

Ageing timers will be reset when existing MAC addresses in table are learned again or added when new MAC addresses
are seen from wired or wireless interfaces as well. When time runs out for a particular entry, it will be pruned from the
table. In that situation, switching packet to that particular MAC address will be discontinued.
Bridge STP Information : Select “Bridge STP Information” on the drop-down list to display a list of bridge STP
information.
77
Page 83

4.4.4 Event Log
The Event log displays system events when system is up and running. Also, it becomes very useful as troubleshooting tool
when issues are experienced in system.
Time: The date and time when the event occurred.
Facility: It helps users to identify source of events such “System” or “User”
Severity: Severity level that a specific event is associated such as “info”, “error”, “warning”, etc.
Message: Description of the event.
Click Refresh button to renew the log, or click Clear button to clear all the record.
78
Page 84

Chapter 5. CPE Mode Configuration
When CPE mode is chosen, the system can be configured as a Customer Premises Equipment(CPE). This section provides
detailed explanation for users to configure in the CPE mode with help of illustrations. In the CPE mode, functions listed in the
table below are also available from the Web-based GUI interface.
OPTION System Wireless Advance Utilities Status
Operating Mode General Setup DMZ Profiles Settings System Overview
WAN Advanced Setup IP Filter Setup Firmware Upgrade DHCP Clients
LAN Site Survey MAC Filter Setup Network Utility Extra Info
Functions
DDNS Virtual Server Reboot Event Log
Management
Time Server
SNMP
UPNP
Table 5-1: CPE Mode Functions
5.1 External Network Connection
5.1.1 Network Requirement
It can be used as an Outdoor Customer Premises Equipment (CPE) to receive wireless signal over last mile application ,
helping WISPs deliver wireless broadband Internet service to residents and business cu stomers. In the CPE mode,
APO1000/APO1010 is a gateway enabled with NAT and DHCP Server functions. The wired clients connected to
APO1000/APO1010 are in different subnet from those connected to Main Base Station, and, in CPE mode, it does not
accept wireless association from wireless clients.
79
Page 85

APO1000/APO1010
Figure 5-1 CPE mode configuration
80
Page 86

5.1.2 Configure WAN Setup
There are three connection types for the WAN p ort : Static IP, Dynamic IP and PPPoE.
Please click on System -> WAN and follow the below setting.
In CPE mode, the WAN Port is the Wireless interface.
Î Mode : By default, it’s “Static IP”. Check “Static IP”, “Dynamic IP” or “PPPoE” to set up system WAN IP.
Î Static IP : Users can manually setup the WAN IP address with a static IP provided by WISP.
9 IP Address : The IP address of the WAN port. By default, the IP address is 192.168.1.254
9 IP Netmask : The Subnet mask of the WAN port. By default, the Netmask is 255.255.255.0
9 IP Gateway : The default gateway of the WAN po rt. By default, the Gateway is 192.168.1.1
Î Dynamic IP : Please consult with WISP for correct wireless settings to associate with WISP AP before a dynamic IP,
along with related IP settings including DNS can be available from DHCP server. If IP Address is not assigned,
please double check with your wireless settings and ensure successful association. Also, you may go to “WAN
Information” in the Overview page to click Release button to release IP address and click Renew button to renew
IP address again.
9 Hostname : The Hostname of the WAN port
Î PPPoE : To create wireless PPPoE WAN connection to a PPPoE server in network.
81
Page 87

Î User Name : Enter User Name for PPPoE connection
Î Password : Enter Password for PPPoE connection
Î Reconnect Mode :
9 Always on – A connection to Internet is always maintained.
9 On Demand – A connection to Internet is made as needed.
When Time Server is enabled at the “On Demand” mode, the “Reconnect Mode” will turn out “Always on”.
9 Manual – Click the “Connect” button on “WAN Information” in the Overview page to connect to the Internet.
Î Idle Time : Time to last before disconnecting PPPoE session when it is idle. Enter preferred Idle Time in minutes.
Î MTU : By default, it’s 1492 bytes. MTU stands fo r Maximum Transmission Unit. Consult with WISP for a correct MTU
setting.
DNS : Check “No Default DNS Server” or “S pecify DNS Server IP” radial button as desired to set up system DNS.
Î Primary : The IP address of the primary DNS server.
Î Secondary : The IP address of the secondary DNS server.
MAC Clone : The MAC address is a 12-digit HEX code uniquely assigned to hardware as identification. Some ISPs
require you to register a MAC address in order to access to Internet. If not, you could use default MAC or clone MAC
from a PC.
Î Keep
Default MAC Address : Keep the default MAC address of WAN port on the system.
Î Clone MAC Address : If you want to clone the MAC address of the PC, then click the Clone MAC Address button.
The system will automatically detect your PC's MAC address.
82
Page 88

The Clone MAC Address field will display MAC address of the PC connected to system. Click “Save” button can
make clone MAC effective.
Î Manual MAC Address : E nter the MAC address registered with your ISP.
Bandwidth : Administrator can control download and upload bandwidth. Default is Disable
Î Upload : The range is from 256 to 8192 in Kbits
Î Download : The range is from 256 to 8192 in Kbits
Click Save button to save your changes. Click Reboot button to activate your changes
83
Page 89

5.1.3 Configure DDNS Setup
Dynamic DNS allows you to map domain name to dynamic IP address.
Please click on System -> DDNS Setup and follow the below setting.
Enabled: By default, it’s “Disable”. The mapping domain name won’t change when dynamic IP changes. The beauty of it
is no need to remember the dynamic WAP IP while accessing to it.
Service Provider: Select the preferred Service Provider from the drop-down list including dyndns, dhs, ods and tzo
Hostname: Host Name that you register to Dynamic-DNS service and export.
User Name & Password: User Name and Password are used to login DDNS service.
Click Save button to save your changes. Click Reboot button to activate your changes
84
Page 90

5.1.4 Configure LAN IP
Here are the instructions for how to setup the local IP Address and Netmask.
Please click on System -> LAN and follow the below setting.
LAN IP : The administrator can manually setup the LAN IP address.
Î IP Address : The IP address of the LAN port; default IP address is 192.168.10.100
Î IP Netmask : The Subnet mask of the LAN port; default Netmask is 255.255.255.0
Î 802.1d Spanning Tree
The spanning tree network protocol provides a loop free topology for a bridged LAN between LAN interface. The
Spanning Tree Protocol, which is also referred to as STP, is defined in the IEEE Standard 802.1d.
DHCP Server : Devices connected to the system can obtain an IP address automatically when this service is enabled.
Î DHCP : Check Enable button to activate this function or Disable to deactivate this service.
Î Start IP / End IP: Specify the range of IP addresses to be used by the DHCP server when a ssigning IP address to
clients. The default range IP address is 192.168.10.101 to 192.168.10.254, the netmask is 255.255.255.0
Î DNS1 IP : Enter IP address of the first DNS serve r; this field is req uired.
85
Page 91

Î DNS2 IP : Enter IP address of the second DNS server; this is optional.
Î WINS IP : Enter IP address of the Windows Internet Name Service (WINS) server; this is optional.
Î Domain : Enter the domain name for this network.
Î Lease Time : The IP addresses given out by the DHCP server will only be valid for the duration specified by the
lease time. Increasing the time ensure client operation without interruptions, but could introduce potential conflicts.
Lowering the lease time will avoid potential address conflicts, but might cause more interruptions to the client while it
will acquire new IP addresses from the DHCP server. Default is 86400 seconds
Click Save button to save your changes. Click Reboot button to activate your changes
86
Page 92

5.2 Access Point Association
5.2.1 Wireless General Setup
The administrator can change the data transmission, channel and output power settings for the system. Please click on
Wireless -> General Setup and follow the below setting.
ESSID : Assign Service Set ID for the wireless system.
Band Mode : Select an appropriate wireless band; bands available are 801.11b, 802.1 1g and 802.11b+802.11g.
Transmit Rate Control : Select the desired rate from the drop-down list; the options are auto or ranging from 1 to
54Mbps for 802.11g and 802.11b/g modes, or 1 to 11Mbps for 802.11b mode.
Country : Select the desired Country code from the drop-down list; the options are US, ETSI or Japan.
Channel : The channel range will be changed by selecting different country code. The channel range from 1 to 11 for US
country code, or 1 to 13 for ETSI country code, or 1 to 14 for JP country code.
Tx Power : You can adjust the output power of the system to get the appropriate coverage for your wireless network.
Select the LEVEL 1 to LEVEL 9 you needed for your environment. If you are not sure of which setting to choose, then
keep the default setting, LEVEL 9.
Security Type : Select the desired security type from the drop-down list; the options are Disabled WEP, WPA-PSK and
WPA2-PSK.
Î Disable : Data are unencrypted during transmission when this option is selected.
Î WEP : Wired Equivalent Privacy(WEP) is a dat a encryption mechanism based on a 64-bit, 128-bit or 152-bit shared
87
Page 93

key. The WEP key configured here must be exactly the same as the key on the access point that this system is
associated with.
88
Page 94

9 Key Length : The available options are 64 bits, 128 bits or 152 bits.
9 WEP auth Method : Enable the desired option among Open system and Shared.
9 Key Index : key index is used to designate the WEP key during data transmission. 4 different WEP keys can be
entered at the same time, but only one is chosen.
9 WEP Key # : Enter HEX or ASCII format WEP key value; the system supports up to 4 sets of WEP keys.
Key Length Hex ASCII
64-bit 10 characte rs 5 characters
128-bit 26 characte rs 13 characters
152-bit 32 characte rs 16 characters
Î WPA-PSK (or WPA2-PSK) : WPA (or WPA2)Algorithms, allows the system accessing the n etwork by using the
WPA-PSK protected access.
9 Cipher Suite : Select either AES or TKIP for the Cipher Suite.
9 Key Type : Select either ASCII or HEX format for the Pre-shared Key.
9 Pre-shared Key : Enter the pre-shared key; the format shall go with the selected key type.
Pre-shared key can be entered with either a 256-bit secret in 64 HEX digits format, or 8 to 63 ASCII characters.
Click Save button to save your changes. Click Reboot button to activate your changes.
89
Page 95

5.2.2 Wireless Advanced Setup
To achieve optimal wireless performance, it is necessary to tweak advance setting per requirements properly, not necessary
higher the better or lower.
The administrator can change the RTS threshold and fragmentation threshold settings for the system. Please click on
Wireless -> Advanced Setup and follow the below setting.
Slot Time : Slot time is in the range of 1~1489 and set in unit of microsecond. The default value is 20 microsecond.
Slot time is the amount of time a device waits after a collision before retransmitting a p acket. Reducing the slot time
decreases the overall back-off, which increases throughput. Back-off, which is a multiple of the slot time, is the random
length of time a station waits before sending a pa cket on the LAN.
For a sender and receiver own right of the
channel the shorter slot time help manage shorter wait time to re-transmit from collision because of hidden
wireless clients or other causes. When collision sources can be removed sooner and other senders
attempting to send are listening the channel(CSMA/CA) the owner of the channel should continue ownership
and finish their transmission and release the channel. Then, following ownership of the channel will be sooner
for the new pair due to shorter slot time. However, when long duration of existing collision sources and shorter
slot time exist the owners might experience subsequent collisions. When adjustment to longer slot time can’t
improve performance then RTS/CTS could supplement and help improve performance.
ACK Timeout : ACK timeout is in the range of 1~372 and set in unit of microsecond. The default value is 48
microsecond.
All data transmission in 802.11b/g request an “Acknowledgement” (ACK) send by receiving radio. The transmitter will
resend the original packet if correspondent ACK failed to arrive within specific time interval, also refer to as “ACK
Timeout”.
ACK Timeout is adju stable due to the fact that distance between two radio links may vary in different deployment. ACK
Timeout makes significant influence in performance of long distance radio link. If ACK T i meout is set too short, transmitter
will start to “Resend” packet before ACK is received, and throughputs become low due to excessively high retransmission.
ACK Timeout is best dete rmined by distance between the radios, data rate of average environment. The Timeout value is
calculated based on round-trip time of packet with a little tolerance, So, if experiencing re-transmissions or poor
90
Page 96

performance the ACK Timeout could be made longer to accommodate.
RTS/CTS
Adjustment of RTS Threshold can be done to turn on RTS. CTS Timeout will take effect only when RTS is turned on.
Unlike wired Ethernet, radio transmission may begin with a RTS (Request to Send) frame, and receiver re sponds with a CTS
(Clear to Send) frame. The RTS/CTS mech anism is called Channel Cleaning, all stations that received CTS will back off for
certain period of time, multiple of the slot time.
Each CTS packet has a NAV (Network Allocation Vector) number n, the channel is reserved for sender and receiver for
additional n-millisecond. The NAV guarantees the channel is free of interference in next n-millisecond. The last packet of ACK
will set NAV to zero, indicated that connection is done and free the channel to others.
CTS Timeout : CTS Timeout is in the range of 1~744 and set in unit of microsecond. The default value is 48
microsecond.
CTS Timeout will take effect only when RTS is turned on. Adjustment of RTS Threshold can be done to turn on RTS.
When hidden wireless stations are present in the wireless network RTS can be considered to turn on to minimize
collisions and increase performance. Ensure CTS timeout is long enough to avoid frequent re-transmission of RTS.
Slot Time and ACK/CTS Timeout settings for long distance links. It is important to tweak settings to achieve the
optimal result based on requirement.
Fragment Threshold : The Fragment Threshold is in the range of 256~2346 byte. The default is 2346 byte.
Each Wi-Fi packet can be divided into smaller packets, marked with a sequential fragment number and re-assemble in
the receiving ends. The purpose is to make a short frame, instead of long frame, transmitting by radio in a heavy noisy
environment. Because of sending smaller frames, corruptions are much less likely to occur. The pros is obvious, the cons
is the overhead for transmission. So, in a clean environment, higher fragment threshold can be an option to increase
throughput.
Fragmentation will be triggered by setting the Fragment Threshold, usually in Byte-length. Only when the frame size is
over the Threshold, fragmentation will take place automatically.
RTS Threshold : RTS Threshold is in the range of 1~2346 byte. The default is 2346 byte.
The main purpose of enabling RTS by changing RTS threshold is to reduce possible collisions due to hidden wireless
clients. RTS in AP will be enabled automatically if the packet size is larger than the Threshold value. By default, RTS is
disabled in a normal environment supports non-jumbo frames.
Short Preamble : By default, it’s “Enable”. To Disable is to use Long 128-bit Preamble Synchronization field.
The preamble is used to signal "here is a train of data coming" to the receiver. The short preamble provides 72-bit
Synchronization field to improve WLAN transmission efficiency with less overhead.
Tx Burst : By default, it’s “Enable”. To Disable is to deactivate Tx Burst.
With TX burst enabled, AP will send many packets in a burst, without collision detection and RTS/CTS for each packet.
TX Burst have better throughput but cause interference with other APs in channel.
WMM : By default, it’s “Disable”.
91
Page 97

Select “Enable”, then packets with WMM QoS will take higher priority.
WMM prioritizes traffic according to four Access Categories (AC) - voice, video, best effort, and background. However, it
does not provide guaranteed throughput. Packets with QoS header including Diffserv/IP ToS and 802.1p will be mapped
into 4 Access Categories of WMM, packets without QoS header will be assigned to the Best Effort queue. Please refer to
the table below for mapping from 802.1p and ToS mapping to WMM:
Queue
AC_BK Background.
AC_BE Best Effort 0, 3 Medium
AC_VI Video
AC_VO Voice
Click Save button to save your changes. Click Reboot button to activate your changes. The items in this page are for AP's RF
advanced settings and will be applied to all VAPs.
Data Transmitted
Clients to AP
IP
ToS
0x08
0x20
0x28
0xa0
0x30
0xe0
0x88
0xb8
802.1P
Priority
1, 2 Low
4, 5 High
6, 7 High
Priority Description
High throughput. Bulk data that requires maximum
throughput and is not time-sensitive is sent to this queue
(FTP data, for example).
Medium throughput and delay. Most traditional IP data is
sent to this queue
Minimum delay. Time-sensitive video data is automatically
sent to this queue
Time-sensitive data like VoIP and streaming media are
automatically sent to this queue
92
Page 98

5.2.3 Site Survey
Use this tool to scan and locate WISP Access Points and select one to associate with.
Please click on Wireless -> Site Survey. Below depicts an example for site survey.
ESSID : Available Extend Service Set ID of surrounding Access Points.
MAC Address : MAC addresses of surrounding Access Points.
Channel : Channel numbers used by all found Access Points.
Signal Level : Received signal strength of all found Access Points.
Security Type : Security type by all found Access Points.
Setup : Click “Select” button to configure settings and associate with chosen AP.
While clicking “Select” button in the Site Survey Table, the “ESSID” and “Security Type” will apply in the
Wireless General Setup. However, more settings are needed including Security Key.
93
Page 99

5.3 System Management
5.3.1 Configure Management
Administrator could specify geographical location of the system via instructions in this page. Administrator could also enter
new Root and Admin passwords and allow multiple login methods.
Please click System -> Management and follow the below settings.
System Information
Î System Name : Enter a desired name or use the default one.
Î Description : Provide description of the system.
Î Location : Enter geographical location information of the system. It helps administrator to locate the system easier.
The system supports two management accounts, root and admin. The network manager is assigned with full administrative
privileges, when logging in as root user, to manage the system in all aspects. While logging in as an admin user, only subset
of privileges is granted such as basic maintenance. For example, root user can change passwords for both root and admin
account, and admin user can only manage its own. For more information about covered privileges for these two accounts,
please refer to Appendix C. Network manager Privileges.
Root Password : Log in as a root user and is allowed to change its own, plus admin user’s password.
Î New Password : Enter a new password if desired
Î Check New Password : Enter the same new password again to check.
Admin Password : Log in as a admin user and is allowed to change its own,
Î New Password : Enter a new password if desired
Î Check New Password : Enter the same new password again to check.
94
Page 100

Admin Login Methods : Only root user can enable or disable system login methods and change services port.
Î Enable HTTP : Check to select HTTP Service.
Î HTTP Port : The default is 80 and the range is between 1 ~ 65535.
Î Enable HTTPS : Check to select HTTPS Service
Î HTTPS Port : The default is 443 and the range is between 1 ~ 65535.
If you already have an SSL Certificate, please click “UploadKey” button to select the file and upload it.
Î Enable Telnet : Check to select Telnet Service
Î Telnet Port : The default is 23 and the range is between 1 ~ 65535.
Î Enable SSH : Check to select SSH Service
Î SSH Port : Please The default is 22 and the range is between 1 ~ 65535.
Click “GenerateKey” button to generate RSA private key. The “host key footprint” gray blank will display content
of RSA key.
Click Save button to save your changes. Click Reboot button to activate your changes
Without a valid certificate, users may encounter the following problem in IE7 when they try to access system's Web GUI
(https://192.168.2.254
). There will be a “Certificate Error”, because the browser treats system as an illegal website.
Click “Continue
to this website” to access the system's Web GUI. The system's Overview page will appear.
95
 Loading...
Loading...