Page 1
ADDONICS TECHNOLOGIES
Model: CRT235SMH
IMPORTANT
There is no back door for the Cipher tower encrypted hard
drives if the Cipher keys are lost or stolen.
Cipher key
Check to make sure you have the
correct version of the Cipher key. A
sample key is shown
Black label AES-256 stands for
Cipher 256-bit key.
To ensure there is a spare key, your Cipher tower comes with
2 pairs of Cipher keys. These cipher keys have all identical
encryption code unless you requested then to be coded
differently. One of these keys should be kept in a safe and
secure location and can be sent back to Addonics for duplicating
additional keys. If you are down to the last key, be sure to make
a back up of all the data stored inside your Cipher tower prior to
sending the last key to Addonics. Addonics is not responsible for
key lost in the mail or retrieval of the data inside the encrypted
hard drive.
Keeping track of the hard drive
If you are using the Cipher tower to encrypt multiple hard drives,
it is important to label your hard drive if you are taking the drive
out of the Cipher tower. The hard drive from the Cipher tower
that is encrypted will look like a brand new drive when attach
directly to the SATA controller of a computer. There will be no
partition or any hint to indicate that the drive contains encrypted
data. When the drive is partitioned, all the encrypted data will be
lost.
The same holds true if a hard drive already has data on it is
installed into the Cipher tower. The computer detects the hard
drive as a brand new drive or a drive that is unallocated. Once
you proceed to partition the drive, the data that was on the hard
drive will be erased and cannot be recovered.
I. Installing drives into the Cipher Tower
Step 1
3.5” SATA hard drive, slide the
Using
drive into the drive bay. Close the
front panel and using the key
provided, turn the key lock to the Lock
position. This will secure the drive and
turn on the power to the hard drive.
Note: It is recommended to fill up the Cipher tower with SATA
drives from top to bottom. This is to help in identifying which
drives connect to which ports for easier troubleshooting.
II. Connecting the power cable and Cipher Tower to the
mputer
co
a. Connect the power cord provided from the wall outlet to the
back of the Cipher Tower.
b. A power switch is located on the front of the tower. Make
sure the power is off on the switch (power LED light should
be off)
c.
Connect the provided eSATA or USB2.0 cable from the back
of the Cipher tower to the eSATA or USB2.0 on the
computer. We recommend connecting the eSATA port for
best performance if this port is available on your computer.
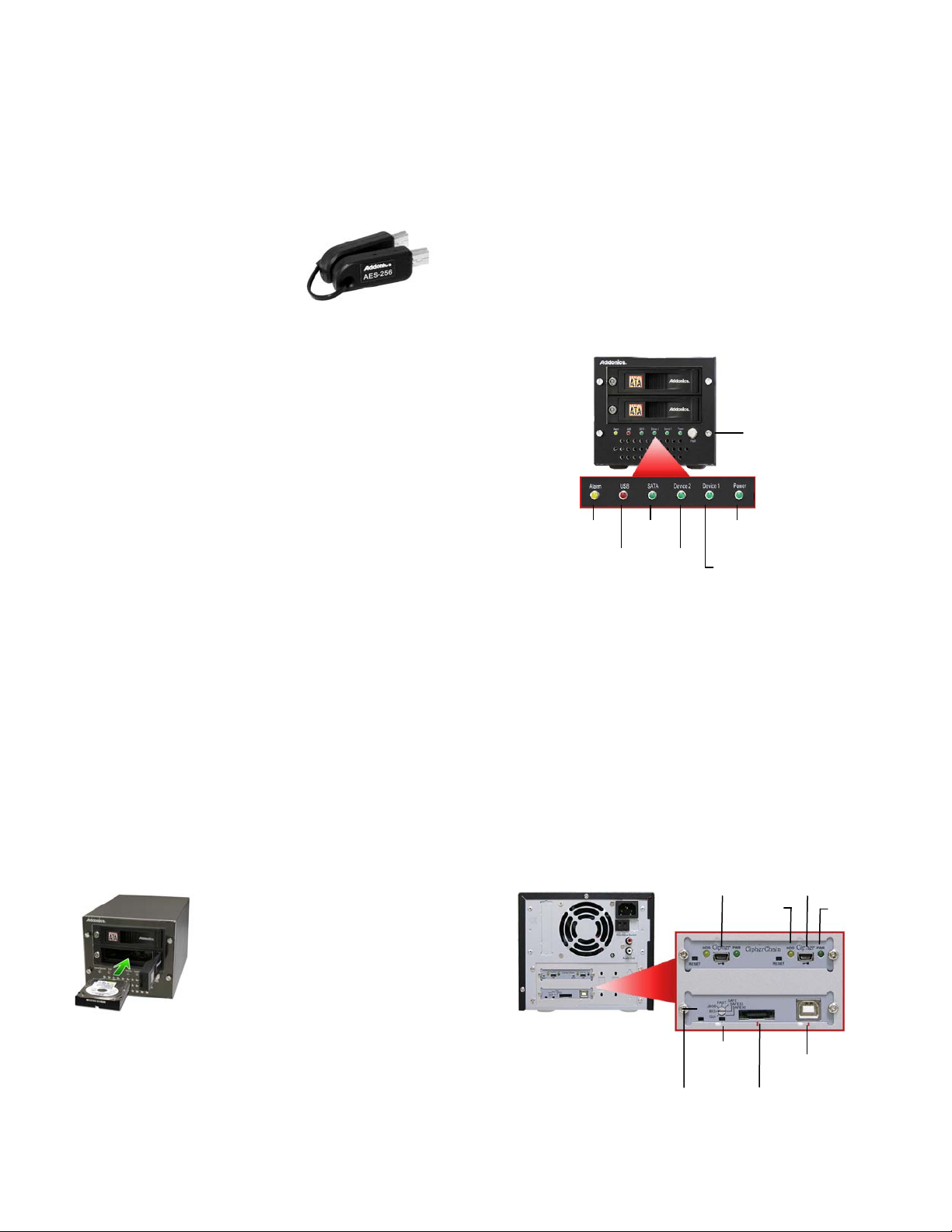
Power
Switch
er
Pow
LED
Drive 1
Activ
ity
LED
HDD LED
eSATA port
Cipher
key
hole
USB port
Cipher
Pow
RAID
Health
USB
Access
eSATA
Access
Drive 2
Activity
LED
LED Inf
ormation:
Power LED: When power switch is turned on, the green
LED lights up.
Drive 1 Activity LED: When there is drive activity, the LED
blinks.
Drive 2 Activity LED: When there is drive activity, the LED
blinks.
eSATA Access LE D : W hen eSATA port is used to connect to a
system, the LED lights up.
USB Access LED: When USB port is used to connect to a
system, the LED lights up.
RAID Health LED: When the RAID volume fails, the LED
blinks.
RAID config
rotary switch
Cipher
keyhole
RAID
setting
button
er LED
Page 2

ADDONICS TECHNOLOGIES
Model: CRT235SMH
III. Initial RAID setup of the Cipher tower:
a. Insert the AES 256-bit cipher keys into the two cipher
keyholes located at the back of the Cipher tower.
b. Set the Rotary switch to the RAID configuration required.
c. Push the RAID Setting button whil e the Cipher tower is
turned off.
d. While holding the RAID setting button, turn on the Cipher
tower and continue to hold for at least 2 seconds to confirm
RAID mode setting.
e. Observed that the green Cipher power LEDs at the back of
the Cipher tower are on. If they did not, reinsert the cipher
keys and re-power the Cipher tower while holding the RAID
setting button.
f. Check in the 57xx SteelVine Manager if the RAID
configuration is correct.
g. Go to the operating system’s management utility to partition,
format and mount the encrypted drives.
IV. How to operate the Cipher tower after initial setup
1. Insert the AES 256-bit cipher keys into the two cipher
keyholes located at the back of the Cipher tower.
2. Push the power switch of the Cipher tower to turn it on.
Observed that the green Cipher power LEDs at the back of
the Cipher tower are on. If they did not, reinsert the cipher
keys and re-power the Cipher tower.
3. Use the system’s File Explorer to access the files on the
encrypted drive.
4. For security purposes, remove the cipher keys from the
Cipher tower after the drives are detected by the system. All
the files being transferred into the drives are still encrypted
even if the cipher key is removed.
5. When the Cipher tower is restarted, the two cipher keys
must be inserted again in order to gain access to the drives.
V. 57xx SteelVine Manager utility installation for Cipher
tower
Note: If you plan to monitor the status of your raid set, you
need to install the Sil5744 SteelVine Manager on your system.
Install the utility from the CD that came with your package.
1. Turn computer ON. Insert Addonics Driver Disk into
CDROM.
2. The Addonics Technologies Driver Disk window pops up.
3. Select Configuration Utilities. Sil5744 SteelVine Manager. To
extract the utility select your operating system from the list.
4. Extract the files into your system.
5. Install SiI5744 Manager by clicking the 5700Package.msi.
Follow the instructions.
6. After software installation, restart your system off.
The 57xx SteelVine Manager Utility manual can found in the
Driver Disk under User Guides or can be downloaded from
http://www.addonics.com/support/user_guides/host_controller/SiI
57XX_Users_Guide_Rev_1.0.pdf
Individual drive configuration:
When the Cipher tower is connected to a SATA Host controller
with SiI3124 or SiI3132 chip, the 2 SATA drives configured as
JBOD would be detected by the system otherwise only one drive
is detected.
Best Practice:
Create a label to identify the SATA hard drive and the associated
Cipher key used.
Technical Support
Contact Information
Phone: 408-573-8580
Fax: 408-573-8588
Email: http://www.addonics.com/sales/query/
Internet: http://www.addonics.com
TECHNICAL SUPPORT
Phone: 408-453-6212
Hours: 8:30 am - 6:00 pm PST
Email: http://www.addonics.com/support/query/
 Loading...
Loading...