Motorola PTP 100-FSK, PMP 400, PMP 100, PTP 200-OFDM User Manual

Software Release 11.0
Release Notes and User Guide
Supplement
PMP 100 and PTP 100 (FSK)
PMP 400 and PTP 200 (OFDM)
March 2011
Issue 1
Notices
See important regulatory and legal notices in Section 11 on Page 43.
Trademarks, Product Names, and Service Names
MOTOROLA, the stylized M Logo, Canopy, and all other trademarks indicated as such herein are registered trademarks of Motorola Solutions, Inc. ® Reg. US Pat & Tm. Office. All other product or service names are the property of their respective owners.
© 2011 Motorola Solutions, Inc. All rights reserved
http://motorola.wirelessbroadbandsupport.com
Release 11.0 Release Notes and User Guide Supplement
Table of Contents
1 Introduction .......................................................................................................... |
6 |
|
1.1 |
Release 11.0 Overview ................................................................................. |
6 |
1.2 |
Document Change History ............................................................................ |
6 |
1.3 |
Abbreviations ................................................................................................ |
6 |
1.4 |
Feedback on Documentation ........................................................................ |
7 |
1.5 |
Technical Support ......................................................................................... |
7 |
2 |
Applicability .......................................................................................................... |
9 |
|
3 |
Upgrading to Release 11.0 ................................................................................. |
10 |
|
|
3.1 |
Obtaining CNUT Upgrade Packages........................................................... |
10 |
|
3.2 |
Network Management ................................................................................. |
10 |
|
3.3 |
PMP 430 – Options for 5, 10, and 20 MHz Channel Size ............................ |
10 |
4 |
Features .............................................................................................................. |
11 |
|
5 |
RADIUS for PMP ................................................................................................. |
13 |
|
|
5.1 |
RADIUS Implementation Overview ............................................................. |
13 |
|
5.2 |
Configuring AP and SM for RADIUS SM Authentication.............................. |
14 |
|
5.3 |
Handling Certificates ................................................................................... |
17 |
|
5.4 |
Configuring your RADIUS Server for SM Authentication ............................. |
18 |
|
5.5 |
Configuring your RADIUS Server for SM Configuration............................... |
19 |
5.6Configuring AP and SM for Centralized AP and SM User Name and Password
|
Management........................................................................................................ |
21 |
|
|
5.7 |
Configuring your RADIUS Server for Device Access Tracking .................... |
23 |
|
5.8 |
Procedures ................................................................................................. |
23 |
6 |
Resolved Issues ................................................................................................. |
25 |
|
7 |
Known Open Issues ........................................................................................... |
26 |
|
8 |
Notes and Reference .......................................................................................... |
27 |
|
|
8.1 |
Notes .......................................................................................................... |
27 |
|
8.2 |
US Region Code Operation......................................................................... |
31 |
|
8.3 |
PMP 430 Center Channels.......................................................................... |
33 |
|
8.4 |
PMP 100 Series DFS Operation Based on Region Code ............................ |
35 |
|
8.5 |
PTP 100 Series DFS Operation Based on Region Code ............................. |
36 |
Issue 1, March 2011 |
Page 3 |
Release 11.0 Release Notes and User Guide Supplement
|
8.6 PMP 400/430 and PTP 200 DFS Operation Based on Region Code........... |
37 |
|
9 |
Canopy MIB......................................................................................................... |
38 |
|
10 |
Performance Benchmarking Process............................................................... |
39 |
|
|
10.1 |
Definitions................................................................................................... |
39 |
|
10.2 |
System Performance and System Constraints............................................ |
39 |
|
10.3 |
Benchmark Definition ................................................................................. |
41 |
11 |
Regulatory and Legal Notices........................................................................... |
43 |
|
|
11.1 |
Important Note on Modifications ................................................................. |
43 |
|
11.2 |
National and Regional Regulatory Notices.................................................. |
43 |
|
11.3 |
RF Exposure Separation Distances ............................................................ |
52 |
|
11.4 |
Legal Notices.............................................................................................. |
54 |
|
11.5 |
Limit of Liability ........................................................................................... |
56 |
List of Tables
Table 1: Release 11.0 Features .................................................................................. |
11 |
Table 2: Canopy RADIUS Vendor Specific Attributes (VSAs) ...................................... |
19 |
Table 3: Improvements and issues resolved in Release 11.0 ...................................... |
25 |
Table 4: Release 11.0 known open issues .................................................................. |
26 |
Table 5: Notes first discussed with Release 11.0 ........................................................ |
27 |
Table 6: Notes first discussed with Release 10.5 ........................................................ |
27 |
Table 7: Notes first discussed with Release 10.3.1...................................................... |
28 |
Table 8: Notes first discussed with Release 9.5 .......................................................... |
29 |
Table 9: 5-GHz OFDM PMP & PTP U.S. Region Code operation................................ |
32 |
Table 10: 5-GHz FSK PMP & PTP U.S. Region Code operation ................................. |
33 |
Table 11: PMP 430 center channels by channel bandwidth and region code .............. |
34 |
Table 12: PMP 100 AP/SM DFS operation based on region code ............................... |
35 |
Table 13: PTP 100 backhaul operation based on region code..................................... |
36 |
Table 14: PMP 400/430 and PTP 200 DFS operation based on region code............... |
37 |
Table 15: US FCC IDs and Industry Canada Certification Numbers and covered |
|
configurations .............................................................................................. |
44 |
Table 16: China disclosure table ................................................................................. |
51 |
Table 17: Exposure separation distances.................................................................... |
52 |
Table 18: Calculated exposure distances and power compliance margins .................. |
53 |
Issue 1, March 2011 |
Page 4 |
Release 11.0 |
Release Notes and User Guide Supplement |
List of Figures |
|
Figure 1: Applicable products ........................................................................................ |
9 |
Figure 2: AP's Configuration > Security tab ................................................................. |
15 |
Figure 3: SM's Configuration > Security tab ................................................................ |
16 |
Figure 4: Certificate Management on SM's Configuration > Security tab ..................... |
18 |
Figure 5: AP's Account > User Authentication tab ....................................................... |
22 |
Figure 6: SM's Account > User Authentication tab....................................................... |
23 |
Figure 7: PMP AP and PTP BH Region Code Set to United States ............................. |
31 |
Figure 8: PPS Benchmark Test Setup ......................................................................... |
42 |
Issue 1, March 2011 |
Page 5 |

Release 11.0 |
Release Notes and User Guide Supplement |
1 Introduction
1.1RELEASE 11.0 OVERVIEW
Release 11.0 is a general release for all Canopy FSK and OFDM radios, including PMP 100, PMP 400/430, PTP 100, and PTP 200 Series modules.
The primary Release 11.0 feature is SM and AP support for the RADIUS (Remote Authentication Dial In User Service) protocol so that RADIUS can be used for
o SM Authentication
o SM Configuration
o Centralized AP and SM user name and password management For information on other Release 11.0 features see section 4 on page 11.
For information on the RADIUS implementation see section 5 on page 13.
For improvements and issues resolved in Release 11.0 see section 6 on page 25.
For release open issues see section 7 on page 26.
Release 11.0 adds no additional features to BHMs or BHSs, but BHMs and BHSs may be upgraded to Release 11.0 if desired.
IMPORTANT!
Floating licenses are not supported when using RADIUS. If you are using floating licenses, you can upgrade to Release 11.0, but do not use RADIUS authentication mode.
Floating licenses are used in conjunction with Prizm or BAM to provide features to SMs. If you are using floating licenses currently and wish to convert them to fixed licenses so you can use RADIUS, please contact technical support.
Modules should be running Release 9.5 or Release 10.5 before upgrading to Release 11.0.
To upgrade modules and distribute certificates to SMs use CNUT 3.20.16.
To manage modules running Release 11.0, including managing features new to this release, use Wireless Manager 3.0. (Prizm does not support the new features.)
1.2DOCUMENT CHANGE HISTORY
Issue 1 |
First Issue |
1.3ABBREVIATIONS
The following abbreviations and acronyms are used in these notes and related documentation:
AAA |
Authentication, Authorization, and |
BH |
Backhaul Module |
AES |
Accounting |
BHM |
Backhaul Module – Master |
Advanced Encryption Standard |
BHS |
Backhaul Module – Slave |
|
AP |
Access Point |
CA |
Certificate Authority |
BAM |
Bandwidth and Authentication Manager |
CAP |
Access Point Module |
Issue 1, March 2011 |
Page 6 |
Release 11.0 |
Release Notes and User Guide Supplement |
CEPT Conference of European Post and
Telecommunications
CHAP Challenge Handshake Authentication
Protocol
CIR Committed Information Rate
CMM Cluster Management Module
CNUT Canopy Network Updater Tool
CSM Subscriber Module
CRL Certificate Revocation List
DES Data Encryption Standard
DFS Dynamic Frequency Selection
DHCP Dynamic Host Configuration Protocol
DNS Domain Name System
EAP Extensible Authentication Protocol
EIRP Equivalent Isotropically Radiated Power
EFTA European Free Trade Association
EMSK Extended Master Session Key
ETSI European Telecommunications
Standards Institute
EU European Union
FCC US Federal Communications
Commission
FSK Frequency Shift Keying
FTP File Transfer Protocol
GPS Global Positioning System
HPAP High Performance AP (PMP 430 AP)
IC Industry Canada
IETF Internet Engineering Task Force
IP Internet Protocol
ISM Industrial, Scientific, Medical
LAN Local Access Network
MAC Media Access Controller
MIB Management Information Base
MIR Maximum Information Rate
MSCHAPMicrosoft CHAP
MSK |
Master Session Key |
MVID |
Management VID |
NAI |
Network Access Identier |
NAS |
Network Access Server (the AP, in this |
|
system) |
NAT |
Network Address Translation |
OFDM |
Orthogonal Frequency Division |
|
Multiplexing |
OID |
SNMP Object Identifier |
P7/P8/P9/P10/P11 Hardware Series |
|
PAP |
Password Authentication Protocol |
PKI |
Public Key Infrastructure |
PMP |
Point to Multi-Point |
PTP |
Point to Point |
PVID |
Port VID |
RADIUS Remote Authentication Dial In User |
|
|
Service |
RF |
Radio Frequency |
RLAN |
Radio Local Area Network |
SM |
Subscriber Module |
SNMP |
Simple Network Management Protocol |
SNR |
Signal to Noise Ratio |
TCP/IP |
Transmission Control Protocol/Internet |
|
Protocol |
TLS |
Transport Layer Security |
TTLS |
Tunneled TLS |
VDC |
Volts Direct Current |
VID |
VLAN ID |
VLAN |
Virtual LAN |
VSA |
Vendor Specific Attribute |
WAN |
Wide Area Network |
WM |
One Point Wireless Manager |
1.4FEEDBACK ON DOCUMENTATION
Is this document accurate, complete, and clear? How can it be improved? Please send your feedback on Canopy documentation to technical-documentation@canopywireless.com.
1.5TECHNICAL SUPPORT
Tip! Do not clear the Event Log after you encounter issues. It may be useful to Technical Support, if you need to escalate the issue.
Here is the escalation path for resolution of a problem:
1.Check documentation:
These Release Notes
Motorola PMP Solutions Users Guide, available at http://motorola.wirelessbroadbandsupport.com/software.
2.Consider checking the Community Forum and Knowledge Base at http://motorola.wirelessbroadbandsupport.com/support/community.
Issue 1, March 2011 |
Page 7 |
Release 11.0 |
Release Notes and User Guide Supplement |
3.Consider checking the Support Home Page at http://motorola.wirelessbroadbandsupport.com/support/technical.php
4.Escalate the problem to your supplier or reseller.
5.Escalate the problem to Technical Support or other designated Tier 3 technical support:
Email: EMS-EICC-RM@motorolasolutions.com
Phone: |
|
All other countries |
+420 533 336 946 |
U.S. and Canada |
1-866-961-9288 |
Asia and Pacific |
1 800 457 439 |
|
|
Australia |
|
Europe, Middle East, and Africa |
Northern China |
10 800 713 0885 |
|
Denmark |
043682114 |
Southern China |
10 800 130 0867 |
France |
0157323434 |
China, local DID |
+86 21 6108 6109 |
Germany |
06950070204 |
Hong Kong |
30 027 861 |
Italy |
0291483230 |
India |
000 800 100 3098 |
Lithuania |
880 030 828 |
Japan |
221626765 |
Netherlands |
0202061404 |
Japan, PSTN |
(81) 335 708 643 |
Norway |
24159815 |
South Korea |
080 681 0880 |
Portugal |
0217616160 |
Malaysia |
1 800 812 384 |
Spain |
0912754787 |
New Zealand |
0 800 448 472 |
Russia |
810 800 228 41044 |
Philippines |
63 29 003 057 |
Saudi Arabia |
800 844 5345 |
Singapore |
64 155 110 |
South Africa |
0800981900 |
Taiwan |
00 801 14 8690 |
United Kingdom |
0203 0277499 |
Thailand |
001 800 441 0950 |
All other countries |
+420 533 336 946 |
Indonesia |
001 803 015 20 20530 |
Latin and Central America |
All other countries |
+420 533 336 946 |
|
|
|
||
Argentina |
0800-666-2789 |
|
|
Brazil |
0800-891-4360 |
|
|
Columbia |
01-800-912-0557 |
|
|
Mexico |
001-800-942-7721 |
|
|
Peru |
0800-70-086 |
|
|
When you send e-mail or call, please include, as appropriate, software release on each module, IP addresses, MAC addresses, and features enabled, like NAT, VLAN, high priority channel, or CIR. You may be asked to run the Support Tool on CNUT or Prizm to provide a complete network picture.
Issue 1, March 2011 |
Page 8 |

Release 11.0 |
Release Notes and User Guide Supplement |
2 Applicability
Release 11.0 is a general release recommended for all the products shown in Figure 1.
Modulation and |
PMP Radio Series |
PTP Radio Series |
Module Type |
(Point-to-MultiPoint) |
(Point-To-Point) |
|
PMP 100 Series |
PTP 100 Series |
|
|
|
FSK |
Frequencies: 900MHz, |
Frequencies: |
AP/SM/BH |
2.4, 5.1, 5.2, 5.4, 5.7, |
2.4, 5.2, 5.4, 5.7-GHz |
|
5.9, 6.050-GHz |
|
|
Note: P7 and P8 APs |
Note: P7 and P8 BHs |
|
cannot be upgraded |
cannot be upgraded |
|
Note: AES P7 and P8 |
|
|
SMs cannot be upgraded |
|
|
(All DES SMs can be) |
|
|
|
|
|
PMP 430 Series |
N/A |
OFDM |
|
|
AP/SM |
|
|
|
|
|
|
Frequencies: |
N/A |
|
5.4-GHz PMP 54430 |
|
|
5.8-GHz PMP 58430 |
|
|
|
|
|
PMP 400 Series |
PTP 200 Series |
OFDM |
|
|
AP/SM/BH |
|
|
|
|
|
|
Frequencies: |
Frequencies: |
|
4.9-GHz PMP 49400 |
4.9-GHz PTP 49200 |
|
5.4-GHz PMP 54400 |
5.4-GHz PTP 54200 |
|
|
|
Figure 1: Applicable products
Not all products are available in all markets. Please check with your local reseller for availability.
Issue 1, March 2011 Page 9
Release 11.0 |
Release Notes and User Guide Supplement |
3 Upgrading to Release 11.0
Upgrade first to R11.0 then enable RADIUS settings if desired (or not). In most cases operators will want to upgrade to R11.0, then trial a friendly sector with RADIUS, then deploy RADIUS to their entire network.
R11.0 does not require using RADIUS. If upgrading a network from an old release, upgrading to R11.0 is recommended, even if not using RADIUS, so as to take advantage of features and fixes through R11.0.
Use version 3.20.16 of the Network Updater Tool (CNUT) to upgrade to Release 11.0. Version 3.20.16 supports distribution of certificates to SMs.
CNUT and its release notes can be downloaded from the Motorola wireless broadband support web site: http://motorola.wirelessbroadbandsupport.com/software/
Modules in operating sectors should be on Release 9.5 or 10.5 before upgrading to avoid upgrade issues.
3.1OBTAINING CNUT UPGRADE PACKAGES
To download the Canopy software to your computer, perform the following steps:
1.Go to http://motorola.wirelessbroadbandsupport.com/software.
2.Follow the directions on that page to access the software download page.
3.On the software download page, select the appropriate package or packages. Options include
CANOPY11BUILDOFFICIAL_DES.pkg3
CANOPY11BUILDOFFICIAL_AES.pkg3
CANOPY11BUILDOFFICIAL_OFDM_DES.pkg3
CANOPY11BUILDOFFICIAL_OFDM_AES.pkg3
4.Click Accept User Agreement and Request Download Links.
RESULT: You will receive an email with a link or links to the software.
5.In the email sent to you, click on the desired link or links.
RESULT: The appropriate.pkg3 package or packages will download to your computer.
For additional information on using CNUT, see the CNUT help file or click on the Help menu in the CNUT application.
3.2NETWORK MANAGEMENT
Use One Point Wireless Manager to manage Motorola PMP and PTP networks, including managing the RADIUS features. For additional information, see http://motorola.wirelessbroadbandsupport.com/support/opws/software/
3.3PMP 430 – OPTIONS FOR 5, 10, AND 20 MHZ CHANNEL SIZE
PMP 430 APs and SMs ship with software with a 10-MHz channel size. This can be changed to 5 or 20 MHz using CNUT. For an operating sector, use CNUT to change the channel size of the SMs first, then the AP. For SMs being deployed into an operating sector, use CNUT to set the channel size before deploying the SMs.
To set the channel size, use the Update > Configure > HPAP Channel Bandwidth menu on CNUT. See the latest CNUT release notes for additional information.
Issue 1, March 2011 |
Page 10 |
Release 11.0 Release Notes and User Guide Supplement
4 Features
Release 11.0 adds the features listed in Table 1.
Table 1: Release 11.0 Features
Regions |
Products |
Feature |
Description |
See for |
Affected |
Affected |
|
|
Details |
All Regions |
AP and SM |
Support for the |
RADIUS can be used for SM authentication, |
Section 5 |
|
|
RADIUS protocol. |
SM configuration, and centralized AP and |
|
|
|
|
SM user name and password management. |
|
|
|
|
|
|
All Regions |
AP and SM |
From AP GUI or |
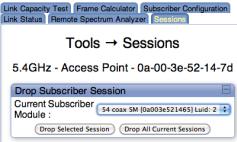
From the AP’s Tools > Sessions tab, |
- |
|
|
SNMP, drop all |
sessions to all SMs in the sector can be |
|
|
|
sessions in the |
dropped. This forces all SMs in the sector to |
|
|
|
sector. |
register again to an AP. Note that a session |
|
|
|
|
to a single selected SM can also be |
|
|
|
|
dropped. |
|
|
|
|
|
|
All Regions |
SM with NAT |
Data entry checking |
Data entry checking now prevents |
- |
|
enabled |
|
mistakenly setting the same IP address for |
|
|
|
|
both the LAN Interface and the Remote |
|
|
|
|
Configuration Interface on an SM with NAT |
|
|
|
|
enabled. These parameters are configured |
|
|
|
|
on the SM’s Configuration > NAT tab. |
|
|
|
|
|
|
All Regions |
PMP 100 |
Can configure 40 mile |
On the AP’s Configuration > Radio tab, the |
- |
|
|
max range on FSK |
Max Range can now be configured up to 40 |
|
|
|
AP. |
miles (instead of the previous max of 30 |
|
|
|
|
miles). Note, this does not change the |
|
|
|
|
transmit power of the radio, does not change |
|
|
|
|
the RF operation, and due to the additional |
|
|
|
|
turnaround time in the frame will reduce |
|
|
|
|
capacity and throughput to some degree. |
|
|
|
|
|
|
All Regions |
PMP 100 |
Can configure SM |
On the AP’s Configuration > Radio tab, the |
- |
|
|
receive target level up |
SM Receive Target Level can now be |
|
|
|
to -40 dBm on FSK |
configured up to -40 dBm (instead of the |
|
|
|
AP. |
previous limit of -55 dBm). Note, this does |
|
|
|
|
not change the transmitter power of the AP, |
|
|
|
|
nor the sensitivity of the AP or the SM – it |
|
|
|
|
just allows a “hotter” SM receive target level |
|
|
|
|
if RF design requires it. |
|
|
|
|
|
|
Issue 1, March 2011 |
Page 11 |

Release 11.0 |
|
Release Notes and User Guide Supplement |
||
|
|
|
|
|
Regions |
Products |
Feature |
Description |
See for |
Affected |
Affected |
|
|
Details |
All Regions |
AP and SM |
Display AP’s site |
On the SM’s Home > General Status tab, |
- |
|
|
name on SM |
the Registered AP field now displays the |
|
|
|
|
SNMP Site Name of the AP as well as the |
|
|
|
|
AP’s MAC address. (SNMP Site Names are |
|
|
|
|
configured on a radio’s Configuration > |
|
|
|
|
SNMP tab in the Site Name field.) |
|
Issue 1, March 2011 |
Page 12 |
Release 11.0 |
Release Notes and User Guide Supplement |
5 RADIUS for PMP
Release 11.0 adds support for the RADIUS (Remote Authentication Dial In User Service) protocol supporting Authentication, Authorization, and Accounting (AAA). The following topics are covered in this document:
o An overview of the Canopy RADIUS implementation
oDescription of the operation of RADIUS with Canopy and the various configurable parameters and their settings
o Procedures for specific tasks associated with configuring Canopy for RADIUS o Reference material, especially information on VSAs and OIDs.
The information does not
oProvide substantial background on the RADIUS protocol. A solid understanding of RADIUS is assumed, or should be gained from other sources.
oProvide detailed information on setting up a RADIUS server. This information should be gained from other sources, including the vendor or provider of the RADIUS server.
A typical course of action to prepare for the migration to RADIUS is
o Study these release notes
oGain any additional knowledge needed on RADIUS and your specific RADIUS server from outside sources and install your RADIUS server and database.
o Experiment with a test system in the lab or field o Develop a migration plan for your network
o Migrate your network to RADIUS
5.1RADIUS IMPLEMENTATION OVERVIEW
5.1.1RADIUS Functions
RADIUS protocol support provides the following functions:
oSM Authentication allows only known SMs onto the network (blocking “rogue” SMs), and can be configured to ensure SMs are connecting to a known network (preventing SMs from connecting to “rogue” APs). RADIUS authentication is used for SMs, but not used for APs, BHMs, or BHSs.
oSM Configuration configures authenticated SMs with MIR (Maximum Information Rate), CIR (Committed Information Rate), High Priority, and VLAN (Virtual LAN) parameters from the RADIUS server when an SM registers to an AP.
oCentralized AP and SM user name and password management allows AP and SM usernames and access levels (Administrator, Installer, Technician) to be centrally administered in the RADIUS server instead of on each radio and tracks access events (logon/logoff) for each username on the RADIUS server. BHMs and BHSs do not support RADIUS accounting. This accounting does not track and report specific configuration actions performed on radios or pull statistics such as bit counts from the radios. Such functions require an Element Management System (EMS) such as the Motorola One Point Wireless Manager. This accounting is not the ability to perform accounting functions on the subscriber/end user/customer account.
Issue 1, March 2011 |
Page 13 |
Release 11.0 |
Release Notes and User Guide Supplement |
5.1.2Tested RADIUS Servers
The Canopy RADIUS implementation has been tested and is supported on o FreeRADIUS, Version 2.1.8
oAradial RADIUS, Version 5.1.12
Note, Aradial 5.3 has a bug that prevents “remote device login”, so doesn’t support the user name and password management feature.
5.2CONFIGURING AP AND SM FOR RADIUS SM AUTHENTICATION
Configuring Canopy for RADIUS authentication requires configuring both the AP and the SMs.
5.2.1AP - Choosing Authentication Mode and Configuring for Authentication Servers
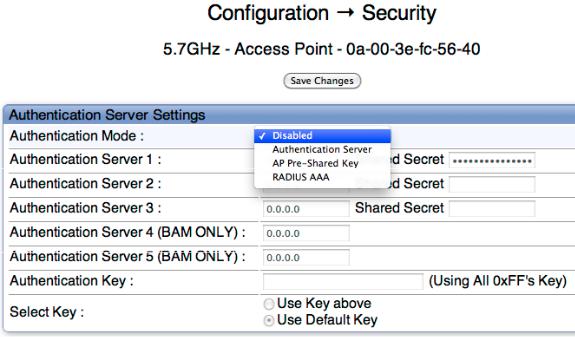
On the AP’s Configuration > Security tab as shown in Figure 2: AP's Configuration > Security tab, select the RADIUS AAA Authentication Mode. The following describes the other Authentication Mode options for reference, and then the RADIUS AAA option.
Disabled
Requires no authentication. Any SM (except an SM that itself has been configured to require RADIUS authentication by enabling Lock AAA as described below) will be allowed to register to the AP.
Authentication Server (BAM)
Authentication Server in this instance refers to BAM. Authentication with BAM will be required for an SM to register to the AP. Only SMs listed by MAC address in the BAM database will be allowed to register to the AP.
When Authentication Server is selected, up to 5 Authentication Server (BAM) IP addresses can be configured. The IP address(es) configured here must match the IP address(es) of the BAM(s).
AP Pre-Shared Key
Canopy offers a pre-shared key authentication option. In this case, an identical key must be entered in the Authentication Key field on the AP’s Configuration > Security tab and in the Authentication Key field on each desired SM’s Configuration > Security tab.
RADIUS AAA
To support RADIUS authentication of SMs, on the AP’s Configuration > Security tab select RADIUS AAA. Only properly configured SMs with a valid certificate will be allowed to register to the AP.
Issue 1, March 2011 |
Page 14 |
Release 11.0 |
Release Notes and User Guide Supplement |
When RADIUS AAA is selected, up to 3 Authentication Server (RADIUS Server) IP addresses and Shared Secrets can be configured. The IP address(es) configured here must match the IP address(es) of the RADIUS server(s). The shared secret(s) configured here must match the shared secret(s) configured in the RADIUS server(s). Servers 2 and 3 are meant for backup and reliability, not splitting the database. If Server 1 doesn’t respond, Server 2 is tried, and then server 3. If Server 1 rejects authentication, the SM is denied entry to the network, and does not progress trying the other servers.
The default IP address is 0.0.0.0 (which obviously won’t match any RADIUS server). The default Shared Secret is “CanopySharedSecret”. The Shared Secret can be up to 32 ASCII characters (no diacritical marks or ligatures, for example).
Figure 2: AP's Configuration > Security tab
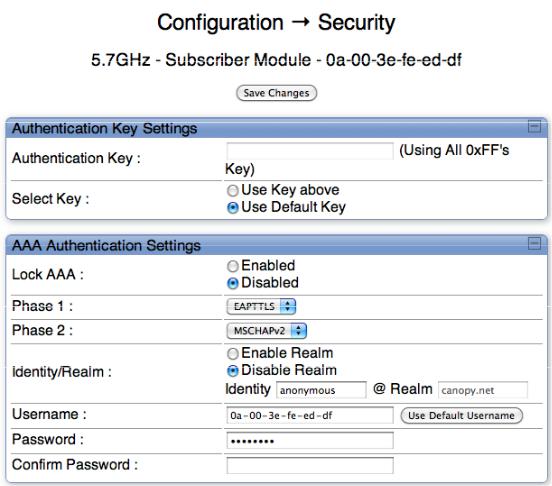
5.2.2 SM Authentication Mode – Require RADIUS or Follow AP
Refer to Figure 3: SM's Configuration > Security tab to see the GUI options.
If it is desired that an SM will only authenticate to an AP that is using RADIUS, on the SM’s Configuration Security tab set Lock AAA to Enabled. With Lock AAA enabled, an SM will not register to an AP that has any Authentication Mode other than RADIUS AAA selected.
If it is desired that an SM use the authentication method configured on the AP it is registering to, set Lock AAA to Disabled. With Lock AAA disabled, an SM will attempt to register using whichever Authentication Mode is configured on the AP it is attempting to register to.
Note, requiring SMs to use RADIUS by enabling Lock AAA avoids the security issue of SMs possibly registering to “rogue” APs which have authentication disabled.
Issue 1, March 2011 |
Page 15 |
Release 11.0 |
Release Notes and User Guide Supplement |
Figure 3: SM's Configuration > Security tab
5.2.3 SM - Phase 1 (Outside Identity) parameters and settings
Refer to Figure 3: SM's Configuration > Security tab to see the GUI options.
The only protocol supported for the Phase 1 (Outside Identity) phase of authentication is EAPTTLS (Extensible Authentication Protocol Tunneled Transport Layer Security).
Configure an outer Identity in the Username field. This must match the Phase 1/Outer Identity username configured in the RADIUS server. The default Phase 1/Outer Identity Username is “anonymous”. The Username can be up to 128 non-special (no diacritical markings) alphanumeric characters.
If Realms are being used, select Enable Realm and configure an outer identity in the Identity field and a Realm in the Realm field. These must match the Phase 1/Outer Identity and Realm configured in the RADIUS server. The default Identity is “anonymous”. The Identity can be up to 128 non-special (no diacritical markings) alphanumeric characters. The default Realm is “canopy.net”. The Realm can also be up to 128 non-special alphanumeric characters.
5.2.4 SM - Phase 2 (Inside Identity) parameters and settings
Refer to Figure 3: SM's Configuration > Security tab to see the GUI options.
Issue 1, March 2011 |
Page 16 |
Release 11.0 |
Release Notes and User Guide Supplement |
Select the desired Phase 2 (Inside Identity) authentication protocol from the Phase 2 options of PAP (Password Authentication Protocol), CHAP (Challenge Handshake Authentication Protocol), and MSCHAP (Microsoft’s version of CHAP, version 2 is used). The protocol must be consistent with the authentication protocol configured on the RADIUS server.
Enter a Username for the SM. This must match the username configured for the SM on the RADIUS server. The default Username is the SM’s MAC address. The Username can be up to 128 non-special (no diacritical markings) alphanumeric characters.
Enter the desired password for the SM in the Password and Confirm Password fields.. The Password must match the password configured for the SM on the RADIUS server. The default Password is “password”. The Password can be up to 128 non-special (no diacritical markings) alphanumeric characters.
5.3HANDLING CERTIFICATES
5.3.1Certificate management on SMs.
The default public Canopy and PMP 320 certificates are loaded into SMs automatically during the upgrade to Release 11.0. The default certificates are not secure and are intended for use during lab and field trials as part of gaining experience with the RADIUS functionality, or as an option during debug. For secure operation, an operator will want to create or procure their own certificates.
Refer to Figure 4: Certificate Management on SM's Configuration > Security tab to see the GUI options.
Up to 2 certificates can be resident on an SM. An installed certificate can be deleted by clicking the Delete button in the certificate’s description block on the Configuration > Security tab. To restore fhe 2 default certificates, click the Use Default Certificates button in the RADIUS Certificate Settings parameter block and reboot the radio.
To upload a certificate manually to an SM, first load it in a known place on your PC or network drive, then click on a Delete button on one of the Certificate description blocks to delete a certificate to provide space for your certificate. Click on Choose File, browse to the location of the certificate, and click the Import Certificate button, and then reboot the radio to use the new certificate.
When a certificate is in use, after the SM successfully registers to an AP, an indication of In Use will appear in the description block of the certificate being used.
The public certificates installed on the SMs are used with the private certificate on the RADIUS server to provide a public/private key encryption system.
Issue 1, March 2011 |
Page 17 |
 Loading...
Loading...