IBM OS-390 User Manual
OS/390 |
IBM |
Security Server (RACF)
Planning: Installation and Migration
GC28-1920-03
OS/390 |
IBM |
Security Server (RACF)
Planning: Installation and Migration
GC28-1920-03

Note
Before using this information and the product it supports, be sure to read the general information under
Fourth |
|
Edition, |
September |
1997 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||
This |
is |
a |
major |
revision |
of |
GC28-1920-02. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||
This |
edition |
applies |
to |
Version |
2 |
Release 4 |
of |
|
OS/390 |
(5647-A01) |
and to all subsequent |
releases |
and |
modifica |
||||||||||||||||
indicated |
in |
new |
editions. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||
Order |
publications |
through |
your |
IBM |
representative |
or |
the IBM |
branch |
office |
serving |
your atlocalitythe . |
Publicati |
||||||||||||||||||
address |
below. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
IBM |
|
welcomes |
your |
comments. A |
form |
for |
readers' |
comments |
may |
be |
provided at |
the back |
of |
this |
publication, |
|||||||||||||||
your comments to the following address: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||||
|
International |
Business |
Machines |
Corporation |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||||||
|
Department |
55JA, |
Station |
P384 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||||
|
522 |
South |
Road |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||
|
Poughkeepsie, NY 12601-5400 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||
|
United |
States |
of |
America |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||
|
FAX |
(United |
States |
& |
Canada): |
1+914+432-9405 |
|
|
|
|
|
|
|
|
|
|
|
|
||||||||||||
|
FAX |
(Other |
Countries): |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||
|
|
Your International Access Code +1+914+432-9405 |
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||||||
|
IBMLink |
|
(United |
States |
customers |
only): KGNVMC(MHVRCFS) |
|
|
|
|
|
|
|
|
|
|
||||||||||||||
|
IBM Mail Exchange: USIB6TC9 at IBMMAIL |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||||||||
|
Internet e-mail: mhvrcfs@vnet.ibm.com |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||||||||
|
World |
Wide |
Web: |
http://www.s390.ibm.com/os390 |
|
|
|
|
|
|
|
|
|
|
|
|
||||||||||||||
If |
|
you |
would |
like |
a |
reply, |
be |
sure |
to |
include |
your |
name, |
address, |
telephone number, |
or |
FAX number. |
||||||||||||||
Make |
sure |
to |
include the following in your comment |
|
or |
note: |
|
|
|
|
|
|
|
|
||||||||||||||||
Ÿ |
Title |
and |
order |
number |
of |
this |
book |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||
Ÿ Page number or topic related |
to |
your |
comment |
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||||
When you send information to |
IBM, you |
grant |
IBM |
a nonexclusive right to use or distribute the information i |
||||||||||||||||||||||||||
appropriate |
without |
incurring |
any |
obligation |
to |
you. |
|
|
|
|
|
|
|
|
|
|
||||||||||||||
|
Copyright |
|
International |
Business |
Machines |
Corporation |
1994, |
1997. |
All |
rights |
reserved. |
|
|
|
|
|
|
|
||||||||||||
Note to U.S. Government Users — |
Documentation related to restricted rights — Use, duplication or disclosure |
|||||||||||||||||||||||||||||
restrictions |
set |
forth |
in |
GSA |
ADP |
Schedule |
Contract |
|
with |
IBM |
Corp. |
|
|
|
|
|
|
|||||||||||||

Contents
Notices |
. . . . . . . . . . . . . . . . . . . vii. . . . |
|
Trademarks |
. . . . . . . . . . . . . . . . . . .ix . . . |
|
About |
This Book |
. . . . . . . . . . . . . . . . . . . . . . . . . . .xi. . . . . |
Who |
Should |
Use This Book. . . . . . . . . . . . . . . . . . . . . . . xi. . . . . . |
How to Use This .Book. . . . . . . . . . . . . . . . . . . . . . . . xi. . . . . .
Where to Find More Information. . . . . . . . . . . . . . . . . . . .xii. . . . .
IBM Systems Center Publications. . . . . . . . . . . . . . . . . . . xiii. . . . . .
Other |
Sources |
of Information. . . . . . . . . . . . . . . . . . . . .xiv. . . . . . |
||
To Request Copies of IBM |
Publications. . . . . . . . . . . . . . . . .xv. . . . |
|||
Summary |
of |
Changes |
. . . . . . . . . . . . . . . . . . . . . . . .xvii. . . . . . |
|
Chapter |
1. Planning for |
Migration |
. . . . . . . . . . . . . . . . . . . 1. . . . . |
|
Migration |
Planning |
Considerations. . . . . . . . . . . . . . . . . . . . .1 . . . . . |
||
Installation Considerations. . . . . . . . . . . . . . 2. . . . |
||||
Customization Considerations . . |
. . . . . . . . . . . .2 . . . |
|||
Administration Considerations . . . . . . . . . . . . . .2 . . .
Auditing Considerations . . . . . . . . . . . . . . . 3. . . .
Application |
Development Considerations. . . . . . . . . . . . . . . . . .3. . . . . |
||||||||||
General User Considerations. . . . . . . . . . . . . . . . . . . . . . .3. . . . . |
|||||||||||
Chapter 2. Release Overview |
|
|
|
. . . . . . . . . . . . . 5 . . . . |
|||||||
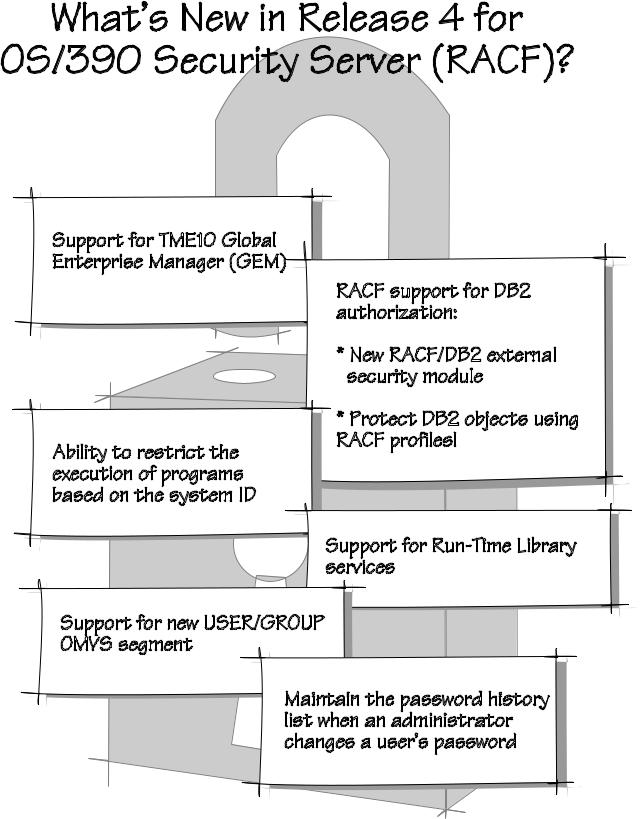
New |
and |
Enhanced |
Support. . . . . . . . . . . . . . . . . . . . . . .5 . . . . . |
||||||||
RACF/DB2 |
External |
Security Module. . . . . . . . . . . . . . . . . . .5 . . . . . |
|||||||||
Enhancements |
to |
Support |
for OpenEdition Services. . . . . . . . . . . . 6. . . |
||||||||
Run-Time |
Library Services. . . . . . . . . . . . . . . . . . . . . . .7 . . . . . |
||||||||||
Password |
History |
Enhancements. . . . . . . . . . . . . . . . . . . .7 . . . . . |
|||||||||
Tivoli |
Management |
Environment |
(TME) 10 Global Enterprise Management |
||||||||
User Administration Service. . . . . . . . . . . . . . . . . . . . . 8. . . . . . |
|||||||||||
Program |
|
Control |
by |
System |
.ID. . . . . . . . . . . . . . . . . . . .8 . . . . . |
||||||
New FMID |
|
. . . . . . . . . . . . . . . . . . 9 . . . . |
|||||||||
OW24966 |
|
Enhancements |
to |
TARGET Command |
. . . . . . . . . . . . .9 . . . |
||||||
Enable/Disable Changes . . . . . . . . . . . . . . |
10. . . . |
||||||||||
OW26237 |
Enhancements |
of |
Global Access |
Checking. . . . . . . . . . .10. . |
|||||||
Chapter |
3. |
Summary |
of |
Changes |
to |
RACF |
Components for |
OS/390 |
|
||
Release 4 |
|
|
. . . . . . . . . . . . . . . . . . |
11. . . . |
|||||||
Callable Services . |
. . . . . . . . . . . . . . . . 11. . . . |
||||||||||
Class Descriptor Table (CDT). . . . . . . . . . . . . . . . . . . . . .12. . . . . |
|||||||||||
Commands |
|
|
. . . . . . . . . . . . . . . . . . |
13. . . . |
|||||||
Data Areas |
|
. . . |
. . |
. . . . . . . . . . . . . |
15. . . . |
||||||
Exits . |
|
. . . . . . . . . . . . . . . . . . . |
16. . . . |
||||||||
Macros |
. . . . . . . . . . . . . . . . . . . .17 . . . . |
||||||||||
Messages |
|
. . . . . . . . . . . . . . . . . . .17 . . . . |
|||||||||
New Messages |
. |
. . |
. . . . . . . . . . . . . |
17. . . . . |
|||||||
Changed Messages |
. . . . . . . . . . . . . . . .17 . . . . |
||||||||||
Deleted Messages |
. . . . . . . . . . . . . . . .18 . . . . |
||||||||||
Panels |
. |
. . . |
. . |
. . . . . . . . . . . . . |
.18 . . . . |
||||||
Copyright IBM Corp. 1994, 1997
iii
SYS1.SAMPLIB |
. . . . . . . . . . . . . . . . . |
19. . . . . |
||||
Publications Library . . |
. . . . . . . . . . . . . . 20. . . . . |
|||||
Chapter 4. |
Planning Considerations |
. . . . . . . . . . . 21. . . . . |
||||
Migration Strategy . . . . . . . . . . . . . . . . |
21. . . . . |
|||||
Migration Paths for OS/390 Release 4 Security Server. . . . (RACF). . . .21. |
||||||
Hardware Requirements . . . . . . . . . . . . . . . |
22. . . . . |
|||||
Compatibility . . . . . . . . . . . . . . . . . .23. . . . . |
||||||
OpenEdition MVS |
. . |
. . . . . . . . . . . . . . 23. . . . . |
||||
Program Control by System .ID. . . . . . . . . . . . . . . . . . . 23. . . . . . |
||||||
RELEASE=2.4 |
Keyword on |
Macros . . . . . . . . . . . . . . . . . .23. . . . . |
||||
Chapter 5. |
Installation Considerations |
. . . . . . . . . . .25 . . . . |
||||
RACF |
Storage |
Considerations. . . . . . . . . . . . . . . . . . . . . .25. . . . . . |
||||
Virtual Storage . . . . . . . . . . . . . . . . . 25. . . . . |
||||||
Templates for RACF |
on OS/390 Release. . .4. . . . . . . . . . . . . .27. . . . |
|||||
Chapter 6. |
Customization Considerations |
. . . . . . . . . |
29. . . . . |
|||
Customer Additions to the Router Table and. . the. . . CDT. . . . . . .29. . |
||||||
RACF/DB2 |
External Security Module Customization. . . . . . . . . . . . 29. . . |
|||||
Exit Processing . . . . |
. . . . . . . . . . . . . |
30. . . . . |
||||
Chapter 7. |
Administration Considerations |
. . . . . . . . . |
31. . . . . |
|||
The |
TMEADMIN |
Class |
. . . . . . . . . . . . . . . . . . . . . . . . .31. . . . . . . |
|||
Password History Changes. . . . . . . . . . . . . . . . . . . . . . .31. . . . . . .
Program Control by System .ID. . . . . . . . . . . . . . . . . . . . .31. . . . . .
Enhancements of Global Access Checking. . . . . . . . . . . . . . . . .32. . . .
Chapter 8. Auditing Considerations |
. |
. |
. . |
. . . . . . |
. 33. . . . . |
||||
SMF Records |
|
. . . . . . . . |
. . . |
. . . . . . .33. . . . . |
|||||
Chapter |
9. Application Development |
Considerations |
|
|
. . . . . . . . . . .35. . |
||||
Programming Interfaces . . . . . . . . . . . . . . . 35. . . . . |
|||||||||
RELEASE=2.4 |
Keyword |
on Macros . . . . . . . . . . . . . . . . . . . 35. . . . . . |
|||||||
FASTAUTH Changes |
|
. . . . . . |
|
. . . . . . . . . .35 . . . . |
|||||
Chapter |
10. |
General |
User |
Considerations |
. . . . . . . . . . . . . . . .37. . . . |
||||
Password History Changes. . . . . . . . . . . . . . . . . . . . . . .37. . . . . . . |
|||||||||
Glossary |
|
. . . . . . . . . |
. . . . . . . . . .39 . . . . . |
||||||
How to |
Get |
Your |
RACF |
CD |
. . . . . . . . . . . . . . . . . . . . . . 47. . . . . . . |
||||
Index |
. . . . . . . . . . |
. |
. . |
. . . . . . |
. 49. . . . . |
||||
iv OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

Figures
1.New Callable Services. . . . . . . . . . . . . . . . . . . . . . 11. . . . . .
2.Changed Callable Services. . . . . . . . . . . . . . . . . . . . .12. . . . . .
3. |
New Classes . . . . . . . . . . . . . . . . 13. . . . . |
|||
4. |
Changes to |
RACF |
Commands . . . . . . . . . . . . . . . . . . . |
13. . . . . . |
5. |
Changes to PSPI Data Areas. . . . . . . . . . . . . . . . . . . |
16. . . . . . |
||
6. |
Changed Executable Macros. . . . . . . . . . . . . . . . . . . . |
17. . . . . . |
||
7. |
New Panels |
for |
RACF. . . . . . . . . . . . . . . . . . . . . . .19. . . . . . |
|
8.Changed Panels for RACF. . . . . . . . . . . . . . . . . . . . .19. . . . . .
9.Change to SYS1.SAMPLIB . . . . . . . . . . . . . . . . . . . . .19. . . . . .
10. Changes to the RACF Publications .Library. . . . . . . . . . . . . 20. . . .
11.RACF Estimated Storage Usage. . . . . . . . . . . . . . . . . .25. . . . .
12.Changes to SMF Records. . . . . . . . . . . . . . . . . . . . .33. . . . . .
Copyright IBM Corp. 1994, 1997 |
v |
vi OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

Notices
References in |
this |
publication |
to IBM |
products, |
programs, |
or |
service |
|||||
that |
IBM |
intends |
to |
make these |
available |
in all |
countries |
in |
which |
I |
||
Any |
reference |
to |
an |
IBM product, program, or service is not intende |
||||||||
imply |
that |
only |
IBM's |
product, program, |
or |
service may be |
used. A |
f |
||||
equivalent product, program, or service which does not infringe on any intellectual property rights may be used instead of the IBM produc service. Evaluation and verification of operation in conjunction with ot programs, or services, except those expressly designated by IBM, i responsibility.
IBM |
may |
have |
patents or |
pending |
patent applications |
covering |
subject |
||||
this |
|
document. |
|
The |
furnishing of this document does |
not give you any |
|||||
these |
patents. |
You can |
send license inquiries, in writing, |
to: |
|||||||
IBM |
|
Director |
|
of |
Licensing |
|
|
|
|||
IBM Corporation |
|
|
|
|
|
|
|||||
500 |
Columbus |
Avenue |
|
|
|
|
|
||||
Thornwood, |
NY |
10594 |
|
|
|
|
|
||||
USA |
|
|
|
|
|
|
|
|
|
|
|
Licensees |
|
of |
this |
program who wish to have information about it for |
|||||||
enabling: |
(i) |
the |
exchange of information between independently creat |
||||||||
and |
other |
programs |
(including this one) and (ii) the |
mutual |
use of t |
||||||
which |
has |
been |
exchanged, should |
contact: |
|
|
|||||
IBM Corporation
Mail Station P300
522 South Road
Poughkeepsie, NY 12601-5400
USA
Attention: Information Request
Such information |
may be |
available, subject to appropriate terms and c |
including in some |
cases, |
payment of a fee. |
Copyright IBM Corp. 1994, 1997 |
vii |
viii OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

Trademarks
The |
following terms |
are trademarks of the IBM Corporation in the Unit |
other countries or |
both: |
|
Ÿ |
AIX/6000 |
|
Ÿ |
BookManager |
|
Ÿ |
CICS |
|
Ÿ |
CICS/ESA |
|
Ÿ |
DB2 |
|
Ÿ |
DFSMS |
|
Ÿ |
FFST |
|
Ÿ |
FFST/MVS |
|
Ÿ |
IBM |
|
Ÿ |
IBMLink |
|
Ÿ |
IMS |
|
Ÿ |
Library Reader |
|
Ÿ |
MVS/ESA |
|
Ÿ |
MVS/XA |
|
Ÿ |
NetView |
|
Ÿ |
OpenEdition |
|
Ÿ |
OS/2 |
|
Ÿ |
OS/390 |
|
Ÿ |
Parallel Sysplex |
|
Ÿ |
RACF |
|
Ÿ |
RETAIN |
|
Ÿ |
S/390 |
|
Ÿ |
SOMobjects |
|
Ÿ |
System/390 |
|
Ÿ |
SystemView |
|
Ÿ |
TalkLink |
|
Ÿ |
VM/ESA |
|
Ÿ |
VM/XA |
|
UNIX is a registered trademark in the United States and other co exclusively through X/Open Company Limited.
Windows |
is a |
trademark |
of Microsoft |
Corporation. |
Other |
company, |
product, |
and service names, which may be denoted by |
|
asterisk (**), |
may be |
trademarks or |
service marks of others. |
|
Copyright IBM Corp. 1994, 1997 |
ix |
x OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

About |
This |
Book |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
This book contains information about the |
Resource |
|
Access |
Control |
Facilit |
|||||||||||||||||||
|
|
|
which is part of the OS/390 Security Server. The Security Server has |
||||||||||||||||||||||||
|
|
|
components: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
Ÿ |
RACF |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ÿ |
OpenEdition |
DCE |
Security |
Server |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||
|
|
|
For information about the OpenEdition DCE |
Security |
Server, |
see |
the |
pub |
|||||||||||||||||||
|
|
|
related |
to |
|
that |
component. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
This book provides information to guide |
you |
through |
the |
migration |
proc |
|||||||||||||||||||
|
|
|
OS/390 Release 3 Security Server (RACF) |
or |
|
RACF |
to |
OS/390 |
Release |
4 |
Se |
||||||||||||||||
|
|
|
Server |
(RACF). |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
|
|
|
The |
purpose |
of |
this |
book |
is |
to ensure |
an |
orderly |
transition |
to |
a |
n |
||||||||||||
|
|
|
It notis |
intended |
for |
customers |
installing |
RACF for the first time or in |
|||||||||||||||||||
|
|
|
release prior to Security Server (RACF) |
Release 3. First-time RACF cust |
|||||||||||||||||||||||
|
|
|
should readOS/390 Security Server (RACF) Introductionand use the program |
|
|
|
|||||||||||||||||||||
|
|
|
directory |
shipped with the |
product |
when |
they |
|
are |
ready |
to install |
||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Who |
Should |
Use |
This |
Book |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
This book is intended for experienced system programmers responsible |
||||||||||||||||||||||||
|
|
|
migrating from OS/390 Release 3 Security |
Server |
(RACF) |
to |
OS/390 |
Releas |
|||||||||||||||||||
|
|
|
Security Server (RACF). This book assumes |
you have |
knowledge |
|
|
of |
OS/390 |
||||||||||||||||||
|
|
|
Release |
3 |
Security |
Server |
(RACF). |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||
|
|
|
If you are migrating from a RACF 2.2, |
or earlier, or from an OS/390 |
|||||||||||||||||||||||
|
|
|
release prior to OS/390 Release 3, |
you |
should |
|
also |
read |
previous |
ve |
|||||||||||||||||
|
|
|
book, as described in “Migration Paths for |
OS/390 |
|
Release |
4 |
|
Security |
||||||||||||||||||
|
|
|
(RACF)” |
|
on |
page 21. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
How |
to |
Use |
This |
Book |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
This book is organized in the following order:
Ÿ |
Chapter 1, |
“Planning |
for |
Migration” |
on |
page 1, |
provides |
information to |
||||||||
|
plan |
your |
installation's |
migration to the |
new |
release |
of |
RACF. |
||||||||
Ÿ |
Chapter 2, |
“Release |
Overview” |
on |
page 5, |
provides |
an |
overview of s |
||||||||
|
the |
new |
release. |
|
|
|
|
|
|
|
|
|
|
|
|
|
Ÿ |
Chapter 3, |
“Summary |
of |
Changes |
to |
RACF |
Components |
for |
OS/390 |
Release |
||||||
|
4” |
on |
page 11, |
lists |
specific |
new |
and changed support for the |
|||||||||
Ÿ |
Chapter 4, |
“Planning |
Considerations” |
on |
page 21, |
describes |
high-level |
|||||||||
|
migration |
considerations |
for customers |
upgrading |
to |
the |
new release |
|||||||||
|
from |
previous levels |
of RACF. |
|
|
|
|
|
|
|
|
|
||||
ŸChapter 5, “Installation Considerations” on page 25, highlights informati about installing the new release of RACF.
Copyright IBM Corp. 1994, 1997
xi
Ÿ |
Chapter 6, |
“Customization Considerations” on page 29, highlights informatio |
|||||||||
|
about customizing function to take advantage of new support |
after t |
|||||||||
|
release |
of |
RACF |
is |
installed. |
|
|
|
|
|
|
Ÿ |
Chapter 7, |
“Administration Considerations” |
on |
page 31, |
summarizes |
changes |
|||||
|
to administration |
procedures for the |
new |
release |
of |
RACF. |
|
||||
Ÿ |
Chapter 8, |
“Auditing Considerations” on page 33, summarizes changes to |
|||||||||
|
auditing |
procedures for the new release of RACF. |
|
|
|
||||||
Ÿ |
Chapter 9, |
“Application Development Considerations” on page 35, identifies |
|||||||||
|
changes in the new release of RACF that might require changes to |
||||||||||
|
installation's |
existing programs. |
|
|
|
|
|
||||
Ÿ |
Chapter 10, |
“General |
User |
Considerations” |
on page 37, |
summarizes new |
|||||
|
support that might |
affect |
general user |
procedures. |
|
|
|||||
Where to Find More |
Information |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||
Where |
necessary, |
this |
book |
|
references information in other books. For |
||||||||||||||||||
titles and order numbers for all products that areOS/390part of OS/390, se |
|||||||||||||||||||||||
Information |
|
Roadmap. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
Softcopy Publications |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
The |
OS/390 |
Security |
Server |
(RACF) |
|
library |
is |
available on |
the following CD- |
||||||||||||||
The CD-ROM collections include |
|
the IBM Library Reader, a program that |
|||||||||||||||||||||
customers |
to read |
the |
softcopy |
books. |
|
|
|
|
|
|
|
|
|||||||||||
Ÿ |
The OS/390 |
Security |
Server |
(RACF) Information , PackageSK2T-2180 |
|
|
|
|
|||||||||||||||
|
This |
softcopy |
collection |
kit |
contains |
|
the |
OS/390 Security |
Server |
(RACF) |
|||||||||||||
|
It also contains the RACF/MVS Version 2 |
product |
libraries, |
the |
RACF/VM |
||||||||||||||||||
|
product library, product books from the OS/390 and VM collections, |
||||||||||||||||||||||
|
International Technical Support Organization (ITSO) books, |
|
and |
Washington |
|||||||||||||||||||
|
System |
Center |
(WSC) |
books |
that |
contain |
substantial |
amounts |
of |
information |
|||||||||||||
|
related to RACF. The kit |
does not contain any licensed |
publications. |
||||||||||||||||||||
|
this CD-ROM, you have access |
|
to |
RACF-related |
information |
from |
IBM prod |
||||||||||||||||
|
such as OS/390, VM, CICS, |
and NetView without maintaining shelves of |
|||||||||||||||||||||
|
hardcopy documentation or handling multiple CD-ROMs. To get more |
|
|||||||||||||||||||||
|
information on OS/390the Security |
Server |
(RACF) |
Information , Packagesee |
|
|
|||||||||||||||||
|
the |
advertisement |
at |
the |
back |
of |
the |
book. |
|
|
|
|
|
||||||||||
Ÿ |
The OS/390 |
Collection |
,Kit SK2T-6700 |
|
|
|
|
|
|
|
|
|
|
|
|
||||||||
|
This |
softcopy |
collection |
contains |
a |
set |
of |
OS/390 |
and |
related |
produc |
||||||||||||
|
This |
kit |
contains |
unlicensed |
books. |
|
|
|
|
|
|
|
|
|
|||||||||
Ÿ |
The Online |
Library |
Omnibus |
Edition MVS CollectionSK2T-0710Kit, |
|
|
|
|
|
||||||||||||||
|
This |
softcopy |
collection |
contains |
a |
set |
of key MVS and MVS-related pr |
||||||||||||||||
|
books. It also includes the RACF Version 2 OS/390productSecuritylibraries. |
|
|||||||||||||||||||||
|
Server (RACF) Messages and Codesis also available asOnlinepartLibraryof |
|
|||||||||||||||||||||
|
Productivity Edition |
Messages |
and |
Codes Collection,SK2T-2068. |
|
|
|
|
|
||||||||||||||
xii OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration
RACF Courses
The |
following |
RACF |
classroom courses are also available: |
Ÿ |
Effective |
RACF |
Administration,H3927 |
Ÿ |
MVS/ESA RACF |
Security Topics, H3918 |
|
Ÿ |
Implementing |
RACF |
Security for CICS/ESA,H3992 |
IBM provides a variety of educational offerings for RACF. For more classroom courses and other offerings, see your IBMBM representative, Mainframe Training Solutions, GR28-5467, or call 1-800-IBM-TEACH
(1-800-426-8322).
IBM Systems |
Center |
Publications |
|
|
|
|
|
|
|
|
|
|
|
|||
|
IBM systems centers produce “red” and “orange” books that can be |
|||||||||||||||
|
setting up and using RACF. |
|
|
|
|
|
|
|
|
|||||||
|
These |
books |
have |
not been subjected to any formal review nor have |
||||||||||||
|
checked for technical accuracy, but |
they |
represent current product |
|||||||||||||
|
(at the |
time |
of |
their |
|
publication) |
and |
provide valuable information on |
||||||||
|
of RACF topics. They are not shipped with RACF. You must order them |
|||||||||||||||
|
separately. |
A |
selected |
list |
of |
these |
books |
follows: |
||||||||
|
Ÿ |
Systems Security Publications Bibliography,G320-9279 |
|
|
||||||||||||
|
Ÿ |
Elements of Security: RACF Overview - StudentGG24Notes,-3970 |
||||||||||||||
|
Ÿ |
Elements of Security: RACF Installation - StudentGG24-3971Notes, |
||||||||||||||
|
Ÿ |
Elements |
of |
Security: |
RACF Advanced |
Topics |
- |
StudentGG24-Notes,3972 |
||||||||
|
Ÿ |
RACF |
Version |
2 |
Release 2 Technical PresentationGG24-2539Guide, |
|||||||||||
|
Ÿ |
RACF |
Version |
2 |
Release |
2 |
Installation |
and |
ImplementationSG24-4580 Guide, |
|||||||
|
Ÿ |
Enhanced |
|
Auditing |
Using |
the |
RACF |
SMF |
Data |
UnloadGG24Utility,-4453 |
||||||
|
Ÿ |
RACF |
Macros |
and |
Exit Coding,GG24-3984 |
|
|
|
|
|
||||||
|
Ÿ |
RACF |
Support |
for |
Open |
Systems Technical |
PresentationGG26Guide,-2005 |
|||||||||
|
Ÿ |
DFSMS |
and |
|
RACF |
Usage Considerations,GG24-3378 |
|
|
||||||||
|
Ÿ Introduction |
to |
System and Network Security: Considerations, Options, |
|||||||||||||
|
|
Techniques, GG24-3451 |
|
|
|
|
|
|
|
|
|
|||||
|
Ÿ |
Network Security Involving the NetView Family ofGG24Products,-3524 |
||||||||||||||
|
Ÿ |
System/390 MVS Sysplex Hardware and Software Migration,GC28-1210 |
||||||||||||||
|
Ÿ |
Secured Single Signon in a Client/Server Environment,GG24-4282 |
||||||||||||||
|
Ÿ |
Tutorial: Options for Tuning GG22RACF, -9396 |
|
|
|
|
||||||||||
| |
Ÿ |
OS/390 Security |
Server |
Audit |
Tool |
and |
Report, |
SG24Application-4820 |
||||||||
Other books are available, but they are not included in this list, information they present has been incorporated into IBM product manua because their technical content is outdated.
About This Book xiii
Other Sources of Information
IBM provides customer-accessible discussion areas where RACF may be discussed by customer and IBM participants. Other information is availa the Internet.
IBM |
Discussion |
Areas |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
Two |
discussion |
areas |
provided |
by |
IBM |
are |
the |
MVSRACF |
discussion |
and |
th |
||||||||||
SECURITY |
|
discussion. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
Ÿ |
MVSRACF |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
MVSRACF |
|
is |
available |
to |
|
customers |
through |
IBM's |
TalkLink |
offering. |
To |
ac |
||||||||
|
MVSRACF |
|
from |
TalkLink: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
1. Select |
S390 |
(the |
S/390 |
Developers' |
Association). |
|
|
|
|
|
||||||||||
|
2. Use |
the |
fastpath |
keyword: |
MVSRACF. |
|
|
|
|
|
|
|
|||||||||
Ÿ |
SECURITY |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
SECURITY |
is |
available |
to |
customers through IBM's |
DialIBM |
offering, |
wh |
|||||||||||||
|
may |
be |
known by |
other |
names |
in |
various countries. To access SECURIT |
||||||||||||||
|
1. Use |
the |
CONFER |
fastpath |
option. |
|
|
|
|
|
|
|
|
||||||||
|
2. Select |
the |
SECURITY |
CFORUM. |
|
|
|
|
|
|
|
|
|
||||||||
Contact |
your |
IBM representative for information on TalkLink, DialIBM, or e |
|||||||||||||||||||
offerings |
for |
your country and for more information |
on |
the |
availability |
||||||||||||||||
MVSRACF and |
SECURITY |
discussions. |
|
|
|
|
|
|
|
|
|
|
|||||||||
Internet Sources
The following resources are available through the Internet:
ŸRACF home page
You can visit the RACF home page on the World Wide Web using this http://www.s39ð.ibm.com/products/racf/racfhp.html
or http://www.s39ð.ibm.com/racf
ŸRACF-L discussion list
Customers and IBM participants may also discuss RACF on the RACF-L
discussion list. RACF-L is not operated or sponsored by IBM; it is University of Georgia.
To |
subscribe |
to the |
RACF-L |
discussion, |
so |
you can |
receive postings, |
||||
note to: |
|
|
|
|
|
|
|
|
|
|
|
listserv@uga.cc.uga.edu |
|
|
|
|
|
|
|
|
|||
Include |
the |
following |
line |
in the |
body |
of the |
note, |
substituting yo |
|||
and last name as indicated: |
|
|
|
|
|
|
|||||
subscribe racf-l first_name last_name |
|
|
|
|
|
|
|||||
To |
post |
a question or |
response to |
RACF-L, |
send |
a |
note |
to: |
|||
racf-l@uga.cc.uga.edu
Include an appropriateSubject: line.
ŸSample code
xivOS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

You can get sample code, |
internally-developed |
tools, |
and |
exits to |
RACF. All this code works |
in our environment, at |
the |
time |
we make i |
but is not officially supported. Each tool or sample has a README
describes |
the |
tool |
or |
sample |
and |
any restrictions on its use. |
|
||||||||||||
The |
simplest |
way |
to |
reach this code is through |
the |
RACF home |
pa |
||||||||||||
home |
page, |
clickSystem/390on |
FTP Servers |
under |
the |
topic, “RACF |
Sample |
|
|||||||||||
Materials.” |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
The |
code |
|
is |
|
also |
availablelscftp.pokfrom.ibm.com |
throughanonymous |
ftp . |
|
|
|||||||||
To get |
access: |
|
|
|
|
|
|
|
|
|
|
|
|
||||||
1. Log |
in |
|
as anonymoususer |
|
. |
|
|
|
|
|
|
|
|
||||||
2. Change |
|
the directorycd ) /pub/racf/mvs( |
to find the subdirectories th |
||||||||||||||||
|
contain |
|
the |
sample |
code. We'll post an announcement on RACF-L, |
|
|||||||||||||
|
MVSRACF, |
and SECURITY CFORUM whenever we add anything. |
|
|
|
||||||||||||||
|
|
Restrictions |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
Because |
|
the |
sample |
code and tools are not |
officially |
supported, |
|||||||||||||
Ÿ |
There |
|
are |
no |
guaranteed |
enhancements. |
|
|
|
|
|
||||||||
Ÿ |
No |
APARs |
can |
be |
accepted. |
|
|
|
|
|
|
|
|||||||
The |
name |
|
and |
availabilityftp ofserverthe |
may |
change |
in |
the |
future. |
We' |
|||||||||
post |
an |
announcement |
on |
RACF-L, |
MVSRACF, |
and |
SECURITY |
CFORUM |
|
|
|
||||||||
if |
this |
|
happens. |
|
|
|
|
|
|
|
|
|
|
||||||
However, |
|
even |
with |
these restrictions, it should be useful for |
|||||||||||||||
access |
to |
this |
code. |
|
|
|
|
|
|
|
|
||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
To Request Copies of |
IBM |
|
Publications |
|
|
|
|
|
|
|
|
|
|||
Direct |
your |
request |
for |
|
copies of |
any |
IBM publication to your IBM |
||||||||
to the IBM branch office serving your |
locality. |
|
|
||||||||||||
There is also a toll-free customer |
support number (1-800-879-2755) availabl |
||||||||||||||
Monday through Friday |
from |
6:30 |
a.m. |
through 5:00 |
p.m. Mountain |
Time. |
You |
||||||||
use |
this |
number |
to: |
|
|
|
|
|
|
|
|
|
|||
Ÿ |
Order |
or |
inquire |
about |
IBM |
publications |
|
|
|
||||||
Ÿ |
Resolve |
any |
software |
manufacturing |
or |
delivery |
concerns |
|
|
||||||
Ÿ Activate the Program Reorder Form |
to |
provide |
faster and |
more |
conve |
||||||||||
|
ordering |
of |
software |
updates |
|
|
|
|
|
||||||
See the advertisement at the back |
of the book forOS/390information abou |
||||||||||||||
Security |
Server |
(RACF) |
Information |
Package. |
|
|
|
|
|||||||
About This Book xv
xvi OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

Summary of |
Changes |
|
|
|
| |
Summary |
of Changes |
|
|
| |
for GC28-1920-03 |
|
|
|
| |
OS/390 |
Version |
2 Release |
4 |
| |
This |
book |
contains primarily new information for OS/390 Version 2 Relea |
|
| |
Security Server (RACF). When any information appeared in an earlier r |
|||
| |
information |
that |
is new is indicated by a vertical line to the lef |
|
Summary of Changes for GC28-1920-02 OS/390 Release 3
This book contains new information for OS/390 Release 3 Security Server
Summary of Changes for GC28-1920-01 OS/390 Release 2
This |
book |
contains |
new information for |
OS/390 |
Release 2 |
Security Server |
|
Summary |
of Changes |
|
|
|
|
|
|
for GC28-1920-00 |
|
|
|
|
|
|
|
OS/390 |
Release |
1 |
|
|
|
|
|
This |
book |
contains |
information |
previously |
presentedRACF Planning: inInstallation |
||
and |
Migration, GC23-3736, which |
supports RACF Version 2 Release 2. |
|||||
This |
book |
includes |
terminology, |
maintenance, |
and editorial |
changes. |
|
Copyright IBM Corp. 1994, 1997 |
xvii |
xviii OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

Chapter 1. Planning |
for |
|
Migration |
|
|
|
|
|
|
|
||
This |
chapter provides |
information |
to |
help you plan your installation's m |
||||||||
the |
new |
release of |
OS/390 Security |
Server (RACF). Before attempting t |
||||||||
you |
should |
define |
a |
plan to ensure a smooth and orderly transition. |
||||||||
thought-out and documented migration plan can help minimize any interrupt |
||||||||||||
service. |
Your |
migration plan |
should |
address |
such topics |
as: |
||||||
Ÿ |
Identifying |
which |
required and |
optional |
products are |
needed |
||||||
Ÿ |
Evaluating |
new |
and |
changed |
functions |
|
|
|||||
Ÿ |
Evaluating |
how |
incompatibilities |
affect your installation |
|
|||||||
Ÿ |
Defining |
necessary |
changes |
to: |
|
|
|
|
||||
–Installation-written code
–Operational procedures
–Application programs
|
– Other |
related products |
|
|
|
|
||
Ÿ |
Defining |
education requirements for operators and |
end |
users |
||||
Ÿ |
Preparing |
your |
staff |
and |
end users for |
migration, |
if |
necessary |
Ÿ |
Acquiring |
and |
installing |
the |
latest service |
level of |
RACF |
for mainten |
The content and extent of a migration plan can vary significantly from installation. To successfully migrate to a new release of RACF, you s installing and stabilizing the new RACF release without activating the n
provided. Installing the new RACF |
release without initially |
exploiting n |
allows you to maintain a stable |
RACF environment. The program |
directory |
with the new OS/390 release gives detailed information about the cor required for installation.
When defining your installation's migration plan, you should consider the
ŸMigration
ŸInstallation
ŸCustomization
ŸAdministration
ŸAuditing
ŸOperation
ŸApplication development
ŸGeneral users
Migration Planning Considerations
Installations |
planning |
to migrate to a |
new release of RACF |
must |
conside |
|
support |
requirements |
such as machine and programming restrictions, migra |
||||
paths, and |
program |
compatibility. |
|
|
|
|
For more |
information, |
see Chapter 4, |
“Planning Considerations” |
on |
page 21. |
|
Copyright IBM Corp. 1994, 1997 |
1 |

Installation Considerations
Before installing a new release of RACF, you must determine what updat needed for IBM-supplied products, system libraries, and non-IBM product
(Procedures |
for installing RACF are described in the program directory |
OS/390, not in |
this book.) |
Be sure you include the following steps when planning your pre-installatio activities:
Ÿ Obtain and install any |
required program |
temporary fixes (PTFs) |
or |
upd |
|||||||
versions |
of |
the |
operating system. |
|
|
|
|
|
|||
Call |
the |
IBM |
Software |
Support |
Center |
to |
obtain |
the preventive |
service |
||
(PSP) |
upgrade |
for |
RACF. |
This |
provides |
the most |
current information |
on P |
|||
for |
RACF. Have RETAIN checked |
again |
just |
before |
testing RACF. Inform |
||
for |
requesting the PSP upgrade |
can be found in the program directo |
|||||
Although |
the program |
directory |
contains a |
list of the required PTFs, |
|||
current |
information is |
available |
from |
the |
support |
center. |
|
Ÿ Contact programmers responsible for updating programs.
Verify that |
your installation's programs will continue |
to run, and, if |
make changes |
to ensure compatibility with the new |
release. |
For more information, see Chapter 5, “Installation Considerations” on page 2
Customization Considerations
In order for RACF to meet the specific |
requirements of your |
installat |
||||||||
customize |
function to |
take |
advantage |
of |
new |
support |
after |
the |
product |
|
For example, you can tailor RACF through the use of |
installation |
exit r |
||||||||
descriptor table (CDT) support, or options |
to |
improve |
performance. This |
|||||||
changes to |
RACF that |
might |
require |
the |
installation to |
tailor |
the |
produc |
||
ensure that RACF runs as before or to accommodate new security contro installation requires.
For more information, see Chapter 6, “Customization Considerations” on page
Administration Considerations
Security |
administrators must |
be |
aware of how changes introduced by a |
|||||||
product |
release |
can |
affect an |
installation's data |
processing |
resources. |
||||
real and virtual |
storage requirements, performance, security, and integr |
|||||||||
interest |
to security |
administrators or |
to system |
programmers |
who |
are |
r |
|||
for making decisions |
about |
the |
computing |
system resources used |
with |
a |
||||
For more information, see Chapter 7, “Administration Considerations” on page
2 OS/390 V2R4.0 Security Server (RACF) Planning: Installation and Migration

Auditing Considerations
Auditors |
who are |
responsible for |
ensuring |
proper |
access |
control and |
|
for their installation are interested in |
changes |
to security |
options, |
||||
report |
generation |
utilities. |
|
|
|
|
|
For more |
information, see Chapter 8, |
“Auditing Considerations” |
on |
page 33 |
|||
Application Development Considerations
Application |
development |
programmers |
must |
be |
aware of |
new |
functions intro |
||
in a new release of RACF. To implement a |
new |
function, |
the |
application |
|||||
development |
personnel |
should read |
this |
book |
and |
the |
following |
books: |
|
ŸOS/390 Security Server External Security Interface (RACROUTE) Macro Reference
Ÿ |
OS/390 |
Security |
Server |
(RACF) |
Data |
Areas |
|
|
|
|||
Ÿ |
OS/390 |
Security |
Server |
(RACF) |
Macros |
and |
Interfaces |
|
||||
To |
ensure |
that |
existing |
programs run as before, the application progr |
||||||||
should be aware of any |
changes |
in |
data |
areas and |
processing requi |
|||||||
book |
provides |
an |
overview |
of |
the |
changes |
that |
might |
affect existing |
|||
programs. |
|
|
|
|
|
|
|
|
|
|
||
For |
more |
information, see |
Chapter 9, |
“Application |
Development Considerations |
|||||||
page |
35. |
|
|
|
|
|
|
|
|
|
|
|
General User Considerations
RACF general users use a RACF-protected system to:
Ÿ Log on to the system
Ÿ Access resources on the system
ŸProtect their own resources and any group resources to which the administrative authority
This book provides an overview of the changes that might affect ex procedures for general users. For more information, see Chapter 10, “G Considerations” on page 37.
Chapter 1. Planning for Migration3
 Loading...
Loading...