Page 1

ADDERLink™ INFINITY 4000
Experts in
Connectivity
Solutions
KVM Extension
Solutions
User Guide
Page 2

Contents
Introduction
Welcome ................................................................................................................ 2
Local feed through ...............................................................................................3
Support for Standard and High Dynamic Ranges .........................................4
Technical Specications ....................................................................................... 5
ALIF4000 unit features ........................................................................................6
Supplied items ....................................................................................................... 7
Optional extras .....................................................................................................8
Installation
Connections .......................................................................................................... 9
Mounting ................................................................................................................9
TX video links ...............................................................................................10
TX analog audio links ..................................................................................10
TX USB links .................................................................................................11
TX AUX (serial) port ..................................................................................11
TX power in ..................................................................................................12
TX/RX high speed links ..............................................................................13
RX video display ...........................................................................................15
RX microphone & speakers .......................................................................15
RX USB devices ............................................................................................16
RX power in ..................................................................................................17
Conguration
ALIF4000 conguration via web pages ..........................................................18
Performing a manual factory reset .................................................................19
Placing the device into recovery mode .........................................................20
Conguring dual touchscreens ........................................................................21
Creating an unmanaged matrix .......................................................................22
Creating and editing presets ............................................................................23
Operation
Front panel indications ......................................................................................24
Using the On Screen Display ...........................................................................25
Further information
Getting assistance ..............................................................................................26
Appendix A - Conguration pages .................................................................27
Appendix B - Support for analog and digital audio.....................................46
Appendix C - Tips for success when networking ALIF units ....................47
Appendix D - Troubleshooting ........................................................................49
Appendix E - Glossary ......................................................................................51
Appendix F - Null modem cable pinout ........................................................54
Appendix G - Fiber/copper modules and cables ........................................55
Appendix H - Using the optional ALIF4000 rack shelf .............................56
Appendix I - Open source licenses ................................................................57
INSTALLATION
CONFIGURATIONOPERATION
FURTHER
INFORMATION
Index
INDEX
1
Page 3

Introduction
WELCOME
Thank you for choosing the ADDERLink™ INFINITY 4000 (aka ALIF4000) high
performance extenders. The ALIF4000 range offers dual-head 4K, audio and USB
delivered over a single ber connection. Pixel-perfect color, accurate picture quality at
5K60 and USB2.0 with fast switching.
Product in brief
• In-built support for dual CATx links at speeds up to 1GbE with additional support for
dual CATx or ber at up to 10GbE using optional SFP modules,
• Dual-head 5K, video, audio and USB over a single ber connection,
• Pixel-perfect, color accuracy at 4K60,
• Support for 5K resolution: 5120 pixels by 2880*, 2160 or 1440 (* at 30Hz refresh)
• Support for 240Hz frame rate at HD resolutions,
• Support for three dynamic color ranges: SDR8, SDR10 and HDR10 (see page 4),
• Bi-directional analog audio,
• DisplayPort audio with 2, 4, 6 or 8 channels on both video heads (supports 5.1 and 7.1),
• Adder’s USB True Emulation for fast switching,
• Support for local feed through, using an additional ALIF transmitter to allow a local
host PC to be connected directly to an ALIF4000 RX in addition to its network links
(see page 3),
• Support for advance diagnostic and troubleshooting tools,
• Backwards compatibility with existing ALIF range,
• Plug and play.
Linking
ALIF4000 units can be linked in two mains ways: Direct or Networked.
Direct linking
Where ALIF4000 transmitters and receivers are directly linked to each other, very
little conguration action is required, provided that they both have their factory default
settings in place - just link them together. If the standard settings have been changed in a
previous installation, you merely need to perform a manual factory reset on each unit.
ALIF4000 TX
Networked linking
Where ALIF4000 units are connected via networked links, you can either congure them
individually, or congure them collectively using an AIM server:
• ConguringnetworkedALIFunitsindividually - In the absence of an AIM server,
unallocated ALIF4000 units have the ability to locate each other. You can alter settings
via the OSD on the console connected to the RX unit by pressing CTRL + ALT + C.
• ConguringnetworkedALIFunitscollectively - The ADDERLink™ INFINITY
Management (AIM) server allows you to congure, control and coordinate any number
of ALIF transmitters and receivers from a single application.
Note: If you are using one or more ALIF4000
transmitters within an installation managed by
an AIM server, the AIM server must be running
rmware version 4.9 or above.
ALIF4000 RX
ALIF4000 RX
INSTALLATION
CONFIGURATIONOPERATION
FURTHER
INFORMATION
Safety
Please refer to the safety booklet provided in the box before use of this product.
ALIF4000 TX
IMPORTANT: When using AIM to congure ALIF
units, it is vital that all units that you wish to
locate and control are set to their factory default
settings. Otherwise they will not be located by
the AIM server. If necessary, perform a manual
factory reset on each ALIF unit.
See Start of Life: AIM or Point to Point conguration
Gigabit
Switching
ALIF4000 RX
INDEX
ALIF4000 RX
2
Page 4

LOCALFEEDTHROUGH
ALIF4000 RX units receivers can be congured to support a local link to a separate
host PC, via a dedicated ALIF TX, in addition to the main link to the network. The locally
linked PC remains completely isolated from the main network.
To congure this arrangement, ensure that the IP port that is used for the local link is
not allocated an IP address. The link local connection to the ALIF TX must use the same
type of port as the main network connection, ie either both SFP or both CATx.
Note: For the local feed through feature to operate, the AIM server must be at version 4.8 or
greater while the endpoints must be at version 4.0 or greater.
INSTALLATION
ALIF TX
ALIF TX
ALIF TX
AdderLink
MANAGEMENT SERVER
www.adder.com
Gigabit
Ethernet
ADMIN
1
O
ALIF4000RX
12V
3A
2
4
optical
OUT
5
Link local
ALIF TX
34
112
CONFIGURATIONOPERATION
In operation, the user of the console at the ALIF
receiver can use the following hotkey combination
to toggle between the network and local links:
To change from a network link to the local link:
enter CTRL+ALT+L
To change from the local link to a network link:
enter CTRL+ALT +C
to display the OSD and choose
FURTHER
INFORMATION
the required connection.
Note: The L and C default hotkeys can be changed
within the AIM control panel.
INDEX
3
Page 5

SUPPORTFORSTANDARDANDHIGHDYNAMICRANGES
(SDR8/SDR10/HDR10)
With the introduction of rmware versions 4.00 (and above), ALIF4000 models now
support video signals with color formats that use 10-bpc (bits per color) as well as the
standard 8-bpc. The supported dynamic ranges are:
• SDR8 - Uses 8-bpc (24-bits in total per pixel), as supported across the ALIF range.
• SDR10 - Uses 10-bpc (30-bits total) in order to dene a wider color gamut.
• HDR10 - Uses 10-bpc to dene a wider color gamut and also benets from support
for ST2084 dynamic range mastering and BT.2020 colorimetry.
All ALIF devices use the AFZ24 codec to support SDR8 signals; ALIF4000 devices (with
rmware v4.xx) also use the newer AFZ30 to support SDR10 and HDR10 modes.
The ability to successfully deliver full SDR10 or HDR10 video signals from a host PC to
any particular remote video display relies upon a series of factors:
• The host PC must produce video signals with SDR10 or HDR10 content.
• The ALIF4000 TX must have rmware v4.00 or greater.
• The receiving ALIF4000 RX units must have rmware v4.00 or greater.
• The video display(s) connected to a receiver must support SDR10 or HDR10.
Where possible, you are recommended to upgrade all ALIF4000 devices to 4.xx
rmware. Where a mix of ALIF4000 and non-ALIF4000 receivers exist, an ALIF4000 TX
will respond in manner discussed on the right to negotiate access.
TolockanALIF4000TXintoSDR8mode
If a mixture of new and legacy devices is unavoidable and it is vital that no legacy
receiver is ever locked out from a particular ALIF4000 TX, then set the ALIF4000 TX to
use a maximum of 8-bpc (regardless of the input signal):
Mixingdevices
Care should be taken when using a mixture of ALIF4000 (v4.00 and greater) and nonALIF4000 devices. It is not possible for an ALIF 4000 TX to deliver SDR10/HDR10
to multiple RX units if one or more of them are only able to process SDR8. When a
mixture of RX devices make connection, the TX will employ the following methods to
negotiate access - on a rst-come, rst-served basis:
TXconguredtouseonly8-bpc
ALIF4000 TX
SDR8
SDR10
HDR10
f/w
4.xx
Max bpc = 8
Max bpc = 10
Non-ALIF4000RXconnectsrst
Second to
2
1
connect
First
to connect
SDR10
HDR10
ALIF4000 TX
Max bpc = 8
f/w
Max bpc = 10
4.xx
ALIF4000 RX
ALIF RX
ALIF4000 RX
ALIF RX
SDR8
SDR8
SDR8
SDR8
Max Bits per Colour is set
to ‘8’ on the ALIF4000 TX.
This means that regardless
of the signal type received
from the host (SDR8,
SDR10 or HDR10), the TX
will only send out SDR8.
Consequently, all types of
ALIF RX units are fully
supported, albeit at the
lower dynamic range and
color depth (see lower left).
Max Bits per Colour is set
to ‘10’ on the ALIF4000 TX.
However, the rst RX to
connect with the TX is a
non-ALIF4000 type, which
means that the TX scales
back the video output
to SDR8 for this and all
subsequent RX units.
INSTALLATION
CONFIGURATIONOPERATION
IftheunitISunderAIMcontrol
1 Login to the AIM suite.
2 Click the Transmitters tab and
locate the ALIF4000 TX within
the list of devices.
3 Click the icon for the
ALIF4000 TX.
4 For video port 1, set the
Maximum Bits Per option to
‘8bpc’.
5 Repeat step 4 for video port 2, if
necessary.
6 Click the Save button.
IftheunitisNOTunderAIMcontrol
1 On the console keyboard attached to
an RX unit, access the OSD by pressing:
CTRL+ALT+C.
2 Click on the Transmitters option and
click the icon for the required TX.
3 Click the Ports link and ensure that the
page is selected.
4 For video port 1, set the Max Bits per
Colour option to ‘8’.
5 Repeat step 4 for video port 2, if
necessary.
6 Click the Apply button.
ALIF4000RXconnectsrst
First to
connect
1
2
Second
to connect
SDR10
HDR10
ALIF4000 TX
Max bpc = 8
f/w
Max bpc = 10
4.xx
ALIF4000 RX
ALIF RX
SDR10
HDR10
The ALIF4000 TX has
been set to either SDR10
or HDR10. The rst to
connect with the TX
is an ALIF4000 RX and
subsequently receives
X
SDR10/HDR10 output.
The next to join is a
non-ALIF4000 RX and is
rejected from connecting. It
will continue to attempt a
connection.
After either of the last two scenarios have occurred; once all RX units have disconnected,
the ALIF4000 TX will revert to SDR8, SDR10 or HDR10 (as determined by the host
signal and the ALIF4000 TX settings) and be ready to respond accordingly to connecting
RX units.
FURTHER
INFORMATION
INDEX
4
Page 6

TECHNICALSPECIFICATIONS
Operating/storageconditions
Operating temperature: 0 to 40ºC / 32 to 104ºF
Storage temperature: 0 to 40ºC / 32 to 104ºF
Storage and operating relative humidity: 10 to 90% non-condensing
Altitude: < 2000m
Power
External power: 12VDC, 5A
Typical power consumption: 20W
Physical
Dimensions (L)210mm /8.3” x (W)215mm/8.5” x
(D)40mm/1.6”
Weight: 1.8kg / 4 lbs
Materials
Aluminium and steel construction
Connectors
Local Unit - Transmitter (TX)
Computer: 2x DisplayPort™, 2x USB type B,
2x 3.5mm audio jack sockets,
1x DB9 socket.
Ethernet: 2x 8p8c (RJ45), 2x SFP+ cages.
Power: 3 pin Kycon socket.
Remote Unit - Receiver (RX)
Desk: 2x DisplayPort, 5x USB type A,
2x 3.5mm audio jack sockets,
1x 3.5mm SPDIF socket.
Ethernet: 2x RJ45, 2x SFP+ cages.
Power: 3 pin Kycon socket.
USB
4 ports of USB2.0 with USB True Emulation to support keyboard, mouse and touch.
1 additional port provides transparent high speed USB2.0, best suited to mass storage,
web cams, headsets and microphones.
USB device seen as: 7 or 13 port hub
Maxvideoresolution
Supports 4K UHD or DCI and refresh rates to 60Hz
Supports 5K at 60, 50 or 30Hz refresh rates (dependent on vertical resolution)
Supports 8- and 10-bit color depth
Audio
Analog Line in/out 2 channel 16bit 48KHz 1V RMS in / 1V RMS out
DisplayPort digital audio (LPCM), up to 8 channels, 16, 20 or 24bit, 32, 44.1, 48, 88.2, 96,
176.4 or 192KHz
Ethernet
In-built support for 1GbE CATx
Support for multirate CATx (up to 10GbE) and ber (up to 10GbE) via SFP modules
PackingBox
Dimensions: (L) 285mm /11.2” x (W) 245mm/9.6” x (D)145mm/5.7”
Weight: 2.5kg / 5.5lb
Approvals/Compliance
CE and FCC: See the compliance web page for the full list
Productinformationlabels
The product information labels are located on the base of each unit.
INSTALLATION
CONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
5
Page 7

ALIF4000UNITFEATURES
The ALIF4000 units are housed within durable, vented enclosures with connectors situated on the front and rear panels. The smart front faces
also feature an OLED information screen with control button (to scroll through the various informational pages) and also a status indicator.
Transmitter-front
AdderLink
1
Reset
switch
Transmitter-rear
12V
3A
4000
2
3
CATxandSFPports-
youcanusetheprimary
and/orsecondaryport
ofeithertype,however,
itisnotpossibletomix
types.WhereCATx
greaterthan1GbEis
required,usemultirate
CATxSFPmodules.
4
12
12
Receiver-front
TRANSMIT
AdderLink
4000
2
4
OLED
screen
Reset
switch
Microphone
(analogaudio)
3
1
USB2.0
transparent
highspeed
Control
button
Headphones
(analogaudio)
USB
andstatus
indicator
port
RECEIVE
INSTALLATION
OLED
screen
CONFIGURATIONOPERATION
Control
button
andstatus
indicator
Receiver-rear
optical
1
12V
IN
OUT
AUX
3A
4
5
2
optical
OUT
1
2
34
FURTHER
INFORMATION
Power
in
USB
Reserved
Secondary
Primary
videoin
videoin
Analog
audioin
Analog
audio
out
Serial
(Auxiliary)
port
Power
in
USB
Primary
display
Secondary
display
Analog
audioline
out
CATxandSFPports-
youcanusetheprimary
and/orsecondaryport
ofeithertype,however,
itisnotpossibletomix
types.WhereCATx
greaterthan1GbEis
required,usemultirate
CATxSFPmodules.
INDEX
6
Page 8
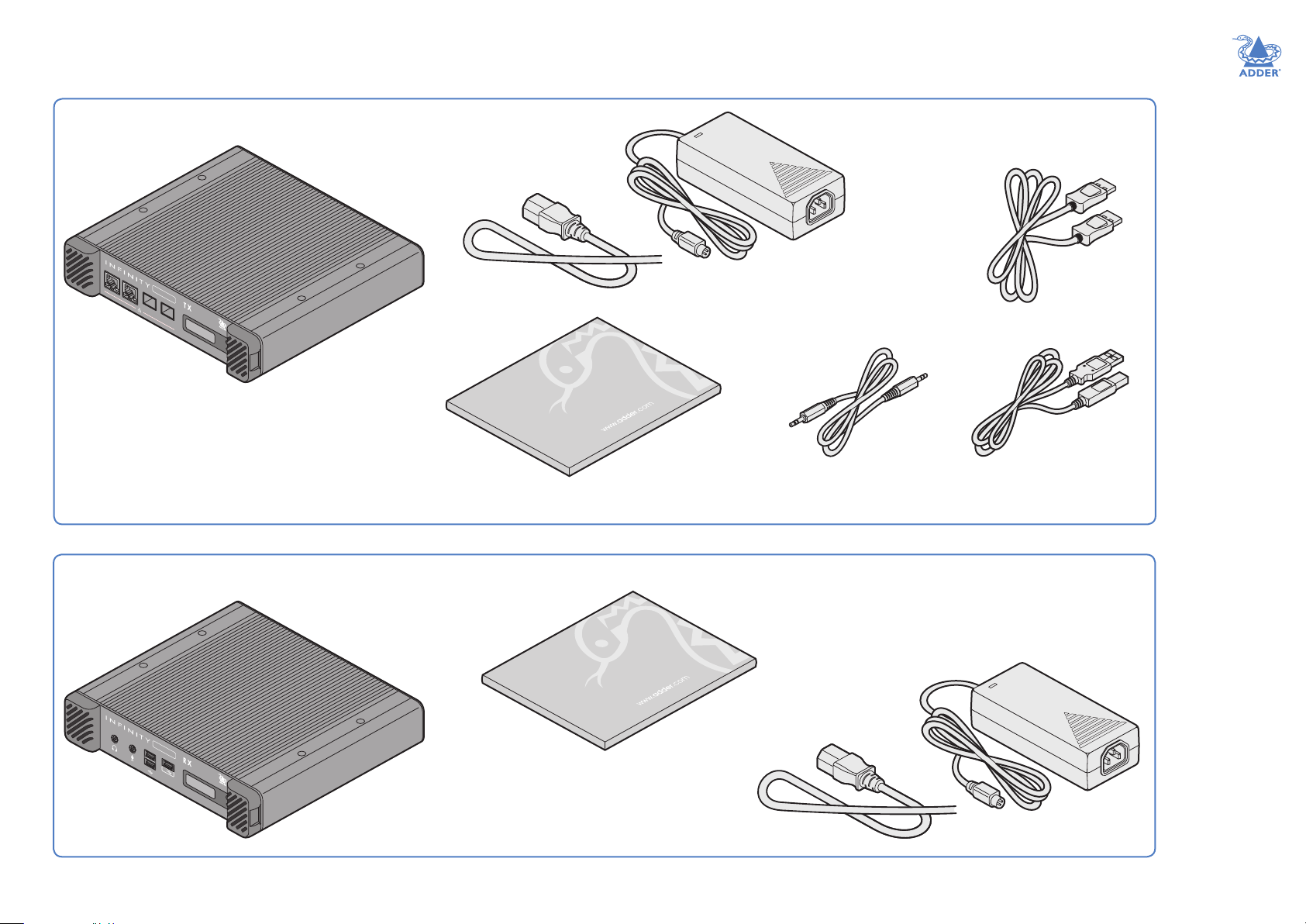
SUPPLIEDITEMS
ALIF4000TXpackage
AdderLink
4 0 0 0
1
2
ALIF4000TXunit
TRANSMIT
3
4
Informationwallet
containing:
Four self-adhesive rubber feet
Quick start guide
Safety document
Poweradapterwith
locking connector
andcountry-specic
powercord
2xAudiocable2m
(3.5mmstereojacks)
2xDisplayport
videocable2m
2xUSBcable2m(typeAtoB)
Part number: VSC24
INSTALLATION
CONFIGURATIONOPERATION
ALIF4000RXpackage
AdderLink
4 0 0 0
2
RECEIVE
3
1
ALIF4000RXunit
Informationwallet
containing:
Four self-adhesive rubber feet
Quick start guide
Safety document
Poweradapterwith
locking connector
andcountry-specic
powercord
FURTHER
INFORMATION
INDEX
7
Page 9

OPTIONALEXTRAS
10GbEsinglemodeberSFPmodule
Part number: SFP-SM-LC-10G
Dualunit19”(1U)rack-mountshelf
Part number: RMK12
Replacementpoweradapter
withlockingconnector
Part number: PSU-IEC-12VDC-5A
Country-specicpowercords
CAB-IEC-AUS (Australia)
CAB-IEC-EURO (Central Europe)
CAB-IEC-UK (United Kingdom)
CAB-IEC-USA (United States)
CAB-IEC-JP (Japan)
CAB-IEC-CN (China)
Rackmountblankingplate
Part number: RMK12-BP
Audiocable2m
(3.5mmstereojacks)
Part number: VSC22
Displayportvideocable2m
Part number: VSCD10A
Please refer to the table in Appendix G for
information about ber modules and cables.
10GbEmultimodeberSFPmodule
Part number: SFP-MM-LC-10G
MultiratecopperSFPmodulefor
10,5,2.5and1GbE
Part number: SFP-CATX-MR
USBcable2m(typeAtoB)
Part number: VSC24
INSTALLATION
CONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
8
Page 10
Installation
CONNECTIONS
Installation involves linking the ALIF4000 TX unit to various ports on the host computer,
while the ALIF4000 RX unit is attached to your peripherals (collectively known as the
Console:
VIDEO
LINK
AUDIO
LINKS
page8
USB
LINK
page9
SERIAL
LINK
page9
page8
FIBRE or
COPPER LINK
POWER
IN
page10
page11
MOUNTING
Please see Appendix H for details about mounting options for the ALIF units.
IMPORTANT:WhenmountingtheALIFunits(andtheirpoweradapters),
ensurethattheventsarenotobscuredandthatthereissufcientairow.
Theoperatingtemperaturerangeis0to40ºC(32to104ºF)andmustnot
beexceeded.
VIDEO
DISPLAY
page 13
MIC &
SPEAKERS
page 13
ALIF4000 RXALIF4000 TX
USB
DEVICES
page14
POWER
IN
page15
Note: RS232
connections are
supported when a
USB to serial adaptor
is used.
INSTALLATIONCONFIGURATIONOPERATION
Click a connection to see details
IMPORTANT: When using an ADDERLink™ INFINITY Management box to
congure ALIF units, it is vital that all ALIF units that you wish to locate and control
are set to their factory default settings. Otherwise they will not be located by the
AIM server. If necessary, perform a factory reset on each ALIF unit.
Please also see Appendix C - Tips for success when networking ALIF units
FURTHER
INFORMATION
INDEX
9
Page 11

1 2
optical
OUT
AUX
IN
1 2
1 2
optical
IN
TXvideolinks
The TX unit supports two DisplayPort
connections, each up to 5K 5120 pixels by
AUDIO
LINKS
VIDEO
LINK
2880, 2160 or 1440, with refresh rates of
30, 50 and 60Hz respectively and at dynamic
ranges of SDR8, SDR10 or HDR10 (ie 8-bit
per colour standard dynamic range, 10-bpc
standard dynamic range, or 10-bpc high
dynamic range). Digital audio, with support
USB
LINK
SERIAL
LINK
ALIF4000 TX
POWER
IN
for stereo, 5.1 surround or 7.1 surround
sound, is also supported via the DisplayPort connections.
Tomakeavideolink
1 Connect your digital video link cable(s) to the DisplayPort
socket(s) on the TX unit rear panel:
LINK
ALIF4000 RX
TXanalogaudiolinks
The TX unit supports two way stereo
analog audio so that you can use a
AUDIO
LINKS
VIDEO
LINK
remote microphone as well as speakers.
Digital audio is handled separately via the
DisplayPort connectors. See Appendix B
- Support for analog and digital audio for
details.
USB
LINK
SERIAL
LINK
ALIF4000 TX
ALIF4000 RX
POWER
IN
Tomakeaudiolinks
1 Connect an audio link cable between the opticalIN socket on the TX
unit rear panel and the speaker output socket of the host computer.
Speakerlinkfrom
hostcomputer
LINK
INSTALLATIONCONFIGURATIONOPERATION
Toprimary
videooutput
port
Tosecondary
videooutput
port
2 Connect the plug at the other end of the cable(s) to the
corresponding video output socket(s) of the host computer.
Microphonelink
tohostcomputer
2 [Where a microphone is to be used]: Connect a second audio link cable
between the OUT socket on the TX unit rear panel and the Line In
socket of the host computer.
FURTHER
INFORMATION
INDEX
10
Page 12
1
1 2
12V
3A
4
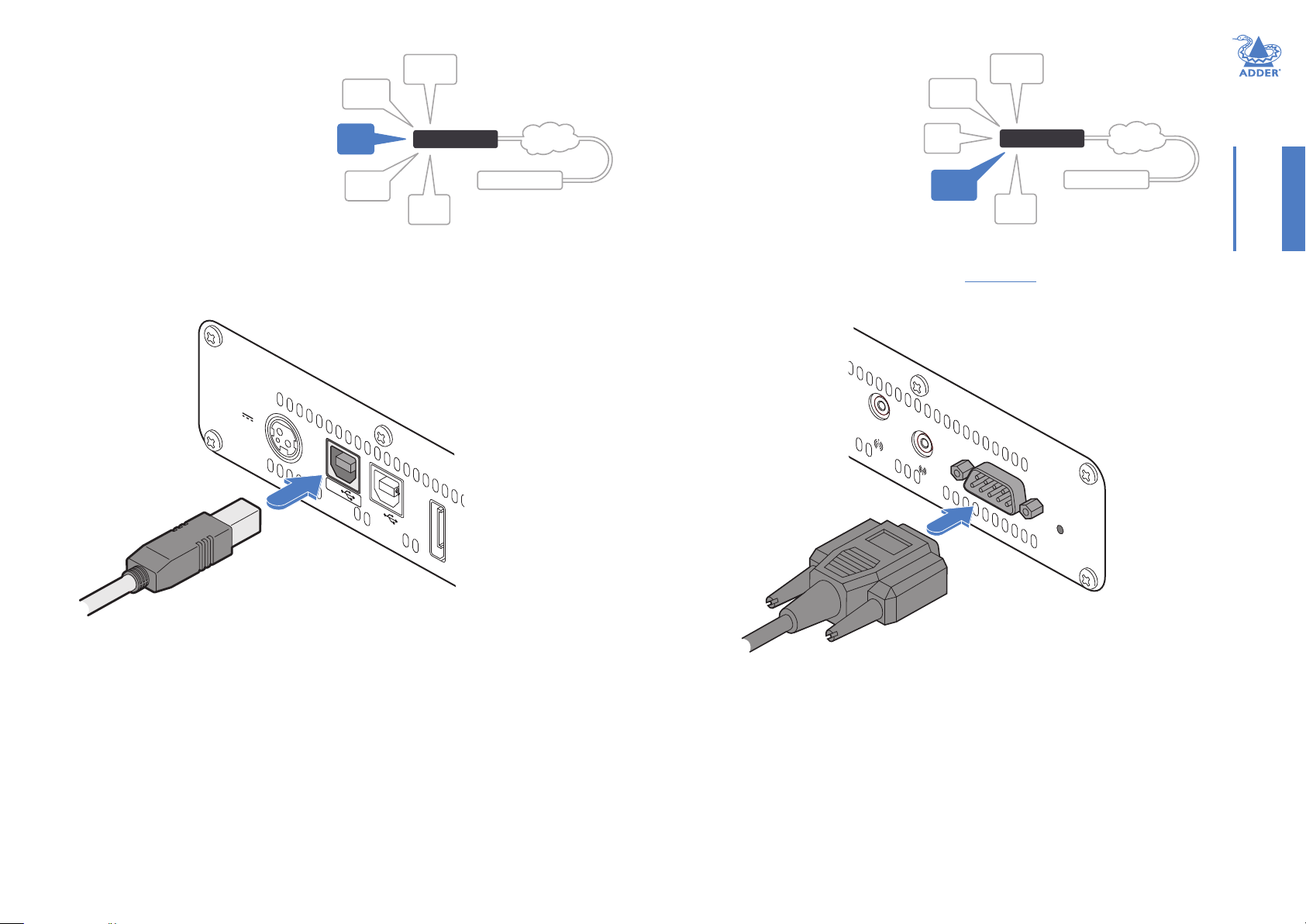
TXUSBlinks
2
optical
OUT
AUX
IN
The TX unit has two USB type B sockets on
the rear panel. Port 2 is not currently used.
AUDIO
LINKS
USB
LINK
SERIAL
LINK
VIDEO
LINK
ALIF4000 TX
POWER
IN
TomakeaUSBlink
1 Connect the type B connector of the supplied USB cable to the
USB port 1 on the TX unit rear panel.
LINK
ALIF4000 RX
TXAUX(serial)port
The AUX port is an RS232 serial port
that allows extension of RS232 signals up
AUDIO
LINKS
VIDEO
LINK
to a baud rate of 115200. The port has
software ow control, but no hardware
ow control. A third-party USB-to-serial
adaptor is required at each RX unit (that
is required to make a serial link).
USB
LINK
SERIAL
LINK
ALIF4000 TX
POWER
IN
LINK
ALIF4000 RX
ToconnecttheAUXport
1 Connect a suitable serial ‘null-modem’ cable (see Appendix F for pin-out) between a
vacant serial port on your computer and the AUX port on the right hand side of the
ALIF rear panel.
Serial(null-modem)link
fromyourcomputer
INSTALLATIONCONFIGURATIONOPERATION
USBlinkfrom
hostcomputer
(supplies ports
2 to 5 on RX)
2 Connect the type A connector of the supplied cable to
a vacant USB socket on the host computer.
2 At the required RX unit(s), use a USB-to-serial adaptor connected to one of the USB
ports.
FURTHER
INFORMATION
INDEX
11
Page 13
1
12V
3A
1 2
12V
3A
4
4
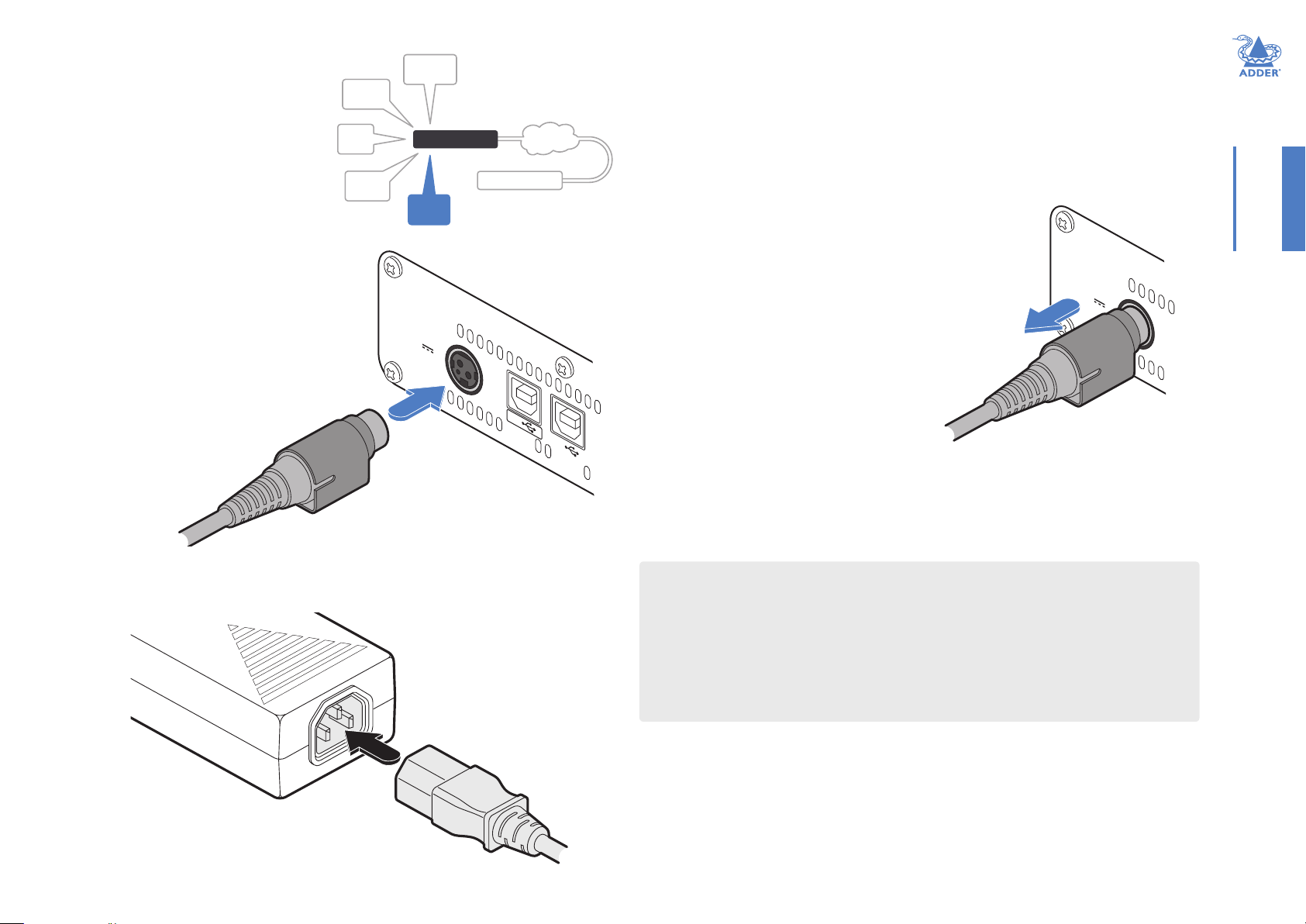
TXpowerin
Each unit is supplied with a power
adapter and country-specic power
cord. The supplied power adapter uses
a locking-type plug to help prevent
accidental disconnection; please follow
the instructions shown on the right
when disconnecting a power adapter.
Toconnectthepoweradapter
1 Attach the output plug of the supplied
power adapter to the power input
socket on the left side of the rear
panel. As you insert the plug, pull back
slightly on the outer body to assist
the locking mechanism until the plug
is fully inserted.
AUDIO
LINKS
USB
LINK
SERIAL
LINK
VIDEO
LINK
ALIF4000 TX
POWER
IN
LINK
ALIF4000 RX
Todisconnectthepoweradapter
1 Isolate the power adapter from the mains supply.
2 Grasp the outer body of the power adapter plug
where it connects with the node.
3 Gently pull the body of the outer plug away from
the node. As the body of the plug slides back, it will
release from the socket and you can fully withdraw
the whole plug.
INSTALLATIONCONFIGURATIONOPERATION
Gentlypullbacktheplugouter
bodytoreleasethelock
Fromthe
poweradapter
2 Insert the IEC connector of the supplied country-specic
power cord to the socket of the power adapter.
3 Connect the power cord to a nearby mains supply socket.
IMPORTANT:Pleasereadandadheretotheelectricalsafetyinformation
givenwithintheSafetyinformationbookletprovidedwiththisproduct.In
particular,donotuseanunearthedpowersocketorextensioncable.
Note: The unit and the power adapter generate heat when in operation and will become
warm to the touch. Do not enclose them or place them in locations where air cannot circulate
to cool the equipment. Do not operate the equipment in ambient temperatures exceeding
40 degrees Centigrade. Do not place the products in contact with equipment whose surface
temperature exceeds 40 degrees Centigrade.
FURTHER
INFORMATION
INDEX
12
Page 14

TX/RXhighspeedlinks
AdderLink
4 0
2
3
1
1 2
2
optical
OUT
ALIF4000 units can be either connected directly to each other or via a high speed (up to
10GbE) network. There are three main ways to make high speed links:
• Using the in-built CATx port(s) for connections up to 1GbE (see below),
Allows high video resolutions but with reduced frame rates. Use both CATx ports in
combination for teaming to mitigate the relatively slow data rate and improve video quality.
• Using the SFP port(s) with optional CATx module(s) for connections up to 10GbE
(see next page),
Single or dual 10GbE links will allow full resolution and high frame rate video to be
transferred. Slower links may be subject to varying frame rates, depending on the video
content and CODEC settings. Dual links to provide teaming will help a great deal,
particularly with slower connection speeds.
• Using the SFP port(s) with optional ber (FCoE) module(s) for connections up to
10GbE (see next page),
Single or dual 10GbE links will allow full resolution and high frame rate video to be
transferred. Dual links to provide teaming will help a great deal, particularly with slower
connection speeds.
VIDEO
DISPLAY
ALIF4000 RX
POWER
IN
MIC &
SPEAKERS
USB
DEVICES
AUDIO
LINKS
USB
LINK
SERIAL
LINK
VIDEO
LINK
ALIF4000 TX
POWER
IN
LINK
LINK
OptionalSFPmoduletypes
• SFP-CATX-MR for use with CAT5e (and above) cable.
• SFP-SM-LC-10G modules require OS1 or OS2 single mode ber.
• SFP-MM-LC-10G modules require OM1, OM2, OM3 or OM4 multi-mode ber.
See Appendix G for further details about SFP modules and cable lengths.
INSTALLATIONCONFIGURATIONOPERATION
TolinkALIF4000unitsin-builtCATxports
1 Insert suitable CATx cables into the primary
and, if necessary, secondary RJ45 ports on the
front panel of the TX unit.
2 Connect the other end(s) of the CATx cable(s)
to either a network switch or...
Primary
CATxlink
Secondary
CATxlink
TXunit
frontpanel
... connect directly to the RX unit: to the RJ45
port(s) on the rear panel of the RX unit.
Primary
CATxlink
Secondary
CATxlink
RXunit
rearpanel
FURTHER
INFORMATION
INDEX
13
Page 15

4 0 0 0
TRANSMIT
2
3
4
4 0 0 0
TRANSMIT
2
3
4
1 2 3 4
4 0 0 0
TRANSMIT
2
3
4
TolinkALIF4000unitsviaCATxmodules
1 2 3 4
4 0 0 0
TRANSMIT
2
3
4
1 Insert the optional SFP module(s) (SFP-
CATX-MR) into socket 3 and, if necessary,
socket 4 located on the front panel of the TX
unit...
Note:Takecarewhen
insertingmultirateSFP
modulesastheycandamage
themetaltabatthetopof
thesocketifmisaligned.
CATxSFP
module
...and the rear panel of the RX unit:
TXunit
frontpanel
TolinkALIF4000unitsviabermodules
1 Insert the appropriate optional SFP module
(SFP-MM-LC-10G or SFP-SM-LC-10G) into
socket 3 located on the front panel of the
TX unit...
FiberSFP
module
...and the rear panel of the RX unit:
TXunit
frontpanel
INSTALLATIONCONFIGURATIONOPERATION
RXunit
rearpanel
2 Make your CATx connection(s)
between the SFP module(s) and
either the other ALIF4000 unit or
to a suitable network switch.
CATxlink
RXunit
rearpanel
2 Make your ber connection(s) between the
SFP module(s) and either the other ALIF4000
unit or to a suitable ber network switch.
3 Close the latch over the link connectors to
lock them into place.
Transmitand
receiveberlinks
FURTHER
INFORMATION
INDEX
14
Page 16

1 2
4
5
optical
OUT
RXvideodisplay
AdderLink
4 0
2
3
The RX unit supports two DisplayPort
connections, each up to 5K 5120 pixels
by 2880, 2160 or 1440, with refresh
rates of 30, 50 and 60Hz respectively.
Digital audio, with support for stereo,
5.1 surround or 7.1 surround sound,
is also supported via the DisplayPort
connections.
ALIF4000 TX
LINK
VIDEO
DISPLAY
ALIF4000 RX
POWER
IN
MIC &
SPEAKERS
USB
DEVICES
RXmicrophone&speakers
The RX unit can support a
microphone as well as speakers
providing the necessary connections
have been made between the TX unit
and the host computer. Digital audio is
handled separately via the DisplayPort
connectors. See Appendix B - Support
for analog and digital audio for details.
ALIF4000 TX
LINK
VIDEO
DISPLAY
ALIF4000 RX
POWER
IN
MIC &
SPEAKERS
USB
DEVICES
INSTALLATIONCONFIGURATIONOPERATION
Toconnectvideodisplays
1 Connect the lead from the primary video display to the DisplayPort
socket marked ‘1’ on the RX unit rear panel:
To
primary
video
display
To
secondary
videodisplay
2 If required, connect the lead from the second video display to the
DisplayPort socket marked ‘2’ on the RX unit rear panel.
Toconnectamicrophone(orlinein)and/orspeakers
1 Connect the lead from a
mono microphone to the
3.5mm socket labeled on
the front panel.
2 Connect the lead from
stereo speakers to the
3.5mm socket labeled on
the front panel.
Tospeakers/
headphones
From
microphone
FURTHER
INFORMATION
INDEX
15
Page 17

RXUSBdevices
4 0 0 0
RECE IVE
2
3
1
1
4
5
A
The ALIF RX unit has ve USB ports
(three on the front panel and two on
the rear) to which peripherals may be
connected.
To connect more than ve peripherals,
ALIF4000 TX
LINK
VIDEO
DISPLAY
ALIF4000 RX
MIC &
SPEAKERS
USB
DEVICES
one or more USB hubs may be used. The
total current that may be drawn from
the USB ports is 1.2A, which should be
POWER
IN
sufcient for a keyboard, mouse (no more than 100mA each) and any two other devices
(500mA maximum each). If more power for USB devices is required, use a powered USB
hub.
ToconnectUSBdevices
1 Connect the lead from the device to any
of the USB sockets on the front and rear
panels of the RX unit.
RS232serialsupport
To support RS232 serial connections, use a third-party USB-to-serial
adaptor connected to any of the USB ports from 2 to 5. The serial
connection will be replicated at the serial port on the connected
ALIF4000 TX unit.
INSTALLATIONCONFIGURATIONOPERATION
ToUSB
peripherals
ToUSB
peripherals
FURTHER
INFORMATION
INDEX
16
Page 18

1
12V
3A
RXpowerin
4
5
12V
3A
Each unit is supplied with a power
adapter and country-specic power
cord. The supplied power adapter uses
a locking-type plug to help prevent
accidental disconnection; please follow
the instructions shown on the right
when disconnecting a power adapter.
Toconnectthepoweradapter
1 Attach the output plug of the supplied
power adapter to the power input
socket on the left side of the rear
panel. As you insert the plug, pull back
slightly on the outer body to assist
the locking mechanism until the plug
is fully inserted.
ALIF4000 TX
LINK
VIDEO
DISPLAY
ALIF4000 RX
POWER
IN
MIC &
SPEAKERS
USB
DEVICES
Todisconnectthepoweradapter
1 Isolate the power adapter from the mains supply.
2 Grasp the outer body of the power adapter plug
where it connects with the node.
3 Gently pull the body of the outer plug away from
the node. As the body of the plug slides back, it will
release from the socket and you can fully withdraw
the whole plug.
INSTALLATIONCONFIGURATIONOPERATION
Gentlypullbacktheplugouter
bodytoreleasethelock
Fromthe
poweradapter
2 Insert the IEC connector of the supplied country-specic power cord to the socket of
the power adapter.
3 Connect the power cord to a nearby mains supply socket.
IMPORTANT:Pleasereadandadheretotheelectricalsafetyinformation
givenwithintheSafetyinformationbookletprovidedwiththisproduct.In
particular,donotuseanunearthedpowersocketorextensioncable.
Note: The unit and the power adapter generate heat when in operation and will become
warm to the touch. Do not enclose them or place them in locations where air cannot circulate
to cool the equipment. Do not operate the equipment in ambient temperatures exceeding
40 degrees Centigrade. Do not place the products in contact with equipment whose surface
temperature exceeds 40 degrees Centigrade.
FURTHER
INFORMATION
INDEX
17
Page 19

Conguration
ALIF4000CONFIGURATIONVIAWEBPAGES
Each ALIF4000 unit hosts its own internal set of web pages which contain all
conguration details and settings (see also Start of Life, shown right). You will need to use
a computer connected to the same network as each ALIF4000 unit to access the web
pages. Additionally, on the console attached to the ALIF4000 RX unit, you can access its
conguration details via the On Screen Display (OSD) by pressing CTRL + ALT + C (or
by tapping the icon on the touchscreen) - see page 25.
TomanuallycongureALIF4000unitsviatheirwebpages
Run a web browser on your computer and enter the IP address of the required
ALIF4000 unit:
The default addresses (if using ports 1 or 3) are TX: https://169.254.1.33
RX: https://169.254.1.32
The default addresses (if using ports 2 or 4) are TX: https://169.254.1.43
RX: https://169.254.1.42
If the IP address of a unit has been changed, you can either:
• Discover the unit’s main IP address by pressing the small
button on the front panel next to the OLED screen to
reveal the value for IP Address 3 (or IP Address 4).
• Alternatively, providing it is appropriate to do so, perform a manual factory reset (see
next page) to restore the default address.
The opening page should be displayed:
IP Address 3
169.254.1.33
StartofLife:AIMorPointtoPointconguration
To streamline initial conguration processes, all ALIF4000 units employ a Start of Life
(SoL) procedure when they are in an uncongured state; either because they are new or
because they have undergone a factory reset.
When an uncongured ALIF4000 unit boots, its SoL procedure will guide it to
automatically determine which of two modes it should adopt:
• AIMmode - place itself into the control of a specic AIM server on the network,
whereupon the ALIF4000 will be assigned suitable conguration details to t within
the network of similar units.
• P2Pmode - place itself into Point to Point (P2P) mode to allow manual conguration
of links with other ALIF units.
The SoL procedure follows this basic logic ow to determine the correct mode:
SoL:
Is a DHCP
server
available?
Y
N
Enter P2P mode
RX units:
seek out suitable
TX endpoints
on the network.
INSTALLATIONCONFIGURATIONOPERATION
For explanations of the options within each page, please see Appendix A.
Does the
DHCP have a valid
Option 125
instruction?
Y
Enter AIM mode
Place yourself under
control of the AIM server
listed in the Option 125
instruction.
N
Stop auto-config
to allow
manual configuration
See next page
FURTHER
INFORMATION
INDEX
18
Page 20

StartofLifeconguration(continued)
PERFORMINGAMANUALFACTORYRESET
A factory reset returns ALIF4000 unit to its default conguration.
Create a preset to
suit the located
TX endpoint.
TX endpoint using
Create a simplified preset
(169.254.x.x) TX address.
Connection
established to a
the preset?
From previous page
RX:
How manyTX
endpoints
located?
0
and assume a link-local
N
Toperformamanualfactoryreset
1 Power on the ALIF4000 unit.
2 Use a long narrow implement
(e.g. a straightened-out paper clip)
to press-and-hold the recessed
>11
Stop auto-config
to allow
manual configuration
reset button on the front panel
for roughly ten seconds, until the
status indicator turns blue (Note:
AdderLink
INSTALLATIONCONFIGURATIONOPERATION
alternating red/green indications will
occur during the ten second period
while the button is still pressed).
3 Release the reset switch. The
indicator will change to red for a
short while (less than ten seconds)
and then back to blue while ALIF4000 unit performs the reset and should then
change to an alternative color, usually orange initially, signifying that the operation is
complete.
Note: If you are performing a factory reset and intend to disconnect the power immediately
after the reset, you must wait at least 30 seconds after you have released the reset button
for it to complete the process.
Y
Operate with TX endpoint
Once the mode has been set to AIM control, an
ALIF4000 will remain operating that way until it
undergoes a factory reset. If set to P2P mode, an
ALIF4000 will remain thus until it undergoes a
factory reset or is discovered by an AIM server.
FURTHER
INFORMATION
INDEX
19
Page 21

PLACINGTHEDEVICEINTORECOVERYMODE
Recovery mode may allow an ALIF4000 unit to be diagnosed or upgraded in the event of
the main mode being non-operational.
Tobootthedeviceintorecoverymode
1 Power on the ALIF4000 unit.
2 Use a long narrow implement (e.g.
a straightened-out paper clip) to
press-and-hold the recessed reset
button on the front panel (for less
than ten seconds) until the status
indicator starts alternating red/
green. Note: A solid blue indication
will occur after the ten second period.
3 Release the reset switch. The
indicator will change to red for a
short while (less than ten seconds)
and then alternating red/green
signifying that the device is in recovery mode. Note: If the indicator turns blue, then a
factory reset has been performed instead, the device will not be in recovery mode and the
operation will need to be attempted again.
AdderLink
INSTALLATIONCONFIGURATIONOPERATION
20
FURTHER
INFORMATION
INDEX
Page 22

CONFIGURINGDUALTOUCHSCREENS
When a single touchscreen is used with an ALIF RX, it should operate correctly as
soon as the USB link is made between the screen and the ALIF RX. However, if two
touchscreens are installed it may be necessary to instruct the ALIF RX which screen to
correctly attribute to each USB input.
Toattributedualtouchscreens
1 Access the Conguration pages on the ALIF RX - see page 25.
2 Click the Ports entry from the list of pages on the left side.
3 Click the USB page icon: to display the following:
INSTALLATIONCONFIGURATIONOPERATION
4 In the USB Port Mapping and Reservations section, match the primary touchscreen to
the port number (2 -5) that its USB cable is connected to.
5 Repeat step 4 for the secondary touchscreen.
6 Click the Apply button and exit from the conguration pages.
FURTHER
INFORMATION
INDEX
21
Page 23
CREATINGANUNMANAGEDMATRIX
Although ALIF units are most often organised and managed by a central AIM server, it is
possible to create small networks of ALIF units, most often in matrix arrangements, ie
multiple TX and RX units which can freely cross-connect.
TRANSMIT
AdderLink
4000
4
3
TX
2
1
TRANSMIT
AdderLink
4000
4
3
TX
2
1
Fiber/IP
network switch
RECEIVE
AdderLink
4000
2
1
RX
3
RECEIVE
AdderLink
4000
2
1
RX
3
This method of connection works well for small numbers of TX and RX units, but will
become more difcult to manage as more units are attached. The maximum number of
TX sources that can be made available to any RX is 16.
Tocreateanunmanagedmatrix
1 Connect ALIF4000 TX and RX units (with their various hosts and peripherals) to a
suitable switch, as described in the Installation section - see page 9.
Note: If any device was previously managed by AIM, then it will need to be given a factory
reset before continuing with this procedure. There must not be an AIM connected on the
matrix network otherwise, when such devices undergo a factory reset, they will automatically
revert to AIM control.
You now need to perform the following procedure on each ALIF RX in turn:
2 Access the Conguration pages - see page 25.
3 Click the Transmitters option from the list on the left side. This page will list all of the
available TX units which are not under AIM control. See page 35.
4 Click the Presets option from the list on the left side. Use this page to add each TX
unit to the list of presets for the RX that you are editing. See page 30.
INSTALLATIONCONFIGURATIONOPERATION
Tousethematrix
• On each RX, use the OSD to access the required TX units in the usual manner.
See page 25.
FURTHER
INFORMATION
INDEX
22
Page 24
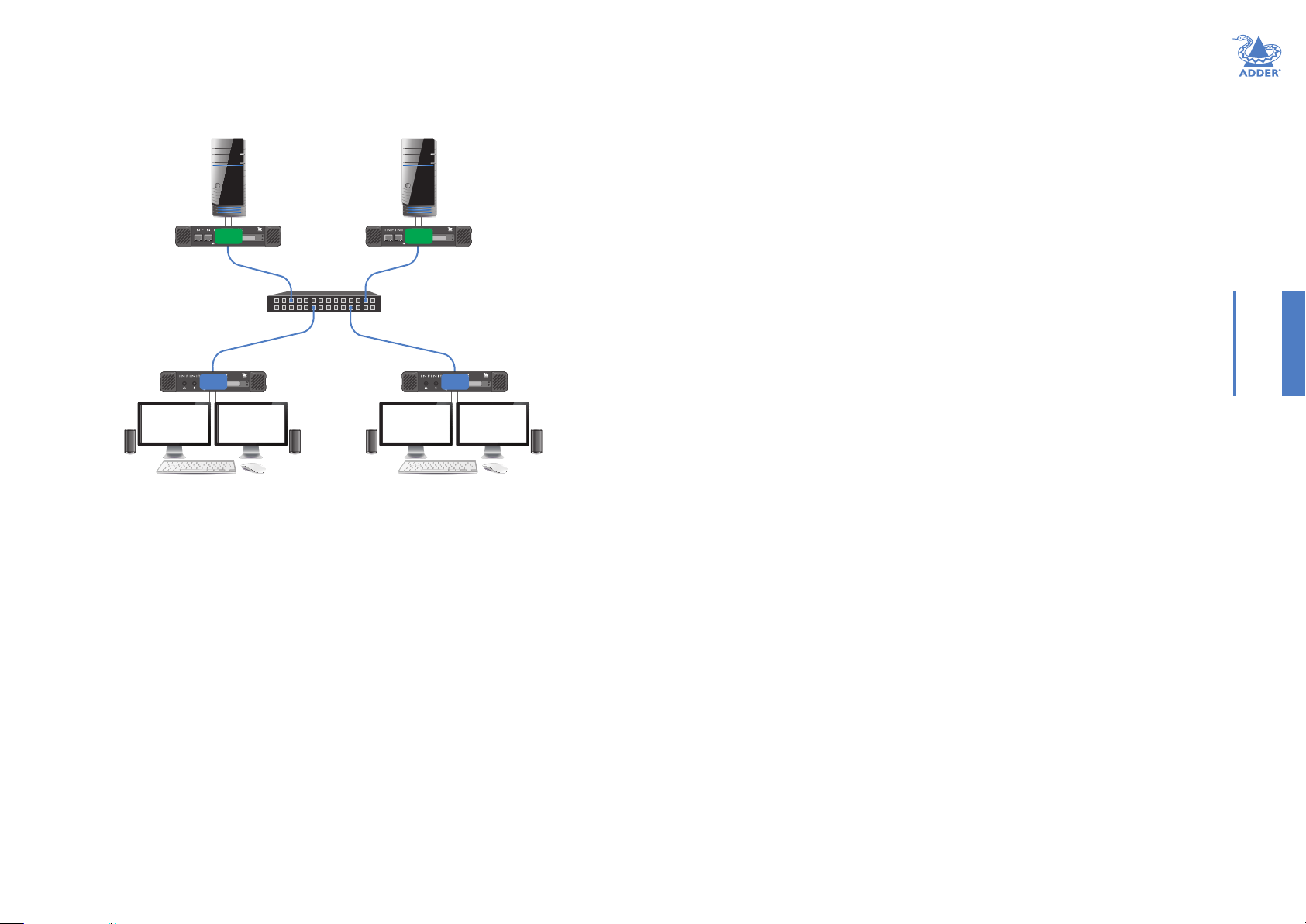
CREATINGANDEDITINGPRESETS
Presets allow you to create shortcuts from any ALIF receivers to any available ALIF
transmitters. These are particularly useful when using an ALIF installation that is not
under AIM control.
ToaccessthePresetcongurationpage
1 On the console keyboard attached to the RX unit, access the OSD by pressing
CTRL+ALT+C or tap the icon on the touchscreen.
2 The Preset Selection page will be displayed:
3 Click/tap the icon in the top right corner.
4 Choose the Presets option from the list on the left side of the screen. This page will
show the same list of presets, but with options to add ( ) or edit ( ) entries:
4 You can now choose how to congure your new preset - Auto or Custom:
• Auto - Click the Auto Congure Preset drop down and choose the ALIF transmitter
that you wish to connect with. All of the required connections will be congured (on a
1-to-1 basis) between the receiver and chosen transmitter. Click the Apply button.
• Custom - Congure individual connections (useful when unusual cross connections
are required).
1 Click the icon on the right side to add a new connection entry.
2 Check that the correct ALIF4000 TX is shown in the TX Device column. Click and
change this entry, if required.
3 In the Type column, click the Select option (highlighted in red) and choose the type
of connection: Video, Audio, USB or Serial.
4 Click the RX Port drop down and choose the required port.
5 Click the TX Port drop down and choose the port that you wish the current RX
port to connect with. If only one option is available it will be auto-selected.
6 Repeat steps 1 to 5 for each of the required ports.
7 Click the Apply button.
Toeditapreset
1 Access the Preset conguration page as discussed left.
2 In the Actions column, click the icon for the preset entry you wish to edit. An
editable list of connections will be shown, together with their status representations:
INSTALLATIONCONFIGURATIONOPERATION
Toremoveapreset
1 Access the Preset conguration page as discussed above.
2 In the Actions column, click the icon for the entry that you wish to remove.
Toaddapreset
1 Access the Preset conguration page as discussed above.
2 Click the icon at the lower right corner of the list to display the conguration page:
3 Enter a name and description for the new preset.
3 Make your changes as required and then click the Apply button to save.
Tore-orderpresets
1 Access the Preset conguration page as discussed left.
2 Click and drag a preset to the required position within the list.
For more information about the options and status indications, see page 30.
FURTHER
INFORMATION
INDEX
23
Page 25

Operation
In operation, many ALIF4000 installations require no intervention once congured. The
TX and RX units take care of all connection control behind the scenes so that you can
continue to work unhindered.
FRONTPANELINDICATIONS
The front panel of each ALIF4000 unit features an OLED information screen plus a single
indicator capable of producing numerous color and ash patterns to provide a useful
guide to operation.
OLEDscreen
Press and release the button to wake the OLED screen and begin showing information.
Press the button repeatedly to change between subjects:
IP Address 3
169.254.1.33
Software Version
3.00
Video Source 1
5120x1440@60
BaseIPaddress
Internalrmwareversion
Videosource
INSTALLATIONCONFIGURATIONOPERATION
Indicatorcolorandashpatterns
The single front panel indicator uses varying color and ashing patterns to signal key
status :
Off No power.
Green All services present as compared to the conguration required.
Amber Running but video, USB or network link missing (or not connected
to another ALIF unit).
Red Booting before processor loaded or failed.
Blue Factory reset mode active.
Red/green ash Booting into factory recovery mode.
Green/blue ash Upgrade mode active.
Fast green ash Identify mode active.
FURTHER
INFORMATION
MAC Address 4
000F5802E7A7
Serial No.
1904A0000164
MACaddresses
INDEX
Serialnumber
24
Page 26

USINGTHEONSCREENDISPLAY
The OSD provides a quick and easy way to access ALIF transmitters as well as
conguration details.
ToaccesstheOSD
1 On the console of your ALIF4000 RX unit, either:
• Press CTRL + ALT + C on the keyboard,
or
• Tap the icon* on the touchscreen.
2 The Preset Selection page will be displayed:
3 On the preset page, either
• Click/tap a preset entry to connect with the required ALIF TX,
or
• Click/tap the icon to enter the rst Conguration page:
TousetheOSDkeyboard(whenusingatouchscreen)
1 Access the OSD as discussed left.
2 Tap the icon in the top right corner:
3 The OSD keyboard will be displayed to assist you when entering text and numerics:
INSTALLATIONCONFIGURATIONOPERATION
TohidetheOSDkeyboard
1 Tap the icon in the top right corner.
For explanations of the options within each page, please see Appendix A.
FURTHER
INFORMATION
INDEX
* To move the icon on your touchscreen, tap and hold it until it changes color and
then drag it to the best position.
25
Page 27

Further information
This chapter contains a variety of information, including the following:
• Getting assistance - see right
• Appendix A - Conguration pages
• Appendix B - Support for analog and digital audio
• Appendix C - Tips for success when networking ALIF units
• Appendix D - Troubleshooting
• Appendix E - Glossary
• Appendix F - RS232 ‘null-modem’ cable pinout
• Appendix G - Fiber modules and cables
• Appendix H - Using the optional ALIF4000 rack shelf
• Appendix I - Open source licenses
GETTINGASSISTANCE
If you are still experiencing problems after checking the information contained within this
guide, then please refer to the Support section of our website:
www.adder.com
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
26
INFORMATION
INDEX
Page 28

APPENDIXA-Congurationpages
This section covers the web page conguration for the ALIF4000 units:
• RX - General Information
• RX - UI Settings
• RX - Presets
• RX - Users
• RX - Ports
• RX - Network
• RX - Transmitters
• RX - Diagnostics and Statistics
• RX - System
• TX - General Information
• TX - UI Settings
• TX - Users
• TX - Ports
• TX - Network
• TX - Diagnostics and Statistics
• TX - System
INSTALLATIONCONFIGURATIONOPERATION
TousetheOSDkeyboard(whenusingatouchscreen)
1 Access the OSD as discussed on page 25.
2 Tap the icon in the top right corner of the screen.
3 The OSD keyboard will be displayed to assist you when entering text and numerics:
TohidetheOSDkeyboard
1 Tap the icon in the top right corner.
FURTHER
INFORMATION
INDEX
27
Page 29

RX-GeneralInformation
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 If necessary, click the General link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 If necessary, click the General link.
INSTALLATIONCONFIGURATIONOPERATION
GeneralInformation
Type - States whether the device is a transmitter (TX) or a receiver
(RX).
Name - Name details that you can alter to distinguish this unit from all
others. Not shown when operating under AIM server control.
Description - Allows you to optionally add a description of the device.
Useful when many ALIF units are being used. Not shown when operating
under AIM server control.
Location - Allows you to optionally add a description of the device’s
location. Useful when many ALIF units are being used. Not shown when
operating under AIM server control.
CurrentSoftwareVersion - Displays the version number of the
currently installed (and active) internal software.
SerialNumber - Displays the xed serial number of the device.
BoardRevision - Displays the revision number of the device’s main
circuit board.
Model - Displays the model number of the device.
DateandTime - Displays the current date and time used by the device
when this page was last loaded (select refresh icon to update).
Uptime - Shows the time period for which the device has currently
being running since the last time this page was loaded (select refresh
icon to update).
IdentifyDevice - When clicked, this button will cause the indicator on
the front panel of the device to ash to assist with identication when
multiple units are installed in the same area. A popup dialog will also be
displayed on screen showing all relevant identication details. Click the
Cancel button to stop the identication process or click the OK button
to close the popup (and then click the Identify Device button when
you’re ready to cancel this operation).
FURTHER
INFORMATION
INDEX
28
Page 30

RX-UISettings
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the UISettings link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 Click the UISettings link.
INSTALLATIONCONFIGURATIONOPERATION
UISettings
OSDNoticationPosition(plusTimeout) - Determines the
location and persistence of notications issued on users’ screens.
OSDBannerPosition(plusTimeout) - Determines the location and
persistence of banners (a banner is a popup showing the current preset/
channel name) displayed on users’ screens.
OSDTimeout - Reserved for future use.
FrontPanelTimeout - Determines the period of inactivity that should
elapse before the front panel display should return to a blank state.
LEDbrightness - Determines the brightness of the front panel LED
indicator.
The following entries are also displayed when the unit is not under AIM
control:
Language - Determines the language used for all text labels within the
conguration pages.
KeyboardLayout - Determines the appropriate keyboard layout for
use with the conguration pages.
TouchShowOSD - (When touch screens are used) Determines
whether the Show OSD icon is displayed continually, not at all or
automatically.
TouchShowIconSize - (When touch screens are used) Determines
the size of the Show OSD icon. Options range from Small to Very Large.
MouseShowOSD - Determines the mouse button press combination
that should be used to call the OSD.
HotkeyModiers - Determines the special modier keys that will be
used to form the basis of all the hotkey functions listed below.
ShowOSD......LastPreset - These entries determine the hotkey
letters required (together with the modier keys selected above) to
enact various presets and modes. Not shown when operating under AIM
server control.
FURTHER
INFORMATION
INDEX
29
Page 31

RX-Presets
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD by pressing CTRL
+ALT+C or tap the touchscreen icon. The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Presets link to show the Preset Selection page.
4 In the list, click the icon for the required TX unit.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit: https://169.254.1.32 (this
is the default address when using SFP port 3 or RJ45 port 1). If you are using SFP port 4
or RJ45 port 2, then the default address will be https://169.254.1.42 If the IP address
is unknown, press the small button on the front panel next to the OLED screen to
reveal the value for IP Address 3 or 1 (or IP Address 4 or 2) and use that address.
3 Click the Presets link to show the Preset Selection page.
4 In the list, click the icon for the required TX unit.
INSTALLATIONCONFIGURATIONOPERATION
PresetInformation
This page lists the details and connection status for the current channel/
preset which the receiver is using. Under AIM control this lists the
connection details for the channel that the RX is currently connected to.
Each row details one type of connection which has been made. It lists
the output port on the RX and the source port from the TX which it is
connected to, as well as the name of the device it is connected to.
Click this icon in the Actions column to remove a particular row of
connections from the list.
Click this icon to manually set the password for the specied device
so that it has the necessary permission to access the appropriate
channel on the selected transmitter. In most connections, the access
passwords for all the peripherals will be set collectively during the
initial linking between the receiver and transmitter. The links
given here provide an alternative method as backup.
Click this icon to add a new connection to the list.
AutoCongurePreset - Select to automatically create a new set of
connection presets from the selected TX.
Analoganddigitalaudio
ALIF4000 units support both analog and digital audio connections from
the host PC. Although originating from possibly the same audio source,
these two connections are switched completely separately and cannot
be mixed. In the connections table, the two types are represented thus:
• Analog audio (
• Digital audio (1 or 2) at RX only connect to (1 or 2) at TX.
For more details, please see Support for analog and digital audio.
) at RX only connects to (
) at TX.
Status
The following icons may be shown within the Status column:
The connection is fully operational.
A connection has not been established.
The control protocol version is incompatible/unsupported between
the peer and this device.
The control protocol security settings are incompatible/unsupported
between the peer and this device.
The connection failed the authorisation stage (most likely a bad
password).
The connection is established but there is no input signal being
received from the peer device.
The connection has an invalid or unsupported input source signal
peer device (audio and video connections only), or
The connection is currently out of resources at the peer device, or
There is insufcient network bandwidth to support the requested
data for this connection.
The encoding of the source data at the peer has stopped (due to an
error or fault).
There is no output device available on the port for this connection
(eg. no monitor connected).
There is no data currently being received by the device.
The video data for the connection produces an output signal that
is out of range for the capabilities of this device, or the appliance
connected to this device, or
The device is currently out of resources to process the video data
for this connection.
The audio data for the connection produces an output signal that
is out of range for the capabilities of this device, or the appliance
connected to this device, or
The device is currently out of resources to process the audio data
for this connection.
The decoding of the data at this device has stopped (due to an error
or fault).
FURTHER
INFORMATION
INDEX
30
Page 32
RX-Users
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Users link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 Click the Users link.
Useraccounts
This page allows you to change the password for the admin user.
Click the icon to display the following dialog:
INSTALLATIONCONFIGURATIONOPERATION
Enter and conrm the current and new admin password and click OK.
FURTHER
INFORMATION
INDEX
31
Page 33

RX-Ports
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Ports link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 Click the Ports link.
INSTALLATIONCONFIGURATIONOPERATION
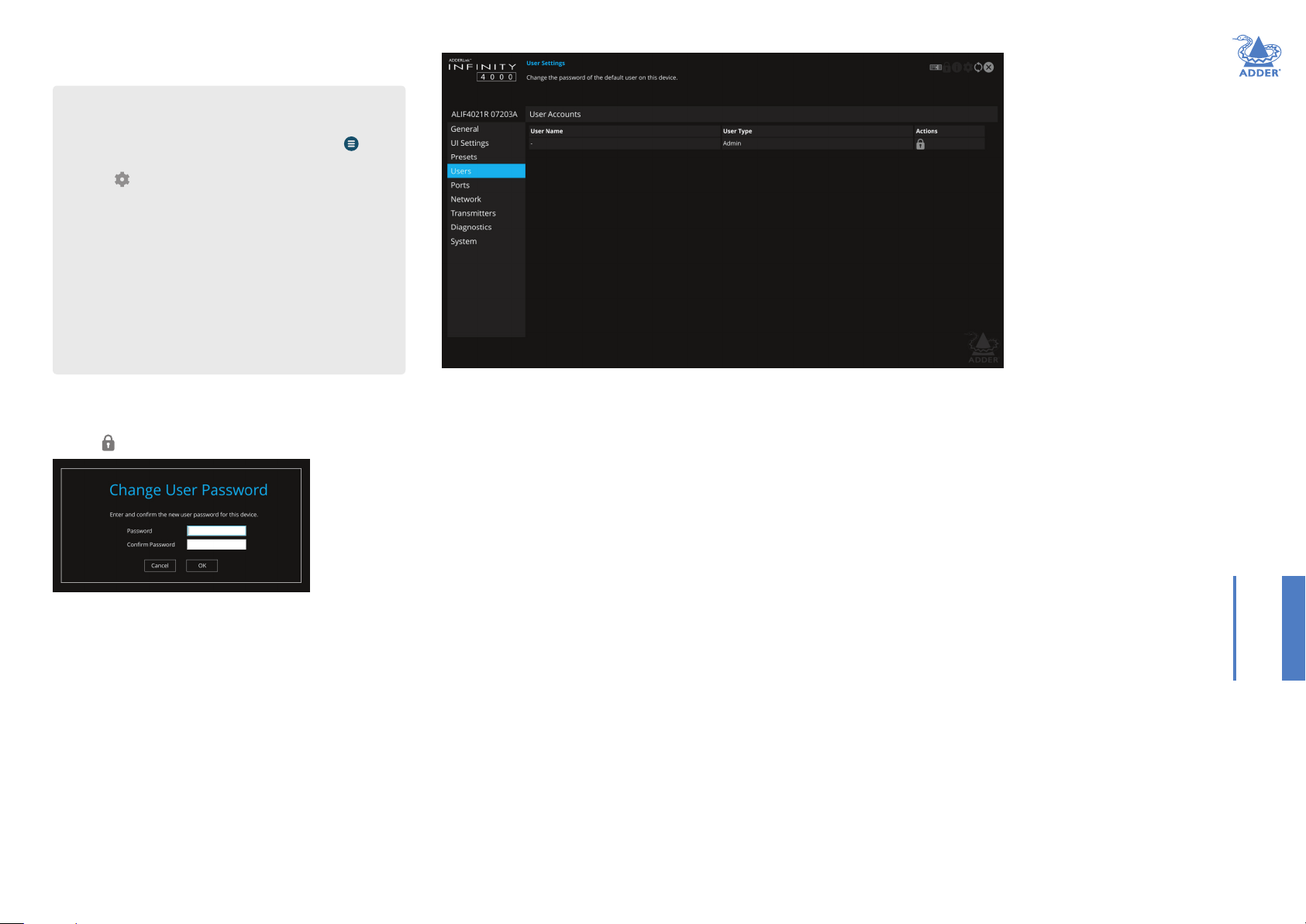
VideoPorts
This page provides basic information about the two video ports located
on the RX unit.
Enabled - Conrms whether each video port is enabled or disabled.
Connected - Conrms whether functioning video displays are
connected to the two video ports.
VideoEDIDDetails - Click the Details button to show a popup for
the connected video display. EDID details listed include: Manufacturer,
model, serial number, manufacture date, EDID version as well as supported
(and preferred) EDID modes, maximum bits per color, encodings, colourimetry
and dynamic range masterings supported by the monitor. Note: EDID modes
that are supported by the monitor but not by the device will be greyed out. In
cases where a resolution reported by the video display is supported, but at a
lower frame rate than the display calls for, such entries will be shown in italics.
CompatibilityCheck - WARNING: Disabling this option can result in
damage to display monitors in certain circumstances. When ticked this
option conrms video compatibility between the source and display
device, (such as the video display’s maximum resolution, bpc, SDR/HDR,
etc.) and prevents signals being sent that the video display can’t support.
When unticked, signals will always be sent regardless of video display’s
declared capabilities. If you untick the option, the following warning will
be displayed:
FrameRateSwitching - Determines the strategy to use for the frame
rate when switching resolutions. Similar in function to the Match Frame
Rate setting on AIM servers:
Force 60 - The frame rate is always forced to be 60Hz unless the
Compatibility check option is on and the monitor does not indicate it
supports 60Hz.
Retain - When switching to the same resolution with a potentially
different frame rate, it will retain the current frame.
Auto - The frame rate always changes to match the mode it is connected to.
AudioPorts
This page provides basic information about the analog and digital audio
ports located on the RX unit.
Enabled - Conrms whether the audio ports are enabled or disabled.
Connected - Conrms whether devices are connected to respective
ports.
Gain - (Analog audio only) Determines the microphone amplication level:
None - no device connected on this port.
Mic - standard gain for normal microphone input devices.
Mic boost - 20dB boost to volume for microphone input devices.
AudioEDIDDetails - Click the Details button to show a popup
listing the audio capabilities of the device connected to that DP port.
Unsupported formats will be greyed out.
CompatibilityCheck - When ticked, the RX will not output audio
on this port if it is not compatible with the attached device’s audio
capabilities. If unticked, audio will be output regardless of the attached
device’s capabilities. For example, if an attached device supports 2
channel stereo but the incoming stream is 6 channels, turning this off
may allow L & R audio output to work - if the attached device can cope,
but other channels will be lost (ie. there is no down-mix support).
USBPorts
This page provides basic information about the USB ports numbered 2
to 5 inclusive, located on the RX unit. USB port 1 is transparent and its
devices are not listed.
Type - Identies the type of the USB port. Port 1 on the front of the RX
is Transparent, 2-3 on the front, 4-5 on the back are the Emulated ports.
Enabled - Conrms whether the USB ports are enabled or disabled.
HIDOnly - (For emulated USB ports only) When ticked, all ports are
limited to supporting Human Interface Devices only, such as keyboards
and mice.
DisableMassStorage - When ticked, this option prevents the use
of USB mass storage devices on the receiver unit. This could be useful
in situations where smart card readers need to be used for security
purposes but the use of USB drives need to be prevented.
Security - (For emulated USB ports only) Controls whether USB data
is encrypted. On forces always on, Off forces always off and Prefer off will
be off unless the TX requests it.
FURTHER
INFORMATION
INDEX
continued
32
Page 34

RX-Ports(continued)
USBPortMappingandReservations - This section is useful when
multiple touchscreens are in use and allows you to match each USB port
input to the correct touchscreen.
ConnectedDevices - This section lists all connected devices with
manufacturer and model details where reported. Click the Details button
against each device to view further information, such as the Device Type,
Protocol Version, Speed and Max Power Consumption.
SerialPort
This page provides basic information about the serial option port located
on the RX unit.
Enabled - Conrms whether the serial port is enabled or disabled.
Connected - Conrms whether a valid serial device is connected to
the port.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
33
INDEX
Page 35

RX-Network
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Network link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 Click the Network link.
INSTALLATIONCONFIGURATIONOPERATION
PortSettings
This page provides numerous network details for each of the installed
ports on the RX unit.
Socket - Details each operational network socket and what connection
speeds they have established. Sockets 3 and 4 are determined by the SFP
modules plugged into them.
MACAddress - Displays the unique, xed hardware identication
number for each port.
LinkUp - Indicates whether the link state of this network interface is
up. This should be the case if the device is connected to a functioning
network.
IPAddress - The IP address of this network interface. This is not
congurable, the device can function in a network zero-cong state
which does not require the setting of a static IP address.
Netmask - The netmask of this network interface. This is not
congurable, the device can function in a network zero-cong state
which does not require the setting of a static netmask.
Gateway - The gateway address of this network interface. This is not
congurable, the device can function in a network zero-cong state
which does not require the setting of a static gateway.
DHCPEnabled - When ticked, the corresponding port will derive its IP
Address, Netmask and Gateway details from the DHCP server listed in
the eld below.
DHCPServerAddress - Indicates the server that provided the DHCP
details.
RoutingTable - Click on ‘Details’ to show the routing table entries
corresponding to this network interface. In it are the destination address,
gateway and netmask for the routes to particular network destinations.
NetworkInformation
DefaultDomain-Reserved for future use.
IndependentNetworks-When ticked, the ALIF4000 receiver
will treat its two main network ports as independent routes to the
transmitter(s) and not attempt to nd secondary cross connections,
which may not be possible due to the network topology. This setting will
have no effect when ALIF4000 receivers link with ALIF4000 transmitters
due to their use of auto discovery. However, when an ALIF4000 receiver
links with other dual port ALIF transmitters (such as an ALIF2002T),
enabling this option can prevent unnecessary delays due to the time
taken looking for routes that are effectively network dead ends.
RouteofLastResort - In a multi-interface device such as this, the
interface which is ticked will be used as the default whenever it is
unclear which interface should be used for network trafc.
DynamicDNSServers - List of DNS server addresses obtained via
DHCP.
StaticDNSServers - Lists DNS server addresses that have been
manually congured.
NTPEnabled - When ticked, the unit will derive its time and date
information from a suitable NTP server.
NTPKeyID - The ID of the key used for secure NTP.
NTPKeyValue - The value of the key used for secure NTP as a
hexadecimal string.
DynamicNTPServers - Lists NTP server addresses obtained via
DHCP.
StaticNTPServers - Lists NTP server addresses that have been
manually congured.
AIMEnabled - Indicates whether server management is enabled for
this device.
DynamicAIMServers - Lists AIM server addresses obtained via
DHCP.
StaticAIMServers - Lists management server addresses that have
been manually congured.
FURTHER
INFORMATION
INDEX
34
Page 36

RX-Transmitters
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 Click the Transmitters link.
Transmitters
This page lists the available transmitters on the network which aren’t
under AIM control - Note: ALIF1xxxT and ALIF2xxxT units are generally not
discoverable using this process, however, if the Start of Life process was able to
connect point-to-point to an ALIF2xxx then it will have created a ‘static’ device
entry and thus it will appear on this screen. However, the cog and light bulb
icons will not function for the entry.
In the Actions column you can perform the following functions for each
listed transmitter:
• Click to view the conguration page of the TX. When clicked, you
will be directed to the General page for the chosen TX. See page 38.
• Click to ash the front panel indicators on the transmitter to
assist with identication.
• Click the X button in the top right corner to return to return to the
RX pages.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
35
INDEX
Page 37

RX-DiagnosticsandStatistics
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Diagnostics link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 Click the Diagnostics link.
LogSettings
This page provides numerous key diagnostic log settings.
Capturediagnosticstodownload - (Only shown when viewing this
page using a PC browser). Request generation of a diagnostics dump
le. This will then be downloaded by the host computer’s browser, this
is an encrypted diagnostics le which can be used by technical support
to diagnose and x an issue. If using the local OSD, then this will show
‘Capture diagnostics to USB’ and will download the same le onto a USB
memory stick inserted into USB ports 2-5. Note: When in point to point
mode, you will need to plug in a USB ash drive and capture the logs to it.
RemoteSupport - When using the Adder remote server, this option
determines which port will be used. Multiple options are offered in case
one or more ports are blocked by your rewall.
LoggingSeverityLevel - Denes the level of messages that will be
logged (according to RFC5424). Level 5 (Notice: normal but signicant
condition) is the default setting; ALIF4000 supports levels 1 to 7. Choosing
levels 6 (Informational) or 7 (Debug) will cause larger numbers of lesser
events to also be logged, with a potential impact to overall performance.
These levels should only be used if working with the support team to
diagnose a specic issue.
RemoteLoggingEnabled - Tick to send log les to the chosen
Remote Logging Address.
RemoteLoggingAddress - Enter a valid IP address for a syslog server
on the local network where status logs can be sent.
LogFile - If viewing this page using a browser: Click to download the log
le to the host computer’s browser. If viewing this page via the OSD, the log
will be shown as a scrollable list.
PingTest - Allows you to conduct a ping test to any selected address or
device.
PerformIGMPTest - Allows you to conduct an IGMP test on connected
devices, selectable from the drop-down list.
BasicGraph
This page shows a real time graph with the following entries:
• ReceivedandTransmittedBitRates - the values of these
correspond to the bandwidth axis on the left.
• FrameRate - for both heads. Values are labeled when they change
and correspond to the axis on the right.
• Codec - for both heads. These represent the compression used: 1 is
better than 4.
• DroppedPackets - for both heads. Values are labeled when they
change and correspond to the axis on the right.
NetworkStatistics
This page allows you to view current communication statistics and also
to create graphs in real time.
CaptureandGraphStatistics - When ticked, the page will create a
real time graph plotting Received Bytes alongside Received Packets.
After Capture and Graph Statistics is enabled, the Show Legend checkbox
will show all other items that can be included on the plot. Click an item
to tick and include it.
VideoPortStatusandStatistics
This page provides wide ranging information for support purposes.
AudioPortStatusandStatistics
This page provides wide ranging information for support purposes.
USBPortStatusandStatistics
This page provides wide ranging information for support purposes.
Currently only supported for transparent USB.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
36
Page 38

RX-System
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon.
The Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the System link.
OR
1 Connect a computer to the same network as the RX unit.
2 Run a web browser and enter the IP address of the RX unit:
https://169.254.1.32 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2, then the default address will be https://169.254.1.42 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 or 1
(or IP Address 4 or 2) and use that address.
3 Click the System link.
SoftwareandSystemOperations
This page contains various indications and options related to the internal
software of the unit.
Note: The highlighted (and colored) entry is the version of software currently
running.
PreferredSoftwareVersion - The software version the device will
boot into upon a reboot.
RecoverySoftwareVersion - The software version the device will
boot into if placed into recovery mode.
AlternateSoftwareVersion - The other (backup) version of software
the device has available.
RebootDevice - Click the Reboot button to Reboot the device.
RestoreDefaultSettings - Click the Restore button to restore the
device to factory default settings.
SwitchSoftwareVersions - Click to switch to the listed ‘Alternative
Software Version’.
UpgradeDevice - If viewing this page using a browser: Allows you to
upgrade the rmware either from a trusted URL or from a locally stored
le. Use the eld to dene the source and then click the Upgrade button.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
37
INDEX
Page 39

TX-GeneralInformation
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon. The
Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters option and then click the icon for the
required transmitter.
4 If necessary, click the General link.
OR
1 Connect a computer to the same network as the TX unit.
2 Run a web browser and enter the IP address of the TX unit:
https://169.254.1.33 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2 then the default address will be https://169.254.1.43 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 (or IP
Address 4) and use that address.
3 If necessary, click the General link.
INSTALLATIONCONFIGURATIONOPERATION
GeneralInformation
Type - States whether the device is a transmitter (TX) or a receiver
(RX).
Name - Name details that you can alter to distinguish this unit from all
others. Not shown when operating under AIM server control.
Description - Allows you to optionally add a description of the device.
Useful when many ALIF units are being used. Not shown when operating
under AIM server control.
Location - Allows you to optionally add a description of the device’s
location. Useful when many ALIF units are being used. Not shown when
operating under AIM server control.
CurrentSoftwareVersion - Displays the version number of the
currently installed and running internal software (unit can have two
different software versions installed at once).
SerialNumber - Displays the xed serial number of the device.
BoardRevision - Displays the revision number of the device’s main
circuit board.
Model - Displays the model number of the device.
DateandTime - Displays the current date and time used by the device
when this page was last loaded (select refresh icon to update).
Uptime - Shows the time period for which the device has currently
being running since the last time this page was loaded (select refresh
icon to update).
IdentifyDevice - When clicked, this button will cause the indicator on
the front panel of the device to ash to assist with identication when
multiple units are installed in the same area. A popup dialog will also be
displayed on screen showing all relevant identication details. Click the
Cancel button to stop the identication process or click the OK button
to close the popup (and then click the Identify Device button when
you’re ready to cancel this operation).
AccessPassword - Sets the password that a RX device must provide in
order to connect (video, audio, etc) to the TX
InsecureConnections - Controls whether the TX will accept insecure
connections from RX devices. Insecure connections are those from
older ALIF products where the security credentials are not implemented.
Initially, the TX will default to ‘auto’ which allows it to decide the setting
based on the type of device that rst connects to it. Once a device has
connected, the setting will be changed to either ‘Allowed’ or ‘Disallowed’.
FURTHER
INFORMATION
INDEX
38
Page 40

TX-UISettings
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon. The
Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters option and then click the icon for the
required transmitter.
4 Click the UISettings link.
OR
1 Connect a computer to the same network as the TX unit.
2 Run a web browser and enter the IP address of the TX unit:
https://169.254.1.33 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2 then the default address will be https://169.254.1.43 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 (or IP
Address 4) and use that address.
3 Click the UISettings link.
UISettings
FrontPanelTimeout - Determines the period of inactivity that should
elapse before the front panel display should return to a blank state.
LEDbrightness - Determines the brightness of the front panel LED
indicator.
Language - Determines the language used for all text labels within the
conguration pages.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
39
INFORMATION
INDEX
Page 41

TX-Users
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon. The
Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters option and then click the icon for the
required transmitter.
4 Click the Users link.
OR
1 Connect a computer to the same network as the TX unit.
2 Run a web browser and enter the IP address of the TX unit:
https://169.254.1.33 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2 then the default address will be https://169.254.1.43 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 (or IP
Address 4) and use that address.
3 Click the Users link.
Useraccounts
This page allows you to change the password for the admin user.
Click the icon to display the following dialog:
INSTALLATIONCONFIGURATIONOPERATION
Enter and conrm the current and new admin password and click OK.
FURTHER
INFORMATION
INDEX
40
Page 42
TX-Ports
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon. The
Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters option and then click the icon for the
required transmitter.
4 Click the Ports link.
OR
1 Connect a computer to the same network as the TX unit.
2 Run a web browser and enter the IP address of the TX unit:
https://169.254.1.33 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2 then the default address will be https://169.254.1.43 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 (or IP
Address 4) and use that address.
3 Click the Ports link.
INSTALLATIONCONFIGURATIONOPERATION
VideoPorts
This page provides basic information about the two video ports located
on the TX unit.
Enabled - Conrms whether each video port is enabled or disabled.
Connected - Conrms whether functioning host video drivers are
connected to the two video ports.
EDIDSource - Lists the EDID mode currently being output on the
two video connectors. For more information about how video and
audio EDID data are derived, see Support for analog and digital audio.
Note: Fixed EDIDs were updated in v3.00 to add support for higher frame
rates at each xed EDID resolution. The default frame rate remains as given
in the xed EDID name (eg. 60), however, HD and higher resolutions will
include higher rates which are supported at those resolutions. eg. 240Hz for
1920x1080p60.
DynamicRange - This option is shown only when a xed EDID is
selected and allows you to determine a particular color depth and
dynamic range. When set to HDR10, the transmitter will also declare
support for the lower SDR8 and SDR10 modes. See page 4.
AttachedMonitorReceiver - If the ‘Attached monitor’ option has
been selected as the ‘EDID Source’, then this displays the name of the
RX device that supplied the EDID currently being used.
EDIDOptimisation - When ticked, and if the EDID source option is
set to ‘Attached monitor’; upon connecting with a new receiver, the
transmitter will compare the preferred video mode of the new monitor
with the current video output from the host PC. Only if they differ will
the transmitter present the new monitor’s EDID to the host PC. This
option speeds up switching as the host PCs graphics card does not
have to go through a hotplug detect routine each time a new receiver is
connected. If this setting is unticked, the transmitter will always present a
new EDID to the host PC.
BackgroundRefresh(frames) - The system will send all changing
video as soon as it changes. In addition, it is possible to send unchanging
video in the background, to overcome problems of lost network trafc.
This control will congure how often a whole frame of video will be
sent alongside changing video. In situations of frequently changing video,
or high reliability networks, this value can be set to a higher number, or
even set to disabled.
CompressionType - Allows you to select the compression method
to best suit the nature of the video sources. Settings are: Pixel Perfect,
Adaptive, Smoothest Video or Advanced (which allows you to set the
maximum and minimum compression levels).
FrameSkipping - Frame Skipping involves ‘missing out’ video frames
between those captured by the TX unit. For video sources that update
only infrequently or for those that update very frequently but where high
delity is not required, frame skipping is a good strategy for reducing the
overall bandwidth consumed by the system. Range: 0 to 100%.
MagicEye - When ticked, this feature increases performance and
reduces network trafc if ALIF units are used with host computers that
have dithered video output. It also improves performance if the video
source is noisy.
MaxBitsperColour - Allows you to choose the maximum color bit
depth that is passed through from the host computer to the ALIF4000
receivers and their connected video display(s). The options are 8-bits
per colour (Standard Dynamic Range) or 10-bits per colour to support
newer video displays that support the SDR10 and HDR10 (High
Dynamic Range) standards. When set to 8, an incoming 10-bpc signal will
be converted down to 8-bpc before being transmitted, most commonly
used to ensure that all ALIF receivers are able to receive the video
output. When set to 10, incoming 10-bpc will pass through unchanged, as
will 8-bpc. See page 4.
MulticastAddresses - This section lists all video multicast IP addresses
that have been congured. Setting the eld to a blank (empty string)
value will cause the system to automatically generate a default multicast
address.
FURTHER
INFORMATION
INDEX
continued
41
Page 43

TX-Ports(continued)
AudioPorts
This page provides basic information about the audio ports located on
the TX unit.
Enabled - Conrms whether the audio ports are enabled or disabled.
Connected - Conrms whether devices are connected to respective
ports.
EDIDSource - Lists the EDID audio mode currently being output on
the digital audio components of the two video connectors. For more
information about how video and audio EDID data are derived, see
Support for analog and digital audio.
AttachedMonitorReceiver - If the ‘Attached monitor’ option has
been selected as the ‘EDID Source’, then this displays the name of the
RX device that supplied the EDID currently being used.
EDIDOptimisation - When ticked, and if the EDID source option is set
to ‘Attached monitor’; upon switching to a new receiver, the transmitter
will compare the preferred audio mode of the new monitor/audio
subsystem with the current video output from the host PC. Only if they
differ will the transmitter present the new audio EDID to the host PC.
This option speeds up switching as the host PC does not have to go
through a hotplug detect routine each time a new receiver is connected.
If this setting is unticked, the transmitter will always present a new EDID
to the host PC.
For audio there is also an extra check. Because the audio stream may not
always be active (whereas video always is); if there is currently no audio
stream being output by the PC, the transmitter will compare the audio
capabilities of the current EDID with the new EDID. If the new EDID’s
capabilities are a subset of the current EDID’s, the existing one will be
changed for the new one. For example, if the current EDID supports
8 channel audio and the new only supports 6, the new will be selected
to ensure the host PC doesn’t attempt to output 8 channel audio to a
device that can’t handle it.
QualityMode - Analog audio only. This option is currently xed at
48khz, 16bit.
MulticastAddresses - This section lists all audio multicast IP addresses
that have been congured. Setting the eld to a blank (empty string)
value will cause the system to automatically generate a default multicast
address.
USBPorts
This page provides basic information about the USB ports located on the
TX unit.
Type - Identies the type of the USB port.
Enabled - Conrms whether the USB ports are enabled or disabled.
Connected - Conrms whether valid devices are connected to either
USB port. Note: As both USB ports share the same physical port, it is not
possible to detect whether a specic port has a device connected.
RateLimit - This option allows you to place an upper limit on the
bandwidth that can be consumed by the transparent USB subsystem
as a whole. This can be useful in situations where the overall network
bandwidth is quite low and high resolution video performance is being
impacted by USB operation; particularly during large le transfers to or
from a mass storage device inserted into the ALIF receiver. Using this
option you can choose an appropriate USB bandwidth rate limit between
1 and 480Mbps.
PresentBootKeyboard - When ticked, the TX unit will report a
virtual dummy boot keyboard to the attached PC to ensure that a
keyboard is always reported when the PC boots up. The dummy boot
keyboard uses one of the 13 USB endpoints, therefore if all 13 endpoints
are required elsewhere for USB devices (or a KVM switch only supports
two HID devices) then it can be disabled by deselecting this option.
MaxHubSize - Using this option you can select whether the TX unit
should report itself as a 13 or a 7 port USB hub. Some USB hosts are
only able to support 7 port USB hubs. If this option is set to 7, then only
7 USB devices are supported by the PC.
Security - Controls whether USB data is encrypted. On forces always
on, Off forces always off and Prefer off will be off unless the RX requests
it.
SerialPort
This page provides basic information about the serial option port located
on the TX unit. These options are congurable via the AIM server.
Enabled - Conrms whether the serial port is enabled or disabled.
Connected - Conrms whether a valid serial device is connected to
the port.
Speed - The ‘baud rate’ of the serial device.
DataBits - The number of data bits to be used (5, 6, 7, or 8).
StopBits - The number of stop bits to be used (1 or 2).
Parity - The parity checking to be used (none, odd or even).
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
42
INDEX
Page 44

TX-Network
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon. The
Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters option and then click the icon for the
required transmitter.
4 Click the Network link.
OR
1 Connect a computer to the same network as the TX unit.
2 Run a web browser and enter the IP address of the TX unit:
https://169.254.1.33 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2 then the default address will be https://169.254.1.43 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 (or IP
Address 4) and use that address.
3 Click the Network link.
PortSettings
This page provides numerous network details for each of the installed
ports on the TX unit.
Socket - Details each operational network socket. Sockets 3 and 4 are
determined by the SFP modules plugged into them.
MACAddress - Displays the unique, xed hardware identication
number for each port.
LinkUp - Indicates whether the link state of this network interface is
up. This should be the case if the device is connected to a functioning
network.
IPAddress - The IP address of this network interface. This is not
congurable, the device can function in a network zero-cong state
which does not require the setting of a static IP address.
Netmask - The netmask of this network interface. This is not
congurable, the device can function in a network zero-cong state
which does not require the setting of a static netmask.
Gateway - The gateway address of this network interface. This is not
congurable, the device can function in a network zero-cong state
which does not require the setting of a static gateway.
DHCPEnabled - When ticked, the corresponding port will derive its IP
Address, Netmask and Gateway details from the DHCP server listed in
the eld below.
DHCPServerAddress - Indicates the server that provided the DHCP
details.
BandwidthLimit - This option can be used to set an upper limit
(between 500 and 10000 Mbps aka 10Gbps) to the amount of the
network bandwidth used on the physical interface. This could be useful if
multiple devices share a common network link upstream; without a limit,
the link could become overloaded and drop data.
RoutingTable - Click on ‘Details’ to show the routing table entries
corresponding to this network interface. In it are the destination address,
gateway and netmask for the routes to particular network destinations:
NetworkSettings
DefaultDomain - Reserved for future use.
RouteofLastResort - In a multi interface device such as this, the
interface which is ticked will be used as the default whenever it is
unclear which interface should be used for network trafc.
DynamicDNSServers - List of DNS server addresses obtained via
DHCP.
StaticDNSServers - Lists DNS server addresses that have been
manually congured.
NTPEnabled - When ticked, the unit will derive its time and date
information from a suitable NTP server.
NTPKeyID - The ID of the key used for secure NTP.
NTPKeyValue - The value of the key used for secure NTP as a
hexadecimal string.
DynamicNTPServers - Lists NTP server addresses obtained via
DHCP.
StaticNTPServers - Lists NTP server addresses that have been
manually congured.
AIMEnabled - Indicates whether server management is enabled for
this device.
DynamicAIMServers - Lists AIM server addresses obtained via
DHCP.
StaticAIMServers - Lists management server addresses that have
been manually congured.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
43
Page 45

TX-DiagnosticsandStatistics
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon. The
Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters option and then click the icon for the
required transmitter.
4 Click the Diagnostics link.
OR
1 Connect a computer to the same network as the TX unit.
2 Run a web browser and enter the IP address of the TX unit:
https://169.254.1.33 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2 then the default address will be https://169.254.1.43 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 (or IP
Address 4) and use that address.
3 Click the Diagnostics link.
INSTALLATIONCONFIGURATIONOPERATION
LogSettings
This page provides numerous key diagnostic log settings.
Capturediagnosticstodownload - (Only shown when viewing this
page using a PC browser). Request generation of a diagnostics dump le.
This will then be downloaded by the host computer’s browser, this is
an encrypted diagnostics le which can be used by technical support to
diagnose and x an issue.
RemoteSupport - When using the Adder remote server, this option
determines which port will be used. Multiple options are offered in case
one or more ports are blocked by your rewall. When the Enable button
is clicked, it will indicate the password to be used.
LoggingSeverityLevel - Denes the level of messages that will be
logged (according to RFC5424). Level 5 (Notice: normal but signicant
condition) is the default setting; ALIF4000 supports levels 1 to 7. Choosing
levels 6 (Informational) or 7 (Debug) will cause larger numbers of lesser
events to also be logged, with a potential impact to overall performance.
These levels should only be used if working with the support team to
diagnose a specic issue.
RemoteLoggingEnabled - Tick to send log les to the chosen
Remote Logging Address.
RemoteLoggingAddress - Enter a valid IP address for a syslog server
on the local network where status logs can be sent.
LogFile - If viewing this page using a browser: Click to download the log
le to the host computer’s browser. If viewing this page via the OSD, the log
will be shown as a scrollable list.
PingTest - Provides a quick and easy way to check the link status to an
ALIF RX. You can specify either an IP address or choose the device from a list.
Click the Start button to begin; a summary of the results will be displayed.
BasicGraph
This page shows a real time graph with the following entries:
• Receivedandtransmittedbitrates - the values of these
correspond to the bandwidth axis on the left.
• Framerate - for both heads. Values are labeled when they change and
correspond to the axis on the right.
• Codec - for both heads. These represent the compression used: 1 is
better than 4.
• Droppedpackets - for both heads. Values are labeled when they
change and correspond to the axis on the right.
NetworkStatistics
This page allows you to view current communication statistics and also
to create graphs in real time.
CaptureandGraphStatistics - When ticked, the page will create a
real time graph plotting Received Bytes alongside Received Packets.
After Capture and Graph Statistics is enabled, the Show Legend checkbox
will show all other items that can be included on the plot. Click an item
to tick and include it.
VideoPortStatusandStatistics
This page provides wide ranging information for support purposes.
AudioPortStatusandStatistics
This page provides wide ranging information for support purposes.
USBPortStatusandStatistics
This page provides wide ranging information for support purposes.
Currently only supported for transparent USB.
FURTHER
INFORMATION
INDEX
44
Page 46
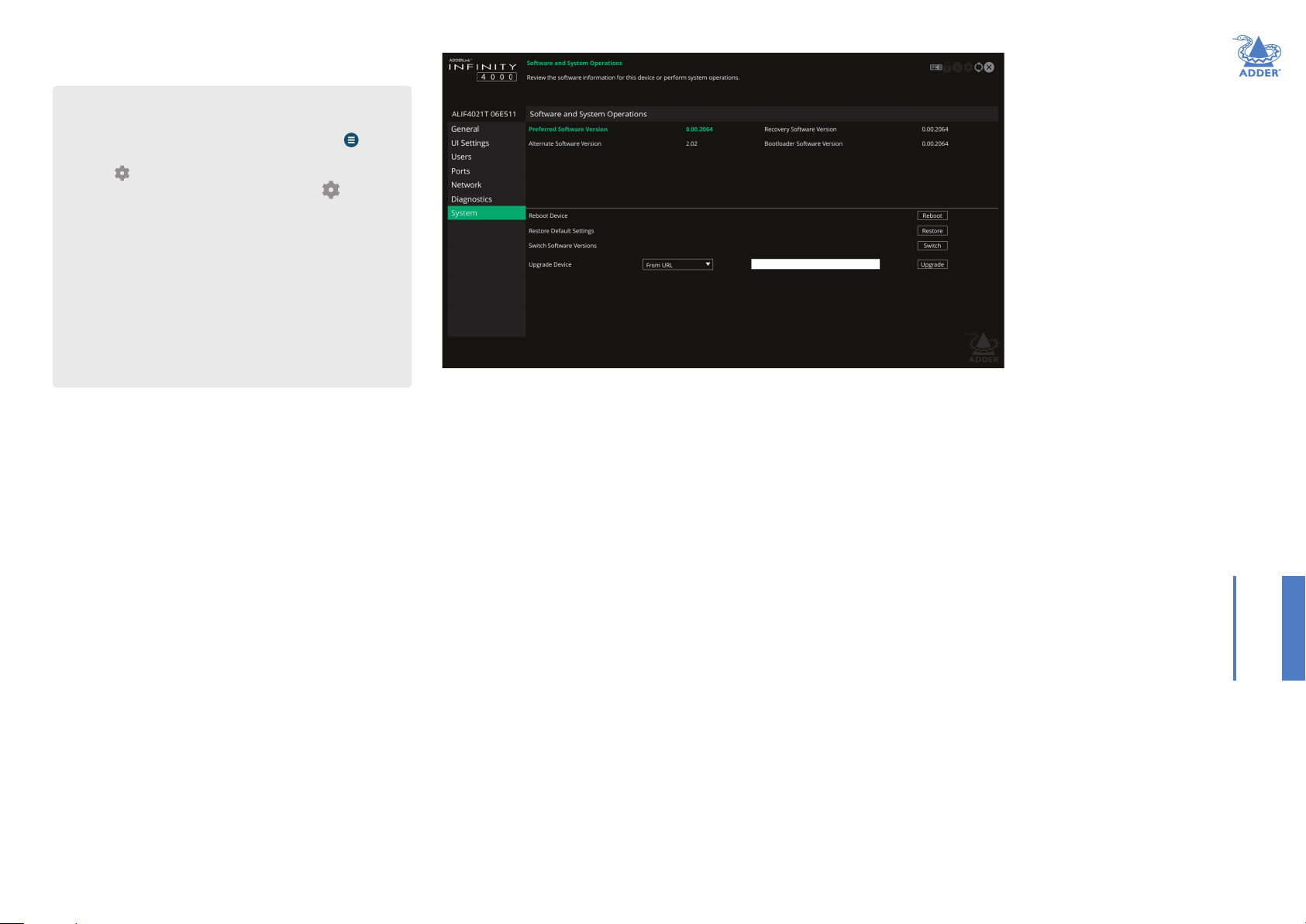
TX-System
Togethere
You can access this page in two ways:
1 On the console keyboard attached to the RX unit, access the OSD
by pressing CTRL+ALT+C or tap the touchscreen icon. The
Preset Selection page will be displayed.
2 Click the icon in the top right corner.
3 Click the Transmitters option and then click the icon for the
required transmitter.
4 Click the System link.
OR
1 Connect a computer to the same network as the TX unit.
2 Run a web browser and enter the IP address of the TX unit:
https://169.254.1.33 (this is the default address when using SFP
port 3 or RJ45 port 1). If you are using SFP port 4 or RJ45 port
2 then the default address will be https://169.254.1.43 If the
IP address is unknown, press the small button on the front panel
next to the OLED screen to reveal the value for IP Address 3 (or IP
Address 4) and use that address.
3 Click the System link.
SoftwareandSystemOperations
This page contains various indications and options related to the internal
software of the unit.
Note: The highlighted (and colored) entry is the version of software currently
running.
PreferredSoftwareVersion - The software version the device will
boot into upon a reboot.
RecoverySoftwareVersion - The software version the device will
boot into if placed into recovery mode.
AlternateSoftwareVersion - The other (backup) version of software
the device has available.
RebootDevice - Click the Reboot button to Reboot the device.
RestoreDefaultSettings - Click the Restore button to restore the
device to factory default settings.
SwitchSoftwareVersions - Click to switch to the listed ‘Alternative
Software Version’.
UpgradeDevice - Allows you to upgrade the rmware either from
a trusted URL or from a locally stored le. Use the eld to dene the
source and then click the Upgrade button.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
45
INDEX
Page 47
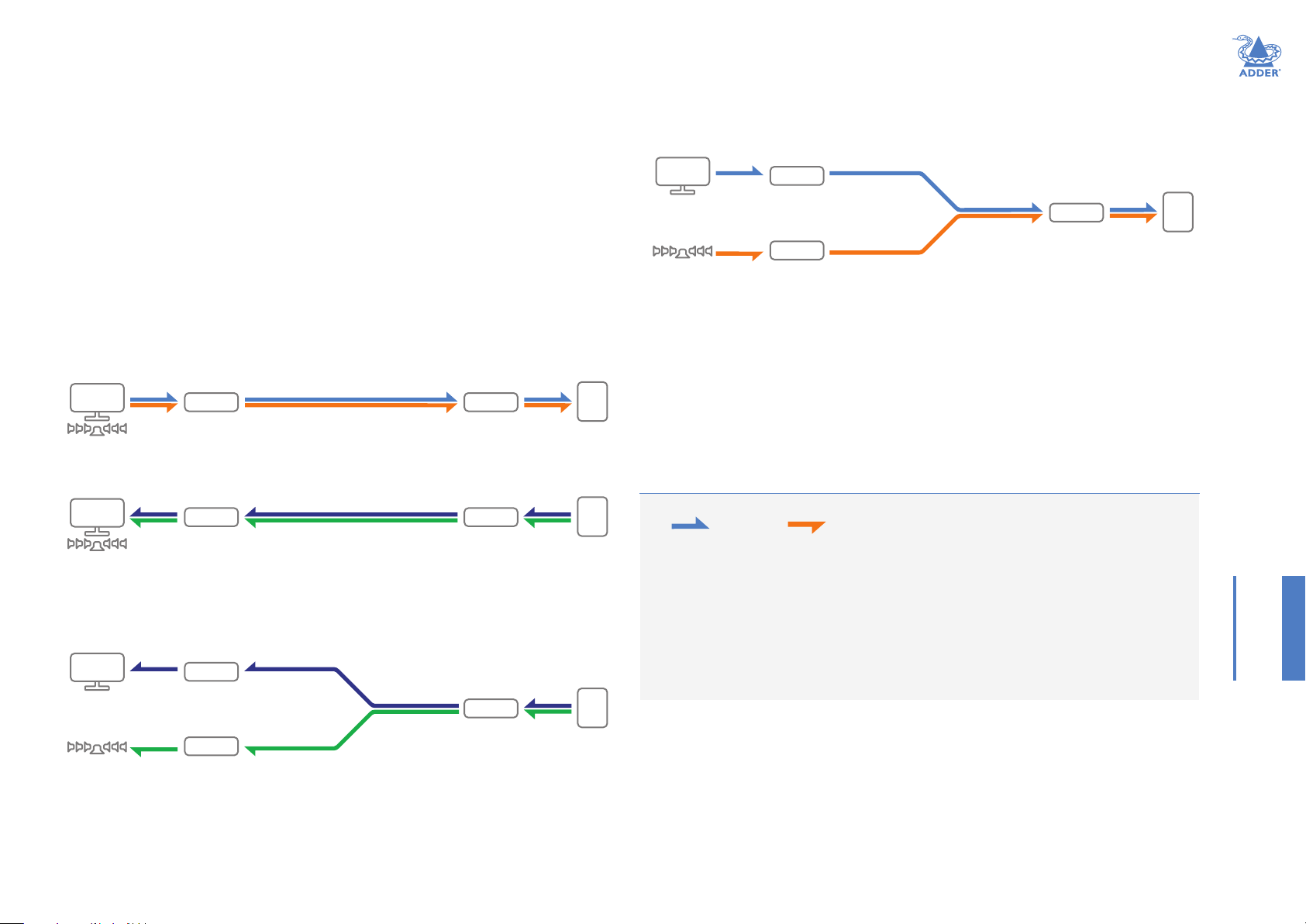
APPENDIXB-Supportforanaloganddigitalaudio
The ALIF4000 benets from two different streams of audio signals:
• Analogaudio - as would be output directly from the host PCs jack socket,
• Digitalaudio - as derived from the Host PC’s DisplayPort video connection.
Even though the analog and digital outputs from a particular host PC might be carrying
signals that originated from the same audio source, the two types are handled completely
separately throughout the ALIF system and can never be mixed.
While standard analog audio will be limited to stereo only; digital audio offers the ability
to send stereo or alternatively, surround sound in either the 5.1 or 7.1 varieties. In
order for the host PC to know which variety of digital audio signal to send out, a valid
denition of the requirement must be sent to the host PC. This is done as an audio
sub-set of the EDID denition that is used to declare the video display capabilities/
requirements.
In the diagram below the display and speaker installation send their video and digital
audio portions of the EDID (Extended Display Identication Data) denition via the
ALIF4000 receiver and transmitter to the host PC:
Display &
Speakers
RX TX
Video EDID
Audio EDID
PC
This presents an issue for the host PC and its ALIF4000 transmitter as they must now
respond to separate EDID denitions from the video display on one receiver (which will
probably also have its own EDID audio sub-set) and the EDID denition from the digital
audio device on the other receiver:
Display
RX
RX
Video EDID
Audio EDID
TX
PC
To solve potential conicts, the ALIF4000 transmitter uses a set of rules to determine
how it mixes different EDID denitions. Firstly, for any connected video or digital audio
devices, the ALIF system can consider each one using any of three selectable states:
• Attached - ALIF will interrogate the attached video/audio device to ascertain its exact
capabilities/requirements.
• Fixed - ALIF will use a xed denition (e.g 3840x2160p60 and 6-channel audio) to
represent the video/audio device(s).
• None - No representation will be made for the device.
INSTALLATIONCONFIGURATIONOPERATION
In response, the host PC begins sending video and audio signals that are appropriate for
the receiving peripherals:
Display &
Speakers
RX TX
Video
Digital audio
PC
In the above case, the video and digital audio from the host PC are both sent to the same
receiver. However, the exibility of the ALIF system is such that peripherals and hosts can
be mixed as required. For instance, the video feed could be sent to one receiver, while
the digital audio is used by a set of speakers on a different receiver:
Display
RX
RX
Video
Digital audio
TX
PC
The above states are then combined by the ALIF4000 transmitter, as connections are
made to the different devices, using the following rules:
VideoEDID AudioEDID Action (taken by the TX as it feeds info to the PC)
Fixed Fixed Merge the video and audio EDID denitions.
Fixed/Attached None Send video EDID denition only.
Attached Attached Use whichever EDID denition is available rst.
Attached/Fixed Fixed/Attached Wait for the Attached device to declare and then
use its data to modify those of the Fixed device.
Note: The video EDID retains precedence for setting
general items, such as serial no., manufacturer, etc.
Note: The analog audio is switched entirely separately to the digital audio feed.
Analoganddigitalaudiospecications
• Analogaudio: Line in/out - 2 channel 16bit 48KHz 1V RMS in / 1V RMS out
• Digitalaudio(DisplayPort):
Up to 8 audio channels,
Seven choices of sampling frequencies: 32, 44.1, 48, 88.2, 96, 176.4 or 192kHz.
Three choices of bit depth, using LPCM Linear Pulse Code Modulation: 16, 20 or 24bit,
FURTHER
INFORMATION
INDEX
46
Page 48

APPENDIXC-TipsforsuccesswhennetworkingALIFunits
ALIF units use multiple strategies to minimize the amount of data that they send
across networks. However, data overheads can be quite high, particularly when very
high resolution video is being transferred, so it is important to take steps to maximize
network efciency and help minimize data output. The tips given in this section have been
proven to produce very benecial results.
Summaryofsteps
• Choose the right kind of switch.
• Create an efcient network layout.
• Congure the switches and devices correctly.
Choosingtherightswitch
Layer 2 switches are what bind all of the hosts together in the subnet. However, they are
all not created equally, so choose carefully. In particular look for the following:
• 10Gigabit ports,
• Support for IGMP v2 (or v3) snooping,
• Support for Jumbo frames up to 9216-byte size,
• High bandwidth connections between switches, preferably Fiber Channel.
• Look for switches that perform their most onerous tasks (e.g. IGMP snooping) using
multiple dedicated processors (ASICS).
• Ensure the maximum number of concurrent ‘snoopable groups’ the switch can
handle meets or exceeds the number of ALIF transmitters that will be used to create
multicast groups.
• Check the throughput of the switch: Full duplex, 10Gbps up- and down- stream speeds
per port.
• Use the same switch make and model throughout a single subnet.
• You also need a Layer 3 switch. Ensure that it can operate efciently as an IGMP
Querier.
Creatinganefcientnetworklayout
Network layout is vital. The use of IGMP snooping also introduces certain constraints, so
take heed:
• Keep it at. Use a basic line-cascade structure rather than a pyramid or tree
arrangement.
• Keep the distances between the switches as short as possible.
• Ensure sufcient bandwidth between switches to eliminate bottlenecks.
• Where the AIM server is used to administer multiple ALIF transceivers, ensure the AIM
server and all ALIF units reside in the same subnet.
• Do not use VGA to DisplayPort converters, instead replace VGA video cards in older
systems with suitable DisplayPort replacements. Converters cause ALIF TX units to
massively increase data output.
• Wherever possible, create a private network.
Therecommendedlayout
The layout shown below has been found to provide the most efcient network layout for
rapid throughput when using IGMP snooping:
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
• Use no more than two cascade levels.
• Ensure high bandwidth between the two L2 switches and very high bandwidth between
the top L2 and the L3. Typically 10GB and 20GB, respectively for 48 port L2 switches.
continued
INDEX
47
Page 49

Conguringtheswitchesanddevices
The layout is vital but so too is the conguration:
• Enable IGMP Snooping on all L2 switches.
• Ensure that IGMP Fast-Leave is enabled on all switches with ALIF units connected
directly to them.
• Enable the L3 switch as an IGMP Querier.
• Enable Spanning Tree Protocol (STP) on all switches and importantly also enable
portfast (only) on all switch ports that have ALIF units connected.
• If any hosts will use any video resolutions using 2048 horizontal pixels (e.g. 2048 x
1152, 2048 x 2048), ensure that Jumbo Frames are enabled on all switches.
• Choose an appropriate forwarding mode on all switches. Use Cut-through if available,
otherwise Store and forward.
• Optimize the settings on the ALIF transmitters:
• If moving video images are being shown frequently, then leave Frame Skipping at a
low percentage and instead reduce the Peak bandwidth limiter.
• Where screens are quite static, try increasing the Background Refresh interval and/
or increasing the Frame skipping percentage setting.
Make changes to the ALIF transmitters one at a time, in small steps, and view typical
video images so that you can attribute positive or negative results to the appropriate
control.
• Ensure that all ALIF units are fully updated to the latest rmware version (at least v2.1).
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
48
INFORMATION
INDEX
Page 50

APPENDIXD-Troubleshooting
Problem:ThevideoimageoftheALIFreceivershowshorizontallinesacross
thescreen.
This issue is known as Blinding because the resulting video image looks as though you’re
viewing it through a venetian blind.
When video is transmitted by ALIF units, the various lines of each screen are divided up
and transmitted as separate data packets. If the reception of those packets is disturbed,
then blinding is caused. The lines are displayed in place of the missing video data packets.
There are several possible causes for the loss of data packets:
• Incorrect switch conguration. The problem could be caused by multicast ooding,
which causes unnecessary network trafc. This is what IGMP snooping is designed to
combat, however, there can be numerous causes of the ooding.
• Speed/memory bandwidth issues within one or more switches. The speed and
capabilities of different switch models varies greatly. If a switch cannot maintain pace
with the quantity of data being sent through it, then it will inevitably start dropping
packets.
• One or more ALIF units may be outputting Jumbo frames due to the video resolution
(2048 horizontal pixels) being used. If Jumbo frames are output by an ALIF unit, but
the network switches have not been congured to use jumbo frames, the switches
will attempt to break the large packets down into standard packets. This process
introduces a certain latency and could be a cause for dropped packets.
• One or more ALIF units may be using an old rmware version. Firmware versions
prior to v2.1 exhibited an issue with the timing of IGMP join and leave commands that
caused multicast ooding in certain congurations.
Remedies:
• Ensure that IGMP snooping is enabled on all switches within the subnet.
• Where each ALIF unit is connected as the sole device on a port connection to
a switch, enable IGMP Fast-Leave (aka Immediate Leave) to reduce unnecessary
processing on each switch.
• Check the video resolution(s) being fed into the ALIF transmitters. If resolutions using
2048 horizontal pixels are unavoidable then ensure that Jumbo frames are enabled on
all switches.
• Check the forwarding mode on the switches. If Store and forward is being used, try
selecting Cut-through as this mode causes reduced latency on lesser switch designs.
• Ensure that one device within the subnet is correctly congured as an IGMP Querier,
usually a layer 3 switch or multicast router.
• Ensure that the rmware in every ALIF unit is version 2.1 or greater.
• Try adjusting the transmitter settings on each ALIF to make the output data stream as
efcient as possible. See ALIF transmitter video settings for details.
continued
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
49
INFORMATION
INDEX
Page 51

Problem:TheaudiooutputoftheALIFreceiversoundslikeascratchedrecord.
This issue is called Audio crackle and is a symptom of the same problem that produces
blinding (see previous page). The issue is related to missing data packets.
Remedies:
As per blinding discussed previously.
Problem:AIMcannotlocateworkingALIFunits.
There are a few possible causes:
• The ALIF units must be reset back to their zero cong IP addresses for AIM discovery.
If you have a working network of ALIF’s without AIM and then add AIM to the network,
AIM will not discover the ALIFs until they are reset to the zero cong IP addresses.
• This could be caused by Layer 2 Cisco switches that have Spanning Tree Protocol
(STP) enabled but do not also have portfast enabled on the ports to which ALIF units
are connected. Without portfast enabled, ALIF units will all be assigned the same zero
cong IP address at reboot and AIM will only acquire them one at a time on a random
basis.
You can easily tell whether portfast is enabled on a switch that is running STP: When
you plug the link cable from a working ALIF unit into the switch port, check how long
it takes for the port indicator to change from orange to green. If it takes roughly one
second, portfast is on; if it takes roughly thirty seconds then portfast is disabled.
Remedies:
• Ensure that the ALIF units and the AIM server are located within the same subnet
because AIM cannot cross subnet boundaries.
• Manually reset the ALIF units to their zero cong IP addresses.
• Enable portfast on all switch ports that have ALIF units attached to them or try
temporarily disabling STP on the switches while AIM is attempting to locate ALIF units.
Problem:VideoperformanceisaffectedwhenusingUSBstorage.
This issue could be related to a relatively slow link connection speed being affected by
high bandwidth data transfers to a USB storage device.
Remedies:
Try placing a limit on the bandwidth being used by the transparent USB ports. Via the
OSD, link to the TX - Ports page, change to the USB Ports section and adjust the Rate
Limit option.
Problem:Followingarmwareupgradeto4.xx,theALIF4000unitsstillcannotsupportSDR10orHDR10videosignals.
When an ALIF4000 unit is upgraded, it may not support the new 10-bits per colour
modes if manual changes had previously been made to the video conguration. This could
mean that the Max Bits per Colour setting may remain set to 8-bits, causing the unit to
not support SDR10 and HDR10 signals.
Remedies:
Access the TX Ports conguration page and change the Max Bits per Colour setting to
‘10’. See page 41.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
50
INFORMATION
INDEX
Page 52

APPENDIXE-Glossary
InternetGroupManagementProtocol
Where an ALIF transmitter is required to stream video to
two or more receivers, multicasting is the method used.
Multicasting involves the delivery of identical data to
multiple receivers simultaneously without the need to
maintain individual links. When multicast data packets enter
a subnet, the natural reaction of the switches that bind
all the hosts together within the subnet, is to spread the
multicast data to all of their ports. This is referred to as
Multicast ooding and means that the hosts (or at least
their network interfaces) are required to process plenty of
data that they didn’t request. IGMP offers a partial solution.
The Internet Group Management Protocol (IGMP) is
designed to prevent multicast ooding by allowing Layer
3 switches to check whether host computers within
their care are interested in receiving particular multicast
transmissions. They can then direct multicast data only to
those points that require it and can shut off a multicast
stream if the subnet has no recipients.
There are currently three IGMP versions: 1, 2 and 3, with
each version building upon the capabilities of the previous
one:
• IGMPv1 allows host computers to opt into a multicast
transmission using a Join Group message, it is then
incumbent on the router to discover when they no
longer wish to receive; this is achieved by polling them
(see IGMP Querier below) until they no longer respond.
• IGMPv2 includes the means for hosts to opt out as well
as in, using a Leave Group message.
• IGMPv3 encompasses the abilities of versions 1 and 2
but also adds the ability for hosts to specify particular
sources of multicast data.
ADDERLink™ INFINITY units make use of IGMPv2 when
performing multicasts to ensure that no unnecessary
congestion is caused.
IGMPSnooping
The IGMP messages are effective but only operate at
layer 2 - intended for routers to determine whether
multicast data should enter a subnet. A relatively recent
development has taken place within the switches that
glue together all of the hosts within each subnet: IGMP
Snooping. IGMP snooping means these layer 2 devices now
have the ability to take a peek at the IGMP messages. As
a result, the switches can then determine exactly which of
their own hosts have requested to receive a multicast –
and only pass on multicast data to those hosts.
IGMPQuerier
When IGMP is used, each subnet requires one Layer 3
switch to act as a Querier. In this lead role, the switch
periodically sends out IGMP Query messages and in
response all hosts report which multicast streams they
wish to receive. The Querier device and all snooping Layer
2 switches then update their lists accordingly (the lists are
also updated when Join Group and Leave Group (IGMPv2)
messages are received).
IGMPFast-Leave(akaImmediateLeave)
When a device/host no longer wishes to receive a
multicast transmission, it can issue an IGMP Leave Group
message as mentioned above. This causes the switch to
issue an IGMP Group-Specic Query message on the port
(that the Leave Group was received on) to check no other
receivers exist on that connection that wish to remain a
part of the multicast. This process has a cost in terms of
switch processor activity and time.
Where ALIF units are connected directly to the switch
(with no other devices on the same port) then enabling
IGMP Fast-Leave mode means that switches can
immediately remove receivers without going through
a full checking procedure. Where multiple units are
regularly joining and leaving multicasts, this can speed up
performance considerably.
Jumboframes(Jumbopackets)
Since its commercial introduction in 1980, the Ethernet
standard has been successfully extended and adapted to
keep pace with the ever improving capabilities of computer
systems. The achievable data rates, for instance, have risen
in ten-fold leaps from the original 10Mbit/s to a current
maximum of 100Gbit/s.
While data speeds have increased massively, the standard
dening the number of bytes (known as the Payload)
placed into each data packet has remained resolutely stuck
at its original level of 1500 bytes. This standard was set
during the original speed era (10Mbits/s) and offered the
best compromise at that speed between the time taken to
process each packet and the time required to resend faulty
packets due to transmission errors.
But now networks are much faster and les/data streams
are much larger; so time for a change? Unfortunately, a
wholesale change to the packet size is not straightforward
as it is a fundamental standard and changing it would mean
a loss of backward compatibility with older systems.
Larger payload options have been around for a while,
however, they have often been vendor specic and at
present they remain outside the ofcial standard. There
is, however, increased consensus on an optional ‘Jumbo’
payload size of 9000 bytes and this is fully supported by
the ADDERLink™ INFINITY (ALIF) units.
Jumbo frames (or Jumbo packets) offer advantages for
ALIF units when transmitting certain high resolution video
signals across a network. This is because the increased data
in each packet reduces the number of packets that need to
be transferred and dealt with - thus reducing latency times.
The main problem is that for jumbo frames to be possible
on a network, all of the devices on the network must
support them.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
51
Page 53

SpanningTreeProtocol(STP)
In order to build a robust network, it is necessary
to include certain levels of redundancy within the
interconnections between switches. This will help to
ensure that a failure of one link does not lead to a
complete failure of the whole network.
The danger of multiple links is that data packets, especially
multicast packets, become involved in continual loops as
neighbouring switches use the duplicated links to send and
resend them to each other.
To prevent such bridging loops from occurring, the
Spanning Tree Protocol (STP), operating at layer 2, is
used within each switch. STP encourages all switches
to communicate and learn about each other. It prevents
bridging loops by blocking newly discovered links until it
can discover the nature of the link: is it a new host or a
new switch?
The problem with this is that the discovery process can
take up to 50 seconds before the block is lifted, causing
problematic timeouts.
The answer to this issue is to enable the portfast variable
for all host links on a switch. This will cause any new
connection to go immediately into forwarding mode.
However, take particular care not to enable portfast on
any switch to switch connections as this will result in
bridging loops.
Forwardingmodes
In essence, the job of a layer 2 switch is to transfer as
fast as possible, data packets arriving at one port out to
another port as determined by the destination address.
This is known as data forwarding and most switches offer
a choice of methods to achieve this. Choosing the most
appropriate forwarding method can often have a sizeable
impact on the overall speed of switching:
• Storeandforward is the original method and requires
the switch to save each entire data packet to buffer
memory, run an error check and then forward if no
error is found (or otherwise discard it).
• Cut-through was developed to address the latency
issues suffered by some store and forward switches.
The switch begins interpreting each data packet as it
arrives. Once the initial addressing information has been
read, the switch immediately begins forwarding the
data packet while the remainder is still arriving. Once
all of the packet has been received, an error check is
performed and, if necessary, the packet is tagged as
being in error. This checking ‘on-the-y’ means that
cut-through switches cannot discard faulty packets
themselves. However, on receipt of the marked packet, a
host will carry out the discard process.
• Fragment-free is a hybrid of the above two methods.
It waits until the rst 64 bits have been received before
beginning to forward each data packet. This way the
switch is more likely to locate and discard faulty packets
that are fragmented due to collisions with other data
packets.
• Adaptive switches automatically choose between the
above methods. Usually they start out as a cut-through
switches and change to store and forward or fragment-
free methods if large number of errors or collisions are
detected.
So which one to choose? The Cut-through method has
the least latency so is usually the best to use with
ADDERLink™ INFINITY units. However, if the network
components and/or cabling generate a lot of errors, the
Store and forward method should probably be used. On
higher end store and forward switches, latency is rarely an
issue.
Layer2andLayer3:TheOSImodel
When discussing network switches, the terms Layer 2 and
Layer 3 are very often used. These refer to parts of the
Open System Interconnection (OSI) model, a standardized
way to categorize the necessary functions of any standard
network.
There are seven layers in the OSI model and these dene
the steps needed to get the data created by you (imagine
that you are Layer 8) reliably down onto the transmission
medium (the cable, optical ber, radio wave, etc.) that
carries the data to another user; to complete the picture,
consider the transmission medium is Layer 0. In general,
think of the functions carried out by the layers at the top
as being complex, becoming less complex as you go lower
down.
As your data travel down from you towards the
transmission medium (the cable), they are successively
encapsulated at each layer within a new wrapper (along
with a few instructions), ready for transport. Once
transmission has been made to the intended destination,
the reverse occurs: Each wrapper is stripped away and the
instructions examined until nally only the original data are
left.
So why are Layer 2 and Layer 3 of particular importance
when discussing ADDERLink™ INFINITY? Because the
successful transmission of data relies upon fast and reliable
passage through network switches – and most of these
operate at either Layer 2 or Layer 3.
The job of any network switch is to receive each incoming
network packet, strip away only the rst few wrappers to
discover the intended destination then rewrap the packet
and send it in the correct direction.
continued
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
52
Page 54

In simplied terms, the wrapper that is added at Layer 2
(by the sending system) includes the physical address of
the intended recipient system, i.e. the unique MAC address
(for example, 09:f8:33:d7:66:12) that is assigned to every
networking device at manufacture. Deciphering recipients
at this level is more straightforward than at Layer 3, where
the address of the recipient is represented by a logical IP
address (e.g. 192.168.0.10) and requires greater knowledge
of the surrounding network structure. Due to their more
complex circuitry, Layer 3 switches are more expensive
than Layer 2 switches of a similar build quality and are
used more sparingly within installations.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
53
INFORMATION
INDEX
Page 55

APPENDIXF-Nullmodemcablepinout
RS232‘null-modem’cablepin-out
9pinD-type
female
9pinD-type
female
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
54
INFORMATION
INDEX
Page 56

APPENDIXG-Fiber/coppermodulesandcables
To suit your installation layout, ber and copper modules are available for the ALIF4000 units to
support various ber optic and CATx cables. The specications for all are summarized in this table:
Name Fibersize Type Coding Distance
at
OM1 (62.5/125) Multimode
(TIA-492AAAA)
OM2 (50/125) Multimode
(TIA-492AAAB)
OM3 (50/125) Multimode
(850 nm Laser-optimized)
(TIA-492AAAC)
OM4 (50/125) Multimode
(850 nm Laser-optimized)
(TIA-492AAAC)
OS1 and OS2 (9/125) Single-mode
(TIA-492C000 / TIA-492E000)
Normal
applications
Orange 62.5/125 2-26m SFP-MM-LC-10G
Orange 50/125 2-26m “
Aqua 850 LO 50 /125 2-82m “
Aqua 850 LO 50 /125 2-300m “
Yellow SM/NZDS, SM 10Km SFP-SM-LC-10G
Suggestedprint
nomenclature
10Gbps
Adderpart
numberforSFP
module
INSTALLATIONCONFIGURATIONOPERATION
CAT x n/a Multi-rate
CAT5e and above
n/a n/a See below SFP-CATX-MR
Speed Cabletype Distance
10GbE CAT 6 30m
100MbE to 5GbE CAT 5e and above 100m
FURTHER
INFORMATION
INDEX
55
Page 57

APPENDIXH-UsingtheoptionalALIF4000rackshelf
1 Install the empty ALIF4000 rack mount tray into your 19” rack frame and fully
secure it.
2 Place an ALIF4000 unit into each side of the rack mount tray so that their rear
panels butt up against the small pegs located on each of the side walls.
3 Locate the supplied thumbscrew and spacer.
4 Insert the thumbscrew through the spacer; then insert into the small hole at the
end of the center divider (A).
5 Gently tighten the thumbscrew so that the spacer engages with the
inner edges of the two ALIF4000 units and holds them in place
(B).
6 Place the power adapters in the rear section of the
rack mount tray and connect them to their
respective ALIF4000 units.
7 Make all other necessary
connections to the
ALIF4000 units.
AdderLink
IMPORTANT:WhenmountingtheALIFunits(andtheir
poweradapters),ensurethattheventsarenotobscured
andthatthereissufcientairow.Theoperating
temperaturerangeis0to40ºC(0to104ºF)andmust
notbeexceeded.
INSTALLATIONCONFIGURATIONOPERATION
(A)
(B)
1
4 0 0 0
2
TRANSMIT
3
4
AdderLink
1
4 0 0 0
2
TRANSMIT
3
4
FURTHER
INFORMATION
INDEX
An optional blanking plate (part number:
RMK12-BP) is available to seal the airow
if only one ALIF4000 unit is installed within
a rack mount tray.
56
Page 58

APPENDIXI-OPENSOURCELICENSES
The software included in this product contains
copyrighted software that is licensed under the GNU
General Public License (GPL) v2. You may obtain the
complete Corresponding Source Code from Adder for
a period of three years after the last shipment of this
product, which will be no earlier than 2028, by contacting
support@adder.com or writing to:
Attn: ACD/Open Source Request,
Adder Technology Ltd,
Saxon Way, Bar Hill,
Cambridge, CB23 8SL,
United Kingdom
Please write “Source for product XXXXXXXX” in the
subject line, where XXXXXXXX is the model and version
number.
This offer is valid to anyone in receipt of this information.
dtc
u-boot-socfpga
linux-socfpga
busybox
termcap
util-linux
libcap
systemd
e2fsprogs
glib
dbus-1
freetype
qt5
libpbe
A complete copy of the GNU General Public License v2 license text is
included at the end of this le.
This product includes binaries that are derived from the open source
community. The modules listed below are licenced under the GNU Lesser
General Public License v2.1 and must be provided, in source form, on
request:
kmod
systemd
libdaemon
avahi
libgpg-error
libgcrypt
gnutls
libmicrohttpd
A complete copy of the GNU Lesser General Public License v2.1 license text
is included at the end of this le.
This product includes binaries that are derived from the open source
community. The modules listed below are licenced under the GNU Lesser
General Public License v3 and must be provided, in source form, on
request:
libunistring
gmp
nettle
libjwt
A complete copy of the GNU Lesser General Public License v3 license text is
included at the end of this le.
In addition to the GPL modules listed, this product also includes
binaries derived from 3rd party open sources that have their own
license requirements. Each module is listed below with their required
Copyright statement and distribution conditions.
----------------------------------------------------------------------------
-
- Module: dhcp
-
----------------------------------------------------------------------------
# Copyright (c) 2004-2017 by Internet Systems Consortium, Inc. (“ISC”)
# Copyright (c) 1995-2003 by Internet Software Consortium
#
# Permission to use, copy, modify, and distribute this software for any
# purpose with or without fee is hereby granted, provided that the above
# copyright notice and this permission notice appear in all copies.
#
# THE SOFTWARE IS PROVIDED “AS IS” AND ISC DISCLAIMS ALL WARRANTIES
# WITH REGARD TO THIS SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF
# MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL ISC BE LIABLE FOR
# ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES
# WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN
# ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT
# OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
#
# Internet Systems Consortium, Inc.
# 950 Charter Street
# Redwood City, CA 94063
# <info@isc.org>
# https://www.isc.org/
----------------------------------------------------------------------------
-
- Module: freebsd-libc
-
----------------------------------------------------------------------------
# @(#)COPYRIGHT 8.2 (Berkeley) 3/21/94
All of the documentation and software included in the 4.4BSD and 4.4BSD-Lite
Releases is copyrighted by The Regents of the University of California.
Copyright 1979, 1980, 1983, 1986, 1988, 1989, 1991, 1992, 1993, 1994
The Regents of the University of California. All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software
must display the following acknowledgement:
This product includes software developed by the University of
California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors
may be used to endorse or promote products derived from this software
without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS ``AS IS’’ AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
SUCH DAMAGE.
The Institute of Electrical and Electronics Engineers and the American
National Standards Committee X3, on Information Processing Systems have
given us permission to reprint portions of their documentation.
In the following statement, the phrase ``this text’’ refers to portions
of the system documentation.
Portions of this text are reprinted and reproduced in electronic form in
the second BSD Networking Software Release, from IEEE Std 1003.1-1988, IEEE
Standard Portable Operating System Interface for Computer Environments
(POSIX), copyright C 1988 by the Institute of Electrical and Electronics
Engineers, Inc. In the event of any discrepancy between these versions
and the original IEEE Standard, the original IEEE Standard is the referee
document.
In the following statement, the phrase ``This material’’ refers to portions
of the system documentation.
This material is reproduced with permission from American National
Standards Committee X3, on Information Processing Systems. Computer and
Business Equipment Manufacturers Association (CBEMA), 311 First St., NW,
Suite 500, Washington, DC 20001-2178. The developmental work of
Programming Language C was completed by the X3J11 Technical Committee.
The views and conclusions contained in the software and documentation are
those of the authors and should not be interpreted as representing ofcial
policies, either expressed or implied, of the Regents of the University
of California.
----------------------------------------------------------------------------
-
- Module: openssl
-
----------------------------------------------------------------------------
LICENSE ISSUES
==============
The OpenSSL toolkit stays under a double license, i.e. both the conditions of
the OpenSSL License and the original SSLeay license apply to the toolkit.
See below for the actual license texts.
OpenSSL License
---------------
/* ==================================================================
==
* Copyright (c) 1998-2019 The OpenSSL Project. All rights reserved.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
57
Page 59

*
* Redistribution and use in source and binary forms, with or without
* modication, are permitted provided that the following conditions
* are met:
*
* 1. Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
*
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in
* the documentation and/or other materials provided with the
* distribution.
*
* 3. All advertising materials mentioning features or use of this
* software must display the following acknowledgment:
* “This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit. (http://www.openssl.org/)”
*
* 4. The names “OpenSSL Toolkit” and “OpenSSL Project” must not be used to
* endorse or promote products derived from this software without
* prior written permission. For written permission, please contact
* openssl-core@openssl.org.
*
* 5. Products derived from this software may not be called “OpenSSL”
* nor may “OpenSSL” appear in their names without prior written
* permission of the OpenSSL Project.
*
* 6. Redistributions of any form whatsoever must retain the following
* acknowledgment:
* “This product includes software developed by the OpenSSL Project
* for use in the OpenSSL Toolkit (http://www.openssl.org/)”
*
* THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS’’ AND ANY
* EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
* PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR
* ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
* NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
* LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
* STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
* ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
* OF THE POSSIBILITY OF SUCH DAMAGE.
* ==================================================================
==
*
* This product includes cryptographic software written by Eric Young
* (eay@cryptsoft.com). This product includes software written by Tim
* Hudson (tjh@cryptsoft.com).
*
*/
Original SSLeay License
-----------------------
/* Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com)
* All rights reserved.
*
* This package is an SSL implementation written
* by Eric Young (eay@cryptsoft.com).
* The implementation was written so as to conform with Netscapes SSL.
*
* This library is free for commercial and non-commercial use as long as
* the following conditions are aheared to. The following conditions
* apply to all code found in this distribution, be it the RC4, RSA,
* lhash, DES, etc., code; not just the SSL code. The SSL documentation
* included with this distribution is covered by the same copyright terms
* except that the holder is Tim Hudson (tjh@cryptsoft.com).
*
* Copyright remains Eric Young’s, and as such any Copyright notices in
* the code are not to be removed.
* If this package is used in a product, Eric Young should be given attribution
* as the author of the parts of the library used.
* This can be in the form of a textual message at program startup or
* in documentation (online or textual) provided with the package.
*
* Redistribution and use in source and binary forms, with or without
* modication, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the copyright
* notice, this list of conditions and the following disclaimer.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. All advertising materials mentioning features or use of this software
* must display the following acknowledgement:
* “This product includes cryptographic software written by
* Eric Young (eay@cryptsoft.com)”
* The word ‘cryptographic’ can be left out if the rouines from the library
* being used are not cryptographic related :-).
* 4. If you include any Windows specic code (or a derivative thereof) from
* the apps directory (application code) you must include an acknowledgement:
* “This product includes software written by Tim Hudson (tjh@cr yptsoft.com)”
*
* THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS’’ AND
* ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
* IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
* FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
* DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS
* OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
* HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
STRICT
* LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY
* OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
* SUCH DAMAGE.
*
* The licence and distribution terms for any publically available version or
* derivative of this code cannot be changed. i.e. this code cannot simply be
* copied and put under another distribution licence
* [including the GNU Public Licence.]
*/
----------------------------------------------------------------------------
-
- Module: libcvt
-
----------------------------------------------------------------------------
Copyright (c) 2001, Andy Ritger aritger@nvidia.com
All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
o Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
o Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer
in the documentation and/or other materials provided with the
distribution.
o Neither the name of NVIDIA nor the names of its contributors
may be used to endorse or promote products derived from this
software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
“AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT
NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL
THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING,
BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT
LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN
ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This program is based on the Generalized Timing Formula(GTF TM)
Standard Version: 1.0, Revision: 1.0
The GTF Document contains the following Copyright information:
Copyright (c) 1994, 1995, 1996 - Video Electronics Standards
Association. Duplication of this document within VESA member
companies for review purposes is permitted. All other rights
reserved.
While every precaution has been taken in the preparation
of this standard, the Video Electronics Standards Association and
its contributors assume no responsibility for errors or omissions,
and make no warranties, expressed or implied, of functionality
of suitability for any purpose. The sample code contained within
this standard may be used without restriction.
----------------------------------------------------------------------------
-
- Module: libdrm
-
----------------------------------------------------------------------------
Copyright 1999, 2000 Precision Insight, Inc., Cedar Park, Texas.
Copyright 2000 VA Linux Systems, Inc., Sunnyvale, California.
All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation les (the “Software”),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
PRECISION INSIGHT AND/OR ITS SUPPLIERS BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER
DEALINGS IN THE SOFTWARE.
-------
Copyright (c) 2007-2008 Tungsten Graphics, Inc., Cedar Park, Texas.
Copyright (c) 2007-2008 Dave Airlie <airlied@linux.ie>
Copyright (c) 2007-2008 Jakob Bornecrantz <wallbraker@gmail.com>
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation les (the “Software”),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
58
Page 60

THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS
IN THE SOFTWARE.
----------------------------------------------------------------------------
-
- Module: libpcap
-
----------------------------------------------------------------------------
Copyright (c) 1999 - 2005 NetGroup, Politecnico di Torino (Italy).
Copyright (c) 2005 - 2010 CACE Technologies, Davis (California).
All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. Neither the name of the Politecnico di Torino, CACE Technologies
nor the names of its contributors may be used to endorse or promote
products derived from this software without specic prior written
permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
“AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes software developed by the University of
California, Lawrence Berkeley Laboratory and its contributors.
This product includes software developed by the Kungliga Tekniska
Högskolan and its contributors.
This product includes software developed by Yen Yen Lim and North
Dakota State University.
---------------------------------------------------------------------
Portions Copyright (c) 1990, 1991, 1992, 1993, 1994, 1995, 1996, 1997
The Regents of the University of California. All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this
software must display the following acknowledgement: “This product
includes software developed by the University of California, Berkeley
and its contributors.”
4. Neither the name of the University nor the names of its contributors
may be used to endorse or promote products derived from this software
without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE INSTITUTE AND CONTRIBUTORS ``AS IS’’
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---------------------------------------------------------------------
Portions Copyright (c) 1983 Regents of the University of California.
All rights reserved.
Redistribution and use in source and binary forms are permitted provided
that the above copyright notice and this paragraph are duplicated in all
such forms and that any documentation, advertising materials, and other
materials related to such distribution and use acknowledge that the
software was developed by the University of California, Berkeley. The
name of the University may not be used to endorse or promote products
derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED ``AS IS’’ AND WITHOUT ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF
MERCHANTIBILITY AND FITNESS FOR A PARTICULAR PURPOSE.
---------------------------------------------------------------------
Portions Copyright (c) 1995, 1996, 1997 Kungliga Tekniska Högskolan
(Royal Institute of Technology, Stockholm, Sweden). All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this
software must display the following acknowledgement: “This product
includes software developed by the Kungliga Tekniska Högskolan and
its contributors.”
4. Neither the name of the University nor the names of its contributors
may be used to endorse or promote products derived from this software
without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE INSTITUTE AND CONTRIBUTORS ``AS IS’’
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE INSTITUTE OR CONTRIBUTORS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF
THE POSSIBILITY OF SUCH DAMAGE.
---------------------------------------------------------------------
Portions Copyright (c) 1997 Yen Yen Lim and North Dakota State University.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software
must display the following acknowledgement: “This product includes software
developed by Yen Yen Lim and North Dakota State University”
4. The name of the author may not be used to endorse or promote products
derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS’’ AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED.
IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED
TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS;
OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
---------------------------------------------------------------------
Portions Copyright (c) 1993 by Digital Equipment Corporation.
Permission to use, copy, modify, and distribute this software for any
purpose with or without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies, and
that the name of Digital Equipment Corporation not be used in advertising
or publicity pertaining to distribution of the document or software without
specic, written prior permission.
THE SOFTWARE IS PROVIDED “AS IS” AND DIGITAL EQUIPMENT CORP. DISCLAIMS ALL
WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING ALL IMPLIED
WARRANTIES
OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL DIGITAL EQUIPMENT
CORPORATION BE LIABLE FOR ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL
DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR
PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS
ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF
THIS
SOFTWARE.
---------------------------------------------------------------------
Portions Copyright (C) 1995, 1996, 1997, 1998, and 1999 WIDE Project.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. Neither the name of the project nor the names of its contributors
may be used to endorse or promote products derived from this software
without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE PROJECT AND CONTRIBUTORS ``AS IS’’
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE PROJECT OR CONTRIBUTORS
BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF
THE POSSIBILITY OF SUCH DAMAGE.
---------------------------------------------------------------------
Portions Copyright (c) 1996 Juniper Networks, Inc. All rights reserved.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
59
Page 61

Redistribution and use in source and binary forms, with or without
modication, are permitted provided that:
(1) source code distributions retain the above copyright notice and this
paragraph in its entirety,
(2) distributions including binary code include the above copyright
notice and this paragraph in its entirety in the documentation or other
materials provided with the distribution. The name of Juniper Networks
may not be used to endorse or promote products derived from this software
without specic prior written permission.
THIS SOFTWARE IS PROVIDED ``AS IS’’ AND WITHOUT ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
---------------------------------------------------------------------
Portions Copyright (c) 2001 Daniel Hartmeier All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
- Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTOR “AS
IS”
AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDERS OR CONTRIBUTORS
BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
---------------------------------------------------------------------
Portions Copyright 1989 by Carnegie Mellon.
Permission to use, copy, modify, and distribute this program for any
purpose and without fee is hereby granted, provided that this copyright
and permission notice appear on all copies and supporting documentation,
the name of Carnegie Mellon not be used in advertising or publicity
pertaining to distribution of the program without specic prior permission,
and notice be given in supporting documentation that copying and
distribution is by permission of Carnegie Mellon and Stanford University.
Carnegie Mellon makes no representations about the suitability of this
software for any purpose. It is provided “as is” without express or implied
warranty.
----------------------------------------------------------------------------
-
- Module: libupnp
-
----------------------------------------------------------------------------
Copyright (c) 2000-2003 Intel Corporation
All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions are met:
* Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright notice,
this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
* Neither name of Intel Corporation nor the names of its contributors
may be used to endorse or promote products derived from this software
without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
``AS IS’’ AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL INTEL OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY
OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
----------------------------------------------------------------------------
-
- Module: libev
-
----------------------------------------------------------------------------
All les in libev are
Copyright (c)2007,2008,2009,2010,2011,2012,2013 Marc Alexander Lehmann.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions are
met:
* Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above
copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided
with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
“AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
----------------------------------------------------------------------------
-
- Module: libaes
-
----------------------------------------------------------------------------
Copyright (c) 1998-2008, Brian Gladman, Worcester, UK. All rights reserved.
LICENSE TERMS
The redistribution and use of this software (with or without changes)
is allowed without the payment of fees or royalties provided that:
1. source code distributions include the above copyright notice, this
list of conditions and the following disclaimer;
2. binary distributions include the above copyright notice, this list
of conditions and the following disclaimer in their documentation;
3. the name of the copyright holder is not used to endorse products
built using this software without specic written permission.
DISCLAIMER
This software is provided ‘as is’ with no explicit or implied warranties
in respect of its properties, including, but not limited to, correctness
and/or tness for purpose.
----------------------------------------------------------------------------
-
- Module: libgcrypt
-
----------------------------------------------------------------------------
Additional license notices for Libgcrypt. -*- org -*-
This le contains the copying permission notices for various les in
the Libgcrypt distribution which are not covered by the GNU Lesser
General Public License (LGPL) or the GNU General Public License (GPL).
These notices all require that a copy of the notice be included
in the accompanying documentation and be distributed with binary
distributions of the code, so be sure to include this le along
with any binary distributions derived from the GNU C Library.
* BSD_3Clause
For les:
- cipher/sha256-avx-amd64.S
- cipher/sha256-avx2-bmi2-amd64.S
- cipher/sha256-ssse3-amd64.S
- cipher/sha512-avx-amd64.S
- cipher/sha512-avx2-bmi2-amd64.S
- cipher/sha512-ssse3-amd64.S
#+begin_quote
Copyright (c) 2012, Intel Corporation
All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions are
met:
* Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the
distribution.
* Neither the name of the Intel Corporation nor the names of its
contributors may be used to endorse or promote products derived from
this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY INTEL CORPORATION “AS IS” AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL INTEL CORPORATION OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
#+end_quote
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
60
Page 62

For les:
- random/jitterentropy-base.c
- random/jitterentropy.h
- random/rndjent.c (plus common Libgcrypt copyright holders)
#+begin_quote
* Copyright Stephan Mueller <smueller@chronox.de>, 2013
*
* License
* =======
*
* Redistribution and use in source and binary forms, with or without
* modication, are permitted provided that the following conditions
* are met:
* 1. Redistributions of source code must retain the above copyright
* notice, and the entire permission notice in its entirety,
* including the disclaimer of warranties.
* 2. Redistributions in binary form must reproduce the above copyright
* notice, this list of conditions and the following disclaimer in the
* documentation and/or other materials provided with the distribution.
* 3. The name of the author may not be used to endorse or promote
* products derived from this software without specic prior
* written permission.
*
* ALTERNATIVELY, this product may be distributed under the terms of
* the GNU General Public License, in which case the provisions of the GPL are
* required INSTEAD OF the above restrictions. (This clause is
* necessary due to a potential bad interaction between the GPL and
* the restrictions contained in a BSD-style copyright.)
*
* THIS SOFTWARE IS PROVIDED ``AS IS’’ AND ANY EXPRESS OR IMPLIED
* WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
* OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE, ALL OF
* WHICH ARE HEREBY DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE
* LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
* CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT
* OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
* BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
* LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
* USE OF THIS SOFTWARE, EVEN IF NOT ADVISED OF THE POSSIBILITY OF SUCH
* DAMAGE.
#+end_quote
* X License
For les:
- install.sh
#+begin_quote
Copyright (C) 1994 X Consortium
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation les (the “Software”), to
deal in the Software without restriction, including without limitation the
rights to use, copy, modify, merge, publish, distribute, sublicense, and/or
sell copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN
NO EVENT SHALL THE X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium shall not
be used in advertising or otherwise to promote the sale, use or other deal-
ings in this Software without prior written authorization from the X Consor-
tium.
#+end_quote
* Public domain
For les:
- cipher/arcfour-amd64.S
#+begin_quote
Author: Marc Bevand <bevand_m (at) epita.fr>
Licence: I hereby disclaim the copyright on this code and place it
in the public domain.
#+end_quote
* OCB license 1
For les:
- cipher/cipher-ocb.c
#+begin_quote
OCB is covered by several patents but may be used freely by most
software. See http://web.cs.ucdavis.edu/~rogaway/ocb/license.htm .
In particular license 1 is suitable for Libgcrypt: See
http://web.cs.ucdavis.edu/~rogaway/ocb/license1.pdf for the full
license document; it basically says:
License 1 — License for Open-Source Software Implementations of OCB
(Jan 9, 2013)
Under this license, you are authorized to make, use, and
distribute open-source software implementations of OCB. This
license terminates for you if you sue someone over their
open-source software implementation of OCB claiming that you have
a patent covering their implementation.
License for Open Source Software Implementations of OCB
January 9, 2013
1 Denitions
1.1 “Licensor” means Phillip Rogaway.
1.2 “Licensed Patents” means any patent that claims priority to United
States Patent Application No. 09/918,615 entitled “Method and Apparatus
for Facilitating Efcient Authenticated Encryption,” and any utility,
divisional, provisional, continuation, continuations-in-part, reexamination,
reissue, or foreign counterpart patents that may issue with respect to the
aforesaid patent application. This includes, but is not limited to, United
States Patent No. 7,046,802; United States Patent No. 7,200,227; United
States Patent No. 7,949,129; United States Patent No. 8,321,675 ; and any
patent that issues out of United States Patent Application No. 13/669,114.
1.3 “Use” means any practice of any invention claimed in the Licensed Patents.
1.4 “Software Implementation” means any practice of any invention
claimed in the Licensed Patents that takes the form of software executing on
a user-programmable, general-purpose computer or that takes the form of a
computer-readable medium storing such software. Software Implementation does
not include, for example, application-specic integrated circuits (ASICs),
eld-programmable gate arrays (FPGAs), embedded systems, or IP cores.
1.5 “Open Source Software” means software whose source code is published
and made available for inspection and use by anyone because either (a) the
source code is subject to a license that permits recipients to copy, modify,
and distribute the source code without payment of fees or royalties, or
(b) the source code is in the public domain, including code released for
public use through a CC0 waiver. All licenses certied by the Open Source
Initiative at opensource.org as of January 9, 2013 and all Creative Commons
licenses identied on the creativecommons.org website as of January 9,
2013, including the Public License Fallback of the CC0 waiver, satisfy these
requirements for the purposes of this license.
1.6 “Open Source Software Implementation” means a Software
Implementation in which the software implicating the Licensed Patents is
Open Source Software. Open Source Software Implementation does not include
any Software Implementation in which the software implicating the Licensed
Patents is combined, so as to form a larger program, with software that is
not Open Source Software.
2 License Grant
2.1 License. Subject to your compliance with the term s of this license,
including the restriction set forth in Section 2.2, Licensor hereby
grants to you a perpetual, worldwide, non-exclusive, non-transferable,
non-sublicenseable, no-charge, royalty-free, irrevocable license to practice
any invention claimed in the Licensed Patents in any Open Source Software
Implementation.
2.2 Restriction. If you or your afliates institute patent litigation
(including, but not limited to, a cross-claim or counterclaim in a lawsuit)
against any entity alleging that any Use authorized by this license
infringes another patent, then any rights granted to you under this license
automatically terminate as of the date such litigation is led.
3 Disclaimer
YOUR USE OF THE LICENSED PATENTS IS AT YOUR OWN RISK AND UNLESS REQUIRED
BY APPLICABLE LAW, LICENSOR MAKES NO REPRESENTATIONS OR WARRANTIES OF
ANY
KIND CONCERNING THE LICENSED PATENTS OR ANY PRODUCT EMBODYING ANY
LICENSED
PATENT, EXPRESS OR IMPLIED, STATUT ORY OR OTHERWISE, INCLUDING, WITHOUT
LIMITATION, WARRANTIES OF TITLE, MERCHANTIBILITY, FITNESS FOR A PARTICULAR
PURPOSE, OR NONINFRINGEMENT. IN NO EVENT WILL LICENSOR BE LIABLE FOR ANY
CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN CONTRACT, TORT OR
OTHERWISE,
ARISING FROM OR RELATED TO ANY USE OF THE LICENSED PATENTS, INCLUDING,
WITHOUT LIMITATION, DIRECT, INDIRECT, INCIDENTAL, CONSEQUENTIAL, PUNITIVE
OR SPECIAL DAMAGES, EVEN IF LICENSOR HAS BEEN ADVISED OF THE POSSIBILITY OF
SUCH DAMAGES PRIOR TO SUCH AN OCCURRENCE.
#+end_quote
----------------------------------------------------------------------------
-
- Module: jansson
-
----------------------------------------------------------------------------
Copyright (c) 2009-2018 Petri Lehtinen <petri@digip.org>
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation les (the “Software”), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN
THE SOFTWARE.
----------------------------------------------------------------------------
-
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
61
Page 63

- Module: mtdev
-
----------------------------------------------------------------------------
mtdev - Multitouch Protocol Translation Library (MIT license)
Copyright (C) 2010 Henrik Rydberg <rydberg@euromail.se>
Copyright (C) 2010 Canonical Ltd.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation les (the “Software”),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
----------------------------------------------------------------------------
-
- Module: libevdev
-
----------------------------------------------------------------------------
Copyright © 2013 Red Hat, Inc.
Copyright © 2013 David Herrmann <dh.herrmann@gmail.com>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting documentation, and
that the name of the copyright holders not be used in advertising or
publicity pertaining to distribution of the software without specic,
written prior permission. The copyright holders make no representations
about the suitability of this software for any purpose. It is provided “as
is” without express or implied warranty.
THE COPYRIGHT HOLDERS DISCLAIM ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS
OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE
OF THIS SOFTWARE.
The following license is from a Linux kernel header le and there is no GPL
code this package links to.
Copyright (c) 1999-2002 Vojtech Pavlik
This program is free software; you can redistribute it and/or modify it
under the terms of the GNU General Public License version 2 as published by
the Free Software Foundation.
----------------------------------------------------------------------------
-
- Module: libinput
-
----------------------------------------------------------------------------
Copyright © 2006-2009 Simon Thum
Copyright © 2008-2012 Kristian Høgsberg
Copyright © 2010-2012 Intel Corporation
Copyright © 2010-2011 Benjamin Franzke
Copyright © 2011-2012 Collabora, Ltd.
Copyright © 2013-2014 Jonas Ådahl
Copyright © 2013-2015 Red Hat, Inc.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation les (the “Software”),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
libinput ships a copy of the GPL-licensed Linux kernel’s linux/input.h
header le. [1] This does not make libinput GPL.
This copy is provided to provide consistent behavior regardless which kernel
version libinput is compiled against. The header is used during compilation
only, libinput does not link against GPL libraries.
[1] http://cgit.freedesktop.org/wayland/libinput/tree/include/linux/input.h
----------------------------------------------------------------------------
-
- Module: strace
-
----------------------------------------------------------------------------
Copyright (c) 1991, 1992 Paul Kranenburg <pk@cs.few.eur.nl>
Copyright (c) 1993 Branko Lankester <branko@hacktic.nl>
Copyright (c) 1993 Ulrich Pegelow <pegelow@moorea.uni-muenster.de>
Copyright (c) 1995, 1996 Michael Elizabeth Chastain <mec@duracef.shout.net>
Copyright (c) 1993, 1994, 1995, 1996 Rick Sladkey <jrs@world.std.com>
Copyright (c) 1998-2001 Wichert Akkerman <wakkerma@deephackmode.org>
Copyright (c) 2001-2017 The strace developers.
All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
3. The name of the author may not be used to endorse or promote products
derived from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR ``AS IS’’ AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED.
IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT
NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF
THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
----------------------------------------------------------------------------
-
- Module: tcpdump
-
----------------------------------------------------------------------------
Licensed under the 3-clause BSD license:
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions
are met:
1. Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright
notice, this list of conditions and the following disclaimer in
the documentation and/or other materials provided with the
distribution.
3. The names of the authors may not be used to endorse or promote
products derived from this software without specic prior
written permission.
THIS SOFTWARE IS PROVIDED ``AS IS’’ AND WITHOUT ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, WITHOUT LIMITATION, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
Some les in this package are licensed under the 4-clause BSD license,
the copyright on most of them belongs to The Regents of the University
of California. Since the license was retroactively changed in 1999 to
remove the advertising clause, they are effectively under the 3-clause
license even if the text of the license in the les hasn’t been
updated. See the following document for more details:
ftp://ftp.cs.berkeley.edu/pub/4bsd/README.Impt.License.Change>
Other les under the 4-clause BSD license and whose copyright doesn’t
belong to the The Regents of the University of California are listed
below:
- aodv.h, Copyright (c) 2003 Bruce M. Simpson
- atmuni31.h, Copyright (c) 1997 Yen Yen Lim and North Dakota State University
- ieee802_11.h, Copyright (c) 2001 Fortress Technologies and Charlie Lenahan
- print-802_11.c, Copyright (c) 2001 Fortress Technologies and Charlie Lenahan
- print-aodv.c, Copyright (c) 2003 Bruce M. Simpson
- print-ascii.c, Copyright (c) 1997, 1998 The NetBSD Foundation, Inc.
- print-cnfp.c, Copyright (c) 1998 Michael Shalayeff
- print-gre.c, Copyright (c) 2002 Jason L. Wright
- print-mobile.c, Copyright (c) 1998 The NetBSD Foundation, Inc.
- print-sunatm.c, Copyright (c) 1997 Yen Yen Lim and North Dakota State
University
- print-telnet.c, Copyright (c) 1997, 1998 The NetBSD Foundation, Inc.
- print-timed.c, Copyright (c) 2000 Ben Smithurst
- missing/inet_aton.c, Copyright (c) 1995, 1996, 1997 Kungliga Tekniska
Högskolan (Royal Institute of Technology, Stockholm,
Sweden).
- missing/inet_ntop.c, Copyright (c) 1995, 1996, 1997 Kungliga Tekniska
Högskolan (Royal Institute of Technology, Stockholm,
Sweden).
- missing/inet_pton.c, Copyright (c) 1995, 1996, 1997 Kungliga Tekniska
Högskolan (Royal Institute of Technology, Stockholm,
Sweden).
----------------------------------------------------------------------------
-
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
62
Page 64

- Module: ntp
-
----------------------------------------------------------------------------
_________________________________________________________________
The following copyright notice applies to all les collectively
called the Network Time Protocol Version 4 Distribution. Unless
specically declared otherwise in an individual le, this entire
notice applies as if the text was explicitly included in the le.
***********************************************************************
* *
* Copyright (c) University of Delaware 1992-2015 *
* *
* Permission to use, copy, modify, and distribute this software and *
* its documentation for any purpose with or without fee is hereby *
* granted, provided that the above copyright notice appears in all *
* copies and that both the copyright notice and this permission *
* notice appear in supporting documentation, and that the name *
* University of Delaware not be used in advertising or publicity *
* pertaining to distribution of the software without specic, *
* written prior permission. The University of Delaware makes no *
* representations about the suitability this software for any *
* purpose. It is provided “as is” without express or implied *
* warranty. *
* *
***********************************************************************
Content starting in 2011 from Harlan Stenn, Danny Mayer, and Martin
Burnicki is:
***********************************************************************
* *
* Copyright (c) Network Time Foundation 2011-2017 *
* *
* All Rights Reserved *
* *
* Redistribution and use in source and binary forms, with or without *
* modication, are permitted provided that the following conditions *
* are met: *
* 1. Redistributions of source code must retain the above copyright *
* notice, this list of conditions and the following disclaimer. *
* 2. Redistributions in binary form must reproduce the above *
* copyright notice, this list of conditions and the following *
* disclaimer in the documentation and/or other materials provided *
* with the distribution. *
* *
* THIS SOFTWARE IS PROVIDED BY THE AUTHORS ``AS IS’’ AND ANY EXPRESS *
* OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED *
* WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE *
* ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHORS OR CONTRIBUTORS BE *
* LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR *
* CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT *
* OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR *
* BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF *
* LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT *
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE *
* USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH *
* DAMAGE. *
***********************************************************************
The following individuals contributed in part to the Network Time
Protocol Distribution Version 4 and are acknowledged as authors of
this work.
1. [1]Takao Abe <takao_abe@xurb.jp> Clock driver for JJY receivers
2. [2]Mark Andrews <mark_andrews@isc.org> Leitch atomic clock
controller
3. [3]Bernd Altmeier <altmeier@atlsoft.de> hopf Elektronik serial
line and PCI-bus devices
4. [4]Viraj Bais <vbais@mailman1.intel.com> and [5]Clayton Kirkwood
<kirkwood@striderfm.intel.com> port to WindowsNT 3.5
5. [6]Michael Barone <michael,barone@lmco.com> GPSVME xes
6. [7]Karl Berry <karl@owl.HQ.ileaf.com> syslog to le option
7. [8]Greg Brackley <greg.brackley@bigfoot.com> Major rework of WINNT
port. Clean up recvbuf and iosignal code into separate modules.
8. [9]Marc Brett <Marc.Brett@westgeo.com> Magnavox GPS clock driver
9. [10]Piete Brooks <Piete.Brooks@cl.cam.ac.uk> MSF clock driver,
Trimble PARSE support
10. [11]Nelson B Bolyard <nelson@bolyard.me> update and complete
broadcast and crypto features in sntp
11. [12]Jean-Francois Boudreault
<Jean-Francois.Boudreault@viagenie.qc.ca> IPv6 support
12. [13]Reg Clemens <reg@dwf.com> Oncore driver (Current maintainer)
13. [14]Steve Clift <clift@ml.csiro.au> OMEGA clock driver
14. [15]Casey Crellin <casey@csc.co.za> vxWorks (Tornado) por t and
help with target conguration
15. [16]Sven Dietrich <sven_dietrich@trimble.com> Palisade reference
clock driver, NT adj. residuals, integrated Greg’s Winnt port.
16. [17]John A. Dundas III <dundas@salt.jpl.nasa.gov> Apple A/UX port
17. [18]Torsten Duwe <duwe@immd4.informatik.uni-erlangen.de> Linux
port
18. [19]Dennis Ferguson <dennis@mrbill.canet.ca> foundation code for
NTP Version 2 as specied in RFC-1119
19. [20]John Hay <jhay@icomtek.csir.co.za> IPv6 support and testing
20. [21]Dave Hart <davehart@davehart.com> General maintenance, Windows
port interpolation rewrite
21. [22]Claas Hilbrecht <neoclock4x@linum.com> NeoClock4X clock driver
22. [23]Glenn Hollinger <glenn@herald.usask.ca> GOES clock driver
23. [24]Mike Iglesias <iglesias@uci.edu> DEC Alpha port
24. [25]Jim Jagielski <jim@jagubox.gsfc.nasa.gov> A/UX port
25. [26]Jeff Johnson <jbj@chatham.usdesign.com> massive prototyping
overhaul
26. [27]Hans Lambermont <Hans.Lambermont@nl.origin-it.com> or
[28]<H.Lambermont@chello.nl> ntpsweep
27. [29]Poul-Henning Kamp <phk@FreeBSD.ORG> Oncore driver (Original
author)
28. [30]Frank Kardel [31]<kardel (at) ntp (dot) org> PARSE <GENERIC>
(driver 14 reference clocks), STREAMS modules for PARSE, support
scripts, syslog cleanup, dynamic interface handling
29. [32]Johannes Maximilian Kuehn <kuehn@ntp.org> Rewrote sntp to
comply with NTPv4 specication, ntpq savecong
30. [33]William L. Jones <jones@hermes.chpc.utexas.edu> RS/6000 AIX
modications, HPUX modications
31. [34]Dave Katz <dkatz@cisco.com> RS/6000 AIX por t
32. [35]Craig Leres <leres@ee.lbl.gov> 4.4BSD port, ppsclock, Magnavox
GPS clock driver
33. [36]George Lindholm <lindholm@ucs.ubc.ca> SunOS 5.1 port
34. [37]Louis A. Mamakos <louie@ni.umd.edu> MD5-based authentication
35. [38]Lars H. Mathiesen <thorinn@diku.dk> adaptation of foundation
code for Version 3 as specied in RFC-1305
36. [39]Danny Mayer <mayer@ntp.org>Network I/O, Windows Port, Code
Maintenance
37. [40]David L. Mills <mills@udel.edu> Version 4 foundation,
precision kernel; clock drivers: 1, 3, 4, 6, 7, 11, 13, 18, 19,
22, 36
38. [41]Wolfgang Moeller <moeller@gwdgv1.dnet.gwdg.de> VMS port
39. [42]Jeffrey Mogul <mogul@pa.dec.com> ntptrace utility
40. [43]Tom Moore <tmoore@evel.daytonoh.ncr.com> i386 svr4 port
41. [44]Kamal A Mostafa <kamal@whence.com> SCO OpenServer port
42. [45]Derek Mulcahy <derek@toybox.demon.co.uk> and [46]Damon
Hart-Davis <d@hd.org> ARCRON MSF clock driver
43. [47]Rob Neal <neal@ntp.org> Bancomm refclock and cong/parse code
maintenance
44. [48]Rainer Pruy <Rainer.Pruy@informatik.uni-erlangen.de>
monitoring/trap scripts, statistics le handling
45. [49]Dirce Richards <dirce@zk3.dec.com> Digital UNIX V4.0 port
46. [50]Wilfredo Sánchez <wsanchez@apple.com> added support for
NetInfo
47. [51]Nick Sayer <mrapple@quack.kfu.com> SunOS streams modules
48. [52]Jack Sasportas <jack@innovativeinternet.com> Saved a Lot of
space on the stuff in the html/pic/ subdirectory
49. [53]Ray Schnitzler <schnitz@unipress.com> Unixware1 port
50. [54]Michael Shields <shields@tembel.org> USNO clock driver
51. [55]Jeff Steinman <jss@pebbles.jpl.nasa.gov> Datum PTS clock
driver
52. [56]Harlan Stenn <harlan@pfcs.com> GNU automake/autocongure
makeover, various other bits (see the ChangeLog)
53. [57]Kenneth Stone <ken@sdd.hp.com> HP-UX port
54. [58]Ajit Thyagarajan <ajit@ee.udel.edu>IP multicast/anycast
support
55. [59]Tomoaki TSURUOKA <tsuruoka@nc.fukuoka-u.ac.jp>TRAK clock
driver
56. [60]Brian Utterback <brian.utterback@oracle.com> General codebase,
Solaris issues
57. [61]Loganaden Velvindron <loganaden@gmail.com> Sandboxing
(libseccomp) support
58. [62]Paul A Vixie <vixie@vix.com> TrueTime GPS driver, generic
TrueTime clock driver
59. [63]Ulrich Windl <Ulrich.Windl@rz.uni-regensburg.de> corrected and
validated HTML documents according to the HTML DTD
_________________________________________________________________
----------------------------------------------------------------------------
-
- Module: libjpeg
-
----------------------------------------------------------------------------
This software is based in part on the work of the Independent JPEG Group.
----------------------------------------------------------------------------
-
- Module: libpng
-
----------------------------------------------------------------------------
COPYRIGHT NOTICE, DISCLAIMER, and LICENSE
=========================================
PNG Reference Library License version 2
---------------------------------------
* Copyright (c) 1995-2019 The PNG Reference Library Authors.
* Copyright (c) 2018-2019 Cosmin Truta.
* Copyright (c) 2000-2002, 2004, 2006-2018 Glenn Randers-Pehrson.
* Copyright (c) 1996-1997 Andreas Dilger.
* Copyright (c) 1995-1996 Guy Eric Schalnat, Group 42, Inc.
The software is supplied “as is”, without warranty of any kind,
express or implied, including, without limitation, the warranties
of merchantability, tness for a particular purpose, title, and
non-infringement. In no event shall the Copyright owners, or
anyone distributing the software, be liable for any damages or
other liability, whether in contract, tort or otherwise, arising
from, out of, or in connection with the software, or the use or
other dealings in the software, even if advised of the possibility
of such damage.
Permission is hereby granted to use, copy, modify, and distribute
this software, or portions hereof, for any purpose, without fee,
subject to the following restrictions:
1. The origin of this software must not be misrepresented; you
must not claim that you wrote the original software. If you
use this software in a product, an acknowledgment in the product
documentation would be appreciated, but is not required.
2. Altered source versions must be plainly marked as such, and must
not be misrepresented as being the original software.
3. This Copyright notice may not be removed or altered from any
source or altered source distribution.
PNG Reference Library License version 1 (for libpng 0.5 through 1.6.35)
-----------------------------------------------------------------------
libpng versions 1.0.7, July 1, 2000, through 1.6.35, July 15, 2018 are
Copyright (c) 2000-2002, 2004, 2006-2018 Glenn Randers-Pehrson, are
derived from libpng-1.0.6, and are distributed according to the same
disclaimer and license as libpng-1.0.6 with the following individuals
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
63
Page 65

added to the list of Contributing Authors:
Simon-Pierre Cadieux
Eric S. Raymond
Mans Rullgard
Cosmin Truta
Gilles Vollant
James Yu
Mandar Sahastrabuddhe
Google Inc.
Vadim Barkov
and with the following additions to the disclaimer:
There is no warranty against interference with your enjoyment of
the library or against infringement. There is no warranty that our
efforts or the library will fulll any of your particular purposes
or needs. This library is provided with all faults, and the entire
risk of satisfactory quality, performance, accuracy, and effort is
with the user.
Some les in the “contrib” directory and some congure-generated
les that are distributed with libpng have other copyright owners, and
are released under other open source licenses.
libpng versions 0.97, January 1998, through 1.0.6, March 20, 2000, are
Copyright (c) 1998-2000 Glenn Randers-Pehrson, are derived from
libpng-0.96, and are distributed according to the same disclaimer and
license as libpng-0.96, with the following individuals added to the
list of Contributing Authors:
Tom Lane
Glenn Randers-Pehrson
Willem van Schaik
libpng versions 0.89, June 1996, through 0.96, May 1997, are
Copyright (c) 1996-1997 Andreas Dilger, are derived from libpng-0.88,
and are distributed according to the same disclaimer and license as
libpng-0.88, with the following individuals added to the list of
Contributing Authors:
John Bowler
Kevin Bracey
Sam Bushell
Magnus Holmgren
Greg Roelofs
Tom Tanner
Some les in the “scripts” directory have other copyright owners,
but are released under this license.
libpng versions 0.5, May 1995, through 0.88, January 1996, are
Copyright (c) 1995-1996 Guy Eric Schalnat, Group 42, Inc.
For the purposes of this copyright and license, “Contributing Authors”
is dened as the following set of individuals:
Andreas Dilger
Dave Martindale
Guy Eric Schalnat
Paul Schmidt
Tim Wegner
The PNG Reference Library is supplied “AS IS”. The Contributing
Authors and Group 42, Inc. disclaim all warranties, expressed or
implied, including, without limitation, the warranties of
merchantability and of tness for any purpose. The Contributing
Authors and Group 42, Inc. assume no liability for direct, indirect,
incidental, special, exemplary, or consequential damages, which may
result from the use of the PNG Reference Library, even if advised of
the possibility of such damage.
Permission is hereby granted to use, copy, modify, and distribute this
source code, or portions hereof, for any purpose, without fee, subject
to the following restrictions:
1. The origin of this source code must not be misrepresented.
2. Altered versions must be plainly marked as such and must not
be misrepresented as being the original source.
3. This Copyright notice may not be removed or altered from any
source or altered source distribution.
The Contributing Authors and Group 42, Inc. specically permit,
without fee, and encourage the use of this source code as a component
to supporting the PNG le format in commercial products. If you use
this source code in a product, acknowledgment is not required but would
be appreciated.
----------------------------------------------------------------------------
-
- Module: libxkbcommon
-
----------------------------------------------------------------------------
-------------------------------------------------------------------------------
Copyright © 2009-2012, 2016 Daniel Stone
Copyright © 2012 Ran Benita <ran234@gmail.com>
Copyright © 2010, 2012 Intel Corporation
Copyright © 2008, 2009 Dan Nicholson
Copyright © 2010 Francisco Jerez <currojerez@riseup.net>
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation les (the “Software”),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
-------------------------------------------------------------------------------
Copyright 1985, 1987, 1988, 1990, 1998 The Open Group
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation les (the “Software”),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE
AUTHORS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN
ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
SOFTWARE.
Except as contained in this notice, the names of the authors or their
institutions shall not be used in advertising or otherwise to promote the
sale, use or other dealings in this Software without prior written
authorization from the authors.
-------------------------------------------------------------------------------
Copyright (c) 1993, 1994, 1995, 1996 by Silicon Graphics Computer Systems, Inc.
Permission to use, copy, modify, and distribute this
software and its documentation for any purpose and without
fee is hereby granted, provided that the above copyright
notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting
documentation, and that the name of Silicon Graphics not be
used in advertising or publicity pertaining to distribution
of the software without specic prior written permission.
Silicon Graphics makes no representation about the suitability
of this software for any purpose. It is provided “as is”
without any express or implied warranty.
SILICON GRAPHICS DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. IN NO EVENT SHALL SILICON
GRAPHICS BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL
DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH
THE USE OR PERFORMANCE OF THIS SOFTWARE.
-------------------------------------------------------------------------------
Copyright 1987, 1988 by Digital Equipment Corporation, Maynard, Massachusetts.
All Rights Reserved
Permission to use, copy, modify, and distribute this software and its
documentation for any purpose and without fee is hereby granted,
provided that the above copyright notice appear in all copies and that
both that copyright notice and this permission notice appear in
supporting documentation, and that the name of Digital not be
used in advertising or publicity pertaining to distribution of the
software without specic, written prior permission.
DIGITAL DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE, INCLUDING
ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO EVENT SHALL
DIGITAL BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL DAMAGES OR
ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS,
WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS
SOFTWARE.
-------------------------------------------------------------------------------
Copyright (C) 2011 Joseph Adams <joeyadams3.14159@gmail.com>
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation les (the “Software”), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
64
Page 66

copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in
all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE
AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM,
OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN
THE SOFTWARE.
-------------------------------------------------------------------------------
----------------------------------------------------------------------------
-
- Module: xkeyboard-cong
-
----------------------------------------------------------------------------
Copyright 1996 by Joseph Moss
Copyright (C) 2002-2007 Free Software Foundation, Inc.
Copyright (C) Dmitry Golubev <lastguru@mail.ru>, 2003-2004
Copyright (C) 2004, Gregory Mokhin <mokhin@bog.msu.ru>
Copyright (C) 2006 Erdal Ronahî
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation, and that the name of the copyright holder(s) not be used in
advertising or publicity pertaining to distribution of the software without
specic, written prior permission. The copyright holder(s) makes no
representations about the suitability of this software for any purpose. It
is provided “as is” without express or implied warranty.
THE COPYRIGHT HOLDER(S) DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE,
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS, IN NO
EVENT SHALL THE COPYRIGHT HOLDER(S) BE LIABLE FOR ANY SPECIAL, INDIRECT OR
CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS
OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1996 Digital Equipment Corporation
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation les (the
“Software”), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be included
in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL DIGITAL EQUIPMENT CORPORATION BE LIABLE FOR ANY CLAIM,
DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR
THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the Digital Equipment
Corporation shall not be used in advertising or otherwise to promote
the sale, use or other dealings in this Software without prior written
authorization from Digital Equipment Corporation.
Copyright 1996, 1998 The Open Group
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation.
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of The Open Group shall
not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization
from The Open Group.
Copyright 2004-2005 Sun Microsystems, Inc. All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a
copy of this software and associated documentation les (the “Software”),
to deal in the Software without restriction, including without limitation
the rights to use, copy, modify, merge, publish, distribute, sublicense,
and/or sell copies of the Software, and to permit persons to whom the
Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice (including the next
paragraph) shall be included in all copies or substantial portions of the
Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS IN THE SOFTWARE.
Copyright (c) 1996 by Silicon Graphics Computer Systems, Inc.
Permission to use, copy, modify, and distribute this
software and its documentation for any purpose and without
fee is hereby granted, provided that the above copyright
notice appear in all copies and that both that copyright
notice and this permission notice appear in supporting
documentation, and that the name of Silicon Graphics not be
used in advertising or publicity pertaining to distribution
of the software without specic prior written permission.
Silicon Graphics makes no representation about the suitability
of this software for any purpose. It is provided “as is”
without any express or implied warranty.
SILICON GRAPHICS DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS
SOFTWARE, INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. IN NO EVENT SHALL SILICON
GRAPHICS BE LIABLE FOR ANY SPECIAL, INDIRECT OR CONSEQUENTIAL
DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE
OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH
THE USE OR PERFORMANCE OF THIS SOFTWARE.
Copyright (c) 1996 X Consortium
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation les (the
“Software”), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of the X Consortium shall
not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization
from the X Consortium.
Copyright (C) 2004, 2006 Ævar Arnfjörð Bjarmason <avarab@gmail.com>
Permission to use, copy, modify, distribute, and sell this software and its
documentation for any purpose is hereby granted without fee, provided that
the above copyright notice appear in all copies and that both that
copyright notice and this permission notice appear in supporting
documentation.
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT.
IN NO EVENT SHALL THE OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall
not be used in advertising or otherwise to promote the sale, use or
other dealings in this Software without prior written authorization of
the copyright holder.
Copyright (C) 1999, 2000 by Anton Zinoviev <anton@lml.bas.bg>
This software may be used, modied, copied, distributed, and sold,
in both source and binary form provided that the above copyright
and these terms are retained. Under no circumstances is the author
responsible for the proper functioning of this software, nor does
the author assume any responsibility for damages incurred with its
use.
Permission is granted to anyone to use, distribute and modify
this le in any way, provided that the above copyright notice
is left intact and the author of the modication summarizes
the changes in this header.
This le is distributed without any expressed or implied warranty.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
65
Page 67

----------------------------------------------------------------------------
-
- Module: icu
-
----------------------------------------------------------------------------
COPYRIGHT AND PERMISSION NOTICE (ICU 58 and later)
Copyright © 1991-2019 Unicode, Inc. All rights reserved.
Distributed under the Terms of Use in https://www.unicode.org/copyright.html.
Permission is hereby granted, free of charge, to any person obtaining
a copy of the Unicode data les and any associated documentation
(the “Data Files”) or Unicode software and any associated documentation
(the “Software”) to deal in the Data Files or Software
without restriction, including without limitation the rights to use,
copy, modify, merge, publish, distribute, and/or sell copies of
the Data Files or Software, and to permit persons to whom the Data Files
or Software are furnished to do so, provided that either
(a) this copyright and permission notice appear with all copies
of the Data Files or Software, or
(b) this copyright and permission notice appear in associated
Documentation.
THE DATA FILES AND SOFTWARE ARE PROVIDED “AS IS”, WITHOUT WARRANTY OF
ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE
WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NONINFRINGEMENT OF THIRD PARTY RIGHTS.
IN NO EVENT SHALL THE COPYRIGHT HOLDER OR HOLDERS INCLUDED IN THIS
NOTICE BE LIABLE FOR ANY CLAIM, OR ANY SPECIAL INDIRECT OR CONSEQUENTIAL
DAMAGES, OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE,
DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER
TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR
PERFORMANCE OF THE DATA FILES OR SOFTWARE.
Except as contained in this notice, the name of a copyright holder
shall not be used in advertising or otherwise to promote the sale,
use or other dealings in these Data Files or Software without prior
written authorization of the copyright holder.
---------------------
Third-Party Software Licenses
This section contains third-party software notices and/or additional
terms for licensed third-party software components included within ICU
libraries.
1. ICU License - ICU 1.8.1 to ICU 57.1
COPYRIGHT AND PERMISSION NOTICE
Copyright (c) 1995-2016 International Business Machines Corporation and others
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation les (the
“Software”), to deal in the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, and/or sell copies of the Software, and to permit persons
to whom the Software is furnished to do so, provided that the above
copyright notice(s) and this permission notice appear in all copies of
the Software and that both the above copyright notice(s) and this
permission notice appear in supporting documentation.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT
OF THIRD PARTY RIGHTS. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR
HOLDERS INCLUDED IN THIS NOTICE BE LIABLE FOR ANY CLAIM, OR ANY
SPECIAL INDIRECT OR CONSEQUENTIAL DAMAGES, OR ANY DAMAGES WHATSOEVER
RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF
CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN
CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Except as contained in this notice, the name of a copyright holder
shall not be used in advertising or otherwise to promote the sale, use
or other dealings in this Software without prior written authorization
of the copyright holder.
All trademarks and registered trademarks mentioned herein are the
property of their respective owners.
2. Chinese/Japanese Word Break Dictionary Data (cjdict.txt)
# The Google Chrome software developed by Google is licensed under
# the BSD license. Other software included in this distribution is
# provided under other licenses, as set forth below.
#
# The BSD License
# http://opensource.org/licenses/bsd-license.php
# Copyright (C) 2006-2008, Google Inc.
#
# All rights reserved.
#
# Redistribution and use in source and binary forms, with or without
# modication, are permitted provided that the following conditions are met:
#
# Redistributions of source code must retain the above copyright notice,
# this list of conditions and the following disclaimer.
# Redistributions in binary form must reproduce the above
# copyright notice, this list of conditions and the following
# disclaimer in the documentation and/or other materials provided with
# the distribution.
# Neither the name of Google Inc. nor the names of its
# contributors may be used to endorse or promote products derived from
# this software without specic prior written permission.
#
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
# CONTRIBUTORS “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES,
# INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
# MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
# DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE
# LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
# CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
# SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR
# BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
# LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
# NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
# SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
#
#
# The word list in cjdict.txt are generated by combining three word lists
# listed below with further processing for compound word breaking. The
# frequency is generated with an iterative training against Google web
# corpora.
#
# * Libtabe (Chinese)
# - https://sourceforge.net/project/?group_id=1519
# - Its license terms and conditions are shown below.
#
# * IPADIC (Japanese)
# - http://chasen.aist-nara.ac.jp/chasen/distribution.html
# - Its license terms and conditions are shown below.
#
# ---------COPYING.libtabe ---- BEGIN--------------------
#
# /*
# * Copyright (c) 1999 TaBE Project.
# * Copyright (c) 1999 Pai-Hsiang Hsiao.
# * All rights reserved.
# *
# * Redistribution and use in source and binary forms, with or without
# * modication, are permitted provided that the following conditions
# * are met:
# *
# * . Redistributions of source code must retain the above copyright
# * notice, this list of conditions and the following disclaimer.
# * . Redistributions in binary form must reproduce the above copyright
# * notice, this list of conditions and the following disclaimer in
# * the documentation and/or other materials provided with the
# * distribution.
# * . Neither the name of the TaBE Project nor the names of its
# * contributors may be used to endorse or promote products derived
# * from this software without specic prior written permission.
# *
# * THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
CONTRIBUTORS
# * “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
# * LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
# * FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE
# * REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
# * INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
# * (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
# * SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
# * HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
# * STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
# * ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
# * OF THE POSSIBILITY OF SUCH DAMAGE.
# */
#
# /*
# * Copyright (c) 1999 Computer Systems and Communication Lab,
# * Institute of Information Science, Academia
# * Sinica. All rights reserved.
# *
# * Redistribution and use in source and binary forms, with or without
# * modication, are permitted provided that the following conditions
# * are met:
# *
# * . Redistributions of source code must retain the above copyright
# * notice, this list of conditions and the following disclaimer.
# * . Redistributions in binary form must reproduce the above copyright
# * notice, this list of conditions and the following disclaimer in
# * the documentation and/or other materials provided with the
# * distribution.
# * . Neither the name of the Computer Systems and Communication Lab
# * nor the names of its contributors may be used to endorse or
# * promote products derived from this software without specic
# * prior written permission.
# *
# * THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
CONTRIBUTORS
# * “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
# * LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
# * FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE
# * REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
# * INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
# * (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
# * SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
# * HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
# * STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
# * ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
# * OF THE POSSIBILITY OF SUCH DAMAGE.
# */
#
# Copyright 1996 Chih-Hao Tsai @ Beckman Institute,
# University of Illinois
# c-tsai4@uiuc.edu http://casper.beckman.uiuc.edu/~c-tsai4
#
# ---------------COPYING.libtabe-----END--------------------------------
#
#
# ---------------COPYING.ipadic-----BEGIN------------------------------ #
# Copyright 2000, 2001, 2002, 2003 Nara Institute of Science
# and Technology. All Rights Reserved.
#
# Use, reproduction, and distribution of this software is permitted.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
66
Page 68

# Any copy of this software, whether in its original form or modied,
# must include both the above copyright notice and the following
# paragraphs.
#
# Nara Institute of Science and Technology (NAIST),
# the copyright holders, disclaims all warranties with regard to this
# software, including all implied warranties of merchantability and
# tness, in no event shall NAIST be liable for
# any special, indirect or consequential damages or any damages
# whatsoever resulting from loss of use, data or prots, whether in an
# action of contract, negligence or other tortuous action, arising out
# of or in connection with the use or performance of this software.
#
# A large portion of the dictionary entries
# originate from ICOT Free Software. The following conditions for ICOT
# Free Software applies to the current dictionary as well.
#
# Each User may also freely distribute the Program, whether in its
# original form or modied, to any third party or parties, PROVIDED
# that the provisions of Section 3 (“NO WARRANTY”) will ALWAYS appear
# on, or be attached to, the Program, which is distributed substantially
# in the same form as set out herein and that such intended
# distribution, if actually made, will neither violate or otherwise
# contravene any of the laws and regulations of the countries having
# jurisdiction over the User or the intended distribution itself.
#
# NO WARRANTY
#
# The program was produced on an experimental basis in the course of the
# research and development conducted during the project and is provided
# to users as so produced on an experimental basis. Accordingly, the
# program is provided without any warranty whatsoever, whether express,
# implied, statutory or otherwise. The term “warranty” used herein
# includes, but is not limited to, any warranty of the quality,
# performance, merchantability and tness for a particular purpose of
# the program and the nonexistence of any infringement or violation of
# any right of any third party.
#
# Each user of the program will agree and understand, and be deemed to
# have agreed and understood, that there is no warranty whatsoever for
# the program and, accordingly, the entire risk arising from or
# otherwise connected with the program is assumed by the user.
#
# Therefore, neither ICOT, the copyright holder, or any other
# organization that participated in or was otherwise related to the
# development of the program and their respective ofcials, directors,
# ofcers and other employees shall be held liable for any and all
# damages, including, without limitation, general, special, incidental
# and consequential damages, arising out of or otherwise in connection
# with the use or inability to use the program or any product, material
# or result produced or otherwise obtained by using the program,
# regardless of whether they have been advised of, or otherwise had
# knowledge of, the possibility of such damages at any time during the
# project or thereafter. Each user will be deemed to have agreed to the
# foregoing by his or her commencement of use of the program. The term
# “use” as used herein includes, but is not limited to, the use,
# modication, copying and distribution of the program and the
# production of secondary products from the program.
#
# In the case where the program, whether in its original form or
# modied, was distributed or delivered to or received by a user from
# any person, organization or entity other than ICOT, unless it makes or
# grants independently of ICOT any specic warranty to the user in
# writing, such person, organization or entity, will also be exempted
# from and not be held liable to the user for any such damages as noted
# above as far as the program is concerned.
#
# ---------------COPYING.ipadic-----END----------------------------------
3. Lao Word Break Dictionary Data (laodict.txt)
# Copyright (c) 2013 International Business Machines Corporation
# and others. All Rights Reserved.
#
# Project: http://code.google.com/p/lao-dictionary/
# Dictionary: http://lao-dictionary.googlecode.com/git/Lao-Dictionary.txt
# License: http://lao-dictionary.googlecode.com/git/Lao-Dictionary-LICENSE.txt
# (copied below)
#
# This le is derived from the above dictionary, with slight
# modications.
# --------------------------------------------------------------------- # Copyright (C) 2013 Brian Eugene Wilson, Robert Martin Campbell.
# All rights reserved.
#
# Redistribution and use in source and binary forms, with or without
# modication,
# are permitted provided that the following conditions are met:
#
#
# Redistributions of source code must retain the above copyright notice, this
# list of conditions and the following disclaimer. Redistributions in
# binary form must reproduce the above copyright notice, this list of
# conditions and the following disclaimer in the documentation and/or
# other materials provided with the distribution.
#
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
# “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
# LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
# FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE
# COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT,
# INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
# (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
# SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION)
# HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT,
# STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
# ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
# OF THE POSSIBILITY OF SUCH DAMAGE.
# --------------------------------------------------------------------------
4. Burmese Word Break Dictionary Data (burmesedict.txt)
# Copyright (c) 2014 International Business Machines Corporation
# and others. All Rights Reserved.
#
# This list is part of a project hosted at:
# github.com/kanyawtech/myanmar-karen-word-lists
#
# ------------------------------------------------------------------------- # Copyright (c) 2013, LeRoy Benjamin Sharon
# All rights reserved.
#
# Redistribution and use in source and binary forms, with or without
# modication, are permitted provided that the following conditions
# are met: Redistributions of source code must retain the above
# copyright notice, this list of conditions and the following
# disclaimer. Redistributions in binary form must reproduce the
# above copyright notice, this list of conditions and the following
# disclaimer in the documentation and/or other materials provided
# with the distribution.
#
# Neither the name Myanmar Karen Word Lists, nor the names of its
# contributors may be used to endorse or promote products derived
# from this software without specic prior written permission.
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND
# CONTRIBUTORS “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES,
# INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
# MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
# DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS
# BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
# EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED
# TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
# DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
# ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
# TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF
# THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF
# SUCH DAMAGE.
# --------------------------------------------------------------------------
5. Time Zone Database
ICU uses the public domain data and code derived from Time Zone
Database for its time zone support. The ownership of the TZ database
is explained in BCP 175: Procedure for Maintaining the Time Zone
Database section 7.
# 7. Database Ownership
#
# The TZ database itself is not an IETF Contribution or an IETF
# document. Rather it is a pre-existing and regularly updated work
# that is in the public domain, and is intended to remain in the
# public domain. Therefore, BCPs 78 [RFC5378] and 79 [RFC3979] do
# not apply to the TZ Database or contributions that individuals make
# to it. Should any claims be made and substantiated against the TZ
# Database, the organization that is providing the IANA
# Considerations dened in this RFC, under the memorandum of
# understanding with the IETF, currently ICANN, may act in accordance
# with all competent court orders. No ownership claims will be made
# by ICANN or the IETF Trust on the database or the code. Any person
# making a contribution to the database or code waives all rights to
# future claims in that contribution or in the TZ Database.
6. Google double-conversion
Copyright 2006-2011, the V8 project authors. All rights reserved.
Redistribution and use in source and binary forms, with or without
modication, are permitted provided that the following conditions are
met:
* Redistributions of source code must retain the above copyright
notice, this list of conditions and the following disclaimer.
* Redistributions in binary form must reproduce the above
copyright notice, this list of conditions and the following
disclaimer in the documentation and/or other materials provided
with the distribution.
* Neither the name of Google Inc. nor the names of its
contributors may be used to endorse or promote products derived
from this software without specic prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
“AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
----------------------------------------------------------------------------
-
- Module: dropbear
-
----------------------------------------------------------------------------
Dropbear contains a number of components from different sources, hence there
are a few licenses and authors involved. All licenses are fairly
non-restrictive.
The majority of code is written by Matt Johnston, under the license below.
Portions of the client-mode work are (c) 2004 Mihnea Stoenescu, under the
same license:
Copyright (c) 2002-2015 Matt Johnston
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
67
Page 69

Portions copyright (c) 2004 Mihnea Stoenescu
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining a copy
of this software and associated documentation les (the “Software”), to deal
in the Software without restriction, including without limitation the rights
to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
copies of the Software, and to permit persons to whom the Software is
furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL
THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR
OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE,
ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR
OTHER DEALINGS IN THE SOFTWARE.
=====
LibTomCrypt and LibTomMath are written by Tom St Denis, and are Public Domain.
=====
sshpty.c is taken from OpenSSH 3.5p1,
Copyright (c) 1995 Tatu Ylonen <ylo@cs.hut.>, Espoo, Finland
All rights reserved
“As far as I am concerned, the code I have written for this software
can be used freely for any purpose. Any derived versions of this
software must be clearly marked as such, and if the derived work is
incompatible with the protocol description in the RFC le, it must be
called by a name other than “ssh” or “Secure Shell”. “
=====
loginrec.c
loginrec.h
atomicio.h
atomicio.c
and strlcat() (included in util.c) are from OpenSSH 3.6.1p2, and are licensed
under the 2 point BSD license.
loginrec is written primarily by Andre Lucas, atomicio.c by Theo de Raadt.
strlcat() is (c) Todd C. Miller
=====
Import code in keyimport.c is modied from PuTTY’s import.c, licensed as
follows:
PuTTY is copyright 1997-2003 Simon Tatham.
Portions copyright Robert de Bath, Joris van Rantwijk, Delian
Delchev, Andreas Schultz, Jeroen Massar, Wez Furlong, Nicolas Barry,
Justin Bradford, and CORE SDI S.A.
Permission is hereby granted, free of charge, to any person
obtaining a copy of this software and associated documentation les
(the “Software”), to deal in the Software without restriction,
including without limitation the rights to use, copy, modify, merge,
publish, distribute, sublicense, and/or sell copies of the Software,
and to permit persons to whom the Software is furnished to do so,
subject to the following conditions:
The above copyright notice and this permission notice shall be
included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND
NONINFRINGEMENT. IN NO EVENT SHALL THE COPYRIGHT HOLDERS BE LIABLE
FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF
CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION
WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
=====
curve25519-donna:
/* Copyright 2008, Google Inc.
* All rights reserved.
*
* Redistribution and use in source and binary forms, with or without
* modication, are permitted provided that the following conditions are
* met:
*
* * Redistributions of source code must retain the above copyright
* notice, this list of conditions and the following disclaimer.
* * Redistributions in binary form must reproduce the above
* copyright notice, this list of conditions and the following disclaimer
* in the documentation and/or other materials provided with the
* distribution.
* * Neither the name of Google Inc. nor the names of its
* contributors may be used to endorse or promote products derived from
* this software without specic prior written permission.
*
* THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS
* “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT
* LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR
* A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT
* OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
* SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
* LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE,
* DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY
* THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
* (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
* OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
*
* curve25519-donna: Curve25519 elliptic curve, public key function
*
* http://code.google.com/p/curve25519-donna/
*
* Adam Langley <agl@imperialviolet.org>
*
* Derived from public domain C code by Daniel J. Bernstein <djb@cr.yp.to>
*
* More information about curve25519 can be found here
* http://cr.yp.to/ecdh.html
*
* djb’s sample implementation of curve25519 is written in a special assembly
* language called qhasm and uses the oating point registers.
*
* This is, almost, a clean room reimplementation from the curve25519 paper. It
* uses many of the tricks described therein. Only the crecip function is taken
* from the sample implementation.
*/
----------------------------------------------------------------------------
-
- Module: libcurl
-
----------------------------------------------------------------------------
COPYRIGHT AND PERMISSION NOTICE
Copyright (c) 1996 - 2019, Daniel Stenberg, <daniel@haxx.se>, and many
contributors, see the THANKS le.
All rights reserved.
Permission to use, copy, modify, and distribute this software for any purpose
with or without fee is hereby granted, provided that the above copyright
notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF THIRD PARTY
RIGHTS. IN
NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM,
DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR
THE USE
OR OTHER DEALINGS IN THE SOFTWARE.
Except as contained in this notice, the name of a copyright holder shall not
be used in advertising or otherwise to promote the sale, use or other dealings
in this Software without prior written authorization of the copyright holder.
----------------------------------------------------------------------------
-
- Module: ssmping
-
----------------------------------------------------------------------------
Copyright (C) 2005, 2006 Stig Venaas <venaas@uninett.no>
Permission to use, copy, modify, and distribute this software for any
purpose with or without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
----------------------------------------------------------------------------
-
- Module: fonts
-
----------------------------------------------------------------------------
Fonts are (c) Bitstream (see below). DejaVu changes are in public domain.
Glyphs imported from Arev fonts are (c) Tavmjong Bah (see below)
Bitstream Vera Fonts Copyright
------------------------------
Copyright (c) 2003 by Bitstream, Inc . All Rights Reserved. Bitstream Vera is
a trademark of Bitstream, Inc.
Permission is hereby granted, free of charge, to any person obtaining a copy
of the fonts accompanying this license (“Fonts”) and associated
documentation les (the “Font Software”), to reproduce and distribute the
Font Software, including without limitation the rights to use, copy, merge,
publish, distribute, and/or sell copies of the Font Software, and to permit
persons to whom the Font Software is furnished to do so, subject to the
following conditions:
The above copyright and trademark notices and this permission notice shall
be included in all copies of one or more of the Font Software typefaces.
The Font Software may be modied, altered, or added to, and in par ticular
the designs of glyphs or characters in the Fonts may be modied and
additional glyphs or characters may be added to the Fonts, only if the fonts
are renamed to names not containing either the words “Bitstream” or the word
“Vera”.
This License becomes null and void to the extent applicable to Fonts or Font
Software that has been modied and is distributed under the “Bitstream
Vera” names.
The Font Software may be sold as part of a larger software package but no
copy of one or more of the Font Software typefaces may be sold by itself.
THE FONT SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTIES OF
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
68
Page 70

MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OF
COPYRIGHT, PATENT, TRADEMARK, OR OTHER RIGHT. IN NO EVENT SHALL BITSTREAM
OR THE GNOME FOUNDATION BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, INCLUDING ANY GENERAL, SPECIAL, INDIRECT, INCIDENTAL, OR
CONSEQUENTIAL DAMAGES, WHETHER IN AN ACTION OF CONTRACT, TORT OR
OTHERWISE, ARISING FROM, OUT OF THE USE OR INABILITY TO USE THE FONT
SOFTWARE OR FROM OTHER DEALINGS IN THE FONT SOFTWARE.
Except as contained in this notice, the names of Gnome, the Gnome
Foundation, and Bitstream Inc., shall not be used in advertising or
otherwise to promote the sale, use or other dealings in this Font Software
without prior written authorization from the Gnome Foundation or Bitstream
Inc., respectively. For further information, contact: fonts at gnome dot
org.
Arev Fonts Copyright
------------------------------
Copyright (c) 2006 by Tavmjong Bah. All Rights Reserved.
Permission is hereby granted, free of charge, to any person obtaining
a copy of the fonts accompanying this license (“Fonts”) and
associated documentation les (the “Font Software”), to reproduce
and distribute the modications to the Bitstream Vera Font Software,
including without limitation the rights to use, copy, merge, publish,
distribute, and/or sell copies of the Font Software, and to permit
persons to whom the Font Software is furnished to do so, subject to
the following conditions:
The above copyright and trademark notices and this permission notice
shall be included in all copies of one or more of the Font Software
typefaces.
The Font Software may be modied, altered, or added to, and in
particular the designs of glyphs or characters in the Fonts may be
modied and additional glyphs or characters may be added to the
Fonts, only if the fonts are renamed to names not containing either
the words “Tavmjong Bah” or the word “Arev”.
This License becomes null and void to the extent applicable to Fonts
or Font Software that has been modied and is distributed under the
“Tavmjong Bah Arev” names.
The Font Software may be sold as part of a larger software package but
no copy of one or more of the Font Software typefaces may be sold by
itself.
THE FONT SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND,
EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTIES OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT
OF COPYRIGHT, PATENT, TRADEMARK, OR OTHER RIGHT. IN NO EVENT SHALL
TAVMJONG BAH BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
INCLUDING ANY GENERAL, SPECIAL, INDIRECT, INCIDENTAL, OR CONSEQUENTIAL
DAMAGES, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF THE USE OR INABILITY TO USE THE FONT SOFTWARE OR FROM
OTHER DEALINGS IN THE FONT SOFTWARE.
Except as contained in this notice, the name of Tavmjong Bah shall not
be used in advertising or otherwise to promote the sale, use or other
dealings in this Font Software without prior written authorization
from Tavmjong Bah. For further information, contact: tavmjong @ free
. fr.
=====
Apache License
Version 2.0, January 2004
http://www.apache.org/licenses/
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
1. Denitions.
“License” shall mean the terms and conditions for use, reproduction,
and distribution as dened by Sections 1 through 9 of this document.
“Licensor” shall mean the copyright owner or entity authorized by
the copyright owner that is granting the License.
“Legal Entity” shall mean the union of the acting entity and all
other entities that control, are controlled by, or are under common
control with that entity. For the purposes of this denition,
“control” means (i) the power, direct or indirect, to cause the
direction or management of such entity, whether by contract or
otherwise, or (ii) ownership of fty percent (50%) or more of the
outstanding shares, or (iii) benecial ownership of such entity.
“You” (or “Your”) shall mean an individual or Legal Entity
exercising permissions granted by this License.
“Source” form shall mean the preferred form for making modications,
including but not limited to software source code, documentation
source, and conguration les.
“Object” form shall mean any form resulting from mechanical
transformation or translation of a Source form, including but
not limited to compiled object code, generated documentation,
and conversions to other media types.
“Work” shall mean the work of authorship, whether in Source or
Object form, made available under the License, as indicated by a
copyright notice that is included in or attached to the work
(an example is provided in the Appendix below).
“Derivative Works” shall mean any work, whether in Source or Object
form, that is based on (or derived from) the Work and for which the
editorial revisions, annotations, elaborations, or other modications
represent, as a whole, an original work of authorship. For the purposes
of this License, Derivative Works shall not include works that remain
separable from, or merely link (or bind by name) to the interfaces of,
the Work and Derivative Works thereof.
“Contribution” shall mean any work of authorship, including
the original version of the Work and any modications or additions
to that Work or Derivative Works thereof, that is intentionally
submitted to Licensor for inclusion in the Work by the copyright owner
or by an individual or Legal Entity authorized to submit on behalf of
the copyright owner. For the purposes of this denition, “submitted”
means any form of electronic, verbal, or written communication sent
to the Licensor or its representatives, including but not limited to
communication on electronic mailing lists, source code control systems,
and issue tracking systems that are managed by, or on behalf of, the
Licensor for the purpose of discussing and improving the Work, but
excluding communication that is conspicuously marked or otherwise
designated in writing by the copyright owner as “Not a Contribution.”
“Contributor” shall mean Licensor and any individual or Legal Entity
on behalf of whom a Contribution has been received by Licensor and
subsequently incorporated within the Work.
2. Grant of Copyright License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
copyright license to reproduce, prepare Derivative Works of,
publicly display, publicly perform, sublicense, and distribute the
Work and such Derivative Works in Source or Object form.
3. Grant of Patent License. Subject to the terms and conditions of
this License, each Contributor hereby grants to You a perpetual,
worldwide, non-exclusive, no-charge, royalty-free, irrevocable
(except as stated in this section) patent license to make, have made,
use, offer to sell, sell, import, and otherwise transfer the Work,
where such license applies only to those patent claims licensable
by such Contributor that are necessarily infringed by their
Contribution(s) alone or by combination of their Contribution(s)
with the Work to which such Contribution(s) was submitted. If You
institute patent litigation against any entity (including a
cross-claim or counterclaim in a lawsuit) alleging that the Work
or a Contribution incorporated within the Work constitutes direct
or contributory patent infringement, then any patent licenses
granted to You under this License for that Work shall terminate
as of the date such litigation is led.
4. Redistribution. You may reproduce and distribute copies of the
Work or Derivative Works thereof in any medium, with or without
modications, and in Source or Object form, provided that You
meet the following conditions:
(a) You must give any other recipients of the Work or
Derivative Works a copy of this License; and
(b) You must cause any modied les to carry prominent notices
stating that You changed the les; and
(c) You must retain, in the Source form of any Derivative Works
that You distribute, all copyright, patent, trademark, and
attribution notices from the Source form of the Work,
excluding those notices that do not pertain to any part of
the Derivative Works; and
(d) If the Work includes a “NOTICE” text le as part of its
distribution, then any Derivative Works that You distribute must
include a readable copy of the attribution notices contained
within such NOTICE le, excluding those notices that do not
pertain to any part of the Derivative Works, in at least one
of the following places: within a NOTICE text le distributed
as part of the Derivative Works; within the Source form or
documentation, if provided along with the Derivative Works; or,
within a display generated by the Derivative Works, if and
wherever such third-party notices normally appear. The contents
of the NOTICE le are for informational purposes only and
do not modify the License. You may add Your own attribution
notices within Derivative Works that You distribute, alongside
or as an addendum to the NOTICE text from the Work, provided
that such additional attribution notices cannot be construed
as modifying the License.
You may add Your own copyright statement to Your modications and
may provide additional or different license terms and conditions
for use, reproduction, or distribution of Your modications, or
for any such Derivative Works as a whole, provided Your use,
reproduction, and distribution of the Work otherwise complies with
the conditions stated in this License.
5. Submission of Contributions. Unless You explicitly state otherwise,
any Contribution intentionally submitted for inclusion in the Work
by You to the Licensor shall be under the terms and conditions of
this License, without any additional terms or conditions.
Notwithstanding the above, nothing herein shall supersede or modify
the terms of any separate license agreement you may have executed
with Licensor regarding such Contributions.
6. Trademarks. This License does not grant permission to use the trade
names, trademarks, service marks, or product names of the Licensor,
except as required for reasonable and customary use in describing the
origin of the Work and reproducing the content of the NOTICE le.
7. Disclaimer of Warranty. Unless required by applicable law or
agreed to in writing, Licensor provides the Work (and each
Contributor provides its Contributions) on an “AS IS” BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
implied, including, without limitation, any warranties or conditions
of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
PARTICULAR PURPOSE. You are solely responsible for determining the
appropriateness of using or redistributing the Work and assume any
risks associated with Your exercise of permissions under this License.
8. Limitation of Liability. In no event and under no legal theory,
whether in tort (including negligence), contract, or otherwise,
unless required by applicable law (such as deliberate and grossly
negligent acts) or agreed to in writing, shall any Contributor be
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
69
Page 71

liable to You for damages, including any direct, indirect, special,
incidental, or consequential damages of any character arising as a
result of this License or out of the use or inability to use the
Work (including but not limited to damages for loss of goodwill,
work stoppage, computer failure or malfunction, or any and all
other commercial damages or losses), even if such Contributor
has been advised of the possibility of such damages.
9. Accepting Warranty or Additional Liability. While redistributing
the Work or Derivative Works thereof, You may choose to offer,
and charge a fee for, acceptance of support, warranty, indemnity,
or other liability obligations and/or rights consistent with this
License. However, in accepting such obligations, You may act only
on Your own behalf and on Your sole responsibility, not on behalf
of any other Contributor, and only if You agree to indemnify,
defend, and hold each Contributor harmless for any liability
incurred by, or claims asserted against, such Contributor by reason
of your accepting any such warranty or additional liability.
END OF TERMS AND CONDITIONS
APPENDIX: How to apply the Apache License to your work.
To apply the Apache License to your work, attach the following
boilerplate notice, with the elds enclosed by brackets “[]”
replaced with your own identifying information. (Don’t include
the brackets!) The text should be enclosed in the appropriate
comment syntax for the le format. We also recommend that a
le or class name and description of purpose be included on the
same “printed page” as the copyright notice for easier
identication within third-party archives.
Copyright [yyyy] [name of copyright owner]
Licensed under the Apache License, Version 2.0 (the “License”);
you may not use this le except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an “AS IS” BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specic language governing permissions and
limitations under the License.
----------------------------------------------------------------------------
-
- Modules: dtc u-boot-socfpga linux-socfpga busybox termcap util-linux
libcap systemd e2fsprogs glib dbus-1 freetype qt5 libpbe
-
----------------------------------------------------------------------------
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.,
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
License is intended to guarantee your freedom to share and change free
software--to make sure the software is free for all its users. This
General Public License applies to most of the Free Software
Foundation’s software and to any other program whose authors commit to
using it. (Some other Free Software Foundation software is covered by
the GNU Lesser General Public License instead.) You can apply it to
your programs, too.
When we speak of free software, we are referring to freedom, not
price. Our General Public Licenses are designed to make sure that you
have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it
if you want it, that you can change the software or use pieces of it
in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid
anyone to deny you these rights or to ask you to surrender the rights.
These restrictions translate to certain responsibilities for you if you
distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether
gratis or for a fee, you must give the recipients all the rights that
you have. You must make sure that they, too, receive or can get the
source code. And you must show them these terms so they know their
rights.
We protect your rights with two steps: (1) copyright the software, and
(2) offer you this license which gives you legal permission to copy,
distribute and/or modify the software.
Also, for each author’s protection and ours, we want to make certain
that everyone understands that there is no warranty for this free
software. If the software is modied by someone else and passed on, we
want its recipients to know that what they have is not the original, so
that any problems introduced by others will not reect on the original
authors’ reputations.
Finally, any free program is threatened constantly by software
patents. We wish to avoid the danger that redistributors of a free
program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any
patent must be licensed for everyone’s free use or not licensed at all.
The precise terms and conditions for copying, distribution and
modication follow.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains
a notice placed by the copyright holder saying it may be distributed
under the terms of this General Public License. The “Program”, below,
refers to any such program or work, and a “work based on the Program”
means either the Program or any derivative work under copyright law:
that is to say, a work containing the Program or a portion of it,
either verbatim or with modications and/or translated into another
language. (Hereinafter, translation is included without limitation in
the term “modication”.) Each licensee is addressed as “you”.
Activities other than copying, distribution and modication are not
covered by this License; they are outside its scope. The act of
running the Program is not restricted, and the output from the Program
is covered only if its contents constitute a work based on the
Program (independent of having been made by running the Program).
Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program’s
source code as you receive it, in any medium, provided that you
conspicuously and appropriately publish on each copy an appropriate
copyright notice and disclaimer of warranty; keep intact all the
notices that refer to this License and to the absence of any warranty;
and give any other recipients of the Program a copy of this License
along with the Program.
You may charge a fee for the physical act of transferring a copy, and
you may at your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion
of it, thus forming a work based on the Program, and copy and
distribute such modications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) You must cause the modied les to carry prominent notices
stating that you changed the les and the date of any change.
b) You must cause any work that you distribute or publish, that in
whole or in part contains or is derived from the Program or any
part thereof, to be licensed as a whole at no charge to all third
parties under the terms of this License.
c) If the modied program normally reads commands interactively
when run, you must cause it, when started running for such
interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a
notice that there is no warranty (or else, saying that you provide
a warranty) and that users may redistribute the program under
these conditions, and telling the user how to view a copy of this
License. (Exception: if the Program itself is interactive but
does not normally print such an announcement, your work based on
the Program is not required to print an announcement.)
These requirements apply to the modied work as a whole. If
identiable sections of that work are not derived from the Program,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Program, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Program.
In addition, mere aggregation of another work not based on the Program
with the Program (or with a work based on the Program) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may copy and distribute the Program (or a work based on it,
under Section 2) in object code or executable form under the terms of
Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable
source code, which must be distributed under the terms of Sections
1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three
years, to give any third party, for a charge no more than your
cost of physically performing source distribution, a complete
machine-readable copy of the corresponding source code, to be
distributed under the terms of Sections 1 and 2 above on a medium
customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer
to distribute corresponding source code. (This alternative is
allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such
an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for
making modications to it. For an executable work, complete source
code means all the source code for all modules it contains, plus any
associated interface denition les, plus the scripts used to
control compilation and installation of the executable. However, as a
special exception, the source code distributed need not include
anything that is normally distributed (in either source or binary
form) with the major components (compiler, kernel, and so on) of the
operating system on which the executable runs, unless that component
itself accompanies the executable.
If distribution of executable or object code is made by offering
access to copy from a designated place, then offering equivalent
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
70
Page 72

access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not
compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program
except as expressly provided under this License. Any attempt
otherwise to copy, modify, sublicense or distribute the Program is
void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under
this License will not have their licenses terminated so long as such
parties remain in full compliance.
5. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Program (or any work based on the
Program), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Program or works based on it.
6. Each time you redistribute the Program (or any work based on the
Program), the recipient automatically receives a license from the
original licensor to copy, distribute or modify the Program subject to
these terms and conditions. You may not impose any further
restrictions on the recipients’ exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties to
this License.
7. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Program at all. For example, if a patent
license would not permit royalty-free redistribution of the Program by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under
any particular circumstance, the balance of the section is intended to
apply and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system, which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Program under this License
may add an explicit geographical distribution limitation excluding
those countries, so that distribution is permitted only in or among
countries not thus excluded. In such case, this License incorporates
the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions
of the General Public License from time to time. Such new versions will
be similar in spirit to the present version, but may differ in detail to
address new problems or concerns.
Each version is given a distinguishing version number. If the Program
species a version number of this License which applies to it and “any
later version”, you have the option of following the terms and conditions
either of that version or of any later version published by the Free
Software Foundation. If the Program does not specify a version number of
this License, you may choose any version ever published by the Free Software
Foundation.
10. If you wish to incorporate parts of the Program into other free
programs whose distribution conditions are different, write to the author
to ask for permission. For software which is copyrighted by the Free
Software Foundation, write to the Free Software Foundation; we sometimes
make exceptions for this. Our decision will be guided by the two goals
of preserving the free status of all derivatives of our free software and
of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
PROVIDE THE PROGRAM “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER
EXPRESSED
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES
ARISING
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY
OTHER
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest
possible use to the public, the best way to achieve this is to make it
free software which everyone can redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest
to attach them to the start of each source le to most effectively
convey the exclusion of warranty; and each le should have at least
the “copyright” line and a pointer to where the full notice is found.
<one line to give the program’s name and a brief idea of what it does.>
Copyright (C) <year> <name of author>
This program is free software; you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation; either version 2 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
You should have received a copy of the GNU General Public License along
with this program; if not, write to the Free Software Foundation, Inc.,
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this
when it starts in an interactive mode:
Gnomovision version 69, Copyright (C) year name of author
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w’.
This is free software, and you are welcome to redistribute it
under certain conditions; type `show c’ for details.
The hypothetical commands `show w’ and `show c’ should show the appropriate
parts of the General Public License. Of course, the commands you use may
be called something other than `show w’ and `show c’; they could even be
mouse-clicks or menu items--whatever suits your program.
You should also get your employer (if you work as a programmer) or your
school, if any, to sign a “copyright disclaimer” for the program, if
necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision’ (which makes passes at compilers) written by James Hacker.
<signature of Ty Coon>, 1 April 1989
Ty Coon, President of Vice
This General Public License does not permit incorporating your program into
proprietary programs. If your program is a subroutine library, you may
consider it more useful to permit linking proprietary applications with the
library. If this is what you want to do, use the GNU Lesser General
Public License instead of this License.
----------------------------------------------------------------------------
-
- Modules: kmod systemd libdaemon avahi libgpg-error libgcrypt gnutls
libmicrohttpd
-
----------------------------------------------------------------------------
GNU LESSER GENERAL PUBLIC LICENSE
Version 2.1, February 1999
Copyright (C) 1991, 1999 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
[This is the rst released version of the Lesser GPL. It also counts
as the successor of the GNU Library Public License, version 2, hence
the version number 2.1.]
Preamble
The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
Licenses are intended to guarantee your freedom to share and change
free software--to make sure the software is free for all its users.
This license, the Lesser General Public License, applies to some
specially designated software packages--typically libraries--of the
Free Software Foundation and other authors who decide to use it. You
can use it too, but we suggest you rst think carefully about whether
this license or the ordinary General Public License is the better
strategy to use in any particular case, based on the explanations below.
When we speak of free software, we are referring to freedom of use,
not price. Our General Public Licenses are designed to make sure that
you have the freedom to distribute copies of free software (and charge
for this service if you wish); that you receive source code or can get
it if you want it; that you can change the software and use pieces of
it in new free programs; and that you are informed that you can do
these things.
To protect your rights, we need to make restrictions that forbid
distributors to deny you these rights or to ask you to surrender these
rights. These restrictions translate to certain responsibilities for
you if you distribute copies of the library or if you modify it.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
71
Page 73

For example, if you distribute copies of the library, whether gratis
or for a fee, you must give the recipients all the rights that we gave
you. You must make sure that they, too, receive or can get the source
code. If you link other code with the library, you must provide
complete object les to the recipients, so that they can relink them
with the library after making changes to the library and recompiling
it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the
library, and (2) we offer you this license, which gives you legal
permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that
there is no warranty for the free library. Also, if the library is
modied by someone else and passed on, the recipients should know
that what they have is not the original version, so that the original
author’s reputation will not be affected by problems that might be
introduced by others.
Finally, software patents pose a constant threat to the existence of
any free program. We wish to make sure that a company cannot
effectively restrict the users of a free program by obtaining a
restrictive license from a patent holder. Therefore, we insist that
any patent license obtained for a version of the library must be
consistent with the full freedom of use specied in this license.
Most GNU software, including some libraries, is covered by the
ordinary GNU General Public License. This license, the GNU Lesser
General Public License, applies to certain designated libraries, and
is quite different from the ordinary General Public License. We use
this license for certain libraries in order to permit linking those
libraries into non-free programs.
When a program is linked with a library, whether statically or using
a shared library, the combination of the two is legally speaking a
combined work, a derivative of the original library. The ordinary
General Public License therefore permits such linking only if the
entire combination ts its criteria of freedom. The Lesser General
Public License permits more lax criteria for linking other code with
the library.
We call this license the “Lesser” General Public License because it
does Less to protect the user’s freedom than the ordinary General
Public License. It also provides other free software developers Less
of an advantage over competing non-free programs. These disadvantages
are the reason we use the ordinary General Public License for many
libraries. However, the Lesser license provides advantages in certain
special circumstances.
For example, on rare occasions, there may be a special need to
encourage the widest possible use of a certain library, so that it becomes
a de-facto standard. To achieve this, non-free programs must be
allowed to use the library. A more frequent case is that a free
library does the same job as widely used non-free libraries. In this
case, there is little to gain by limiting the free library to free
software only, so we use the Lesser General Public License.
In other cases, permission to use a particular library in non-free
programs enables a greater number of people to use a large body of
free software. For example, permission to use the GNU C Library in
non-free programs enables many more people to use the whole GNU
operating system, as well as its variant, the GNU/Linux operating
system.
Although the Lesser General Public License is Less protective of the
users’ freedom, it does ensure that the user of a program that is
linked with the Library has the freedom and the wherewithal to run
that program using a modied version of the Library.
The precise terms and conditions for copying, distribution and
modication follow. Pay close attention to the difference between a
“work based on the library” and a “work that uses the library”. The
former contains code derived from the library, whereas the latter must
be combined with the library in order to run.
GNU LESSER GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License Agreement applies to any software library or other
program which contains a notice placed by the copyright holder or
other authorized party saying it may be distributed under the terms of
this Lesser General Public License (also called “this License”).
Each licensee is addressed as “you”.
A “library” means a collection of software functions and/or data
prepared so as to be conveniently linked with application programs
(which use some of those functions and data) to form executables.
The “Library”, below, refers to any such software library or work
which has been distributed under these terms. A “work based on the
Library” means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a
portion of it, either verbatim or with modications and/or translated
straightforwardly into another language. (Hereinafter, translation is
included without limitation in the term “modication”.)
“Source code” for a work means the preferred form of the work for
making modications to it. For a library, complete source code means
all the source code for all modules it contains, plus any associated
interface denition les, plus the scripts used to control compilation
and installation of the library.
Activities other than copying, distribution and modication are not
covered by this License; they are outside its scope. The act of
running a program using the Library is not restricted, and output from
such a program is covered only if its contents constitute a work based
on the Library (independent of the use of the Library in a tool for
writing it). Whether that is true depends on what the Library does
and what the program that uses the Library does.
1. You may copy and distribute verbatim copies of the Library’s
complete source code as you receive it, in any medium, provided that
you conspicuously and appropriately publish on each copy an
appropriate copyright notice and disclaimer of warranty; keep intact
all the notices that refer to this License and to the absence of any
warranty; and distribute a copy of this License along with the
Library.
You may charge a fee for the physical act of transferring a copy,
and you may at your option offer warranty protection in exchange for a
fee.
2. You may modify your copy or copies of the Library or any portion
of it, thus forming a work based on the Library, and copy and
distribute such modications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) The modied work must itself be a software library.
b) You must cause the les modied to carry prominent notices
stating that you changed the les and the date of any change.
c) You must cause the whole of the work to be licensed at no
charge to all third parties under the terms of this License.
d) If a facility in the modied Library refers to a function or a
table of data to be supplied by an application program that uses
the facility, other than as an argument passed when the facility
is invoked, then you must make a good faith effort to ensure that,
in the event an application does not supply such function or
table, the facility still operates, and performs whatever part of
its purpose remains meaningful.
(For example, a function in a library to compute square roots has
a purpose that is entirely well-dened independent of the
application. Therefore, Subsection 2d requires that any
application-supplied function or table used by this function must
be optional: if the application does not supply it, the square
root function must still compute square roots.)
These requirements apply to the modied work as a whole. If
identiable sections of that work are not derived from the Library,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Library, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote
it.
Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Library.
In addition, mere aggregation of another work not based on the Library
with the Library (or with a work based on the Library) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License.
3. You may opt to apply the terms of the ordinary GNU General Public
License instead of this License to a given copy of the Library. To do
this, you must alter all the notices that refer to this License, so
that they refer to the ordinary GNU General Public License, version 2,
instead of to this License. (If a newer version than version 2 of the
ordinary GNU General Public License has appeared, then you can specify
that version instead if you wish.) Do not make any other change in
these notices.
Once this change is made in a given copy, it is irreversible for
that copy, so the ordinary GNU General Public License applies to all
subsequent copies and derivative works made from that copy.
This option is useful when you wish to copy part of the code of
the Library into a program that is not a library.
4. You may copy and distribute the Library (or a portion or
derivative of it, under Section 2) in object code or executable form
under the terms of Sections 1 and 2 above provided that you accompany
it with the complete corresponding machine-readable source code, which
must be distributed under the terms of Sections 1 and 2 above on a
medium customarily used for software interchange.
If distribution of object code is made by offering access to copy
from a designated place, then offering equivalent access to copy the
source code from the same place satises the requirement to
distribute the source code, even though third parties are not
compelled to copy the source along with the object code.
5. A program that contains no derivative of any portion of the
Library, but is designed to work with the Library by being compiled or
linked with it, is called a “work that uses the Library”. Such a
work, in isolation, is not a derivative work of the Library, and
therefore falls outside the scope of this License.
However, linking a “work that uses the Library” with the Library
creates an executable that is a derivative of the Library (because it
contains portions of the Library), rather than a “work that uses the
library”. The executable is therefore covered by this License.
Section 6 states terms for distribution of such executables.
When a “work that uses the Library” uses material from a header le
that is part of the Library, the object code for the work may be a
derivative work of the Library even though the source code is not.
Whether this is true is especially signicant if the work can be
linked without the Library, or if the work is itself a library. The
threshold for this to be true is not precisely dened by law.
If such an object le uses only numerical parameters, data
structure layouts and accessors, and small macros and small inline
functions (ten lines or less in length), then the use of the object
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
72
Page 74

le is unrestricted, regardless of whether it is legally a derivative
work. (Executables containing this object code plus portions of the
Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may
distribute the object code for the work under the terms of Section 6.
Any executables containing that work also fall under Section 6,
whether or not they are linked directly with the Library itself.
6. As an exception to the Sections above, you may also combine or
link a “work that uses the Library” with the Library to produce a
work containing portions of the Library, and distribute that work
under terms of your choice, provided that the terms permit
modication of the work for the customer’s own use and reverse
engineering for debugging such modications.
You must give prominent notice with each copy of the work that the
Library is used in it and that the Library and its use are covered by
this License. You must supply a copy of this License. If the work
during execution displays copyright notices, you must include the
copyright notice for the Library among them, as well as a reference
directing the user to the copy of this License. Also, you must do one
of these things:
a) Accompany the work with the complete corresponding
machine-readable source code for the Library including whatever
changes were used in the work (which must be distributed under
Sections 1 and 2 above); and, if the work is an executable linked
with the Library, with the complete machine-readable “work that
uses the Library”, as object code and/or source code, so that the
user can modify the Library and then relink to produce a modied
executable containing the modied Library. (It is understood
that the user who changes the contents of denitions les in the
Library will not necessarily be able to recompile the application
to use the modied denitions.)
b) Use a suitable shared library mechanism for linking with the
Library. A suitable mechanism is one that (1) uses at run time a
copy of the library already present on the user’s computer system,
rather than copying library functions into the executable, and (2)
will operate properly with a modied version of the library, if
the user installs one, as long as the modied version is
interface-compatible with the version that the work was made with.
c) Accompany the work with a written offer, valid for at
least three years, to give the same user the materials
specied in Subsection 6a, above, for a charge no more
than the cost of performing this distribution.
d) If distribution of the work is made by offering access to copy
from a designated place, offer equivalent access to copy the above
specied materials from the same place.
e) Verify that the user has already received a copy of these
materials or that you have already sent this user a copy.
For an executable, the required form of the “work that uses the
Library” must include any data and utility programs needed for
reproducing the executable from it. However, as a special exception,
the materials to be distributed need not include anything that is
normally distributed (in either source or binary form) with the major
components (compiler, kernel, and so on) of the operating system on
which the executable runs, unless that component itself accompanies
the executable.
It may happen that this requirement contradicts the license
restrictions of other proprietary libraries that do not normally
accompany the operating system. Such a contradiction means you cannot
use both them and the Library together in an executable that you
distribute.
7. You may place library facilities that are a work based on the
Library side-by-side in a single library together with other library
facilities not covered by this License, and distribute such a combined
library, provided that the separate distribution of the work based on
the Library and of the other library facilities is otherwise
permitted, and provided that you do these two things:
a) Accompany the combined library with a copy of the same work
based on the Library, uncombined with any other library
facilities. This must be distributed under the terms of the
Sections above.
b) Give prominent notice with the combined library of the fact
that part of it is a work based on the Library, and explaining
where to nd the accompanying uncombined form of the same work.
8. You may not copy, modify, sublicense, link with, or distribute
the Library except as expressly provided under this License. Any
attempt otherwise to copy, modify, sublicense, link with, or
distribute the Library is void, and will automatically terminate your
rights under this License. However, parties who have received copies,
or rights, from you under this License will not have their licenses
terminated so long as such parties remain in full compliance.
9. You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Library or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Library (or any work based on the
Library), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Library or works based on it.
10. Each time you redistribute the Library (or any work based on the
Library), the recipient automatically receives a license from the
original licensor to copy, distribute, link with or modify the Librar y
subject to these terms and conditions. You may not impose any further
restrictions on the recipients’ exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties with
this License.
11. If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Library at all. For example, if a patent
license would not permit royalty-free redistribution of the Library by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Library.
If any portion of this section is held invalid or unenforceable under any
particular circumstance, the balance of the section is intended to apply,
and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice.
This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License.
12. If the distribution and/or use of the Library is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Library under this License may add
an explicit geographical distribution limitation excluding those countries,
so that distribution is permitted only in or among countries not thus
excluded. In such case, this License incorporates the limitation as if
written in the body of this License.
13. The Free Software Foundation may publish revised and/or new
versions of the Lesser General Public License from time to time.
Such new versions will be similar in spirit to the present version,
but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library
species a version number of this License which applies to it and
“any later version”, you have the option of following the terms and
conditions either of that version or of any later version published by
the Free Software Foundation. If the Library does not specify a
license version number, you may choose any version ever published by
the Free Software Foundation.
14. If you wish to incorporate parts of the Library into other free
programs whose distribution conditions are incompatible with these,
write to the author to ask for permission. For software which is
copyrighted by the Free Software Foundation, write to the Free
Software Foundation; we sometimes make exceptions for this. Our
decision will be guided by the two goals of preserving the free status
of all derivatives of our free software and of promoting the sharing
and reuse of software generally.
NO WARRANTY
15. BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO
WARRANTY FOR THE LIBRARY, TO THE EXTENT PERMITTED BY APPLICABLE LAW.
EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR
OTHER PARTIES PROVIDE THE LIBRARY “AS IS” WITHOUT WARRANTY OF ANY
KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE
LIBRARY IS WITH YOU. SHOULD THE LIBRARY PROVE DEFECTIVE, YOU ASSUME
THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
16. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN
WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY
AND/OR REDISTRIBUTE THE LIBRARY AS PERMITTED ABOVE, BE LIABLE TO YOU
FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE
LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING
RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A
FAILURE OF THE LIBRARY TO OPERATE WITH ANY OTHER SOFTWARE), EVEN IF
SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Libraries
If you develop a new library, and you want it to be of the greatest
possible use to the public, we recommend making it free software that
everyone can redistribute and change. You can do so by permitting
redistribution under these terms (or, alternatively, under the terms of the
ordinary General Public License).
To apply these terms, attach the following notices to the library. It is
safest to attach them to the start of each source le to most effectively
convey the exclusion of warranty; and each le should have at least the
“copyright” line and a pointer to where the full notice is found.
<one line to give the library’s name and a brief idea of what it does.>
Copyright (C) <year> <name of author>
This library is free software; you can redistribute it and/or
modify it under the terms of the GNU Lesser General Public
License as published by the Free Software Foundation; either
version 2.1 of the License, or (at your option) any later version.
This library is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU
Lesser General Public License for more details.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
73
Page 75

You should have received a copy of the GNU Lesser General Public
License along with this library; if not, write to the Free Software
Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Also add information on how to contact you by electronic and paper mail.
You should also get your employer (if you work as a programmer) or your
school, if any, to sign a “copyright disclaimer” for the library, if
necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the
library `Frob’ (a library for tweaking knobs) written by James Random Hacker.
<signature of Ty Coon>, 1 April 1990
Ty Coon, President of Vice
That’s all there is to it!
----------------------------------------------------------------------------
-
- Modules: libunistring gmp nettle libjwt
-
----------------------------------------------------------------------------
GNU LESSER GENERAL PUBLIC LICENSE
Version 3, 29 June 2007
Copyright (C) 2007 Free Software Foundation, Inc. <https://fsf.org/>
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed.
This version of the GNU Lesser General Public License incorporates
the terms and conditions of version 3 of the GNU General Public
License, supplemented by the additional permissions listed below.
0. Additional Denitions.
As used herein, “this License” refers to version 3 of the GNU Lesser
General Public License, and the “GNU GPL” refers to version 3 of the GNU
General Public License.
“The Library” refers to a covered work governed by this License,
other than an Application or a Combined Work as dened below.
An “Application” is any work that makes use of an interface provided
by the Library, but which is not otherwise based on the Library.
Dening a subclass of a class dened by the Library is deemed a mode
of using an interface provided by the Library.
A “Combined Work” is a work produced by combining or linking an
Application with the Library. The particular version of the Library
with which the Combined Work was made is also called the “Linked
Version”.
The “Minimal Corresponding Source” for a Combined Work means the
Corresponding Source for the Combined Work, excluding any source code
for portions of the Combined Work that, considered in isolation, are
based on the Application, and not on the Linked Version.
The “Corresponding Application Code” for a Combined Work means the
object code and/or source code for the Application, including any data
and utility programs needed for reproducing the Combined Work from the
Application, but excluding the System Libraries of the Combined Work.
1. Exception to Section 3 of the GNU GPL.
You may convey a covered work under sections 3 and 4 of this License
without being bound by section 3 of the GNU GPL.
2. Conveying Modied Versions.
If you modify a copy of the Library, and, in your modications, a
facility refers to a function or data to be supplied by an Application
that uses the facility (other than as an argument passed when the
facility is invoked), then you may convey a copy of the modied
version:
a) under this License, provided that you make a good faith effort to
ensure that, in the event an Application does not supply the
function or data, the facility still operates, and performs
whatever part of its purpose remains meaningful, or
b) under the GNU GPL, with none of the additional permissions of
this License applicable to that copy.
3. Object Code Incorporating Material from Library Header Files.
The object code form of an Application may incorporate material from
a header le that is part of the Library. You may convey such object
code under terms of your choice, provided that, if the incorporated
material is not limited to numerical parameters, data structure
layouts and accessors, or small macros, inline functions and templates
(ten or fewer lines in length), you do both of the following:
a) Give prominent notice with each copy of the object code that the
Library is used in it and that the Library and its use are
covered by this License.
b) Accompany the object code with a copy of the GNU GPL and this license
document.
4. Combined Works.
You may convey a Combined Work under terms of your choice that,
taken together, effectively do not restrict modication of the
portions of the Library contained in the Combined Work and reverse
engineering for debugging such modications, if you also do each of
the following:
a) Give prominent notice with each copy of the Combined Work that
the Library is used in it and that the Library and its use are
covered by this License.
b) Accompany the Combined Work with a copy of the GNU GPL and this license
document.
c) For a Combined Work that displays copyright notices during
execution, include the copyright notice for the Library among
these notices, as well as a reference directing the user to the
copies of the GNU GPL and this license document.
d) Do one of the following:
0) Convey the Minimal Corresponding Source under the terms of this
License, and the Corresponding Application Code in a form
suitable for, and under terms that permit, the user to
recombine or relink the Application with a modied version of
the Linked Version to produce a modied Combined Work, in the
manner specied by section 6 of the GNU GPL for conveying
Corresponding Source.
1) Use a suitable shared library mechanism for linking with the
Library. A suitable mechanism is one that (a) uses at run time
a copy of the Library already present on the user’s computer
system, and (b) will operate properly with a modied version
of the Library that is interface-compatible with the Linked
Version.
e) Provide Installation Information, but only if you would otherwise
be required to provide such information under section 6 of the
GNU GPL, and only to the extent that such information is
necessary to install and execute a modied version of the
Combined Work produced by recombining or relinking the
Application with a modied version of the Linked Version. (If
you use option 4d0, the Installation Information must accompany
the Minimal Corresponding Source and Corresponding Application
Code. If you use option 4d1, you must provide the Installation
Information in the manner specied by section 6 of the GNU GPL
for conveying Corresponding Source.)
5. Combined Libraries.
You may place library facilities that are a work based on the
Library side by side in a single library together with other library
facilities that are not Applications and are not covered by this
License, and convey such a combined library under terms of your
choice, if you do both of the following:
a) Accompany the combined library with a copy of the same work based
on the Library, uncombined with any other library facilities,
conveyed under the terms of this License.
b) Give prominent notice with the combined library that part of it
is a work based on the Library, and explaining where to nd the
accompanying uncombined form of the same work.
6. Revised Versions of the GNU Lesser General Public License.
The Free Software Foundation may publish revised and/or new versions
of the GNU Lesser General Public License from time to time. Such new
versions will be similar in spirit to the present version, but may
differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the
Library as you received it species that a certain numbered version
of the GNU Lesser General Public License “or any later version”
applies to it, you have the option of following the terms and
conditions either of that published version or of any later version
published by the Free Software Foundation. If the Librar y as you
received it does not specify a version number of the GNU Lesser
General Public License, you may choose any version of the GNU Lesser
General Public License ever published by the Free Software Foundation.
If the Library as you received it species that a proxy can decide
whether future versions of the GNU Lesser General Public License shall
apply, that proxy’s public statement of acceptance of any version is
permanent authorization for you to choose that version for the
Library.
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
INDEX
74
Page 76

www.adder.com
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
Documentation by:
www.ctxd.com
INDEX
© 2020 Adder Technology Limited
All trademarks are acknowledged.
Part No. MAN-ALIF4000-ADDER • Release 4.1
75
Page 77

Index
A
Adaptive 52
addresses
default 18
AIM mode 18
Audio
analog and digital 46
Audio EDID 46
C
Cable
null-modem 54
CATx 13
Conguration
browser-based utility 18
Connections
network link 13
overview 9
RX audio 15
RX USB devices 16
RX video display 15
TX audio links 10
TX AUX port 11
TX power in 12
TX USB link 11
TX video link 10
Connectors
overview 6
Cut-through 52
D
Default address 18
E
EDID 46
Extras 8
F
Factory reset 19
Fast-Leave 51
FCoE 13
Forwarding modes 52
Fragment-free 52
Front panel 6
Front panel indicators 24
H
HDR10 4
High Dynamic Range 4
I
IGMP 51
fast-leave 51
querier 51
snooping 51
Indicators 24
IP addresses
default 18
J
Jumbo frames (packets) 51
L
Layers 2 and 3 52
Local feed through 3
LPCM 46
M
Matrix
unmanaged 22
Mounting 9
N
Network address 18
Network layout 47
Network switch
choosing 47
Null-modem cable
pin-out 54
O
OSI model 52
P
P2P mode 18
Point to Point mode 18
Presets
creating and editing 23
Q
Querier 51
R
Rear panel 6
Recovery mode 20
Reset 19
RS232 serial 16
S
SDR 4
SDR8/SDR10 4
SFP port 13
Snooping 51
SoL 18
Spanning Tree Protocol 52
Specications 5
Start of Life 18
Store and forward 52
Switch
choosing 47
conguring 48
T
Touchscreen
dual conguration 21
OSD access 23,25
Troubleshooting 26,49
U
USB-to-serial adaptor 16
V
Video EDID 46
INSTALLATIONCONFIGURATIONOPERATION
FURTHER
INFORMATION
76
INDEX
 Loading...
Loading...