Intel CORE I7, CORE I5 User Manual

White Paper
Intel® Core™ i7
vPro™ Processor
Intel® Core™ i5
vPro™ Processor
The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence
that Adapts to Your Needs
Secure your PCs. Cut your costs.
Achieve more control. Now that’s smart ROI.
PCs powered by a new 2010 Intel® Core™ vPro™ processor can adapt to the needs of your business with smart security, cost-saving manageability, and intelligent, adaptable performance1. The all new 2010 Intel Core vPro processor family is designed to keep downtime and desk-side visits to a minimum, helping IT reduce costs and improve services through enhanced remote monitoring, KVM Remote Control2 (keyboard video mouse), and other tools to diagnose and repair PCs – even if the PCs are shut down or the operating system (OS) is unresponsive. Intelligent, energy-efficient performance – including Intel® Turbo Boost Technology3 – adapts to a user’s multitasking demands so the PC consumes only the power it needs. With an all new 2010 Intel Core vPro processor inside, PCs can even disable themselves via Intel® Anti-Theft Technology4 if they get lost or stolen. With a
new Intel Core vPro processor, control meets cost savings while still delivering exceptional business performance.
White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
Table of Contents
Executive Summary. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
3 |
All-New 2010 Intel® Core™ vPro™ Processor Family . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
4 |
The way we do business has changed. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
4 |
New and proven technologies pair up to deliver intelligent performance, |
|
manageability, and security. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
4 |
PCs can now be managed as strategic assets. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 5 |
Spend wisely and recoup costs rapidly . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 5 |
New in the all new 2010 Intel Core vPro processor family. . . . . . . . . . . . . . . . . . . . . . . . . |
. 5 |
Key features of the all new 2010 Intel Core vPro processor family. . . . . . . . . . . . . . . . . . . . . . |
. 6 |
What, exactly, is Intel® vPro™ technology? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
7 |
Intelligent features to solve key challenges. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 7 |
Manage PCs regardless of power state. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 8 |
Use an existing management console for both laptop and desktop PCs. . . . . . . . . . . . . . . . . . . |
9 |
Remote communication – virtually anytime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 9 |
Communication outside the corporate firewall. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Communicate remotely with wired or wireless PCs . . . . . . |
. . . . . . . . . . |
. . . . . |
. . . . . . . 10 |
PC-initiated secure communication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 |
|||
Robust security schemes for remote communication . . . . . |
. . . . . . . . . . |
. . . . . |
. . . . . . . 11 |
Better protection through smarter security. . . . . . . . . . . |
. . . . . . . . . . |
. . . . . . . . . . . . 11 |
|
Intel® Anti-Theft Technology (Intel® AT). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 |
|||
Hardware-based acceleration for encryption. . . . . . . . . |
. . . . . . . . . . |
. . . . . |
. . . . . . . 13 |
Push updates down the wire — regardless of PC power state. . . . . . . . . . . . . . |
. . . . . . . . . 13 |
|
Filter threats and isolate PCs automatically based on IT policy. . . . . . . . . . . . . . . . . . . . . . . . . . . |
. . . . . . . . . . |
. . . . . . . . 14 |
Automated, continual checking for agents. . . . . . . . . . . . . . . . . . . . . . . . |
. . . . . |
. . . . 14 |
Receive alerts even if a system is off the corporate network. . . . . . . . . . . . . . . |
. . . . . |
. . . . 15 |
Out-of-band management even with 802 1x, Cisco SDN, and Microsoft NAP. . . . . . . |
. . . . . |
. . . . 15 |
Intel® Trusted Execution Technology (Intel® TXT) . . . . . . . . . . . . . . . . . . . . |
. . . . . |
. . . . 15 |
Faster, easier remote manageability helps reduce costs. . . . . . . . . . . . . . . . . . |
. . . . . |
. . . . 15 |
Remote upgrades save IT and user time. . . . . . . . . . . . . . . . . . . . . . . . . |
. . . . . |
. . . . 15 |
Resolve more problems remotely . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Accurate, remote discovery and inventory for wired or wireless systems. . . . . . . . |
. . . . . |
. . . . . 17 |
KVM Remote Control lowers support costs. . . . . . . . . . . . . . . . . . . . . . . |
. . . . . |
. . . . 17 |
PC Alarm Alock – local wake from any sleep state. . . . . . . . . . . . . . . . . . . . |
. . . . . |
. . . . 18 |
Power down at night and save on power bills. . . . . . . . . . . . . . . . . . . . . . |
. . . . . |
. . . . 18 |
Virtualization enables flexible computing models. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Usage models. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Virtualization: Virtual containers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Virtualization: Multiple OSs (traditional model). . . . . . . . . . . . . . . . . . . . . . . . . . . |
. . . . 20 |
|||
Intel® Virtualization Technology (Intel® VT) features. . . . . . . . . . . . . . . . . . . . . . . . |
. . . . 21 |
|||
Intel® VT is compatible with other technologies. . . . . . . . . . . . . . . . . . . . . . . . . . |
. . . . 21 |
|||
Key benefits of virtualization. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. |
. |
. |
. 21 |
Go mobile – cut costs and improve productivity. . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. |
. |
. |
. 22 |
Wireless mobility. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Responsive, energy-efficient intelligent performance. . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Energy Star compliance and energy efficient. . . . |
. . . . . |
. . . . . . . . . . |
. . . . . |
. . . . . |
. |
. |
23 |
Intel® Turbo Boost Technology. . . . . . . . . . . |
. . . . . |
. . . . . . . . . . |
. . . . . |
. . . . . |
. |
. |
23 |
Intel® Hyper-Threading Technology. . . . . . . . . |
. . . . . |
. . . . . . . . . . |
. . . . . |
. . . . . |
. |
. |
24 |
Simplify and speed up activation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
General provisioning process. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Methods to establish security credentials. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Activation models. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. . . . 25 |
||||
Ready for the future. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. |
. |
. |
. |
25 |
Stable, standards-based, and with broad industry support. . . . . . . . . . . . . . . . . . . . . . |
. |
. |
. |
. |
26 |
Wired or wireless: The intelligence of security and manageability on every chip. . . . . . . . . . . . |
|
. |
. |
. |
. 26 |
2
White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
Executive Summary
The all new 2010 Intel® Core™ vPro™ processor family can help businesses by delivering intelligent security; cost-saving remote manageability; and adaptable performance. Smart security with programmable filters can systematically guard against viruses and malicious attacks. Continuous, intelligent polling for the presence of software agents helps ensure full protection from malware and attacks. Advanced features help prevent tampering or disabling of security software. With built-in Intel® Anti-Theft Technology4 (Intel® AT), PCs can even disable themselves if they are lost or stolen. And, because data is protected rather than erased, reactivation can be easy when the PC is recovered. Intel AT must be enabled in order to enjoy the benefits of this advanced security technology.
The all new 2010 Intel Core vPro processor family makes it easier to manage systems from a central location. KVM Remote Control2
(keyboard video mouse) and other built-in capabilities let you remotely configure, diagnose, isolate, and repair an infected PC – even if the OS is unresponsive1. You can also quickly upgrade to Windows* 7 remotely
and overnight – saving on average about 40 minutes per upgrade per machine.5 This helps minimize disruptions to your users and makes it easier to retain access to your legacy applications. In order to enjoy the benefits of these intelligent remote manageability capabilities, Intel® vPro™ technology must be activated (see page 25 of this white paper).
Laptops powered by a new Intel Core vPro processor include Intel® Centrino® wireless technology (either WiFi or WiFi with optional WiMAX), and are more energy efficient. These laptop and desktop PCs also include Intel® Turbo Boost Technology3 and Intel® Hyper-Threading Technology6 (Intel® HT Technology), which can automatically adapt to each user’s unique needs so users can move faster when multitasking and get more accomplished in less time.
Studies have shown that return on investment (ROI) can be as little as 19 months for PCs based on the a new 2010 Intel® Core™ i5
processor.7 For businesses that implement the remote management and security capabilities of a PC with a new 2010 Intel Core i5 vPro processor, positive ROI can be achieved in as little as 9 months.7
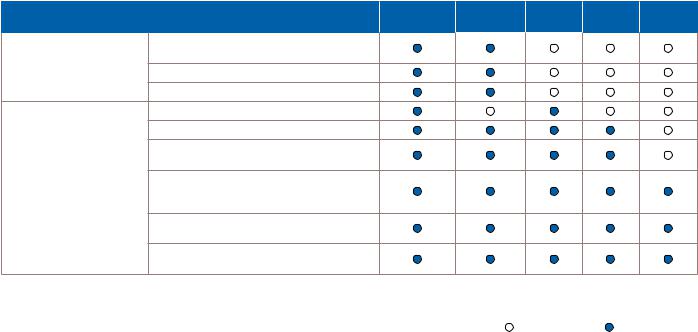
Lineup of all new 2010 Intel® Core™ processor family and all new 2010 Intel® Core™ vPro™ processor family.
Choose the Intel® Core™ processor |
Intel® Core™ |
Intel® Core™ |
Intel® |
Intel® |
Intel® |
|
that meets your business needs |
i7 vPro™ |
i5 vPro™ |
Core™ i7 |
Core™ i5 |
Core™ i3 |
|
Intelligent Performance, |
Hardware-assisted smart security, anti-theft |
|
|
|
|
|
Security and Manageability |
technology and cost-saving manageabilitya |
|
|
|
|
|
|
Hardware-based KVM Remote Control2,a,b |
|
|
|
|
|
|
Hardware-assisted remote power managementa |
|
|
|
|
|
Intelligent Business |
Top-of-the-line performance with biggest cache |
|
|
|
|
|
Performance |
Hardware-based acceleration of encryption8 |
|
|
|
|
|
|
|
|
|
|
|
|
Increased processor speeds when performance is needed with Intel® Turbo Boost Technology3
Hardware-assisted virtualization support for running multiple operating systems, such as Windows* XP with Windows* 79
Intelligent performance with Intel® Hyper-Threading
Technology6 and Intel® Smart Cache
Energy Efficiency with Intel® Intelligent
Power Technology
aIT must activate Intel® vPro™ technology in order to take advantage of these intelligent security and remote manageability technologies. For more information about activating Intel vPro technology, which includes Intel® AMT and Intel® AT, see page 25 of this white paper.
bHardware-based KVM Remote Control works on all new 2010 Intel® Core™ i5 vPro™ processor-based PCs that have Intel® HD integrated graphics, and select all new 2010 Intel® Core™ i7 vPro™ processor-based PCs that have Intel® HD integrated graphics. Hardware-based KVM Remote Control will not work on PCs that use discrete graphics.
Not applicable |
Advanced capability |
3
White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
All New 2010 Intel® Core™ vPro™ Processor Family
Intelligent security, remote manageability, and adaptable performance to help businesses cut costs and improve efficiencies
The way we do business has changed
In today’s global markets, business is increasingly borderless, and mobility is becoming mandatory. The amount of e-mail that corporate users manage each day has also increased dramatically. Video has become mainstream for corporate communications – the use of video conferencing alone is expected to double from 2007 to 2012.10 At the same time, countries around the world are implementing increasingly stringent energy-compliance regulations for PCs. In addition, security threats continue to grow each year. Along with increased purchasing power in emerging markets, these shifts are driving major changes in business models worldwide.
Today’s business challenges include:
•Critical need to become more efficient, reducing costs while still reaching new customers
•Increased demand for video tools for mainstream communications, both internal, such as for sales and marketing, and external, for customers
•Exponential increase in security threats, along with a shift from ego-based attacks to economically focused attacks
•Pressure from governments around the world to use PCs that are more environmentally friendly and consume less power
Information Technology (IT) managers face a corresponding set of challenges in managing PCs as strategic assets:
•Support an increasingly mobile workforce.
•Protect networks and assets both inside and outside the corporate firewall.
•Reduce operating costs for managing and securing PCs.
•Support new, compute-intensive applications and the transition to Windows* 7.
Organizations can no longer wait to capitalize on global integration and advanced technology tools. The challenge for IT is to support business goals, managing PCs as strategic assets. To do so, IT organizations need laptop and desktop PCs that are easier to configure, manage, use, and secure.
New and proven technologies pair up to deliver intelligent security, remote manageability, and adaptable performance
Control meets cost savings in laptop and desktop PCs powered by the all new Intel® Core™ vPro™ processor family.
Laptop and desktop PCs with a new Intel Core vPro processor deliver intelligent performance and unique hardware-assisted features that improve security, remote manageability, and energy management.
•New 2010 Intel® Core™ i5 vPro™ processor-based PCs1
•New 2010 Intel® Core™ i7 vPro™ processor-based PCs1
New features in this new generation of processors include intelligent security, such as Intel Anti-Theft Technology, and easier manageability – including KVM Remote Control2 (hardware-based keyboard video mouse) and PC Alarm Clock. Additional new features for adaptable performance include Intel® Turbo Boost Technology,3 as well as AES-NI8 (advanced encryption standard – new instructions), to improve performance for encryption and decryption. For example, using Intel AT, you can remotely disable a PC with a “poison pill” that locks down the
system after it has been reported lost or stolen.
Access the PC virtually anytime, anywhere
The hardware-based capabilities of the all new 2010 Intel Core vPro processor family are built directly into the PC’s hardware. The
capabilities let authorized technicians remotely access PCs that have traditionally been unavailable to the management console. Technicians can now manage the laptop or desktop PC even if PC power is off,
the OS is unresponsive, hardware (such as a hard drive) has failed, or management agents are missing. Best of all, technicians can remotely maintain, update, and repair both laptop and desktop PCs that are outside the corporate firewall on an open wired or wireless connection via a secure, protected tunnel.
4
White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
PCs can now be managed as strategic assets
With the new 2010 Intel Core vPro processors, businesses can significantly cut IT service costs, reduce power bills, increase efficiency, and improve productivity. For example:
•Experience up to 2x faster multitasking11 and up to 3.5x faster encryption/decryption of sensitive data on a new Intel® Core™ i5 processor.11
•Cut PC maintenance costs by up to 50%7.
•Speed up patch saturation by 56%12 and reduce patch deployment costs by up to 98%13.
•Shift more workers to laptops and gain up to 51 more minutes per user per day in user productivity.14
•Reduce energy costs enabled by secure remote power up/down15.
Spend wisely and recoup costs rapidly
Less-capable PCs can get bogged down when trying to support the latest OS, such as Windows 7, or the latest application updates.
After 3 years, annual PC support costs can exceed the purchase price for a new PC7. On average, a 4-year-old PC can cost 59% more to support than it did in its first year.7 In addition, 3-year-old PCs are 53% more likely per year to experience a security incident.7 Worse, a single PC out of compliance can create an expensive security incident – up to $300,000 or more in costs – but businesses do not always budget for the full cost of a security breach16.
Laptop and desktop PCs with a new Intel Core vPro processor can handle the latest multi-threaded OSs, end-user applications and IT software load – including Windows 7, Office* 2007, encryption software, application streaming, and video conferencing. These PCs can also be more easily secured, via intelligent client-side capabilities, as well as through remote security features, such as PC disable via
“poison pill” responses. With better remote troubleshooting and problem resolution – through secure console redirection and KVM Remote Control – IT can reduce user downtime, help improve user productivity, keep desk-side visits to a minimum, and help businesses significantly reduce TCO.
In an environment in which businesses have a critical need to spend wisely, this new generation of PCs makes it easier for organizations to manage systems as strategic assets. In fact, studies show that businesses can recoup their investment in as little as 9 months.7
Refreshing wisely means keeping TCO at a minimum. Refreshing with PCs with new Intel Core vPro processors can help you achieve a positive ROI rapidly and continuously for years to come.
New in the all new 2010 Intel Core vPro processor family
The new 2010 Intel Core vPro processors includes powerful new capabilities built into the hardware:
•Intel Anti-Theft Technology (Intel AT), lock down and “brick” the PC if it fails to check in to the central server, or if it fails preboot login based on local, hardware-level preboot/OS IT-defined rules. As part of the lockdown, delete or disable critical elements of encryption keys in order to prevent access to the keys and stored data. Allow rapid reactivation, integrated with existing software vendor preboot login.
•Manageability of PCs with encrypted hard drives – remotely unlock encrypted drives that require pre-boot authentication, even when the OS is inoperable or software agents are missing. Remotely manage data security settings even when PC is powered down.
•AES-NI instructions (Advanced Encryption Standard New Instructions)8. which offload from the processor some of the performance burden of encryption, and file decryption.
•KVM Remote Control,2 a new hardware-based feature that works for wired and wireless PCs with a new Intel Core vPro processor that have integrated Intel® HD Graphics. This feature helps IT remotely resolve the most complex software failures, and eliminates the need
to purchase and maintain costly hardware KVM switches in the production environment. KVM Remote Control works for PCs both inside and outside the corporate firewall.
•Fast call for help for wired or wireless systems, even beyond the firewall.17 Helps users avoid the costly downtime of shipping PCs back to IT to be fixed. If a PC crashes, a user can phone IT for help and, during the boot process, press a specific key to securely connect the PC to IT for troubleshooting. IT can then take over via remote console redirection or hardware-based KVM Remote Control.
•PC Alarm Clock,1 a new hardware-based feature that lets IT schedule a PC to wake itself from any idle, powered off, or sleep state without a network connection. The PC can then perform scheduled, IT-defined tasks, such as initiate a secure call to the service center for automated,
off-hour services – even if outside the corporate firewall. As with other features, PC Alarm Clock is configured via a management console. However, once the feature is implemented, businesses do not need
a management console to access or use the feature in their production environment. PC Alarm Clock works even if there is no network or communication with the PC. For example, the feature allows independent software vendors (ISVs), such as McAfee, to enable IT-scheduled product updates even for businesses that don’t have an IT console.
5
White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
Key features of the all new 2010 Intel Core vPro processor family
The all new 2010 Intel Core vPro processor family delivers unique and powerful technologies in security, remote manageability, energy management, mobility, virtualization, and performance improvements. Tables 1 and 2 list some of the key features
of laptop and desktop PCs with a new Intel Core vPro processor.
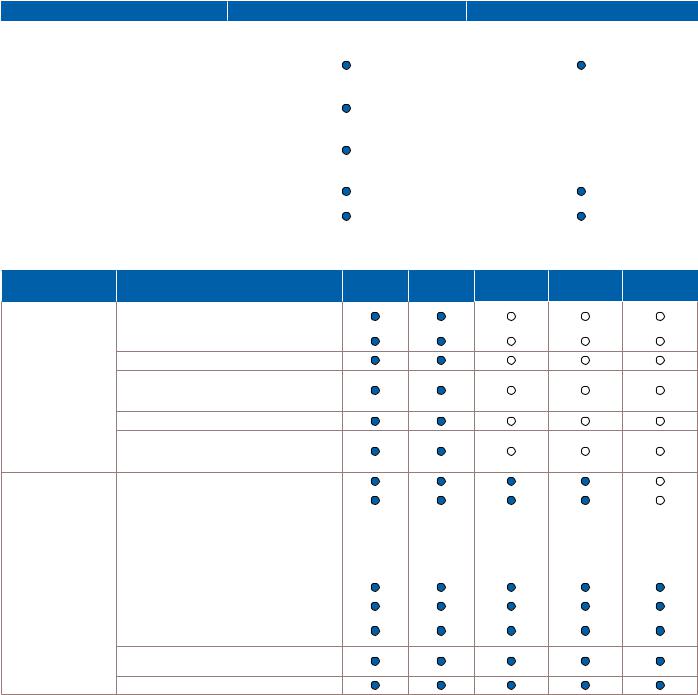
Table 1. Laptop and desktop PCs with a new Intel® Core™ vPro™ processor.
Feature |
Laptop with Intel® Core™ vPro™ processor |
Desktop PC with Intel® Core™ vPro™ processor |
|
|
|
All new 2010 Intel® Core™ vPro™ processor family |
Intel® Core™ i5 vPro™ processor and Intel® Core™ i7 vPro™ |
Intel® Core™ i5 vPro™ processor and Intel® Core™ i7 vPro™ |
|
processor with Intel® QM57 or QS57 Express Chipsets |
processor with Intel® Q57 Express Chipset |
|
|
|
Intel® Active Management Technology1 |
|
|
(Intel® AMT), release 6.0 |
|
|
|
|
|
Intel® Gigabit network connection |
Intel® 82567LM-3 |
Intel® 82566DM |
|
|
|
Support for 802.11agn wireless protocols |
|
N/A |
|
|
|
WiFi and optional WiMAX support, with either |
|
|
Intel® WiMAX/WiFi 6060 2x2 agn, Intel® Centrino® |
|
|
Ultimate-N/Advanced-N 6000 Series 2x2 or |
|
N/A |
3x3 agn, or Intel® Centrino® Wireless-N 1000 |
|
|
Series 1x2 bgn |
|
|
|
|
|
Support for 802.1x |
|
|
|
|
|
Intel® Stable Image Platform Program |
|
|
(Intel® SIPP)18 |
|
|
Table 2. All new 2010 Intel® Core™ processor family and all new 2010 Intel® Core™ vPro™ processor family.
|
|
Intel® Core™ |
Intel® Core™ |
|
Features for... |
Description |
i7 vPro™ |
i5 vPro™ |
Intel® Core™ i7 Intel® Core™ i5 Intel® Core™ i3 |
Intelligent Performance, |
Hardware-assisted smart security,1 anti-theft |
|
|
|
Security and |
technology and cost-saving manageabilitya |
|
|
|
Manageability |
|
|
|
|
Hardware-assisted remote power managementa |
|
|
|
|
|
|
|
|
Hardware-based KVM Remote Controla,b,2
Intel® Virtualization Technology9 (Intel® VT) including Intel® VT for Directed I/O, and support
for OS and application streaming
Intel® Trusted Execution Technology19 (Intel® TXT)
Support for Cisco Self-Defending Network* (Cisco SDN*), Microsoft Network Access Protection* (NAP), and PXE (preexecution environment)
Intelligent Business |
Hardware-based acceleration of encryption8 |
|
|
|
|
|
Performance |
|
|
|
|
|
|
Intel® Turbo Boost Technology3 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Intel® Smart Cache Technology and new L3 cache |
Up to |
Up to |
Up to |
Up to |
Up to |
|
|
8 MB L3 |
4 MB L3 |
8 MB L3 |
4 MB L3 |
4 MB L3 |
|
|
|
|
|
|
|
|
Number of processor cores |
2 to 4 cores |
2 cores |
2 to 4 cores |
2 cores |
2 cores |
|
|
|
|
|
|
|
|
Intel® Hyper-Threading Technology6 |
4 to 8 threads |
4 threads |
4 to 8 threads |
4 threads |
4 threads |
|
64-bit enabled20 |
|
|
|
|
|
Support for Operating |
Windows* 7 ready |
|
|
|
|
|
System Requirements |
|
|
|
|
|
|
Hardware-assisted virtualization for Windows* XP |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
in Windows* 7c |
|
|
|
|
|
Intel integrated graphics support of 64-bit graphics, including Windows 7 Aero interfaced
Execute Disable Bit21
aIT must activate Intel® vPro™ technology in order to take advantage of these intelligent security and remote manageability technologies. For more information about activating Intel vPro technology, which includes Intel® AMT and Intel® AT, see page 25 of this white paper.
bHardware-based KVM Remote Control is available on Intel® Core™ i5 vPro™ and Intel® Core™ i7 vPro™ processors that have Intel integrated graphics.
cHardware-assisted Intel® Virtualization Technology (Intel® VT) can significantly improve performance for users running a legacy OS (for example, Windows* XP) in Windows 7. dSome new Intel Core processors do not include integrated graphics. Some allow for discrete graphic cards.
6

White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
What, exactly, is Intel® vPro™ technology?
Intel® vPro™ technology is a set of IT capabilities – manageability, security, power management – embedded into the hardware of all new 2010 Intel Core vPro processor family-based PCs. Because the capabilities are built into the hardware, they are available virtually anytime, even if the OS is inoperable, PC power is off, or the hard drive has failed.
•Intelligent security. Disable a PC and/or disable access to the data even if the PC is already lost or stolen. Encrypted PCs are also fully manageable if PC power is off, the OS is unavailable, or the hard drive has failed.
•Expanded management capabilities. Remotely access, control, and manage client PCs “as if you were there” with hardware-based KVM Remote Control. Save power and keep up with compliance by scheduling PCs to wake from off to run local tasks according to policy.
•Improved power management and rapid ROI. Realize rapid ROI simply by implementing better power management enabled by Intel vPro technology.
Intel vPro technology takes advantage of an intelligent processor, chipset, and networking silicon features, along with protected flash memory. When combined with existing independent software vendor (ISV) consoles that support Intel vPro technology, Intel vPro technology can deliver a comprehensive, tamper-resistant solution for security and manageability.
A key benefit of being embedded in hardware is that the capabilities are less susceptible to the problems that typically affect an OS, applications or hard drive. For example, because Intel vPro technology is designed into PC hardware, it is resistant to tampering, boot issues, and other problems that can affect an OS and/or security applications.
Intelligent features to solve key challenges
The all new 2010 Intel Core vPro processor family can provide a comprehensive solution to manageability and security challenges. Table 3 provides an overview of some of the features of these new processors. New features and some of the more critical proven technologies are described in detail later in this paper.
Table 3. Key IT challenges and solutions addressed with a new 2010 Intel® Core™ vPro™ processor-based PC.
Challenge |
Solutiona |
PCs unmanageable when |
Remotely and securely monitor and manage PCs anytime: |
powered down1 |
• Access the PC even if PC power is off, the OS is unresponsive, management agents are missing, or hardware |
|
(such as a hard drive) has failed. |
|
• Access critical system information (asset information, event logs, BIOS information, etc.) virtually anytime, even if |
|
PC power is off, to identify systems that need maintenance or service. |
|
• Remotely and securely power up PCs for maintenance and service, initiated by the service center. |
|
• PC Alarm Clock, in which client-side intelligence performs a scheduled wake from any powered off or sleep states, so |
|
the PC itself can call in and initiate a maintenance, security or other task off-hours. |
|
|
Unsecured communications with PCs |
More securely communicate with laptop and desktop PCs both inside or outside the corporate firewall: |
|
• Secure, remote communication inside the firewall. |
|
• Secure, remote communication outside the firewall, on an open wired or wireless LAN. |
|
|
Spiraling and costly deskside visits |
Significantly reduce deskside visits with: |
|
• Remote remediation, even if management agents are missing or the OS is unresponsive. |
|
• Remote problem resolution, even if the OS is unresponsive or hardware (such as a hard drive) has failed. |
|
• KVM Remote Control2 to help resolve complex issues, so you can see exactly what the user sees, and repair the PC |
|
more effectively from a remote location. |
|
|
Protect assets from |
Protect assets better: |
software-based attacks |
• Remotely power up PCs anytime to help ensure more complete saturation for patching and other updates. |
|
• Built-in, programmable system defense filters and agent-presence checking for automated, hardware-based |
|
protection against viruses and attacks. |
|
|
Thwart thieves – secure assets and |
Disable or “brick” a PC and/or protect its data virtually anytime: |
data even if the PC is lost or stolen4 |
• Poison-pill to “brick” a lost or stolen PC; data is not destroyed or lost in the process, and reactivation is rapid, simply by |
|
entering an authentication token. |
|
• Remote notification via a 3G modem in a cell phone, to flag a system that might be in the process of being stolen. |
|
• Built-in, programmable triggers and responses to protect data and the PC after loss or theft of the system.4 |
|
• Intelligent, policy-based PC-side timers that trigger a lockdown if the user has not logged in before timer expiry. |
|
|
Lack of configuration compliance |
Ensure compliance: |
|
• Remote inventory and agent presence checking as a hardware-based, automated, policy-based service. |
|
|
Costly and time-consuming |
Eliminate virtually all manual inventories: |
manual inventories |
• Accurate, remote asset inventories, even if PCs are powered off or management agents are missing. |
|
|
Undiscoverable assets |
Discover virtually all PCs: |
|
• Persistent device ID available anytime, even if PC power is off, the OS has been rebuilt, hardware or software |
|
configuration has changed, or the hard drive has been reimaged. |
|
|
Reimage systems without |
Reduce deskside visits, speed up remote deployment, and minimize user interruptions: |
a deskside visit |
• Remotely reimage systems even if PC power is off at the start of the upgrade cycle. |
|
|
aIT must activate Intel® vPro™ technology in order to take advantage of these intelligent security and remote manageability technologies. For more information about activating Intel vPro technology, which includes Intel® AMT and Intel® AT, see page 25 of this white paper.
7

White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
Manage PCs regardless of power state
PCs based on the all new 2010 Intel Core vPro processor family are designed to give IT technicians greater remote visibility into and access to the system in both wired and wireless states, as described in Table 4. When managing PCs with the all new 2010 Intel Core vPro processor family, technicians can remotely power up a PC almost anytime. (In order to prevent unexpected battery use in laptops, remote power-up is not applicable to the battery-powered, wireless sleep state.) Technicians can also reboot the PC, use secure console redirection and KVM Remote
Control, and use other critical maintenance and management capabilities of a new 2010 Intel Core vPro processor for wired or wireless PCs. PCs can even perform their own local, scheduled wake from any powered-off state without a network connection. The PC can then call into a central server for updates, maintenance, and other off-hours tasks.
With the ability to remotely manage PCs regardless of power state, IT can streamline more work and implement more automation. In turn, this helps business minimize user downtime, reduce IT service costs, and realize a rapid ROI.
Table 4. Capability matrix for PCs with new 2010 Intel® Core™ vPro™ processors.
|
|
|
|
Works with wired |
AC-powered wired or wireless |
Battery-powered |
|||||
|
|
|
|
laptop or wired desktop |
wired or wireless laptop |
||||||
|
|
|
|
PC-initiated secure |
|||||||
|
|
|
|
|
|
|
|
|
|
||
Use Cases |
|
Usages |
|
communication outside |
AWAKE, |
AWAKE, |
|
AWAKE, |
AWAKE, |
|
|
a |
a |
corporate firewall |
a |
PROPERLY |
UNRESPONSIVE |
|
PROPERLY |
UNRESPONSIVE |
|
||
|
|
|
OS WORKING |
BUT OS |
Asleep (Sx) |
OS WORKING |
BUT OS |
Asleep (Sx) |
|||
|
|
IT remotely powers PC down, then |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Remote power |
up again to reset to clean state |
|
|
|
|
YES |
YES |
|
N/A |
||
(or powers up PC for servicing). |
YES |
|
YES |
YESb |
YESb |
||||||
up/power cycle |
|
||||||||||
Use power management to |
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
||
|
|
reduce energy costs. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Remote |
|
Power up PCs during off hours |
|
|
|
|
|
|
|
|
|
|
for software updates. Also client- |
YES |
|
YES |
YESb |
YES |
YES |
YESb |
N/A |
||
software update |
initiated scheduled wake for |
|
|||||||||
|
|
|
|
|
|
|
|
||||
|
|
update. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Agent presence |
Ensure critical applications are |
|
|
|
|
|
|
|
|
||
checking and |
|
running, and be quickly notified |
YES |
|
YESc |
YESb |
N/A |
YESc |
YESb |
N/A |
|
alerting |
|
when they miss a check in. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
System isolation |
Automated or manual policy-based |
YES |
|
YES |
YESb |
N/A |
YES |
YESb |
N/A |
||
and recovery |
|
protection against virus outbreaks. |
|
||||||||
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Identify and prevent unauthorized |
|
|
|
|
|
|
|
|
|
Protection for |
access to encrypted data, or disable |
|
|
|
|
|
|
|
|
||
the laptop remotely or via client-side |
|
|
YESc |
YES |
|
YESc |
YES |
|
|||
data if a laptop |
intelligence if it is lost or stolen. |
N/A |
|
N/A |
N/A |
||||||
is lost or stolen |
Upon lock-down, disable or delete |
|
|
for laptops |
for laptops |
|
for laptops |
for laptops |
|
||
|
|
|
|
|
|
|
|
||||
|
|
access to encryption keys. Rapid |
|
|
|
|
|
|
|
|
|
|
|
reactivation if laptop is returned. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Diagnose and repair problems |
|
|
|
|
|
|
|
|
|
Remote |
|
remotely via out-of-band event |
|
|
|
|
|
|
|
|
|
|
log, remote/redirected boot, |
|
|
|
|
|
|
|
|
||
diagnosis and |
YES |
|
YES |
YESb |
YES |
YES |
YESb |
N/A |
|||
console redirection, KVM Remote |
|
||||||||||
repair |
|
|
|
|
|
|
|
|
|
||
|
Control,2 and preboot access to |
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
||
|
|
BIOS settings. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Remote |
|
Take a hardware or software |
|
|
|
|
|
|
|
|
|
hardware and/or |
|
|
|
|
YES |
YES |
|
N/A |
|||
inventory regardless of OS state or |
YES |
|
YESc |
YESb |
YESb |
||||||
software asset |
|
||||||||||
power state. |
|
|
|
|
|
|
|
|
|
||
tracking |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
aIT must activate Intel® vPro™ technology in order to take advantage of these intelligent security and remote manageability technologies. For more information about activating Intel vPro technology, which includes Intel® AMT and Intel® AT, see page 25 of this white paper.
bRequires WPA or WPA2/802.11i security and Controller Link 1 for wireless operation when the user OS is down.
cAlso available when using host OS-based VPN.
8
White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
Use an existing management console for both laptop and desktop PCs
PCs with a new 2010 Intel Core vPro processor can use the same management console and communication mechanisms as other PCs. You can manage both laptop and desktop PCs with a new Intel Core vPro processor from the same IT console.
LeadingmanagementsoftwarecompaniessuchasHP,LANDesk,
Microsoft, and Symantec have optimized their software to take advantage of the intelligent capabilities of a new 2010 Intel Core vPro processor. For small businesses with less than 500 PCs, IT administrators can turn to managementsoftwaresuchasN-ableTechnologies’N-central*totake advantage of a new 2010 Intel Core vPro processor.
These vendors support both previous and current versions of Intel vPro technology. IT administrators who have already deployed PCs with Intel vPro technology do not have to change their management console to use PCs with a new 2010 Intel Core vPro processor. Ask your manage- ment-console vendor about specific implementation schedules and support for the new hardware-based security and remote-manage- ment capabilities for both laptop and desktop PCs.
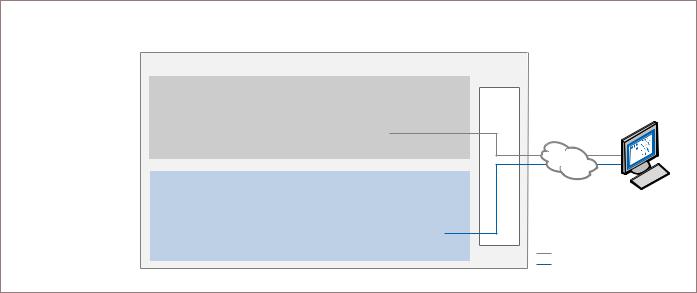
Remote communication – virtually anytime
Software-only management applications are usually installed at the same level as the OS (see Figure 1). This leaves their management agents vulnerable to tampering. Communication privacy is also an issue in today’s PCs because the in-band, software-based communication channel they use is not secure.
In contrast, the all new 2010 Intel Core vPro processor family delivers both “readily-available” (out-of-band) remote communication built into the PC, as well as robust security technologies. These security technologies help ensure that the powerful capabilities of Intel vPro technology, as well as your stored information, are better protected.
The communication channel used by Intel vPro technology runs “under” or outside the OS (see Figure 1). This out-of-band (OOB) channel is based on the TCP/IP firmware stack designed into PC hardware, and does not use the software stack in the OS. The channel allows critical system communication (such as alerting) and operations (such as agent presence checking, remote booting,
and console redirection) to continue more securely virtually anytime, even if OS, applications, or hard drive have failed.
A new 2010 Intel® Core™ vPro™ processor uses an out-of-band communication channel to communicate with the IT console
PC
In-band communication goes through the software stack in the OS, and Is secured via OS features and softwarebased security applications
Out-of-band communication tunnel sits “below” the OS and applications, goes through the
TCP/IP firmware stack, and is secured with hardware-based TLS encryption
Hard drive and memory with OS and applications – “In-band” communication
|
System memory |
|
|
OS and applications |
||
|
|
|
|
|
|
|
|
RAM |
|
|
|
Software stack |
|
|
|
|
||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Motherboard – Communication below the OS (out-of-band)
|
|
Isolated, |
|
|
Intel® processor |
|
|
|
Intel® chipset |
||||||
|
|
|
|
|
|
|
|
|
|
||||||
|
tamper-resistant memory |
|
|
|
|
|
|
|
Firmware |
|
|||||
|
|
|
|
Intel® AMT |
|
|
|
New 2010 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
TCP/IP |
|
|
||
|
|
|
|
|
|
|
Intel® Core™ |
|
|
|
|
|
|
||
|
BIOS |
|
|
nonvolatile |
|
|
|
vPro™ Processor |
|
|
|
|
firmware stack |
|
|
|
|
|
|
memory |
|
|
|
|
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Intel® network adapter
Internet
IT console
In-band communication
Out-of-band communication
Figure 1. Out-of-band communication. Secure communication channel runs “under” or outside the OS regardless of the health of the operating system or the power state of the PC, even if the PC’s hard drive is removed.
9
 Loading...
Loading...