Aficio 3035, 3045 Service Manual

Operating Instructions
General Settings Guide
Getting Started
1
Combined Function Operations
2
Document Server
3
User Tools (System Settings)
4
Registering Addresses and Users for Facsimile/Scanner Functions
5
Troubleshooting
6
Remarks
7
Entering Text
8
Specifications
9
Read this manual carefully before you use this machine and keep it handy for future reference. For safe and correct use, be sure to read the
Safety Information before using the machine.

Introduction
This manual contains detailed instructions and notes on the operation and use of this machine. For your
safety and benefit, read this manual carefully before using the machine. Keep this manual in a handy
place for quick reference.
Important
Contents of this manual are subject to change without prior notice. In no event will the company be liable for direct, indirect, special, incidental, or consequential damages as a result of handling or operating the machine.
Notes:
Some illustrations in this manual might be slightly different from the machine.
Certain options might not be available in some countries. For details, please contact your local dealer.
Laser Safety:
This machine is considered a class 1 laser device, safe for office/EDP use. The machine contains two
GaAIAs laser diodes, 5-milliwatt, 760-800 nanometer wavelength for each emitter. Direct (or indirect
reflected ) eye contact with the laser beam might cause serious eye damage. Safety precautions and
interlock mechanisms have been designed to prevent any possible laser beam exposure to the operator.
The following label is attached on the back side of the machine.
Caution:
Use of controls or adjustments or performance of procedures other than those specified in this manual
might result in hazardous radiation exposure.
Notes:
The model names of the machines do not appear in the following pages. Check the type of your machine before reading this manual. (For details, see p.15 “Machine Types”.)
• Type 1: Aficio 3035
• Type 2: Aficio 3045
Certain types might not be available in some countries. For details, please contact your local dealer.
Two kinds of size notation are employed in this manual. With this machine refer to the metric version.
For good copy quality, Ricoh recommends that you use genuine Ricoh toner.
Ricoh shall not be responsible for any damage or expense that might result from the use of parts other
than genuine Ricoh parts with your Ricoh office products.
Power Source
220 - 240V, 50/60Hz, 8A or more
Please be sure to connect the power cord to a power source as above. For details about power source,
see p.153 “Power Connection”.

Manuals for This Machine
The following manuals describe the operational procedures of this machine. For
particular functions, see the relevant parts of the manual.
Note
❒ Manuals provided are specific to machine type.
❒ Adobe Acrobat Reader/Adobe Reader is necessary to view the manuals as a
PDF file.
❒ Two CD-ROMs are provided:
• CD-ROM 1 “Operating Instructions”
• CD-ROM 2 “Scanner Driver and Document Management Utility”
❖ General Settings Guide (this manual) (PDF file - CD-ROM1)
Provides an overview of the machine and describes System Settings (such as
Tray Paper Settings), Document Server functions, and troubleshooting.
Refer to this manual for Address Book procedures such as registering fax
numbers, e-mail addresses, and user codes.
❖ Security Reference
This manual is for administrators of this machine. It describes security functions that the administrators can use to protect data from being tampered, or
prevent the machine from unauthorized use.
Also refer to this manual for the procedures for registering administrators, as
well as setting user and administrator authentication.
❖ Network Guide (PDF file - CD-ROM1)
Provides information about configuring and operating the printer in a network environment or using software.
This manual covers all models, and therefore contains functions and settings
that may not be available for your model. Images, illustrations, functions, and
supported operating systems may differ from those of your model.
❖ Copy Reference (PDF file - CD-ROM1)
Describes operations, functions, and troubleshooting for the machine's copier
function.
❖ Facsimile Reference <Basic Features> (PDF file - CD-ROM1)
Describes operations, functions, and troubleshooting for the machine's facsimile function.
❖ Facsimile Reference <Advanced Features> (PDF file - CD-ROM1)
Describes advanced facsimile functions such as line settings and procedures
for registering IDs.
❖ Printer Reference (PDF file - CD-ROM1)
Describes system settings, operations, functions, and troubleshooting for the
machine's printer function.
i

❖ Scanner Reference (PDF file - CD-ROM1)
Describes operations, functions, and troubleshooting for the machine's scanner function.
❖ Manuals for DeskTopBinder Lite
DeskTopBinder Lite is a utility included on the CD-ROM labeled “Scanner
Driver and Document Management Utility”.
• DeskTopBinder Lite Setup Guide (PDF file - CD-ROM2)
Describes installation of, and the operating environment for DeskTopBinder Lite in detail. This guide can be displayed from the [Setup] display
when DeskTopBinder Lite is installed.
• DeskTopBinder Introduction Guide (PDF file - CD-ROM2)
Describes operations of DeskTopBinder Lite and provides an overview of
its functions. This guide is added to the [Start] menu when DeskTopBinder
Lite is installed.
•Auto Document Link Guide (PDF file - CD-ROM2)
Describes operations and functions of Auto Document Link installed with
DeskTopBinder Lite. This guide is added to the [Start] menu when DeskTopBinder Lite is installed.
❖ Other manuals
• PS3 Supplement (PDF file - CD-ROM1)
• Unix Supplement (Available from an authorized dealer, or as a PDF file on
our Web site.)
ii

What You Can Do with This Machine
The following introduces the functions of this machine, and the relevant manuals containing detailed information about them.
Products marked with * are optional. For details about optional products, see
p.19 “Options”, or contact your local dealer.
Copier, Facsimile, Printer, and Scanner Functions
AHT002S
This machine provides copier, facsimile*, printer*, and scanner* functions.
• You can make copies of originals.
With a finisher*, you can sort and
staple copies. See Copy Reference.
• You can send originals by fax or email, and receive faxes from other
parties. See Facsimile Reference <Ba-
sic Features>, and Facsimile Reference <Advanced Features>.
• You can print documents created
in computer applications. See
Printer Reference .
• You can scan originals and send
scan files to a computer. See Scan-
ner Reference.
Utilizing Stored Documents
GCKONN2J
• You can store files scanned by this
machine, or files sent from other
fax machine or computers, into the
machine's hard disk. You can print
and fax stored files as required.
You can also change print settings
and print multiple documents
(Document Server). See p.37 “Using the Document Server”.
• With DeskTopBinder Professional*/Lite, you can search, check,
print, and delete stored documents
using your computer. You can also
retrieve stored documents scanned
in scanner mode. With file format
converter*, you can even download documents stored in copy and
printer functions to your computer. See Network Guide and Scanner
Reference.
iii

Paperless Fax Transmission
Fax Transmission and
and Reception
Reception
GCKONN3J
• You can store received fax messages on the machine's hard disk, instead of printing them onto paper.
You can use DeskTopBinder Professional or Web Image Monitor to
check, print, delete, retrieve, or
download documents using your
computer (Storing received documents). See Facsimile Reference
<Advanced Features>.
Transmission
Reception Through the
Internet
xxx@xxx.com
xxx@xxx.com
GCKONN8J
•
You can send fax documents through
e-mail by specifying the recipient’s
e-mail address (Internet Fax Transmission).
You can receive sent documents
via Internet Fax, or from computers (Internet Fax Reception).
See Facsimile Reference<Basic Fea-
tures>.
• You can send faxes by using data
such as the IP address to specify
the IP-Fax destination (IP-Fax
Transmission).
The transmitted files can be received using an Internet fax machine (IP-Fax Reception). See
Facsimile Reference <Basic Features>.
• You can send documents created
in computer applications to another party's fax machine directly,
without performing a print job
(LAN-Fax). See Facsimile Reference
<Advanced Features>.
iv
AHT003S

Using the Scanner in a
Administrating the
Network Environment
AHT005S
• You can send scan files to a specified destination using e-mail
(Sending scan file by e-mail). See
Scanner Reference.
• With ScanRouter delivery software, you can save scan files in
specified destinations on network
computers (Using the network delivery scanner function). See Scan-
ner Reference.
• You can send scan files directly to
folders (Sending scan file by Scan
to Folder). See Scanner Reference.
Machine/Protecting
Documents (Security
Functions)
AHT006S
• You can protect documents from
unauthorized access and stop
them from being copied without
permission. See Security Reference.
• You can control the use of the machine, as well as prevent machine
settings from being changed without authorization. See Security Ref-
erence.
• By setting passwords, you can prevent unauthorized access via the
network. See Security Reference.
• You can erase the data on the hard
disk to prevent the information
from leaking out. See the manual
for the DataOverWriteSecurity
Unit* and Security Reference.
v

Monitoring the Machine Via
Preventing an Unauthorized
Computer
AHT007S
You can monitor machine status and
change settings using a computer.
• Using SmartDeviceMonitor for
Admin, SmartDeviceMonitor for
Client, or Web Image Monitor, you
can use a computer to view the machine's status, such as to check on
paper quantities, or misfeeds, etc.
See Network Guide.
• You can use Web Image Monitor to
make network settings. See Net-
work Guide.
• You can also use Web Image Monitor to register and manage items
such as user codes, fax numbers, email addresses, and folders in the
Address Book. See the Web Image
Monitor's Help.
•Using Web Image Monitor, you
can receive e-mails notifying you
when toner runs out or a paper
misfeed occurs. See the Web Image
Monitor Help.
•Using Web Image Monitor, you
can receive information on the machine status via e-mail. See the
Web Image Monitor Help.
Copy
AHU004S
• Using the printer driver, you can
embed a pattern in the printed
document. If the document is copied on a machine with the Copy
Data Security Unit*, protected pages are grayed out in the copy, preventing confidential information
from being copied. If the document is copied on a machine without the Copy Data Security Unit*,
the hidden text becomes conspicuous in the copy, showing that the
copy is unauthorized. See the
printer driver Help and Printer Ref-
erence.
• Using the printer driver, you can
embed text in the printed document for unauthorized copy prevention. If the document is copied,
scanned, or stored in a Document
Server by a copier or multifunction
printer, the embedded text appears conspicuous in the copy, discouraging such unauthorized
copying. See the printer driver
Help and Printer Reference.
• If a document protected by unauthorized copy guard is copied on a
machine that is equipped with the
Copy Data Security Unit*, the machine beeps to notify users that unauthorized copying is being
attempted. See Security Reference.
vi

TABLE OF CONTENTS
Manuals for This Machine ......................................................................................i
What You Can Do with This Machine..................................................................iii
Copier, Facsimile, Printer, and Scanner Functions................................................... iii
Utilizing Stored Documents....................................................................................... iii
Paperless Fax Transmission and Reception............................................................. iv
Fax Transmission and Reception Through the Internet............................................ iv
Using the Scanner in a Network Environment ........................................................... v
Administrating the Machine/Protecting Documents (Security Functions) ..................v
Monitoring the Machine Via Computer...................................................................... vi
Preventing an Unauthorized Copy ............................................................................ vi
Notice ......................................................................................................................1
Copyrights and Trademarks .................................................................................2
Trademarks................................................................................................................2
Information about Installed Software..........................................................................3
How to Read This Manual .....................................................................................9
Safety Information ...............................................................................................10
Safety During Operation...........................................................................................10
Positions of RWARNING and RCAUTION labels ............................................12
ENERGY STAR Program .....................................................................................13
Machine Types .....................................................................................................15
1. Getting Started
Guide to Components .........................................................................................17
Options .................................................................................................................19
External Options.......................................................................................................19
Internal Options........................................................................................................20
Control Panel........................................................................................................21
Display Panel ...........................................................................................................23
When the Authentication Screen is displayed..........................................................24
Turning On the Power .........................................................................................25
Turning On the Main Power .....................................................................................25
Turning On the Power..............................................................................................25
Turning Off the Power..............................................................................................26
Turning Off the Main Power .....................................................................................26
Saving Energy..........................................................................................................27
2. Combined Function Operations
Changing Modes ..................................................................................................29
Multi-Access.........................................................................................................31
vii

3. Document Server
Relationship between the Document Server and Other Functions.................35
Document Server Display ........................................................................................36
Using the Document Server................................................................................37
Storing Data .............................................................................................................37
Changing Stored Document's File Name, User Name, or Password.......................40
Searching for Stored Documents.............................................................................41
Printing Stored Documents ......................................................................................42
Deleting Stored Documents .....................................................................................45
Viewing Stored Documents Using Web Image Monitor ...........................................46
Downloading Stored Documents..............................................................................46
Settings for the Document Server......................................................................47
4. User Tools (System Settings)
User Tools Menu (System Settings)...................................................................49
Accessing User Tools (System Settings)..........................................................52
Changing Default Settings .......................................................................................52
Quitting User Tools ..................................................................................................52
Settings You Can Change with User Tools .......................................................53
General Features .....................................................................................................53
Tray Paper Settings .................................................................................................57
Timer Settings..........................................................................................................60
Administrator Tools ..................................................................................................62
5. Registering Addresses and Users for Facsimile/Scanner
Functions
Address Book.......................................................................................................69
Registering Names ..............................................................................................72
Registering a Name .................................................................................................72
Changing a Registered Name..................................................................................73
Deleting a Registered Name....................................................................................73
Authentication Information .................................................................................74
Registering a New User Code..................................................................................74
Changing a User Code.............................................................................................75
Deleting a User Code...............................................................................................76
Displaying the Counter for Each User Code ............................................................76
Printing the Counter for Each User Code.................................................................76
Clearing the Number of Prints..................................................................................77
Fax Destination ....................................................................................................78
Registering a Fax Destination..................................................................................79
Changing a Registered Fax Destination ..................................................................81
Deleting a Registered Fax Destination.....................................................................82
Registering an IP-Fax Destination ...........................................................................83
Changing a Registered IP-Fax Destination..............................................................84
Deleting a Registered IP-Fax Destination................................................................85
E-mail Destination................................................................................................87
Registering an E-mail Destination............................................................................87
Changing a Registered E-mail Destination ..............................................................88
Deleting a Registered E-mail Destination ................................................................89
viii
Registering Folders .............................................................................................90
Using SMB to Connect.............................................................................................90
Using FTP to Connect..............................................................................................94
Using NCP to Connect.............................................................................................97
Registering Names to a Group .........................................................................101
Registering a New Group.......................................................................................101
Registering Names to a Group...............................................................................102
Displaying Names Registered in Groups ...............................................................102
Removing a Name from a Group ...........................................................................103
Changing a Group Name .......................................................................................103
Deleting a Group....................................................................................................104
Adding a Group to Another Group .........................................................................104
Deleting a Group within a Group............................................................................104
Registering a Protection Code .........................................................................106
Registering a Protection Code To a Single User ...................................................106
Registering a Protection Code To a Group User ...................................................107
Registering the Transfer Request ....................................................................108
Registering a Transfer Station/Receiving Station ..................................................108
Changing a Registered Transfer Station/Receiving Station...................................110
Deleting a Registered Transfer Station/Receiving Station.....................................111
Registering Authentication...............................................................................112
SMTP Authentication .............................................................................................112
LDAP Authentication..............................................................................................113
6. Troubleshooting
If Your Machine Does Not Operate As You Want............................................115
General ..................................................................................................................115
Document Server ...................................................................................................118
B Loading Paper ...............................................................................................119
Loading Paper into Paper Trays ............................................................................119
Loading Paper into Large Capacity Tray (optional)................................................119
D Adding Toner.................................................................................................122
Removing Toner.................................................................................................123
Inserting Toner...................................................................................................124
x Clearing Misfeeds .........................................................................................125
Changing the Paper Size...................................................................................134
Changing the Paper Size of the Paper Tray .........................................................134
d Adding Staples..............................................................................................137
1000-Sheet Finisher...............................................................................................137
2 Tray Finisher .......................................................................................................138
Booklet Finisher .....................................................................................................140
Removing Jammed Staples ..............................................................................142
1000-Sheet Finisher...............................................................................................142
2 Tray Finisher .......................................................................................................143
Booklet Finisher .....................................................................................................144
y Removing Punch Waste ...............................................................................146
Replacing the Stamp Cartridge ........................................................................147
ix

7. Remarks
Dos and Don'ts...................................................................................................149
Toner...................................................................................................................150
Handling Toner.......................................................................................................150
Toner Storage ........................................................................................................151
Used Toner ............................................................................................................151
Where to Put Your Machine ..............................................................................152
Machine Environment ............................................................................................152
Moving....................................................................................................................152
Power Connection..................................................................................................153
Access to the Machine...........................................................................................153
Maintaining Your Machine ................................................................................154
Cleaning the Exposure Glass.................................................................................154
Cleaning the Exposure Glass Cover......................................................................154
Cleaning the Auto Document Feeder.....................................................................154
Changing the Photoconductor Unit (PCU) .............................................................155
Other Functions .................................................................................................156
Inquiry ....................................................................................................................156
Changing the Language.........................................................................................156
Counter ...............................................................................................................157
Displaying the Total Counter..................................................................................157
8. Entering Text
Entering Text ......................................................................................................159
Available Characters..............................................................................................159
Keys .......................................................................................................................159
How to Enter Text ..................................................................................................160
9. Specifications
Main unit .............................................................................................................161
Options ...............................................................................................................165
Exposure Glass Cover ...........................................................................................165
Auto Document Feeder..........................................................................................165
1000-Sheet Finisher...............................................................................................165
2 Tray Finisher .......................................................................................................167
Punch Kit................................................................................................................168
Booklet Finisher .....................................................................................................169
Bridge Unit .............................................................................................................170
Internal Tray 2 (1 bin tray)......................................................................................171
Large Capacity Tray...............................................................................................171
Paper Tray Unit......................................................................................................172
Copy Paper .........................................................................................................173
Recommended Paper Sizes and Types.................................................................173
Unusable Paper .....................................................................................................176
Paper Storage........................................................................................................177
INDEX....................................................................................................... 178
x

Notice
Notice To Wireless LAN Interface (optional) Users
Notice to Users in EEA Countries
This product complies with the essential requirements and provisions of Directive 1999/5/EC of the European Parliament and of the Council of 9 March 1999
on radio equipment and telecommunications terminal equipment and the mutual recognition of their conformity.
The CE Declaration of Conformity is available on the Internet at URL:
http://www.ricoh.co.jp/fax/ce_doc/.
This product is only for use in EEA or other authorized countries. Outdoor use
of this product in Belgium, France, Germany, Italy, or the Netherlands is prohibited.
1

Copyrights and Trademarks
Trademarks
Microsoft®, Windows® and Windows NT® are registered trademarks of Microsoft Corporation in the United States and/or other countries.
Acrobat
The Bluetooth
any use of such marks by Ricoh Company, Ltd. is under license.
NetWare is a registered trademark of Novell, Inc.
Other product names used herein are for identification purposes only and might
be trademarks of their respective companies. We disclaim any and all rights to
those marks.
The proper names of the Windows operating systems are as follows:
• The product name of Windows
• The product name of Windows
• The product name of Windows
• The product names of Windows
• The product names of Windows
• The product names of Windows Server™ 2003 are as follows:
• The product names of Windows
®
is a registered trademark of Adobe Systems Incorporated.
®
word mark and logos are owned by the Bluetooth SIG, Inc. and
Edition (Windows Me)
Microsoft
Microsoft
Microsoft
Microsoft
Microsoft
Microsoft
Microsoft
Microsoft
Microsoft
Microsoft
®
Windows® 2000 Advanced Server
®
Windows® 2000 Server
®
Windows® 2000 Professional
®
Windows® XP Professional
®
Windows® XP Home Edition
®
Windows Server™ 2003 Standard Edition
®
Windows Server™ 2003 Enterprise Edition
®
Windows Server™ 2003 Web Edition
®
Windows NT® Server 4.0
®
Windows NT® Workstation 4.0
®
95 is Microsoft® Windows® 95
®
98 is Microsoft® Windows® 98
®
Me is Microsoft® Windows® Millennium
®
2000 are as follows:
®
XP are as follows:
®
NT are as follows:
2

Information about Installed Software
expat
• The software including controller, etc. (hereinafter "software") installed on
this product uses the expat under the conditions mentioned below.
• The product manufacturer provides warranty and support to the software of
the product including the expat, and the product manufacturer makes the initial developer and copyright holder of the expat, free from these obligations.
• Information relating to the expat is available at:
http://expat.sourceforge.net/
Copyright (c) 1998, 1999, 2000 Thai Open Source Software Centre, Ltd. and Clark
Cooper.
Copyright © 2001, 2002 Expat maintainers.
Permission is hereby granted, free of charge, to any person obtaining a copy of
this software and associated documentation files (the "Software"), to deal in the
Software without restriction, including without limitation the rights to use,
copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the
Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY
KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE
WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR
PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT,
TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
NetBSD
1. Copyright Notice of NetBSD
For all users to use this product:
This product contains NetBSD operating system:
For the most part, the software constituting the NetBSD operating system is not
in the public domain; its authors retain their copyright.
The following text shows the copyright notice used for many of the NetBSD
source code. For exact copyright notice applicable for each of the files/binaries,
the source code tree must be consulted.
A full source code can be found at http://www.netbsd.org/.
Copyright © 1999, 2000 The NetBSD Foundation, Inc.
All rights reserved.
3

Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
A Redistributions of source code must retain the above copyright notice, this list
of conditions and the following disclaimer.
B Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
C All advertising materials mentioning features or use of this software must
display the following acknowledgment:
This product includes software developed by The NetBSD Foundation, Inc.
and its contributors.
D Neither the name of The NetBSD Foundation nor the names of its contribu-
tors may be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE NETBSD FOUNDATION, INC. AND
CONTRIBUTORS ''AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE FOUNDATION OR CONTRIBUTORS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF
USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE,
EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
2.Authors Name List
All product names mentioned herein are trademarks of their respective owners.
The following notices are required to satisfy the license terms of the software
that we have mentioned in this document:
• This product includes software developed by the University of California,
Berkeley and its contributors.
• This product includes software developed by Jonathan R. Stone for the NetB-
SD Project.
•This product includes software developed by the NetBSD Foundation, Inc.
and its contributors.
• This product includes software developed by Manuel Bouyer.
• This product includes software developed by Charles Hannum.
• This product includes software developed by Charles M. Hannum.
• This product includes software developed by Christopher G. Demetriou.
• This product includes software developed by TooLs GmbH.
• This product includes software developed by Terrence R. Lambert.
•
This product includes software developed by Adam Glass and Charles Hannum.
• This product includes software developed by Theo de Raadt.
4
• This product includes software developed by Jonathan Stone and Jason R.
Thorpe for the NetBSD Project.
• This product includes software developed by the University of California,
Lawrence Berkeley Laboratory and its contributors.
• This product includes software developed by Christos Zoulas.
• This product includes software developed by Christopher G. Demetriou for
the NetBSD Project.
• This product includes software developed by Paul Kranenburg.
• This product includes software developed by Adam Glass.
• This product includes software developed by Jonathan Stone.
• This product includes software developed by Jonathan Stone for the NetBSD
Project.
• This product includes software developed by Winning Strategies, Inc.
•This product includes software developed by Frank van der Linden for the
NetBSD Project.
• This product includes software developed for the NetBSD Project by Frank
van der Linden
• This product includes software developed for the NetBSD Project by Jason R.
Thorpe.
• The software was developed by the University of California, Berkeley.
• This product includes software developed by Chris Provenzano, the Univer-
sity of California, Berkeley, and contributors.
Sablotron
Sablotron (Version 0.82) Copyright © 2000 Ginger Alliance Ltd. All Rights Reserved
a) The application software installed on this product includes the Sablotron software Version 0.82 (hereinafter, "Sablotron 0.82"), with modifications made by
the product manufacturer. The original code of the Sablotron 0.82 is provided by
Ginger Alliance Ltd., the initial developer, and the modified code of the Sablotron 0.82 has been derived from such original code provided by Ginger Alliance
Ltd.
b) The product manufacturer provides warranty and support to the application
software of this product including the Sablotron 0.82 as modified, and the product manufacturer makes Ginger Alliance Ltd., the initial developer of the Sablotron 0.82, free from these obligations.
c)
The Sablotron 0.82 and the modifications thereof are made available under the
terms of Mozilla Public License Version 1.1 (hereinafter, "MPL 1.1"), and the application software of this product constitutes the "Larger Work" as defined in
MPL 1.1. The application software of this product except for the Sablotron 0.82 as
modified is licensed by the product manufacturer under separate agreement(s).
d) The source code of the modified code of the Sablotron 0.82 is available at: http://support-download.com/services/device/sablot/notice082.html
e)
The source code of the Sablotron software is available at: http://www.gingerall.com
f) MPL 1.1 is available at: http://www.mozilla.org/MPL/MPL-1.1.html
5

JPEG LIBRARY
• The software installed on this product is based in part on the work of the In-
dependent JPEG Group.
SASL
CMU libsasl
Tim Martin
Rob Earhart
Rob Siemborski
Copyright (c) 2001 Carnegie Mellon University. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
A Redistributions of source code must retain the above copyright notice, this list
of conditions and the following disclaimer.
B Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
C The name "Carnegie Mellon University" must not be used to endorse or pro-
mote products derived from this software without prior written permission.
For permission or any other legal details, please contact:
Office of Technology Transfer
Carnegie Mellon University
5000 Forbes Avenue
Pittsburgh, PA 15213-3890
(412) 268-4387, fax: (412) 268-7395
tech-transfer@andrew.cmu.edu
D Redistributions of any form whatsoever must retain the following acknowl-
edgment:
"This product includes software developed by Computing Services at Carnegie Mellon University (http://www.cmu.edu/computing/)."
CARNEGIE MELLON UNIVERSITY DISCLAIMS ALL WARRANTIES WITH
REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL CARNEGIE
MELLON UNIVERSITY BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING
FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT
OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
6

MD4
Copyright (C) 1990-2, RSA Data Security, Inc. All rights reserved.
License to copy and use this software is granted provided that it is identified as
the "RSA Data Security, Inc. MD4 Message-Digest Algorithm" in all material
mentioning or referencing this software or this function.
License is also granted to make and use derivative works provided that such
works are identified as "derived from the RSA Data Security, Inc. MD4 MessageDigest Algorithm" in all material mentioning or referencing the derived work.
RSA Data Security, Inc. makes no representations concerning either the merchantability of this software or the suitability of this software for any particular
purpose. It is provided "as is" without express or implied warranty of any kind.
These notices must be retained in any copies of any part of this documentation
and/or software.
MD5
Copyright (C) 1991-2, RSA Data Security, Inc. Created 1991. All rights reserved.
License to copy and use this software is granted provided that it is identified as
the "RSA Data Security, Inc. MD5 Message-Digest Algorithm" in all material
mentioning or referencing this software or this function.
License is also granted to make and use derivative works provided that such
works are identified as "derived from the RSA Data Security, Inc. MD5 MessageDigest Algorithm" in all material mentioning or referencing the derived work.
RSA Data Security, Inc. makes no representations concerning either the merchantability of this software or the suitability of this software for any particular
purpose. It is provided "as is" without express or implied warranty of any kind.
These notices must be retained in any copies of any part of this documentation
and/or software.
7

Samba(Ver 2.2.2-ja-1.1)
For SMB transmission, this machine uses Samba ver 2.2.2-ja-1.1 (hereinafter referred to as Samba 2.2.2-ja-1.1).
Copyright © Andrew Tridgell 1994-1998
This program is free software; you can redistribute it and/or modify it under the
terms of the GNU General Public License as published by the Free Software
Foundation; either version 2 of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT
ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public
License for more details.
You should have received a copy of the GNU General Public License along with
this program; if not, write to the Free Software Foundation, Inc., 675 Mass Ave,
Cambridge, MA 02139, USA
Note
❒ The source code for SMB transmission by this machine can be downloaded
from the following website:
http://support-download.com/services/scbs
RSA BSAFE
®
• This product includes RSA BSAFE® cryptographic or security protocol soft-
ware from RSA Security Inc.
• RSA and BSAFE are registered trademarks of RSA Security Inc. in the United
States and/or other countries.
• RSA Security Inc. All rights reserved.
8

How to Read This Manual
R
R
Symbols
The following set of symbols is used in this manual.
WARNING:
This symbol indicates a potentially hazardous situation that might result in
death or serious injury when you misuse the machine without following the instructions under this symbol. Be sure to read the instructions, all of which are described in the Safety Information section.
CAUTION:
This symbol indicates a potentially hazardous situation that might result in minor or moderate injury or property damage that does not involve personal injury
when you misuse the machine without following the instructions under this
symbol. Be sure to read the instructions, all of which are described in the Safety
Information section.
* The statements above are notes for your safety.
Important
If this instruction is not followed, paper might be misfed, originals might be
damaged, or data might be lost. Be sure to read this.
Preparation
This symbol indicates information or preparations required prior to operating.
Note
This symbol indicates precautions for operation, or actions to take after abnormal operation.
Limitation
This symbol indicates numerical limits, functions that cannot be used together,
or conditions in which a particular function cannot be used.
Reference
This symbol indicates a reference.
[]
Keys that appear on the machine's display panel.
{}
Keys built into the machine's control panel.
9

Safety Information
R
R
When using this machine, the following safety precautions should always be followed.
Safety During Operation
In this manual, the following important symbols are used:
WARNING:
CAUTION:
Indicates a potentially hazardous situation which, if instructions
are not followed, could result in death or serious injury.
Indicates a potentially hazardous situation which, if instructions are not
followed, may result in minor or moderate injury or damage to property.
R WARNING:
• Connect the power cord directly into a wall outlet and do not use an
extension cord.
• Disconnect the power plug (by pulling the plug, not the cable) if the
power cable or plug becomes frayed or otherwise damaged.
• To avoid hazardous electric shock or laser radiation exposure, do not
remove any covers or screws other than those specified in this manual.
• Turn off the power and disconnect the power plug (by pulling the plug,
not the cable) if any of the following occurs:
• You spill something into the machine.
• You suspect that your machine needs service or repair.
• The external housing of your machine has been damaged.
• Do not incinerate used toner or toner containers. Toner dust might ig-
nite when exposed to an open flame.
• Disposal can take place at our authorized dealer.
• Dispose of used toner containersin accordance with local regulations.
• Keep the machine away from flammable liquids, gases, and aerosols.
A fire or an electric shock might occur.
• Connect the machine only to the power source described on the inside front cover of this manual.
• Do not damage, break or make any modifications to the power cord.
Do not place heavy objects on it. Do not pull it hard nor bend it more
than necessary. These actions could cause an electric shock or fire.
10

R CAUTION:
• Protect the machine from dampness or wet weather, such as rain and snow.
• Unplug the power cord from the wall outlet before you move the machine.
While moving the machine, you should take care that the power cord will not
be damaged under the machine.
• When you disconnect the power plug from the wall outlet, always pull the
plug (not the cable).
• Do not allow paper clips, staples, or other small metallic objects to fall inside
the machine.
• Keep toner (used or unused) and toner containers out of reach of children.
• For environmental reasons, do not dispose of the machine or expended
supply waste at household waste collection points. Disposal can take place
at an authorized dealer.
• The inside of the machine could be very hot. Do not touch the parts with a
label indicating the “hot surface”. Otherwise, an injury might occur.
• The fusing section of this machine might be very hot. Caution should be taken when removing misfed paper.
• Keep the machine away from humidity and dust. Otherwise a fire or an electric shock might occur.
• Do not place the machine on an unstable or tilted surface. If it topples over,
an injury might occur.
• Do not use aluminum foil, carbon paper, or similar conductive paper to avoid
a fire or machine failure.
• If you use the machine in a confined space, make sure there is a continuous
air turnover.
• If toner or used toner is inhaled, gargle with plenty of water and move into a
fresh air environment. Consult a doctor if necessary.
• If toner or used toner gets into your eyes, flush immediately with large
amounts of water. Consult a doctor if necessary.
• If toner or used toner is swallowed, dilute by drinking a large amount of water. Consult a doctor if necessary.
• Avoid getting toner on your clothes or skin when removing a paper jam or
replacing toner. If your skin comes into contact with toner, wash the affected
area thoroughly with soap and water.
• If toner gets on your clothing, wash with cold water. Hot water will set the
toner into the fabric and may make removing the stain impossible.
11

Positions of RWARNING and RCAUTION
labels
This machine has labels for RWARNING and RCAUTION at the positions shown
below. For safety, please follow the instructions and handle the machine as indicated.
12
ZKZH010E

ENERGY STAR Program
As an ENERGY STAR Partner, we have determined
that this machine model meets the ENERGY STAR
Guidelines for energy efficiency.
The ENERGY STAR Guidelines intend to establish an international energy-saving system for
developing and introducing energy-efficient office equipment to deal with environmental issues, such as global warming.
When a product meets the ENERGY STAR Guidelines for energy efficiency, the Partner shall
place the ENERGY STAR logo onto the machine model.
This product was designed to reduce the environmental impact associated with office equipment by means of energy-saving features, such as Low-power mode.
❖ Low-Power mode and Off mode or Sleep mode
This product automatically lowers its power consumption when it is not operated for a fixed time (standard setting time: 1 minute). This is called “Off
mode” on a single function copying machine, and “Sleep mode” on a multiple
function machine equipped with optional facsimile and printing functions.
• Off mode: Same as the condition when the operation switch is turned off.
• Sleep mode: Same as the condition when the operation switch is turned off.
Receiving fax messages and printing from a computer are possible.
If you want to operate this product while it is in either of these modes, do one
of the following:
• Turn on the operation switch.
• Place an original in the Auto Document Feeder (ADF).
• Lift and lower the exposure glass cover or the ADF.
The default interval before entering Off mode or Sleep mode can be adjusted.
To change it, see p.60 “Auto Off Timer”.
The ENERGY STAR Program establishes two modes which lower the power
consumption of the product when it is not operated for a fixed time. These
modes are the Low-power mode and the Off mode or Sleep mode. This product has only one mode, the Off mode or Sleep mode. This mode meets the requirements of both the Low-power mode and Off mode or Sleep mode. In this
manual, the Off mode is called the Auto Off mode.
❖ Duplex Priority
The ENERGY STAR Program recommends the duplex function. By conserving paper resources this function is less of a burden to the environment. For
applicable machines, duplex function (one-sided originals→ two-sided copies) can be selected preferentially when the operation switch or the main power switch is turned on, the {Energy Saver} key is pressed, or the machine resets
automatically.
13

Reference
To change the settings of the Duplex Priority mode, see “Duplex Mode Priority”in “General Features 2/4”, Copy Reference.
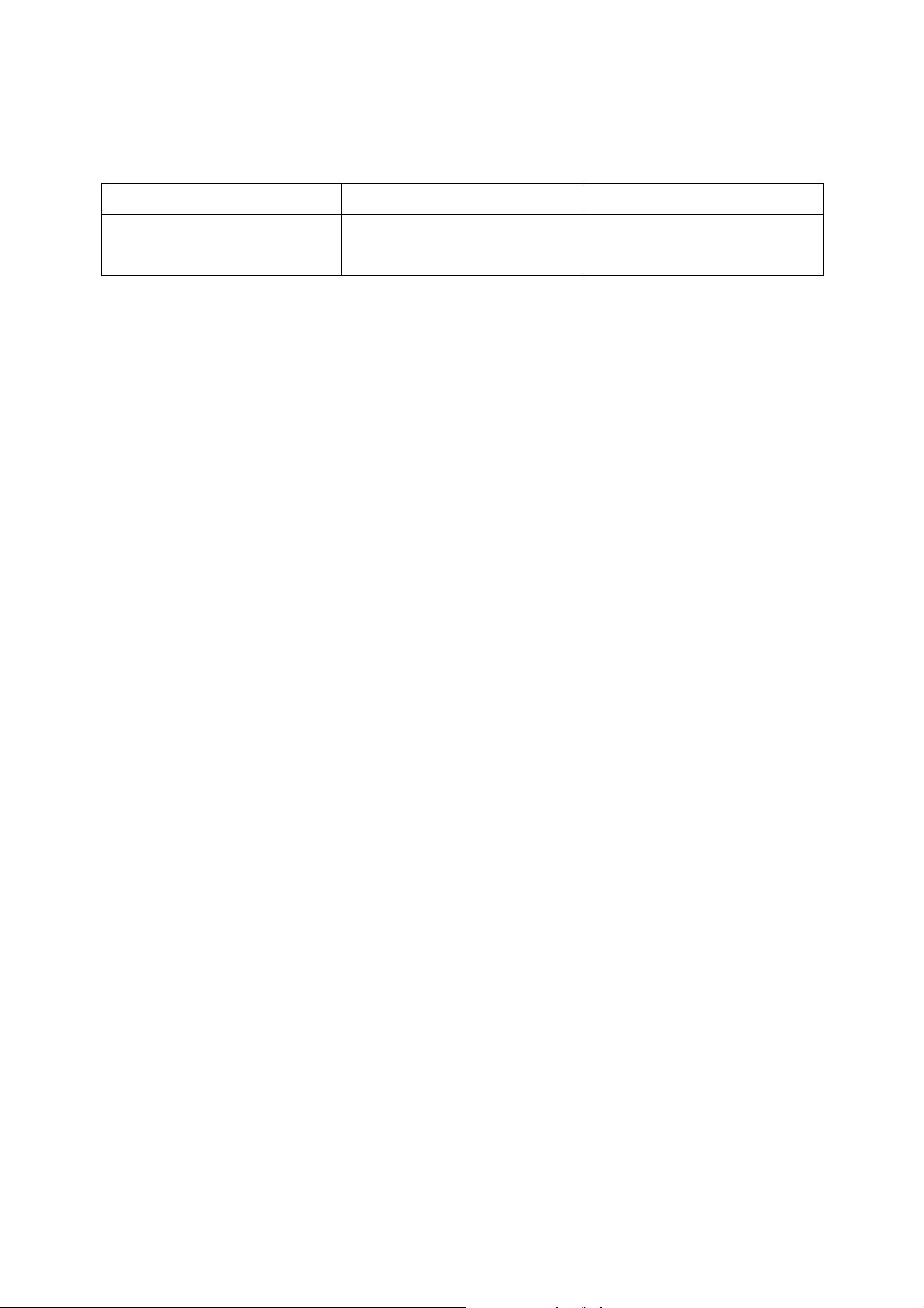
Specifications
Copier only
Type 1 Type 2 Type 1 Type 2
Low-power
Mode, Off
Mode
Low-power
mode, Sleep
mode
Duplex priority One-sided→One-sided
Power consumption
Default interval
Recovery time
Power consumption
Default interval
Recovery time
1.2 W
1 minute —
10 seconds or less —
—
— 1 minute
— 10 seconds or less
Fax, printer and scanner installed
—
8.4 W
Recycled Paper
In accordance with the ENERGY STAR Program, we recommend use of recycled
paper which is environmentally friendly. Please contact your sales representative for recommended paper.
14
Machine Types
This machine comes in two models which vary in copy speed. To ascertain
which model you have, see the inside front cover.
Type 1 Type 2
Copy speed 35 copies/minute
(A4K, 8
1
/2" × 11"K)
45 copies/minute
(A4K, 81/2" × 11"K)
15

16

1. Getting Started
Guide to Components
1. Exposure glass cover (optional) or
Auto Document Feeder (ADF) (optional)
See p.19 “External Options”.
(The illustration shows the ADF.)
2. Exposure glass
Place originals face down here for copying.
3. Internal tray
Copied, printed paper or fax messages
are delivered here.
4. Main power switch
If the machine does not operate after
turning on the operation switch, check
the main power switch is turned on. See
p.25 “Turning On the Power”.
5. Main power indicator
Lights when the main power switch is
turned on, and goes off when the switch
is turned off.
AHU003S
6. On indicator
Lights when the operation switch is
turned on, and goes off when the switch
is turned off.
7. Operation switch
Press to turn the power on (the On indicator lights up). To turn the power off,
press again (the On indicator goes off).
See p.25 “Turning On the Power”.
8. Control panel
See p.21 “Control Panel”.
9.
Internal tray 2 (1 bin tray) (optional)
The indicator lights when paper is delivered to internal tray 2 (1 bin tray). If internal tray 2 has not been installed, the
indicator does not light. See p.19 “External Options”.
10. Duplex unit (unit for two-sided
copies)
Allows you to print on both sides of a
piece paper in copier and printer function.
17

Getting Started
1
11. Front cover
Open to access the inside of the machine.
12. Paper tray (upper: Tray 1, lower:
Tray 2)
Load paper here.
1. Bypass tray
Use when copying onto OHP transparencies, adhesive labels, translucent paper,
postcards, and custom size paper.
13. Paper tray unit (optional <up-
per: Tray 3, lower: Tray 4>)
ZDSH020J
2. Right side cover
Open this when a paper jam occurs.
1. Ventilation holes
Prevent overheating. Do not obstruct the
ventilation holes by placing objects near
them or leaning things against them. If
the machine overheats, a fault might occur.
18
AHU009S
 Loading...
Loading...