Page 1
2 Megapixels
Compact High-End
Network Camera
User’s Manual
Draft v1.2
- 1 -
Page 2

INDEX
1 OVERVIEW ..................................................................................................................- 3 -
2 PRODUCT DESCRIPTION .............................................................................................- 3 -
2.1 H
ARDWARE DESCRIPTION
........................................................................................... - 4 -
3 SETTING UP THE NETWORK CAMERA .......................................................................- 5 -
3.1 R
3.2 H
3.3 U
EAD BEFORE USE
ARDWARE INSTALLATION STEPS
SING THE NETWORK CAMERA FOR THE FIRST TIME
.....................................................................................................- 5 -
.................................................................................. - 5 -
......................................................... - 6 -
4 ACCESSING THE NETWORK CAMERA.........................................................................- 7 -
4.1 F
4.2 B
4.3 E
4.4 A
4.5 A
4.6 T
INDING THE CAMERA
EFORE ASSIGNING AN IP ADDRESS
XECUTING THE IP DISCOVERY
SSIGNING THE IP ADDRESS TO THE NETWORK CAMERA
CCESS THE CAMERA FROM THE BROWSER
HE LIVE VIEW PAGE
................................................................................................. - 7 -
.............................................................................. - 7 -
..................................................................................... - 7 -
...................................................................... - 8 -
............................................................................................... - 10 -
.................................................... - 8 -
5 CONFIGURING THE CAMERA ...................................................................................- 12 -
5.1 V
5.2 C
IDEO SETTINGS
AMERA SETTINGS
......................................................................................................- 12 -
................................................................................................... - 14 -
5.3 S
5.4 E
5.5 N
5.6 S
5.7 A
TORAGE SETTINGS
VENT SETTINGS
ETWORK SETTINGS
YSTEM SETTINGS
PPLICATION
.....................................................................................................- 16 -
.......................................................................................................... - 27 -
.................................................................................................. - 15 -
................................................................................................ - 20 -
....................................................................................................- 27 -
6 TROUBLESHOOTING.................................................................................................- 35 -
6.1 E
6.2 V
MERGENCY FACTORY DEFAULT
IEWING THE CAMERA FROM A REMOTE LOCATION
................................................................................. - 35 -
......................................................... - 36 -
7 FREQUENTLY ASKED QUESTIONS ............................................................................- 39 -
8 TECHNICAL SPECIFICATIONS ....................................................................................- 41 -
9 GLOSSARY OF TERMS ...............................................................................................- 43 -
10 FCC STATEMENT………………………………………………………………………………………………- 50 -
- 2 -
Page 3
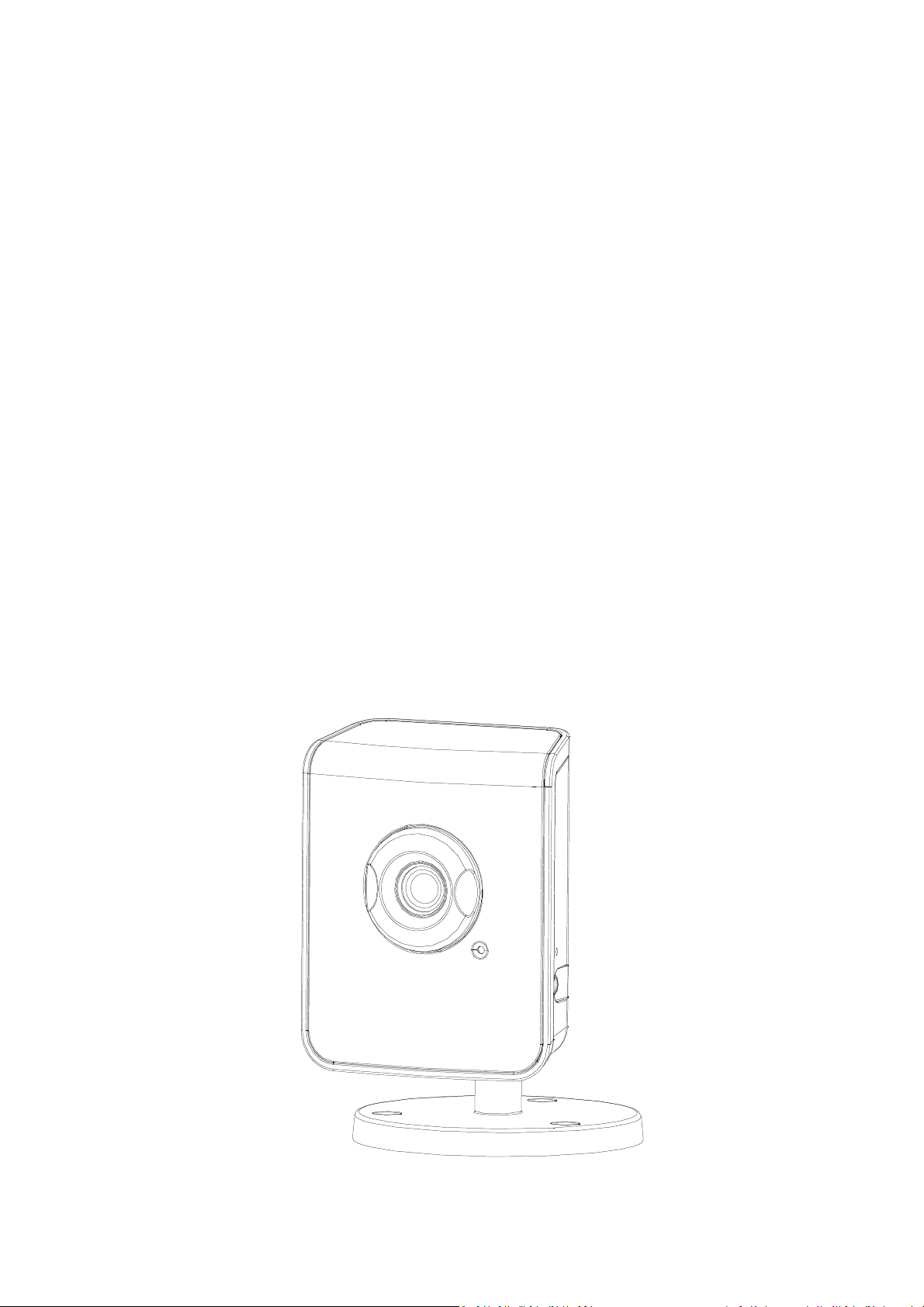
1 Overview
This network camera is intended for your home and commercial surveillance usage under indoor environments.
It comes with a High-end 2-megapixel CMOS Sensor, with a maximum resolution of 1600 x 1200, delivering detailed
images and covering 6 times larger than a VGA camera.
The dPTZ (Digital Pan Tilt Zoom) allows user to navigate through the area of the image of most interest without
relocating the camera physically. With unique features it delivers a simple solution for securing and monitoring.
2 Product Description
Key features
1. H.264 High Profile / MJPEG Dual Compression:
Offers the user the option to select H.264 or MJPEG compression.
2. Compact Size for Easy Installation and Maneuvering:
Small and light weighted, for areas that are limited in space.
3. ONVIF ® Compliant for Easy Integration & Fast Deployment:
Web services built-in with international standard protocols, integration cycles have been reduced and
deployment has become easier. ( Contact your distributor for documentation).
4. Multiple video profiles simultaneously for streaming:
Streams up to 6 independent streams with multiple profiles.
Different configurations can be set according to the bandwidth that is available from the network.
5. Speaker and Microphone Hidden & Built-In:
Offers integrated speaker and Microphone, allowing remote listening in the area where the camera is
installed, as well as communication with the other person using the speaker.
6. Micro SD Card Slot for Local Storage
For saving snapshots that can be later checked by the user, upon events occurred during motion detection.
7. Wi-Fi, IEEE 802.11 b/g for Wireless Networks (Optional)
For areas that wiring network cables is difficult and arduous work, using the wireless feature can be an
effort-saver.
8. Infrared LED for Day & Night Model,3 ~5 Meters (Optional)
There are 7 infrared LEDs located underneath the transparent cover.
- 3 -
Page 4
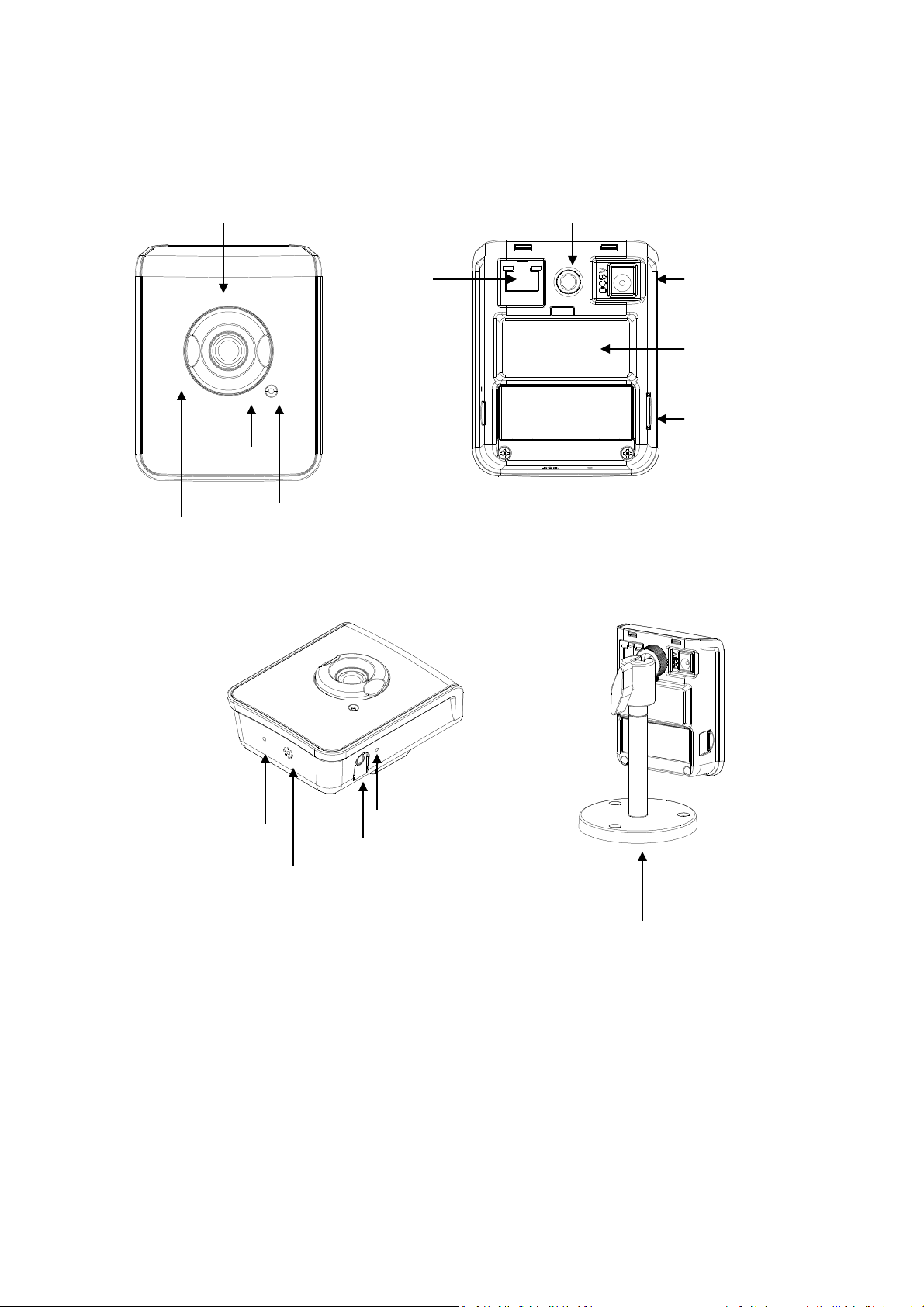
2.1 Hardware Description
Bracket
(
Back
Side
View
)
Speaker
Microphone
Audio Out
(
Lower Side
View
)
Default Button
Network
Power Connector
Built-In Wireless
A
ntenna
(optional)
Micro SD Card slot
Bracket Nut Hole
(
Back
Panel View
)
Light Sensor (Optional)
*
Lens Focus Ring
( Front Panel View
)
Built-In
Infrared
Power LED
Connector
LEDs (optional)
- 4 -
Note: * For Day only models, the Light Sensor will be replaced with the Power LED
Page 5
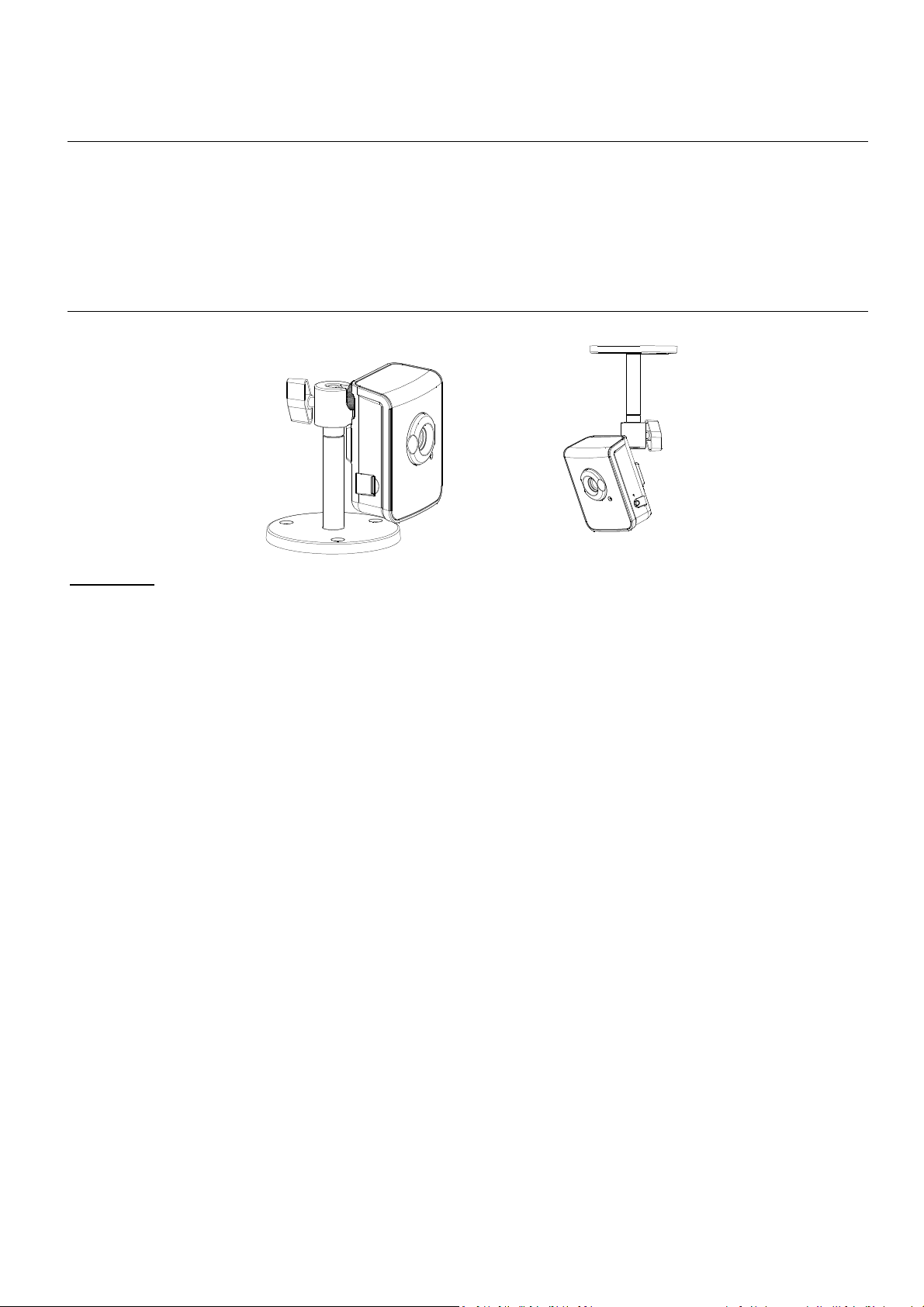
3 Setting up the Network Camera
1. Attach
the bracket that
(
Back
Panel View
)
3.1 Read Before Use
The use of surveillance devices may be prohibited by law in your country. The Network Camera is not only a
high-performance web-ready camera but can also be part of a flexible surveillance system. It is the user’s
responsibility to ensure that the operation of such devices is legal before installing this unit for its intended use.
It is important to first verify that all contents received are complete. Take note of the warnings in the Quick
Installation Guide before the Network Camera is installed; then carefully read and follow the instructions in the
Installation chapter to avoid damage due to faulty assembly and installation. This also ensures the product is used
properly as intended. It is designed for various applications including video sharing, general security/surveillance,
etc.
3.2 Hardware Installation Steps
After unpacking the package and identifying its parts, assemble the network camera to run the device for the first
time.
It is recommended set up the camera before installing it to the intended location.
The following instructions will consist of basic steps that will help you through the hardware preparation.
Other required devices before powering up the Network Camera:
1. Personal Computer or Laptop; and
2. Network Hub or Switch and 2 (two) pieces of Ethernet Cable; or
3. 1(one) piece of Crossover Ethernet Cable
STEPS:
comes in the package to the
Bracket Nut Hole
2. Connect the Ethernet Plug to
the Network Connector RJ-45
from the device
3. Plug the Power Jack to the
Power Connector
4. After the Power Connector is
plugged in, the Network
Camera will boot up.
The Power LED will be on to
guarantee the proper
functioning.
5. Wait a few seconds for the
Network Camera to be
detected in the network.
6. Refer to the section of “Using
the Network Camera for the
first time” in the next page
- 5 -
Page 6
3.3 Using the Network Camera for the first time
The Network Camera is a network device and its use should be straightforward for those who have basic
networking knowledge. Making the initial steps for setting up the network camera will be based on a simple
network connection.
Option 1
Connect the network camera to a HUB / Switch which is connected to a PC
Option 2
Connect the network camera directly to a PC with a crossover cable.
After the network camera has its activity lights on, use the PC for setting up the IP Address of the Network camera.
Refer to the section of “Accessing the Network Camera” at the next page for detailed instructions.
Hints: Possible Network Configurations in your network infrastructure
1. Configuration 1
Internet Access: ADSL or Cable Modem
IP address: One real IP or one dynamic IP
Connection Type: Only the Network Camera connects to the internet
For fixed real IP, set up the IP into the Network camera. For dynamic IP, start PPPoE.
2. Configuration 2
Internet Access: ADSL or Cable Modem
IP address: More than one real IP or one dynamic IP
Connection Type: The Network Camera and PC connect to the internet
Device needed: Switch Hub
For fixed real IP, set up the IP into the Network camera and PC. For dynamic IP, start
PPPoE.
3. Configuration 3
Internet Access: ADSL or Cable Modem
IP address: one real IP or one dynamic IP
Connection Type: The Network Camera and PC connect to the internet
Device needed: IP sharing such as Hub / Switch and a Router
Use virtual IP, set up port forwarding in IP sharing.
(Suggestion: Refer to your Network Administrator if necessary for more information)
- 6 -
Page 7

4 Accessing the Network Camera
4.1 Finding the camera
IP Discovery Tool
IP Discovery is the software that provides an easier way for setting the IP address and network configurations of
the Network Camera. Using this tool, you can easily set multiple Network Cameras at the same time.
By utilizing the IP Discovery tool, the setting process is largely simplified and the setting time is effectively
shortened.
4.2 Before Assigning an IP Address
Make sure the Network Camera is powered on and correctly connected to the network.
Obtain a LAN IP address not yet used and its related configuration from your network administrator.
The following will be required:
1. IP Address
2. Subnet Mask
3. Gateway
4. DNS1
5. DNS2
6. Port
MAC Address: Each Network Camera has a unique Ethernet address (MAC address) shown on the bottom of the
Network Camera as the serial number (S/N) with 12 digits (e.g. 00-0E-C9-03-21-73) .
Hints: When assigning an IP Address
Always consult your network administrator before assigning an IP address to your server.
4.3 Executing the IP Discovery
Locate the IP Discovery software in the CD and click on “IPDIS.exe” to execute the software.
After executing the IP Discovery software, you will have the following screen.
- 7 -
Page 8
4.4 Assigning the IP address to the network camera
Identify your Network Camera by its MAC address, which is located in the Product Label on the Network Camera.
Click on the network camera for which a new IP address will be assigned to it, and proceed to fill with the
following information.
1. IP Address
2. Subnet Mask
3. Gateway
Once filled in, click on “Change IP” to apply the changes made on the Network Camera.
Close the IP Discovery Utility tool and you should be able to access the camera from the browser.
To access the network camera, select the MAC address and click on Browse.
4.5 Access the camera from the browser
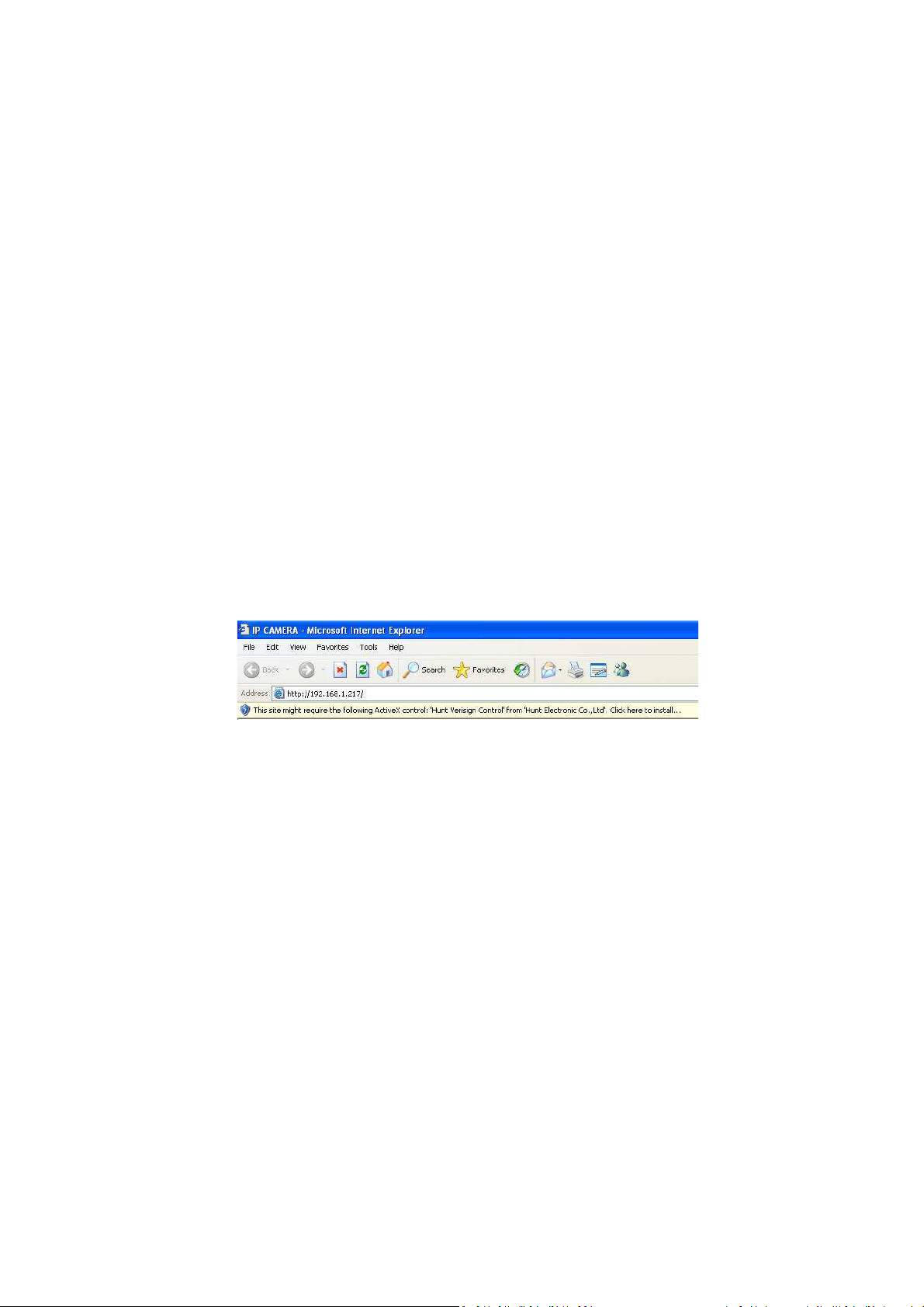
Start the Internet Explorer browser to start accessing the network camera.
Enter the IP address or host name of the camera in the Location/Address field of your browser.
The first time when the Network Camera is accessed, the Live View page will be shown without
restrictions.
Once entered, click OK and you should be able to see Live View Page.
For the first time to view the camera video via Internet Explorer, it will ask you to install the ActiveX component.
To allow the installation of the ActiveX , adjust the Security Options of Internet Explorer follow the below
instructions:
Internet Explorer > Tools > Internet Options > Security Tab > Custom Level > Security Settings > Download
unsigned ActiveX controls > Select “Enable” or Prompt.
Internet Explorer > Tools > Internet Options > Security Tab > Custom Level > Initialize and script ActiveX controls
not marked as safe > Select “Enable” or Prompt
- 8 -
Page 9
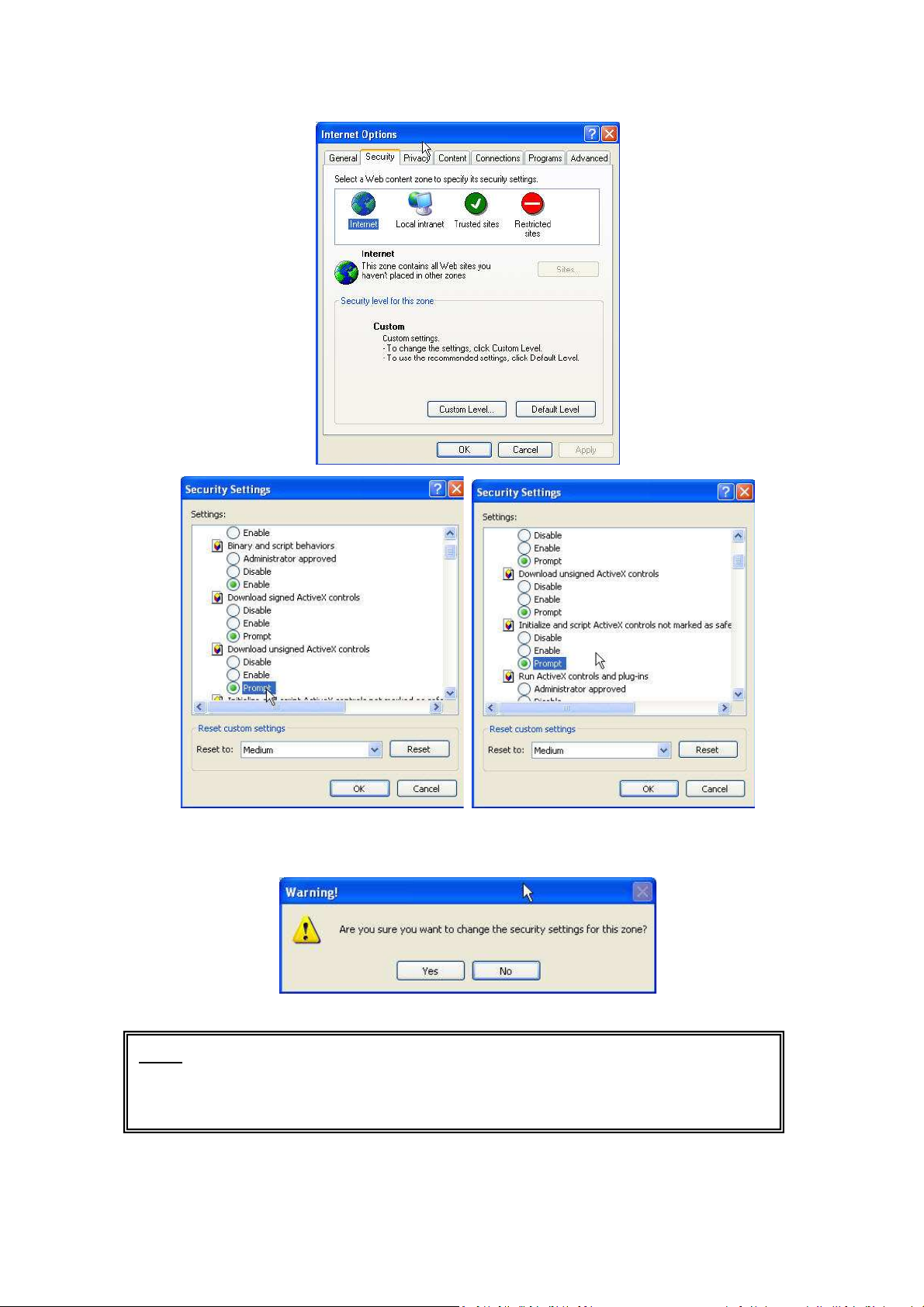
When popup the following dialogue box, click “Yes”
Hints: Changing the root password
To avoid security breaches, it is recommended changing the Username and Password once the
device is set up to work. Refer to Chapter 5, Configuring the Camera, System Settings.
- 9 -
Page 10
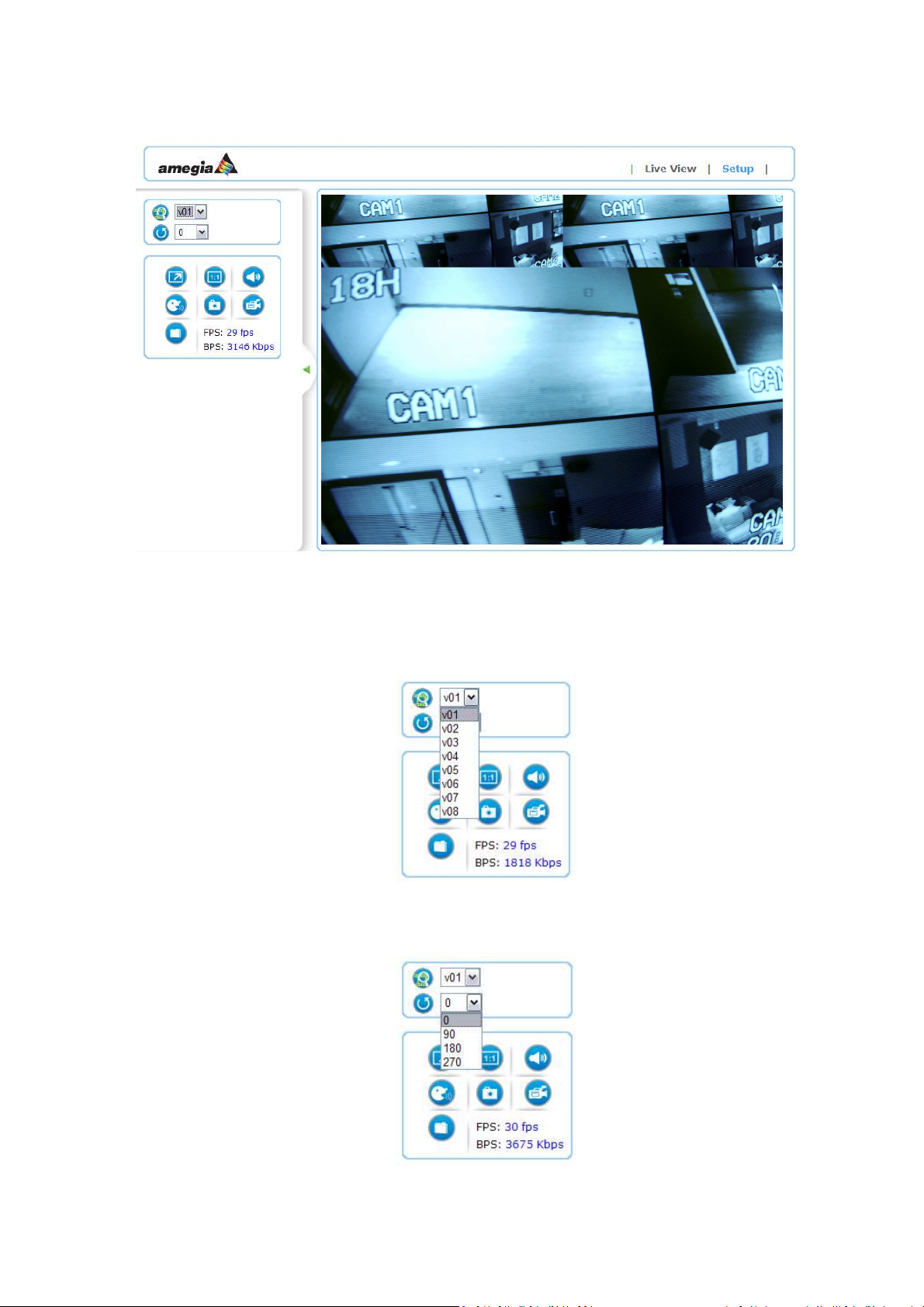
4.6 The Live View Page
Video Source:
The Stream Profile drop-down list allows you to select a customized or pre-programmed stream profile on
the Live View page. Refer to Streaming Settings of this chapter for more references.
Rotation: allows the rotation of the video to be viewed in an angle of 0 (current), 90, 180 or 270 degrees at a
clockwise direction.
- 10 -
Page 11
Full Screen: Maximizes the video to be displayed at a full screen size.
Real Size: Displays the real size of the video; (the initial video size will be adjusted to fit your monitor,
while the real size could be bigger than it is being shown in the monitor).
Listen: allows the user from the PC listen the location where the camera is set.
Talk: allows the user from the PC talk remotely to the camera, for which the speaker will emit the
voice.
Manual Record: Once pressed, it records and saves the currently viewed video the indicated path
below. To stop the recording, press back the Recording button.
Snapshot: once clicked, it will take a snapshot and save it to the indicated path below.
Path Button: Sets the location where the video and snapshot are saved to. To change the location,
click on the button and select the desired path.
FPS Frames per Seconds: Indicates the quantity of frames displayed in the current view.
BPS Bit per second: Indicates the bandwidth allocated for the streaming of the live video.
Setup: Enters into the configuration pages of the settings of the camera.
In order to change the configurations of the network camera, click on the Setup link of the Live View
page.
It will show the following dialogue box asking for the Username and Password.
The default username and password are “admin” and “admin”.
- 11 -
Page 12

5 Configuring the camera
Video: Main features and advanced configurations of video streaming.
Camera: Image adjustments such as brightness, white balance and more.
Storage: Displays information of the files located in the Micro SD card (if any).
Event: Smart features for event settings to send emails, snapshots and more.
Network: Network configuration for the network camera and Event features.
System: Firmware version information and upgrade, User access management, and
system information.
Yoics: Yoics features easy access to the network camera remotely from the
Internet, avoiding the need of configuring the network devices.
5.1 Video Settings
The video settings page contains setting for the streaming
5.1.1 General Settings
Video General Setting:
Enable Digital PTZ: The Digital PTZ feature allows you pan, tilt and zoom electronically around the image
without having moving parts at the device. Once enabled, it will display a frame which will let you slide it
through different areas and automatically zoom the area being focused on, to have a bigger and more
detailed image for your viewing.
The streams for using Digital PTZ are streams 3 and 5; the naming of the streams by default are v03 and
v05 respectively. Such naming can be changed in this same section of Video, going to the page of
Advanced settings.
- 12 -
Page 13
OSD Setting:
Enable: Once enabled, a text message can be displayed on top of the video. This is useful to indicate a
Camera Name or the location where the Network Camera is installed in.
Camera Name: To display the OSD, type a text on the box with a maximum of 20 characters.
Date / Time: Displays the date and time on the video which is streamed from the Network Camera.
Save: Once the options have been selected, click on Save to make the changes permanent for the device.
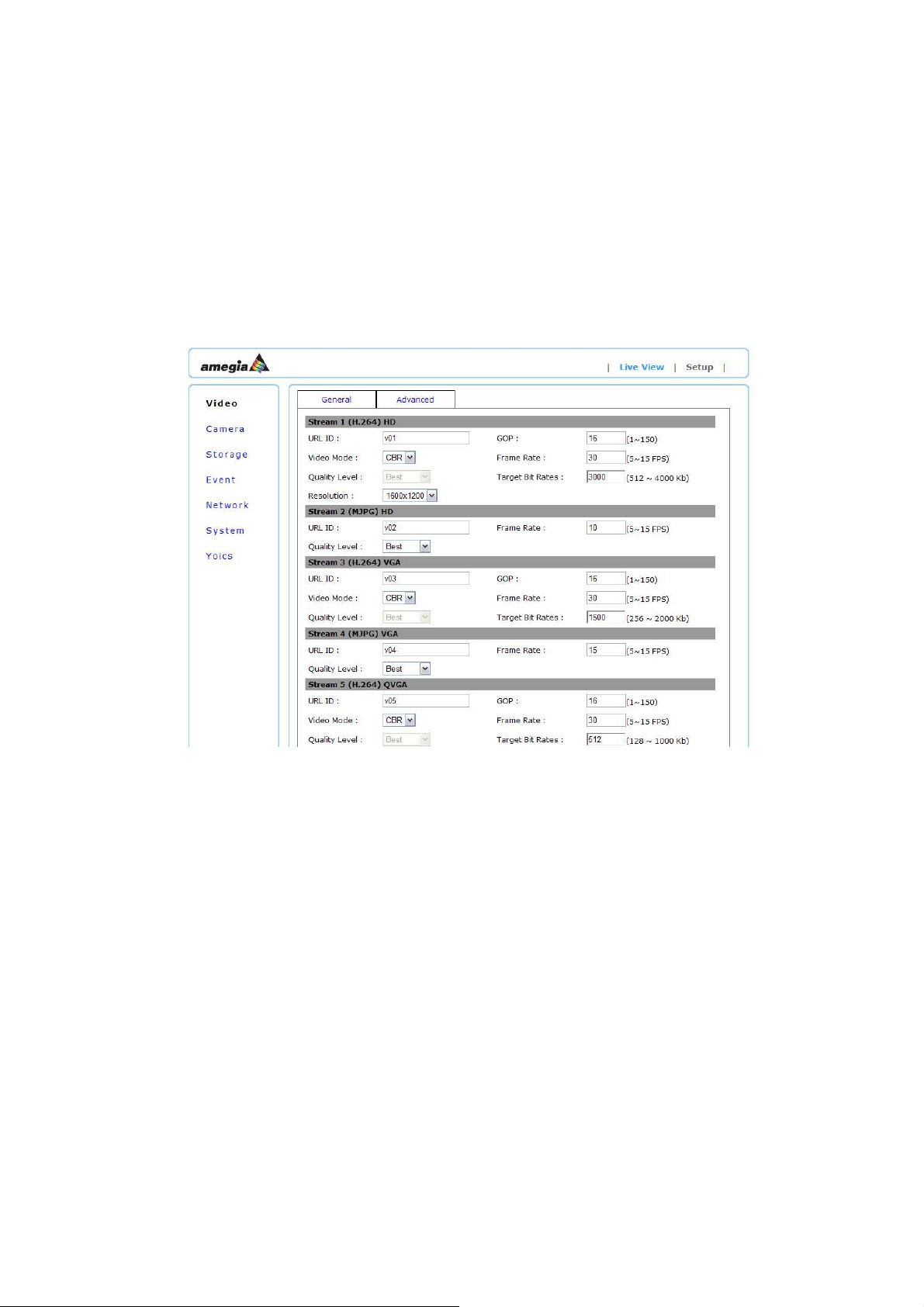
5.1.2 Advanced Settings
The Network Camera has in total 8 independent and simultaneous streams which can be used.
Your requirements and the properties of your network will determine the type you use.
The Live View page in the network camera provides access to a list of streams which are set in this page.
They can either be H.264 or Motion JPEG video streams that are configured according to each user’s need.
Other applications and clients can also access these video streams/images directly, without going via the Live
View page.
Stream Types:
Stream 1, 3, 5 and 7: H.264
Stream 2, 4, 6 and 8: MJPEG
URL ID: Sets the name for the streaming; input an appropriate name to indicate the stream type
which is being used.
Video Mode: CBR:512 Kbps ~ 4Mbps – Increase CBR to increase the picture quality; or vice versa
VBR:The network camera will adjust itself automatically to fit the best picture quality
through the bandwidth provided by the network.
The balance between VBR and network
- 13 -
Page 14
bandwidth will affect picture quality.
Quality Level: There are three levels to adjust: Best, Good and Standard
The higher the quality is, the more bandwidth it will use for streaming the video.
Resolution: You can set up a different video resolution for different viewing devices.
Note that a larger frame size takes up more bandwidth.
GOP: GOP stands for "Group of Pictures".
Frame Rate: This limits the maximum refresh frame rate per second. Set the frame rate higher for
5.2 Camera Settings
5.2.1 Camera General Settings
a coded video stream.
smoother video quality.
The GOP is a group of successive pictures within
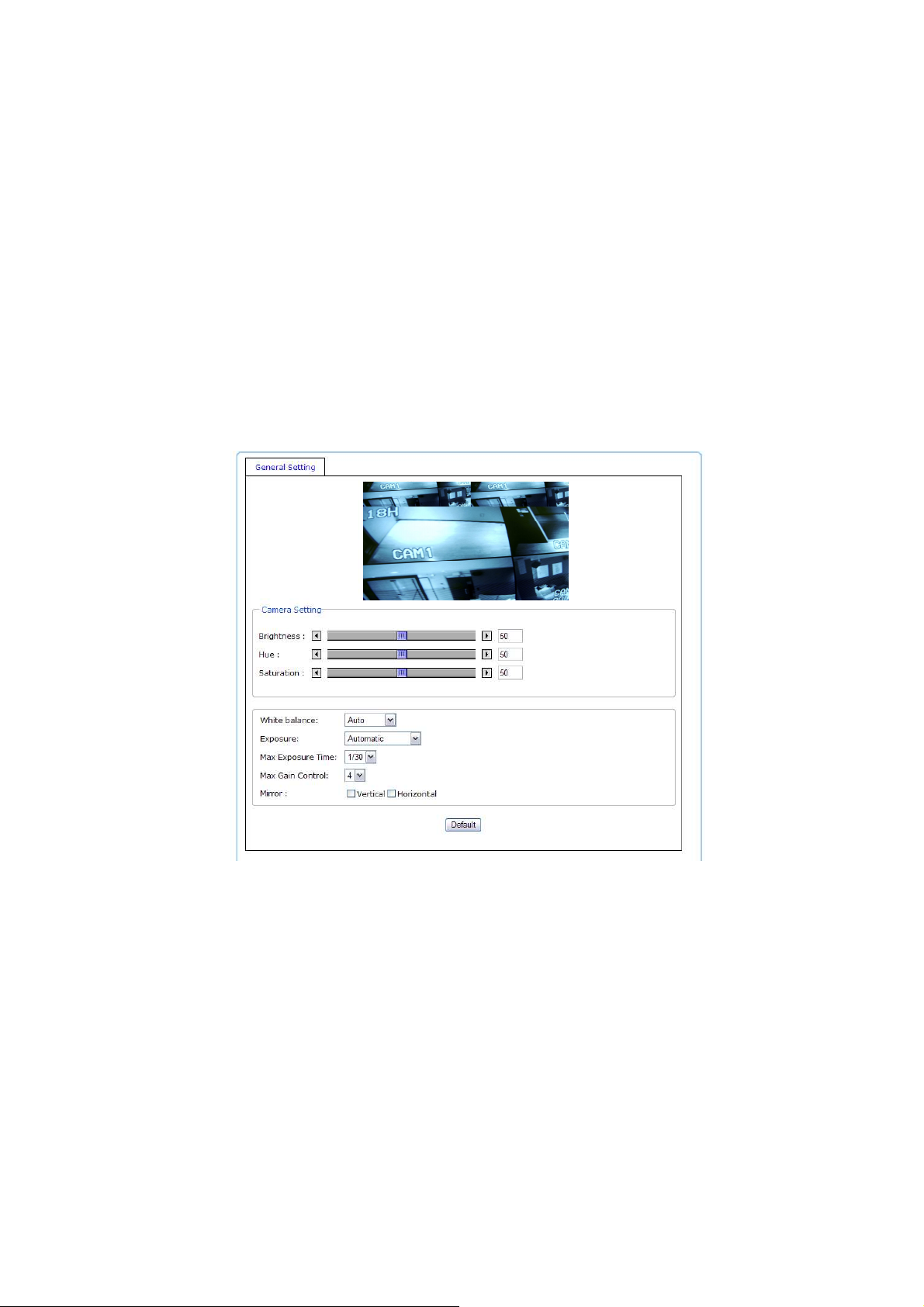
Brightness: The image brightness can be adjusted in the range 0-100, where a higher value produces a
brighter image.
Hue: The image hue can be adjusted in the range 0-100, where a higher value produces more stimulus
on the image.
Saturation: The image saturation can be adjusted in the range 0-100, where a higher value produces more
neutral image.
White balance: This is used to compensate for the different colors present in different light sources, to make
the colors in the image appear the same. The Network Camera can be set to automatically
identify the light source and compensate for its color. Alternatively, the type of light source
can be manually selected from the drop-down list.
Exposure: Configure the exposure settings to suit the image quality requirements in relation to lighting,
- 14 -
Page 15

frame rate and bandwidth considerations. Values can be set to: Automatic, 50 or 60 kHz
Max Exposure Time: Select the exposure time for the camera for the duration of the time that gets into the
sensor.
Max Gain Control: Select the level gain control for the camera
Mirror: Flips the video based on Vertical and Horizontal view.
5.3 Storage Settings
5.3.1 Disk Information
Displays information on the Micro SD Card inserted in the network camera that the user is working with,
which will be useful for saving live videos and snapshots, lately used in the built-in live recording Schedule
feature of this same section.
- 15 -
Page 16

Below, a graphic representation of the page when a disk is inserted, with files store inside.
5.3.2 File list
Displays the list of files which are stored in the Micro SD Card.
A checkbox is shown to allow the deletion of the file if necessary.
5.4 Event Settings
The Event Settings page allows the user to customize the Network Camera to perform actions during a
period of time, upon the occurrence of certain events in order to have a result.
For example: Capture a snapshot, at anytime, when a motion is detected; and send the snapshot to an email
address.
In simple words: Upon some condition, during a time, do something with a result.
The condition will be set by “Trigger by”
- 16 -
Page 17

The time of doing something will be set by “Respond to Trigger”
Doing something with a result will be set by “When Triggered…”
5.4.1 Event Configuration
Event Type List
Add: In order to turn on the capability of setting an Event, go to the Event Configuration page and click
on Add to see the available options. Note: the maximum number of events are limited to 10 (ten).
Remove: In order to remove any existing event, click on the name of the Event and click on Remove.
Event Type Setup
Name: Input a name to identify the Event that will perform the action upon some event occurrence.
Trigger by: (Condition)
Schedule: it will perform an action during a time defined by the user.
Motion Detection: it will perform an action upon a motion detected set in some are defined by the
user.
By Boot: it will perform an action when the camera is booted or restarted. This feature is useful to
detect reconnections that are not anticipated or expected.
Respond to Trigger (Time)
Always: always keep the Network Camera alert to wait for some condition to happen.
Only during time frame: it will perform the action only for the time frame set. This is different from
- 17 -
Page 18

the Schedule condition, since the Schedule condition sets the time as the main reason to start doing
something, while the “time frame” sets the duration of the action.
Check the corresponding days to execute the triggering time.
Start Time: indicates that time that the trigger will be start executing
Interval: indicates the interval between each action.
Duration: indicates the duration of the trigger from the Start Time.
Temporal Disable: don’t do anything while activated. In other words, even if the condition has
happened the Network Camera shall not do anything. This option is useful to pre-set conditions that
will probably be used in the future by desire, but that hasn’t to be activated now.
When Triggered…(Do some action with a result)
Upload Images: sends the images to an FTP server.
Send Email notification: Send an email message to a predefined email address set in the Network
Configuration.
Sent HTTP notification: Send a text message as a parameter to an HTTP port that should be expecting a
text message or a command.
Send TCP notification: Send a text message to an TCP port that should be expecting a text message
For configuring the FTP, Email, HTTP and TCP settings, refer to the Network Configuration, on Event
Server.
- 18 -
Page 19

5.4.2 Motion Detection
Video motion detection is used to generate an alarm whenever movement occurs (or stops) in the video
image.
A total of 3 Include and/or Exclude windows can be configured.
Once configured, the video motion detection windows appear in the list of available triggers, for
triggering events.
Note: Using the motion detection feature may decrease the camera’s overall performance
Motion Detection List
Add: 3 areas can be set for which they will be identified in 3 colors each, Red, Green or Blue.
Once clicked, according to the color selected, a squared block can be drawn on top of the video displayed
using the mouse.
Press the left click of the mouse to start drawing the box, and drag it upon the video to mark the desired
area. Once finished, release the left click of the mouse, and the box will be drawn as intended.
- 19 -
Page 20

Remove: In case any of the area is not required, click on the name of the Area Name from the Motion
Detection List, and click on Remove.
Windows Area Name: Descriptive name of your choice
Trigger Level: values run from 0 to 100; for which the higher the number, the faster the trigger is executed.
Sensitivity: values run from 0 to 100; for which the higher the number, the more sensitive is the motion
area.
Color: 3 colors can be chosen among the areas set for the motion detection; Red, Blue or Yellow.
Save: Once the process has been completed click on “Save” to make the changes permanent.
Cancel: in case for any reason, the selection was not properly configured, click on Reset to clear up the values
for each feature.
5.5 Network Settings
The Network Settings page allows the user to change and add more sophisticated configurations based on the
network infrastructure where the Network Camera is installed.
As for the IP Discovery Tool is useful for initial boot up and straight network configuration, the Network Settings
page offers a flexible way to fully utilize the network capabilities.
General: Basic IP configuration settings.
Advanced: Page for network settings that include Time Server, Hostname and Port for services.
DDNS: Service for accessing the Network Camera through domain names rather than IP addresses.
PPPoE: Configuration page for connecting directly to ADSL internet services.
Event Server: Sets up the servers utilized in the Event feature page, such as FTP, HTTP, SMTP and TCP.
Note: Consult your Network Administrator for the availability of the services and the values for the
configuration to be used.
- 20 -
Page 21

5.5.1 General
DHCP: Obtain IP address via DHCP
Dynamic Host Configuration Protocol (DHCP) is a protocol that lets network administrators centrally manage
and automate the assignment of IP addresses on a network. Although a DHCP server is mostly used to set an
IP address dynamically, it is also possible to use it to set a static, known IP address for a particular MAC
address.
SMTP Server: Select the Email server to notify your current IP address.
To: Once selected, fill a destination of email in which the IP address will be sent as message.
Static IP Address
IP address: Specify a unique IP address for your network camera.
Subnet mask: Specify the mask for the subnet the network camera.
Gateway: Specify the IP address for the Gateway
DNS1: Specify the IP address for the first group of DNS
DNS2: Specify the IP address for the second group of DNS
5.5.2 Advanced
NTP Configuration
Obtain NTP server address via DHCP - check this radio button to automatically look up and use the
NTP server settings as provided by DHCP. Click the View button to see the current settings.
Use the following NTP server address - to create manual settings, check this radio button and enter
the host name or IP address of the NTP server.
Host Name Configuration
The network cameras can be accessed using a host name, instead of an IP address.
Obtain Host Name server address via ipV4 DHCP - automatically use the DNS server settings
- 21 -
Page 22

provided by the DHCP server. Click the View button to see the current settings.
Use the Host Name - enter the desired DNS server by specifying the following:
Domain name - enter the domain(s). Multiple domains can be separated by semicolons (;). The host
name is always the first part of a Fully Qualified Domain Name, for example, myserver is the host
name in the Fully Qualified Domain Name myserver.mycompany.com where mycompany.com is the
Domain name.
HTTP
The default HTTP port number 80 can be changed according to the user’s need. This is useful for simple
security port mapping.
RTSP
The RTSP protocol allows a connecting client to start an H.264/MJPEG stream. Check the box to enable
the server and enter the RTSP port number to use. The default setting is 554. Note that H.264/MJPEG
video streams will not be available if this service is not enabled.
FTP
The FTP server running in the network cameras enables the upload of new firmware, and user
applications. Check the box to enable the service.
Arp / Ping
Enabling Arp / Ping will offer an additional tool to the user in order to detect the status of the Network
Camera. For related commands to ARP/Ping, refer to your Network Administrator.
5.5.3 DDNS
The DDNS (Dynamic Domain Name Service) feature allows users to access the Network Camera without
the need of remembering the IP address, but rather using a name.
For example: http://www.mycamera.com
- 22 -
Page 23

To be able to use the DDNS feature, a domain name must be registered first in a domain name service
from a 3rd party service provider, such as DynDNS (www.dyndns.org).
The DDNS feature only forwards the information between the Host Name server and the Network Camera,
therefore the Username and Password must be obtained from the 3rd party service provider before using
the feature.
Note: Refer to your Domain Name Service Provider for more information on setting up a domain name. Some Domain
Name Service providers charge a fee for the registration, while some offer the service as free of charge. It will be in
the user’s decision which service to acquire.
In order to use the DDNS feature, it is assumed that the Network Camera already has direct access to Internet.
For more information on how to allow the Network Camera to access the Internet, consult with your Network
Administrator and you can also refer to the Port Forwarding Section in this manual for a basic guide line and a better
understanding of the topic in matter.
5.5.4 PPPoE
The PPPoE feature enables the user to connect the Network Camera directly to the ADSL Modem having
direct access to Internet. Click on the PPPoE Enable box to activate the feature, and enter the Username and
respective Password.
The Username and Password, as well as the internet service that goes with the ADSL Modem are provided by
an Internet Service Provider (ISP) such as your local telephone company.
Contact your ISP for more information on how to acquire such service.
SMTP Server: Select an SMTP server to allow an email to be sent through in order to have a status update.
To: Enter an email address for which the status message will be sent to.
5.5.5 Event Server
Event Servers are used to receive uploaded image files and/or notification messages. To set up Event
Server connections in your camera, go to Setup > Event Configuration > Event Servers and enter the
required information for the required server type.
- 23 -
Page 24

Add FTP: adds an FTP to be used as a recipient for the images
AddHTTP: adds an HTTP server to receive text messages.
AddTCP: adds a TCP port to received text messages.
AddSMTP: adds an Email server/address to receive email messages
Remove: to remove any existing Event Server, select a Name from the Event Server List and click on
Remove.
Upon clicking on any button to add FTP, HTTP, TCP or SMTP server a box will show up for
filling the required information.
FTP Server
Receives uploaded images
Name: Descriptive name of your choice
Network address (IP address or host name)
User Name and Password: Enter the Username and Password for allowing the upload of the images.
Note: Consult your Network Administrator for the correct Username and Password applied to the folder. Make
sure that the Username applied in this folder does have Write and Delete permissions to it. In case Write and
Delete permissions are not applicable, the intended files to be stored will not take into effect
- 24 -
Page 25

HTTP Server
Receives notification messages
Name: Descriptive name of your choice
URL: URL (IP address or host name)
Username and Password: Enter the Username and Password for allowing the reception of
messages.
Note: Consult your Network Administrator for the correct Username and Password applied to the HTTP and Proxy
Server. Make sure that the Username applied in the HTTP and Proxy does have Write and Delete permissions to it.
In case Write and Delete permissions are not applicable, the intended messages to be delivered will not take into
effect
TCP Server
Receives notification messages
Name: Descriptive name of your choice
Network Address: IP address or host name
Port number: Enter the port number of the TCP service that is expecting to receive the message.
- 25 -
Page 26

Note: Consult your Network Administrator for the availability of the TCP service and Port number to be used.
Note: The SMTP Server is set in the Event Settings > Event Server configuration. Refer that section for more references.
5.5.6 Wireless ( Optional )
Wireless Mode
The wireless feature is available only for wireless models.
Wireless Network:
Once activated, the network camera will detect the Access Points available in the current network.
Enable / Disable:
The wireless function is disabled by default; enable the wireless mode in case a wireless connection is
- 26 -
Page 27

desired rather than the wired connection.
In order to avoid network conflicts, it is recommended that the wireless IP address be different from
the wired connection.
Network Name (SSID):
When the user wants to use the wireless function, an Access Point must be designated to serve the
wireless connection. Commonly a Router acts like an Access Point for serving wireless connections.
The SSID identifies the Access Point in the network; it is usually a number or name being used by the
Router when it has the wireless function enabled.
Network Type:
Master: Select this to enable the wireless function for which it may function under a wireless
connection infrastructure such as an Access Point.
Ad-hoc: Select this to enable a point-to-point connection to a computer.
Security:
The encryption will depend on whether the Access Point (Wireless Router) utilizes an encryption key to
authorize and authenticate client connections to access the wireless service.
Select among the encryption methods: WEP, WPA-PSK; WPA-PSK.
Save: Save the changes made.
Note: Contact your network administrator for a better understanding of the wireless connection under your
network infrastructure and the type of encryption used in such network.
5.6 System Settings
5.6.1 Information
The System Settings page displays information about the current status of the Network Camera.
- 27 -
Page 28

Such information is useful to have references when direct information is required without going through the
different pages of configuration of the Network Camera.
5.6.2 User
The user configuration page allows the Network Camera to have multiple users and profiles to access the
Network Camera.
Enable anonymous login:
To allow the access to the Network Camera without restrictions, select the box of Enable anonymous login
and click on “Save” to make the changes permanent.
Such change will allow anyone to access the Network Camera without a username or password.
Note: it is in the user’s discretion whether or not to allow authorized and unauthorized to access the Network
Camera.
Adding a user
In order to add a new user, click on the “Add “button and fill the information which is required.
After filling the information, click on “Save” to make changes permanent to the device.
Administrator: Permission to view and change the configuration of the Network Camera.
Operator: Has permission to change certain configuration of the camera.
Viewer: Has only permission to view the Network Camera.
Note: follow the instructions displayed on the User’s page while selecting of a Username and Password.
- 28 -
Page 29

Deleting a user
To delete user, click on a Name from the Users list and click on “Remove”, then click on “Save” to make the
changes permanent.
5.6.3 Date & Time
Displays the date and time (24 hours clock) of the Network Camera.
Set Server Time
Select the Automatically adjust for daylight saving time changes if necessary.
From the Time Mode section, select the preferred method to use for setting the time:
Synchronize with computer time - sets the time from the clock on your computer.
Synchronize with NTP Server - the camera will obtain the time from an NTP server every 60 minutes.
- 29 -
Page 30

Set manually - this option allows you to manually set the time and date.
Note: If using a host name for the NTP server, a DNS server must be configured under Network Settings.
Click on “Save” to make the changes permanent.
In case there was error during the selection, click on “Reset” and restart the process.
5.6.4 Server Maintenance
The Server Maintenance page allows the user to make changes in the Network Camera, such as:
Reboot: restarts the Network Camera
Load Default: sets the Network Camera back to the default parameters from factory.
Upload File: Upgrades the Network Camera to a new released firmware. Look up for the file and select it.
Click on “Upgrade” to proceed with the upgrading of the firmware.
Restore: Look up for the file that restores a previous configuration of the Network Camera. Click on
“Upload“ to begin the process.
Backup: click on “Backup” to save the current parameters of the Network Camera to a file.
Note: Before making any changes to the system of the Network Camera, make sure it is what is required while all
alternatives have been considered and executed.
5.6.5 I/O
Power LED: Check the box if the Power LED is required to be off while the Network Camera is on.
- 30 -
Page 31

5.7 Application
5.7.1 Yoics Setup
5.7.1.1 Register the camera
Have a Yoics account already
Please go to www.yoics.net to sign in your account.
Create a new Yoics account
You can view it locally by typing the IP address on your browser. The IP-Discovery tool (IPDIS) can help
you find the IP address of your camera.
Enter [Setup] → [Application] → [Yoics] page (Fig1),
then click (register this camera).
Follow the Yoics website instructions [NEW REGISTERATION] (Fig2) to fill in and get a new account.
Follow Instructions on Webpage
The New Product Detected Window will pop up (Fig3), please follow the webpage instructions to finish
adding the new camera.
- 31 -
Page 32

Fig1.Register this camera
Register Here
Fig2. New Registration
- 32 -
Page 33

5.7.1.2 Unregister Camera
Login into Yoics Website
Please go to www.yoics.net to sign in to your account.
Delete Service from Camera Settings.
Choose [MY STUFF]-> Settings of Camera Name.(Fig4)
Click [Advanced Service Settings]->[Delete Service].(Fig5)
Fig3.Detect new product window
Fig4.Camera Settings
- 33 -
Click Here
Page 34

Fig5.Advanced Service Settings
Click Here
- 34 -
Page 35

6 Troubleshooting
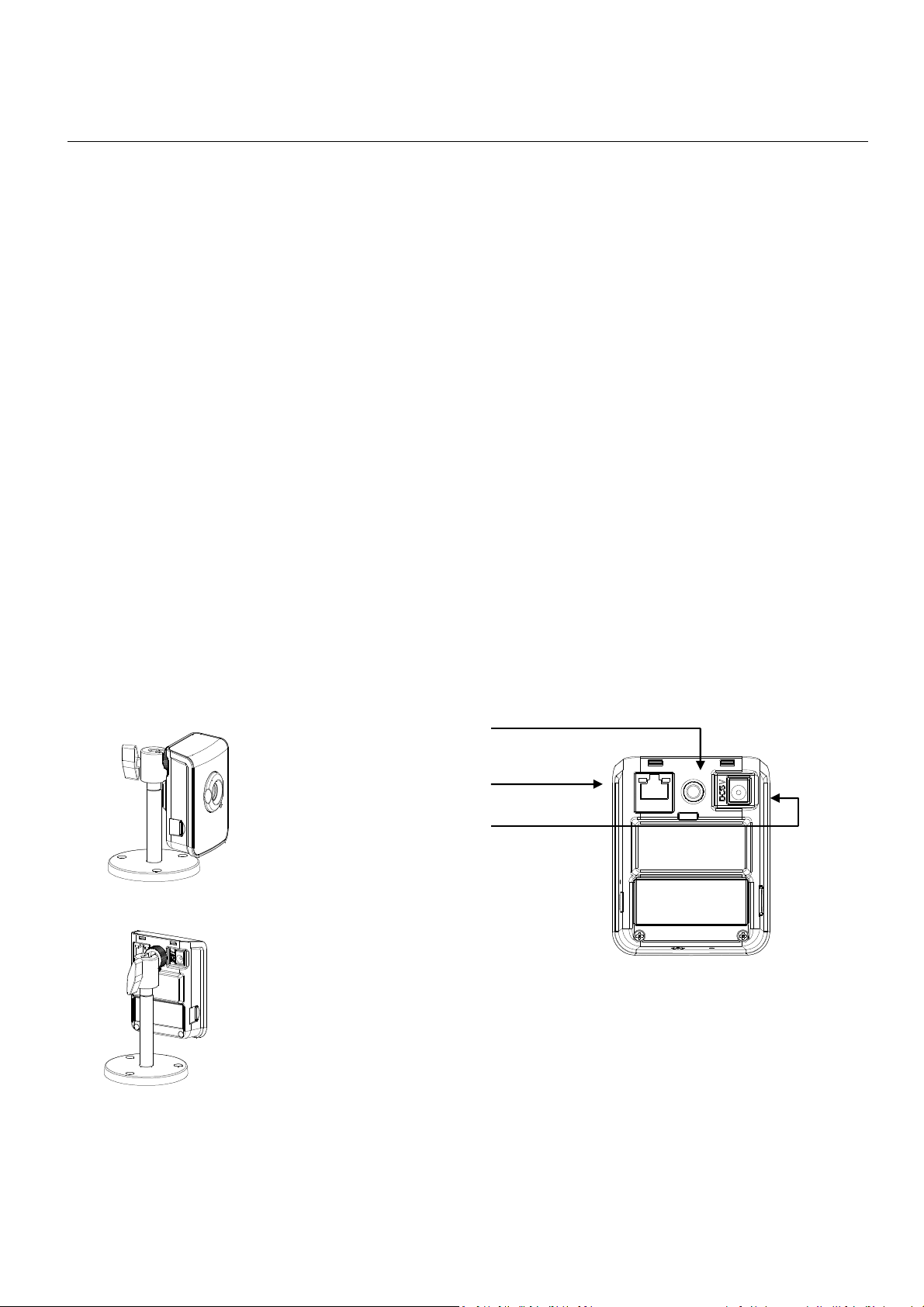
6.1 Emergency Factory Default
To execute the Emergency Factory Default, proceed as follows:
1. Remove the power adapter from the socket power of the network camera
2. With a pin thin enough to go through the Default Button hole, push inside gently
3. Plug back the socket power
Default Button
4. The Power LED will flash
5. Release the pin
6. The network camera enters into the process of getting back to factory defaults
The device is back to factory default. All settings will be erased from the device, and the assigned IP will be back
to 192.168.1.200 and Subnet to 255.255.0.0.
- 35 -
Page 36

Internet
Local
N
etwork
6.2 Viewing the camera from a remote location
The below guideline shows you how to setup the Network Camera for viewing it from a remote location.
The network infrastructure demonstration is just for your reference only. Each network infrastructure may vary
upon the needs of the organization.
Note: Consult your Network Administrator for a better understanding of networking concepts and related topics.
6.2.1 Standard connection
Network Camera 192.168.1.21 / Port 80
Internet Service
Provider
Broadband
Router
ADSL Modem
Public IP
210.20.34.23
Terminal
192.168.1.22
Company Web Server
192.168.1.23
Remote Location
In this case what we have here is:
Public IP Address 210.20.34.23, assigned by the Internet Service Provider (ISP)
Network Camera, with a local IP of 192.168.1.22
Broadband router
Since we are sharing only one single Internet connection through our Local Network, the Port Forwarding
configuration in our Broadband Router for the camera will be as follows:
Private IP Private Port Type Public Port
192.168.1.22 80
192.168.1.22 554
Notice that the Port 80 is the default port for any Web-Server, but this also can be changed. Since Port 80 is
the default, when we type our IP address at the Address bar, there won't be any need to type the port
number.
The default port for streaming an H.264 video is port 554, being the same as the port 80, it can also be
changed.
Once the broadband router's configurations are set, we can open the Internet Explorer and type in the
- 36 -
TCP ● ○ UDP
TCP ● ○ UDP
80
554
Page 37

Address bar the Public IP address.
Internet
Local
N
etwork
Once the broadband router's configurations are set, we can open the Internet Explorer and type in the
address bar the Public IP address.
http://210.20.34.23/
6.2.2 Assigning Ports Manually
Network Camera 192.168.1.21 / Port 8080
Internet Service
Provider
Broadband
Router
Terminal
192.168.1.22
Company Web Server
192.168.1.23
ADSL Modem
Public IP
210.20.34.23
Port 8080
For the
Network
Camera
Remote Location
In this case what we have here is:
Public IP Address 210.20.34.23, assigned by the Internet Service Provider (ISP), but we will be using Port
9999 for accessing the camera from the Internet.
The Network Camera, with a local IP of 192.168.1.22, using port 8080 to get access to the camera through
the Local Network.
Broadband router
Since we are sharing only one single Internet connection through our Local Network, the Port Forwarding
configuration in our Broadband Router for the camera will be as follows:
Private IP Private Port Type Public Port
192.168.1.22 8080
192.168.1.22 554
In this case we are using Port 8080 for the Network Camera at 192.168.1.22, and using Port 8080 for the
Internet access at 210.20.34.23.
When we are in a remote location, in order to access our camera through Internet, we have to specify the
Public Port when typing the Public IP Address as the figure below
http://210.20.34.23:8080/
- 37 -
TCP ● ○ UDP
TCP ● ○ UDP
8080
554
Page 38

6.2.3 Using two ore more public IPs
Local
N
etwork
The following figure is just an illustration on how the camera can be connected when 2 or more Public IPs
Network Camera
are involved in a network infrastructure
Hub / Switch
Public IP
Broadband
Router
Company Web Server
192.168.1.23
Terminal
192.168.1.22
ADSL Modem
Internet Service
Provider
2 Public IP
- 38 -
Page 39

7 Frequently Asked Questions
Symptoms, Possible Causes, and Remedial Action
Problems setting the IP address
The camera is located on a different subnet
If the IP address intended for the camera and the IP address of your computer are located on different subnets, you will not be
able to set the IP address. Contact your network administrator to obtain an appropriate IP address.
The IP address is being used by another device
Disconnect the camera from the network. Run the Ping command. (In a Command/DOS window, type ping and the IP address
of the unit).
If you receive: Reply from <IP address>: bytes = 32; time = 10 ms..... - this means that the IP address may already be in use by
another device on your network. You must obtain a new IP address and reinstall the unit.
If you see: Request timed out - this means that the IP address is available for use with your camera. In this case, check all
cabling and reinstall the unit.
Possible IP address conflict with another device on the same subnet
The static IP address in the camera is used before the DHCP server sets a dynamic address. This means that if the same default
static IP address is also used by another device, there may be problems accessing the camera. To avoid this, set the static IP
address
to 0.0.0.0.
The camera cannot be accessed from a browser
The IP address has been changed by DHCP
If the camera and client are on the same network, run the IP Discovery Utility to locate the camera.
Identify the camera using its model or serial number
Alternatively:
1) Move the camera to an isolated network or to one with no DHCP or BOOTP server. Set the IP address again, using the IP
Discovery Utility (see the Installation Guide) or the ARP/Ping commands.
2) Access the unit and disable DHCP in the TCP/IP settings. Return the unit to the main network. The unit now has a fixed IP
address that will not change.
3) As an alternative to 2), if dynamic IP address via DHCP or BOOTP is required, select the required service and then configure
IP address change notification from the network settings.
Return the unit to the main network. The unit now has a dynamic IP address, but will notify you if the address changes.
Other networking problems
Test the network cable by connecting it to another network device, then Ping that device from your workstation. See
instructions above.
Camera is accessible locally, but not externally
Broadband router configuration
To configure your broadband router to allow incoming data traffic to the camera, enable the NAT port forwarding feature
which will configures the router to allow access to the camera.
Firewall protection
Check the Internet firewall with your system administrator.
Default routers required
Check if you need to configure the default router settings.
Problems with the H.264/MJPEG format
No H.264/MJPEG displayed in the client
Check with your network administrator to see if there is a firewall preventing viewing.
Poor rendering of H.264
Color depth set incorrectly on clients. Set to 16-bit or 32-bit color.
Ensure that your graphics card is using the latest device driver. The latest drivers can usually be downloaded from the
manufacturer's web site.
Color saturation is different in H.264 and Motion JPEG
Modify the settings for your graphics adapter. See the adapter's documentation for more information.
Lower frame rate than expected
- 39 -
Page 40

Reduce number of applications running on the client computer.
Limit the number of simultaneous viewers.
Check with the system administrator that there is enough bandwidth available. See also the online help.
Lower the image resolution.
No images displayed on web page
Installation of additional ActiveX component restricted
Configure your Internet Explorer to allow the installation of ActiveX by lowering temporally the Internet Explorer security
settings.
Video/Image problems, general
Image too dark or too light
Check the video image settings.
Missing images in uploads
This can occur when trying to use a larger image buffer than is actually available. Try lowering the frame rate or the upload
period.
Slow image update
Configuring motion detection, high-resolution images, or high frame rates, will affect the performance of the camera.
Poor performance
Poor performance may be caused by heavy network traffic, multiple users accessing the unit, low performance clients, use of
features such as Motion Detection, Event handling.
Poor quality snapshot images
Screen incorrectly configured on your workstation
In Display Properties, configure your screen to show at least 65000 colors, that is, at least 16-bit. Using only 16 or 256 colors
will produce dithering artifacts in the image.
Audio volume too low/high
Volume settings incorrect
The volume of the microphone is either too high or too low. Change the volume for the microphone in the toolbar on the Live
View page.
Poor audio quality
CPU overloaded
Reduce the number of listeners and viewers and decrease the image resolution and compression.
Unsynchronized audio and video
It is recommended that the camera's time setting is synchronized with an NTP Server. This is enabled under System Options >
Date & Time.
Distorted audio
Select Microphone for the internal microphone or for a connected external microphone.
Select Line for a connected line in source.
- 40 -
Page 41

8 Technical Specifications
Main Video Specifications, Performance & Capabilities
Video Compression H.264 / Motion JPEG
Video Resolution UXGA: 1600 x 1200
Bit Rate 64K ~ 4M bits/sec (CBR/VBR configurable)
Frame Rate 15 FPS @ UXGA
Image Device 2 Megapixels 1/3” CMOS Sensor (High Definition)
Lens Type Board Lens, Focal Length 4.2 mm, F1.8
Radiant Distance
(optional)
Minimum Illumination AM1201 / AM1201-W
Video Control
Digital PTZ By Image Area
Image Adjustment
Event System
Local Storage Micro SD slot (Up to 16 GB)
Audio Capability 1 x Built-in Microphone; 1 x Audio Speaker
Trigger Motion detection , Manual trigger
Action
HD-720P: 1280 x 720
VGA: 640 x 480
QVGA: 320 x 240
QQVGA: 160x120
30 FPS @ HD-720P / VGA / QVGA / QQVGA
AM1201 / AM1201-W : Infrared Light LEDs
ON: 3 Meters ~ 5 Meters
LED off : 1 ~ 10,000 Lux
LED on: 0 Lux
Stream Resolution (up to 4)
H.264 or Motion JPEG
VBR/CBR for quality/bitrate control
RTSP URI
Brightness, Saturation, Sharpness, Exposure control, White balance,
Backlight compensation, Rotation
File upload via FTP, HTTP, Email
Save Video to Micro-SD card
Notification via email, HTTP and TCP
Audio Compression G.711 AAC-LC PCM 8Khz
Networking & Accessing
Network Interface 10BASE-T/100 BASE-TX
Wireless LAN
(optional)
Wireless Security
( for wireless models)
Protocols
Security
User Environment Requirements
Minimum System
Requirements
Operation Platform Microsoft Windows XP/Vista Home Edition
Browser IE 7.0 above
Hardware Operation & Characteristics
Power Supply
Power Consumption Less than 8W
Operation Temperature 0°C ~ 50°C
Operation Humidity 20% ~ 80% RHG
AM1200-W / AM1201-W
IEEE 802.11b/g
AM1200-W / AM1201-W
Security WEP(64/128 bit), WPA-PSK(AES/TKIP), WPA2-PSK(AES/TKIP)
HTTP, TCP/IP, IPv4, UDP, SMTP, FTP, PPPoE, DHCP, DDNS, NTP, DNS, ARP,
RSTP, RTP
Password Protection
User access log
CPU: Pentium Dual Core RAM: 512M
Graphic Card: 128MB
AC/DC switching power Adapter. Input AC100 ~ 240V; Output DC 5V/
2A
- 41 -
Page 42

Dimension 70 (W) x 38 (L) x 88.5 (H) mm
Net Weight
Certification Report CE/FCC, ROHS
I/O Connectors
Camera only 90g
Camera with Stand 210 g
1x RJ45 10BASE-T/100 BASE-TX
1x DC Power Jack
1x Default setting button
1x Micro SD slot
1x Audio Out
- 42 -
Page 43

9 Glossary of Terms
ActiveX -
A standard that enables software components to interact with one another in a networked environment, regardless of the
language(s) used to create them. Web browsers may come into contact with ActiveX controls, ActiveX documents, and ActiveX
scripts. ActiveX controls are often downloaded and installed automatically as required.
ARP (Address Resolution Protocol) -
This protocol is used to associate an IP address to a hardware MAC address. A request is broadcast on the local network to
discover the MAC address for an IP address.
Autoiris (DC-Iris) -
This special type of iris is electrically controlled by the camera, to automatically regulate the amount of light allowed to enter.
Bitmap -
A bitmap is a data file representing a rectangular grid of pixels. It defines a display space and color for each pixel (or ‘bit’) in the
display space. This type of image is known as a ‘raster graphic.’ GIFs and JPEGs are examples of image file types that contain
bitmaps.
Because a bitmap uses this fixed raster method, it cannot easily be rescaled without losing definition. Conversely, a vector graphic
image uses geometrical shapes to represent the image, and can thus be quickly rescaled.
Bit rate -
The bit rate (in kbit/s or Mbit/s) is often referred to as speed, but actually defines the number of bits/time unit and not
distance/time unit.
Bonjour -
Also known as zero-configuration networking, Bonjour enables devices to automatically discover each other on a network,
without having to enter IP addresses or configure DNS servers. Bonjour is a trademark of Apple Computer, Inc.
Broadband -
In network engineering terms, this describes transmission methods where two or more signals share the same carrier. In more
popular terminology, broadband is taken to mean high-speed data transmission.
CCD (Charged Coupled Device) -
This light-sensitive image device used in many digital cameras is a large integrated circuit that contains hundreds of thousands of
photo-sites (pixels) that convert light energy into electronic signals. Its size is measured diagonally and can be 1/4", 1/3", 1/2" or
2/3".
CGI (Common Gateway Interface) -
A specification for communication between a web server and other (CGI) programs. For example, a HTML page that contains a
form might use a CGI program to process the form data once it is submitted.
CIF (Common Intermediate Format) -
CIF refers to the analog video resolutions 352x288 pixels (PAL) and 352x240 pixels (NTSC). See also Resolution.
Client/Server -
Client/server describes the relationship between two computer programs in which one program, the client, makes a service
request from another program, the server, which fulfils the request. Typically, multiple client programs share the services of a
common server program. A web browser is a client program that requests services (the sending of web pages or files) from a web
server.
CMOS (Complementary Metal Oxide Semiconductor) -
A CMOS is a widely used type of semiconductor that uses both negative and positive circuits. Since only one of the circuit types is
on at any given time, CMOS chips require less power than chips using just one type of transistor. CMOS image sensors also allow
processing circuits to be included on the same chip, an advantage not possible with CCD sensors, which are also much more
expensive to produce.
Codec -
In communications engineering, a codec is usually a coder/decoder. Codecs are used in integrated circuits or chips that convert
e.g. analog video and audio signals into a digital format for transmission. The codec also converts received digital signals back into
analog format. A codec uses analog-to-digital conversion and digital-to-analog conversion in the same chip.
Codec can also mean compression/decompression, in which case it is generally taken to mean an algorithm or computer program
for reducing the size of large files and programs.
- 43 -
Page 44

DC-Iris (Autoiris) -
This special type of iris is electrically controlled by the camera, to automatically regulate the amount of light allowed to enter.
DHCP (Dynamic Host Configuration Protocol) -
DHCP is a protocol that lets network administrators automate and centrally manage the assignment of Internet Protocol (IP)
addresses to network devices in a network.
DHCP uses the concept of a ‘lease’ or amount of time that a given IP address will be valid for a computer. The lease time can vary,
depending on how long a user is likely to require the network connection at a particular location.
DHCP also supports static addresses for e.g. computers running web servers, which need a permanent IP address.
DNS (Domain Name System) -
DNS is used to locate and translate Internet domain names into IP (Internet Protocol) addresses. A domain name is a meaningful
and easy-to-remember name for an Internet address. For example the domain name www.example.com is much easier to
remember than 192.0.34.166. The translation tables for domain names are contained in Domain name servers.
Domain Server -
Domains can also be used by organizations who wish to centralize the management of their (Windows) computers. Each user
within a domain has an account that usually allows them to log in to and use any computer in the domain, although restrictions
may also apply. The domain server is the server that authenticates the users on the network.
Ethernet -
Ethernet is the most widely installed local area network technology. An Ethernet LAN typically uses special grades of twisted pair
wires. The most commonly installed Ethernet systems are 10BASE-T and 100BASE-T10, which provide transmission speeds up to
10 Mbps and 100 Mbps respectively.
Factory default settings -
These are the settings that originally applied for a device when it was first delivered from the factory. If it should become
necessary to reset a device to its factory default settings, this will, for many devices, completely reset any settings that were
changed by the user.
Firewall -
A firewall works as a barrier between networks, e.g. between a Local Area Network and the Internet. The firewall ensures that
only authorized users are allowed to access the one network from the other. A firewall can be software running on a computer, or
it can be a standalone hardware device.
Focal length -
Measured in millimeters, the focal length of a camera lens determines the width of the horizontal field of view, which in turn is
measured in degrees.
FTP (File Transfer Protocol) -
An application protocol that uses the TCP/IP protocols. It is used to exchange files between computers/devices on networks.
Frame -
A frame is a complete video image. In the 2:1 interlaced scanning format of the RS-170 and CCIR formats, a frame is made up of
two separate fields of 262.5 or 312.5 lines interlaced at 60 or 50 Hz to form a complete frame, which appears at 30 or 25 Hz. In
video cameras with a progressive scan, each frame is scanned line-by-line and not interlaced; most are also displayed at 30 and 25
Hz.
Frame rate -
The frame rate used to describe the frequency at which a video stream is updated is measured in frames per second (fps). A
higher frame rate is advantageous when there is movement in the video stream, as it maintains image quality throughout.
Gain -
Gain is the amplification factor and the extent to which an analog amplifier boosts the strength of a signal. Amplification factors
are usually expressed in terms of power. The decibel (dB) is the most common way of quantifying the gain of an amplifier.
Gateway -
A gateway is a point in a network that acts as an entry point to another network. In a corporate network for example, a computer
server acting as a gateway often also acts as a proxy server and a firewall server. A gateway is often associated with both a router,
which knows where to direct a given packet of data that arrives at the gateway, and a switch, which furnishes the actual path in
and out of the gateway for a given packet.
H.264 -
- 44 -
Page 45

A standard for video compression, also known as MPEG-4 Part 10.
HTML (Hypertext Markup Language) -
HTML is the set of "markup" symbols or codes inserted in a file intended for display in web browser. The markup tells the browser
how to display the page's words and images for the user.
HTTP (Hypertext Transfer Protocol) HTTP is the set of rules for exchanging files (text, graphic images, sound, video, and other multimedia files) on the web. The HTTP
protocol runs on top of the TCP/IP suite of protocols.
Hub -
A (network) hub is used to connect multiple devices to the network. The hub transmits all data to all devices connected to it,
whereas a switch will only transmit the data to the device it is specifically intended for.
IEEE 802.11 -
A family of standards for wireless LANs. The 802.11 standard supports 1 or 2 Mbit/s transmission on the 2.4 GHz band. IEEE
802.11b specifies an 11 Mbit/s data rate on the 2.4 GHz band, while 802.11a allows up to 54 Mbit/s on the 5 GHz band.
Image compression Image compression minimizes the file size (in bytes) of an image. Two of the most common compressed image formats are JPEG
and GIF.
Interlacing -
Interlaced video is video captured at 50 pictures (known as fields) per second, of which every 2 consecutive fields (at half height)
are then combined into 1 frame. Interlacing was developed many years ago for the analog TV world and is still used widely today.
It provides good results when viewing motion in standard TV pictures, although there is always some degree of distortion in the
image.
To view interlaced video on e.g. a computer monitor, the video must first be de-interlaced, to produce progressive video, which
consists of complete images, one after the other, at 25 frames per second. See also Progressive scan.
IP (Internet Protocol) -
The Internet Protocol is a method transmitting data over a network. Data to be sent is divided into individual and completely
independent "packets." Each computer (or host) on the Internet has at least one address that uniquely identifies it from all others,
and each data packet contains both the sender's address and the receiver's address.
The Internet Protocol ensures that the data packets all arrive at the intended address. As IP is a connectionless protocol, which
means that there is no established connection between the communication end-points, packets can be sent via different routes
and do not need to arrive at the destination in the correct order.
Once the data packets have arrived at the correct destination, another protocol - Transmission Control Protocol (TCP) - puts them
in the right order. See also TCP.
IP Address -
An IP address is simply an address on an IP network used by a computer/device connected to that network. IP addresses allow all
the connected computers/devices to find each other and to pass data back and forth.
To avoid conflicts, each IP address on any given network must be unique. An IP address can be assigned as fixed, so that it does
not change, or it can be assigned dynamically (and automatically) by DHCP.
An IP address consists of four groups (or quads) of decimal digits separated by periods, e.g. 130.5.5.25. Different parts of the
address represent different things. Some part will represent the network number or address, and some other part will represent
the local machine address. See also IP (Internet Protocol).
JPEG (Joint Photographic Experts Group) -
Together with the GIF file format, JPEG is an image file type commonly used on the web. A JPEG image is a bitmap, and usually has
the file suffix '.jpg' or ".jpeg." When creating a JPEG image, it is possible to configure the level of compression to use. As the
lowest compression (i.e. the highest quality) results in the largest file, there is a trade-off between image quality and file size.
kbit/s (kilobits per second) - A measure of the bit rate, i.e. the rate at which bits are passing a given point. See also Bit rate.
LAN (Local Area Network) -
A LAN is a group of computers and associated devices that typically share common resources within a limited geographical area.
LED -
A light-emitting diode (LED) is a semiconductor device that emits visible light when an electric current passes through it. LEDs are
widely used as indicator lights on electronic devices. products commonly have LEDs for network, power and status.
Linux -
Linux is an open source operating system within the UNIX family. Because of its robustness and availability, Linux has won
popularity in the open source community and among commercial application developers.
- 45 -
Page 46

MAC address (Media Access Control address) -
A MAC address is a unique identifier associated with a piece of networking equipment, or more specifically, its interface with the
network. For example, the network card in a computer has its own MAC address.
Manual iris -
This is the opposite to an autoiris, i.e. the camera iris must be adjusted manually to regulate the amount of light allowed to reach
the image sensor.
Mbit/s (Megabits per second) -
A measure of the bit rate, i.e. the rate at which bits are passing a given point. Commonly used to give the ‘speed’ of a network. A
LAN might run at 10 or 100 Mbit/s. See also Bit rate.
Monitor -
A monitor is very similar to a standard television set, but lacks the electronics to pick up regular television signals.
Motion JPEG -
Motion JPEG is a simple compression/decompression technique for networked video. Latency is low and image quality is
guaranteed, regardless of movement or complexity of the image. Image quality is controlled by adjusting the compression level,
which in turn provides control over the file size, and thereby the bit rate.
High-quality individual images from the Motion JPEG stream are easily extracted. See also JPEG.
Megapixel -
See Pixel.
MPEG (Moving Picture Experts Group) -
The Moving Picture Experts Group develops standards for digital video and audio compression. It operates under the auspices of
the International Organization for Standardization (ISO). The MPEG standards are an evolving series, each designed for a different
purpose.
Network connectivity -
The physical (wired or wireless) and logical (protocol) connection of a computer network or an individual device to a network,
such as the Internet or a LAN.
NTSC (National Television System Committee) -
NTSC is the television and video standard in the United States. NTSC delivers 525 lines at 60 half-frames/second.
PAL (Phase Alternating Line) -
PAL is the dominant television standard in Europe. PAL delivers 625 lines at 50 half-frames/second.
Ping -
Ping is a basic network program used diagnostically to check the status of a network host or device. Ping can be used to see if a
particular network address (IP address or host name) is occupied or not, or if the host at that address is responding normally. Ping
can be run from e.g. the Windows Command prompt or the command line in UNIX.
Pixel -
A pixel is one of the many tiny dots that make up a digital image. The color and intensity of each pixel represents a tiny area of the
complete image.
PoE (Power over Ethernet) -
Power over Ethernet provides power to a network device via the same cable as used for the network connection. This is very
useful for IP-Surveillance and remote monitoring applications in places where it may be too impractical or expensive to power the
device from a power outlet.
PPP (Point-to-Point Protocol) -
A protocol that uses a serial interface for communication between two network devices. For example, a PC connected by a phone
line to a server.
Progressive scan -
Progressive scan, as opposed to interlaced video, scans the entire picture, line by line every sixteenth of a second. In other words,
captured images are not split into separate fields as in interlaced scanning.
Computer monitors do not need interlace to show the picture on the screen, but instead show them progressively, on one line at
a time in perfect order, i.e. 1, 2, 3, 4, 5, 6, 7 etc., so there is virtually no ‘flickering’ effect. In a surveillance application, this can be
critical when viewing detail within a moving image, such as a person running. A high-quality monitor is required to get the best
from progressive scan. See also Interlacing.
- 46 -
Page 47

Protocol -
A special set of rules governing how two entities will communicate. Protocols are found at many levels of communication, and
there are hardware protocols and software protocols.
Proxy server -
In an organization that uses the Internet, a proxy server acts as an intermediary between a workstation user and the Internet. This
provides security, administrative control, and a caching service. Any proxy server associated with a gateway server, or part of a
gateway server, effectively separates the organization’s network from the outside network and the local firewall. It is the firewall
server that protects the network against outside intrusion.
A proxy server receives requests for Internet services (such as web page requests) from many users. If the proxy server is also a
cache server, it looks in its local cache of previously downloaded web pages. If it finds the page, it is returned to the user without
forwarding the request to the Internet. If the page is not in the cache, the proxy server, acting as a client on behalf of the user,
uses one of its own IP addresses to request the page from another server over the Internet. When the requested page is returned,
the proxy server forwards it to the user that originally requested it.
Resolution -
Image resolution is a measure of how much detail a digital image can hold: the greater the resolution, the greater the level of
detail. Resolution can be specified as the number of pixel-columns (width) by the number of pixel-rows (height), e.g. 320x240.
Alternatively, the total number of pixels (usually in megapixels) in the image can be used. In analog systems it is also common to
use other format designations, such as CIF, QCIF, 4CIF, etc.
RTCP (Real-Time Control Protocol) -
RTCP provides support for real-time conferencing of groups of any size within an intranet. This support includes source
identification and support for gateways like audio and video bridges as well as multicast-to-unicast translators.
RTCP offers quality-of-service feedback from receivers to the multicast group as well as support for the synchronization of
different media streams.
RTP (Real-Time Transport Protocol) -
RTP is an Internet protocol for the transport of real-time data, e.g. audio and video. It can be used for media-on-demand as well as
interactive services such as Internet telephony.
RTSP (Real Time Streaming Protocol) -
RTSP is a control protocol, and a starting point for negotiating transports such as RTP, multicast and Unicast, and for negotiating
codecs.
RTSP can be considered a ‘remote control’ for controlling the media stream delivered by a media server. RTSP servers typically use
RTP as the protocol for the actual transport of audio/video data.
Router -
A device that determines the next network point to which a packet should be forwarded on its way to its final destination. A
router creates and/or maintains a special routing table that stores information on how best to reach certain destinations. A router
is sometimes included as part of a network switch. See also switch.
Server -
In general, a server is a computer program that provides services to other computer programs in the same or other computers. A
computer running a server program is also frequently referred to as a server. In practice, the server may contain any number of
server and client programs. A web server is the computer program that supplies the requested HTML pages or files to the client
(browser).
Sharpness -
This is the control of fine detail within a picture. This feature was originally introduced into color TV sets that used notch filter
decoders. This filter took away all high frequency detail in the black and white region of the picture. The sharpness control
attempted to put some of that detail back in the picture. Sharpness controls are mostly superfluous in today's high-end TVs. The
only logical requirement for it nowadays is on a VHS machine.
SMTP (Simple Mail Transfer Protocol) -
SMTP is used for sending and receiving e-mail. However, as it is ‘simple,’ it is limited in its ability to queue messages at the
receiving end, and is usually used with one of two other protocols, POP3 or IMAP. These other protocols allow the user to save
messages in a server mailbox and download them periodically from the server.
SMTP authentication is an extension of SMTP, whereby the client is required to log into the mail server before or during the
sending of email. It can be used to allow legitimate users to send email while denying the service to unauthorized users, such as
spammers.
Sockets -
- 47 -
Page 48

Sockets are a method for communication between a client program and a server program over a network. A socket is defined as
‘the endpoint in a connection. Sockets are created and used with a set of programming requests or ‘function calls’ sometimes
called the sockets application programming interface (API).
SSL/TSL (Secure Socket Layer/Transport Layer Security)
These two protocols (SSL is succeeded by TSL) are cryptographic protocols that provide secure communication on a network. SSL
is commonly used over HTTP to form HTTPS, as used e.g. on the Internet for electronic financial transactions. SSL uses public key
certificates to verify the identity of the server.
Subnet/subnet mask -
A subnet is an identifiably separate part of an organization's network. Typically, a subnet may represent all the machines at one
geographic location, in one building, or on the same local area network (LAN). Having an organization's network divided into
subnets allows it to be connected to the Internet with a single shared network address.
The subnet mask is the part of the IP address that tells a network router how to find the subnet that the data packet should be
delivered to. Using a subnet mask saves the router having to handle the entire 32-bit IP address; it simply looks at the bits
selected by the mask.
Switch -
A switch is a network device that connects network segments together, and which selects a path for sending a unit of data to its
next destination. In general, a switch is a simpler and faster mechanism than a router, which requires knowledge about the
network and how to determine the route. Some switches include the router function. See also Router.
TCP (Transmission Control Protocol) -
TCP is used along with the Internet Protocol (IP) to transmit data as packets between computers over the network. While IP takes
care of the actual packet delivery, TCP keeps track of the individual packets that the communication (e.g. requested a web page
file) is divided into, and, when all packets have arrived at their destination, it reassembles them to re-form the complete file.
TCP is a connection-oriented protocol, which means that a connection is established between the two end-points and is
maintained until the data has been successfully exchanged between the communicating applications.
Telnet -
Telnet is a simple method with which to access another network device, e.g. a computer. The HTTP protocol and the FTP protocols
allow you to request specific files from remote computers, but do not allow you logon as a user of that computer. With Telnet,
you log on as a regular user with whatever privileges you may have been granted for specific applications and data residing on
that computer.
UDP (User Datagram Protocol) -
UDP is a communications protocol that offers limited service for exchanging data in a network that uses the Internet Protocol (IP).
UDP is an alternative to the Transmission Control Protocol (TCP). The advantage of UDP is that it is not required to deliver all data
and may drop network packets when there is e.g. network congestion. This is suitable for live video, as there is no point in
re-transmitting old information that will not be displayed anyway.
Unicast -
Communication between a single sender and a single receiver over a network. A new connection is established for each new user.
URL (Uniform Resource Locator) An "address" on the network.
Varifocal lens -
A varifocal lens provides a wide range of focal lengths, as opposed to a lens with a fixed focal length, which only provides one.
WAN (Wide-Area-Network) -
Similar to a LAN, but on a larger geographical scale.
W-LAN (Wireless LAN) -
A wireless LAN is a wireless local area network that uses radio waves as its carrier: where the network connections for end-users
are wireless. The main network structure usually uses cables.
Web server -
A web server is a program, which allows web browsers to retrieve files from computers connected to the Internet. The web server
listens for requests from web browsers and upon receiving a request for a file sends it back to the browser.
The primary function of a web server is to serve pages to other remote computers; consequently, it needs to be installed on a
computer that is permanently connected to the Internet. It also controls access to the server whilst monitoring and logging server
access statistics.
WEP (Wireless Equivalent Privacy) -
- 48 -
Page 49

A wireless security protocol, specified in the IEEE 802.11 standard, which is designed to provide a wireless local area network
(WLAN) with a level of security and privacy comparable to that usually expected of a wired LAN. Security is at two different levels;
40-bit and 128-bit encryption. The higher the bit number, the more secure the encryption.
WPA-PSK (Wi-Fi Protected Access - Pre-Shared Key) -
This wireless encryption method uses a pre-shared key (PSK) for key management. Keys can usually be entered as manual hex
values, as hexadecimal characters, or as a Passphrase. WPA-PSK provides a greater degree of security than WEP.
WPA Enterprise -
Instead of a pre-shared key or passphrase, WPA Enterprise uses 802.1 x RADIUS servers and an Extensible Authentication Protocol
(EAP) for authentication. The enhanced WPA2 uses Advanced Encryption Standard (AES) instead of Temporal Key Integrity
Protocol (TKIP) to provide stronger encryption mechanism. This encryption method provides greater security, but is difficult to
configure and is not recommended for home users.
Zoom lens -
A zoom lens can be moved (zoomed) to enlarge the view of an object to show more detail.
- 49 -
Page 50

10 FCC Statement
This device compiles with FCC Rules Part 15. Operation is subject to the following two conditions.
This device may not cause harmful interference, and
This device must accept any interference received, including interference that may cause undesired
operation.
This equipment has been tested and found to comply with the limits for a Class B Digital Device, pursuant to part 15
of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a
residential installation.
This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance
with the instruction, may cause harmful interference to radio communication. However, there is no guarantee that
interference will not occur in a particular installation. If this equipment dose cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and on, the user is encouraged to try
to correct the interference by one or more of the following measures:
Reorient or relocate the receiving antenna.
Increase the separation between the equipment and receiver.
Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
Consult the dealer or an experienced radio/TV technician for help.
Model:oooooo
FCC ID : 000XXXXXXXXXXXXXX
This device complies with Part 15 of the FCC Rules. Operation is
subject to the following two conditions: (1) this device may not cause
harmful interference, and (2) this device must accept any interference
received, including interference that may cause undesired operation.
The changes or modifications not expressly approved by the party responsible for compliance could void the
user’s authority to operate the equipment.
To comply with the FCC RF exposure compliance requirements, this device and its antenna must not be
co-located or operating to conjunction with any other antenna or transmitter.
This equipment should be installed and operated with minimum distance 20cm between the radiator & your
body.
End of Document
- 50 -
 Loading...
Loading...