Siemens S223, S323 User Manual

User Manual
SURPASS hiD 6615 S223/S323 R1.5
UMN:CLI
A50010-Y3-C150-2-7619

UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
Important Notice on Product Safety
Elevated voltages are inevitably present at specific points in this electrical equipment. Some of the parts may also have elevated operating temperatures.
Non-observance of these conditions and the safety instructions can result in personal injury or in property damage.
Therefore, only trained and qualified personnel may install and maintain the system.
The system complies with the standard EN 60950-1 / IEC 60950-1. All equipment connected has to comply with the applicable safety standards.
The same text in German:
Wichtiger Hinweis zur Produktsicherheit
In elektrischen Anlagen stehen zwangsläufig bestimmte Teile der Geräte unter Spannung. Einige Teile können auch eine hohe Betriebstemperatur aufweisen.
Eine Nichtbeachtung dieser Situation und der Warnungshinweise kann zu Körperverletzungen und Sachschäden führen.
Deshalb wird vorausgesetzt, dass nur geschultes und qualifiziertes Personal die Anlagen installiert und wartet.
Das System entspricht den Anforderungen der EN 60950-1 / IEC 60950-1. Angeschlossene Geräte müssen die zutreffenden Sicherheitsbestimmungen erfüllen.
Trademarks:
All designations used in this document can be trademarks, the use of which by third parties for their own purposes could violate the rights of their owners.
Copyright (C) Siemens AG 2005-2006.
Issued by the Communications Group
Hofmannstraße 51
D-81359 München
Technical modifications possible.
Technical specifications and features are binding only insofar as they are specifically and expressly agreed upon in a written contract.
2 |
A50010-Y3-C150-2-7619 |
User Manual |
UMN:CLI |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
|
Reason for Update
Summary: System software upgrade added
Details:
Chapter/Section |
Reason for Update |
|
|
11 |
System software upgrade added |
|
|
Issue History
Issue |
Date of Issue |
Reason for Update |
Number |
|
|
|
|
|
01 |
07/2006 |
Initial release |
|
|
|
02 |
08/2006 |
System software upgrade added |
|
|
|
A50010-Y3-C150-2-7619 |
3 |
UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
This document consists of a total 381 pages. All pages are issue 2.
Contents |
|
|
1 |
Introduction ....................................................................................................... |
20 |
1.1 |
Audience........................................................................................................... |
20 |
1.2 |
Document Structure.......................................................................................... |
20 |
1.3 |
Document Convention ...................................................................................... |
21 |
1.4 |
Document Notation ........................................................................................... |
21 |
1.5 |
CE Declaration of Conformity ........................................................................... |
21 |
1.6 |
GPL/LGPL Warranty and Liability Exclusion .................................................... |
22 |
2 |
System Overview.............................................................................................. |
23 |
2.1 |
System Features............................................................................................... |
24 |
3 |
Command Line Interface (CLI) ......................................................................... |
27 |
3.1 |
Command Mode ............................................................................................... |
27 |
3.1.1 |
Privileged EXEC View Mode ............................................................................ |
29 |
3.1.2 |
Privileged EXEC Enable Mode......................................................................... |
29 |
3.1.3 |
Global Configuration Mode............................................................................... |
29 |
3.1.4 |
Bridge Configuration Mode............................................................................... |
30 |
3.1.5 |
Rule Configuration Mode.................................................................................. |
31 |
3.1.6 |
DHCP Configuration Mode ............................................................................... |
32 |
3.1.7 |
DHCP Option 82 Configuration Mode .............................................................. |
32 |
3.1.8 |
Interface Configuration Mode ........................................................................... |
33 |
3.1.9 |
RMON Configuration Mode .............................................................................. |
33 |
3.1.10 |
Router Configuration Mode .............................................................................. |
34 |
3.1.11 |
VRRP Configuration Mode ............................................................................... |
34 |
3.1.12 |
Route-Map Configuration Mode ....................................................................... |
35 |
3.2 |
Useful Tips ........................................................................................................ |
36 |
3.2.1 |
Listing Available Commands ............................................................................ |
36 |
3.2.2 |
Calling Command History................................................................................. |
37 |
3.2.3 |
Using Abbreviation............................................................................................ |
38 |
3.2.4 |
Using Command of Privileged EXEC Enable Mode......................................... |
38 |
3.2.5 |
Exit Current Command Mode ........................................................................... |
39 |
4 |
System Connection and IP Address ................................................................. |
40 |
4.1 |
System Connection........................................................................................... |
40 |
4.1.1 |
System Login .................................................................................................... |
40 |
4.1.2 |
Password for Privileged EXEC Mode............................................................... |
41 |
4.1.3 |
Changing Login Password................................................................................ |
42 |
4.1.4 |
Management for System Account..................................................................... |
42 |
4.1.4.1 |
Creating System Account ................................................................................. |
42 |
4.1.4.2 |
Configuring Security Level................................................................................ |
43 |
4.1.5 |
Limiting Number of User................................................................................... |
47 |
4.1.6 |
Telnet Access.................................................................................................... |
47 |
4.1.7 |
Auto Log-out ..................................................................................................... |
48 |
4.1.8 |
System Rebooting ............................................................................................ |
48 |
4.1.8.1 |
Manual System Rebooting ............................................................................... |
48 |
4.1.8.2 |
Auto System Rebooting.................................................................................... |
49 |
4.2 |
System Authentication ...................................................................................... |
49 |
4.2.1 |
Authentication Method...................................................................................... |
50 |
4 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
4.2.2 |
Authentication Interface..................................................................................... |
50 |
4.2.3 |
Primary Authentication Method ......................................................................... |
50 |
4.2.4 |
RADIUS Server ................................................................................................. |
51 |
4.2.4.1 |
RADIUS Server for System Authentication ....................................................... |
51 |
4.2.4.2 |
RADIUS Server Priority ..................................................................................... |
51 |
4.2.4.3 |
Timeout of Authentication Request.................................................................... |
51 |
4.2.4.4 |
Frequency of Retransmit ................................................................................... |
52 |
4.2.5 |
TACACS Server................................................................................................. |
52 |
4.2.5.1 |
TACACS Server for System Authentication....................................................... |
52 |
4.2.5.2 |
TACACS Server Priority .................................................................................... |
52 |
4.2.5.3 |
Timeout of Authentication Request.................................................................... |
52 |
4.2.5.4 |
Additional TACACS+ Configuration................................................................... |
53 |
4.2.6 |
Accounting Mode............................................................................................... |
54 |
4.2.7 |
Displaying System Authentication ..................................................................... |
54 |
4.2.8 |
Sample Configuration........................................................................................ |
55 |
4.3 |
Assigning IP Address......................................................................................... |
56 |
4.3.1 |
Enabling Interface.............................................................................................. |
57 |
4.3.2 |
Disabling Interface............................................................................................. |
57 |
4.3.3 |
Assigning IP Address to Network Interface ....................................................... |
58 |
4.3.4 |
Static Route and Default Gateway .................................................................... |
58 |
4.3.5 |
Displaying Forwarding Information Base(FIB) Table......................................... |
59 |
4.3.6 |
Forwarding Information Base(FIB) Retain......................................................... |
59 |
4.3.7 |
Displaying Interface ........................................................................................... |
60 |
4.3.8 |
Sample Configuration........................................................................................ |
60 |
4.4 |
SSH (Secure Shell) ........................................................................................... |
61 |
4.4.1 |
SSH Server........................................................................................................ |
61 |
4.4.1.1 |
Enabling SSH Server......................................................................................... |
61 |
4.4.1.2 |
Displaying On-line SSH Client........................................................................... |
61 |
4.4.1.3 |
Disconnecting SSH Client ................................................................................. |
61 |
4.4.1.4 |
Displaying Connection History of SSH Client.................................................... |
61 |
4.4.1.5 |
Assigning Specific Authentication Key............................................................... |
62 |
4.4.2 |
SSH Client ......................................................................................................... |
62 |
4.4.2.1 |
Login to SSH Server.......................................................................................... |
62 |
4.4.2.2 |
File Copy ........................................................................................................... |
62 |
4.4.2.3 |
Configuring Authentication Key ......................................................................... |
62 |
4.5 |
802.1x Authentication ........................................................................................ |
64 |
4.5.1 |
802.1x Authentication ........................................................................................ |
65 |
4.5.1.1 |
Enabling 802.1x................................................................................................. |
65 |
4.5.1.2 |
Configuring RADIUS Server.............................................................................. |
65 |
4.5.1.3 |
Configuring Authentication Mode ...................................................................... |
66 |
4.5.1.4 |
Authentication Port ............................................................................................ |
67 |
4.5.1.5 |
Force Authorization............................................................................................ |
67 |
4.5.1.6 |
Configuring Interval for Retransmitting Request/Identity Packet ...................... |
67 |
4.5.1.7 |
Configuring Number of Request to RADIUS Server ......................................... |
68 |
4.5.1.8 |
Configuring Interval of Request to RADIUS Server .......................................... |
68 |
4.5.2 |
802.1x Re-Authentication .................................................................................. |
68 |
4.5.2.1 |
Enabling 802.1x Re-Authentication ................................................................... |
68 |
4.5.2.2 |
Configuring the Interval of Re-Authentication ................................................... |
69 |
4.5.2.3 |
Configuring the Interval of Requesting Re-authentication................................. |
69 |
4.5.2.4 |
802.1x Re-authentication .................................................................................. |
69 |
4.5.3 |
Initializing Authentication Status ........................................................................ |
70 |
A50010-Y3-C150-2-7619 |
5 |

UMN:CLI |
|
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
4.5.4 |
Applying Default Value...................................................................................... |
70 |
4.5.5 |
Displaying 802.1x Configuration....................................................................... |
70 |
4.5.6 |
802.1x User Authentication Statistic ................................................................. |
70 |
4.5.7 |
Sample Configuration ....................................................................................... |
71 |
5 |
Port Configuration............................................................................................. |
73 |
5.1 |
Port Basic ......................................................................................................... |
73 |
5.1.1 |
Selecting Port Type........................................................................................... |
73 |
5.2 |
Ethernet Port Configuration .............................................................................. |
74 |
5.2.1 |
Enabling Ethernet Port ..................................................................................... |
74 |
5.2.2 |
Auto-negotiation................................................................................................ |
75 |
5.2.3 |
Transmit Rate ................................................................................................... |
75 |
5.2.4 |
Duplex Mode..................................................................................................... |
76 |
5.2.5 |
Flow Control...................................................................................................... |
76 |
5.2.6 |
Port Description ................................................................................................ |
77 |
5.2.7 |
Traffic Statistics................................................................................................. |
78 |
5.2.7.1 |
The Packets Statistics....................................................................................... |
78 |
5.2.7.2 |
The CPU statistics ............................................................................................ |
79 |
5.2.7.3 |
The Protocol statistics....................................................................................... |
79 |
5.2.8 |
Port Status ........................................................................................................ |
80 |
5.2.9 |
Initializing Port Statistics ................................................................................... |
80 |
5.3 |
Port Mirroring .................................................................................................... |
80 |
6 |
System Environment ........................................................................................ |
83 |
6.1 |
Environment Configuration ............................................................................... |
83 |
6.1.1 |
Host Name........................................................................................................ |
83 |
6.1.2 |
Time and Date .................................................................................................. |
83 |
6.1.3 |
Time Zone......................................................................................................... |
84 |
6.1.4 |
Network Time Protocol ..................................................................................... |
84 |
6.1.5 |
NTP (Network Time Protocol)........................................................................... |
85 |
6.1.6 |
Simple Network Time Protocol (SNTP) ............................................................ |
85 |
6.1.7 |
Terminal Configuration...................................................................................... |
86 |
6.1.8 |
Login Banner .................................................................................................... |
87 |
6.1.9 |
DNS Server....................................................................................................... |
87 |
6.1.10 |
Fan Operation................................................................................................... |
88 |
6.1.11 |
Disabling Daemon Operation ........................................................................... |
88 |
6.1.12 |
System Threshold............................................................................................. |
88 |
6.1.12.1 |
CPU Load ......................................................................................................... |
88 |
6.1.12.2 |
Port Traffic ........................................................................................................ |
89 |
6.1.12.3 |
Fan Operation................................................................................................... |
89 |
6.1.12.4 |
System Temperature......................................................................................... |
90 |
6.1.12.5 |
System Memory................................................................................................ |
90 |
6.1.13 |
Enabling FTP Server ........................................................................................ |
90 |
6.1.14 |
Assigning IP Address of FTP Client.................................................................. |
91 |
6.2 |
Configuration Management .............................................................................. |
91 |
6.2.1 |
Displaying System Configuration...................................................................... |
91 |
6.2.2 |
Saving System Configuration ........................................................................... |
92 |
6.2.3 |
Auto-Saving ...................................................................................................... |
92 |
6.2.4 |
System Configuration File ................................................................................ |
92 |
6.2.5 |
Restoring Default Configuration ....................................................................... |
93 |
6.3 |
System Management........................................................................................ |
94 |
6.3.1 |
Network Connection ......................................................................................... |
94 |
6 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
6.3.2 |
IP ICMP Source-Routing ................................................................................... |
97 |
6.3.3 |
Tracing Packet Route ........................................................................................ |
98 |
6.3.4 |
Displaying User Connecting to System ............................................................. |
99 |
6.3.5 |
MAC Table ......................................................................................................... |
99 |
6.3.6 |
Configuring Ageing time .................................................................................. |
100 |
6.3.7 |
Running Time of System ................................................................................. |
100 |
6.3.8 |
System Information.......................................................................................... |
100 |
6.3.9 |
System Memory Information ........................................................................... |
101 |
6.3.10 |
CPU packet limit .............................................................................................. |
101 |
6.3.11 |
Average of CPU Load...................................................................................... |
101 |
6.3.12 |
Running Process ............................................................................................. |
101 |
6.3.13 |
Displaying System Image................................................................................ |
102 |
6.3.14 |
Displaying Installed OS ................................................................................... |
102 |
6.3.15 |
Default OS ....................................................................................................... |
102 |
6.3.16 |
Switch Status ................................................................................................... |
103 |
6.3.17 |
Tech Support ................................................................................................... |
103 |
7 |
Network Management ..................................................................................... |
104 |
7.1 |
Simple Network Management Protocol (SNMP) ............................................. |
104 |
7.1.1 |
SNMP Community ........................................................................................... |
104 |
7.1.2 |
Information of SNMP Agent............................................................................. |
105 |
7.1.3 |
SNMP Com2sec .............................................................................................. |
106 |
7.1.4 |
SNMP Group ................................................................................................... |
106 |
7.1.5 |
SNMP View Record......................................................................................... |
107 |
7.1.6 |
Permission to Access SNMP View Record ..................................................... |
107 |
7.1.7 |
SNMP Version 3 User...................................................................................... |
108 |
7.1.8 |
SNMP Trap ...................................................................................................... |
108 |
7.1.8.1 |
SNMP Trap Host.............................................................................................. |
109 |
7.1.8.2 |
SNMP Trap Mode ............................................................................................ |
109 |
7.1.8.3 |
Enabling SNMP Trap ....................................................................................... |
110 |
7.1.8.4 |
Disabling SNMP Trap ...................................................................................... |
111 |
7.1.8.5 |
Displaying SNMP Trap .................................................................................... |
112 |
7.1.9 |
SNMP Alarm .................................................................................................... |
112 |
7.1.9.1 |
Enabling Alarm Notification ............................................................................. |
112 |
7.1.9.2 |
Default Alarm Severity..................................................................................... |
113 |
7.1.9.3 |
Alarm Severity Criterion................................................................................... |
113 |
7.1.9.4 |
Generic Alarm Severity.................................................................................... |
114 |
7.1.9.5 |
ADVA Alarm Severity ....................................................................................... |
115 |
7.1.9.6 |
ERP Alarm Severity ......................................................................................... |
116 |
7.1.9.7 |
STP Guard Alarm Severity .............................................................................. |
117 |
7.1.10 |
Displaying SNMP Configuration ...................................................................... |
117 |
7.1.11 |
Disabling SNMP .............................................................................................. |
118 |
7.2 |
Operation, Administration and Maintenance (OAM)........................................ |
119 |
7.2.1 |
OAM Loopback................................................................................................ |
119 |
7.2.2 |
Local OAM Mode............................................................................................. |
120 |
7.2.3 |
OAM Unidirection ............................................................................................ |
120 |
7.2.4 |
Remote OAM................................................................................................... |
120 |
7.2.5 |
Displaying OAM Configuration ........................................................................ |
121 |
7.3 |
Link Layer Discovery Protocol (LLDP) ............................................................ |
123 |
7.3.1 |
LLDP Operation............................................................................................... |
123 |
7.3.2 |
LLDP Operation Type ...................................................................................... |
123 |
A50010-Y3-C150-2-7619 |
7 |

UMN:CLI |
|
User Manual |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
7.3.3 |
Basic TLV........................................................................................................ |
123 |
7.3.4 |
LLDP Message ............................................................................................... |
124 |
7.3.5 |
Interval and Delay Time.................................................................................. |
124 |
7.3.6 |
Displaying LLDP Configuration....................................................................... |
125 |
7.4 |
Remote Monitoring (RMON)........................................................................... |
126 |
7.4.1 |
RMON History................................................................................................. |
126 |
7.4.1.1 |
Source Port of Statistical Data........................................................................ |
127 |
7.4.1.2 |
Subject of RMON History ............................................................................... |
127 |
7.4.1.3 |
Number of Sample Data ................................................................................. |
127 |
7.4.1.4 |
Interval of Sample Inquiry............................................................................... |
127 |
7.4.1.5 |
Activating RMON History................................................................................ |
128 |
7.4.1.6 |
Deleting Configuration of RMON History........................................................ |
128 |
7.4.1.7 |
Displaying RMON History............................................................................... |
128 |
7.4.2 |
RMON Alarm................................................................................................... |
129 |
7.4.2.1 |
Subject of RMON Alarm ................................................................................. |
129 |
7.4.2.2 |
Object of Sample Inquiry ................................................................................ |
130 |
7.4.2.3 |
Absolute Comparison and Delta Comparison ................................................ |
130 |
7.4.2.4 |
Upper Bound of Threshold ............................................................................. |
130 |
7.4.2.5 |
Lower Bound of Threshold ............................................................................. |
131 |
7.4.2.6 |
Configuring Standard of the First Alarm.......................................................... |
131 |
7.4.2.7 |
Interval of Sample Inquiry............................................................................... |
131 |
7.4.2.8 |
Activating RMON Alarm.................................................................................. |
132 |
7.4.2.9 |
Deleting Configuration of RMON Alarm.......................................................... |
132 |
7.4.2.10 |
Displaying RMON Alarm................................................................................. |
132 |
7.4.3 |
RMON Event................................................................................................... |
132 |
7.4.3.1 |
Event Community ........................................................................................... |
132 |
7.4.3.2 |
Event Description............................................................................................ |
133 |
7.4.3.3 |
Subject of RMON Event ................................................................................. |
133 |
7.4.3.4 |
Event Type...................................................................................................... |
133 |
7.4.3.5 |
Activating RMON Event.................................................................................. |
133 |
7.4.3.6 |
Deleting Configuration of RMON Event.......................................................... |
134 |
7.4.3.7 |
Displaying RMON Event................................................................................. |
134 |
7.5 |
Syslog ............................................................................................................. |
135 |
7.5.1 |
Syslog Output Level ....................................................................................... |
135 |
7.5.2 |
Facility Code ................................................................................................... |
137 |
7.5.3 |
Syslog Bind Address....................................................................................... |
137 |
7.5.4 |
Debug Message for Remote Terminal ............................................................ |
138 |
7.5.5 |
Disabling Syslog ............................................................................................. |
138 |
7.5.6 |
Displaying Syslog Message............................................................................ |
138 |
7.5.7 |
Displaying Syslog Configuration..................................................................... |
138 |
7.6 |
Rule and QoS ................................................................................................. |
139 |
7.6.1 |
How to Operate Rule and QoS....................................................................... |
139 |
7.6.2 |
Rule Configuration.......................................................................................... |
140 |
7.6.2.1 |
Rule Creation.................................................................................................. |
140 |
7.6.2.2 |
Rule Priority .................................................................................................... |
140 |
7.6.2.3 |
Packet Classification ...................................................................................... |
141 |
7.6.2.4 |
Rule Action...................................................................................................... |
143 |
7.6.2.5 |
Applying Rule.................................................................................................. |
145 |
7.6.2.6 |
Modifying and Deleting Rule........................................................................... |
145 |
7.6.2.7 |
Displaying Rule............................................................................................... |
146 |
7.6.3 |
QoS................................................................................................................. |
146 |
8 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
7.6.3.1 |
Scheduling Algorithm....................................................................................... |
147 |
7.6.3.2 |
Qos Weight...................................................................................................... |
149 |
7.6.3.3 |
802.1p Priory-to-queue Mapping..................................................................... |
149 |
7.6.3.4 |
Queue Parameter ............................................................................................ |
150 |
7.6.3.5 |
Displaying QoS................................................................................................ |
150 |
7.6.4 |
Admin Access Rule.......................................................................................... |
150 |
7.6.4.1 |
Rule Creation................................................................................................... |
151 |
7.6.4.2 |
Rule Priority ..................................................................................................... |
151 |
7.6.4.3 |
Packet Classification ....................................................................................... |
152 |
7.6.4.4 |
Rule Action ...................................................................................................... |
153 |
7.6.4.5 |
Applying Rule .................................................................................................. |
153 |
7.6.4.6 |
Modifying and Deleting Rule ........................................................................... |
154 |
7.6.4.7 |
Displaying Rule................................................................................................ |
154 |
7.7 |
NetBIOS Filtering............................................................................................. |
155 |
7.8 |
Martian Filtering............................................................................................... |
156 |
7.9 |
Max Host ......................................................................................................... |
156 |
7.9.1 |
Max New Hosts ............................................................................................... |
157 |
7.10 |
Port Security .................................................................................................... |
158 |
7.10.1 |
Port Security on Port ....................................................................................... |
158 |
7.10.2 |
Port Security Aging .......................................................................................... |
160 |
7.11 |
MAC Table ....................................................................................................... |
161 |
7.12 |
MAC Filtering................................................................................................... |
163 |
7.12.1 |
Default Policy of MAC Filtering........................................................................ |
163 |
7.12.2 |
Adding Policy of MAC Filter............................................................................. |
163 |
7.12.3 |
Deleting MAC Filter Policy............................................................................... |
164 |
7.12.4 |
Listing of MAC Filter Policy ............................................................................. |
164 |
7.12.5 |
Displaying MAC Filter Policy ........................................................................... |
164 |
7.13 |
Address Resolution Protocol (ARP) ................................................................ |
165 |
7.13.1 |
ARP Table........................................................................................................ |
165 |
7.13.1.1 |
Registering ARP Table..................................................................................... |
166 |
7.13.1.2 |
Displaying ARP Table ...................................................................................... |
166 |
7.13.2 |
ARP Alias......................................................................................................... |
167 |
7.13.3 |
ARP Inspection................................................................................................ |
167 |
7.13.4 |
Gratuitous ARP................................................................................................ |
169 |
7.13.5 |
Proxy-ARP....................................................................................................... |
169 |
7.14 |
ICMP Message Control ................................................................................... |
169 |
7.14.1 |
Blocking Echo Reply Message........................................................................ |
170 |
7.14.2 |
Interval for Transmit ICMP Message ............................................................... |
170 |
7.14.3 |
Transmitting ICMP Redirect Message............................................................. |
172 |
7.14.4 |
The policy of unreached messages................................................................. |
173 |
7.15 |
IP TCP Flag Control......................................................................................... |
173 |
7.15.1 |
RST Configuration ........................................................................................... |
173 |
7.15.2 |
SYN Configuration........................................................................................... |
174 |
7.16 |
Packet Dump ................................................................................................... |
174 |
7.16.1 |
Verifying Packet Dump .................................................................................... |
174 |
7.16.1.1 |
Packet Dump by Protocol................................................................................ |
175 |
7.16.1.2 |
Packet Dump with Option................................................................................ |
175 |
7.16.2 |
Debug Packet Dump ....................................................................................... |
177 |
7.17 |
Displaying the usage of the packet routing table............................................. |
177 |
8 |
System Main Functions ................................................................................... |
178 |
A50010-Y3-C150-2-7619 |
9 |

UMN:CLI |
|
User Manual |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
8.1 |
VLAN .............................................................................................................. |
178 |
8.1.1 |
Port-Based VLAN ........................................................................................... |
179 |
8.1.1.1 |
Creating VLAN................................................................................................ |
180 |
8.1.1.2 |
Specifying PVID.............................................................................................. |
180 |
8.1.1.3 |
Assigning Port to VLAN .................................................................................. |
180 |
8.1.1.4 |
Deleting VLAN ................................................................................................ |
180 |
8.1.1.5 |
Displaying VLAN............................................................................................. |
181 |
8.1.2 |
Protocol-Based VLAN..................................................................................... |
181 |
8.1.3 |
MAC address-based VLAN ............................................................................ |
181 |
8.1.4 |
Subnet-based VLAN....................................................................................... |
182 |
8.1.5 |
Tagged VLAN.................................................................................................. |
182 |
8.1.6 |
VLAN Description ........................................................................................... |
183 |
8.1.7 |
Displaying VLAN Information.......................................................................... |
183 |
8.1.8 |
QinQ ............................................................................................................... |
184 |
8.1.8.1 |
Double Tagging Operation.............................................................................. |
185 |
8.1.8.2 |
Double Tagging Configuration ........................................................................ |
185 |
8.1.8.3 |
TPID Configuration ......................................................................................... |
186 |
8.1.9 |
Layer 2 Isolation ............................................................................................. |
186 |
8.1.9.1 |
Port Isolation................................................................................................... |
187 |
8.1.9.2 |
Shared VLAN.................................................................................................. |
187 |
8.1.10 |
VLAN Translation............................................................................................ |
189 |
8.1.11 |
Sample Configuration ..................................................................................... |
189 |
8.2 |
Link Aggregation............................................................................................. |
192 |
8.2.1 |
Port Trunk ....................................................................................................... |
193 |
8.2.1.1 |
Configuring Port Trunk.................................................................................... |
193 |
8.2.1.2 |
Disabling Port Trunk ....................................................................................... |
194 |
8.2.1.3 |
Displaying Port Trunk Configuration............................................................... |
194 |
8.2.2 |
Link Aggregation Control Protocol (LACP) ..................................................... |
194 |
8.2.2.1 |
Configuring LACP........................................................................................... |
195 |
8.2.2.2 |
Packet Route .................................................................................................. |
195 |
8.2.2.3 |
Operating Mode of Member Port .................................................................... |
196 |
8.2.2.4 |
Identifying Member Ports within LACP........................................................... |
197 |
8.2.2.5 |
BPDU Transmission Rate............................................................................... |
197 |
8.2.2.6 |
Key value of Member Port .............................................................................. |
197 |
8.2.2.7 |
Priority of Member Port................................................................................... |
198 |
8.2.2.8 |
Priority of Switch............................................................................................. |
198 |
8.2.2.9 |
Displaying LACP Configuration ...................................................................... |
199 |
8.3 |
Spanning-Tree Protocol (STP)........................................................................ |
200 |
8.3.1 |
STP Operation ................................................................................................ |
201 |
8.3.2 |
RSTP Operation ............................................................................................. |
205 |
8.3.3 |
MSTP Operation ............................................................................................. |
209 |
8.3.4 |
Configuring STP/RSTP/MSTP/PVSTP/PVRSTP Mode (Required) ................ |
211 |
8.3.5 |
Configuring STP/RSTP/MSTP........................................................................ |
212 |
8.3.5.1 |
Activating STP/RSTP/MSTP .......................................................................... |
212 |
8.3.5.2 |
Root Switch..................................................................................................... |
212 |
8.3.5.3 |
Path-cost......................................................................................................... |
212 |
8.3.5.4 |
Port-priority ..................................................................................................... |
213 |
8.3.5.5 |
MST Region.................................................................................................... |
214 |
8.3.5.6 |
MSTP Protocol................................................................................................ |
215 |
8.3.5.7 |
Point-to-point MAC Parameters...................................................................... |
215 |
8.3.5.8 |
Edge Ports ...................................................................................................... |
215 |
10 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
8.3.5.9 |
Displaying Configuration ................................................................................. |
216 |
8.3.6 |
Configuring PVSTP/PVRSTP.......................................................................... |
217 |
8.3.6.1 |
Activating PVSTP/PVRSTP............................................................................. |
217 |
8.3.6.2 |
Root Switch ..................................................................................................... |
218 |
8.3.6.3 |
Path-cost ......................................................................................................... |
218 |
8.3.6.4 |
Port-priority ...................................................................................................... |
218 |
8.3.7 |
Root Guard ...................................................................................................... |
219 |
8.3.8 |
Restarting Protocol Migration .......................................................................... |
219 |
8.3.9 |
Bridge Protocol Data Unit Configuration ......................................................... |
220 |
8.3.9.1 |
Hello Time........................................................................................................ |
220 |
8.3.9.2 |
Forward Delay ................................................................................................. |
221 |
8.3.9.3 |
Max Age........................................................................................................... |
221 |
8.3.9.4 |
BPDU Hop ....................................................................................................... |
222 |
8.3.9.5 |
BPDU Filter...................................................................................................... |
222 |
8.3.9.6 |
BPDU Guard.................................................................................................... |
222 |
8.3.9.7 |
Self Loop Detection ......................................................................................... |
223 |
8.3.9.8 |
Displaying BPDU Configuration ...................................................................... |
224 |
8.3.10 |
Sample Configuration...................................................................................... |
225 |
8.4 |
Virtual Router Redundancy Protocol (VRRP).................................................. |
227 |
8.4.1 |
Configuring VRRP ........................................................................................... |
228 |
8.4.1.1 |
Associated IP Address..................................................................................... |
228 |
8.4.1.2 |
Access to Associated IP Address .................................................................... |
229 |
8.4.1.3 |
Master Router and Backup Router.................................................................. |
229 |
8.4.1.4 |
VRRP Track Function ...................................................................................... |
231 |
8.4.1.5 |
Authentication Password................................................................................. |
232 |
8.4.1.6 |
Preempt ........................................................................................................... |
233 |
8.4.1.7 |
VRRP Statistics ............................................................................................... |
234 |
8.5 |
Rate Limit ........................................................................................................ |
234 |
8.5.1 |
Configuring Rate Limit..................................................................................... |
235 |
8.5.2 |
Sample Configuration...................................................................................... |
235 |
8.6 |
Flood Guard..................................................................................................... |
236 |
8.6.1 |
Configuring Flood-Guard................................................................................. |
236 |
8.6.2 |
Sample Configuration...................................................................................... |
237 |
8.7 |
Bandwidth........................................................................................................ |
237 |
8.8 |
Dynamic Host Configuration Protocol (DHCP)................................................ |
238 |
8.8.1 |
DHCP Server................................................................................................... |
239 |
8.8.1.1 |
DHCP Pool Creation........................................................................................ |
240 |
8.8.1.2 |
DHCP Subnet .................................................................................................. |
240 |
8.8.1.3 |
Range of IP Address........................................................................................ |
240 |
8.8.1.4 |
Default Gateway .............................................................................................. |
241 |
8.8.1.5 |
IP Lease Time.................................................................................................. |
241 |
8.8.1.6 |
DNS Server ..................................................................................................... |
242 |
8.8.1.7 |
Manual Binding................................................................................................ |
242 |
8.8.1.8 |
Domain Name.................................................................................................. |
243 |
8.8.1.9 |
DHCP Server Option ....................................................................................... |
243 |
8.8.1.10 |
Static Mapping ................................................................................................. |
243 |
8.8.1.11 |
Recognition of DHCP Client ............................................................................ |
243 |
8.8.1.12 |
IP Address Validation....................................................................................... |
244 |
8.8.1.13 |
Authorized ARP ............................................................................................... |
244 |
8.8.1.14 |
Prohibition of 1:N IP Address Assignment....................................................... |
245 |
8.8.1.15 |
Ignoring BOOTP Request................................................................................ |
245 |
A50010-Y3-C150-2-7619 |
11 |

UMN:CLI |
|
User Manual |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
8.8.1.16 |
DHCP Packet Statistics .................................................................................. |
245 |
8.8.1.17 |
Displaying DHCP Pool Configuration ............................................................. |
246 |
8.8.2 |
DHCP Address Allocation with Option 82....................................................... |
247 |
8.8.2.1 |
DHCP Class Capability................................................................................... |
247 |
8.8.2.2 |
DHCP Class Creation..................................................................................... |
247 |
8.8.2.3 |
Relay Agent Information Pattern..................................................................... |
247 |
8.8.2.4 |
Associating DHCP Class ................................................................................ |
248 |
8.8.2.5 |
Range of IP Address for DHCP Class ............................................................ |
248 |
8.8.3 |
DHCP Lease Database .................................................................................. |
249 |
8.8.3.1 |
DHCP Database Agent ................................................................................... |
249 |
8.8.3.2 |
Displaying DHCP Lease Status ...................................................................... |
249 |
8.8.3.3 |
Deleting DHCP Lease Database .................................................................... |
250 |
8.8.4 |
DHCP Relay Agent ......................................................................................... |
250 |
8.8.4.1 |
Packet Forwarding Address............................................................................ |
251 |
8.8.4.2 |
Smart Relay Agent Forwarding....................................................................... |
251 |
8.8.5 |
DHCP Option 82 ............................................................................................. |
252 |
8.8.5.1 |
Enabling DHCP Option 82.............................................................................. |
253 |
8.8.5.2 |
Option 82 Sub-Option..................................................................................... |
253 |
8.8.5.3 |
Option 82 Reforwarding Policy ....................................................................... |
254 |
8.8.5.4 |
Option 82 Trust Policy .................................................................................... |
254 |
8.8.5.5 |
Simplified DHCP Option 82 ............................................................................ |
255 |
8.8.6 |
DHCP Client ................................................................................................... |
256 |
8.8.6.1 |
Enabling DHCP Client .................................................................................... |
256 |
8.8.6.2 |
DHCP Client ID............................................................................................... |
256 |
8.8.6.3 |
DHCP Class ID ............................................................................................... |
256 |
8.8.6.4 |
Host Name...................................................................................................... |
256 |
8.8.6.5 |
IP Lease Time................................................................................................. |
257 |
8.8.6.6 |
Requesting Option.......................................................................................... |
257 |
8.8.6.7 |
Forcing Release or Renewal of DHCP Lease ................................................ |
257 |
8.8.6.8 |
Displaying DHCP Client Configuration ........................................................... |
257 |
8.8.7 |
DHCP Snooping ............................................................................................. |
258 |
8.8.7.1 |
Enabling DHCP Snooping .............................................................................. |
258 |
8.8.7.2 |
DHCP Trust State ........................................................................................... |
258 |
8.8.7.3 |
DHCP Rate Limit ............................................................................................ |
259 |
8.8.7.4 |
DHCP Lease Limit .......................................................................................... |
259 |
8.8.7.5 |
Source MAC Address Verification................................................................... |
259 |
8.8.7.6 |
DHCP Snooping Database Agent................................................................... |
260 |
8.8.7.7 |
Displaying DHCP Snooping Configuration ..................................................... |
261 |
8.8.8 |
IP Source Guard ............................................................................................. |
261 |
8.8.8.1 |
Enabling IP Source Guard.............................................................................. |
261 |
8.8.8.2 |
Static IP Source Binding ................................................................................. |
262 |
8.8.8.3 |
Displaying IP Source Guard Configuration..................................................... |
262 |
8.8.9 |
DHCP Filtering................................................................................................ |
263 |
8.8.9.1 |
DHCP Packet Filtering.................................................................................... |
263 |
8.8.9.2 |
DHCP Server Packet Filtering ........................................................................ |
263 |
8.8.10 |
Debugging DHCP ........................................................................................... |
264 |
8.9 |
Ethernet Ring Protection (ERP)...................................................................... |
265 |
8.9.1 |
ERP Operation................................................................................................ |
265 |
8.9.2 |
Loss of Test Packet (LOTP)............................................................................ |
267 |
8.9.3 |
Configuring ERP............................................................................................. |
267 |
8.9.3.1 |
ERP Domain ................................................................................................... |
267 |
12 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
8.9.3.2 |
RM Node ......................................................................................................... |
268 |
8.9.3.3 |
Port of ERP domain......................................................................................... |
268 |
8.9.3.4 |
Protected VLAN............................................................................................... |
268 |
8.9.3.5 |
Protected Activation......................................................................................... |
268 |
8.9.3.6 |
Manual Switch to Secondary........................................................................... |
269 |
8.9.3.7 |
Wait-to-Restore Time....................................................................................... |
269 |
8.9.3.8 |
Learning Disable Time..................................................................................... |
269 |
8.9.3.9 |
Test Packet Interval ......................................................................................... |
269 |
8.9.3.10 |
Displaying ERP Configuration ......................................................................... |
270 |
8.10 |
Stacking ........................................................................................................... |
270 |
8.10.1 |
Switch Group ................................................................................................... |
271 |
8.10.2 |
Designating Master and Slave Switch............................................................. |
271 |
8.10.3 |
Disabling Stacking ........................................................................................... |
272 |
8.10.4 |
Displaying Stacking Status .............................................................................. |
272 |
8.10.5 |
Accessing to Slave Switch from Master Switch .............................................. |
272 |
8.10.6 |
Sample Configuration...................................................................................... |
272 |
8.11 |
Broadcast Storm Control ................................................................................. |
274 |
8.12 |
Jumbo-frame Capacity .................................................................................... |
275 |
8.13 |
Blocking Direct Broadcast ............................................................................... |
276 |
8.14 |
Maximum Transmission Unit (MTU) ................................................................ |
276 |
9 |
IP Multicast ...................................................................................................... |
278 |
9.1 |
Multicast Routing Information Base................................................................. |
279 |
9.1.1 |
Enabling Multicast Routing (Required)............................................................ |
279 |
9.1.2 |
Limitation of MRIB Routing Entry .................................................................... |
279 |
9.1.3 |
Clearing MRIB Information .............................................................................. |
280 |
9.1.4 |
Displaying MRIB Information........................................................................... |
281 |
9.1.5 |
Multicast Time-To-Live Threshold.................................................................... |
281 |
9.1.6 |
MRIB Debug .................................................................................................... |
281 |
9.1.7 |
Multicast Aging ................................................................................................ |
282 |
9.2 |
Internet Group Management Protocol (IGMP) ................................................ |
283 |
9.2.1 |
IGMP Basic Configuration ............................................................................... |
283 |
9.2.1.1 |
IGMP Version per Interface ............................................................................. |
283 |
9.2.1.2 |
Removing IGMP Entry..................................................................................... |
284 |
9.2.1.3 |
IGMP Debug.................................................................................................... |
284 |
9.2.1.4 |
IGMP Robustness Value ................................................................................. |
284 |
9.2.2 |
IGMP Version 2 ............................................................................................... |
284 |
9.2.2.1 |
IGMP Static Join Setting.................................................................................. |
284 |
9.2.2.2 |
Maximum Number of Groups .......................................................................... |
285 |
9.2.2.3 |
IGMP Query Configuration .............................................................................. |
285 |
9.2.2.4 |
IGMP v2 Fast Leave........................................................................................ |
287 |
9.2.2.5 |
Displaying the IGMP Configuration ................................................................. |
287 |
9.2.3 |
L2 MFIB ........................................................................................................... |
288 |
9.2.4 |
IGMP Snooping Basic Configuration............................................................... |
288 |
9.2.4.1 |
Enabling IGMP Snooping per VLAN ............................................................... |
288 |
9.2.4.2 |
Robustness Count for IGMP v2 Snooping ...................................................... |
289 |
9.2.5 |
IGMP v2 Snooping .......................................................................................... |
289 |
9.2.5.1 |
IGMP v2 Snooping Fast Leave ....................................................................... |
290 |
9.2.5.2 |
IGMP v2 Snooping Querier ............................................................................. |
291 |
9.2.5.3 |
IGMP v2 Snooping Last-Member-Interval ....................................................... |
293 |
9.2.5.4 |
IGMP v2 Snooping Report Method ................................................................. |
294 |
A50010-Y3-C150-2-7619 |
13 |

UMN:CLI |
|
User Manual |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
9.2.5.5 |
Mrouter Port.................................................................................................... |
294 |
9.2.5.6 |
Multicast TCN Flooding .................................................................................. |
295 |
9.2.6 |
IGMP v3 Snooping.......................................................................................... |
297 |
9.2.6.1 |
IGMP Snooping Version ................................................................................. |
297 |
9.2.6.2 |
Join Host Management................................................................................... |
297 |
9.2.6.3 |
Immediate Block ............................................................................................. |
298 |
9.2.7 |
Multicast VLAN Registration (MVR) ............................................................... |
298 |
9.2.7.1 |
Enabling MVR................................................................................................. |
299 |
9.2.7.2 |
MVR Group Address....................................................................................... |
299 |
9.2.7.3 |
MVR IP Address ............................................................................................. |
299 |
9.2.7.4 |
Send and Receive Port................................................................................... |
300 |
9.2.7.5 |
Displaying MVR Configuration........................................................................ |
300 |
9.2.8 |
IGMP Filtering and Throttling.......................................................................... |
300 |
9.2.8.1 |
Creating IGMP Profile..................................................................................... |
301 |
9.2.8.2 |
Policy of IGMP Profile..................................................................................... |
301 |
9.2.8.3 |
Group Range of IGMP Profile......................................................................... |
301 |
9.2.8.4 |
Applying IGMP Profile to the Filter Port.......................................................... |
302 |
9.2.8.5 |
Max Number of IGMP Join Group .................................................................. |
302 |
9.2.9 |
Displaying IGMP Snooping Table ................................................................... |
303 |
9.3 |
PIM-SM (Protocol Independent Multicast-Sparse Mode) ............................... |
303 |
9.3.1 |
PIM Common Configuration ........................................................................... |
304 |
9.3.1.1 |
PIM-SM and Passive Mode ............................................................................ |
305 |
9.3.1.2 |
DR Priority ...................................................................................................... |
305 |
9.3.1.3 |
Filters of Neighbor in PIM ............................................................................... |
306 |
9.3.1.4 |
PIM Hello Query ............................................................................................. |
306 |
9.3.1.5 |
PIM Debug...................................................................................................... |
307 |
9.3.2 |
BSR and RP ................................................................................................... |
307 |
9.3.3 |
Bootstrap Router (BSR).................................................................................. |
307 |
9.3.4 |
RP Information................................................................................................ |
308 |
9.3.4.1 |
Static RP for Certain Group ............................................................................ |
308 |
9.3.4.2 |
Enabling Transmission of Candidate RP Message ........................................ |
309 |
9.3.4.3 |
KAT (Keep Alive Time) of RP.......................................................................... |
310 |
9.3.4.4 |
Ignoring RP Priority......................................................................................... |
310 |
9.3.5 |
PIM-SM Registration ...................................................................................... |
310 |
9.3.5.1 |
Rate Limit of Register Message ..................................................................... |
310 |
9.3.5.2 |
Registeration Suppression Time..................................................................... |
310 |
9.3.5.3 |
Filters for Register Message from RP ............................................................. |
311 |
9.3.5.4 |
Source Address of Register Message ............................................................. |
311 |
9.3.5.5 |
Reachability for PIM Register Process........................................................... |
312 |
9.3.6 |
SPT Switchover .............................................................................................. |
312 |
9.3.7 |
PIM Join/Prune Interoperability ...................................................................... |
313 |
9.3.8 |
Cisco Router Interoperability .......................................................................... |
313 |
9.3.8.1 |
Checksum of Full PIM Register Message ...................................................... |
313 |
9.3.8.2 |
Candidate RP Message with Cisco BSR........................................................ |
314 |
9.3.8.3 |
Excluding GenID Option ................................................................................. |
314 |
9.3.9 |
PIM-SSM Group ............................................................................................. |
315 |
9.3.10 |
PIM Snooping ................................................................................................. |
315 |
9.3.11 |
Displaying PIM-SM Configuration................................................................... |
316 |
10 |
IP Routing Protocol......................................................................................... |
317 |
10.1 |
Border Gateway Protocol (BGP) .................................................................... |
317 |
14 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
10.1.1 |
Basic Configuration ......................................................................................... |
318 |
10.1.1.1 |
Configuration Type of BGP.............................................................................. |
318 |
10.1.1.2 |
Enabling BGP Routing..................................................................................... |
318 |
10.1.1.3 |
Disabling BGP Routing.................................................................................... |
319 |
10.1.2 |
Advanced Configuration .................................................................................. |
319 |
10.1.2.1 |
Summary of Path............................................................................................. |
320 |
10.1.2.2 |
Automatic Summarization of Path ................................................................... |
320 |
10.1.2.3 |
Multi-Exit Discriminator (MED) ........................................................................ |
321 |
10.1.2.4 |
Choosing Best Path......................................................................................... |
321 |
10.1.2.5 |
Graceful Restart .............................................................................................. |
323 |
10.1.3 |
IP Address Family............................................................................................ |
324 |
10.1.4 |
BGP Neighbor ................................................................................................. |
325 |
10.1.4.1 |
Default Route................................................................................................... |
325 |
10.1.4.2 |
Peer Group ...................................................................................................... |
325 |
10.1.4.3 |
Route Map ....................................................................................................... |
326 |
10.1.4.4 |
Force Shutdown .............................................................................................. |
326 |
10.1.5 |
BGP Session Reset......................................................................................... |
327 |
10.1.5.1 |
Session Reset of All Peers .............................................................................. |
327 |
10.1.5.2 |
Session Reset of Peers within Particular AS................................................... |
328 |
10.1.5.3 |
Session Reset of Specific Route ..................................................................... |
329 |
10.1.5.4 |
Session Reset of External Peer ...................................................................... |
329 |
10.1.5.5 |
Session Reset of Peer Group.......................................................................... |
330 |
10.1.6 |
Displaying and Managing BGP ....................................................................... |
331 |
10.2 |
Open Shortest Path First (OSPF).................................................................... |
333 |
10.2.1 |
Enabling OSPF................................................................................................ |
333 |
10.2.2 |
ABR Type Configuration .................................................................................. |
335 |
10.2.3 |
Compatibility Support ...................................................................................... |
335 |
10.2.4 |
OSPF Interface................................................................................................ |
335 |
10.2.4.1 |
Authentication Type ......................................................................................... |
336 |
10.2.4.2 |
Authentication Key........................................................................................... |
336 |
10.2.4.3 |
Interface Cost .................................................................................................. |
337 |
10.2.4.4 |
Blocking Transmission of Route Information Database .................................. |
338 |
10.2.4.5 |
Routing Protocol Interval ................................................................................. |
338 |
10.2.4.6 |
OSPF Maximum Transmission Unit (MTU) ..................................................... |
340 |
10.2.4.7 |
OSPF Priority................................................................................................... |
340 |
10.2.4.8 |
OSPF Network Type........................................................................................ |
341 |
10.2.5 |
Non-Broadcast Network .................................................................................. |
341 |
10.2.6 |
OSPF Area ...................................................................................................... |
342 |
10.2.6.1 |
Area Authentication ......................................................................................... |
342 |
10.2.6.2 |
Default Cost of Area ........................................................................................ |
343 |
10.2.6.3 |
Blocking the Transmission of Routing Information Between Area .................. |
343 |
10.2.6.4 |
Not So Stubby Area (NSSA)............................................................................ |
344 |
10.2.6.5 |
Area Range ..................................................................................................... |
346 |
10.2.6.6 |
Shortcut Area................................................................................................... |
346 |
10.2.6.7 |
Stub Area ......................................................................................................... |
347 |
10.2.6.8 |
Virtual Link....................................................................................................... |
347 |
10.2.7 |
Default Metric .................................................................................................. |
349 |
10.2.8 |
Graceful Restart Support................................................................................. |
349 |
10.2.9 |
Opaque-LSA Support ...................................................................................... |
351 |
10.2.10 |
Default Route................................................................................................... |
351 |
10.2.11 |
Finding Period ................................................................................................. |
352 |
A50010-Y3-C150-2-7619 |
15 |

UMN:CLI |
|
User Manual |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
10.2.12 |
External Routes to OSPF Network................................................................. |
353 |
10.2.13 |
OSPF Distance ............................................................................................... |
354 |
10.2.14 |
Host Route...................................................................................................... |
355 |
10.2.15 |
Passive Interface ............................................................................................ |
355 |
10.2.16 |
Blocking Routing Information.......................................................................... |
356 |
10.2.17 |
Summary Routing Information........................................................................ |
356 |
10.2.18 |
OSPF Monitoring and Management............................................................... |
356 |
10.2.18.1 |
Displaying OSPF Protocol Information........................................................... |
357 |
10.2.18.2 |
Displaying Debugging Information.................................................................. |
359 |
10.2.18.3 |
Limiting Number of Database ......................................................................... |
359 |
10.2.18.4 |
Maximum Process of LSA .............................................................................. |
360 |
10.3 |
Routing Information Protocol (RIP)................................................................. |
361 |
10.3.1 |
Enabling RIP................................................................................................... |
361 |
10.3.2 |
RIP Neighbor Router ...................................................................................... |
362 |
10.3.3 |
RIP Version..................................................................................................... |
363 |
10.3.4 |
Creating available Static Route only for RIP .................................................. |
364 |
10.3.5 |
Redistributing Routing Information ................................................................. |
364 |
10.3.6 |
Metrics for Redistributed Routes .................................................................... |
366 |
10.3.7 |
Administrative Distance .................................................................................. |
367 |
10.3.8 |
Originating Default Information....................................................................... |
367 |
10.3.9 |
Routing Information Filtering .......................................................................... |
367 |
10.3.9.1 |
Filtering Access List and Prefix List ................................................................ |
368 |
10.3.9.2 |
Disabling the transmission to Interface .......................................................... |
368 |
10.3.9.3 |
Offset List........................................................................................................ |
368 |
10.3.10 |
Maximum Number of RIP Routes................................................................... |
369 |
10.3.11 |
RIP Network Timer.......................................................................................... |
369 |
10.3.12 |
Split Horizon.................................................................................................... |
370 |
10.3.13 |
Authentication Key.......................................................................................... |
370 |
10.3.14 |
Restarting RIP ................................................................................................ |
371 |
10.3.15 |
UDP Buffer Size of RIP................................................................................... |
371 |
10.3.16 |
Monitoring and Managing RIP ........................................................................ |
372 |
11 |
System Software Upgrade.............................................................................. |
373 |
11.1 |
General Upgrade ............................................................................................ |
373 |
11.2 |
Boot Mode Upgrade ....................................................................................... |
374 |
11.3 |
FTP Upgrade .................................................................................................. |
377 |
12 |
Abbreviations .................................................................................................. |
379 |
16 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
Illustrations |
|
|
Fig. 2.1 |
Network Structure with hiD 6615 S223/S323................................................. |
23 |
Fig. 3.1 |
Software mode structure ................................................................................ |
28 |
Fig. 4.1 |
Process of 802.1x Authentication................................................................... |
64 |
Fig. 4.2 |
Multiple Authentication Servers...................................................................... |
65 |
Fig. 5.1 |
hiD 6615 S223/S323 Interface ....................................................................... |
73 |
Fig. 5.2 |
Port Mirroring.................................................................................................. |
81 |
Fig. 6.1 |
Ping Test for Network Status .......................................................................... |
97 |
Fig. 6.2 |
IP Source Routing .......................................................................................... |
97 |
Fig. 7.1 |
Weighted Round Robin ................................................................................ |
147 |
Fig. 7.2 |
Weighted Fair Queuing ................................................................................ |
148 |
Fig. 7.3 |
Strict Priority Queuing .................................................................................. |
148 |
Fig. 7.4 |
NetBIOS Filtering ......................................................................................... |
155 |
Fig. 8.1 |
Port-based VLAN ......................................................................................... |
179 |
Fig. 8.2 |
Example of QinQ Configuration ................................................................... |
184 |
Fig. 8.3 |
QinQ Frame.................................................................................................. |
184 |
Fig. 8.4 |
In Case Packets Going Outside in Layer 2 environment ............................. |
187 |
Fig. 8.5 |
In Case External Packets Enter under Layer 2 environment (1) ................. |
188 |
Fig. 8.6 |
In Case External Packets Enter under Layer 2 environment (2) ................. |
188 |
Fig. 8.7 |
Link Aggregation........................................................................................... |
193 |
Fig. 8.8 |
Example of Loop .......................................................................................... |
200 |
Fig. 8.9 |
Principle of Spanning Tree Protocol............................................................. |
200 |
Fig. 8.10 |
Root Switch .................................................................................................. |
201 |
Fig. 8.11 |
Designated Switch ....................................................................................... |
202 |
Fig. 8.12 |
Port Priority................................................................................................... |
203 |
Fig. 8.13 |
Port State...................................................................................................... |
204 |
Fig. 8.14 |
Alternate Port and Backup port .................................................................... |
205 |
Fig. 8.15 |
Example of Receiving Low BPDU................................................................ |
206 |
Fig. 8.16 |
Convergence of 802.1d Network.................................................................. |
207 |
Fig. 8.17 |
Network Convergence of 802.1w (1)............................................................ |
207 |
Fig. 8.18 |
Network Convergence of 802.1w (2)............................................................ |
208 |
Fig. 8.19 |
Network Convergece of 802.1w (3).............................................................. |
208 |
Fig. 8.20 |
Compatibility with 802.1d (1)........................................................................ |
209 |
Fig. 8.21 |
Compatibility with 802.1d (2)........................................................................ |
209 |
Fig. 8.22 |
CST and IST of MSTP (1) ............................................................................ |
210 |
Fig. 8.23 |
CST and IST of MSTP (2) ............................................................................ |
211 |
Fig. 8.24 |
Example of PVSTP....................................................................................... |
217 |
Fig. 8.25 |
Root Guard................................................................................................... |
219 |
Fig. 8.26 |
Example of Layer 2 Network Design in RSTP Environment........................ |
225 |
Fig. 8.27 |
Example of Layer 2 Network Design in MSTP Environment........................ |
226 |
Fig. 8.28 |
VRRP Operation........................................................................................... |
227 |
Fig. 8.29 |
VRRP Track.................................................................................................. |
232 |
Fig. 8.30 |
Rate Limit and Flood Guard ......................................................................... |
236 |
Fig. 8.31 |
DHCP Service Structure............................................................................... |
238 |
Fig. 8.32 |
Example of DHCP Relay Agent.................................................................... |
250 |
Fig. 8.33 |
DHCP Option 82 Operation.......................................................................... |
253 |
Fig. 8.34 |
DHCP Server Packet Filtering...................................................................... |
264 |
Fig. 8.35 |
Ethernet Ring Protocol Operation in Failure State ....................................... |
265 |
Fig. 8.36 |
Ring Protection............................................................................................. |
266 |
Fig. 8.37 |
Link Failure Recovery .................................................................................. |
266 |
A50010-Y3-C150-2-7619 |
17 |

UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
Fig. 8.38 |
Ring Recovery............................................................................................. |
267 |
Fig. 8.39 |
Example of Stacking.................................................................................... |
270 |
Fig. 9.1 |
IGMP Snooping Configuration Network ...................................................... |
278 |
Fig. 9.2 |
PIM-SM Configuration Network................................................................... |
278 |
Fig. 9.3 |
IGMP Snooping and PIM-SM Configuration Network ................................. |
279 |
Fig. 9.4 |
IP Multicasting ............................................................................................. |
290 |
Fig. 9.5 |
RPT of PIM-SM ........................................................................................... |
304 |
Fig. 9.6 |
STP of PIM-SM............................................................................................ |
304 |
Fig. 9.7 |
In Case Multicast Source not Directly Connected to Multicast Group ........ |
313 |
18 |
A50010-Y3-C150-2-7619 |

User Manual |
|
UMN:CLI |
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
Tables |
|
|
Tab. 1.1 |
Overview of Chapters..................................................................................... |
20 |
Tab. 1.2 |
Command Notation of Guide Book ................................................................ |
21 |
Tab. 3.1 |
Main Commands of Privileged EXEC View Mode ......................................... |
29 |
Tab. 3.2 |
Main Commands of Privileged EXEC Enable Mode...................................... |
29 |
Tab. 3.3 |
Main Commands of Global Configuration Mode ............................................ |
30 |
Tab. 3.4 |
Main Commands of Bridge Configuration Mode ............................................ |
31 |
Tab. 3.5 |
Main Commands of Rule Configuration Mode ............................................... |
31 |
Tab. 3.6 |
Main Commands of DHCP Configuration Mode ............................................ |
32 |
Tab. 3.7 |
Main Commands of DHCP Option 82 Configuration Mode............................ |
32 |
Tab. 3.8 |
Main Commands of Interface Configuration Mode ........................................ |
33 |
Tab. 3.9 |
Main Commands of RMON Configuration Mode ........................................... |
33 |
Tab. 3.10 |
Main Commands of Router Configuration Mode............................................ |
34 |
Tab. 3.11 |
Main Commands of VRRP Configuration Mode............................................. |
34 |
Tab. 3.12 |
Main Commands of Route-map Configuration Mode..................................... |
35 |
Tab. 3.13 |
Command Abbreviation.................................................................................. |
38 |
Tab. 6.1 |
World Time Zone ............................................................................................ |
84 |
Tab. 6.2 |
Options for Ping.............................................................................................. |
95 |
Tab. 6.3 |
Options for Ping for Multiple IP Addresses..................................................... |
96 |
Tab. 6.4 |
Options for Tracing Packet Route .................................................................. |
98 |
Tab. 7.1 |
Default 802.1p Priory-to-queue Map............................................................ |
149 |
Tab. 7.2 |
ICMP Message Type .................................................................................... |
170 |
Tab. 7.3 |
Mask Calculation of Default Value ............................................................... |
171 |
Tab. 7.4 |
Options for Packet Dump ............................................................................. |
176 |
Tab. 8.1 |
Advantages and Disadvantages of Tagged VLAN ....................................... |
183 |
Tab. 8.2 |
STP Path-cost .............................................................................................. |
213 |
Tab. 8.3 |
RSTP Path-cost............................................................................................ |
213 |
A50010-Y3-C150-2-7619 |
19 |
UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
1 Introduction
1.1Audience
This manual is intended for SURPASS hiD 6615 S223/S323 single-board Fast Ethernet switch operators and maintenance personnel for providers of Ethernet services. This manual assumes that you are familiar with the following:
•Ethernet networking technology and standards
•Internet topologies and protocols
•Usage and functions of graphical user interfaces.
1.2Document Structure
Tab. 1.1 briefly describes the structure of this document.
|
Chapter |
Description |
|
|
|
|
|
1 |
Introduction |
Introduces the overall information of the document. |
|
|
|
|
|
2 |
System Overview |
Introduces the hiD 6615 S223/S323 system. It also lists the features |
|
of the system. |
|||
|
|
||
|
|
|
|
3 |
Command Line Interface (CLI) |
Describes how to use the Command Line Interface (CLI). |
|
|
|
|
|
4 |
System Connection and IP Address |
Describes how to manage the system account and IP address. |
|
|
|
|
|
5 |
Port Configuration |
Describes how to configure the Ethernet ports. |
|
|
|
|
|
6 |
System Environment |
Describes how to configure the system environment and manage- |
|
ment functions. |
|||
|
|
||
|
|
|
|
7 |
Network Management |
Describes how to configure the network management functions. |
|
|
|
|
|
8 |
System Main Functions |
Describes how to configure the system main functions. |
|
|
|
|
|
9 |
IP Multicast. |
Describes how to configure the IP multicast packets. |
|
|
|
||
10 IP Routing Protocol. |
Describes how to configure IP routing protocol. |
||
|
|
|
|
12 Abbreviations |
Lists all abbreviations and acronyms which appear in this docu- |
||
ment. |
|||
|
|
||
|
|
|
|
Tab. 1.1 Overview of Chapters
20 |
A50010-Y3-C150-2-7619 |
User Manual |
UMN:CLI |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
|
1.3Document Convention
This guide uses the following conventions to convey instructions and information.
|
Information |
|
|
This information symbol provides useful information when using commands to configure |
|
i |
||
and means reader take note. Notes contain helpful suggestions or references. |
||
|
Warning |
|
|
This warning symbol means danger. You are in a situation that could cause bodily injury |
!or broke the equipment. Before you work on any equipment, be aware of the hazards involved with electrical circuitry and be familiar with standard practices for preventing accidents by making quick guide based on this guide.
1.4Document Notation
The following table shows commands used in guide book. Please be aware of each command to use them correctly.
Notation |
Description |
|
|
|
|
a |
Commands you should use as is. |
|
|
|
|
NAME, PROFILE, VALUE, … |
Variables for which you supply values. |
|
|
|
|
PORTS |
For entry this variable, see Section 5.1. |
|
|
|
|
[ ] |
Commands or variables that appear within square brackets [ ] are |
|
optional. |
||
|
||
|
|
|
< > |
Range of number that you can use. |
|
|
|
|
{ } |
A choice of required keywords appears in braces { }. You must se- |
|
lect one. |
||
|
||
|
|
|
| |
Optional variables are separated by vertical bars |. |
|
|
|
Tab. 1.2 Command Notation of Guide Book
1.5CE Declaration of Conformity
The CE declaration of the product will be fulfilled if the construction and cabling is undertaken in accordance with the manual and the documents listed there in, e.g. mounting instructions, cable lists where necessary account should be taken of project-specific documents.
Deviations from the specifications or unstipulated changes during construction, e.g. the use of cable types with lower screening values can lead to violation of the CE requirements. In such case the conformity declaration is invalidated and the responsibility passes to those who have caused the deviations.
A50010-Y3-C150-2-7619 |
21 |
UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
1.6GPL/LGPL Warranty and Liability Exclusion
The Siemens product, SURPASS hiD 6615, contains both proprietary software and “Open Source Software”. The Open Source Software is licensed to you at no charge under the GNU General Public License (GPL) and the GNU Lesser General Public License (LGPL). This Open Source Software was written by third parties and enjoys copyright protection. You are entitled to use this Open Source Software under the conditions set out in the GPL and LGPL licenses indicated above. In the event of conflicts between Siemens license conditions and the GPL or LGPL license conditions, the GPL and LGPL conditions shall prevail with respect to the Open Source portions of the software.
The GPL can be found under the following URL:
http://www.gnu.org/copyleft/gpl.html
The LGPL can be found under the following URL:
http://www.gnu.org/copyleft/lgpl.html
In addition, if the source code to the Open Source Software has not been delivered with this product, you may obtain the source code (including the related copyright notices) by sending your request to the following e-mail address: opensrc@dasannetworks.com You will, however, be required to reimburse Siemens for its costs of postage and copying.
Any source code request made by you must be sent within 3 years of your purchase of the product. Please include a copy of your sales receipt when submitting your request. Also please include the exact name and number of the device and the version number of the installed software.
The use of Open Source Software contained in this product in any manner other than the simple running of the program occurs at your own risk, that is, without any warranty claims against Siemens. For more information about the warranties provided by the authors of the Open Source Software contained in this product, please consult the GPL and LGPL.
You have no warranty claims against Siemens when a defect in the product is or couldhave been caused by changes made by you in any part of the software or its configuration. In addition, you have no warranty claims against Siemens when the Open Source Software infringes the intellectual property rights of a third party.
Siemens provides no technical support for either the software or the Open Source Software contained therein if either has been changed.
22 |
A50010-Y3-C150-2-7619 |
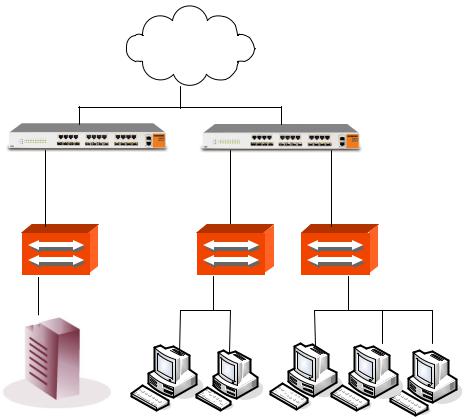
User Manual |
UMN:CLI |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
|
2 System Overview
SURPASS hiD 6615 L3 switch is typical Layer 3 switch intended to construct large-scale network, which provides aggregated function of upgraded LAN network consisted of typical Ethernet switch. Layer 3 switch can connect to PC, web server, LAN equip-ment, backbone equipment, or another switch through various interfaces.
SURPASS hiD 6615 L3 switch supports routing based on VLAN, IP multicasting, and provides Layer 3 switching service such as IP packet filtering or DHCP.
The Fig. 2.1 shows network construction with using hiD 6615 S223/S323.
Fig. 2.1 Network Structure with hiD 6615 S223/S323
A50010-Y3-C150-2-7619 |
23 |
UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
2.1System Features
Main features of hiD 6615 S223/S323, having Fast Ethernet switch and Layer 3 switching function which supports both Ethernet switching and IP routing, are follow.
Routing functionalities such as RIP, OSPF, BGP and PIM-SM are only available for hiD
!6615 S323. (Unavailable for hiD 6615 S223)
VLAN
Virtual Local Area Network (VLAN) is made by dividing one network into several logical networks. Packet can not be transmitted and received between different VLANs. Therefore it can prevent unnecessary packets accumulating and strengthen security. The hiD 6615 S223/S323 recognizes 802.1q tagged frame and supports maximum 4096 VLANs and Port based, Protocol based, MAC based VLANs.
Quality of Service (QoS)
For the hiD 6615 S223/S323, QoS-based forwarding sorts traffic into a number of classes and marks the packets accordingly. Thus, different quality of service is providing to each class, which the packets belong to. The QoS capabilities enable network managers to protect mission-critical applications and support differentiated level of bandwidth for managing traffic congestion. The hiD 6615 S223/S323 support ingress and egress (shaping) rate limiting, and different scheduling type such as SP (Strict Priority), WRR (Weighted Round Robin) and WFQ (Weighted Fair Queuing).
Multicasting
Because broadcasting in a LAN is restricted if possible, multicasting could be used instead of broadcasting by forwarding multicast packets only to the member hosts who joined multicast group. The hiD 6615 S223/S323 provides IGMP V2, IGMP snooping and PIM-SM for host membership management and multicast routing.
SNMP
Simple Network Management Protocol (SNMP) is to manage Network Elements using TCP/IP protocol. The hiD 6615 S223/S323 supports SNMP version 1, 2, 3 and Remote Monitoring (RMON). Network operator can use MIB also to monitor and manage the hiD 6615 S223/S323.
IP Routing
The hiD 6615 S323 is Layer 3 switch, which has routing table and IP address as router. Therefore, it supports static routing, RIP v1/v2, OSPF v2 and BGP v4 for unicast routing.
24 |
A50010-Y3-C150-2-7619 |
User Manual |
UMN:CLI |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
|
DHCP
The hiD 6615 S223/S323 supports DHCP (Dynamic Host Control Protocol) Server that automatically assigns IP address to clients accessed to network. That means it has IP address pool, and operator can effectively utilize limited IP source by leasing temporary IP address. In layer 3 network, DHCP request packet can be sent to DHCP server via DHCP relay and Option 82 function.
Spanning Tree Protocol (STP)
To prevent loop and preserve backup route in layer 2 network, the hiD 6615 S223/S323 supports STP (802.1D). Between STP enabled switches, a root bridge is automatically selected and the network remains in tree topology. But the recovery time in STP is very slow (about 30 seconds), RSTP (Rapid Spanning Tree Protocol) is also provided. IEEE 802.1W defines the recovery time as 2 seconds. If there is only one VLAN in the network, traditional STP works. However, in more than one VLAN network, STP cannot work per VLAN. To avoid this problem, the hiD 6615 S223/S323 supports Multiple Spanning Tree Protocol (MSTP).
Link Aggregation (Trunking)
The hiD 6615 S223/S323 aggregates several physical interfaces into one logical port (aggregate port). Port trunk aggregates interfaces with the standard of same speed, same duplex mode, and same VLAN ID. According to IEEE 802.3ad, the hiD 6615 S223/S323 can configure maximum 8 aggregate ports and up to 12 trunk groups.
LACP
The hiD 6615 S223/S323 supports Link Aggregation Control Protocol (LACP), complying with IEEE 802.3ad, which aggregates multiple links of equipments to use more enlarged bandwidth.
System Management based on CLI
It is easy for users who administer system by using telnet or console port to configure the functions for system operating through CLI. CLI is easy to configure the needed functions after looking for available commands by help menu different with UNIX.
Broadcast Storm Control
Broadcast storm control is, when too much of broadcast packets are being transmitted to network, a situation of network timeout because the packets occupy most of transmit capacity. The hiD 6615 S223/S323 supports broadcast and multicast storm control, which disuses flooding packet, that exceed the limit during the time configured by user.
A50010-Y3-C150-2-7619 |
25 |
UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
RADIUS and TACACS+
hiD 6615 S223/S323 supports client authentication protocol, that is RADIUS(Remote Authentication Dial-In User Service) and TACACS+(Terminal Access Controller Access Control System Plus). Not only user IP and password registered in switch but also authentication through RADIUS server and TACACS+ server are required to access. Therefore, security of system and network management is strengthened.
26 |
A50010-Y3-C150-2-7619 |
User Manual |
UMN:CLI |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
|
3 Command Line Interface (CLI)
This chapter describes how to use the Command Line Interface (CLI) which is used to configure the hiD 6615 S223/S323 system.
•Command Mode
•Useful Tips
3.1Command Mode
You can configure and manage the hiD 6615 S223/S323 by console terminal that is installed on user’s PC. For this, use the CLI-based interface commands. Connect RJ45-to- DB9 console cable to the hiD 6615 S223/S323.
This chapter explains how CLI command mode is organized before installing. CLI command mode is consisted as follow:
•Privileged EXEC View Mode
•Privileged EXEC Enable Mode
•Global Configuration Mode
•Bridge Configuration Mode
•Rule Configuration Mode
•DHCP Configuration Mode
•DHCP Option 82 Configuration Mode
•Interface Configuration Mode
•RMON Configuration Mode
•Router Configuration Mode
•VRRP Configuration Mode
•Route-Map Configuration Mode
A50010-Y3-C150-2-7619 |
27 |
UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
Fig. 3.1 shows hiD 6615 S323 software mode structure briefly.
Fig. 3.1 Software mode structure
28 |
A50010-Y3-C150-2-7619 |

User Manual |
UMN:CLI |
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
|
3.1.1Privileged EXEC View Mode
When you log in to the switch, the CLI will start with Privileged EXEC View mode that is a read-only mode. In this mode, you can see a system configuration and information with several commands.
Tab. 3.1 shows main command of Privileged EXEC View mode.
Command |
Description |
|
|
enable |
Opens Privileged EXEC Enable mode. |
|
|
exit |
Logs out the switch. |
|
|
show |
Shows a system configuration and information. |
|
|
Tab. 3.1 Main Commands of Privileged EXEC View Mode
3.1.2Privileged EXEC Enable Mode
To configure the switch, you need to open Privileged EXEC Enable mode with the enable command, then the system prompt will changes from SWITCH> to SWITCH#.
Command |
Mode |
Description |
|
|
|
enable |
View |
Opens Privileged EXEC Enable mode. |
|
|
|
You can set a password to Privileged EXEC Enable mode to enhance security. Once setting a password, you should enter a configured password, when you open Privileged EXEC Enable mode.
Tab. 3.2 shows main commands of Privileged EXEC Enable mode.
Command |
Description |
|
|
clock |
Inputs time and date in system. |
|
|
configure terminal |
Opens Configuration mode. |
|
|
telnet |
Connects to another device through telnet. |
|
|
terminal length |
Configures the number of lines to be displayed in screen. |
|
|
traceroute |
Traces transmission path of packet. |
|
|
where |
Finds users accessed to system through telnet. |
|
|
Tab. 3.2 Main Commands of Privileged EXEC Enable Mode
3.1.3Global Configuration Mode
In Global Configuration mode, you can configure general functions of the system. You can also open another configuration mode from this mode.
To open Global Configuration mode, enter the configure terminal command, and then the system prompt will be changed from SWITCH# to SWITCH(config)#.
Command |
Mode |
Description |
|
|
|
|
|
configure terminal |
Enable |
Opens Global Configuration mode from Privileged |
|
EXEC Enable mode. |
|||
|
|
||
|
|
|
A50010-Y3-C150-2-7619 |
29 |
UMN:CLI |
User Manual |
|
|
SURPASS hiD 6615 S223/S323 R1.5 |
|
|
|
|
Tab. 3.3 shows a couple of important main commands of Global Configuration mode.
Command |
Description |
|
|
access-list |
Configures policy to limit routing information on the standard of AS. |
|
|
arp |
Registers IP address and MAC address in ARP table. |
|
|
bgp |
Helps BGP configuration. |
|
|
bridge |
Opens Bridge Configuration mode. |
|
|
copy |
Makes a backup file for the configuration of the switch. |
|
|
dot1x |
Configures various functions of 802.1x daemon. |
|
|
end |
Closes current mode and returns to User EXEC mode. |
|
|
exit |
Closes current mode and returns to previous mode. |
|
|
hostname |
Changes host name of the switch. |
|
|
exec-timeout |
Configures auto-logout function. |
|
|
fan |
Configures fan operation |
|
|
interface |
Opens Interface Configuration mode. |
|
|
ip |
Configures various functions of the interface. |
|
|
passwd |
Changes a system password. |
|
|
qos |
Configures QoS. |
|
|
restore factory-defaults |
Restores the default configuration of the switch. |
|
|
rmon-alarm |
Opens Rmon-alarm configuration mode. |
|
|
rmon-event |
Opens Rmon-event configuration mode. |
|
|
rmon-history |
Opens Rmon-history configuration mode. |
|
|
route-map |
Opens Route-map Configuration mode. |
|
|
router |
Opens Router Configuration mode.(OSPF. RIP, VRRP, PIM, BGP) |
|
|
snmp |
Configures SNMP. |
|
|
sntp |
Configures SNTP |
|
|
syslog |
Configures syslog. |
|
|
time-zone |
Configures time zone. |
|
|
Tab. 3.3 Main Commands of Global Configuration Mode
3.1.4Bridge Configuration Mode
In Bridge Configuration mode, you can configure various Layer 2 functions such as VLAN, STP, LACP, EFM OAM, etc.
To open Bridge Configuration mode, enter the bridge command, then the system prompt will be changed from SWITCH(config)# to SWITCH(bridge)#.
Command |
Mode |
Description |
|
|
|
bridge |
Global |
Opens Bridge Configuration mode. |
|
|
|
30 |
A50010-Y3-C150-2-7619 |
 Loading...
Loading...