Page 1

KGS-810F
Web Smart 8-Port Gigabit Ethernet Switch
with 1 mini-GBIC Port
,
User
s Manual
DOC.111205
-1-
Page 2

(C) 2008 KTI Networks Inc. All rights reserved. No part of this documentation may be reproduced in any form
or by any means or used to make any directive work (such as translation or transformation) without permission
from KTI Networks Inc.
KTI Networks Inc. reserves the right to revise this documentation and to make changes in content from time to
time without obligation on the part of KTI Networks Inc. to provide notification of such revision or change.
For more information, contact:
United States KTI Networks Inc.
P.O. BOX 631008
Houston, Texas 77263-1008
Phone: 713-2663891
Fax: 713-2663893
E-mail: kti@ktinet.com
URL: http://www.ktinet.com/
International Fax: 886-2-26983873
E-mail: kti@ktinet.com.tw
URL: http://www.ktinet.com.tw/
-2-
Page 3

The information contained in this document is subject to change without prior notice. Copyright (C) All Rights
Reserved.
TRADEMARKS
Ethernet is a registered trademark of Xerox Corp.
FCC NOTICE
This device complies with Class A Part 15 the FCC Rules. Operation is subject to the following two conditions:
(1) This device may not cause harmful interference, and (2) this device must accept any interference received
including the interference that may cause.
CE NOTICE
Marking by the symbol indicates compliance of this equipment to the EMC directive of the European
Community. Such marking is indicative that this equipment meets or exceeds the following technical
standards:
EMC Class A
EN 50081-1/1992 : EN55022:1994/A1:1995/A2:1997 Class A
EN61000-3-2:2000
EN61000-3-3:1995/A1:2001
EN 55024:1998/A1:2001
IEC 61000-4-2:1995
IEC 61000-4-3:1995
IEC 61000-4-4:1995
IEC 61000-4-5:1995
IEC 61000-4-6:1996
IEC 61000-4-8:1993
IEC 61000-4-11:1994
-3-
Page 4

Table of Contents
1. Introduction...................................................................................................................................7
1.1 Features................................................................................................................8
1.2 Product Panels...................................................................................................... 8
1.3 LED Indicators ...................................................................................................... 9
1.4 Specifications........................................................................................................9
2. Installation...................................................................................................................................12
2.1 Unpacking........................................................................................................... 12
2.2 Safety Cautions................................................................................................... 12
2.3 Mounting the Switch on a Wall............................................................................ 13
2.4 Mounting the Switch on a Din-rail Chassis..........................................................13
2.5 Applying Power................................................................................................... 14
2.6 Reset Button .......................................................................................................15
2.7 Making UTP Connections ................................................................................... 15
2.8 Making Fiber Connection.................................................................................... 16
2.9 LED Indication..................................................................................................... 17
2.10 Configuring IP Address and Password for the Switch.......................................17
3. Advanced Functions..................................................................................................................18
3.1 Abbreviation........................................................................................................ 18
3.2 QoS Function...................................................................................................... 19
3.2.1 Packet Priority Classification............................................................................ 20
3.2.2 Priority Class Queues ...................................................................................... 20
3.2.3 Egress Service Policy ...................................................................................... 20
3.3 VLAN Function....................................................................................................21
3.3.1 VLAN Operation............................................................................................... 21
3.3.2 Ingress Rules................................................................................................... 21
3.3.2.1 802.1Q Tag Aware Per port setting...............................................................21
3.3.2.2 Keep Tag Per port setting............................................................................. 21
3.3.2.3 Drop Untagged Per Port Setting ................................................................... 22
3.3.2.4 Drop Tagged Per Port Setting....................................................................... 22
-4-
Page 5

3.3.3 Ingress Default Tag Per Port Setting ............................................................... 22
3.3.4 Packet Tag Information....................................................................................22
3.3.5 VLAN Group Table Configuration ....................................................................23
3.3.6 VLAN Classification ......................................................................................... 23
3.3.7 Packet Forwarding........................................................................................... 23
3.3.8 Egress Tagging Rules...................................................................................... 24
3.3.8.1 Egress Settings.............................................................................................24
3.3.9 Summary of VLAN Function............................................................................. 24
3.4 802.1X Authentication.........................................................................................25
4. Web Management.......................................................................................................................26
4.1 Start Browser Software and Making Connection ................................................26
4.2 Login to the Switch Unit ...................................................................................... 26
4.3 Main Management Menu .................................................................................... 27
4.4 System................................................................................................................ 29
4.4.1 Management VLAN.......................................................................................... 31
4.5 Ports.................................................................................................................... 32
4.5.1 Port Type ......................................................................................................... 33
4.5.2 SFP DDM Status.............................................................................................. 34
4.6 VLANs.................................................................................................................35
4.6.1 Port-based VLAN Mode...................................................................................36
4.6.2 Port-based VLAN ISP Mode ............................................................................ 37
4.6.3 Advanced VLAN Mode..................................................................................... 38
4.6.3.1 Ingress Default Tag....................................................................................... 39
4.6.3.2 Ingress Settings............................................................................................ 40
4.6.3.3 Egress Settings.............................................................................................42
4.6.3.4 VLAN Groups................................................................................................ 44
4.6.4 Important Notes for VLAN Configuration.......................................................... 45
4.7 Aggregation......................................................................................................... 46
4.8 LACP................................................................................................................... 47
4.9 RSTP .................................................................................................................. 48
4.10 802.1X Configuration ........................................................................................ 50
4.10.1 802.1X Re-authentication Parameters........................................................... 51
-5-
Page 6

4.11 Mirroring............................................................................................................52
4.12 Quality of Service.............................................................................................. 53
4.12.1 802.1p Mapping ............................................................................................. 54
4.12.2 DSCP Mapping .............................................................................................. 55
4.12.3 QoS Service Policy ........................................................................................ 56
4.13 Storm Control.................................................................................................... 58
4.14 Statistics Overview............................................................................................ 59
4.15 Detailed Statistics..............................................................................................60
4.16 LACP Status ..................................................................................................... 61
4.17 Ping...................................................................................................................63
4.18 Reboot System ................................................................................................. 63
4.19 Restore Default................................................................................................. 64
4.20 Update Firmware .............................................................................................. 64
4.21 Logout............................................................................................................... 64
5. SNMP Support ............................................................................................................................65
Appendix. Factory Default Settings..............................................................................................66
-6-
Page 7

1. Introduction
The KGS-810F is a managed Gigabit Ethernet switch which is featured with the following switched ports:
Seven 10/100/1000Mbps Gigabit copper ports
One combo port - 10/100/1000Mbps copper & 1000Base-X SFP
and the following advantages in a small footprint box:
Plug and Play
The switch is shipped with factory default configuration which behaves like an unmanaged Gigabit switch for
workgroup. It provides eight 10/100/1000Mbps copper ports for connections to Ethernet, Fast Ethernet, and
Gigabit Ethernet devices. With the featured auto-negotiation function, the switch can detect and configure the
connection speed and duplex automatically. The switch also provides auto MDI/MDI-X function, which can
detect the connected cable and switch the transmission wire pair and receiving pair automatically. This
auto-crossover function can simplify the type of network cables used.
Fiber Connectivity
The combo port provides one 1000M SFP slot, which can be installed with an optional SFP optical fiber
transceiver to support one Gigabit 1000Base-X fiber connection when needed.
Web Management
The switch is embedded with an Http server which provides management functions for advanced network
functions including Port Control, Quality of Service, and Virtual LAN functions. The management can be
performed via Web browser based interface over TCP/IP network.
Quality of Service
For advanced application, the switch is featured with powerful Quality of Service (QoS) function which can
classify the priority for received network frames based on the ingress port and frame contents. Furthermore,
many service priority policies can be configured for egress operation in per-port basis.
Virtual LAN (VLAN)
For increasing Tagged VLAN applications, the switch is also featured with powerful VLAN function to fulfill
the up-to-date VLAN requirements. The switch supports both port-based VLAN and tagged VLAN in per-port
basis.
802.1x Authentication
IEEE 802.1X port-based network access control function provide a means of authenticating and authorizing
devices attached to the switched port that has point-to-point connection characteristics, and of preventing
access to that port in cases in which the authentication and authorization process fails.
-7-
Page 8
1.1 Features
Provides 8 10/100/1000Mbps RJ-45 and one 1000M SFP slot
Provides in-band web-based and SNMP management interface
Copper ports support auto-negotiation and auto-MDI/MDI-X detection.
Provides full wire speed forwarding
Supports 802.3x flow control for full-duplex and backpressure for half-duplex
Provides port status, statistic monitoring and control function
Supports DHCP IP configuration
Supports port-based and 802.1Q Tag-based VLAN
Provides QoS function
Provides link aggregation (port trunking) function with LACP support
Provides port mirroring function
Provides 802.1X authentication for port access
Supports 802.1w RSTP, 802.1D STP and 802.1S MSTP
Watchdog timer function
Supports SFP with Digital Diagnostic Monitoring (DDM)
Provides packet storm control function
In-band embedded firmware upgrade function
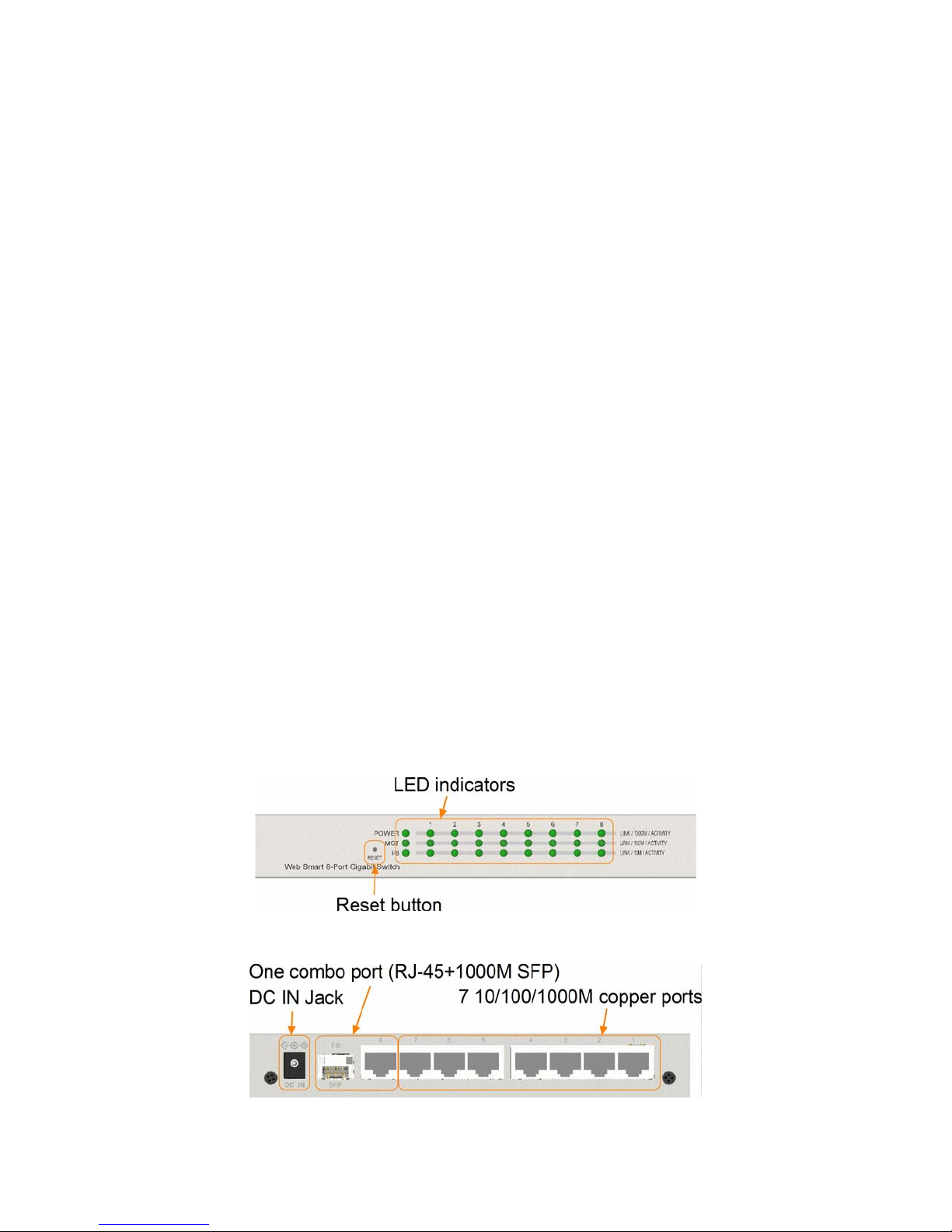
1.2 Product Panels
The following figure illustrates the front panel and rear panel of the switch:
Front panel
Rear panel
-8-
Page 9

1.3 LED Indicators
LED Function
POWER Power status
MGT Management status
LNK/1000M/ACT Network port 1000M link status (Port 1 - Port 8)
LNK/100M/ACT Network port 100M link status (Port 1 - Port 8)
LNK/10M/ACT Network port 10M link status (Port 1 - Port 8)
FX8 SFP Fiber is selected on Port 8
1.4 Specifications
10/100/1000 Copper Ports
Compliance IEEE 802.3 10Base-T, IEEE 802.3u 100Base-TX, IEEE 802.3u 1000Base-T
Connectors Shielded RJ-45 jacks
Pin assignments Auto MDI/MDI-X detection
Configuration Auto-negotiation or software control
Transmission rate 10Mbps, 100Mbps, 1000Mbps
Duplex support Full/Half duplex
Network cable Cat.5 UTP
Combo Port with 10/100/1000 RJ-45 and 1000Mbps Mini-GBIC SFP
Copper interface
Compliance IEEE 802.3 10Base-T, IEEE 802.3u 100Base-TX,
IEEE 802.3u 1000Base-T
Connectors Shielded RJ-45 jacks
Pin assignments Auto MDI/MDI-X detection
Configuration Auto-negotiation or software control
Transmission rate 10Mbps, 100Mbps, 1000Mbps
Duplex support Full/Half duplex
Network cable Cat.5 UTP
Fiber interface
Compliance IEEE 802.3z 1000Base-SX/LX (mini-GBIC)
Connectors SFP for optional SFP type fiber transceivers
Configuration Auto/Forced, 1000Mbps, Full duplex
Transmission rate 1000Mbps
Network cables MMF 50/125 60/125, SMF 9/125
Eye safety IEC 825 compliant
-9-
Page 10
Switch Functions
MAC Addresses Table 8K entries
Forwarding & filtering Non-blocking, full wire speed
Switching technology Store and forward
Maximum packet length 1526 bytes (when Jumbo frame support disabled)
Flow control IEEE 802.3x pause frame base for full duplex operation
Back pressure for half duplex operation
VLAN function Port-based VLAN and IEEE 802.1Q Tag-based VLAN
QoS function Port-based, 802.1p-based, IP DSCP-based
Port control Port configuration control via software management
Storm control Broadcast, Multicast storm protection control via software management
Aggregation Link aggregation (port trunking)
Port Mirroring Mirror received frames to a sniffer port
Software Management Functions
Interfaces Web browser
Management objects System configuration - IP settings, Name, Password
Port configuration control and status
VLAN function settings
Port Link Aggregation function settings
Link Aggregation LACP settings
RSTP settings
802.1X port access control
Port mirroring settings
QoS function settings
Storm protection control settings
Port statistic, LACP status, RSTP status
Reboot, restore factory default, update firmware
-10-
Page 11

DC Power Input
Interfaces DC Jack ( -D 6.3mm / + D 2.0mm)
Operating Input Voltages +6 ~ +12.6VDC
Power Consumption 7.3W max. @7.5V
Mechanical
Dimension (base) 180 x 114 x 26 mm
Housing Enclosed metal with no fan
Mounting Desktop mounting, wall mounting, Din-rail mounting
Environmental
o
Operating Temperature Typical -5
Storage Temperature -20
o
C ~ 80oC
C ~ 50oC
Relative Humidity 10% ~ 90%
Electrical Approvals
FCC Part 15 rule Class A
CE EMC, CISPR22 Class A
-11-
Page 12

2. Installation
2.1 Unpacking
The product package contains:
The switch unit
One power adapter
One product CD-ROM
2.2 Safety Cautions
To reduce the risk of bodily injury, electrical shock, fire and damage to the product, observe the following
precautions.
Do not service any product except as explained in your system documentation.
Opening or removing covers may expose you to electrical shock.
Only a trained service technician should service components inside these compartments.
If any of the following conditions occur, unplug the product from the electrical outlet and replace the part
or contact your trained service provider:
- The power cable, extension cable, or plug is damaged.
- An object has fallen into the product.
- The product has been exposed to water.
- The product has been dropped or damaged.
- The product does not operate correctly when you follow the operating instructions.
Do not push any objects into the openings of your system. Doing so can cause fire or electric shock by
shorting out interior components.
Operate the product only from the type of external power source indicated on the electrical ratings label. If
you are not sure of the type of power source required, consult your service provider or local power
company.
-12-
Page 13
2.3 Mounting the Switch on a Wall
The switch can be mounted on a desktop or shelf or a wall. Make sure that there is proper heat dissipation from
and adequate ventilation around the device. Do not place heavy objects on the device.
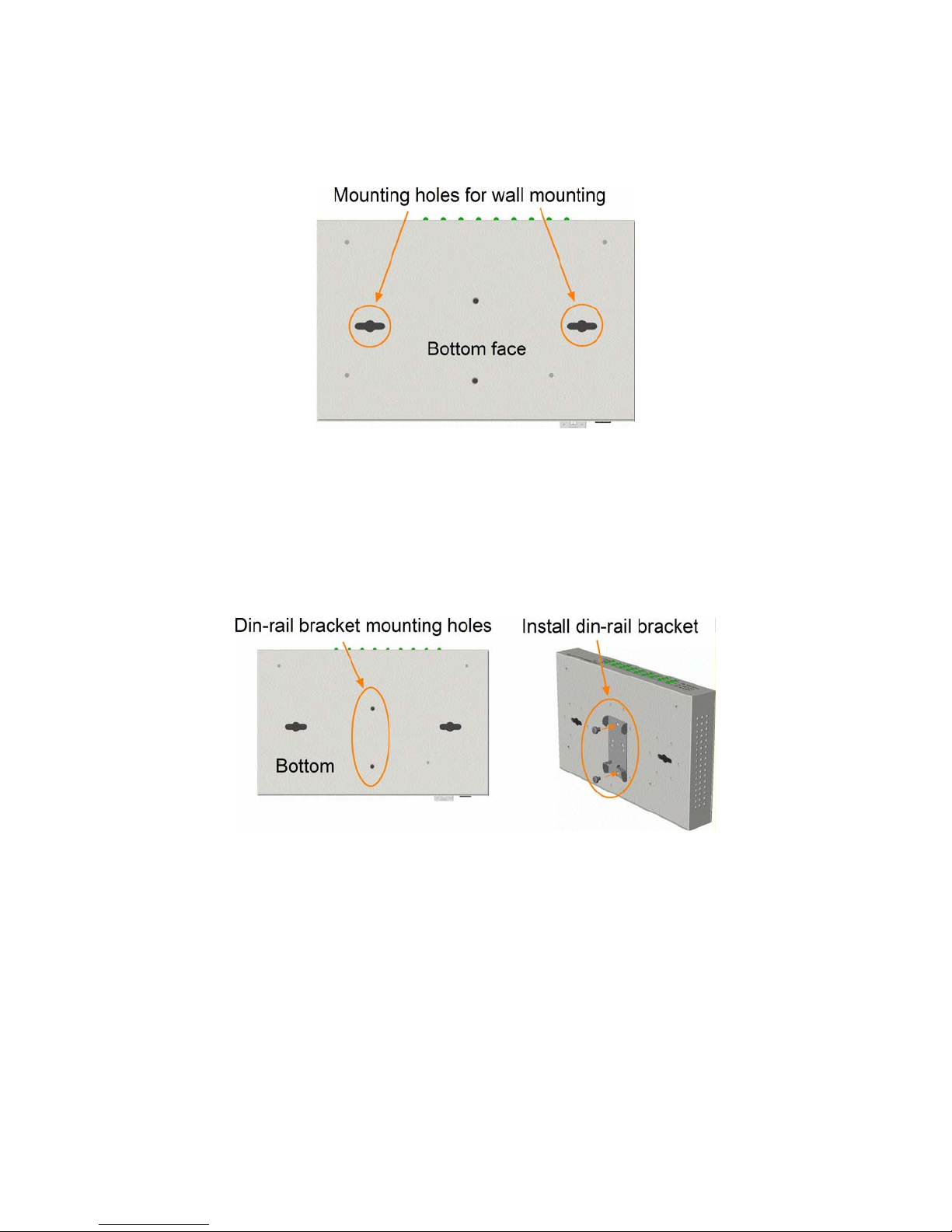
2.4 Mounting the Switch on a Din-rail Chassis
The switch also can be mounted on a din-rail chassis.
The steps are:
1. Screw the din-rail mounting bracket on the bottom of the switch.
2. Mount the units on a din-rail chassis
The din-rail mounting bracket is optional. Consult the place where you purchased the product.
-13-
Page 14

2.5 Applying Power
Before you begin the installation, check the AC voltage of your area. The AC power adapter which is used to
supply the DC power for the unit should have the AC voltage matching the commercial power voltage in your
area.
The AC Power Adapter Specifications
AC input power: AC power voltage of your area, options Rated AC100 - 240V/47-63Hz DC7.5V 1.2A
The steps to apply the power to the product are:
1. Connect power adapter DC plug to the DC input jack located on the back of the unit before connecting to the
AC outlet.
2. Connect the power adapter to the AC outlet.
3. Check Power LED indication.
Note: Before you begin the installation, check the AC voltage of your area. The AC power adapter which is
used to supply the DC power for the unit should have the AC voltage matching the commercial power voltage
in your area.
-14-
Page 15

2.6 Reset Button
The reset button is used to perform a reset to the switch. It is not used in normal cases and can be used for
diagnostic purpose. If any network hanging problem is suspected, it is useful to push the button to reset the
switch without turning off the power. Check whether the network is recovered.
The button can also be used to restore the software configuration settings to factory default values.
The operations are:
Operation Function
Press the button more than 5 seconds when power up Restore all factory default settings
Press the button and release during switch operation Reboot the switch
2.7 Making UTP Connections
The 10/100/1000 RJ-45 copper ports support the following connection types and distances:
Network Cables
10BASE-T: 2-pair UTP Cat. 3, 4, 5, EIA/TIA-568B 100-ohm
100BASE-TX: 2-pair UTP Cat. 5, EIA/TIA-568B 100-ohm
1000BASE-T: 4-pair UTP Cat. 5 or higher (Cat.5e is recommended), EIA/TIA-568B 100-ohm
Link distance: Up to 100 meters
Auto MDI/MDI-X Function
This function allows the port to auto-detect the twisted-pair signals and adapts itself to form a valid MDI to
MDI-X connection with the remote connected device automatically. No matter a straight through cable or
crossover cable are connected, the ports can sense the receiving pair automatically and configure themselves to
match the rule for MDI to MDI-X connection. It simplifies the cable installation.
Auto-negotiation Function
The ports are featured with auto-negotiation function and full capability to support connection to any Ethernet
devices. The port performs a negotiation process for the speed and duplex configuration with the connected
device automatically when each time a link is being established. If the connected device is also
auto-negotiation capable, both devices will come out the best configuration after negotiation process. If the
connected device is incapable in auto-negotiation, the switch will sense the speed and use half duplex for the
connection.
Port Configuration Management
For making proper connection to an auto-negotiation incapable device, it is suggested to use port control
function via software management to set forced mode and specify speed and duplex mode which match the
configuration used by the connected device.
-15-
Page 16

2.8 Making Fiber Connection
The SFP slot must be installed with an SFP fiber transceiver for making fiber connection. Your switch may
come with some SFP transceivers pre-installed when it is shipped.
Installing SFP Fiber Transceiver
To install an SFP fiber transceiver into SFP slot, the steps are:
1. Turn off the power to the switch.
2. Insert the SFP fiber transceiver into the SFP slot. Normally, a bail is provided for every SFP transceiver.
Hold the bail and make insertion.
3. Until the SFP transceiver is seated securely in the slot, place the bail in lock position.
Connecting Fiber Cables
LC connectors are commonly equipped on most SFP transceiver modules. Identify TX and RX connector
before making cable connection. The following figure illustrates a connection example between two fiber
ports:
Make sure the Rx-to-Tx connection rule is followed on the both ends of the fiber cable.
Network Cables
Multimode (MMF) - 50/125μm, 62.5/125 μm
Single mode (SMF) - 9/125 μm
Fiber Port Configuration
For 1000M fiber application on Port 8, just leave the default port configuration Auto for fiber connection.
-16-
Page 17

2.9 LED Indication
LED Function State Interpretation
POWER Power status ON The power is supplied to the switch.
OFF The power is not supplied to the switch.
MGT Management status OFF The switch is in initialization.
ON The switch is initialized completely.
LNK/1000M/ACT Port link status ON A 1000Mbps link is established. (No traffic)
BLINK Port link is up and there is traffic.
OFF Port link is down.
LNK/100M/ACT Port link status ON A 100Mbps link is established. (No traffic)
BLINK Port link is up and there is traffic.
OFF Port link is down.
LNK/10M/ACT Port link status ON A 10Mbps link is established. (No traffic)
BLINK Port link is up and there is traffic.
OFF Port link is down.
FX8 FX8 status OFF RJ-45 copper connection is selected on Port 8.
ON SFP fiber connection is selected on Port 8.
2.10 Configuring IP Address and Password for the Switch
The switch is shipped with the following factory default settings for software management:
Default IP address of the switch: 192.168.0.2 / 255.255.255.0
The IP Address is an identification of the switch in a TCP/IP network. Each switch should be designated a new
and unique IP address in the network. Refer to Web management interface for System Configuration.
The switch is shipped with factory default password 123 for software management.
The password is used for authentication in accessing to the switch via Http web-based interface. For security
reason, it is recommended to change the default settings for the switch before deploying it to your network.
Refer to Web management interface for System Configuration.
-17-
Page 18

3. Advanced Functions
To help a better understanding about the software management interfaces, this chapter describes some
advanced functions provided by the switch.
3.1 Abbreviation
Ingress Port: Ingress port is the input port on which a packet is received.
Egress Port: Egress port is the output port from which a packet is sent out.
IEEE 802.1Q Packets: A packet which is embedded with a VLAN Tag field
VLAN Tag: In IEEE 802.1Q packet format, 4-byte tag field is inserted in the original Ethernet frame between
the Source Address and Type/Length fields. The tag is composed of:
#of bits 16 3 1 12
Frame field TPID User priority CFI VID
TPID: 16-bit field is set to 0x8100 to identify a frame as an IEEE 802.1Q tagged packet
User Priority: 3-bit field refer to the 802.1p priority
CFI: The Canonical Format Indicator for the MAC address is a 1 bit field.
VID: VLAN identifier, 12-bit field identifies the VLAN to which the frame belongs to.
Untagged packet: A standard Ethernet frame with no VLAN Tag field
Priority-tagged packet: An IEEE 802.1Q packet which VID filed value is zero (VID=0)
VLAN-Tagged packet: An IEEE 802.1Q packet which VID filed value is not zero (VID<>0)
PVID (Port VID): PVID is the default VID of an ingress port. It is often used in VLAN classification for
untagged packets. It is also often used for egress tagging operation.
DSCP: Differentiated Service Code Point, 6-bit value field in an IP packet
VLAN Table lookup: The process of searching VLAN table to find a VLAN which matches the given VID index
MAC address table lookup: The process of searching MAC address table to find a MAC entry which matches
the given destination MAC address and the port where the MAC address is located
Packet forwarding: also known as packet switching in a network switch based on MAC address table and
VLAN table information
VLAN forwarding: the operation that a packet is forwarded to an egress destination port based on VLAN
table information
VLAN group: configuration information about a VLAN which can be recognized in the switch. The
information includes a VID associated to the VLAN, member ports, and some special settings.
-18-
Page 19

3.2 QoS Function
The switch provides a powerful Quality of Service (QoS) function to guide the packet forwarding in four
priority classes. The versatile classification methods can meet most of the application needs. The following
figure illustrates the QoS operation flow when a packet received on the ingress port until it is transmitted out
from the egress port:
-19-
Page 20

3.2.1 Packet Priority Classification
Each received packet is examined and classified into one of four priority classes, Class 3, Class 2, Class 1 and
Class 0 upon reception. The switch provides the following classification methods:
802.1p classification
class
: use User Priority tag value in the received IEEE 802.1Q packet to map to one priority
DSCP classification
Port-based classification: used when 802.1p and DSCP are disabled or fail to be applied
They all can be configured to be activated or not. More than one classification methods can be enabled at the
same time. However, 802.1p classification is superior than DSCP classification.
802.1p mapping tables
DSCP mapping table
Default port priority: A port default priority class is used when port-based classification is applied
All configuration settings are in per port basis except that DSCP mapping table is global to all ports. A received
packet is classified into one of four priority class before it is forwarded to an egress port.
: use DSCP value in the received IP packet to map to one priority class
: Each ingress port has its own mapping table for 802.1p classification.
: All ingress ports share one DSCP mapping table for DSCP classification.
3.2.2 Priority Class Queues
Each egress port in the switch is equipped with four priority class egress queues to store the packets for
transmission. A packet is stored into the class queue which is associated to the classified priority class. For
example, a packet is stored into Class 3 egress queue if it is classified as priority Class 3.
3.2.3 Egress Service Policy
Each port can be configured with an egress service policy to determine the transmission priority among four
class queues. By default, higher class number has higher priority than the lower class numbers.
Four policies are provided for selection as follows:
Strict priority: Packets in high priority class queue are sent first until the queue is empty
Weighted ratio priority Class 3:2:1:0 = 4:3:2:1: four queues are served in 4:3:2:1 ratio
Weighted ratio priority Class 3:2:1:0 = 5:3:1:1: four queues are served in 5:3:1:1 ratio
Weighted ratio priority Class 3:2:1:0 = 1:1:1:1: four queues are served equally
Strict priority policy lets high priority class queue is served first until it is empty. Lower priority queue may not
get any service (or egress bandwidth) when higher priority traffic is heavy for long time. Three weighted ratio
policies are provided to resolve such problem. Four class queues are served in weighted round robin basis.
Every priority class can get a guaranteed ratio for the egress bandwidth.
-20-
Page 21

3.3 VLAN Function
The switch supports port-based VLAN, 802.1Q Tag VLAN and eight VLAN groups.
3.3.1 VLAN Operation
The following figure illustrates the basic VLAN operation flow beginning from a packet received on an ingress
port until it is transmitted from an egress port.
The following sections describe the VLAN processes and Advanced VLAN mode settings provided by the
switch. A global setting means the setting is applied to all ports of the switch. A per port setting means each
port can be configured for the setting respectively.
3.3.2 Ingress Rules
When a packet is received on an ingress port, the ingress rules are applied for packet filtering and packet tag
removal. The related Ingress port settings are:
3.3.2.1 802.1Q Tag Aware Per port setting
Tag-aware - 802.1Q Tag Aware mode is used. The switch examines the tag content of every received packet.
For a VLAN tagged packet, the packet VLAN tag data is retrieved as packet tag information for
VLAN classification and egress tagging operation. For untagged packet and priority-tagged packet,
port-based mode is used.
Tag-ignore - Port-based mode is used. The switch ignores the tag content of every received packet. Ingress Port
Default Tag is always used as packet tag information for VLAN classification.
3.3.2.2 Keep Tag Per port setting
Enable - The VLAN tag in the received VLAN tagged packet will be kept as it is and is not stripped in
whole forwarding operation.
Disable - The VLAN tag data in the received VLAN tagged packet is stripped (removed).
-21-
Page 22

3.3.2.3 Drop Untagged Per Port Setting
Enable - All untagged packets and priority-tagged packets are dropped. A priority-tagged packet is treated
as an untagged packet in this switch. Only VLAN-tagged packets are admitted.
Disable - Disable Untagged packet filtering
3.3.2.4 Drop Tagged Per Port Setting
Enable - All VLAN-tagged packets are dropped. A priority-tagged packet is treated as an untagged packet
in this switch. Only untagged packets are admitted.
Disable - Disable VLAN-tagged packet filtering
3.3.3 Ingress Default Tag Per Port Setting
Each port can be configured with one Ingress Default Tag. This ingress port default tag is used when ingress
port is in
includes
Tag-ignore mode or for the received untagged packets in Tag-aware mode. The Ingress Default Tag
PVID, CFI and User Priority configuration.
When Ingress port default tag is used, it is copied as packet associated Packet Tag Information for VLAN
classification. The PVID is used as index to one VLAN group in VLAN group table.
3.3.4 Packet Tag Information
Under VLAN process, every packet is associated with one Packet’s Tag information in packet forwarding
operation. The tag information includes VID, CFI and User Priority data and is used for two purposes:
The VID in tag is used as index for VLAN classification.
The tag is used for egress tag insertion if egress tagging is enabled.
The following table lists how the Packet Tag information is generated:
Tag Aware setting Received Packet Type Packet Tag information source
Tag-ignore Untagged packet Ingress Port Default Tag
Tag-ignore
Tag-ignore
Priority-tagged packet Ingress Port Default Tag
VLAN-tagged packet Ingress Port Default Tag
Tag-aware Untagged packet Ingress Port Default Tag
Tag-aware
Priority-tagged packet Ingress Port Default Tag
Tag-aware VLAN-tagged packet Received packet VLAN Tag
-22-
Page 23

3.3.5 VLAN Group Table Configuration
The switch provides a table of eight VLAN groups to support up to eight VLANs at the same time. Each
VLAN group is associated to one unique VLAN. The table is referred for VLAN classification.
A VLAN group contains the following configuration settings:
: 12-bit VLAN Identifier index to the VLAN to which the group is associated
VID
Member Ports
Source Port Check: the ingress port of the packet must also be the member port of this VLAN. Otherwise, the
packet is discarded.
: the admitted egress ports for packets belonging to this VLAN
3.3.6 VLAN Classification
VLAN classification is a process to classify a VLAN group to which a received packet belongs. The VID of the
generated Packet Tag information associated to the received packet is used as an index for VLAN group table
lookup. The VID matched VLAN group will be used for packet forwarding. If no matched VLAN group is
found in table lookup, the packet is dropped.
Refer to section 3.2.4 for details about how the Packet Tag information is generated.
The member ports specified in the matched VLAN group are the admitted egress port range for the packet. The
packet will never be forwarded to other ports which are not in the member ports.
The Source Port Check setting of the matched VLAN group is also referred. If it is enabled, the ingress port
will be checked whether it is a member port of this group.
3.3.7 Packet Forwarding
The forwarding is a process to forward the received packet to one or more egress ports. The process uses the
following information as forwarding decision:
Member ports of the matched VLAN group: the egress port range for forwarding
Source Port Check setting of the matched VLAN group: check ingress port membership
Packet destination MAC address: for MAC address table loop up
Switch MAC address table: to find the associated port where a MAC address is learned
If the MAC address table lookup is matched and the learned port is the VLAN member port, the packet is
forwarded to the port (egress port). If the lookup failed, the switch will broadcast the packet to all member
ports.
-23-
Page 24

3.3.8 Egress Tagging Rules
Egress Tagging rules are used to make change to the packet before it is stored into egress queue of an egress
port. Three egress settings are provided for each port and are described as follows:
3.3.8.1 Egress Settings
Insert Tag (per port setting)
Enable - Insert the Tag data of the associated Packet Tag information into the packet
Disable - No tagging is performed.
Untagging Specific VID (per port setting)
Enable - No tag insertion if the VID data of the associated Packet Tag information matches the Untagged
VID configured in next setting even [Insert Tag] is enabled.
Disable - This rule is not applied.
3.3.9 Summary of VLAN Function
VLAN Modes
Port-based VLAN Mode:
Port-based VLAN ISP Mode: simple port-based 5-VLAN-groups mode
Advanced VLAN Mode: Full VLAN configuration for port-based and Tag-based VLAN
Advanced VLAN Mode
Egress Settings (per port):
Ingress Default Tag (per port):
VLAN Groups (global): 8 VLAN groups
VLAN Group Settings (per group):
Egress Settings:
VLAN range supported: 1 ~ 4095 (eight VLANs at the same time)
[PVID] [VID] [Untagged VID] value range: 1 ~ 4095
[Insert Tag], [Untagging Specific VID], [Untagged VID]
simple port-based 2-VLAN-groups mode
[Tag Aware], [Keep Tag], [Drop Untag], [Drop Tag]
[PVID], [CFI], [User Pr io r ity]
[VID], [Member Ports], [Source Port Check]
-24-
Page 25
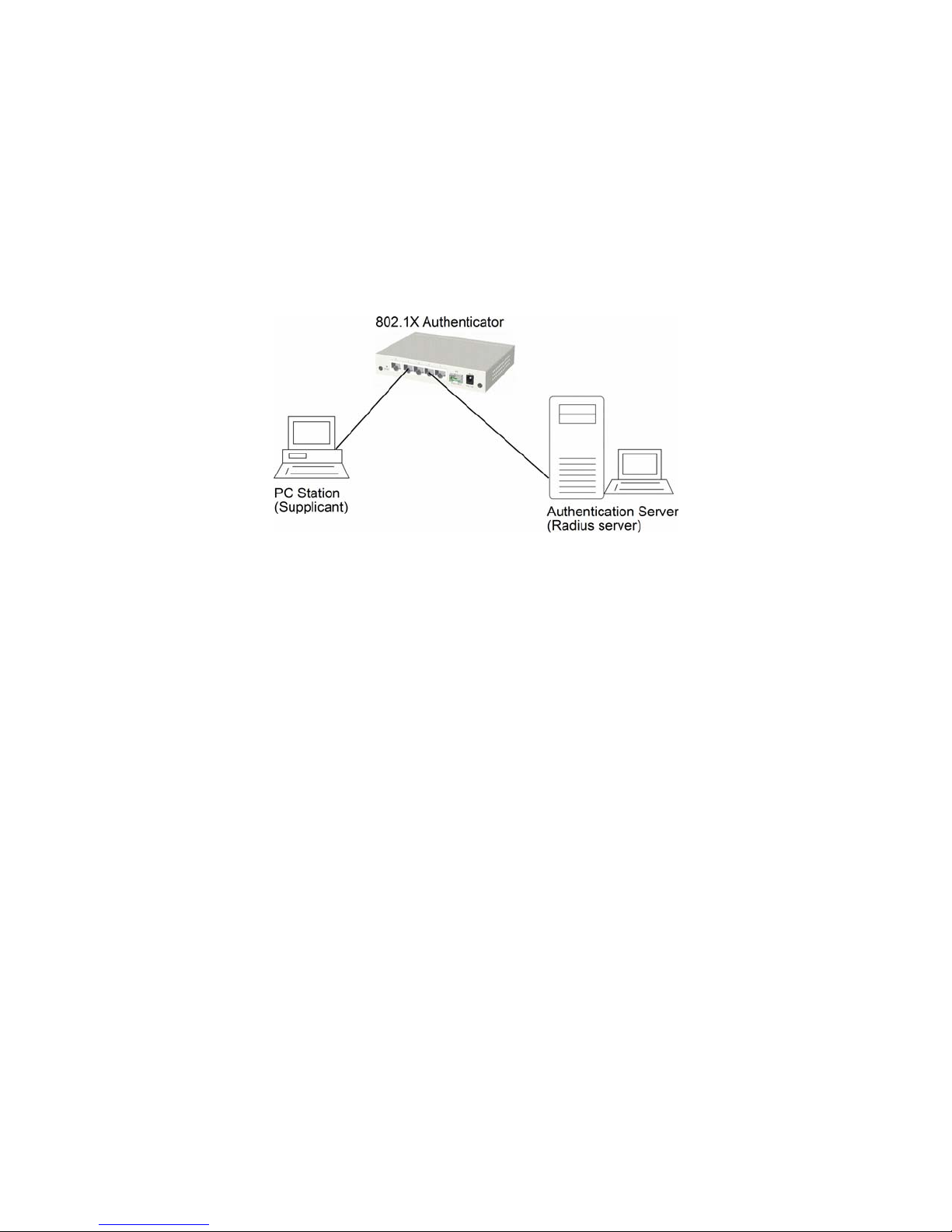
3.4 802.1X Authentication
For some IEEE 802 LAN environments, it is desirable to restrict access to the services offered by the LAN to
those users and devices that are permitted to make use of those services. IEEE 802.1X Port-based network
access control function provide a means of authenticating and authorizing devices attached to a LAN port that
has point-to-point connection characteristics, and of preventing access to that port in cases in which the
authentication and authorization process fails. The 802.1X standard relies on the client to provide credentials in
order to gain access to the network. The credentials are not based on a hardware address. Instead, they can be
either a username/password combination or a certificate. The credentials are not verified by the switch but are
sent to a Remote Authentication Dial-In User Service (RADIUS) server, which maintains a database of
authentication information. 802.1X consists of three components for authentication exchange, which are as
follows:
An 802.1X authenticator: This is the port on the switch that has services to offer to an end device, provided
the device supplies the proper credentials.
An 802.1X supplicant: This is the end device; for example, a PC that connects to a switch that is requesting
to use the services (port) of the device. The 802.1X supplicant must be able to respond to communicate.
An 802.1X authentication server: This is a RADIUS server that examines the credentials provided to the
authenticator from the supplicant and provides the authentication service. The authentication server is
responsible for letting the authenticator know if services should be granted.
The 802.1X authenticator operates as a go-between with the supplicant and the authentication server to provide
services to the network. When a switch is configured as an authenticator, the ports of the switch must then be
configured for authorization. In an authenticator-initiated port authorization, a client is powered up or plugs
into the port, and the authenticator port sends an Extensible Authentication Protocol (EAP) PDU to the
supplicant requesting the identification of the supplicant. At this point in the process, the port on the switch is
connected from a physical standpoint; however, the 802.1X process has not authorized the port and no frames
are passed from the port on the supplicant into the switching engine. If the PC attached to the switch did not
understand the EAP PDU that it was receiving from the switch, it would not be able to send an ID and the port
would remain unauthorized. In this state, the port would never pass any user traffic and would be as good as
disabled. If the client PC is running the 802.1X EAP, it would respond to the request with its configured ID.
(This could be a username/password combination or a certificate.)
After the switch, the authenticator receives the ID from the PC (the supplicant). The switch then passes the ID
information to an authentication server (RADIUS server) that can verify the identification information. The
RADIUS server responds to the switch with either a success or failure message. If the response is a success, the
port will be authorized and user traffic will be allowed to pass through the port like any switch port connected
to an access device. If the response is a failure, the port will remain unauthorized and, therefore, unused. If
there is no response from the server, the port will also remain unauthorized and will not pass any traffic.
-25-
Page 26
4. Web Management
The switch features an http server which can serve the management requests coming from any web browser
software over TCP/IP network.
Web Browser
Compatible web browser software with JAVA script support
Microsoft Internet Explorer 4.0 or later
Netscape Communicator 4.x or later
Set IP Address for the System Unit
Before the switch can be managed from a web browser software, make sure a unique IP address is configured
for the switch.
4.1 Start Browser Software and Making Connection
Start your browser software and enter the IP address of the switch unit to which you want to connect. The IP
address is used as URL for the browser software to search the device.
URL: http://xxx.xxx.xxx.xxx/
Factory default IP address: 192.168.0.2
4.2 Login to the Switch Unit
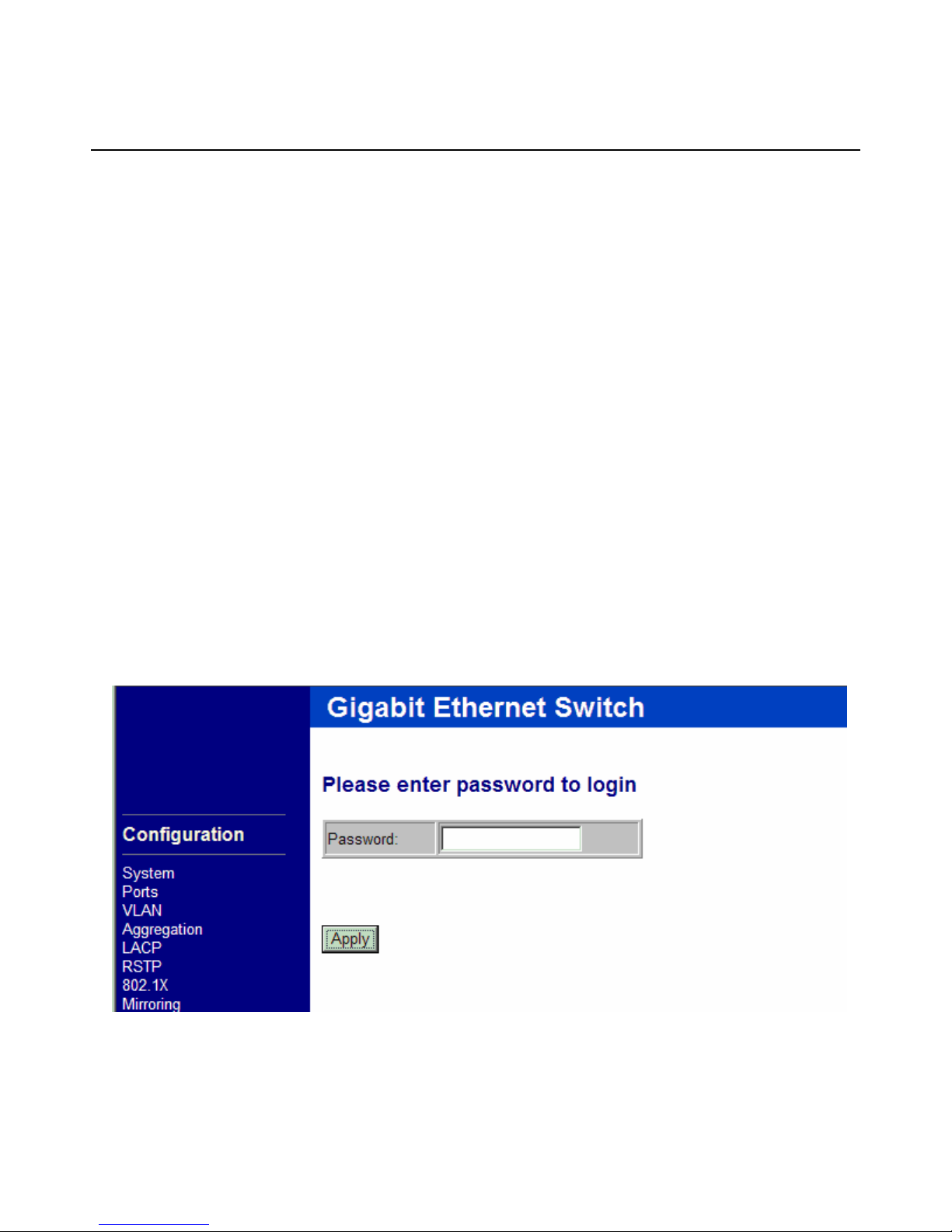
When browser software connects to the switch unit successfully, a Login screen is provided for you to login to
the device as the left display below:
The switch will accept only one successful management connection at the same time. The other connection
attempts will be prompted with a warning message as the right display above.
-26-
Page 27
A new connection will be accepted when the current user logout successfully or auto logout by the switch due
to no access for time out of 3 minutes.
System Configuration is displayed after a successful login.
4.3 Main Management Menu
Configuration
System Switch information, system and IP related settings
Ports Port link status, port operation mode configuration
VLAN VLAN related configuration
Aggregation Port link aggregation (port trunking) related configuration
LACP LACP configuration for port link aggregation
RSTP RSTP (Rapid spanning tree protocol) related configuration
802.1X 802.1X authentication related configuration
-27-
Page 28

Mirroring Port mirroring related configuration
QoS Quality of Service related configuration
Storm Control Packet Storm protection control configuration
Monitoring
Statistics Overview List simple statistics for all ports
Detailed Statistics List detailed statistics for all ports
LACP Status LACP port status
RSTP Status RSTP protocol status
Ping Ping command from the switch to other IP devices
Maintenance
Reboot System Command to reboot the switch
Restore Default Co mmand to restore the switch with factory default settings
Update Firmware Co mmand to update the switch firmware
Logout Command to logout from the switch management
-28-
Page 29
4.4 System
-29-
Page 30

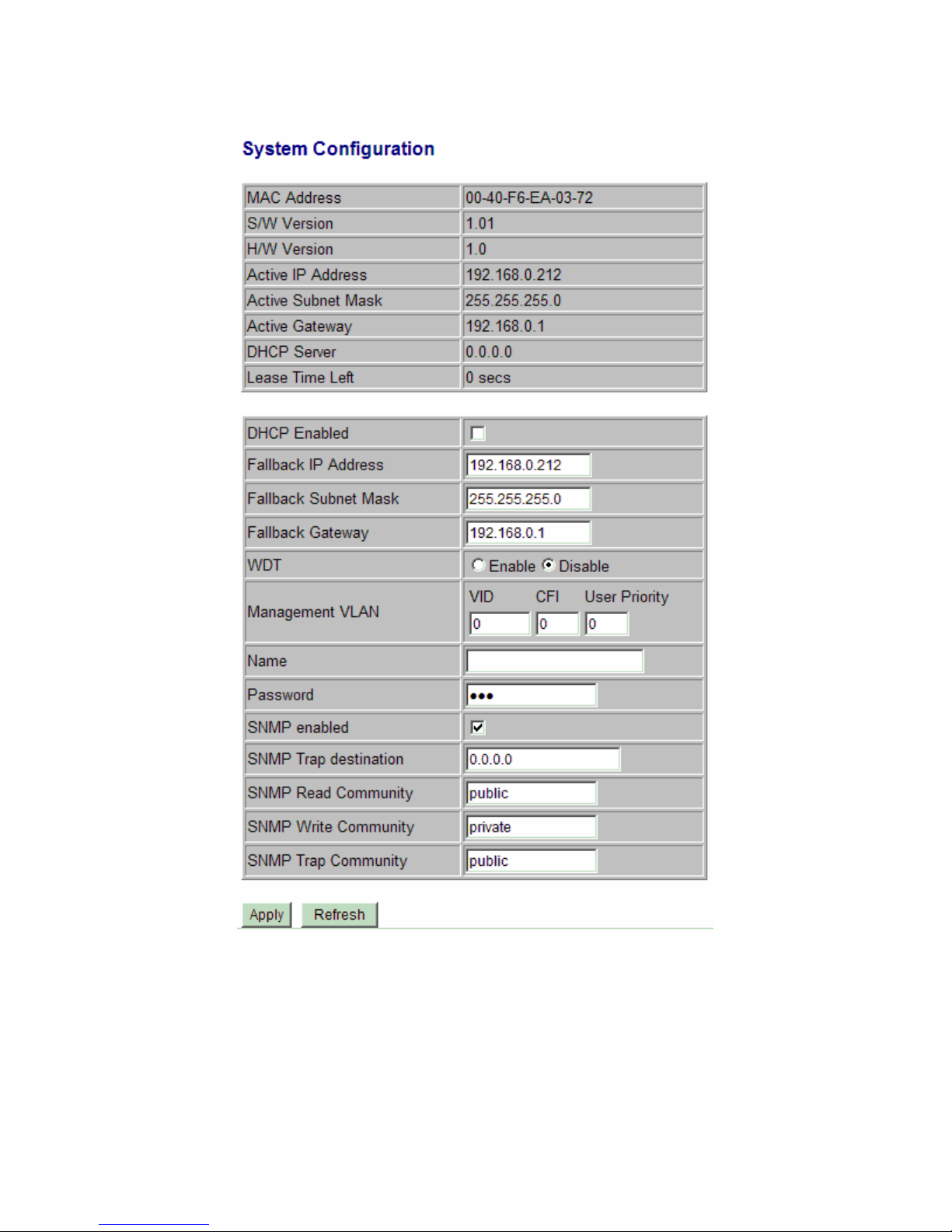
Configuration Description
MAC Address The MAC address factory configured for the switch
It can not be changed in any cases.
S/W Version The firmware version currently running
H/W Version The hardware version currently operating
Active IP Address Currently used IP address for the switch management
Active Subnet Mask Currently used subnet mask for IP address for the switch management
Active Gateway Currently used gateway IP address for the switch management
DHCP Server Current IP address of the DHCP server
Lease Time Left The time left for the lease IP address currently used
DHCP Enabled Use DHCP to get dynamic IP address configuration for the switch
Fallback IP Address IP address used when DHCP mode is not enabled
Fallback Subnet Mask Subnet mask for IP address used when DHCP mode is not enabled
Fallback Gateway Default gateway IP address used when DHCP mode is not enabled
WDT Enable WDT (Watch Dog Timer)
Management VLAN Set management VLAN information
- VID VLAN ID configured for web management to the switch
- CFI CFI value for web reply packets from the switch
- User priority Priority value for web reply packets from the switch
Name * Set the system name for this switch unit
Password Set new password
SNMP enabled Enable SNMP agent
SNMP Trap destination The IP address of the SNMP trap manager
SNMP Read community The community allowed for the SNMP [get] message
SNMP Write community The community allowed for the SNMP [set] message
SNMP Trap community The community used for the SNMP trap messages sent by the switch
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
Note:
1. It is suggested to give each switch unit a system name as an alternative unique identification beside IP
address.
2. Setting change of DHCP mode takes effective in next bootup.
3. A watch dog timer (WDT) is a hardware timing device that triggers a system reset if the system firmware, due to
some fault condition, such as a hang, neglects to regularly service the watc h dog tim er. The intention is to bring
the system back from the hung state into normal operation. The timer is set to 1.72 seconds in this switch.
-30-
Page 31

4.4.1 Management VLAN
Management VLAN settings allow administrator to access the switch and perform the switch management over
a dedicated VLAN.
The following rules are applied with the Management VLAN:
1. If the VLAN function is disabled, Management VLAN settings are ignored and no VLAN limitation is
applied in accessing the switch web management interface. The switch web (http) server only accepts
untagged management packets and replies untagged packets to the management host.
2. If [Management VLAN - VID] settings is zero, no VLAN limitation is applied in accessing the switch web
management interface. The switch web (http) server only accepts untagged management packets and replies
untagged packets to the management host.
3. If [Management VLAN - VID] settings is not zero, The switch web (http) server only accepts tagged
management packets matched [Management VLAN -VID] and replies tagged packets with tag composed of
[Management VLAN] VID, CFI and User Priority settings to the management host. The egress port will
also be limited in the member ports of the matched VLAN group.
Summary of the rules:
VLAN Function Management VID Switch Embedded Web Server operation
VLAN disabled Ignore Accept untagged web packets
Reply untagged packets
No VLAN group member checking
VLAN enabled VID=0 Accept untagged web packets
Reply untagged packets
No VLAN group member checking
VLAN enabled VID<>0 Accept matched tagged web packets only
( 1 ~ 4095) Reply tagged packets with the configured tag
Matched VLAN group member checking
Notes:
1. To apply management VLAN function, be sure to configure a VLAN group that matches the management
VID first.
2. No matter how management VLAN is configured, login password authentication is still required.
-31-
Page 32

4.5 Ports
Configuration Function
Enable Jumbo Frames Select to enable jumbo frame support
Port The port number
Ex.
7 Indicates Port 7 type - RJ-45
8 Indicates Port 8 type - RJ-45
8(SFP) Indicates Port 8 type - SFP
Link Speed and duplex status with green background - port is link on
Down with red background - port is link down
Mode Select port operating mode
Disabled - disable the port operation
Mode Au to-negotiation Speed capability Duplex capability
Auto Enable 10, 100, 1000M Full, Half
10 Half Disable 10M Half
10 Full Disable 10M Full
100 Half Disable 100M Half
100 Full Disable 100M Full
-32-
Page 33

1000 Full Enable 1000M Full
Auto 1000 Full Enable 1000M Full
Force 1000 Full Disable 1000M Full
Flow Control Set port flow control function
v - set to enable 802.3x pause flow control for ingress and egress
[SFP DDM] Click to display DDM information and status of the SFP transceivers
[Port Type] Click to set port type, RJ-45 or SFP for Port 7 and Port 8
[Apply] Click to apply the configuration change
4.5.1 Port Type
Port 8 supports two media types, RJ-45 and SFP. Use this button to select the port type.
Information Function
Port # Port number (Port 8)
Type RJ-45 Use RJ-45.
SFP Use SFP.
Notes:
The available mode options for RJ-45 port type on Port 7 and Port 8 are:
Mode Auto-negotiation Speed capability Duplex capability
Auto Enable 10, 100, 1000M Full, Half
10 Half Disable 10M Half
10 Full Disable 10M Full
100 Half Disable 100M Half
100 Full Disable 100M Full
1000 Full Enable 1000M Full
The available mode options for SFP port type on Port 8 are:
Mode Auto-negotiation Speed capability Duplex capability
Auto 1000 Full Enable 1000M Full
Force 1000 Full Disable 1000M Full
-33-
Page 34
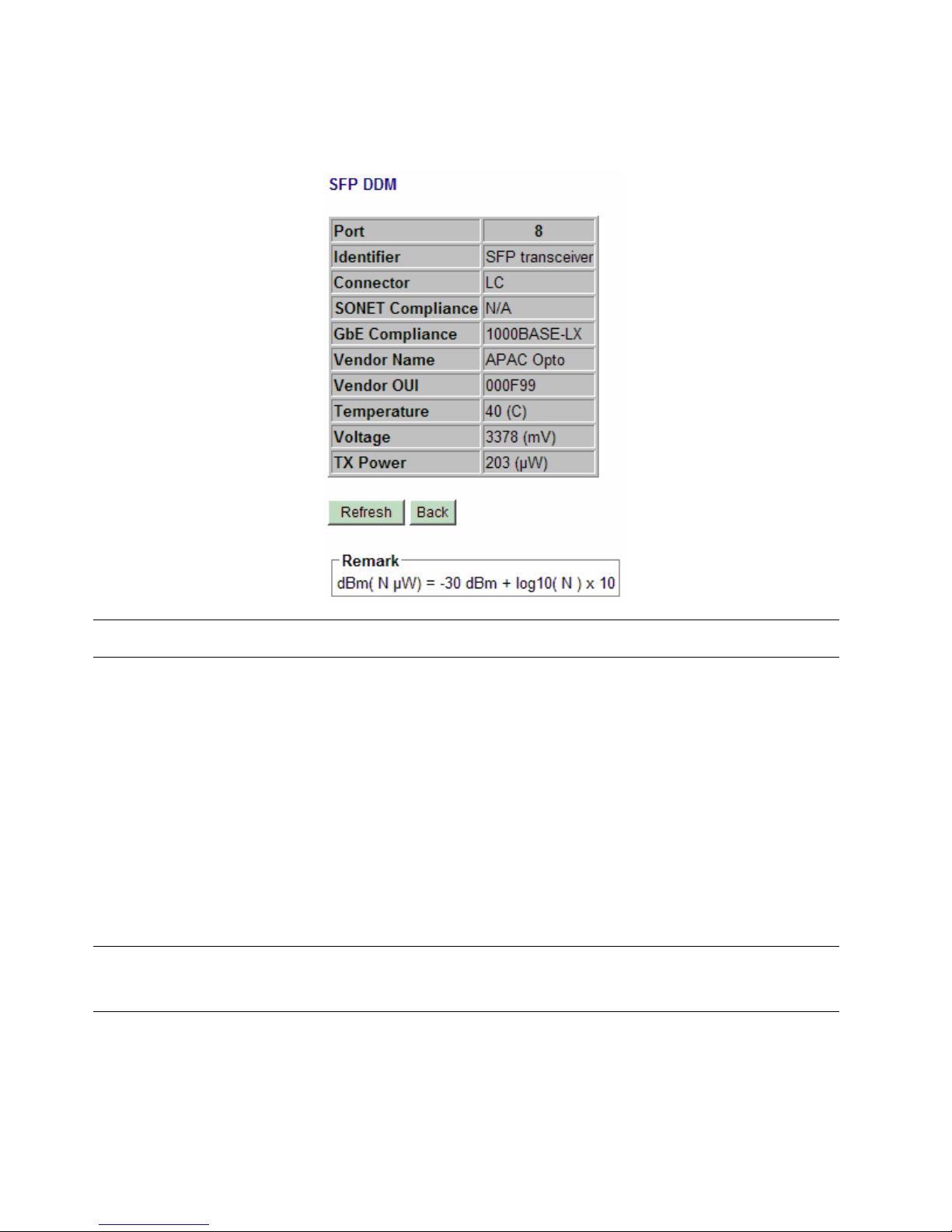
4.5.2 SFP DDM Status
DDM (Digital Diagnostic Monitoring) information and status are provided in some SFP transceivers. Part of
the information are retrieved and listed as follows:
Information Function
Port Port number which has SFP slot (Port 4, Port 5, Port 6 come with SFP.)
Identifier The identifier information of the transceiver
Connector The connector type used on the transceiver
SONET Compliance SONET compliance information of the transceiver
GbE Compliance Gigabit Ethernet compliance information of the transceiver
Vendor Name The vendor name of the transceiver
Vendor OUI The vendor OUI of the transceiver
Temperature The current temperature sensed inside the transceiver
Voltage The working voltage sensed inside the transceiver
TX Power The transmission optical power sensed
[Refresh] Click to refresh current configuration
[Back] Click to back to previous page
Note:
1. TX power data is displayed with unit of mW. It can be converted to dBm as remark.
2. N/A: the information is not available
-34-
Page 35

4.6 VLANs
VLAN Configuration Description
VLAN Disable Select to disable VLAN function
All ports are allowed to communicate with each others freely with no VLAN
limitation.
Port-based VLAN Mode Simple configuration for 2 port-based VLAN groups
Port-based VLAN ISP Mode Simple configuration for 5 port-based VLAN groups
Advance VLAN Mode Full VLAN configuration for port-based and Tag-based VLAN
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
-35-
Page 36

4.6.1 Port-based VLAN Mode
Configuration Description
Group 1, 2 Port-based VLAN group number
Member ports Select member ports for the group
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
Operation in this mode:
1. The member ports of two groups are allowed to overlap.
2. The member ports in same group can communicate with other members only.
3. No packet tag is examined.
4. A received packet will not be modified (i.e. tagging or untagging) through VLAN operation till it is
transmitted.
-36-
Page 37

4.6.2 Port-based VLAN ISP Mode
Configuration Description
Joint port Select a port as the joint port for all 7 port-based VLAN groups
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
Example:
If Port 8 is selected as the joint port, the 7 port-based VLAN groups are configured as follows automatically:
Group 1 - member [Port 1, Port 8]
Group 2 - member [Port 2, Port 8]
Group 3 - member [Port 3, Port 8]
Group 4 - member [Port 4, Port 8]
Group 5 - member [Port 5, Port 8]
Group 6 - member [Port 6, Port 8]
Group 7 - member [Port 7, Port 8]
-37-
Page 38

Mode Operation:
1. The joint port is the shared member port for all groups.
2. Two member ports are configured in each group.
3. The member ports in same group can communicate with other only.
4. No packet tag is examined.
5. A received packet will not be modified (i.e. tagging or untagging) through VLAN operation till it is
transmitted.
4.6.3 Advanced VLAN Mode
Configuration Description
Ingress Default Tag Click to configure per port Ingress Default Tag settings
Ingress Settings Click to configure per port ingress settings
Egress Settings Click to configure per port egress settings
VLAN Groups Click to configure VLAN group table
-38-
Page 39

4.6.3.1 Ingress Default Tag
Configuration Description
Port Port number
PVID Port VID, VID for Ingress Default Tag
1 ~ 4095 - decimal 12-bit VID value
CFI CFI for Ingress Default Tag
0, 1 - 1-bit CFI value
User Priority User priority for Ingress Default Tag
0 ~ 7 - decimal 3-bit value
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
PVID is used as index for VLAN classification (VLAN group table lookup) in one of the following conditions:
1. Ingress port [Tag Aware] setting = Tag-ignore
2. Ingress port [Tag Aware] setting = Tag-aware
and the received packet is untagged or priority-tagged
[PVID+CFI+User Priority] = Ingress Default Tag for the ingress port
It is used as the tag for insertion in egress tagging operation in one of the following conditions:
1. Ingress port [Tag Aware] setting = Tag-ignore, Egress port [Insert Tag] = Enable
2. Ingress port [Tag Aware] setting = Tag-aware, Egress port [Insert Tag] = Enable
and the received packet is untagged or priority-tagged
-39-
Page 40

4.6.3.2 Ingress Settings
Configuration Description
Port Port number
Tag Aware Check tag data for every received packet
Tag-aware - set to activate Tag-based mode
Tag-ignore - set to use port-based mode and ignore any tag in packet
Keep Tag Tag is removed from the received packet if exists
Enable - set to activate tag removal for VLAN-tagged packets
Disable - set to disable tag removal function
Drop Untag Drop all untagged packets and priority-tagged packets
Enable - drop untagged packets and priority-tagged packets
Disable - admit untagged packets and priority-tagged packets
Drop Tag Drop all VLAN-tagged packets
Enable - drop VLAN-tagged packets
-40-
Page 41

Disable - admit VLAN-tagged packets
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
Note:
1. Priority-tagged packet (VID=0) is treated as untagged packet in the switch.
2. [Tag Aware] setting affects the index used for VLAN classification (VLAN table lookup). The following
table lists the index used:
Ingress [Tag Aware] setting
Received packet type Tag-ignore Tag-aware
Untagged PVID PVID
Priority-tagged (VID=0) PVID PVID
VLAN-tagged (VID>0) PVID Packet tag VID
3. Both [Drop Untag] and [Drop Tag] are set to Disable to admit all packets.
-41-
Page 42
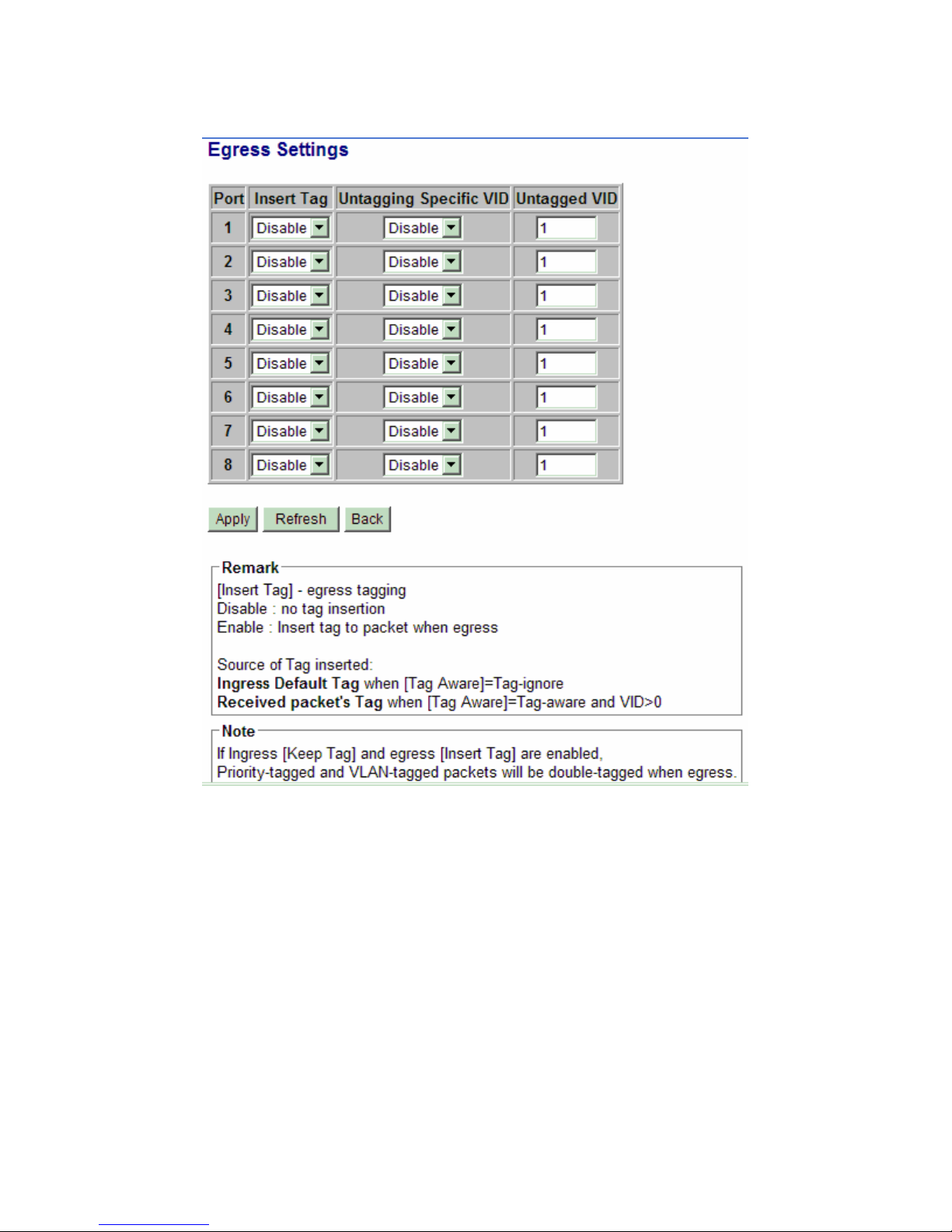
4.6.3.3 Egress Settings
-42-
Page 43

Configuration Description
Port Port number
Insert Tag Activate tagging (Insert a tag to the packet)
Enable - set to activate tagging
Disable - set to disable tagging function
Untagging Specific VID No tag insertion if packet tag information matches [Untagged VID]
Enable - set to enable this function
Disable - set to disable this function
Untagged VID VID for [Untagging Specific VID] setting
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
1 ~ 4095 - decimal 12-bit VID value
The inserted tag sources when [Insert Tag] = Enable is listed as follows:
Received packet type [Tag Aware]=Tag-ignore [Tag Aware]=Tag-aware
Untagged Ingress Default Tag Ingress Default Tag
Priority-tagged (VID=0) Ingress Default Tag Ingress Default Tag
VLAN-tagged (VID>0) Ingress Default Tag Packet own tag
-43-
Page 44
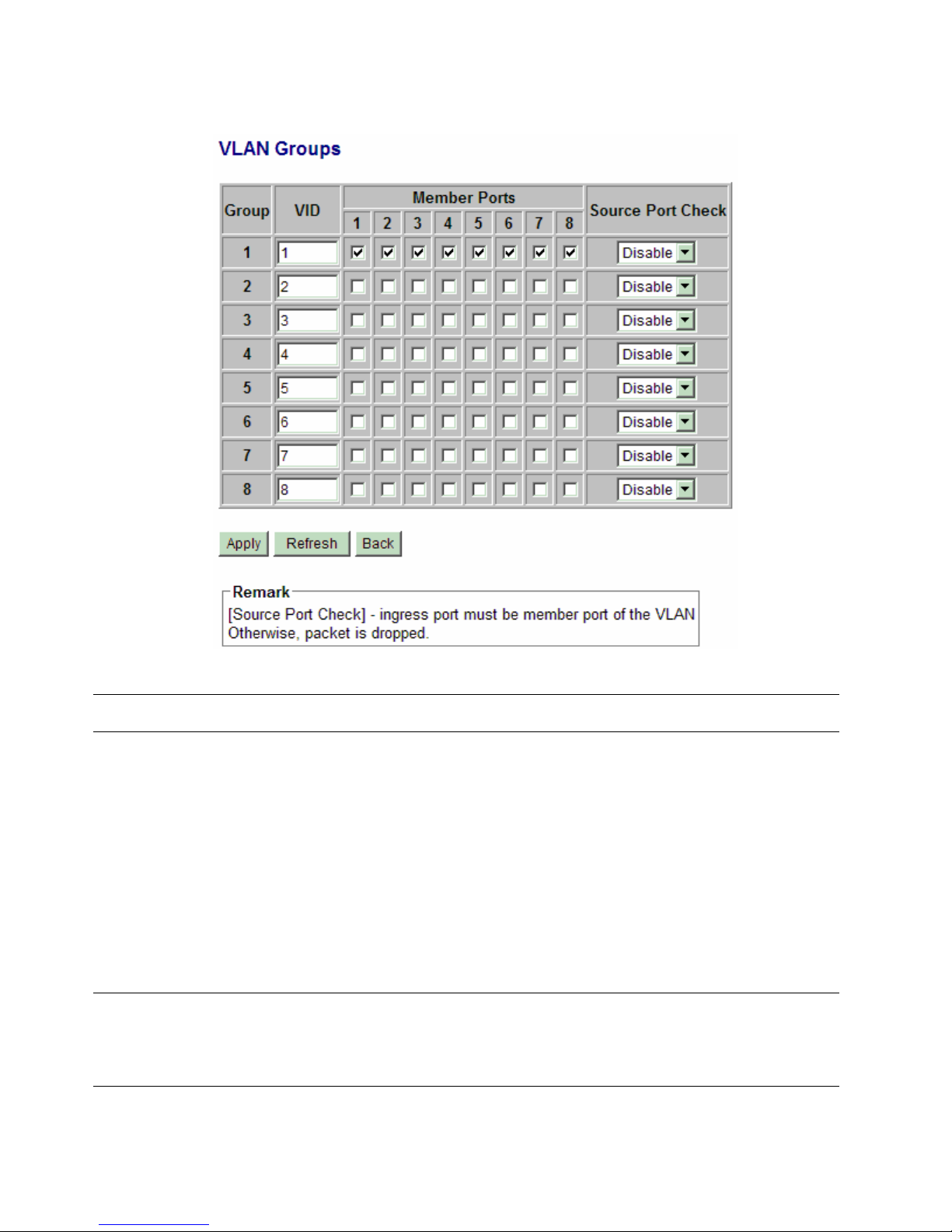
4.6.3.4 VLAN Groups
Configuration Description
Group Group number
VID VID of the VLAN to which this group is associated
1 ~ 4095 - decimal 12-bit VID value
Member Ports Select the admitted egress ports for the packets belong to the VLAN
Port 1 ~ 8 - click to select
Source Port Check Check whether the ingress port is the member port of the VLAN
Enable - set to enable this check, the packet is dropped if ingress port is not member
port of the VLAN.
Disable - set to disable this check
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
-44-
Page 45
4.6.4 Important Notes for VLAN Configuration
Some considerations should be checked in configuring VLAN settings:
1. Switch VLAN Mode selection
It is suggested to evaluate your VLAN application first and plan your VLAN configuration carefully before
applying it. Any incorrect setting might cause network problem.
2. Aggregation/Trunking configuration
Make sure the members of a link aggregation (trunk) group are configured with same VLAN configuration
and are in same VLAN group.
3. Double Tagged in Advanced VLAN Mode
For a received packet, Ingress port [Keep Tag] setting and Egress port [Insert Tag] setting are enabled at the
same time. It will cause the packet double-tagged when egress. Although, it is often applied in Q-in-Q
provider bridging application, however, such condition should be avoided in normal VLAN configuration.
See table below:
Ingress port Egress port
[Keep Tag] [Insert Tag] Received Packet Packet Transmitted
Enable Enable Priority-tagged Double-tagged
Enable Enable VLAN-tagged Double-tagged
-45-
Page 46
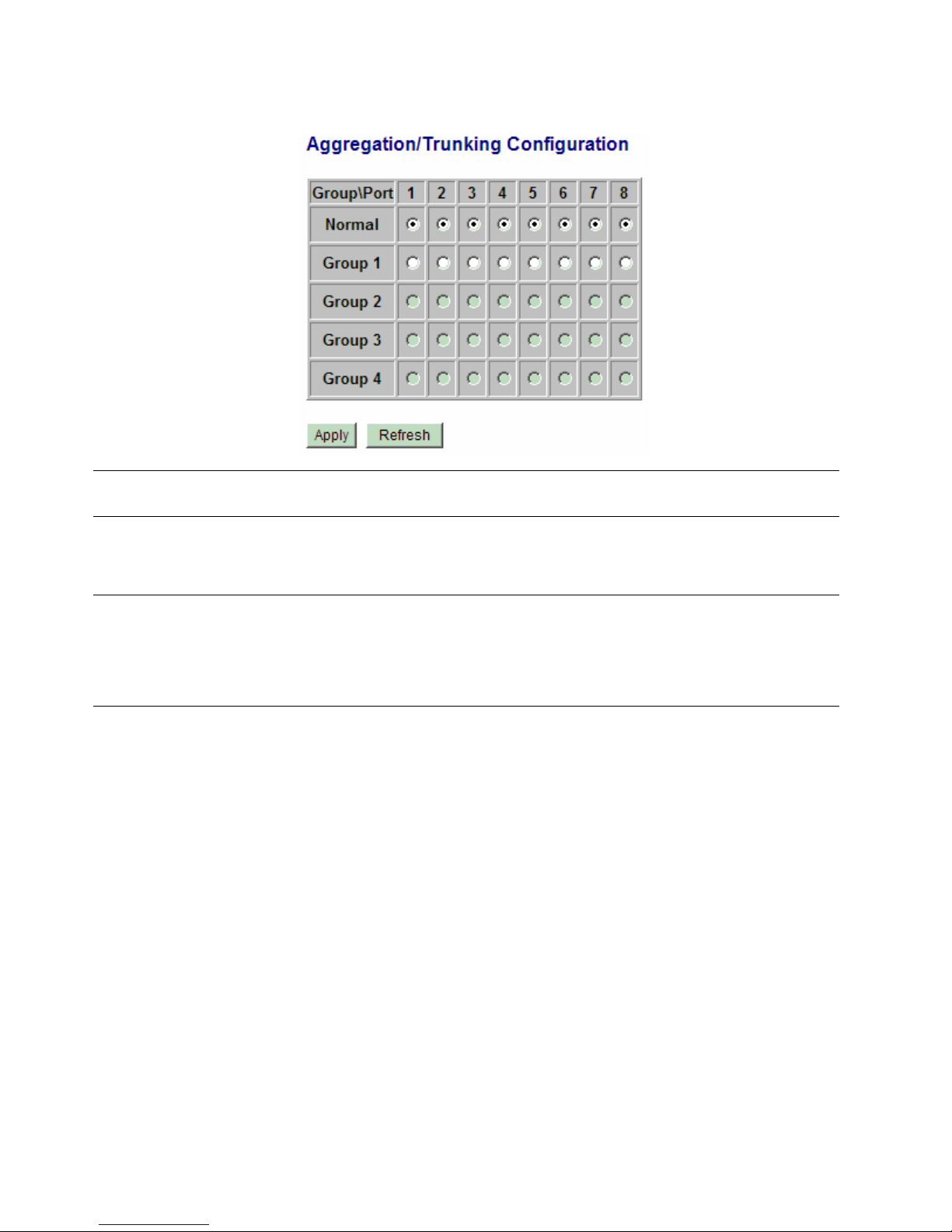
4.7 Aggregation
Configuration Description
Group Trunk group number
Port # Click to select the port as member port of the trunk group
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
Link aggregation function allows making connection between two switches using more than one physical links.
It can increase the connection bandwidth between two switches. The switch supports up to four trunk groups
and the number of member ports belonging to one trunk group is not limited.
Notes:
1. The LACP enabled ports are not available in this configuration..
2. One port cannot belong to two trunk groups at the same time.
3. The member ports of one trunk group must also belong to same VLAN group and have same VLAN
configuration settings. Otherwise, abnormal operation might be experienced.
-46-
Page 47
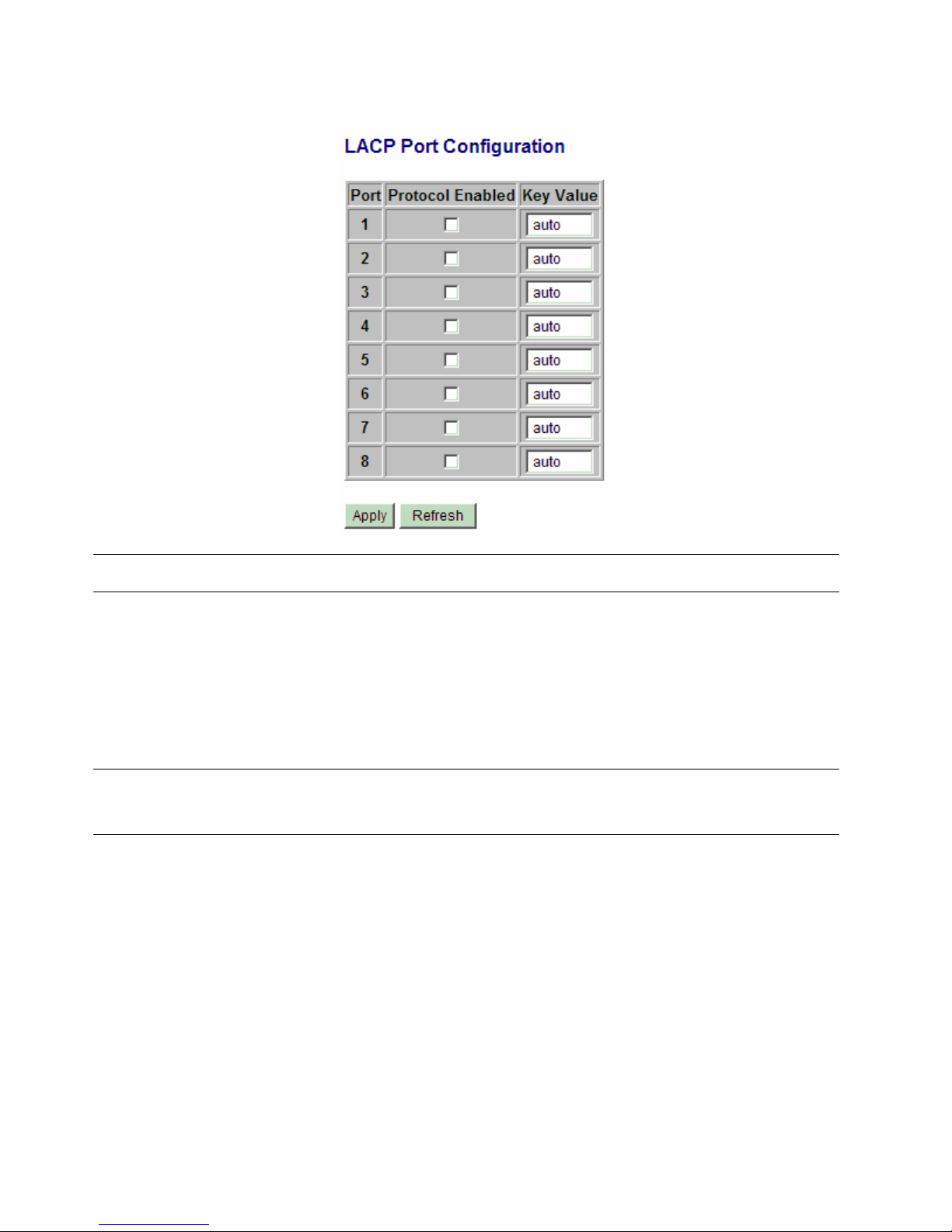
4.8 LACP
Configuration Description
Port Port number
Protocol Enabled Enable LACP support for the port
Key Value An integer value assigned to the port that determines which ports are aggregated into
an LACP link aggregate. Set same value to the ports in
same LACP link aggregate. Value: 1 ~ 255.
Auto - key value is assigned by the system
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
Notes:
1. This configuration is used to configure LACP aggregate groups.
2. The ports with same key value are in same LACP aggregate group.
3. The ports with Auto key are in same LACP aggregate group.
4. The ports configured in non-LACP aggregation are not available in this configuration.
-47-
Page 48
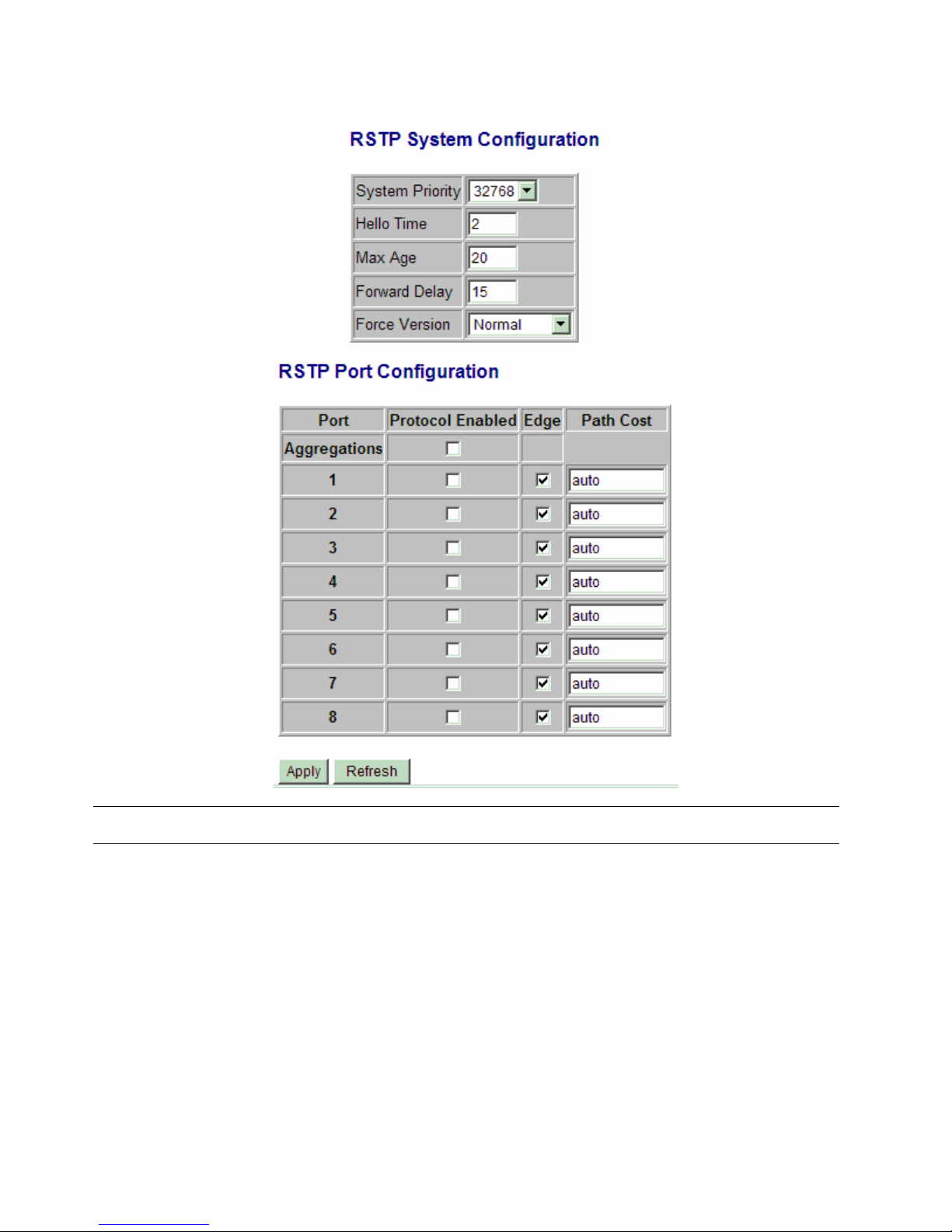
4.9 RSTP
Configuration Description
System Priority The lower the bridge priority is the higher priority it has. Usually, the bridge with the
highest bridge priority is the root. Value: 0 ~ 61440
Hello Time Hello Time is used to determine the periodic time to send normal BPDU from
designated ports among bridges. It decides how long a bridge should send this
message to other bridge to tell I am alive.
Max Age When the switch is the root bridge, the whole LAN will apply this setting as their
maximum ag e t ime.
Forward Delay This figure is set by Root Bridge only. The forward delay time is defined as the time
spent from Listening state moved to Learning state and also from Learning state
moved to Forwarding state of a port in bridge.
-48-
Page 49

Force Version Two options are offered for choosing STP algorithm.
Compatible - STP (IEEE 802.1D)
Normal - RSTP (IEEE 802.1w)
Aggregations Enabled to support port trunking in STP. It means a link aggregate is treated as a
physical port in RSTP/STP operation.
Port Protocol Enabled Port is enabled to support RSTP/STP.
Port Edge An Edge Port is a port connected to a device that knows nothing about STP or RSTP.
Usually, the connected device is an end station. Edge Ports will immediately transit to
forwarding state and skip the listening and learning state because the edge ports
cannot create bridging loops in the network.
Port Path Cost Specifies the path cost of the port that switch uses to determine which port are the
forwarding ports the lowest number is forwarding ports, the rage is 1 ~ 200,000,000
and Auto. Auto means a default cost is automatically calculated in RSTP operation
based on the port link speed.
The default costs are :
Link Speed Auto Default Cost
10Mbps 2000000
100Mbps 200000
1000Mbps 20000
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
-49-
Page 50
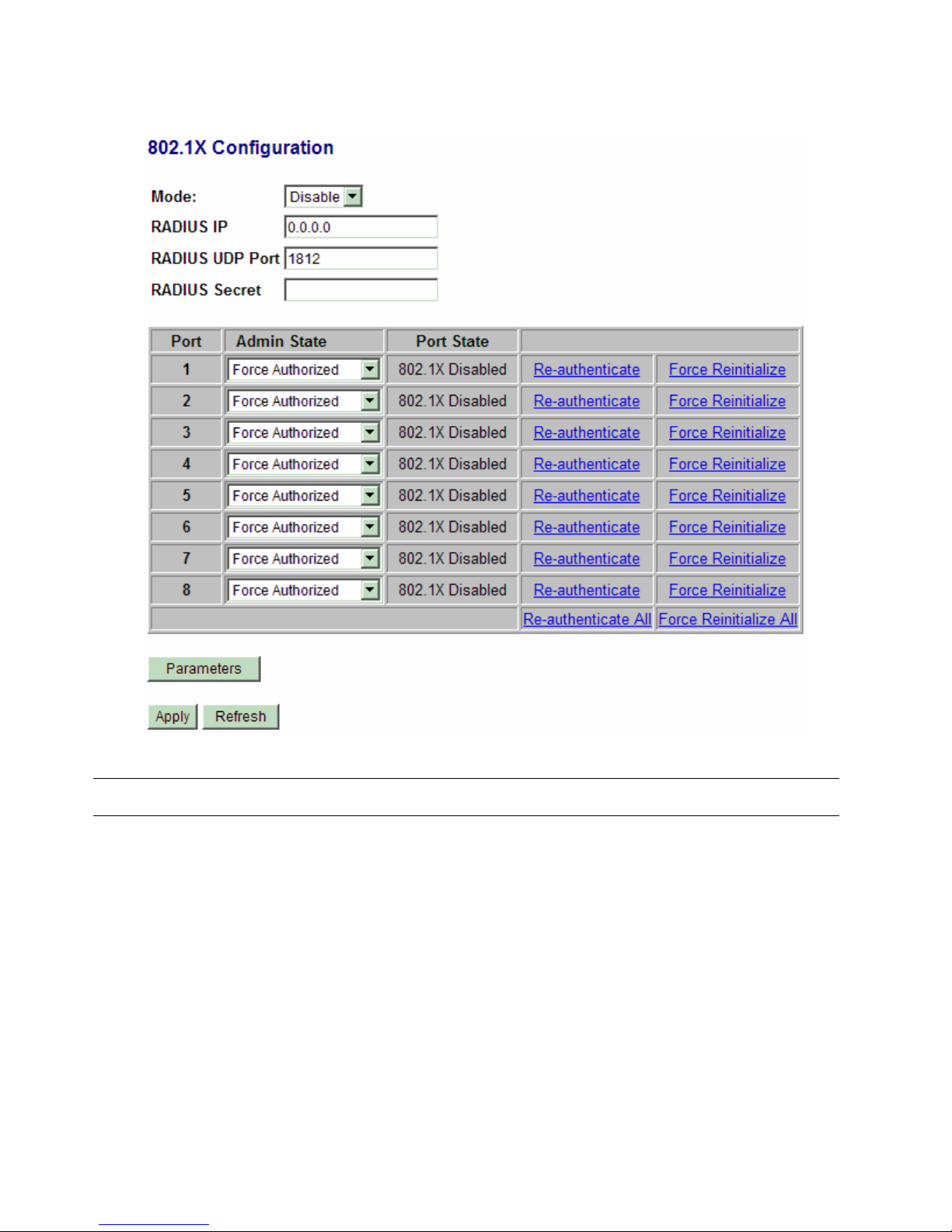
4.10 802.1X Configuration
Configuration Description
Mode Disabled - disable 802.1X function
Enabled - enable 802.1X function
RADIUS IP IP address of the Radius server
RADIUS UDP Port The UDP port for authentication requests to the specified Radius server
RADIUS Secret The encryption key for use during authentication sessions with the Radius server. It
must match the key used on the Radius server.
Port Port number
Admin State Port 802.1X control
Auto - set to the Authorized or Unauthorized state in accordance with the outcome of
an authentication exchange between the Supplicant and the Authentication Server.
Force Authorized - the port is forced to be in authorized state.
-50-
Page 51

Force Unauthorized - the port is forced to be in unauthorized state.
Port State Port 802.1X state
802.1X Disabled - the port is in 802.1X disabled state
Link Down - the port is in link down state
Authorized (green color) - the port is in 802.1X authorized state
[Re-authenticate] Click to perform a manual authentication for the port
[Force Reinitialize] Click to perform an 802.1X initialization for the port
[Re-authenticate All] Click to perform manual authentication for all ports
[Force Reinitialize All] Click to perform 802.1X initialization for all ports
[Parameters] Click to configure Re-authentication parameters
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
Unauthorized (red color) - the port is in 802.1X unauthorized state
4.10.1 802.1X Re-authentication Parameters
Configuration Description
Re-authentication Enabled Check to enable periodical re-authentication for all ports
Re-authentication Period The period of time after which the connected radius clients must be
re-authenticated (unit: second), Value: 1- 3600
EAP timeout The period of time the switch waits for a supplicant response to an EAP
request (unit: second), Value: 1 - 255
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
-51-
Page 52

4.11 Mirroring
Configuration Description
Mirror Port The port is forwarded all packets received on the mirrored ports
Mirror Source Select the ports which will be mirrored all received packets to the mirror port.
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
-52-
Page 53

4.12 Quality of Service
QoS Configuration Description
Port Port number
802.1p 802.1p priority classification
Enable - set to enable this classification to the port for priority-tagged and
VLAN-tagged packets
Disable - 802.1p classification is not applied to the port
DSCP DSCP classification
Enable - set to enable DSCP classification to the port for IP packets
Disable - DSCP classification is not applied to the port
Port Priority Port default priority class, it is used as a port-based QoS mode when 802.1p and
DSCP classifications are disabled. It is also used as default priority class for the
received packet when both 802.1p and DSCP classification failed in classification.
Class 3 ~ Class 0 - priority class
-53-
Page 54

[802.1p Mapping] Click to configure 802.1p mapping tables.
[DSCP Mapping] Click to configure DSCP mapping table.
[Service Policy] Click to configure per port egress service policy mode.
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
Note:
802.1p classification is superior over DSCP classification if both are enabled. That means if a received packet
is classified successfully in 802.1p classification, the classified priority class is used directly for the packet and
the result of DSCP classification is ignored.
4.12.1 802.1p Mapping
Configuration Description
Port n Port number n
tag m 3-bit User priority tag value m ( range : 0 ~ 7 )
Priority class Mapped priority class for tag m on Port n
Class 3 ~ Class 0
-54-
Page 55
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
Every ingress port has its own 802.1p mapping table. The table is referred in 802.1p priority classification for
the received packet.
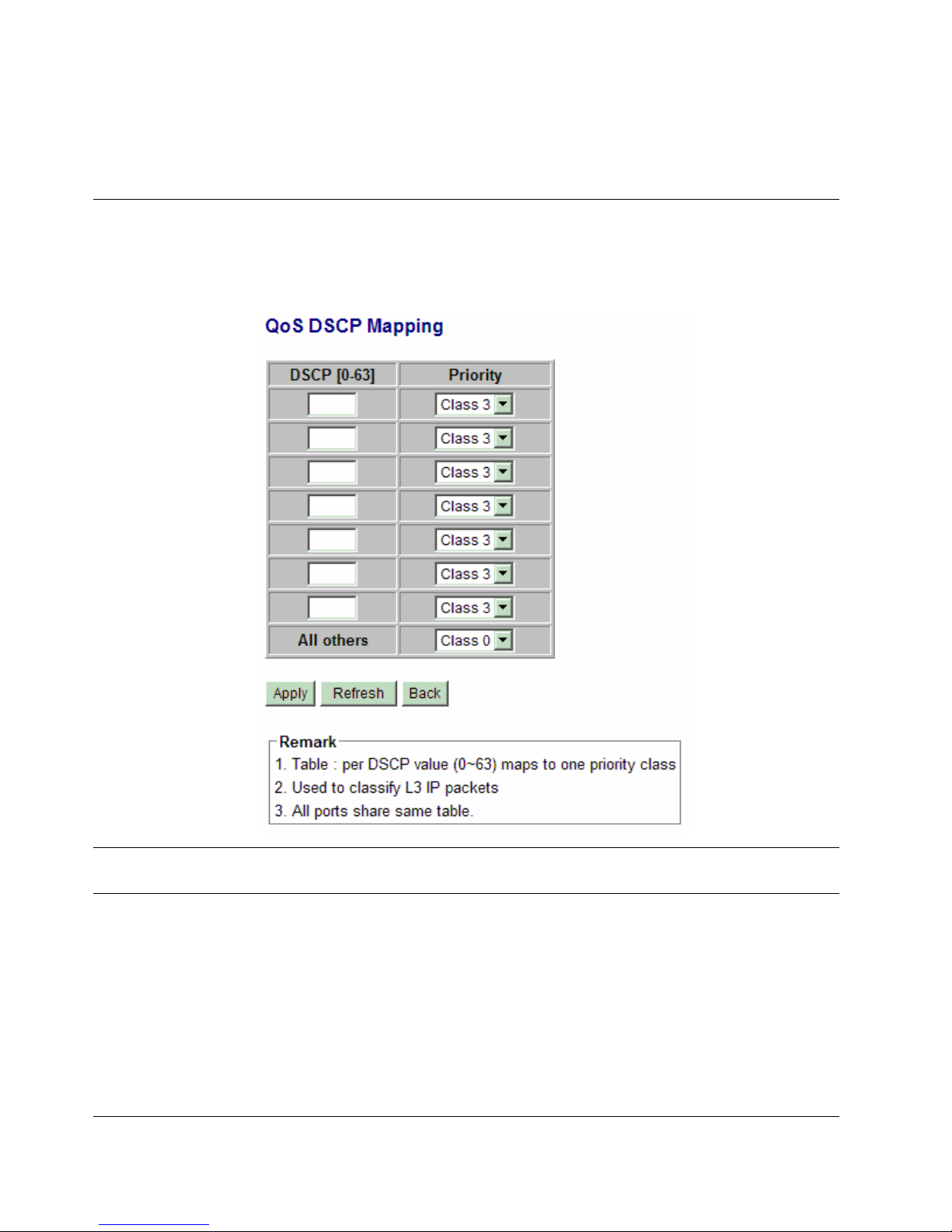
4.12.2 DSCP Mapping
Configuration Description
DSCP [0-63] Seven user-defined DSCP values which are configured with a priority class
0 ~ 63 - 6-bit DSCP value in decimal
Priority The priority class configured for the user-defined DSCP value
Class 3 ~ Class 0
All others The other DSCP values not in the seven user-defined values are assigned a default priority
class
Class 3 ~ Class 0
-55-
Page 56

[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
Only one DSCP mapping table is configured and applied to all ports. The table is referred in DSCP priority
classification.
4.12.3 QoS Service Policy
-56-
Page 57

Configuration Description
Port Port number
Policy Service policy for egress priority among four egress class queues
Strict priority - high class queue is served first always till it is empty
Weighted ratio priority Class 3:2:1:0 = 4:3:2:1 - weighted ratio 4:3:2:1
Weighted ratio priority Class 3:2:1:0 = 5:3:1:1 - weighted ratio 5:3:1:1
Weighted ratio priority Class 3:2:1:0 = 1:1:1:1 - weighted ratio 1:1:1:1
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
[Back] Click to go back to upper menu
Notes:
1. Queue with higher class number has higher priority than queue with lower class number. That means Class
3 > Class 2 > Class 1 > Class 0 by default.
2. In weighted ratio policies, a weighted fairness round robin service is guaranteed normally. However, when
excess bandwidth exists higher class queue will take advantage on bandwidth allocation.
-57-
Page 58

4.13 Storm Control
Configuration Description
Broadcast Rate The rate limit of the broadcast packets transmitted on a port.
Broadcast Rate The rate limit of the Multicast packets transmitted on a port.
Flooded Unicast Rate The rate limit of the flooded unicast packets transmitted on a port. The flooded
unicast packets are those unicast packets whose destination address is not learned in
the MAC address table.
[Apply] Click to apply the configuration change
[Refresh] Click to refresh current configuration
Notes:
1. The unit of the rates is pps (packets per second).
2. No Limit - no protection control
-58-
Page 59

4.14 Statistics Overview
Statistics Description
Port Port number
Tx Bytes Total of bytes transmitted on the port
Tx Frames Total of packet frames transmitted on the port
Rx Bytes Total of bytes received on the port
Rx Frames Total of packet frames received on the port
Tx Errors Total of error packet frames transmitted on the port
Rx Errors Total of error packet frames received on the port
[Clear] Click to reset all statistic counters
[Refresh] Click to refresh all statistic counters
-59-
Page 60
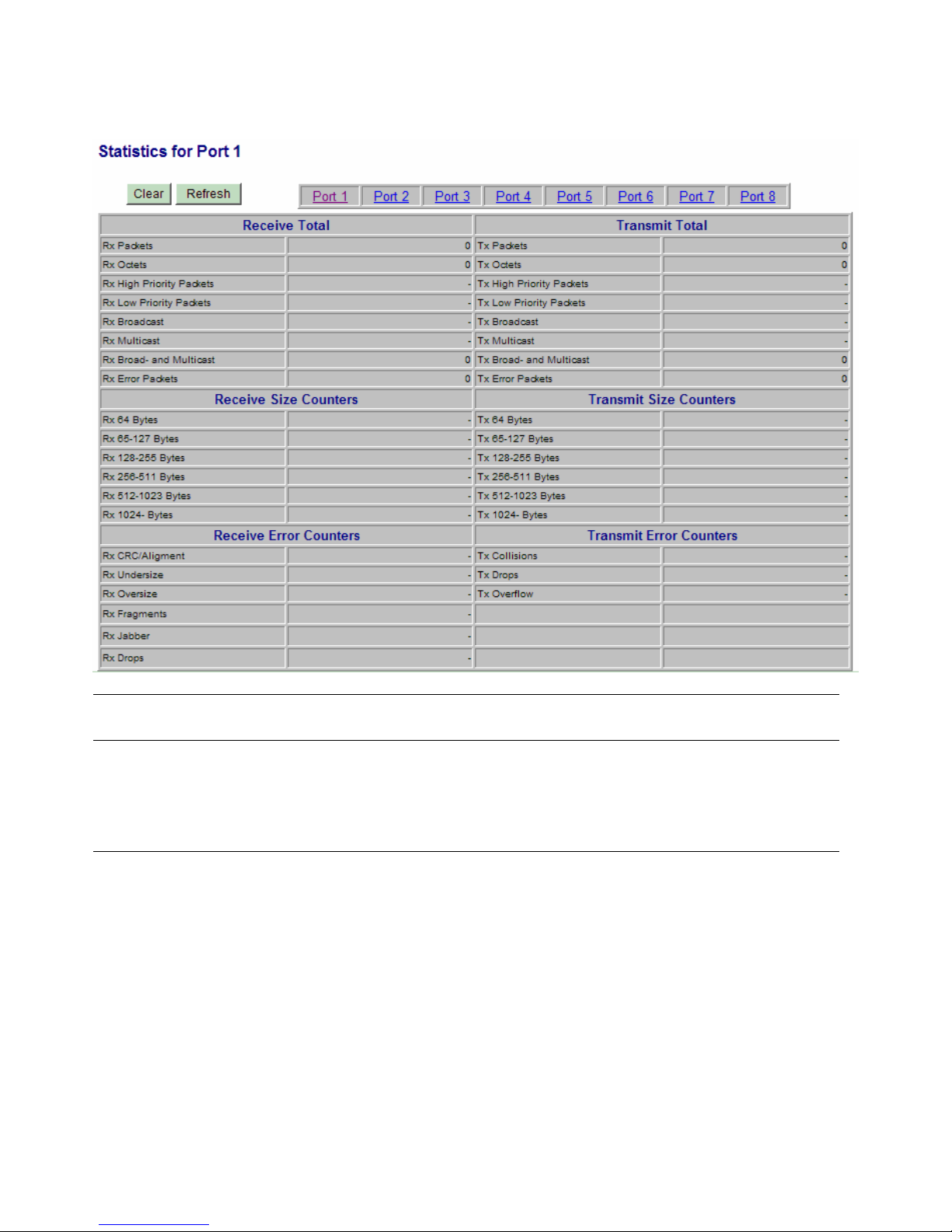
4.15 Detailed Statistics
Button Description
[Port #] Click to display the detailed statistics of Port #.
[Clear] Click to reset all statistic counters
[Refresh] Click to refresh the displayed statistic counters
-60-
Page 61
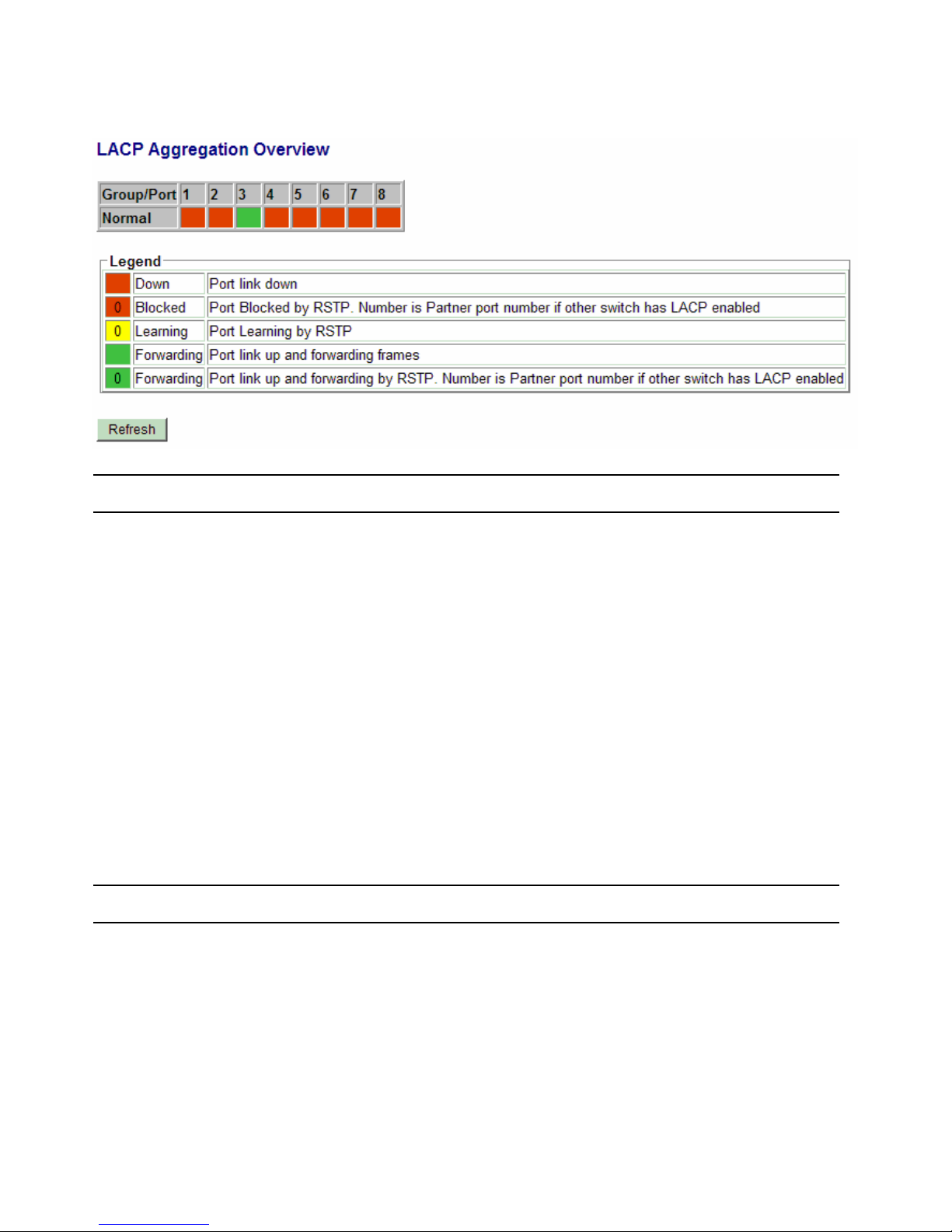
4.16 LACP Status
Status Description
Port The port number
Normal Display the ports not LACP enabled.
Group # The LACP group
Status The LACP port status presented with color and a number
<Down> - the port is link down
<Blocked & #> - the port is blocked by RSTP and the # is the port number of LACP
link partner
<Learning> - the port is learning by RSTP
<Forwarding> - the port is link up and forwarding frames
<Forwarding & #> - the port is link up and forwarding frames and the # is the port
number of LACP link partner
Partner MAC address The MAC address of the link partner at the other end of the LACP aggregate
Local Port Aggregated The ports at local end which are aggregated in same LACP group
[Refresh] Click to refresh the status
Note: the figure shows an example that two LACP link aggregates are configured.
-61-
Page 62

Status Description
Port The port number
Protocol Active yes - the port is link up and in LACP operation
no - the port is link down or not in LACP operation
Partner Port Number The port number of the remote link partner
Operation Port Key The operation key generated by the system
-62-
Page 63
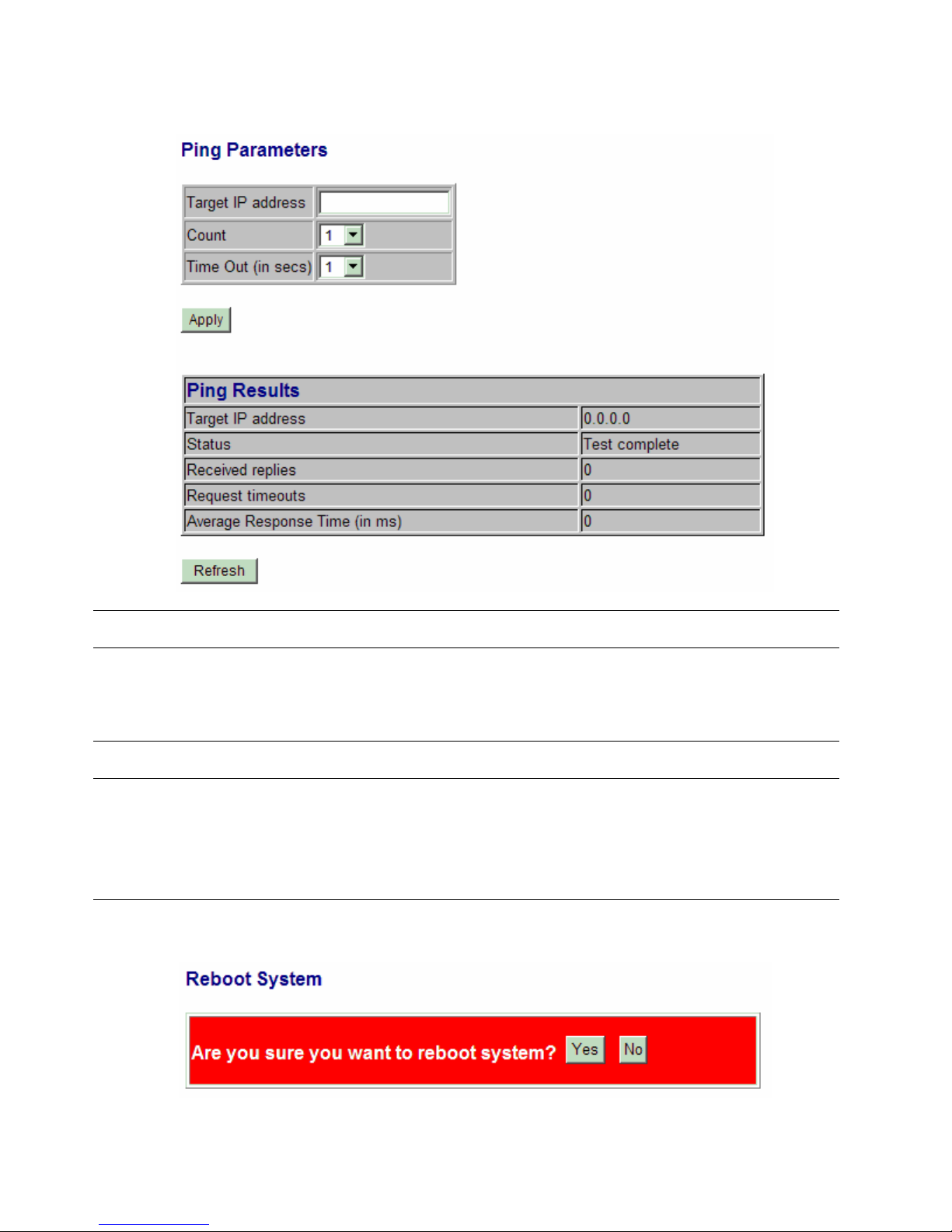
4.17 Ping
Ping Description
Target IP Address The target IP address to which the ping command issues
Count The number of ping commands generated
Time Out (in secs) The time out for a reply (in seconds)
[Apply] Start the ping command
Status The command status
Received replies The number of replies received by the system
Request time-outs The number of requests time out
Average Response Time The average response time of a ping request (in mini-seconds)
4.18 Reboot System
This menu is used to reboot the switch unit remotely with current configuration. Starting this menu will make
-63-
Page 64

your current http connection lost. You must rebuild the connection to perform any management operation to
the unit.
4.19 Restore Default
This menu is used to restore all settings of the switch unit with factory default values except current IP
configuration and Management VLAN configuration.
4.20 Update Firmware
This menu is used to perform in-band firmware (switch software) upgrade. Enter the path and file name of new
firmware image file for uploading.
Configuration Description
Filename Path and filename (warp format)
[Browse] Click to browse your computer file system for the firmware image file
[Upload] Click to start upload
4.21 Logout
This menu is used to perform a logout from the switch management. If current user does not perform any
management operation over 3 minutes, the switch will execute an auto logout and abort the current connection.
-64-
Page 65

5. SNMP Support
SNMP version support Snmp v1, v2c management
Managed Objects MIB-II
system OBJECT IDENTIFIER ::= { mib-2 1 }
interfaces OBJECT IDENTIFIER ::= { mib-2 2 }
ip OBJECT IDENTIFIER ::= { mib-2 4 }
snmp OBJECT IDENTIFIER ::= { mib-2 11 }
dot1dBridge OBJECT IDENTIFIER ::= { mib-2 17 }
ifMIB OBJECT IDENTIFIER ::= { mib-2 31 }
RFC RFC 3418 - Management Information Base (MIB) for the Simple Network
Management Protocol (SNMP)
RFC 1907 - Management Information Base for Version 2 of the Simple
Network Management Protocol (SNMPv2)
RFC 1213 - Management Information Base for Network Management of
TCP/IP-based internets: MIB-II
RFC 1158 - Management Information Base for network management of
TCP/IP-based internets: MIB-II
RFC 1493 - Definitions of Managed Objects for Bridges
RFC 2863 - The Interfaces Group MIB
RFC 1573 - Evolution of the Interfaces Group of MIB-II
SNMP Trap Support TRAP_COLDSTART - the device boot up trap
TRAP_LINKUP - the port link recovery trap
TRAP_LINKDOWN - port link down trap
-65-
Page 66

Appendix. Factory Default Settings
System Configuration
DHCP Enabled Not select (disabled)
Fallback IP Address 192.168.0.2
Fallback IP Subnet mask 255.255.255.0
Fallback Gateway IP 192.168.0.1
Management VLAN - VID 0
Management VLAN - CFI 0
Management VLAN - User priority 0
WDT Enable Not select (disabled)
Name Null
Password 123
SNMP enabled Not select (disabled)
SNMP Trap destination 0.0.0.0
SNMP Read community public
SNMP Write community private
SNMP Trap community public
Ports Configuration
Enable Jumbo Frames Not select (disabled)
Mode Auto for all ports
Flow Control v: Enable for all ports
Port Type Port 8: RJ-45
VLAN Configuration
Main Mode VLAN Disable
Port-based VLAN Mode setting
Member Ports Port 1, 2, 3, 4, 5, 6, 7, 8 for Group 1
None for Group 2
Port-based VLAN ISP Mode setting
-66-
Page 67

Joint Port Port 8
Advanced VLAN Mode Settings
Ingress Default Tag - PVID 1 for all ports
Ingress Default Tag - CFI 0 for all ports
Ingress Default Tag - User Priority 0 for all ports
Ingress Setting - Tag Aware Tag-ignore for all ports
Ingress Setting - Keep Tag Enable for all ports
Ingress Setting - Drop Untag Disable for all ports
Ingress Setting - Drop Tag Disable for all ports
Egress Setting - Insert Tag Disable for all ports
Egress Setting - Untagging VID Disable for all ports
Egress Setting - Untagged VID 1 for all ports
VLAN Group 1 - VID 1
VLAN Group 1 - Member Ports Port 1, 2, 3, 4, 5, 6, 7, 8
VLAN Group 1 - Source Port Check Disable
VLAN Group 2 - VID 2
VLAN Group 2 - Member Ports None
VLAN Group 2 - Source Port Check Disable
VLAN Group 3 - VID 3
VLAN Group 3 - Member Ports None
VLAN Group 3 - Source Port Check Disable
VLAN Group 4 - VID 4
VLAN Group 4 - Member Ports None
VLAN Group 4 - Source Port Check Disable
VLAN Group 5 - VID 5
VLAN Group 5 - Member Ports None
VLAN Group 5 - Source Port Check Disable
VLAN Group 6 - VID 6
VLAN Group 6 - Member Ports None
VLAN Group 6 - Source Port Check Disable
VLAN Group 7 - VID 7
-67-
Page 68

VLAN Group 7 - Member Ports None
VLAN Group 7 - Source Port Check Disable
VLAN Group 8 - VID 8
VLAN Group 8 - Member Ports None
VLAN Group 8 - Source Port Check Disable
Aggregation/Trunking Configuration
Group 1 -4 Member Ports None
LACP Port Configuration
Protocol Enabled Not select (disabled) for all ports
Key Value Auto for all ports
RSTP System Configuration
System Priority 32768
Hello Time 2
Max Age 20
Forward Delay 15
Force Version Normal
RSTP Port Configuration
Protocol enabled Not select (disabled) for all ports
Edge v: Select for all ports
Max Age 20
Forward Delay 15
Force Version Normal
802.1X Configuration
Mode Disabled
RADIUS IP 0.0.0.0
RADIUS UDP Port 1812
RADIUS Secret None
-68-
Page 69

Admin State Force Authorized for all ports
Reauthentication Enabled No
Reauthentication Period 3600
EAP Timeout 30
Port 1~Port 8 - tag 1 Class 0
Port 1~Port 8 - tag 2 Class 1
Port 1~Port 8 - tag 3 Class 1
Port 1~Port 8 - tag 4 Class 2
Port 1~Port 8 - tag 5 Class 2
Port 1~Port 8 - tag 6 Class 3
Port 1~Port 8 - tag 7 Class 3
Mirroring Configuration
Mirror source Not select for all ports
Mirror Port 1 (Port 1)
Quality of Service Configuration
802.1p Classification Disable for all ports
DSCP Classification Disable for all ports
Port Priority Class 3 for all ports
QoS 802.1p Mapping
Port 1~Port 8 - tag 0 Class 0
Port 1~Port 8 - tag 1 Class 0
Port 1~Port 8 - tag 2 Class 1
Port 1~Port 8 - tag 3 Class 1
Port 1~Port 8 - tag 4 Class 2
Port 1~Port 8 - tag 5 Class 2
Port 1~Port 8 - tag 6 Class 3
Port 1~Port 8 - tag 7 Class 3
QoS DSCP Mapping
-69-
Page 70

DSCP 1 / Priority 0, Class 0
DSCP 2 / Priority 0, Class 0
DSCP 3 / Priority 0, Class 0
DSCP 4 / Priority 0, Class 0
DSCP 5 / Priority 0, Class 0
DSCP 6 / Priority 0, Class 0
DSCP 7 / Priority 0, Class 0
All others DSCP Class 0
QoS Service Policy
Port 1 Strict priority
Port 2 Strict priority
Port 3 Strict priority
Port 4 Strict priority
Port 5 Strict priority
Port 6 Strict priority
Port 7 Strict priority
Port 8 Strict priority
Storm Control Configuration
Broadcast Rate No limit
Multicast Rate No limit
Flooded Unicast Rate No limit
-70-
 Loading...
Loading...