HP 4100gl, 2600, 2600-PWR, 6108, 2626 User Manual
...
ProCurve Switches
Access Security Guide
Switch 2600 Series
Switch 2600-PWR Series
Switch 2800 Series
Switch 4100 Series
Switch 6108 Series

ProCurve
Switch 2600 Series
Switch 2600-PWR Series
Switch 2800 Series
Switch 4100gl Series
Switch 6108
December 2008
Access Security Guide

© Copyright 2001-2008 Hewlett-Packard Company, L..P.
The information contained herein is subject to change without notice.
Publication Number
5990-6024 December 2008
Applicable Products
ProCurve Switch 2626 |
(J4900A/B) |
ProCurve Switch 2650 |
(J4899A/B) |
ProCurve Switch 2600-8-PWR |
(J8762A) |
ProCurve Switch 2626-PWR |
(J8164A) |
ProCurve Switch 2650-PWR |
(J8165A) |
ProCurve Switch 2824 |
(J4903A) |
ProCurve Switch 2848 |
(J4904A) |
ProCurve Switch 4104GL |
(J4887A) |
ProCurve Switch 4108GL |
(J4861A/J4865A) |
ProCurve Switch 4140GL |
(J8151A) |
ProCurve Switch 4148GL |
(J4888A) |
ProCurve Switch 4160GL |
(J8152A) |
ProCurve Switch 6108 |
(J4902A). |
Trademark Credits
Windows NT®, Windows®, and MS Windows® are US registered trademarks of Microsoft Corporation.
Software Credits
SSH on ProCurve Switches is based on the OpenSSH software toolkit. This product includes software developed by the OpenSSH Project for use in the OpenSSH Toolkit. For more information on OpenSSH, visit http:// www.openssh.com.
SSL on ProCurve Switches is based on the OpenSSL software toolkit. This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. For more information on OpenSSL, visit
http://www.openssl.org.
This product includes cryptographic software written by Eric Young (eay@cryptsoft.com)
This product includes software written by Tim Hudson (tjh@cryptsoft.com)
Disclaimer
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this material.
Hewlett-Packard Company shall not be liable for technical or editorial errors or omissions contained herein. The information is provided "as is" without warranty of any kind and is subject to change without notice. The warranties for Hewlett-Packard Company products are set forth in the express limited warranty statements for such products. Nothing herein should be construed as constituting an additional warranty.
Hewlett-Packard assumes no responsibility for the use or reliability of its software on equipment that is not furnished by Hewlett-Packard.
Warranty
See the Customer Support/Warranty booklet included with the product.
A copy of the specific warranty terms applicable to your Hewlett-Packard products and replacement parts can be obtained from your HP Sales and Service Office or authorized dealer.
Hewlett-Packard Company
8000 Foothills Boulevard, m/s 5551 Roseville, California 95747-5551
http://www.procurve.com

Contents
Product Documentation
About Your Switch Manual Set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xi Feature Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xii
1 Getting Started
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2 Overview of Access Security Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2 Management Access Security Protection . . . . . . . . . . . . . . . . . . . . . . . . 1-3 General Switch Traffic Security Guidelines . . . . . . . . . . . . . . . . . . . . . . 1-4 Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5 Feature Descriptions by Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5 Command Syntax Statements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5 Command Prompts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6 Screen Simulations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6 Port Identity Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6 Sources for More Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7 Need Only a Quick Start? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8 IP Addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8 To Set Up and Install the Switch in Your Network . . . . . . . . . . . . . . . . 1-9
2 Configuring Username and Password Security
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Configuring Local Password Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Menu: Setting Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
CLI: Setting Passwords and Usernames . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Web: Setting Passwords and Usernames . . . . . . . . . . . . . . . . . . . . . . . . 2-6
iii

Front-Panel Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
When Security Is Important . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Front-Panel Button Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-8
Configuring Front-Panel Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-10
Password Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-15
Password Recovery Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-17
3Web and MAC Authentication for the Series 2600/ 2600-PWR and 2800 Switches
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-2
Client Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3
General Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4
How Web and MAC Authentication Operate . . . . . . . . . . . . . . . . . . . . . . . . 3-5
Authenticator Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-5
Terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-9
Operating Rules and Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-10
General Setup Procedure for Web/MAC Authentication . . . . . . . . . . . . . . 3-12 Do These Steps Before You Configure Web/MAC Authentication . . 3-12
Additional Information for Configuring the RADIUS Server To Support MAC Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-14
Configuring the Switch To Access a RADIUS Server . . . . . . . . . . . . . . . . 3-15
Configuring Web Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-17 Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-17 Configure the Switch for Web-Based Authentication . . . . . . . . . . . . . 3-18
Configuring MAC Authentication on the Switch . . . . . . . . . . . . . . . . . . . . 3-22 Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-22 Configure the Switch for MAC-Based Authentication . . . . . . . . . . . . 3-23
Show Status and Configuration of Web-Based Authentication . . . . . . . . 3-26
Show Status and Configuration of MAC-Based Authentication . . . . . . . . 3-27
Show Client Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-29
iv

4 TACACS+ Authentication
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-2
Terminology Used in TACACS Applications: . . . . . . . . . . . . . . . . . . . . . . . . 4-3
General System Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-5
General Authentication Setup Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-5
Configuring TACACS+ on the Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 4-8 |
Before You Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 4-8 |
CLI Commands Described in this Section . . . . . . . . . . . . . . . . . . . . . . . |
4-9 |
Viewing the Switch’s Current Authentication Configuration . . . . . . . |
4-9 |
Viewing the Switch’s Current TACACS+ Server Contact Configuration . |
|
4-10 |
|
Configuring the Switch’s Authentication Methods . . . . . . . . . . . . . . . |
4-11 |
Configuring the Switch’s TACACS+ Server Access . . . . . . . . . . . . . . |
4-15 |
How Authentication Operates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
4-20 |
General Authentication Process Using a TACACS+ Server . . . . . . . . |
4-20 |
Local Authentication Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
4-22 |
Using the Encryption Key . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
4-23 |
Controlling Web Browser Interface Access When Using TACACS+
Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-24
Messages Related to TACACS+ Operation . . . . . . . . . . . . . . . . . . . . . . . . . 4-25
Operating Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-25
5 RADIUS Authentication and Accounting
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-2
Terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-3
Switch Operating Rules for RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-4
General RADIUS Setup Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
Configuring the Switch for RADIUS Authentication . . . . . . . . . . . . . . . . . . 5-6 Outline of the Steps for Configuring RADIUS Authentication . . . . . . 5-7
v

1. Configure Authentication for the Access Methods You Want RADIUS
To Protect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
. 5-8 |
2. Configure the Switch To Access a RADIUS Server . . . . . . . . . . . . |
5-10 |
3. Configure the Switch’s Global RADIUS Parameters . . . . . . . . . . . |
5-12 |
Local Authentication Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-16
Controlling Web Browser Interface Access When Using RADIUS
Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-17
Configuring RADIUS Accounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-17 Operating Rules for RADIUS Accounting . . . . . . . . . . . . . . . . . . . . . . 5-19 Steps for Configuring RADIUS Accounting . . . . . . . . . . . . . . . . . . . . . 5-19
Viewing RADIUS Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-25
General RADIUS Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-25
RADIUS Authentication Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-27
RADIUS Accounting Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-28
Changing RADIUS-Server Access Order . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-29
Messages Related to RADIUS Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-31
6 Configuring Secure Shell (SSH)
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-2
Terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-4
Prerequisite for Using SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Public Key Formats . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Steps for Configuring and Using SSH for Switch and Client Authentication . 6-6
General Operating Rules and Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-8
Configuring the Switch for SSH Operation . . . . . . . . . . . . . . . . . . . . . . . . . . 6-9 1. Assign Local Login (Operator) and Enable (Manager) Password . 6-9 2. Generate the Switch’s Public and Private Key Pair . . . . . . . . . . . . 6-10 3. Provide the Switch’s Public Key to Clients . . . . . . . . . . . . . . . . . . . 6-12
4. Enable SSH on the Switch and Anticipate SSH Client Contact Behavior 6-15
5. Configure the Switch for SSH Authentication . . . . . . . . . . . . . . . . . 6-18
vi

6. Use an SSH Client To Access the Switch . . . . . . . . . . . . . . . . . . . . . 6-21
Further Information on SSH Client Public-Key Authentication . . . . . . . . 6-21
Messages Related to SSH Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-27
7 Configuring Secure Socket Layer (SSL)
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-2
Terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-3
Prerequisite for Using SSL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-5
Steps for Configuring and Using SSL for Switch and Client Authentication . 7-5
General Operating Rules and Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-6
Configuring the Switch for SSL Operation . . . . . . . . . . . . . . . . . . . . . . . . . . 7-7 1. Assign Local Login (Operator) and Enable (Manager) Password . 7-7 2. Generate the Switch’s Server Host Certificate . . . . . . . . . . . . . . . . . 7-9
3. Enable SSL on the Switch and Anticipate SSL Browser Contact Behavior . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-17
Common Errors in SSL Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-21
8 Configuring Port-Based Access Control (802.1X)
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-3
Why Use Port-Based Access Control? . . . . . . . . . . . . . . . . . . . . . . . . . . 8-3
General Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-3
How 802.1X Operates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-6
Authenticator Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-6
Switch-Port Supplicant Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-7
Terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-8
General Operating Rules and Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-10
General Setup Procedure for Port-Based Access Control (802.1X) . . . . . 8-12 Do These Steps Before You Configure 802.1X Operation . . . . . . . . . 8-12 Overview: Configuring 802.1X Authentication on the Switch . . . . . . 8-13
vii

Configuring Switch Ports as 802.1X Authenticators . . . . . . . . . . . . . . . . . 8-15 1. Enable 802.1X Authentication on Selected Ports . . . . . . . . . . . . . . 8-15 3. Configure the 802.1X Authentication Method . . . . . . . . . . . . . . . . . 8-19 4. Enter the RADIUS Host IP Address(es) . . . . . . . . . . . . . . . . . . . . . . 8-20 5. Enable 802.1X Authentication on the Switch . . . . . . . . . . . . . . . . . 8-20
802.1X Open VLAN Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
8-21 |
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
8-21 |
Use Models for 802.1X Open VLAN Modes . . . . . . . . . . . . . . . . . . . . . |
8-22 |
Operating Rules for Authorized-Client and Unauthorized-Client VLANs |
|
8-25 |
|
Setting Up and Configuring 802.1X Open VLAN Mode . . . . . . . . . . . . |
8-27 |
802.1X Open VLAN Operating Notes . . . . . . . . . . . . . . . . . . . . . . . . . . |
8-31 |
Option For Authenticator Ports: Configure Port-Security To Allow Only 802.1X Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-32
Configuring Switch Ports To Operate As Supplicants for 802.1X Connections to Other Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-34
Displaying 802.1X Configuration, Statistics, and Counters . . . . . . . . . . . . 8-38 Show Commands for Port-Access Authenticator . . . . . . . . . . . . . . . . 8-38 Viewing 802.1X Open VLAN Mode Status . . . . . . . . . . . . . . . . . . . . . . 8-40 Show Commands for Port-Access Supplicant . . . . . . . . . . . . . . . . . . . 8-43
How RADIUS/802.1X Authentication Affects VLAN Operation . . . . . . . . 8-44
Messages Related to 802.1X Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-48
9 Configuring and Monitoring Port Security
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-2
Basic Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-2
Blocking Unauthorized Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-3
Trunk Group Exclusion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-4
Planning Port Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-5
Port Security Command Options and Operation . . . . . . . . . . . . . . . . . . . . . 9-6 Retention of Static MAC Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-10 Displaying Current Port Security Settings . . . . . . . . . . . . . . . . . . . . . . 9-10 Configuring Port Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-12
viii

MAC Lockdown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-17
Differences Between MAC Lockdown and Port Security . . . . . . . . . 9-19
Deploying MAC Lockdown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-21
MAC Lockout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-25
Port Security and MAC Lockout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-27
IP Lockdown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-28
Web: Displaying and Configuring Port Security Features . . . . . . . . . . . . . 9-29
Reading Intrusion Alerts and Resetting Alert Flags . . . . . . . . . . . . . . . . . . 9-29 Notice of Security Violations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-29 How the Intrusion Log Operates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-30 Keeping the Intrusion Log Current by Resetting Alert Flags . . . . . . . 9-31 Using the Event Log To Find Intrusion Alerts . . . . . . . . . . . . . . . . . . . 9-36
Web: Checking for Intrusions, Listing Intrusion Alerts, and Resetting Alert Flags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-36
Operating Notes for Port Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-37
10Traffic/Security Filters
(ProCurve Series 2600/2600-PWR and 2800 Switches)
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-2
Using Source-Port Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-4
Operating Rules for Source-Port Filters . . . . . . . . . . . . . . . . . . . . . . . . 10-4
Configuring a Source-Port Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-5
Viewing a Source-Port Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-7
Filter Indexing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-8
Editing a Source-Port Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-9
Using Named Source-Port Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-10
11 Using Authorized IP Managers
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-1
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-2
Configuration Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-3
Access Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-3
ix

Defining Authorized Management Stations . . . . . . . . . . . . . . . . . . . . . . . . . 11-4 Overview of IP Mask Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-4 Menu: Viewing and Configuring IP Authorized Managers . . . . . . . . . 11-5 CLI: Viewing and Configuring Authorized IP Managers . . . . . . . . . . . 11-6
Web: Configuring IP Authorized Managers . . . . . . . . . . . . . . . . . . . . . . . . . 11-9
Building IP Masks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-9 Configuring One Station Per Authorized Manager IP Entry . . . . . . . 11-9 Configuring Multiple Stations Per Authorized Manager IP Entry . . 11-10 Additional Examples for Authorizing Multiple Stations . . . . . . . . . 11-11
Operating Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-12
x

Product Documentation
About Your Switch Manual Set
The switch manual set includes the following:
■ Read Me First - a printed guide shipped with your switch. Provides software update information, product notes, and other information.
■ Installation and Getting Started Guide - a printed guide shipped with your switch. This guide explains how to prepare for and perform the physical installation and connection to your network.
■ Management and Configuration Guide - included as a PDF file on the Documentation CD. This guide describes how to configure, manage, and monitor basic switch operation.
■ Advanced Traffic Management Guide - included as a PDF file on the Documentation CD. This guide explains the configuration and operation of traffic management features such as spanning tree, VLANs, and IP routing.
■ Access Security Guide - included as a PDF file on the
|
Documentation CD. This guide explains the configuration and |
|
operation of access security and user authentication features on the |
|
switch. |
|
■ Release Notes - posted on the ProCurve web site to provide |
|
information on software updates. The release notes describe new |
|
features, fixes, and enhancements that become available between |
|
revisions of the above guides. |
|
|
Note |
For the latest version of all ProCurve switch documentation, including release |
|
notes covering recently added features, visit the ProCurve Networking |
|
website at http://www.procurve.com. Click on Technical support, and then |
|
click on Product manuals. |
|
|
xi

Product Documentation
Feature Index
For the manual set supporting your switch model, the following feature index indicates which manual to consult for information on a given software feature. (Note that some software features are not supported on all switch models.)
Feature |
Management and |
Advanced Traffic |
Access Security |
|
Configuration |
Management |
Guide |
|
|
|
|
802.1Q VLAN Tagging |
- |
X |
- |
|
|
|
|
802.1X Port-Based Priority |
X |
- |
- |
|
|
|
|
Authentication |
- |
- |
X |
|
|
|
|
Authorized IP Managers |
- |
- |
X |
|
|
|
|
Config File |
X |
- |
- |
|
|
|
|
Copy Command |
X |
- |
- |
|
|
|
|
Debug |
X |
- |
- |
|
|
|
|
DHCP Configuration |
- |
X |
- |
|
|
|
|
DHCP/Bootp Operation |
X |
- |
- |
|
|
|
|
Diagnostic Tools |
X |
- |
- |
|
|
|
|
Downloading Software |
X |
- |
- |
|
|
|
|
Event Log |
X |
- |
- |
|
|
|
|
Factory Default Settings |
X |
- |
- |
|
|
|
|
File Management |
X |
- |
- |
|
|
|
|
File Transfers |
X |
- |
- |
|
|
|
|
GVRP |
- |
X |
- |
|
|
|
|
IGMP |
- |
X |
- |
|
|
|
|
Interface Access (Telnet, Console/Serial, Web) |
X |
- |
- |
|
|
|
|
IP Addressing |
X |
- |
- |
|
|
|
|
IP Routing |
- |
X |
- |
|
|
|
|
xii

Product Documentation
Feature |
Management and |
Advanced Traffic |
Access Security |
|
Configuration |
Management |
Guide |
|
|
|
|
LACP |
X |
- |
- |
|
|
|
|
Link |
X |
- |
- |
|
|
|
|
LLDP |
X |
- |
- |
|
|
|
|
MAC Address Management |
X |
- |
- |
|
|
|
|
MAC Lockdown |
- |
- |
X |
|
|
|
|
MAC Lockout |
- |
- |
X |
|
|
|
|
MAC-based Authentication |
- |
- |
X |
|
|
|
|
Monitoring and Analysis |
X |
- |
- |
|
|
|
|
Multicast Filtering |
- |
X |
- |
|
|
|
|
Network Management Applications (LLDP, SNMP) |
X |
- |
- |
|
|
|
|
Passwords |
- |
- |
X |
|
|
|
|
Ping |
X |
- |
- |
|
|
|
|
Port Configuration |
X |
- |
- |
|
|
|
|
Port Security |
- |
- |
X |
|
|
|
|
Port Status |
X |
- |
- |
|
|
|
|
Port Trunking (LACP) |
X |
- |
- |
|
|
|
|
Port-Based Access Control |
- |
- |
X |
|
|
|
|
Port-Based Priority (802.1Q) |
X |
- |
- |
|
|
|
|
Power over Ethernet (PoE) |
X |
- |
- |
|
|
|
|
Quality of Service (QoS) |
- |
X |
- |
|
|
|
|
RADIUS Authentication and Accounting |
- |
- |
X |
|
|
|
|
Routing |
- |
X |
- |
|
|
|
|
Secure Copy |
X |
- |
- |
|
|
|
|
SFTP |
X |
- |
- |
|
|
|
|
SNMP |
X |
- |
- |
|
|
|
|
Software Downloads (SCP/SFTP, TFTP, Xmodem) |
X |
- |
- |
|
|
|
|
xiii

Product Documentation
Feature |
Management and |
Advanced Traffic |
Access Security |
|
Configuration |
Management |
Guide |
|
|
|
|
Source-Port Filters |
- |
- |
X |
|
|
|
|
Spanning Tree (STP, RSTP, MSTP) |
- |
X |
- |
|
|
|
|
SSH (Secure Shell) Encryption |
- |
- |
X |
|
|
|
|
SSL (Secure Socket Layer) |
- |
- |
X |
|
|
|
|
Stack Management (Stacking) |
- |
X |
- |
|
|
|
|
Syslog |
X |
- |
- |
|
|
|
|
System Information |
X |
- |
- |
|
|
|
|
TACACS+ Authentication |
- |
- |
X |
|
|
|
|
Telnet Access |
X |
- |
- |
|
|
|
|
TFTP |
X |
- |
- |
|
|
|
|
Time Protocols (TimeP, SNTP) |
X |
- |
- |
|
|
|
|
Traffic/Security Filters |
- |
- |
X |
|
|
|
|
Troubleshooting |
X |
- |
- |
|
|
|
|
VLANs |
- |
X |
- |
|
|
|
|
Web-based Authentication |
- |
- |
X |
|
|
|
|
Xmodem |
X |
- |
- |
|
|
|
|
xiv

1
Getting Started
Contents
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
Overview of Access Security Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
Management Access Security Protection . . . . . . . . . . . . . . . . . . . . . . . . 1-3
General Switch Traffic Security Guidelines . . . . . . . . . . . . . . . . . . . . . . 1-4
Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Feature Descriptions by Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Command Syntax Statements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Command Prompts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Screen Simulations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Port Identity Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Sources for More Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . |
1-7 |
Need Only a Quick Start? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8 IP Addressing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8 To Set Up and Install the Switch in Your Network . . . . . . . . . . . . . . . . 1-9
1-1

Getting Started
Introduction
Introduction
This Access Security Guide describes how to use ProCurve’s switch security features to protect access to your switch. This guide is intended to support the following switches:
■ProCurve Series 2600
■ProCurve Series 2600-PWR
■ProCurve Series 2800
■ProCurve Series 4100gl
■ProCurve Switch 6108
For an overview of other product documentation for the above switches, refer to “Product Documentation” on page xi.
The Product Documentation CD-ROM shipped with the switch includes a copy of this guide. You can also download a copy from the ProCurve website, http://www.procurve.com.
Overview of Access Security Features
The access security features covered in this guide include:
■Local Manager and Operator Passwords (page 2-1): Control access and privileges for the CLI, menu, and web browser interfaces.
■TACACS+ Authentication (page 4-1): Uses an authentication application on a server to allow or deny access to a switch.
■RADIUS Authentication and Accounting (page 5-1): Like TACACS+, uses an authentication application on a central server to allow or deny access to the switch. RADIUS also provides accounting services for sending data about user activity and system events to a RADIUS server.
■Secure Shell (SSH) Authentication (page 6-1): Provides encrypted paths for remote access to switch management functions.
1-2

Getting Started
Overview of Access Security Features
■Secure Socket Layer (SSL) (page 7-1): Provides remote web access to the switch via encrypted authentication paths between the switch and management station clients capable of SSL/TLS operation.
■Port-Based Access Control (802.1X) (page 8-1): On point-to-point connections, enables the switch to allow or deny traffic between a port and an 802.1X-aware device (supplicant) attempting to access the switch. Also enables the switch to operate as a supplicant for connections to other 802.1X-aware switches.
■Port Security (page 9-1): Enables a switch port to maintain a unique list of MAC addresses defining which specific devices are allowed to access the network through that port. Also enables a port to detect, prevent, and log access attempts by unauthorized devices.
■Traffic/Security Filters (page 10-1): Source-Port filtering enhances in-band security by enabling outbound destination ports on the switch to forward or drop traffic from designated source ports (within the same VLAN).
■Authorized IP Managers (page 11-1): Allows access to the switch by a networked device having an IP address previously configured in the switch as "authorized".
Management Access Security Protection
In considering management access security for your switch, there are two key areas to protect:
■Unauthorized client access to switch management features
■Unauthorized client access to the network.
Table 1-1 on page 1-4 provides an overview of the type of protection offered by each switch security feature.
Note |
ProCurve recommends that you use local passwords together with your |
|
switch’s other security features to provide a more comprehensive security |
|
fabric than if you use only local passwords. |
|
|
1-3
Getting Started
Overview of Access Security Features
Table 1-1. Management Access Security Protection
Security Feature |
Offers Protection Against Unauthorized Client Access to |
Offers Protection |
||||
|
|
Switch Management Features |
|
Against |
||
|
Connection |
Telnet |
SNMP |
Web |
SSH |
Unauthorized Client |
|
Access to the |
|||||
|
|
|
(Net Mgmt) |
Browser |
Client |
|
|
|
|
Network |
|||
|
|
|
|
|
|
|
Local Manager and Operator |
PtP: |
Yes |
No |
Yes |
Yes |
No |
Usernames and Passwords1 |
Remote: |
Yes |
No |
Yes |
Yes |
No |
|
||||||
TACACS+1 |
PtP: |
Yes |
No |
No |
Yes |
No |
|
Remote: |
Yes |
No |
No |
Yes |
No |
RADIUS1 |
PtP: |
Yes |
No |
No |
Yes |
No |
|
Remote: |
Yes |
No |
No |
Yes |
No |
|
|
|
|
|
|
|
SSH |
Ptp: |
Yes |
No |
No |
Yes |
No |
|
Remote: |
Yes |
No |
No |
Yes |
No |
|
|
|
|
|
|
|
SSL |
Ptp: |
No |
No |
Yes |
No |
No |
|
Remote: |
No |
No |
Yes |
No |
No |
|
|
|
|
|
|
|
Port-Based Access Control (802.1X) |
PtP: |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Remote: |
No |
No |
No |
No |
No |
|
|
|
|
|
|
|
Port Security (MAC address) |
PtP: |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Remote: |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
|
|
|
|
|
Authorized IP Managers |
PtP: |
Yes |
Yes |
Yes |
Yes |
No |
|
Remote: |
Yes |
Yes |
Yes |
Yes |
No |
1 The local Manager/Operator, TACACS+, and RADIUS options (direct connect or modem access) also offer protection for serial port access.
General Switch Traffic Security Guidelines
Where the switch is running multiple security options, it implements network traffic security based on the OSI (Open Systems Interconnection model) precedence of the individual options, from the lowest to the highest. The following list shows the order in which the switch implements configured security features on traffic moving through a given port.
1.Disabled/Enabled physical port
2.MAC lockout (applies to all ports on the switch)
3.MAC lockdown
4.Port security
5.Authorized IP Managers
6.Application features at higher levels in the OSI model, such as SSH
(The above list does not address the mutually exclusive relationship that exists among some security features.)
1-4

Getting Started
Conventions
Conventions
This guide uses the following conventions for command syntax and displayed information.
Feature Descriptions by Model
In cases where a software feature is not available in all of the switch models covered by this guide, the section heading specifically indicates which product or product series offer the feature.
For example (the switch model is highlighted here in bold italics):
“Web and MAC Authentication for the Series 2600/2600-PWR and 2800 Switches”.
Command Syntax Statements
Syntax: aaa port-access authenticator < port-list >
[ control < authorized | auto | unauthorized >]
■Vertical bars ( | ) separate alternative, mutually exclusive elements.
■Square brackets ( [ ] ) indicate optional elements.
■Braces ( < > ) enclose required elements.
■Braces within square brackets ( [ < > ] ) indicate a required element within an optional choice.
■Boldface indicates use of a CLI command, part of a CLI command syntax, or other displayed element in general text. For example:
“Use the copy tftp command to download the key from a TFTP server.”
■Italics indicate variables for which you must supply a value when executing the command. For example, in this command syntax, < portlist > indicates that you must provide one or more port numbers:
Syntax: aaa port-access authenticator < port-list >
1-5

Getting Started
Conventions
Command Prompts
In the default configuration, your switch displays one of the following CLI prompts:
ProCurve Switch 4104#
ProCurve Switch 4108#
ProCurve Switch 2626#
ProCurve Switch 2650#
ProCurve Switch 6108#
To simplify recognition, this guide uses ProCurve to represent command prompts for all models. For example:
ProCurve#
(You can use the hostname command to change the text in the CLI prompt.)
Screen Simulations
Figures containing simulated screen text and command output look like this:
Figure 1-1. Example of a Figure Showing a Simulated Screen
In some cases, brief command-output sequences appear outside of a numbered figure. For example:
ProCurve(config)# ip default-gateway 18.28.152.1/24
ProCurve(config)# vlan 1 ip address 18.28.36.152/24
ProCurve(config)# vlan 1 ip igmp
Port Identity Examples
This guide describes software applicable to both chassis-based and stackable ProCurve switches. Where port identities are needed in an example, this guide uses the chassis-based port identity system, such as “A1”, “B3 - B5”, “C7”, etc. However, unless otherwise noted, such examples apply equally to the stackable switches, which for port identities typically use only numbers, such as “1”, “3-5”, “15”, etc.
1-6
Note
Getting Started
Sources for More Information
Sources for More Information
For additional information about switch operation and features not covered in this guide, consult the following sources:
■For information on which product manual to consult on a given software feature, refer to “Product Documentation” on page xi.
For the latest version of all ProCurve switch documentation, including release notes covering recently added features, visit the ProCurve Networking website at http://www.procurve.com. Click on Technical support, and then click on Product manuals.
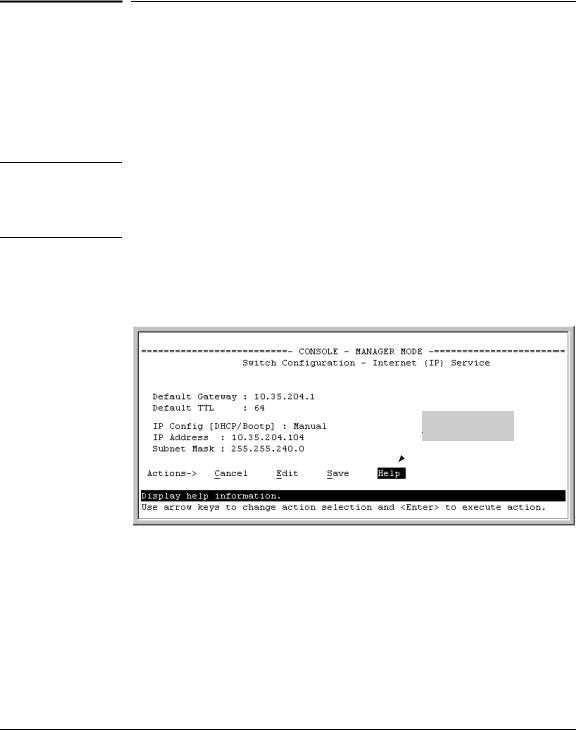
■For information on specific parameters in the menu interface, refer to the online help provided in the interface. For example:
Online Help for
Menu interface
Figure 1-2. Getting Help in the Menu Interface
■For information on a specific command in the CLI, type the command name followed by “help”. For example:
1-7

Getting Started
Need Only a Quick Start?
Figure 1-3. Getting Help in the CLI
■For information on specific features in the Web browser interface, use the online help. For more information, refer to the Management and Configuration Guide for your switch.
■For further information on ProCurve Networking switch technology, visit the ProCurve website at:
http://www.procurve.com
Need Only a Quick Start?
IP Addressing
If you just want to give the switch an IP address so that it can communicate on your network, or if you are not using multiple VLANs, ProCurve recommends that you use the Switch Setup screen to quickly configure IP addressing. To do so, do one of the following:
■Enter setup at the CLI Manager level prompt.
ProCurve# setup
■In the Main Menu of the Menu interface, select
8.Run Setup
For more on using the Switch Setup screen, see the Installation and Getting Started Guide you received with the switch.
1-8

Getting Started
Need Only a Quick Start?
To Set Up and Install the Switch in Your Network
Important!
Use the Installation and Getting Started Guide shipped with your switch for the following:
■Notes, cautions, and warnings related to installing and using the switch and its related modules
■Instructions for physically installing the switch in your network
■Quickly assigning an IP address and subnet mask, setting a Manager password, and (optionally) configuring other basic features.
■Interpreting LED behavior.
For the latest version of the Installation and Getting Started Guide and other documentation for your switch, visit the ProCurve website. (Refer to “Product Documentation” on page xi of this guide for further details.)
1-9

Getting Started
Need Only a Quick Start?
— This page is intentionally unused. —
1-10

2
Configuring Username and Password Security
Contents
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Configuring Local Password Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Menu: Setting Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
CLI: Setting Passwords and Usernames . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Web: Setting Passwords and Usernames . . . . . . . . . . . . . . . . . . . . . . . . 2-6
Front-Panel Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
When Security Is Important . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Front-Panel Button Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-8
Configuring Front-Panel Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-10
Password Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-15
Password Recovery Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-17
2-1

Configuring Username and Password Security
Overview
Note
Overview
Feature |
Default |
Menu |
CLI |
Web |
Set Usernames |
none |
— |
— |
page 2-6 |
Set a Password |
none |
page 2-4 |
page 2-5 |
page 2-6 |
Delete Password Protection |
n/a |
page 2-4 |
page 2-6 |
page 2-6 |
The following features apply only to the Series 2600, 2600-PWR, and 2800 Switches.
Show front-panel-security |
n/a |
— |
page 1-13 |
— |
Front-panel-security |
|
— |
page 1-13 |
— |
password-clear |
enabled |
— |
page 1-13 |
— |
reset-on-clear |
disabled |
— |
page 1-14 |
— |
factory-reset |
enabled |
— |
page 1-15 |
— |
password-recovery |
enabled |
— |
page 1-15 |
— |
|
|
|
|
|
Console access includes both the menu interface and the CLI. There are two levels of console access: Manager and Operator. For security, you can set a password pair (username and password) on each of these levels.
Usernames are optional. Also, in the menu interface, you can configure passwords, but not usernames. To configure usernames, use the CLI or the web browser interface.
Level |
Actions Permitted |
|
|
Manager: |
Access to all console interface areas. |
|
This is the default level. That is, if a Manager password has not been set prior |
|
to starting the current console session, then anyone having access to the |
|
console can access any area of the console interface. |
Operator: |
Access to the Status and Counters menu, the Event Log, and the CLI*, but no |
|
Configuration capabilities. |
|
On the Operator level, the configuration menus, Download OS, and Reboot |
|
Switch options in the Main Menu are not available. |
*Allows use of the ping, link-test, show, menu, exit, and logout commands, plus the enable command if you can provide the Manager password.
2-2

Note
Caution
Configuring Username and Password Security
Overview
To configure password security:
1.Set a Manager password pair (and an Operator password pair, if applicable for your system).
2.Exit from the current console session. A Manager password pair will now be needed for full access to the console.
If you do steps 1 and 2, above, then the next time a console session is started for either the menu interface or the CLI, a prompt appears for a password. Assuming you have protected both the Manager and Operator levels, the level of access to the console interface will be determined by which password is entered in response to the prompt.
If you set a Manager password, you may also want to configure the
Inactivity Time parameter. (Refer to the Management and Configuration Guide for your switch.) This causes the console session to end after the specified period of inactivity, thus giving you added security against unauthorized console access.
The manager and operator passwords and (optional) usernames control access to the menu interface, CLI, and web browser interface.
If you configure only a Manager password (with no Operator password), and in a later session the Manager password is not entered correctly in response to a prompt from the switch, then the switch does not allow management access for that session.
Passwords are case-sensitive.
If the switch has neither a Manager nor an Operator password, anyone having access to the switch through either Telnet, the serial port, or the web browser interface can access the switch with full manager privileges. Also, if you configure only an Operator password, entering the Operator password enables full manager privileges.
The rest of this section covers how to:
■Set passwords
■Delete passwords
■Recover from a lost password
2-3

Configuring Username and Password Security
Configuring Local Password Security
Configuring Local Password Security
Menu: Setting Passwords
As noted earlier in this section, usernames are optional. Configuring a username requires either the CLI or the web browser interface.
1.From the Main Menu select:
3. Console Passwords
Figure 2-1. The Set Password Screen
2.To set a new password:
a.Select Set Manager Password or Set Operator Password. You will then be prompted with Enter new password.
b.Type a password of up to 16 ASCII characters with no spaces and press [Enter]. (Remember that passwords are case-sensitive.)
c.When prompted with Enter new password again, retype the new password and press [Enter].
After you configure a password, if you subsequently start a new console session, you will be prompted to enter the password. (If you use the CLI or web browser interface to configure an optional username, the switch will prompt you for the username, and then the password.)
To Delete Password Protection (Including Recovery from a Lost Password): This procedure deletes all usernames (if configured) and passwords (Manager and Operator).
2-4
 Loading...
Loading...